Substation inspection robot data transmission encryption and decryption method and system
An inspection robot and data transmission technology, applied in the field of information security, can solve the problems of strong dependence on the center, high construction cost of PKICA, and not suitable for the data transmission security system of inspection robots, etc., to achieve efficient and safe data transmission, protection The effect of leaking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
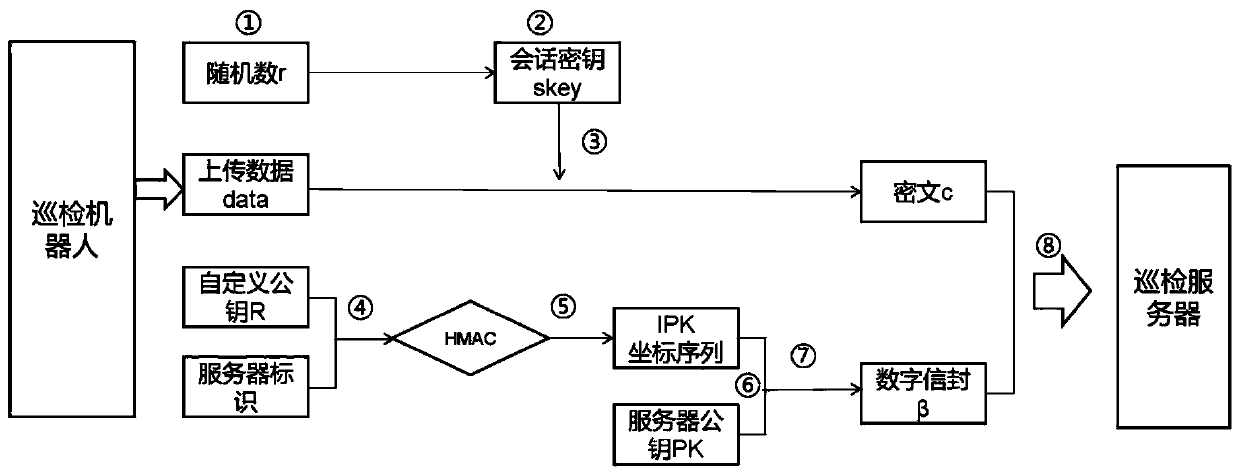
[0034] This embodiment provides a data transmission encryption and decryption method for a substation inspection robot, such as figure 1 As shown, it includes the steps:
[0035] When the inspection robot uploads data to the information management system as the data sender, the uploaded data uses the SM4 encryption algorithm to encrypt the data, and uses the IPK digital envelope technology to realize the encrypted transmission of the session key. The encryption process specifically includes:
[0036] 1) The inspection robot calls the SDK of IPK to generate a random number r, 0
[0037] 2) Calculate the session key skey for data encryption, that is, skey=x mod n, where (x, y)=r. G, G is the base point of the elliptic curve, and mod is the modular operation;
[0038] 3) Use skey as the symmetric encryption key to perform SM4 encryption on the data to be uploaded to obtain the ciphertext to be uploaded, that i...
Embodiment 2
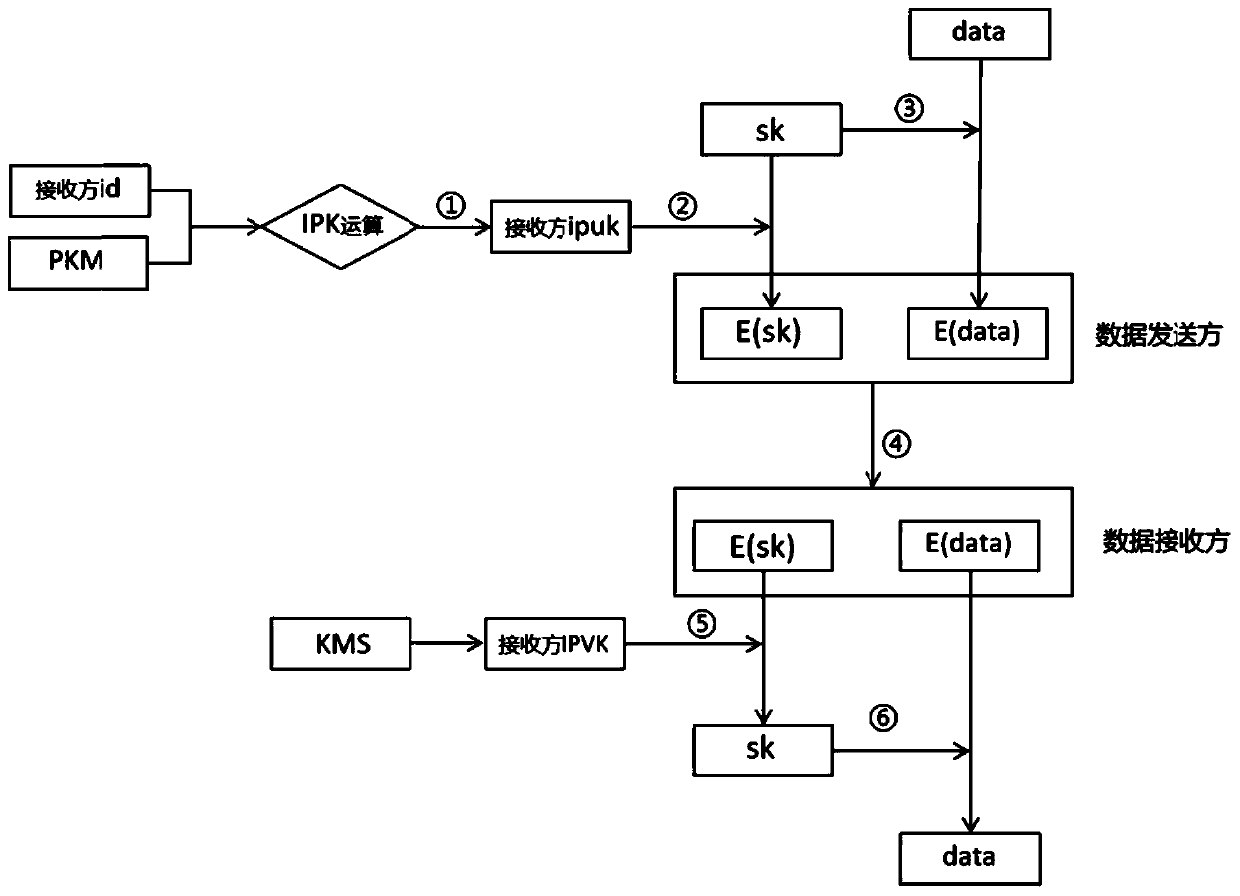
[0050] This embodiment provides a substation inspection robot data transmission encryption and decryption system, such as figure 2 As shown, it includes a data encryption module and a data decryption module; when the inspection robot uploads data to the information management system as the data sender, the inspection robot calls the data encryption module, and uses the data encryption module to encrypt the data; the information management system receives After inspecting the ciphertext data E(data) and session key ciphertext E(sk) sent by the inspection robot, use the data decryption module to decrypt.
[0051] Data encryption module: first use the receiver management server identification id and public key matrix PKM to calculate the receiver server's identification public key ipuk through the IPK mapping algorithm, then input the identification public key ipuk into the IPK USB shield to generate the session key sk, use Identify the public key ipuk to encrypt the session key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com