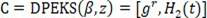Supervisable data privacy sharing method based on end-side cloud collaboration
A data privacy, end-to-end technology, applied in the field of edge computing technology and blockchain, can solve problems that are not conducive to data privacy protection, and achieve the effect of protection from being leaked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
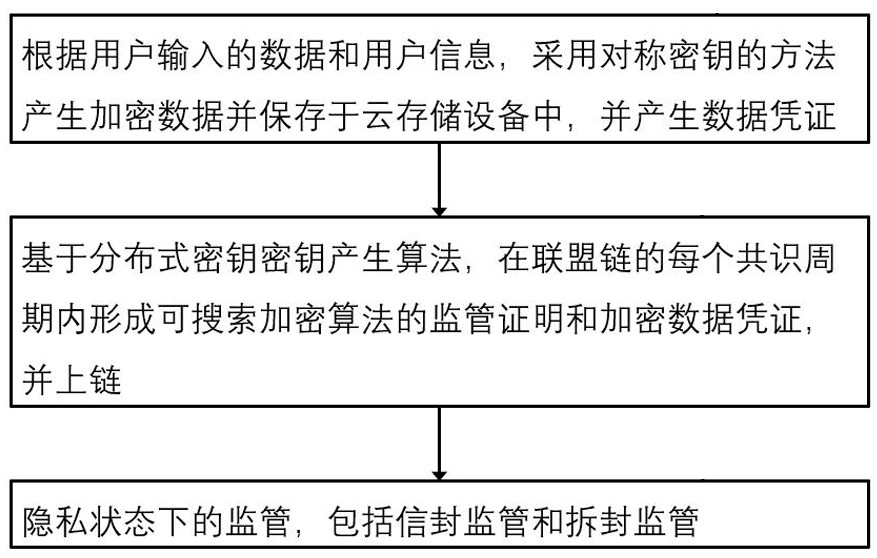
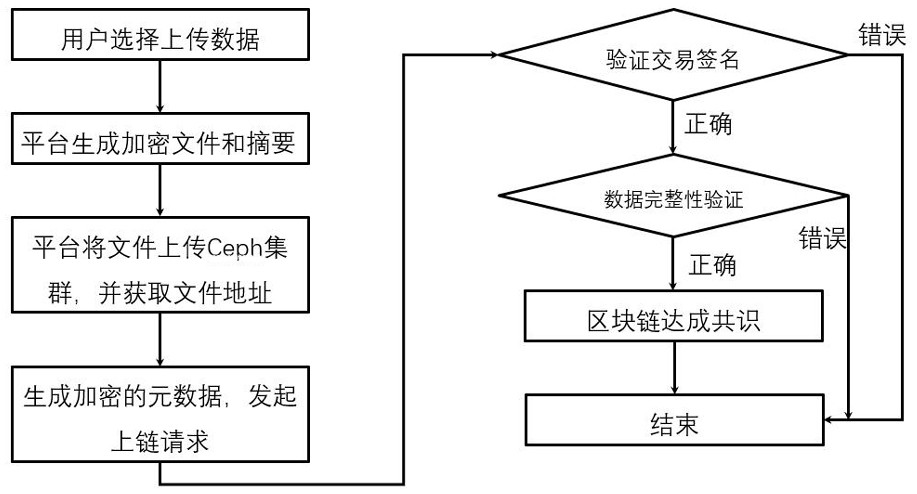
[0047]Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. It should be understood that the specific embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
[0048] Traditional physical storage has problems such as resource dispersal and storage reliability cannot be guaranteed. Storage virtualization refers to the mapping of various scattered and heterogeneous storage devices into a logical storage space with unified and continuous addressing according to certain strategies, called It is a virtual storage pool and provides the access address of the virtual storage pool to the application system. Storage virtualization improves the reliability and availability of data through technologies such as data mirroring, data verification, and multipathing.
[0049] The Ceph cluster is the data storage part in this embodiment,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com