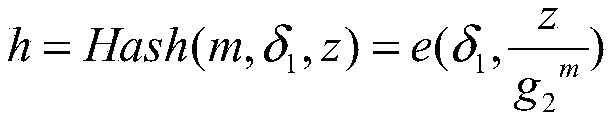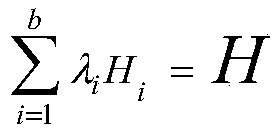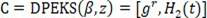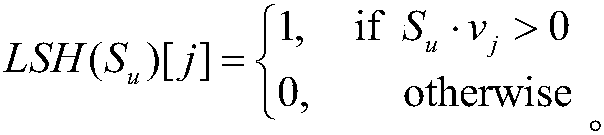Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
88results about How to "Protection from being leaked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
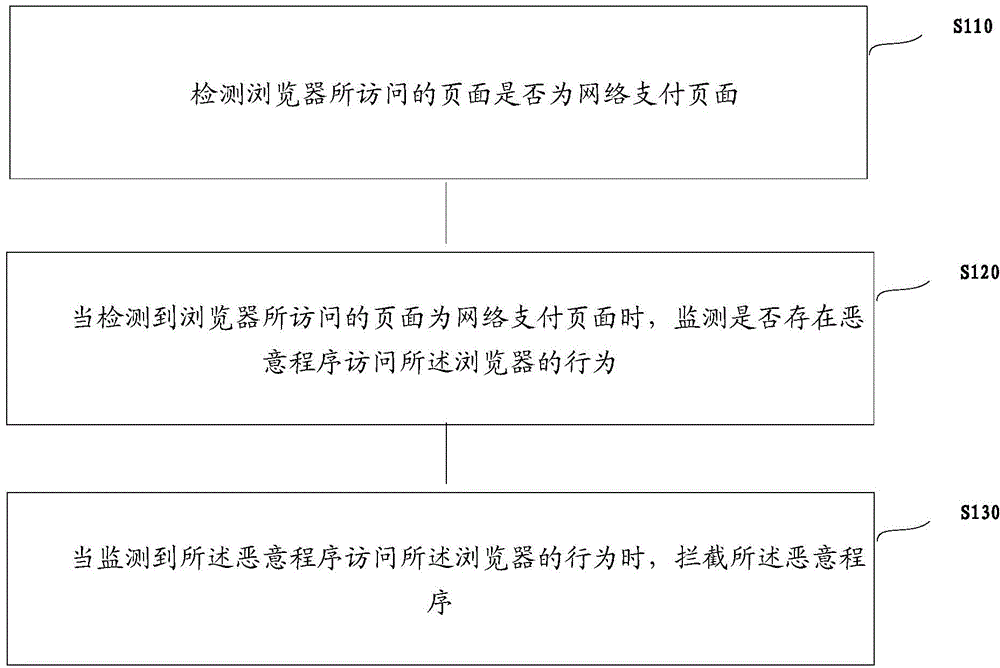
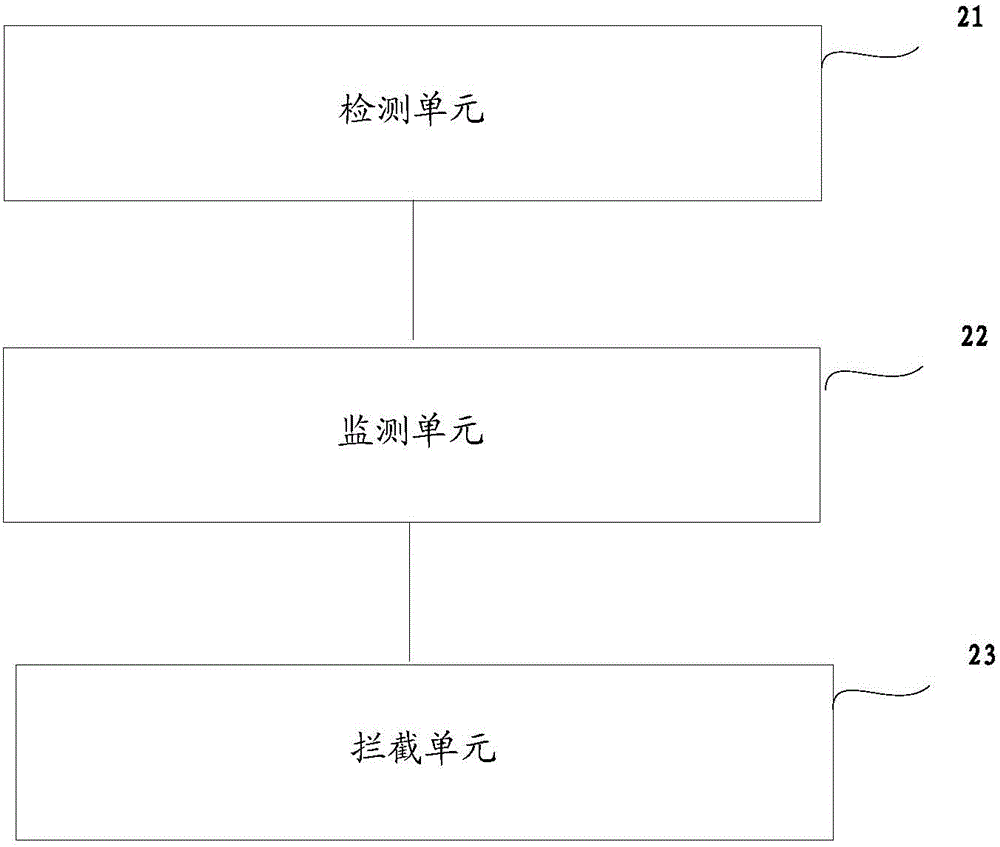
Method and device for preventing malicious program from attacking online payment page
ActiveCN103605924AEasy to monitorProtection from being leakedPlatform integrity maintainanceComputer securityNetwork communication
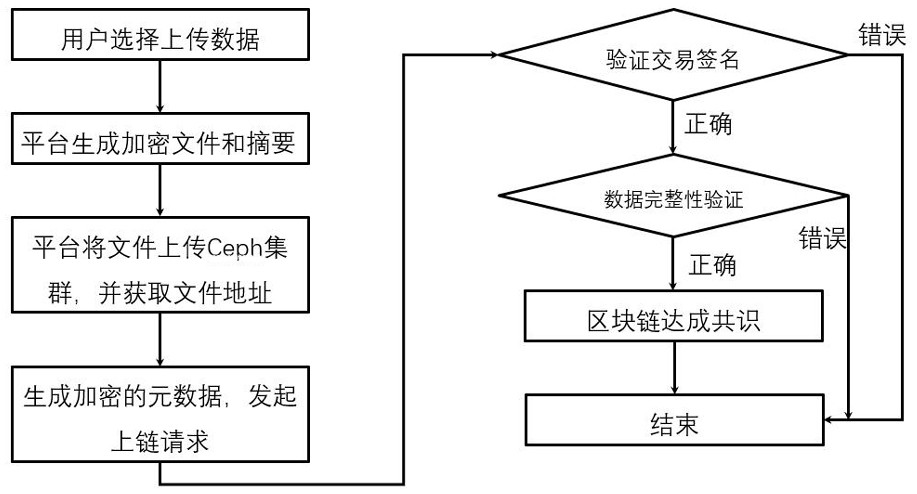
The invention relates to the technical field of network communication, and discloses a method and device for preventing a malicious program from attacking an online payment page. The method includes the steps of detecting whether a page to which a browser has access is the online payment page or not, monitoring whether a behavior that the malicious program has access to the browser exists or not when the page to which the browser has access is detected to be the online payment page, and interrupting the malicious program when the behavior that the malicious program has access to the browser is monitored to exist. Therefore, once the page to which the browser has access is detected to be the online payment page, monitoring of the browser is enhanced, so that whether the behavior that the malicious program has access to the browser exists or not can be conveniently determined when the browser has access to the online payment page. When the behavior exists, the malicious program is interrupted, and therefore payment information can be protected against leakage, and the payment safety effect is improved.
Owner:BEIJING QIHOO TECH CO LTD
SM2 signature algorithm protection method for resisting error attack based on lattice
ActiveCN104852805AFull resistanceAvoid being leakedUser identity/authority verificationDigital data protectionScalar multiplicationComputer security
The present invention discloses an SM2 signature algorithm protection method for resisting error attack based on lattice. The method comprises the following steps: (1) a signer A carries out Hash operation on an inputted message M to be signed and combines an operation result ZA and the message M to obtain M<->, (2) M<-> is subjected to hashing compression to obtain a pre-processing result e, (3) two random numbers k and w are generated, the scalar multiplication kG of the random number k and a base point G and the scalar multiplication wPA of the random number w and a public key PA are calculated respectively, then the above two scalar multiplications are summed to an elliptic curve point Q, (4) the coordinate x1 mode n add of e and point Q is calculated to obtain an r value, (5) private keys dA, k, w, r are subjected to substitution to obtain a signature result s. By using the method provided by the invention, the lattice attack of an SM2 signature algorithm can be effectively and comprehensively resisted.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +2
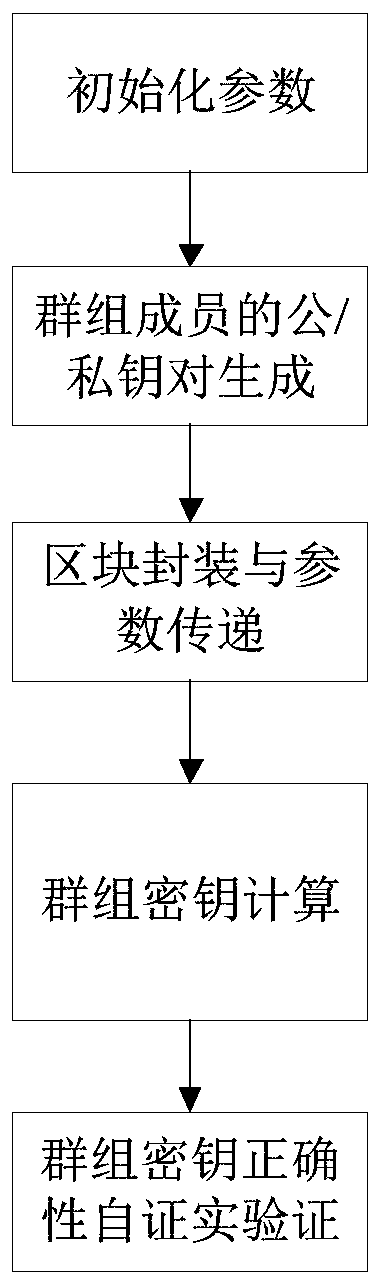
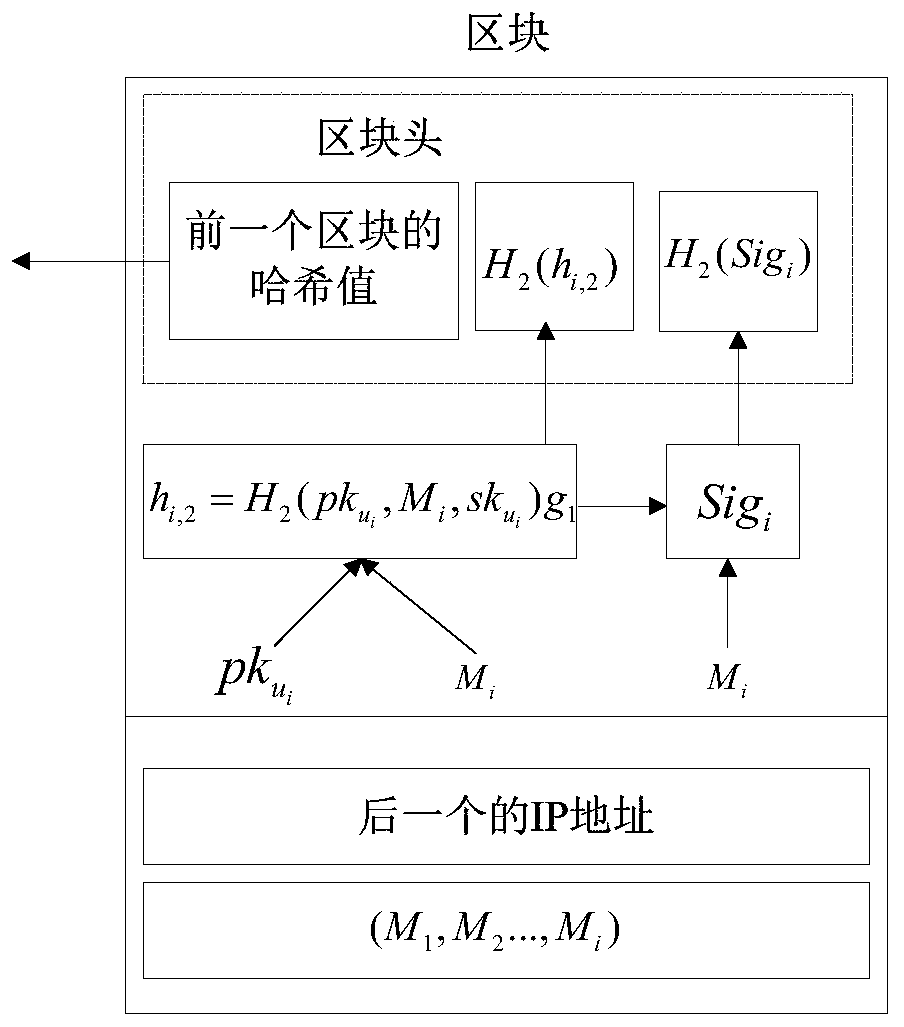
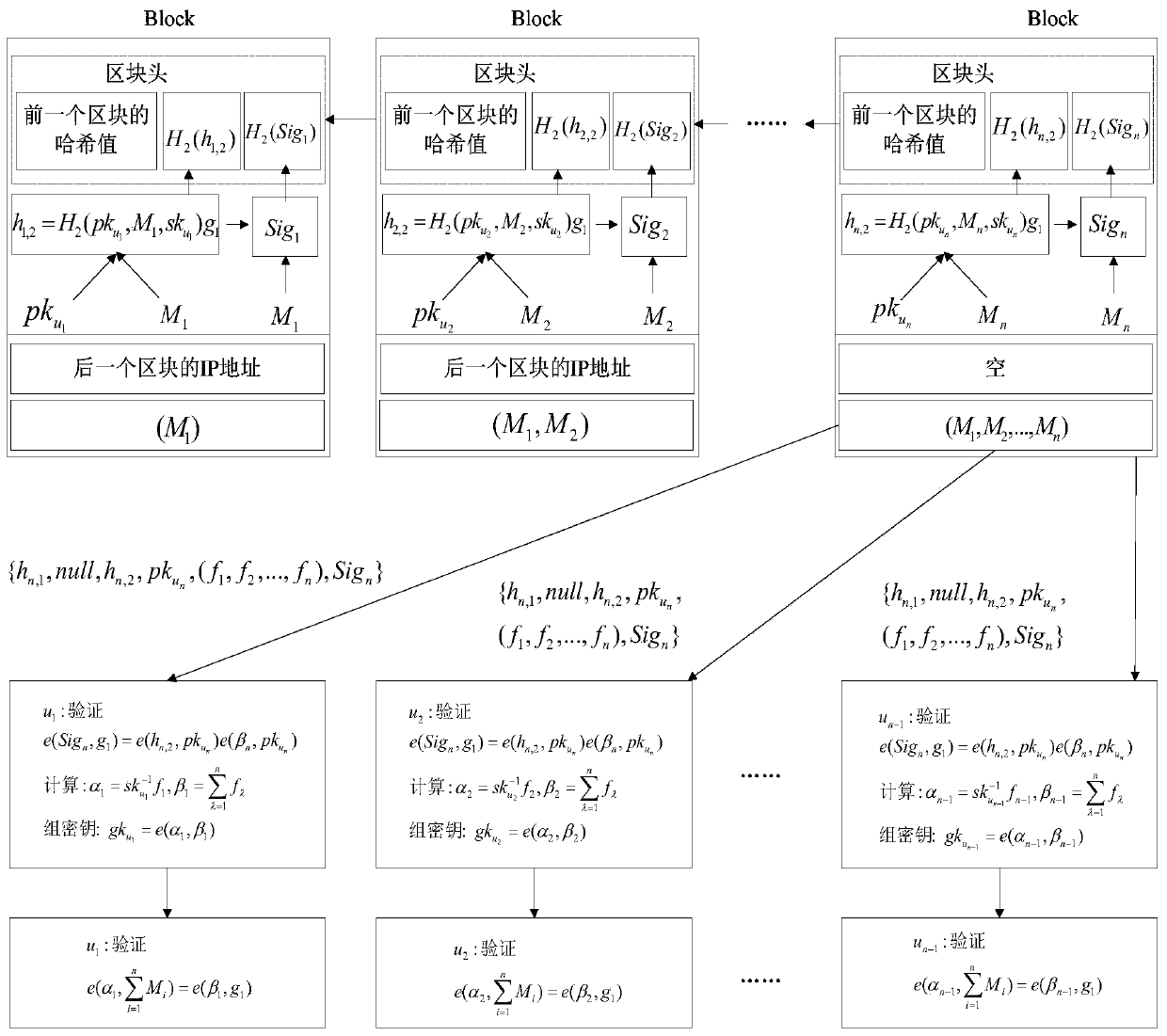
Symmetric group key negotiation method based on block chain
ActiveCN110011795AEnable secure exchangePrevent crashKey distribution for secure communicationUser identity/authority verificationBlockchainIp address
The invention provides a symmetric group key negotiation method based on a block chain. The symmetric group key negotiation method comprises the following steps that a key generation center and terminal members in a group information exchange network domain generate respective public / private key pairs; information composed of the IP addresses and the public key pairs is mutually broadcasted amongthe terminal members, and the information is ranked based on the sizes of the IP addresses to obtain a sequence pair set of all the members of the group; the first node in the sequence pair set packages the message composed of the group key parameters to a block and transmits the message to the next node, and the steps are sequentially circulated to the last node; the last node calculates a groupkey of the last node, packages a message composed of group key parameters into a block and broadcasts the message to other nodes; the other nodes calculate respective group keys; group key correctnessverification is performed. The personal privacy is protected by adopting a block chain technology, so that the group key calculation and communication are more balanced, the traceability is high, andthe group key negotiation of the mobile ad hoc network is more flexible, efficient and practical.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
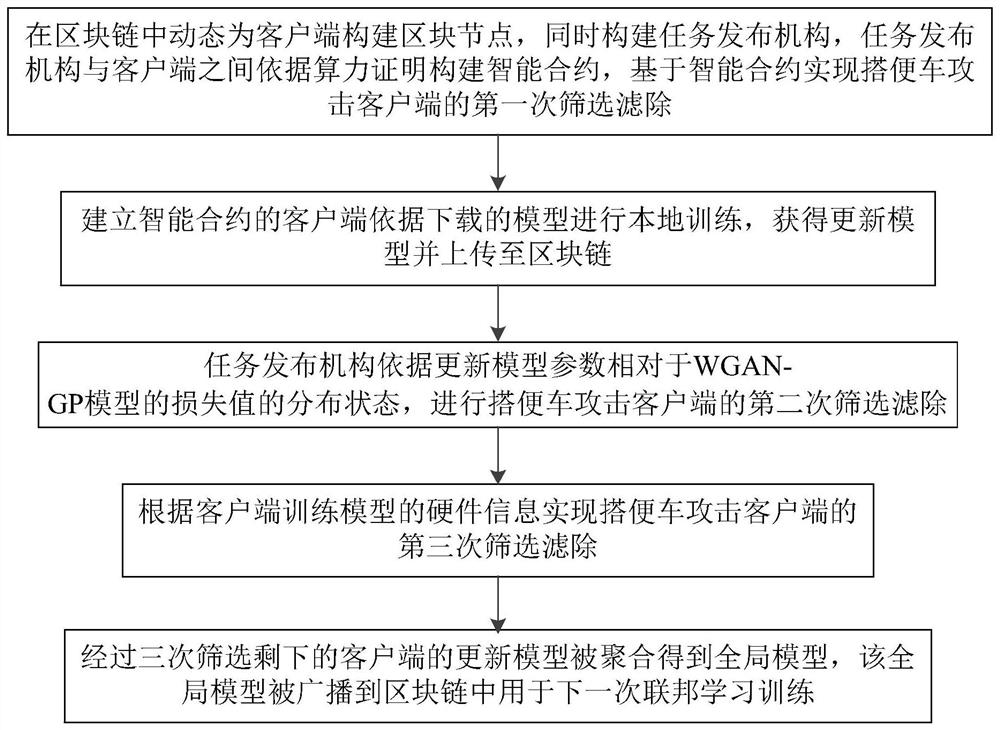
Federated learning toilet vehicle attack defense method based on block chain
ActiveCN112714106APrivacy protectionProtection from being leakedMachine learningTransmissionAttackEngineering
The invention discloses a federated learning toilet vehicle attack defense method based on a block chain, and the method comprises the steps: building an intelligent contract between a task publishing mechanism and a client in the block chain according to a calculation capability proof, and achieving the first screening and filtering of a toilet vehicle attack client based on the intelligent contract; enabling the task issuing mechanism to perform secondary screening and filtering of the toilet vehicle attack client according to the distribution state of the updated model parameters of the client relative to the loss value of the WGANGP model; according to the hardware information of the client training model, realizing the third screening and filtering of the toilet vehicle attack client; and aggregating the update models of the remaining clients after three times of screening to obtain a global model, wherein the global model is broadcasted to the block chain for next federation learning training. According to the method, the toilet car attacking client is prevented from participating in aggregation to obtain the aggregation model, defense of federated learning toilet car attacks is achieved, and then privacy of the client and leakage of a global model are protected.
Owner:HANGZHOU QULIAN TECH CO LTD
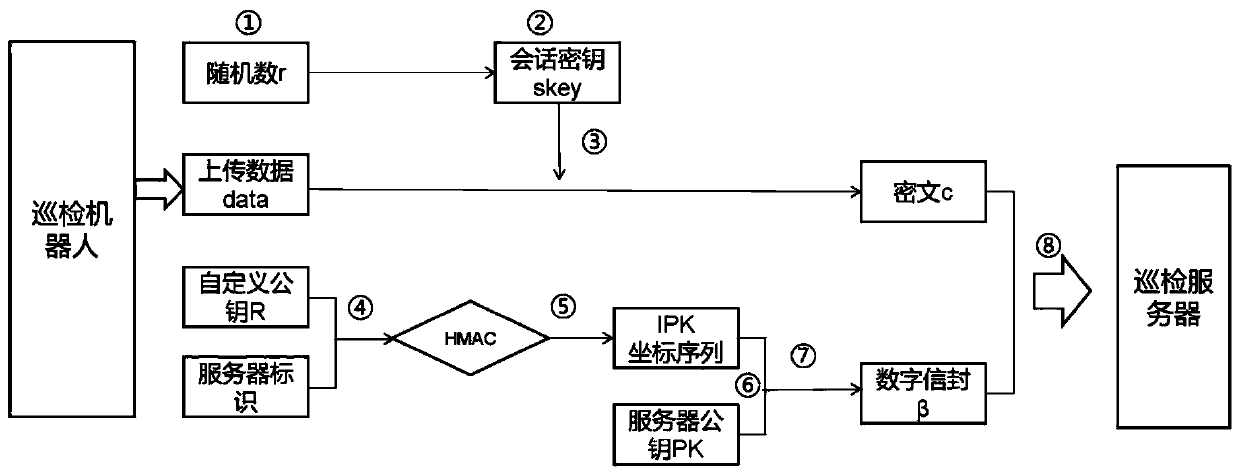
Substation inspection robot data transmission encryption and decryption method and system
ActiveCN110995716AProtection from being leakedSolve management problemsKey distribution for secure communicationRegistering/indicating time of eventsAlgorithmCiphertext
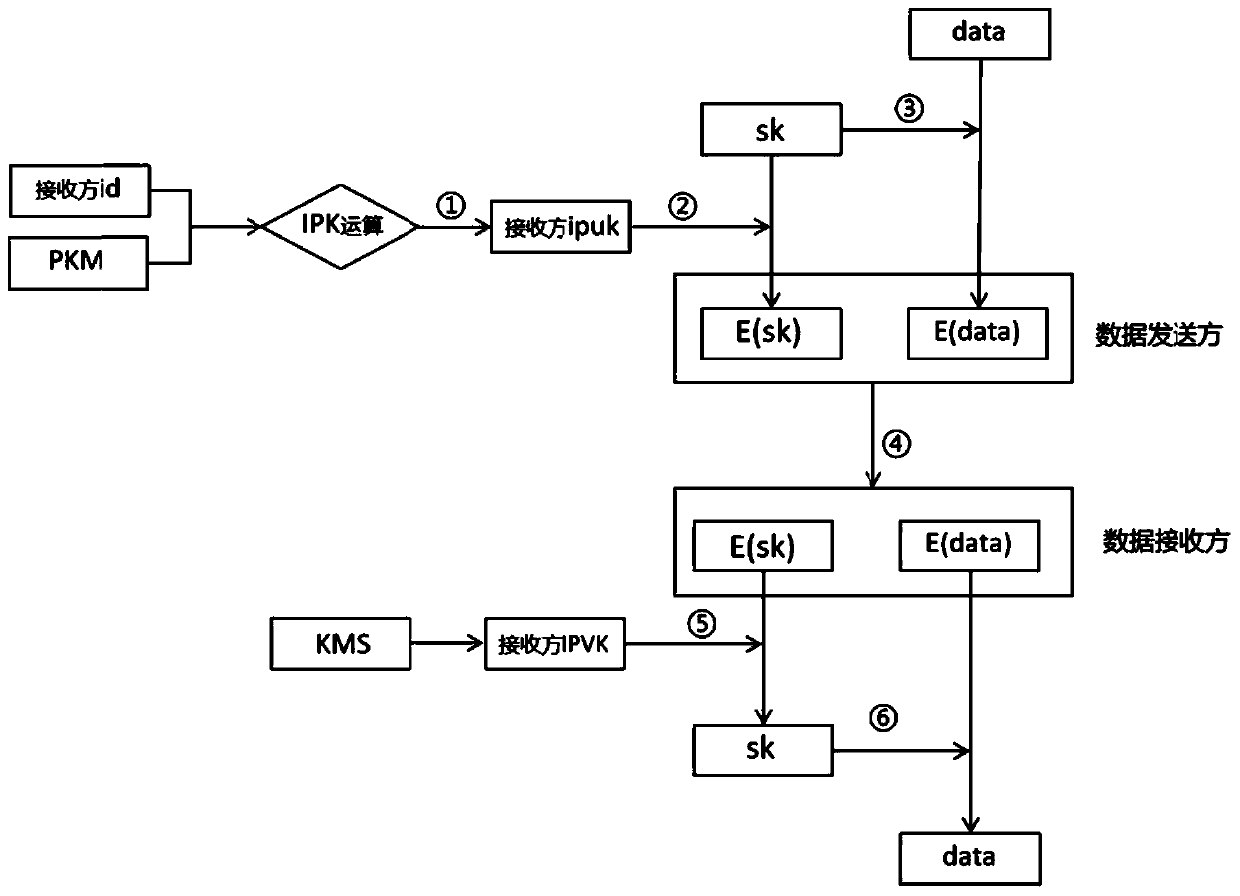
The invention discloses a data transmission encryption and decryption method and system of a transformer substation inspection robot. The method provided by the invention comprises the following steps: when an inspection robot is used as a data sender to upload data to an information management system, the uploaded data is encrypted by adopting an SM4 encryption algorithm, and encrypted transmission of a session key is realized by adopting a digital envelope technology of IPK; the information management system serves as a data receiver, receives ciphertext data C and a digital envelope beta sent by the inspection robot, calls a pre-configured private key sk to open the digital envelope beta to obtain a session key, and decrypts the ciphertext C by using the session key through an SM4 algorithm to obtain original data data. According to the invention, the public key management problem is solved through an IPK recognition public key system, and direct point-to-point data transmission encryption can be realized. According to the invention, efficient and safe inspection robot data transmission is realized.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
Hydrogen gas cylinder fixing device with protection function
InactiveCN109210371AReasonable designSimple structureVessel mounting detailsVessel geometry/arrangement/sizeBackplaneFixed frame
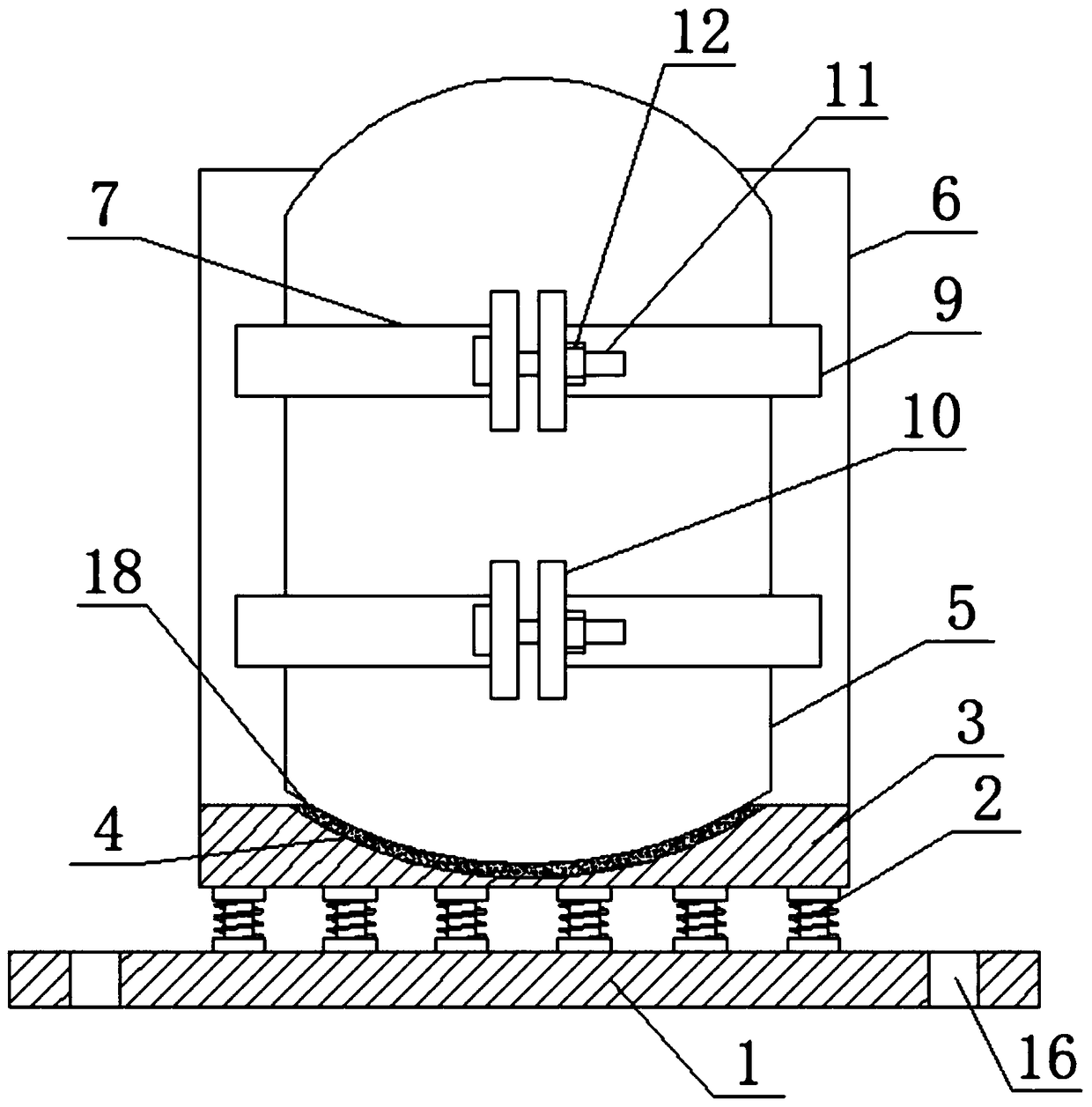
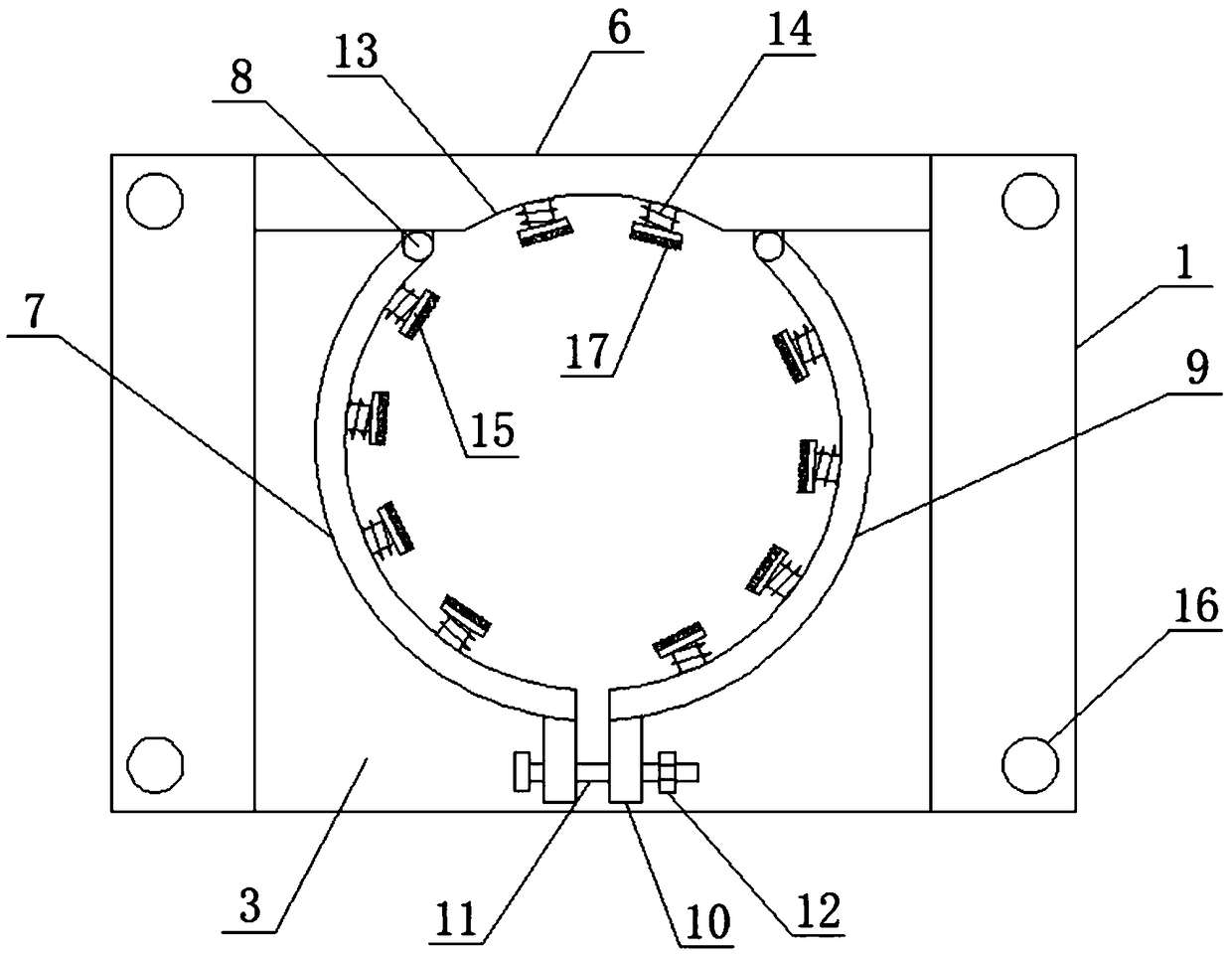
The invention discloses a hydrogen gas cylinder fixing device with a protection function. The hydrogen gas cylinder fixing device comprises a fixed base, wherein the upper end of the fixed base is fixedly connected with a first damping spring; the upper end of the first damping spring is fixedly connected with a damping base; a limiting slot is formed in the upper end of the damping base; the upper end of the damping base is fixedly connected with a back board; the right side of the front surface of the back board is hinged with a second fixed frame through a hinged part; and the side end of the first fixed frame is fixedly connected with a fixed block. The first damping spring and a second damping spring are arranged, and a hydrogen gas cylinder is placed at the upper end of a limiting slot of the damping base. When a hydrogen gas cylinder bears outside collision to bump, the first damping spring and the second damping spring can effectively release most of external force, so that hydrogen gas in a hydrogen gas cylinder is protected from leaking, and threat, on personal safety, of explosion as a result of hydrogen gas leakage is avoided. The hydrogen gas cylinder fixing device isreasonable in design, is simple in structure, and is suitable for being popularized and widely applied.
Owner:杭州蓝捷氢能科技有限公司
Illuminating lamp control method and system
ActiveCN111339831AProtect facial featuresProtection from being leakedImage analysisElectrical apparatusLight equipmentComputer graphics (images)
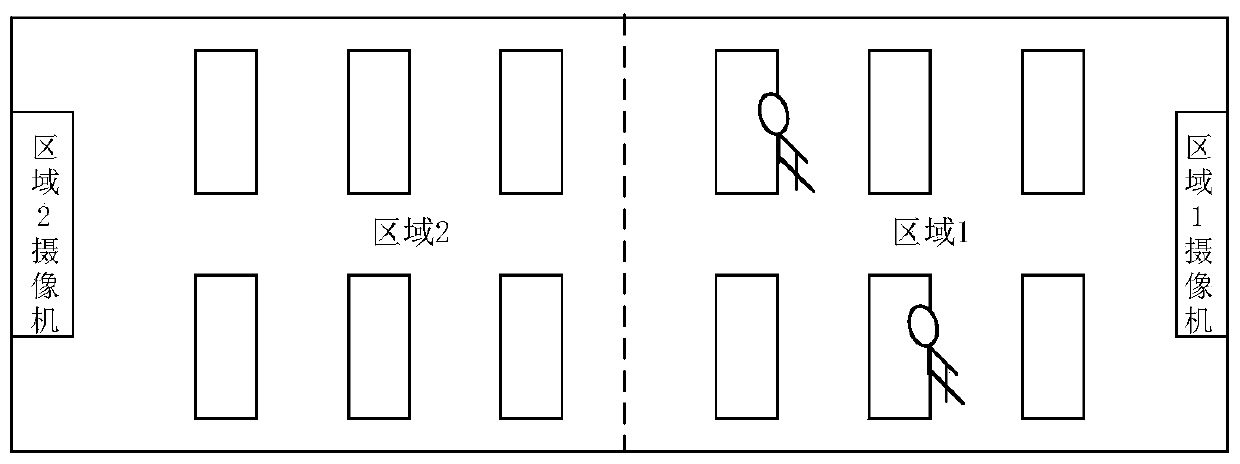
The invention discloses an illuminating lamp control method and system, and the method comprises the steps that a camera obtains a plane image of a target region, wherein the plane image comprises a plurality of target main bodies; the camera processes the plane image to obtain a first image of the target area and sends the first image to a cloud server, wherein the first image comprises contour information of a plurality of target main bodies; the cloud server segments the first image to obtain a plurality of segmented images; the cloud server respectively inputs the plurality of segmented images into an identification model so as to obtain a plurality of identification results, and each identification result in the plurality of identification results is in a manned state or an unmanned state; and the cloud server controls the illumination state of the illumination lamp in the target area according to the plurality of identification results. By implementing the embodiment of the invention, the partition control of the office area lighting equipment can be realized, the electric energy is saved, and meanwhile, the privacy information of employees is prevented from being leaked.
Owner:SHENZHEN DANALE TECH
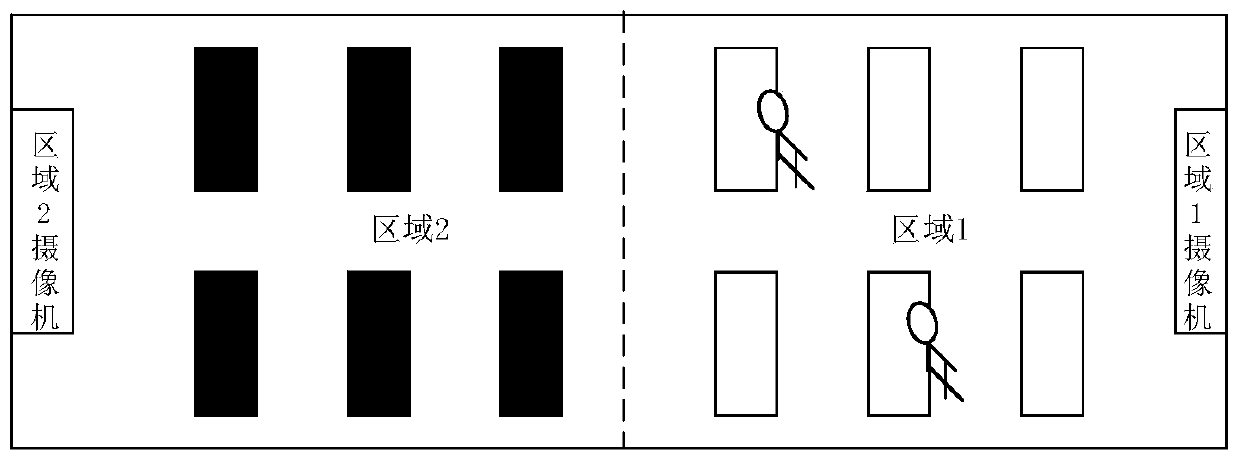
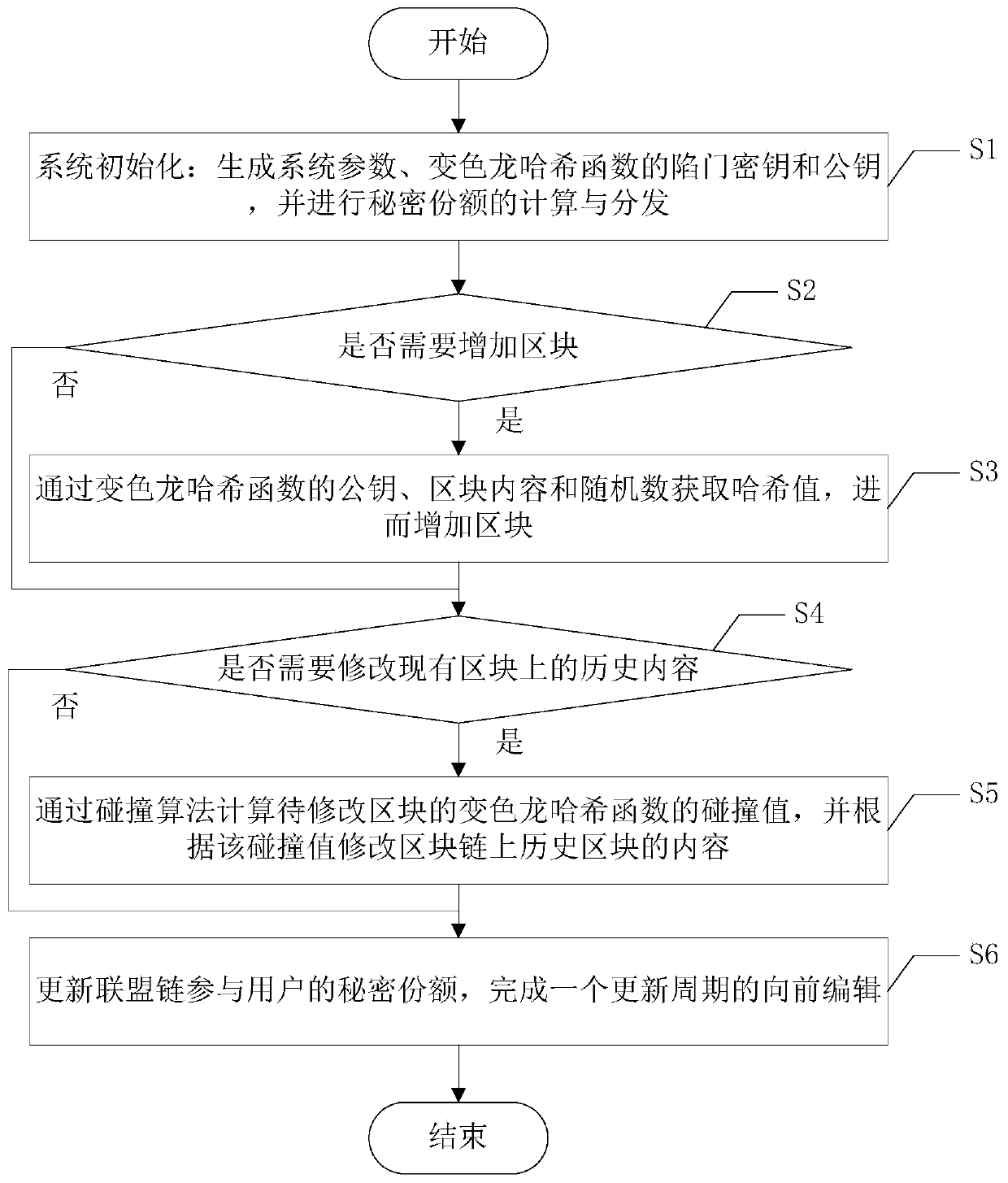
Forward security editable blockchain construction method suitable for alliance chain
ActiveCN111526009AProtection from being leakedMultiple interactionsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSecret shareBlockchain
The invention discloses a forward security editable blockchain construction method suitable for an alliance chain. The method comprises the following steps: S1, initializing a system; S2, judging whether a block needs to be added or not, if so, entering the step S3, and otherwise, entering the step S4; S3, adding blocks by acquiring hash values; S4, judging whether historical content on an existing block needs to be modified or not, if yes, entering the step S5, and otherwise, entering the step S6; S5, modifying the content of the historical block on the blockchain through the collision valueof the chameleon hash function of the to-be-modified block; S6, updating the secret share of the alliance chain participating user, and completing forward editing of one updating period. According tothe method, the trap door secret key is stored in a distributed manner by adopting a secret sharing technology, and compared with a secure multi-party computing protocol, the structure of computing collision in the method not only protects the trap door secret key and the secret share from being leaked, but also has fewer interaction times and lower computing overhead.
Owner:SOUTHWEST JIAOTONG UNIV
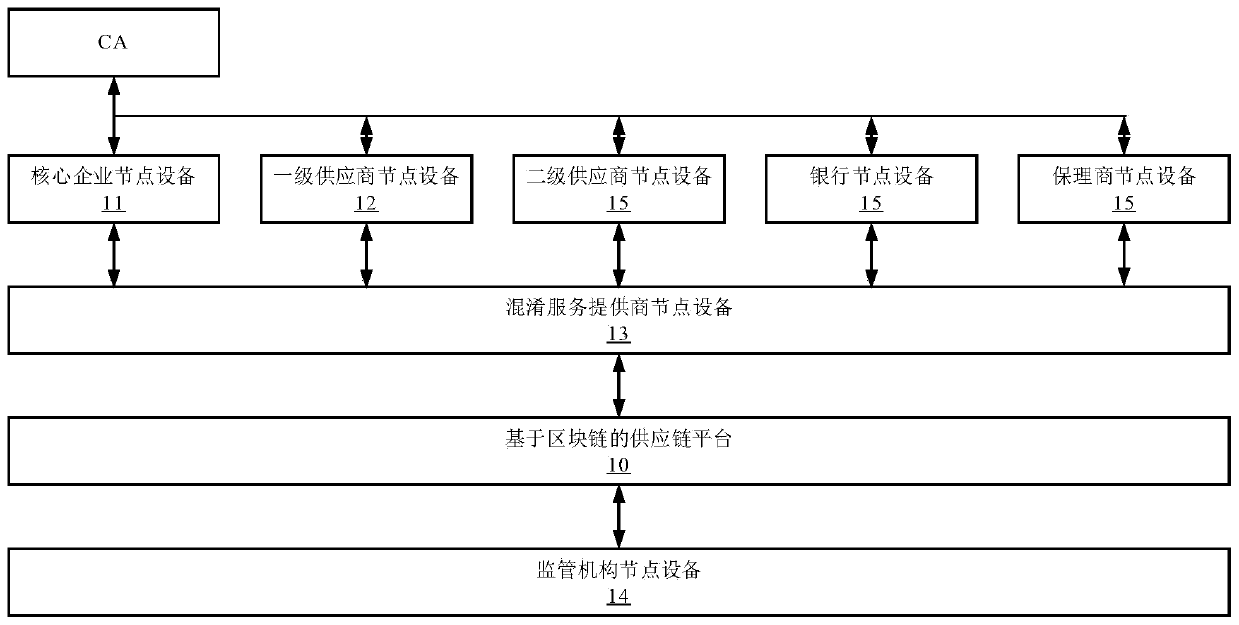
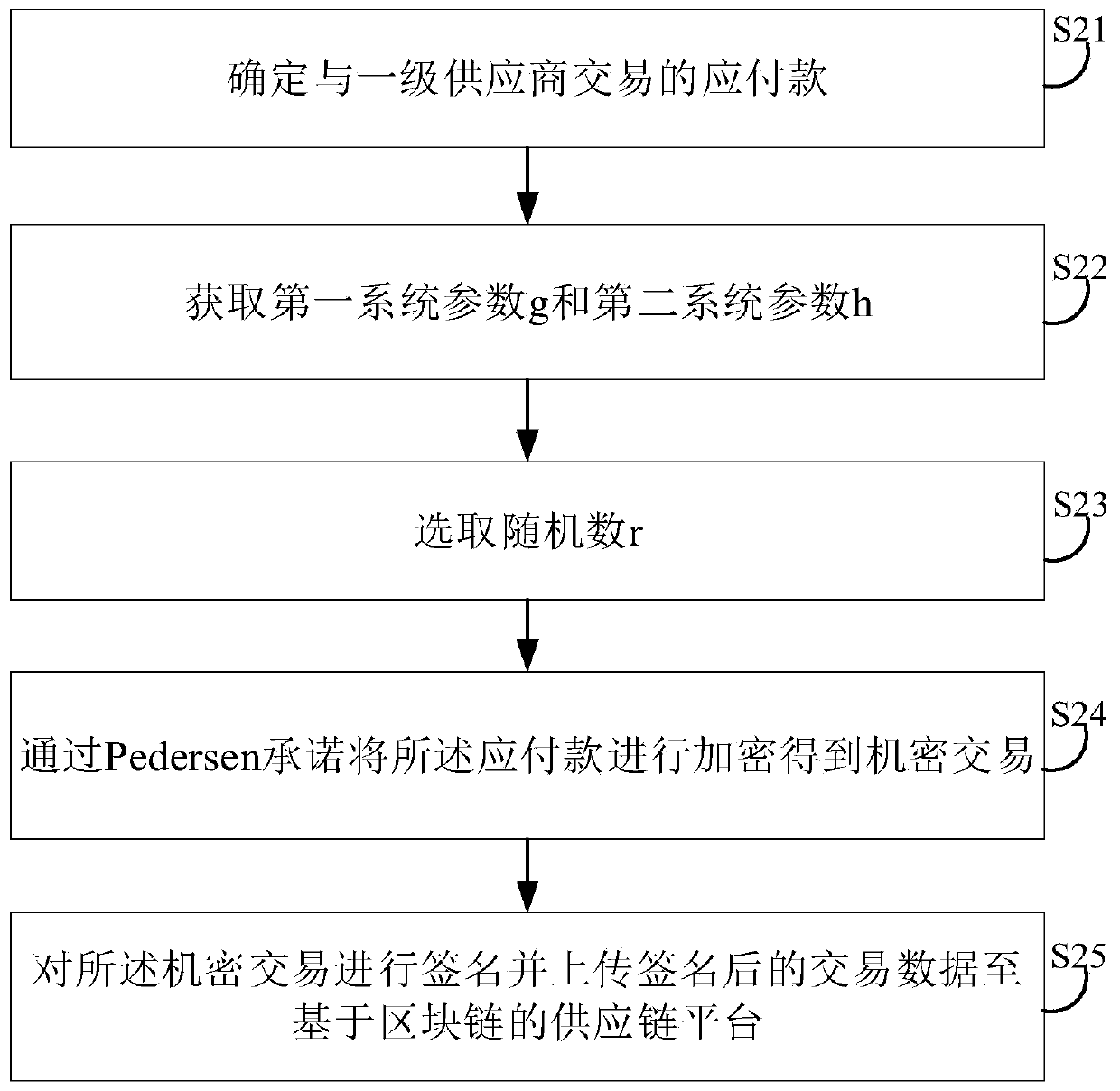
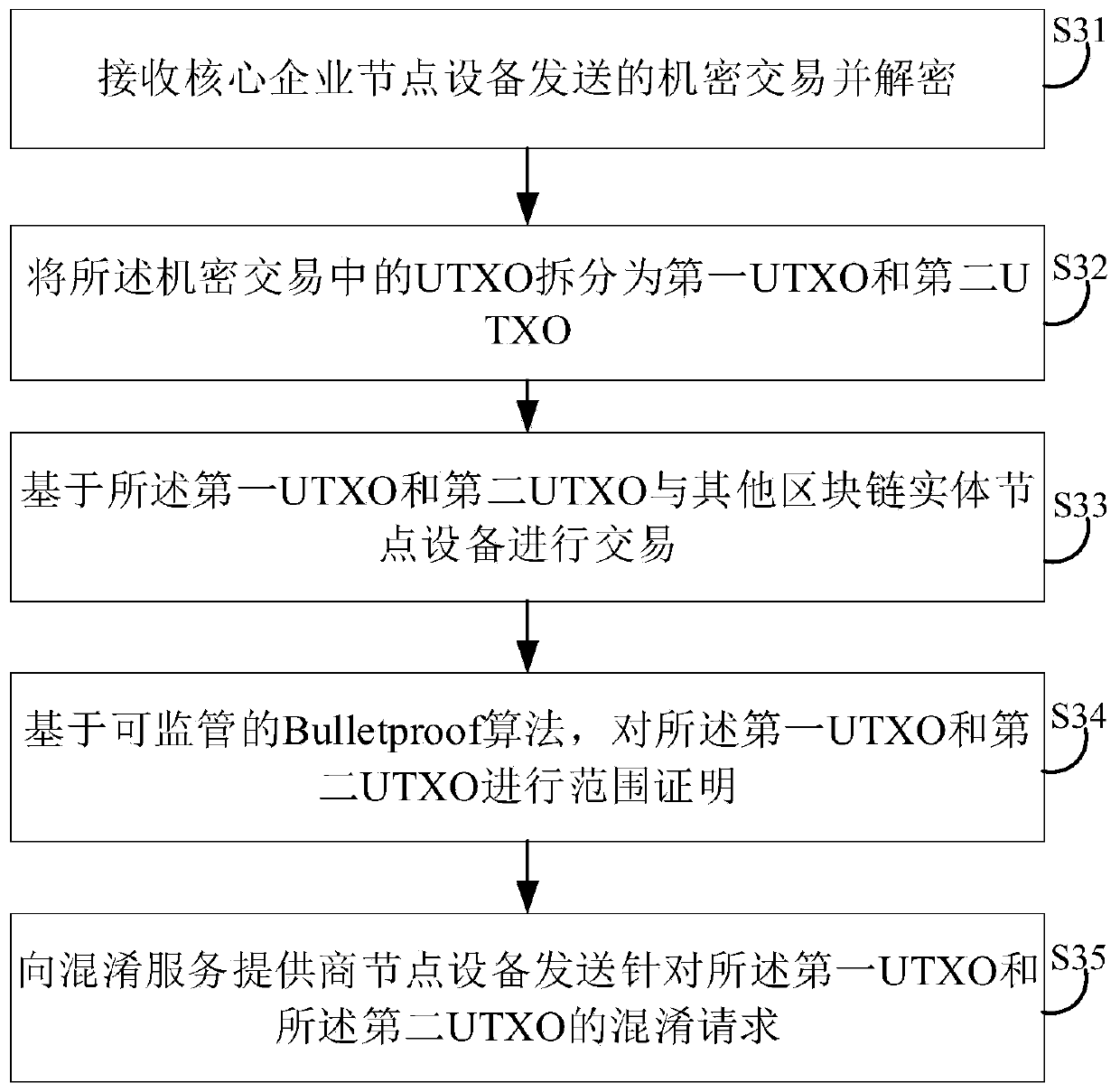
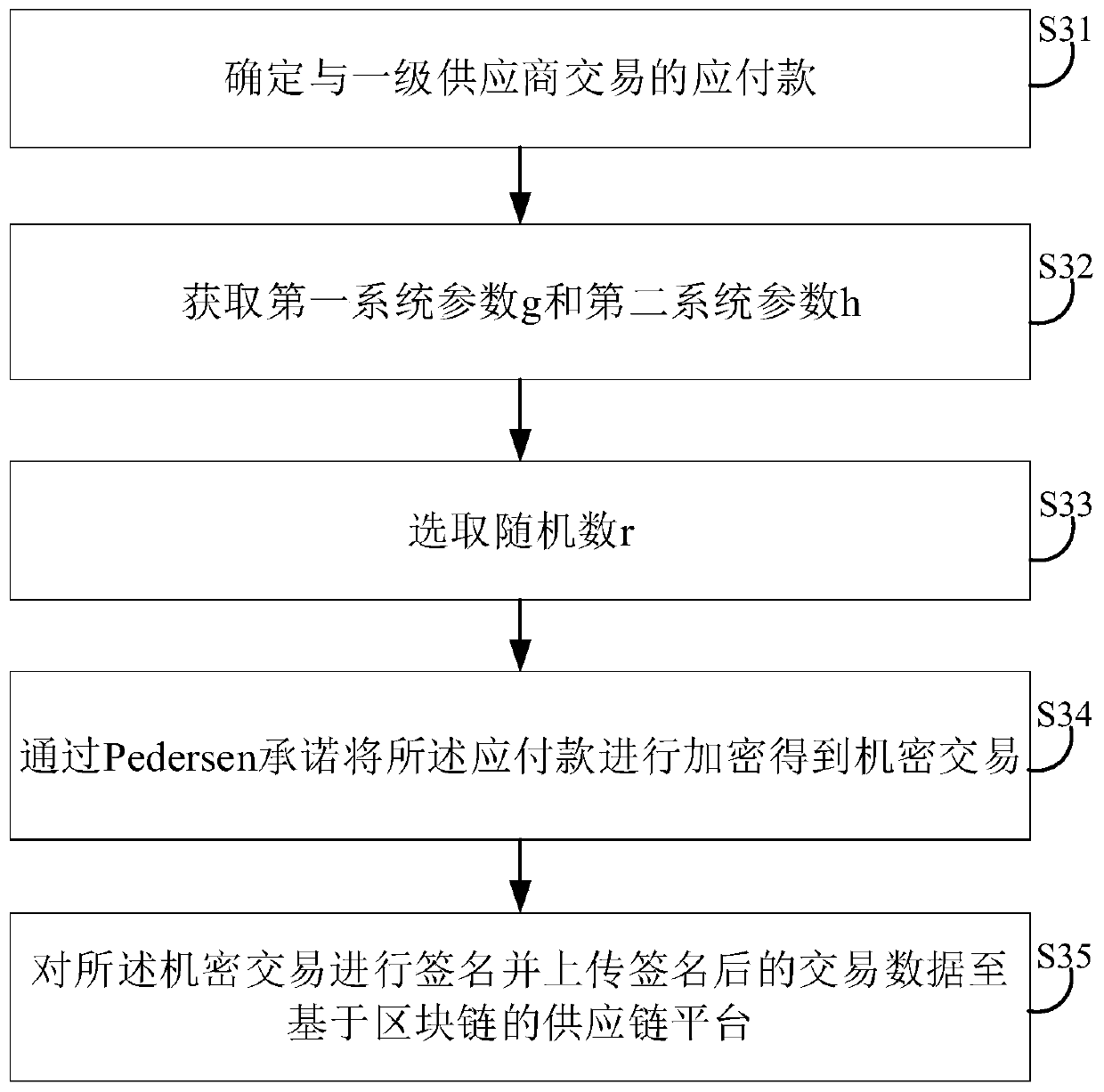
Supply chain transaction privacy protection system and method based on block chain and related equipment
PendingCN111160908AProtect entity business secretsProtection from being leakedDigital data protectionPayment protocolsComputer networkBusiness enterprise
The invention discloses a supply chain transaction privacy protection system based on a block chain, and the system comprises core enterprise node equipment which is used for encrypting payable committed by a core enterprise to a first-level supplier to obtain a confidential transaction, and uploading signed transaction data to a supply chain platform based on the block chain; first-level suppliernode equipment used for performing range certification on split transactions in confidential transactions based on a supervisible Bulletproof algorithm, and sending an obfuscation request to the obfuscation service provider node equipment; obfuscation service provider node equipment which is used for obfuscating the split transaction into other transactions equivalent to the split transaction based on a supervisible proving obfuscation algorithm; a supply chain platform based on the block chain used for storing the received transaction data; and supervision mechanism node equipment used for tracking confusion of the transaction data. The invention further provides a supply chain transaction privacy protection method based on the block chain and related equipment. According to the invention, transaction privacy can be protected from being leaked, and transaction supervision is realized at the same time.
Owner:SHENZHEN THUNDER NETWORK TECH +1
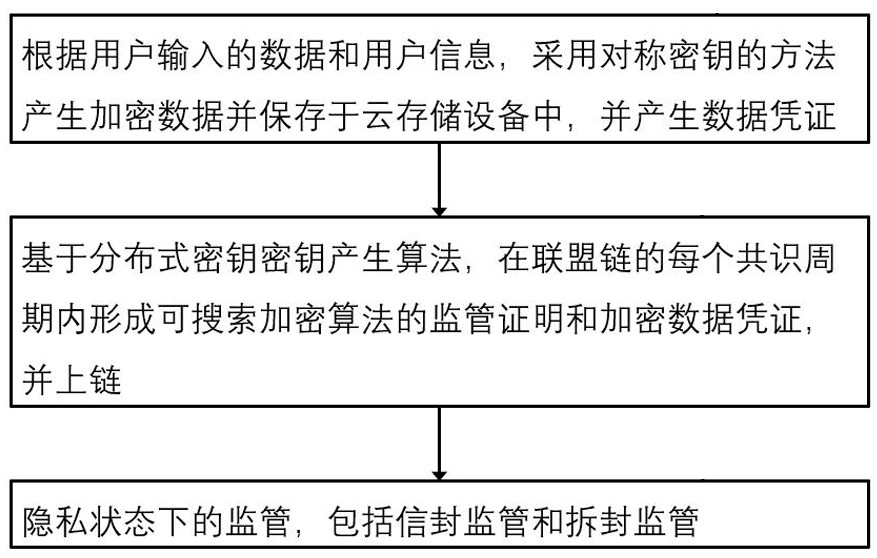
Supervisable data privacy sharing method based on end-side cloud collaboration
ActiveCN112751673AProtection from being leakedEnsure safetyKey distribution for secure communicationFinanceBlockchainCloud storage
The invention discloses a supervisible data privacy sharing method based on end-side cloud collaboration, which aims at data privacy sharing and supervision in an end-side cloud scene and comprises the steps of data cloud storage based on symmetric key encryption and generation of metadata, uplink of metadata based on a distributed key of an alliance chain and data supervision based on searchable encryption. Supervision modes include envelope supervision and unsealing supervision, and the envelope supervision confirms whether a user submits a storage voucher of metadata within a certain time or not under the condition of consensus of all nodes; if unsealing supervision is carried out, a metadata storage voucher of a user is obtained, stored data is decrypted, and a data plaintext is obtained; and the block chain system is used for storing private data of the user, protecting data privacy from being leaked, and realizing supervision under a data privacy sharing condition.
Owner:ZHEJIANG LAB
Individuation difference privacy recommendation method based on local clustering
ActiveCN108256000AProtection from being leakedHigh precisionCharacter and pattern recognitionSpecial data processing applicationsPersonalizationData set
The invention relates to an individuation difference privacy recommendation method based on local clustering. The method comprises the steps that for the situation that the privacy requirements of different users for different goods are different, firstly, a user file data set is sampled, then a noise-containing KNN of a target user is selected by using the sampled data set, goods are clustered based on the local similarity, user data is modified by using a clustered result, and finally a recommendation result is calculated by using the modified user data. The individuation difference privacyrecommendation method has high availability, and the privacy requirement of any user can be precisely met.
Owner:WUHAN UNIV
User anti-harassment system and method based on intelligent network
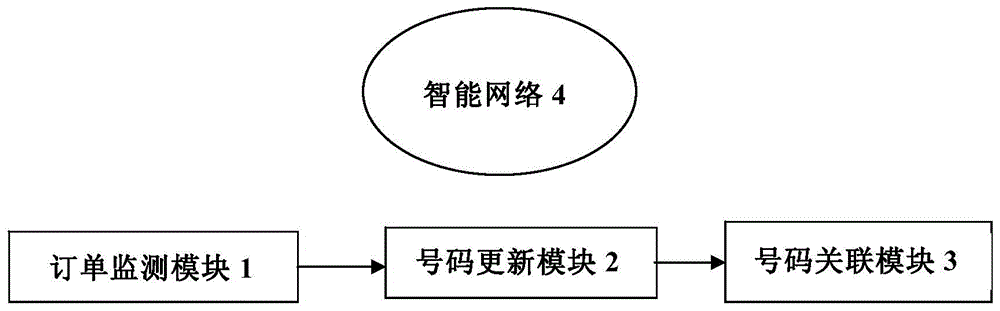
ActiveCN105763753AAvoid adverse effectsReduce adverse effectsSpecial service for subscribersCommmunication supplementary servicesData miningSmart network
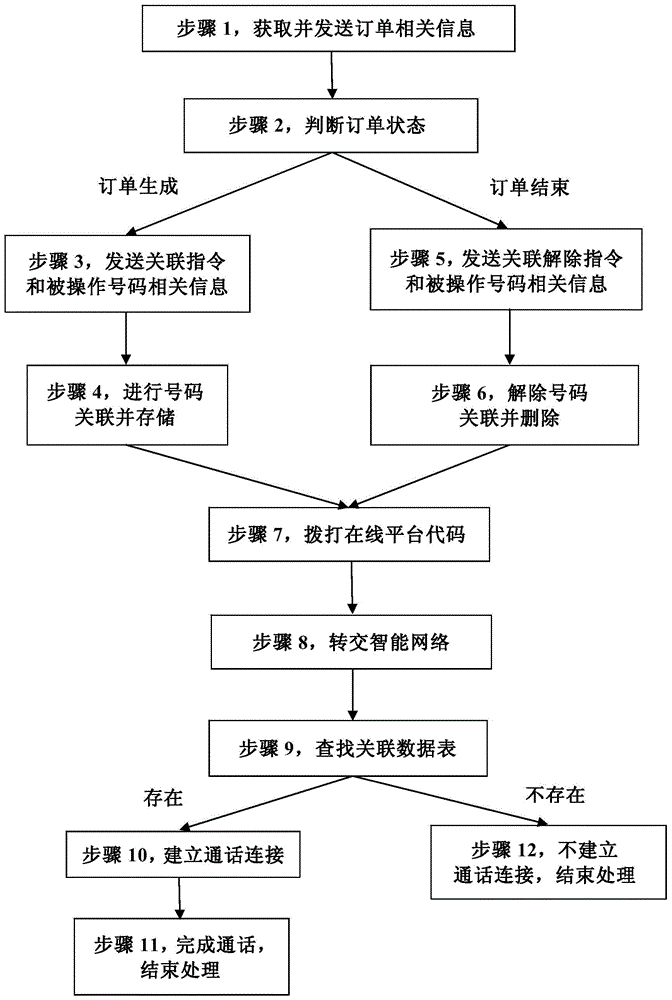
The present invention discloses a user anti-harassment system and method based on an intelligent network. The system comprises an order monitoring module, a number update module and a number association module. The order monitoring module is configured to obtain order relevant information and send the order relevant information to the number update module. The number update module is configured to determine the order state, send number relevant instructions or relevant releasing instruction to the number association module and send the relevant information of numbers to be operated to the number association module. The number association module is configured to associate with both-side contact numbers of the order and store the contact numbers in a number associated data table, or is configured to release the association of the both-side contact numbers of the order and delete the numbers from the number associated data table. A calling party calls online platform codes and delivers the online platform codes to an intelligent network for processing. The intelligent network is configured to search a number associated data table corresponding to the online platform codes in the number association module, and build or does not build a calling connection according to whether there is a calling number in the number associated data table or not.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Method and apparatus for securely transmitting data through Bluetooth technology
ActiveCN103906048AProtection from being leakedNear-field transmissionSecurity arrangementTerminal equipmentPersonal computer
The invention discloses a method and apparatus for securely transmitting data through a Bluetooth technology. The method comprises the following steps: a registration step, i.e., a predetermined terminal device receiving and storing device information and a secret key which are sent by a detection device; and a transmission step, i.e., utilizing the device information and the secret key, through identity verification or after encryption of detection data, the detection device transmitting the data to the terminal device. According to the method and apparatus provided by the embodiments of the invention, the detection device employs an open mode, and under the condition that personnel information is effectively protected from being leaked, through multiple means such as multiple intelligent mobile phones, personal computers, special-purpose wireless receiving gateways and the like, the data can be transmitted to a cloud end database or one or more mobile terminals.
Owner:GUANGDONG TRANSTEK MEDICAL ELECTRONICS CO LTD
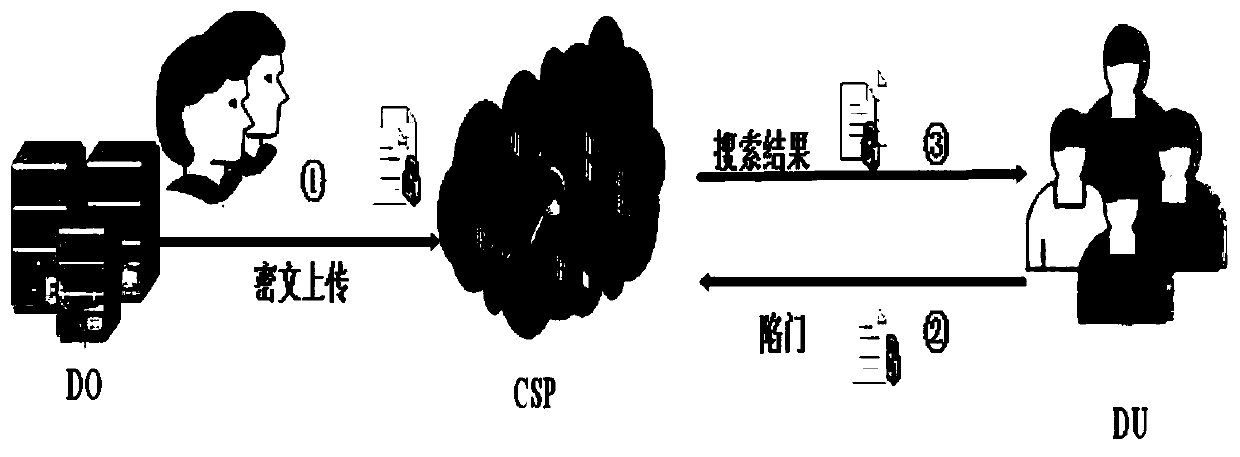
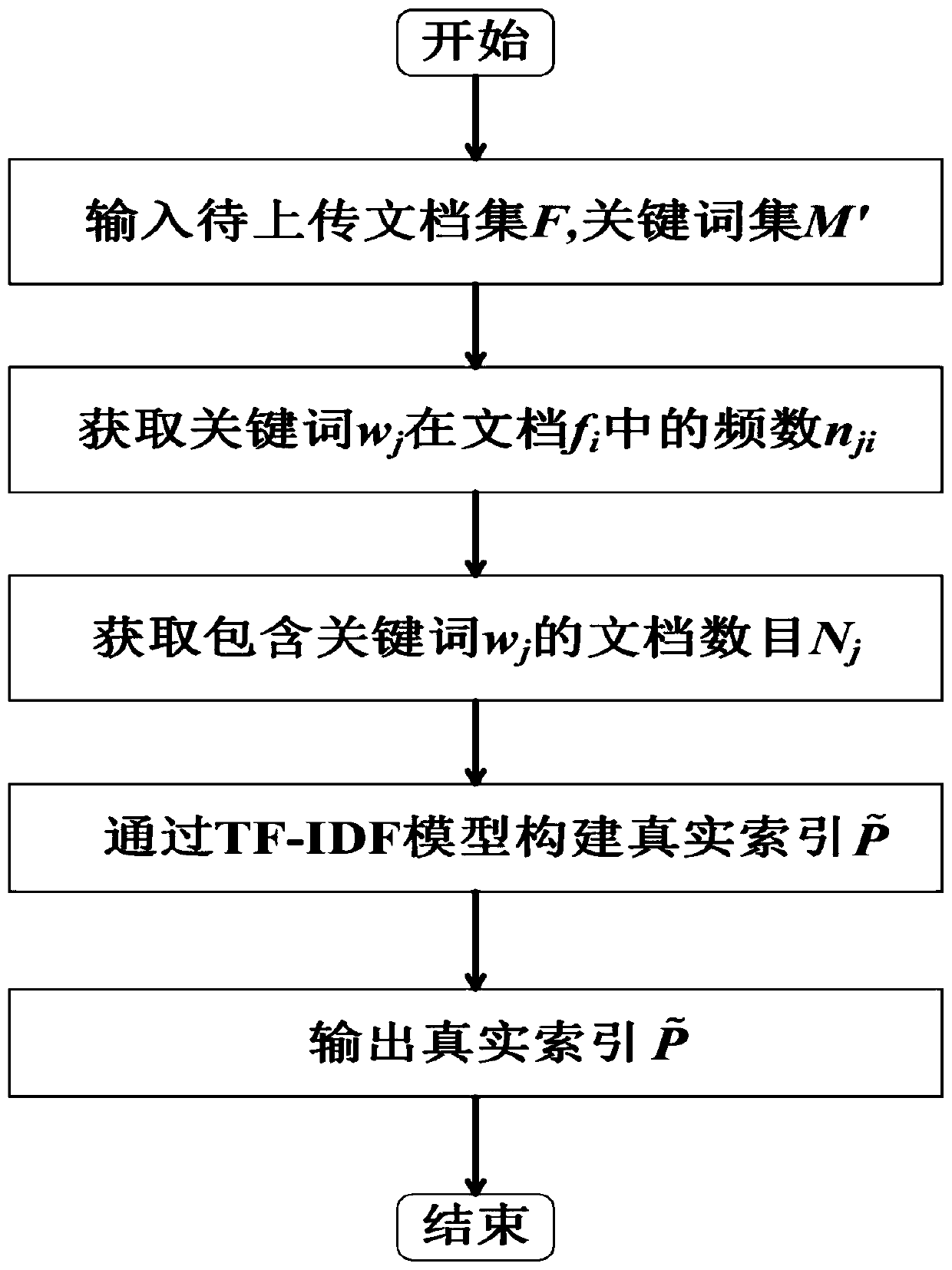
A safe pair index construction and retrieval method capable of resisting keyword privacy disclosure
ActiveCN109740378AEliminate differencesPrevent access toDigital data protectionCiphertextDocumentation
The invention relates to a security pair index construction and retrieval method capable of resisting keyword privacy disclosure. The method comprises the following steps: constructing a security pairindex and retrieving the security pair index, and the security pair index construction comprises the following steps: S1, a data owner calculates a related score corresponding to each keyword according to a to-be-uploaded data document, calculates a real index and encrypts and accesses a keyword pair set; S2, the data owner calculates a false index and a mixed index through a real index, encryptsthe false index and the mixed index by using an authorization secret key, and obtains a safe pair index by combining an access keyword pair set; S3, the data owner encrypts the to-be-uploaded data document to obtain a ciphertext document set; S4, the data owner uploads the security pair index and the ciphertext set to the cloud server. According to the method and the device, keyword privacy leakage caused by an access mode and a search mode based on keywords can be resisted.
Owner:福建国科信息科技有限公司
Convenient-to-use lubricating grease capsule
InactiveCN108045703AEasy to carryEasy extrusionContainer/bottle contructionRigid containersBiomedical engineeringNozzle
The invention discloses a convenient-to-use lubricating grease capsule. The convenient-to-use lubricating grease capsule comprises a shell, wherein the shell is of a cylindrical structure; the inner part of the shell is of a cavity structure; a capsule body is placed in the shell; the capsule body is cylindrical; an extending pipe is arranged at the upper part of the capsule body; the extending pipe is connected with a filling nozzle; the filling nozzle is of a tapered structure; the filling nozzle is made of an iron material. The convenient-to-use lubricating grease capsule disclosed by the invention is simple in structure and reliable to pack; the problems in the prior art that lubricating grease filling equipment is large and a lubricating grease packing barrel is too great and is not easy to carry are solved; the convenient-to-use lubricating grease capsule disclosed by the invention is very convenient to carry and is suitable for conditions of emergently filling the equipment withlubricating grease in travel or wild environments; the convenient-to-use lubricating grease capsule has extremely great market generalization and applicability and is suitable for being placed or carried as stand-by equipment.
Owner:JIANGSU SHORTCUT DISABILITIES LUBRICANT
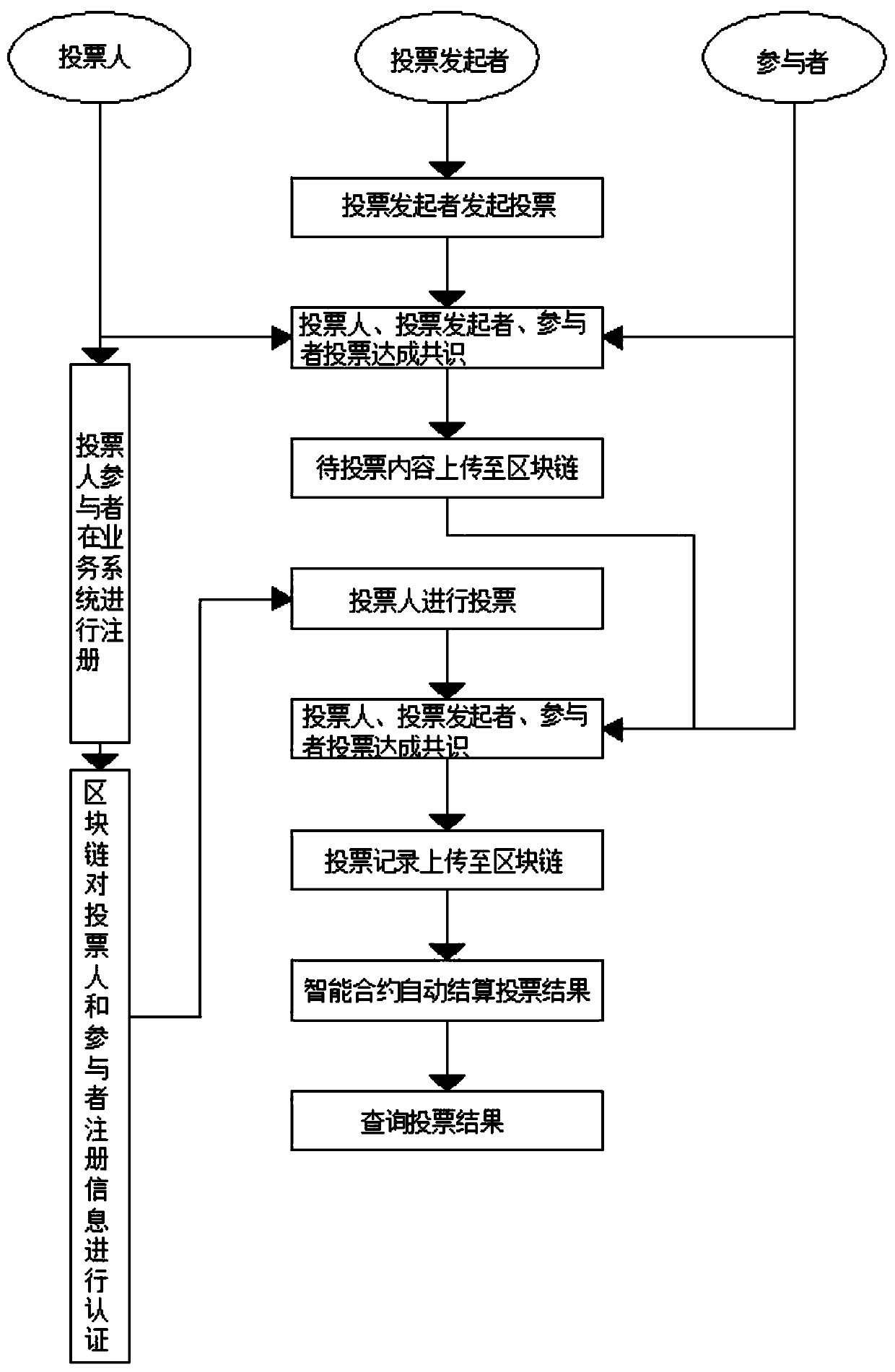
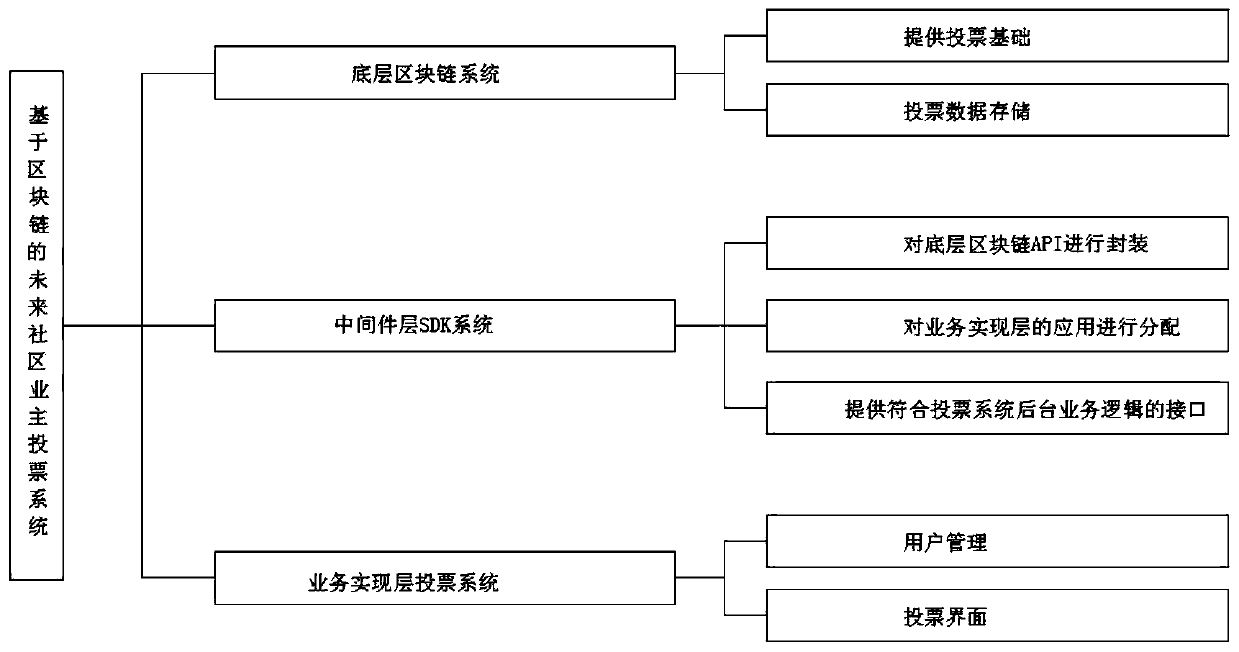
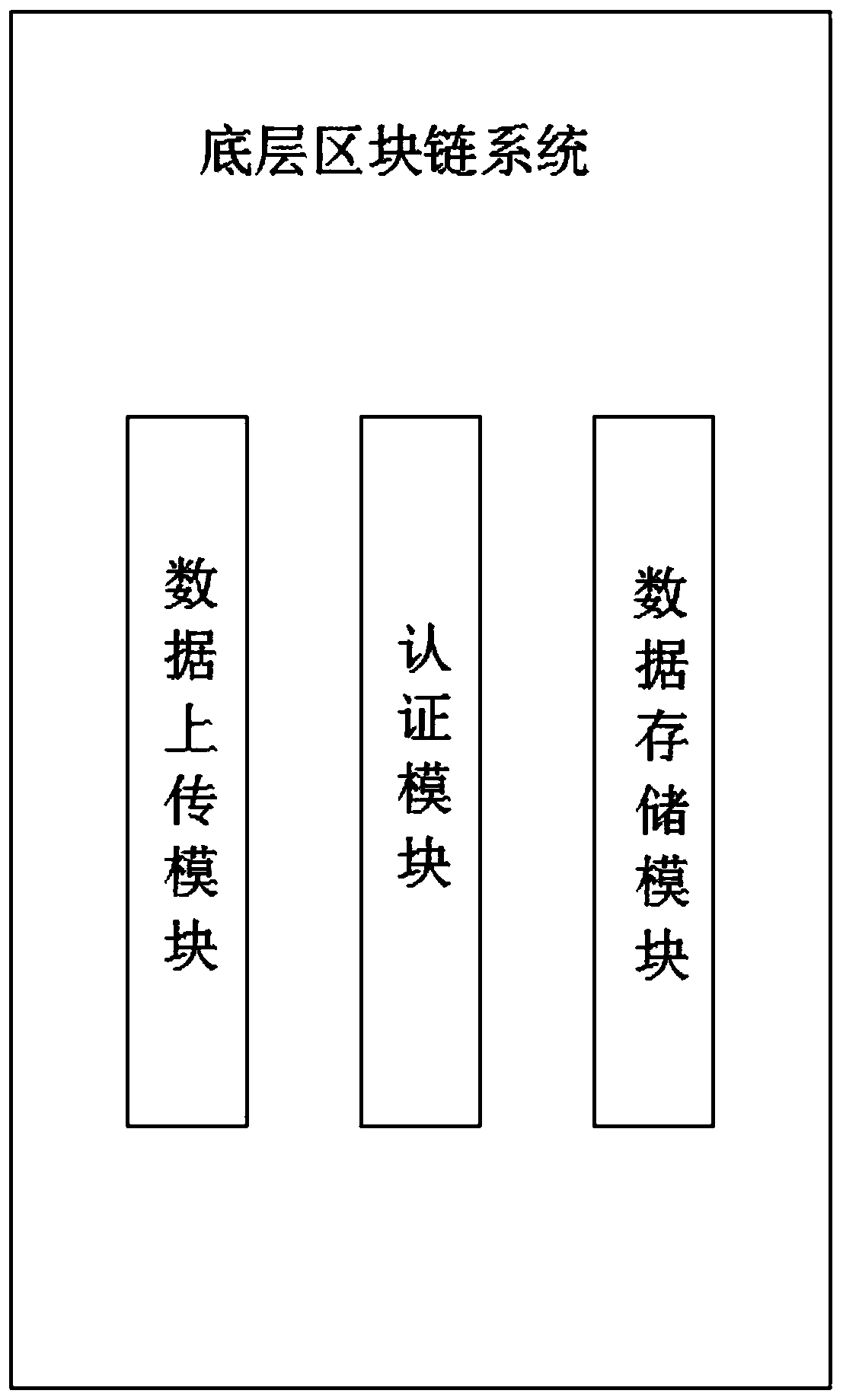
Blockchain-based future community owner voting system
InactiveCN110197547AHard to tamper withPrevent tamperingVoting apparatusPayment protocolsService implementationSmart contract
The invention discloses a blockchain-based future community owner voting system, which comprises a bottom blockchain system, a middleware layer SDK system and a service implementation layer voting system. A voter and a participant register in the service implementation layer voting system, and the registered information is uploaded to the bottom blockchain module for authentication by a data uploading module; a voting sponsor further initiates a vote, writing to a blockchain after consensus authentication by the voter, the sponsor and the participant, the voter submits a voting option throughthe service implementation layer voting system, and the option of the voter is further recorded on the blockchain through identity authentication and voting qualification; after the voting time is over, the voting result is automatically calculated and written to the blockchain by a smart contract based on a predetermined rule; and finally, the voter and the participant query the voting result ofthe blockchain through the service implementation layer voting system.
Owner:浙江申跃信息科技有限公司
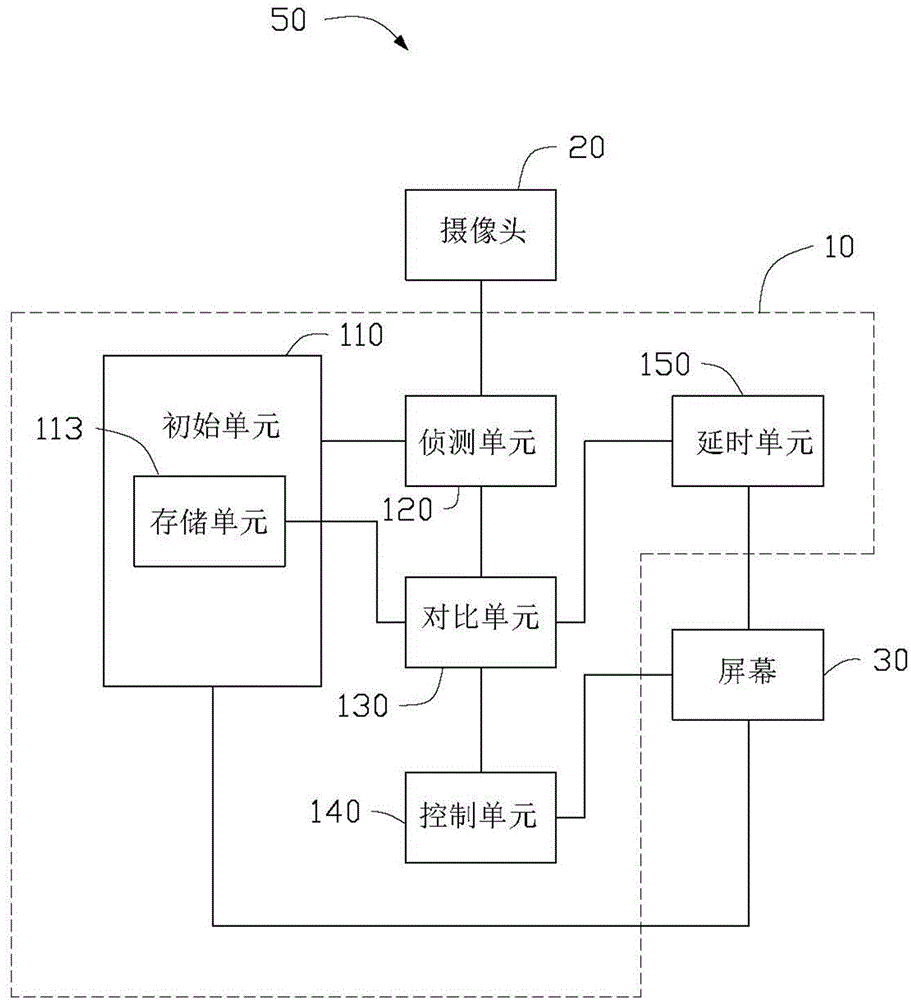
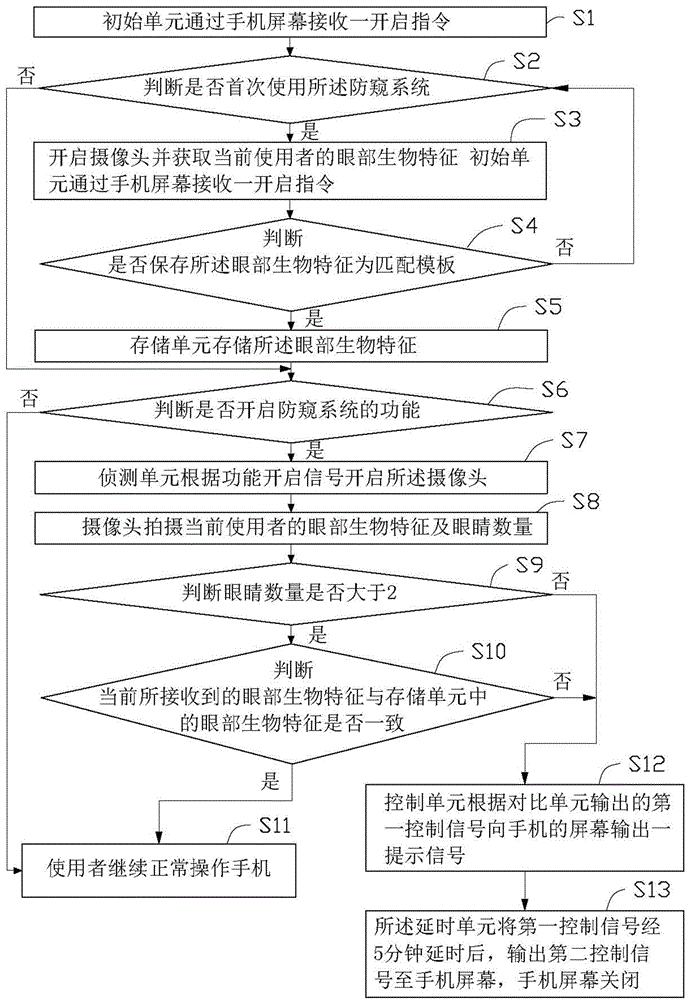
Peeping-proof system and method based on eyeball recognition
The invention relates to a peeping-proof system and method based on eyeball recognition. The peeping-proof system based on the eyeball recognition comprises an initial unit, a detection unit, a comparison unit and a control unit, wherein the initial unit outputs a function starting signal when the initial unit receives a function starting instruction; the detection unit starts a camera of a mobile terminal according to the function starting signal, and obtains the eye biological characteristics which are shot by the camera, of a current user; the comparison unit compares the eye biological characteristics of the current user with the eye biological characteristics in a storage unit, and a first control signal is output when a comparison result shows that the eye biological characteristics of the current user and the eye biological characteristics in the storage unit are inconsistent; and the control unit outputs prompt information to a screen of the mobile terminal according to the first control signal to prompt information leakage for the user. The peeping-proof system and the method can help the user to prevent personal information from being leaked when the mobile terminal is used.
Owner:HONG FU JIN PRECISION IND WUHAN CO LTD +1
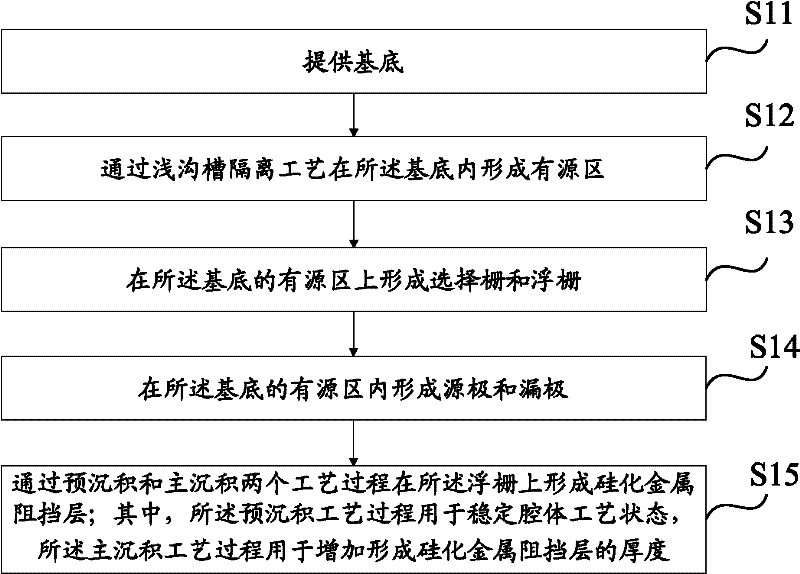
Method for manufacturing one time programmable (OTP) device
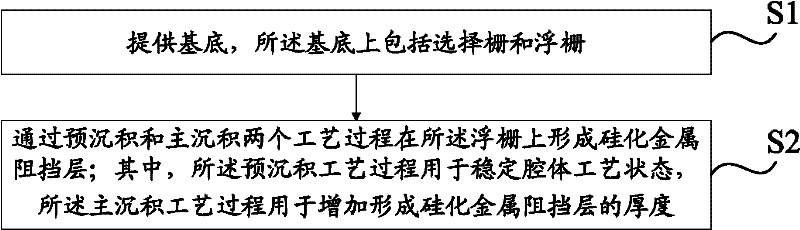
ActiveCN102543884AImprove data storage characteristicsIncreasing the thicknessSemiconductor/solid-state device manufacturingChemical vapor deposition coatingSalicideEngineering
The embodiment of the invention discloses a method for manufacturing a one time programmable (OTP) device. The method comprises the following steps of: providing a substrate, wherein the substrate comprises a selection gate and a floating gate (FG); and forming a salicide block (SAB) on the FG by pre-deposition and main deposition processes, wherein the pre-deposition process is used for stabilizing the process state of a cavity, and the main deposition process is used for increasing the thickness of the formed SAB. By the method for manufacturing the OTP device, a thick SAB can be formed on the FG, so that damage and defects caused by the subsequent plasma bombardment can be avoided, charges in the FG can be prevented from being leaked after the OTP device is programmed, leakage current is prevented from being increased, and the service life of the OTP device is prolonged.
Owner:CSMC TECH FAB2 CO LTD
Supply chain transaction privacy protection system and method based on block chain and related equipment
PendingCN111105235AProtect entity business secretsProtection from being leakedFinanceAnonymous user systemsComputer networkBusiness enterprise
The invention discloses a supply chain transaction privacy protection system based on a block chain, and the system comprises: core enterprise node equipment which is used for encrypting payable committed by a core enterprise to a first-level supplier to obtain a confidential transaction, carrying out the signature of the confidential transaction, and uploading the signed transaction data to a supply chain platform based on the block chain; a first-level supplier node equipment which is used for receiving the confidential transaction, decrypting the confidential transaction, outputting the decrypted confidential transaction to a first-level supplier, and sending an obfuscation request for a split transaction in the confidential transaction to the obfuscation service provider node equipment; an obfuscation service provider node device which is used for obfuscating the split transaction into other transactions equivalent to the split transaction; and a supply chain platform based on theblock chain which is used for storing the received transaction data. The invention further provides a supply chain transaction privacy protection method based on the block chain and related equipment.According to the invention, transaction privacy can be protected from being leaked, and anonymity of the transaction is realized, so that anyone cannot track a receiver of the transaction.
Owner:SHENZHEN THUNDER NETWORK TECH +1
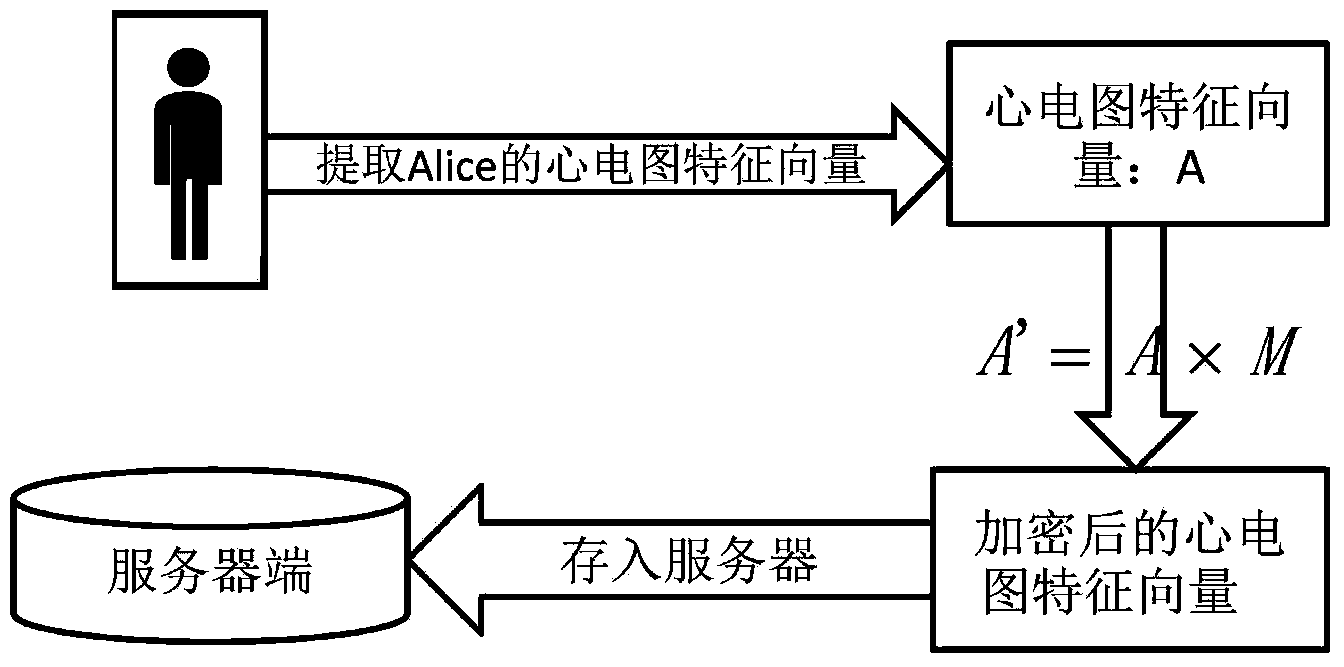
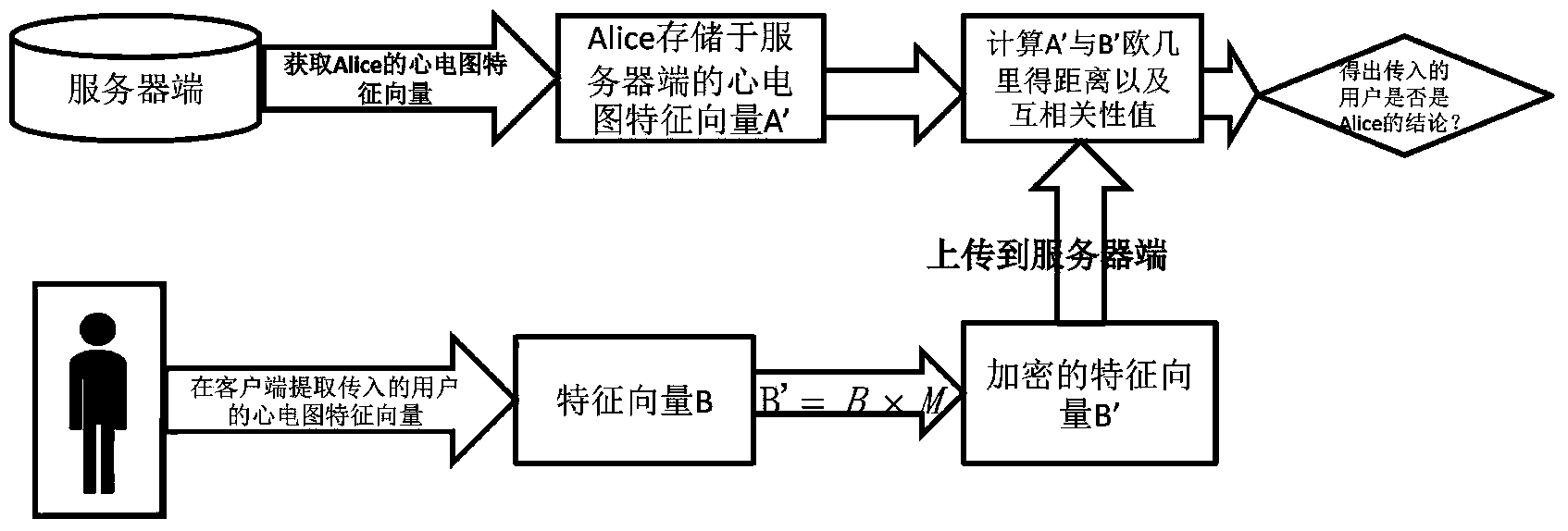
Electrocardiogram recognizing method based on privacy protection
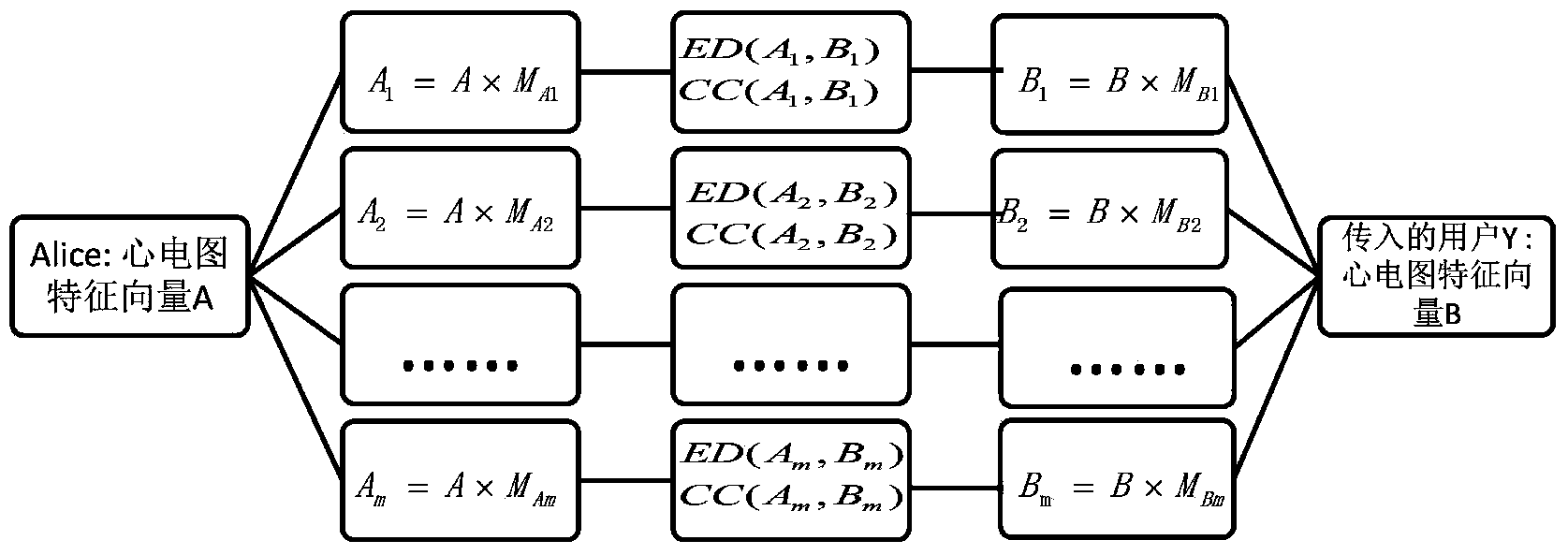
ActiveCN103955677AProtection from being leakedAddress privacy breachesCharacter and pattern recognitionDiagnostic recording/measuringFeature vectorPrivacy protection
The invention discloses an electrocardiogram recognizing method based on privacy protection. Firstly, ECG data are disorganized in a client, and then a vector B achieved from conversion instead of an initial vector A is utilized as a characteristic vector of a user to be uploaded to a server database to be used for recognizing the user in an identity recognizing stage. A disorganizing method is that a characteristic vector A which is extracted from the electrocardiogram signals obtained from measurement of the user and contains n elements multiplies a n*n random matrix. The electrocardiogram recognizing method can well protect electrocardiogram privacy of users in a training stage and an identity recognizing process.
Owner:NANJING UNIV
Micro-nursing doctor case management system
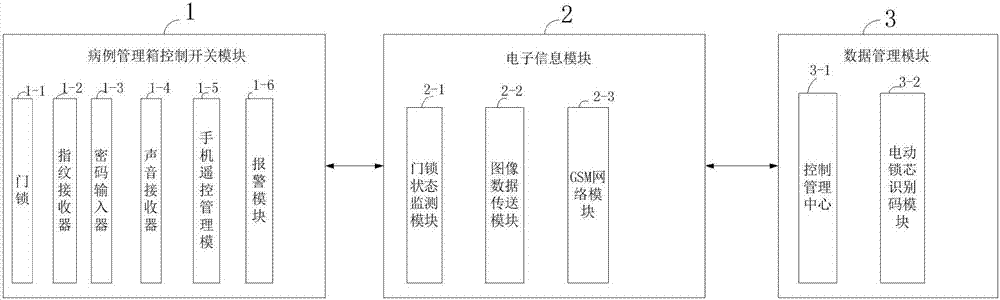
InactiveCN107292104AImprove service functionsImprove accuracyKey distribution for secure communicationPublic key for secure communicationElectronic informationNetwork service
The invention relates to the electric field, in particular to a micro-nursing doctor case management system. The micro-nursing doctor case management system comprises a case management box control switch module, an electronic information module and a data management module, wherein data transmission between the case management box control switch module and the data management module is completed through the electronic information module and a mobile phone; the case management box control switch module comprises a door lock, a fingerprint receiver, a password input device, a sound receiver, a mobile phone remote control management module and an alarm module; the door lock comprises an electric control lock cylinder, a shell, a camera and the like, the electric control lock cylinder is arranged in a door panel and connected with the electronic information module, and the shell, the camera and the like are arranged on the outer surface of the door panel. The system has the advantages that safety and locking state monitoring accuracy is increased by the camera, data transmission is achieved through a sensor, and a network service function and the like are enhanced by a network server.
Owner:微护(武汉)健康服务有限公司
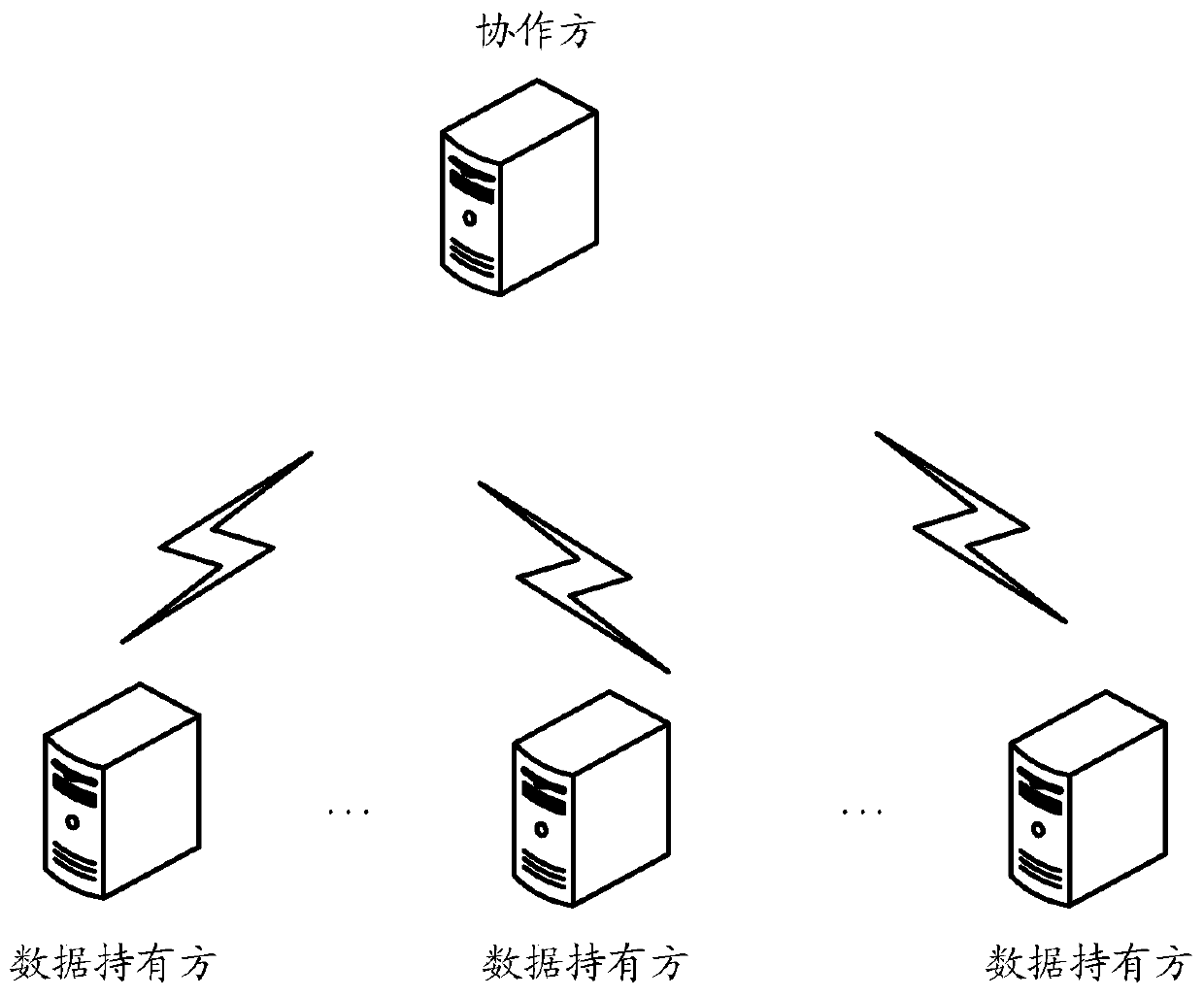
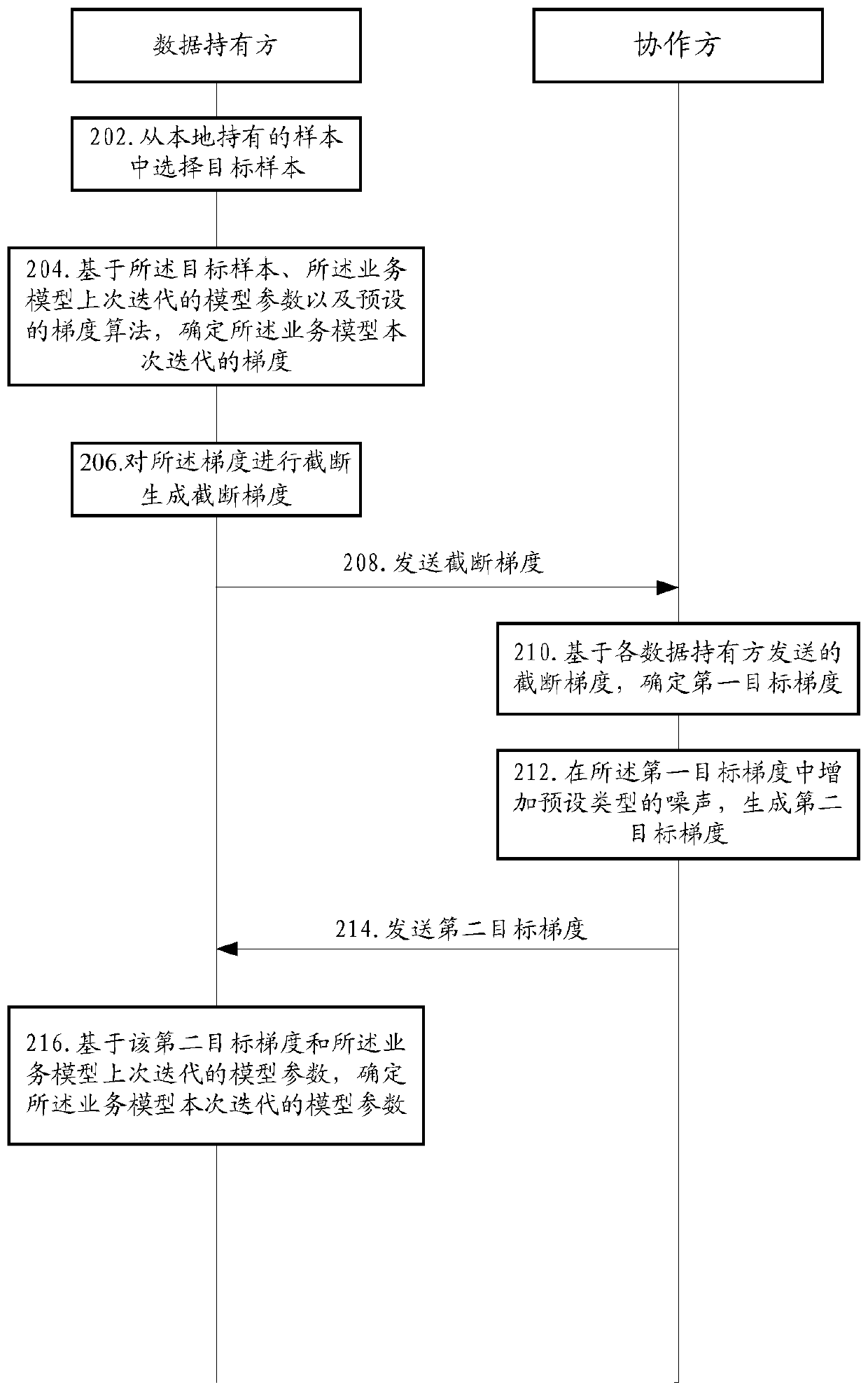
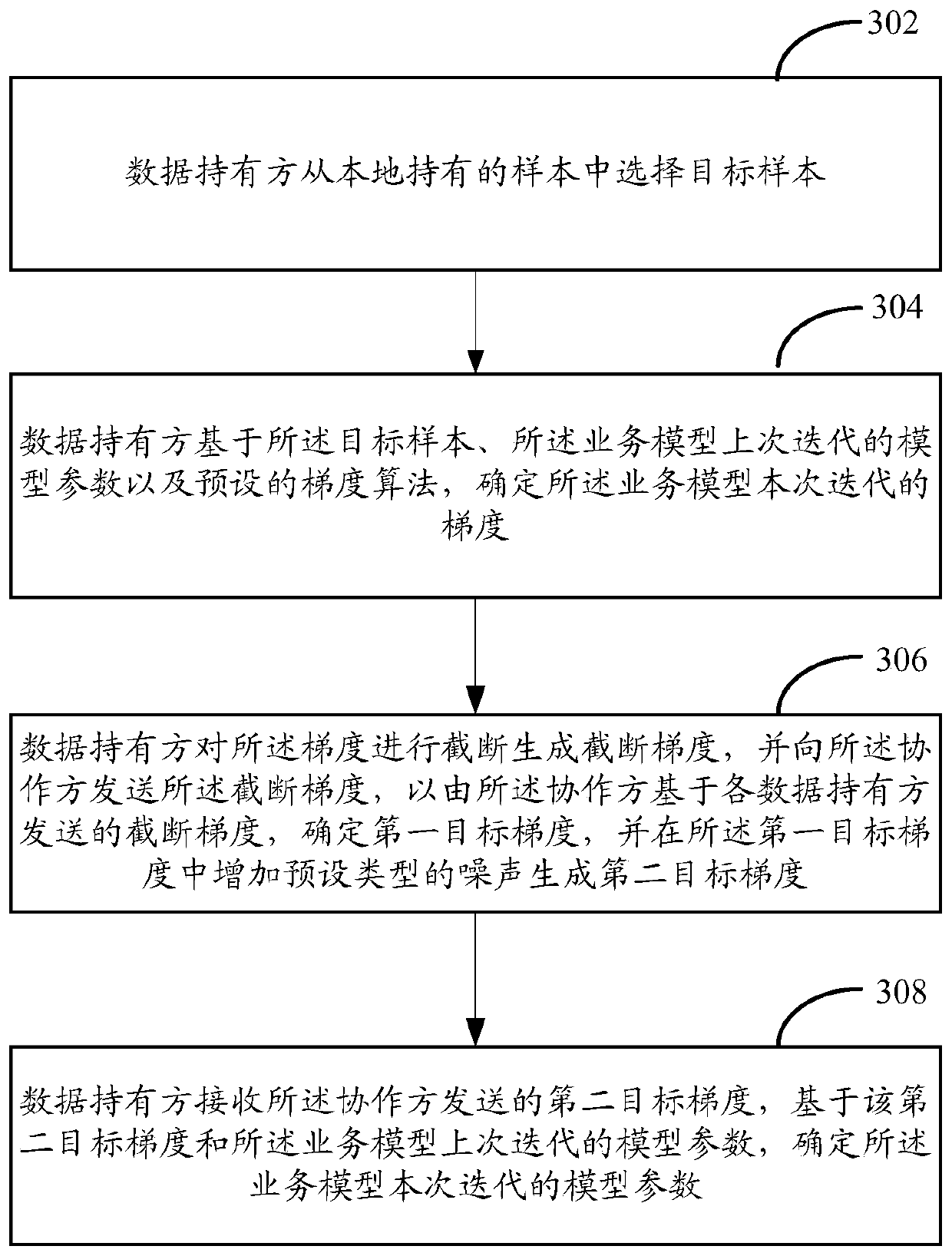
Multi-party joint training method, device, system and equipment for business model
ActiveCN111461215AProtection from being leakedNot to be leakedCharacter and pattern recognitionDigital data protectionIndividual dataModel parameter
The invention provides a multi-party joint training method, device, system and equipment for a business model. The method comprises the following steps: in a multi-party joint training service model process, data holders cut off the gradient of the iteration and then send the cut-off gradient to the collaboration party; and the collaboration party calculates a first target gradient based on the truncation gradient sent by each data holder, and adds noise in the first target gradient to obtain a second target gradient, so that each data holder determines a model parameter of the current iteration based on the second target gradient and the model parameter of the last iteration. According to the method, the calculated gradient is cut off through the data holder, and noise is added to the first target gradient summarized by the collaboration party, so that personal data leakage is prevented in a differential privacy mode in the model training process.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
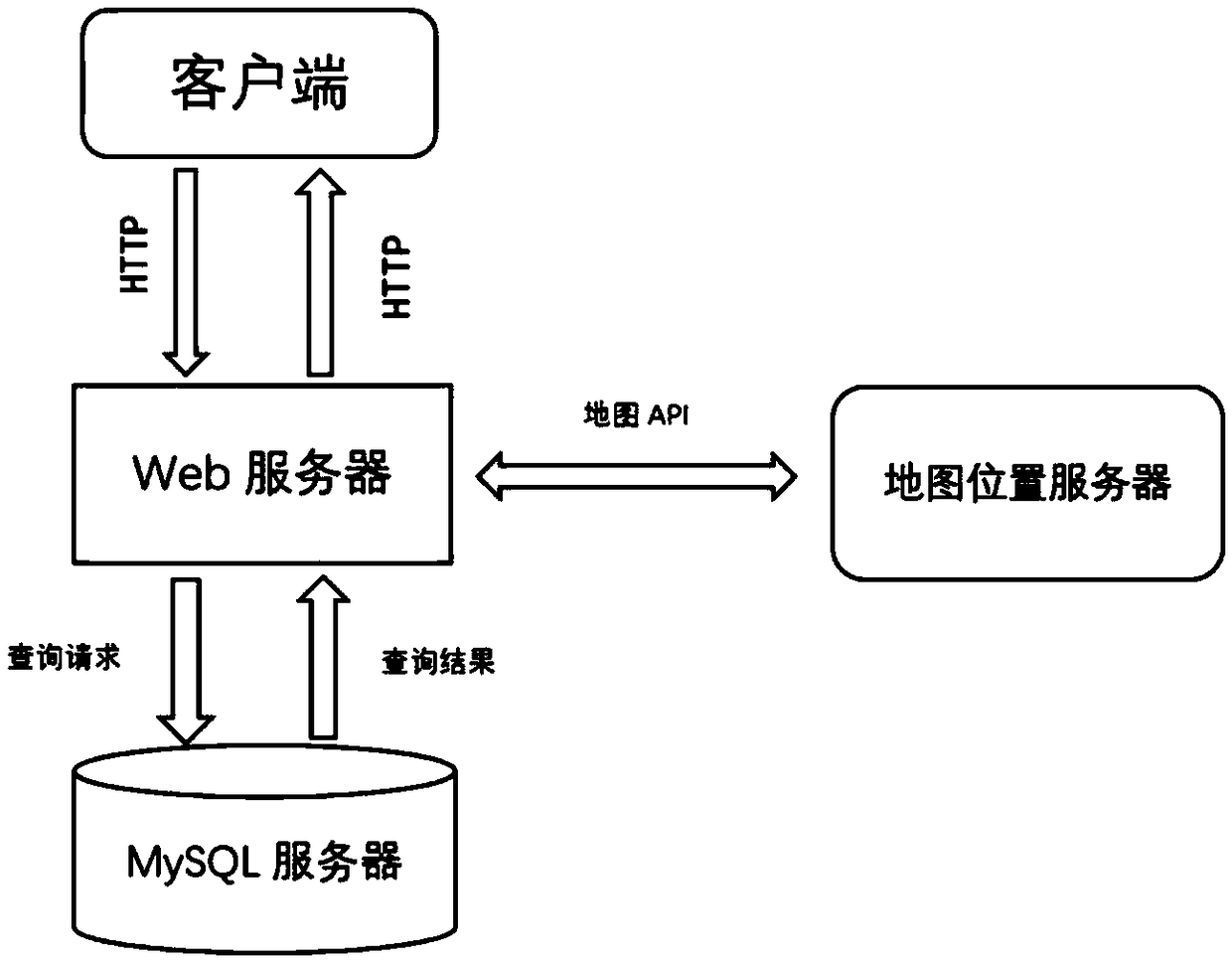
Real-time location sharing method for shared car and mobile terminal
InactiveCN109495841ARealize multi-directional location sharingImprove accuracyLocation information based serviceSecurity arrangementLocation sharingMap Location
The present invention relates to a real-time location sharing method for a shared automobile and a mobile terminal. A web server receives and responds to multi-party request information, and performsinformation interaction with a map location server and a MySQL server. A mobile terminal sends an HTTP request message to the map location server by using a network interface module. The map locationserver uses a GPS positioning system to locate in real time and accurately locate the mobile terminal and the shared car, and then encrypts a location latitude and longitude by using an encryption module. A location sharing module invokes a request encapsulation function of the network interface module, uses the encrypted location latitude and longitude as a multi-party request parameter, generates a client multi-party request message, and sends the client multi-party request message to the web server. The map location server uses the encrypted client location latitude and longitude as a multi-party request parameter, and generates a client multi-party request message. A user receives a multi-party response sent back by the server by using the network interface module, and parses the response message to obtain multi-party result information. In this way, presentation of real-time locations of multi-party friends is implemented.
Owner:安徽小明出行科技有限公司
Medical autocorrelation time series data differential privacy release method
PendingCN111797428AImprove processing efficiencyPrivacy protectionDigital data protectionData privacy protectionOriginal data
The invention provides a medical autocorrelation time series data differential privacy release method. The method comprises the following steps: firstly, constructing personal medical time series data; dividing the personal medical time series data into a plurality of disjoint and equal-length personal medical time series data sub-sequences through a set sliding window; calculating a normalized autocorrelation function of the sub-sequence according to the sub-sequence, and calculating the periodic sensitivity of the sub-sequence according to a query function; and generating Laplace noise sequences corresponding to the sub-sequences, splicing all the noise sequences to obtain Laplace noise sequences corresponding to the sub-sequences, and adding the Laplace noise sequences to the original time series data to obtain a final to-be-released result. According to the method, the privacy of the user is protected from being leaked to a greater extent, and recently-arrived medical time series data can be processed. According to the invention, on the premise of ensuring that the relevancy of the released data is the same as that of the original data, the security of medical time series dataprivacy protection and the time series data processing efficiency can be effectively improved.
Owner:WUHAN UNIV
Webpage real-time synchronization method and system
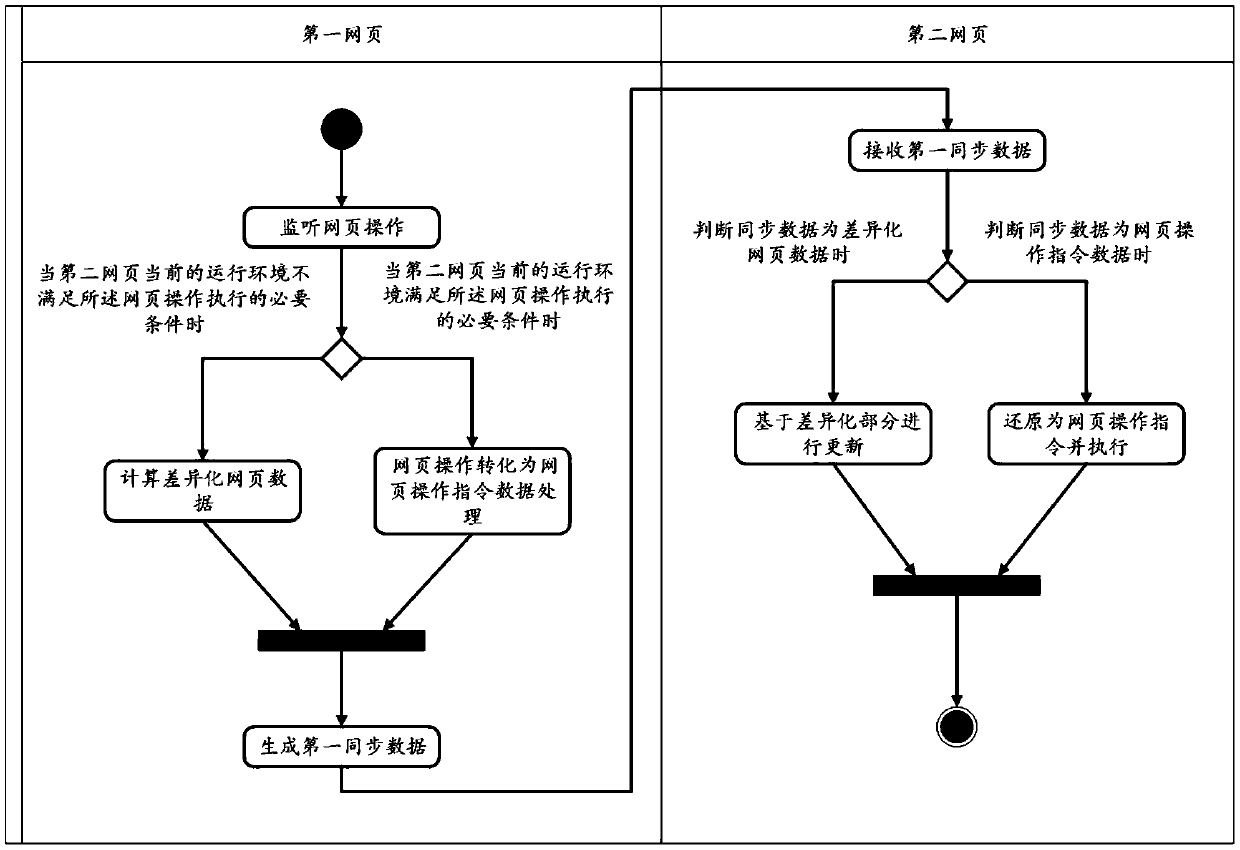
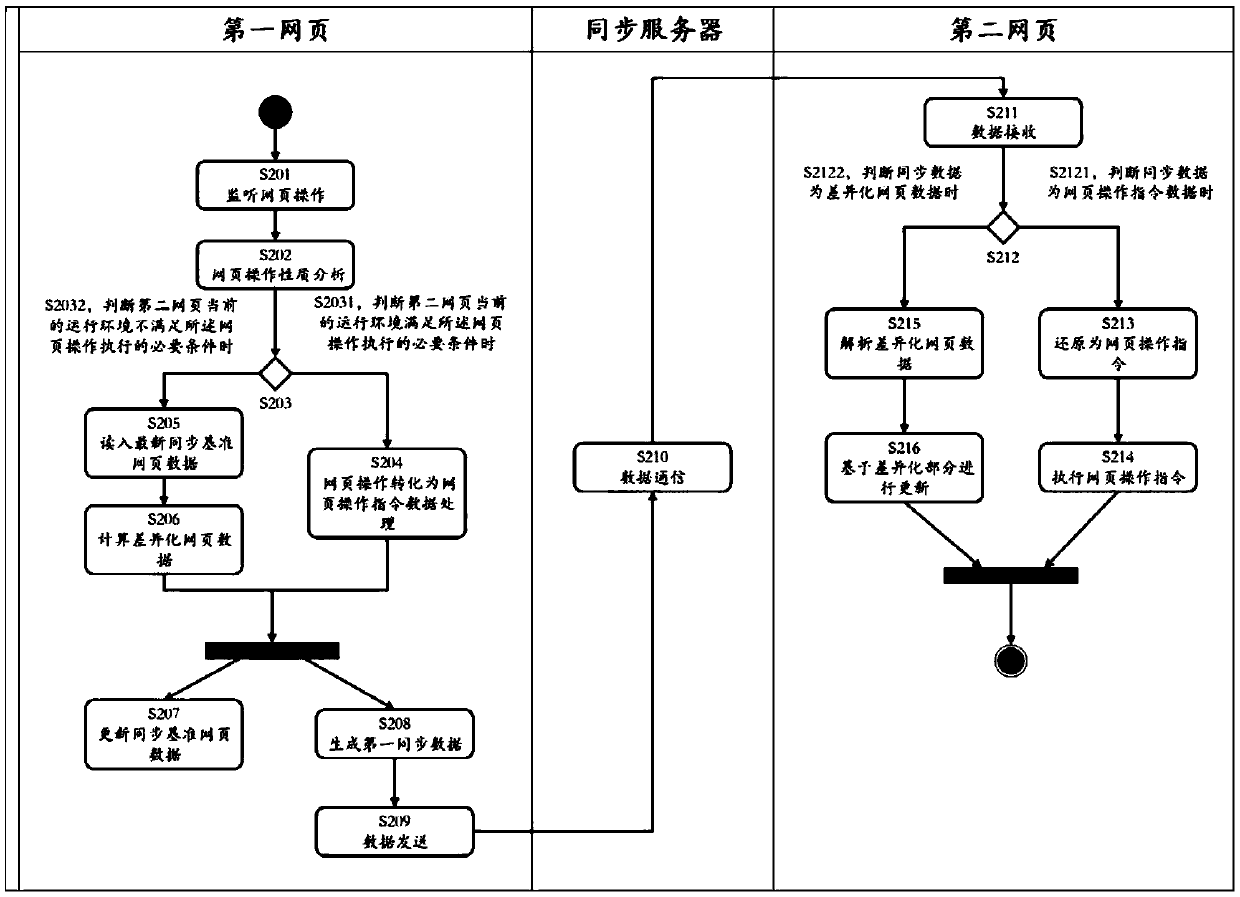
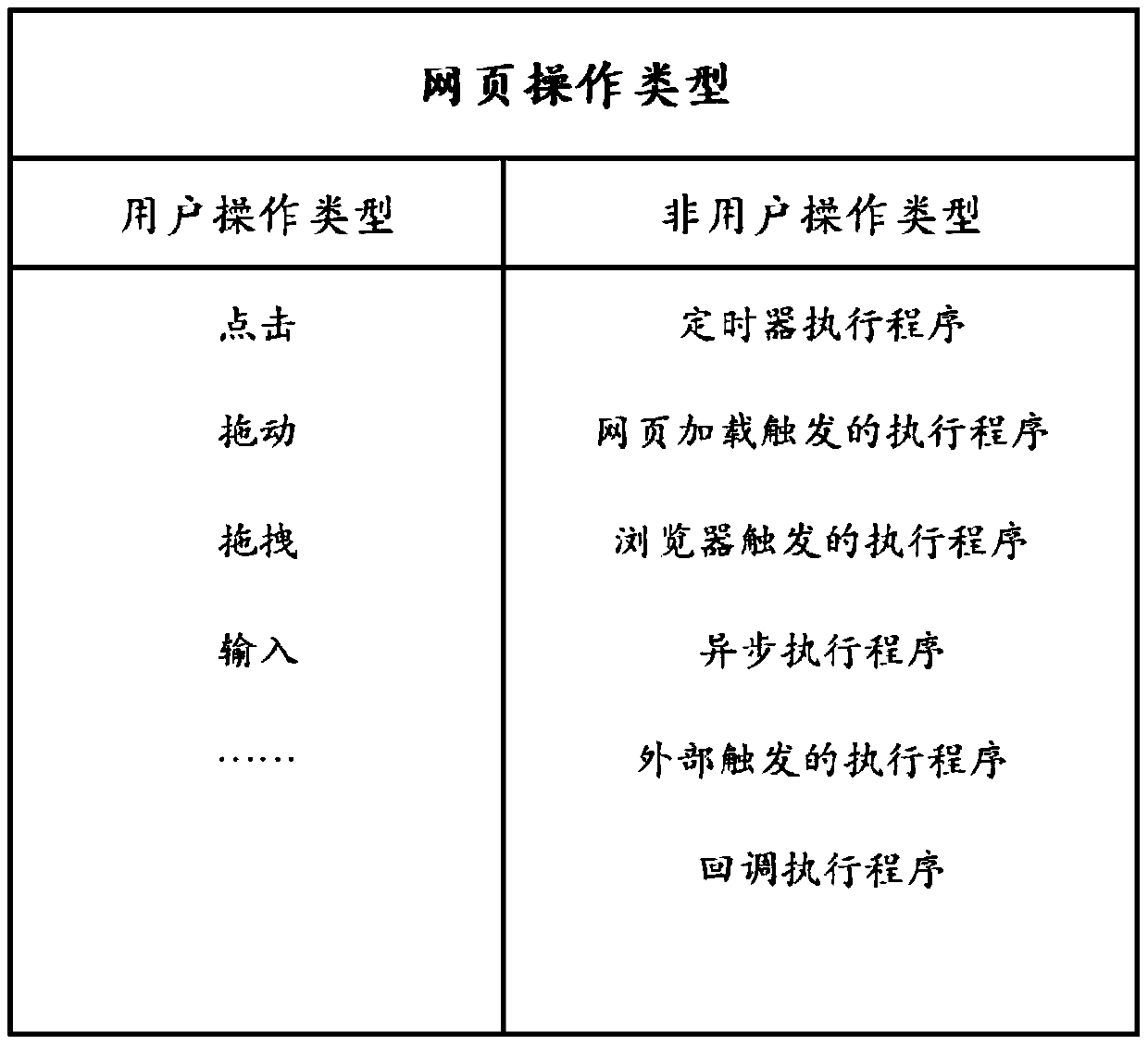
PendingCN111400639AProtection from being leakedReduce data transferDigital data protectionWebsite content managementWeb pageDatabase
The invention provides a webpage real-time synchronization method and system. The method comprises the following steps: after monitoring a webpage operation in a first webpage, converting the webpageoperation into webpage operation instruction data and sending the webpage operation instruction data as first synchronous data when the running environment of the second webpage is judged to meet thenecessary conditions for executing the webpage operation, otherwise, carrying out differentiation analysis on the webpage data after the webpage operation is executed and the latest synchronous reference webpage data by the first webpage to obtain differentiated webpage data, and sending the differentiated webpage data as the first synchronous data; enabling the second webpage to receive the firstsynchronous data and judge the type of the first synchronous data, and when the judgment result is webpage operation instruction data, restoring the webpage operation instruction data to a webpage operation instruction to be executed; when the judgment result is the differentiated webpage data, analyzing the differentiated webpage data and updating the second webpage data based on the differentiated part, so the second webpage data is consistent with the webpage data of the first webpage for displaying the part. The method is suitable for static and dynamic webpages at the same time.
Owner:QINGDAO HOPE BIRD TECH CO LTD
Method and system for JPEG image decompression under ciphertext based on homomorphic encryption
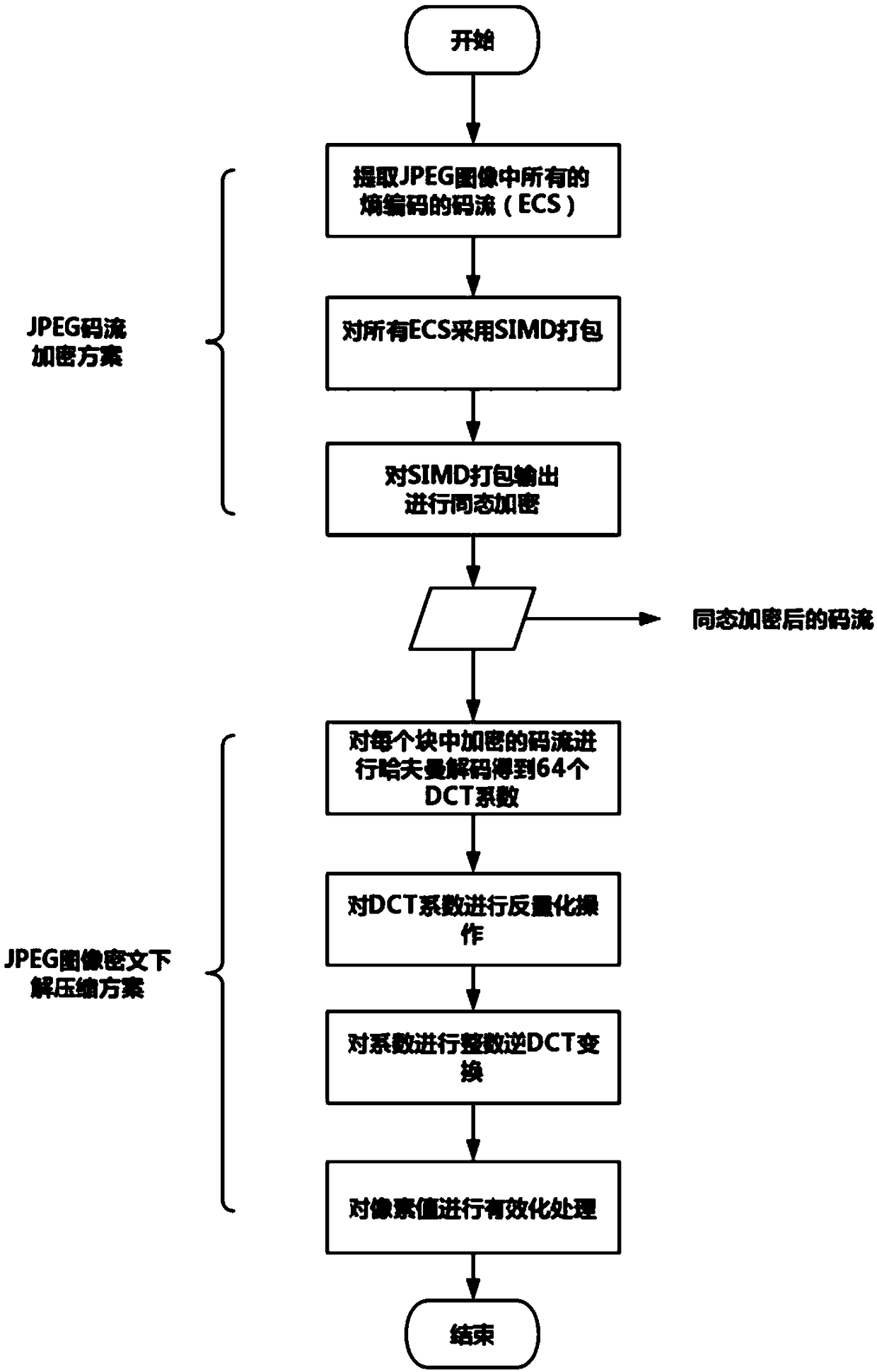
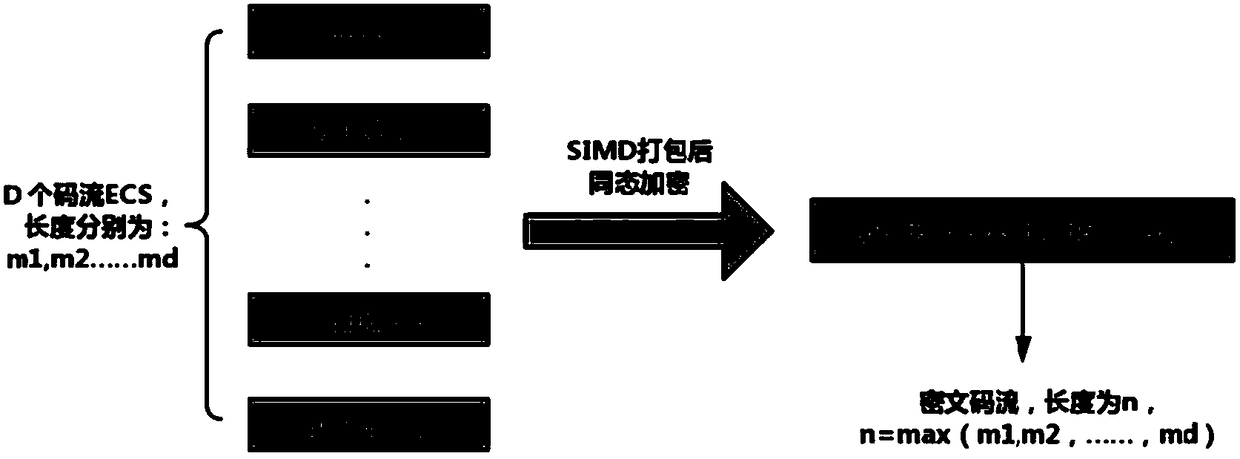
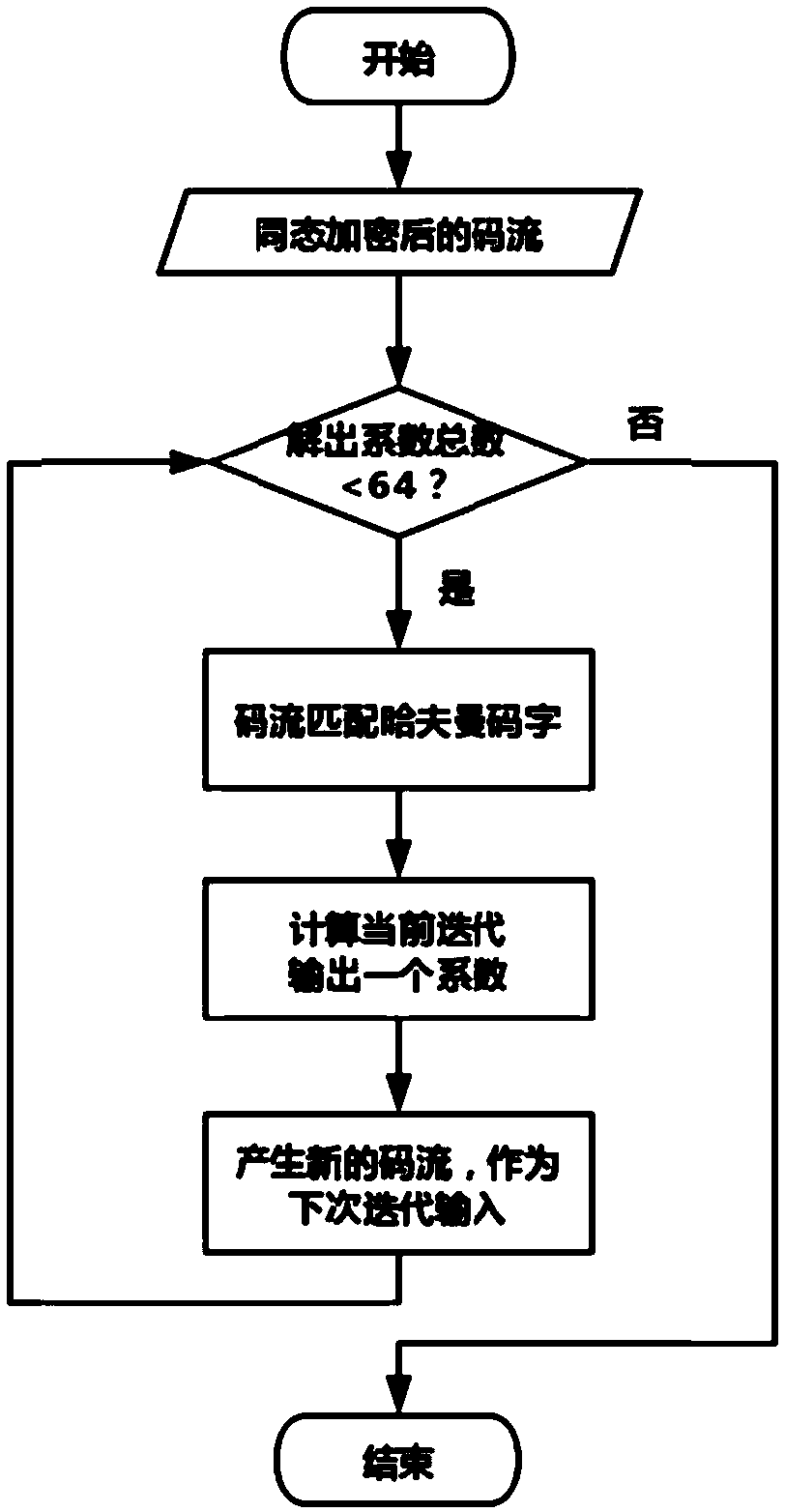
ActiveCN108924552AProtection from being leakedReduce the total number of ciphertextsDigital video signal modificationSelective content distributionComputer hardwareHuffman decoding
The invention discloses a method and a system for JPEG image decompression under ciphertext based on homomorphic encryption, belonging to the technical field of multimedia information protection. Themethod comprises the following steps: encrypting a JPEG image through a homomorphic encryption method, thereby protecting privacy information in the image; obtaining a ciphertext code stream through asingle instruction multiple data encryption method; in a Huffman decoding process, eliminating branch operations in entropy coding through a static iterative method, obtaining one DCT coefficient byperforming iterative operation once, and decoding out all the DCT coefficients through performing iterative operation for many times; matching each code word through a code matching table to decode out the DCT coefficient, and finally converting floating-point arithmetic into integer arithmetic through integer inverse DCT in HEVC, thereby obtaining a decoded pixel value. With the method and the system provided by the invention, decompression of cloud JPEG images under a homomorphic domain can be realized, the homomorphically encrypted pixel value can be obtained for follow-up coherent processing of the homomorphic domain, and image privacy information is protected.
Owner:HUAZHONG UNIV OF SCI & TECH
Protection of confidential resource data
InactiveCN103886261AReduce the burden onProtection from being leakedDigital data protectionComputer securitySignature database
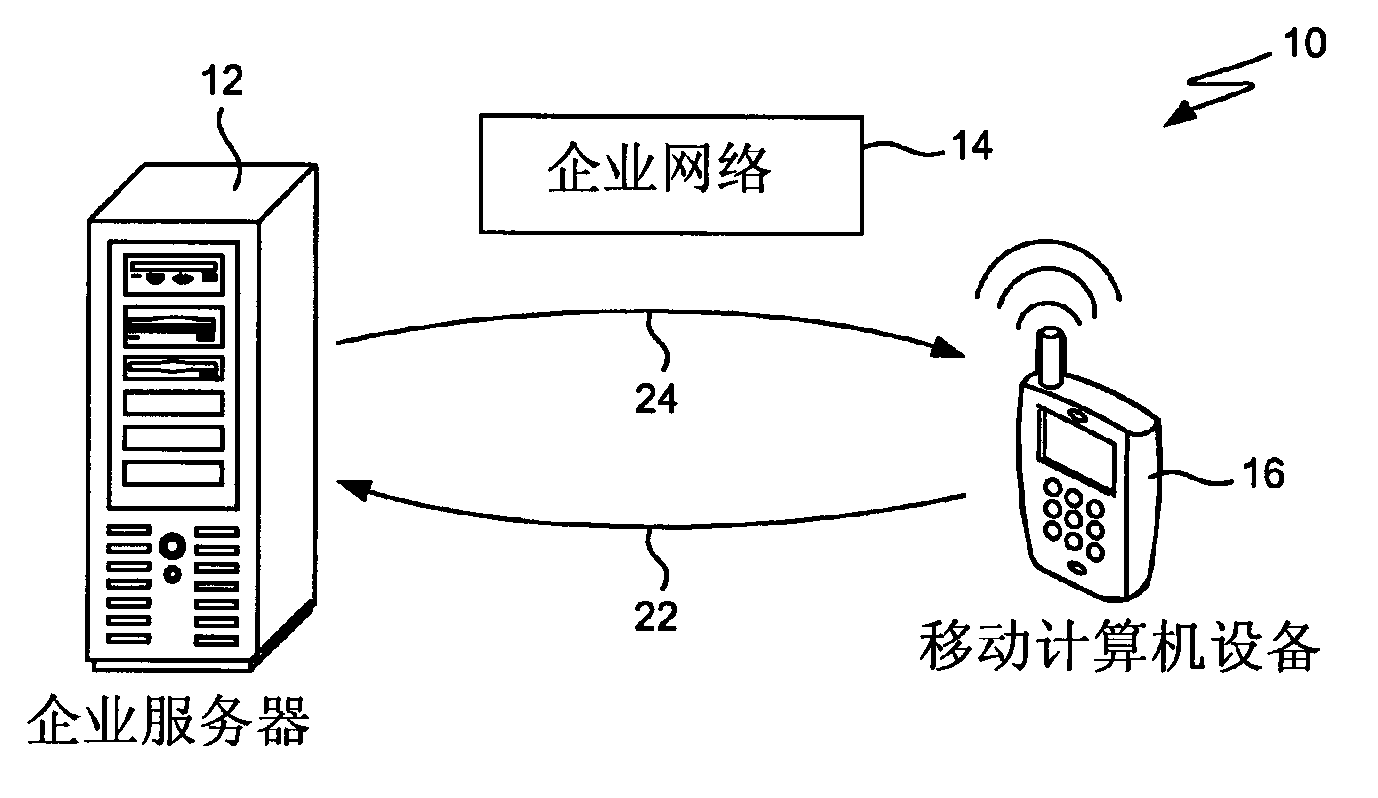
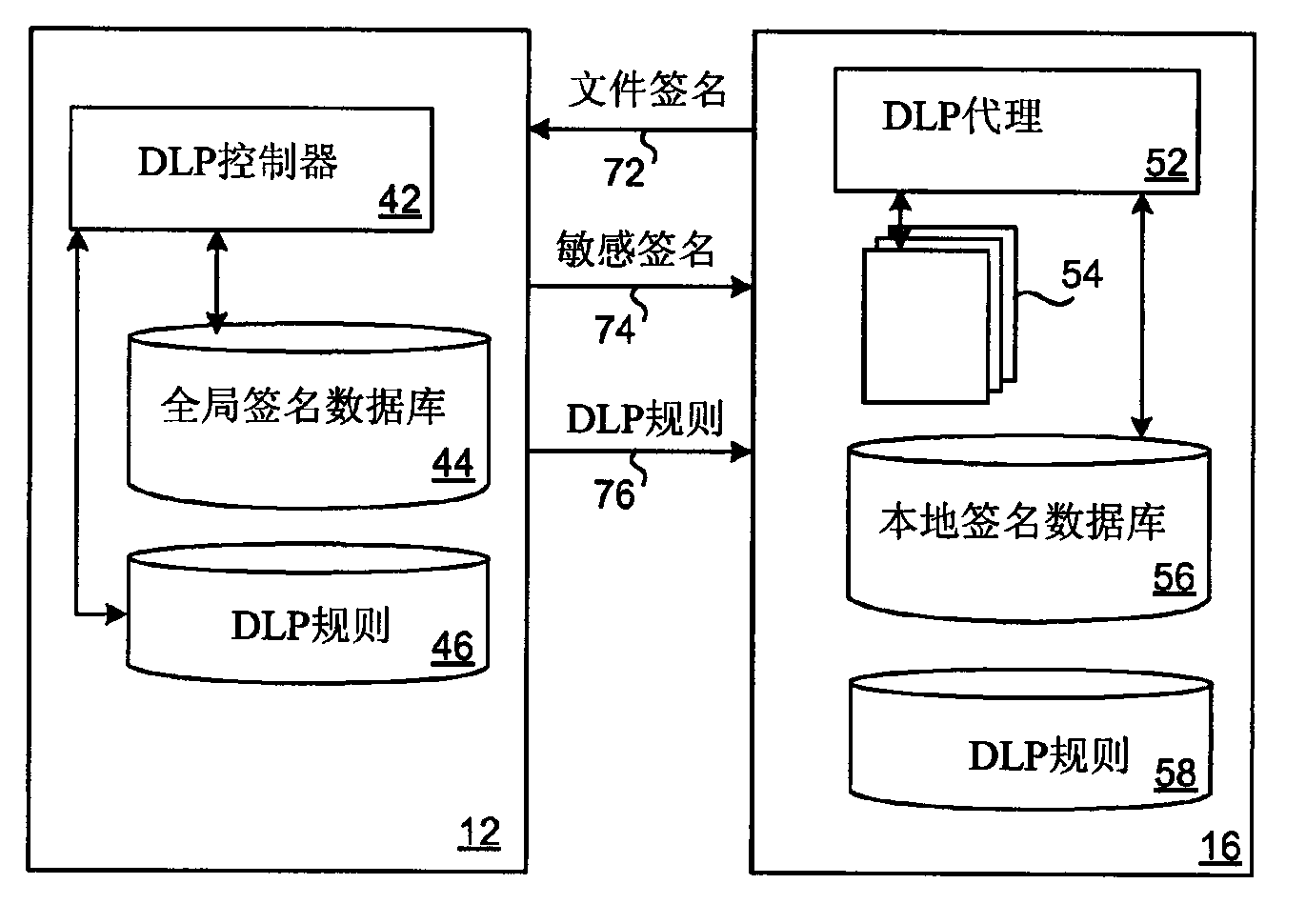
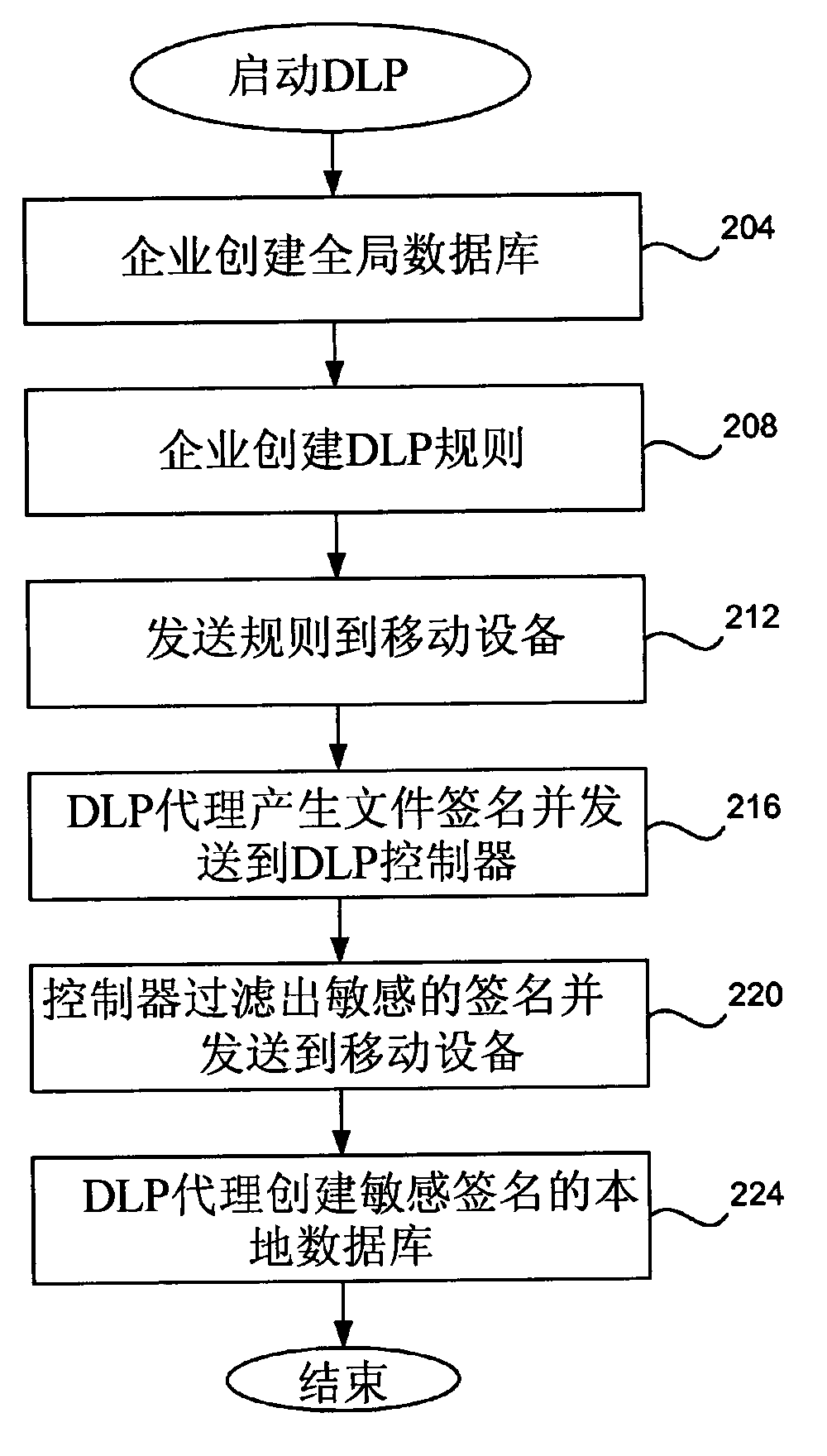
The invention relates to protection of confidential resource data. The protection is achieved by building a local trusted signature database on mobile equipment. When resource-limited equipment (such as a mobile phone) joins an enterprise network, the agent in the equipment generates a digital signature for each file in the equipment and transmits the signatures to an enterprise controller; the controller compares the digital signatures of the files with a globe digital signature database, the filter of the controller filters sensitive digital signatures and feeds the sensitive digital signatures back to the equipment agent, and the agent receives digital signature information and solidifies the same to the database of the agent; the agent analyzes each to-be-transmitted file according to the local digital signature database and DLP rules; transmission of one file is stopped if the signature of the file is found in the local database; if a new file is created, the agent generates a digital signature of the file and transmits the signature to the controller for checking, and if the signature is sensitive, the signature is saved in the local digital signature database; if the DLP controller updates, the equipment retransmits the digital signatures for comparison.
Owner:RES INST OF SUN YAT SEN UNIV & SHENZHEN
Firmware starting method based on PIN code authorization
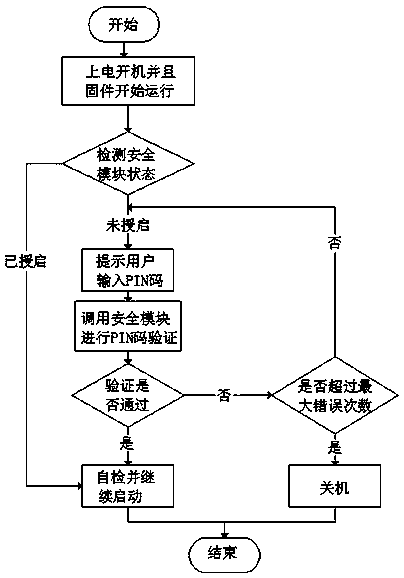
PendingCN109992933AAvoid startingAvoid exposurePlatform integrity maintainanceProgram loading/initiatingComputer resourcesUser input
The invention discloses a firmware starting method based on PIN code authorization. The method comprises the following steps that 1, a TCM security card is used in a computer integrated with the TCM security card; step 2, starting up and electrifying, and detecting the TCM security card by the security firmware; 3, when it is detected that the state of the security card is normal and the firmwareflag bit is not started, the screen pops up a prompt box to prompt a user to input a PIN code; 4, the user inputs the PIN code in a manual input mode or in a mode of reading the file from the storagedevice; step 5, the firmware sends the received PIN code to the TCM for verification; and step 6, after the verification is passed, the firmware starts the mark position and continues to start the system, and if the verification is not passed, prompts re-input and prompts the remaining input times, and shuts down when the maximum fault-tolerant times are exceeded. The method can prevent TCM resources from being exposed in an unsafe environment, prevent the computer from being started in the unsafe environment and use the computer resources, and is better in safety.
Owner:昆仑太科(北京)技术股份有限公司
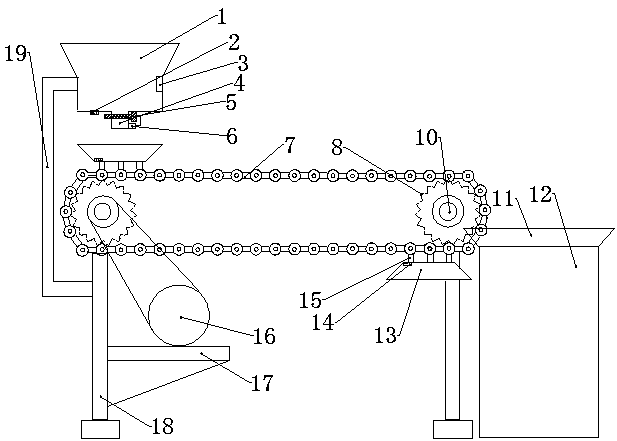
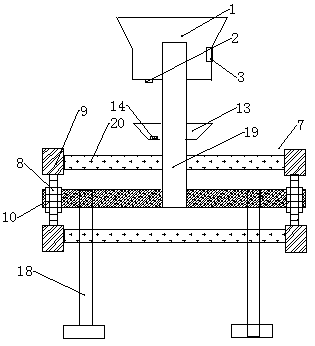
Phenolic molding compound feeding device
The invention relates to a phenolic molding compound feeding device. The device comprises a support, wherein a supporting plate is arranged on the support, a motor is arranged on the supporting plate,the motor is connected with chain wheels through a belt, connecting rods are welded to the left side and the right side of the upper portion of the support, the chain wheels sleeve the two ends of the connecting rods, and the peripheries of the chain wheels are meshed with a chain conveying belt; and the chain conveying belt is composed of a front chain, a fixed rod and a rear chain; the fixed rod is provided with a bearing plate, the bearing plate is connected with the fixed rod through a connecting seat, a light-emitting device is embedded in the bearing plate, a feeding part is arranged above the chain conveying belt, a light sensing alarm is arranged in the feeding part, a discharging port and a photoelectric sensor are arranged at the lower portion of the feeding part, an electromagnetic valve is arranged on the discharging port, the electromagnetic valve is electrically connected with the photoelectric sensor and a time relay, a die is arranged on the right side of the chain conveying belt, and a feeding port is formed in the upper portion of the die. The device has the advantages of being automatic in production, practical and reasonable, and high in applicability.
Owner:YUZHOU YUANDA PLASTIC ELECTRICAL APPLIANCE
Personalized voice/software icon button matching combined control for communication equipment such as mobile phone
InactiveCN106303010ASafe and reliable unlockingProtection from being leakedDevices with voice recognitionSubstation equipmentPersonalizationSolid-state storage
The invention relates to personalized voice / software icon button matching combined control for communication equipment such as a mobile phone. The personalized voice / software icon button matching combined control comprises setting of a personal user voice / software icon button matching combination for the communication equipment such as the mobile phone, authentication of personal user identity authentication and the voice / software icon button matching combination setting by an operator or a website, and introduction of a voice / software icon button matching combined control ('voice spell') technology to electronic cartoon games. A user transmits a personalized voice physical signal ('voice spell') and the software icon button matching combination for the communication equipment such as the mobile phone to the operator and a website remote server, and the personalized voice physical signal and the software icon button matching combination are returned to a solid-state storage of the communication equipment such as the mobile phone to be stored and used after authentication. The user can make an alarm safely and reliably in an emergency state or perform locking and unlocking when the communication equipment such as the mobile phone is in a standby state or a working state according to a priority level through the set 'voice spell'. Meanwhile, high-level electronic cartoon games operated and controlled by the voice spell such as 'Journey to the West' can be developed in a mobile way. The personalized voice / software icon button matching combined control is suitable for civil use, police use, military use and the electronic cartoon games.
Owner:康子纯
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com