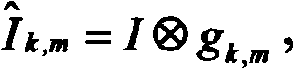Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
171results about How to "Simplify the certification process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
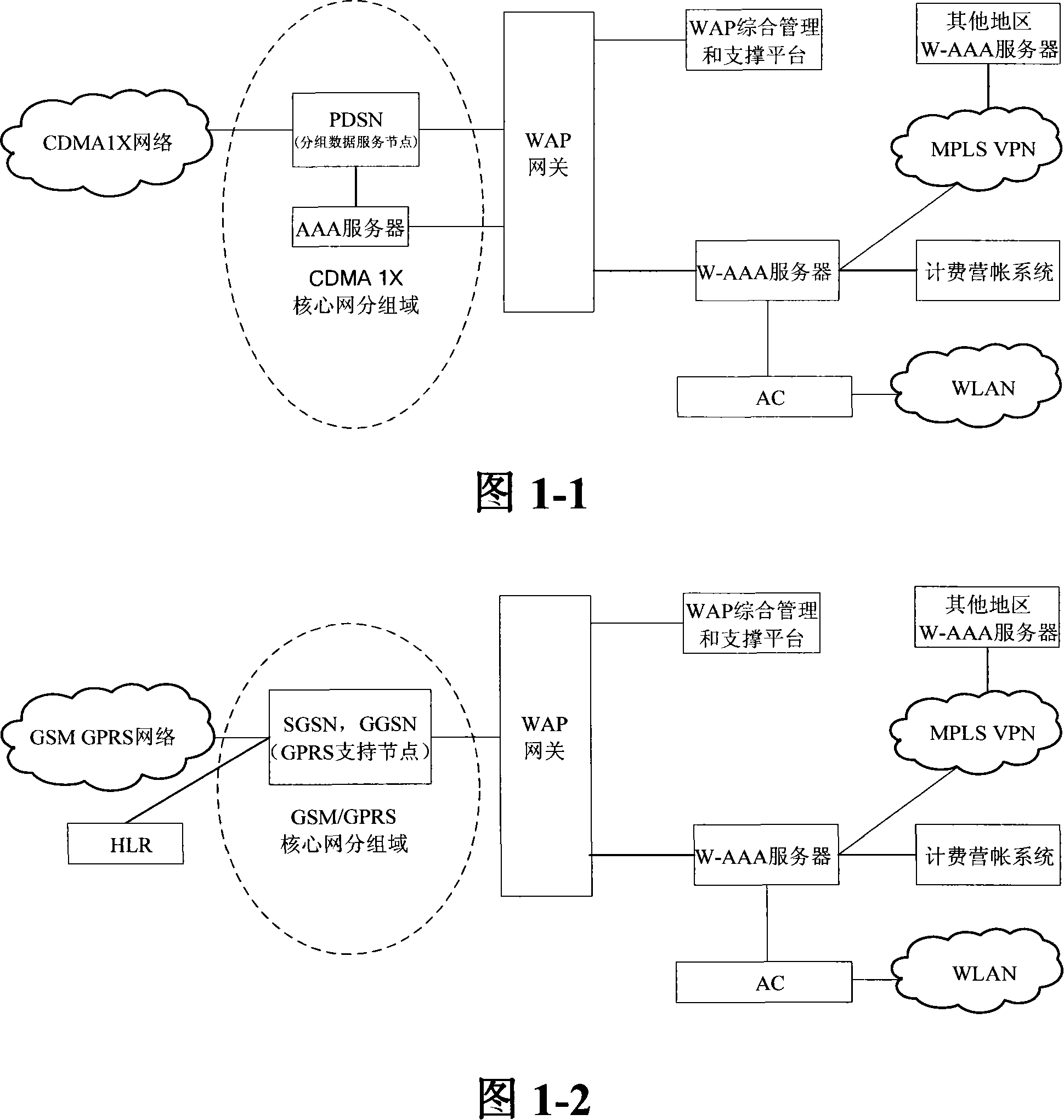
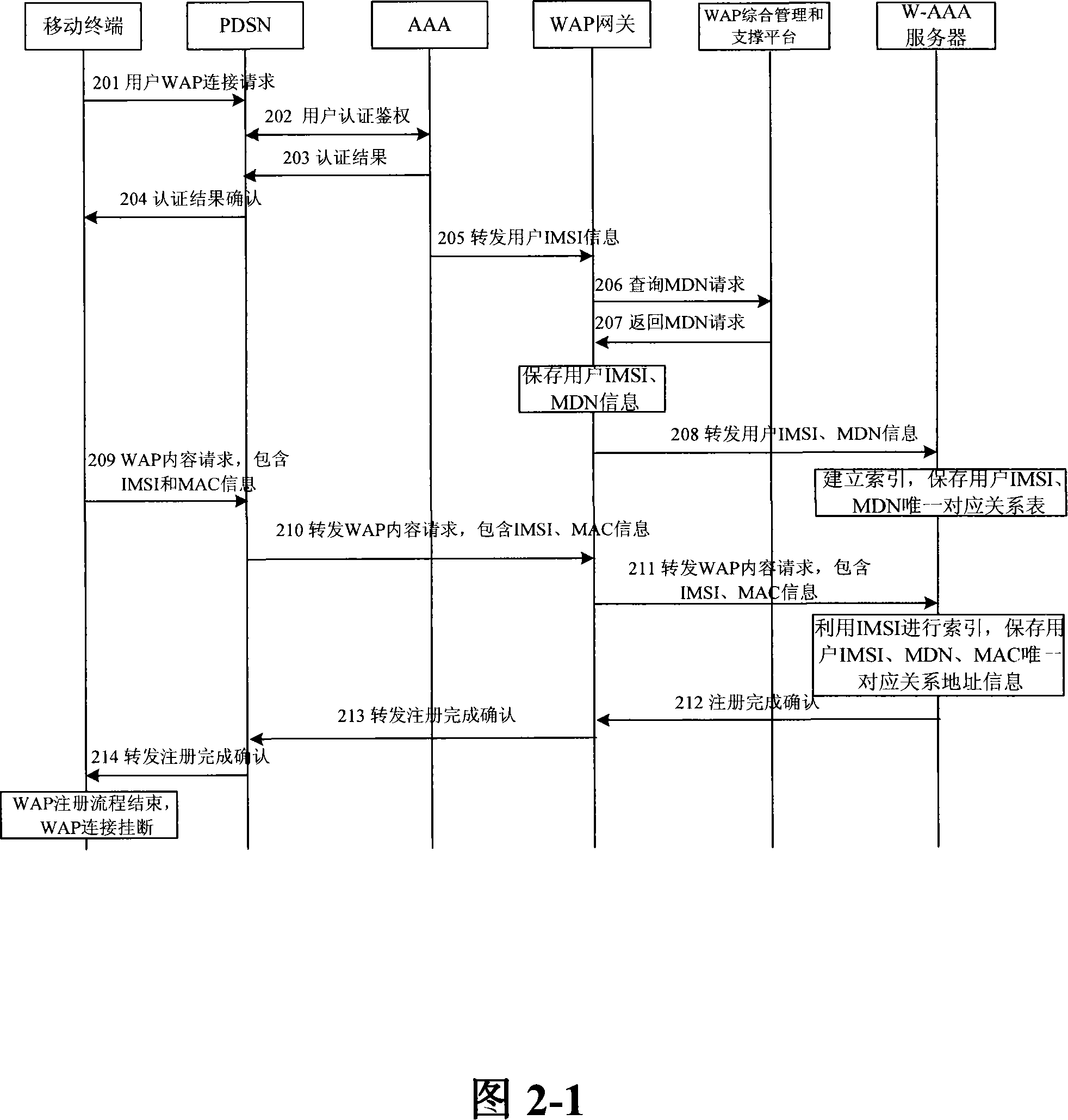
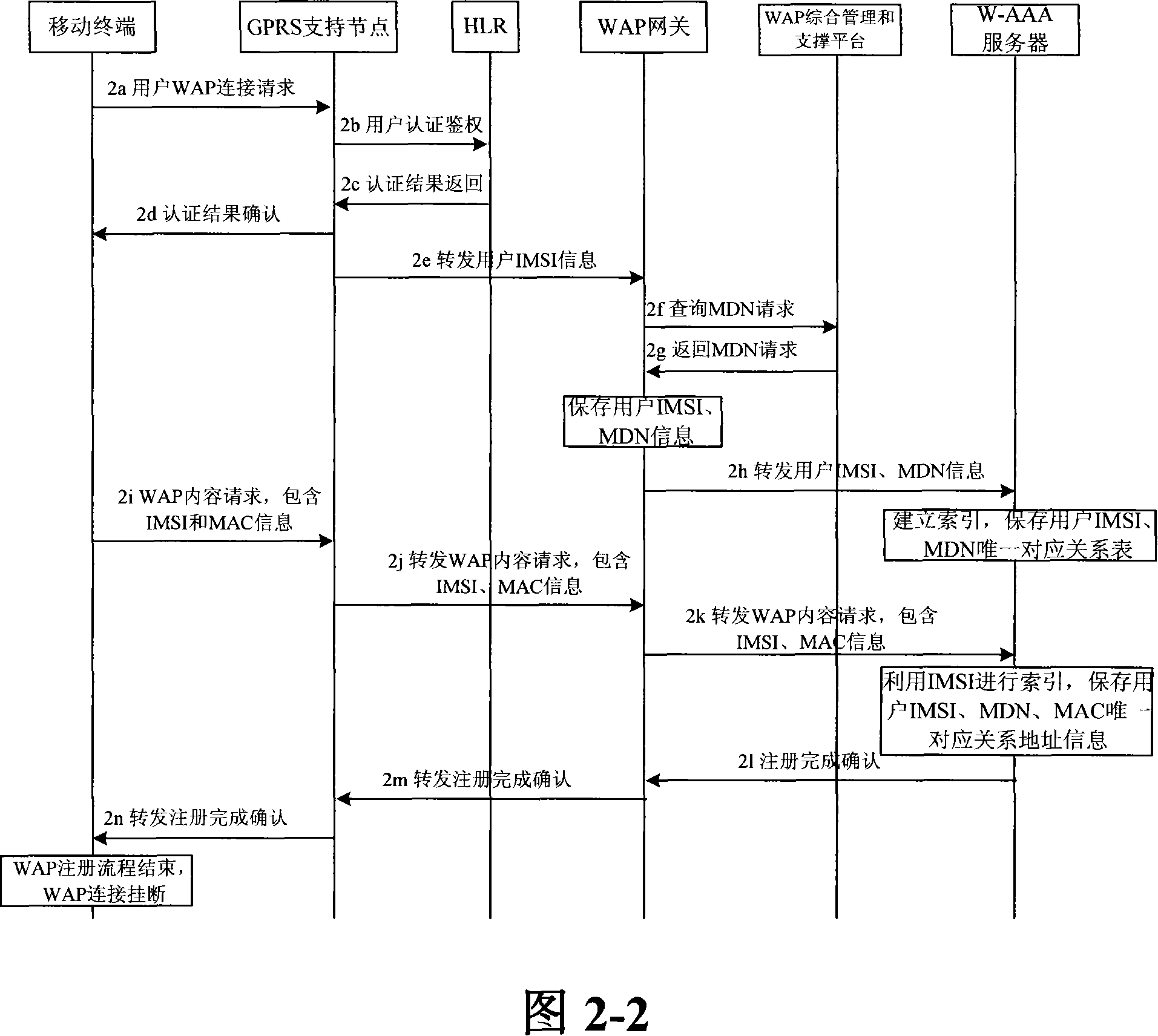
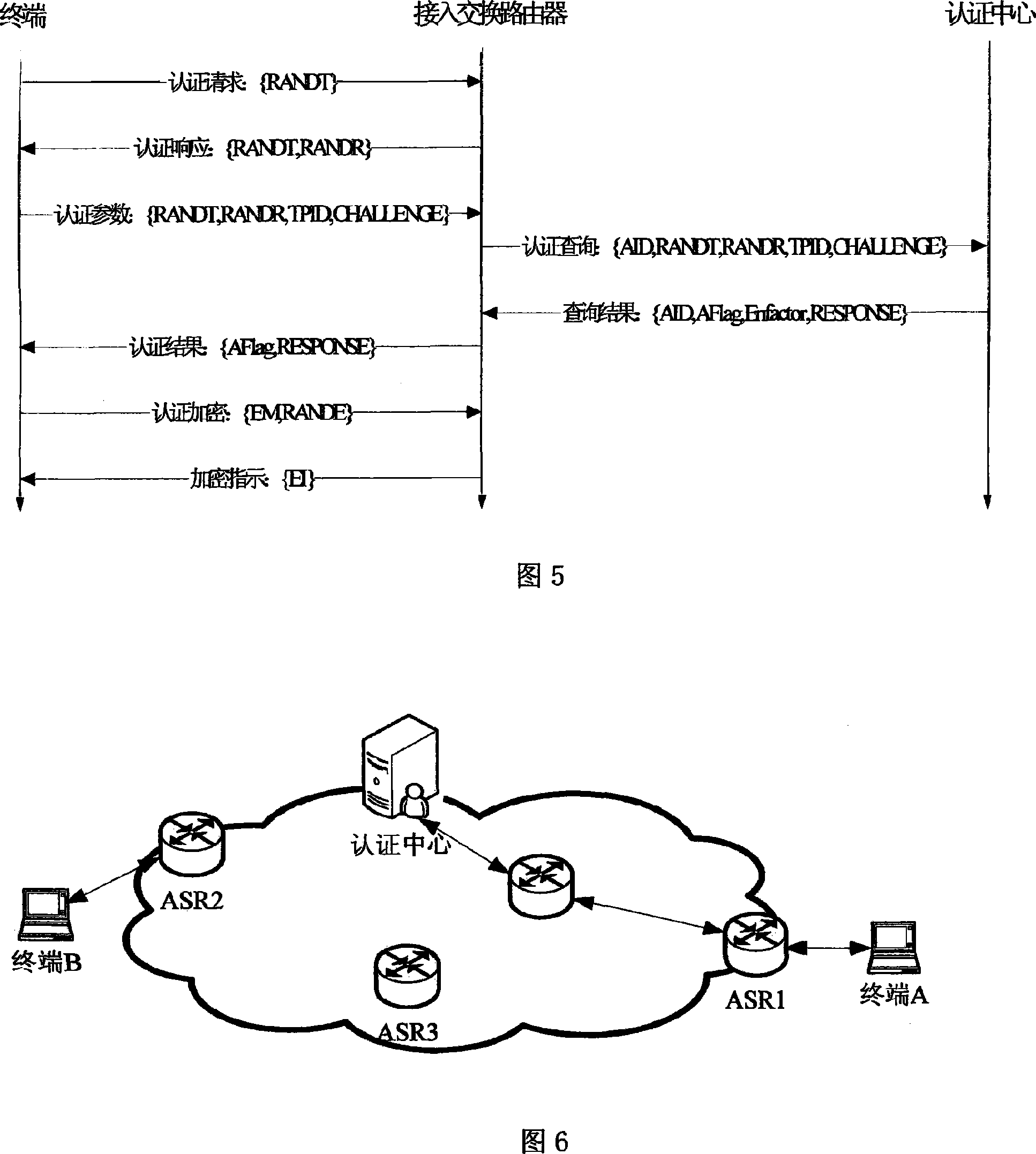
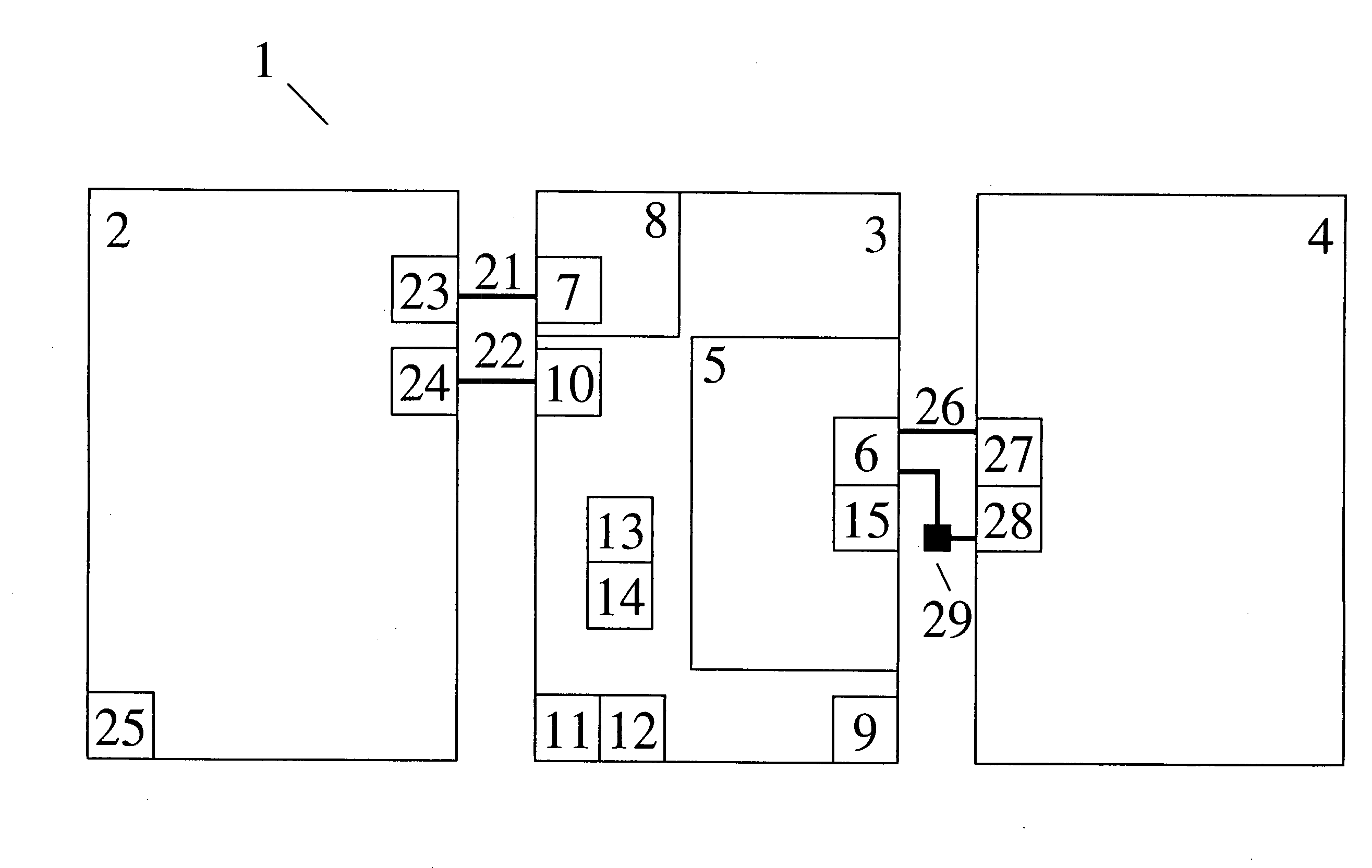
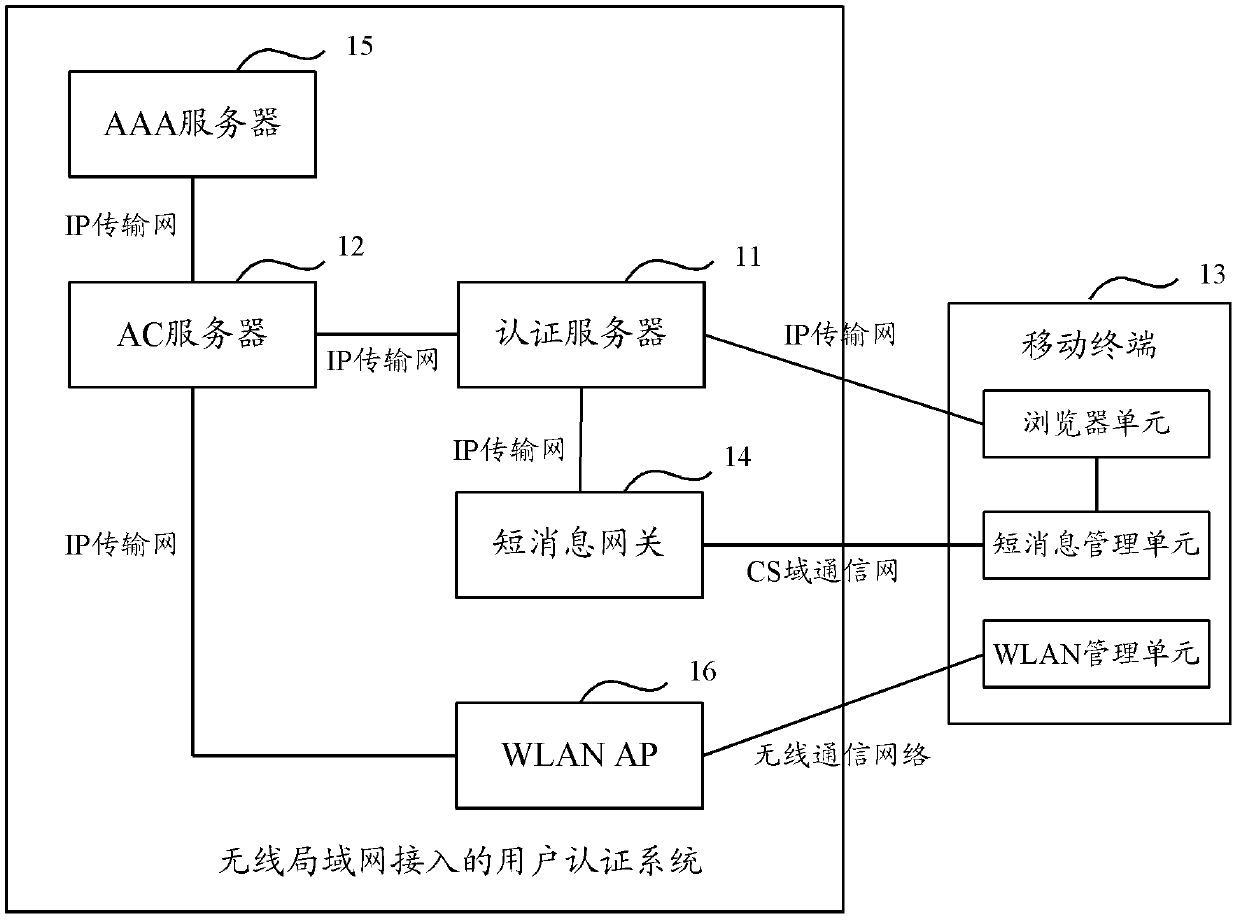
An integrated access method and system for mobile cellular network and WLAN
ActiveCN101150594ASimplify the certification processEasy to operateData switching by path configurationRadio/inductive link selection arrangementsPacket data serving nodeService flow
The invention relates to a unified access method for mobile cellular network and radio local area network, comprising: step 1, setting a radio local area network authentication, authorization, charging server which is connected with a WAP gateway, a wireless controller respectively; step 2, a mobile terminal does a WAP registration to the radio local area network authentication, authorization, charging server; step 3, a radio local area network authentication of the mobile terminal is authenticated by the radio local area network authentication, authorization, charging server. The invention needs not rebuild PDSN (package data service node) of the CDMA1X network or SGSN / GGSN, WAP gateways of the GSM / GPRS network, keeps the package data service flow of the original mobile cellular network basically, does not change existing CDMA1X, CDMA1X service flow and net element functions, has high safety, centralized service flow, which is convenient to manage.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
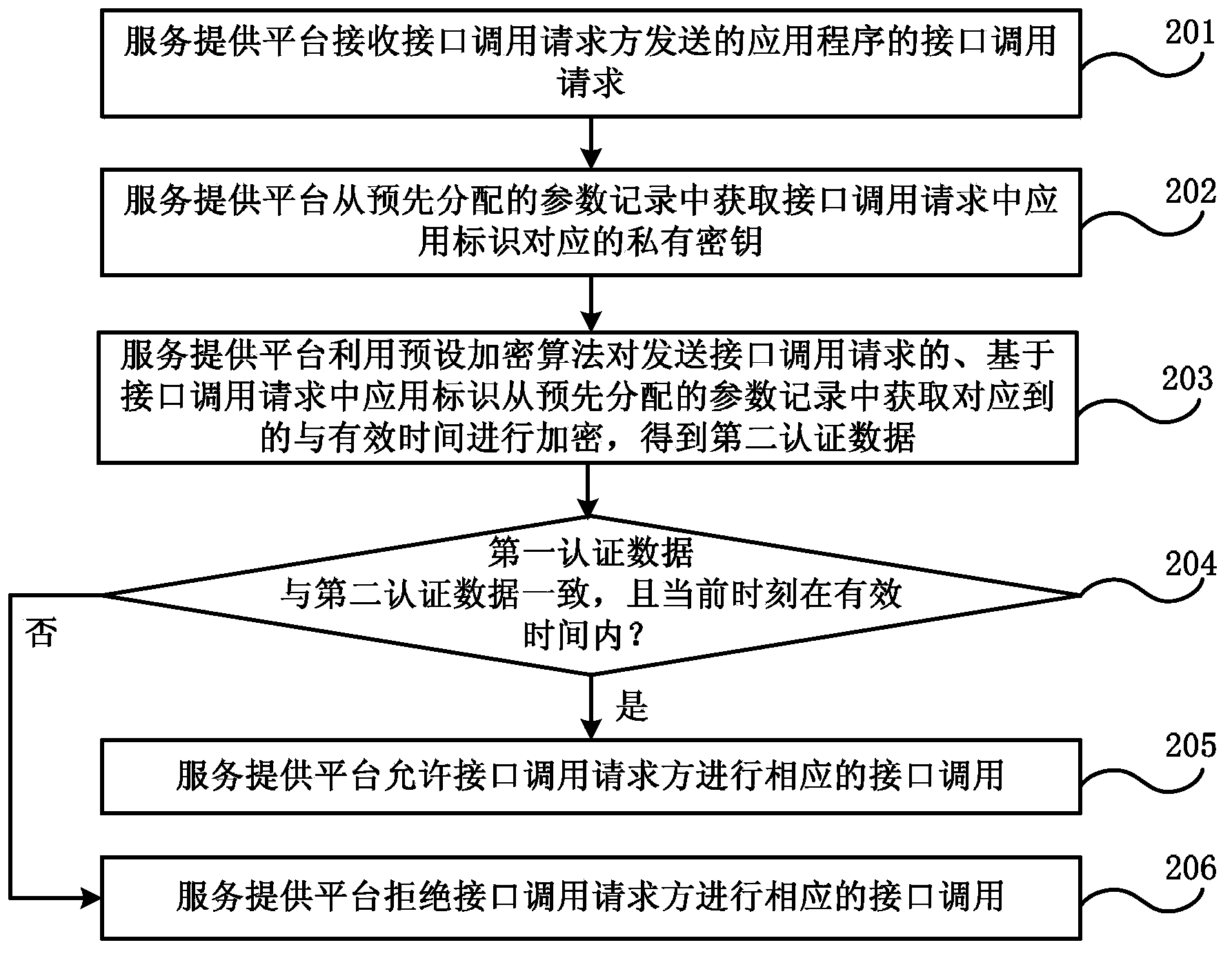
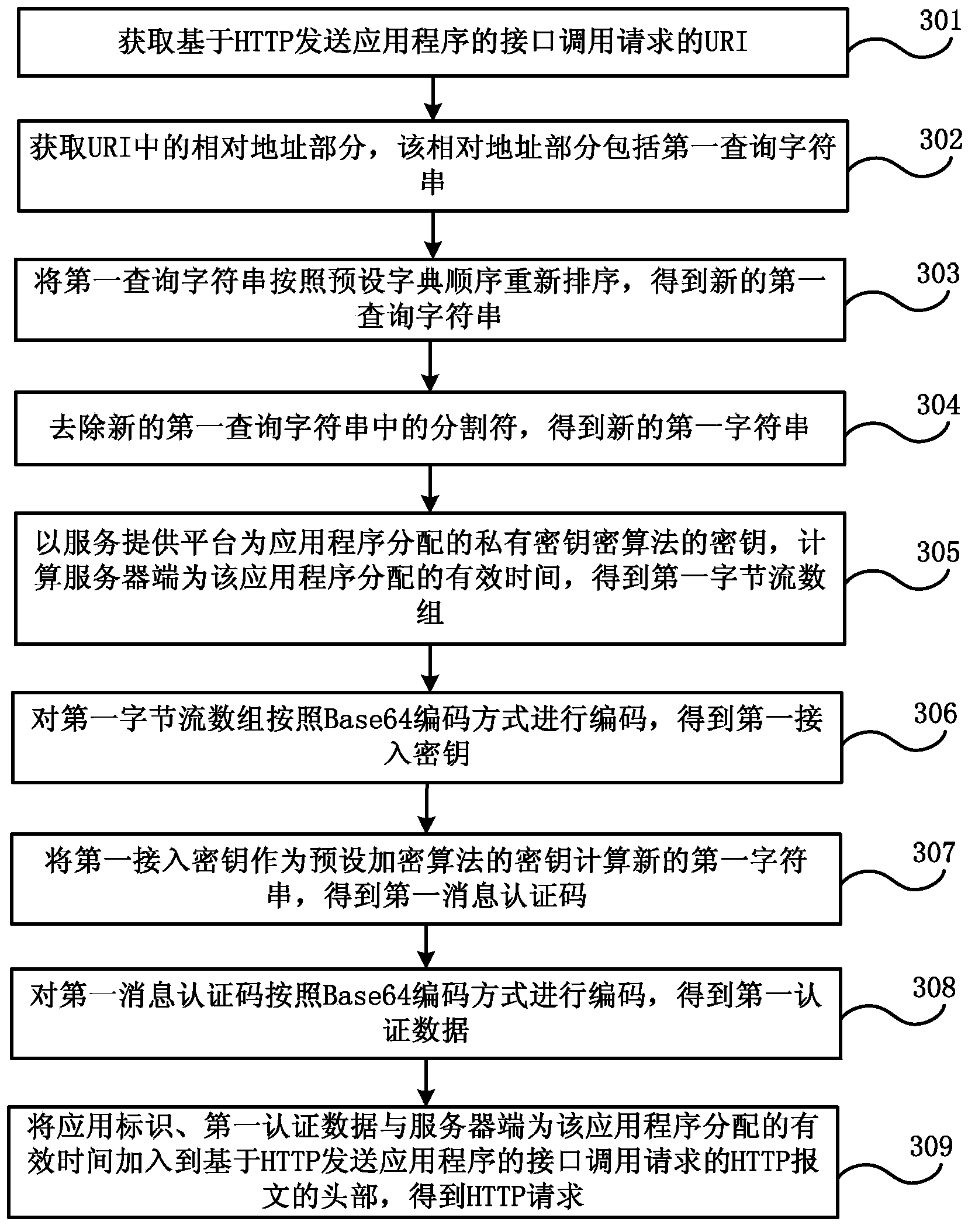
Authentication method for invoking open interface and system
The embodiment of the invention discloses an authentication method for invoking an open interface and a system for executing the method. The method comprises the following steps: a service provision platform receives an interface invoking request of an application program transmitted by a server side or a client side, wherein the interface invoking parameters comprise application identification, a private secret key and valid time allocated by the server side for the interface invoking; the private secret key is allocated by the service provision platform when the server side is registered in the service provision platform; the client side logs in the server side, acquires authentication and acquires the interface invoking parameters from the server side; the service provision platform acquires the private secret key corresponding to the application identification from the pre-assigned parameter records, and authenticates the interface invoking request based on the acquired private secret key; if the authentication is successful, the corresponding interface invoking is permitted; or, the interface invoking request party is refused to invoke the corresponding interface. The authentication method can ensure the interface invoking security, the interface invoking process is simple, and the interface invoking efficiency is high.
Owner:CHINA TELECOM CORP LTD
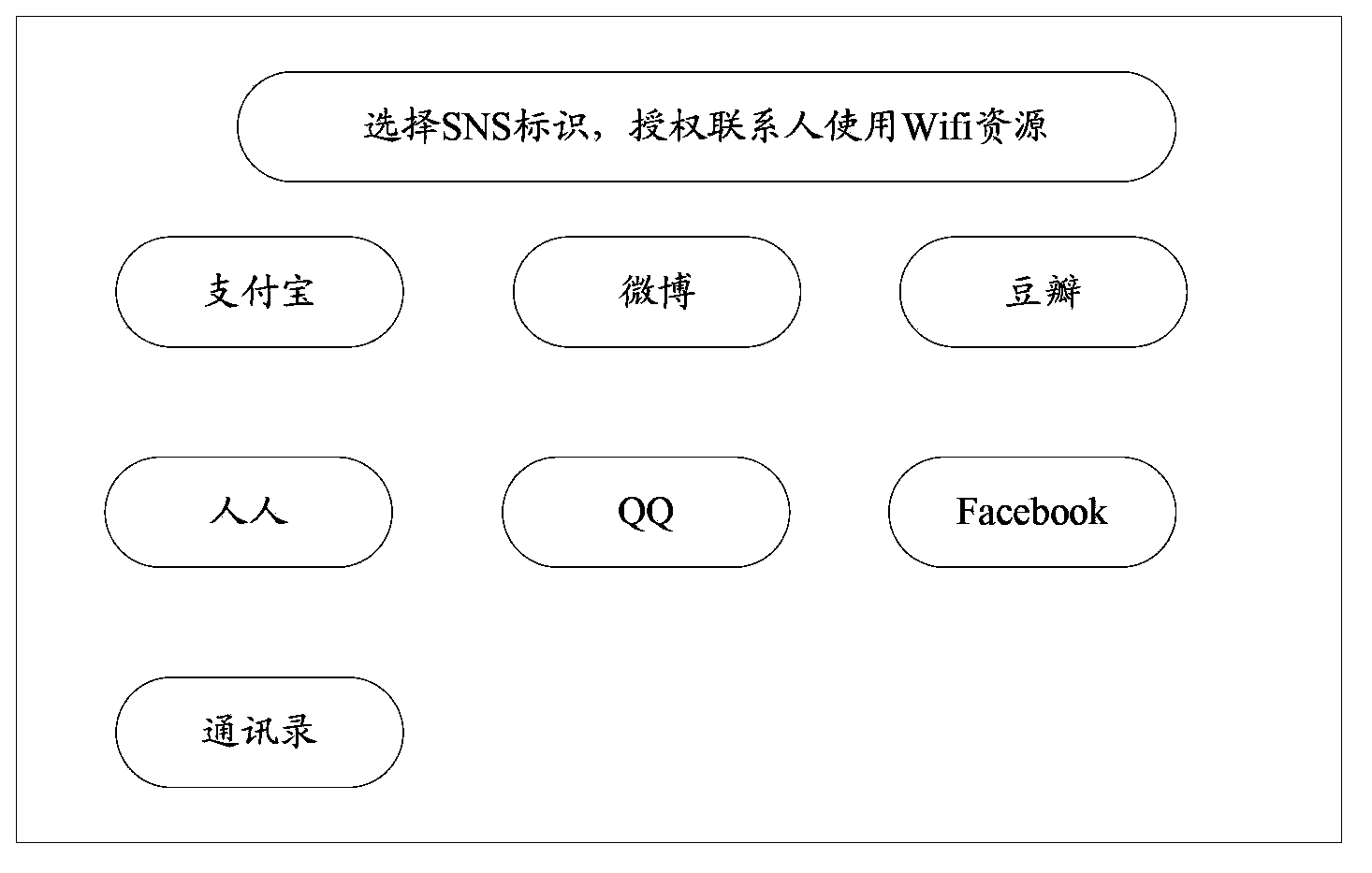
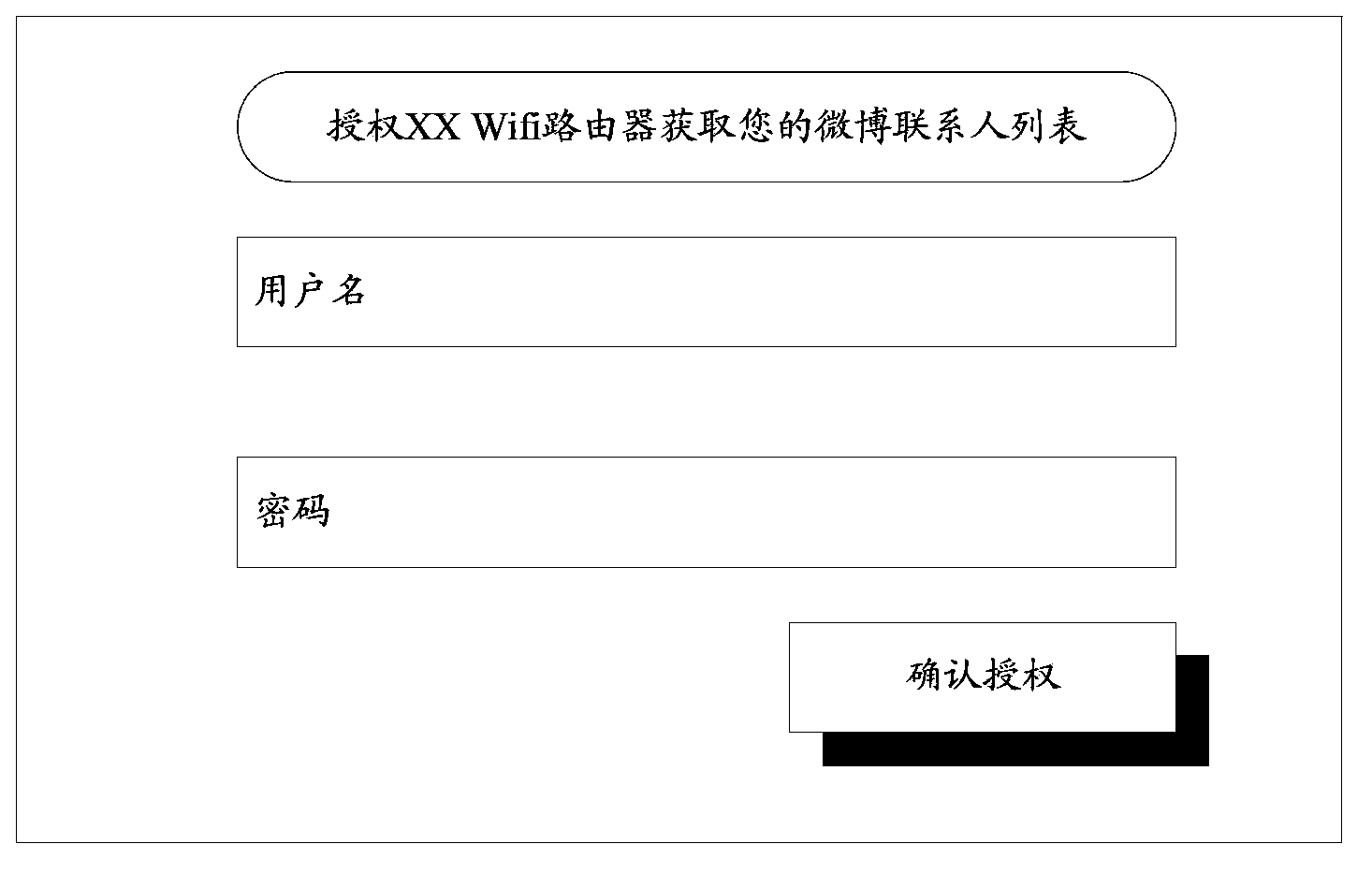
Method and device for setting Wifi access authority and Wifi authentication
The invention discloses a method and a device for setting Wifi access authority and Wifi authentication. The method comprises steps of obtaining user information of users having social association relation of a terminal which initiates an authorization request in an SNS website server by a Wifi router, and setting Wifi access authorization for the obtained user information by the terminal. After the setting of the Wifi access authority and the Wifi authorization, the Wifi router can perform querying only according to the fact that whether the user information of other terminals in the SNS website server is provided with Wifi access authorization when the Wifi router is performing authorization on other terminals, can determines the Wifi access authorization of other terminal user information according to the querying result and then finishes the authorization process. Because the invention doesn't need to perform verification on the user name and the password mode on the other terminals the resources of which are shared through Wifi, the verification process is simplified while the network security is guaranteed.
Owner:ADVANCED NEW TECH CO LTD
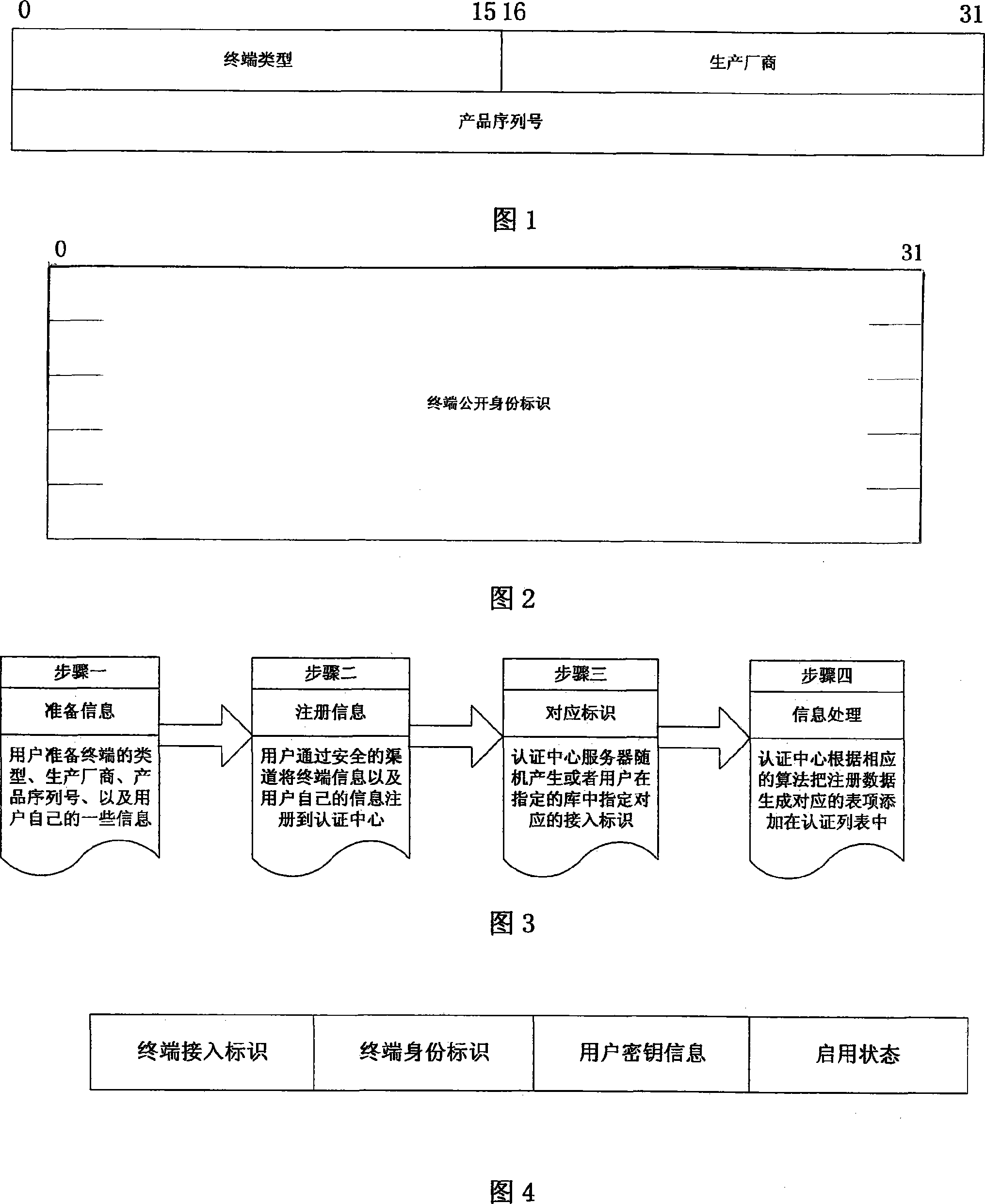
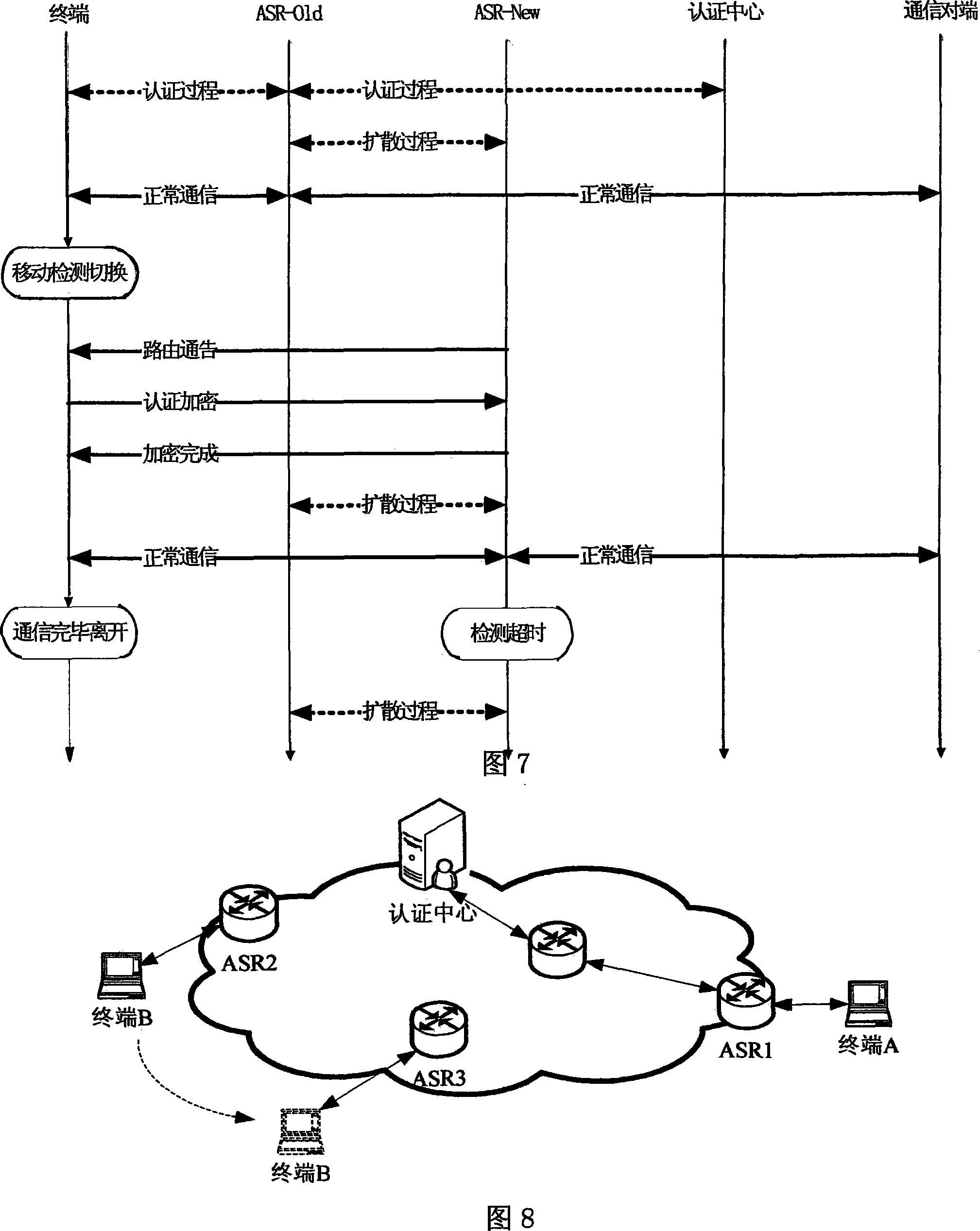
Identification based integrated network terminal united access control method
InactiveCN101119206AAccess control solutionEnsure safetyUser identity/authority verificationData switching by path configurationNetwork terminationElectricity
The present invention relates to an all-in-one network terminal unifying accessing and controlling method based on the marks and is an electric figure communication processing method by utilizing the network. The present invention comprises a network which consists of a resting net and a movable net, a terminal, an accessing router and an authenticating center. The steps are as follows: the terminal unifies the define of the identity marks, the terminal unifies the registering process of the identity marks, the terminal unifies the accessing and controlling authentication process, the terminal movably switches the quick authentication processing process, the encrypting communication is between the terminal and the accessing exchanging router ASR. The method unifies the identity marks of heterogenous network terminals and provides a good premise to the accessing of the heterogenous network terminals. The effective authenticating method effectively solves the problem that the illegal users are unable to use the network by the accessing control of the network to the terminal. The simple authenticating process brings little time delay to the moving of the terminal and simultaneously processes the authentication and confirmation of the terminal. The communication between the terminal and the accessing exchanging router adopts an encrypting method so as to conquer the menace of the clone.
Owner:BEIJING JIAOTONG UNIV
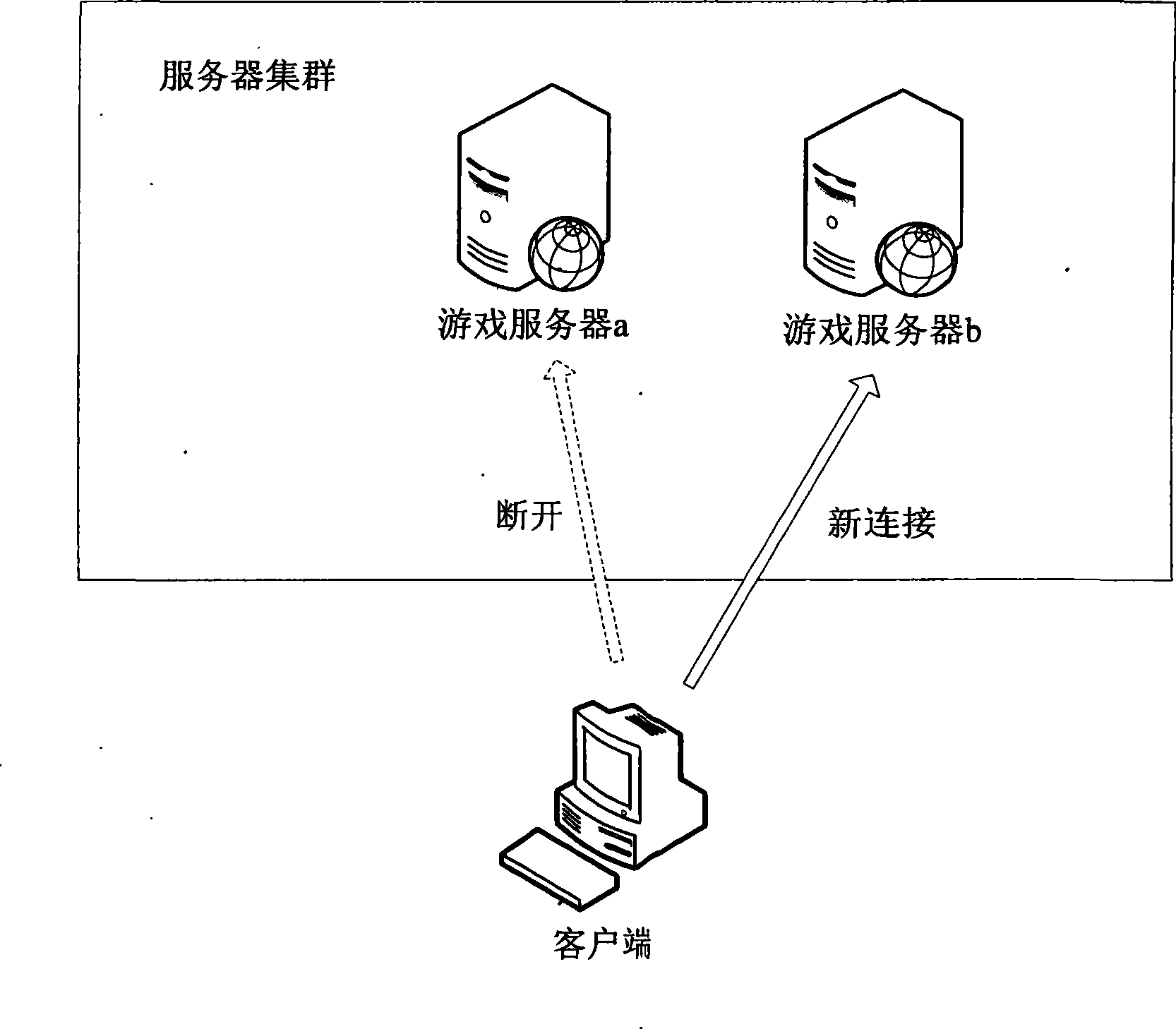
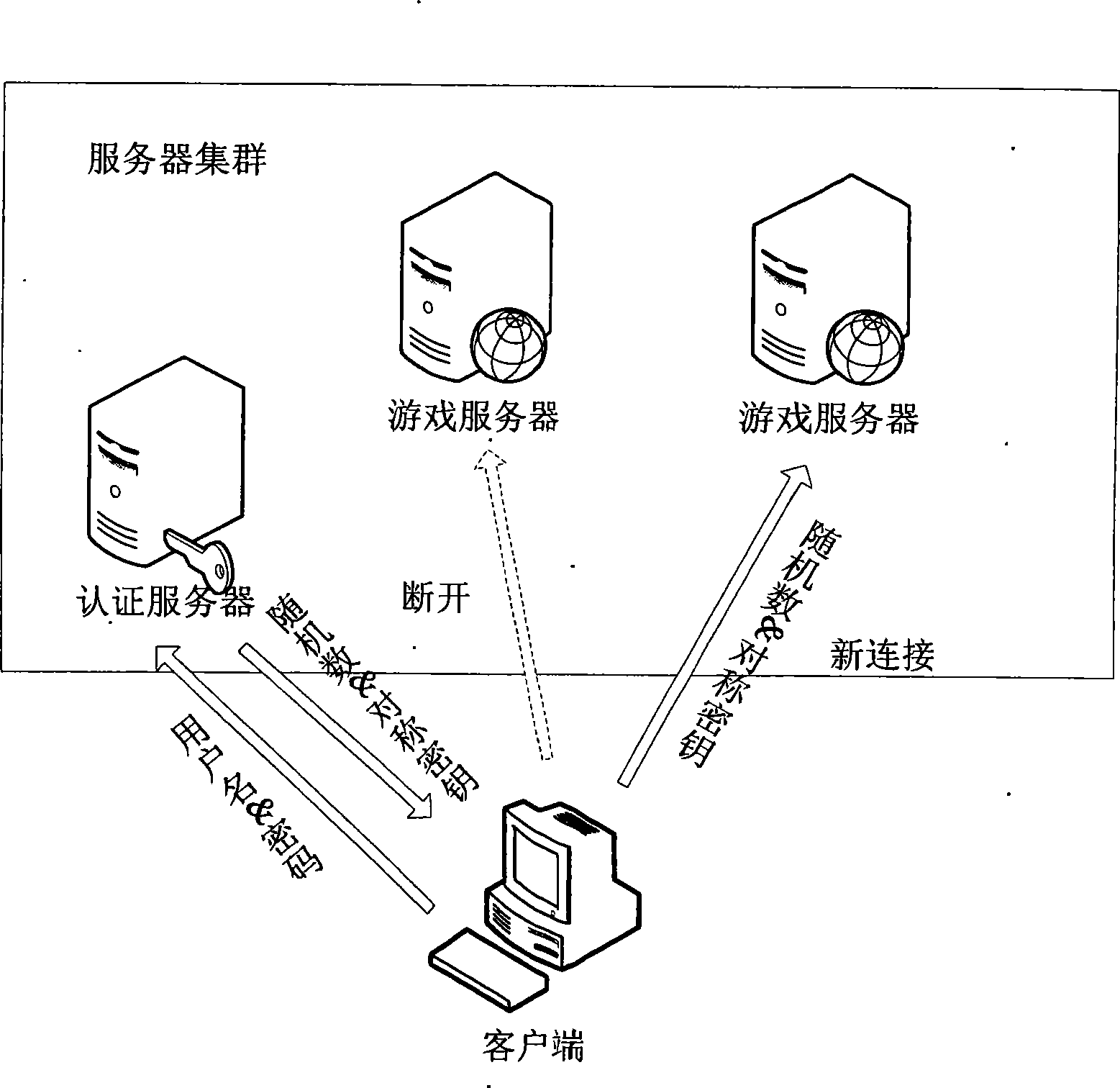
Authentication method for network game client and server cluster
ActiveCN101431410ASimplify the certification processImprove efficiencySpecial service provision for substationPublic key for secure communicationPasswordAuthentication server
The present invention discloses a verification method to on-line game client side and server cluster and comprises the following steps: verifying ID to authentication server with username and password by client; assigning a random number and a symmetric encryption key to client; encrypting the random number with the symmetric encryption key by client and taking the encrypted random number as verification evidence for ID verification with other server in server cluster. The random number and symmetric encryption key assigned by authentication server are taken as the basis of ID verification and authentication between client and on-line game server in server cluster through the invention; hence, there is no need to save username and password for long time in client side and possibility of leaking username and password is prevented, verification process of server cluster is simplified, efficiency of on-line game server is improved.
Owner:KONKA GROUP
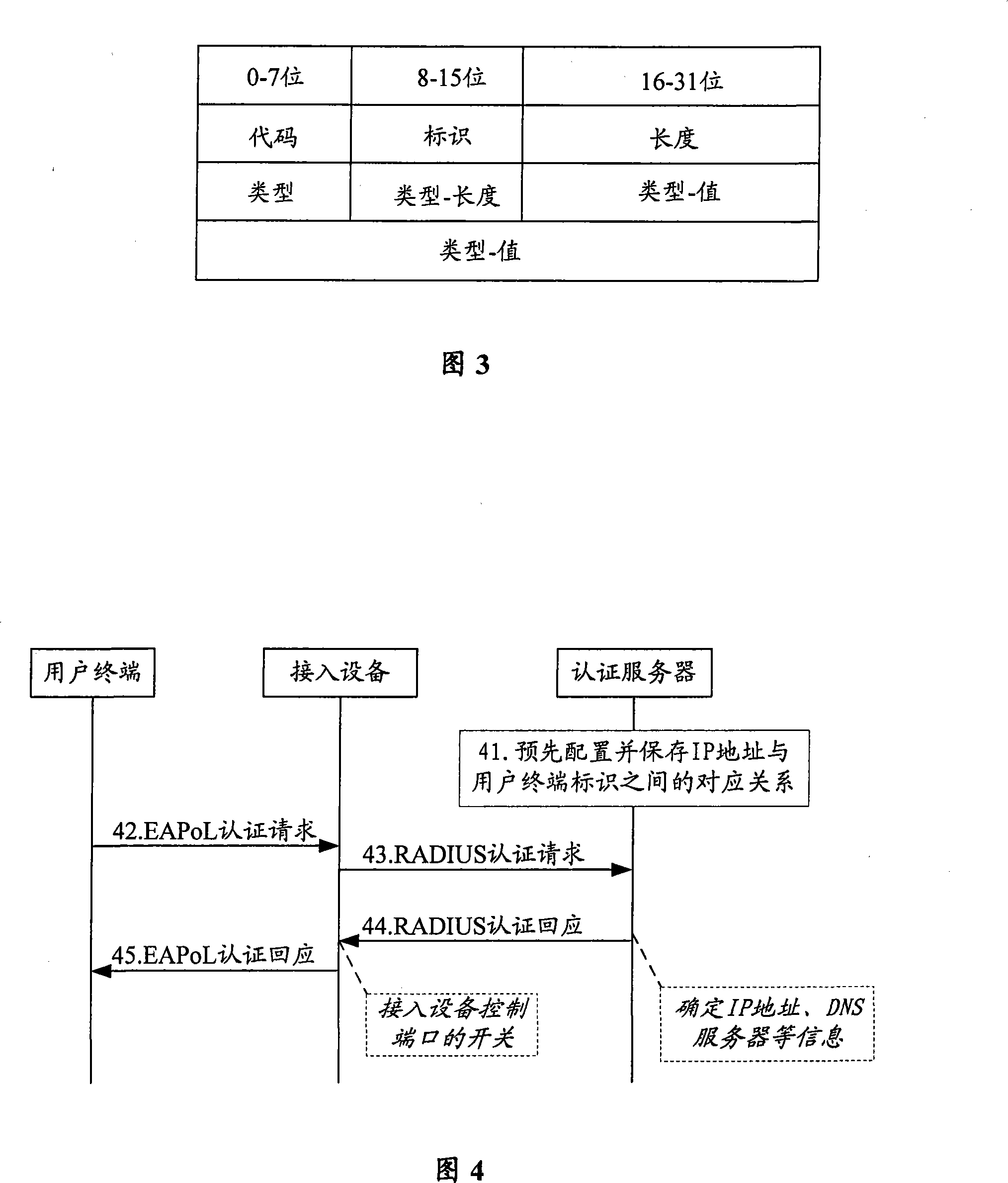
An IP address allocation and device in user end certification process
InactiveCN101217575AImprove securitySimplify the certification processData switching by path configurationIp addressAuthentication server
The invention provides a method which is used for distributing an IP address in the process of authorizing a user terminal and a device thereof, wherein, after an authorizing server is authorized at the user terminal, the IP address is distributed to the user terminal. By adopting the method and the device of the invention, a DHCP server is not needed to be deployed in a network, thus reducing the cost of network building.
Owner:NEW H3C TECH CO LTD
Mobile commerce identity authentication method
InactiveCN101969446AEliminate inconvenienceMeet the inconvenienceUser identity/authority verificationInternet Authentication ServiceThird party
The invention provides a mobile commerce identity authentication method. In the method, key negotiation is realized by the most efficient elliptic curve-based public key cryptosystem in public key cryptosystems. An elliptic curve algorithm has the characteristics of low calculated amount and high safety, so the elliptic curve algorithm is used for generating a public key and a private key, and a public key cryptosystem without a third-party is realized and applied to the two-way authentication service of a client and a server.
Owner:BEIJING JIAOTONG UNIV
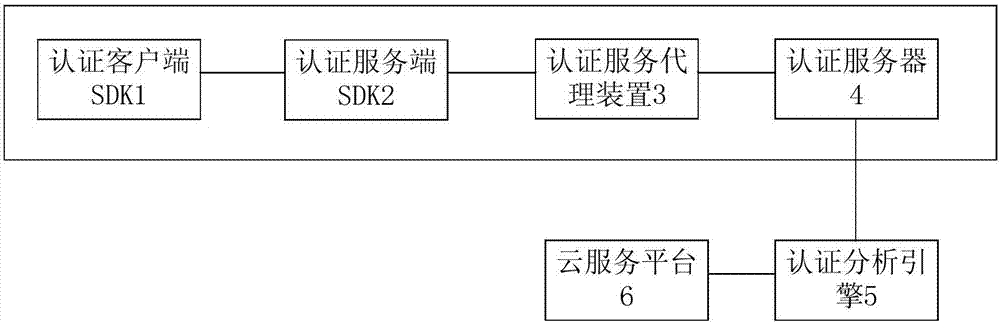
Intelligent identity authentication system
InactiveCN107172049ASimplify the certification processGuarantee authentication securityTransmissionRisk levelRisk Control
The invention provides an intelligent identity authentication system. The intelligent identity authentication system comprises an authentication client SDK, an authentication server SDK, an authentication service proxy device, an authentication server, an authentication analysis engine and a cloud service platform, wherein the authentication client SDK is used for acquiring client information of authenticated users; the authentication server SDK is used for checking service strategies, and executing and forwarding information of an authentication client; the authentication service proxy device is used for providing a server reverse proxy when the authentication server SDK cannot implement an authentication function; the authentication server is used for managing the service strategies, authentication modes and cases, and displaying authentication analysis results; the authentication analysis engine is used for performing risk analysis based on a risk control model, wherein the risk analysis includes the steps of performing risk level scoring based on predefined rules and implementing big data analysis in combination with a big data analysis engine; and the cloud service platform dynamically adjusts identity authentication modes and requirements according to risk analysis results of the authentication server and the authentication analysis engine, performs identity authentication for the users, and returns an authentication result to the authentication analysis engine. According to the intelligent identity authentication system provided by the invention, an appropriate identity authentication mode can be selected for the users based on a risk analysis method.
Owner:北京信安世纪科技股份有限公司
Method of access authentication and recertification in home NodeB system of user terminal
InactiveCN101854629ARealization of privacyAchieve privacySecurity arrangementDigest access authenticationAuthentication server
The invention discloses methods of access authentication and recertification of a user terminal in a home NodeB system, mainly overcoming the defect that the existing standard does not provide an authentication method of the user terminal for accessing a core network through the home NodeB. The access authentication process comprises the following steps: firstly, simultaneously sending the identification of a user and the identification of the home NodeB to HNBHLR to inquire, judging according to whether the identification of the user exists in the CSG list of the home NodeB; and secondly, adopting the modified EAP-AKA protocol to perform authentication between the user terminal and a authentication server. The recertification process comprises the following steps: firstly, judging according to whether the identification of the user is as the same as the identification stored in the home NodeB network, and secondly, using a hierarchy secret key to modify the existing EAP-AKA recertification method to realize the mutual authentication between the user terminal and the authentication server. The methods of the invention has the advantages of simple processes, high efficiency, reliable performance, good safety and the like, thus being applicable to the access authentication and recertification of the user terminal in the home NodeB system.
Owner:XIDIAN UNIV
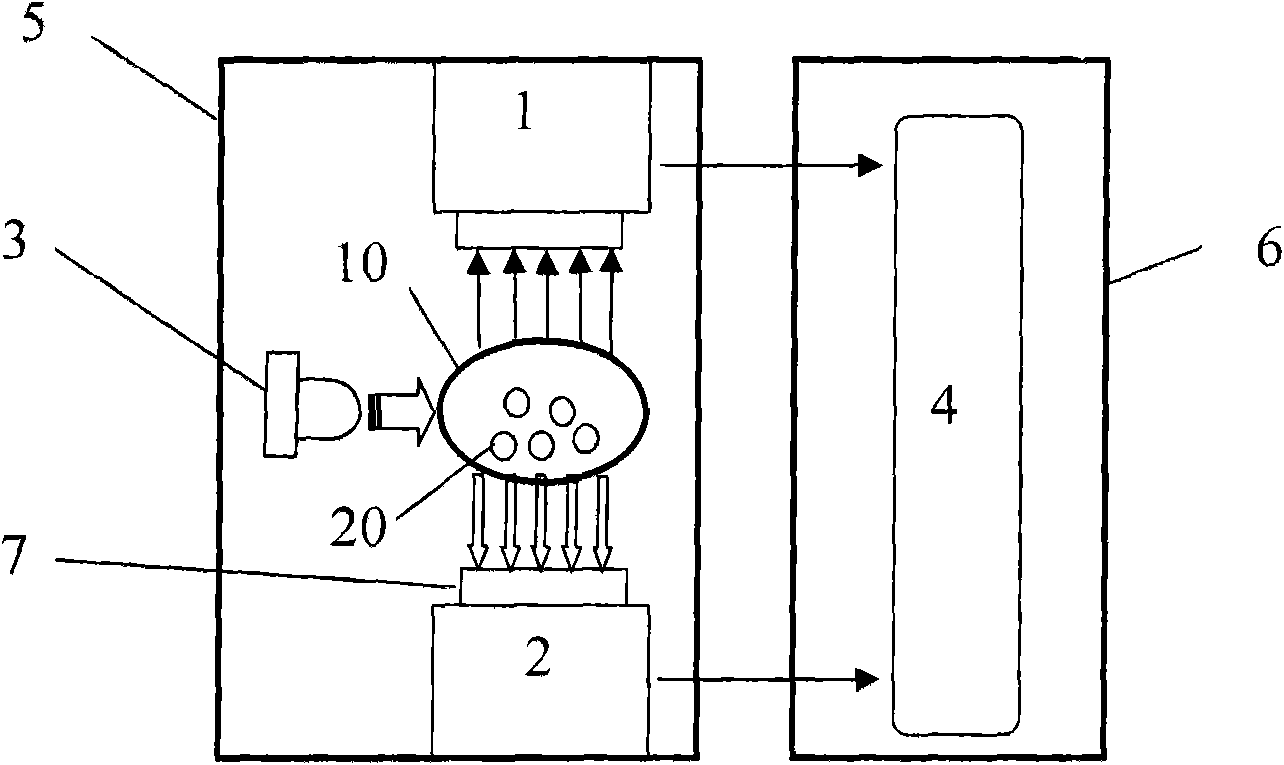
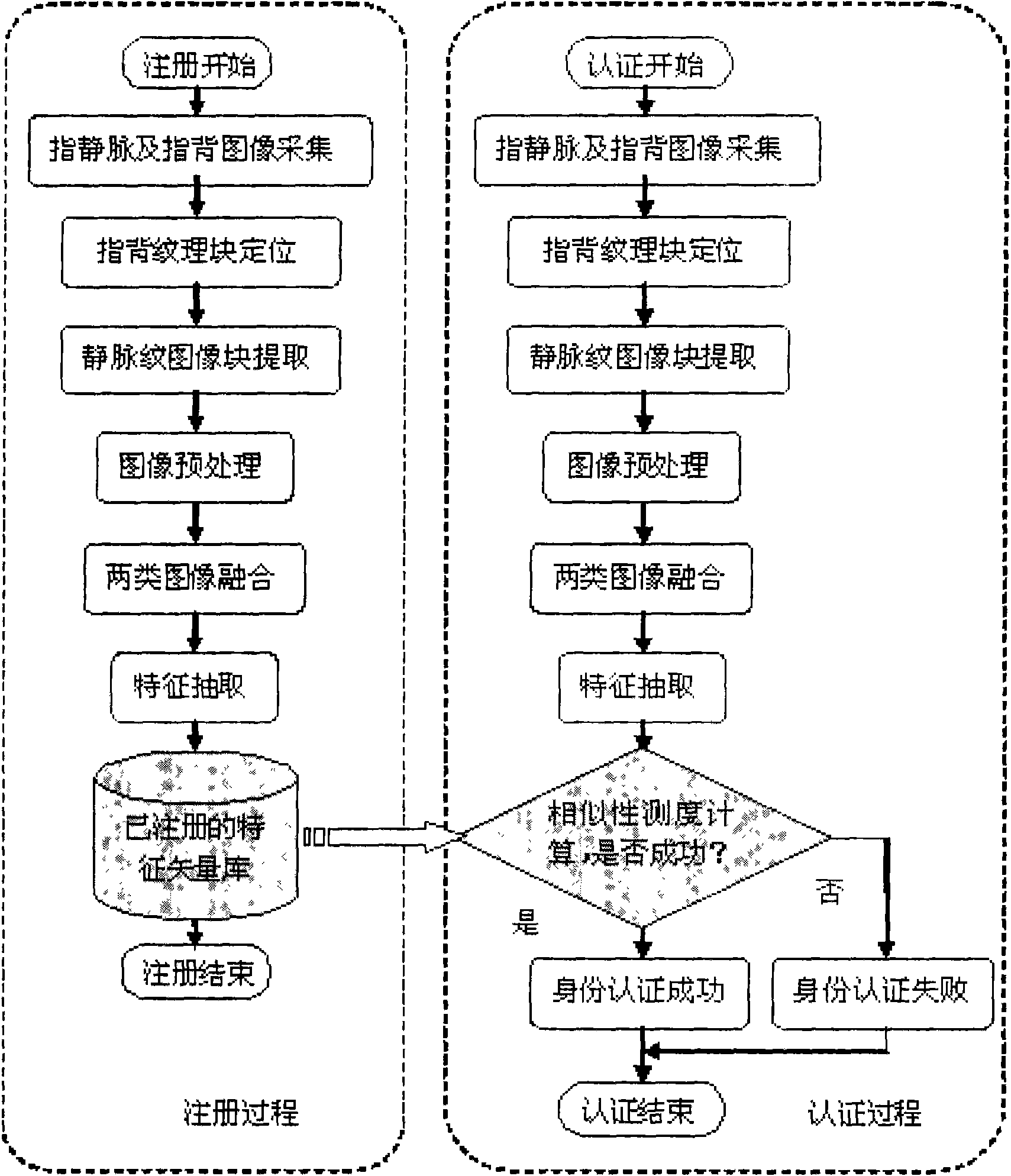
Imaging device based on vein pattern and backside pattern of finger and multimode identity authentication method
ActiveCN101539995AImprove stabilityImprove applicabilityCharacter and pattern recognitionVeinBiometrics
The invention discloses an imaging device based on vein pattern and backside pattern of a finger and a multimode identity authentication method, wherein the imaging device comprises an acquisition support on which a concave finger putting area is arranged; a visible light imaging device which is arranged at one side of the concave finger putting area of the acquisition support and used for acquiring the back picture of the finger; a near infrared imaging device which is arranged at the other side of the concave finger putting area of the acquisition support and opposite to the visible light imaging device, and used for acquiring the vein picture of the finger by the irradiation of a near infrared light supply; and the bar-shaped near infrared light supply which is arranged on the acquisition support and used for irradiating near infrared light to the finger from the side of the finger. The identity authentication method comprises a logon procedure and an authentication procedure, and the adopted biological features thereof comprise the backside pattern and vein pattern of the same finger. The invention also relates to identity authentication equipment comprising the imaging device, which has better anti-counterfeit performance, and can effectively improve the stability and applicability of a biometrics identification system.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Computer system for aircraft
InactiveUS20060282597A1Minimize timeParts are smallDigital data processing detailsCathode-ray tube indicatorsGraphicsNetwork connection
Computer system to be used in the cockpit of an aircraft, comprising a fixed screen, a docking unit and a portable computer in order to display on the fixed screen in the cockpit information which is stored on the portable computer, wherein the docking unit comprises an embedded computer with a network connection for connecting an arbitrary portable computer to the computer system, a screen connection for connecting the fixed screen to the docking unit, a graphic processor, a power connection and an input connection for receiving signals from input means and a corresponding retrofitting set, a corresponding docking unit and a corresponding method.
Owner:LUFTHANSA SYST GROUP
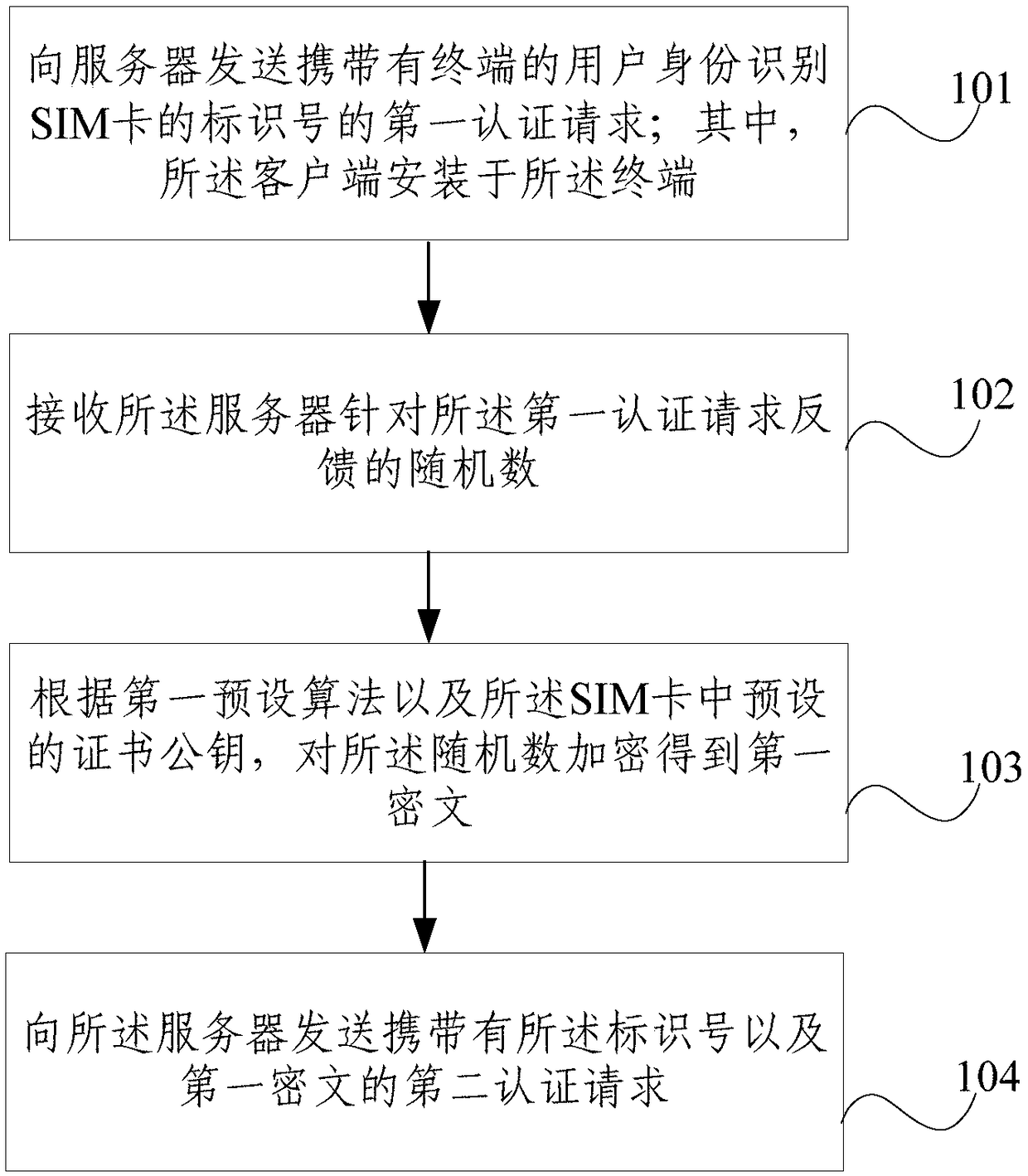
Identity authentication method and device
ActiveCN109005155ASimplify the certification processEasy to operateKey distribution for secure communicationUser identity/authority verificationComputer hardwareCiphertext
The embodiment of the invention provides an identity authentication method and a device. The method is applied to a client end. The method comprises the following steps: sending a first authenticationrequest carrying an identification number of a user identification SIM card of a terminal to a server, wherein the client is installed on the terminal; receiving a random number fed back by the server for the first authentication request; encrypting the random number to obtain a first ciphertext according to a first preset algorithm and a preset certificate public key in the SIM card; sending a second authentication request carrying the identification number and the first ciphertext to the server. The authentication process in the embodiment of the invention is simple and convenient to operate. As most communication terminals are provided with SIM card slots, the embodiment of the invention is easy to popularize, has strong applicability, and does not need to add other hardware equipment.
Owner:BEIJING QIANXIN TECH
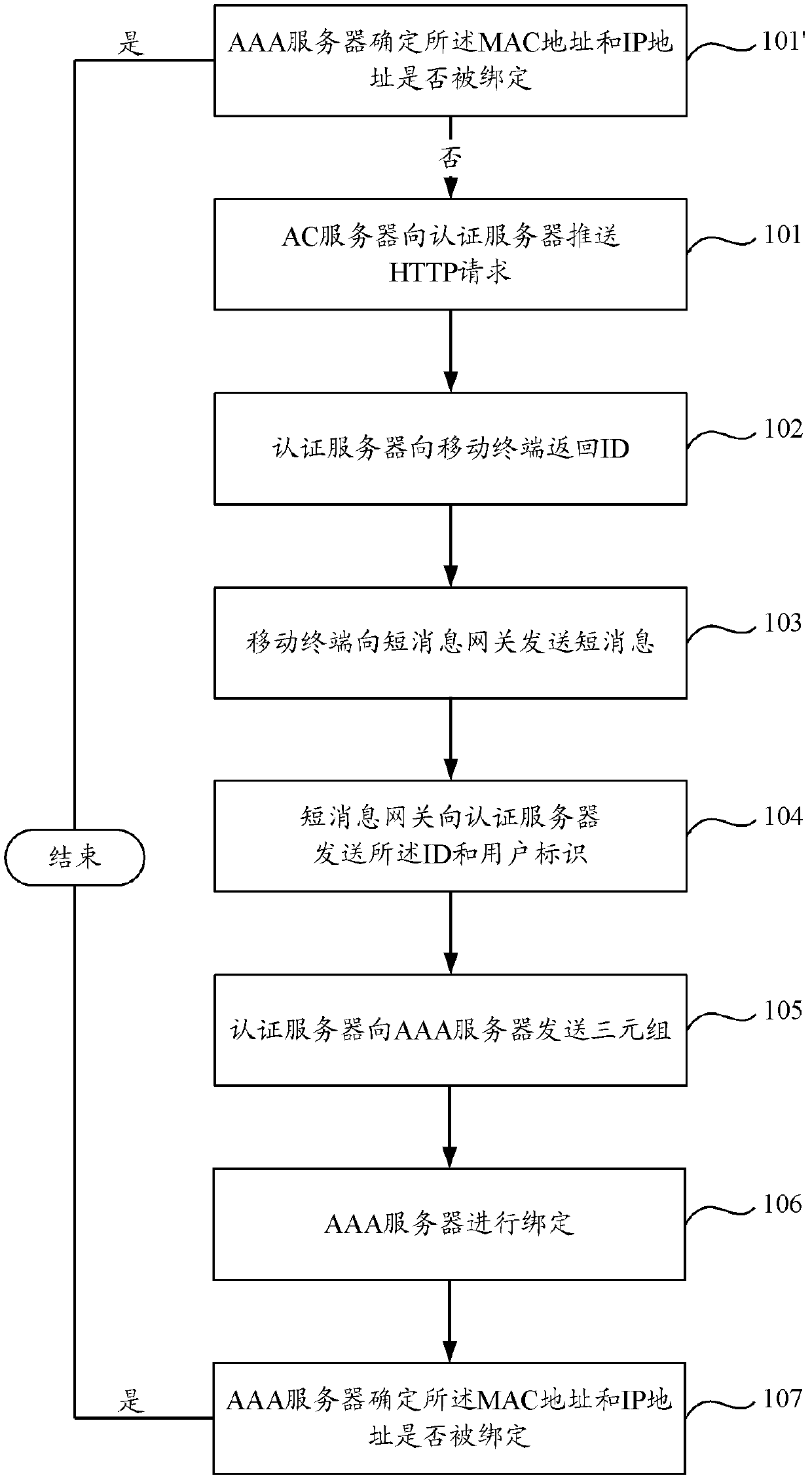
Method, device and system for user authentication in access of wireless local area network
ActiveCN103297967ASimplify the certification processAvoid occupyingTransmissionSecurity arrangementIp addressUser input
The invention provides a method, device and system for user authentication in access of a wireless local area network. The method includes the steps of constructing an ID by means of a binary group formed by a MAC address and an IP address which correspond to a mobile terminal when an authentication server receives an HTTP request pushed by an AC server, returning the ID to the mobile terminal, forming a binding relationship among the MAC address, the IP address and a user identification in an AAA server when the mobile terminal uploads the user identification through short messages, and accordingly achieving the user authentication in the access process of the wireless local area network. According to the technical scheme, a client is needless to be uploaded, downloaded, installed and managed on the mobile terminal, occupation of system resources is avoided, the problem that a special authentication client installed on the mobile terminal needs to adapt to different operation systems is avoided, meanwhile, a user is needless to input a user name, a code and other authentication information, and the user authentication process is simplified.
Owner:CHINA MOBILE COMM GRP CO LTD
Pile installation and monitoring system and method of using the same
InactiveUS20120203462A1Simplify the certification processEasy to installSpecial data processing applicationsElectric/magnetic detectionReal-time dataDisplay device
A system and method of monitoring the installation of a pile in a ground surface. The system and method including the use of a portable monitoring device configured to allow real time data entry and display relating to the pile(s) being installed and having at least one data entry button for at least a portion of the data entry. The device further including a display for the display of desired data to help monitor and control the installation process.
Owner:PILE DYNAMICS
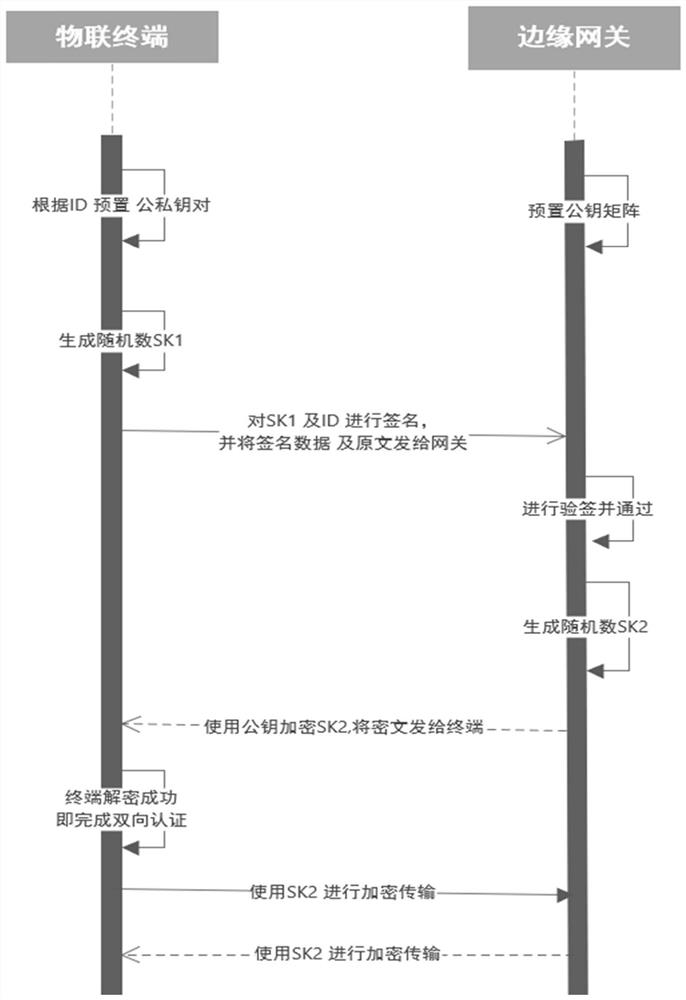
Data security authentication transmission method and device for Internet of Things terminal
ActiveCN112291230AImplement mutual authenticationImplement data encryptionUser identity/authority verificationInstrumentsKey (cryptography)Cryptographic protocol
The invention discloses a data security certification transmission method and device for an Internet of Things terminal. The method comprises the steps: presetting identification key pairs in a factory of an Internet of Things terminal, and presetting a corresponding public key matrix in an edge gateway; according to a preset identification key pair of the Internet of Things terminal and a presetpublic key matrix of the edge gateway, completing the bidirectional authentication of the Internet of Things terminal and the edge gateway, and acquiring a communication encryption / decryption key; andcompleting the encryption and decryption of transmission data between the Internet of Things terminal and the edge gateway by using the communication encryption / decryption key. And the problem that the traditional safety means is difficult to meet the Internet-of-Things scene is effectively solved. A key management system which is realized based on a public key cryptography technology and can beapplied to an Internet of Things terminal is constructed through a lightweight authentication system, online support of a third party is not needed, large-scale key generation is conveniently realized, the authentication efficiency is high, the authentication process is simple, a cryptographic protocol and a cryptographic module are realized on the basis of a national cryptographic algorithm, andthe interactive authentication and data encryption of the Internet of Things terminal are realized.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY
Web authentication method and device
ActiveCN102916949ASimplify the certification processSave transmission resourcesTransmissionTransmission protocolWeb authentication
The invention discloses a Web authentication method and a Web authentication device, aiming at simplifying Web authentication process and saving network transmission resource. The method comprises the following steps: when a Web authentication is enabled, issuing an ACL (Access Control List) rule, which is an HTTP protocol, before the Web authentication, and forwarding IP message of which the destination IP address is not the local IP address to a CPU; permitting the forwarding of DNS protocol message; permitting the forwarding of broadcasting message; permitting direction communication between equipment connected with the local port and an switch; receiving the HTTP message, including message transmission information, sent by internal network users, wherein the message transmission information includes a destination IP address transmitted by the HTTP message, the used transmission protocol information and a destination port; judging whether the destination IP address is the local IP address, the used transmission protocol is TCP, and the destination port is 80; and if all results are yes, performing Web authentication of the internal network user.
Owner:KYLAND TECH CO LTD
Network equipment identification method
InactiveCN101068143AAddress Communication ThreatsSimplify the certification processSecuring communicationRelevant informationSmart card
A method for certifying network device includes providing intelligent card to network device, obtaining enciphered result E by network device, sending enciphered result and relevant data to CA center, distributing a communication cipher key to said network device by CA and informing new switched-in network device information of the other network device passed certification of CA by enciphering information with cipher key and informing relevant information of new switch-in network device to the other network device passed certification by CA center.
Owner:ZTE CORP
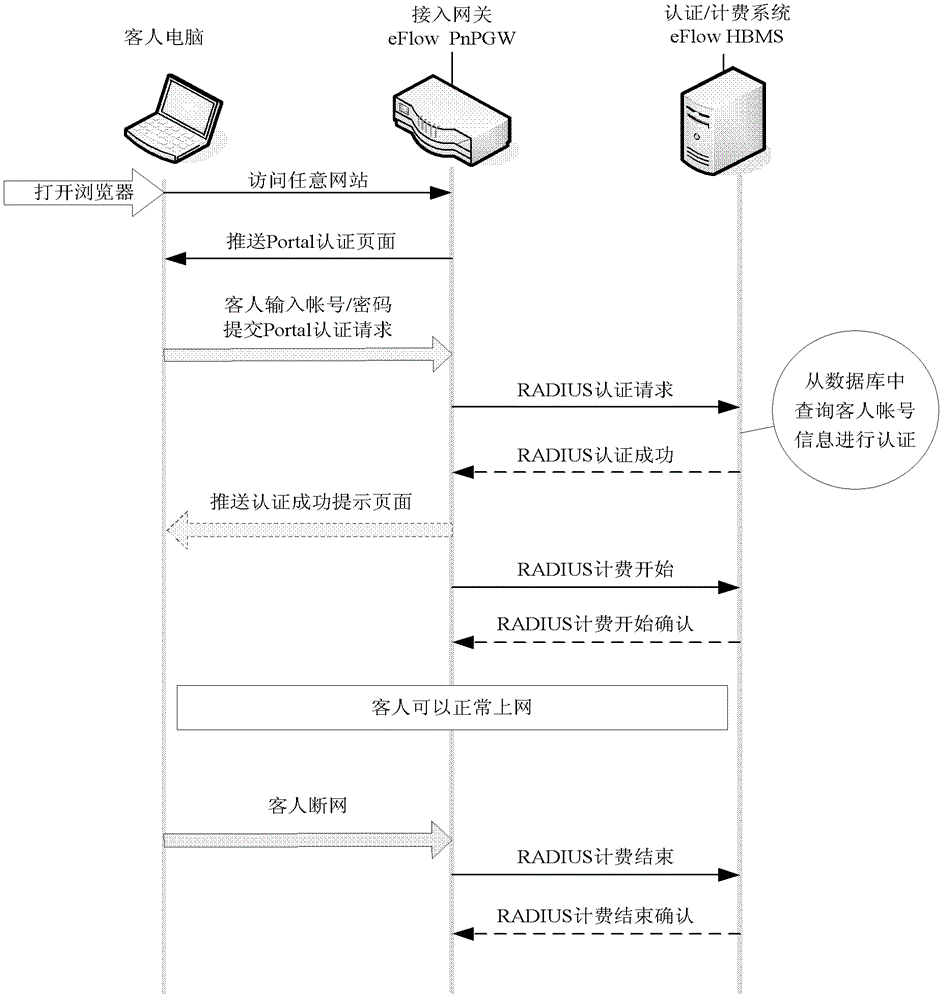
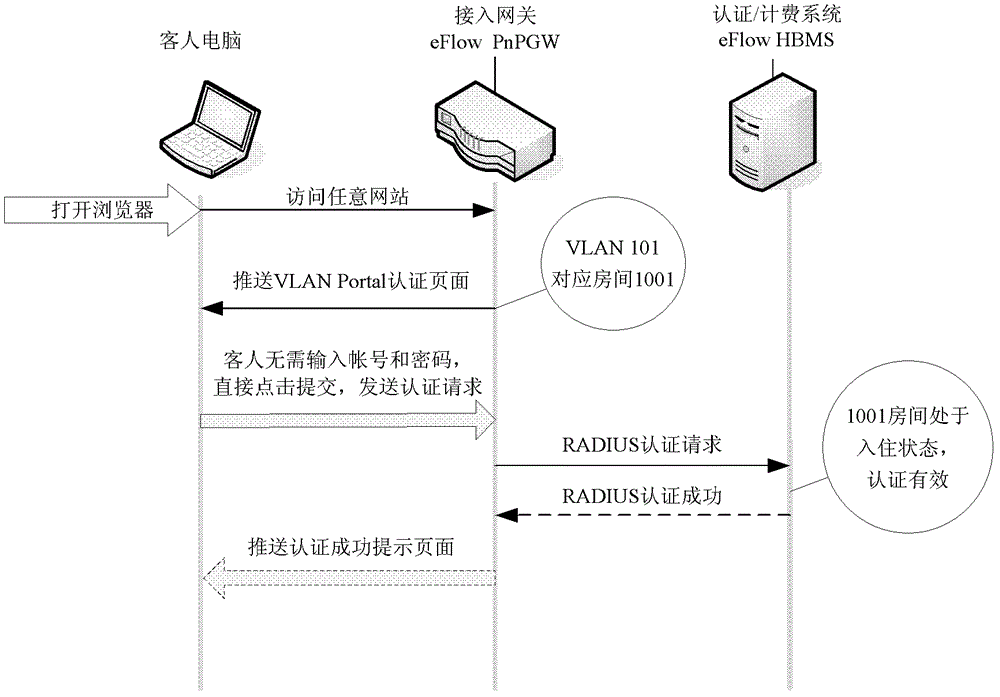
Hotel public network wired/wireless unified authentication roaming method
InactiveCN103067348ASimplify the certification processSave yourself the hassle of entering your passwordTransmissionSecurity arrangementCable networkAuthentication protocol
The invention discloses a hotel public network wired / wireless unified authentication roaming method. During two-layer networking, an unique 802.1Q virtual local area network (VLAN) number is configured for a wired network port for each guest room, a VLAN which is different from wired networks of the guest rooms is configured for other public wireless coverage areas, and all the VLANs end at an access port of a high speed internet access (HSIC). When a guest accesses the wired / wireless network port in the guest room, the HSIC can conduct authentication according to the 802.1Q VLAN or Portal passwords of an upward message. When the authentication is passed, HSIA works out an authentication record. When the user accesses the network again, the HSIA conduct the authentication directly according to a machine aided cognition (MAC) address of an accessed terminal device or Cookie identification (ID) of the accessed terminal device. Authentication is not needed for accessing each time, and therefore an authentication process of accessing the terminal device of the guest is greatly simplified and fast and intelligentized surfing authentication service is provided for hotel users.
Owner:安美世纪(北京)科技有限公司
Key digital identification method using once variable quantity
InactiveCN1980124AImprove integrityAchieve freshnessUser identity/authority verificationComputer hardwareMessage authentication code
Using message authentication code (MAC) to authenticate message, the invention uses one-off variable. The method includes steps: before using one-off variable, saving range and use state of one-off variable; it must carry out operation for one-off variable and message together to calculate MAC; in authenticating MAC, must authenticate one-off variable, and its state; after using one-off variable, must mark and save use state; for certain cipher key and authentication function, one-off variable is only use for once to authenticate message effectively. Using one-off variable can realize integrality and freshness of authenticating message. Advantages are: synchronous use one-off variable to prevent security attack in many ways, and simple method for realizing complicated authentication application.
Owner:刘金宏
Network access method and system
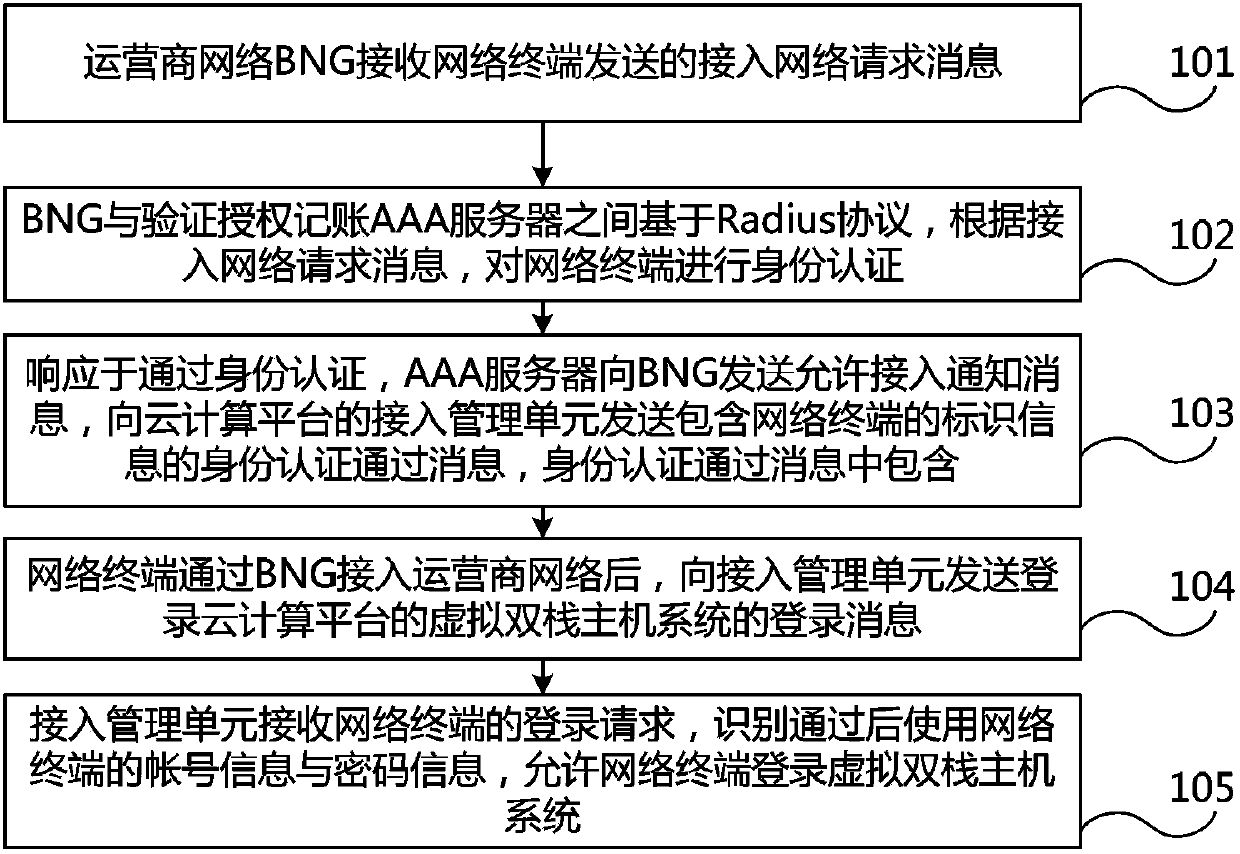
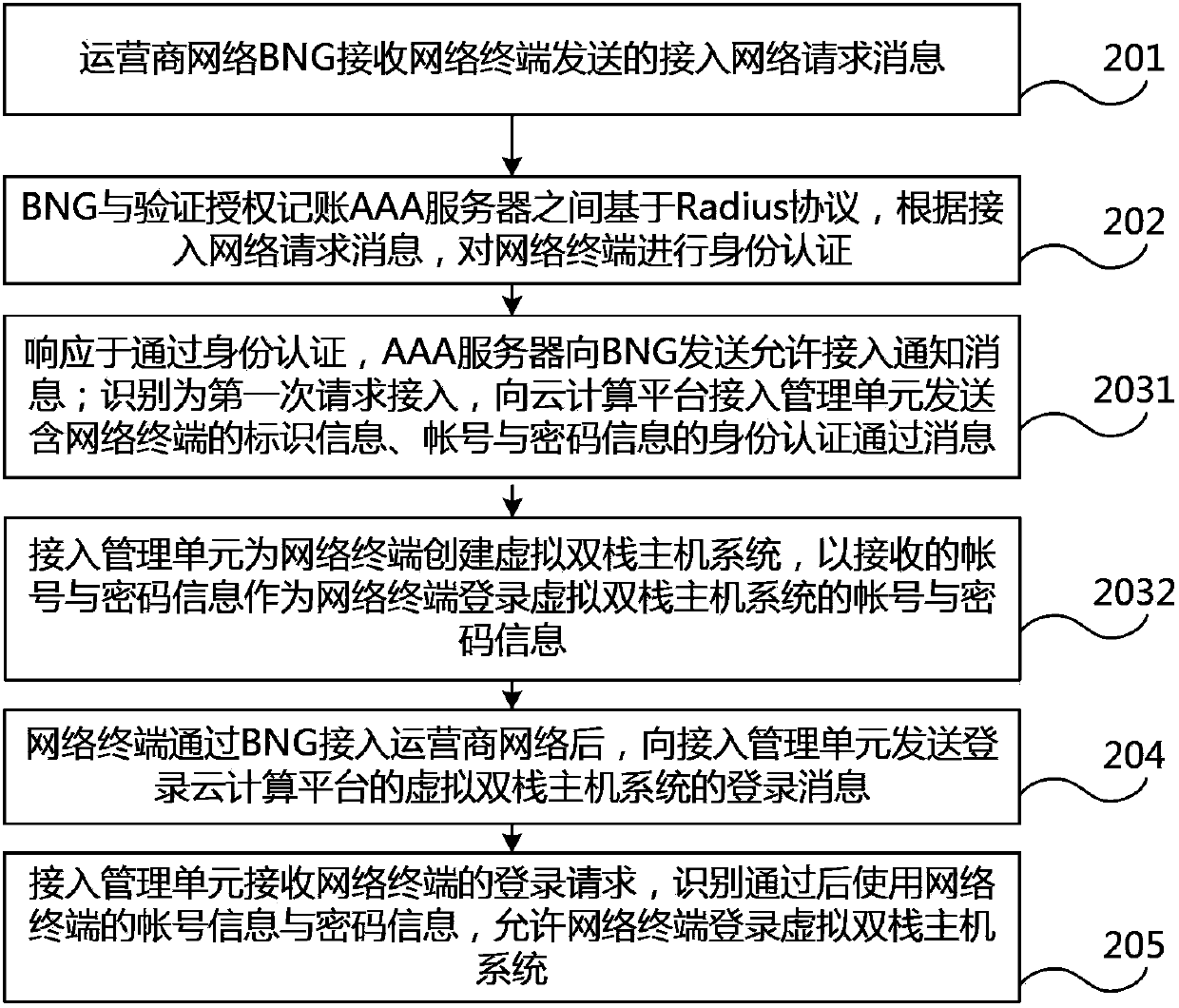
ActiveCN103873449AAvoid secondary authenticationSimplify the certification processNetworks interconnectionNetwork terminationThe Internet
The invention discloses a network access method and a network access system. The network access method comprises the following steps: performing identity authentication on a network terminal based on a Radius protocol through an operator network BNG (broadband network gateway) and an AAA (authentication authorization accounting) server; in response to passing of the identity authentication, sending an identity authentication passing message for the network terminal to an access management unit of a cloud computing platform by the AAA server, so that when the network terminal logs in a virtual dual-stack host system of the cloud computing platform, the access management unit of the cloud computing platform can directly identify the network terminal according to the identity authentication passing message sent by the AAA server, and allows the network terminal to log in the virtual dual-stack host system. According to the technical scheme provided by the invention, secondary authentication on the network terminal caused by isolation between the BNG equipment of a network layer and the cloud computing platform of an application layer is avoided, the authentication flow of a user is simplified, and meanwhile, the user can conveniently access the internet through the virtual dual-stack host system provided by the cloud computing platform.
Owner:CHINA TELECOM CORP LTD
Authentication method and authentication device for user request
InactiveCN104980925ASolve the inconvenience of operationEasy to operateTransmissionSecurity arrangementAuthentication serverApplication software
The invention discloses an authentication method and an authentication device for a user request. The authentication method for the user request comprises the following steps of receiving the user request; authenticating the user request according to authentication information stored in a target application program; when the user request passes the authentication, sending the user request to a server to obtain a response message which responds to the user request; when the user request does not pass the authentication, sending a first refresh request to the server to obtain a second access token; and when the second access token sent by the server is received, sending the first access token included in the user request to the server after replacing to a second access token in order to obtain a response message which responds to the user request. According to the authentication method and the authentication device, the problem of inconvenience for user operation due to a more complicated way for authenticating the user request in the prior art is solved, so that the effects of simplifying an authentication process for the user request and improving the authentication efficiency are achieved.
Owner:走遍世界(北京)信息技术有限公司
Server having an automatic management mechanism
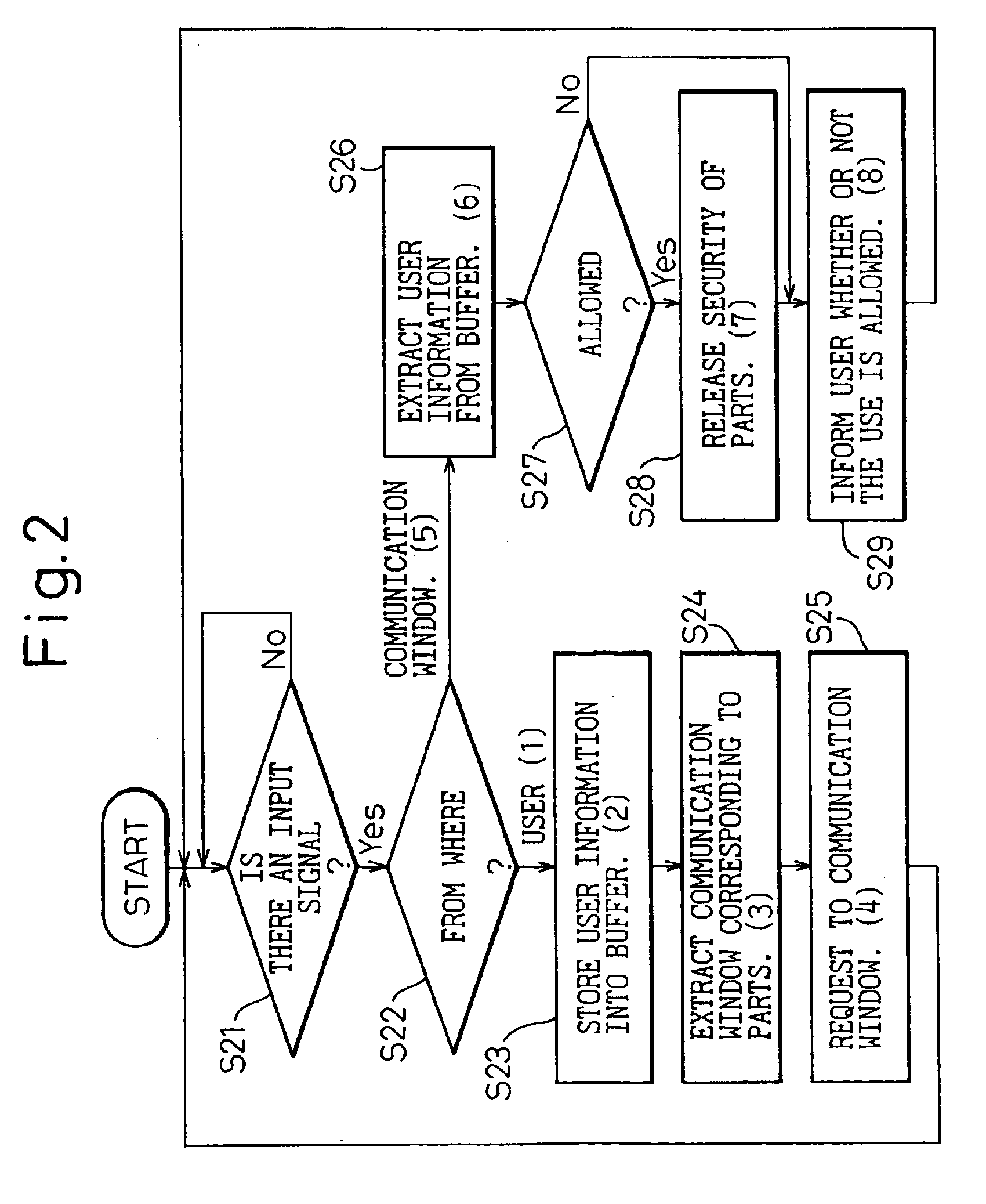
InactiveUS6983262B1Reduce the necessary timeSimplify the certification processProgram control using stored programsDigital data processing detailsSoftware engineeringDocumentation
A server, having an automatic management mechanism, automatically delivers a request for license from a user to a communication window, automatically arranges information such as titles of software parts, keywords of the software parts, etc. in a hierarchical structure, performs a certification only when a user access a web page for which a certification is necessary, or automatically extracts, from a document such as a specification or a manual, an explanation of a software part to be registered, whereby the procedure for arranging images is automated, the process for certification is simplified so that the time necessary for the certification procedure is shortened, and the time necessary for a user to wait until the explanation becomes useable is shortened.
Owner:FUJITSU LTD
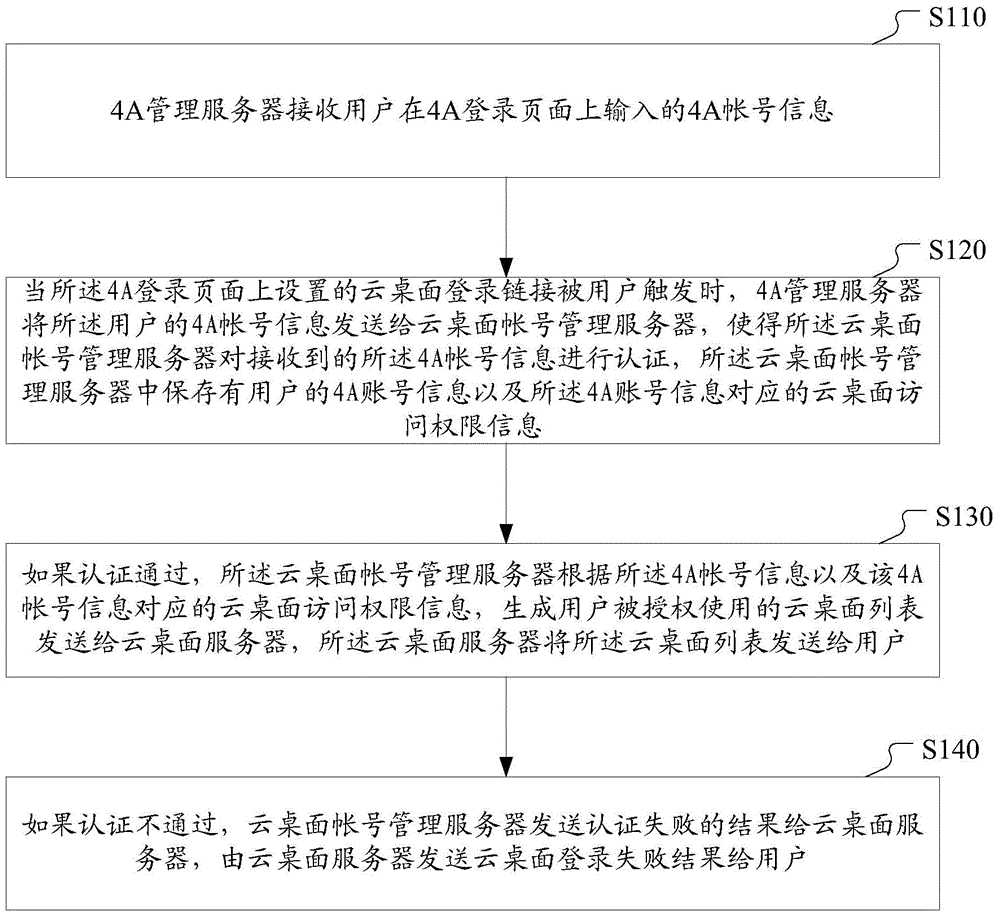
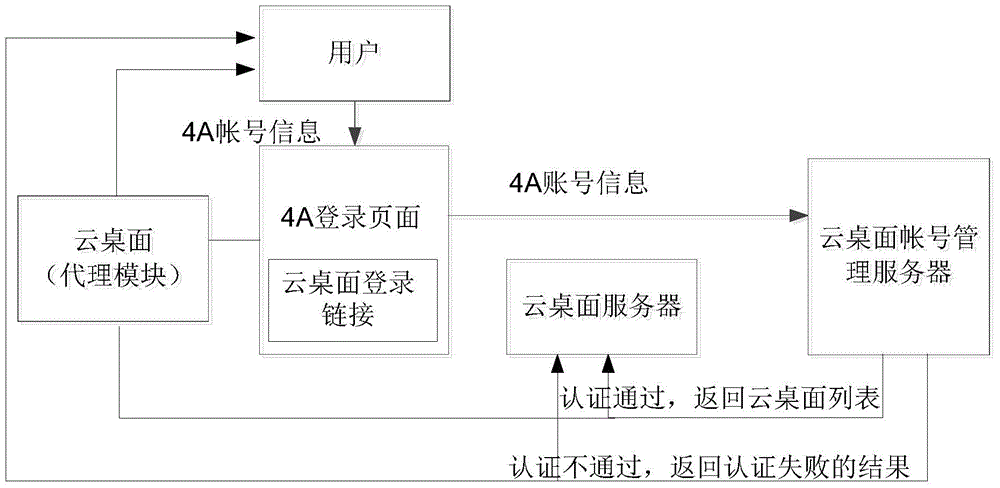
Method and system for logging in cloud desktop
The invention discloses a method and a system for logging in a cloud desktop. The method comprises steps of: receiving 4A account information input by a user on a 4A login page; when a cloud desktop login link is triggered, sending the 4A account information to a cloud desktop account management server so as to allow the cloud desktop account management server to authenticate the received 4A account information; storing the 4A account information of the user and corresponding cloud desktop access authority information on the cloud desktop account management server; if the authentication is passed, according to the 4A account information of the user and the corresponding cloud desktop access authority information, generating a cloud desktop list and sending the cloud desktop list to the cloud desktop server so as to send the cloud desktop list to the user; and the authentication is not passed, sending an authentication failure to the cloud desktop server so as to send a cloud desktop login failure to the user. According to the invention, by carrying out unified management and storage on the 4A account information of the user and the corresponding cloud desktop access authority information, the user is required to only input the 4A account information for authentication once when logging in the cloud desktop, so authentication processes are saved and use experience of the user is improved.
Owner:ULTRAPOWER SOFTWARE
Method and system for identifying wireless mesh network
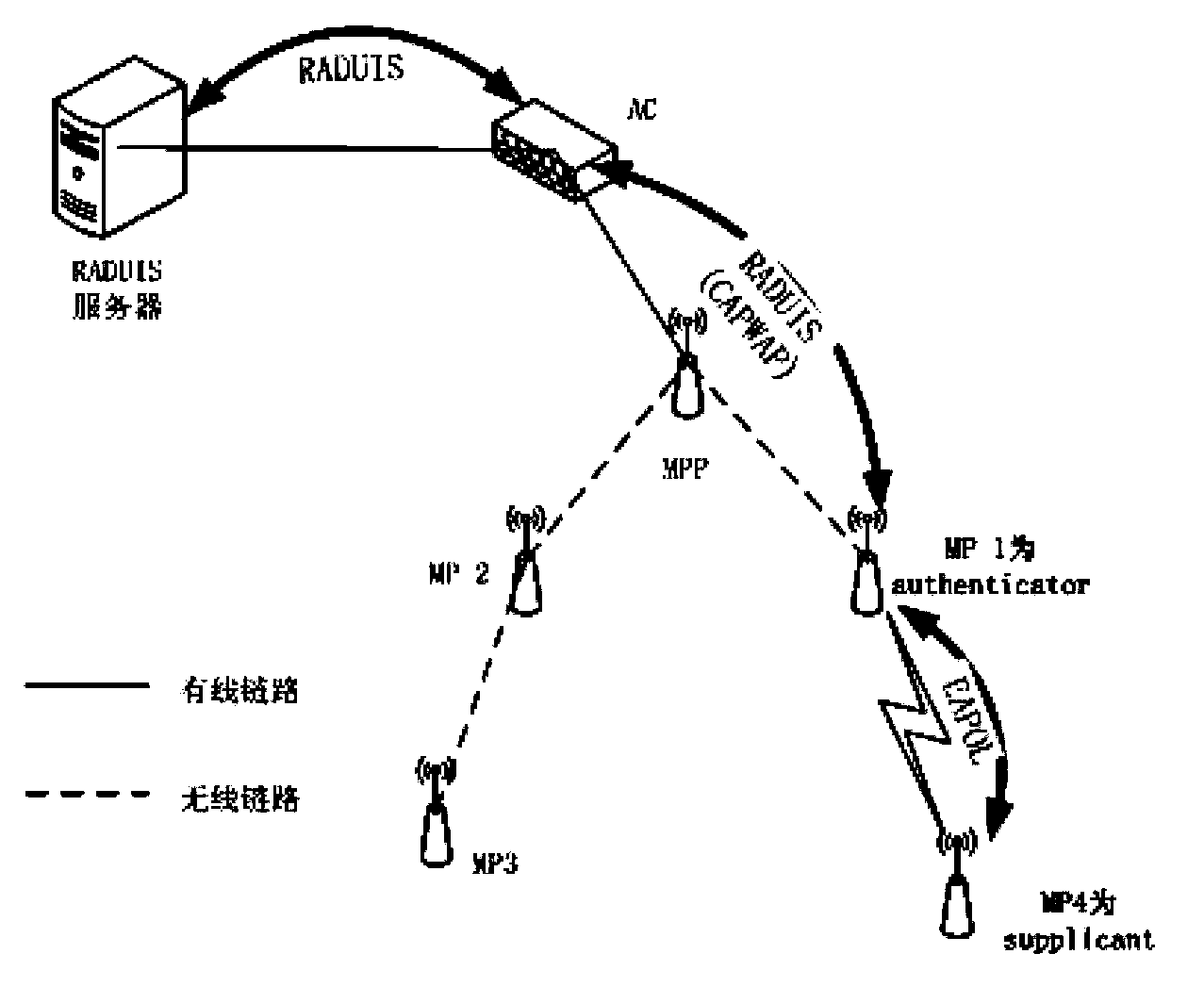
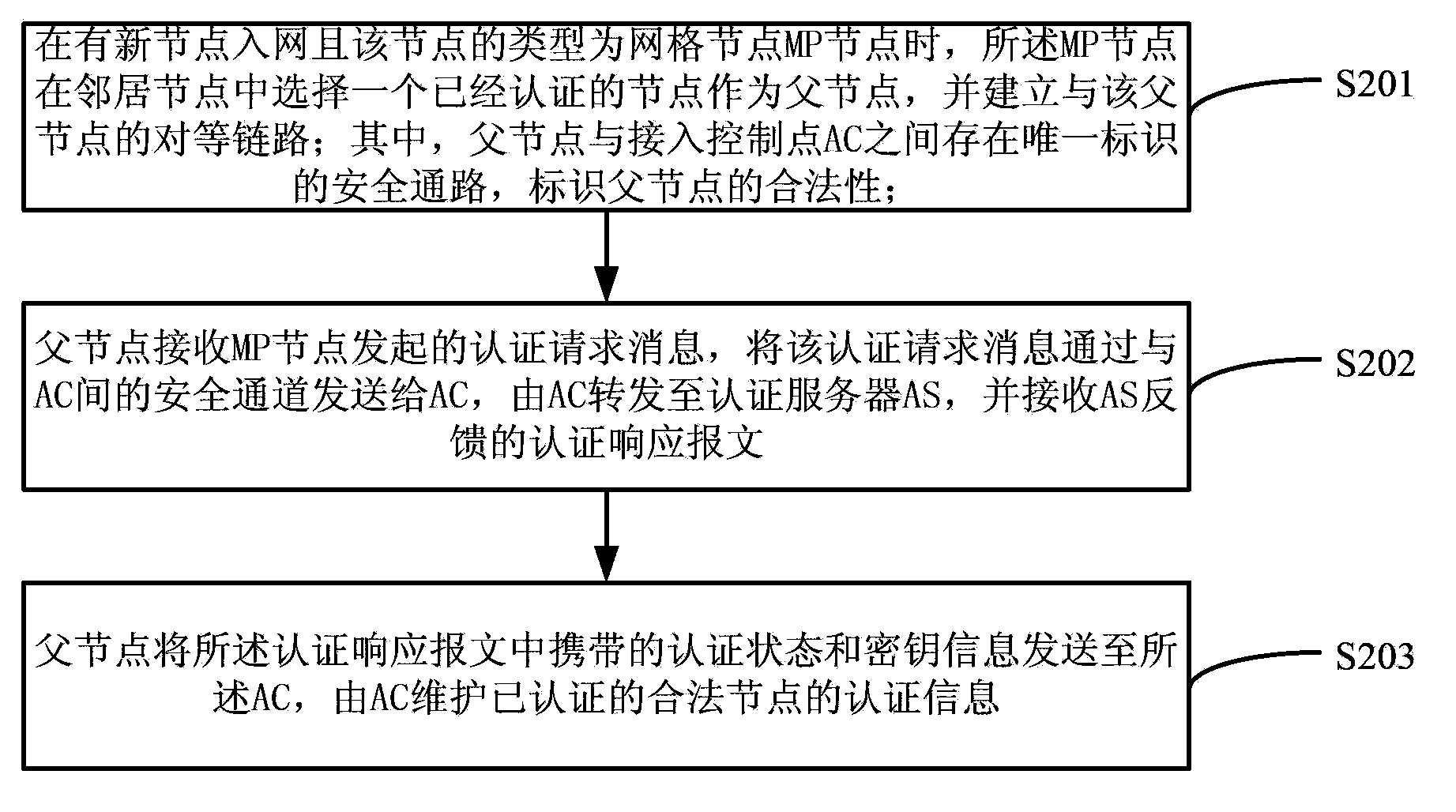
ActiveCN103686709ARealize managementSimplify the certification processNetwork topologiesConnection managementWireless mesh networkWireless grid
The invention discloses a method and a system for identifying a wireless mesh network. The method comprises the following steps: an MP node selects an identified node as a father node when a new node is accessed into the network and the node is a grid node MP node; a solely marked safe passage exists between the father node and AC; the MP node identifies by using the father node as an identification point; an identification message is transmitted to the AC through the safe passage between the father node and the AC and then transferred to AS by the AC; in the same way, a return message of the AS is transferred to the father node by the AC through the safe passage; the MP node is identified; the identification information is simultaneously stored on the AC so as to identify the MP node for the second time. By adopting the method and the system which are disclosed by the invention, the problem that the access delay is increased because the identification mode adopted in the prior art is fussy is solved.
Owner:ZTE CORP
Identity authentication system and method based on identifiers
ActiveCN104202170AReliableEnsure safetyUser identity/authority verificationDigital signatureTerminal equipment
The invention relates to the field of information security, particularly to security authentication system and method when an intelligent device receives a control command and discloses an identity authentication system based on identifiers. The identity authentication system comprises a client, a private key generation server and at least one terminal device. The client is used for generating a public key to identify a user and controlling digital signatures of the control commands of the terminal devices to generate signing messages; the private key generation server is used for generating a private key and a public parameter. Each terminal device is internally provided with an authentication module based on identifiers and certificating the control command according to the public parameter and the public key. According to the arrangement, IBC (identity-based cryptography) modules are arranged in the terminal devices, allowing the control commands received by the terminal devices to be more reliable and safe; bad effects, caused by the fact that the terminal devices receive the wrong commands, are avoided; once the faults occur to the terminal devices, the causes of the problems can be rapidly found, and effective measures are taken.
Owner:SHANGHAI PEOPLENET SECURITY TECH
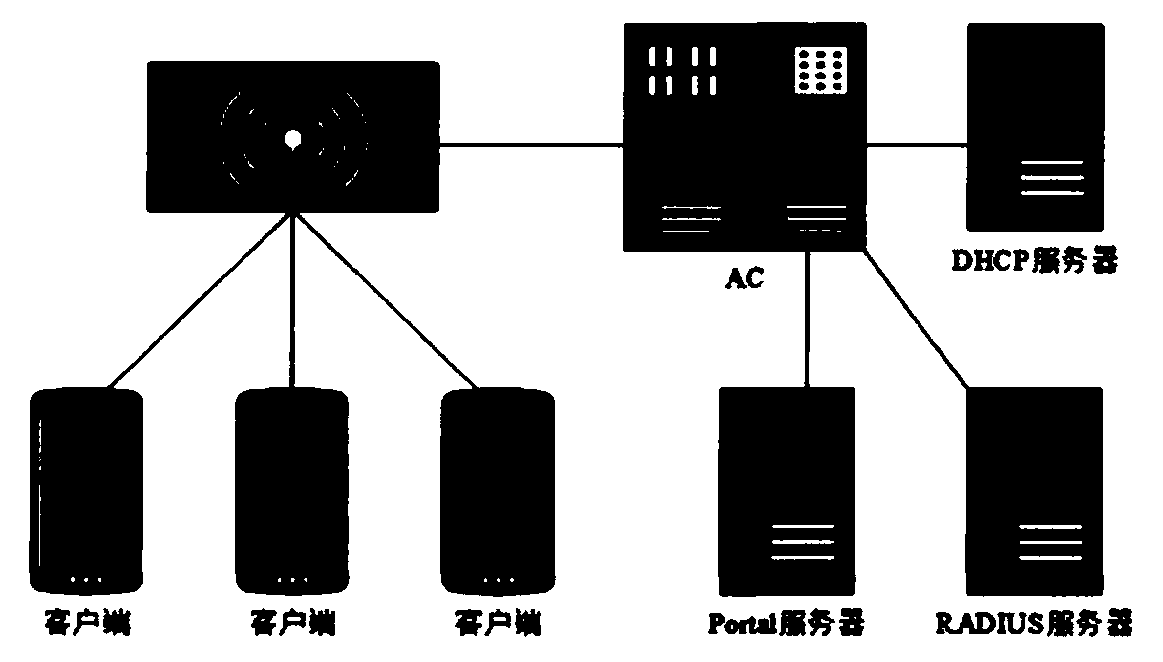
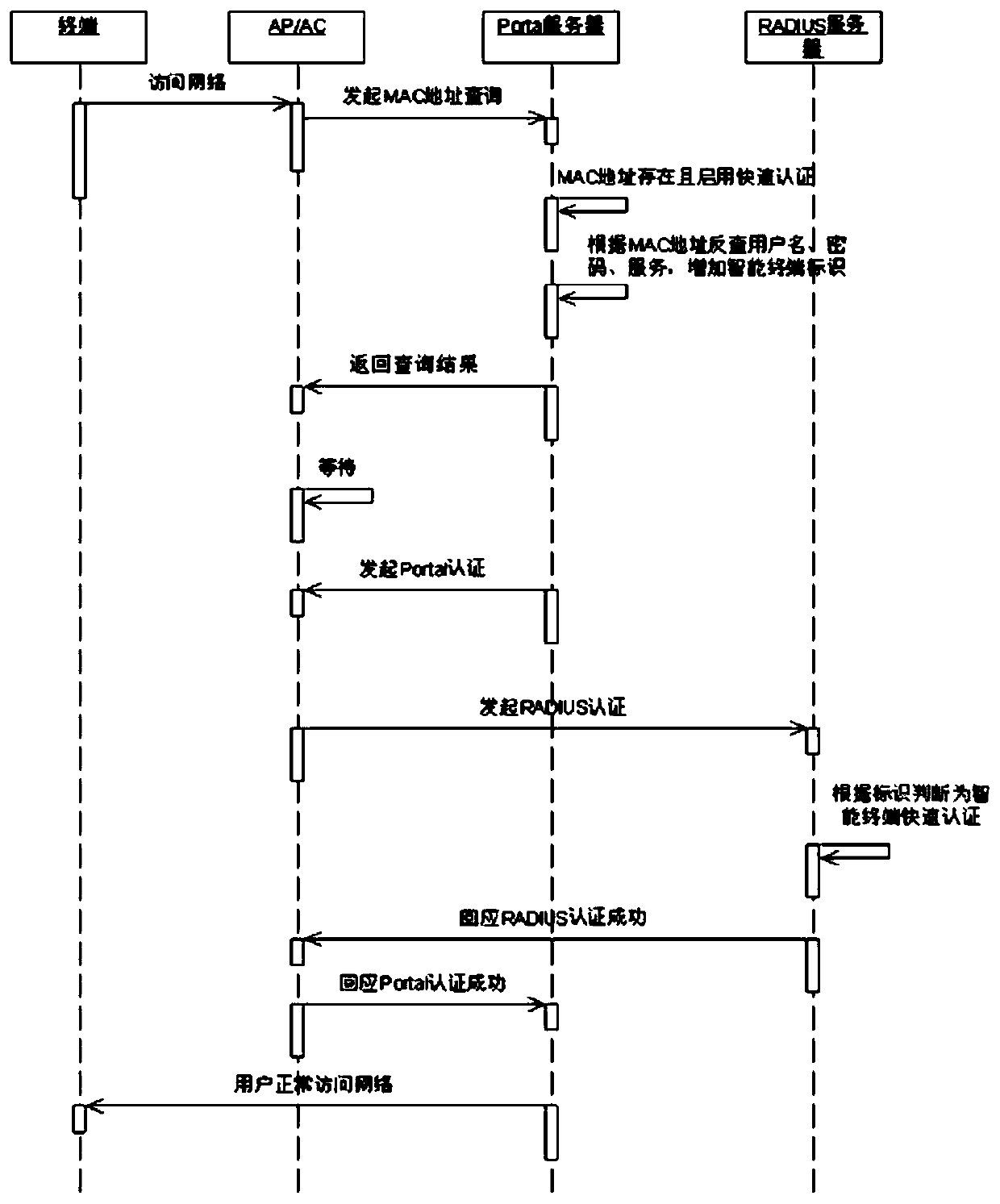
Wireless local area network non-perception control method and system and readable storage medium
InactiveCN109862565ASimplify the certification processImprove and enhance the user experienceNetwork topologiesSecurity arrangementPattern perceptionWireless gateway
The invention relates to a wireless local area network non-perception control method and system and a readable storage medium. The method comprises the steps that a wireless gateway receives access request information; the wireless gateway generates MAC address query information according to the access request information; the MAC address query information is sent to a Portal server; the Portal server queries whether the MAC address information is recorded or not; and if the MAC address information is recorded, authentication success information is returned to the wireless gateway, and a wireless link of an access address is established. According to the invention, the authentication information is automatically authenticated in the secondary login process of the user; on one hand, the management level and the information security protection level of the wireless local area network are enhanced; on the other hand, the problem of non-perception authentication is solved through binding of AD domain accounts, so that the authentication process of the user is simplified, the use experience of the user is improved, a better wireless local area network service is provided for the user, and the user can use the wireless local area network service more conveniently, quickly and freely.
Owner:GUANGDONG URBAN & RURAL PLANNING & DESIGN INST
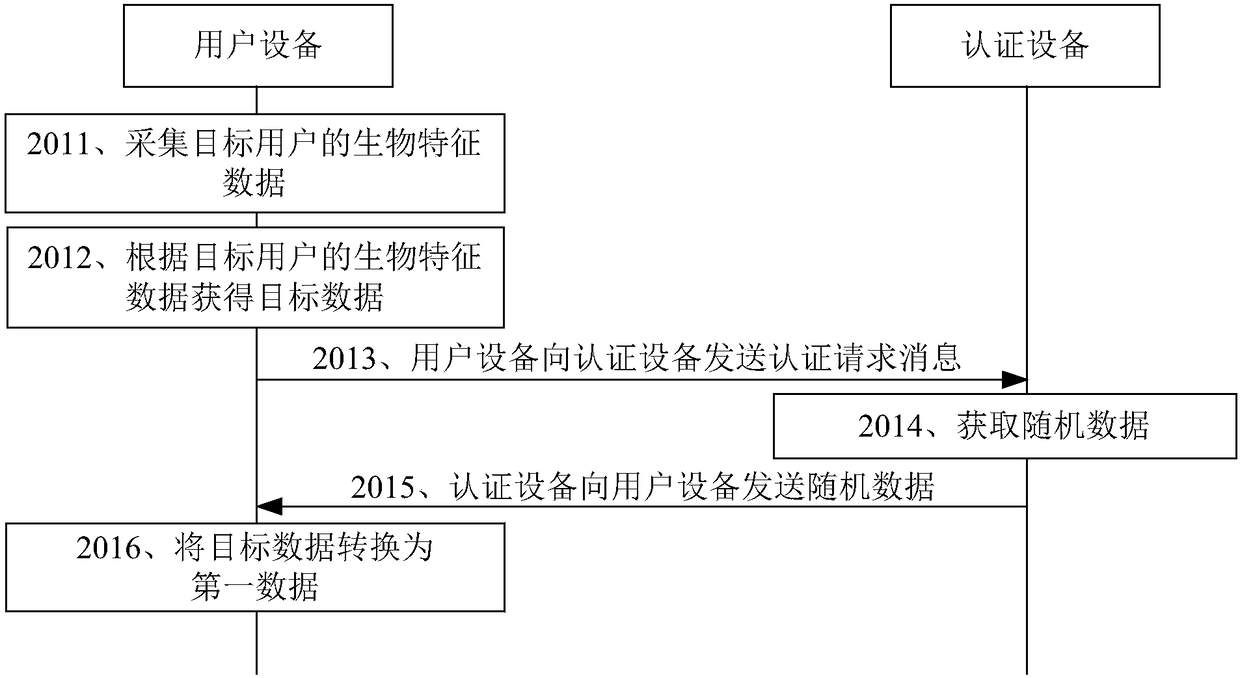
Authentication method and authentication equipment for implementing network access, and user equipment
ActiveCN108810891ASimplify the certification processImprove usabilityTransmissionMultiple biometrics useBiometric dataUsability
The invention discloses an authentication method and authentication equipment for implementing network access, and user equipment, and belongs to the technical field of communication. The method is applied to the authentication equipment. The method comprises the steps as follows: the authentication equipment receives an authentication response message sent by the user equipment, wherein the authentication response message comprises first data, and the first data is the data acquired by the user equipment according to biological characteristic data of a target user; then the authentication equipment acquires second data from a server, wherein the second data is the data acquired by the server based on the biological characteristic data of the user; when the first data is the same as the second data, the authentication equipment generates an indication message that is used for indicating the user equipment that authentication is successful; and then the authentication equipment sends the indication message to the user equipment. According to the method and equipment provided by the invention, the problems that the authentication process of network access is relatively complex, the network is relatively poor in usability and the security is relative poor are solved, the authentication process of network access is simplified, and the network usability and security are improved.
Owner:HUAWEI TECH CO LTD
VoWiFi business achieving method, system and AAA server
ActiveCN106686589ASolve wasteReduce Authentication LatencyTransmissionSecurity arrangementData streamDigest access authentication
The invention discloses a VoWiFi business achieving method, system and an AAA server. The method comprises the steps that the EAP-AKA authentication requests initiated by UE are verified by the AAA server, if the verification is passed, a first authentication success information is returned to the UE and the EAP-AKA authorized authentication success information of the UE is saved; the IKE-Auther-Request information initiated by the UE is verified by the AAA server, if the EAP-AKA authorized authentication success information of the UE is saved in the AAA server, the verification is passed. The VoWiFi business achieving method, system and the AAA server can avoid the problem of a second time billing of the WiFi data stream and the VoWiFi voice data stream and the WiFi business stream passing through the P-GW device twice, through the saving of the EAP-AKA authorized authentication success information of a user on 3GPP-AAA at the time of crediting the WiFi access authentication, a second time EAP-AKA authentication is no longer needed when the S2b is being authenticated, and the time delay and the system computation amount at the authentication of the user are effectively reduced.
Owner:CHINA TELECOM CORP LTD
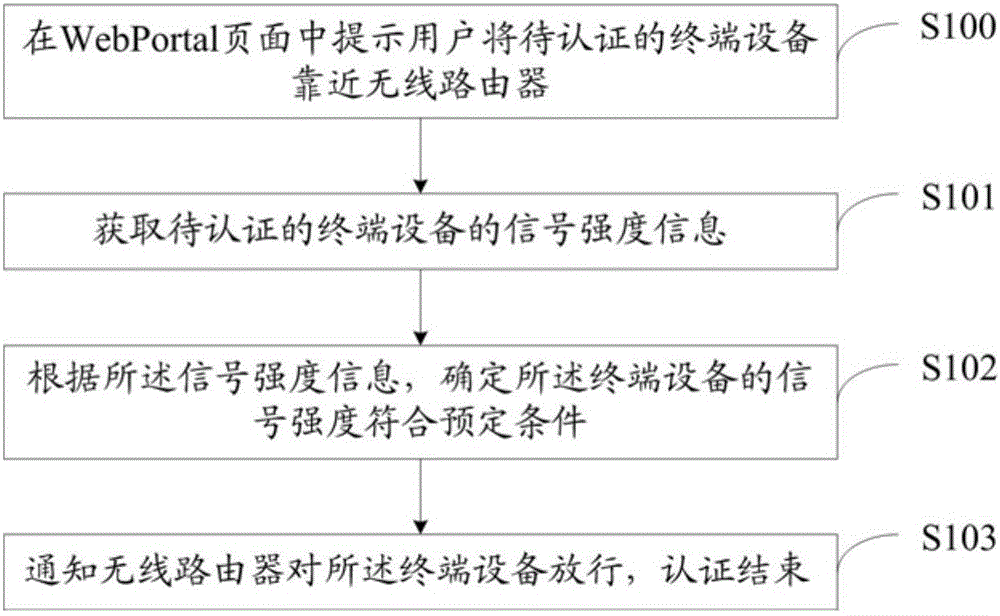
Portal authentication method, Portal authentication device and Portal authentication system based on signal strength
The invention discloses a Portal authentication method, a Portal authentication device and a Portal authentication system based on signal strength, belonging to the field of wireless communication. The method comprises the steps of acquiring signal strength information of terminal equipment to be authenticated, determining that the signal strength of the terminal equipment meets predetermined conditions according to the signal strength information, and notifying a wireless router to release the terminal equipment, thus ending authentication. The predetermined conditions can be conditions which can be met only by indoor visitors. Thus, only when the terminal equipment meets the predetermined conditions, identity authentication can be completed to get the access to Internet. Ordinary network squatters (illegal users) are generally unable to meet the predetermined conditions, so identity authentication fails to be completed. Compared with the prior art, the method, the device and the system are characterized in that password leak is prevented, authentication is simple, and the network is prevented from being squatted.
Owner:北京必虎科技股份有限公司
Identity authentication method, terminal and server
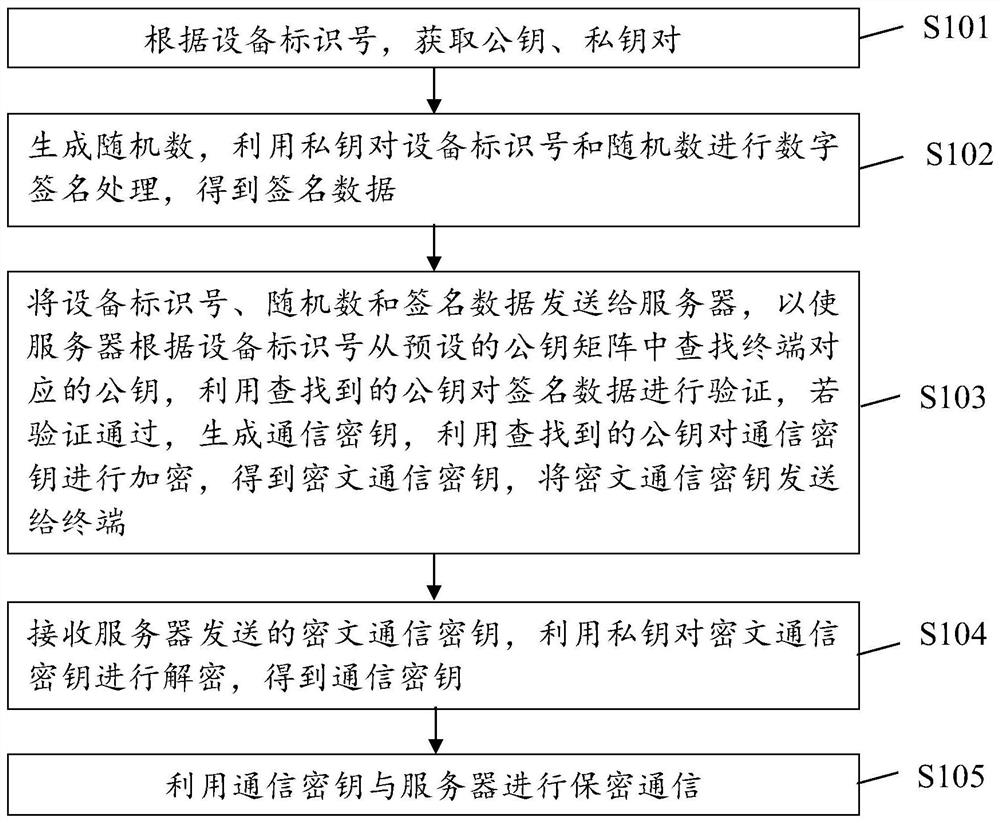
ActiveCN112291190AAchieving Lightweight AuthenticationImplement identity authenticationKey distribution for secure communicationUser identity/authority verificationDigital signatureCiphertext
One or more embodiments of the present specification provide an identity authentication method, a terminal and a server. The terminal obtains a public key and a private key pair according to a deviceidentification number, generates a random number, and performs digital signature processing on the device identification number and the random number by using a private key to obtain signature data, and sends the device identification number, the random number and the signature data to a server, so that the server searches a public key corresponding to the terminal from a preset public key matrixaccording to the device identification number, verifies the signature data by using the searched public key, generates a communication key if the verification is passed, encrypts the communication keyby using the searched public key, obtains a ciphertext communication key, sends the ciphertext communication key to the terminal, receives a ciphertext communication key sent by the server, decryptsthe ciphertext communication key by using the private key to obtain a communication key, and performs secret communication with the server by using the communication key. According to the embodiment of the invention, identity authentication between the terminal and the server can be realized, and the authentication process is relatively simple.
Owner:国网思极网安科技(北京)有限公司 +4
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com