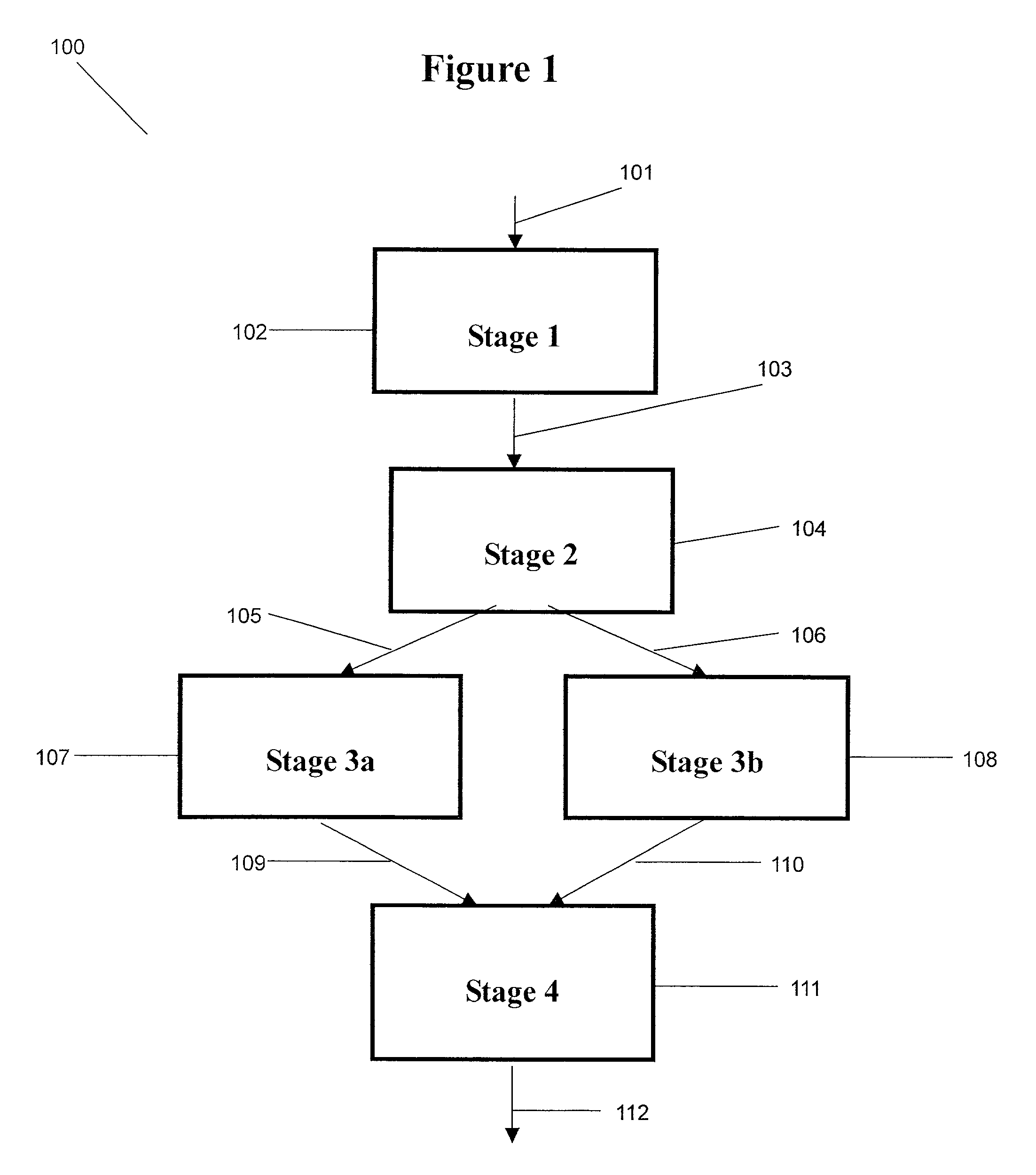
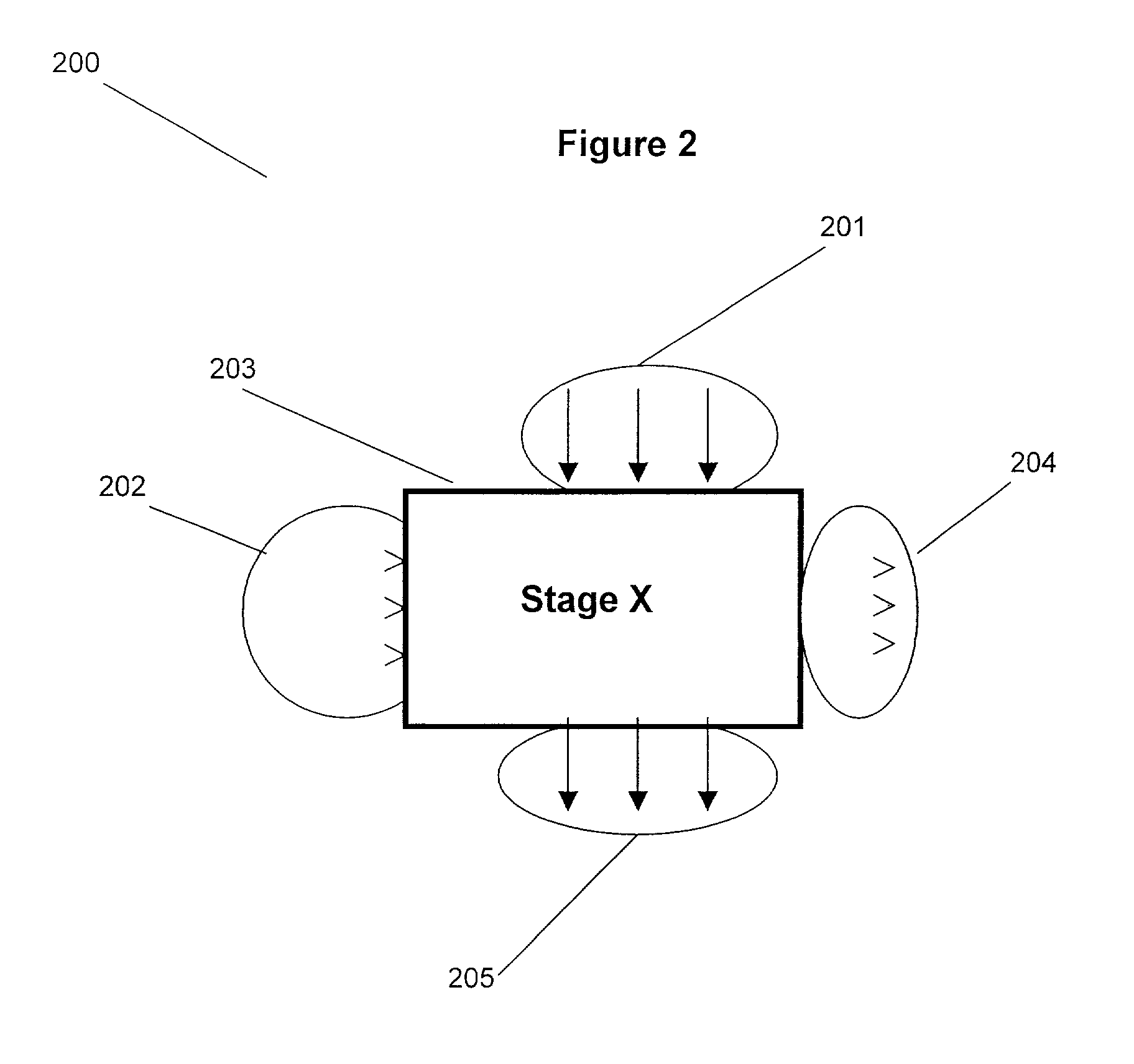
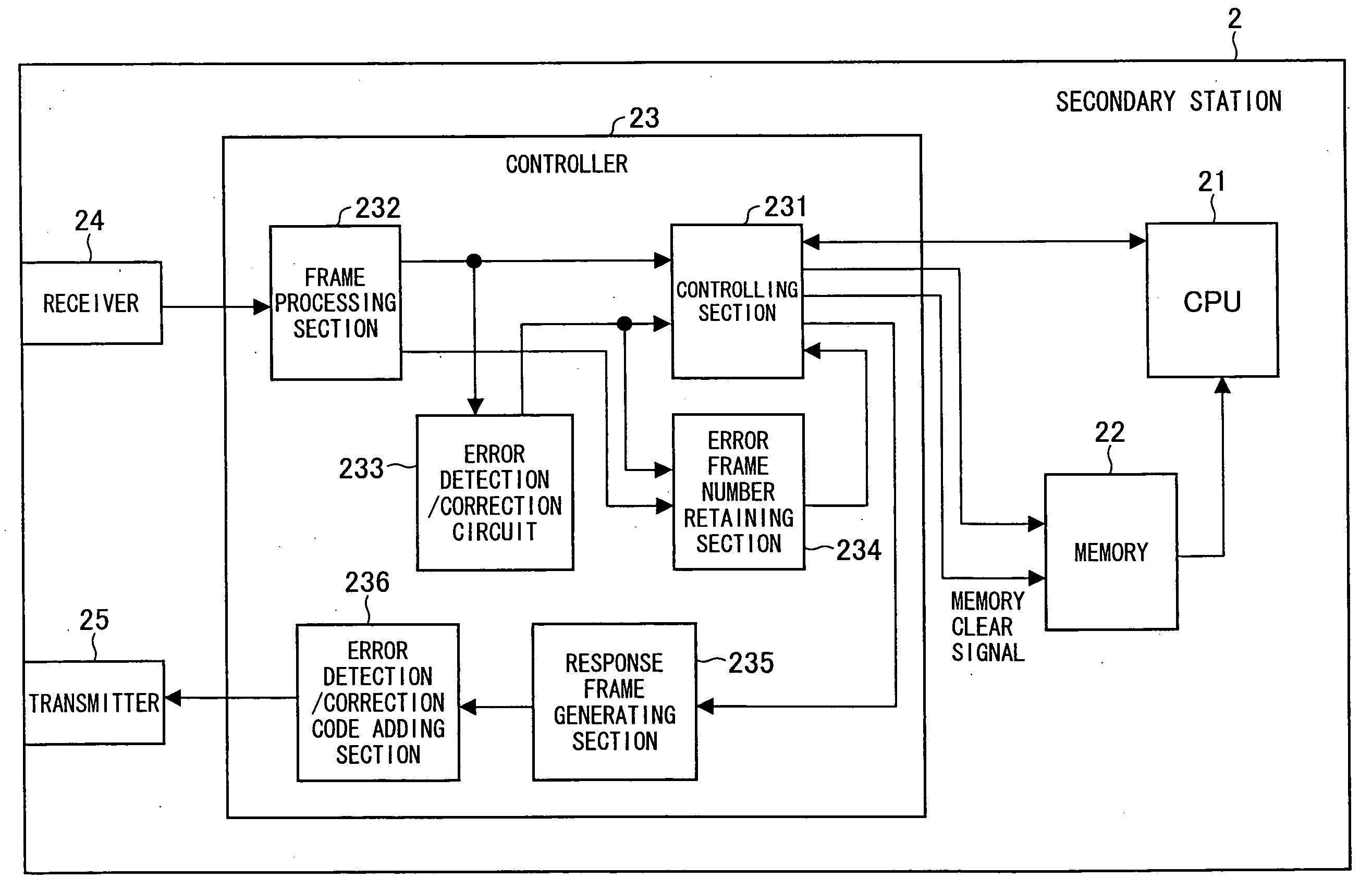
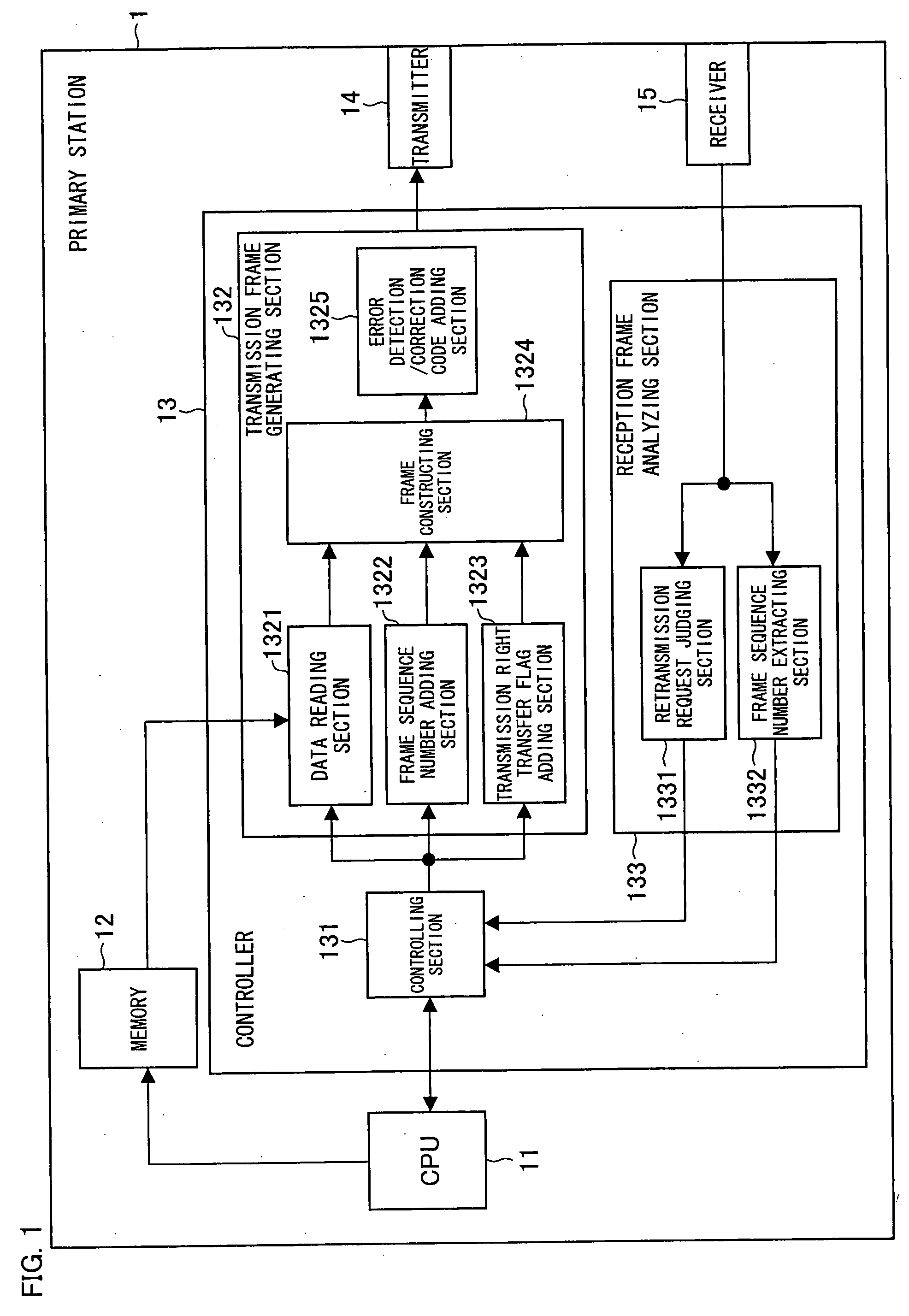
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
275 results about "SequenceNumber" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
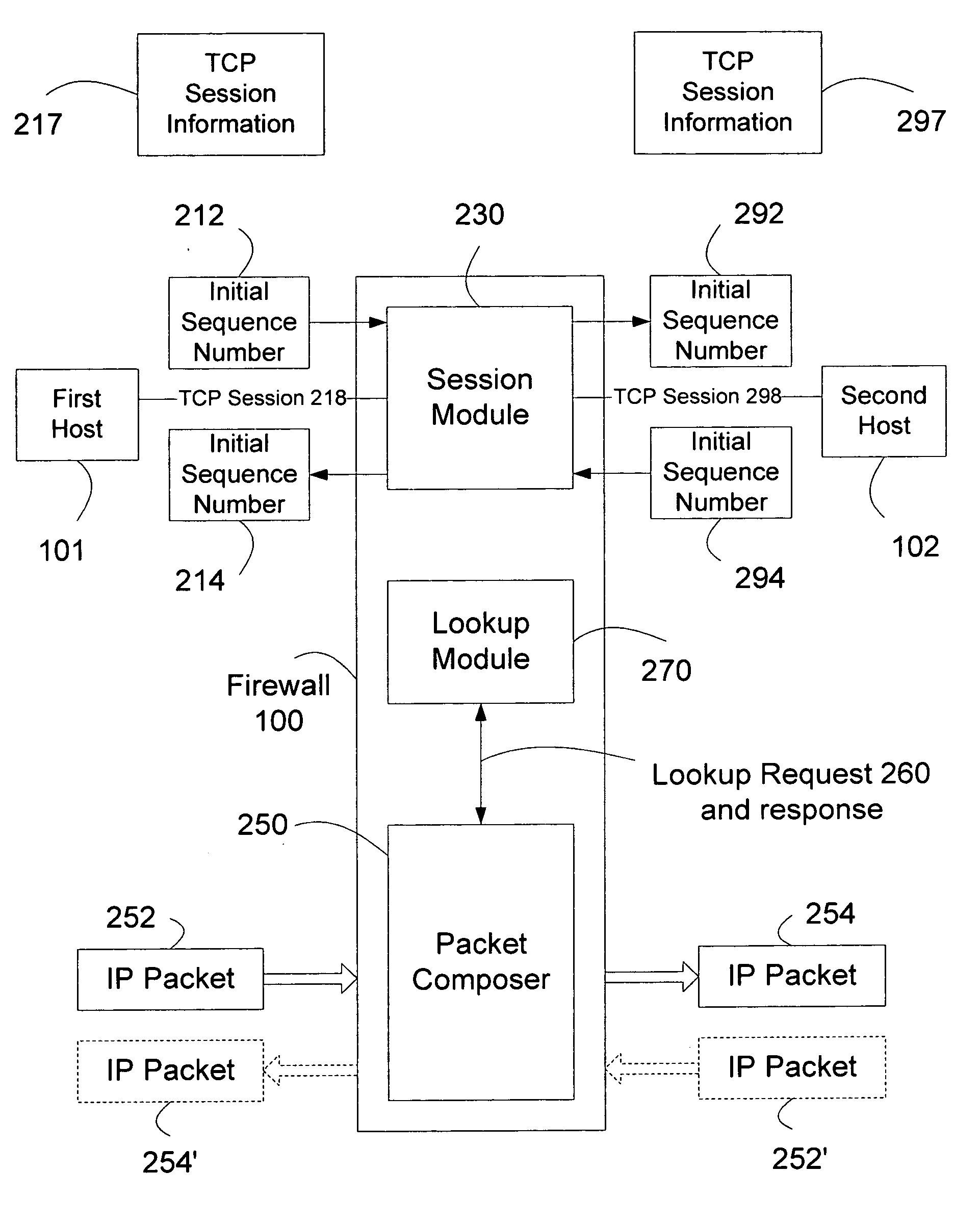
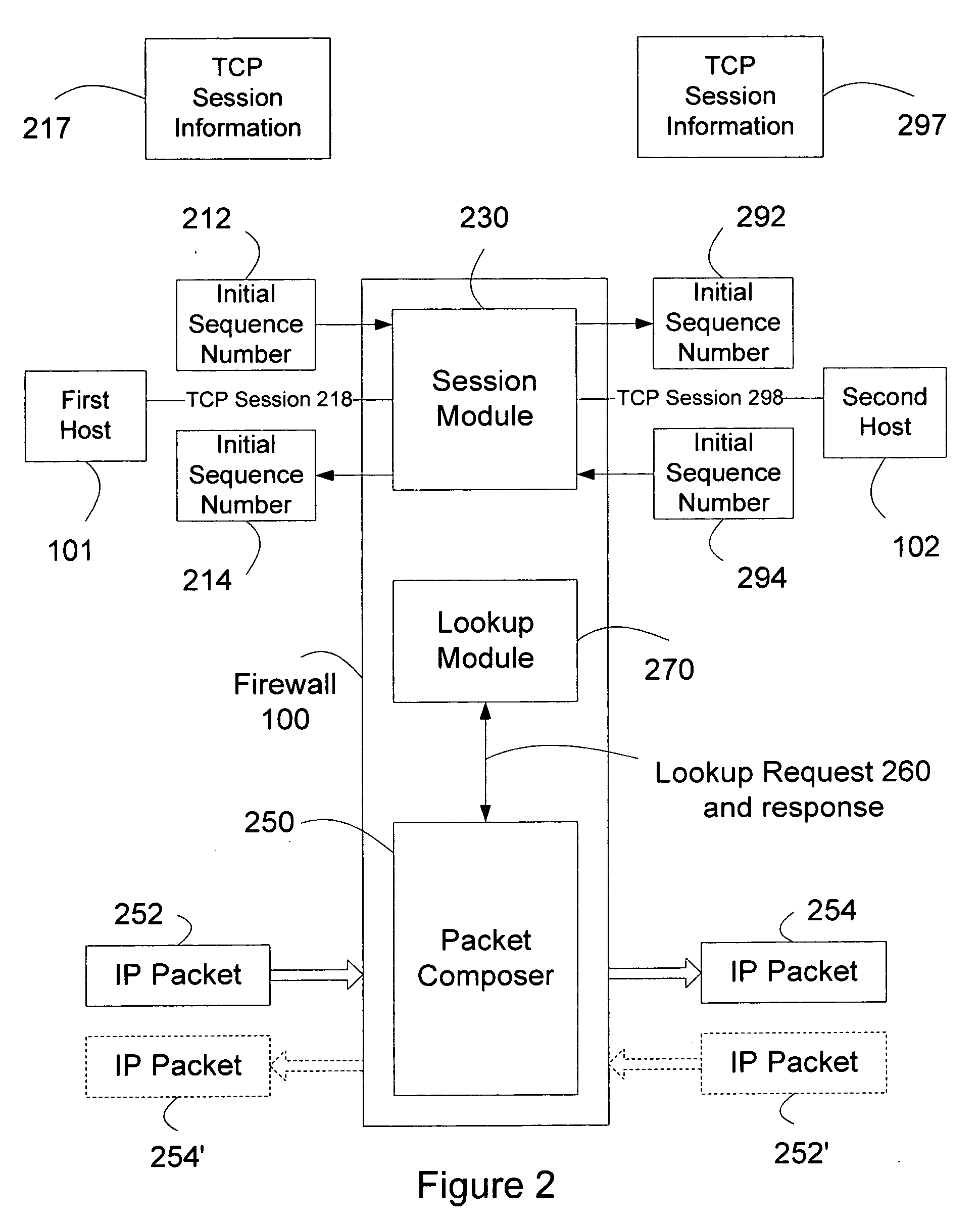
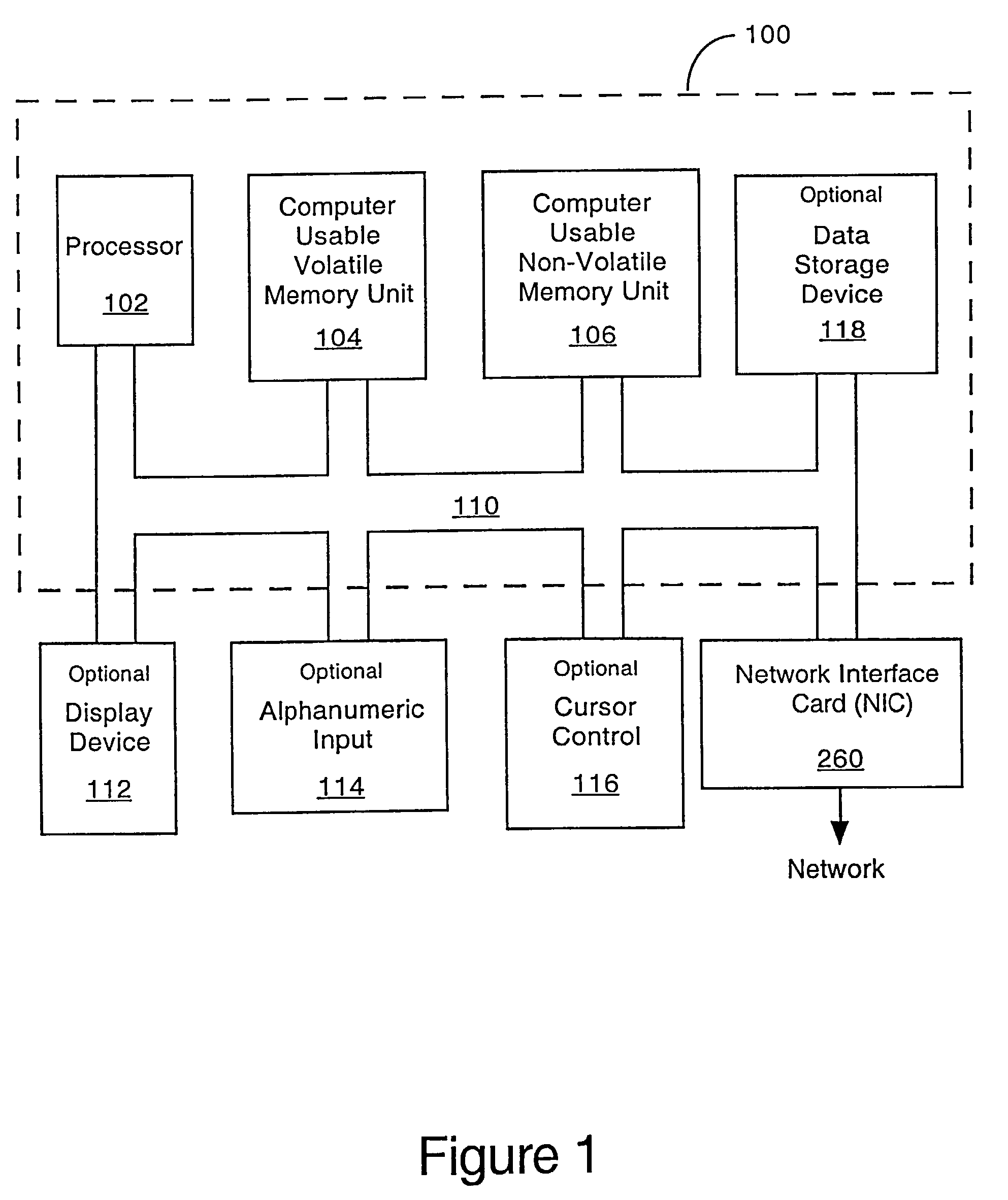
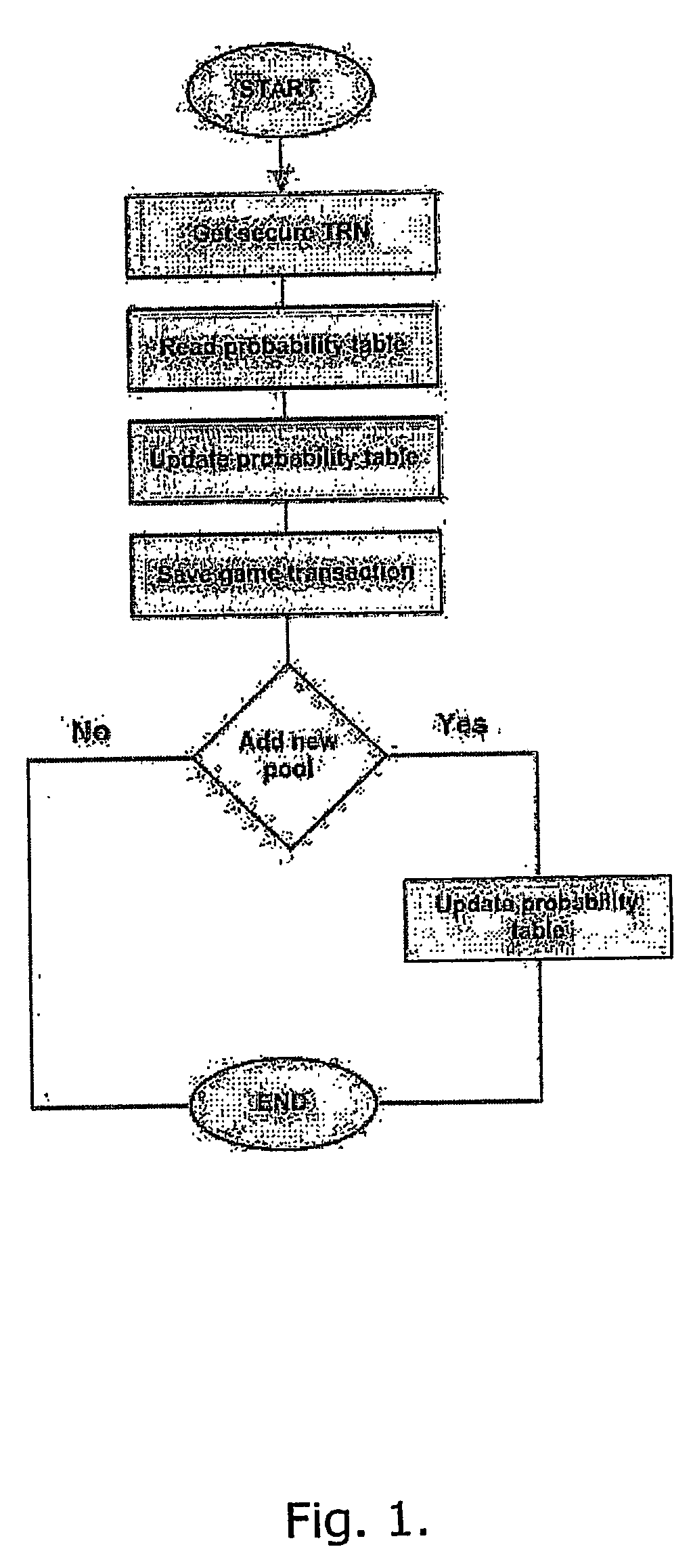
Sequence number based TCP session proxy
InactiveUS20070283429A1High speed communicationReduces commitmentMultiple digital computer combinationsProgram controlNetwork packetByte
In a computer communication network including a firewall which protects a secured host against attack from outside computers, the host communicating with an outside computer, through the firewall, via data packets which include byte sequence numbers. In a communication between the host and computer in which one of them acts as a source and the other as a destination for the communication, a sequence number offset is derived by the firewall which characterizes the byte sequence number received from the source and the byte sequence number the firewall will provide to the destination for that communication. In a communication received from the source, the firewall adds the offset to byte sequence numbers in a packet passing between the source and destination, in order to determine the byte sequence numbers it will provide to the destination. Thus, proper sequence numbers can be provided to both locations, without the firewall having to restructure packets. This speeds communication between the source and destination and substantially reduces the commitment of processing and storage resources.
Owner:A10 NETWORKS
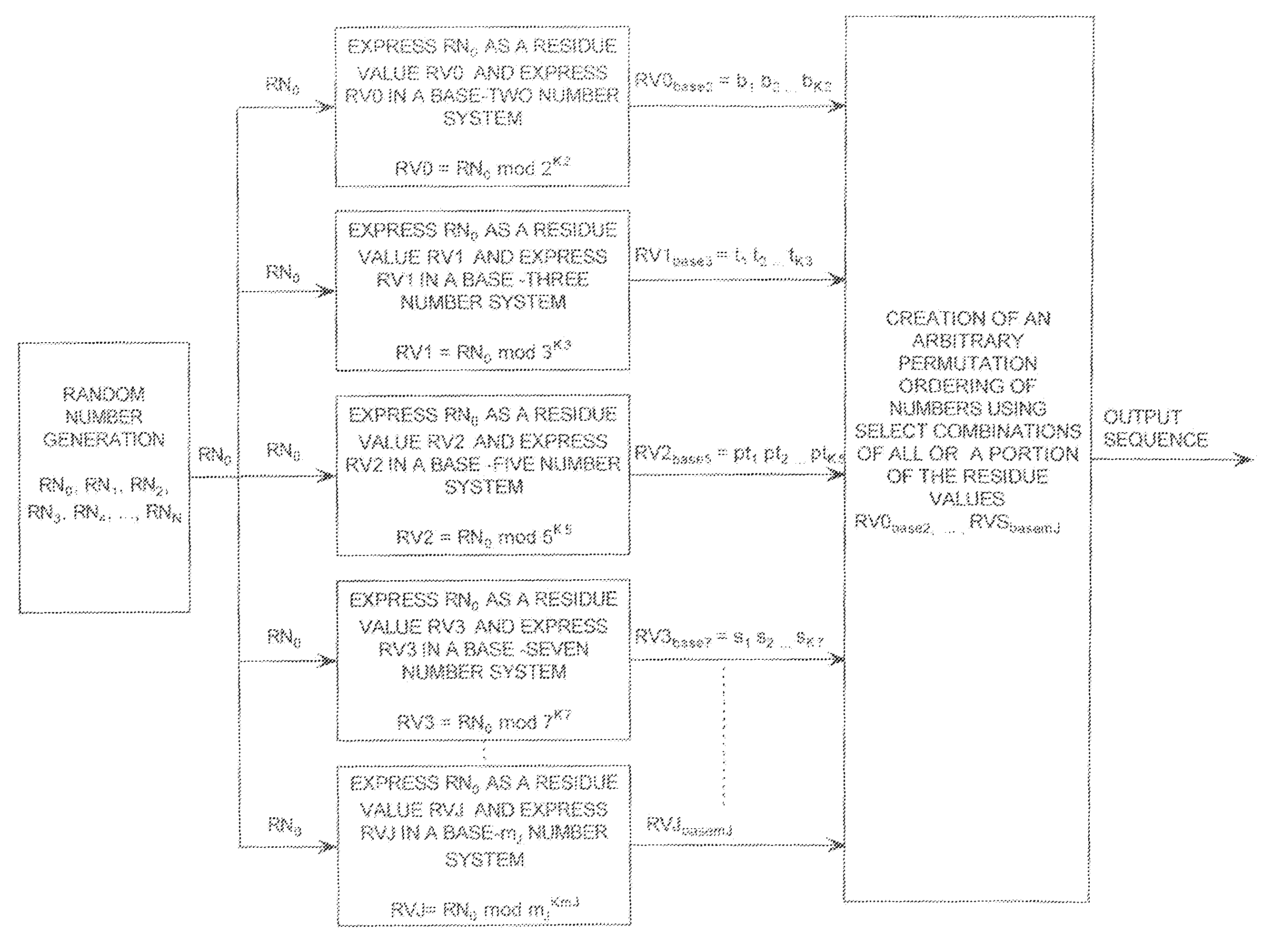
Cryptographic system configured for extending a repetition period of a random sequence
ActiveUS20090110197A1Data stream serial/continuous modificationDigital data processing detailsData streamNumbering system
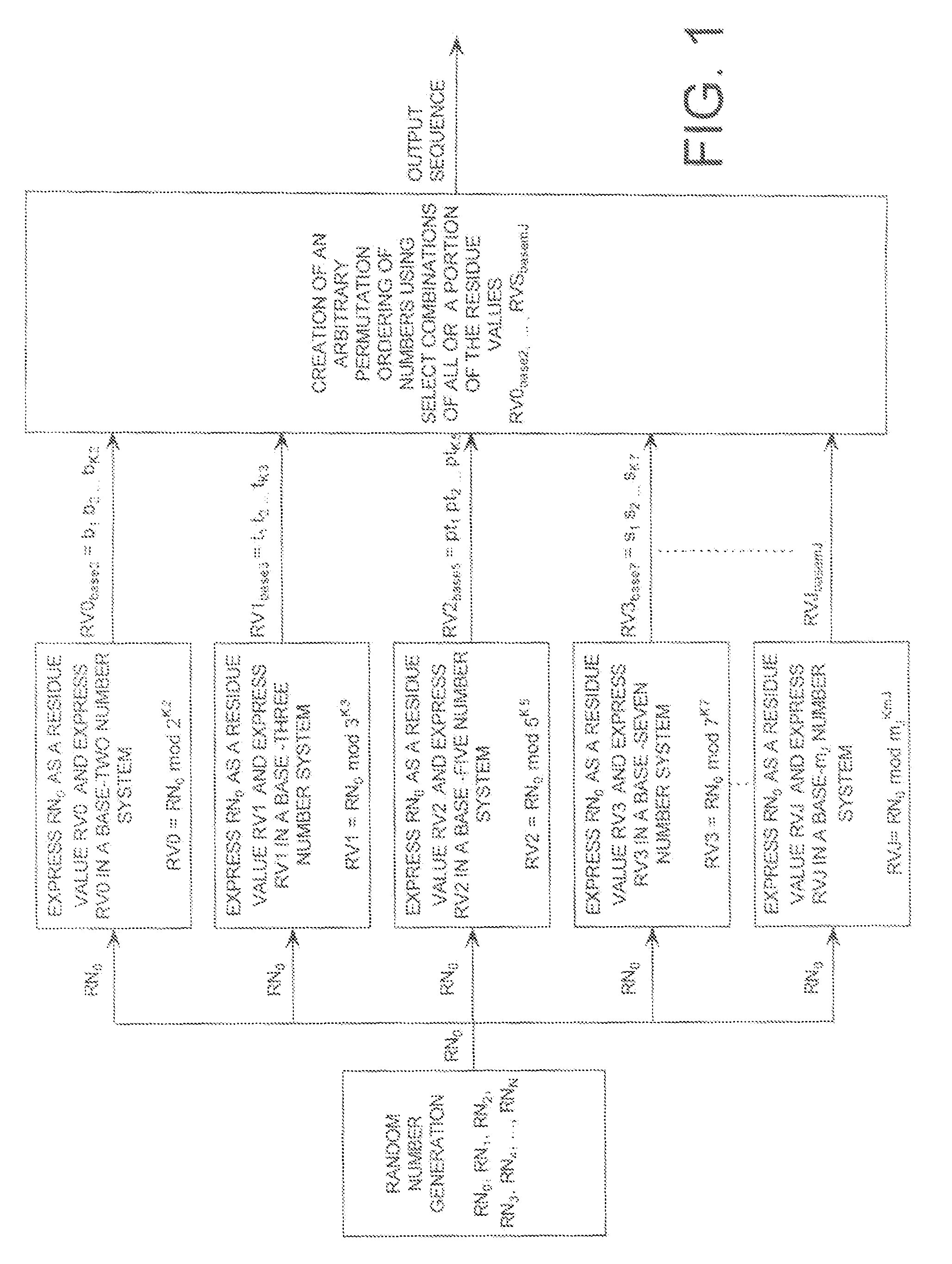
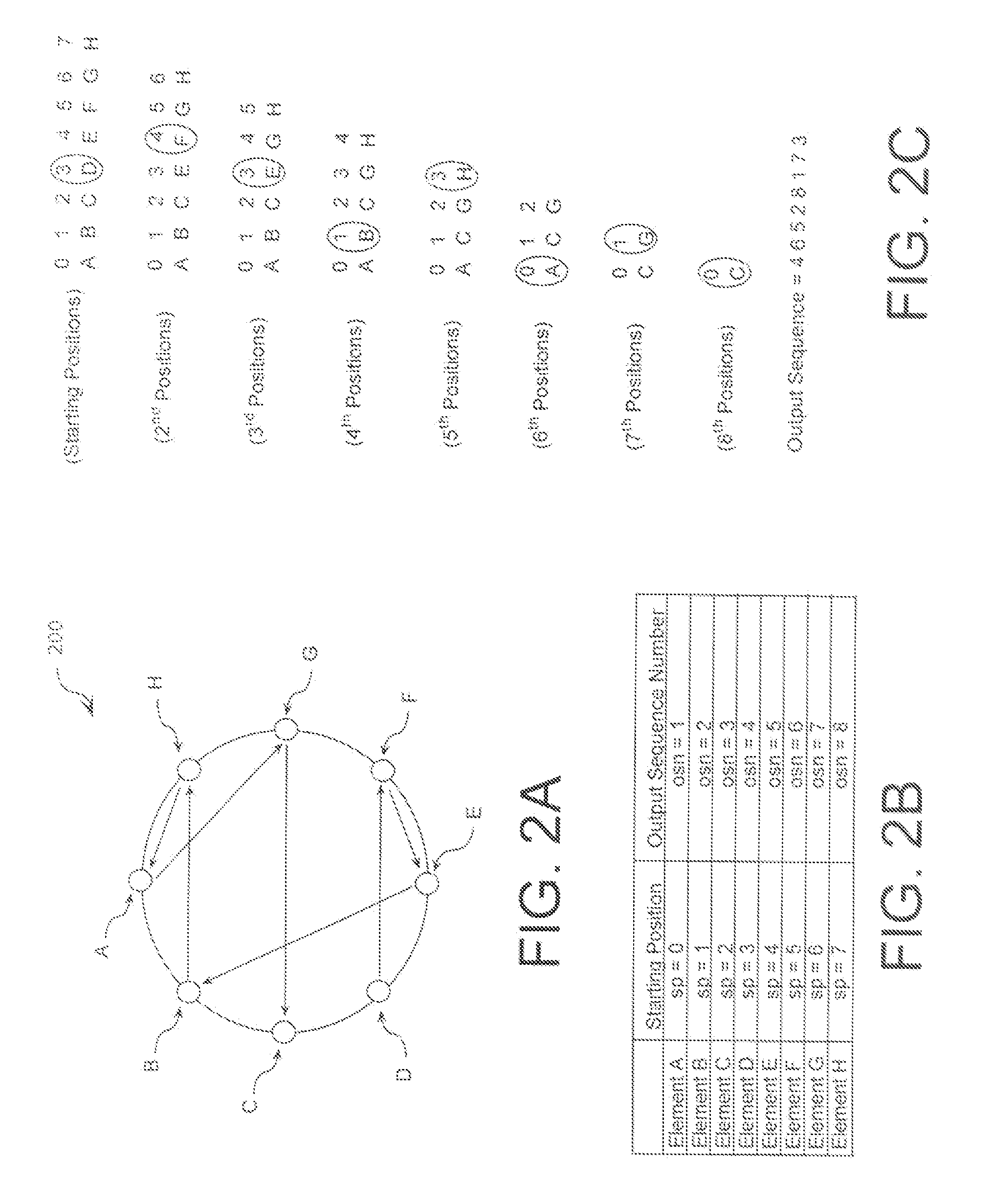
A cryptographic system (CS) is provided. The CS (500) is comprised of a data stream receiving means (DSRM), a ring generator (RG) and an encryptor. The DSRM (602) provides a data stream (DS). The RG (400) includes a computing (404-408), converting (404-408) and permutation (410) means. The computing means is configured to perform RNS arithmetic operations to express a random number in a random number sequence as RNS residue values (RNSRV). The converting means is configured to convert each RNSRV to a relatively prime number system so that each RNSRV includes at least one digit. The permutation means is configured to generate an arbitrary permutation ordering of output sequence numbers (OSNs) using a select combination of digits associated with each RNSRV. The arbitrary permutation ordering is determined using a cyclic structure. The encryptor is configured to generate a modified data stream by combining the OSNs and DS.
Owner:HARRIS CORP
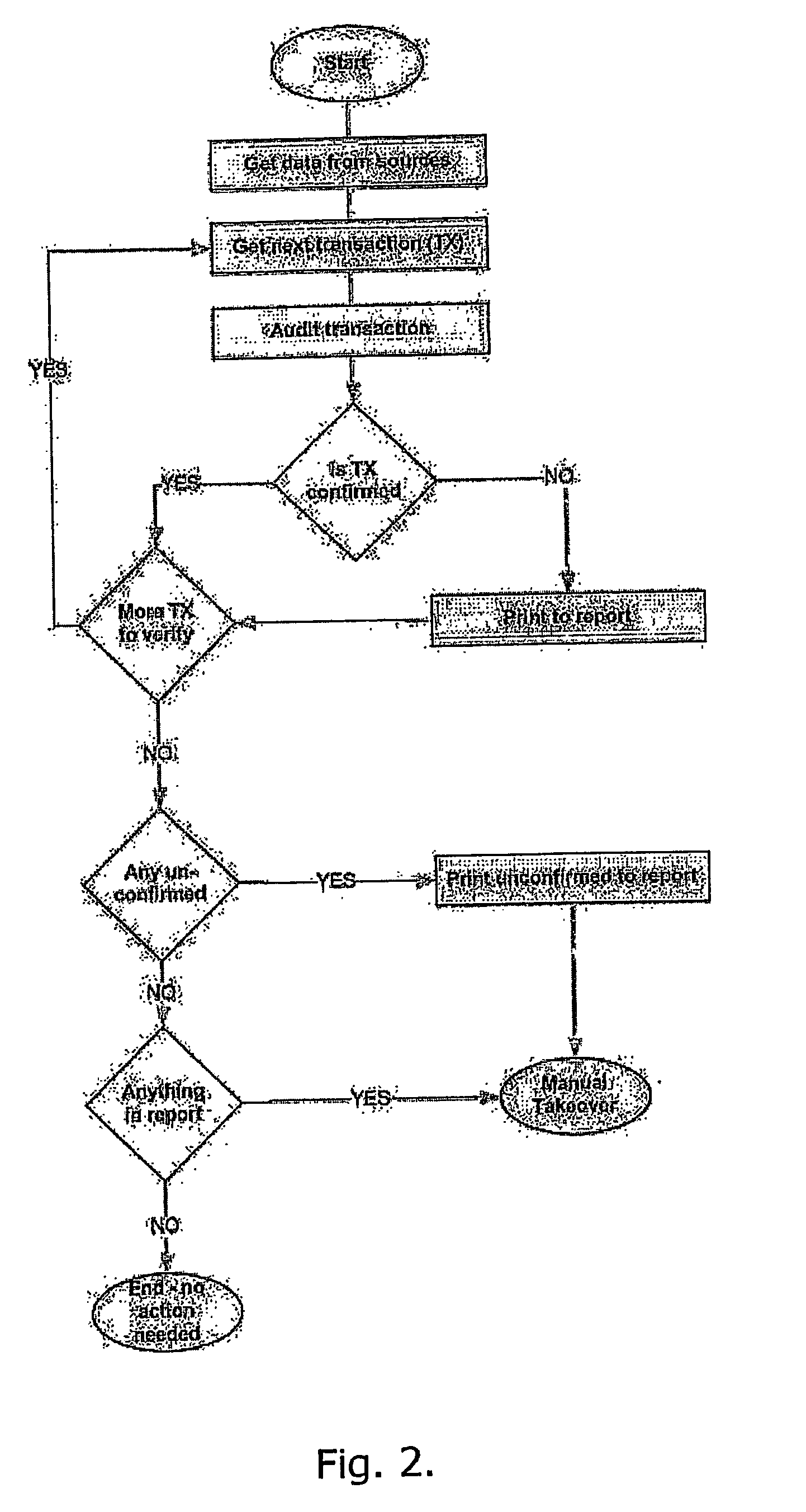
Sequence number schemes for acceptance/rejection of duplicated packets in a packet-based data network
Owner:ALCATEL-LUCENT USA INC +1
Transport control channel program chain linking
ActiveUS20100030920A1Digital computer detailsSpecific program execution arrangementsComputer hardwareControl channel
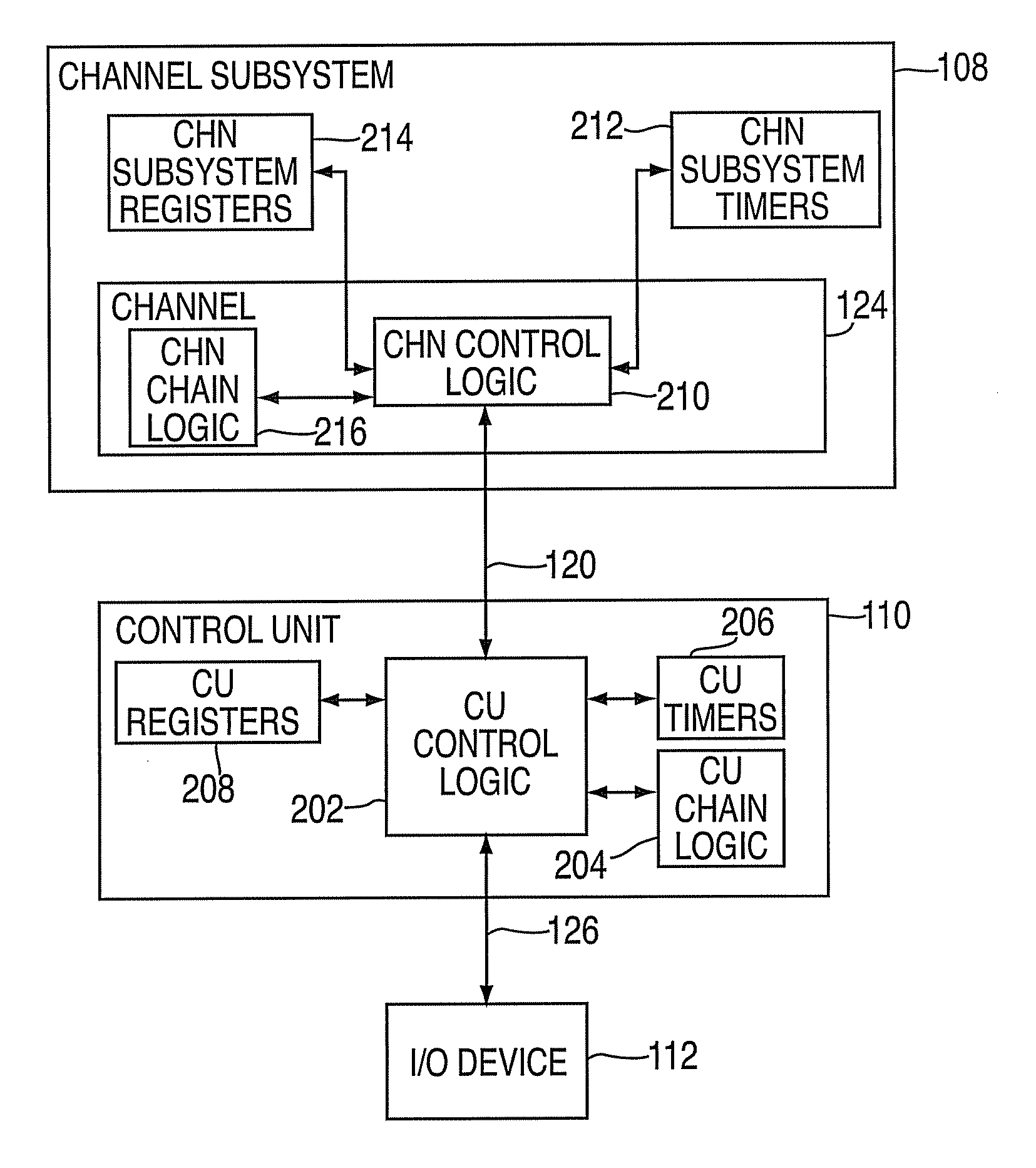
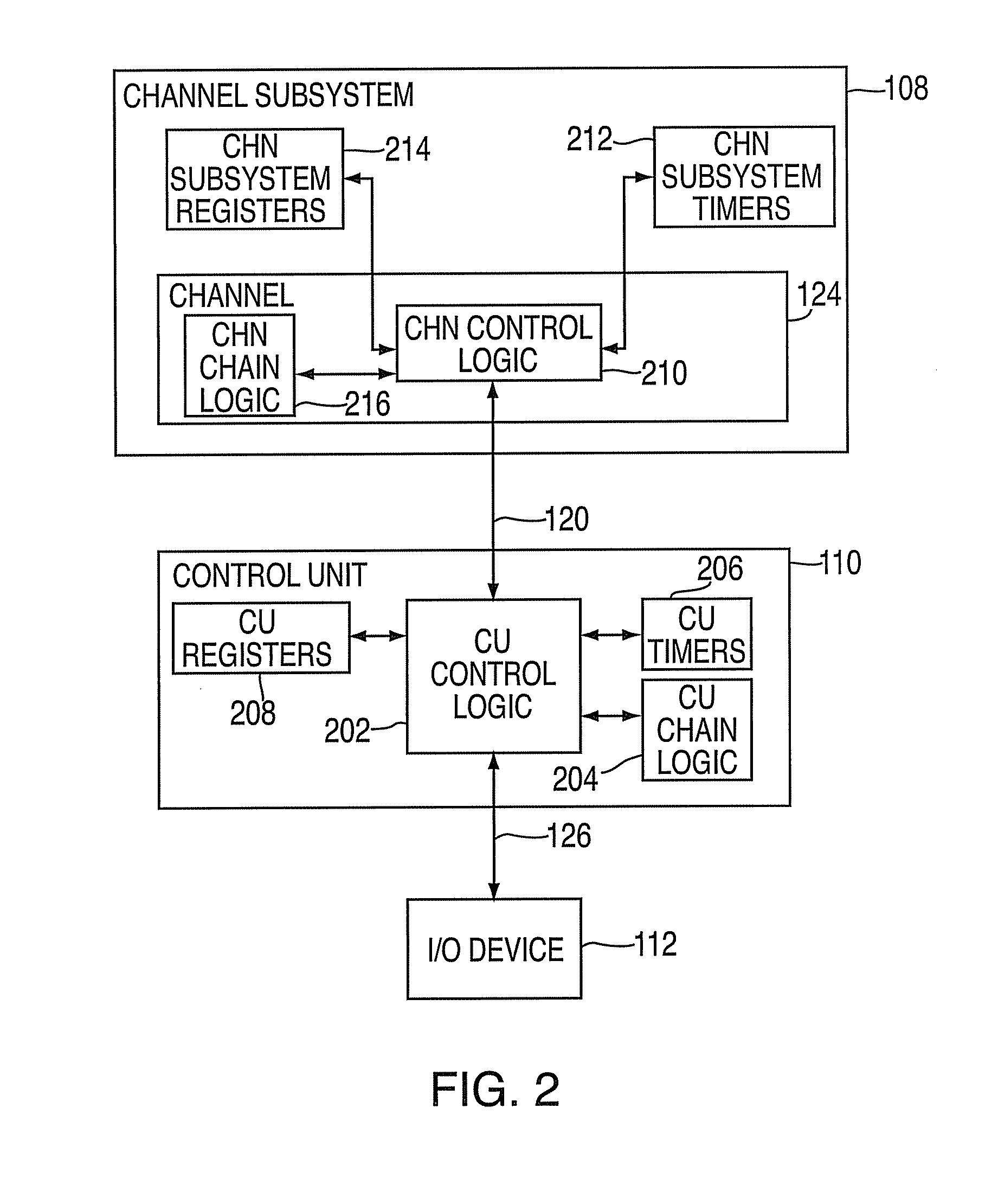
A method, apparatus, and computer program product for processing a chain linked transport control channel program in an I / O processing system is provided. The method includes receiving a first command message at a control unit specifying a first predetermined sequence number for performing a first set of one or more commands as part of an I / O operation. The method further includes receiving a second command message specifying a second predetermined sequence number for performing a second set of one or more commands as part of the I / O operation. The method also includes comparing the sequence numbers to a next expected predetermined sequence number to determine an order of performing the commands. The method additionally includes executing the commands in the determined order to perform the I / O operation.
Owner:IBM CORP
Strategic method for process control
InactiveUS7461040B1Increase productivityImprove efficiencySpeech analysisSound input/outputData setValidation methods
A strategic method for process control wherein the method includes, for a predetermined process juncture, the steps of: (A) defining an interconnection cell having associated therewith (i) at least one set of input data or at least one set of process control parameters, and (ii) at least one set of output data; (B) assigning at least one boundary value to at least one set of the sets associated with the defined interconnection cell; (C) using the assigned at least one boundary value, forming a plurality of discrete respective set combinations, and (D) for the interconnection cell, processing data from the plurality of respective formed set combinations into respective corresponding data record clusters.The strategic method for process control is a continuation-in-part of a Knowledge-Engineering Protocol-Suite, (U.S. patent application Ser. No. 09 / 588,681 filed on 7 Jun. 2000) incorporated herein by reference, that generally includes methods and systems, apparatus for search-space organizational validation, and appurtenances for use therewith. The protocol-suite includes a search-space organizational validation method for synergistically combining knowledge bases of disparate resolution data-sets, such as by actual or simulated integrating of lower resolution expert-experience based model-like templates to higher resolution empirical data-capture dense quantitative search-spaces. The protocol-suite includes facile algorithmic tools for use with the method.
Owner:ADA ANALYTICS ISRAEL
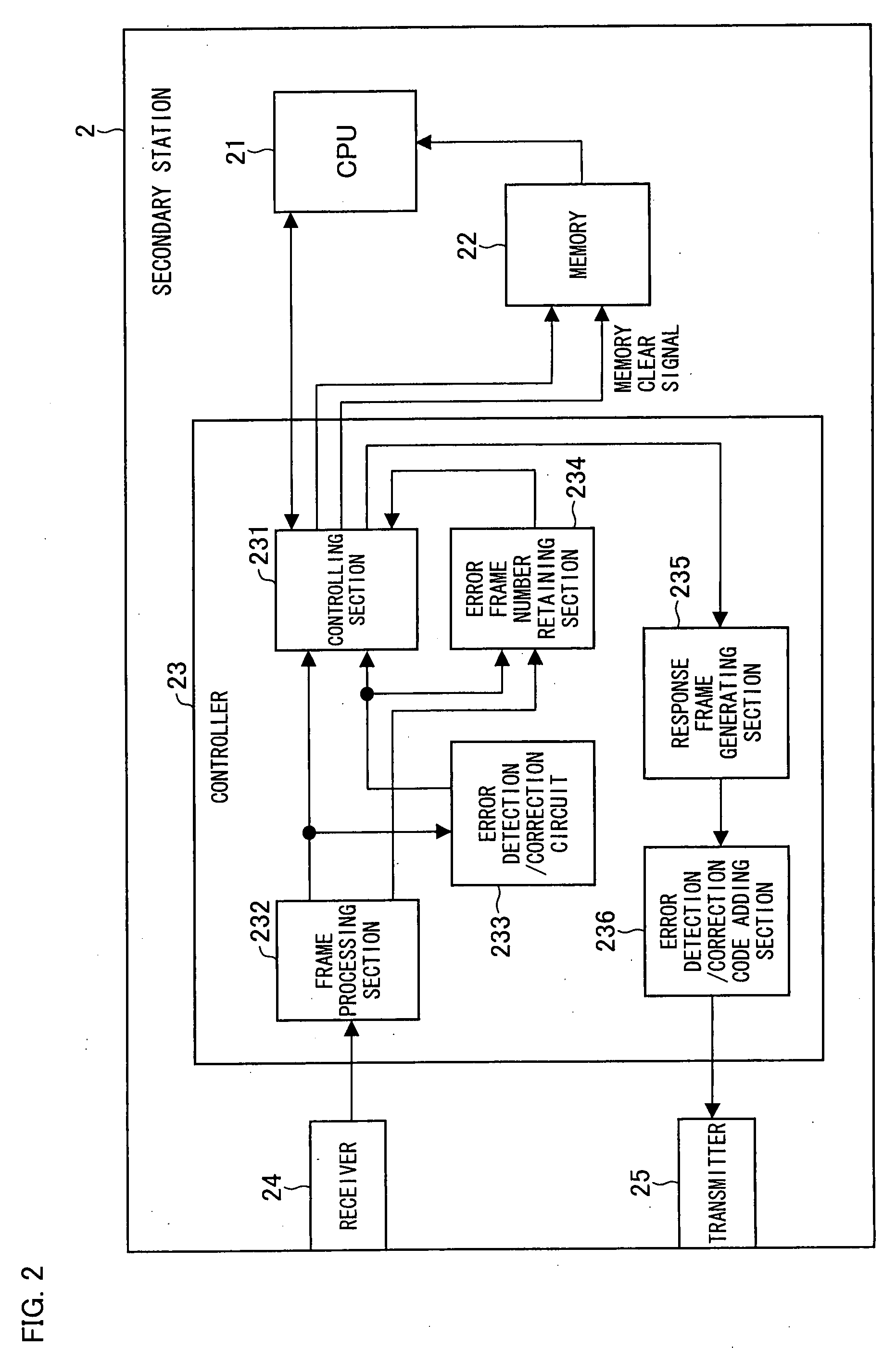
Communication Device, Communication System, Communication Method, Communication Program, and Communication Circuit
ActiveUS20080313518A1Quality improvementHigh transfer efficiencyError prevention/detection by using return channelTransmission systemsCommunications systemData transmission
In a transmitter (2001), when generating a transmission frame having no limitation to a window size, a batch-transmission-end flag generating circuit (2004) and a sequence number generating circuit (2005) respectively adds a batch-transmission-end flag and a sequence number to the transmission frame. In a receiver, if an omission of a sequence number is detected as a result of analyzing sequence numbers of frames having received from the transmitter (2001), retransmission request is made when receiving a frame whose batch-transmission-end flag indicates the end. In this way, retransmission is possible in data transmission using UI frames, and the communication efficiency can be improved.
Owner:SHARP KK
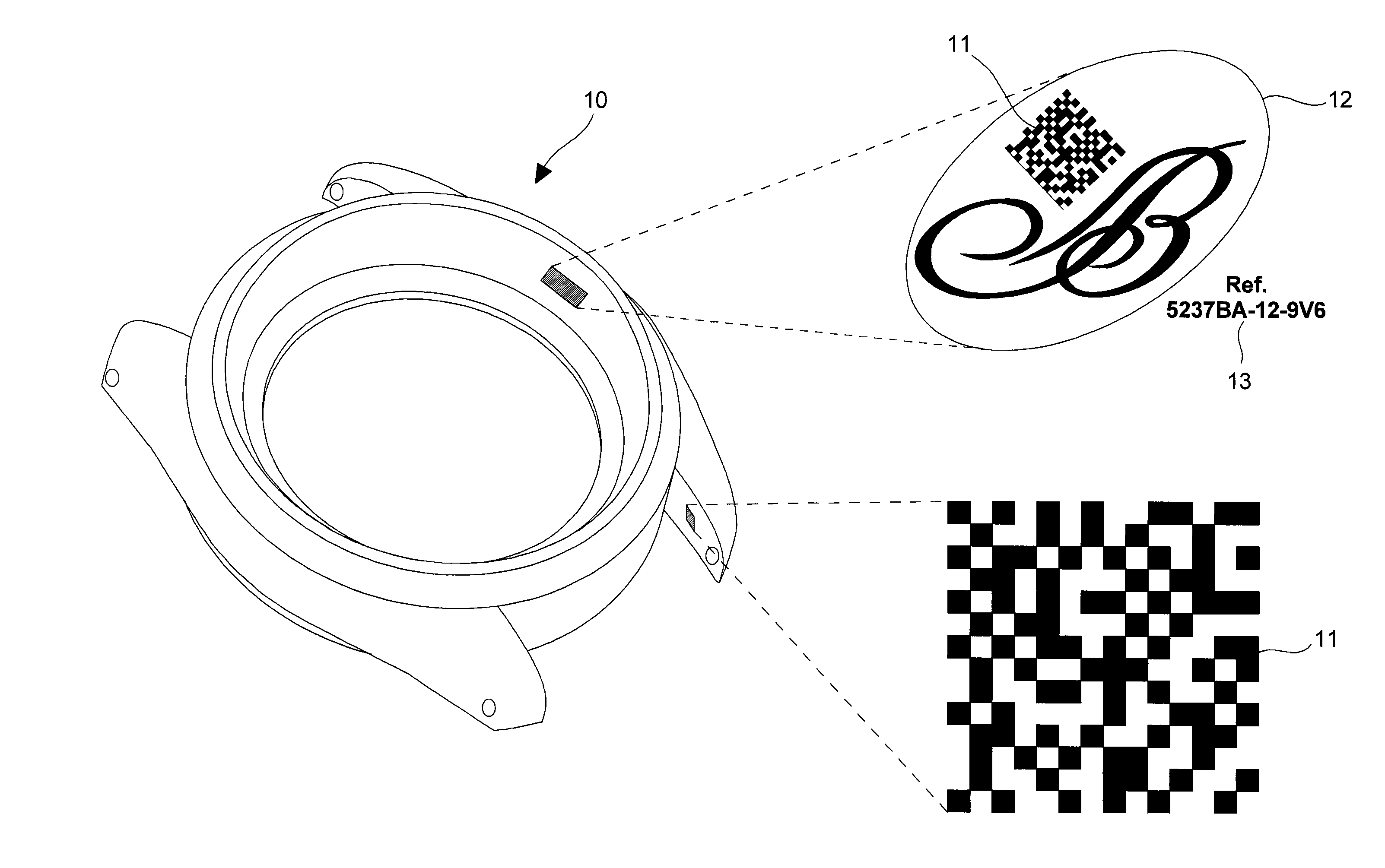
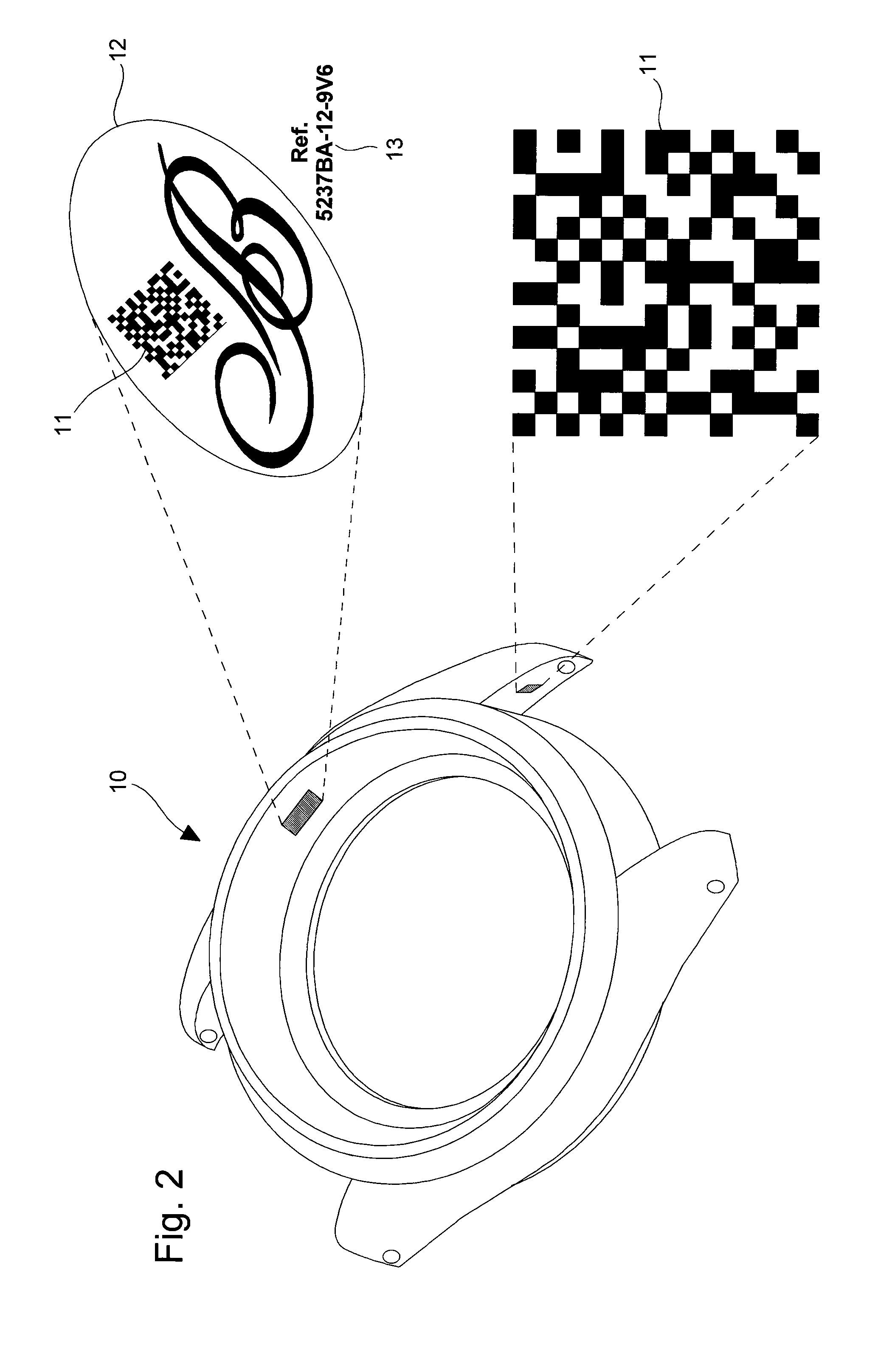
Method of coded marking of a product of small size, and marked product obtained according to said method
InactiveUS20090302123A1Small sizeImprove securityRecord carriers used with machinesBarcodeComputer science
The method is for coded marking of a product of small size, such as horological or jewelry product (10). The method consists in carrying out a first mathematical operation of encrypting an identifier (13), such as a serial number of the product to be marked using a specific security algorithm key to obtain a first authenticator. The first authenticator includes a first data length defined by a first large number of alphanumerical characters. This first authenticator is encrypted using a second mathematical operation using a Hash type function into a second authenticator. This second authenticator includes a second data length defined by a second reduced number of alphanumerical characters shorter than the first number of characters. The second authenticator is converted into a coded image, which is preferably a two dimensional barcode (11) so as to be placed on the product as the coded mark in order to allow said product to be authenticated.
Owner:MONTRES BREGUET
Assigning recoverable unique sequence numbers in a transaction processing system
InactiveUS6874104B1Data processing applicationsDigital data information retrievalManagement systemTransaction processing system
A method, apparatus, article of manufacture, and data structure for use in providing transaction control for a computer-implemented database management system. The database management system manages one or more databases. A transaction processing system provides transaction control for one or more of the databases managed by the database management system, wherein the transaction processing system assigns a recoverable, unique sequence number whenever a request is made by an application.
Owner:IBM CORP
Packet authentication
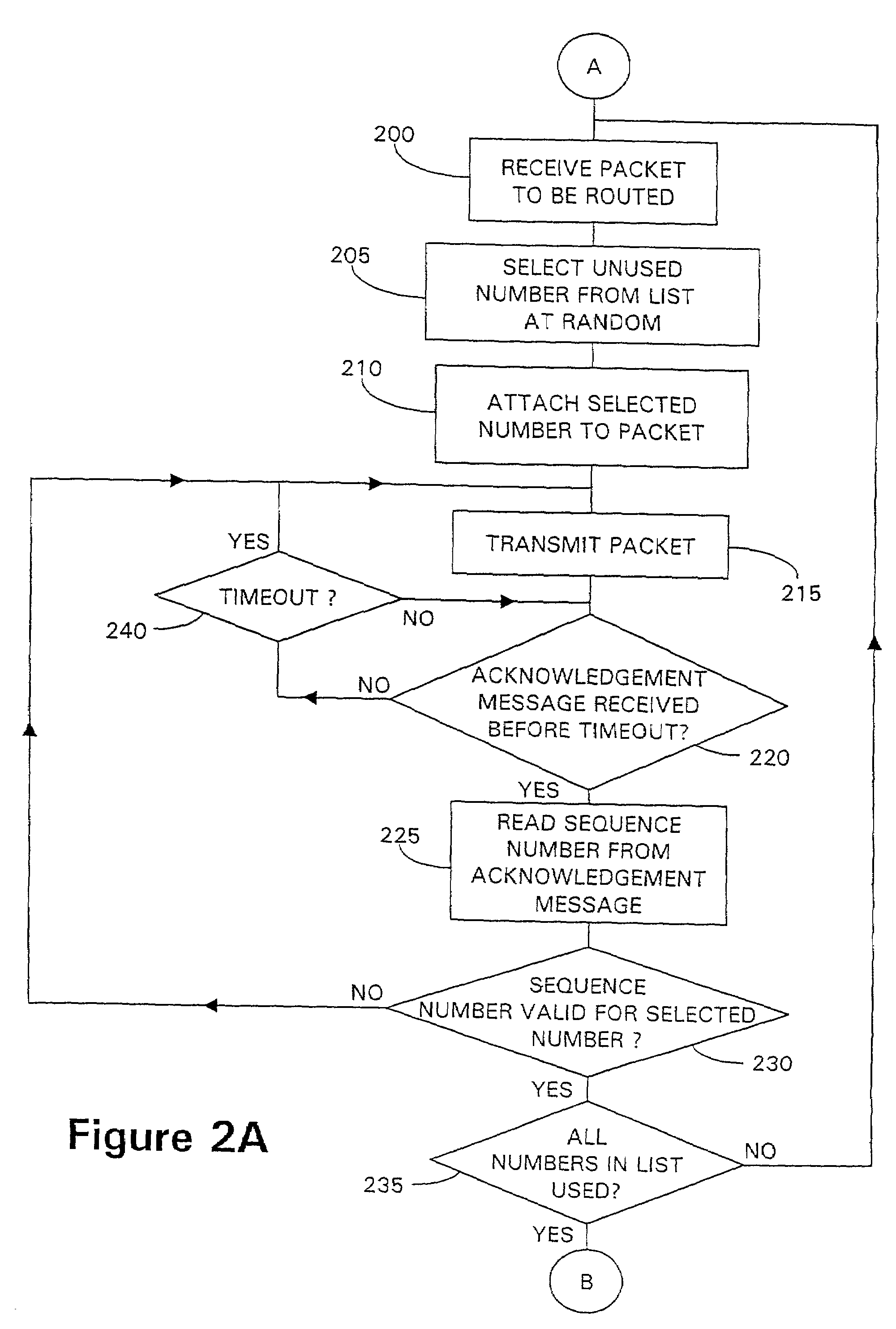
InactiveUS7337316B1Reduce throughputMore processing overheadData taking preventionMultiple digital computer combinationsData packTelecommunications
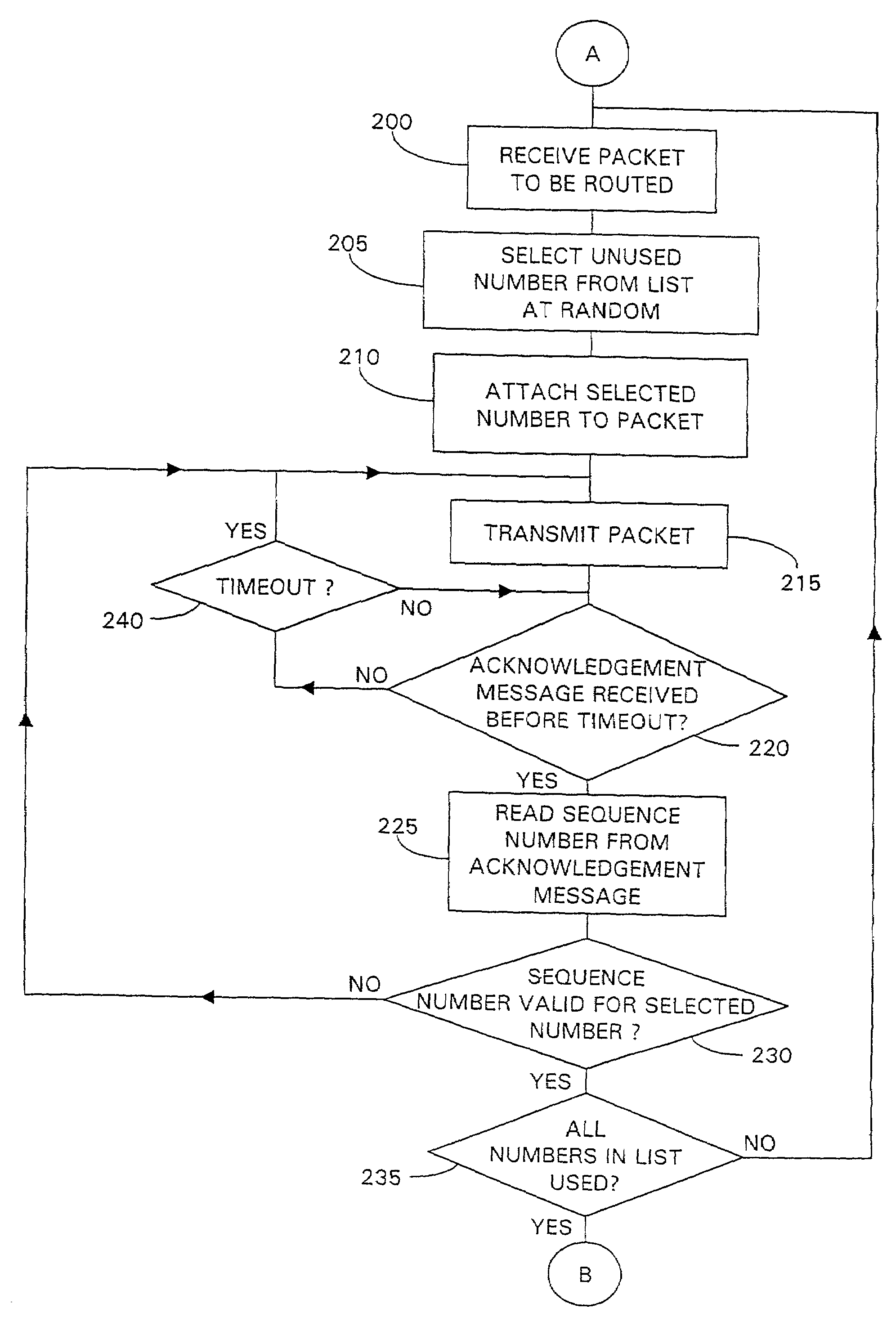
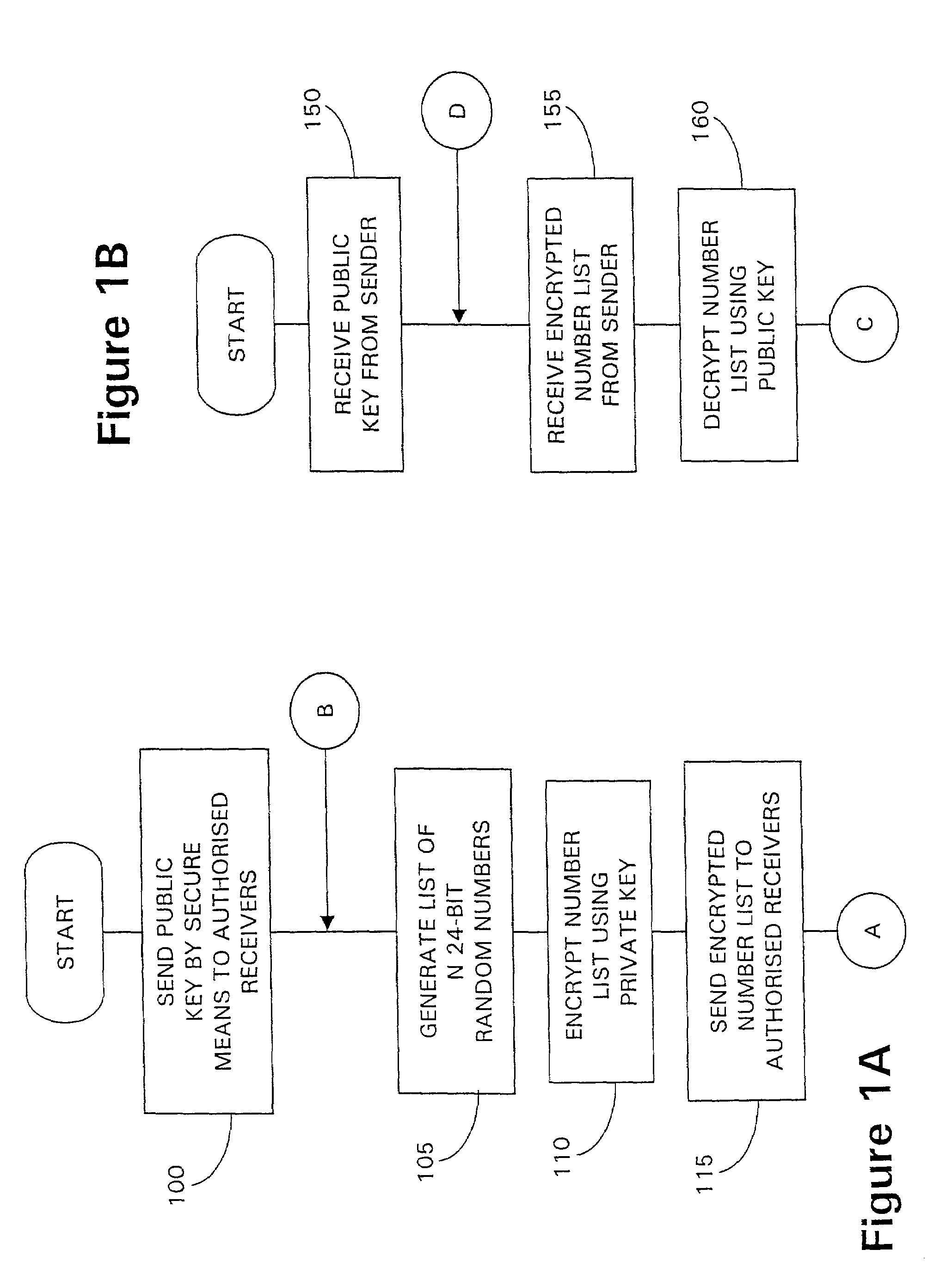
A data packet is conveyed between servers connected to a packet network. A first server securely distributes a list of distinct numbers to one or more authorized receiving servers. Subsequently, upon receiving a packet to be transferred, the first server selects an unused number from the number list and writes the number into the packet before routing the packet to one or more of the authorized receiving servers. Upon receipt of the packet, an authorized receiving server checks that the number included in the packet is valid in that it is both contained in the latest number list and has not already been used in another packet. If valid, the receiving server determines a sequence number representative of the position of the number in the latest number list and sends an acknowledgement message to the originating server, including the determined sequence number. The originating server checks the sequence number to verify the authenticity of the acknowledgement message, re-sending the packet if invalidly acknowledged.
Owner:BRITISH TELECOMM PLC
Hard-disc fan-area data enciphering and deciphering method and system
InactiveCN1936870AImprove securityPrevent leakageUnauthorized memory use protectionSecuring communicationProgrammable read-only memoryTransfer procedure
This invention discloses an encryption and decryption method for data in hardware. It consists of several steps: obtain the key by reading data from the ROM; obtain the original key by the expending mechanism; operate the logic address and the sequence number and shift the result to get the address key; encryption on the address key by the original key to form a key flow; encryption and decryption on transmitting data. This invention could enhance data security on storage device and protect them from missing.
Owner:ZHEJIANG XUNBO INFORMATION ENG
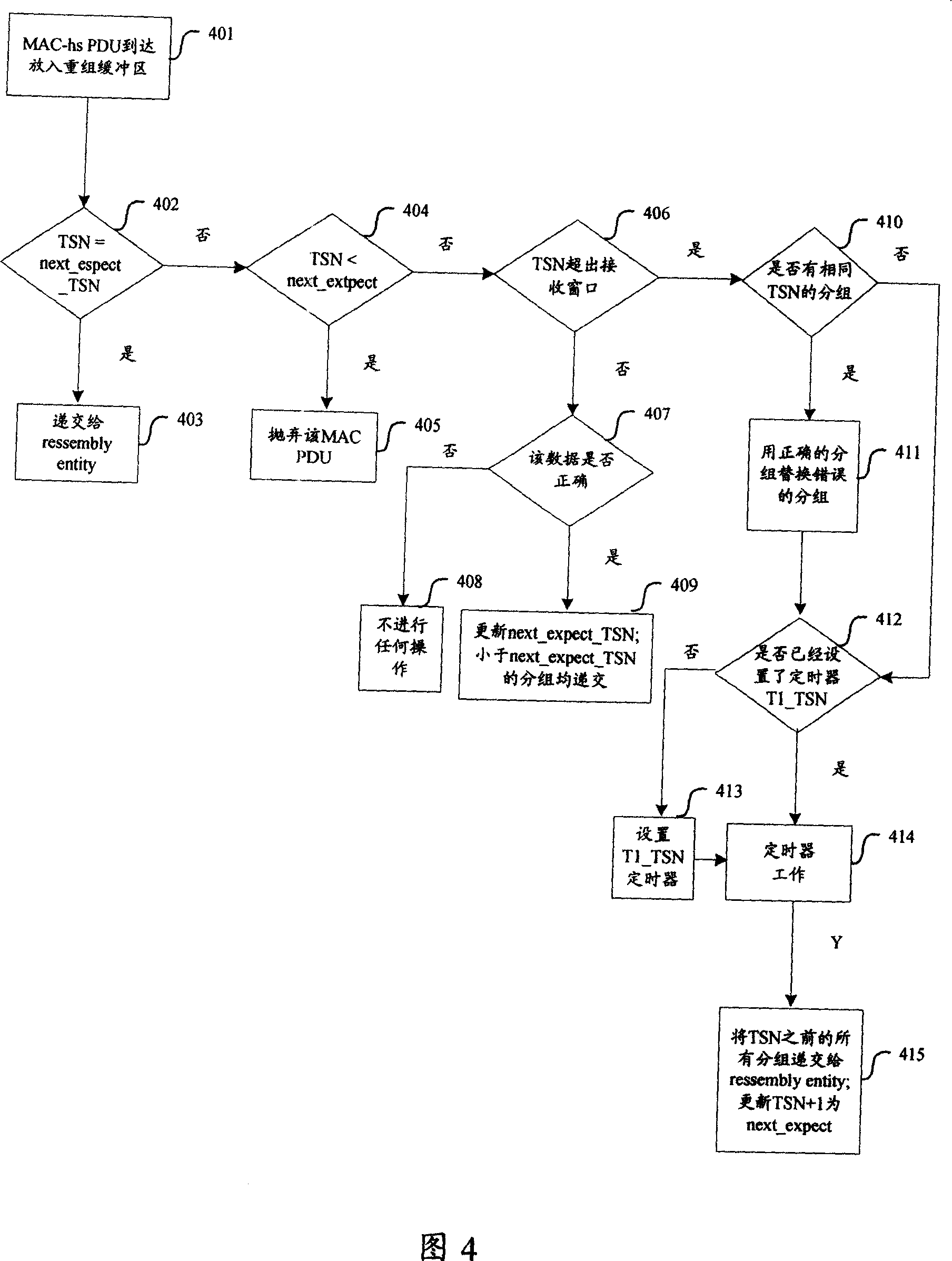
Method and apparatus for data mixing and automatic requesting for retransmission
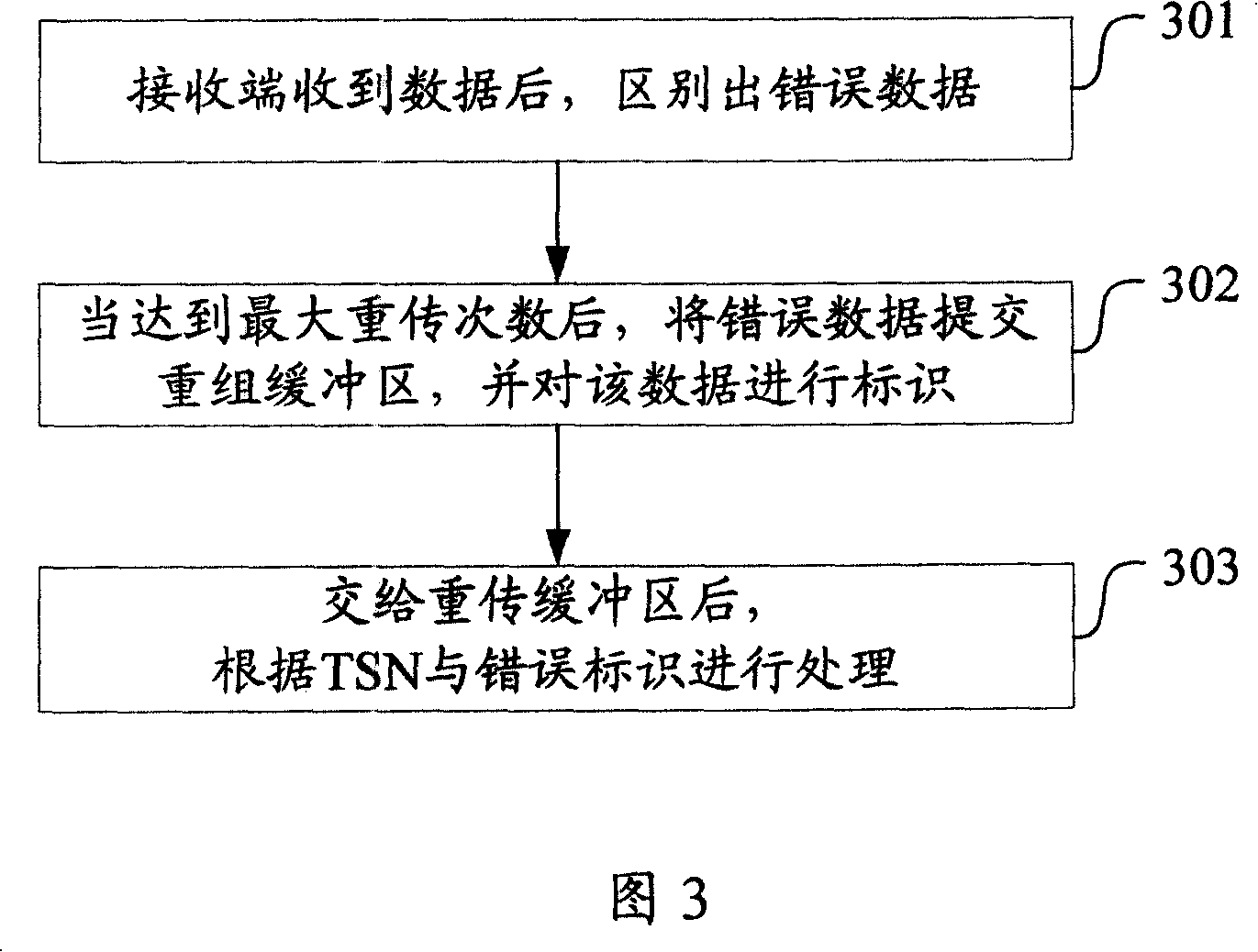
InactiveCN101155014AImprove satisfactionAvoid useless transmissionError prevention/detection by using return channelComputer scienceAutomatic testing
The present invention discloses a method of hybrid automatic repeat request and the device, which includes the steps of: differentiating the wrong data by the receiving end when the receiving end receives the data; identifying the wrong data and presenting to the regrouping buffer area when the hybrid automatic repeat request has reached a maximum repeat number; processing the wrong data and presenting to the high layer by the receiving end at the regrouping buffer area according to the data identification and the transferring sequence number. The invention increases the error presenting faculty of the base layer when the hybrid automatic repeat has reached the maximum repeat number, at the same time further takes measure to avoid the effect caused by the error of the grouping data head thereby obtaining the advantages of providing the useful information to the high layer as much as possible, avoiding the useless transmission of the base layer data and meanwhile increasing the satisfaction of the user.
Owner:HUAWEI TECH CO LTD
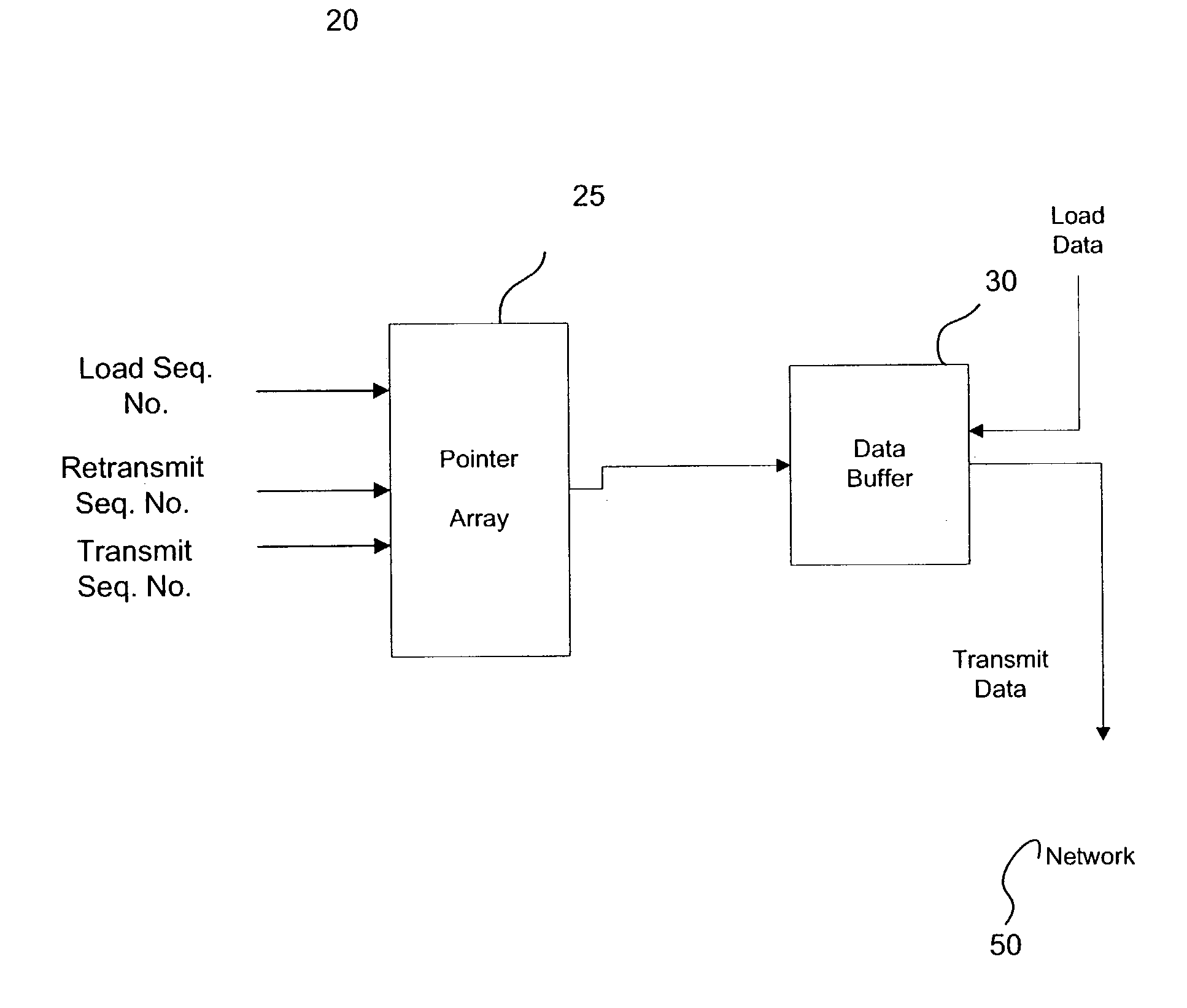
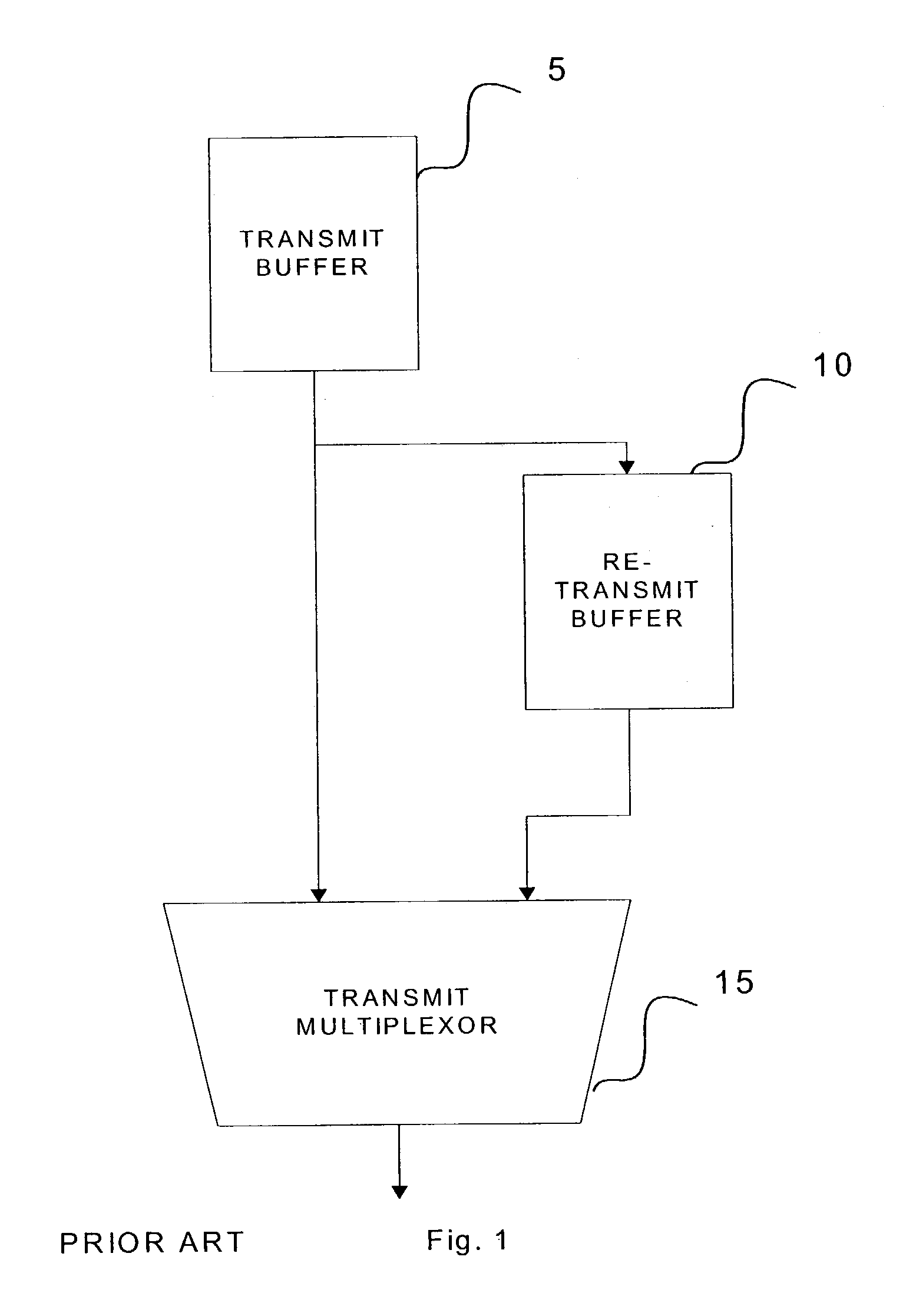
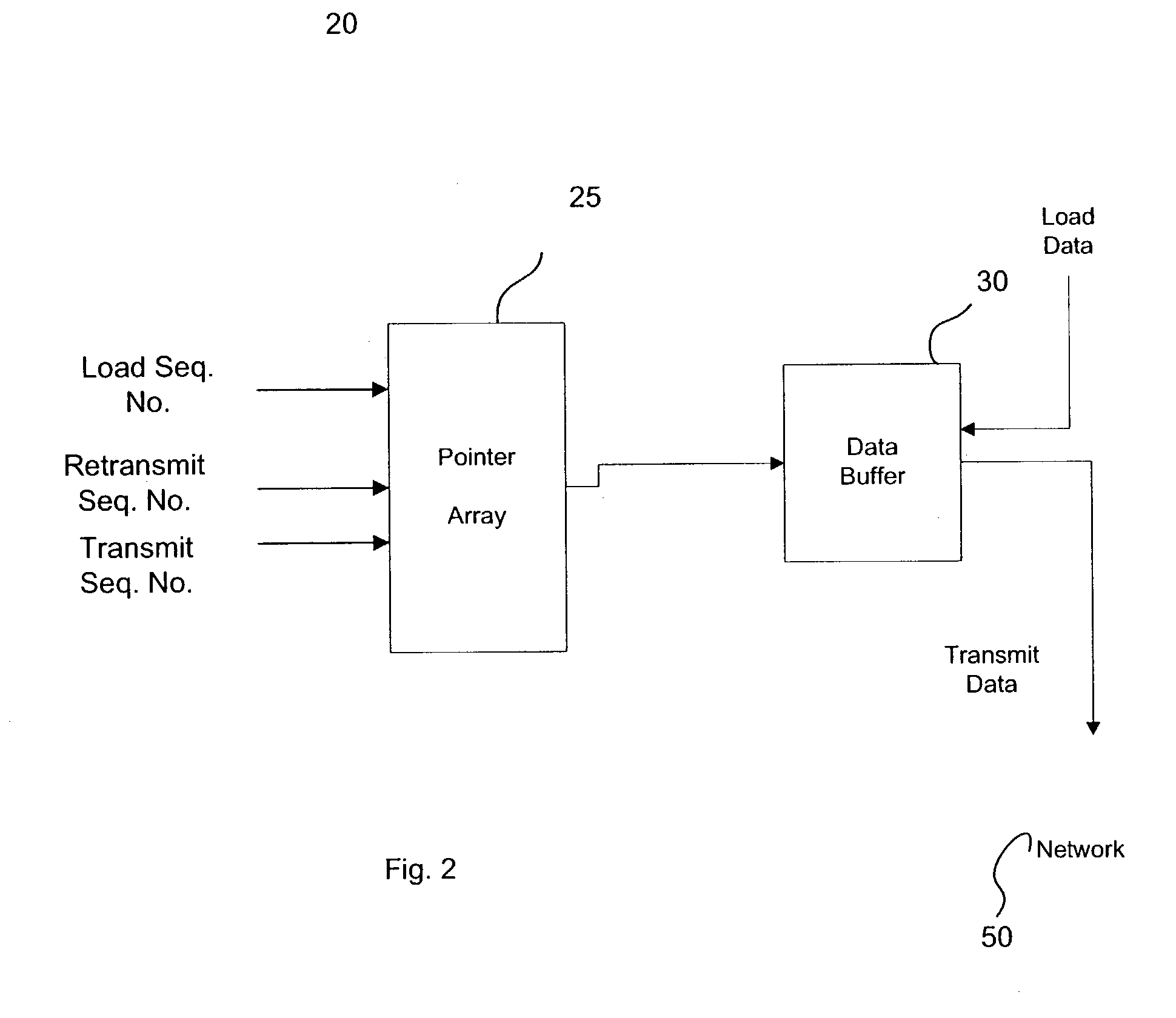
Method and device for managing transmit buffers
ActiveUS20040131074A1Store-and-forward switching systemsData conversionArray data structureNetwork packet
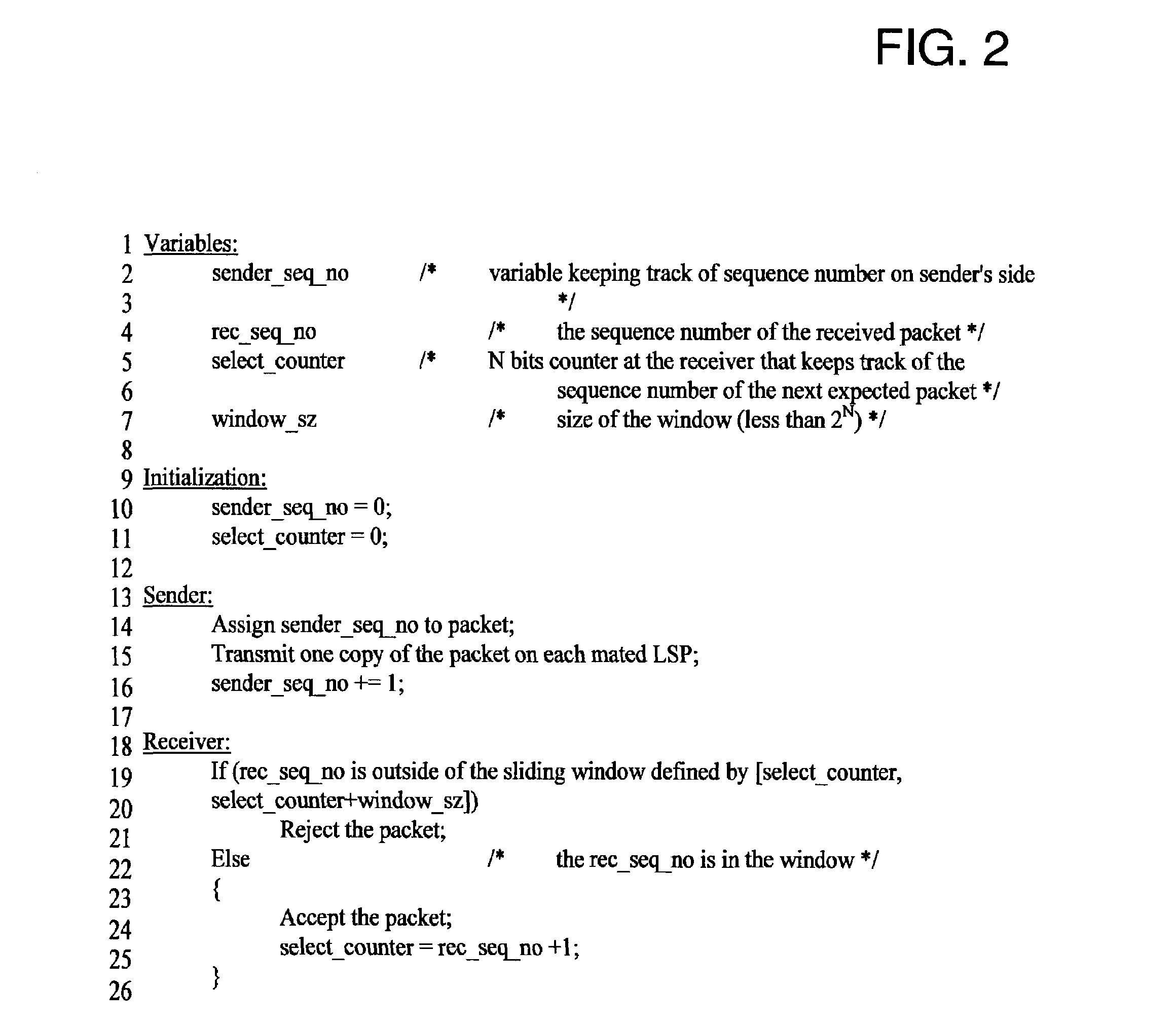
A method and device for managing a data buffer that stores packets for transmission. Packets are loaded into the data buffer, which is managed as a first-in-first-out (FIFO) circular queue, at the tail of the queue. Three sequence numbers index a pointer array addressing the buffer. These sequence numbers correspond to the tail of the queue, the point in the queue from which the next packet is to be transmitted and the head of the queue, corresponding to the last packet acknowledged as correctly received plus one. When a packet is negatively acknowledged, the sequence number corresponding to the next packet to be transmitted is reset to the head of the queue.
Owner:ORACLE INT CORP
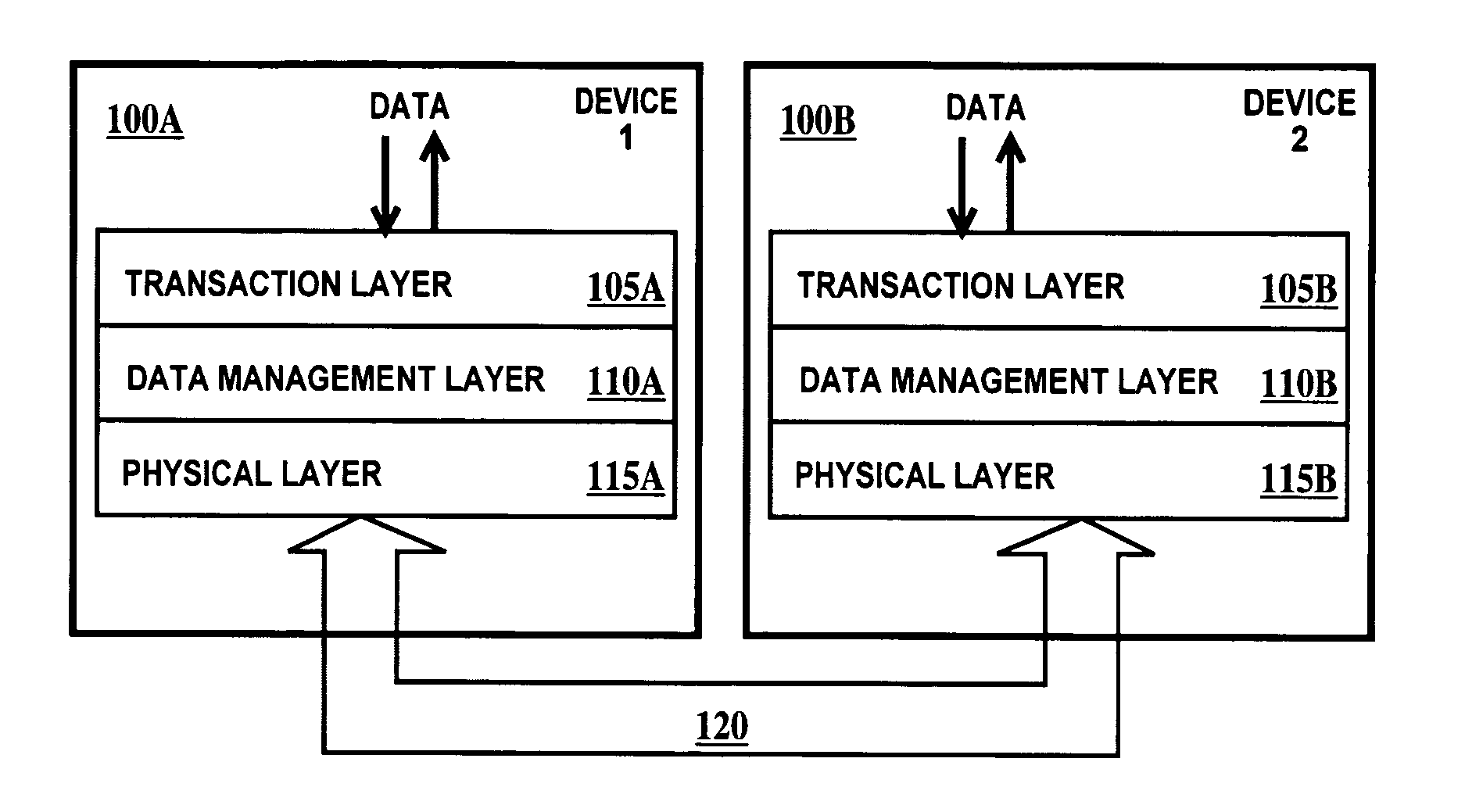
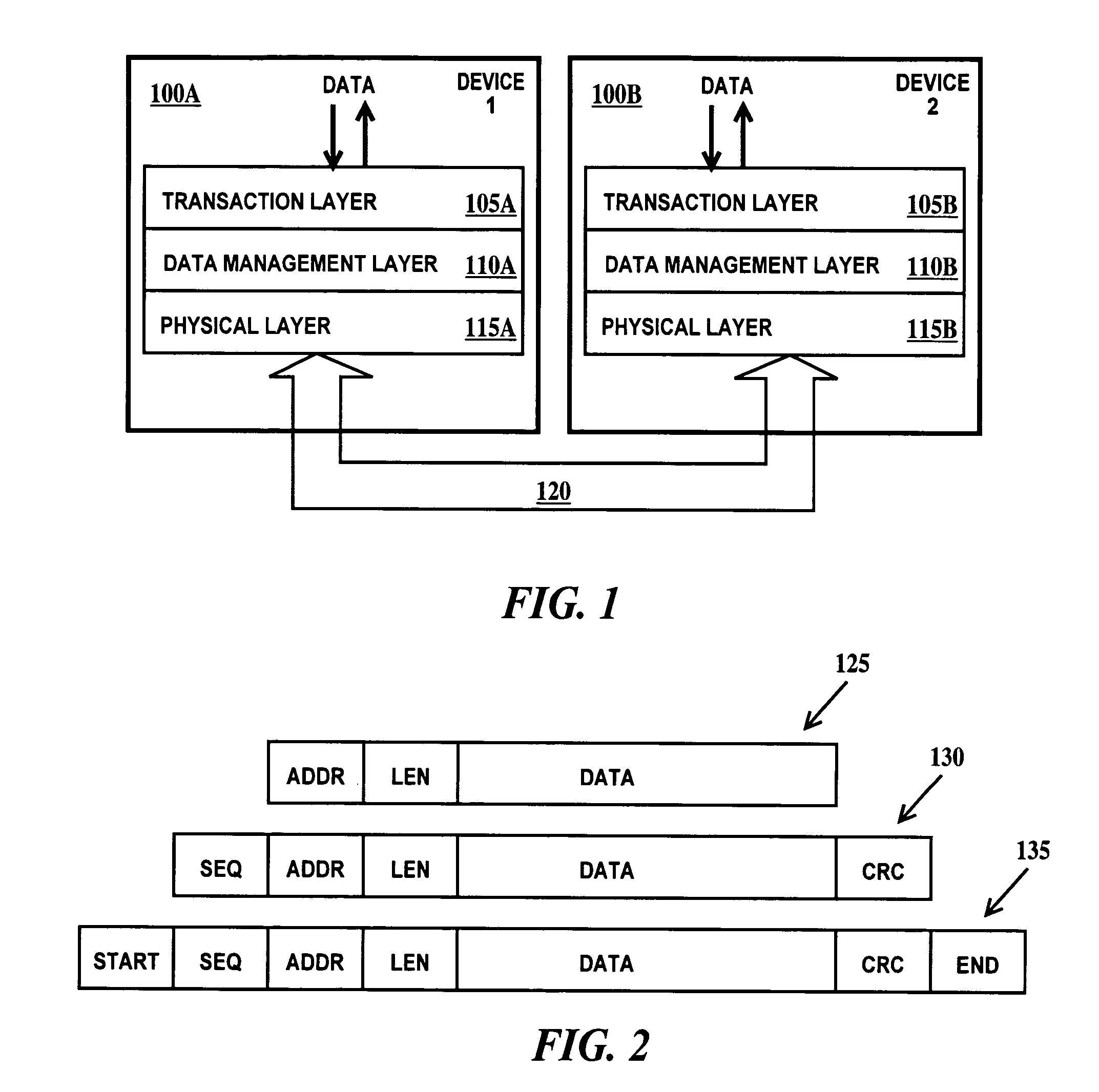
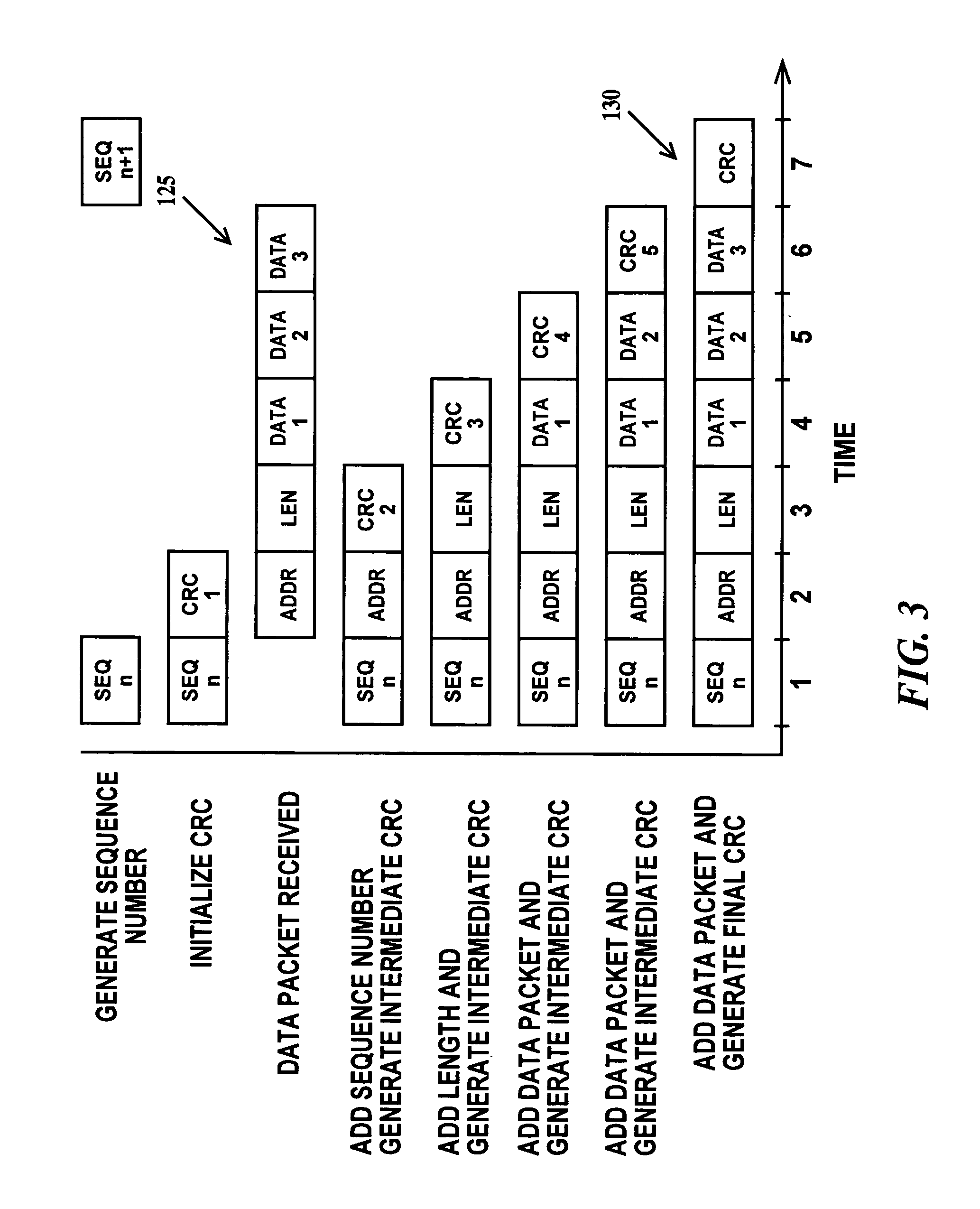
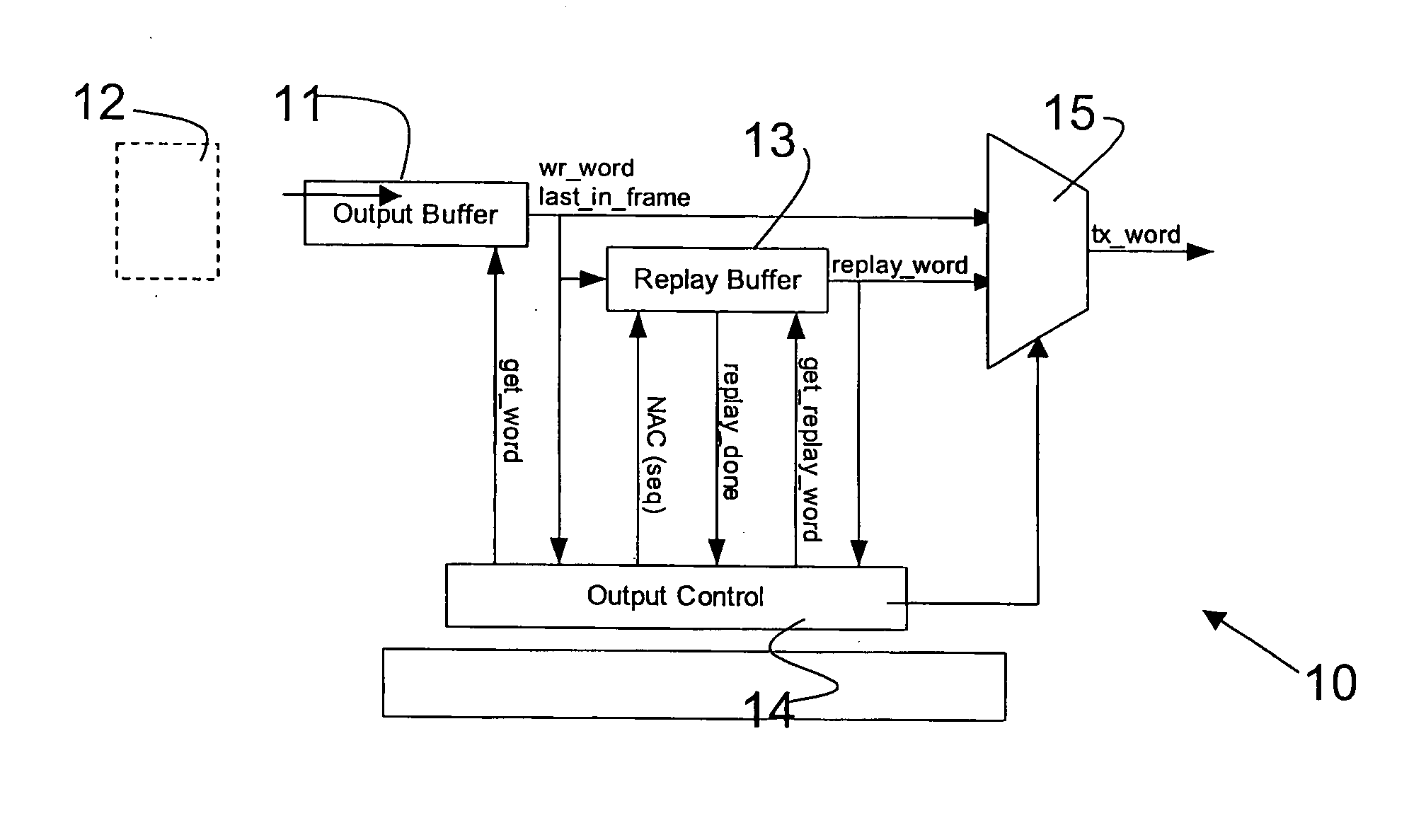
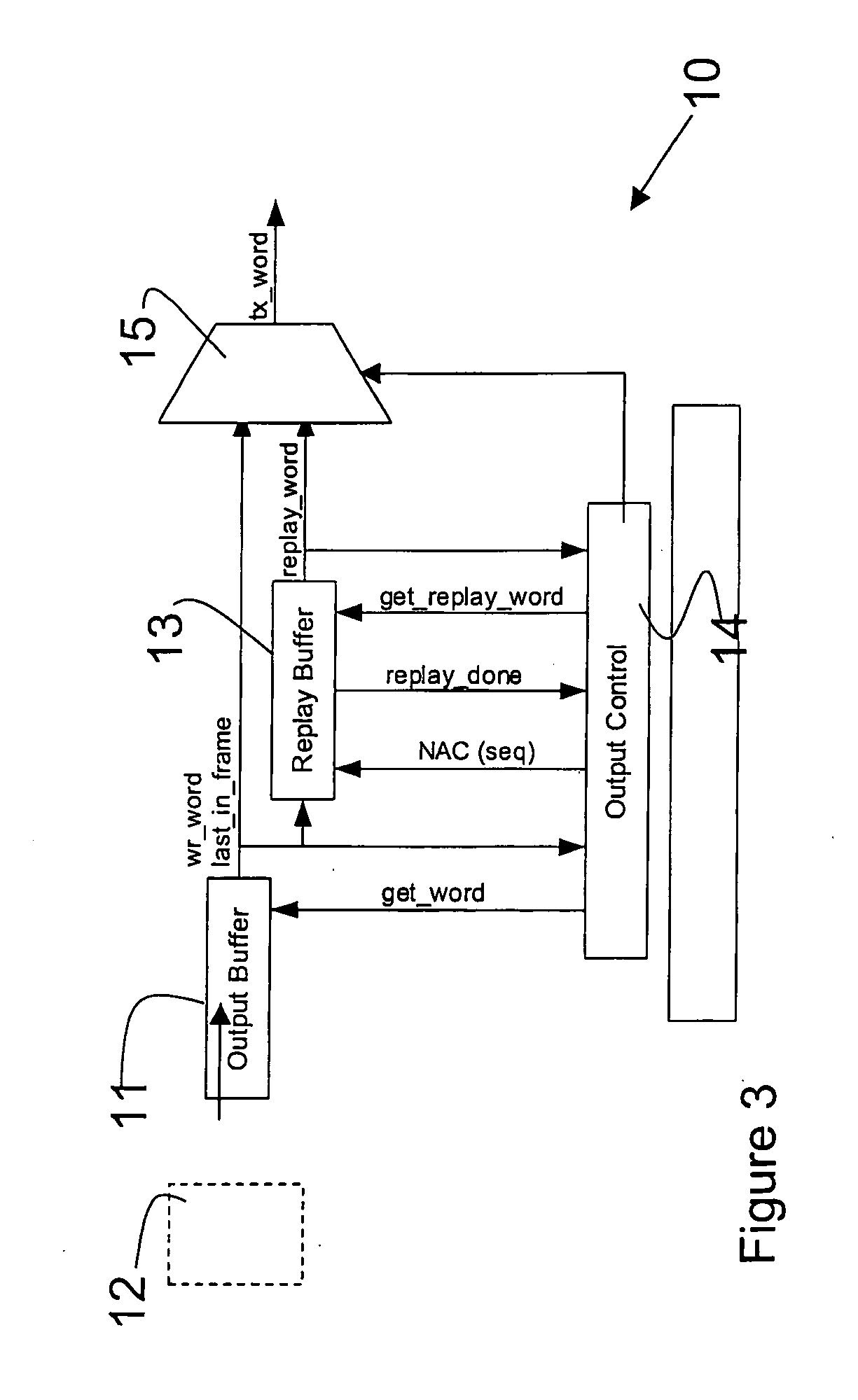
Method and apparatus for data transfer
A data management layer of a layered protocol system and a method of transmitting data. The data management layer including: a cyclic redundancy check generator connected to a retry buffer through a multiplexer; a sequence number generator connected to the retry buffer through the multiplexer; means for generating a sequence number cyclic redundancy check remainder connected to preset inputs of a cyclic redundancy check remainder latch of the cyclic redundancy check generator; an input data bus connected directly to the cyclic redundancy check generator and connected to the retry buffer through the multiplexer; and an output data bus directly connected to the retry buffer.
Owner:IBM CORP
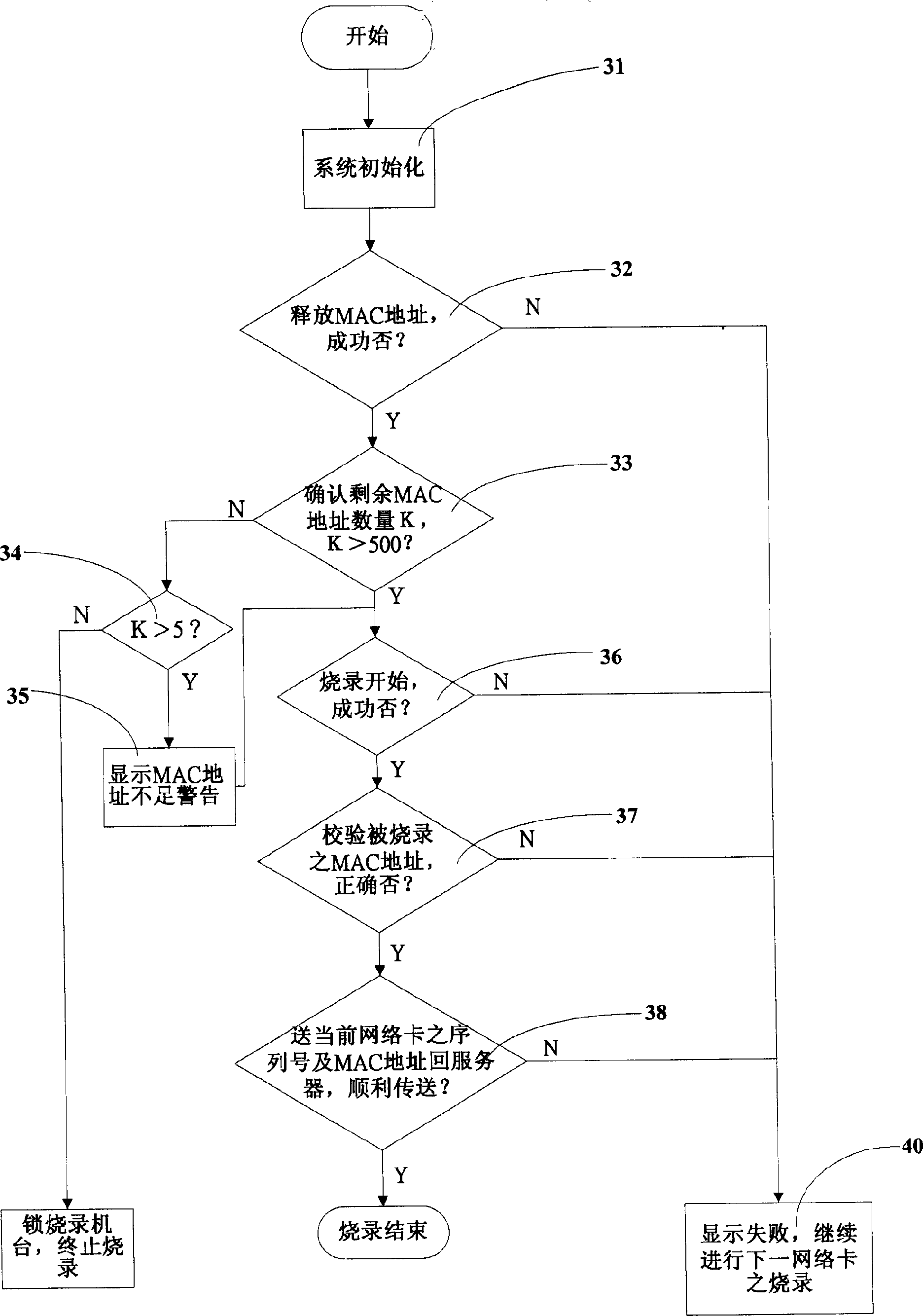
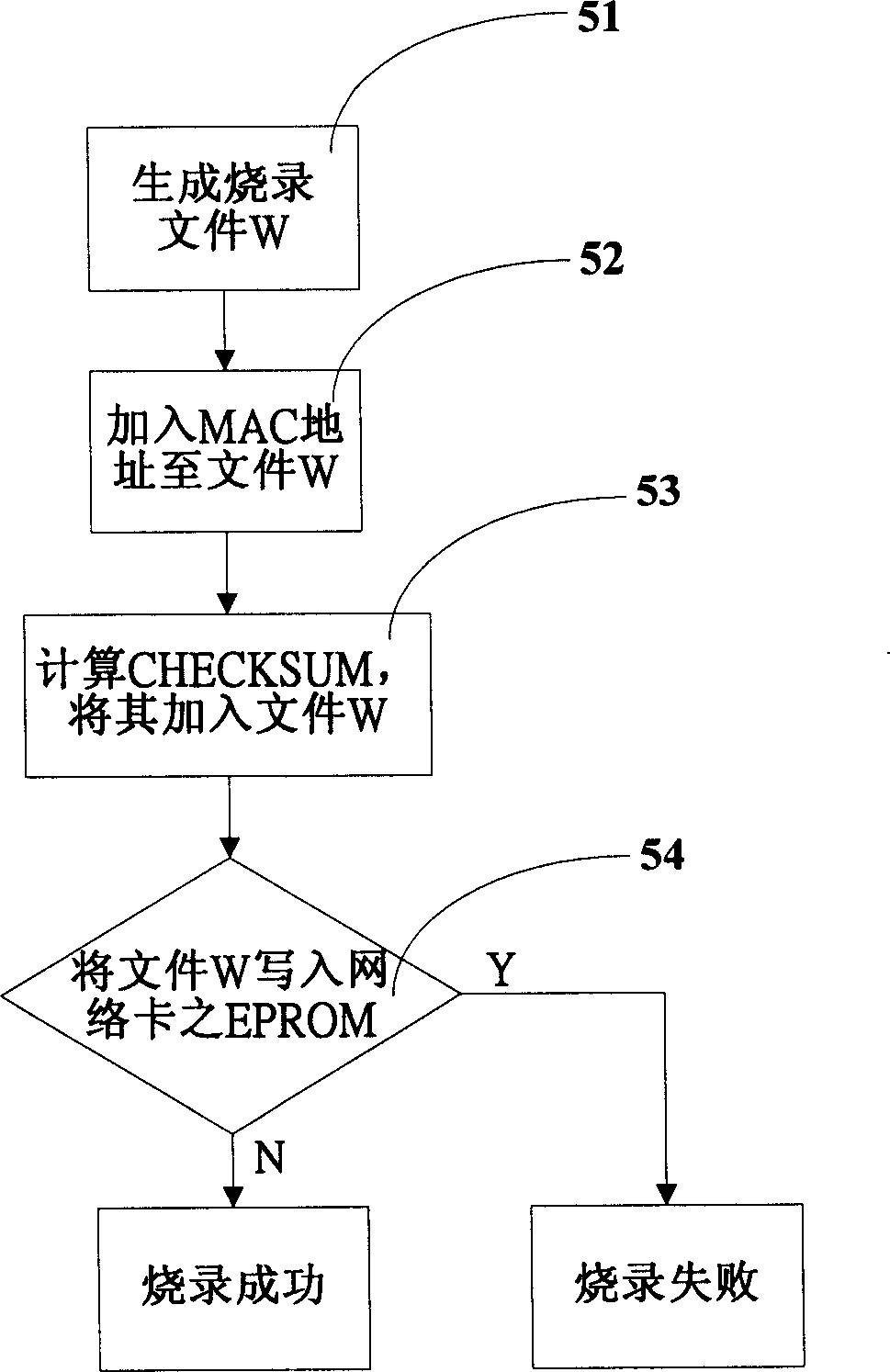
MAC address burning method
InactiveCN1635480ABurn to achieveAutomatically verify that it is correctData switching detailsNetwork connectionsMedia access controlSerial code
This invention relates to a media access control address burst copy method, which comprises the following steps: storing the multiple mediums interface control addresses into one burst copy machine to copy the net card through the device; then reading the burst contents in the machine and comparing it with the burst contents to test whether the content is right; the servo recoding the above sequence number and the control address and comparing the sequence number with the control address to avoid the burst copy repeating.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Data receiving and transmitting methods, devices and equipment
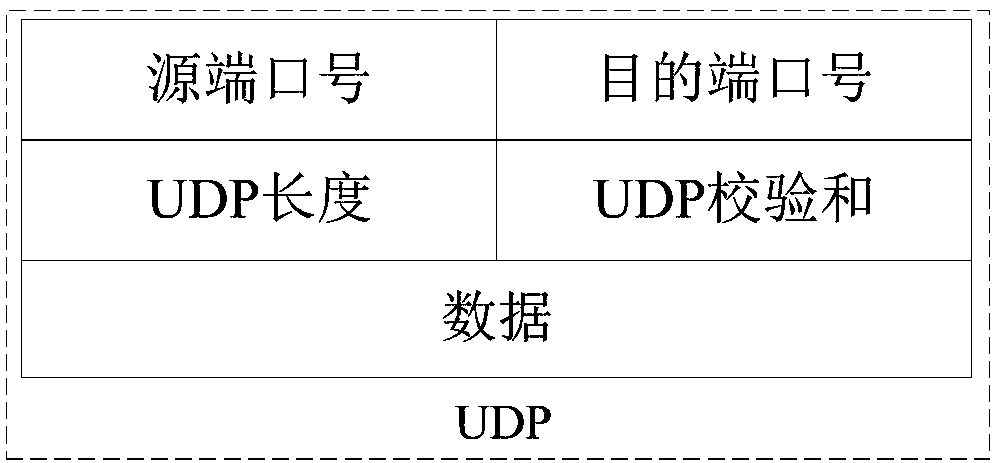
InactiveCN108234084ASolve packet lossError prevention/detection by transmission repeatPacket lossUser Datagram Protocol
The invention is applicable to the field of communication technology, and provides data receiving and transmitting methods, devices and equipment. The data transmitting method comprises the steps of:adding a sequence number for identifying a transmitting sequence of a data packet to a packet header of the transmitted data packet, wherein the sequence number is used for identifying the unreceiveddata packet by a receiving end; if the receiving end returns the sequence number of the unreceived data packet, storing the sequence number of the unreceived data packet to a preset packet loss list;detecting whether the packet loss list is empty, and if the packet loss list is not empty, transmitting the data packet corresponding to the sequence number stored in the packet loss list to the receiving end. According to the method, a packet loss list is created at a transmitting end to store the sequence number of the data packet that is not received by the receiving end, and then the sequencenumber in the packet loss list is transmitted to solve the problem of packet loss during transmission using a user datagram protocol in the prior art.
Owner:SHENZHEN SINOBRY ELECTRONICS LTD
Transmission method, transmitter and data processing system comprising a transmitter
InactiveUS20100107008A1Easy to useNot enough space to solveError preventionCode conversionData processing systemWrite buffer
A method for transmitting data is described that includes the steps of: Producing a data frame for transmission, the data frame including a sequence number and user data, saving a copy of the data frame in a retransmission buffer, and if said step of saving a copy requires that data already present in the retransmission buffer is overwritten, selecting the one or more oldest data frames in the retransmission buffer to be overwritten, in case an error is determined in the received data frame, communicating an error message to the transmitter of the data frame, which error message at least comprises an indication of the sequence number of the last correctly received data frame—upon receipt of such message and if available, retransmitting one or more data frames from the retransmission buffer having a sequence number higher than the sequence number communicated in the message.
Owner:ST ERICSSON SA
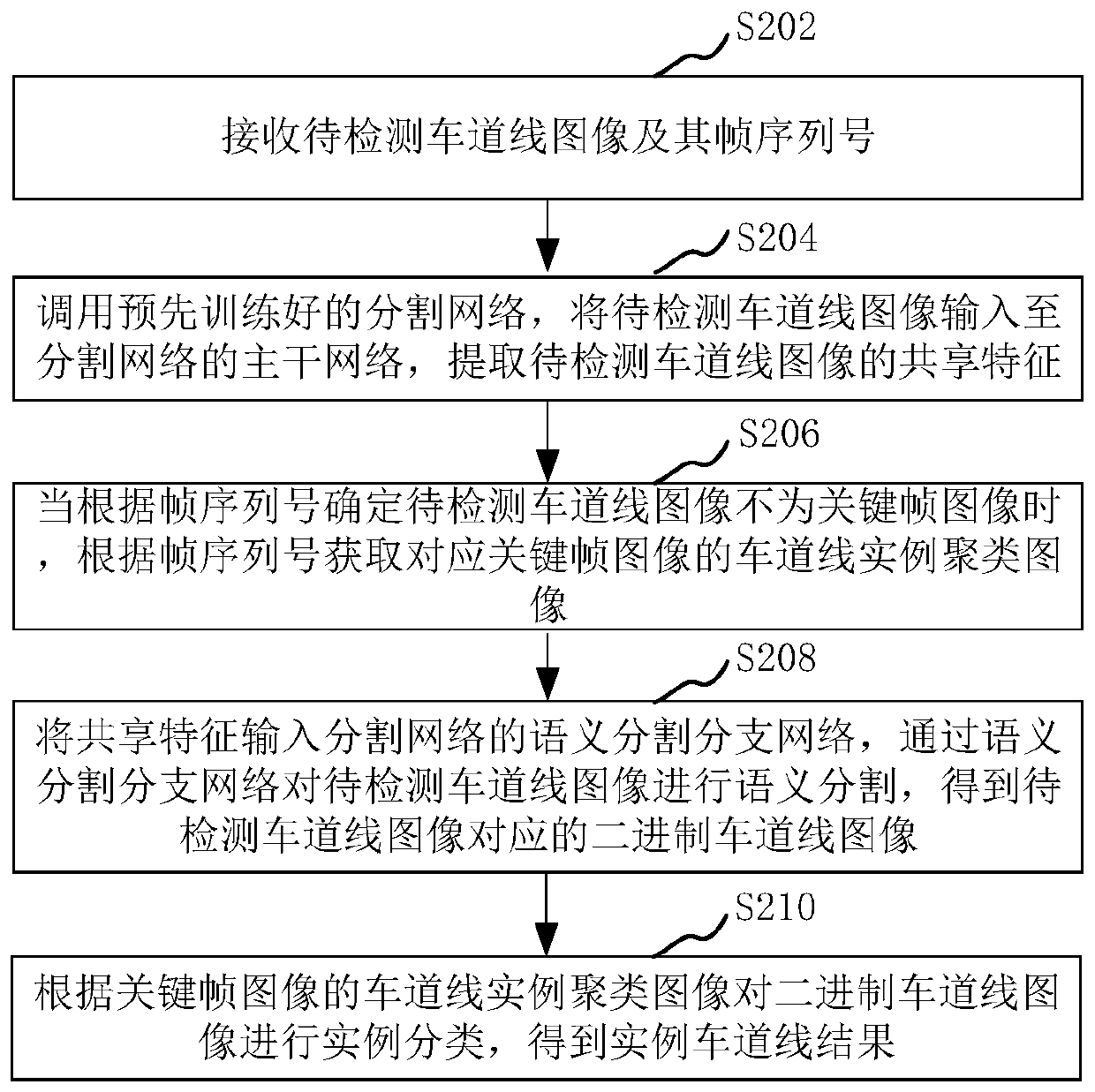
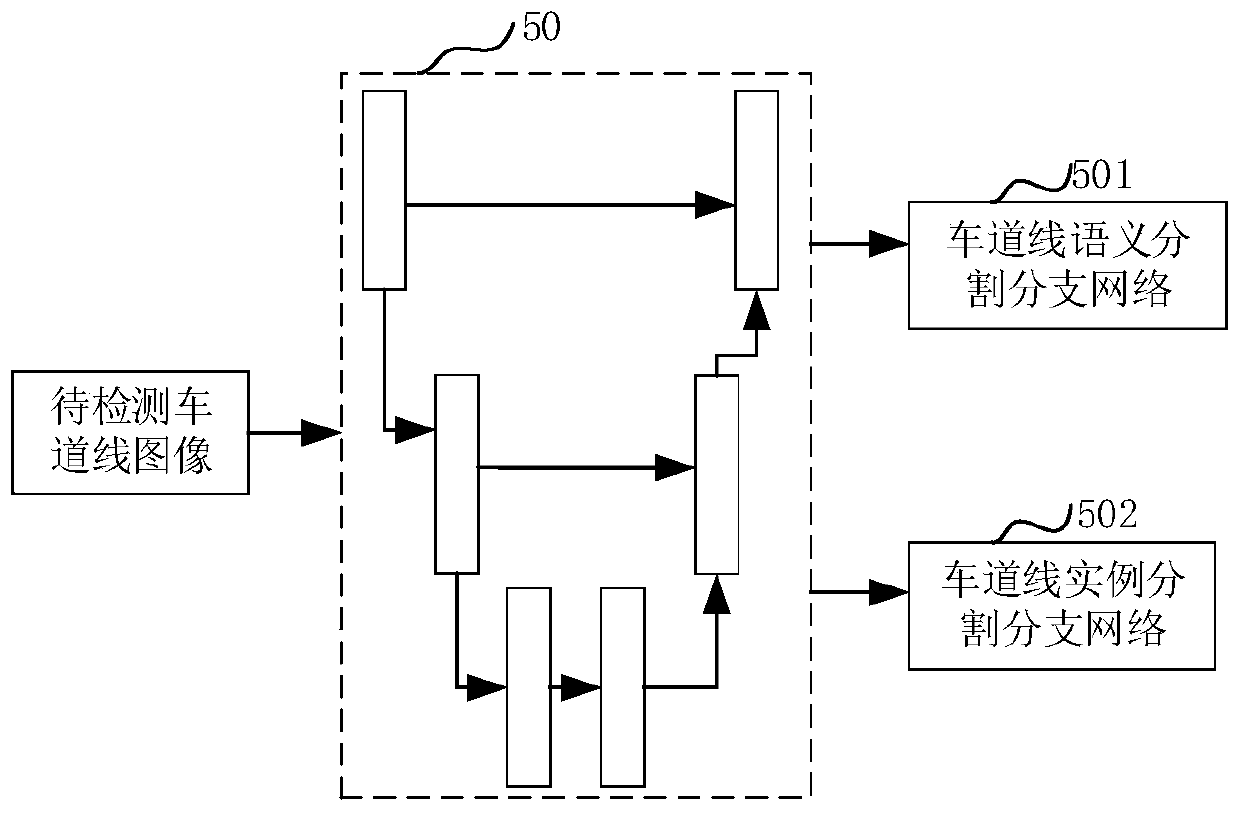
Lane line detection method and device, computer equipment and storage medium
PendingCN111178245AGuaranteed detection accuracySmall amount of calculationCharacter and pattern recognitionNeural architecturesPattern recognitionFrame sequence
The invention relates to a lane line detection method and device, computer equipment and a storage medium. The method comprises the following steps: receiving a to-be-detected lane line image and a frame sequence number thereof; calling a pre-trained segmentation network, inputting the to-be-detected lane line image into a backbone network of the segmentation network, and extracting sharing features of the to-be-detected lane line image; when it is determined that the to-be-detected lane line image is not the key frame image according to the frame sequence number, obtaining a lane line instance clustering image corresponding to the key frame image according to the frame sequence number; inputting the shared features into a semantic segmentation branch network of a segmentation network, andperforming semantic segmentation on the to-be-detected lane line image through the semantic segmentation branch network to obtain a binary lane line image corresponding to the to-be-detected lane line image; and performing instance classification on the binary lane line image according to the lane line instance clustering image of the key frame image to obtain an instance lane line image. The method can improve precision and reduce time consumption.
Owner:佑驾创新(北京)技术有限公司
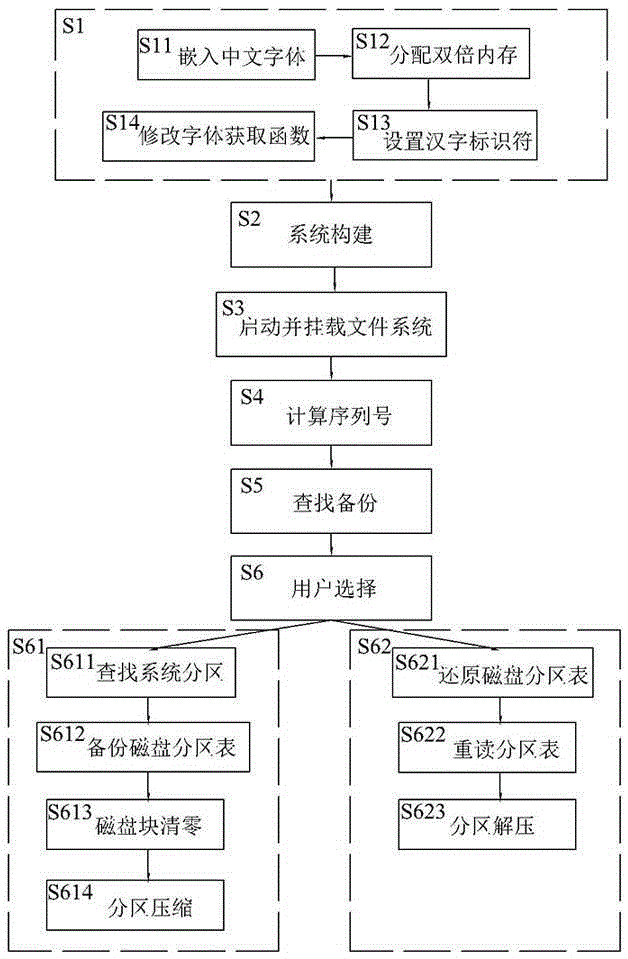
Method for backing up and restoring Windows operating system
ActiveCN105242986APrevent accidental deletionEliminate riskSpecial data processing applicationsRedundant operation error correctionFile systemBIOS
The present invention discloses a method for backing up and restoring a Windows operating system. The method comprises: firstly, adding a Chinese font into a FreeBSD kernel, and simultaneously modifying a font acquisition function of the kernel, so as to implement kernel-level Chinese display support; secondly, combining a GRUB2 boot manager that simultaneously supports BIOS (Basic Input / Output System) and UEFI specification, the FreeBSD kernel that is modified into a Chinese way, a user space program that implements backup and restoration functions, and a storage space that stores a backup file, so as to form a backup and restoration system; thirdly, by means of one of three modes of a local hard disk, an external memory and a PXE network, starting the backup and restoration system, and separately mounting a ZFS or NFS file system according to different starting modes; fourthly, by means of a sequence number module, calculating a "host sequence number" and a "hard disk sequence number" of a local computer, and using the sequence number as a unique sequence number, and checking whether a corresponding backup file exists; and finally, entering a "backup" or " restoration" process according to selection of a user.
Owner:金步国
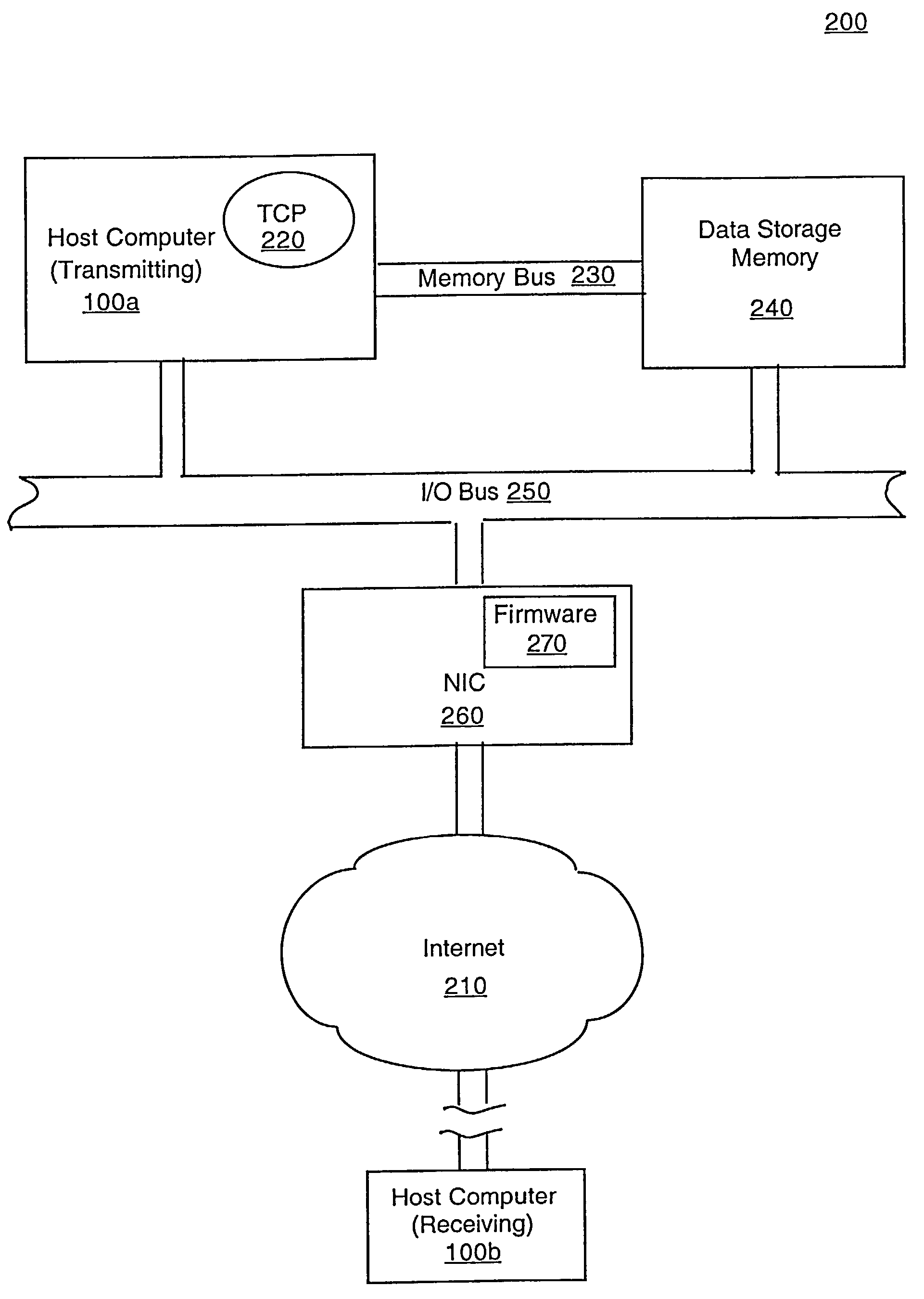
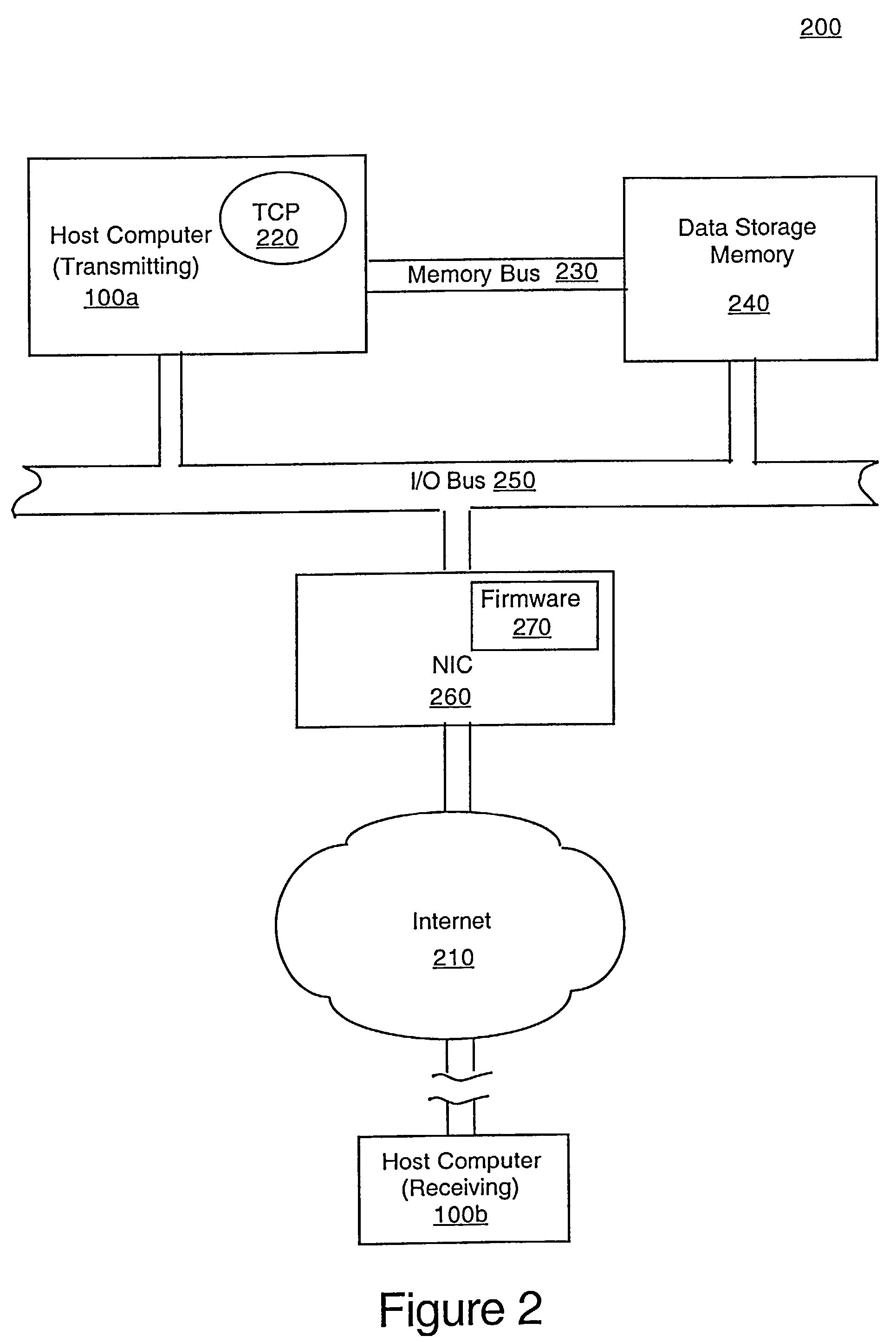
Method and system for TCP large segment offload with ack-based transmit scheduling
ActiveUS7313148B2Large amount of processingReduce the burden onData switching by path configurationLarge segment offloadData transmission
A method and system for offloading the transmission of large blocks of data from Transmission Control Protocol residing on a transmitting host computer to an intelligent network interface card (NIC) that schedules and performs transmittals. The NIC receives a pointer to the location of data to be transmitted, partitions the data into packets and writes sequence numbers in the headers of the packets. The NIC receives acknowledgements (ACKs) from the recipient system which contain a window size and beginning sequence number for the next transmittal. Provided the ACK indicates appropriate forward progress, the NIC continues to transmit until its buffer is empty. By allowing the NIC to process many packets in this fashion, significant burden is taken off the host computer system. In case of no forward progress, as evidenced by a duplicate ACK, or of an empty buffer, NIC returns control to the transmitting host computer for further action.
Owner:ORACLE INT CORP
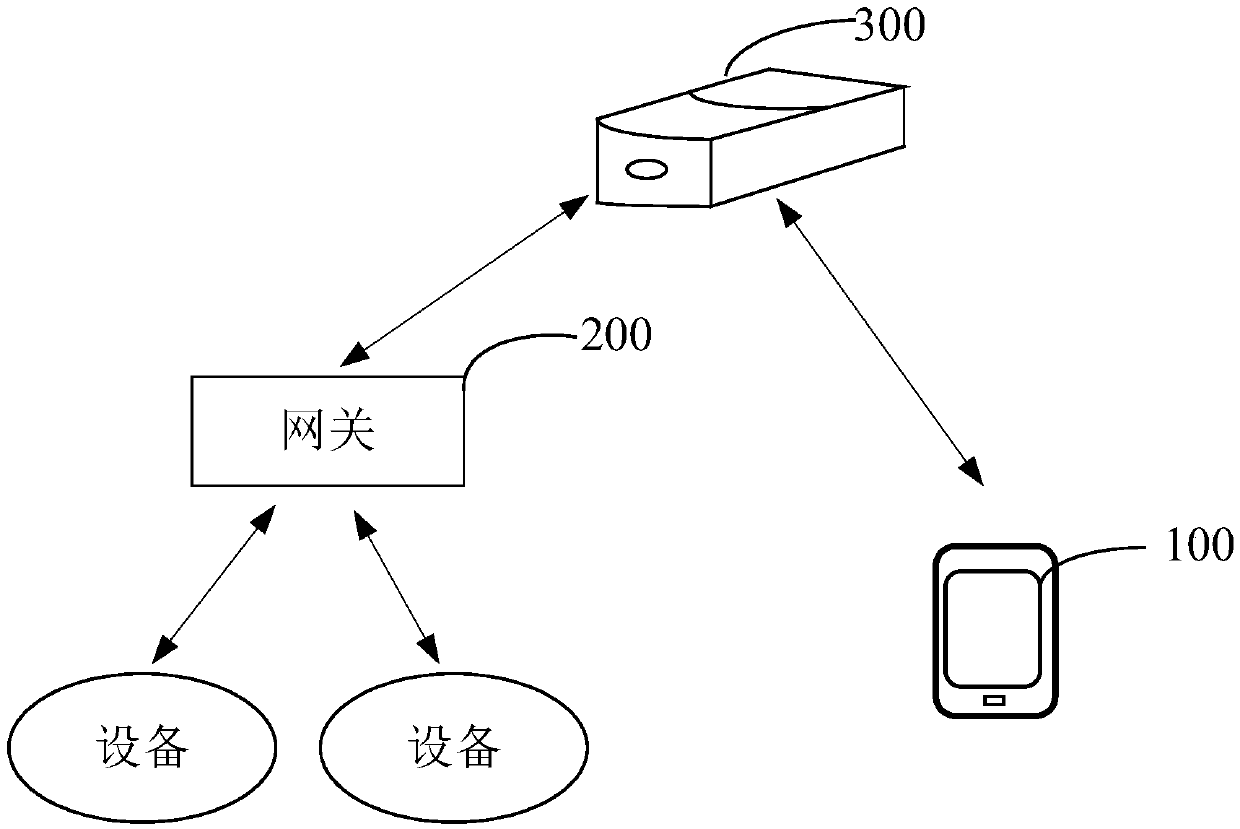
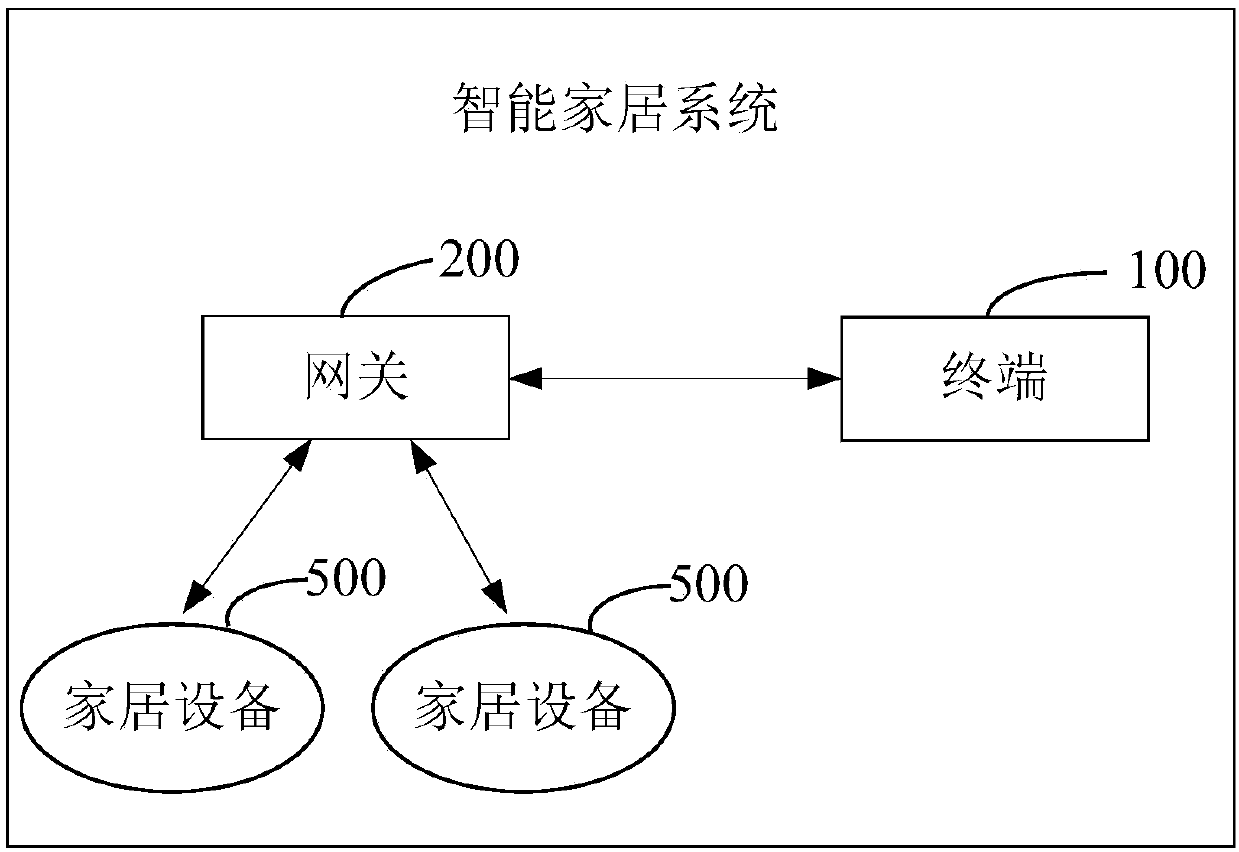
Intelligent home system, information encryption method, information encryption device and terminal
InactiveCN107948178AEnsure communication securityImprove securityKey distribution for secure communicationData switching by path configurationCommunications securityComputer terminal
The invention discloses an intelligent home system, an information encryption method, an information encryption device and a terminal, and belongs to the technical field of computer application. The intelligent home system comprises the terminal, a gateway and home equipment, wherein when generating control information according to a triggered control operation, the terminal obtains a key sequencenumber sent by the gateway, selects a key from stored key sequences according to the key sequence number to obtain an encryption key, encrypts the control information, and sends the encrypted controlinformation to the gateway; and, when receiving the encrypted information sent by the terminal, the gateway selects a decryption key according to the sent key sequence number, decrypts the encryptedinformation to obtain the control information, and sends the control information to the related home equipment, so that the home equipment works according to the control information. The invention further provides the information encryption device and the terminal. By means of the intelligent home system, the information encryption method, the information encryption device and the terminal disclosed by the invention, communication security in a local area network can be ensured; and the security of controlling the home equipment through the local area network can be improved.
Owner:SHENZHEN LUMIUNITED TECH CO LTD
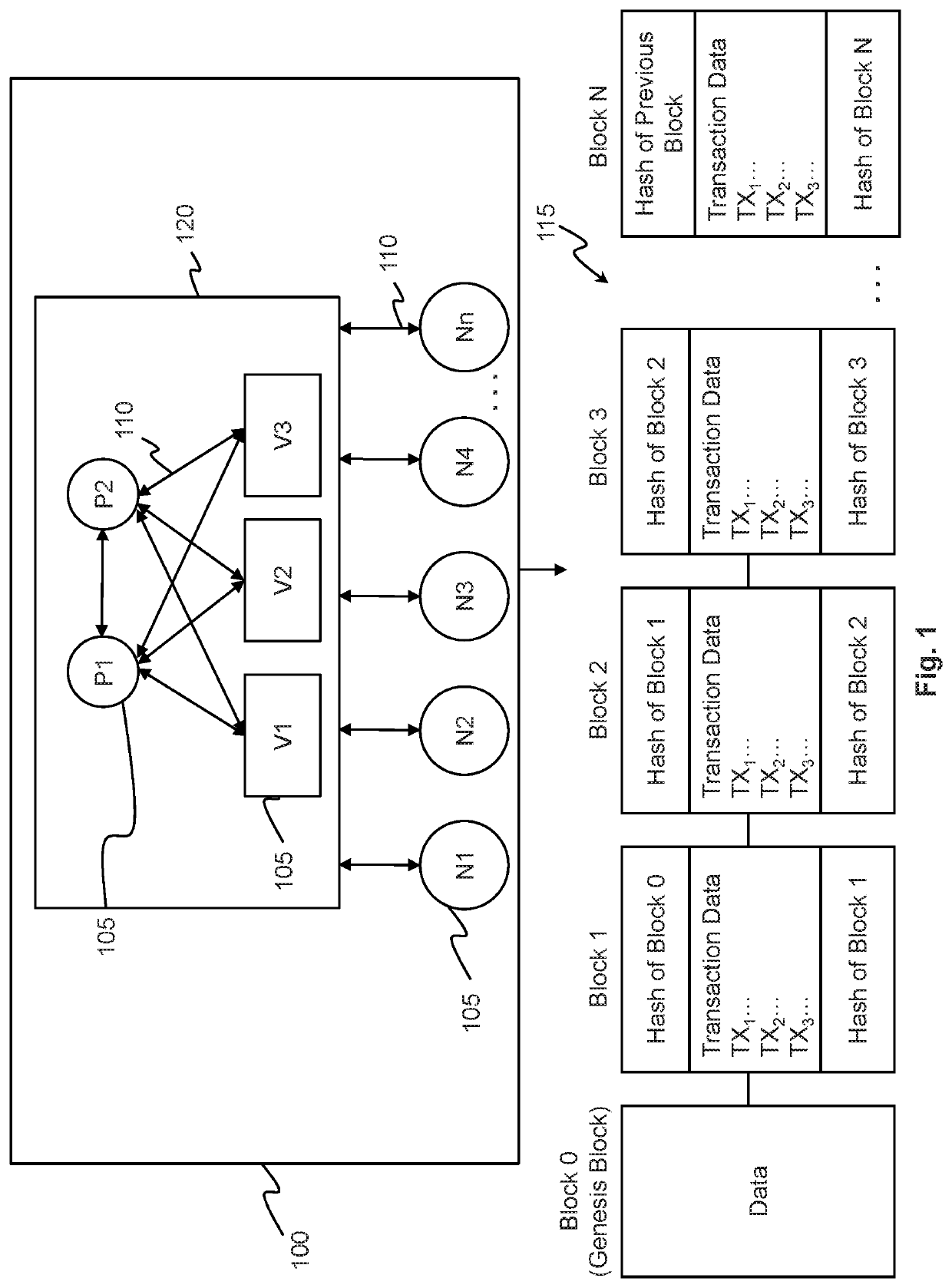
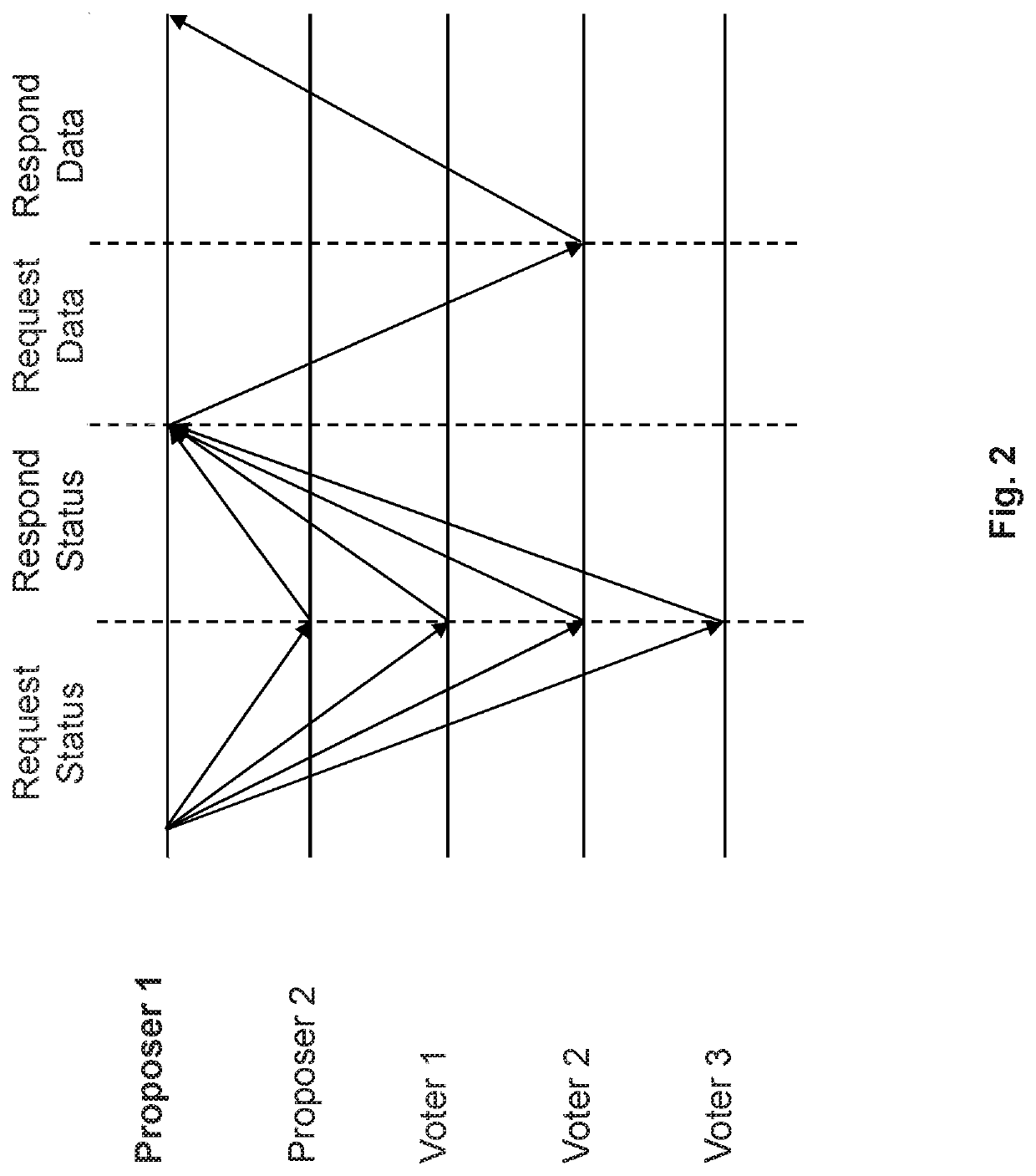
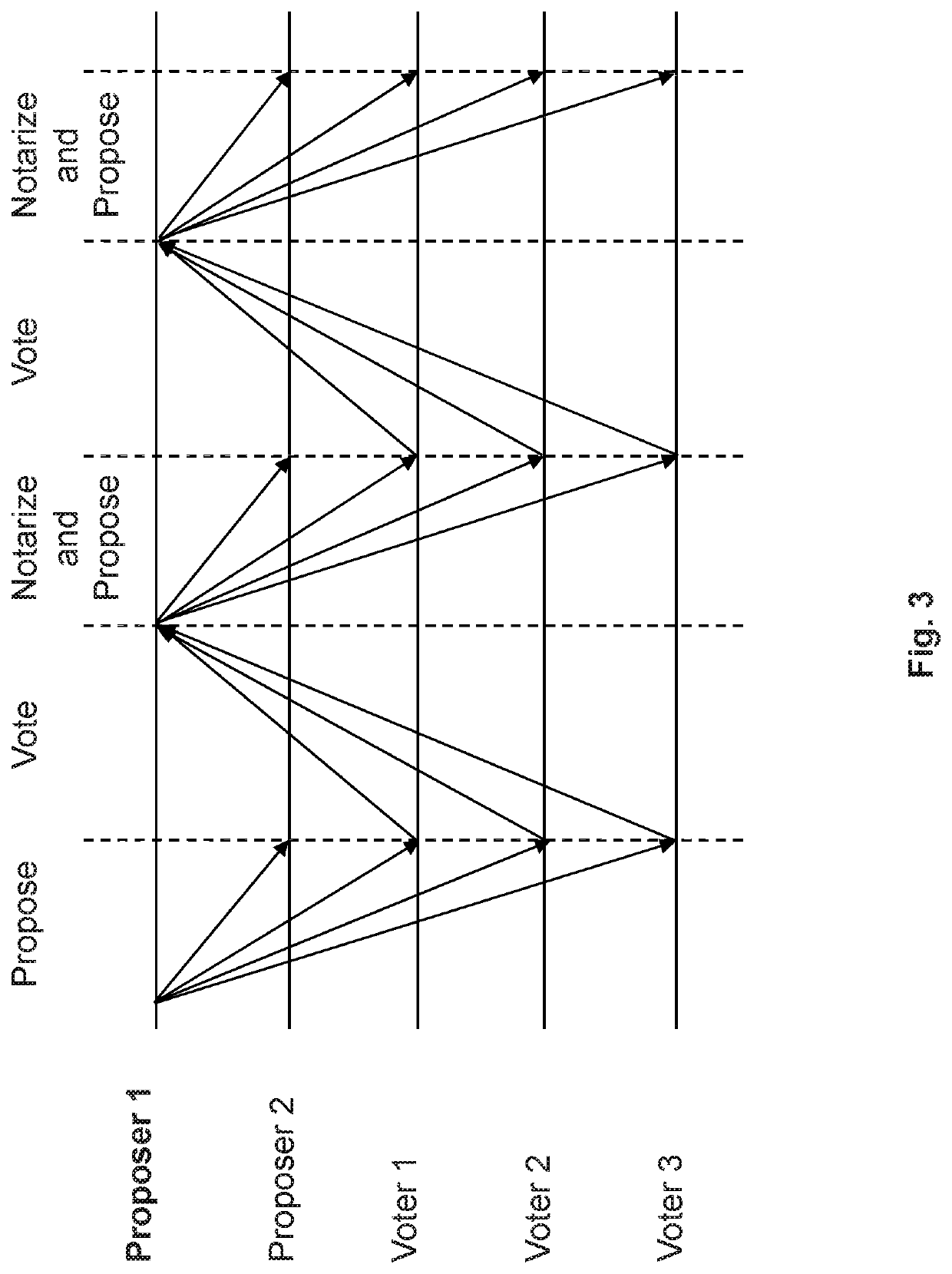
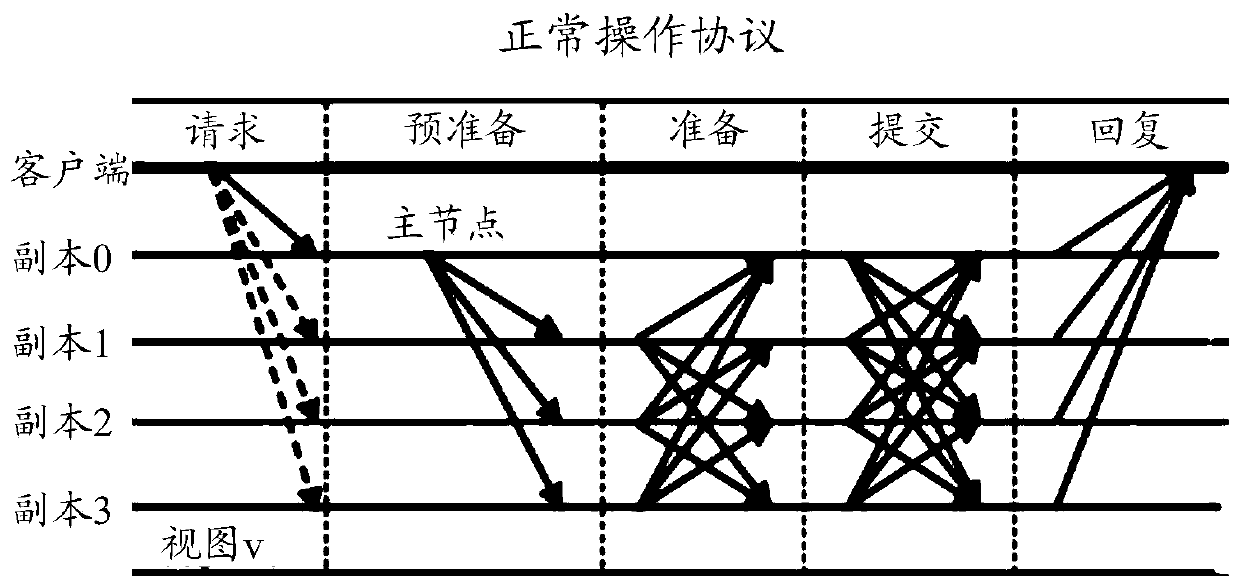
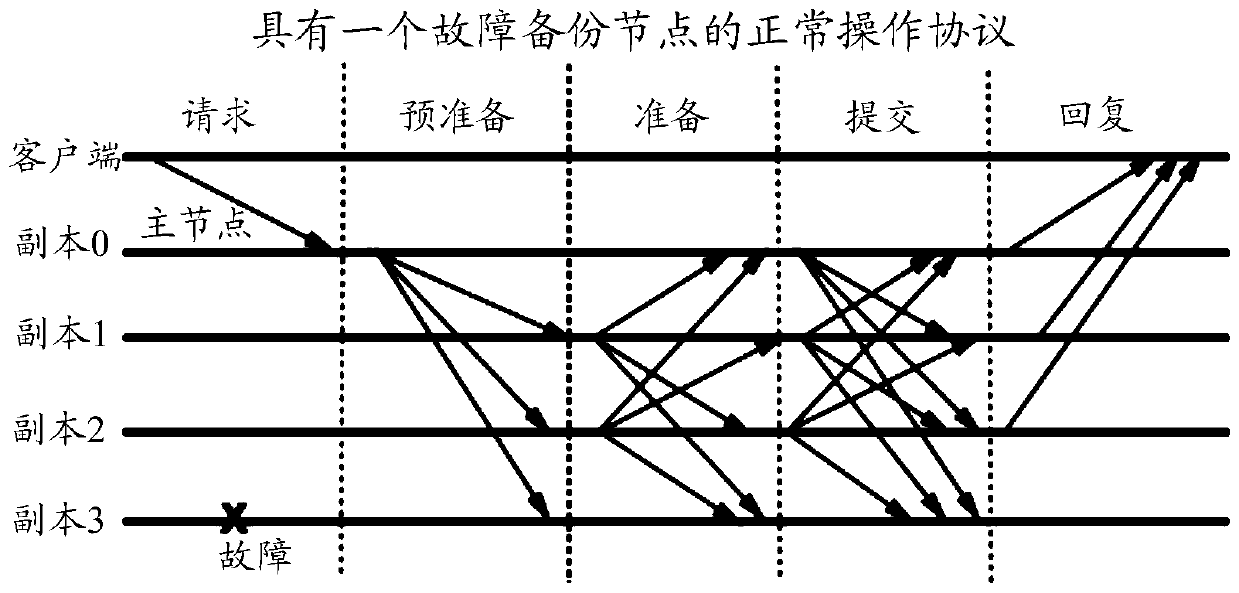
High throughput blockchain consensus systems and methods with low finalization time
The present invention is directed blockchain systems and censuses protocols that adopt a pipelining technique. The systems and protocols involve a committee of consensus nodes that include proposer nodes and voter nodes. Each proposer node can send two or more unnotarized proposals to the voter nodes, and the voter nodes can vote on an unnotarized proposal when they have the same freshest notarized chain or block. A sequence number is provided to facilitate the operation of the systems and protocols. The sequence number can be used to determine the freshest notarized chain or block and the finalized chain and switch proposer node. The systems and protocols also provide other features such as chain syncer, committee election scheme, and committee reconfiguration. The systems and protocols further provide a simple finalization process and thus have a low finalization time.
Owner:THUNDER TOKEN INC
Double word compare and swap implemented by using triple single word compare and swap
InactiveUS20080228784A1Runtime instruction translationSpecial data processing applicationsComputer scienceSerial code
A Lock Free and Wait Free method of the appearance of an atomic double word compare and swap (DCAS) operation on a pointer and ABA avoidance sequence number pair of words while using atomic single word compare and swap (CAS) instructions. To perform this function an area of memory is used by this invention and described as a protected pointer. The protected pointer consists of three words, comprising of: a) a pointer to a memory location, such as a node in linked list, together with b) an ABA avoidance sequence number, and combined together with a third word containing c) a specially crafted hash code derived from the pointer and the ABA avoidance sequence number. The three words together are referred to as a three word protected pointer and are used by this invention for implementing a Lock-Free and Wait-Free method of simulating DCAS using three CAS instructions. The specially crafted hash code, when used in a manner as described in this invention, enable competing threads in a multithreaded environment to advance a partially completed method of the appearance of an atomic double word compare and swap (DCAS) operation on a pointer and ABA avoidance sequence number pair of words while using atomic single word compare and swap (CAS) instructions as partially executed by a different thread. The ability for any thread to complete a partially completed appearance of DCAS provides for wait free operation.
Owner:DEMPSEY JAMES G
PDCP packet transmission method
InactiveUS8804742B2Improve transmission performanceAvoid data lossError preventionData switching by path configurationWireless transmissionData loss
Owner:LG ELECTRONICS INC
Secure and auditable on-line system
InactiveUS20060236400A1Memory loss protectionError detection/correctionClosed systemTheoretical computer science
The present invention provides a method a system and a device for obtaining security and auditability in an on-line system. The system is a closed system and only auditors and / or authorities have access to the system. By means of a random number generator and a processing means a random number—sequence number pair is generated and stored in a storage means. By verifying stored random number—sequence number pairs, every stored random number—sequence number pair can be authenticated.
Owner:BETWARE A ISLANDI
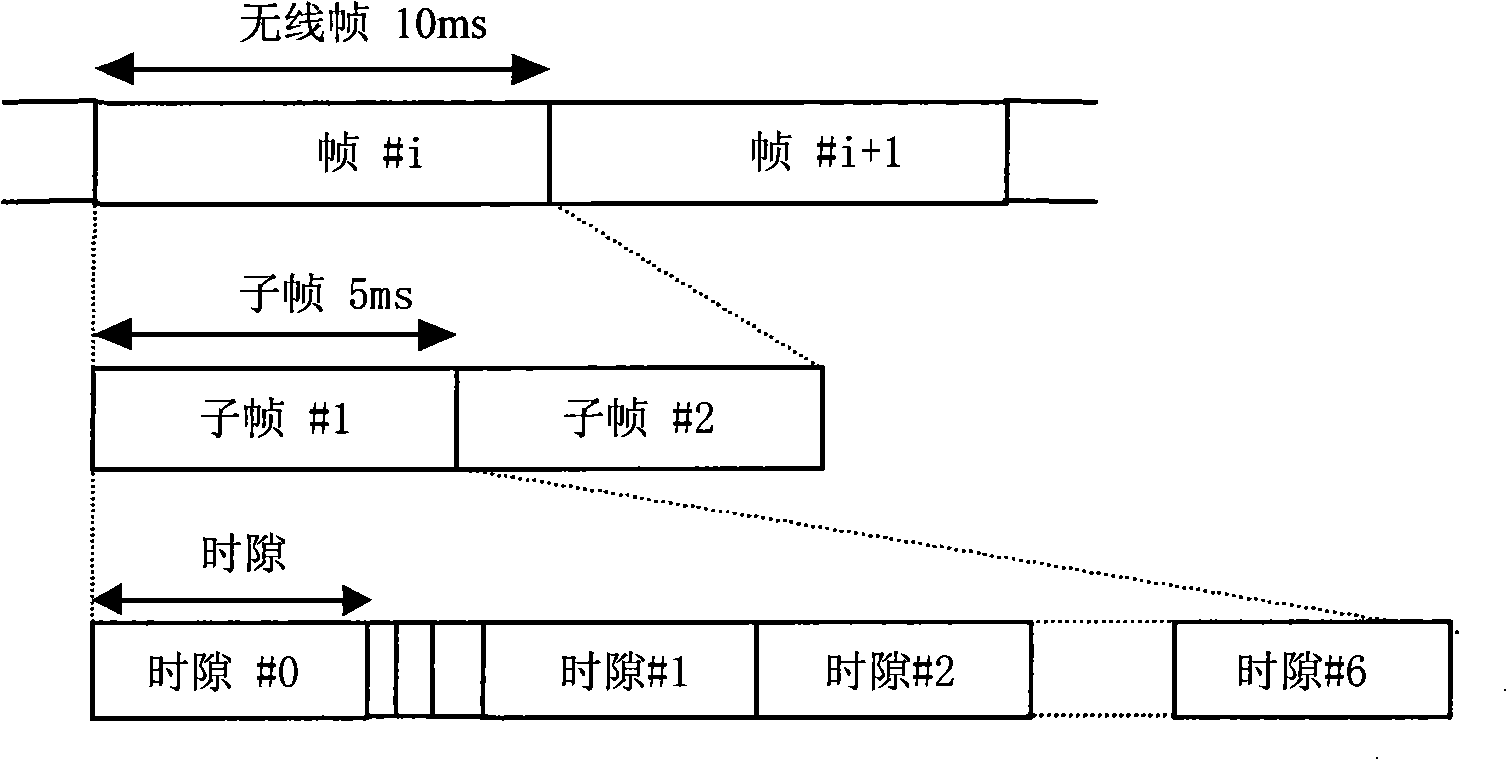
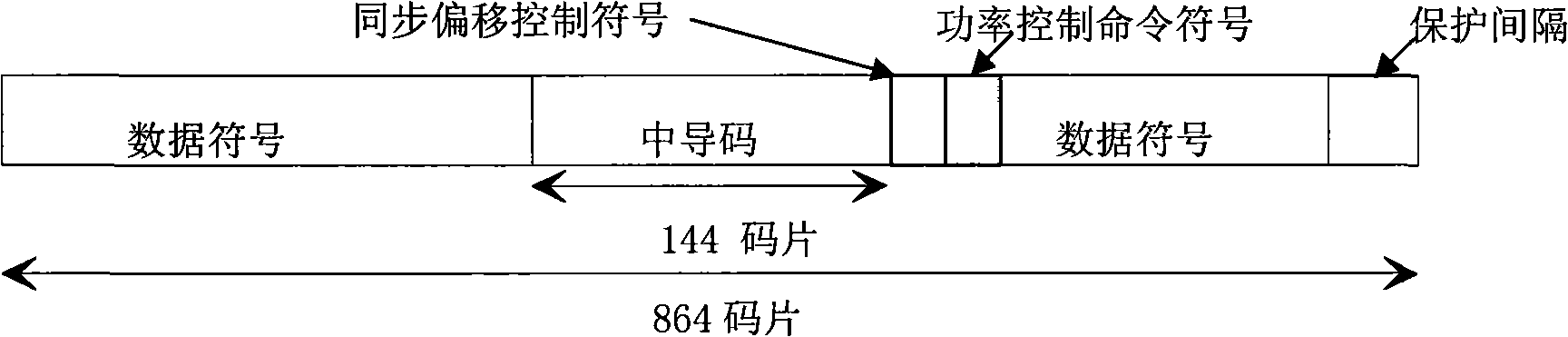
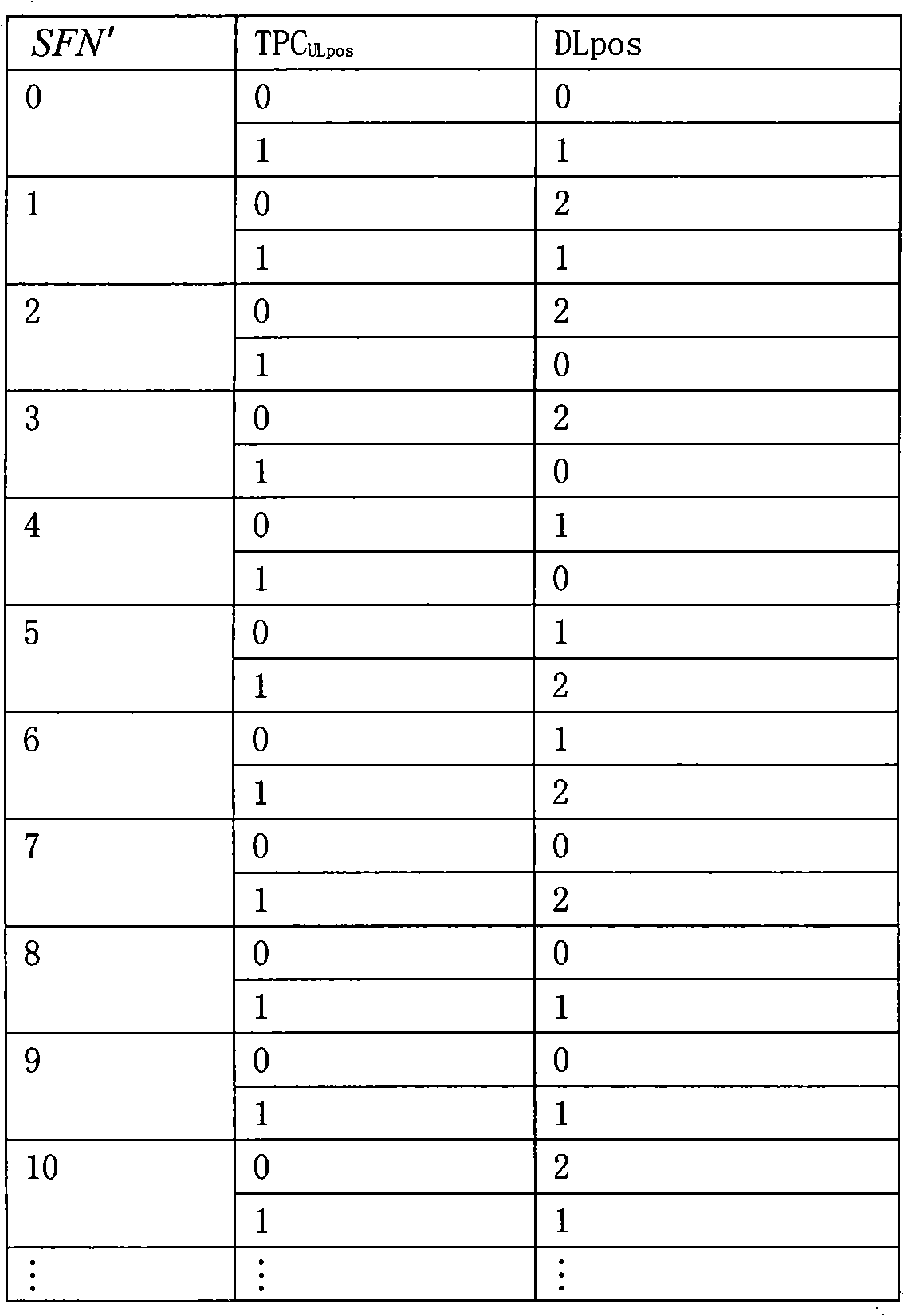
Power control command transmitting/receiving method and apparatus
ActiveCN101309096ARealize sendingAchieve receptionTransmission control/equalisingHigh level techniquesStart timeTransmitted power
The invention discloses a power control command transmitting and receiving method and the device thereof. The corresponding relation between a sequence number of a being transmitted or received power control command and a sequence number of a controlled time slot and code combined transmission channel pair can be obtained through a pre-generated search table of the sequence number of the time slot and code combined transmission channel pair or through an updating of the search table at the start time of each frame, so that to transmit the power control command in the time slot which carries the power control command, or to adjust the transmitting power level of the time slot and code combined transmission channel pair according to the obtained corresponding relation to realize the transmitting or receiving of the power control command. The realization of the method and device of the invention are simple and have little calculation, thus increase the processing efficiency of the transmitting or receiving of the power control command.
Owner:芯鑫融资租赁(厦门)有限责任公司
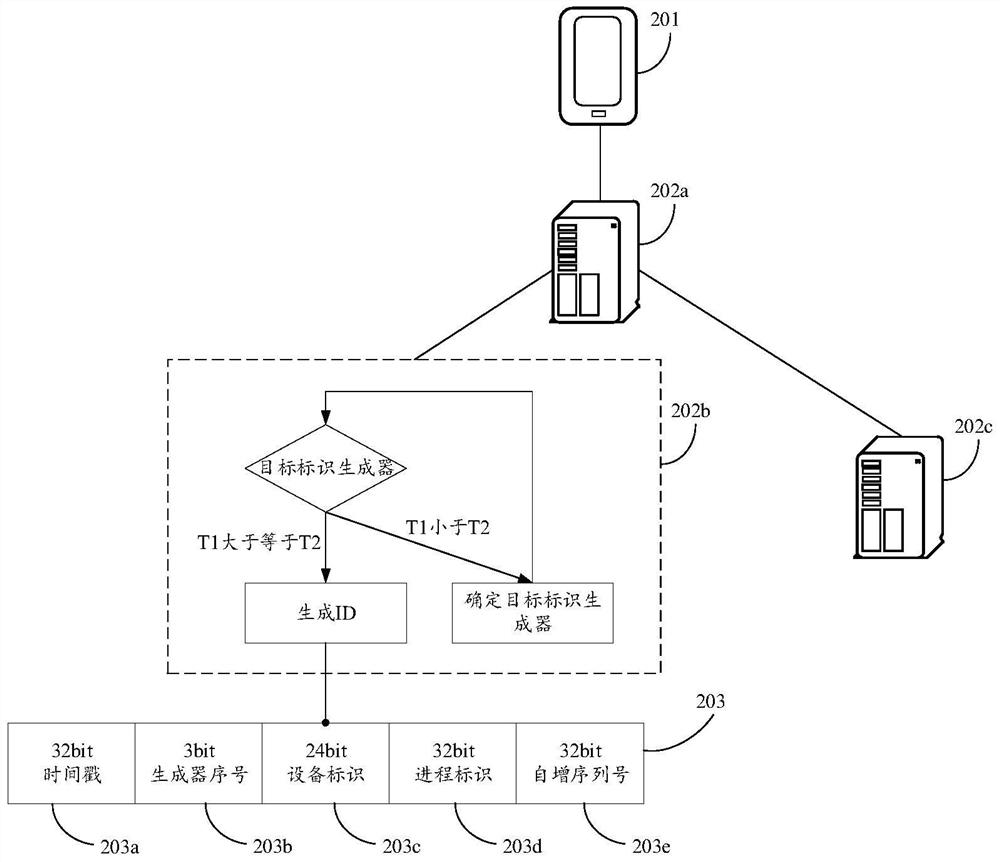
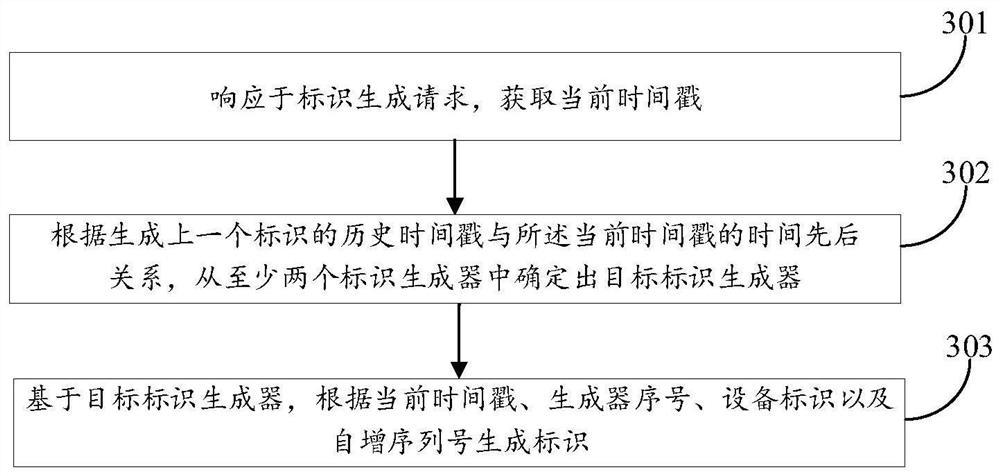
Identifier generation method and device, equipment and storage medium
PendingCN111917897AImprove reliabilityUniqueness guaranteedDatabase updatingTransmissionGeneration processClock recovery
The invention discloses an identifier generation method and device, equipment and a storage medium, and belongs to the technical field of computers. The method comprises the steps of obtaining a current timestamp in response to an identifier generation request; and determining a target identifier generator from the at least two identifier generators according to the time sequence relationship between the historical timestamp for generating the previous identifier and the current timestamp; based on the target identifier generator, generating an identifier according to the current timestamp, the generator serial number, the equipment identifier and the self-increasing serial number; when a clock callback condition occurs, enabling a identifier generation process to switch the target identifier generator for generating IDs until a clock returns to normal. The generator serial number is the serial number of the target identifier generator in the at least two identifier generators, and theserial numbers of the identifier generators are different. Uniqueness of the generated ID when the target identifier generator is switched is ensured. Reliability of ID generation is improved.
Owner:深圳市腾讯网域计算机网络有限公司
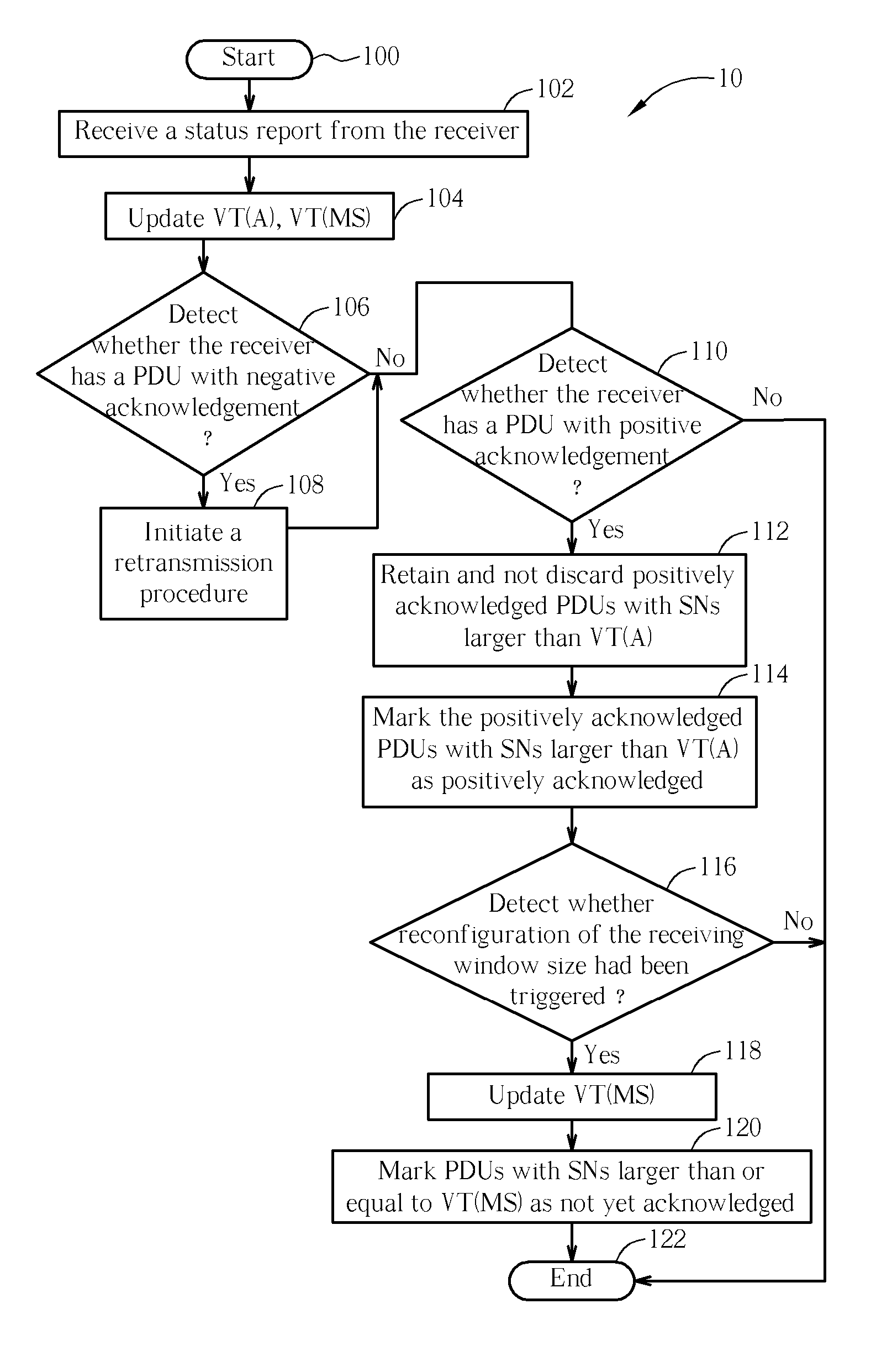
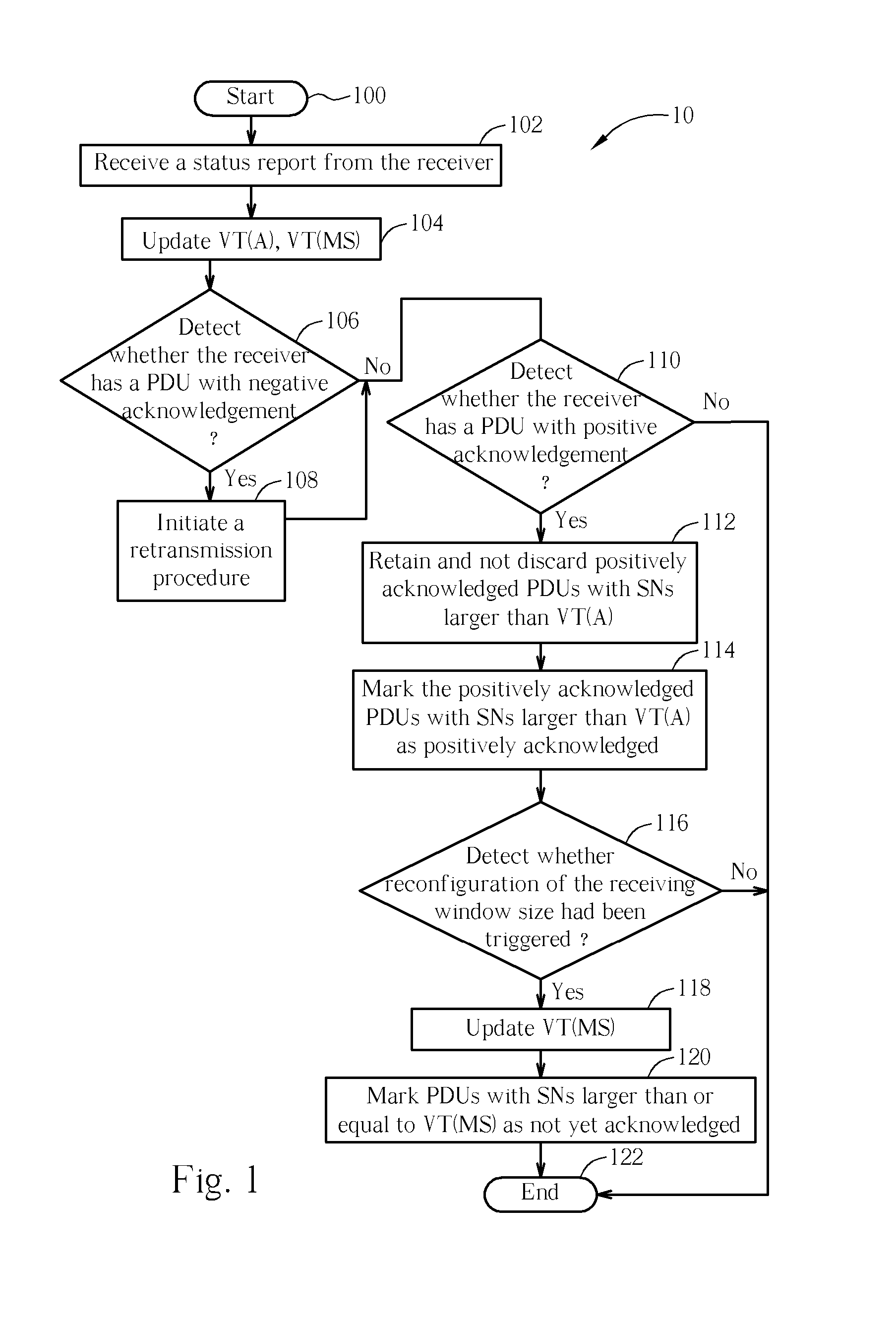
Method and Apparatus of a Procedure for Receiving Window Size Reconfiguration in a Communication System
InactiveUS20060245430A1Robust and efficient transmissionAvoid resetError preventionNetwork topologiesComputer hardwareState variable
A method for reconfiguring receiving window size of a receiving end of a communication system in a transmitting end of the communication system includes receiving a status report unit from the receiving end and updating an acknowledge state variable and a maximum send state variable according to the status report unit. Positively acknowledged packets with sequence numbers greater than the acknowledge state variable are retained in a buffer of the transmitting end. Positively acknowledged packets with sequence numbers greater than the acknowledge state variable are marked by the transmitter end as positively acknowledged packets. The maximum send state variable is updated according to a command for reconfiguring receiving window size of the communication system. Positively acknowledged packets with sequence numbers greater than or equal to the maximum send state variable are marked as not yet acknowledged packets.
Owner:INNOVATIVE SONIC
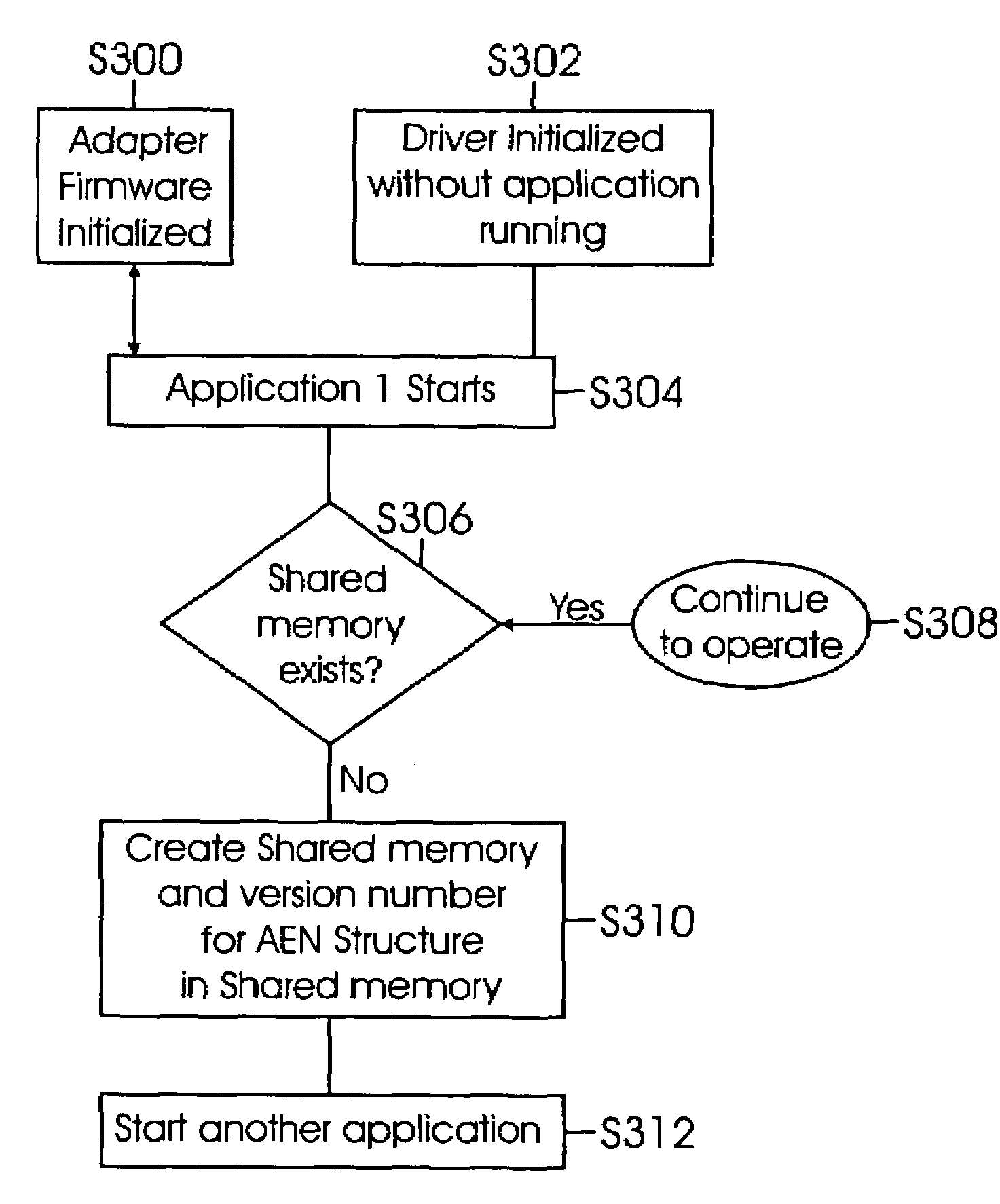
Method and system for processing asynchronous event notifications
InactiveUS7457887B1Quick understandingProgram controlInput/output processes for data processingComputer architectureEngineering
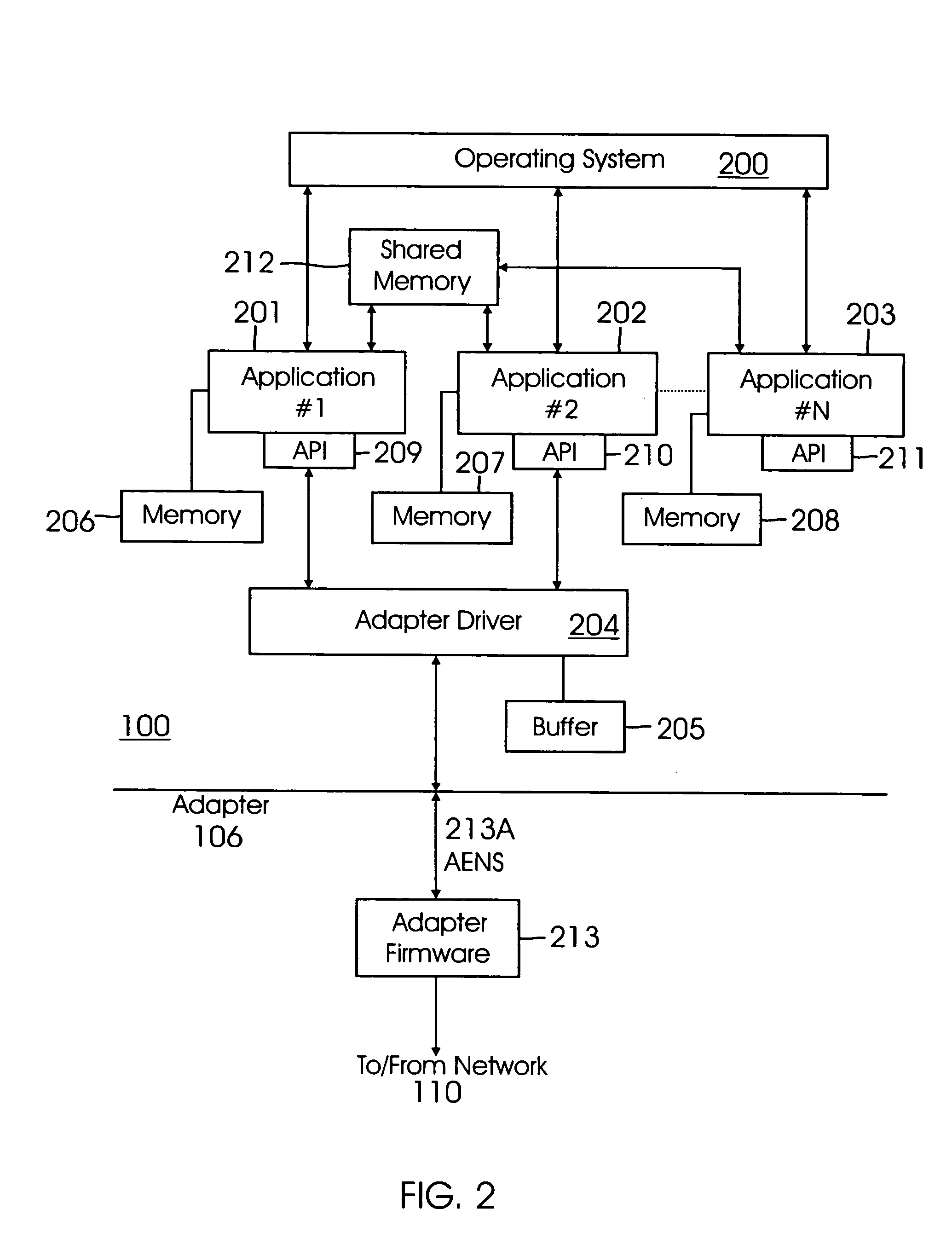
Method and system for managing asynchronous event notifications (AENs) including comparing an AEN sequence number at a shared memory location with an AEN sequence number at a local memory location controlled by a application; acquiring an AEN from the shared memory, if the sequence number of the AEN in the local memory is different from the sequence number of the AEN in shared memory; determining if a version number of the AEN is current; and generating an AEN if the version number is not current, wherein the generated AEN allows other applications to update AEN version numbers. The system includes firmware code executed in an adapter; an adapter driver executed on a host computing system stores the AENs in a memory buffer; and a plurality of applications that use a shared memory where AENs and a version number associated with the AENs are stored.
Owner:MARVELL ASIA PTE LTD
Data fragmentation secure transmission method and device based on pseudo-random number
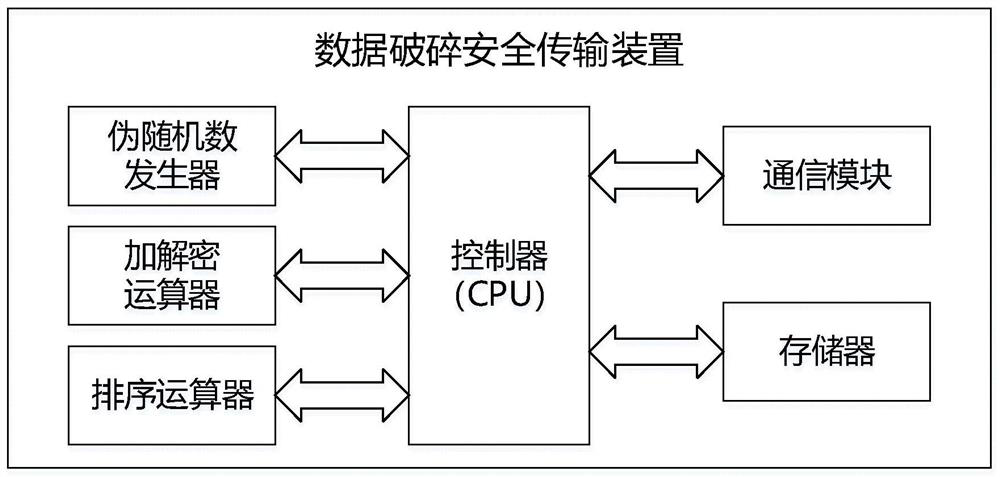
ActiveCN111865584AImprove confidentialityIncrease the difficulty of crackingKey distribution for secure communicationSequenceNumberEngineering
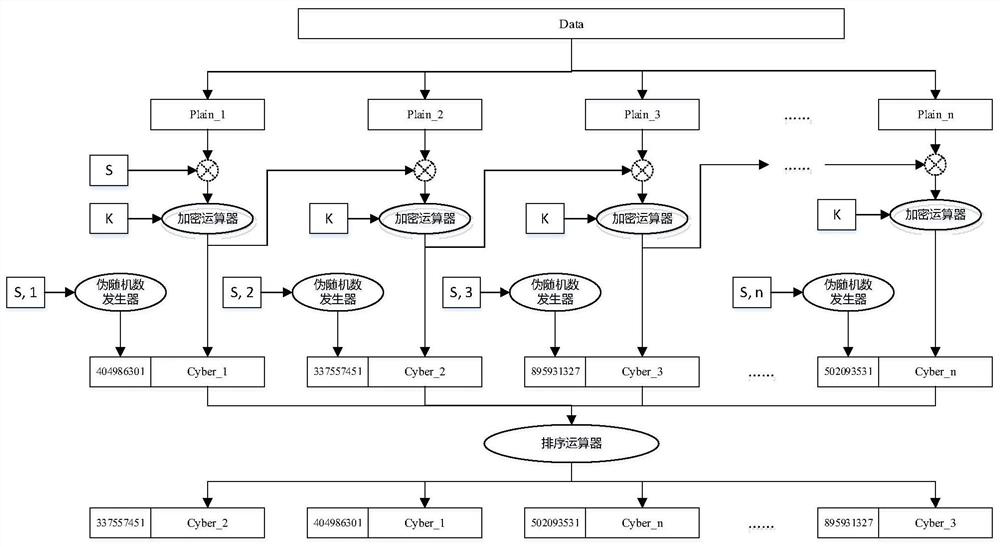
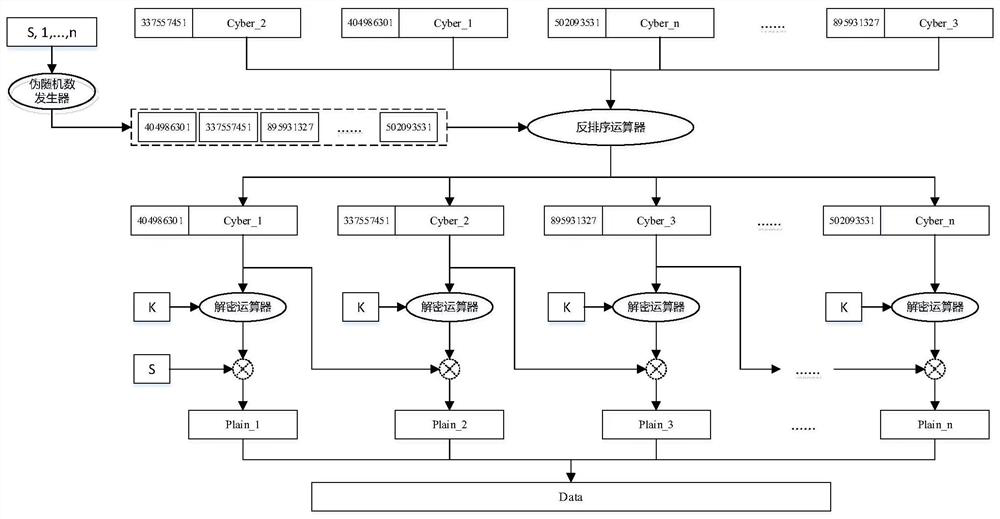
The invention provides a data fragmentation secure transmission method and device based on a pseudo random number, a computer storage medium and electronic equipment. The method comprises the following steps that: a data sender and a data receiver negotiate a key and a random seed; the data sender groups and encrypts plaintext data to be sent according to the secret key to obtain a plurality of ciphertext groups, generates a unique corresponding random serial number for each ciphertext group according to the random seed, sorts the ciphertext groups according to a certain rule and sends the sorted ciphertext groups to the data receiver; and the data receiver receives the ciphertext groups, generates a random serial number list according to the random seeds, rearranges the plurality of ciphertext groups according to the random serial number list, and decrypts the plurality of ciphertext groups according to the key to obtain plaintext data. According to the method, the sequence of the ciphertext groups is randomly scattered before the data is sent, and because the correct sequence of the plaintext groups is unknown, an attacker cannot obtain correct data information even if the attacker cracks a secret key, so that the confidentiality of the data is enhanced.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
System and method for ending view change protocol
ActiveCN110800258AOptimize the number of nodesPayment protocolsFault response safety measuresComputer engineeringComputer program
Methods, systems, and apparatus, including computer programs encoded on computer storage media, for performing view change. One of the methods is to be implemented on a blockchain maintained a number(N) of nodes and performed by a first node of the N nodes that is in a view change protocol. The method includes: obtaining, respectively from at least Q second nodes of the N nodes, at least Q firstmessages each comprising (1) a consistent current view known to the second node indicating a primary node designated among the N nodes and (2) a consistent current sequence number known to the secondnode, the current sequence number associated with a latest transaction or a latest block, wherein the current sequence number is larger than a first sequence number known to the first node; and responsive to obtaining the at least Q first messages, ending the view change protocol.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com