Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41results about How to "Troubleshoot authentication issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
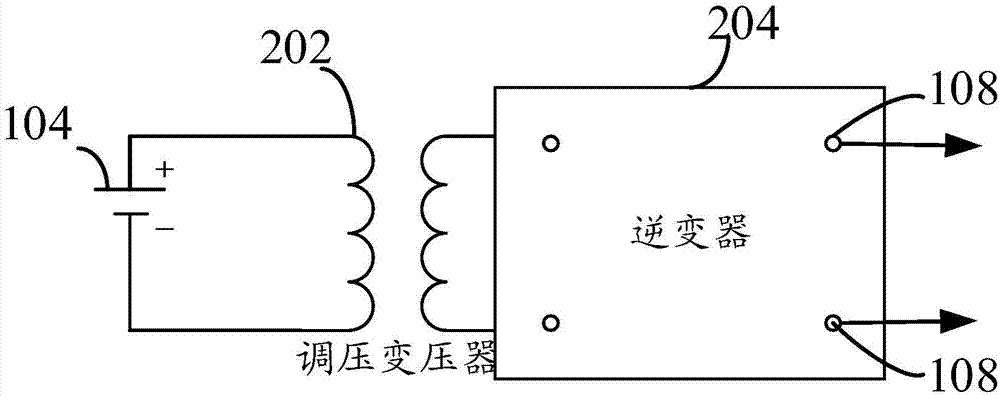
Cross-trust-domain identity authentication method
ActiveCN104378210AImplement single sign-onSimplify the identity development processUser identity/authority verificationPasswordService provision
Owner:成都卫士通信息安全技术有限公司
Method and system for dynamically authenticating password by multi-password seed self-defined by user
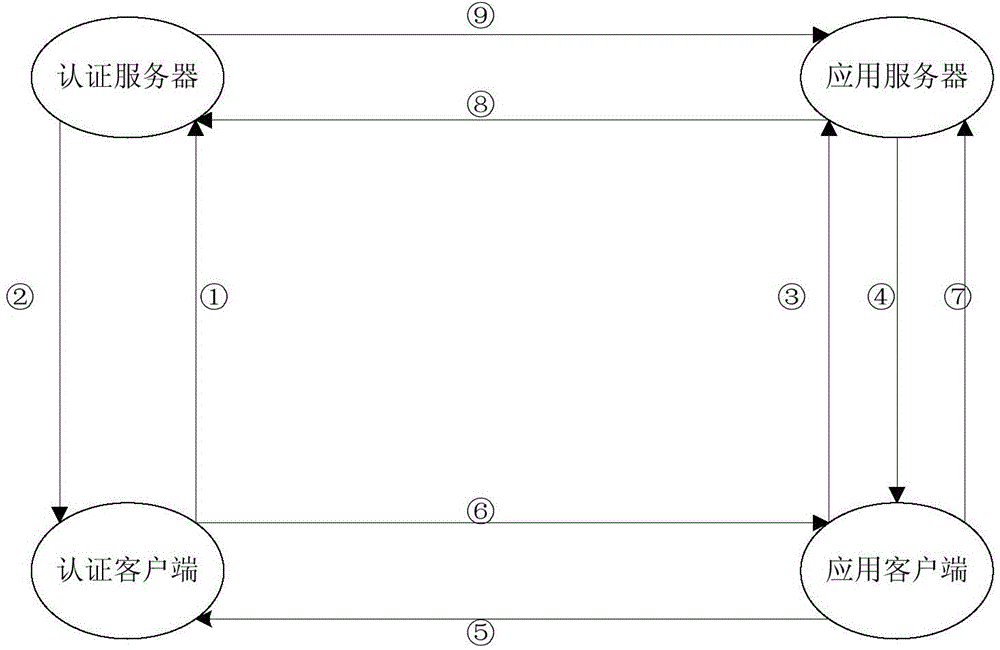
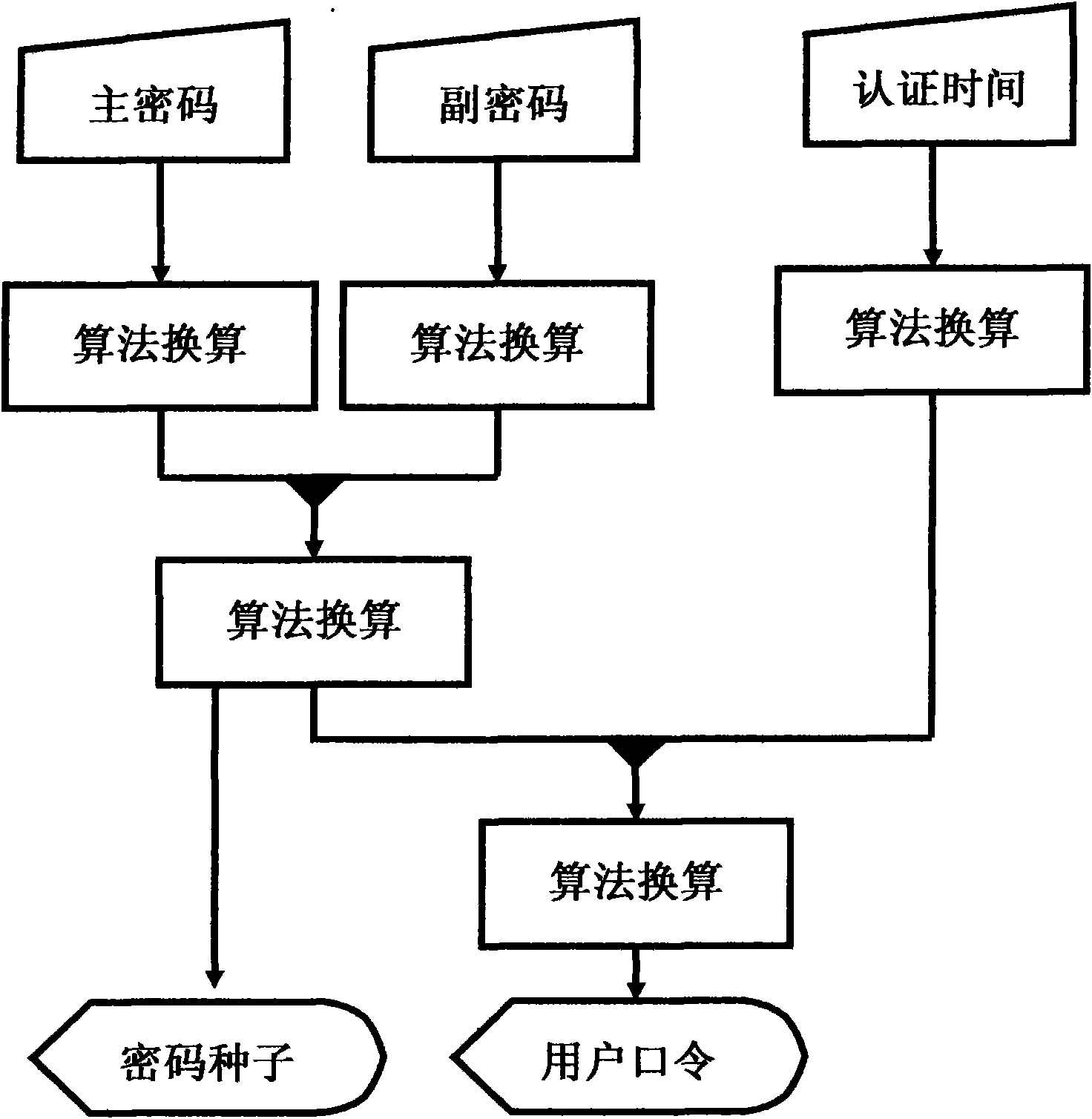
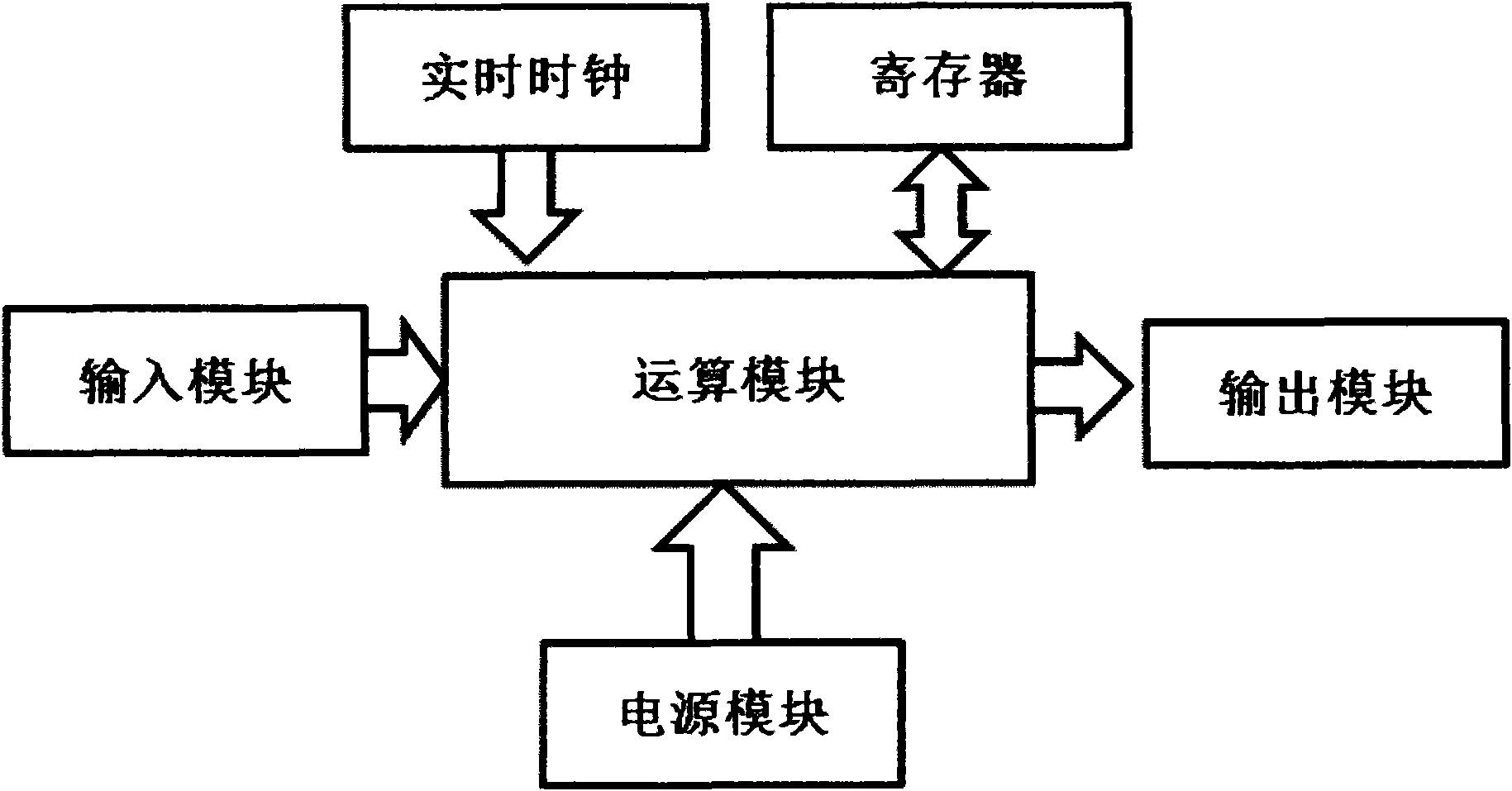
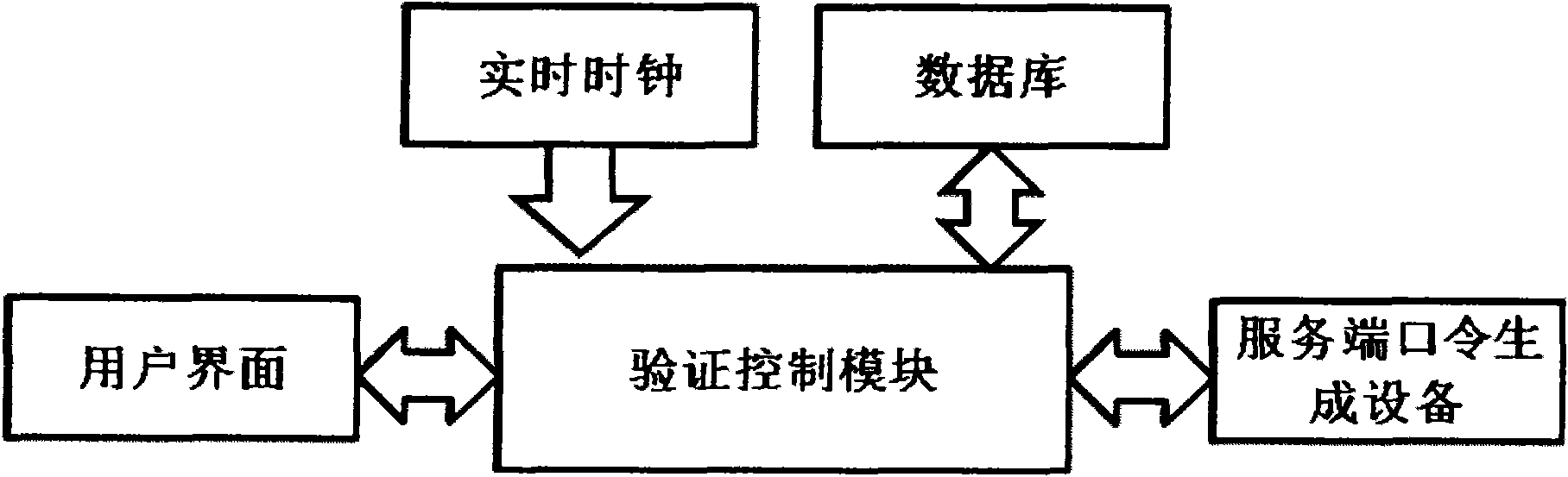
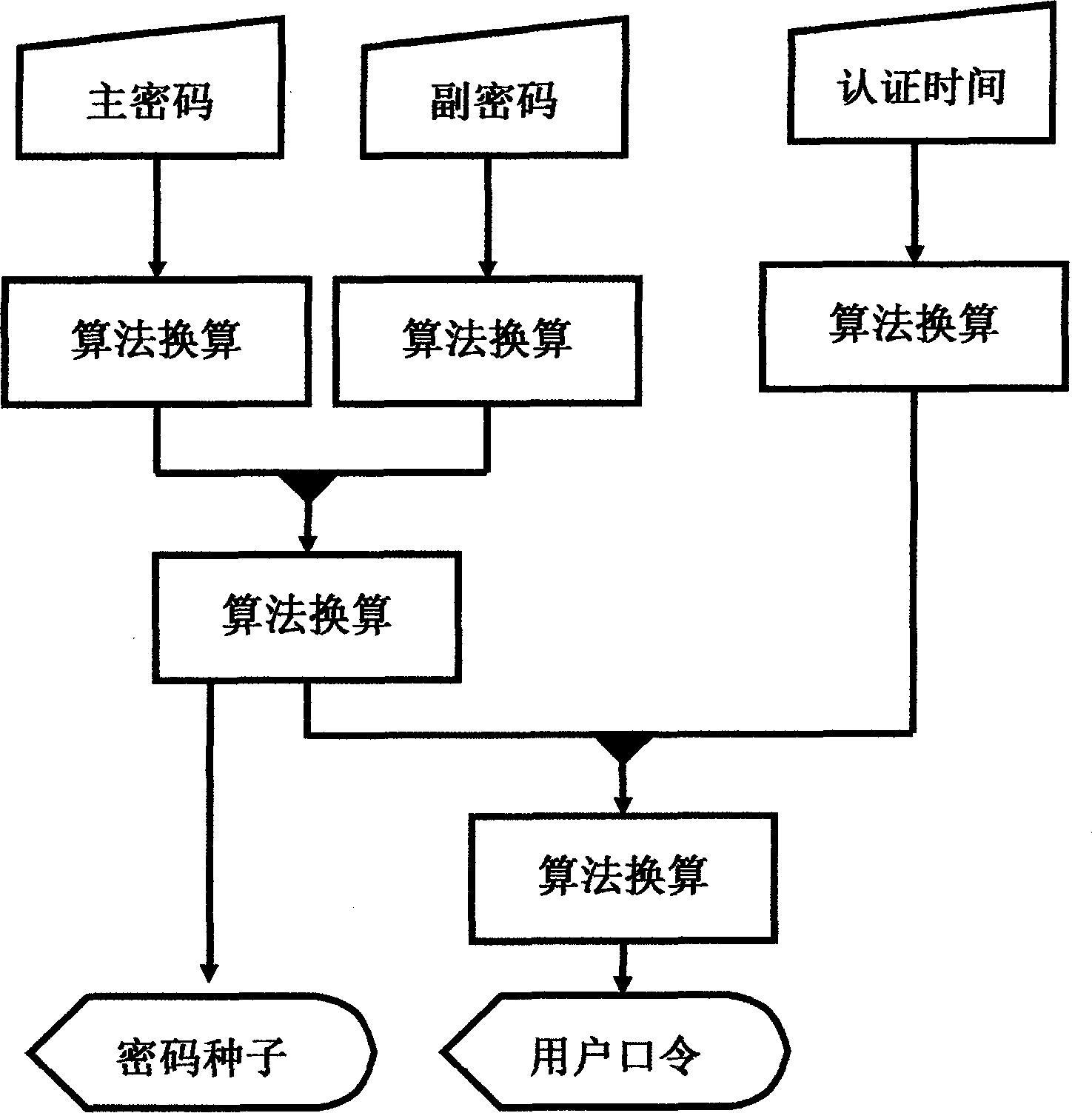
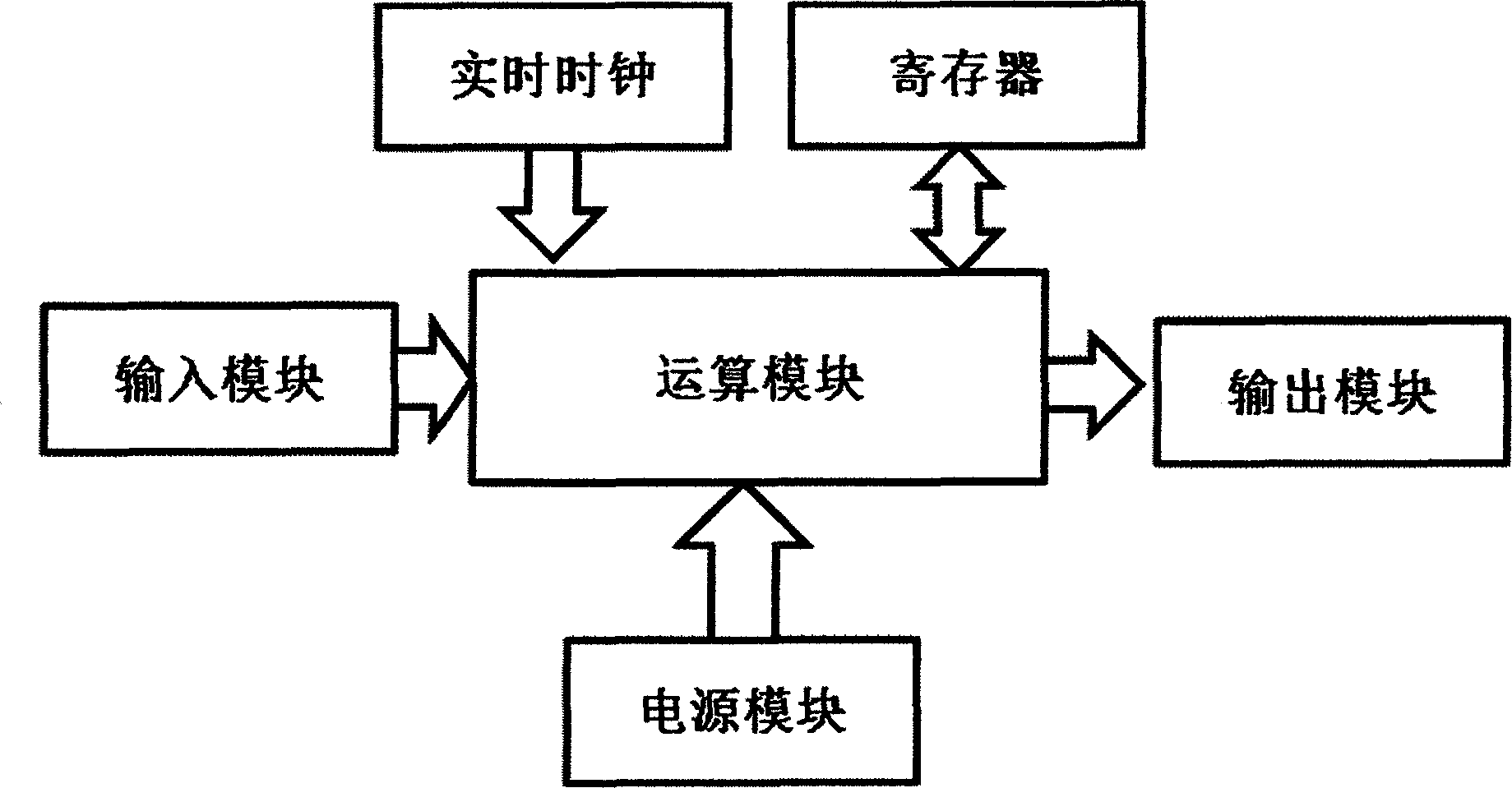
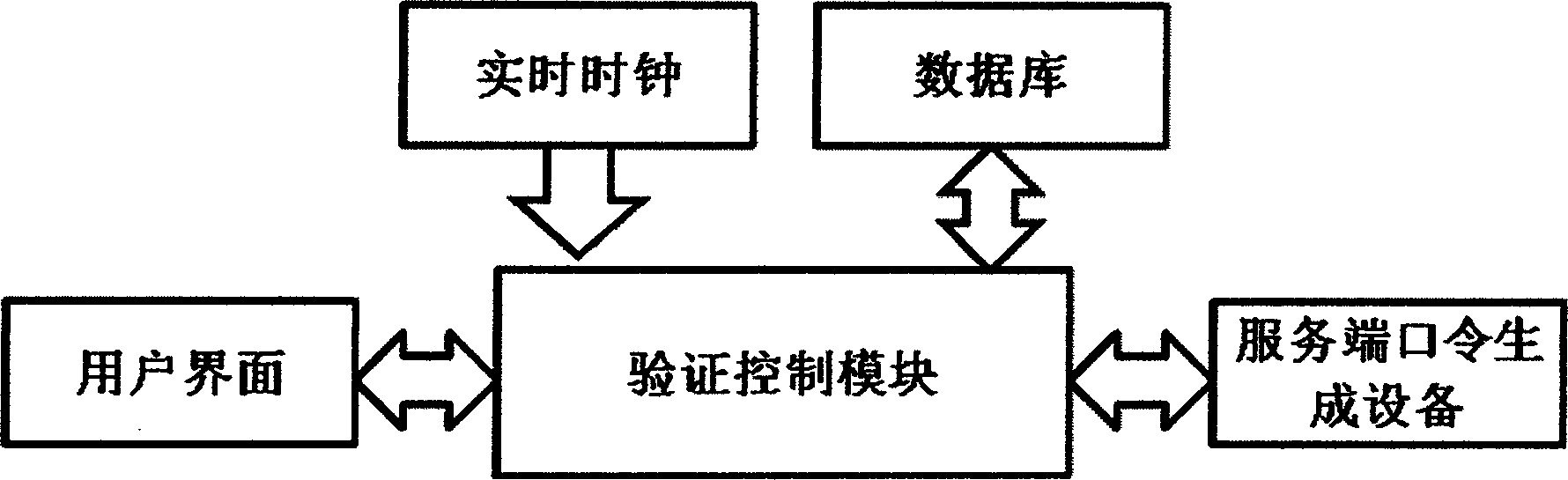
InactiveCN102148685ATroubleshoot authentication issuesMultiple keys/algorithms usageUser identity/authority verificationReal-time clockPassword
The invention aims to disclose a system for dynamically authenticating a password by a multi-password seed self-defined by a user. The method and the system are implemented by user equipment, a server system, server password generation equipment, a registration method and an authentication method. A user inputs a primary password and a secondary password at the user equipment, performs conversion to obtain a password seed, and submits the password seed to a server for registration and binding. When authentication is required, the server obtains a current authentication time by a real time clock, displays the current authentication time on a user interface, and can obtain a current server password of the user by the password seed submitted in the registration of the user and the authentication time. The user inputs the primary and secondary passwords at the user equipment, the server displays the current authentication time, and the conversion is performed to obtain a user password. The user password is judged whether to be consistent with the server password by comparison, and then a user operation can be verified whether to be legal or not. By the authentication method and the authentication system, all authentication needs of online authentication, offline authentication and the like can be satisfied. By the method provided by the invention, not only the absolute privacy of password information set by the user can be ensured, but also the problem of middleman breach of confidence which cannot be solved by a conventional dynamic password system is solved; and when using a multi-authentication server, the user is not required to buy and carry a plurality of pieces of user dynamic password equipment, so the user cost is reduced.
Owner:陈祖石
Encryption method applied to MQTT-SN protocol
InactiveCN107708112AImplement encryptionAchieve authenticationNetwork topologiesTransmissionComputer hardwarePlaintext
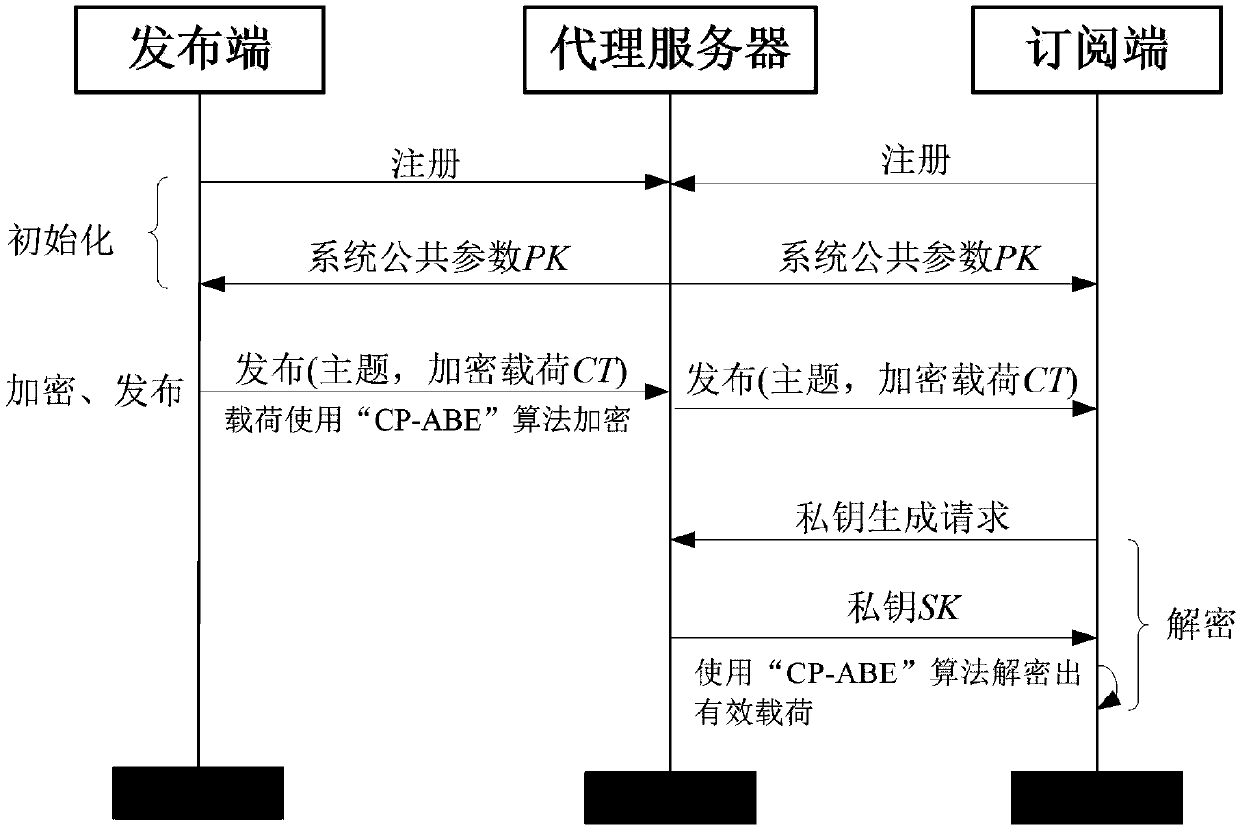
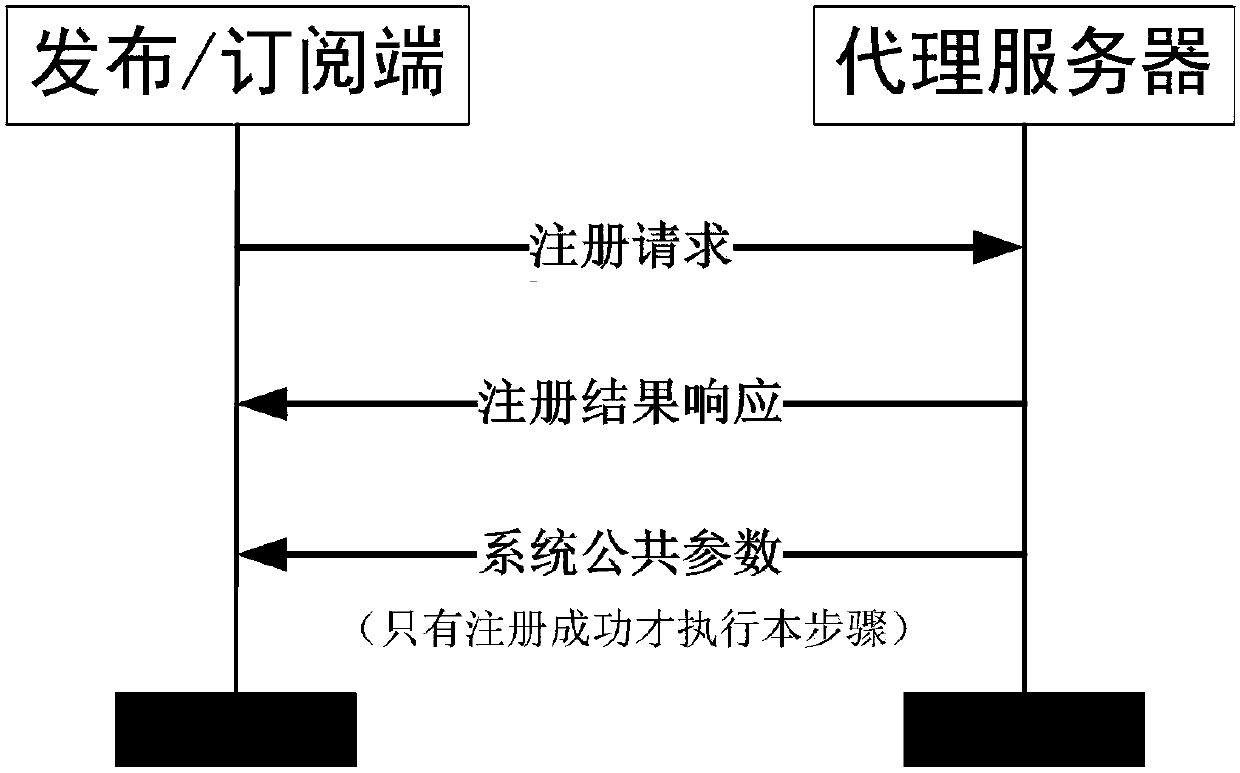
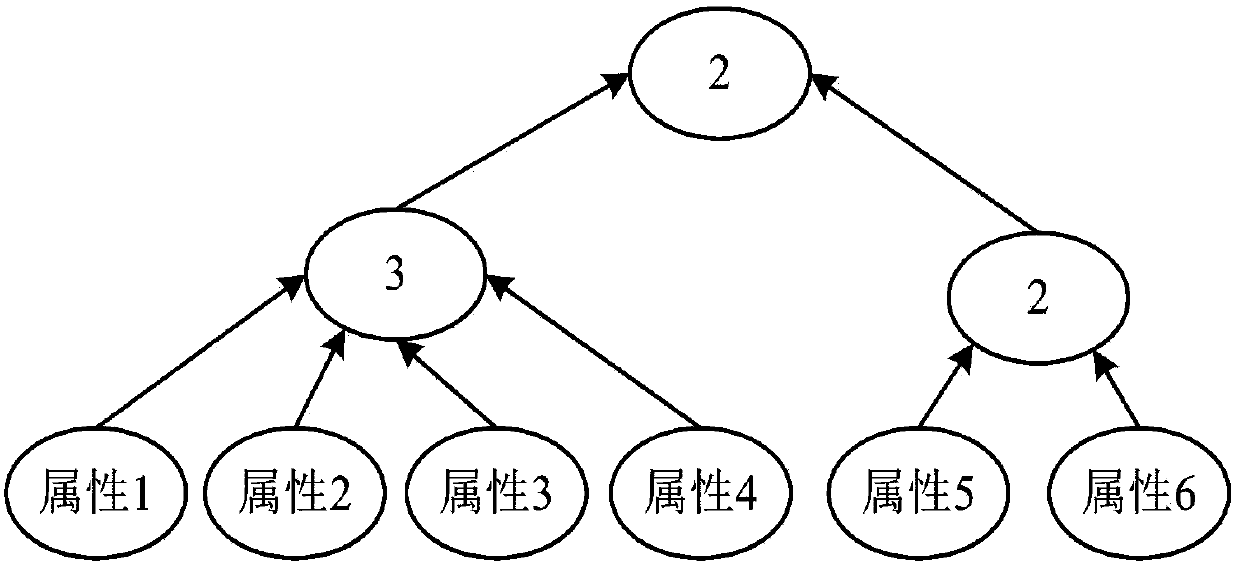
The invention relates to an encryption method applied to a MQTT-SN protocol, and relates to the field of communication. The method employs a harsh algorithm and ciphertext-policy attribute-based encryption method, so that a publishing terminal, an agent server and one or a plurality of subscription terminals can complete encrypted communication. The method herein includes the following steps: an agent server verifying the identity of a publishing / subscription terminal, performing registration of the publishing / subscription terminal, and generating a system common parameter; the publishing terminal encrypting a plaintext load by using the ciphertext-policy attribute-based encryption method; the publishing terminal transmitting the encrypted load to the agent server, the agent server forwarding the encrypted load to one or a plurality of subscription terminals; and the subscription terminal applying for a secrete key from the agent server, decrypting the encrypted load, obtaining a plaintext. According to the invention, the method can implement identity verification of a MQTT-SN protocol publishing / subscription terminal, data integrity verification, and data confidentiality protection, and better addresses the safety issues faced by the MQTT-SN protocol in terminals of wireless sensor network applications.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Access authentication method of terminals and access gateway
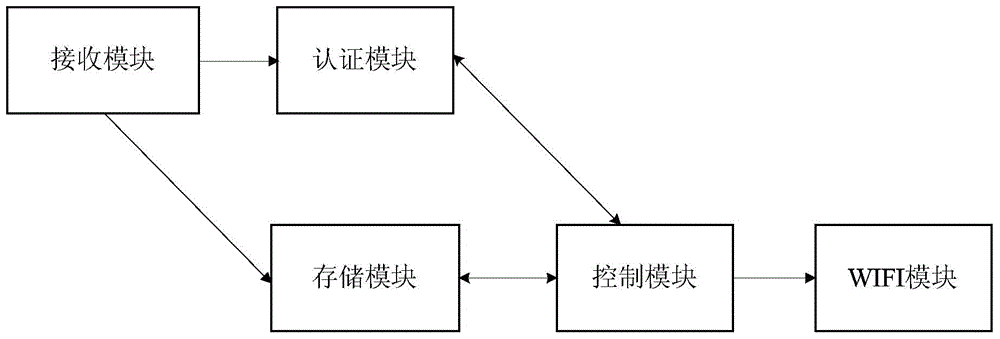
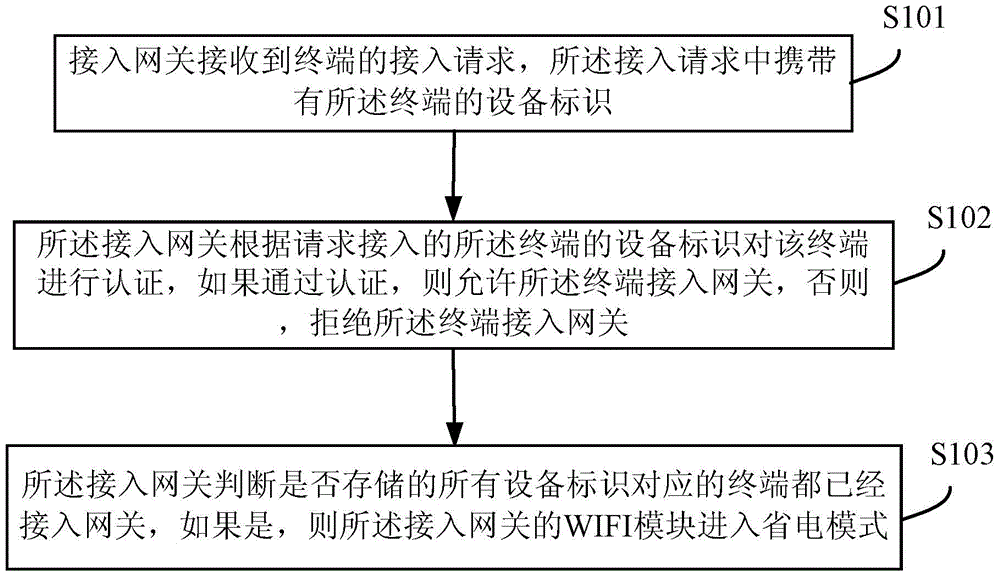
InactiveCN103987042ATroubleshoot authentication issuesReduce power consumptionEnergy efficient ICTSecurity arrangementAuthenticationPower consumption
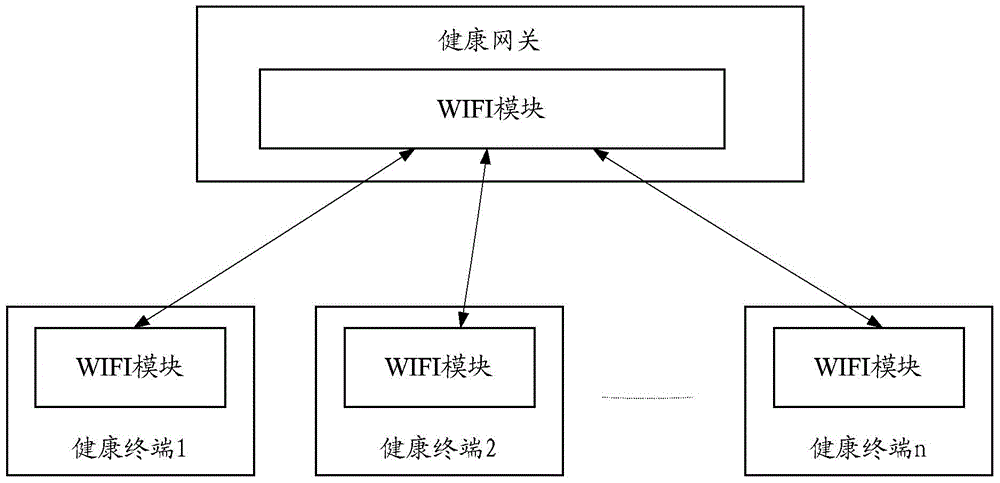
The invention discloses an access authentication method of terminals and an access gateway. The method includes the steps that an access request of each terminal is received by the access gateway, and each access request carries equipment identification of the corresponding terminal; authentication is conducted on each terminal according to the equipment identification of the terminal requiring for access by the access gateway; if the authentication is successful, the corresponding terminal is permitted to have access to the gateway, and if the authentication is not successful, the corresponding terminal is not permitted to have access to the gateway; whether the terminals corresponding to all the stored equipment identification have access to the gateway or not is judged by the access gateway, and if yes, a WIFI module of the access gateway enters a power saving module. According to the access authentication method of terminals and the access gateway, equipment identities of terminals are used as authentication identities, the authentication problem of the terminals is solved through simple operation, power consumption of the gateway is reduced, the service life of a battery of the gateway is prolonged, and operation complexity is greatly reduced as for the terminals.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Safety certification device and method for user identity based on far and near field data interaction
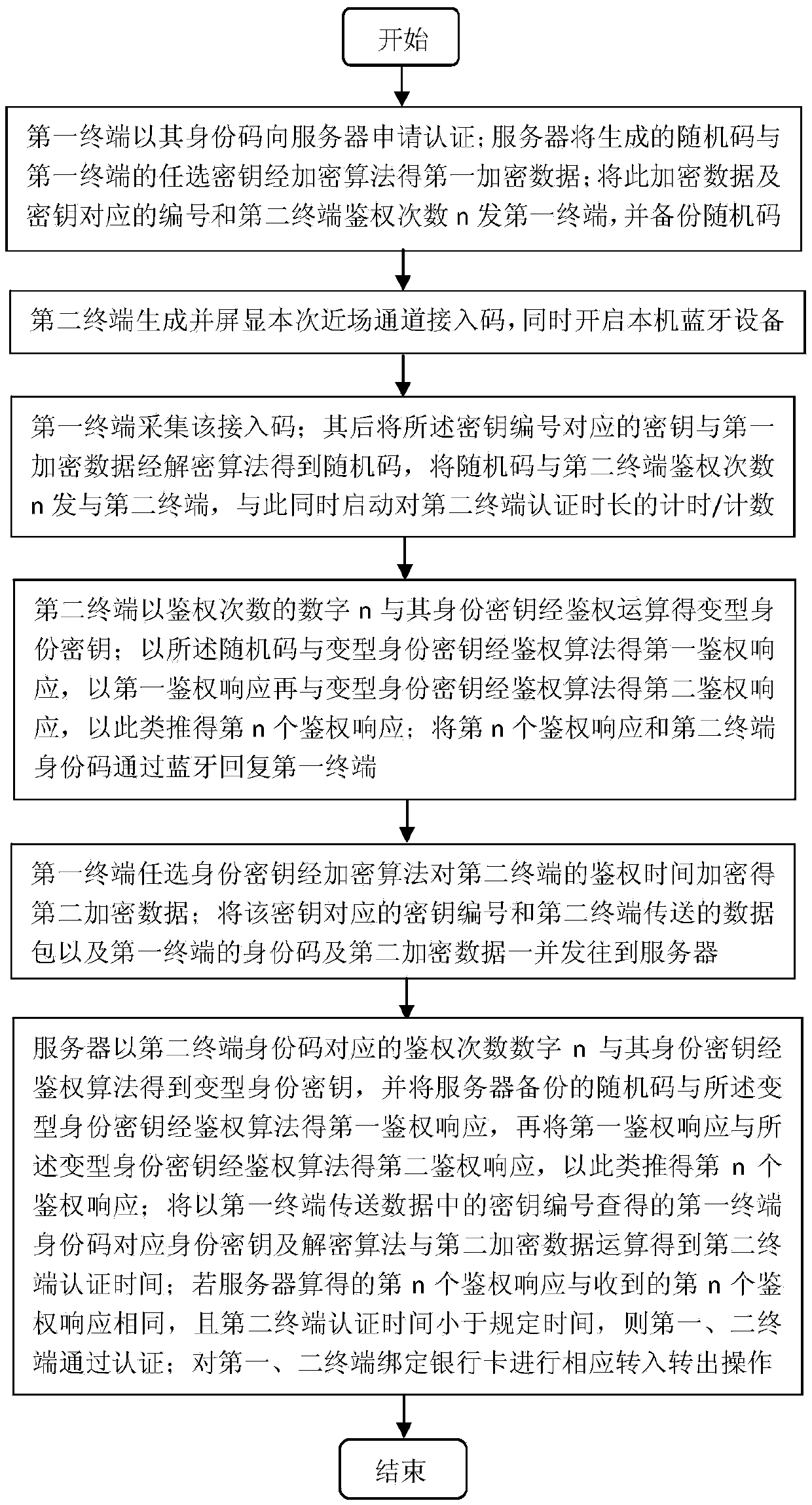
InactiveCN105373919ATroubleshoot authentication issuesReduce threatPoint-of-sale network systemsProtocol authorisationCarrier signalField data
The invention provides a safety certification device and method for the user identity based on far and near field data interaction, relates to the field of long and short range communication and data safety, and aims at solving the problem that the safety of long and short range data interaction is hard to ensure in the prior art; and the method can realize mobile payment, roaming free with virtual number and multi-number multi-channel network speed improvement via user identity based safety identification. A Micro-sd or U / SIM card integrated with certification function of the system is replaced to enhance the resistance to Trojan of a mobile phone and enable the intelligent mobile phone to serve as POS comprehensively; in near-field payment, a system server issues certification data to the mobile phone POS, the mobile phone POS transfers time-limited feedback certification data to the paying mobile phone, and the identity certification passes when returned data is the same with data of the server; in remote payment, the system carries out twice identification on the identity codes of user to prevent user data from being stolen remotely; and a set of safety guarantee flow for remote virtual number authentication is provided, so that roaming-free application of the virtual number and the network speed improvement of multiple virtual numbers and multiple carrier waves are realized.
Owner:熊文俊
Simulation platform and method based on IEEE802.1X security protocol of EAP
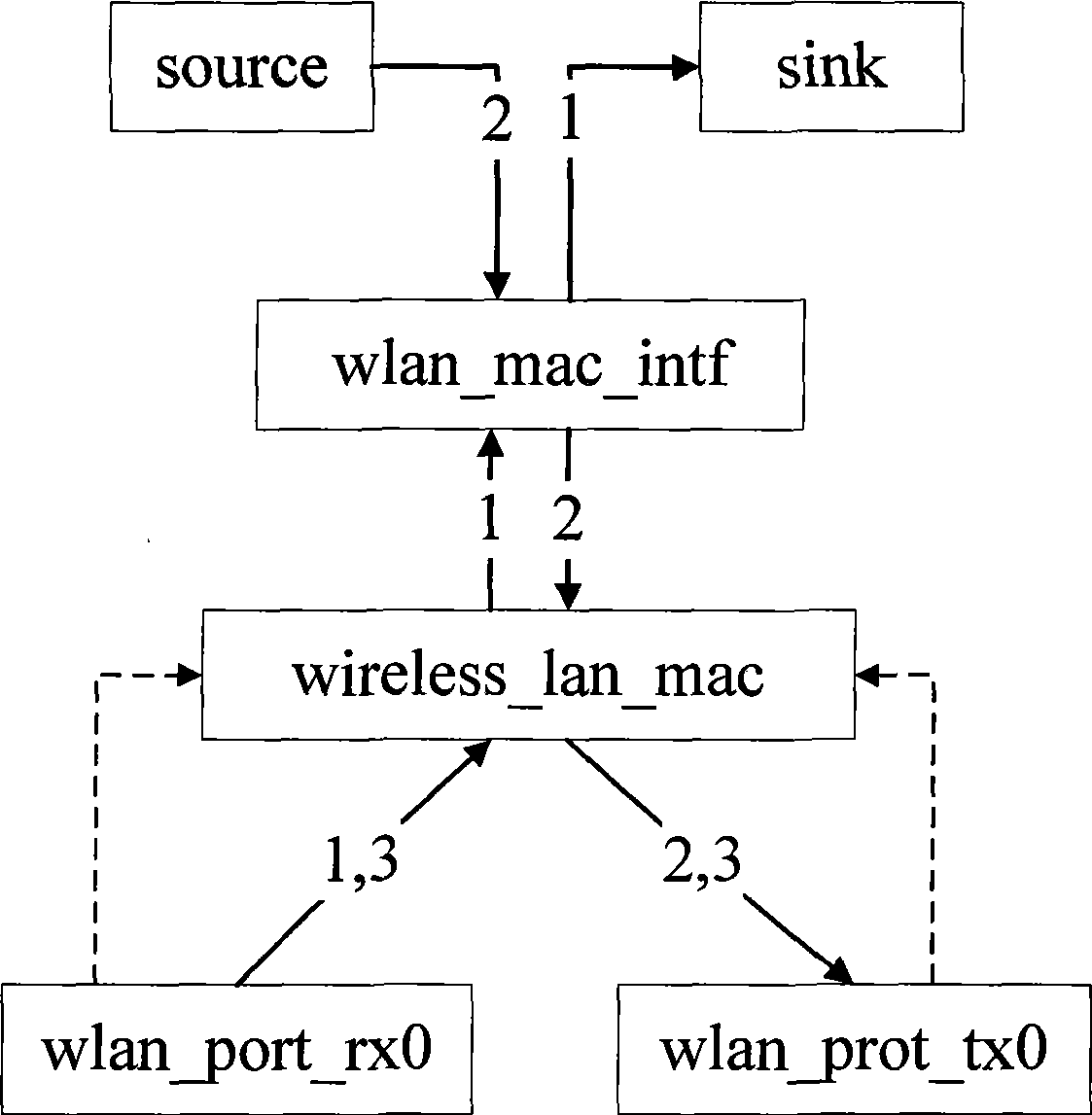
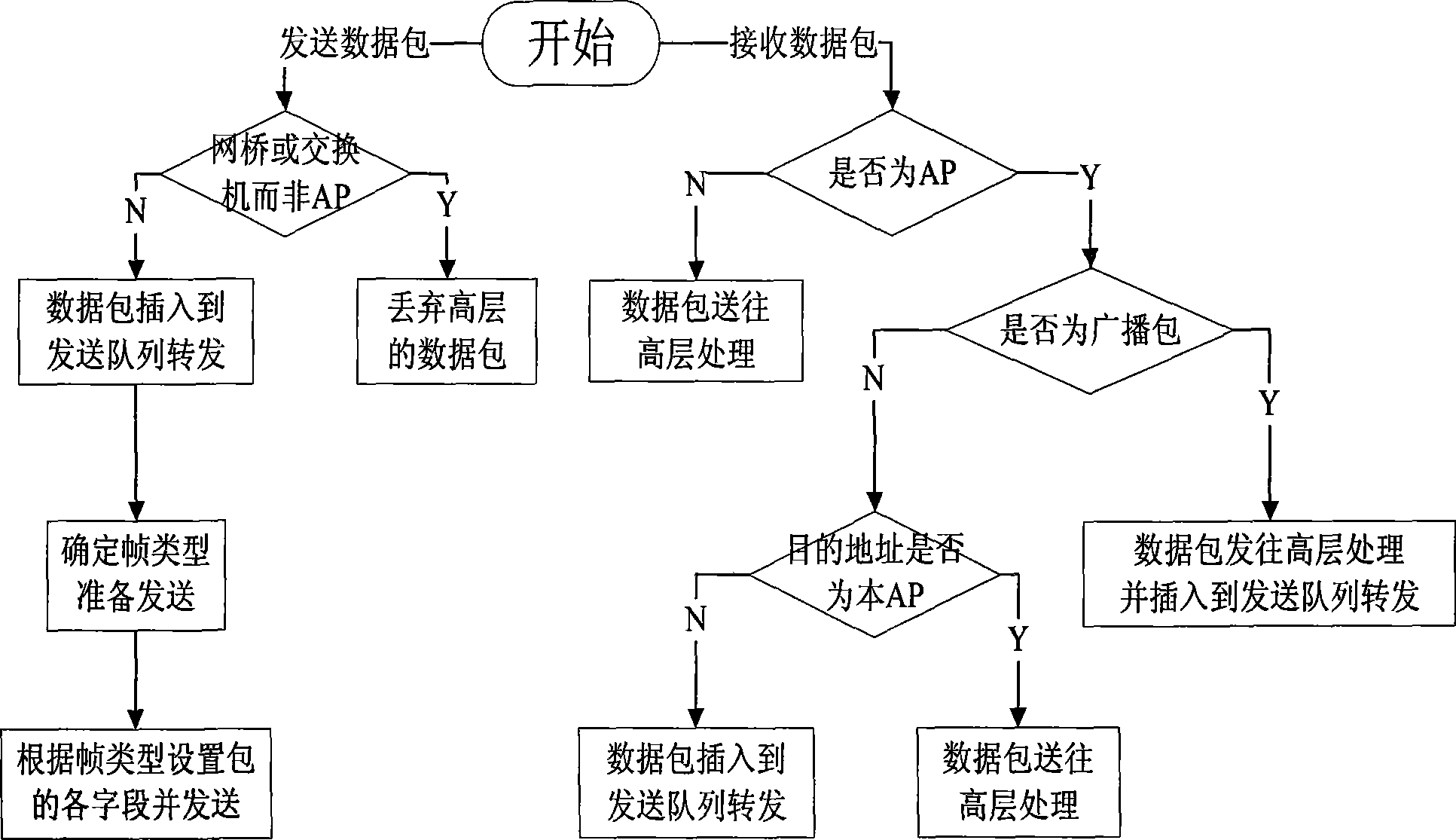
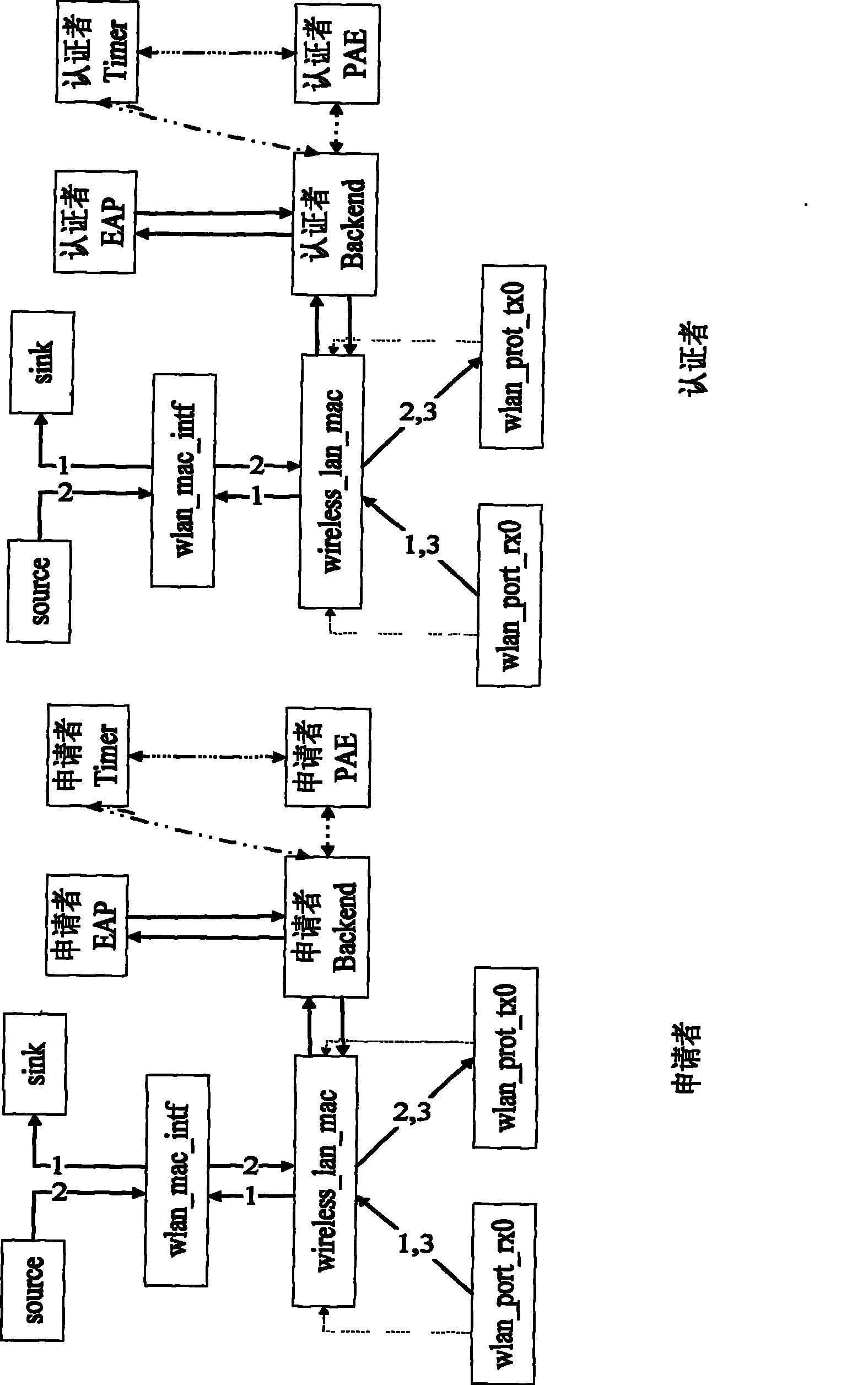
InactiveCN101360020AIntegrity guaranteedGuaranteed non-repudiationData switching by path configurationConfidentialityFinite-state machine
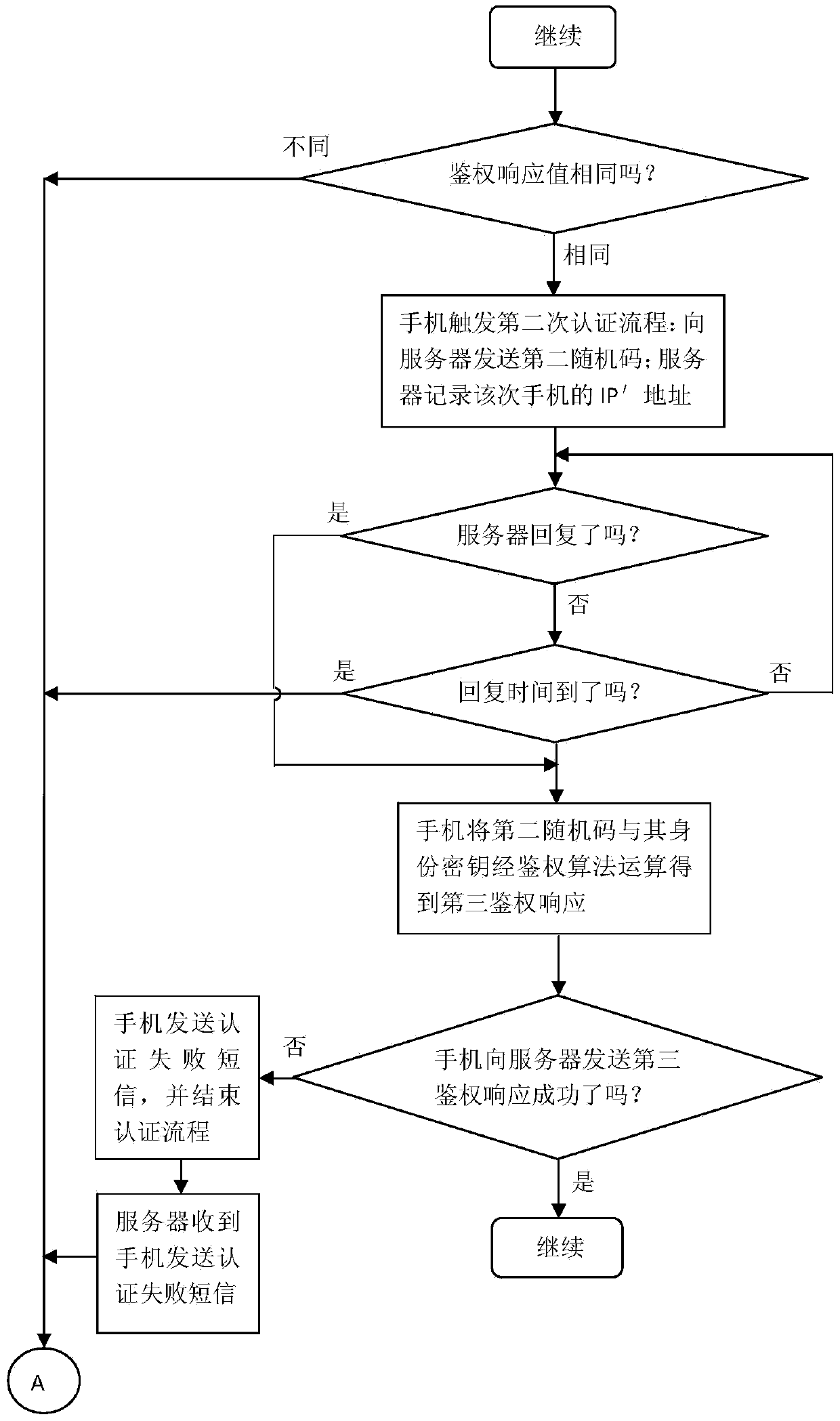
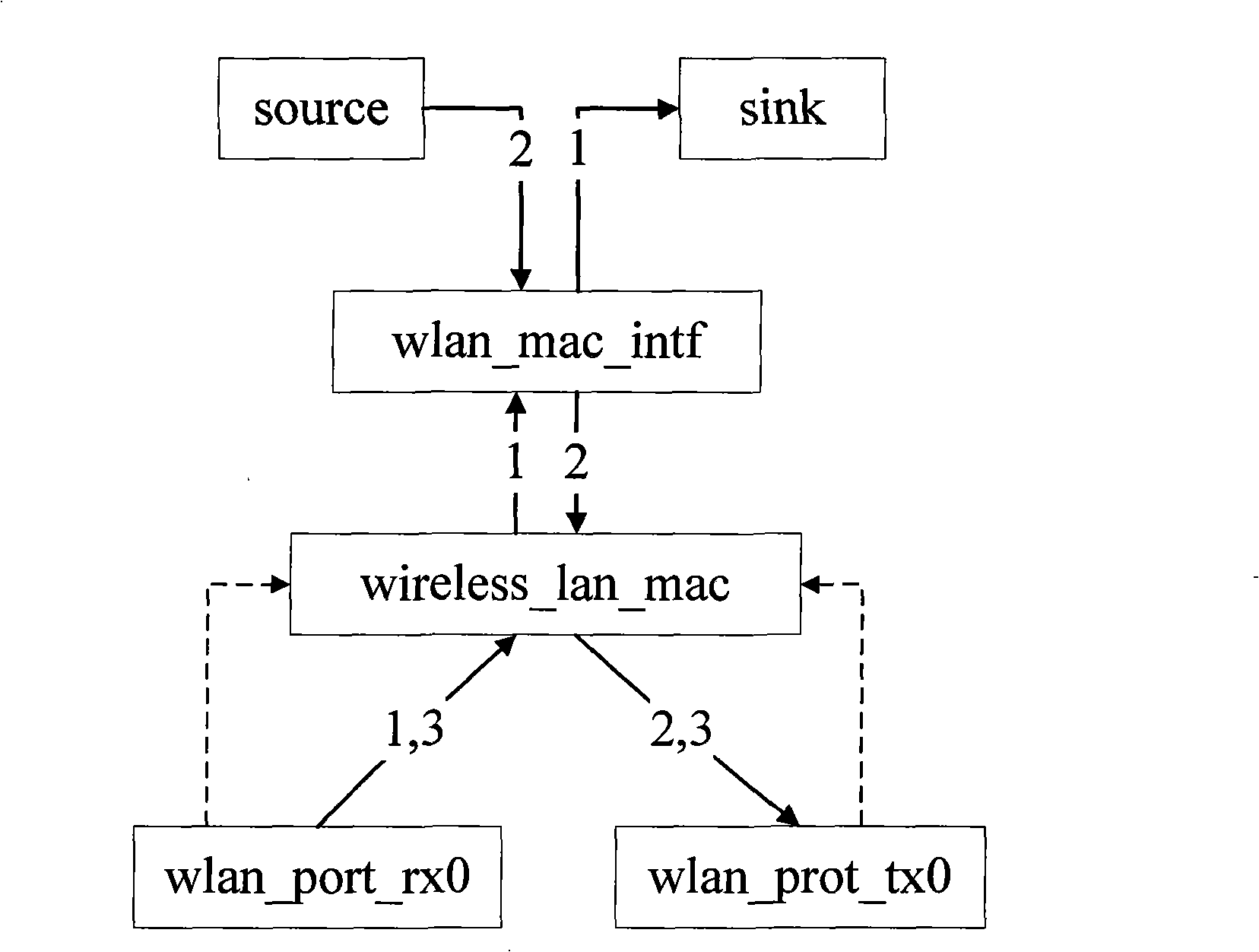
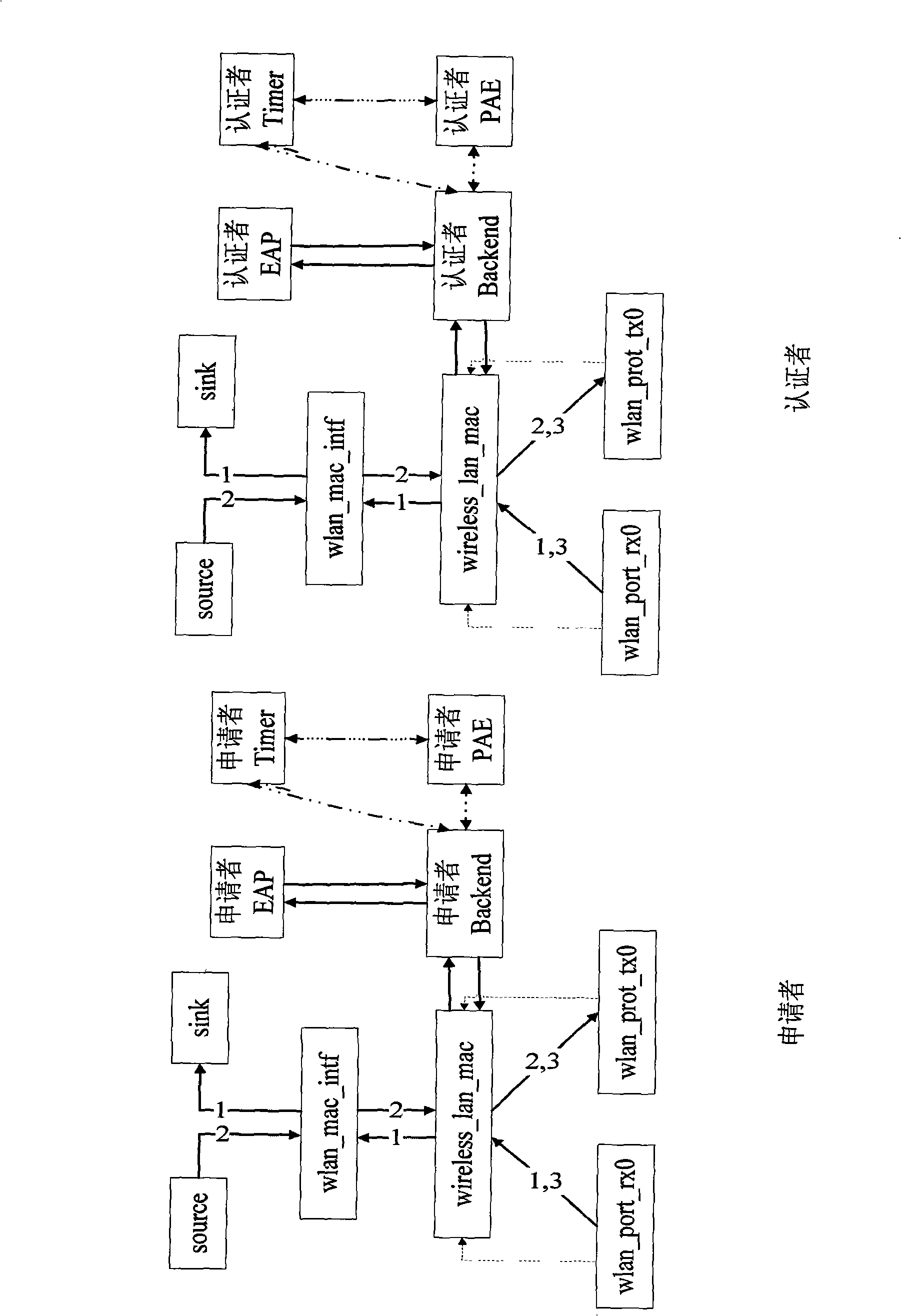
The invention provides a simulation platform based on the IEEE802.1X secure protocol of EAP as well as a method thereof, wherein, a wireless_lan_mac module in the original wireless node of OPNET is improved, and extended authentication modules are added including an EAP authentication module and a port control module, and the added parts and the wireless_lan_mac module are converged to add the function of security authentication successfully. The EAP authentication module is provided with an authenticator and an applicant communicating mutually to complete the security authentication, so the authentication process is presented completely, meanwhile, the complexity is not high and the simulation efficiency is rather good. The port control module is acquired through the equivalent transformation by a finite state machine of IEEE802.1X, the design correctness of a protocol model state machine is ensured, and the disorder among model versions is avoided. The invention realizes the simulation scene for roaming and re-authentication in different BSS of the wireless node, and solves the authentication problem of roaming access. The invention can ensure the integrity, non-repudiation and confidentiality of WLAN data, and can test other various realized wireless secure protocols and multimode access among various protocols on that basis.
Owner:XIDIAN UNIV
Method for recognizing efficiency of aircraft elevator
InactiveCN105509946ATroubleshoot authentication issuesAccurate dataAerodynamic testingWork measurementAviationUncrewed vehicle
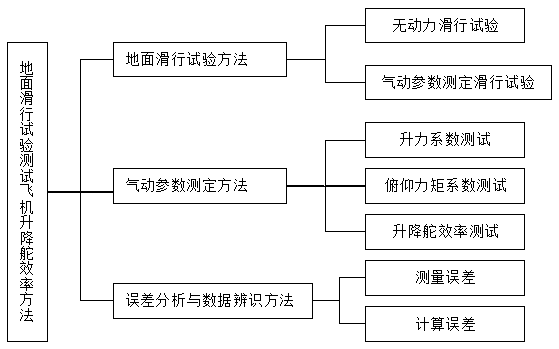
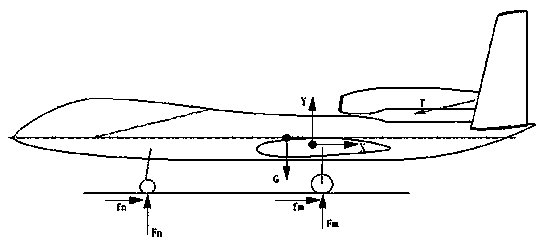
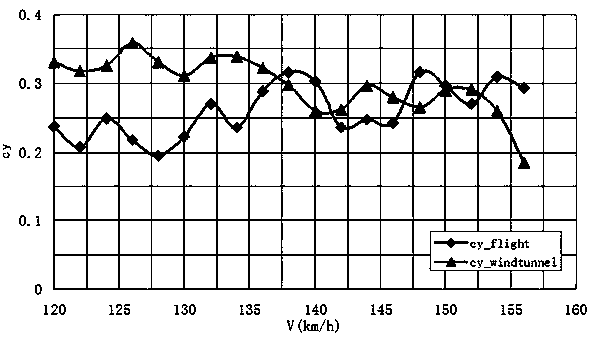
The invention relates to the field of aeronautical manufacture, and relates to the field of testing in the field of aeronautical manufacture, especially a method for recognizing the efficiency of an aircraft elevator. The method is characterized in that the method comprises the methods: a, a ground sliding testing method; b, a pneumatic parameter measurement method; c, an error analysis and data recognition method. The ground sliding testing method comprises the steps: a1, no-power sliding testing; a2, pneumatic parameter measurement sliding testing. The pneumatic parameter measurement method comprises the steps: b1, lift coefficient testing; b2, pitching moment coefficient testing; b3, elevator efficiency testing. The error analysis and data recognition method comprises the steps: c1, error measurement; c2, error calculation. The method can obtain the efficiency of the aircraft elevator, is simple, is accurate in data, is safe and reliable, is low in cost, analyzes the result data through employing a testing error analysis method, solves a problem of the verification of key pneumatic parameters of an unmanned plane before flying, and guarantees the safety of the first flight of the unmanned plane.
Owner:CHENGDU AIRCRAFT INDUSTRY GROUP
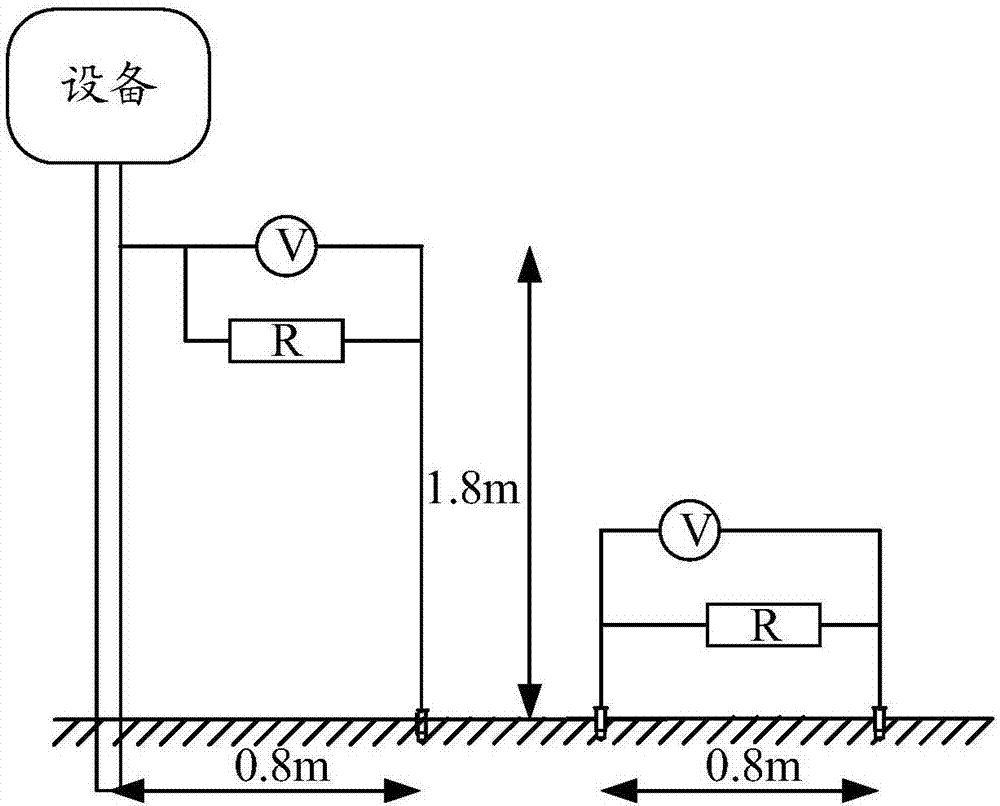
Grounding detection device
ActiveCN107037256ATroubleshoot authentication issuesEasy to carryCurrent/voltage measurementFault location by conductor typesGrounding gridOutput device
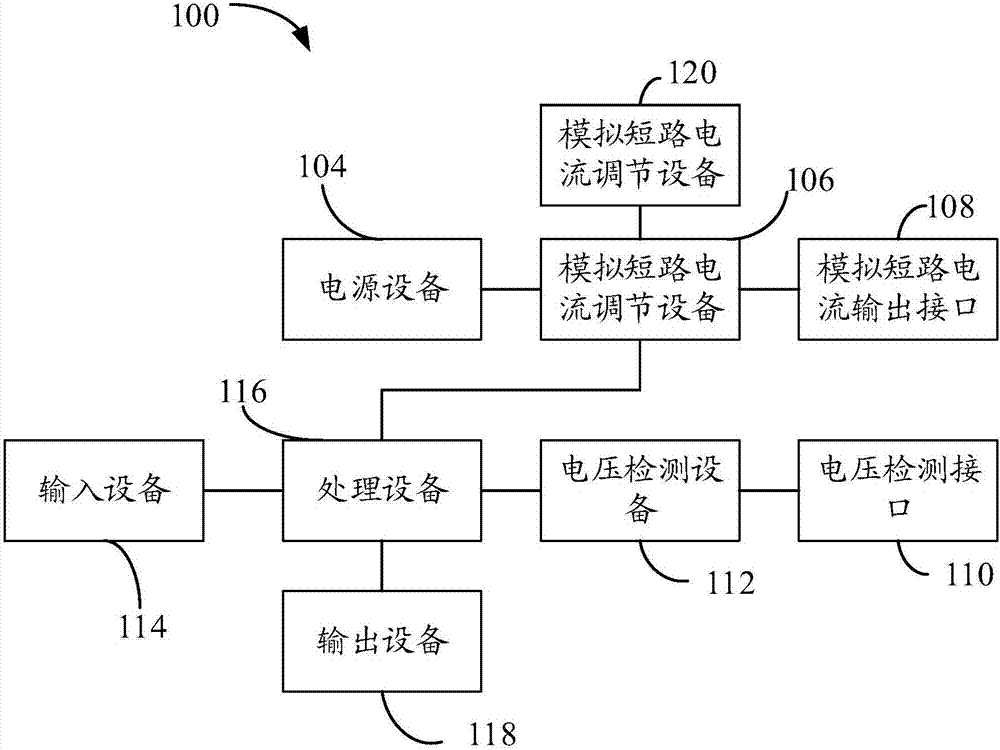
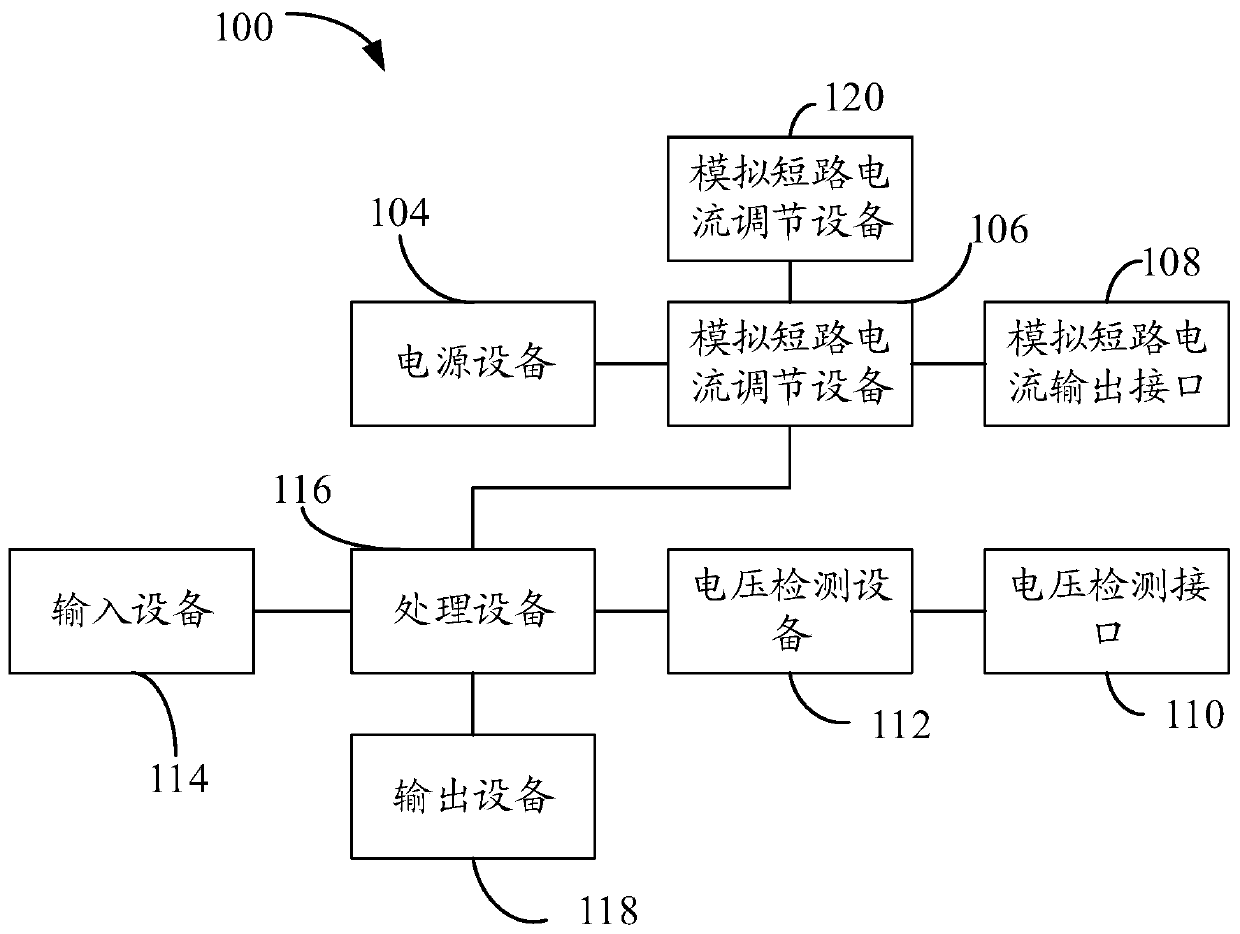
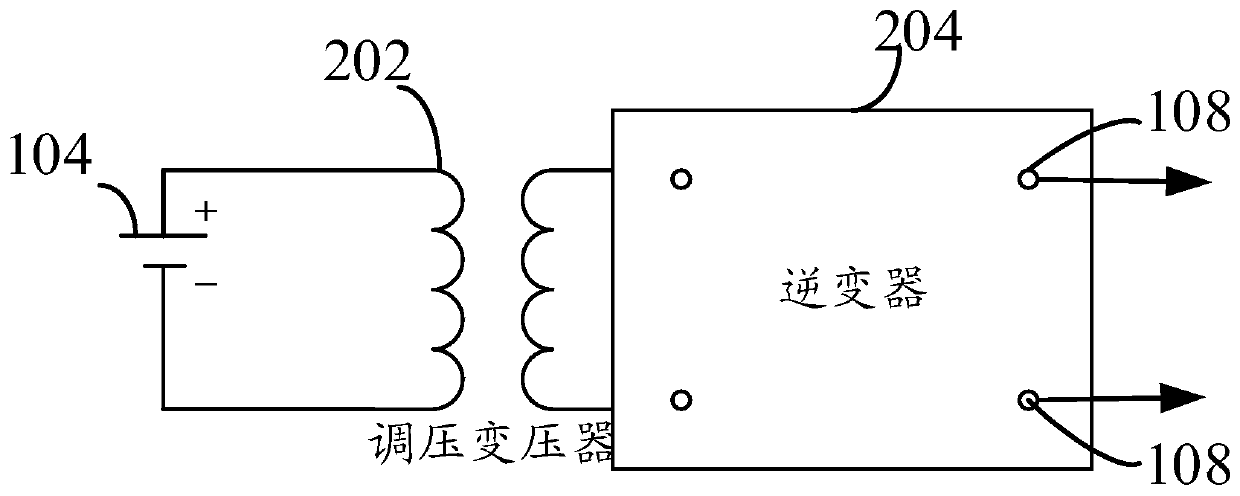
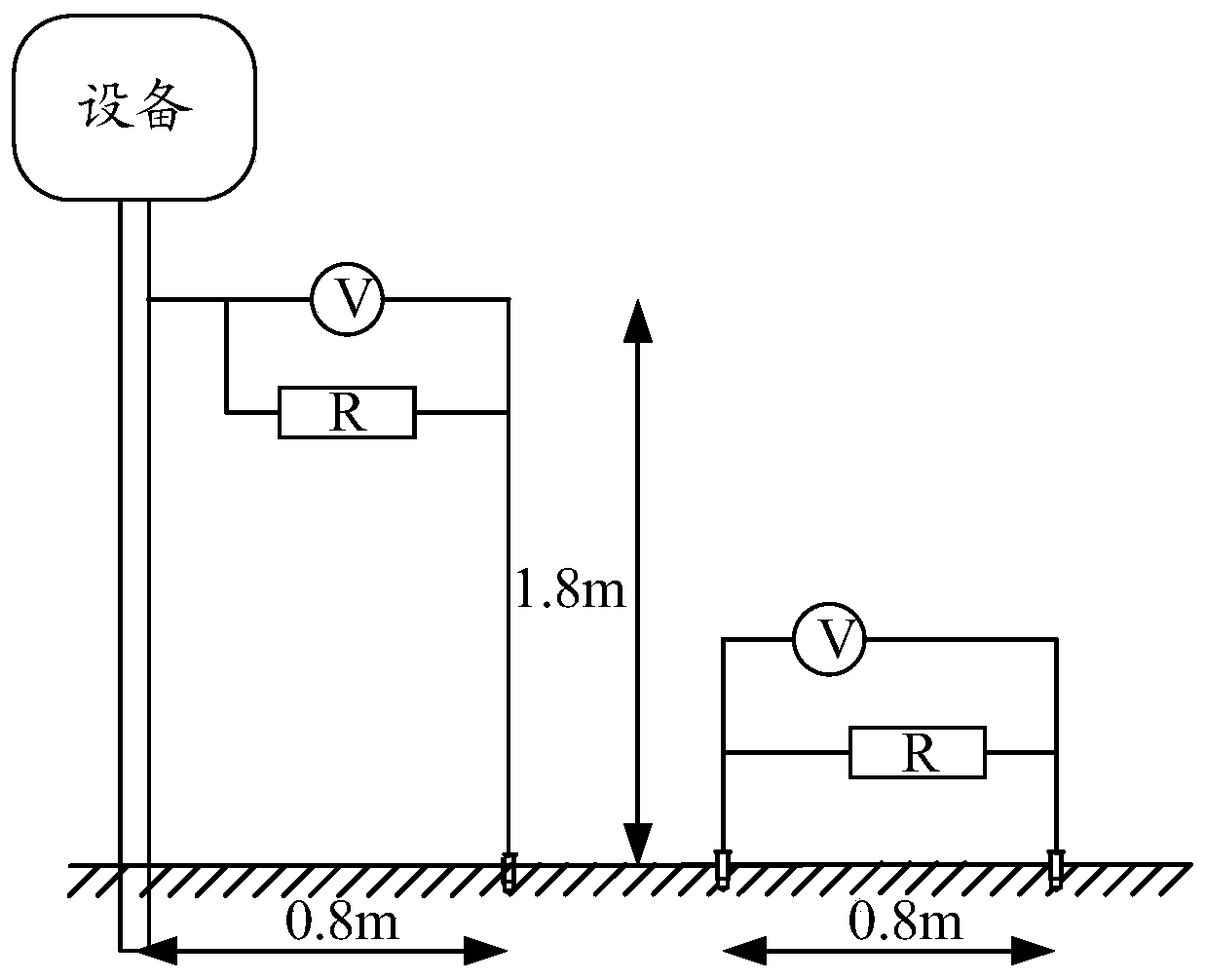
A grounding detection device comprises a shell. The shell is internally hollow to form a holding cavity. The grounding detection device also comprises a simulation short-circuit circuit output interface, a voltage detection interface, an input device and an output device which are fixed on the shell, and a power supply, a simulation circuit current generation device, a voltage detection device and a processing device which are fixed in the holding cavity. The input device is used for the personnel to input the physical parameters of the soil in the area where the grounding grid is located, the fault parameters of the electrical equipment with the grounding fault and the design parameters of the grounding grid, then the processing equipment is enabled to obtain the actual value of the target voltage, the required value of the target voltage and the theoretical value of the target voltage which are output by the output device. The grounding detection device can improve the acceptance accuracy and efficiency, is easy to carry, and can be applied to the design and acceptance stages.
Owner:CHINA GENERAL NUCLEAR POWER OPERATION +2
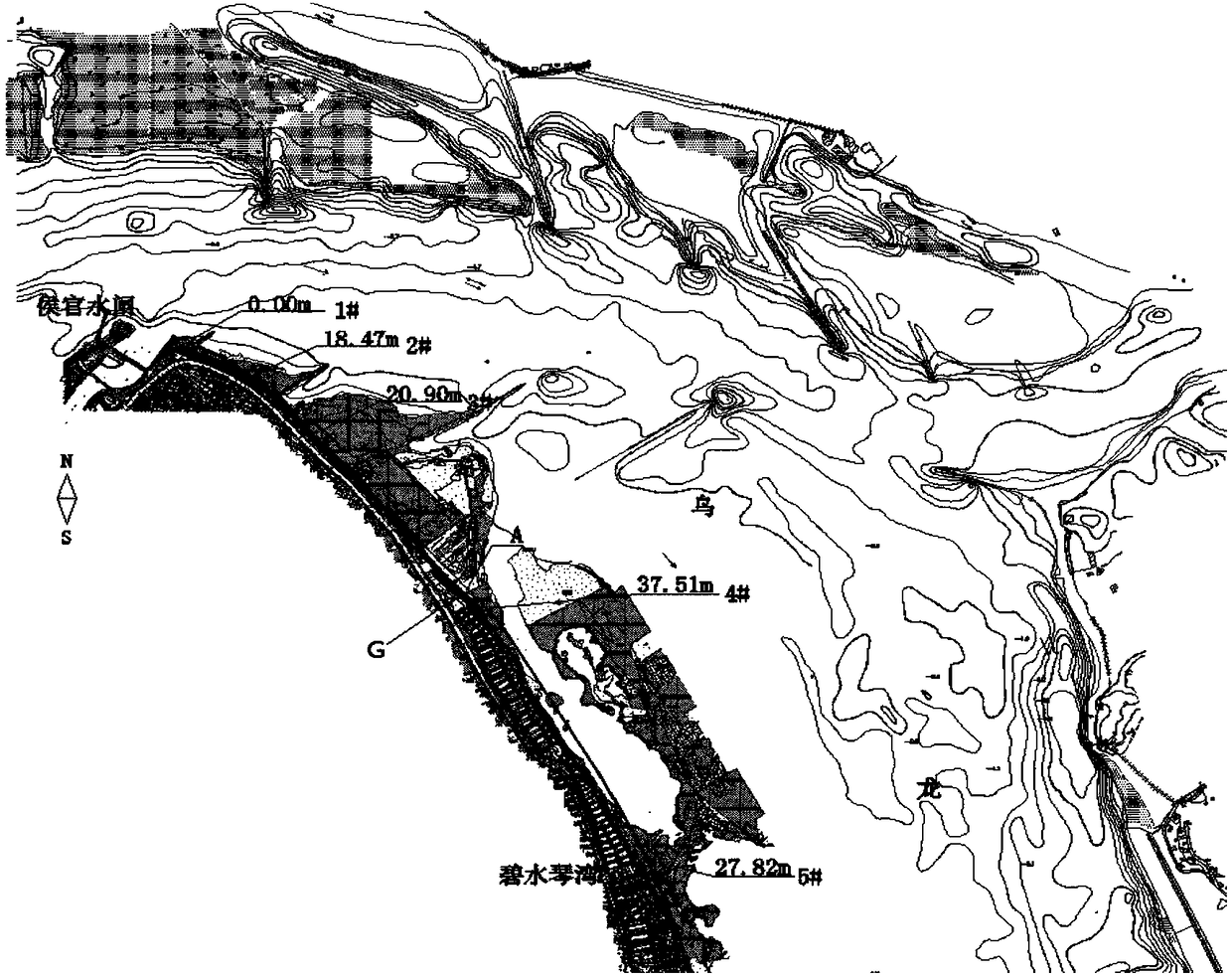
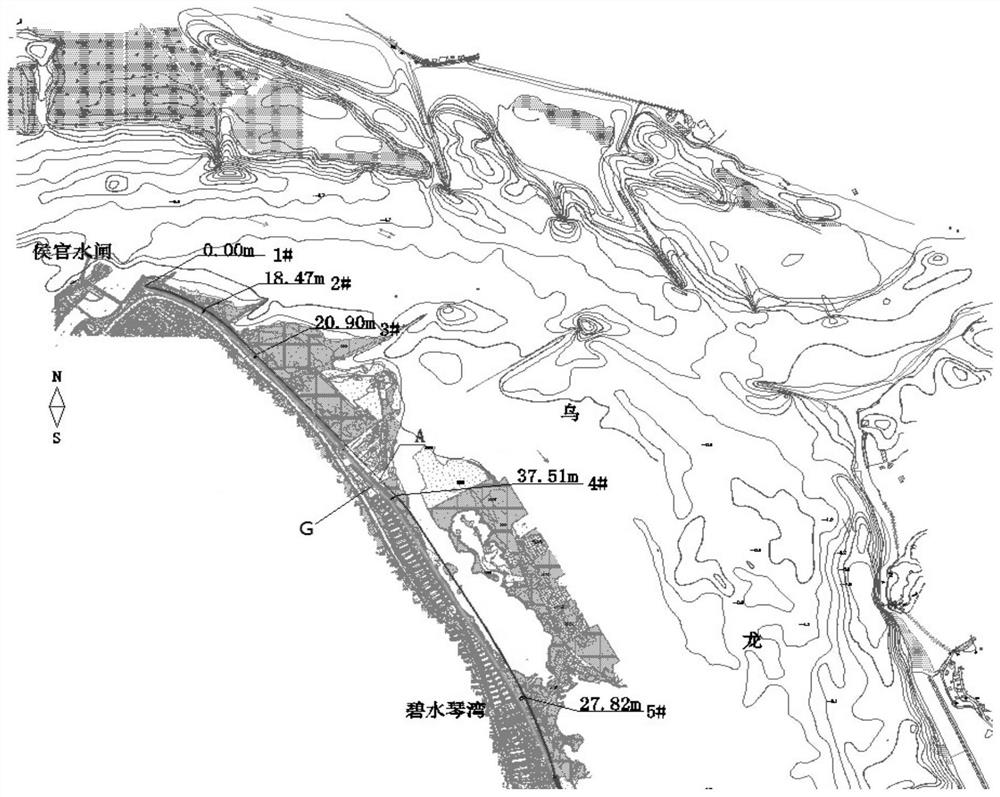
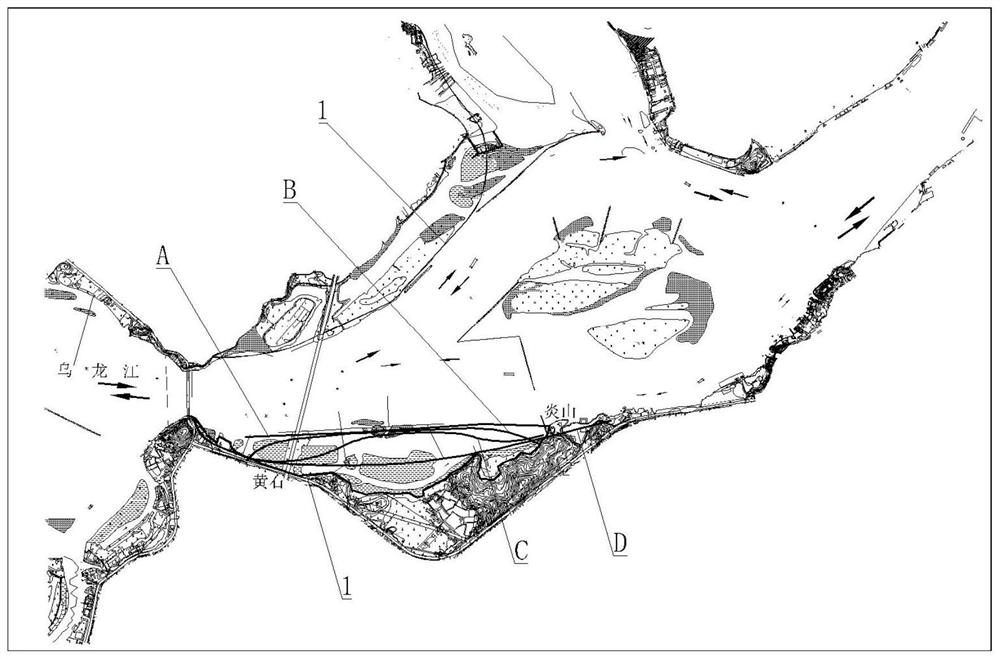
Tide-sensing river channel flood prevention and moisture prevention shoreline making method
ActiveCN108532532ATroubleshoot authentication issuesEffective simulationHydraulic modelsTerrainMathematical model
The invention discloses a tide-sensing river channel flood prevention and moisture prevention shoreline making method, and belongs to the technical field of flood prevention and moisture prevention foundation water conservancy facilities. The method is based on actually measured river channel terrain and hydrology sediment materials, a river channel physical model and a mathematical model are established, the mathematical model comprises a two-dimensional mathematical model and a three-dimensional mathematical model, and the river channel physical model, the two-dimensional mathematical modeland the three-dimensional mathematical model are carrying out digital-to-analogue coupling; and according to hydrodynamic characteristics under different regional tidal currents and different workingconditions, water force of a river channel field, change rule of flow velocity gradient, distribution rule a water power curve, erosion and silting process of a riverbed and a form of ultimate erosionand silting are under the long-time action of the river flood and the outer sea boundary at different frequencies are achieved, and a shoreline conforming to a natural river tidal flooding intersection movement rule is formulated. The tide-sensing river channel flood prevention and moisture prevention shoreline making method has the advantages that the defect that in traditional shoreline making,the flood power function is considered independently and the long-term effect of the tidal power is ignored are broken through, and the adaptability of a combined action area river channel shorelineof a runoff and a tide is enhanced.
Owner:FUJIAN PROVINCIAL INVESTIGATION DESIGN & RES INST OF WATER CONSERVANCY & HYDROPOWER
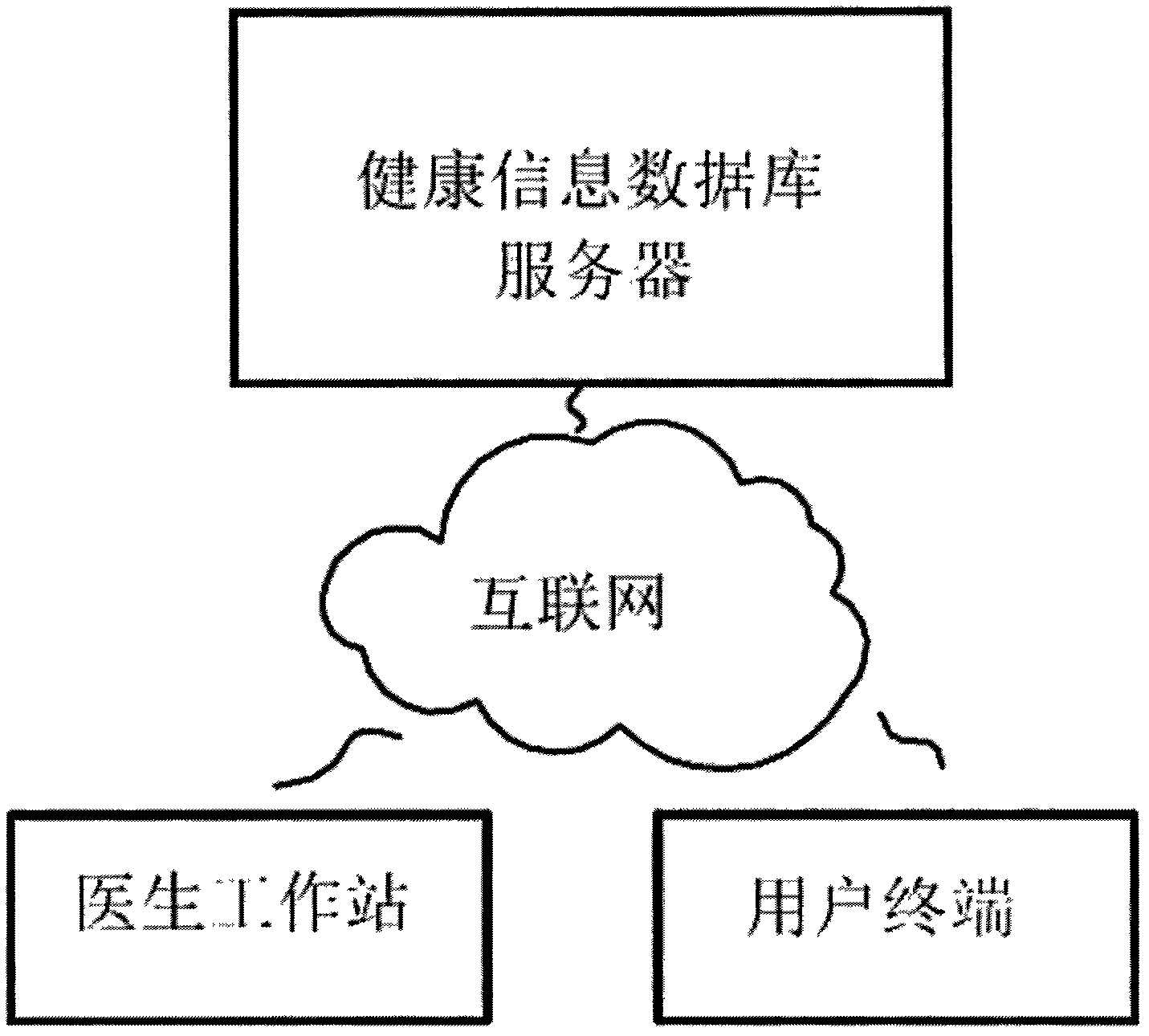
Secure transmission method for health information
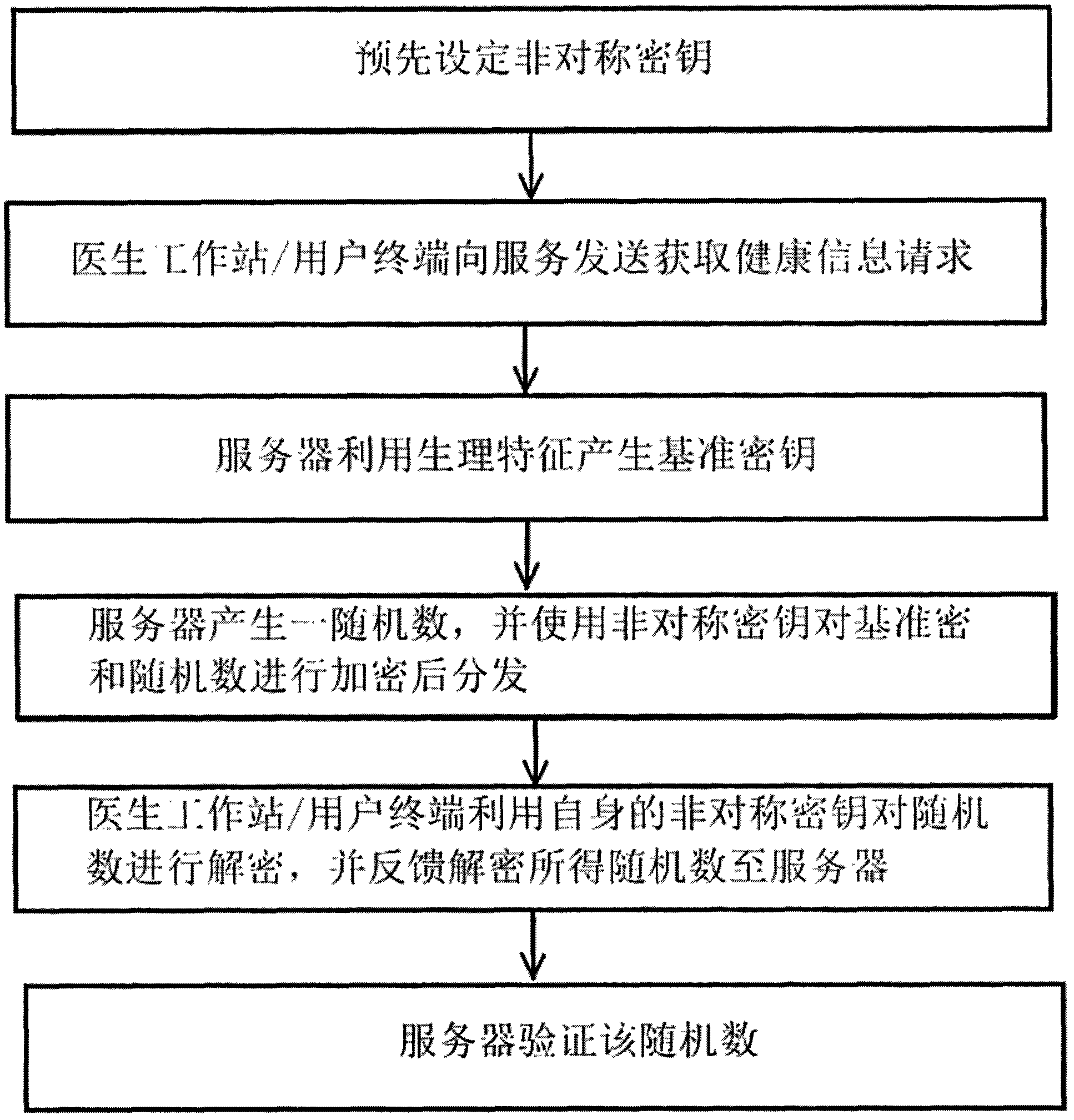
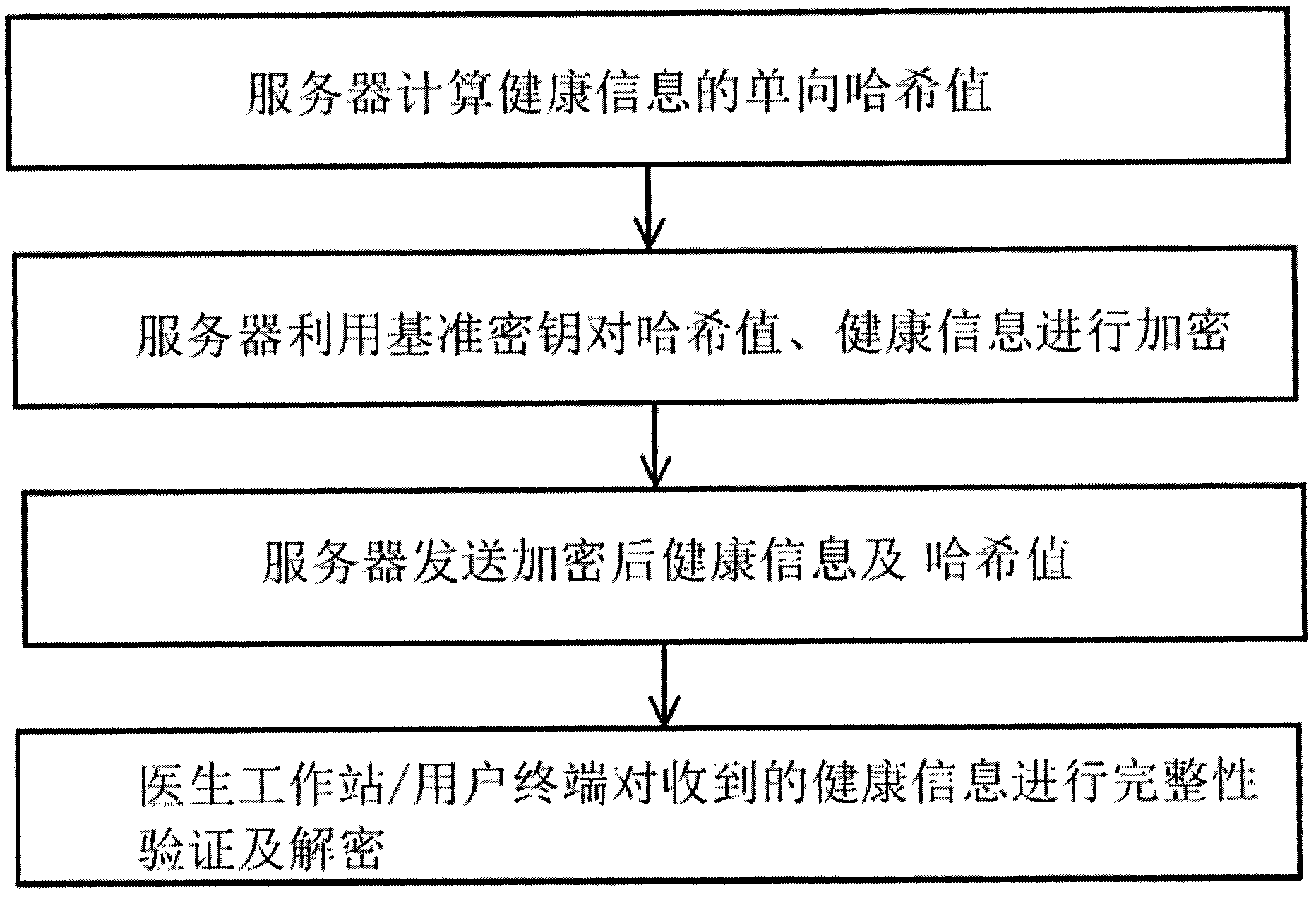
InactiveCN102546655AEnsure safetyReduce loadKey distribution for secure communicationDiagnostic recording/measuringDatabase serverSecure transmission
The invention discloses a secure transmission method for health information, and aims to realize the secure transmission of the health information between a health information database server and a doctor workstation / user terminal. The method is characterized by comprising the following steps that: 1, an asymmetric key is set in advance between the health information database server and the doctor workstation / user terminal; 2, the health information database server generates a reference key by utilizing physiological characteristics; 3, the health information database server encrypts the reference key through the asymmetric key, and distributes the reference key; 4, a random number is verified; 5, after the random number passes the verification, the health information database server calculates a one-way hash value, encrypts the hash value and the health information by utilizing the reference key, and transmits the encrypted hash value and the encrypted health information; and 6, the doctor workstation / user terminal performs integrity verification and decryption on the received health information.
Owner:ZHONGSHAN IKER DIGITAL TECH
Automatic teller machine based on face recognition on three sides
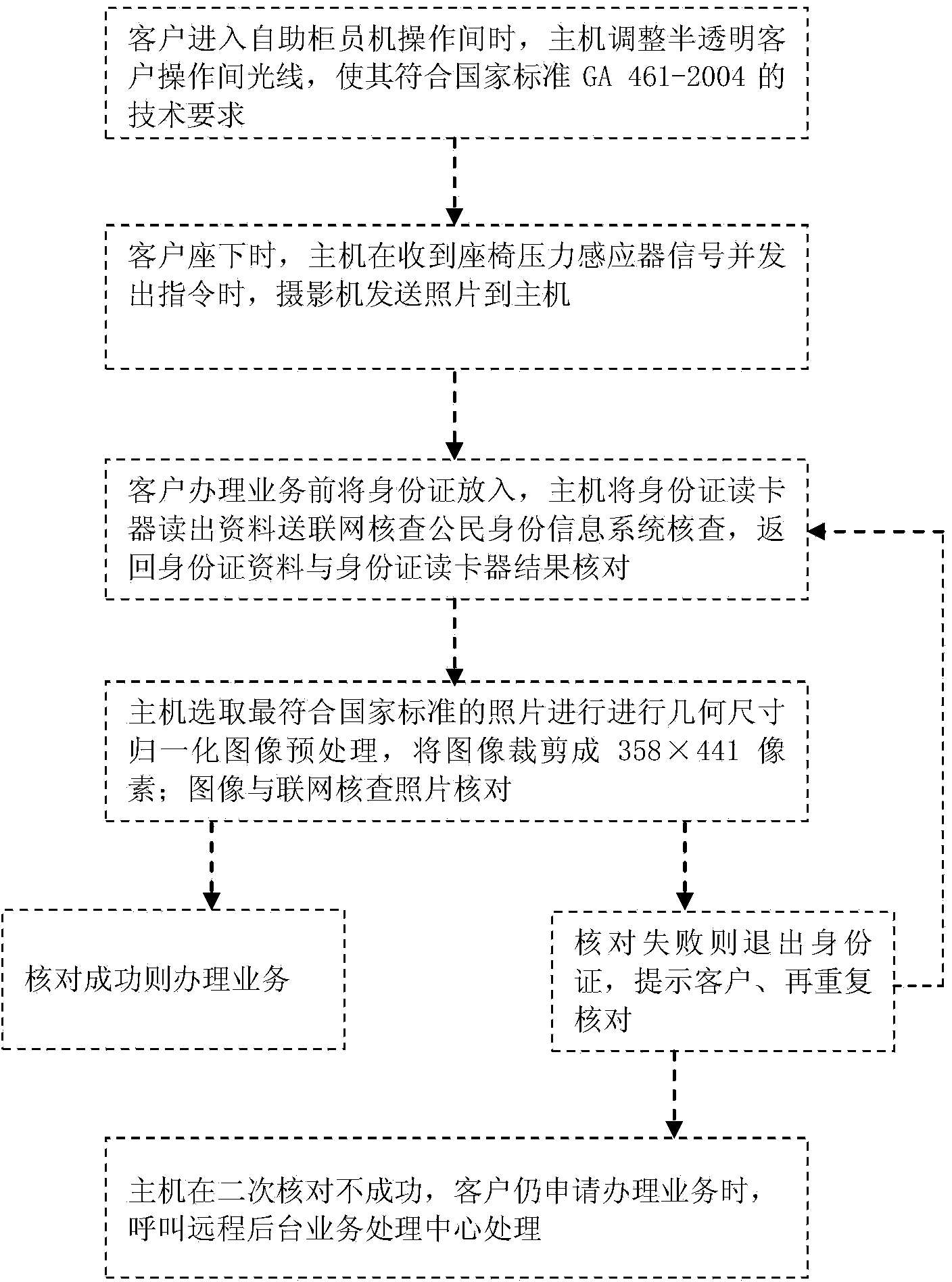
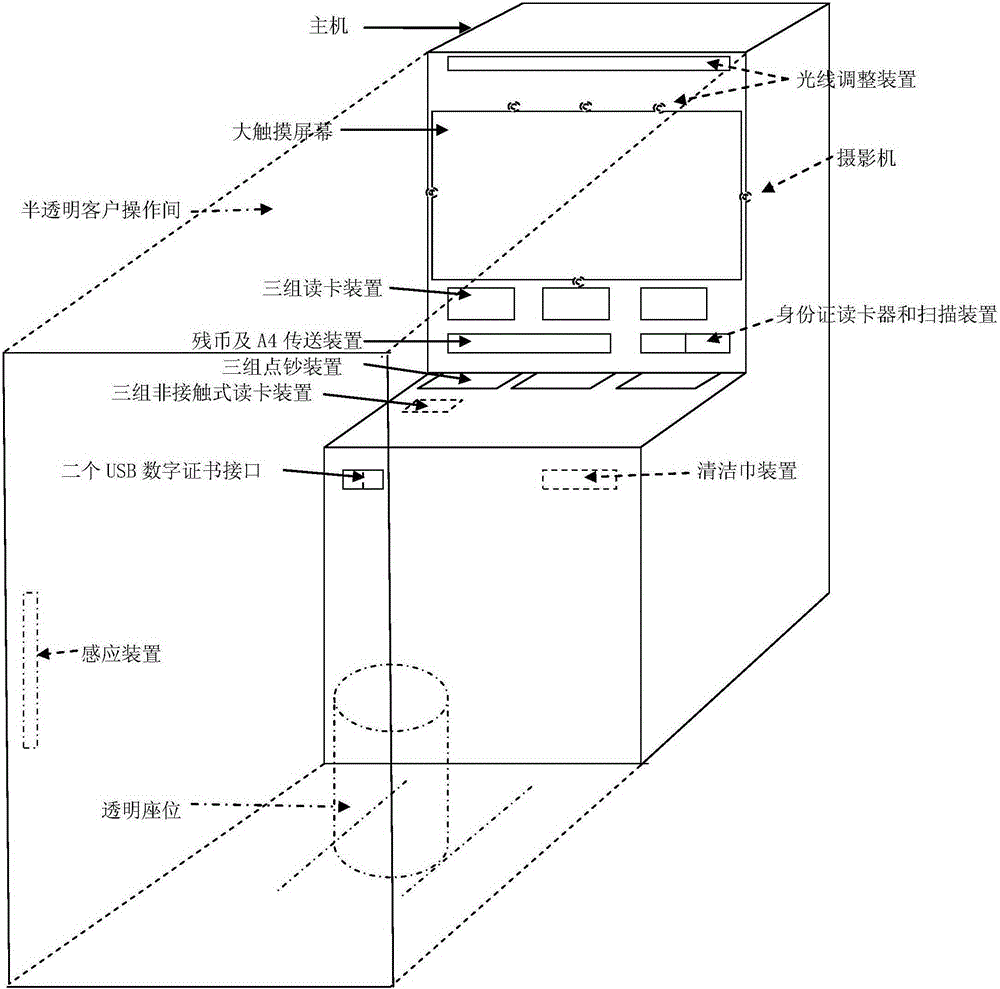
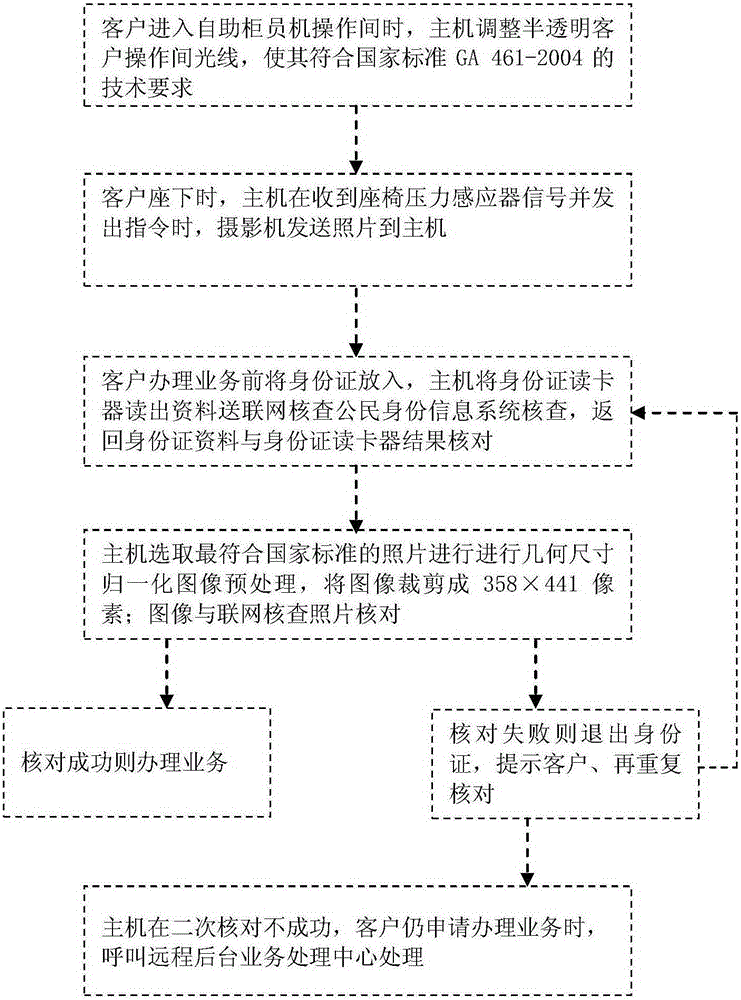
InactiveCN103871174ATroubleshoot authentication issuesSolve the problem of inaccurate face recognitionComplete banking machinesDigital data authenticationComputer graphics (images)Information device
The invention relates to an automatic teller machine based on face recognition on three sides. The automatic teller machine is characterized by comprising a main machine, a camera group, a semitransparent customer operating room, a large touch screen, a light adjusting device, a face recognition device, an identity card reader, an identity card double-sided scanning device, a second-generation identity card reader, a second-generation identity card double-sided scanning device, two USB (universal serial bus) digital certificate interface, an online verification citizen identity information device, a cleaning towel device and a remote background service processing center; the automatic teller machine photographs a picture of a customer to be respectively checked with the picture on the identity card read by the identity card reader and the picture of the identity card returned by the online verification citizen identity information system, and the service can be carried out when the picture is successfully checked; the identity card is withdrawn if the picture checking is failed, the cleaning towel device is powered on, the customer is reminded of removing a helmet, a gauze mask and spectacles and having normal facial expression so as to repeatedly check; when the picture is still failed in the second checking and the customer still applies to the service, the host machine calls the remote background service processing center to process.
Owner:西安美达威网络科技有限公司
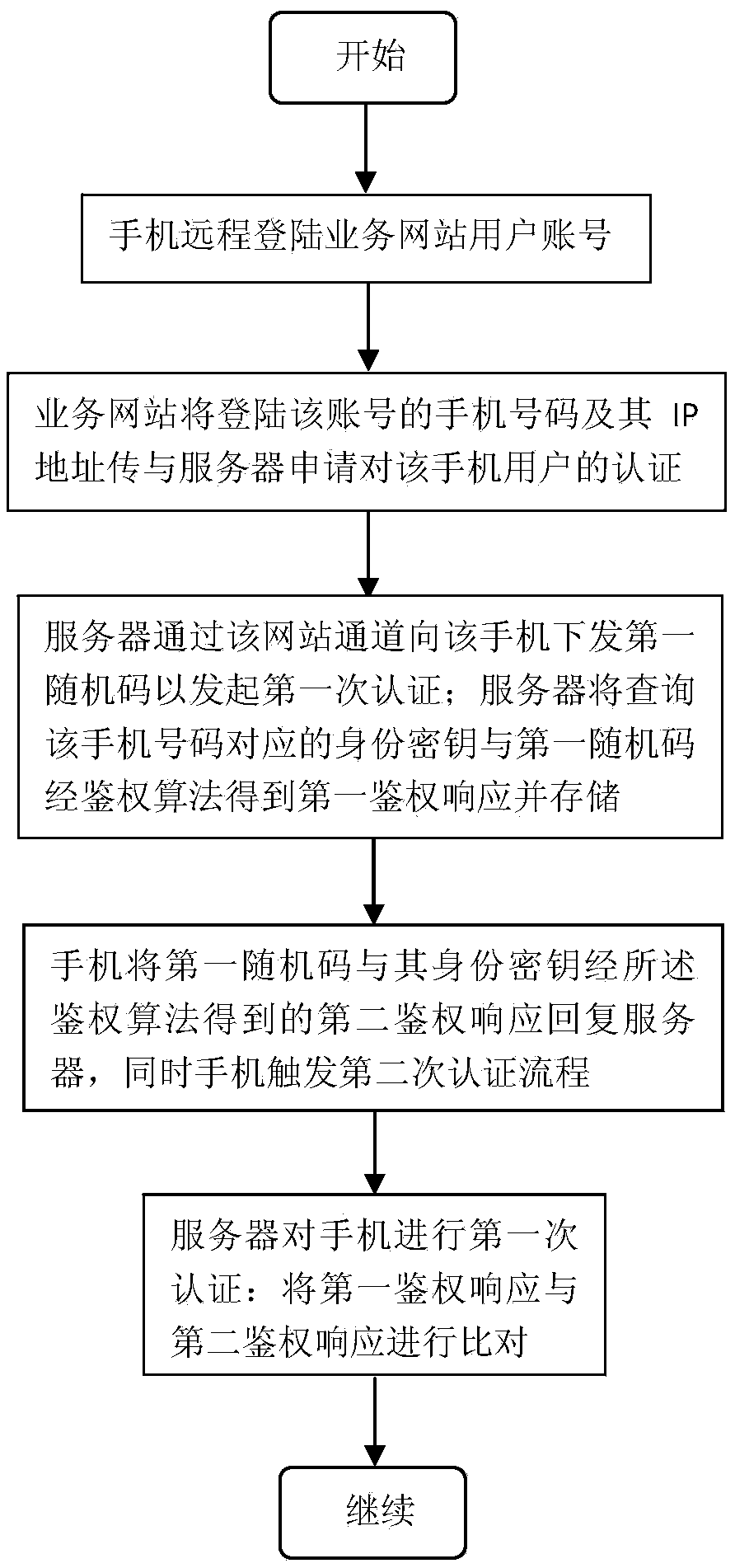
Identity verifying method and relevant apparatus
InactiveCN106470200ATroubleshoot authentication issuesImprove verification accuracyTransmissionData miningStatus changed
According to the embodiments of the invention, an identity verifying method and relevant apparatus are provided. In the invention, when a terminal receives a request for identity verification, the identity information is obtained and transmitted to a first server. The terminal receives a first matching result transmitted from the first server. When the first matching result is a successful one, the terminal acquires the biological characteristic information and transmits the biological characteristic information to the first server. The terminal receives a second matching result transmitted from the first server. When the second matching result is also a successful one, the terminal determines that the identity is verified successfully. The embodiments of the invention verify the identity of a person through the identity information and the biological characteristic information, which can achieve a high verification rate. In addition, such identity verifying method can be realized through a terminal, which better solves the problem that when a person opens an account in a bank, the person has to be present in person to have his identity verified.
Owner:方正国际软件(北京)有限公司
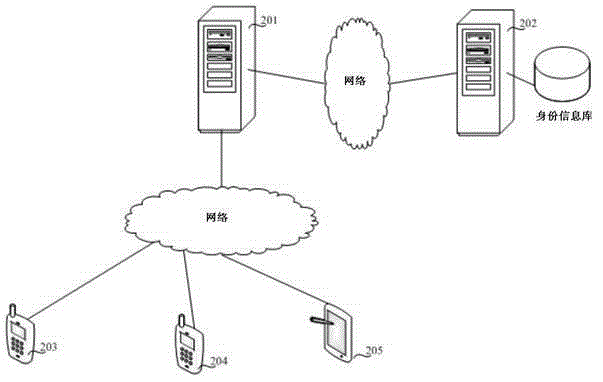
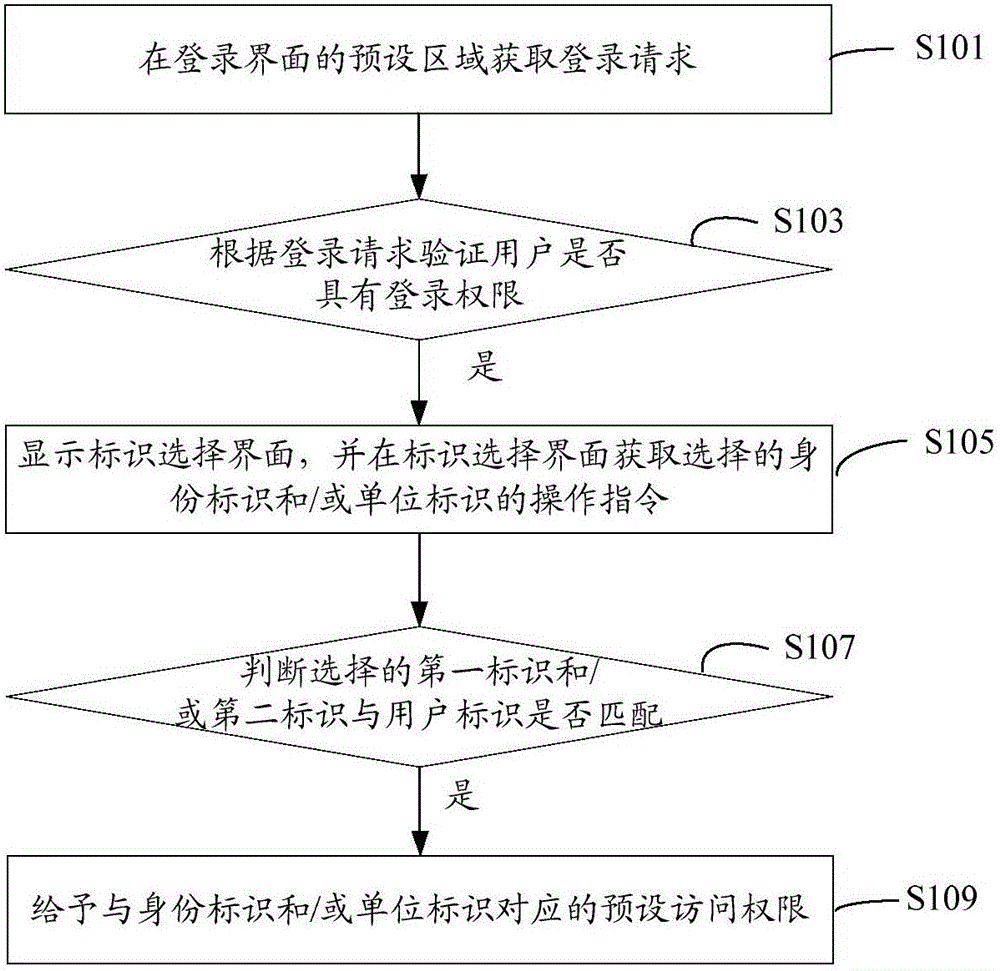
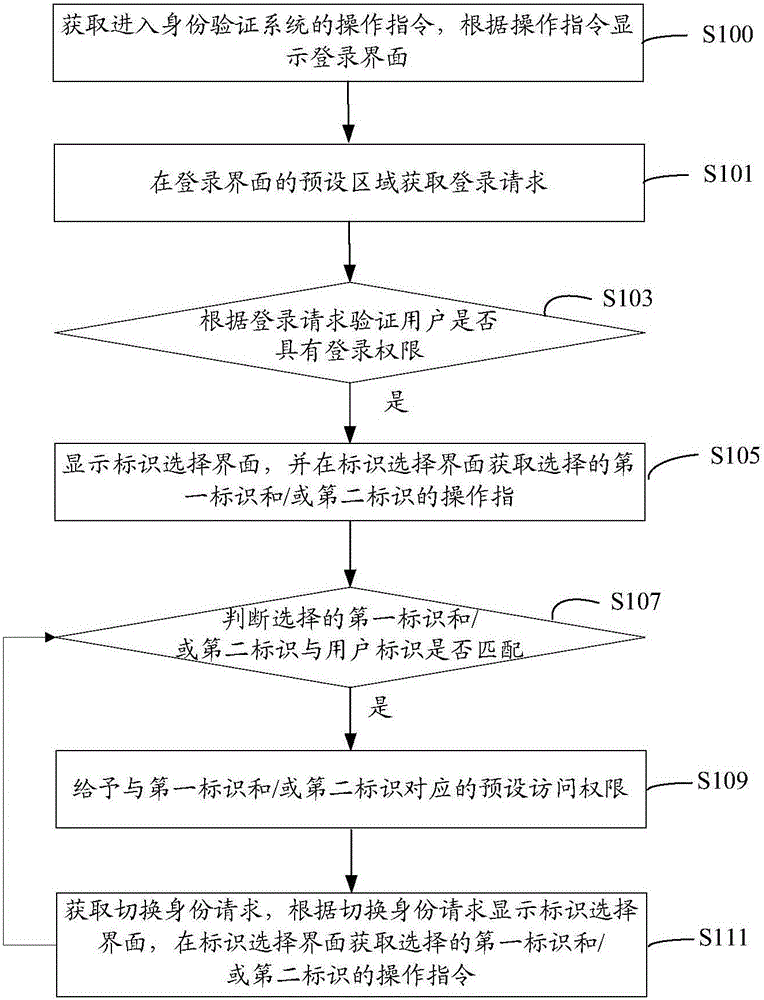
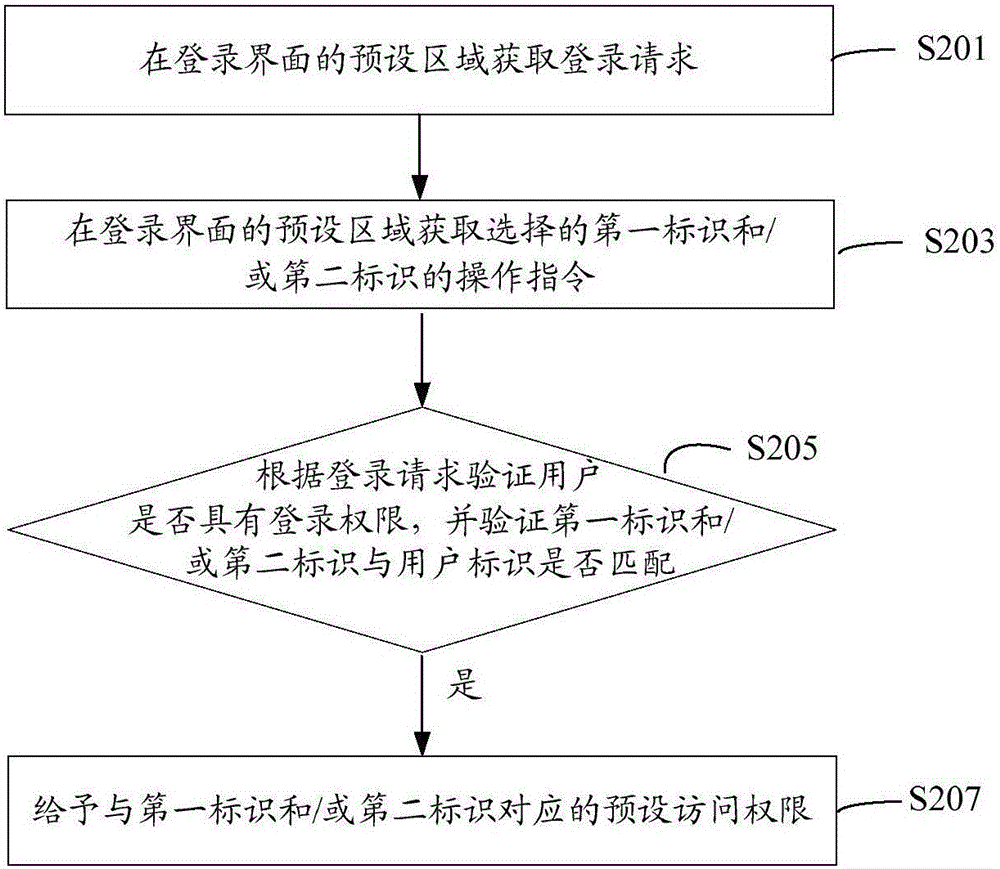
Method and system for user identity verification, and campus management system
The invention relates to a method and system for user identity verification, and a campus management system. The method comprises: a logging-in request is obtained at a preset area of a logging-in interface, wherein the logging-in request includes a user identifier and a user password; according to the logging-in request, whether the user has the logging-in permission is verified; if the verification is done successfully, an identifier selection interface is displayed and operation instructions or an operation instruction of a selected first identifier and / or a selected second identifier are / is obtained at the identifier selection interface; whether the selected first identifier and / or the selected second identifier match / matches the user identifier is determined; if so, preset access permission corresponding to the first identifier and / or the second identifier is provided. With the method, with different first identifiers and / or second identifier, the user can have multiple different identities; and the same user can carry out verification on several kinds of identities by one user identifier and the access permission corresponding to the first identifiers and the second identifiers of the different identities of the user are also provided. Therefore, identity verification of user having multiple different identities is realized.
Owner:HUNAN YIGU TECH DEV
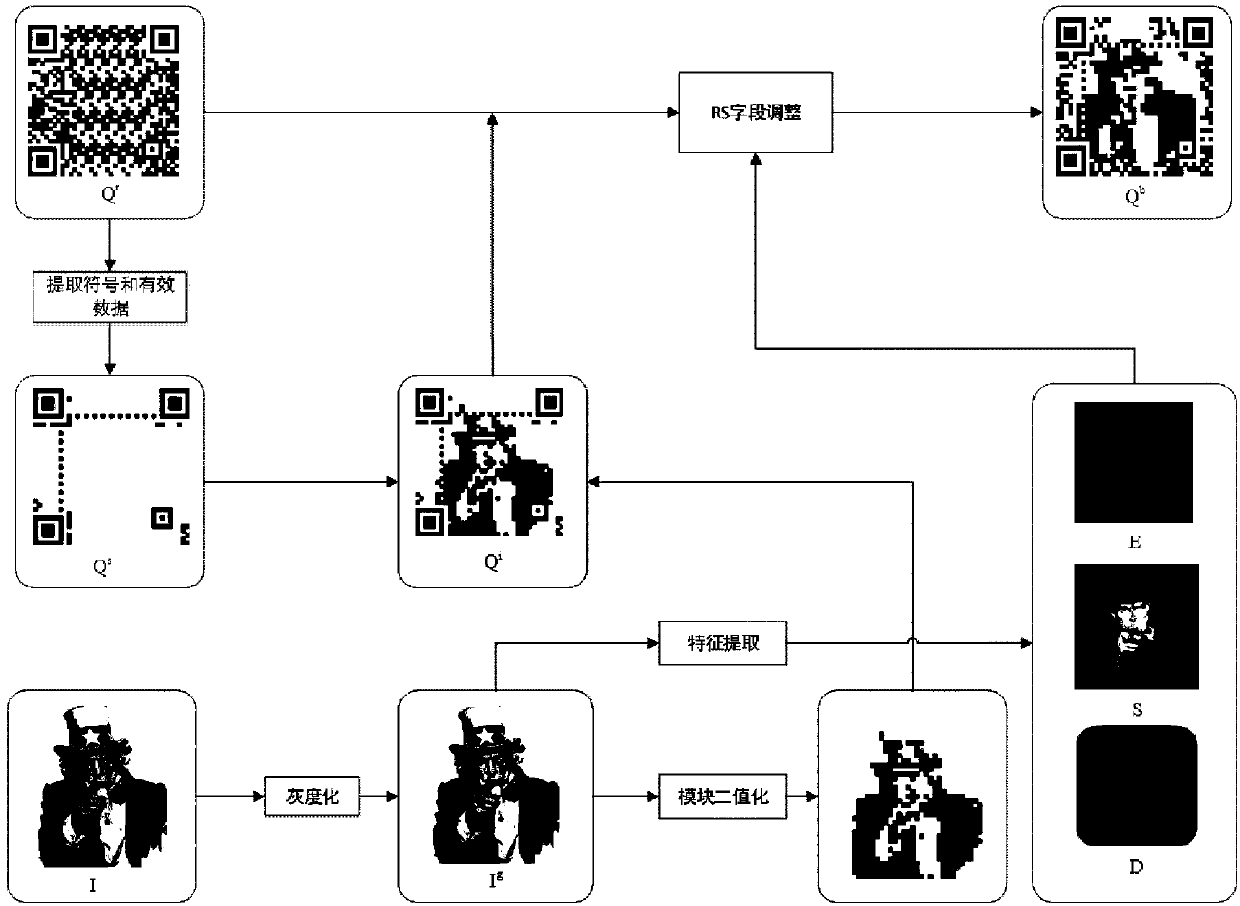
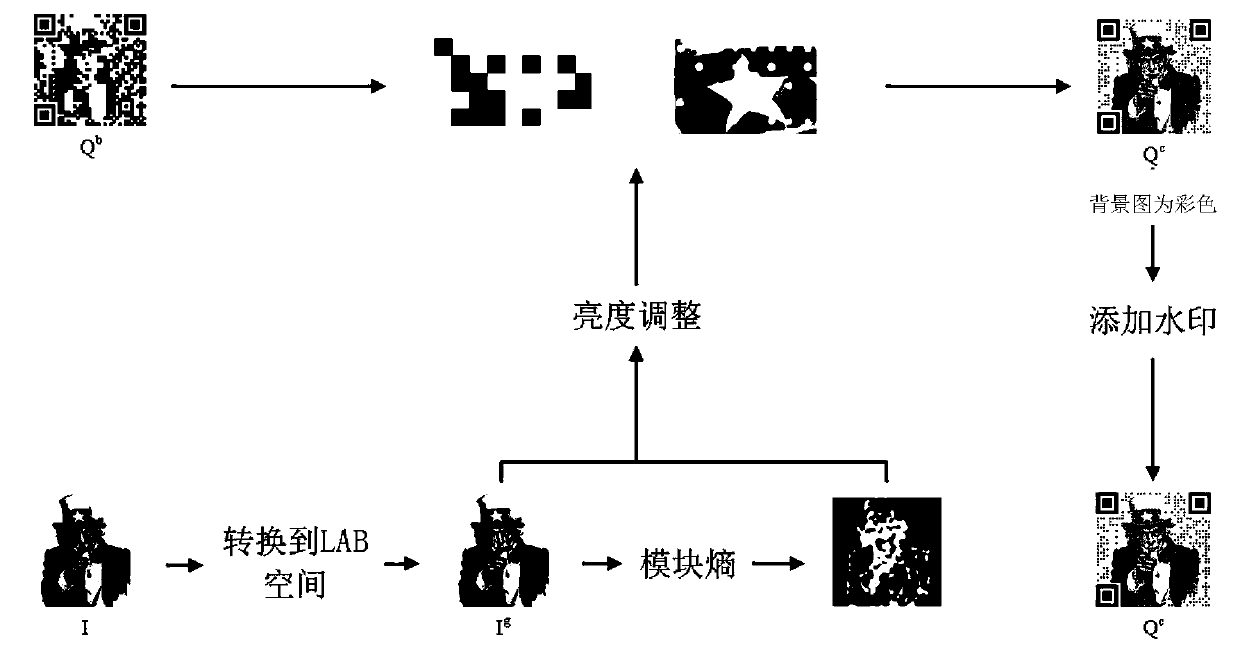
Secret-containing beautification QR code authentication method
ActiveCN108491913AImprove visual effectsAvoid occlusionImage data processing detailsRecord carriers used with machinesComputer hardwareBackground image
The invention discloses a secret-containing beautification QR code authentication method. The method comprises the following generation steps of binarizing an input background image to generate a reference QR code; according to an RS code, establishing a forward basis matrix, and generating a reverse basis matrix through a Gaussian Jordan elimination method; performing black and white turnover ona module with a high QR code priority by utilizing the forward and reverse basis matrixes to obtain a transient QR code image; judging a module attribute for brightness adjustment of a small check inthe module; adjusting module brightness and generating a beautification QR code image in combination with other two channels; and combining the beautification QR code with a digital watermark anti-counterfeit technology to generate a secret-containing beautification QR code. By adopting the beautification QR code, a tag carries a large amount of product information and the attractiveness of a package is improved; a digital watermark is added based on the beautification QR code, so that the anti-counterfeit performance of the QR code is enhanced; and the QR code is combined with the digital watermark anti-counterfeit technology, so that the anti-counterfeit performance is greatly improved.
Owner:绍兴聚量数据技术有限公司
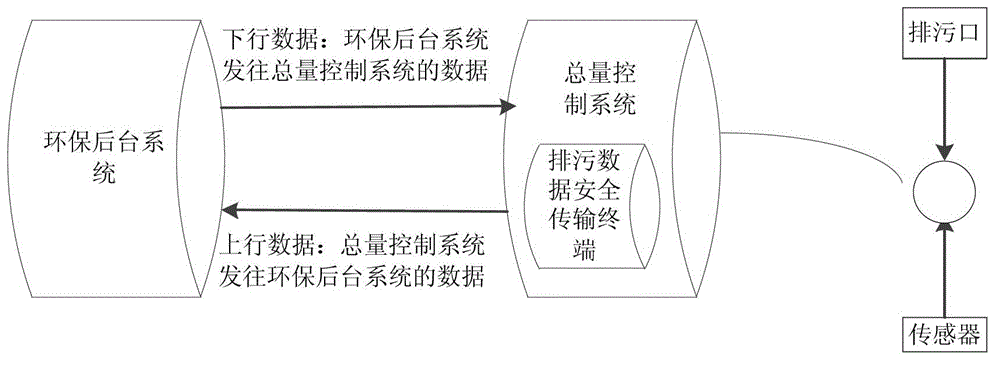
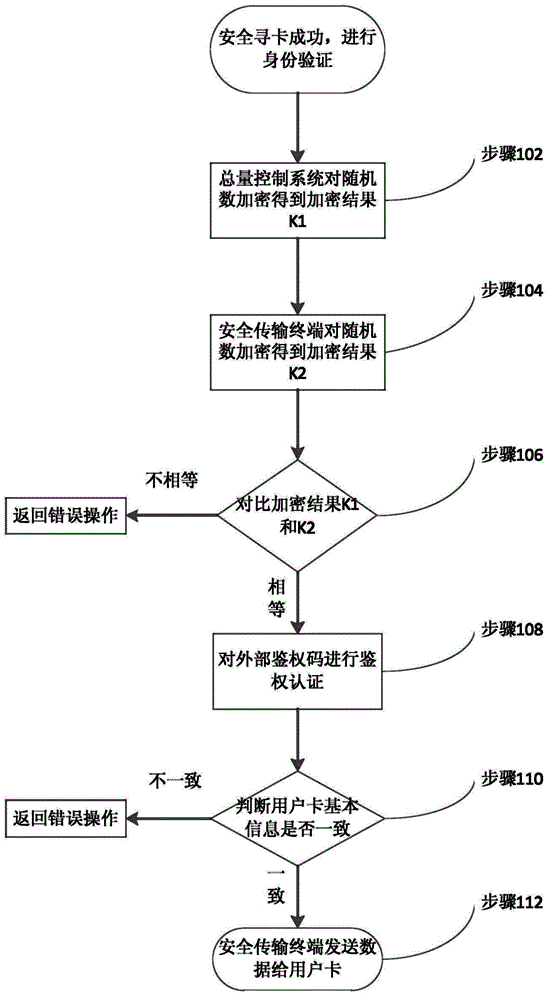
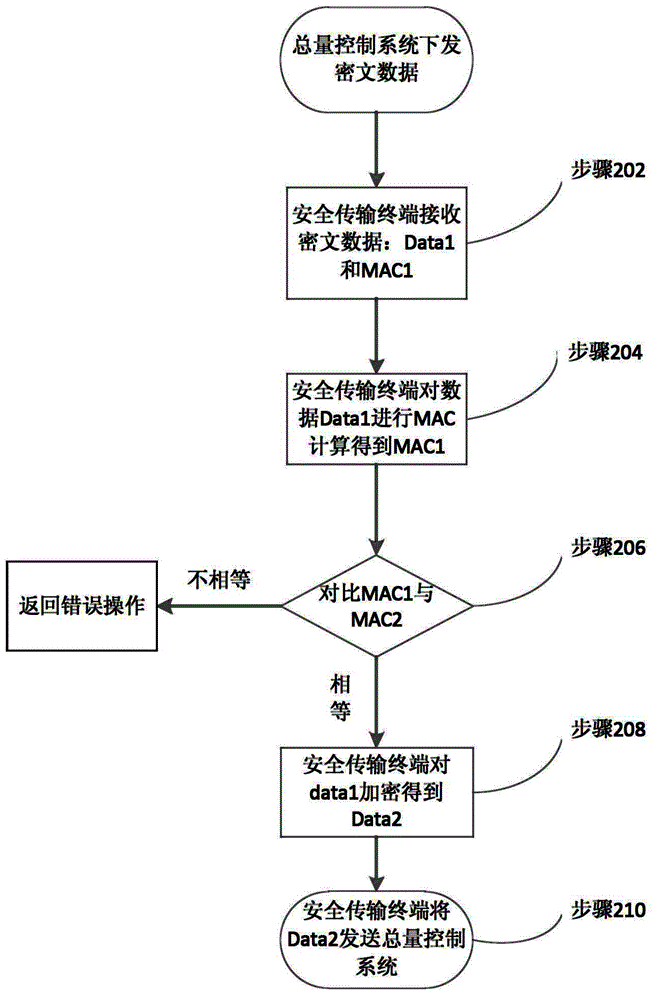
Pollution discharge data secure transmission method and terminal and system
InactiveCN104378201ATroubleshoot authentication issuesImprove securityUser identity/authority verificationDigital data authenticationControl systemTransfer procedure
The invention discloses a pollution discharge data secure transmission method and terminal and a system. The method comprises the steps that a random number is obtained from a user card, and an encryption result K1 is obtained after the random number is encrypted based on a built-in secret key of the user card; an encryption result K2 is obtained after the random number is encrypted based on a built-in secret key of the secure transmission terminal; the encryption result K1 and the encryption result K2 are compared, and if K1 is equal to K2, the user card passes authentication. The system comprises a pollution discharge system and a total quantity control system. The pollution discharge system comprises an environment-friendly background system and the total quantity control system, and the total quantity control system comprises the pollution discharge data secure transmission terminal. According to the pollution discharge data secure transmission method and terminal and the system, pollution discharge data are encrypted and decrypted based on a pre-appointed built-in secret key through an SM1 algorithm in the transmission process, and security and confidentiality of the pollution discharge data in the storage and transmission process are guaranteed.
Owner:STATE GRID CORP OF CHINA +1
Smart power grid multi-dimensional multi-subset privacy protection data aggregation method based on block chain
PendingCN112800459AImplement multiple subset partitioningEffective monitoringDatabase distribution/replicationDigital data protectionPrivacy protectionData aggregator
The invention discloses a smart grid multi-dimensional multi-subset privacy protection data aggregation method based on a block chain. According to the method, each dimension of power consumption data in the system is divided into a plurality of subsets by using two super-increasing sequences, Horner rule and a Paillier encryption algorithm, so that multi-subset division of multi-dimensional power consumption data is realized; a control center not only can obtain the number of users in each subset in each dimension of power consumption data in the system, but also obtains the total power consumption of each subset in the power consumption data of each dimension, so that an electric power company can perform fine-grained analysis on the power consumption information on the basis of protecting the privacy of the power consumption data of the user, and the electric power company can effectively monitor and manage a power grid; therefore, the power demand can be better predicted and a reasonable gradient electricity price strategy can be formulated. In addition, by means of the block chain technology, the integrity and validity of the data can be conveniently verified, and the verification problem of a third party is well solved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
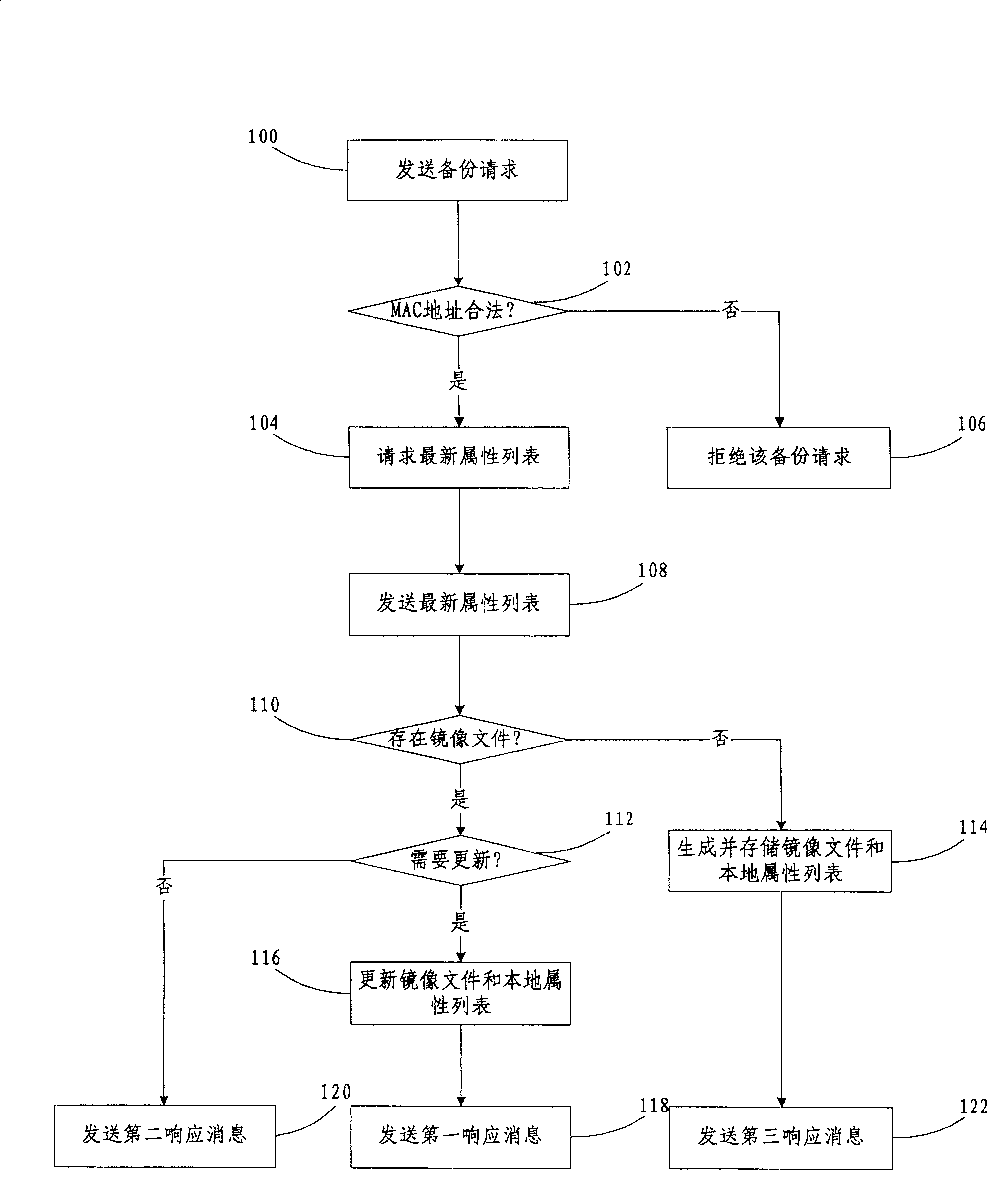
System backup and recovery method, and backpu and recovery server
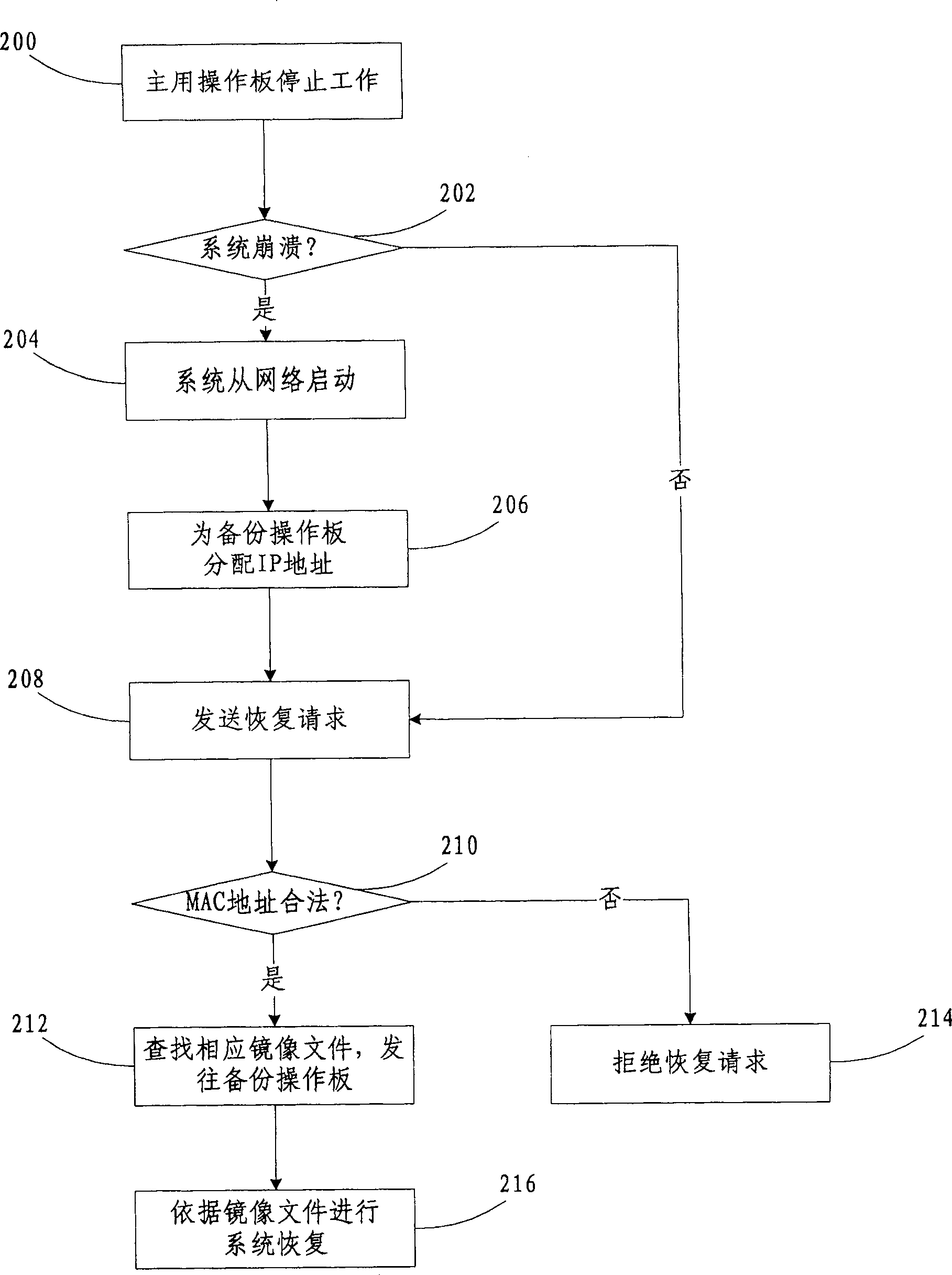
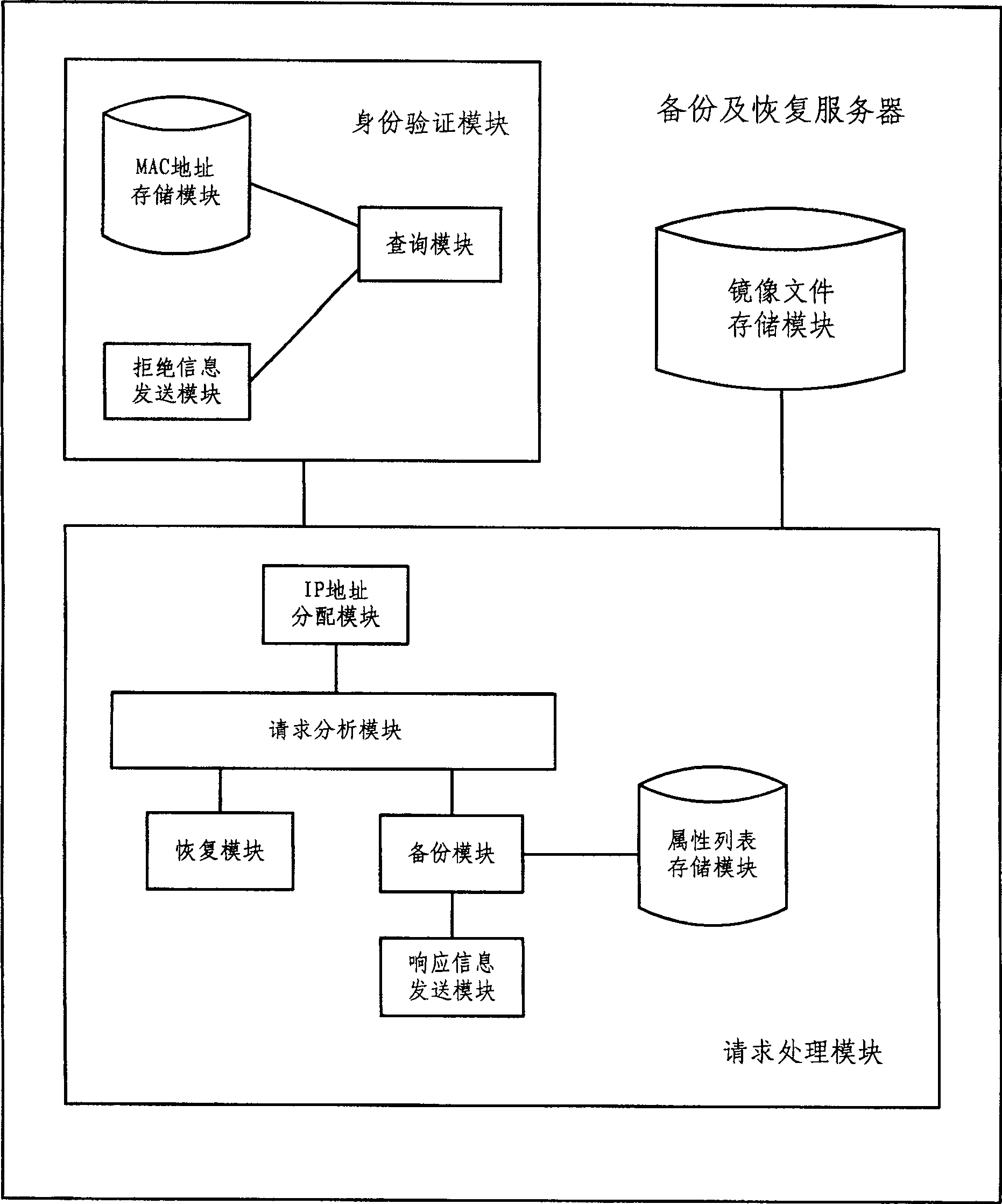
ActiveCN100505614CImprove reliabilityTroubleshoot authentication issuesError preventionUser identity/authority verificationRecovery methodSystem recovery
The invention discloses a system backup method with ID checking. The backup server judges whether the MAC address of backup aim board of sending the backup request is legal or not; if yes, then responding the request; otherwise, rejecting the request. This invention offers also a system restoration method as well as a backup and restoration server related to the above two methods. Using MAC address in multi-host backup to verify ID of backup aim board exerts advantages of hi-reliability of multi backup as well as realizes the ID checking in multi backup system based on the aid of the uniqueness of the MAC address.
Owner:XFUSION DIGITAL TECH CO LTD
Method for terminal of Internet of Things to communicate with Internet host
InactiveCN103957232ATroubleshoot authentication issuesSolve the resolution problemData switching networksTTEthernetComputer network
The invention discloses a method for a terminal of the Internet of Things to communicate with an Internet host, for controlling and protecting various wireless devices in the Internet of Things of a wireless data collector. The method comprises the following content: the types of the wireless devices comprise wireless networking devices, wireless switches, wireless PDAs and wireless mobile phones. The wireless networking devices are in grid connection with other types of wireless devices for grid connected control, and the grid connection mode of the wireless devices comprises initial grid connection and re-grid connection; the communication structure of the Internet of Things employs motion type protection and timely reflects the situations about the wireless devices in the Internet of Things accessing into / breaking from the Internet of Things; and by means of wireless environment adjusting step type bandwidth switching, when a wireless environment is lower than a tolerance threshold, step type bandwidth is switched to a wireless environment with a better channel for transmission of the Internet of Things. According to the invention, the method for the terminal of the Internet of Things to communicate with the Internet host is established, and a user is provided with higher-quality support for the Internet of Things of the wireless data collector.
Owner:BEIJING LIHESHUNDA ELECTRONICS TECH
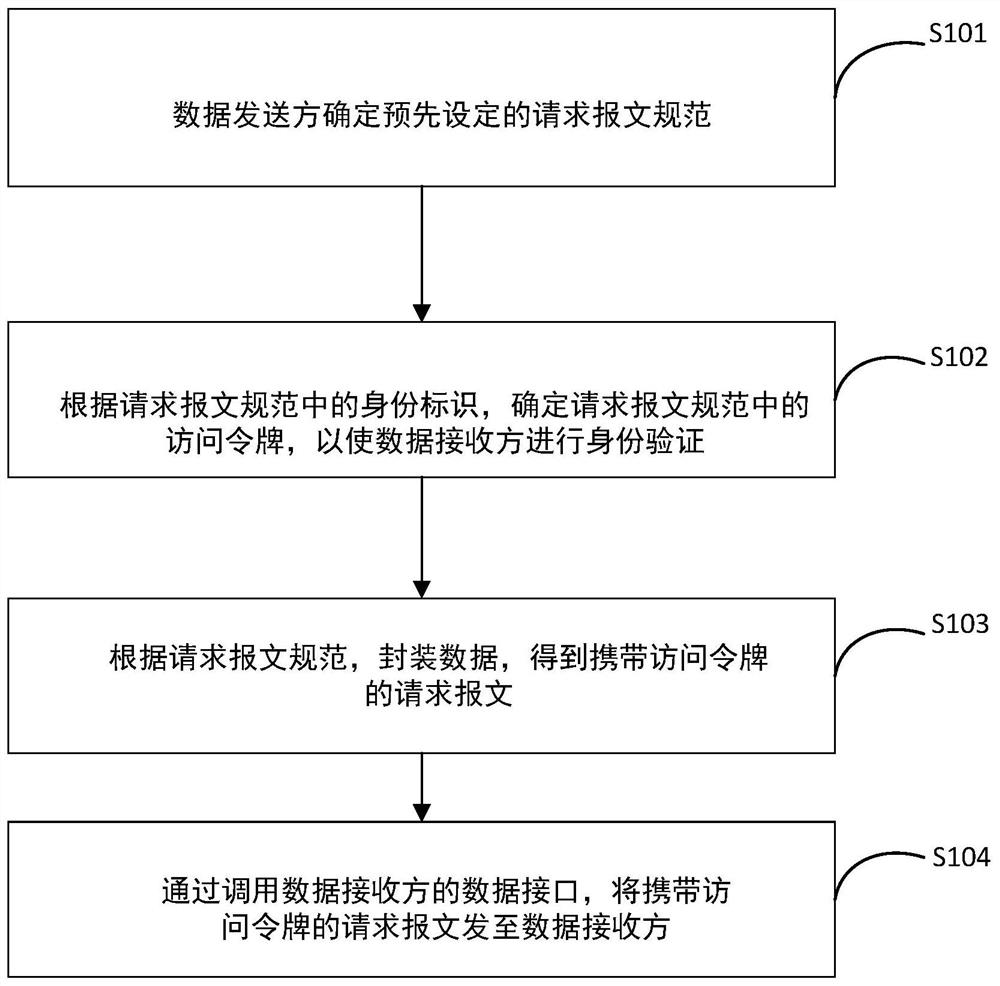
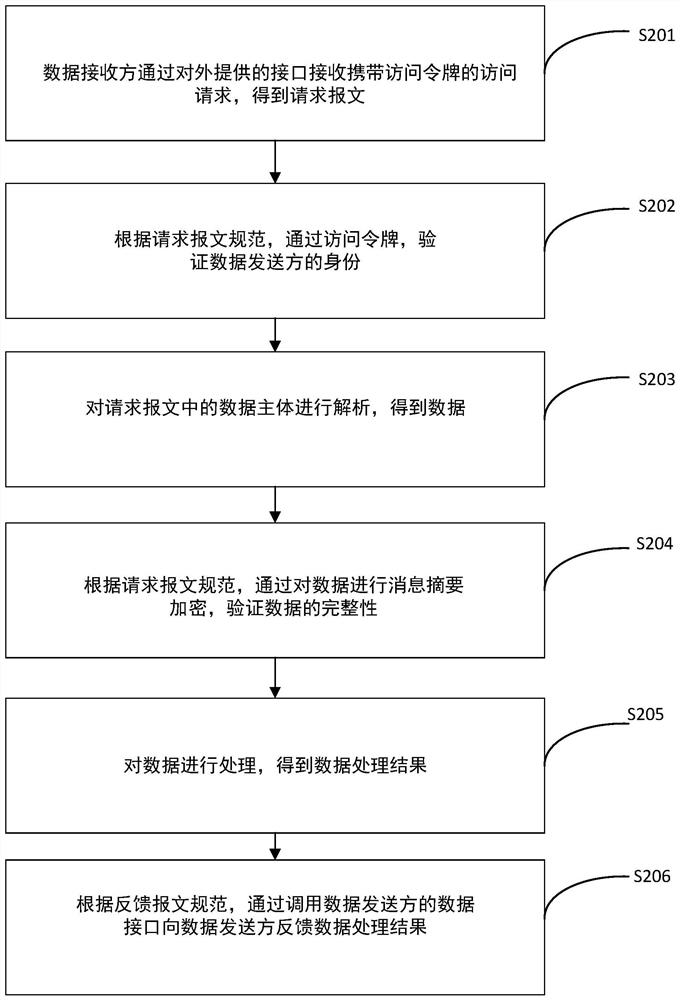
Data interface docking method and device
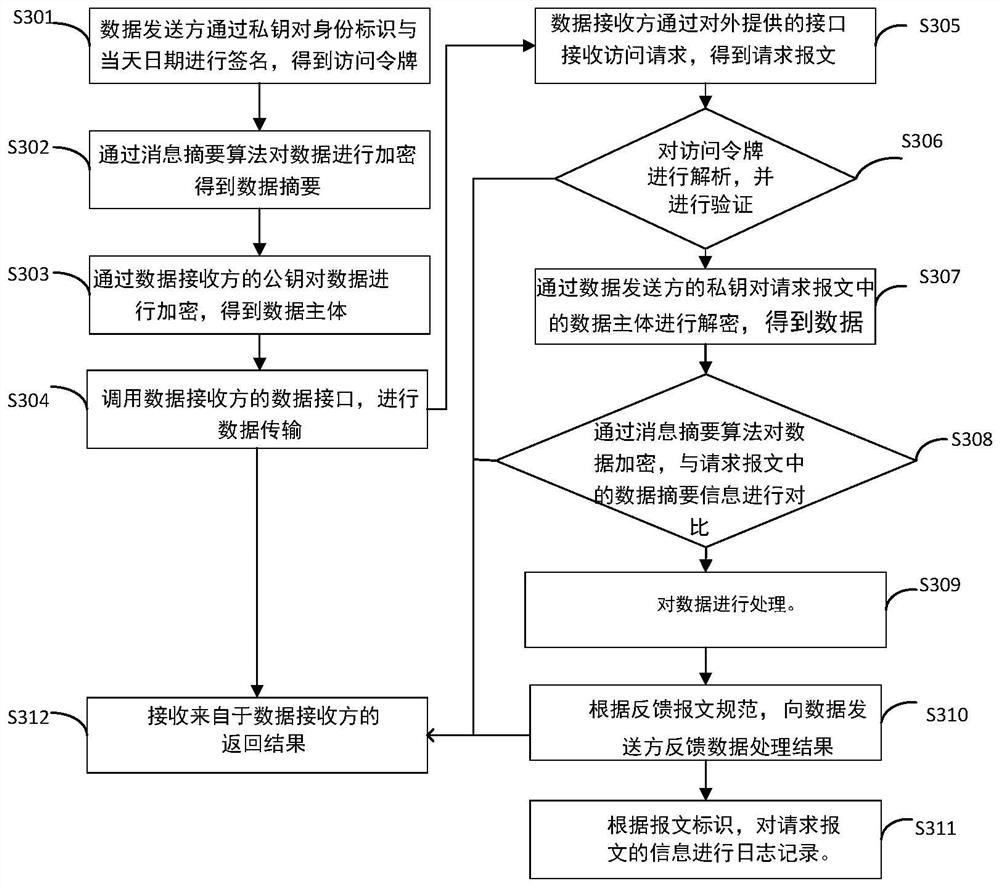
ActiveCN112261002ASatisfy the security requirements of encrypted transmissionReduced development effortTransmissionEncapsulated dataData transmission
The invention discloses a data interface docking method and device. The method comprises the steps that a data sender determines a preset request message specification, wherein the request message specification is obtained through agreement of the data sender and the data receiver; determining an access token in the request message specification according to an identity identifier in the request message specification, so that the data receiver performs identity authentication; encapsulating data according to the request message specification to obtain a request message carrying an access token; and sending the request message carrying the access token to the data receiver by calling a data interface of the data receiver. Through a standard interface parameter, the security requirements ofsystem identity authentication and data encryption transmission can be met at the same time, the security of data transmission is ensured, and various application systems can directly adopt and use the method.
Owner:INSPUR COMMON SOFTWARE
A self-service teller machine based on three-face recognition
InactiveCN103871174BTroubleshoot authentication issuesSolve the problem of inaccurate face recognitionComplete banking machinesDigital data authenticationInformation deviceCard reader
The invention relates to an automatic teller machine based on face recognition on three sides. The automatic teller machine is characterized by comprising a main machine, a camera group, a semitransparent customer operating room, a large touch screen, a light adjusting device, a face recognition device, an identity card reader, an identity card double-sided scanning device, a second-generation identity card reader, a second-generation identity card double-sided scanning device, two USB (universal serial bus) digital certificate interface, an online verification citizen identity information device, a cleaning towel device and a remote background service processing center; the automatic teller machine photographs a picture of a customer to be respectively checked with the picture on the identity card read by the identity card reader and the picture of the identity card returned by the online verification citizen identity information system, and the service can be carried out when the picture is successfully checked; the identity card is withdrawn if the picture checking is failed, the cleaning towel device is powered on, the customer is reminded of removing a helmet, a gauze mask and spectacles and having normal facial expression so as to repeatedly check; when the picture is still failed in the second checking and the customer still applies to the service, the host machine calls the remote background service processing center to process.
Owner:西安美达威网络科技有限公司
Design method of tidal river flood control and tidal protection coastline
ActiveCN108532532BTroubleshoot authentication issuesEffective simulationHydraulic modelsHydrometryTerrain
Owner:FUJIAN PROVINCIAL INVESTIGATION DESIGN & RES INST OF WATER CONSERVANCY & HYDROPOWER
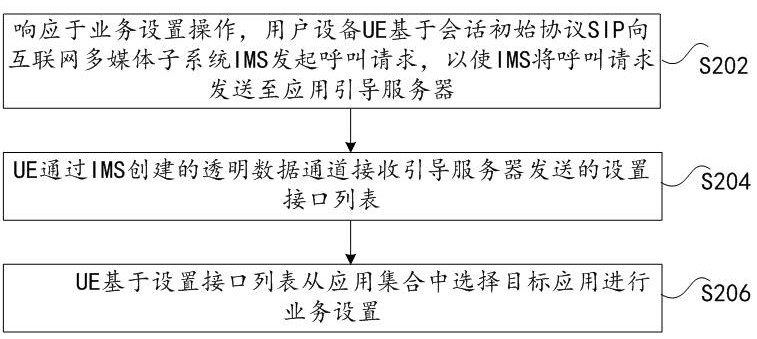
Service setting method and device, storage medium and electronic device
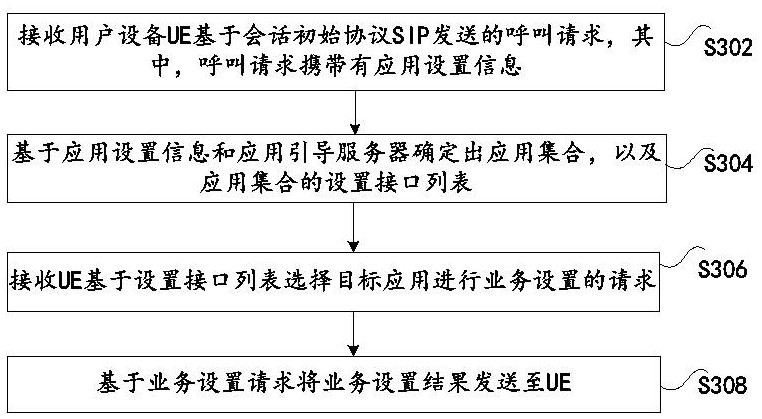
ActiveCN113709190BFix setup inefficienciesImprove setup efficiencySecuring communicationSession Initiation ProtocolEngineering
Embodiments of the present invention provide a service setting method and device, a storage medium, and electronic equipment; the method includes: in response to the service setting operation, the user equipment UE initiates a call request to the Internet Multimedia Subsystem IMS based on the Session Initiation Protocol SIP, so that The IMS sends the call request to the application guidance server; wherein, the call request carries application setting information, and the application setting information is used to enable the application guidance server to determine the application set and the set interface list of the application set; the UE receives it through the transparent data channel created by the IMS The setting interface list sent by the application guidance server; the UE selects a target application from the application set based on the setting interface list to perform service setting. The present invention solves the problems of low efficiency of IMS service setting and difficulty in application access caused by the need for additional HTTP authentication on the UT interface, thereby achieving the effects of improving the efficiency of IMS service setting and reducing the difficulty of service deployment.
Owner:ZTE CORP
Power supply system ground simulation comparison test system and method
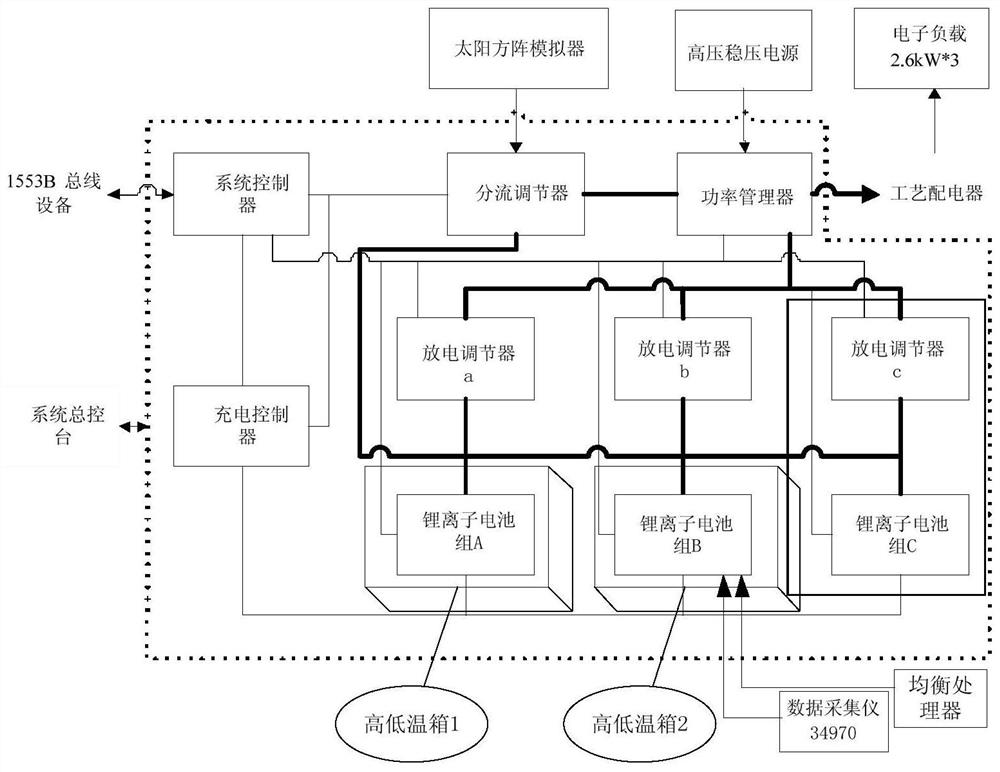
ActiveCN112462290AVerification abilityVerify reliabilityElectric powerPower supply testingElectronic loadElectrical battery
The invention provides a power supply system ground simulation comparison test system and method, and the system comprises a power supply system, 1553 bus equipment, a system console, a solar array simulator, a high-voltage stabilized power supply, an electronic load, a power distributor, a high-low temperature box, a data collection instrument, and an equalization processor. The power supply system comprises a storage battery pack, a bus voltage adjusting unit and a storage battery charging control unit, wherein the storage battery pack comprises a lithium ion storage battery pack A, a lithium ion storage battery pack B and a lithium ion storage battery pack C; the bus voltage regulating unit comprises a shunt regulator, a power manager, a discharge regulator and a system controller; thestorage battery charging control unit includes a charging controller. According to the invention, the actual temperature difference of each group of on-orbit batteries is simulated through the high-low temperature box, which is closer to the real working condition of on-orbit operation of the spacecraft, and the working capability and reliability of the multi-unit grid-connected aircraft power supply system can be verified.
Owner:SHANGHAI INST OF SPACE POWER SOURCES
Method and system for dynamically authenticating password by multi-password seed self-defined by user
InactiveCN102148685BTroubleshoot authentication issuesMultiple keys/algorithms usageUser identity/authority verificationReal-time clockPassword
The invention aims to disclose a system for dynamically authenticating a password by a multi-password seed self-defined by a user. The method and the system are implemented by user equipment, a server system, server password generation equipment, a registration method and an authentication method. A user inputs a primary password and a secondary password at the user equipment, performs conversion to obtain a password seed, and submits the password seed to a server for registration and binding. When authentication is required, the server obtains a current authentication time by a real time clock, displays the current authentication time on a user interface, and can obtain a current server password of the user by the password seed submitted in the registration of the user and the authentication time. The user inputs the primary and secondary passwords at the user equipment, the server displays the current authentication time, and the conversion is performed to obtain a user password. The user password is judged whether to be consistent with the server password by comparison, and then a user operation can be verified whether to be legal or not. By the authentication method and the authentication system, all authentication needs of online authentication, offline authentication and the like can be satisfied. By the method provided by the invention, not only the absolute privacy of password information set by the user can be ensured, but also the problem of middleman breach of confidence which cannot be solved by a conventional dynamic password system is solved; and when using a multi-authentication server, the user is not required to buy and carry a plurality of pieces of user dynamic password equipment, so the user cost is reduced.
Owner:陈祖石
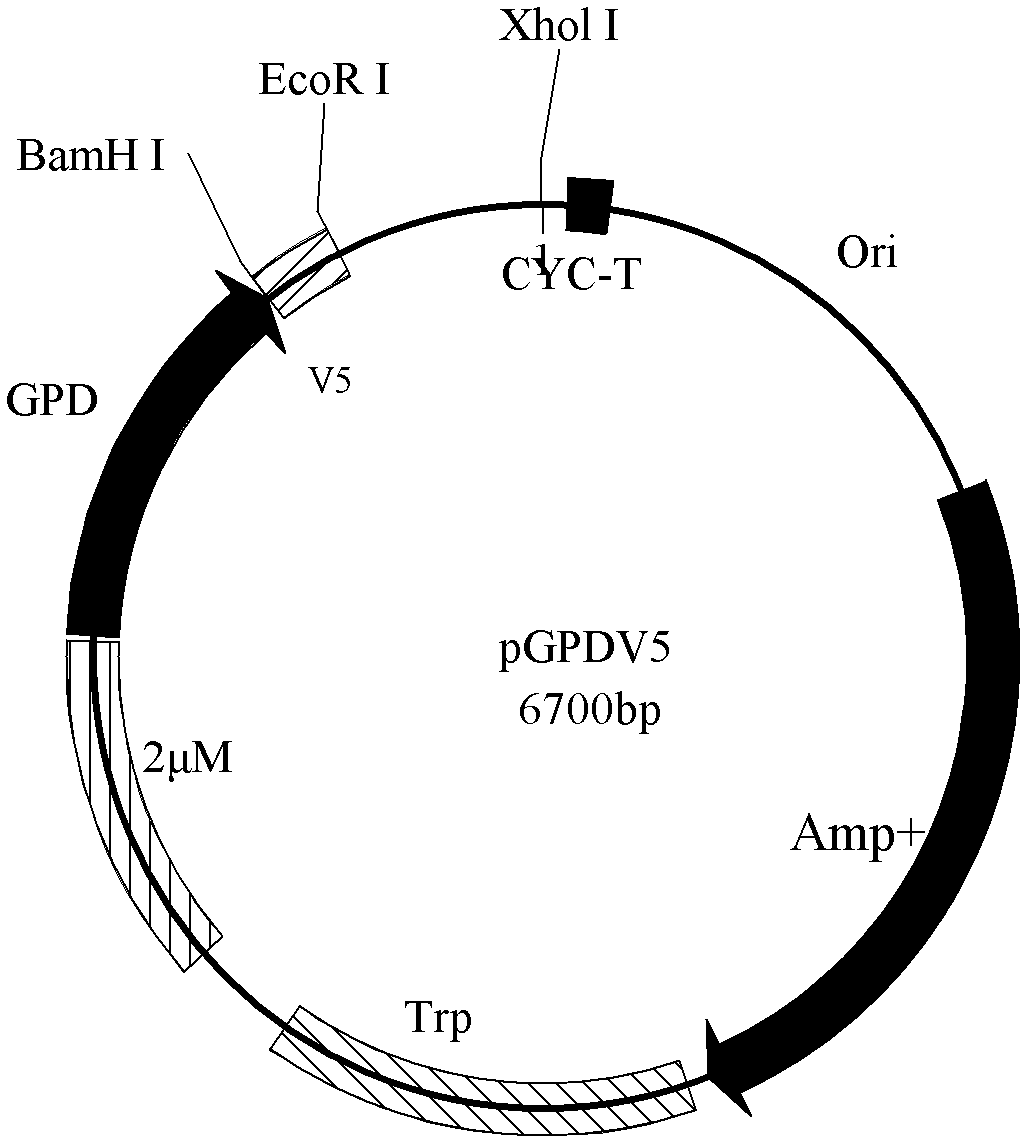
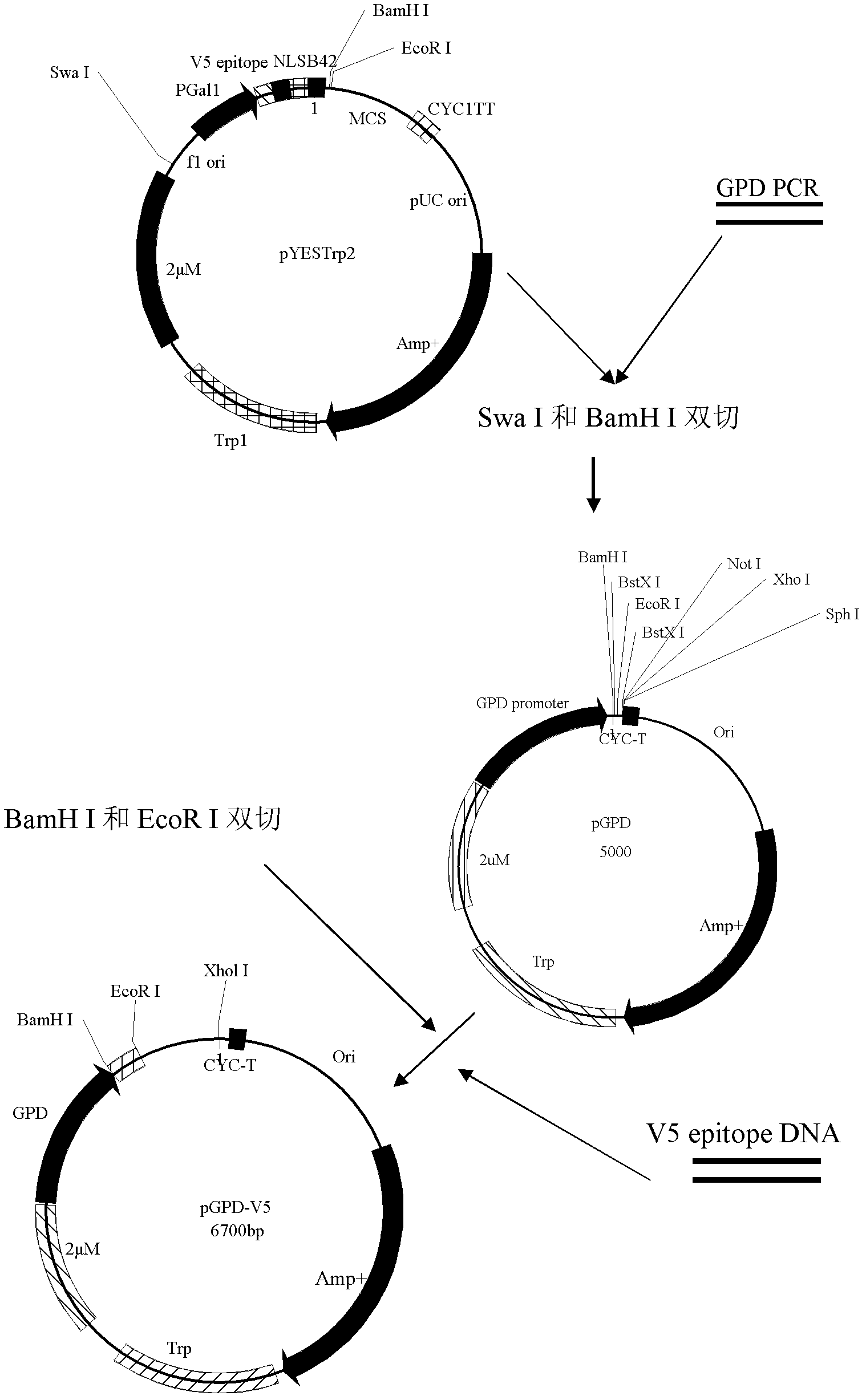
V5 epitope fusion yeast expression vector and construction method thereof
InactiveCN102533843ATroubleshoot authentication issuesVector-based foreign material introductionYeastEpitope
The invention relates to a V5 epitope fusion yeast expression vector and a construction method thereof. The V5 epitope fusion yeast expression vector is a yeast expression vector containing a V5 tag, wherein the tag can be fused with downstream genes through a flexible small peptide Gly-Ile, and the biological activity of downstream expression proteins cannot be affected. The construction method comprises the following steps of: taking a pYestrp2 vector of Invitrogen as a basic framework, inserting a yeast strong promoter GPD into the pYestrp2 vector to construct a yeast expression vector pGPD, and inserting V5 epitope DNA with BamHI and EcoRI cohesive termini at 5' and 3' ends into corresponding endonuelease sites of the pGPD to construct a V5 fusion yeast expression vector pGPDV5, wherein the pGPDV5 can be fused with the downstream genes through flexible small peptides. According to the invention, as V5 antibodies are commercialized, the expression of exogenous genes in yeast cells can be conveniently, specifically and effectively verified, and the cost is relatively low.
Owner:YANGZHOU UNIV
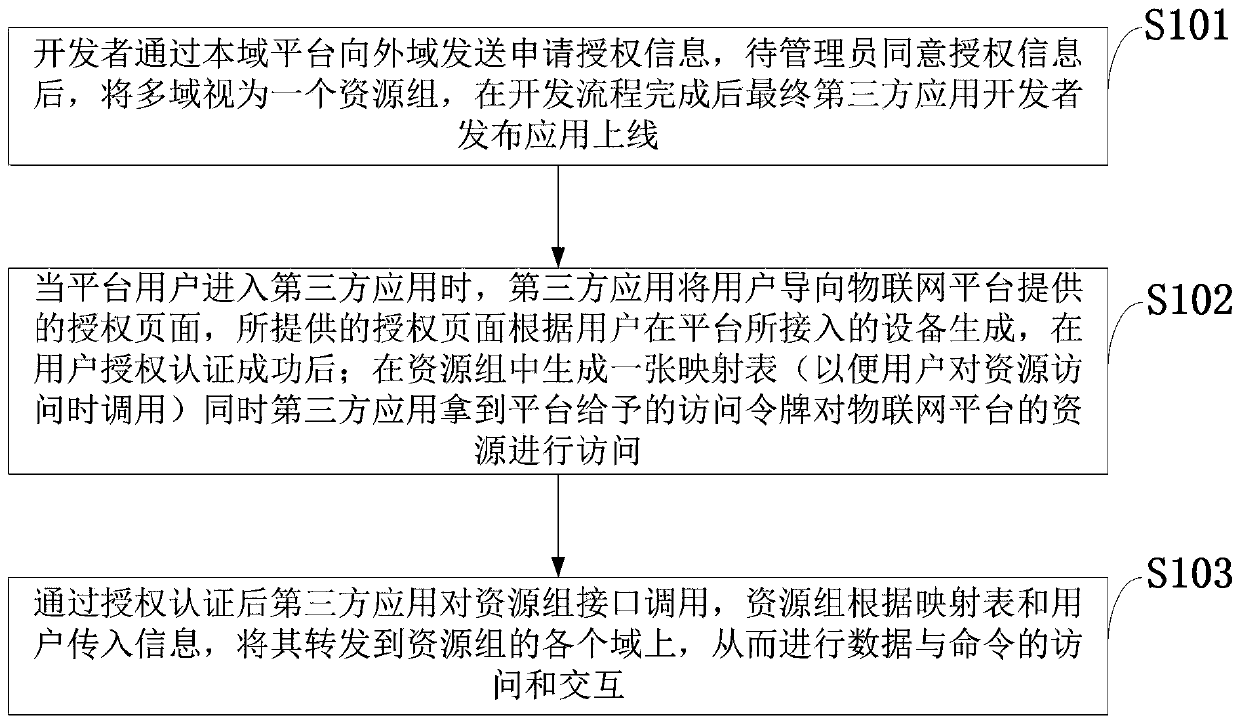
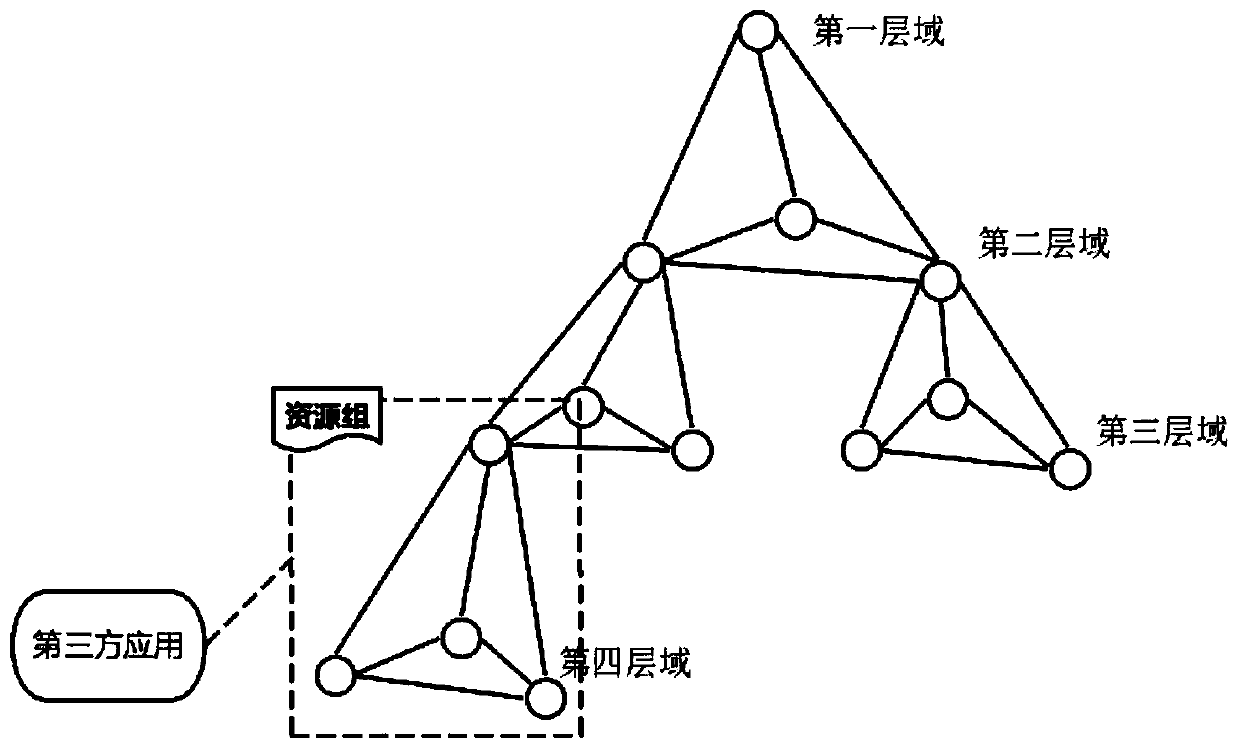
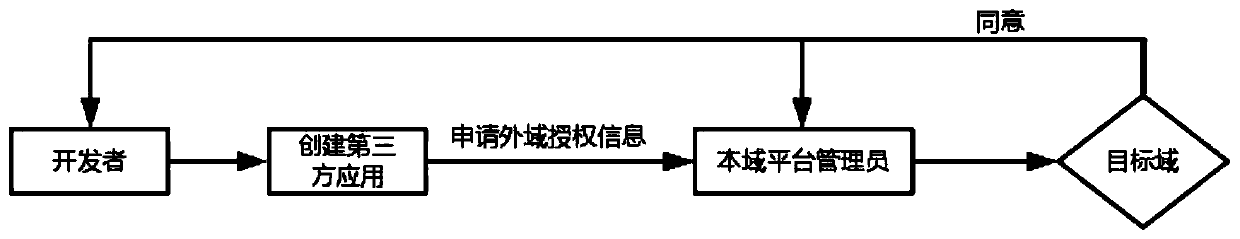
A third-party application authorization authentication method based on multi-domain collaborative architecture
ActiveCN107018128BSafe and reliable authorized accessTroubleshoot authentication issuesTransmissionThird partySoftware engineering
Owner:陕西沃傲信息科技有限公司
Simulation platform and method based on IEEE802.1X security protocol of EAP
InactiveCN101360020BIntegrity guaranteedGuaranteed non-repudiationData switching by path configurationRound complexityConfidentiality
The invention provides a simulation platform based on the IEEE802.1X secure protocol of EAP as well as a method thereof, wherein, a wireless_lan_mac module in the original wireless node of OPNET is improved, and extended authentication modules are added including an EAP authentication module and a port control module, and the added parts and the wireless_lan_mac module are converged to add the function of security authentication successfully. The EAP authentication module is provided with an authenticator and an applicant communicating mutually to complete the security authentication, so the authentication process is presented completely, meanwhile, the complexity is not high and the simulation efficiency is rather good. The port control module is acquired through the equivalent transformation by a finite state machine of IEEE802.1X, the design correctness of a protocol model state machine is ensured, and the disorder among model versions is avoided. The invention realizes the simulation scene for roaming and re-authentication in different BSS of the wireless node, and solves the authentication problem of roaming access. The invention can ensure the integrity, non-repudiation and confidentiality of WLAN data, and can test other various realized wireless secure protocols and multimode access among various protocols on that basis.
Owner:XIDIAN UNIV
Ground detection device
ActiveCN107037256BTroubleshoot authentication issuesEasy to carryCurrent/voltage measurementFault location by conductor typesDevice simulationHemt circuits
A grounding detection device comprises a shell. The shell is internally hollow to form a holding cavity. The grounding detection device also comprises a simulation short-circuit circuit output interface, a voltage detection interface, an input device and an output device which are fixed on the shell, and a power supply, a simulation circuit current generation device, a voltage detection device and a processing device which are fixed in the holding cavity. The input device is used for the personnel to input the physical parameters of the soil in the area where the grounding grid is located, the fault parameters of the electrical equipment with the grounding fault and the design parameters of the grounding grid, then the processing equipment is enabled to obtain the actual value of the target voltage, the required value of the target voltage and the theoretical value of the target voltage which are output by the output device. The grounding detection device can improve the acceptance accuracy and efficiency, is easy to carry, and can be applied to the design and acceptance stages.
Owner:CHINA GENERAL NUCLEAR POWER OPERATION +2
A credit-based service system and method
PendingCN111091458AProtect interestsNo security issuesFinanceDigital data authenticationCredit systemThe Internet
The invention relates to the field of financial science and technology, and discloses a credit-based service system and an application method. According to the invention, a credit-based service systemis constructed, and based on the credit-based service system, all transactions in the system can be ensured to be real or traceable and are non-repudiation. The credit service system provided by theinvention is a financial service system and method. Internet and financial science and technology are applied; financial transactions and financial behaviors are established under a credit system, allfinancial behaviors become credit behaviors under a credit service system, through the service system and method, the virtual world, namely the Internet, is connected with the entity world with credit, and the financial behaviors become real, credible and traceable. Financial science and technology tools and technologies such as the Internet, big data, distributed data processing, a cloud technology, a database and a terminal technology are utilized.
Owner:王永勤
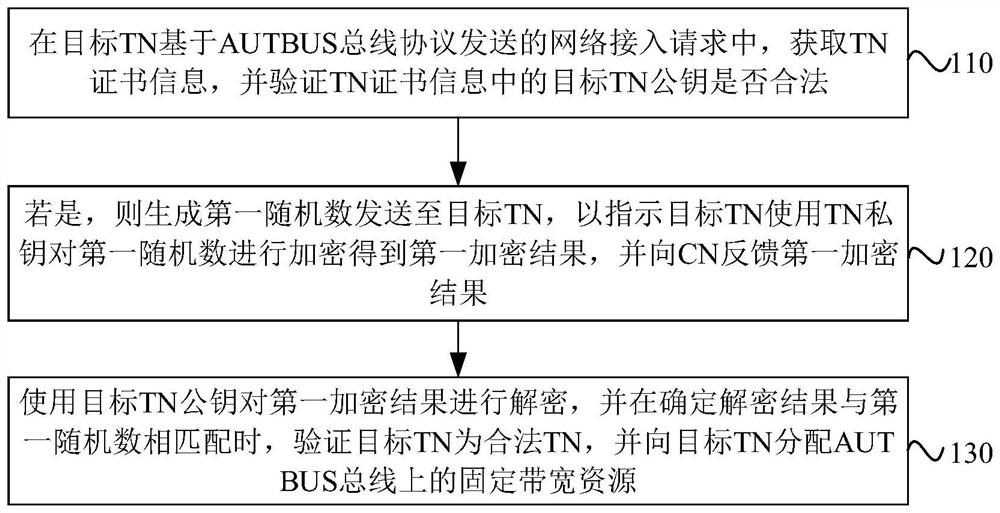
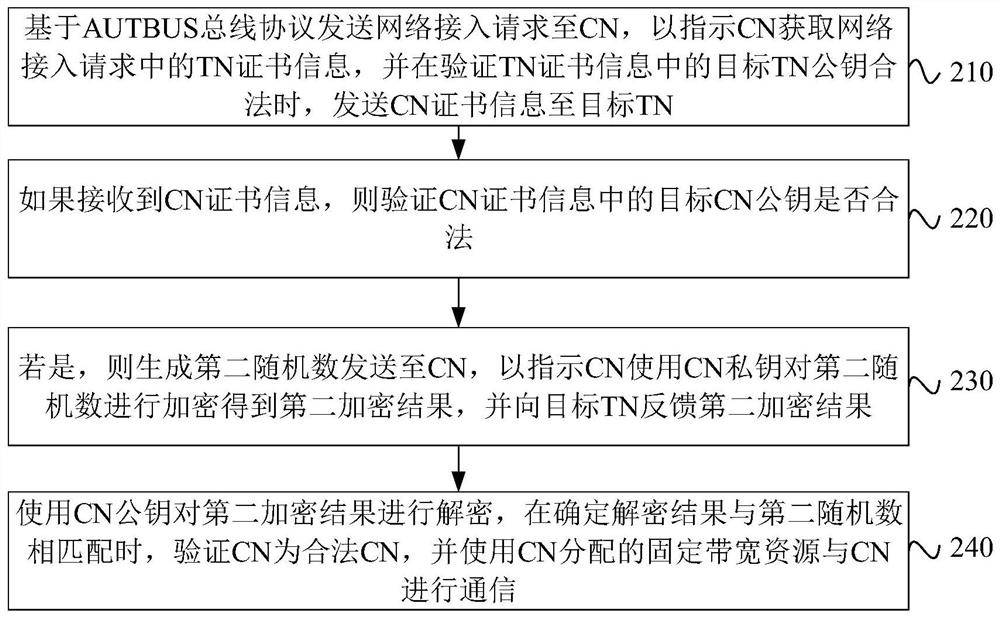
Communication method, system and device based on AUTBUS and medium
PendingCN114124378AAvoid accessTroubleshoot authentication issuesKey distribution for secure communicationUser identity/authority verificationCommunications securityInternet privacy
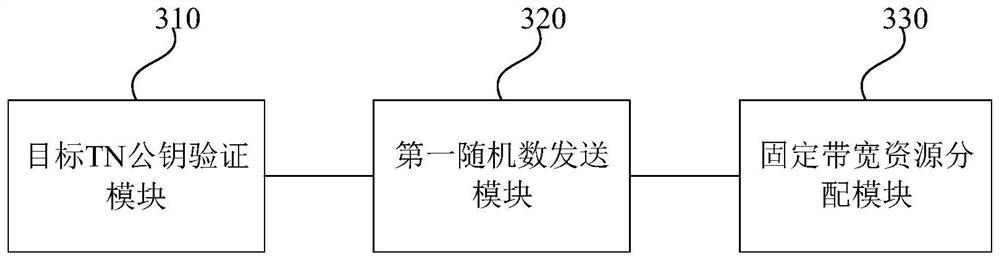
The embodiment of the invention discloses a communication method, system and device based on an AUTBUS and a medium. The method is executed by a CN, and comprises the following steps: in a network access request sent by a target TN based on an AUTBUS bus protocol, obtaining TN certificate information, and verifying whether a target TN public key in the TN certificate information is legal; if yes, generating a first random number, sending the first random number to the target TN to indicate the target TN to encrypt the first random number by using the TN private key to obtain a first encryption result, and feeding back the first encryption result to the CN; and decrypting the first encryption result by using the target TN public key, verifying that the target TN is a legal TN when determining that the decryption result is matched with the first random number, and allocating fixed bandwidth resources on the AUTBUS to the target TN. According to the method, the equipment identity can be verified when the AUTBUS equipment is accessed, so that the legality of the equipment is ensured, and the communication security is further ensured.
Owner:北京神经元网络技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com