A method and system for certificating vehicle identity
A vehicle identity and vehicle technology, applied in user identity/authority verification, security devices, electrical components, etc., can solve problems such as not handling vehicle service request messages that fail authentication, key escrow, and private key information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
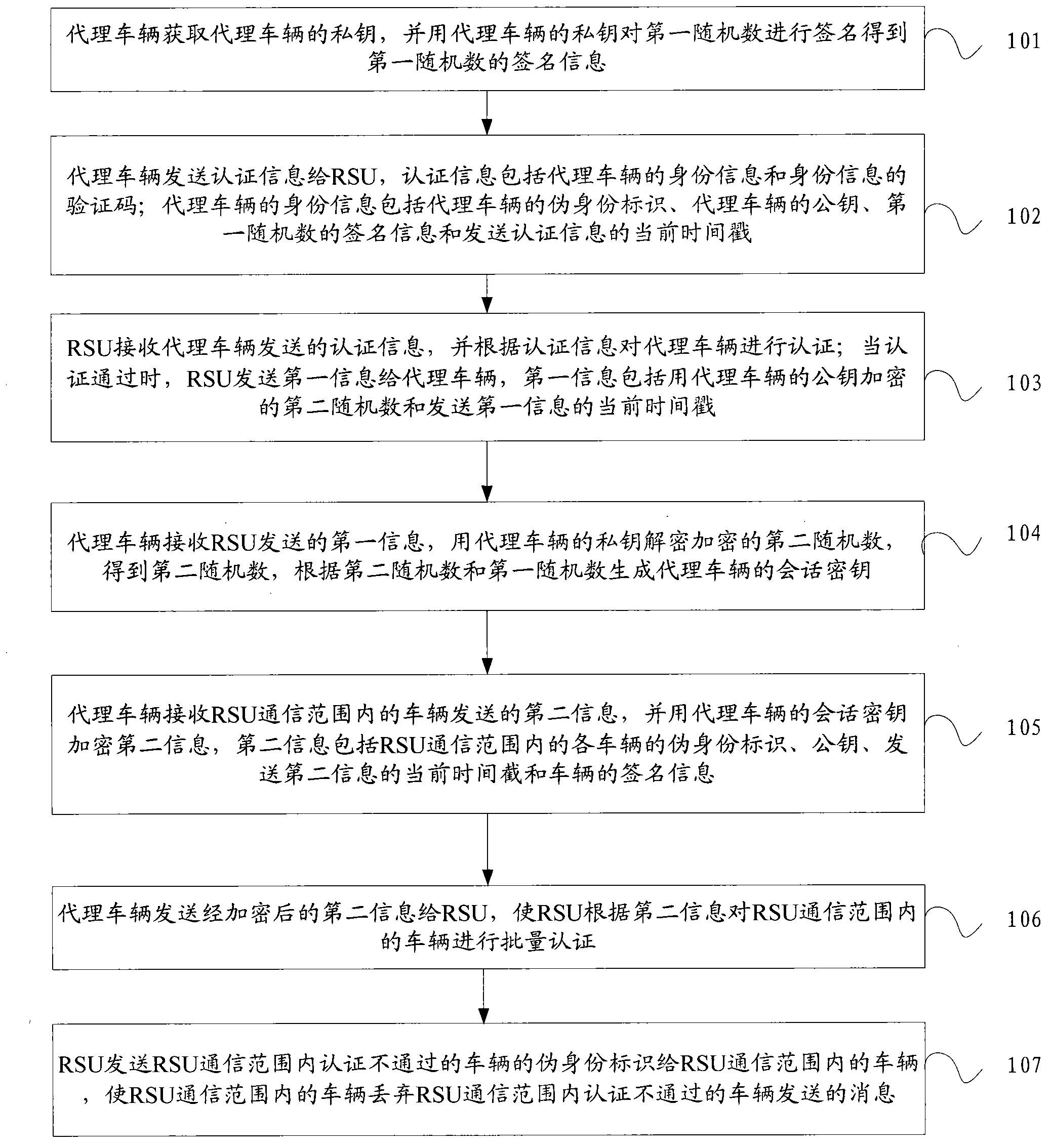
[0070] An embodiment of the present invention provides a method for authenticating a vehicle. see figure 1 , where the method includes:
[0071] 101: The proxy vehicle obtains the private key of the proxy vehicle, and uses the private key of the proxy vehicle to sign the first random number to obtain the signature information of the first random number;
[0072] 102: The agent vehicle sends authentication information to the RSU (Road Side Unit, roadside unit). The authentication information includes the identity information of the agent vehicle and the verification code of the identity information; the identity information of the agent vehicle includes the false identity mark of the agent vehicle, the The public key, the signature information of the first random number and the current timestamp of sending the authentication information;
[0073] 103: The RSU receives the authentication information sent by the agent vehicle, and authenticates the agent vehicle according to th...
Embodiment 2
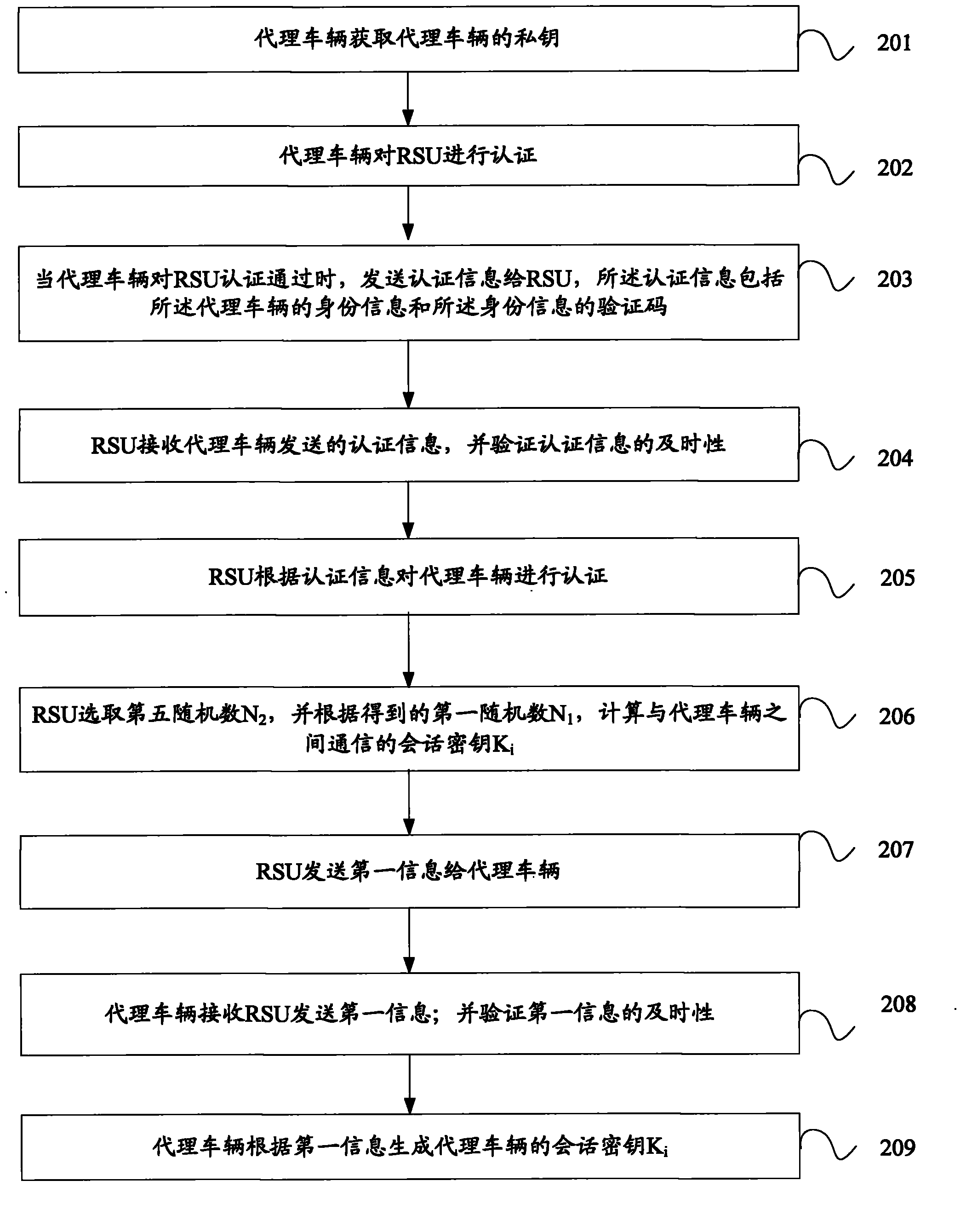
[0100] An embodiment of the present invention provides a method for authenticating a vehicle. see figure 2 , where the method includes:
[0101] 201: The proxy vehicle obtains the private key of the proxy vehicle;
[0102] The proxy vehicle is any vehicle within the communication range of the roadside unit RSU. When authenticating the identity of the vehicle, the RSU randomly selects any vehicle within the communication range of the RSU as the proxy vehicle, and performs identity authentication on the proxy vehicle. When the RSU passes the identity authentication of the proxy vehicle, the proxy vehicle builds a group.
[0103] Among them, the private key sk of the proxy vehicle i Including the first private key and the second private key, the first private key is sk i 1 , the second private key is sk i 2 , the first private key and the second private key of the proxy vehicle form the private key of the proxy vehicle, namely sk i =(sk i 1 ,sk i 2 ).
[0104] Where...
Embodiment 3
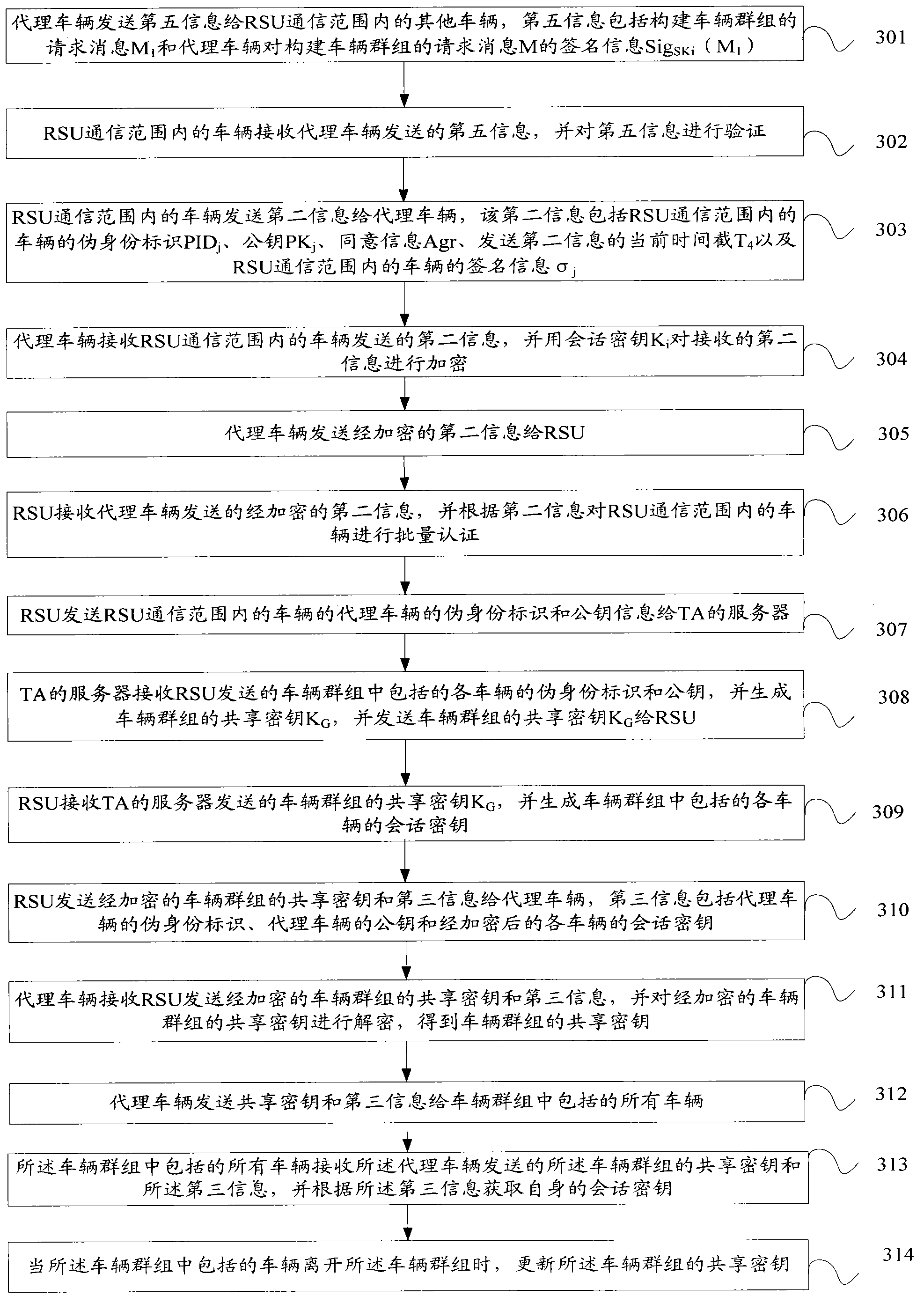
[0140] An embodiment of the present invention provides a method for authenticating a vehicle. see image 3 , where the method includes:
[0141] 301: The proxy vehicle sends fifth information to other vehicles within the communication range of the RSU, the fifth information includes a request message M for building a vehicle group 1 and the request message M of the agent vehicle to construct the vehicle group 1 The signature information Sig SKi (M 1 );
[0142] Among them, the request message M for constructing a group 1 Including the pseudo-identification PID of the agent vehicle i , the public key PK of the proxy vehicle i , the construction request identifier CGR and the current timestamp T of sending the fifth information 3 . Proxy vehicle according to the private key SK of proxy vehicle i Request message M for building a vehicle group 1 Sign and get the signature information Sig SKi (M 1 ).
[0143] 302: Vehicles within the communication range of the RSU rec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com