Data security authentication transmission method and device for Internet of Things terminal
An Internet of Things terminal and data security technology, applied in the field of network security, can solve problems such as lack of scale, large maintenance, and practical operation difficulties, and achieve interactive authentication and data encryption, reduce storage resource consumption, and reduce bandwidth the effect of consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
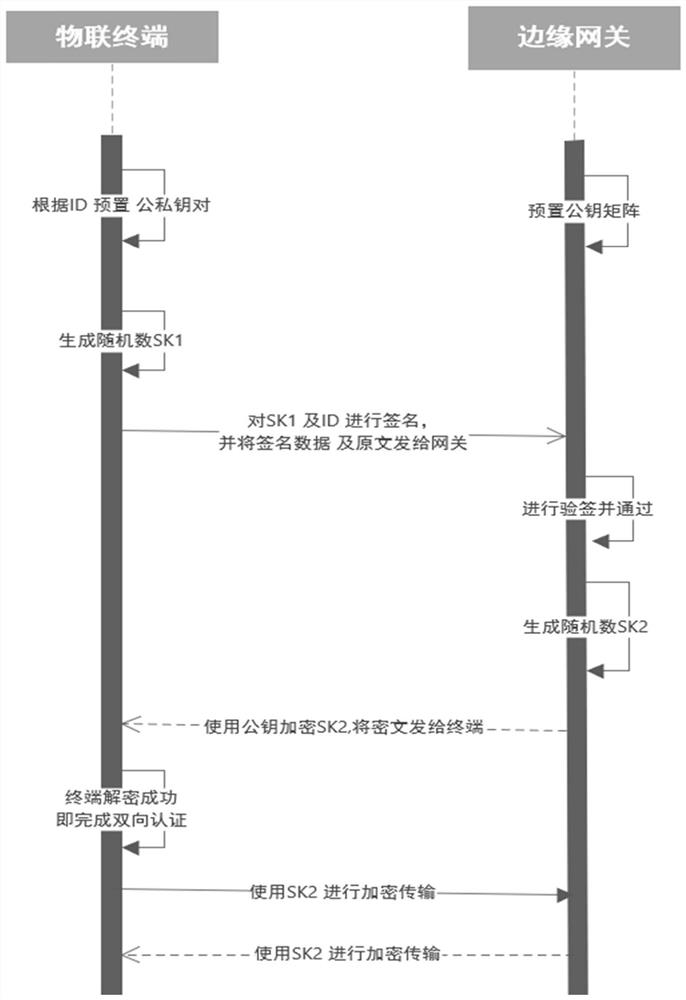
[0040] The technical content of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0041] In order to enable those skilled in the art to better understand the present invention, some technical terms appearing in the embodiments of the present invention are explained as follows:
[0042] Host computer software "preset key tool": a dedicated customized production tool for batch, automatic, and graphical realization of key presetting work for client devices. The main body of the tool is an .exe executable client program.
[0043] CPK: Combined Public Key, combined public key authentication technology.
[0044] SM2: In 2012, the State Cryptography Administration publicly released the asymmetric cryptographic algorithm that became the standard of the national cryptographic industry.
[0045] SM4: In 2012, the State Encryption Administration publicly released the symmetric encryption algorithm t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com