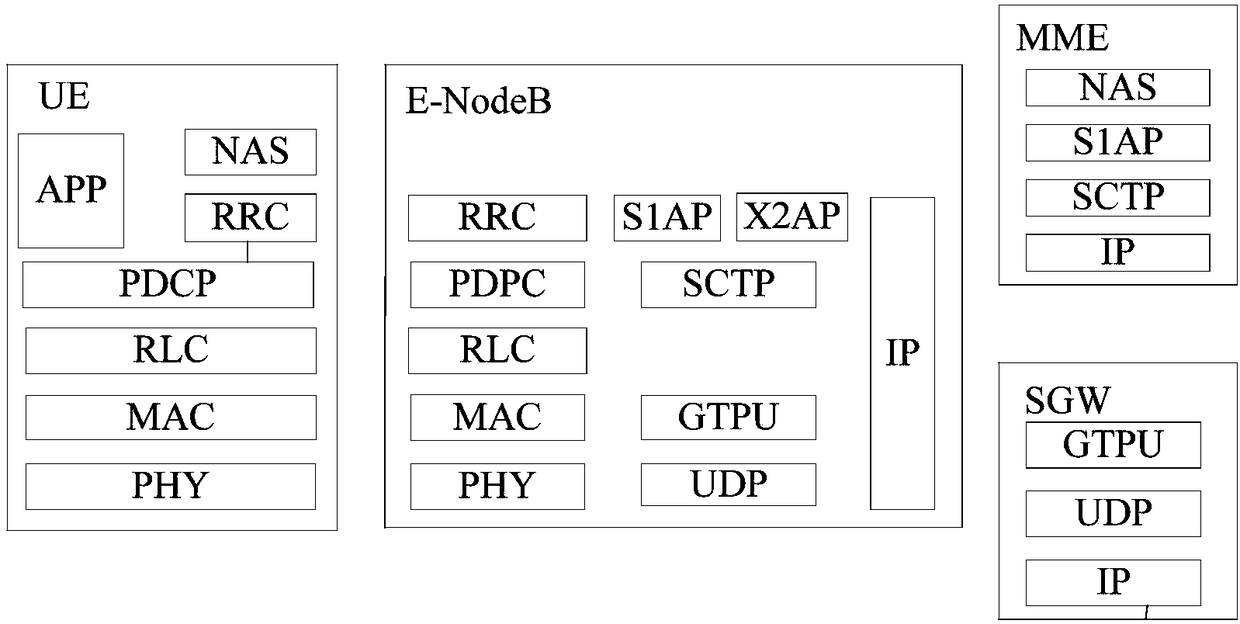
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
43results about How to "Avoid being leaked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Differential privacy protection method of medical data dissemination
ActiveCN105608389AAvoid being leakedGuaranteed to be availableDigital data protectionPatient informationDistortion
The invention discloses a differential privacy protection method of medical data dissemination. A K-anonymous technology and a differential privacy technology are effectively combined to solve the problems that the statistical information of data can not guaranteed to be prevented from being leaked when the K-anonymous technology is solely used, a great quantity of noise is introduced while the differential privacy technology is solely used to only protect the statistical information, a data distortion degree becomes high to lower data utilizability; and therefore, on the premise that the medical data is guaranteed to be available, the risk of patient information leakage when the medical data is collected and disseminated can be effectively avoided so as to perform the efficacy of the medical data during statistics and mining.
Owner:GUANGXI NORMAL UNIV
SM2 signature algorithm protection method for resisting error attack based on lattice
ActiveCN104852805AFull resistanceAvoid being leakedUser identity/authority verificationDigital data protectionScalar multiplicationComputer security
The present invention discloses an SM2 signature algorithm protection method for resisting error attack based on lattice. The method comprises the following steps: (1) a signer A carries out Hash operation on an inputted message M to be signed and combines an operation result ZA and the message M to obtain M<->, (2) M<-> is subjected to hashing compression to obtain a pre-processing result e, (3) two random numbers k and w are generated, the scalar multiplication kG of the random number k and a base point G and the scalar multiplication wPA of the random number w and a public key PA are calculated respectively, then the above two scalar multiplications are summed to an elliptic curve point Q, (4) the coordinate x1 mode n add of e and point Q is calculated to obtain an r value, (5) private keys dA, k, w, r are subjected to substitution to obtain a signature result s. By using the method provided by the invention, the lattice attack of an SM2 signature algorithm can be effectively and comprehensively resisted.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +2
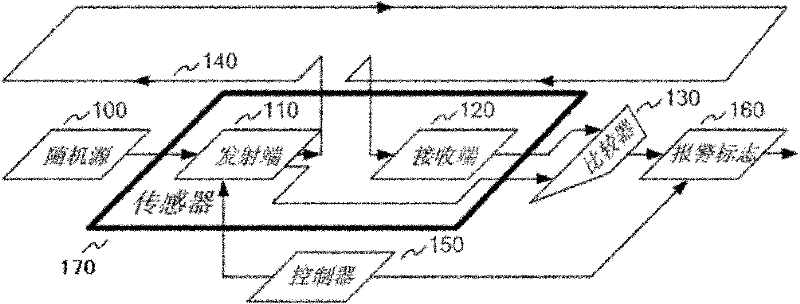
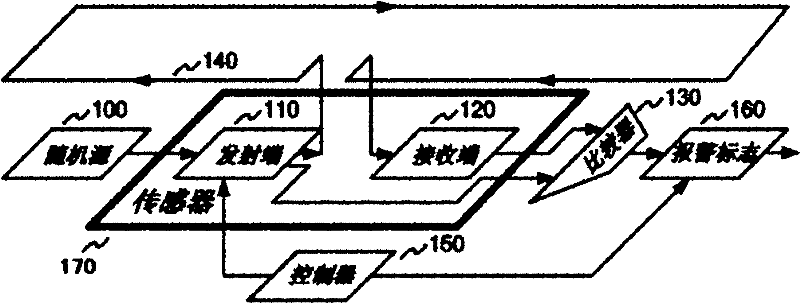
Device for defending invasive attack
InactiveCN102455394AAvoid being leakedImprove securityElectrical testingEngineeringUltimate tensile strength
The invention discloses a device for defending invasive attack. The device comprises one or more sensors, one or more metal wires, a comparator and a controller, wherein the signal transmitting end of each sensor is used for transmitting a signal, and the signal receiving end of each sensor is used for detecting the integrity of the signal; the metal wires are covered above a protected circuit and used for connecting the signal transmitting ends and the signal receiving ends of the sensors together; the input end of the comparator is respectively connected with the signal transmitting ends and the signal receiving ends of the sensors and used for comparing the signals of the signal transmitting ends and the signal receiving ends, and the output end of the comparator is connected with the data input end of an alarm mark; and the controller is used for controlling the signal update of the signal transmitting ends of the sensors, controlling the comparator to periodically detect the connectivity of the metal wires and enabling the alarm mark to be valid when the connectivity of the metal wires is abnormal. Through the device, the internal signals of an integrated circuit (IC) chip can be effectively prevented from being detected by the invasive attack, the security of user data is protected, and the security strength of the IC chip is improved.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
Method and terminal for displaying encrypted information
ActiveCN104732125AAvoid viewingAvoid being leakedDigital data authenticationUser inputComputer terminal
The invention discloses a method for displaying encrypted information. The method includes the following steps of obtaining verification information input by a user, wherein the verification information is used for checking the encrypted information of a current application program; displaying the encrypted information on an interface of the current application program if the verification information input by the user is consistent with preset verification information. The invention further discloses a terminal for displaying the encrypted information. The method and terminal need the verification step that information needs to be verified before the encrypted information is displayed in the interface of the current application program, effectively prevent others from checking the encrypted information in the terminal, are higher in safety, and avoid the phenomenon that personal user information contained in the encrypted information is leaked.
Owner:NUBIA TECHNOLOGY CO LTD
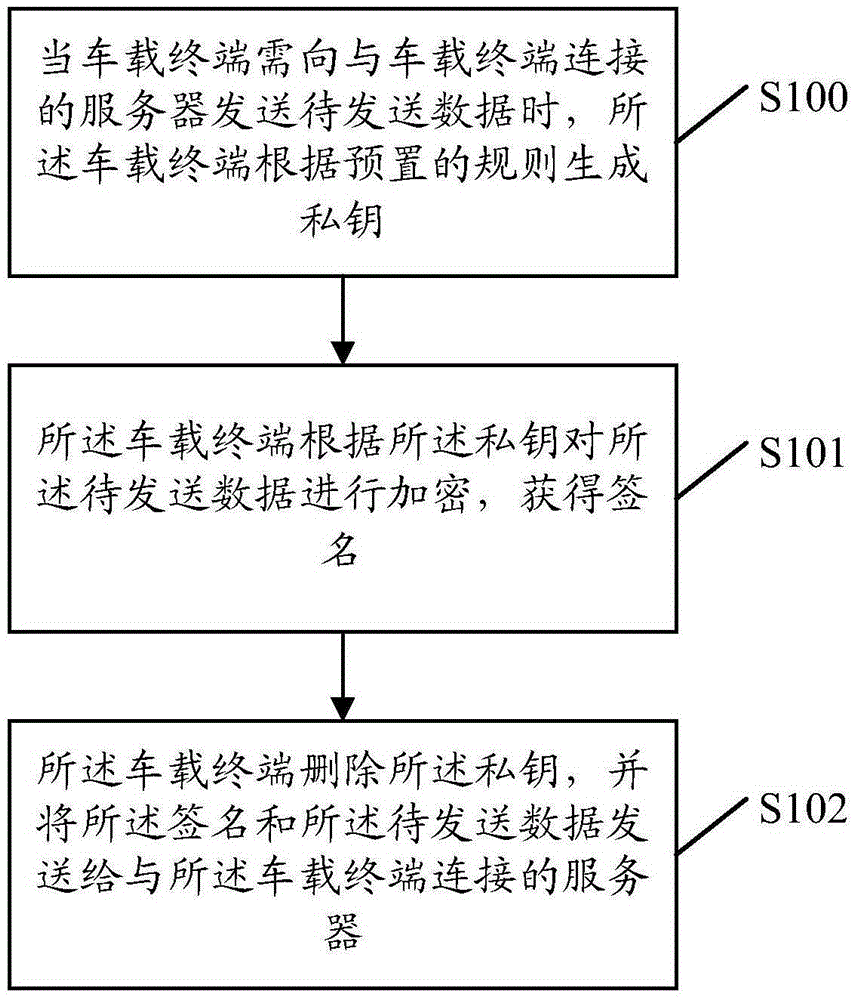
Data transmission method, device and system
The embodiment of the invention discloses a data transmission method, comprising: when a vehicle terminal is required to send data to be sent to a server in connection with the vehicle terminal, the vehicle terminal generating a private key according to a preset rule; the vehicle terminal encrypting the data to be sent according to the private key to obtain a signature; and the vehicle terminal deleting the private key, and sending the signature and the data to be sent to the server in connection with the vehicle terminal. The embodiment of the invention also discloses a device and a system. According to the invention, the data transmission security of the vehicle terminal can be improved.
Owner:LAUNCH TECH CO LTD
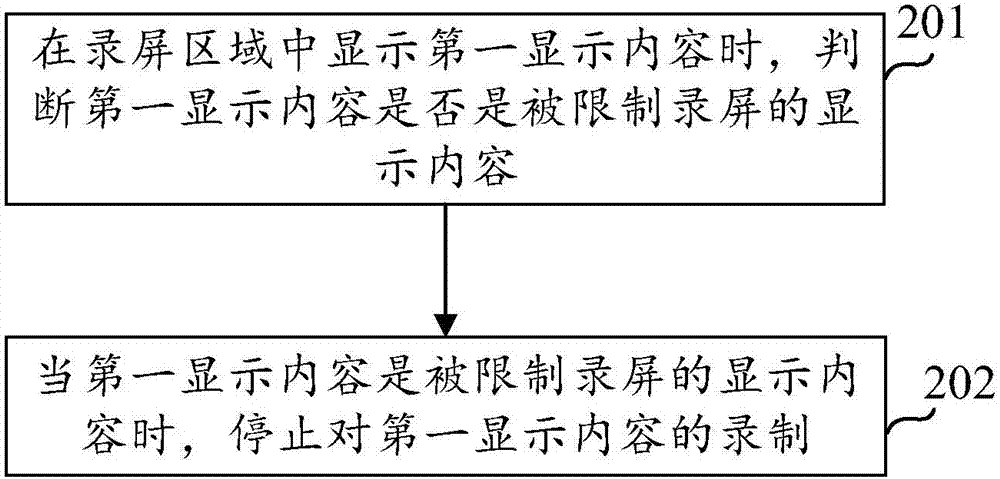
Screen recording method, screen recording device and terminal
InactiveCN107958168AAvoid being leakedEnsure information securityInternal/peripheral component protectionPrivacy protectionInformation security
The invention discloses a screen recording method, a screen recording device and a terminal, and relates to the technical field of terminals. The screen recording method includes judging whether firstdisplay contents are display contents with screen recording restrictions or not when the first display contents are displayed in screen recording zones; stopping recording the first display contentswhen the first display contents are the display contents with the screen recording restrictions. The screen recording method, the screen recording device and the terminal in an embodiment of the invention have the advantages that whether the first display contents are the display contents with the screen recording restrictions or not is judged, the terminal stops recording screens with the first display contents when the first display contents are the display contents with the screen recording restrictions, the display contents with the screen recording restrictions can be the display contentswith privacy protection requirements, accordingly, privacy information of users can be prevented from being recorded in video files and further can be prevented from being leaked, and the informationsafety of the users can be guaranteed.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
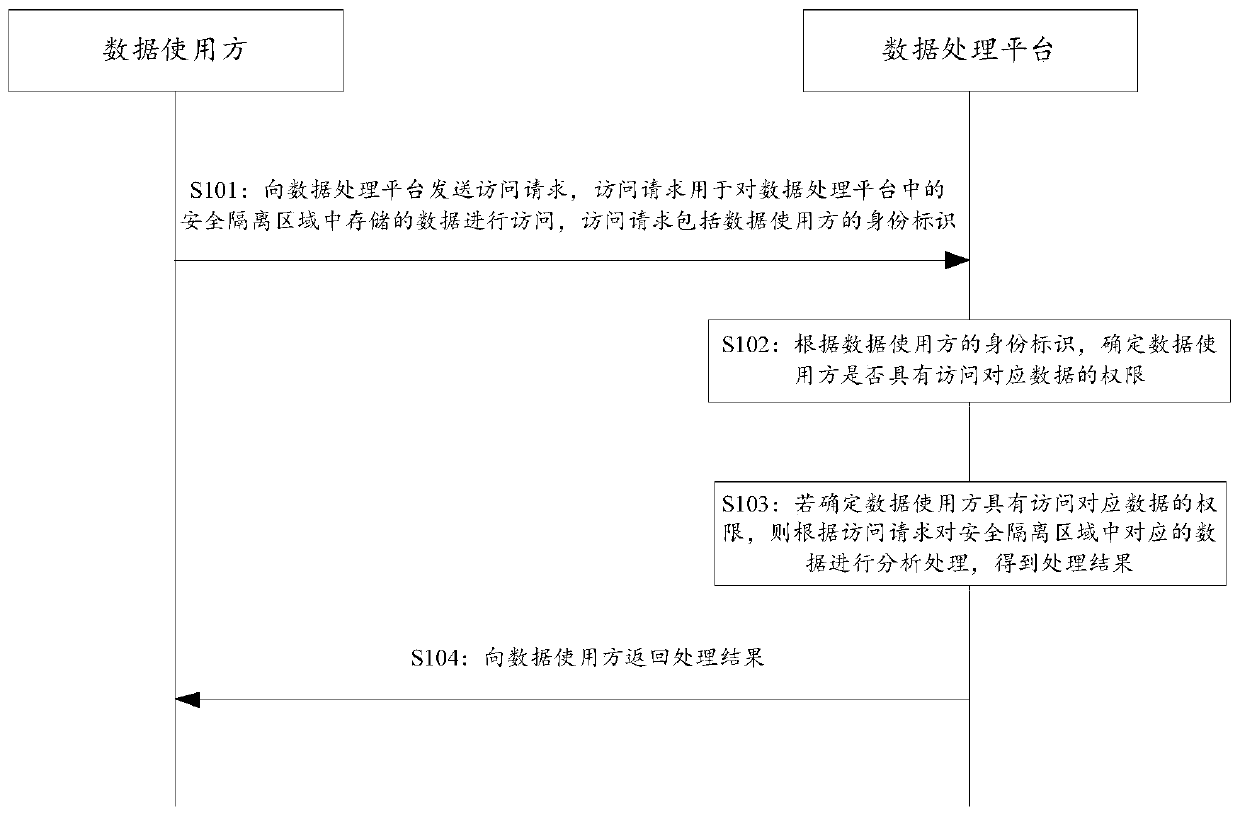
Data processing method, device and equipment and storage medium
ActiveCN111079182AImprove securityAvoid being leakedDigital data protectionData providerData security
The invention discloses a data processing method, device and equipment and a storage medium. The method comprises the following steps: a data processing platform receives an access request carrying anidentity identifier sent by a data user, wherein the access request is used for accessing data stored in the security isolation area, and data in the security isolation area cannot be copied; and themethod further includes determining whether the data user has the authority to access the corresponding data or not according to the identity identifier, if so, analyzing and processing the corresponding data in the security isolation area according to the access request to obtain a processing result, and returning the processing result to the data user. According to the platform provided by thescheme, the data provider uploads the data to the security isolation area which cannot be copied, and the data user can only use the data on the platform, so that the data is effectively prevented from being leaked, and the data security is improved.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Medical health information platform using method for citizens
InactiveCN105069732APrevent data from being leakedAvoid being leakedData processing applicationsAuthorizationMedical health
The invention discloses a medical health information platform using method for citizens. The method comprises a person of interest health record management step and a personal health record or person of interest health record checking step. The step of person of interest health record management includes associating health records of persons of interest to obtain authorization of the persons of interest, and checking and managing health records of persons of interest, wherein the persons of interest comprise relatives or non-relative persons. A wearable equipment association step includes associating wearable equipment with a medical information platform, and inputting data detected by the wearable equipment into the medical information platform. According to the invention, on the basis of the conventional medical health information platform, convenience is provided by the citizens by the person of interest health record management step, the wearable equipment association step, and the personal health record or person of interest health record checking step.
Owner:CHENGDU GOLDISC UESTC MULTIMEDIA TECH
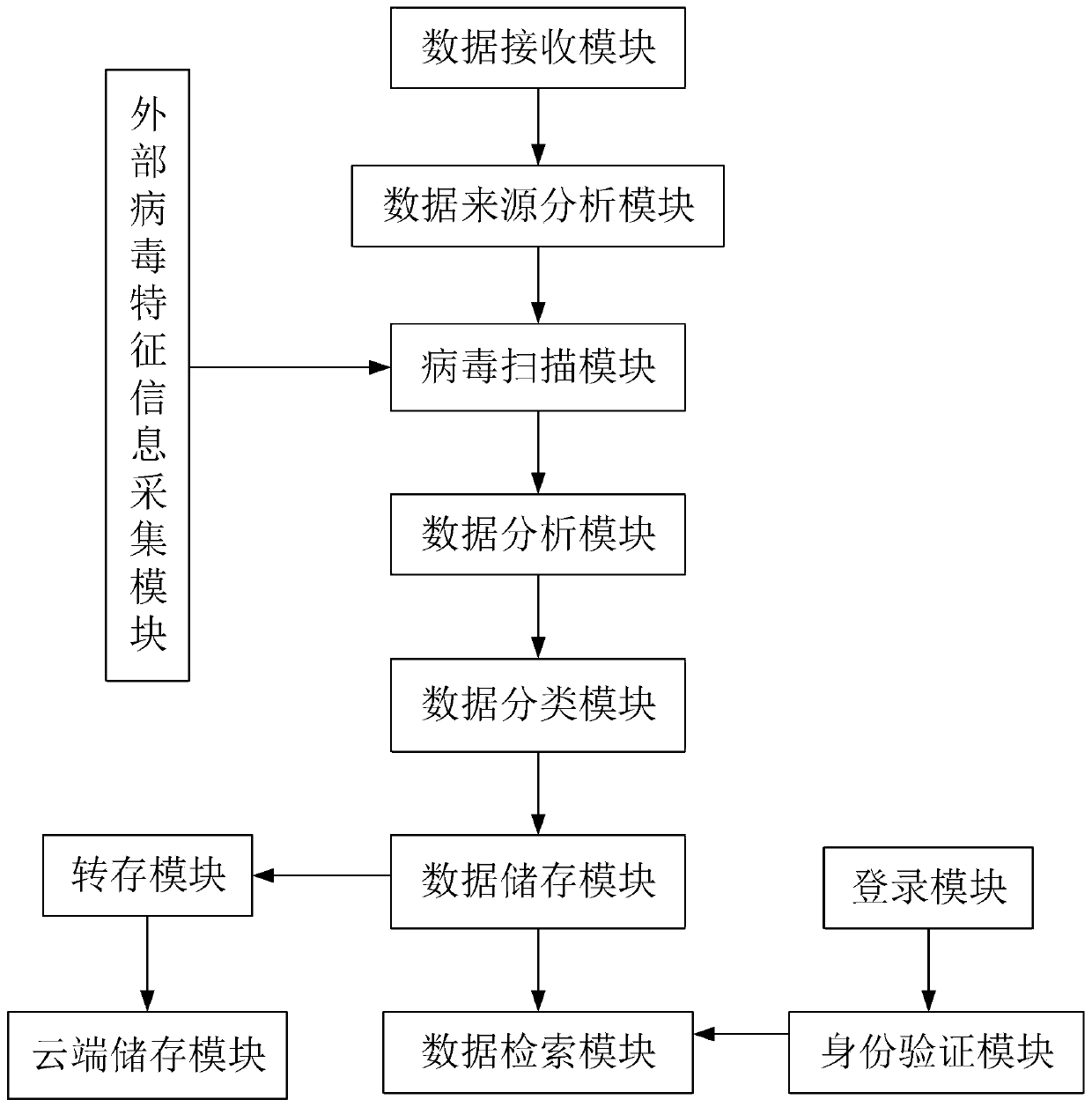
Electronic information intelligent storage system for industrial management
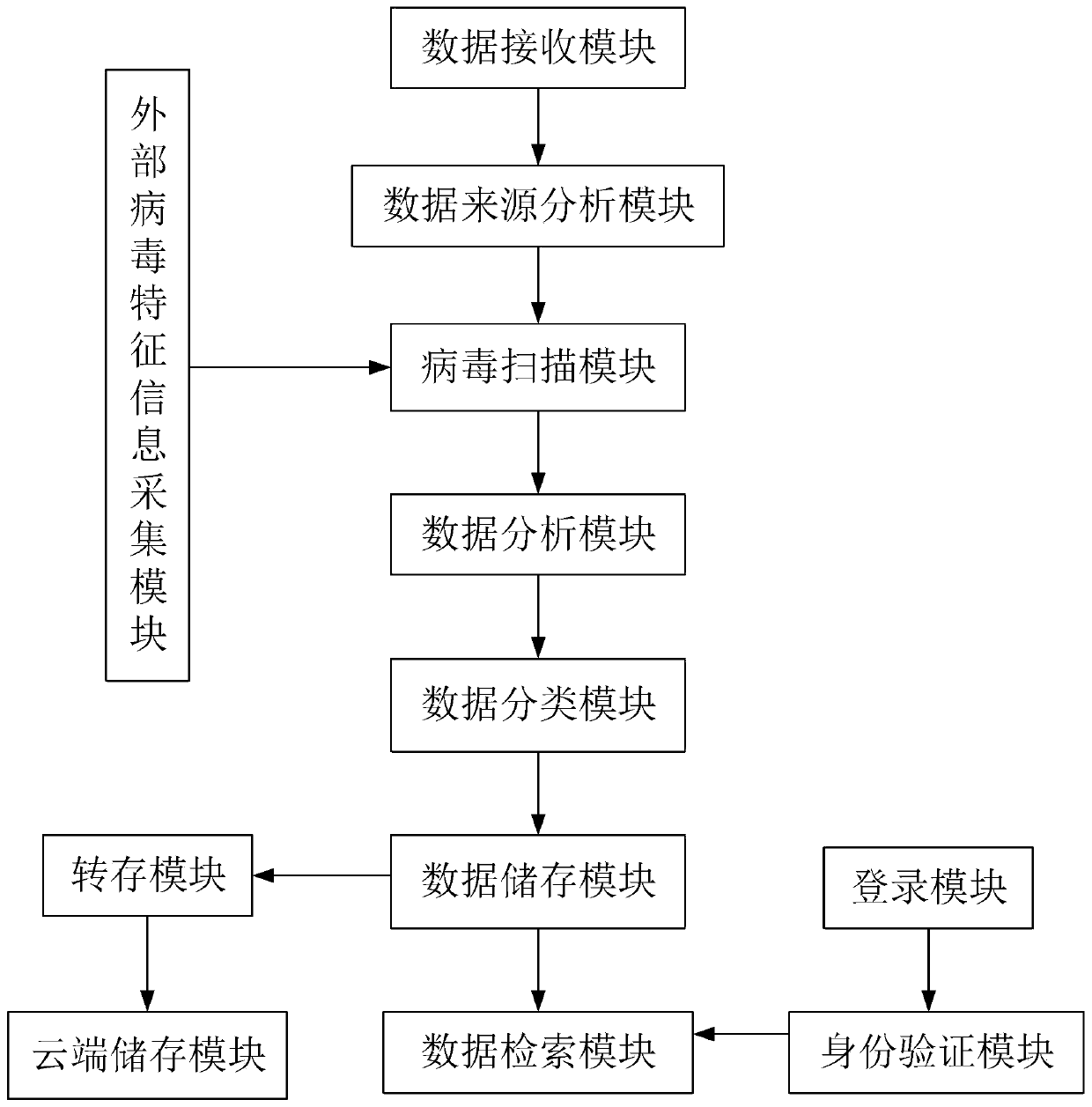
ActiveCN110008704AEnsure safetyAvoid being leakedDigital data authenticationPlatform integrity maintainanceData retrievalData source
The invention discloses an electronic information intelligent storage system for industrial management. The electronic information intelligent storage system comprises a data receiving module, a datasource analysis module, a virus scanning module, a data processing module, a data classification module, a data storage module, a transfer storage module, a cloud storage module, a data retrieval module, an identity verification module and a login module. The data receiving module is in communication connection with the data source analysis module; the data source analysis module is in communication connection with the virus scanning module; wherein the external virus characteristic information acquisition module is in communication connection with the virus scanning module, the virus scanningmodule is in communication connection with the data processing module, the data processing module is in communication connection with the data classification module, and the data classification module is in communication connection with the data storage module; according to the invention, the security of the stored data can be better ensured, and meanwhile, the system can be more convenient to use and is more suitable for popularization and application.
Owner:深圳市熠华智能科技有限公司
Encryption method, device and equipment based on features of information and storage medium
PendingCN112131593AIncrease the difficulty of decryptionImprove securityFinanceSemantic analysisCiphertextEngineering
The embodiment of the invention discloses an encryption method, device and equipment based on features of information and a storage medium, and the method comprises the steps: obtaining a target function for describing information, and the feature information of to-be-processed target information; dividing the target information according to the feature information of the target information to obtain at least two pieces of sub-information; obtaining coordinate information corresponding to each piece of sub-information in the at least two pieces of sub-information according to the target function; encrypting the coordinate information of each piece of sub-information in the at least two pieces of sub-information to obtain a ciphertext of the coordinate information corresponding to each piece of sub-information; and determining the ciphertext of the coordinate information corresponding to each piece of sub-information as the ciphertext of the target information, and storing the ciphertext of the target information in a blockchain network. By adopting the method, the security of the target information can be improved, the method is suitable for the field of smart medical treatment, and the construction of smart cities can be further promoted.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Secret divulging prevention method, terminal and computer readable storage medium
PendingCN110020551AAvoid being leakedPrevent leakageDigital data protectionNatural language data processingComputer engineering
The invention discloses a secret divulging prevention method, a terminal and a computer readable storage medium. According to the method, a to-be-detected file is picked up through a multimedia pickupdevice in a terminal; whether a preset confidential object exists in the to-be-detected file or not is judged; if yes, the to-be-detected file is processed according to a preset anti-divulging processing mode. The defect that the user experience satisfaction degree is low due to the fact that confidential files are prone to flow out in the prior art is overcome. The invention further discloses the terminal and the computer readable storage medium, by implementing the scheme, when the file with the secret object is detected, the file can be processed, so that the file is prevented from being leaked, and the user experience is improved.
Owner:NUBIA TECHNOLOGY CO LTD
Data processing method, device and system
InactiveCN106101105APrevent theftImprove user experienceTransmissionData operationsApplication software
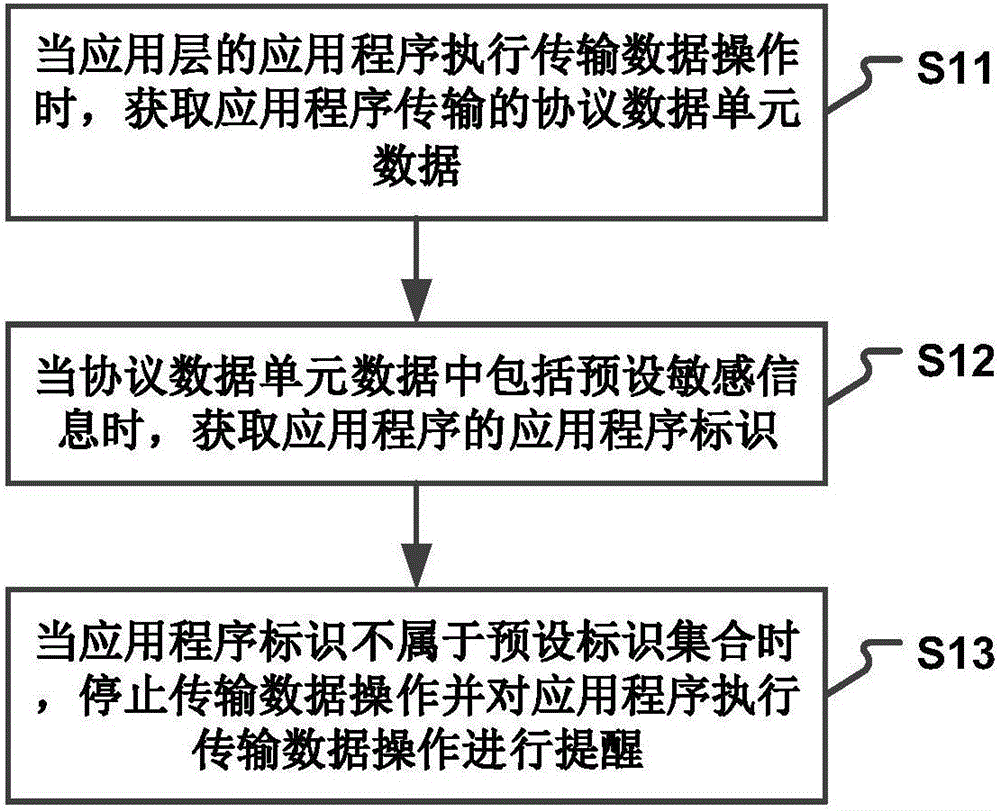
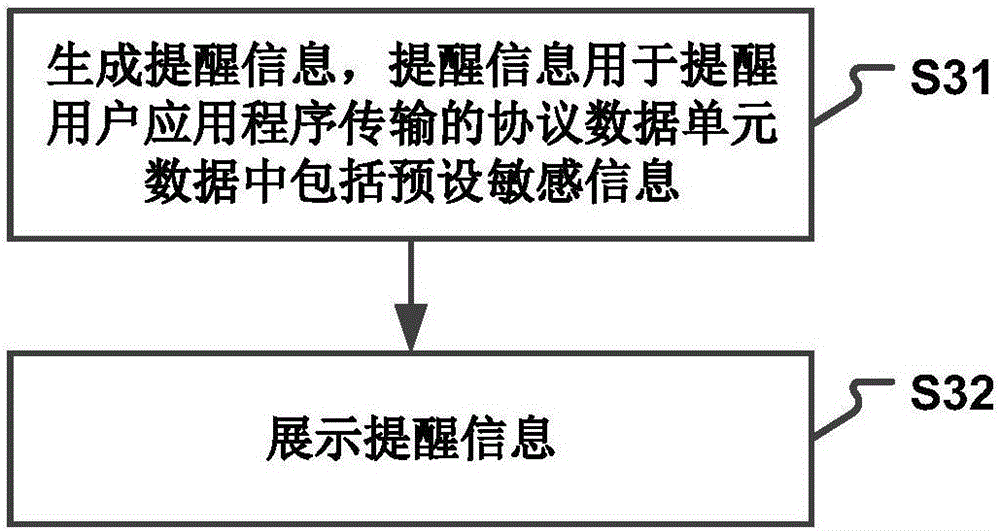
The invention relates to a data processing method, device and system. The method comprises the following steps: when an application of an application layer executes a data transmission operation, acquiring protocol data unit data transmitted by the application; when the protocol data unit data include preset sensitive information, acquiring an application identifier of the application; and when the application identifier does not belong to a preset identifier set, stopping the data transmission operation and instructing the application to execute the data transmission operation. Through the technical scheme, sensitive information in a terminal can be prevented from being stolen by Trojan programs or phishing websites; a user can easily and accurately get the Trojan programs hidden in the terminal; and the information security and property security of the terminal user are protected. Moreover, on the basis of not influencing the work of trusted applications, the information intercepting accuracy and the suspicious Trojan program identification accuracy are increased; the sensitive information of the user is protected from being leaked; and the user experience of the terminal is improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Voice interaction method, device, system and equipment for protecting privacy and storage medium
ActiveCN113472806AAvoid being leakedPrivacy protectionSpeech analysisTransmissionComputer securityUser - individual
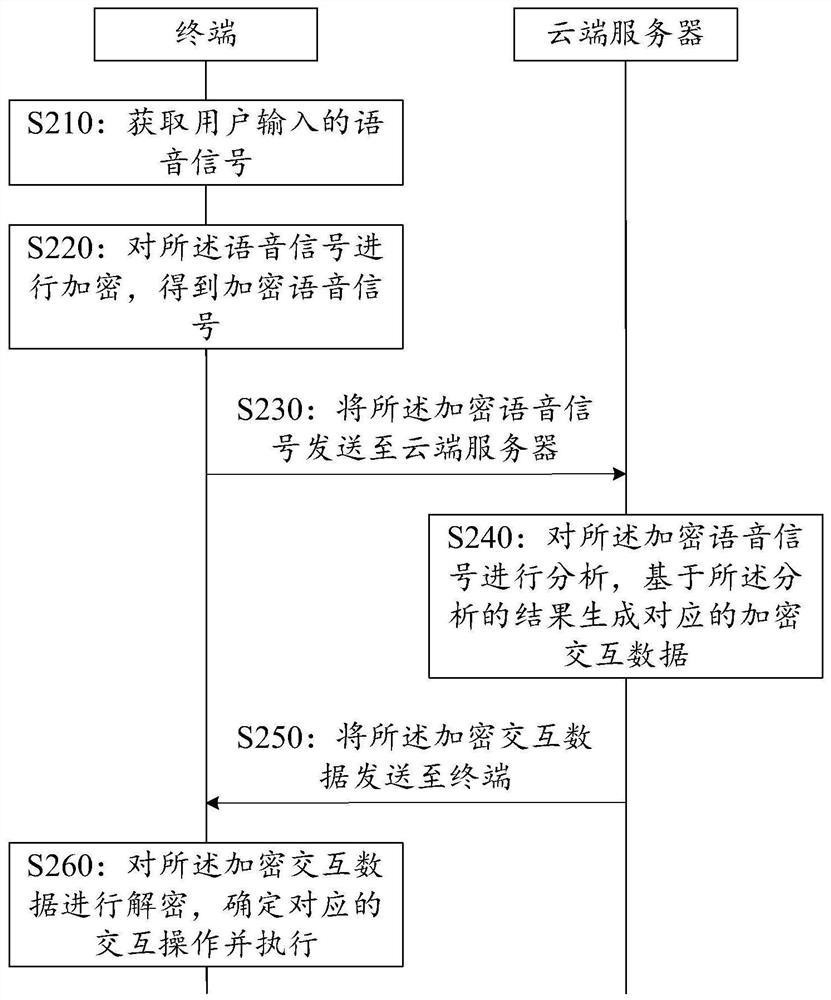
The invention provides a privacy-protecting voice interaction method, device, system and equipment and a storage medium. The method comprises the steps: acquiring, by a terminal, a voice signal input by a user; encrypting the voice signal to obtain an encrypted voice signal; sending the encrypted voice signal to a cloud server; analying, by the cloud server, the encrypted voice signal and generating the corresponding encrypted interaction data based on an analysis result; sending the encrypted interaction data to the terminal; decrpyting, by the terminal, the encrypted interaction data, and determining and executing a corresponding interaction operation. According to the voice interaction method, in the whole voice interaction process, the cloud server carries out analysis processing completely based on the encrypted information, the problem that personal information of the user is leaked is avoided, and the privacy of the user is effectively protected.
Owner:ZEBRED NETWORK TECH CO LTD
Finger vein encryption communication terminal for confidential file
InactiveCN106372482AEncrypted file securityAvoid being leakedDigital data authenticationUser identifierLoudspeaker
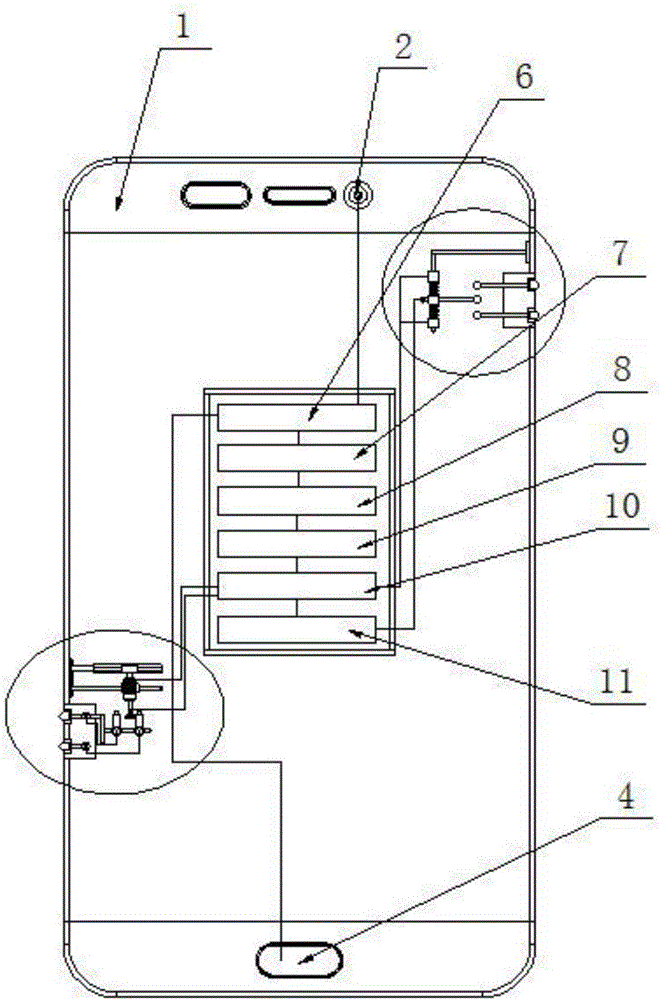
The invention discloses a finger vein encryption communication terminal for a confidential file, and relates to finger vein application equipment and facilities. The terminal comprises a terminal body, a human face identifier, a display, a vein identifier and a loudspeaker, wherein the display, the vein identifier and the human face identifier are arranged on the front surface of the terminal body; the loudspeaker is arranged at the bottom of the terminal body; a human face identification apparatus, a control apparatus and a vein identification apparatus are arranged in the terminal body; the control apparatus is connected with the human face identification apparatus through a lead wire; the control apparatus is connected with the vein identification apparatus through a lead wire; the control apparatus is connected with the human face identifier through a lead wire; the control apparatus is connected with the vein identifier through a lead wire; and the control apparatus is connected with the loudspeaker through a lead wire. Double encryption is performed through the human face identification apparatus and the vein identification apparatus, so that an encrypted file of a user is securer and the contents of the encrypted file can be effectively prevented from being leaked.
Owner:同略科技有限公司
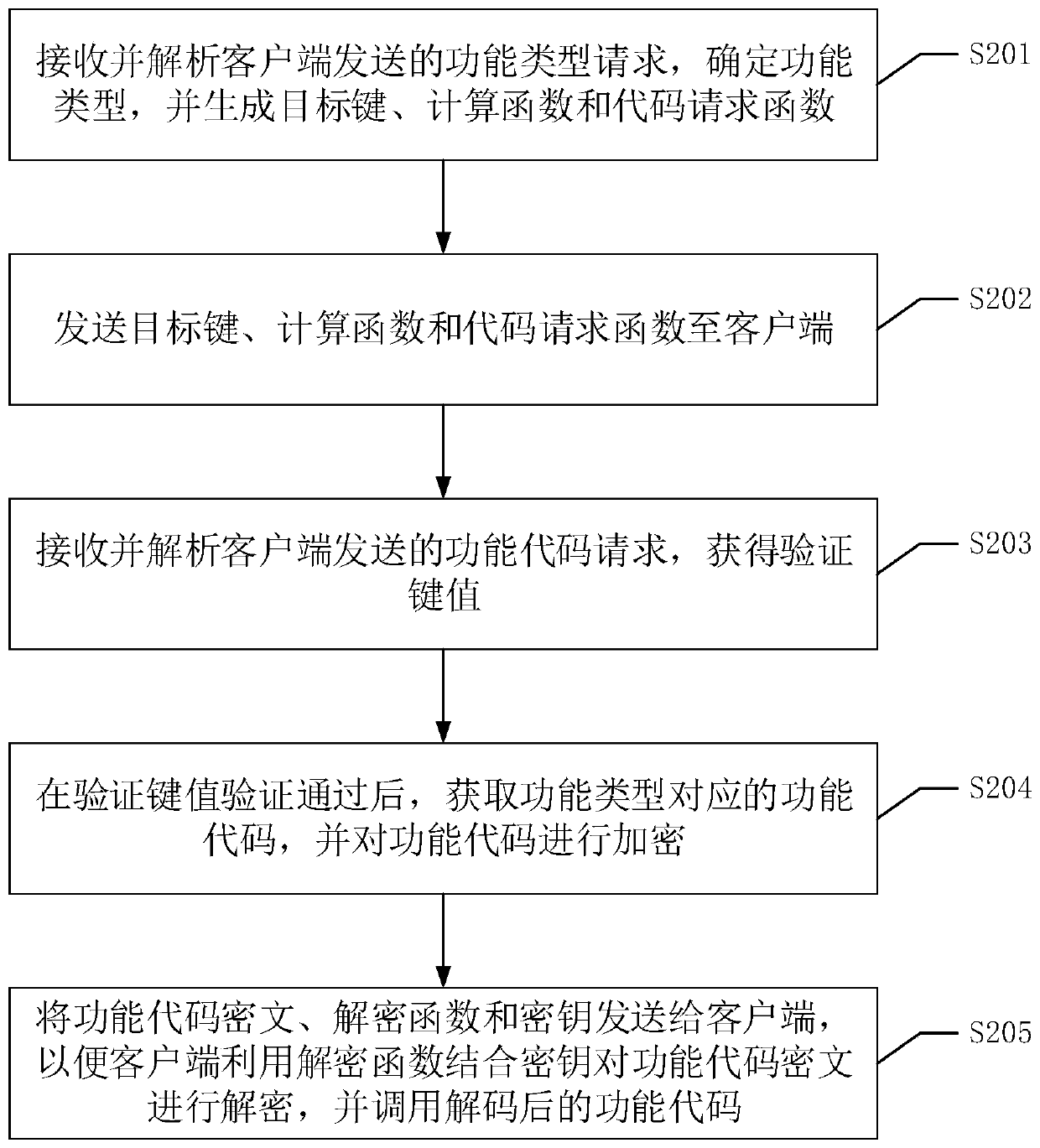
Code protection method, device and system and readable storage medium
ActiveCN110851800AAchieve protectionProtection of rights and interestsProgram/content distribution protectionProgramming languageCiphertext
The invention discloses a code protection method, device and system and a readable storage medium. According to the code protection method applied to the client side and the code protection method applied to the server side, even if an illegal person performs breakpoint debugging on the client side, only the target key, the calculation function and the code request function can be obtained, and the function code needing to be protected cannot be obtained. And after the client executes the calculation function and the code request function, a function code request is sent to the server, and a function code ciphertext, a key and a decryption function sent by the server are received after the verification of the verification key value is passed. Therefore, the client can automatically load the function code ciphertext and decrypt the function code ciphertext in combination with the secret key and the decryption function, and then the function code can be executed. Namely, according to themethod provided by the invention, the function code can be protected under the condition that the normal function business service provided for the client is not influenced, and leakage is avoided.
Owner:SUZHOU KEDA TECH
Encryption method and device based on shared root key, equipment and medium
PendingCN112165383AReduce complexityImprove efficiencyKey distribution for secure communicationCiphertextSmart city
The embodiment of the invention discloses an encryption method and device based on a shared root key, equipment and a medium, and relates to a block chain technology. The method comprises the steps: obtaining a target function used for describing information and a root key corresponding to target information to be processed, wherein the target information comprises at least two pieces of sub-information; generating a key of each piece of sub-information in the at least two pieces of sub-information according to the root key; obtaining coordinate information corresponding to each piece of sub-information in the at least two pieces of sub-information according to the target function; encrypting the coordinate information corresponding to each piece of sub-information in the at least two pieces of sub-information by adopting the key of each piece of sub-information to obtain a ciphertext of the coordinate information corresponding to each piece of sub-information; and determining the ciphertext of the coordinate information corresponding to each piece of sub-information as the ciphertext of the target information, and storing the ciphertext of the target information in a block chain network. By adopting the method, the security of information can be improved, the method is suitable for the field of smart medical treatment, and the construction of smart cities can be further promoted.
Owner:PING AN TECH (SHENZHEN) CO LTD
Palmprint and face recognition method based on cellular neural network hetero-associative memory model
ActiveCN111652166AImprove protectionHigh verification reliabilityNeural architecturesMatching and classificationPattern recognitionPalm print
The invention relates to a palmprint and face recognition method based on a cellular neural network hetero-associative memory model, and belongs to the technical field of intelligent recognition. Themethod comprises registration and identification. According to the method, the hetero-associative memory and the cellular neural network model are combined; palm print picture data and face picture data are converted into a series of parameters to be stored, identity information, namely the palm print picture data and the face picture data, is high in verification reliability, the picture storagemode is high in confidentiality and safety coefficient, and the identity information of people is effectively prevented from being leaked. The mode of converting the picture into the parameter throughthe model is adopted, and the method is simple, convenient, good in practicability, good in picture recognition effect and good in face picture data protection effect.
Owner:CHONGQING UNIVERSITY OF SCIENCE AND TECHNOLOGY
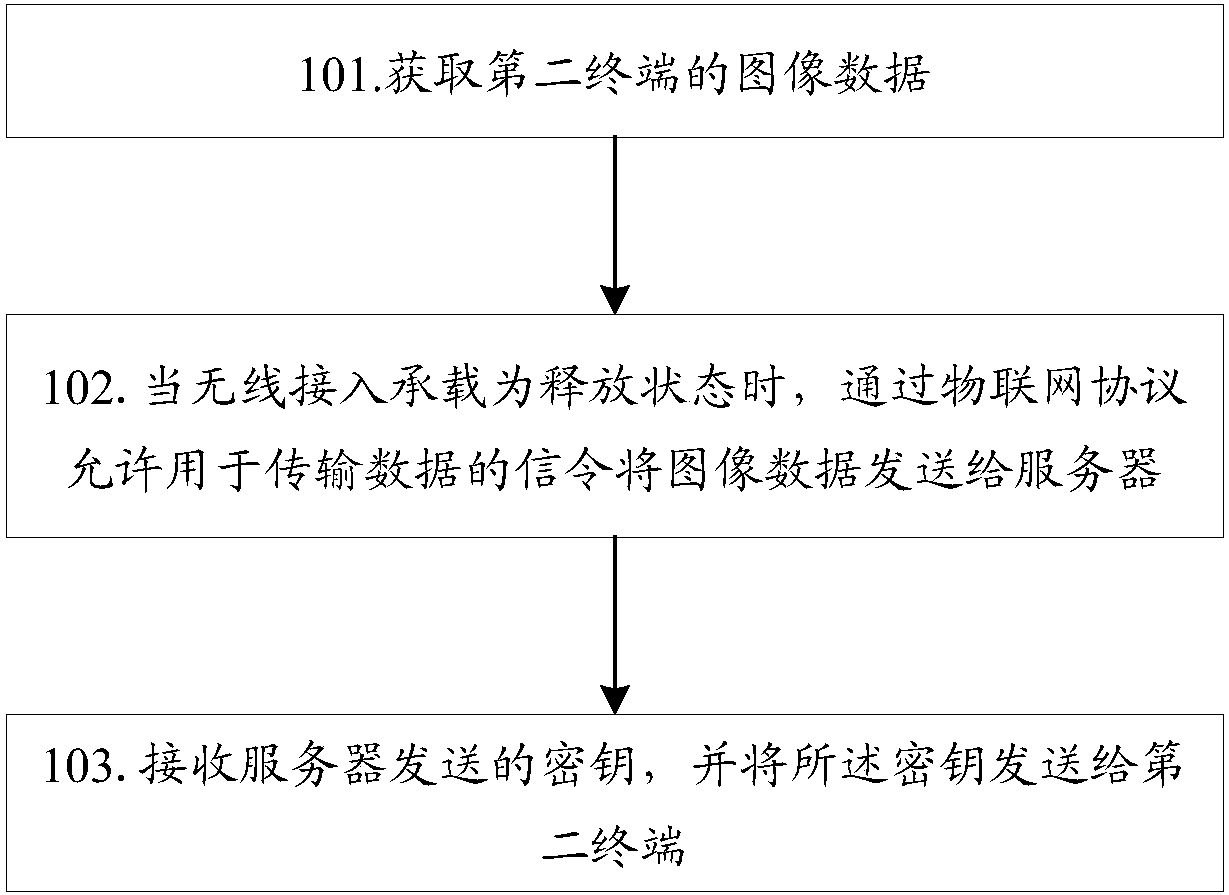
Authentication method, terminal and server
ActiveCN108809898AFast authenticationAvoid being leakedSecurity arrangementSecuring communicationData transmissionRadio access
The invention discloses an authentication method, comprising the following steps: acquiring image data of a second terminal; when a radio access bearer is in a release state, by virtue of an Internetof Things protocol, allowing a signaling used for data transmission to send the image data to a server, wherein the image data is used for requesting the server to send a secret key corresponding to afirst terminal; and receiving the secret key sent by the server, and sending the secret key to the second terminal, wherein the secret key is used for authenticating the first terminal by the secondterminal. The invention also discloses a terminal and a server.
Owner:ZTE CORP
Method and device for distributing document permission
ActiveCN108229137AAvoid being leakedReduce riskDigital data protectionNatural language data processingDocument preparationMinimum distance
The invention relates to a method and device for distributing a document permission. The method includes the steps of obtaining a document with a to-be-distributed permission; calculating a document value of the document with the to-be-distributed permission; according to the document value of the document with the to-be-distributed permission and document values of documents with existing permissions, calculating a distance value between the document with the to-be-distributed permission and each document with the existing permission; in the distance values obtained through calculation, determining a minimum distance value; when the minimum distance value is smaller than a preset threshold, distributing the permission of the document with the existing permission corresponding to the minimum distance value to the document with the to-be-distributed permission. The device includes an obtaining module, a first calculation module, a second calculation module, a determination module and adistribution module. The method and the device can automatically distribute the document permission to the new document, and avoid the new document from the risk of being disclosed or illegally accessed due to permission lack.
Owner:北京长御科技有限公司
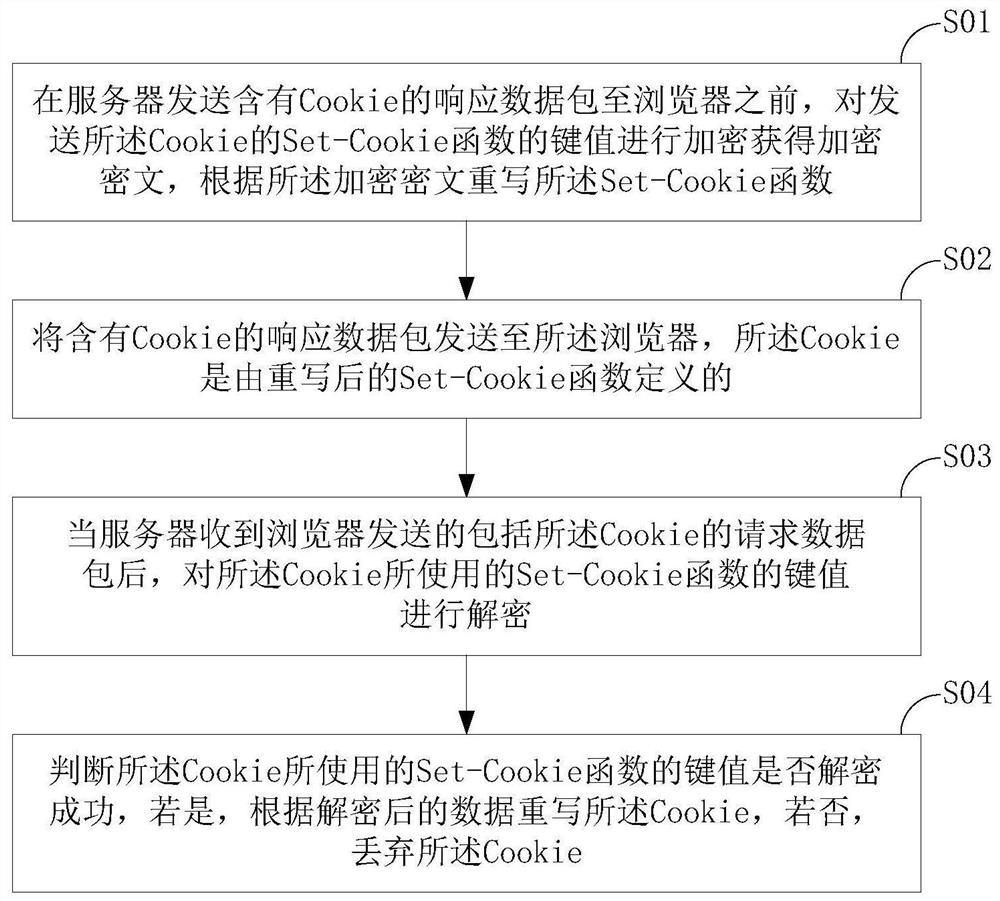
Cookie security protection method and server based on encryption technology
ActiveCN109347879BAvoid being leakedImprove securityEncryption apparatus with shift registers/memoriesData packWeb site
The present invention relates to the field of information security. The present invention aims to solve the problem that cookies in the existing network transmission are easily obtained by website attackers, and the security of servers is not high due to injection attacks initiated through cookies. The protection method and server, the method mainly includes the following steps: by encrypting and rewriting the key value of the Set-Cookie function, and then sending the Cookie defined by the rewritten Set-Cookie function to the browser, when the server receives the After the request packet of the Cookie, the key value of the Set-Cookie function used by the Cookie is successfully decrypted and then the information in the Cookie is read to prevent website attackers from stealing the Cookie, avoid user information leakage, prevent injection attacks, and improve User information and server security, applicable to Web servers.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
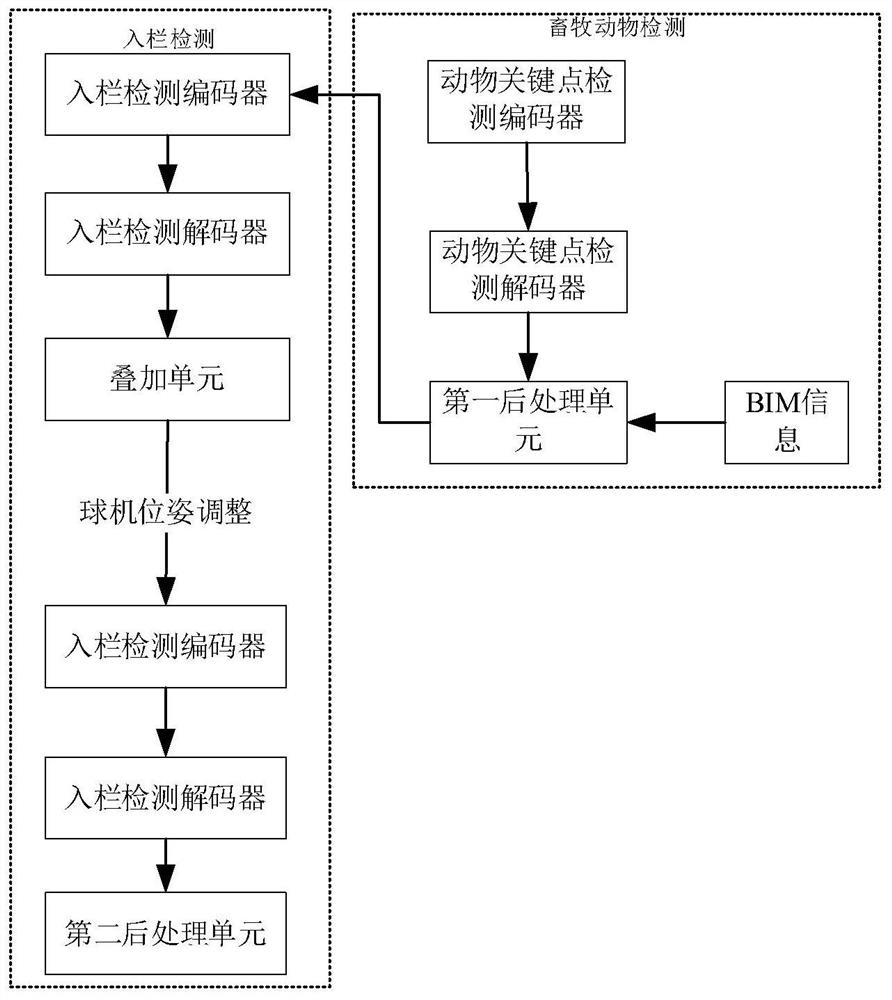
Livestock animal fence entry detection method based on gun-ball linkage and BIM
InactiveCN111612645AImprove efficiencyGood generalization performanceData processing applicationsCharacter and pattern recognitionAnimal scienceData processing
The invention discloses a livestock animal fence entry detection method based on gun-ball linkage and BIM. The method comprises the following steps: carrying out animal detection on an animal image ofa large-range free-ranging area acquired by a gunlock; carrying out coordinate regression to obtain animal key point coordinates; when the distance between the animal and the fence is smaller than aset threshold value, calling the gunlock; enabling the gunlock to collect a fence entrance image and process the fence entrance image to obtain a fence entrance animal thermodynamic diagram; superposing thermodynamic diagrams of animals at the entrance of the fence, and adjusting the pose of the dome camera after the track disappears; acquiring an animal image of an internal area of the fence, andprocessing to obtain an animal thermodynamic diagram in the fence; counting the number of peak points of animal thermodynamic diagram hot spots in the fence; and combining the WebGIS technology to visualize the livestock breeding area building information model. By means of the animal husbandry in-fence detection system and method, automatic animal husbandry in-fence detection is achieved, the animal husbandry in-fence detection efficiency and precision are improved, and the safety in the data processing and transmission process is improved.
Owner:各珍珍
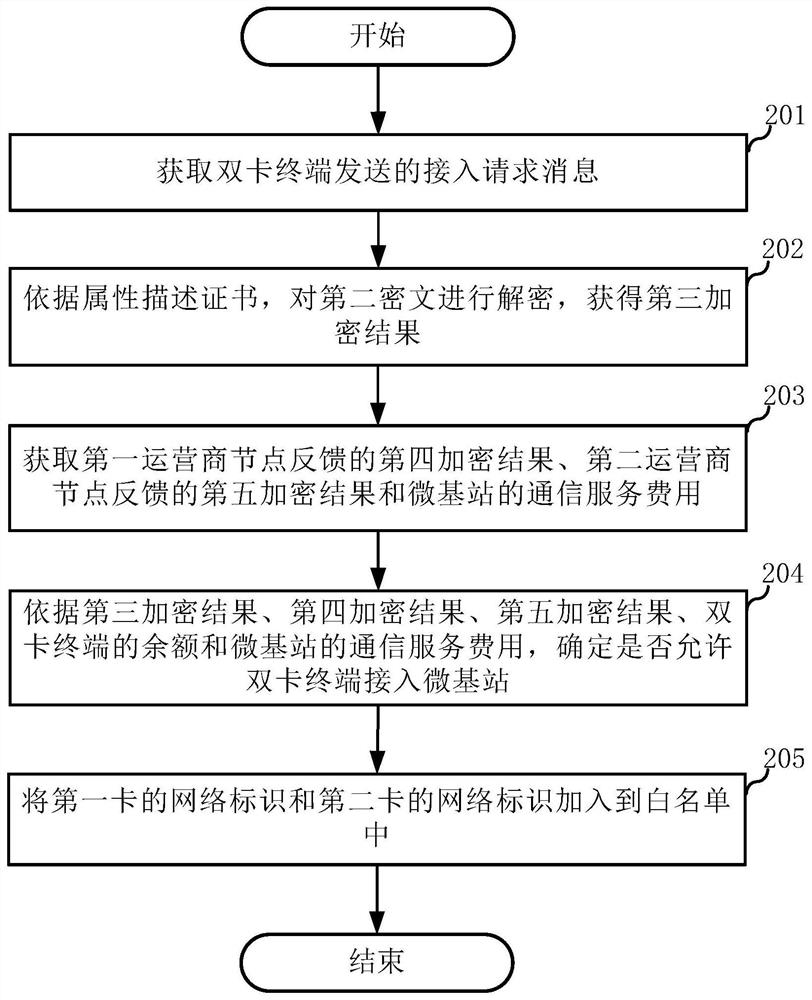
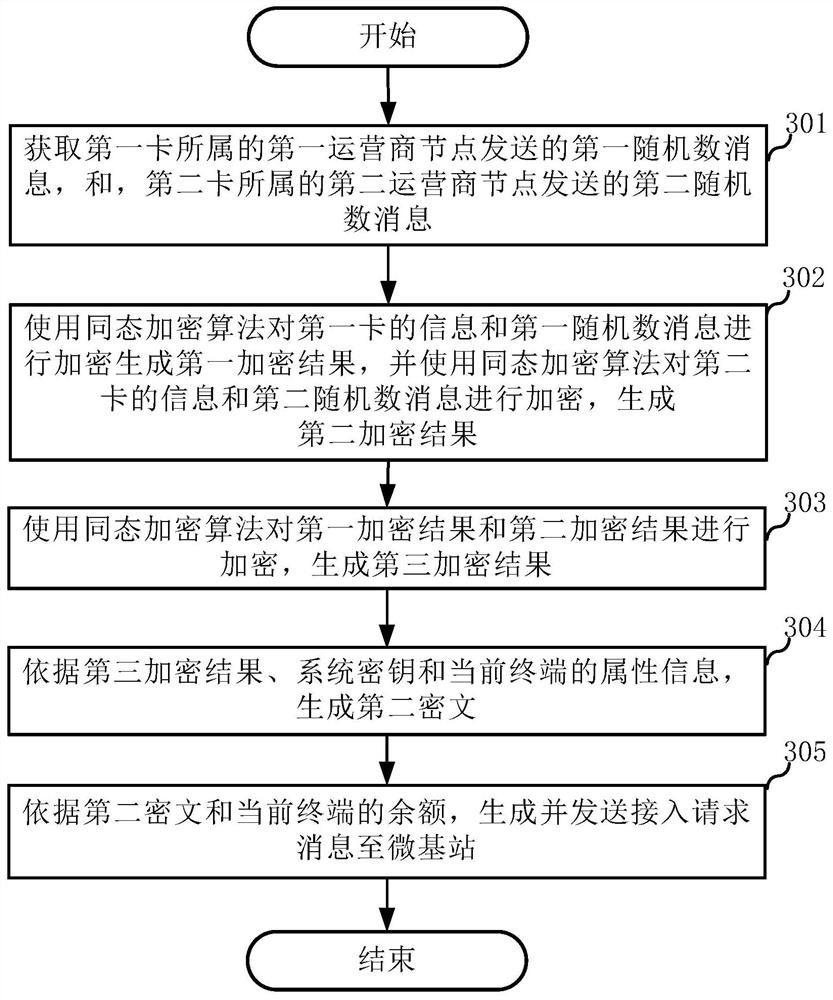
Access method of dual-card terminal, terminal and server
PendingCN112040473ASimplify the certification processSimplify the access processKey distribution for secure communicationAccounting/billing servicesAccess methodCiphertext
The invention discloses an access method of a dual-card terminal, a terminal and a server, and the method comprises the steps: obtaining an access request message sent by the dual-card terminal, wherein the access request message comprises a second ciphertext and the balance of the dual-card terminal; decrypting the second ciphertext according to an attribute description certificate to obtain a third encryption result; obtaining a fourth encryption result fed back by a first operator node, a fifth encryption result fed back by a second operator node and the communication service cost of a micro base station; and according to the third encryption result, the fourth encryption result, the fifth encryption result, the balance of the dual-card terminal and the communication service cost of themicro base station, determining whether the dual-card terminal is allowed to access the micro base station.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
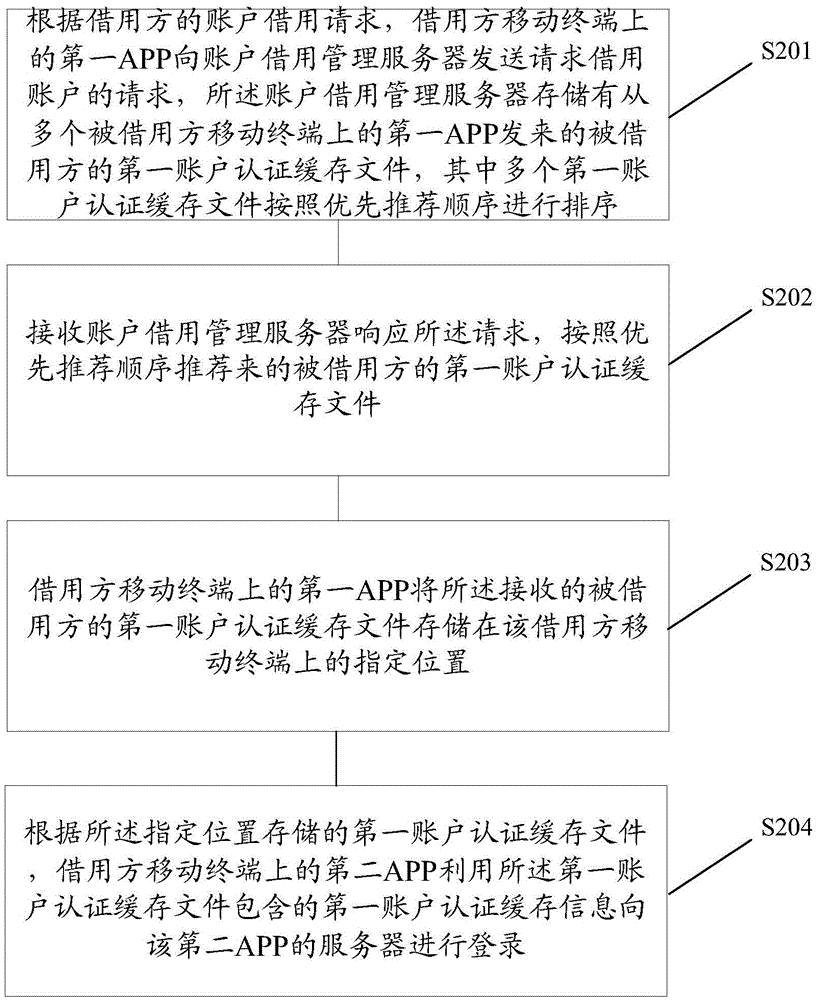
Method and system for logging in by borrowing accounts of other people
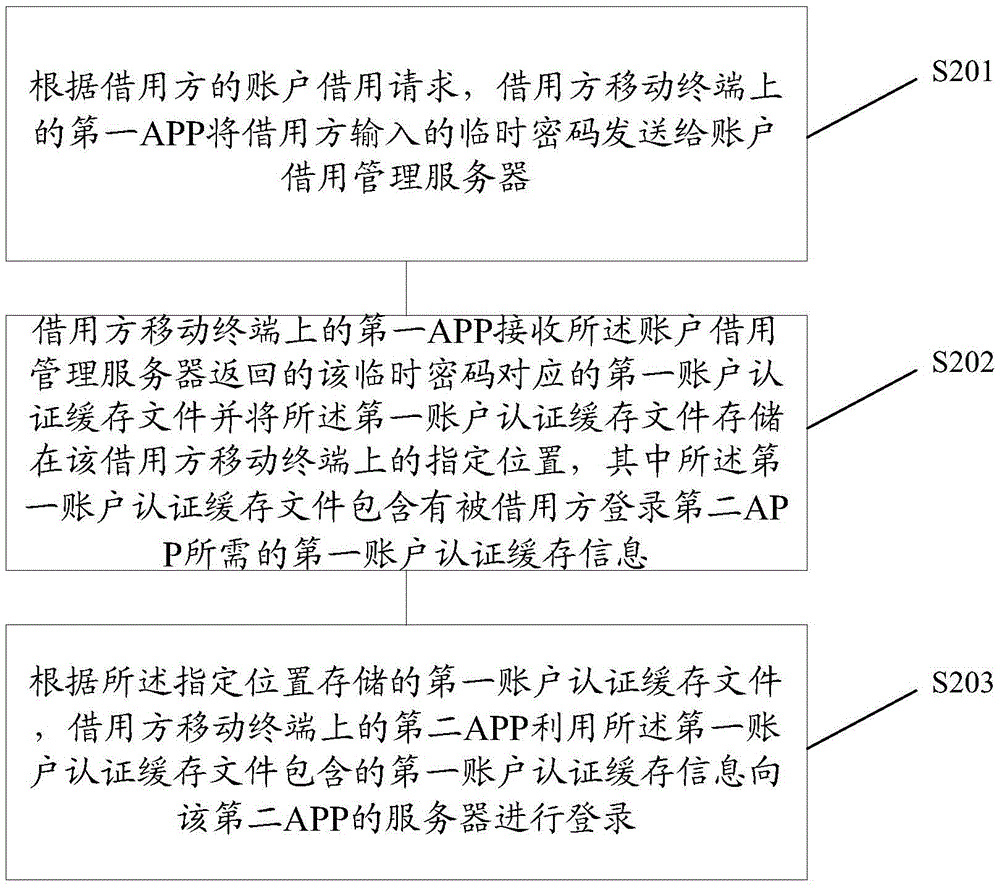
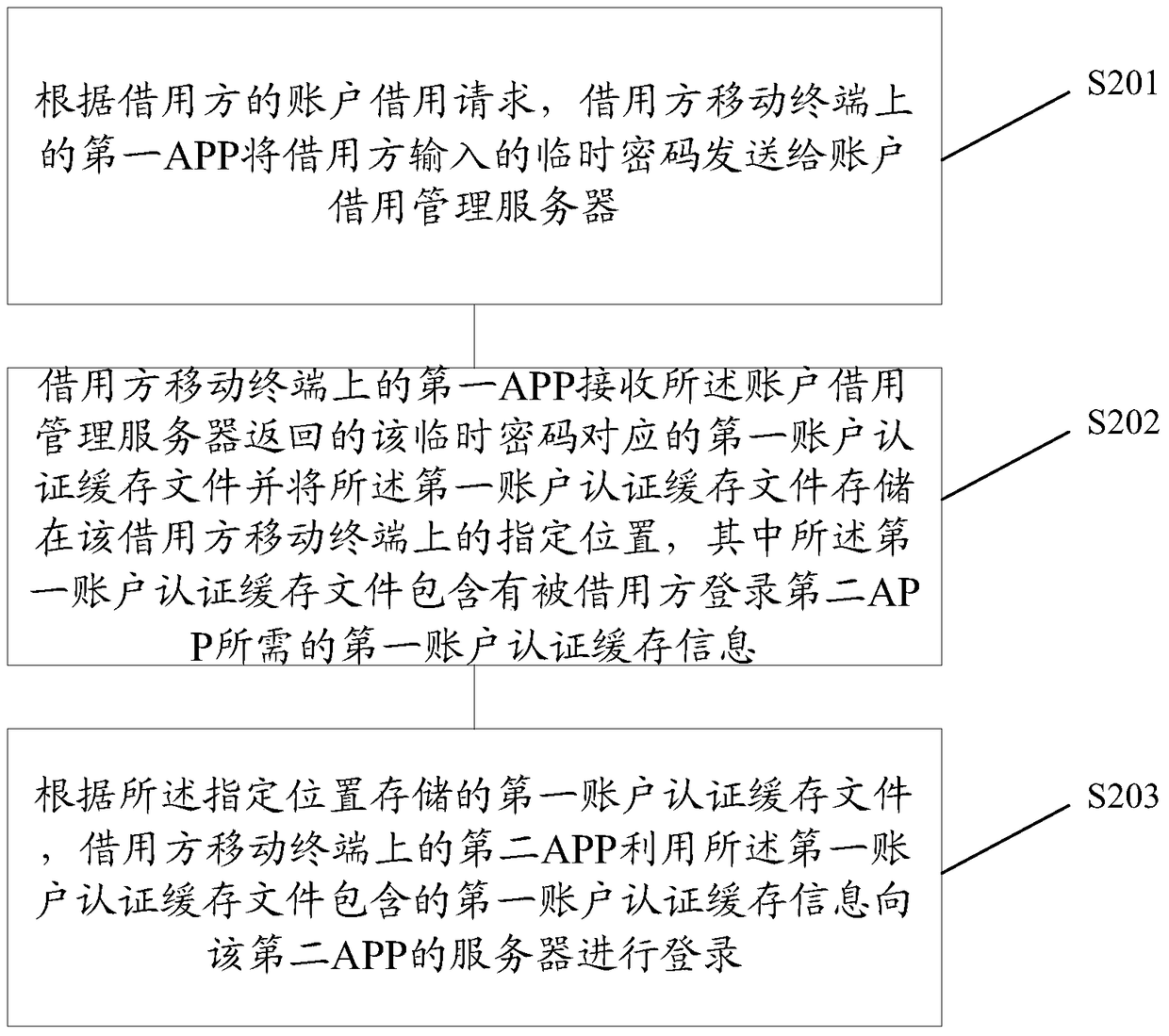
InactiveCN105610801AReduce the risk of privacy being leakedAvoid being leakedTransmissionPasswordAuthentication
The invention discloses a method and system for logging in by borrowing accounts of other people. The method comprises following steps of receiving the first account authentication cache file sent by the first APP on the mobile terminal of each borrowed party; carrying out prior recommendation sequence ranking to the first account authentication cache file of each borrowed party; preferentially obtaining the first account authentication cache files of the borrowed parties with higher ranks according to the account borrowing requests of borrowing parties; sending the obtained first account authentication cache files to the first APPs on the mobile terminals of the borrowing parties, wherein the borrowing parties store the first account authentication cache files in the appointed locations through the first APPs on the mobile terminals; the second APPs on the mobile terminals of the borrowing parties log in through the first account authentication cache information contained in the first account authentication cache files, thus realizing the login by other people through using the accounts of the borrowed parties without providing accounts and passwords by the borrowed parties.
Owner:BEIJING QIHOO TECH CO LTD +1
Differential privacy protection method for medical data release
ActiveCN105608389BAvoid being leakedGuaranteed to be availableDigital data protectionDifferential privacyPrivacy protection
The invention discloses a differential privacy protection method of medical data dissemination. A K-anonymous technology and a differential privacy technology are effectively combined to solve the problems that the statistical information of data can not guaranteed to be prevented from being leaked when the K-anonymous technology is solely used, a great quantity of noise is introduced while the differential privacy technology is solely used to only protect the statistical information, a data distortion degree becomes high to lower data utilizability; and therefore, on the premise that the medical data is guaranteed to be available, the risk of patient information leakage when the medical data is collected and disseminated can be effectively avoided so as to perform the efficacy of the medical data during statistics and mining.
Owner:GUANGXI NORMAL UNIV
An electronic information intelligent storage system for industrial management
ActiveCN110008704BEnsure safetyAvoid being leakedDigital data authenticationPlatform integrity maintainanceData OriginData retrieval
The invention discloses an electronic information intelligent storage system for industrial management. The electronic information intelligent storage system comprises a data receiving module, a datasource analysis module, a virus scanning module, a data processing module, a data classification module, a data storage module, a transfer storage module, a cloud storage module, a data retrieval module, an identity verification module and a login module. The data receiving module is in communication connection with the data source analysis module; the data source analysis module is in communication connection with the virus scanning module; wherein the external virus characteristic information acquisition module is in communication connection with the virus scanning module, the virus scanningmodule is in communication connection with the data processing module, the data processing module is in communication connection with the data classification module, and the data classification module is in communication connection with the data storage module; according to the invention, the security of the stored data can be better ensured, and meanwhile, the system can be more convenient to use and is more suitable for popularization and application.
Owner:深圳市熠华智能科技有限公司
Information processing method and device, electronic equipment and storage medium
PendingCN112926924AAvoid being leakedPrevent leakageDigital data protectionLogisticsInformation processingSoftware engineering
The invention relates to a block chain, and discloses an information processing method and device, electronic equipment and a storage medium, and the method comprises the steps: obtaining a first waybill and a second waybill; if a difference value between a first moment included in the first waybill and a second moment included in the second waybill is smaller than or equal to a preset time difference, comparing cargo information in the first waybill with corresponding information in the second waybill, the preset time difference being a ratio of a preset distance to a preset speed, wherein the first moment is the moment when the first node obtains the cargo, and the second moment is the moment when the second node obtains the cargo; and if the comparison is successful, displaying information that the comparison between the first waybill and the second waybill is successful on a display interface. According to the embodiment of the invention, the waybill comparison efficiency is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method and system for realizing login through borrowing account of others
The invention discloses a method and a system for realizing login through borrowing an account of others. The method comprises the following steps that according to an account borrowing request of a borrowing party, a first APP on a borrowing party mobile terminal sends a temporary password input by the borrowing party to an account borrowing management server; the first APP on the borrowing party mobile terminal receives a first account authentication cache file corresponding to the temporary password from the account borrowing management server and stores the first account authentication cache file at a specified position on the borrowing party mobile terminal, wherein the first account authentication cache file contains first account authentication cache information needed for a loaning party to login to a second APP; according to the first account authentication cache file stored at the specified position, the second APP on the borrowing party mobile terminal logins to a server of the second APP by making use of the first account authentication cache information contained in the first account authenticationcache file, namely, the loaning party can enable others to login at a specified application website through the account of the loaning party without providing the account and the password on the specified application website.
Owner:BEIJING QIHOO TECH CO LTD
A method and system for logging in by borrowing someone else's account
ActiveCN105610798BFacilitate active lendingActive lending is convenientTransmissionPasswordComputer science
The invention discloses a method and system for logging in by borrowing another person's account. According to the account borrowing request of the borrower, the first APP on the mobile terminal of the borrower sends the temporary password input by the borrower to the account borrowing management server; the borrower moves The first APP on the terminal receives the first account authentication cache file corresponding to the temporary password returned by the account borrowing management server and stores the first account authentication cache file in a specified location on the borrower's mobile terminal, wherein the The first account authentication cache file contains the first account authentication cache information required by the borrowed party to log in to the second APP; according to the first account authentication cache file stored in the specified location, the second APP on the borrower's mobile terminal uses The first account authentication cache information contained in the first account authentication cache file logs in to the server of the second APP, that is, it is not necessary for the borrowed party to provide the account and password on the designated application website to allow others to pass through the borrowed party's account and password. The account is logged in on the designated application website.
Owner:BEIJING QIHOO TECH CO LTD
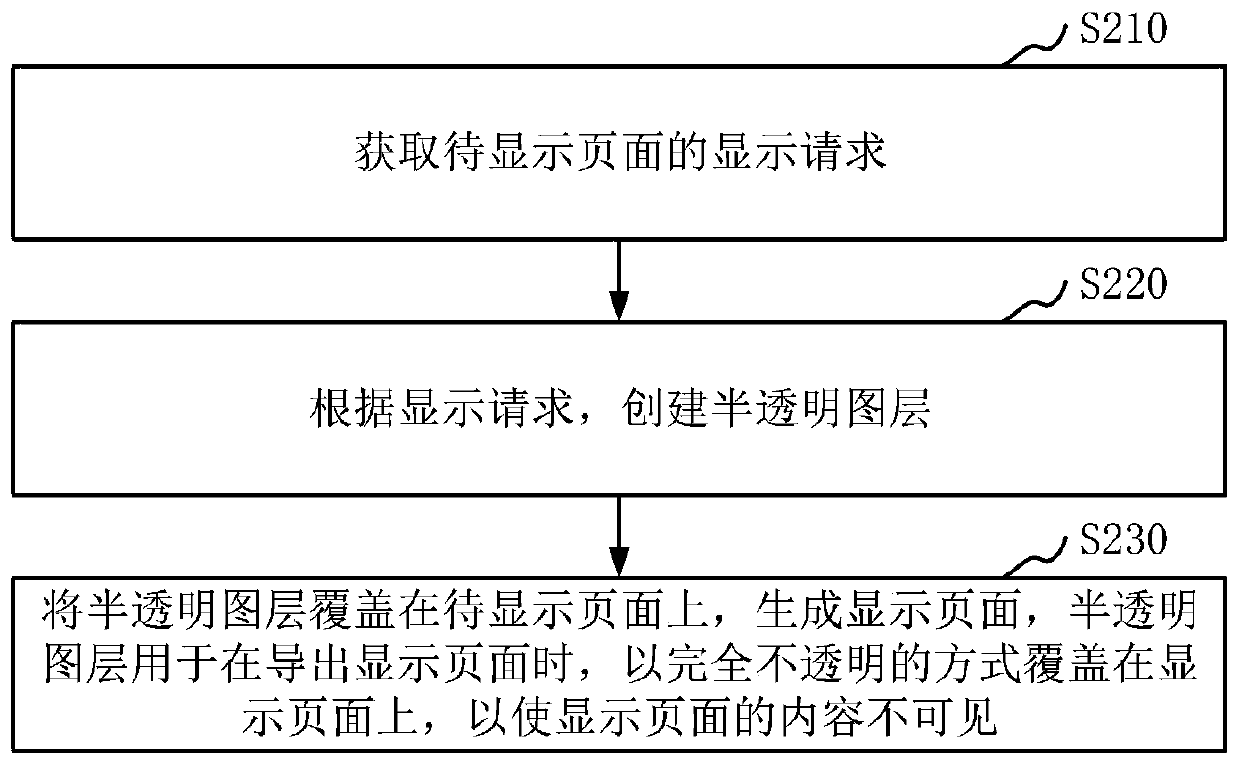
Page processing method and device, electronic equipment and storage medium
PendingCN111428282AInvalid transparency propertyAvoid being leakedInternal/peripheral component protectionExecution for user interfacesComputer hardwareEngineering
The invention relates to a page processing method and device, electronic equipment and a storage medium. The method comprises the steps of obtaining a display request of a to-be-displayed page; creating a semitransparent layer according to the display request; and covering the to-be-displayed page with the semitransparent layer to generate a display page, wherein the semitransparent layer is usedfor covering the display page in a completely opaque manner when the display page is exported, so that the content of the display page is invisible. According to the method, the to-be-displayed page is covered with the semitransparent layer, when the browser exports the display page, the transparency attribute of the display page cannot be recognized, and therefore the transparency attribute is invalid. Wherein the invalid transparency is opaque, and the exported or printed semitransparent layer on the display page covers the display page in a completely opaque manner, so that the content on the page is prevented from being leaked and invisible.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
Encrypted information display method and terminal
ActiveCN104732125BAvoid viewingAvoid being leakedDigital data authenticationComputer hardwareUser input
Owner:NUBIA TECHNOLOGY CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com