Authentication method, terminal and server
A server and terminal technology, applied in the field of the Internet of Things, can solve the problems of long waiting time, low efficiency, peeping, etc., and achieve the effect of fast authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
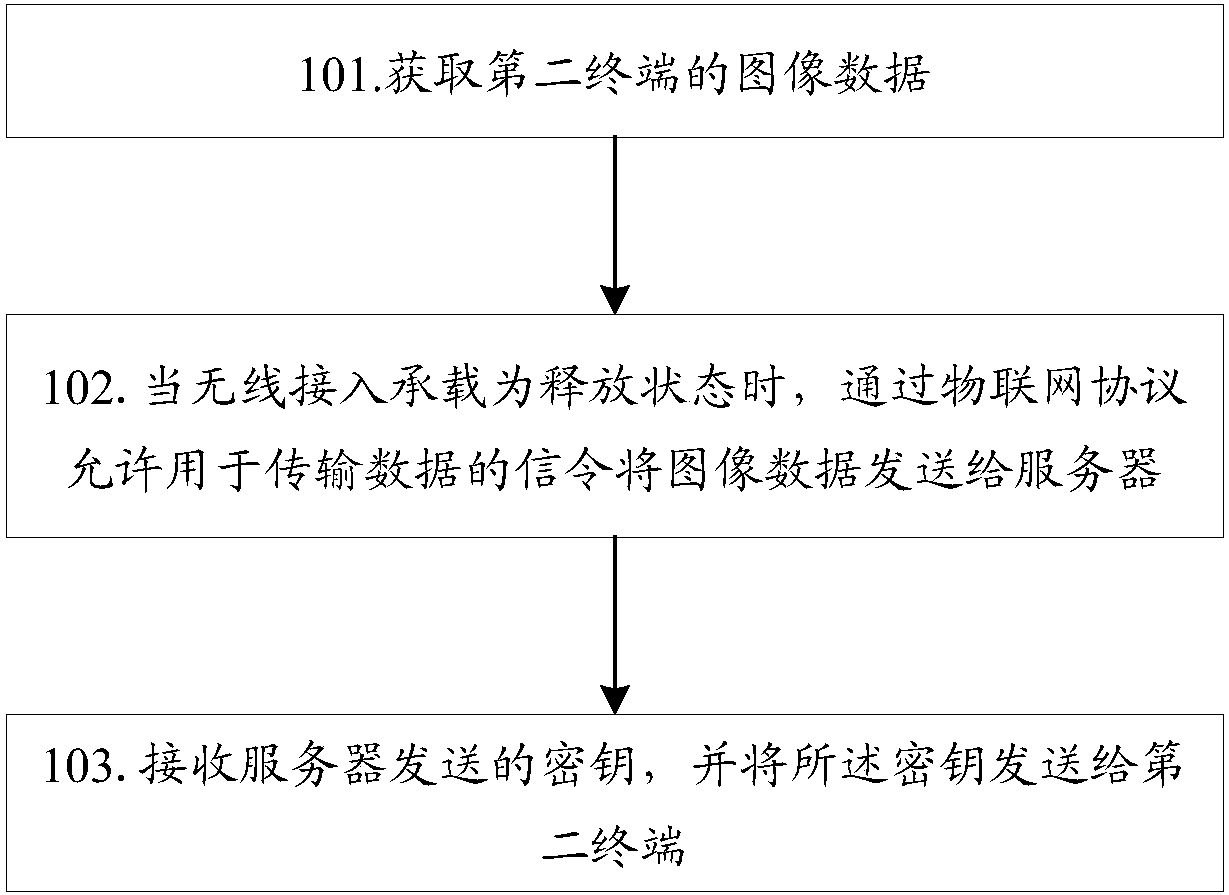
[0068] Such as figure 1 As shown, this embodiment takes the first terminal side as an example to describe the authentication method in detail, including the following steps:
[0069] Step 101: Obtain image data of the second terminal.
[0070] Here, the acquiring image data of the second terminal includes:
[0071] Search for at least one terminal;
[0072] Determine the second terminal from the at least one terminal;
[0073] The image of the second terminal is collected to obtain the image data.
[0074] Here, in actual application, the first terminal can search for at least one terminal through Bluetooth, and can also use other local area network protocols, such as wireless fidelity (WiFi, Wireless Fidelity), ZigBee, etc., to search for at least one terminal; where the terminal is specific It can be ATM machines, access security gates, smart buses or credit card machines on the subway, etc.
[0075] Before searching, you can identify at least one terminal, for example, ATM machines us...
Embodiment 2
[0123] Such as Figure 5 As shown, this embodiment takes the server side as an example to describe the authentication method in detail, including the following steps:
[0124] Step 501: Receive the image data of the second terminal that is sent by the first terminal through the signaling of the Internet of Things protocol that allows for data transmission.
[0125] Here, the receiving the image data of the second terminal that the first terminal allows the signaling to be used to transmit data through the Internet of Things protocol includes:
[0126] Through the signaling radio bearer between the terminal and the core network, the non-access stratum signaling message sent by the first terminal on the signaling radio bearer through the non-access stratum of the signaling plane is received; Let the message contain the image data of the second terminal.
[0127] In actual application, through the signaling radio bearer between the terminal and the core network, the core network side cor...
Embodiment 3
[0141] In order to implement the method in the first embodiment, this embodiment provides a first terminal, such as Image 6 As shown, the first terminal includes: an acquiring module 61, a first sending module 62, and a first receiving module 63; wherein,
[0142] The obtaining module 61 is configured to obtain image data of the second terminal;
[0143] The first sending module 62 is configured to send the image data to the server through the signaling for data transmission through the Internet of Things protocol when the wireless access bearer is in the released state; and send the key to the second terminal;
[0144] Wherein, the image data is used to request the server to send a key corresponding to the first terminal; the key is used for the second terminal to authenticate the first terminal;
[0145] The first receiving module 63 is configured to receive the key sent by the server.
[0146] The acquisition module 61 is specifically configured to search for at least one terminal; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com