Voice interaction method, device, system and equipment for protecting privacy and storage medium
A technology for privacy protection and voice interaction, applied in voice analysis, transmission systems, electrical components, etc., can solve problems such as poor protection of user privacy, disclosure of privacy by drivers and passengers, and no protection for content information, etc. Risk, avoiding being leaked, and protecting privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
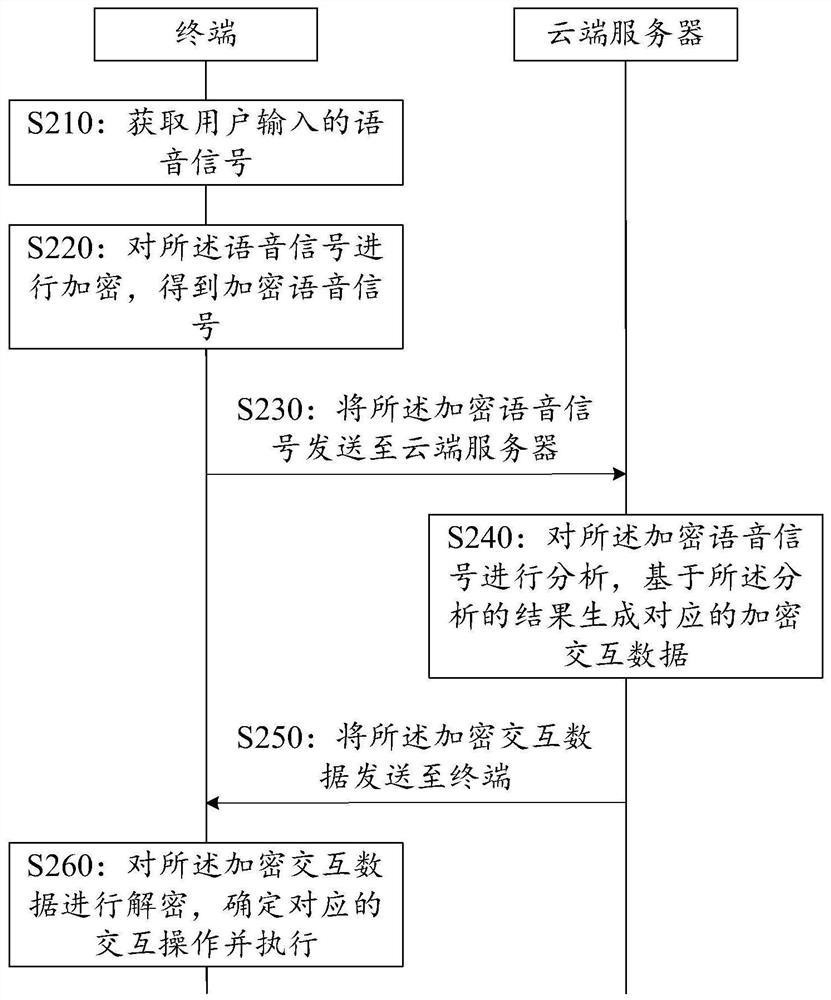
[0068] Reference manual attached figure 2 , which shows the flow of a privacy-preserving voice interaction method provided by an embodiment of the present invention, which can be applied to figure 1 In the implementation environment shown, specifically as figure 2 As shown, the method may include the following steps:
[0069] S210: The terminal acquires a voice signal input by the user.
[0070] In the embodiment of the present invention, the terminal may be provided with a voice collection module for collecting the voice input by the user to obtain the voice signal. Wherein, the voice collection module can be a sound sensor, a microphone, etc., and the voice signal can include information such as the user's voice characteristics and voice content, and the voice characteristics can include the user's voiceprint characteristics, age characteristics, gender characteristics, and health characteristics. Features, etc., the voice content may include instruction information iss...
Embodiment 2
[0133] Reference manual attached Figure 5 , which shows the flow of a privacy-preserving voice interaction method provided by another embodiment of the present invention, which can be applied to figure 1 In the cloud server 120 in, specifically as Figure 5 As shown, the method may include the following steps:
[0134] S510: Acquire an encrypted voice signal sent by the terminal, where the encrypted voice signal is obtained by the terminal encrypting a voice signal input by a user.
[0135] S520: Analyze the encrypted voice signal, and generate corresponding encrypted interaction data based on a result of the analysis.
[0136] Optionally, analyzing the encrypted voice signal, and generating corresponding encrypted interaction data based on a result of the analysis may include:
[0137] performing speech recognition on the encrypted speech signal to obtain corresponding encrypted speech text;
[0138] Performing semantic analysis on the encrypted speech text to obtain cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com