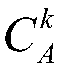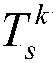Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
72results about How to "To achieve effective identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
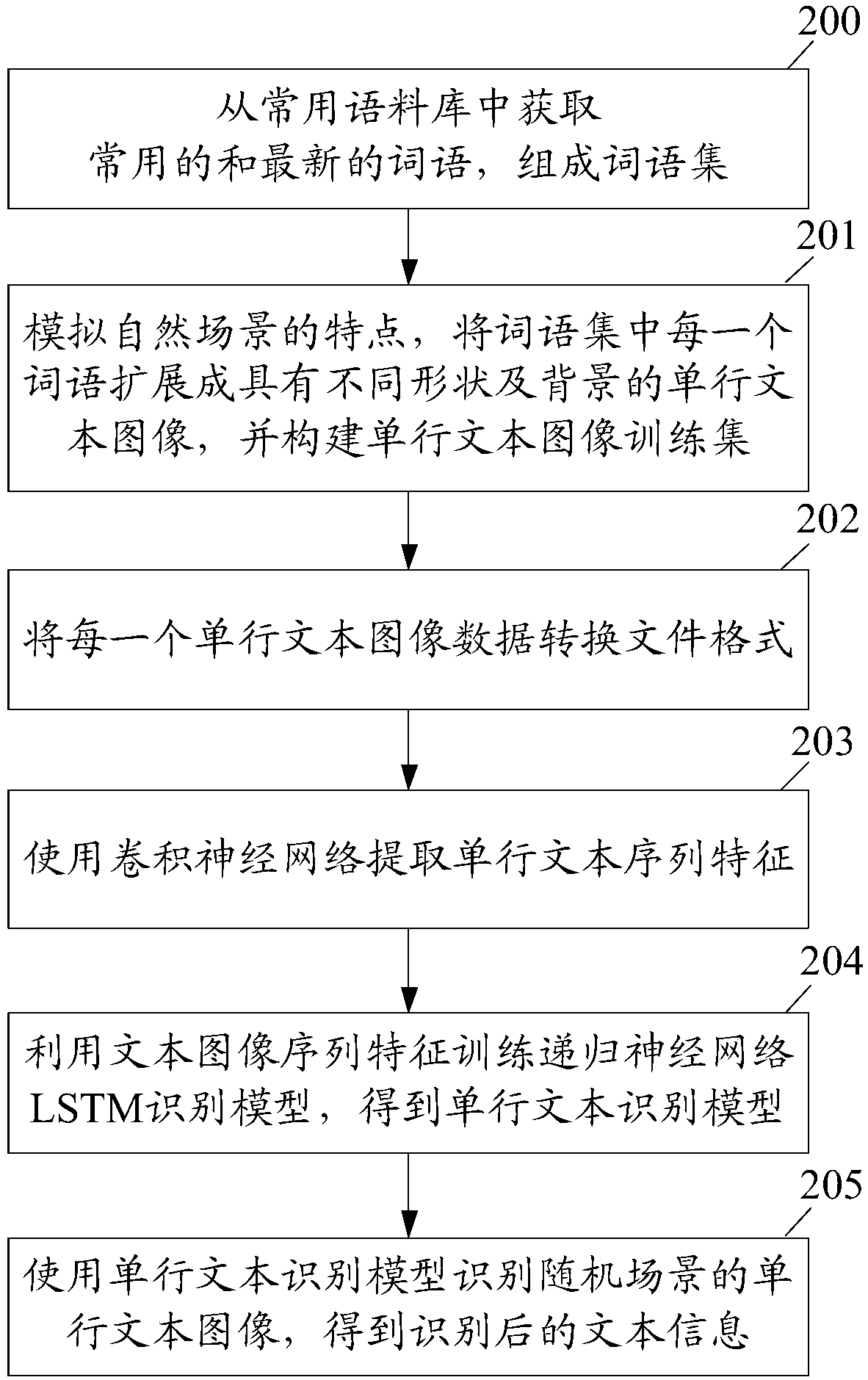
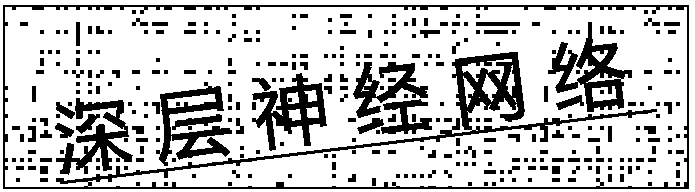
Image text identification method and device
ActiveCN108090400AImprove accuracyTo achieve effective identificationCharacter and pattern recognitionNeural learning methodsComputer visionIdentification device
The embodiment of the invention discloses an image text identification method comprising the following steps: creating a single-line text image training set; using the single-line text image trainingset to train a preset nerve network model, thus obtaining a single-line text identification model; using the single-line text identification model to identify single-line text images in a random scene, thus obtaining identified text information. Therefore, the method and device can effectively identify single-line text information in natural scenes, thus reducing the manual segmenting costs. The embodiment of the invention also discloses an image text identification device.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
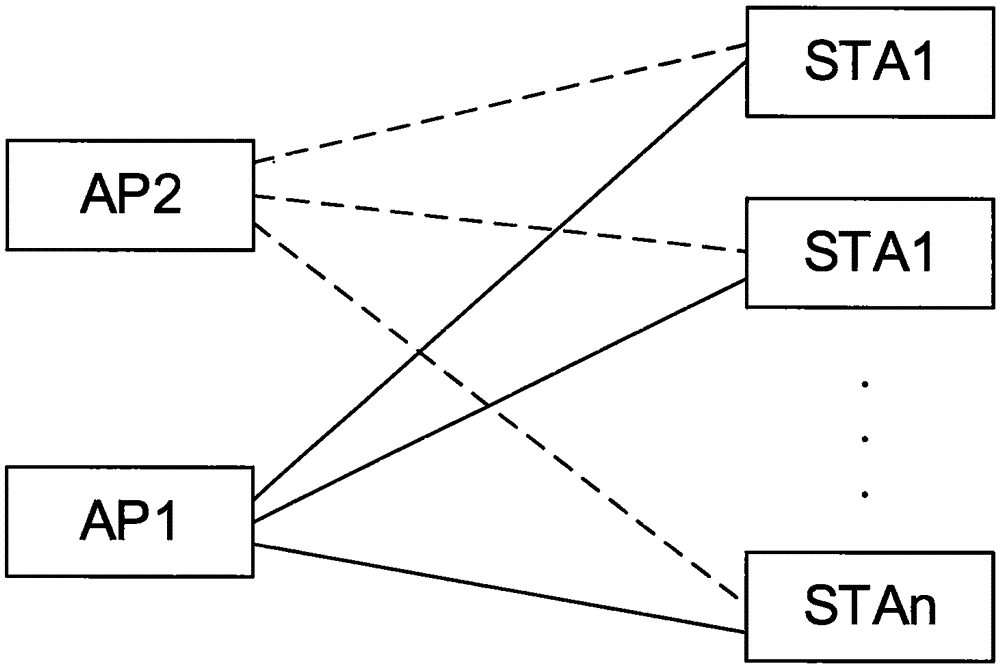
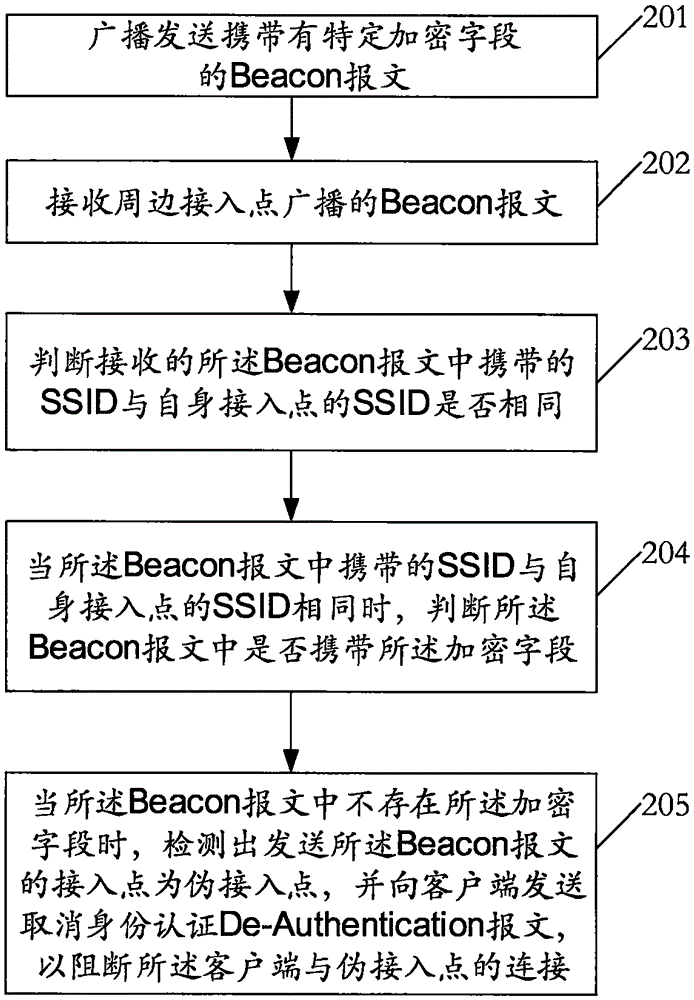
False-AP detecting and blocking method, wireless device and router
InactiveCN105657713ATo achieve effective identificationBlock connectionSecurity arrangementComputer hardwareBlocked Connection
The invention relates to the field of wireless network application and discloses a false-AP detecting and blocking method, a wireless device and a router. By broadcasting a Beacon message carrying a specific encrypted field and receiving Beacon messages broadcast by peripheral APs, whether SSIDs carried in the received Beacon messages are identical with an SSID of a self AP or not is judged; when the SSIDs carried in the received Beacon messages are identical with the SSID of the self AP, whether the encrypted field is carried in the Beacon messages or not is judged, it is detected that the AP sending the corresponding Beacon message is a false AP when the encrypted field does not exist in the corresponding Beacon message, and a De-Authentication message for canceling identity authentication is sent to a client side to block connection between the client side and the false AP. The false AP is effectively identified, and the client side is blocked and protected against the risk that personal information is stolen due to the fact that the client side is connected with the false AP.
Owner:ZHUHAI NETBOX INFORMATION TECH
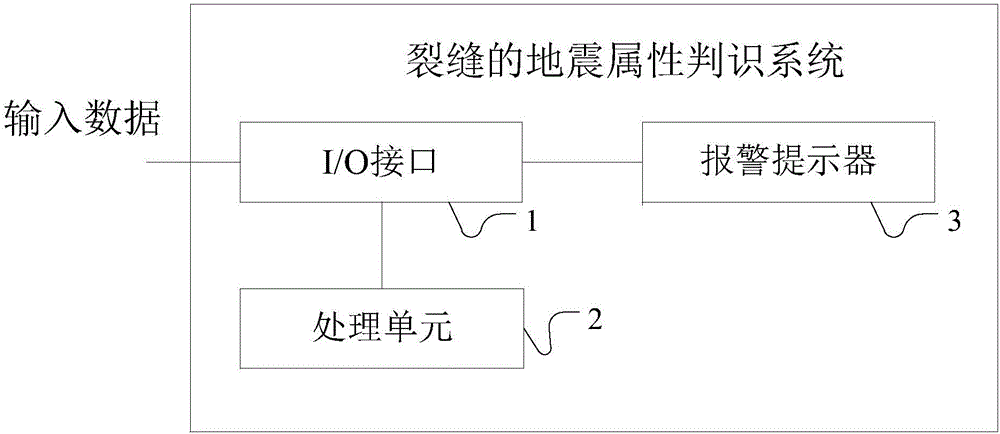
Crack seismic attribute judging system and crack seismic attribute judging method
ActiveCN106610508AIntelligently distinguish the advantages and disadvantages of seismic attributesQuick and effective identificationSeismic signal processingSeismology for water-loggingAnalysis dataLogging
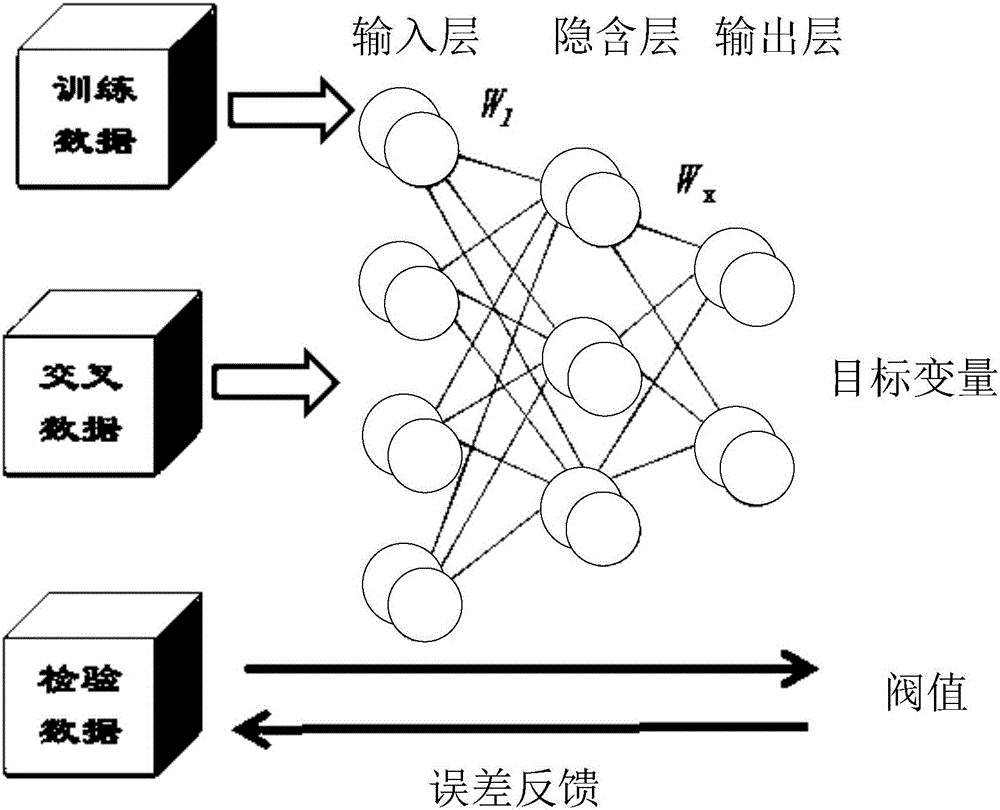
The application provides a crack seismic attribute judging system and a crack seismic attribute judging method. The method comprises the following steps: identifying and calculating out crack information of single-well crack density according to acquired imaging logging data and core analysis data, and generating a single-well crack model; extracting seismic attribute data of a specified type from acquired seismic data, and selecting an optimal seismic attribute of which the correlation with the reservoir meets a preset requirement; building a training model by taking the single-well crack model as an input signal and the optimal seismic attribute as an output signal; using an artificial intelligence nonlinear neural network to train the training model; and when the optimal seismic attribute in the training model meets a set screening condition, outputting the optimal seismic attribute meeting the set screening condition. According to the embodiments of the application, the advantages and disadvantages of numerous seismic attributes can be identified intelligently, quickly and accurately, well detection cracks can be identified effectively based on seismic attributes, and the effect and efficiency of actual operation are improved greatly.
Owner:PETROCHINA CO LTD
DSRC-based vehicle following interference prevention method and device, and application system
ActiveCN103514750ASolve the problem of car following interferenceGuaranteed uptimeTicket-issuing apparatusTransmission systemsError processingInterference problem
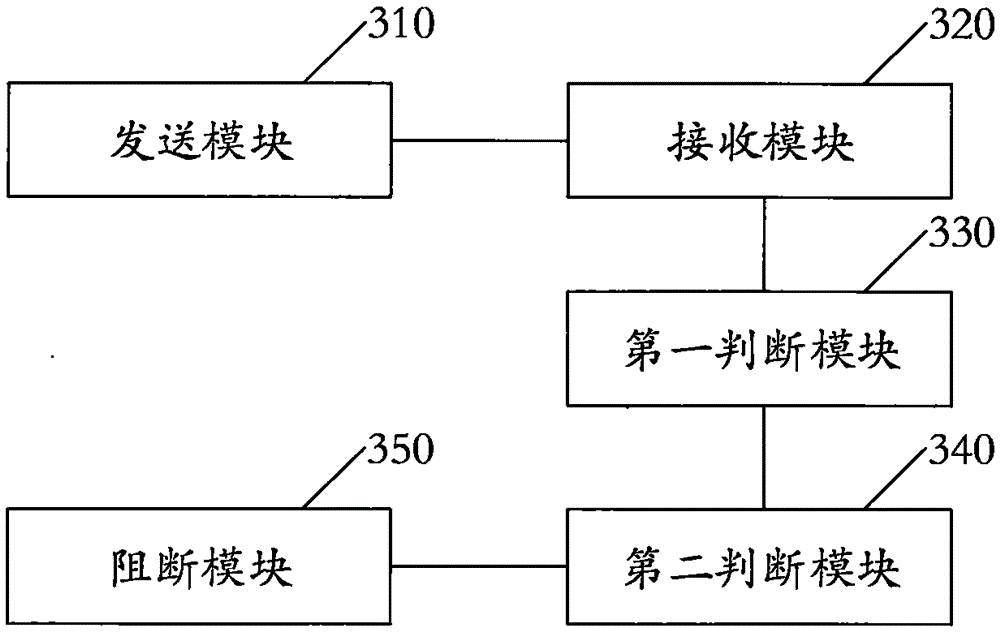
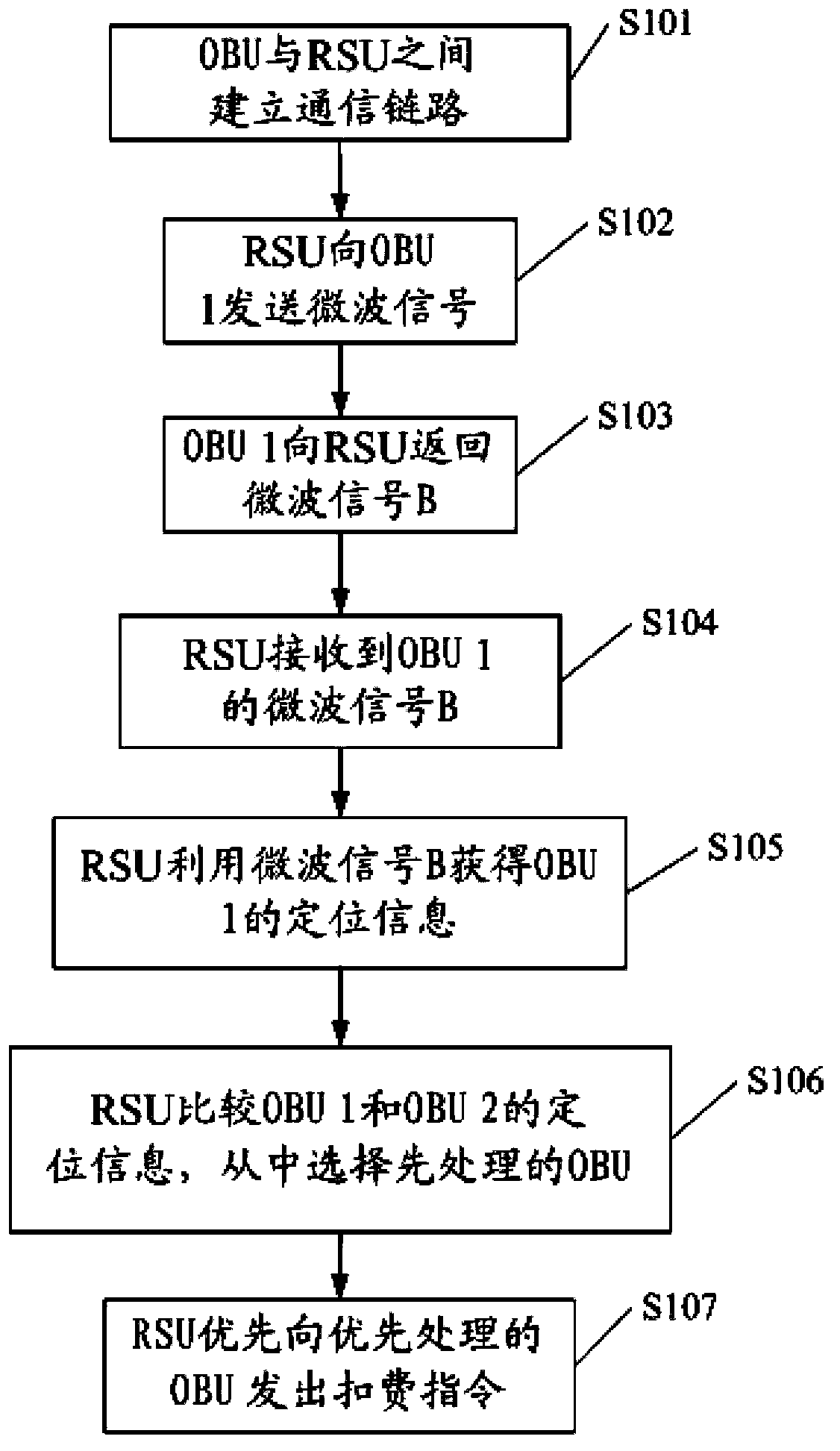
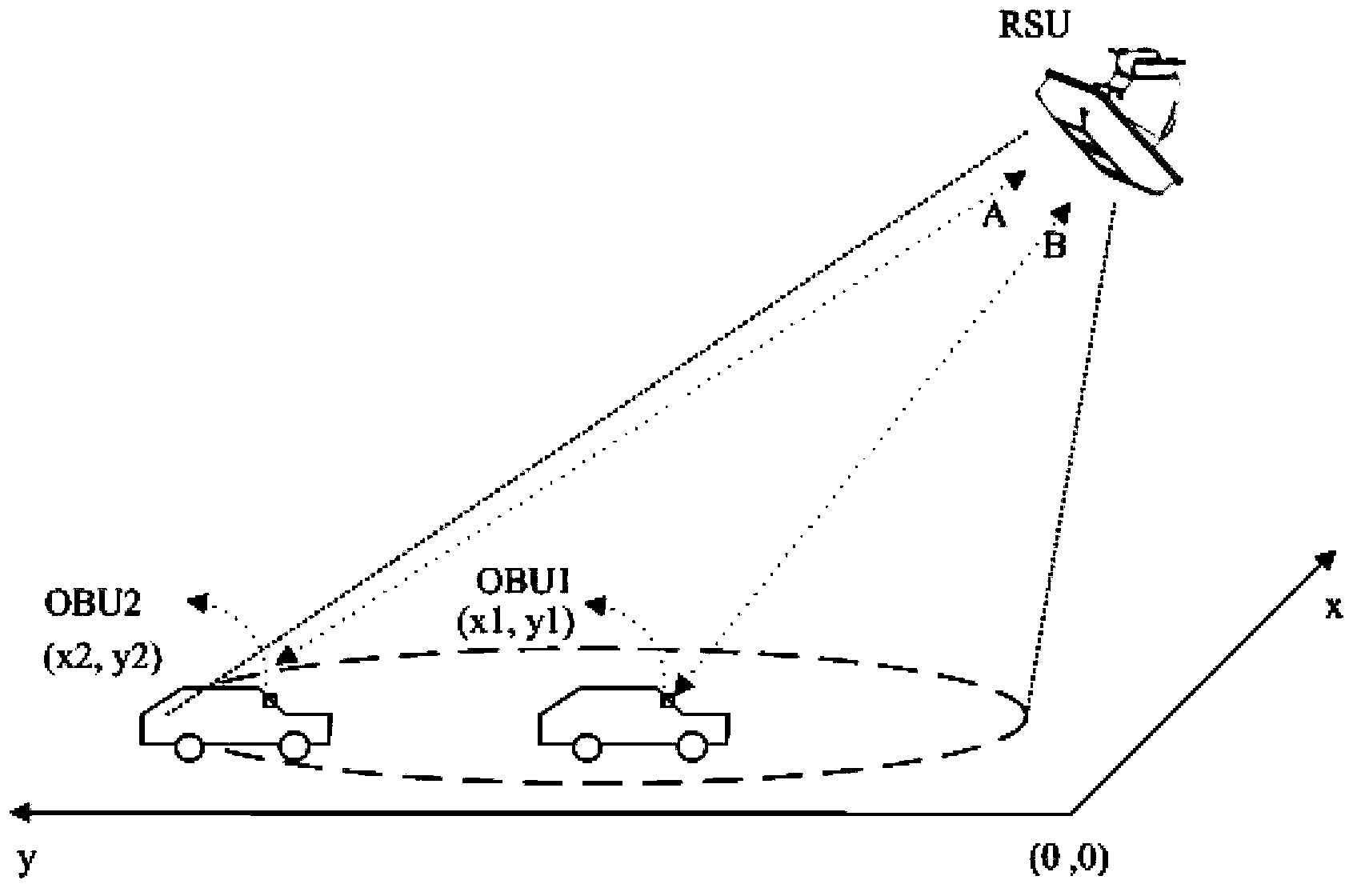
The invention discloses a DSRC-based vehicle following interference prevention method and device, and an application system. The method comprises the following step: the signal receiving step, wherein a RSU is used to receive microwave signals sent by a plurality of OBUs comprising a first OBU and a second OBU; the positioning step, wherein the RSU is used to acquire the positioning information of each OBU according to each microwave signal; and a comparing step, wherein the positioning information of the OBUs are compared, so that the RSU select the prioritized OBU from the OBUs. The method and device of the invention are applied in the field of highway traffic, valid identification is performed on positions of vehicles through the vehicle positioning technology, so that the prioritized OBU is selected accurately and the vehicle having the OBU is prioritized, so the normal interaction process between the prioritized OBU and the RSU will not be interfered by OBU on other vehicles, so that the vehicle following interference problem of the vehicles can be effectively solved, and the probability of error handling can be reduced.
Owner:SHENZHEN GENVICT TECH
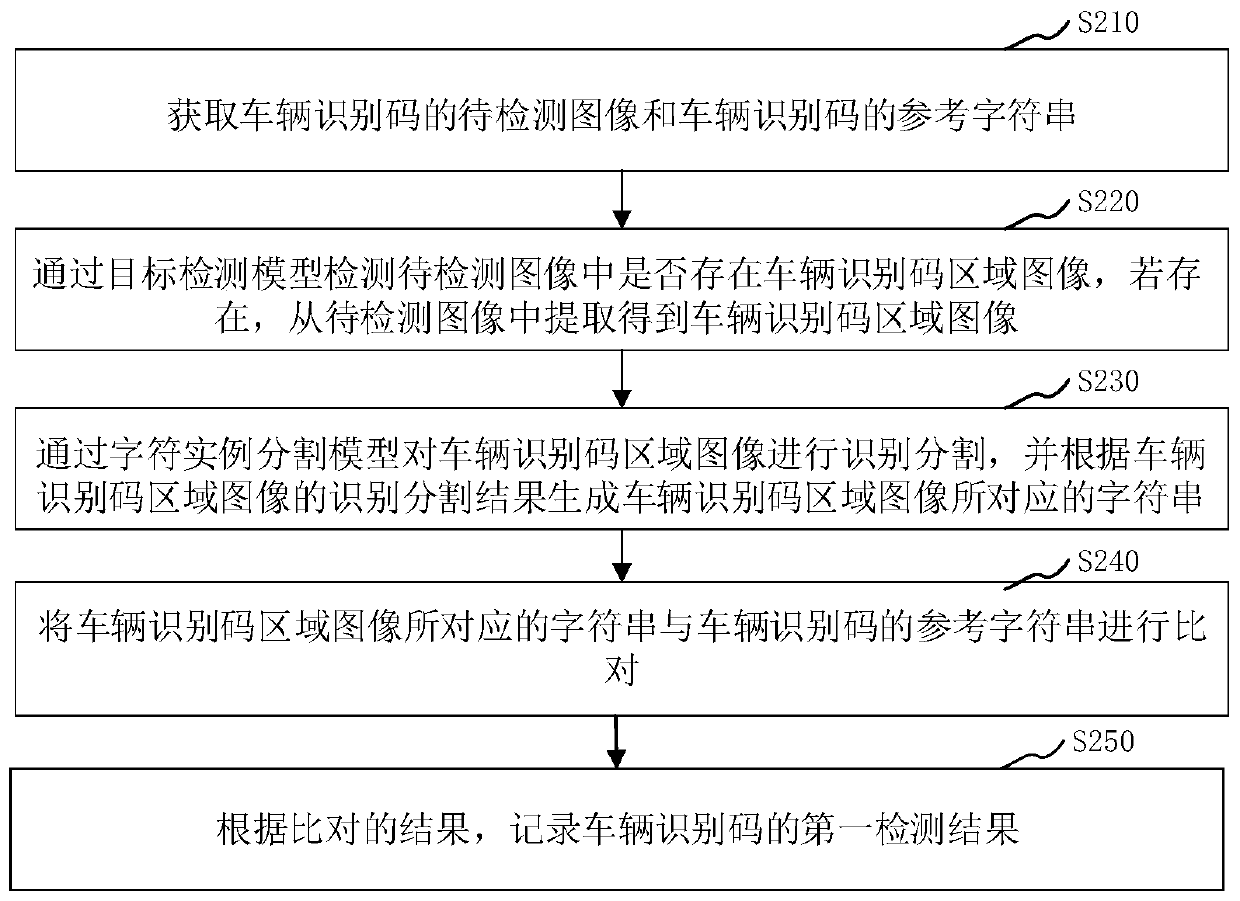
Vehicle identification code detection method and device and computer device
InactiveCN110598687AImprove accuracyTo achieve effective identificationCharacter and pattern recognitionPattern recognitionComputer vision
The invention relates to a vehicle identification code detection method and device, and a computer device. The method comprises the steps of obtaining a to-be-detected image of a vehicle identification code and a reference character string of the vehicle identification code; detecting whether a vehicle identification code area image exists in the to-be-detected image or not through a target detection model, and if yes, extracting the vehicle identification code area image from the to-be-detected image; performing identification segmentation on the vehicle identification code area image througha character instance segmentation model, and generating a character string corresponding to the vehicle identification code area image according to an identification segmentation result of the vehicle identification code area image; comparing a character string corresponding to the vehicle identification code area image with a reference character string of the vehicle identification code; according to the comparison result, recording the first detection result of the vehicle identification code. The technical problem that the vehicle identification code cannot be accurately detected in the prior art is solved, and the accuracy of vehicle identification code detection is improved.
Owner:上海眼控科技股份有限公司
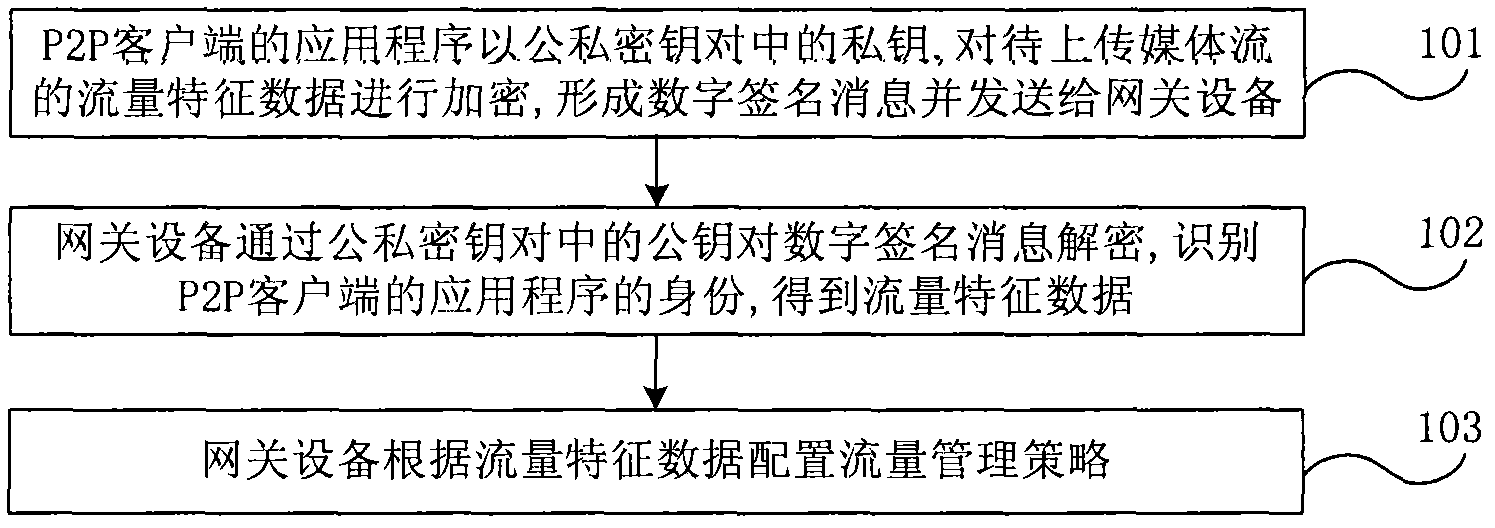
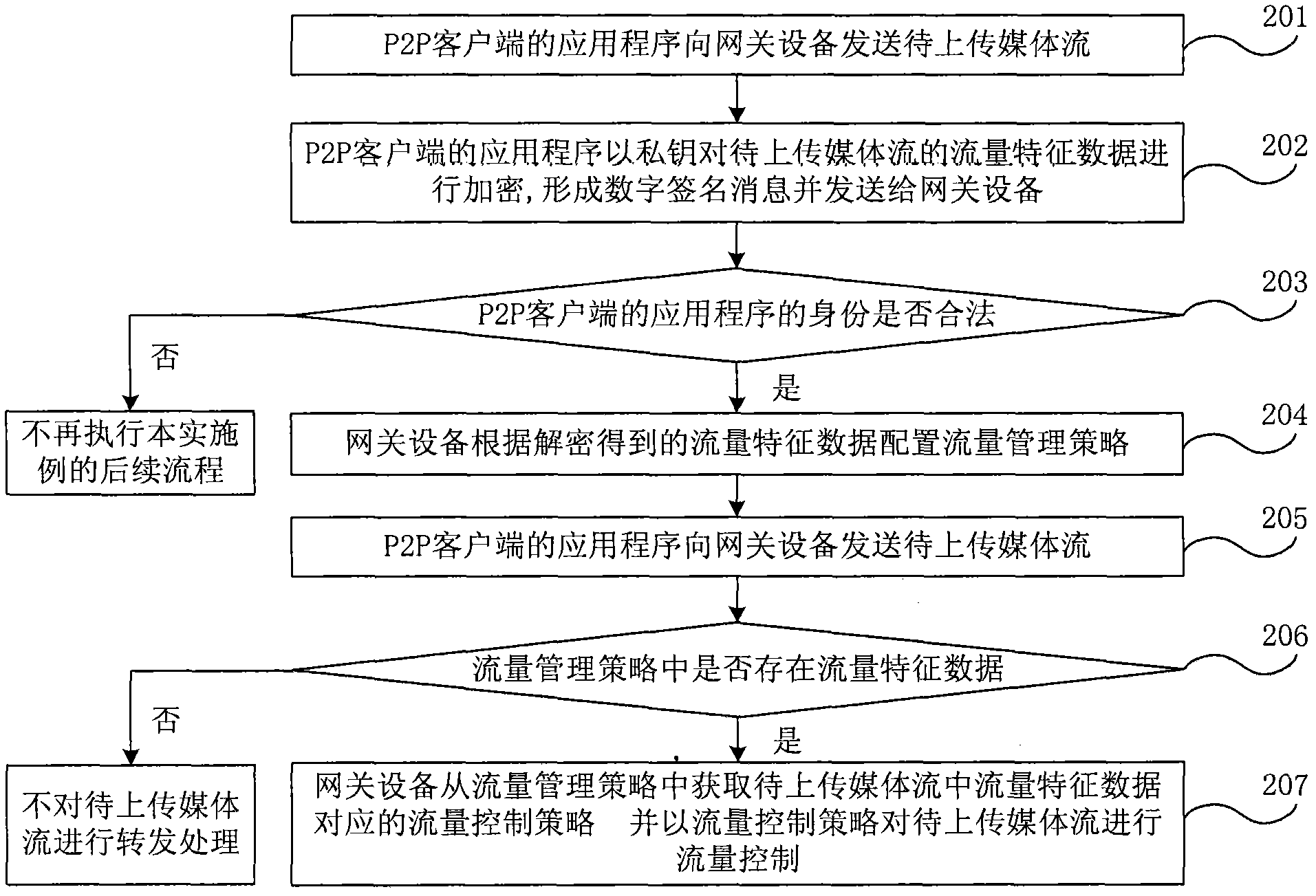
Digital signature-based point-to-point flow control method and system
ActiveCN101980500AEasy to controlTo achieve effective identificationUser identity/authority verificationData switching networksPersonalizationDifferentiated services
The invention discloses a digital signature-based point-to-point flow control method, which comprises that: after a P2P client is started, an application program of the P2P client encrypts flow characteristic data of a media flow to be uploaded by a private key in a public and private key pair to form a digital signature message, and sends the digital signature message to gateway equipment, wherein the public and private key pair is generated by digital signature technology; the gateway equipment decrypts the digital signature message through a public key in the public and private key pair, and identifies the identity of the application program of the P2P client to acquire the flow characteristic data; and the gateway equipment configures a flow management strategy according to the flow characteristic data so as to perform flow control of the media flow to be uploaded according to the flow management strategy. The method can control the uplink flow of a P2P node according to individual requirement of the P2P node so as to provide differentiated service for the P2P node.
Owner:CHINA TELECOM CORP LTD
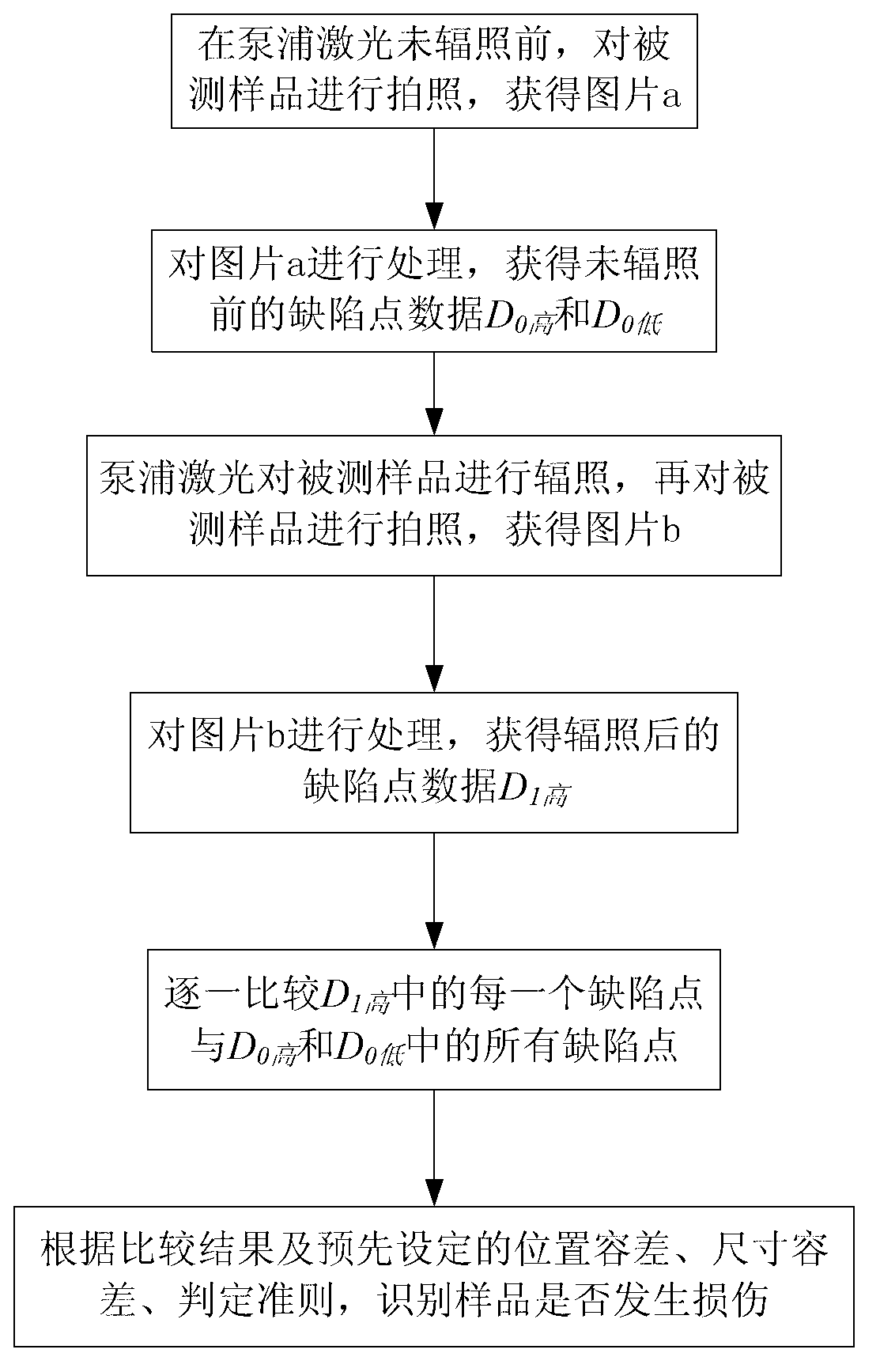
Recognition method and device for micro-scale damage point in damage threshold measurement
ActiveCN102841102ATo achieve effective identificationOptically investigating flaws/contaminationPattern recognitionTest sample
The invention relates to a recognition method and device for a micro-scale damage point in damage threshold measurement. The recognition method comprises the following steps of: photographing a tested sample by an on-line microscope before radiation of a pumping laser to obtain a picture a by using dark field illumination; processing the picture a by a computer, and recognizing all defect points of which the gray levels are higher than thresholds T high and T low in the picture a to obtain deflect point data D0 high and D0 low respectively; photographing the tested sample after radiation by the on-line microscope to obtain a picture b, and recognizing all defect points of which the gray levels are higher than the T high in the picture b by the computer to obtain defect point data D1 high; comparing each defect point in the D1 high with all defect points in D0 high and D0 low one by one; and recognizing whether the sample is damaged according to the comparison result and a judgment rule by the computer,. The recognition device comprises the pumping laser, an electric translation table, a lighting source, the on-line microscope and the computer. Compared with the prior art, the recognition method and the recognition device have the advantages of capability of effectively recognizing the micro-scale damage points, high recognition accuracy and the like.
Owner:TONGJI UNIV
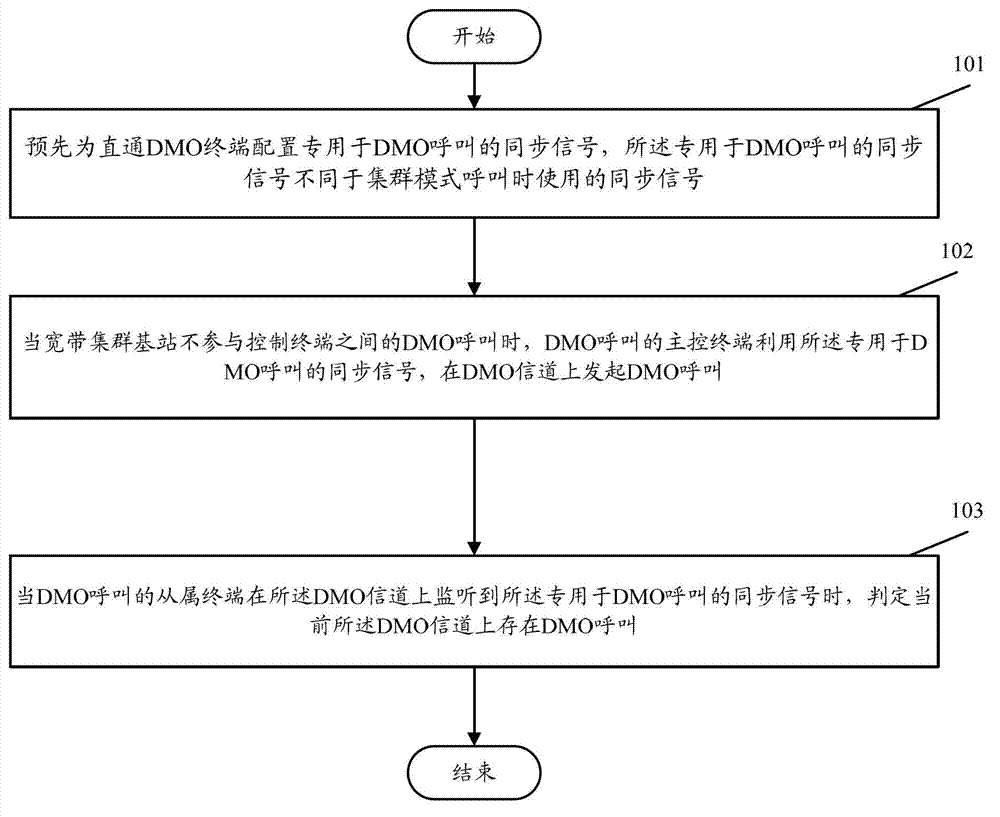
Method for identifying broadband trunking direct mode operation call
InactiveCN103945421ATo achieve effective identificationBroadcast service distributionMonitor modeTrunking
The invention discloses a method for identifying a broadband trunking direct mode operation call. The method comprises the steps that a direct mode operation (DMO) terminal is configured with a synchronizing signal special for DMO calling in advance, wherein the synchronizing signal special for DMO calling is different from a synchronizing signal used in trunking mode operation calling; when a broadband trunking evolved Node B (eNB) is not involved in DMO calling between control terminals, a master control terminal of DMO calling uses the synchronizing signal special for DMO calling to initiate a DMO call on a DMO channel; and when monitoring the synchronizing signal special for DMO calling on the DMO channel, a slave terminal of DMO calling determines that the DMO call exists on the current DMO channel. By adopting the method, a DMO slave terminal in a dual-monitor mode can effectively identify the DMO call.
Owner:CHINA POTEVIO INFORMATION IND
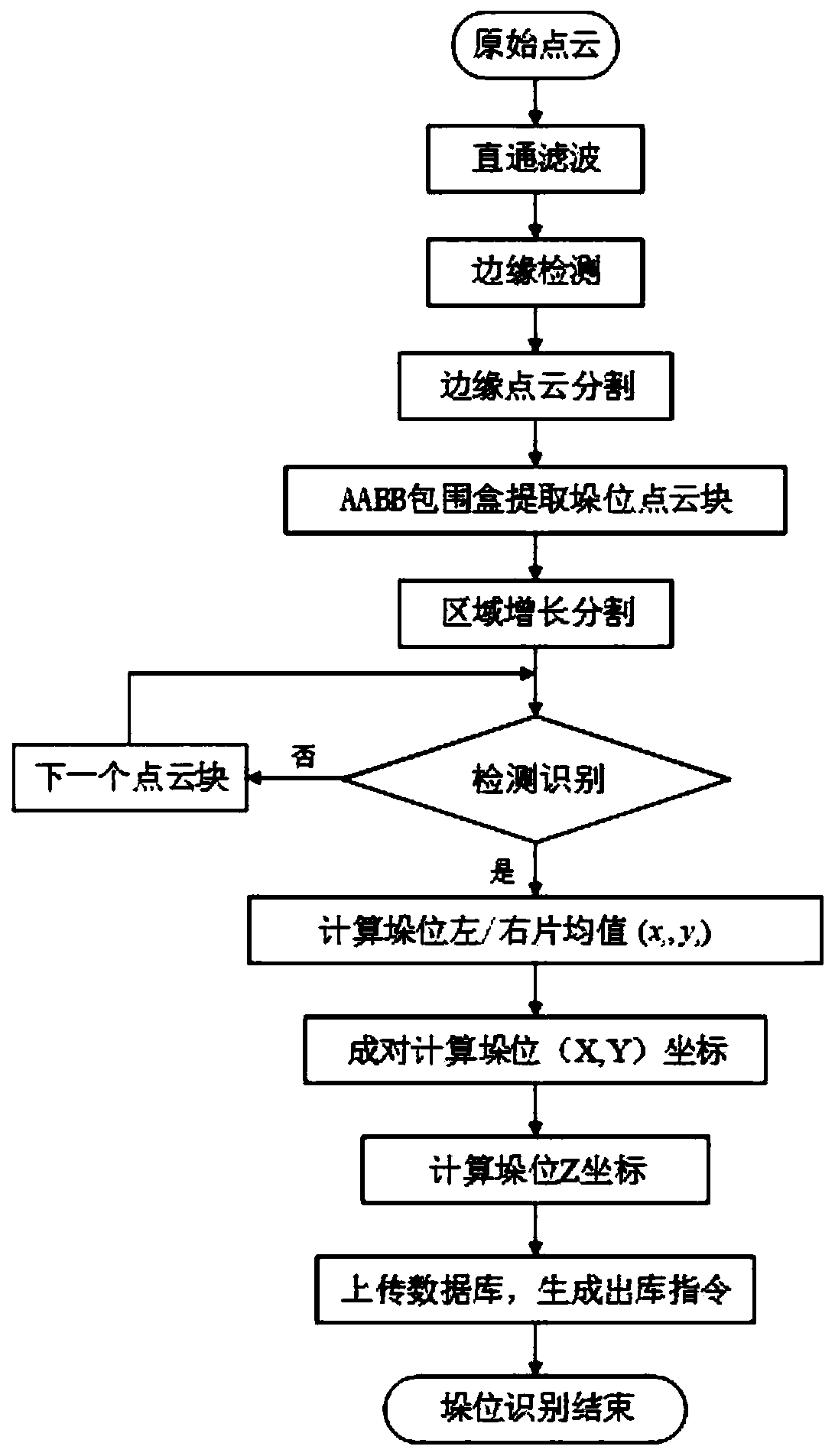
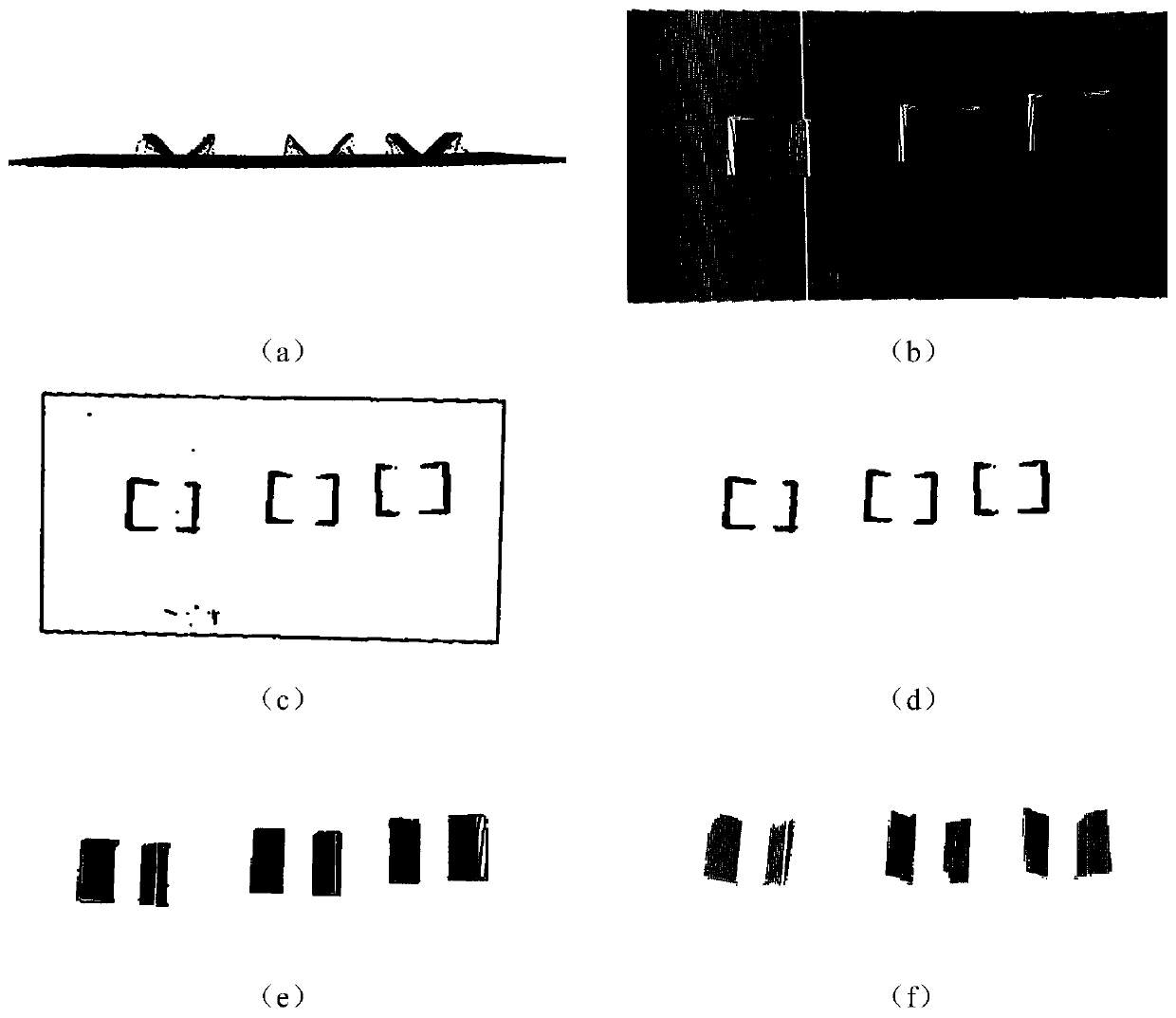
Stack point cloud positioning method based on edge detection and regional growth
PendingCN110223308AImprove stack positioning accuracyHigh positioning accuracyImage enhancementImage analysisEdge detectionPoint cloud
The invention discloses a stack point cloud positioning method based on edge detection and regional growth, which realizes accurate segmentation of a stack point cloud through edge detection, edge point cloud clustering and AABB stack position extraction, realizes effective identification of a stack position through detection and identification of a point cloud block, and improves the stack position positioning precision. The method effectively solves the problem of low segmentation efficiency in the prior art.
Owner:SOUTHEAST UNIV +2
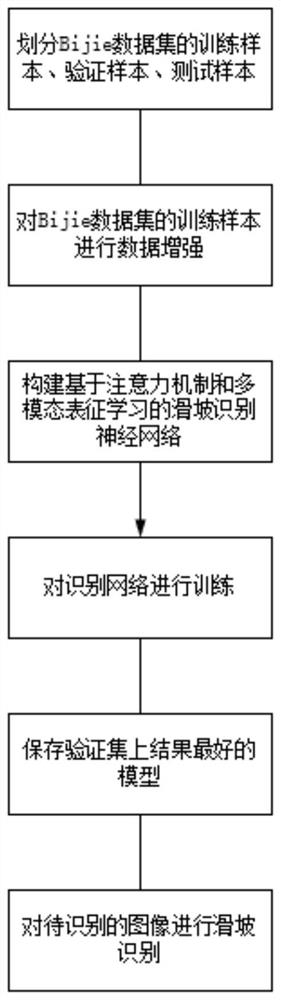
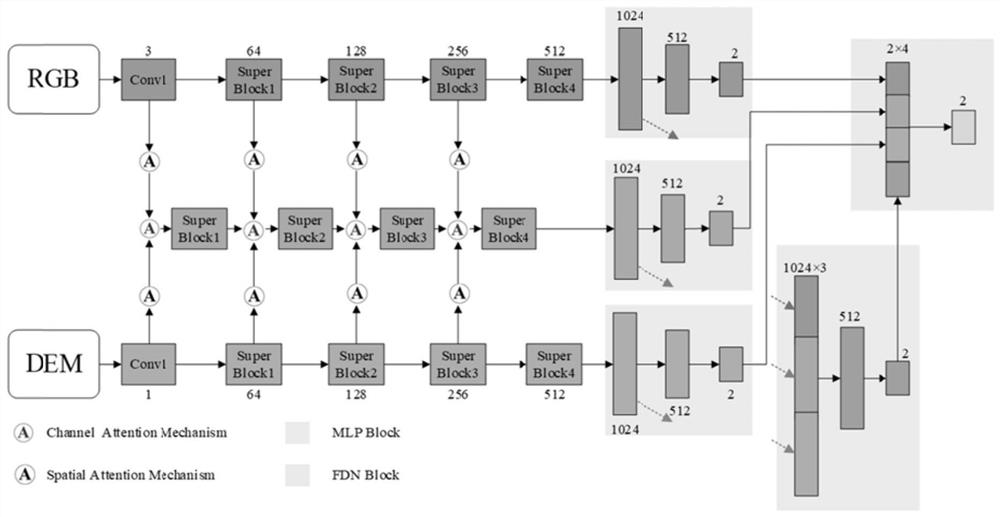
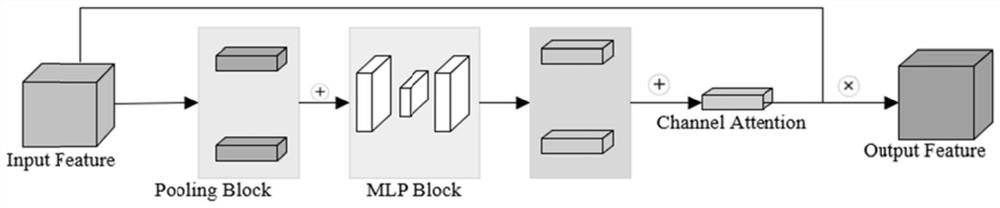
Landslide identification method and system based on attention mechanism and multi-modal representation learning
PendingCN114170533ASolve the problem of missing multimodal high-level semantic featuresImproving the Accuracy of Landslide IdentificationCharacter and pattern recognitionNeural architecturesEngineeringNetwork model
The invention discloses a landslide identification method and system based on an attention mechanism and multi-modal representation learning. The method comprises the following steps: dividing a positive sample containing a landslide and a negative sample containing a non-landslide into a training set, a verification set and a test set; carrying out data enhancement on the training set, adjusting the image sizes of the verification set, the test set and the training set after data enhancement, and normalizing the pixel value of each channel of the image; constructing a multi-channel convolutional neural network based on an attention mechanism and multi-modal representation learning; using a cross entropy loss function to train the multi-channel convolutional neural network based on the attention mechanism and the multi-modal representation learning; using the normalized training set to train the trained attention mechanism and the multi-modal representation learning multi-path convolutional neural network, using the normalized verification set to verify, and storing the network model with the best performance on the verification set; and testing on the stored network model by using the normalized test set to obtain a landslide identification result, thereby reducing the consumption of computing resources.
Owner:XIDIAN UNIV
Interference alarm recognition method based on alarm duration feature
ActiveCN109087490AEfficient identificationTo achieve effective identificationAlarmsProcess industryComputer science
The invention belongs to the field of process industry production process monitoring, in particular to an interference alarm recognition method based on an alarm duration feature. The method comprisesthe following steps that: step S1, an acquired monitoring process signal is compared with an alarm threshold value thereof to generate an alarm signal; step S2, an alarm duration set is defined; stepS3, if C<k> is not satisfied C<k> > RC, there is no interference alarm, and an algorithm is ended; if C<k> > RC, a sample probability distribution and an estimated geometric distribution of the alarm duration set are calculated; and step S4, degree of fitting R<2> between the sample probability distribution and the estimated geometric distribution is calculated; if the degree of fitting R<2> >= 0.95, alarms corresponding to elements in the alarm duration set are all interference alarms, and the entire algorithm is ended; if the degree of fitting R<2> < 0.95, a new alarm duration set is formed after a largest element in the alarm duration set is removed; and the method is skipped to step S3 to continue the calculation. The interference alarm recognition method based on the alarm duration feature provided by the invention provides an effective technical means for eliminating the interference alarm and realizing performance optimization of an alarm system.
Owner:SHANDONG UNIV OF SCI & TECH
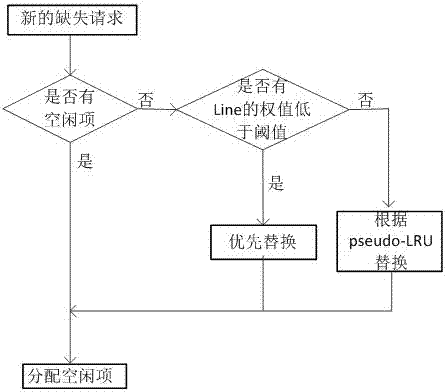
Multi-core processor directory cache replacement method
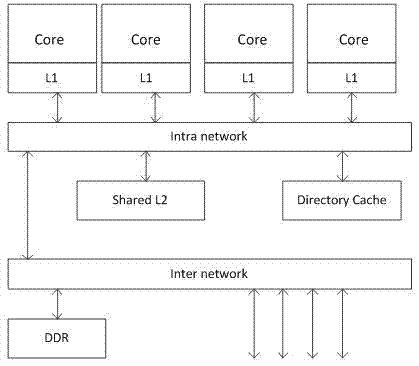
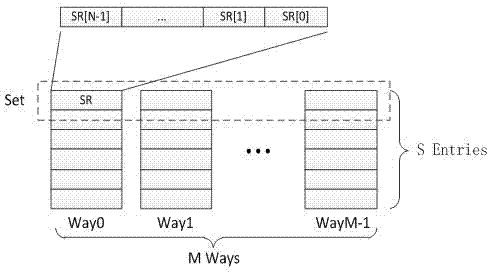
ActiveCN104778132AImprove performanceIncrease effective capacityMemory adressing/allocation/relocationReplacement methodMulti-core processor
The invention discloses a multi-core processor directory cache replacement method, and belongs to the technical field of computer storage. The multi-core processor directory cache replacement method comprises the following concrete steps that a multi-core processor adopts a two-stage caching structure, each processor core is combined into an L1 Cache, and all processor cores share an L2 Cache; the data consistency is maintained between the L1 Caches through a directory cache, and the number of no-message replacement times generated by a certain buffer group of the L1 Cache corresponding to each processor core is determined according to interactive messages of the directory cache and the L1 Caches; no-message replacement counting vector group of each L1 Cache group is additionally added for the directory cache, and the number of no-message replacement times generated by each L1 Cache in the cache group is stored, so that cache blocks to be replaced are determined. The multi-core processor directory cache replacement method has the advantages that invalid terms in the directory cache are effectively recognized, limited replacement is carried out, the effective capacity of the directory cache is improved, and the integral performance of the multi-core processor is improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
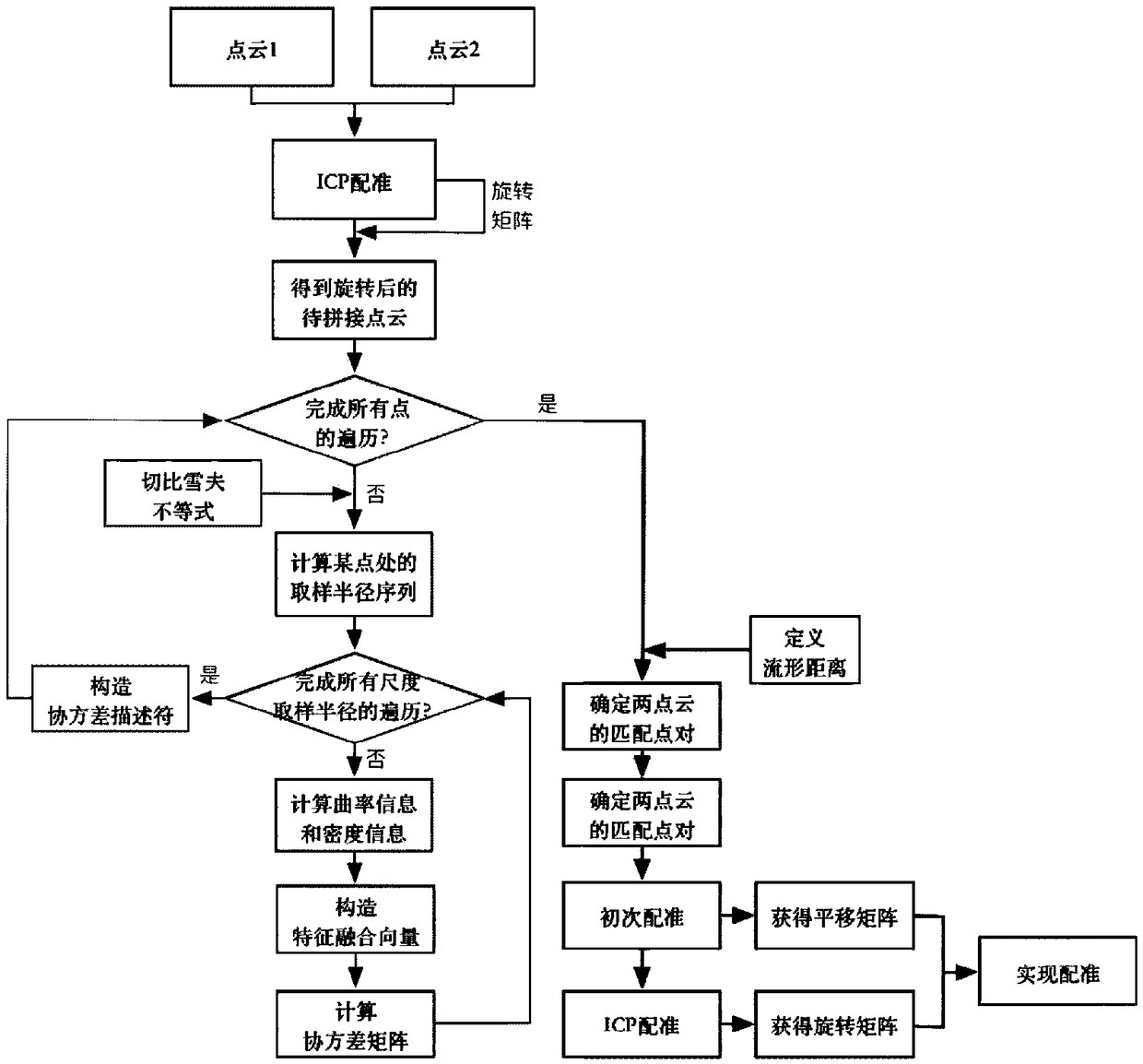
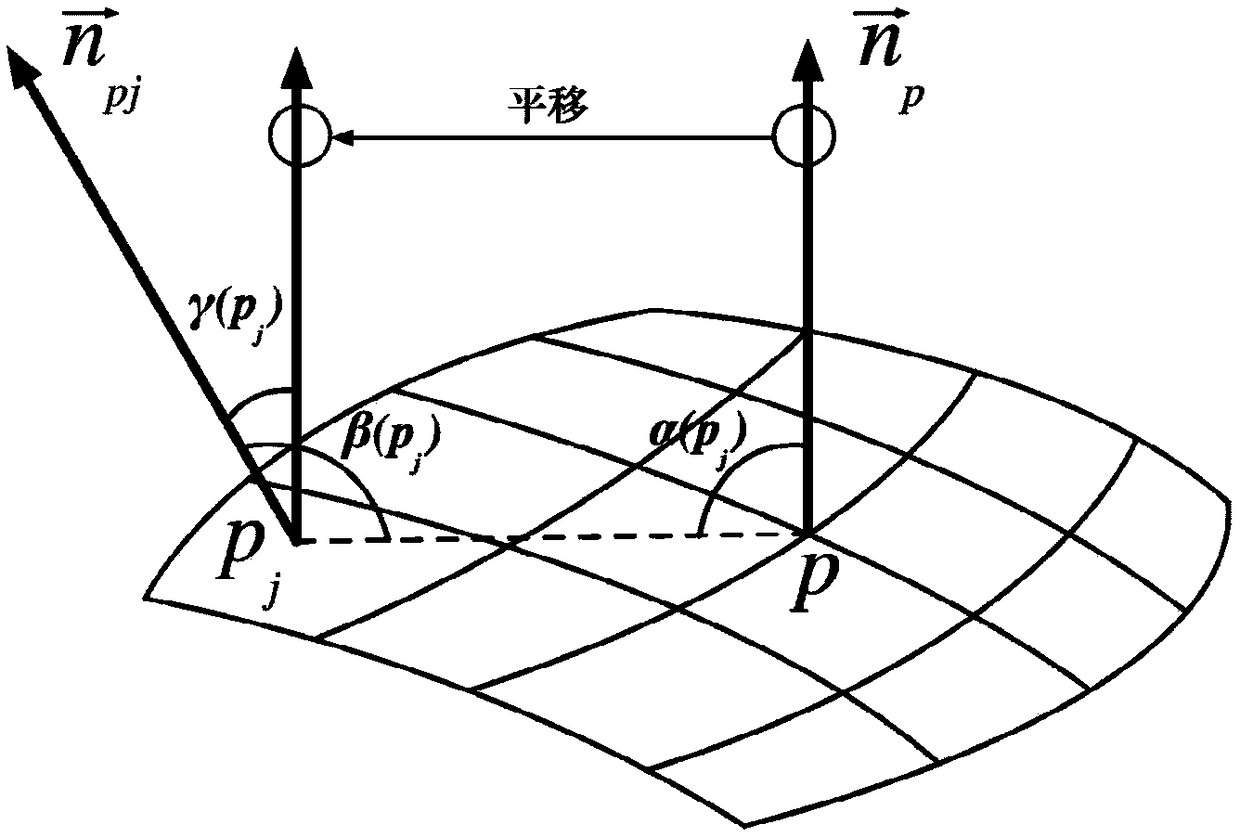
A point cloud splicing method for flat parts based on invariant features in multi-dimensional space
ActiveCN109242774ATo achieve effective identificationImprove visibilityImage enhancementImage analysisPoint cloudAlgorithm
The invention discloses a method for splicing point cloud of flat plate type parts based on multidimensional space invariant features. The nearest neighbor iterative algorithm is used to compute the rotation matrix of point cloud and multiple sampling radii. According to different sampling radii, the covariance matrices of each point at different scales are computed by using the features of pointcloud texture and point cloud density, and the covariance descriptors are constructed. A multiscale flow distance between two covariance descriptors is defined; The matching point pairs in the two point clouds are determined according to the distance of the flow pattern and the rough registration is performed to obtain the translation matrix. Then the nearest neighbor iterative algorithm is used to obtain the rotation matrix. The final transformation matrix is obtained and the splicing is completed. By defining covariance descriptors for each point in the point cloud, the invention realizes automatic splicing of the point cloud of a flat plate type part by utilizing density features and texture features with space invariant characteristics at a certain point, and is suitable for splicing of the point cloud of a plate type part with hole features.
Owner:ZHEJIANG UNIV
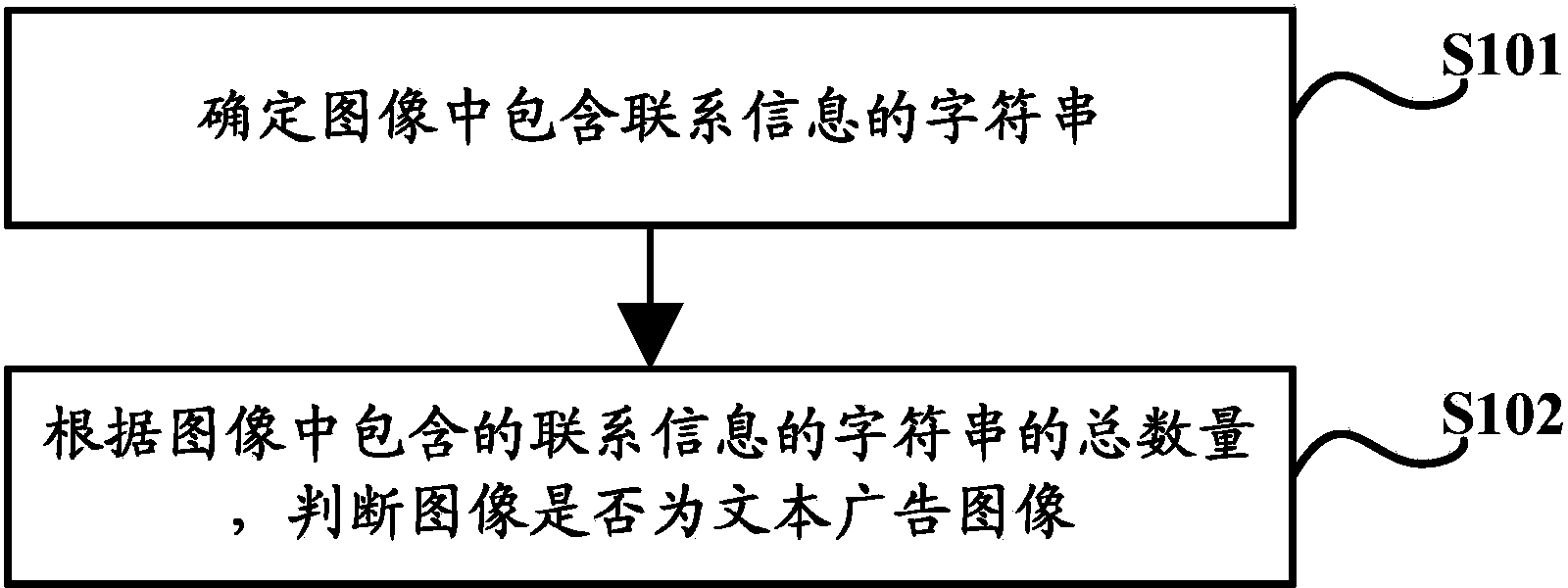
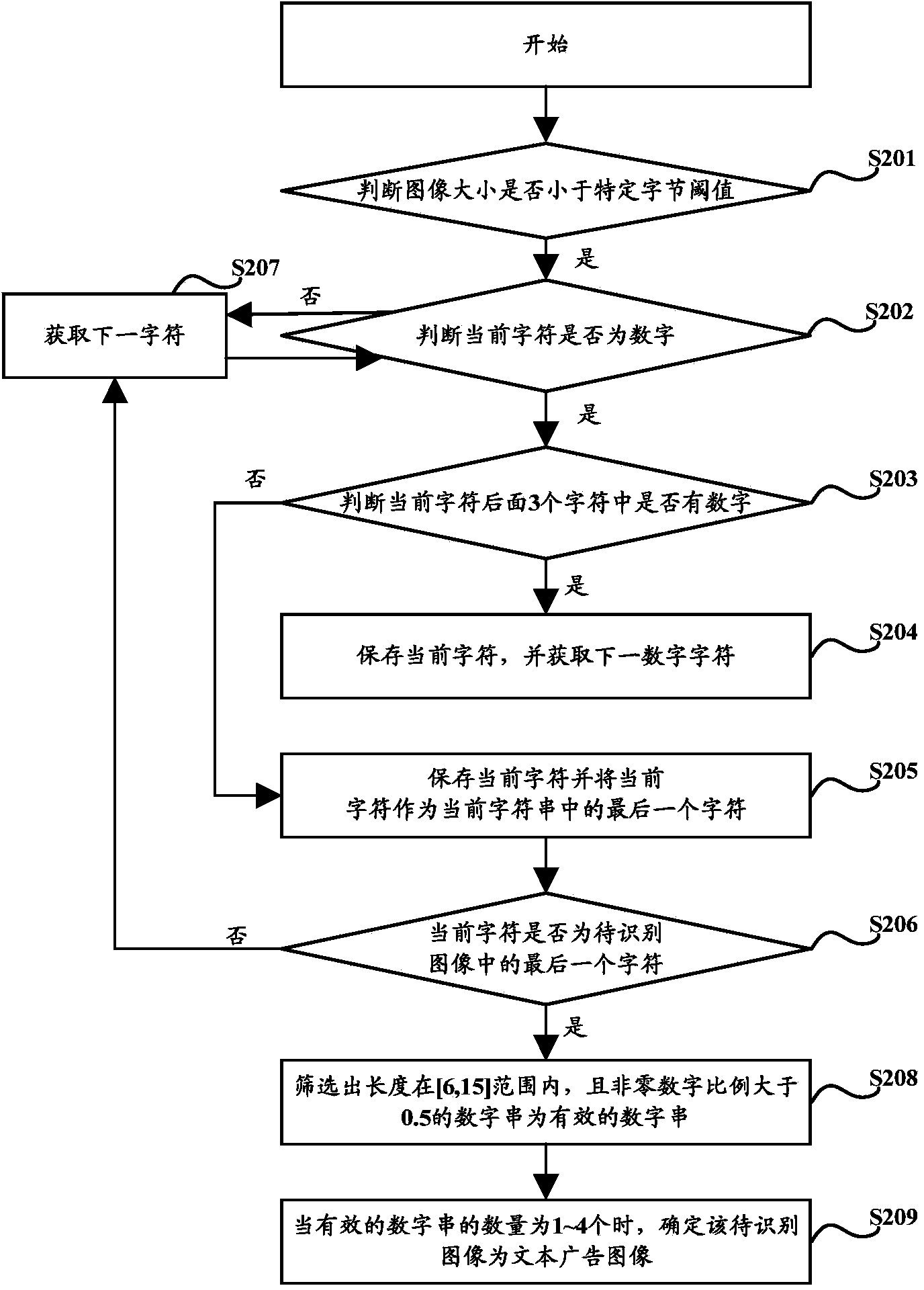
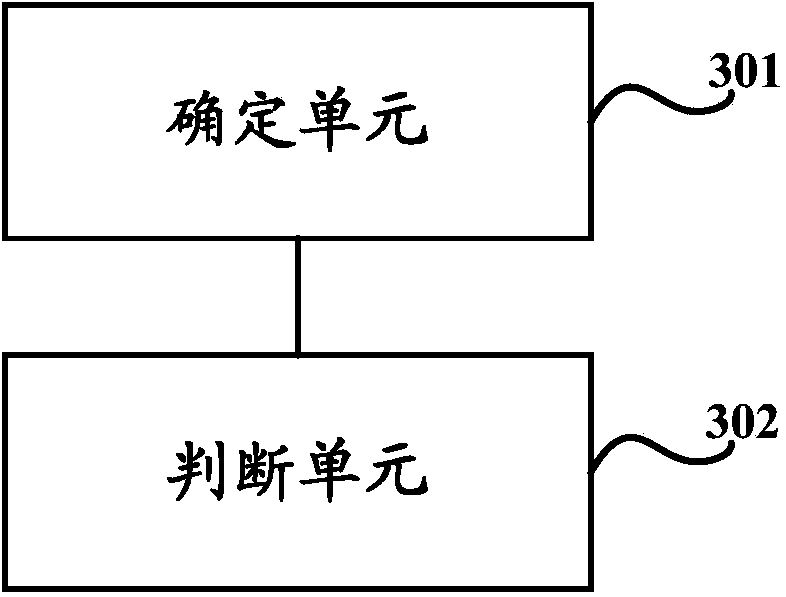
Identification method and device for text advertisement image
ActiveCN104376304ATo achieve effective identificationNatural language data processingCharacter recognitionPattern recognitionIdentification device
The invention discloses an identification method for a text advertisement image. The method solves the problem that it is difficult to effectively identity the text advertisement image according to the prior art. The method comprises the steps of determining character strings, containing contact information, in an image and judging whether the image is the text advertisement image according to the total number of the character strings, containing the contact information, in the image. The invention further discloses an identification device for the text advertisement image.
Owner:新浪技术(中国)有限公司
Identification method and device between equipment, electronic equipment and storage medium
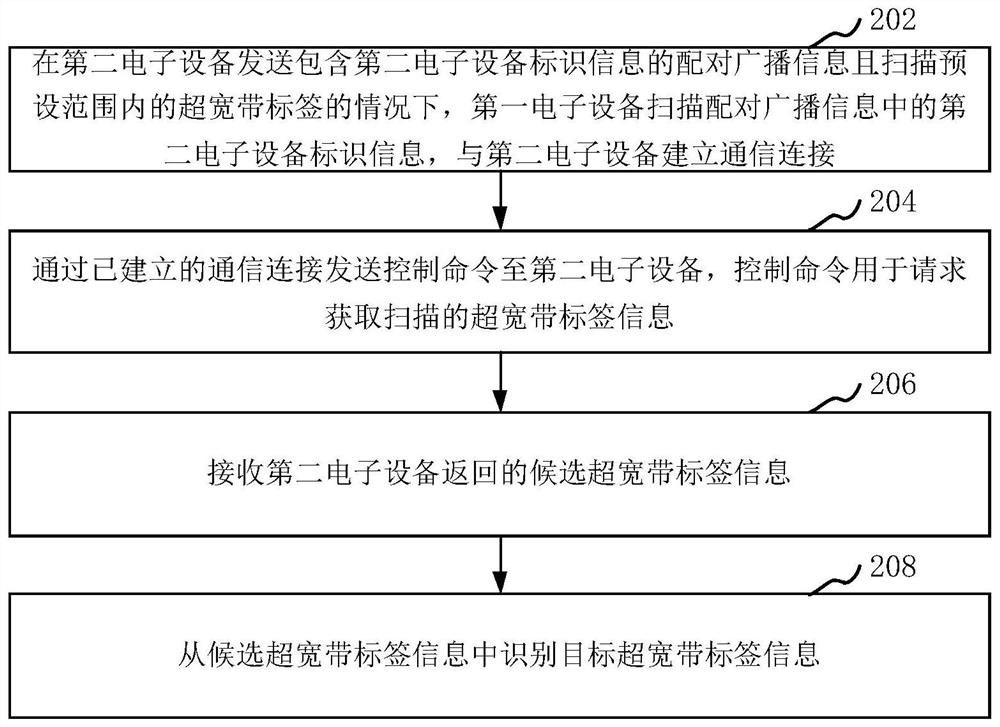
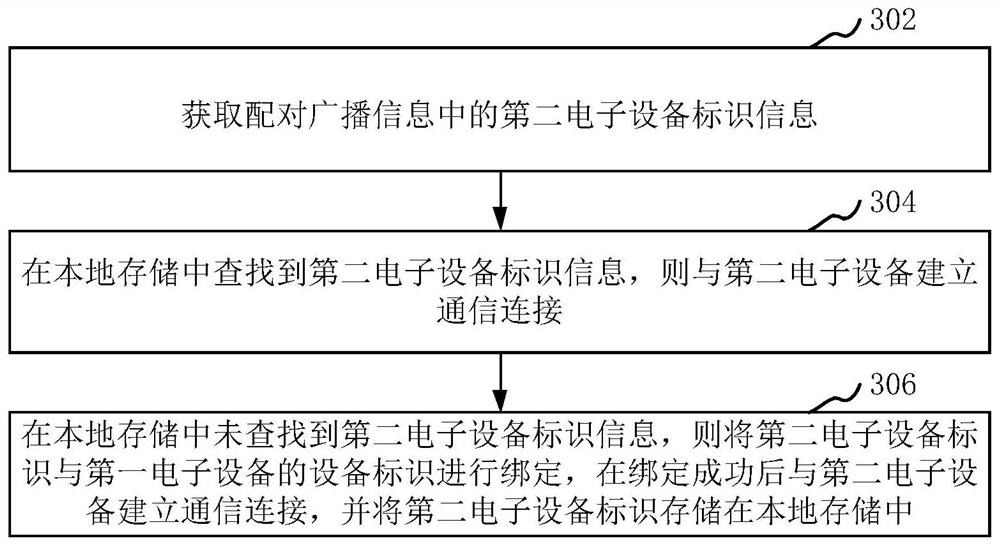
ActiveCN113055873AAccurately determineTo achieve effective identificationConnection managementHigh level techniquesComputer equipmentReal-time computing
The invention relates to an identification method and device between equipment, computer equipment and a storage medium. The method comprises the following steps: under the condition that second electronic equipment sends pairing broadcast information containing second electronic equipment identification information and scans an ultra wide band label in a preset range, first electronic equipment scans the second electronic equipment identification information in the pairing broadcast information, and establishes communication connection with the second electronic equipment; a control command is sent to the second electronic equipment through the established communication connection, wherein the control command is used for requesting to acquire scanned ultra-wideband tag information; candidate ultra-wideband tag information returned by the second electronic equipment is received; and target ultra wide band label information is identified from the candidate ultra wide band label information. By adopting the method, rapid and effective identification between equipment can be realized.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Information processing method, device and system
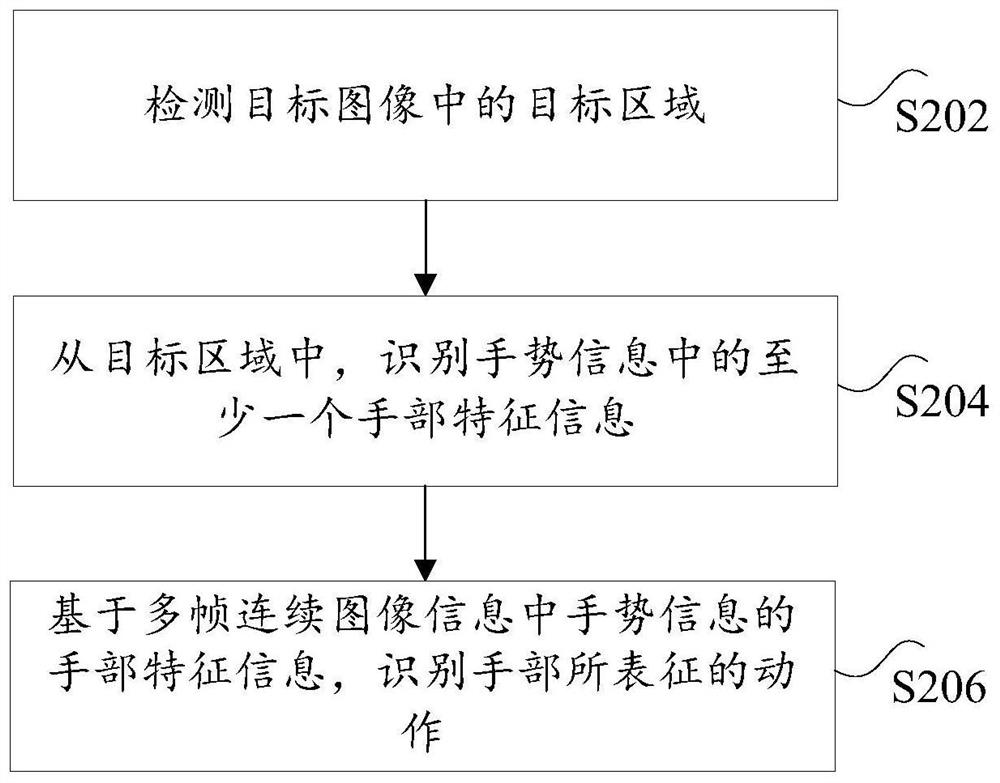
PendingCN111860082AReduce operational complexityImprove recognition rateCharacter and pattern recognitionNeural architecturesInformation processingRadiology
The invention discloses an information processing method, device and system. The method comprises the steps that a target area in a target image is detected, the target image is at least two frames inmultiple frames of continuous images, and gesture information of a hand in the target image is contained in the target area; identifying at least one part of hand feature information in the gesture information from the target area; and based on the hand feature information of the gesture information in the multi-frame continuous image information, identifying an action represented by the hand. The technical problem that in the prior art, when gesture recognition is carried out, the whole image information is input into the neural network model for operation, and consequently the operation complexity degree is high is solved.
Owner:ALIBABA GRP HLDG LTD
Static image behavior identification method based on main and auxiliary clues
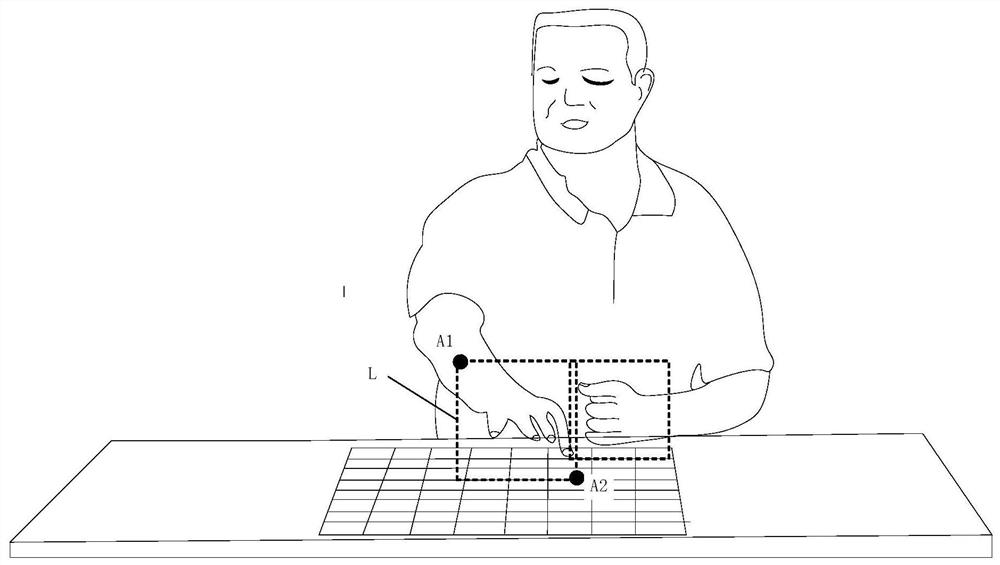
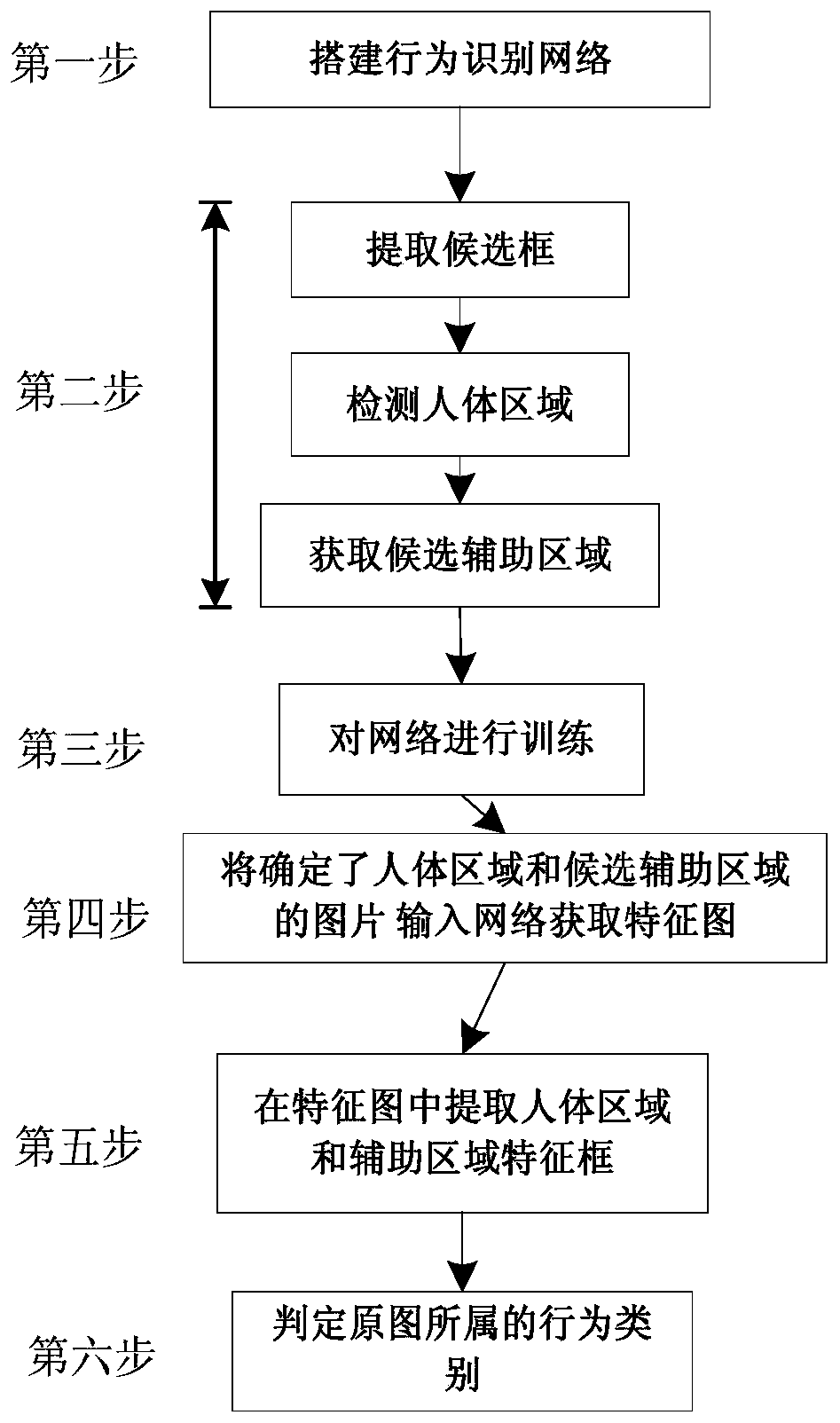
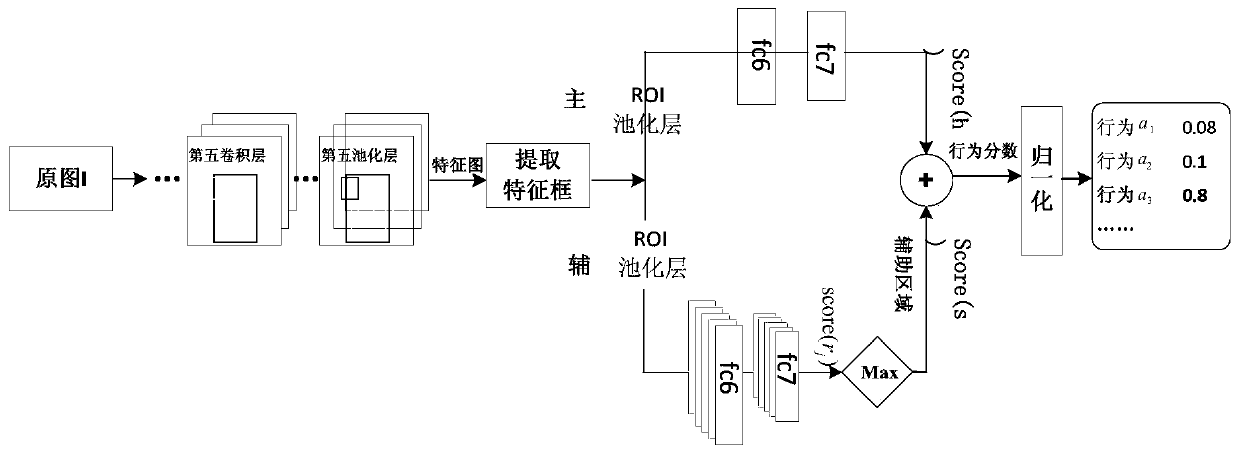
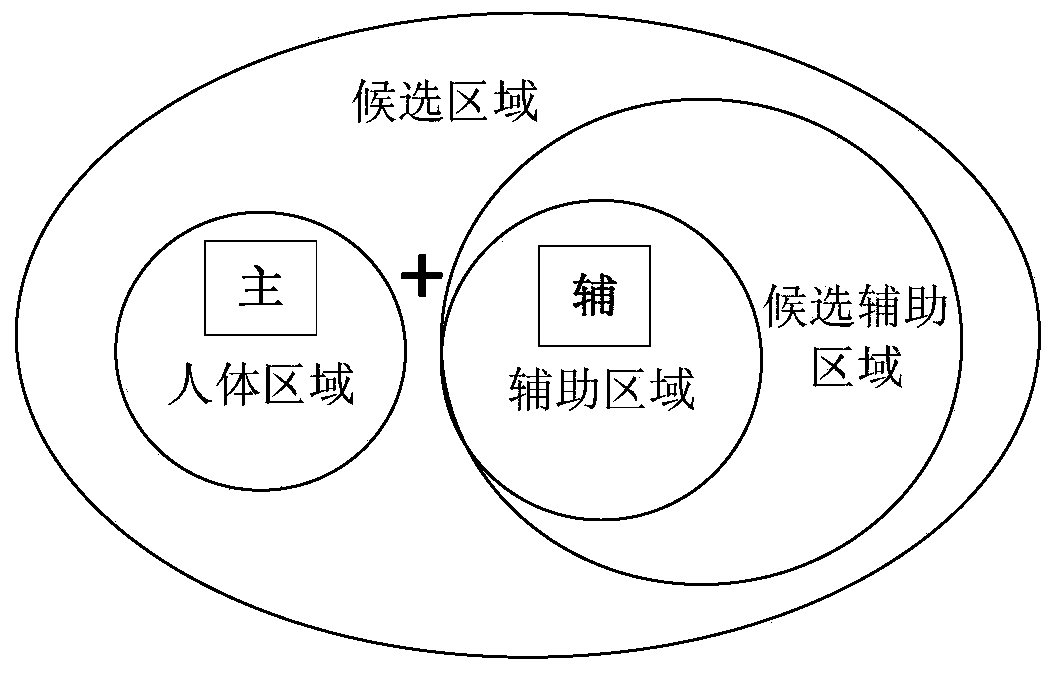
InactiveCN109815883AHigh speedImprove accuracyCharacter and pattern recognitionNeural architecturesHuman bodyBehavior recognition
The invention discloses a static image behavior identification method based on main and auxiliary clues. The technical scheme is characterized in that a behavior recognition network containing a mainclue branch and an auxiliary clue branch is established; the feature frames corresponding to all the candidate auxiliary areas and the feature frames corresponding to the human body areas are found inthe feature graph; the main clue branch calculates a judgment score that the image I belongs to the behavior category ak according to the human body region information; the auxiliary clue branch calculates a judgment score that I belongs to the behavior category ak according to the auxiliary area information; and the sum of the scores of the two branches is used as a behavior score of which I belongs to ak, so that a behavior score of each type of behavior in the behavior type set of I is obtained, and all the scores are normalized to obtain the probability that I belongs to each type of behavior, and the maximum probability is the behavior type described by I. By adopting the method, the human body behavior in the image can be effectively identified, and the speed and the accuracy of thestatic image behavior identification are improved.
Owner:NAT UNIV OF DEFENSE TECH
Remote parking method and system based on real-time video stream monitoring
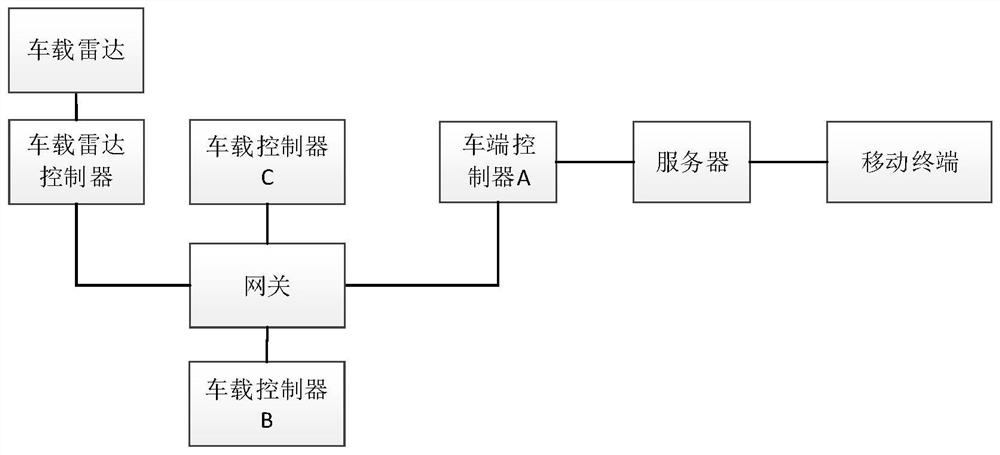
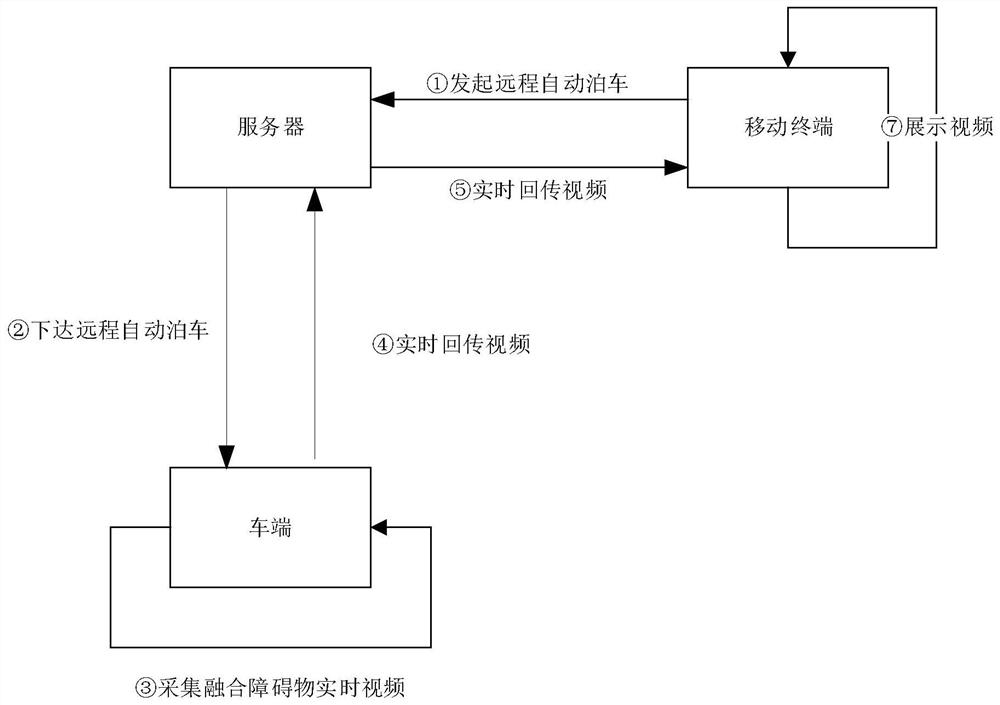
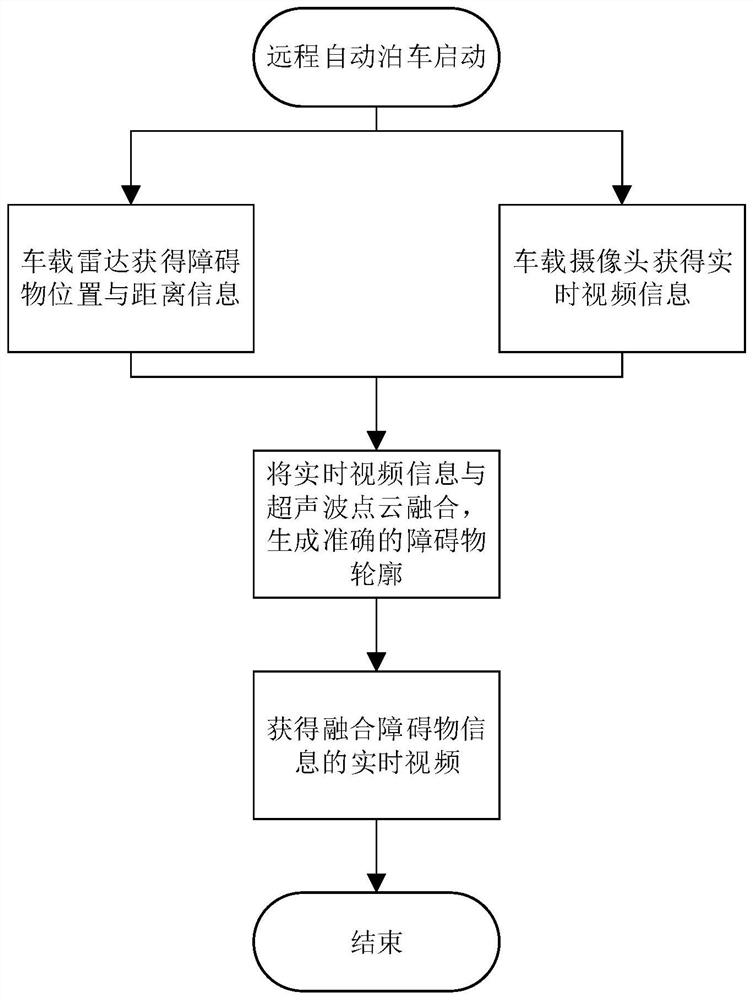
The invention discloses a remote parking method and system based on real-time video stream monitoring. The method comprises the steps that the surrounding environment information is collected through a vehicle-mounted camera and a vehicle-mounted wave radar in an automatic parking process; the information collected by the vehicle-mounted camera establishes a visual 3D point cloud map through a real-time visual three-dimensional point cloud reconstruction technology, the information collected by the vehicle-mounted radar establishes ultrasonic 2D point cloud, the 3D point cloud map and the 2D point cloud map are fused through a fusion algorithm to generate a high-precision obstacle boundary, and the information is fitted into a real-time video to realize effective identification of various complex parking scenes; and meanwhile, the video is sent to the mobile terminal of a user in real time through a server by using a real-time video streaming technology, so that the vehicle owner can remotely check the vehicle in real time, the judgment on the surrounding environment of the vehicle is realized, and the remote operation of the user on an automatic parking function can be assisted.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD
Network data exception detection method and system based on high-order association mining
ActiveCN109818971AImprove accuracyIncrease profitCharacter and pattern recognitionTransmissionCluster algorithmData set
The invention discloses a network data exception detection method and system based on high-order association mining, and the method comprises the steps: 1, generating a discrete forest according to anobtained network data set, and calculating a discrete value of network data in the network data set; 2, generating a clustering center point according to a clustering algorithm and the abnormal network data, and calculating a similarity value between the network data and the clustering center point; 3, calculating the weight of the network data in the network data set according to the discrete value and the similarity value; 4, calculating a label matrix of unmarked network data in the network data set according to the weight of the network data and the hypergraph model; And step 5, determining the security type of the unlabeled network data according to the label matrix. Through the technical scheme provided by the invention, effective identification of a large amount of unmarked networkdata in an industrial network environment is realized, and the identification accuracy of the unmarked network data and the utilization rate of the marked network data are improved.
Owner:TSINGHUA UNIV
Shared riding system and method for unmanned vehicles
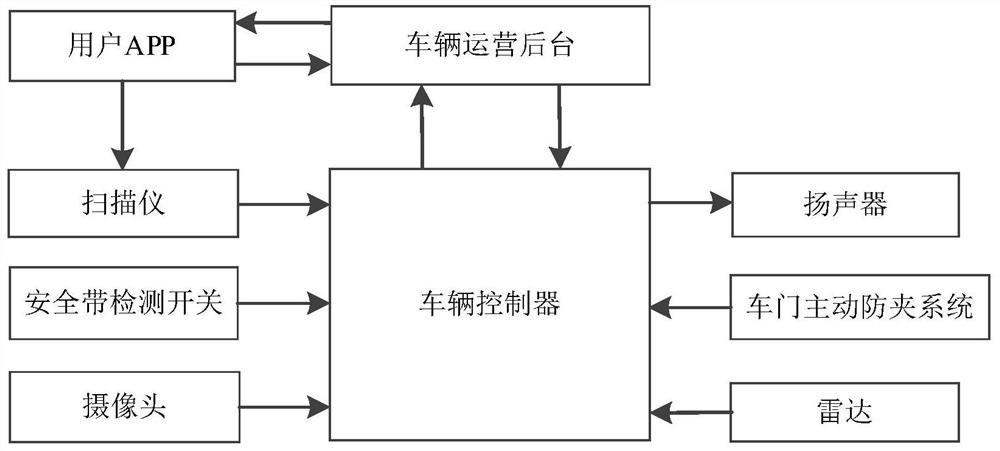
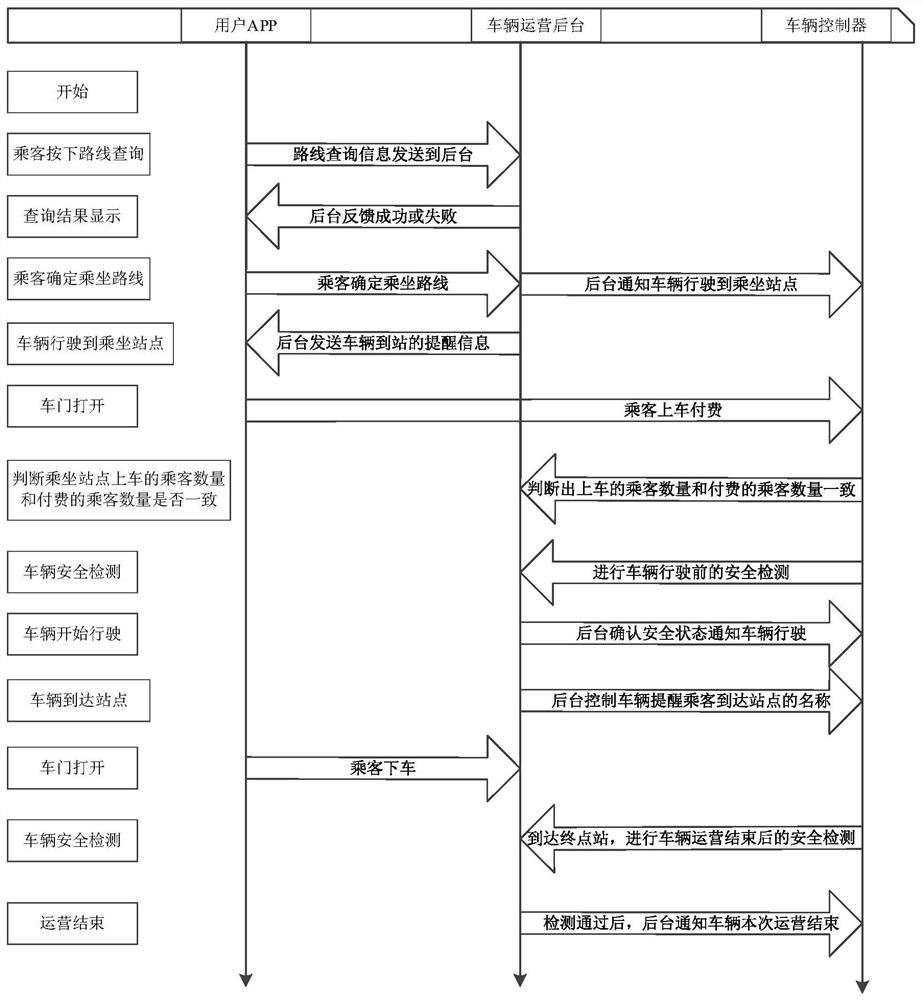
InactiveCN111612978ALow costTo achieve effective identificationRoad vehicles traffic controlApparatus for meter-controlled dispensingTransport engineeringVehicle control
The invention provides a shared riding system and method for unmanned vehicles, and belongs to the technical field of unmanned driving. The shared riding system comprises a user APP, a vehicle operation background and a vehicle controller, and the user APP is used for sending riding request information to the vehicle operation background, receiving station arrival reminding information of an unmanned vehicle and paying for the unmanned vehicle after a passenger gets on the vehicle; the vehicle operation background is used for receiving the riding request information sent by the user APP, determining a corresponding unmanned vehicle according to the received riding request information, and sending reminding information of arrival of the unmanned vehicle to the user APP when the corresponding unmanned vehicle arrives at the riding station; and the vehicle controller is used for counting the number of passengers getting on the bus at the riding station and the number of paid passengers, and when the two numbers are inconsistent, the vehicle controller controls the vehicle not to be started. According to the invention, the problem that the existing unmanned shared vehicle cannot identify that passengers get on the vehicle without payment is solved.
Owner:ZHENGZHOU YUTONG BUS CO LTD
Blast furnace condition identification method and system based on fuzzy clustering
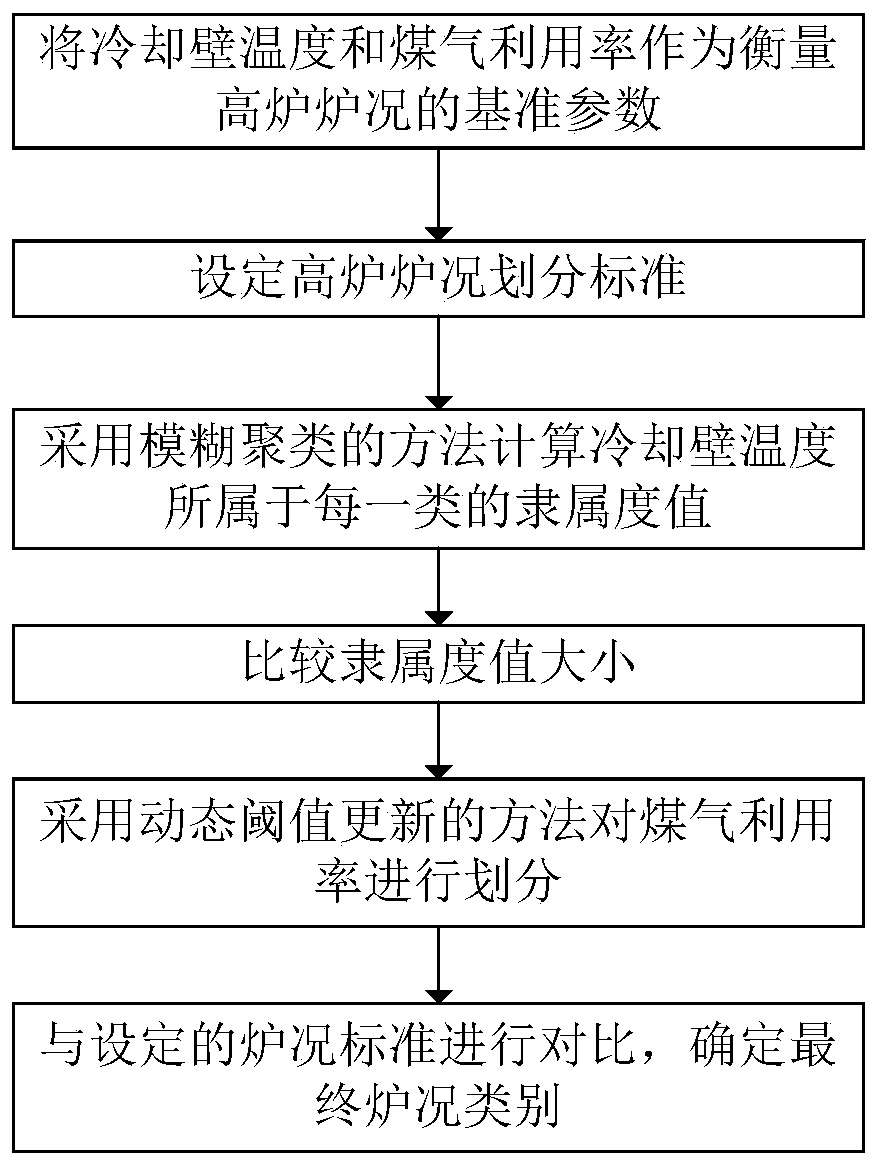
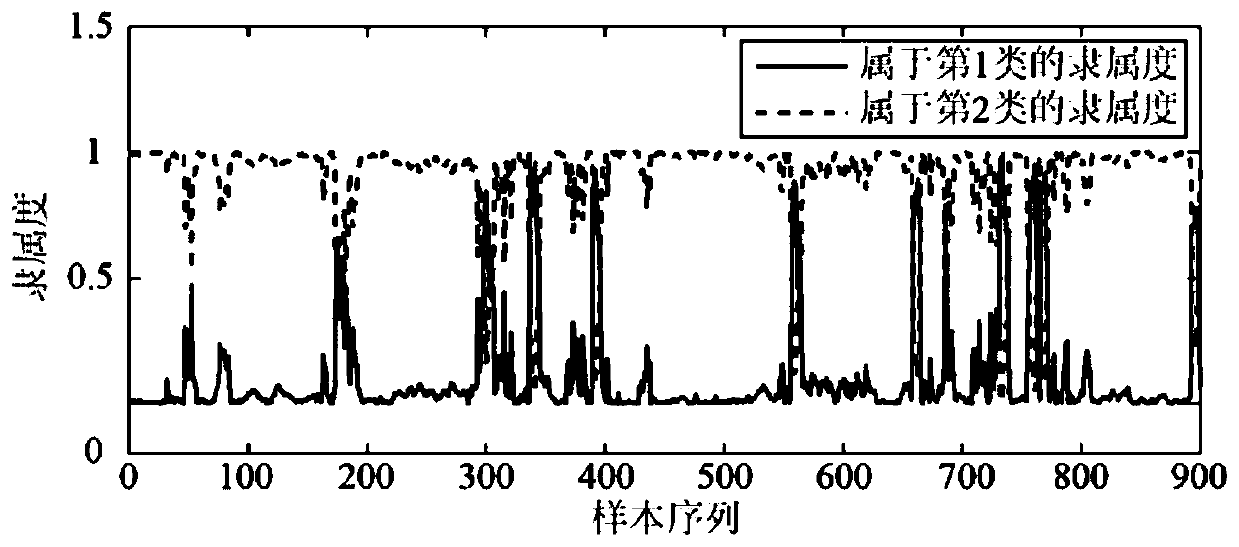
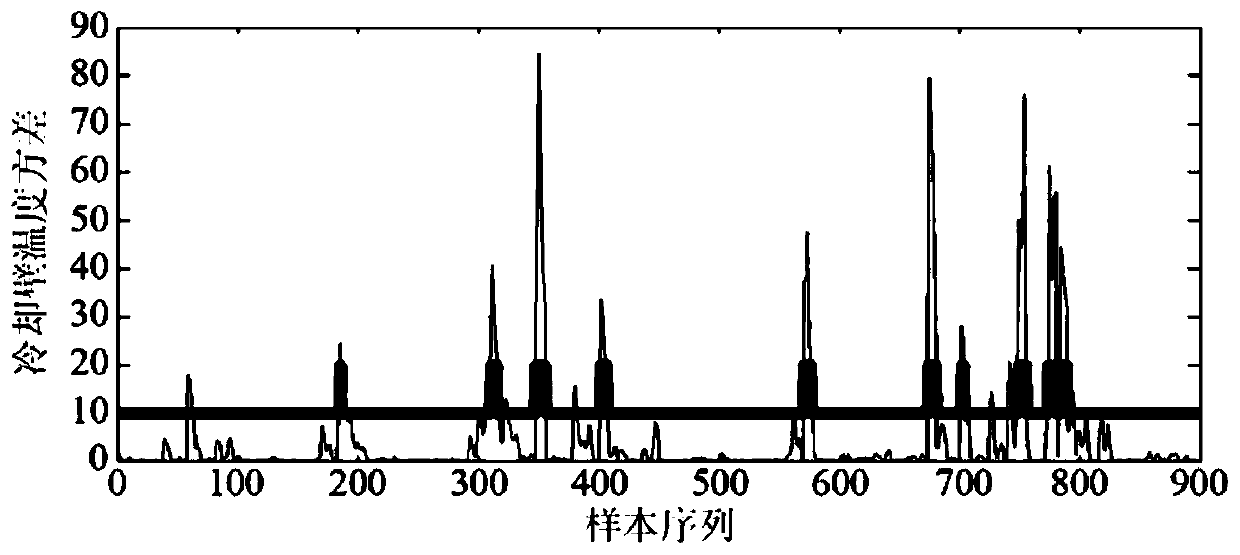
InactiveCN110245690AEffective identificationTo achieve effective identificationCharacter and pattern recognitionEngineeringEnergy consumption
The invention discloses a blast furnace condition identification method and system based on fuzzy clustering, and the method comprises the steps of firstly, determining the cooling wall temperature and the gas utilization rate as the furnace condition division parameters from the perspective of edge cooling wall stability and energy consumption; setting four different types of furnace conditions according to the actual production requirements; calculating the membership values of different types of cooling wall temperature parameters based on a fuzzy clustering method, and determining the type of the sample according to the membership values; and finally, dividing the gas utilization rate by adopting a dynamic threshold updating method; and determining the final furnace condition category according to the division result and one of the four furnace conditions. By the adoption of the method, the blast furnace parameters can be effectively divided at the aspects of furnace condition stability and energy consumption, and the real-time identification of the blast furnace condition can be achieved.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
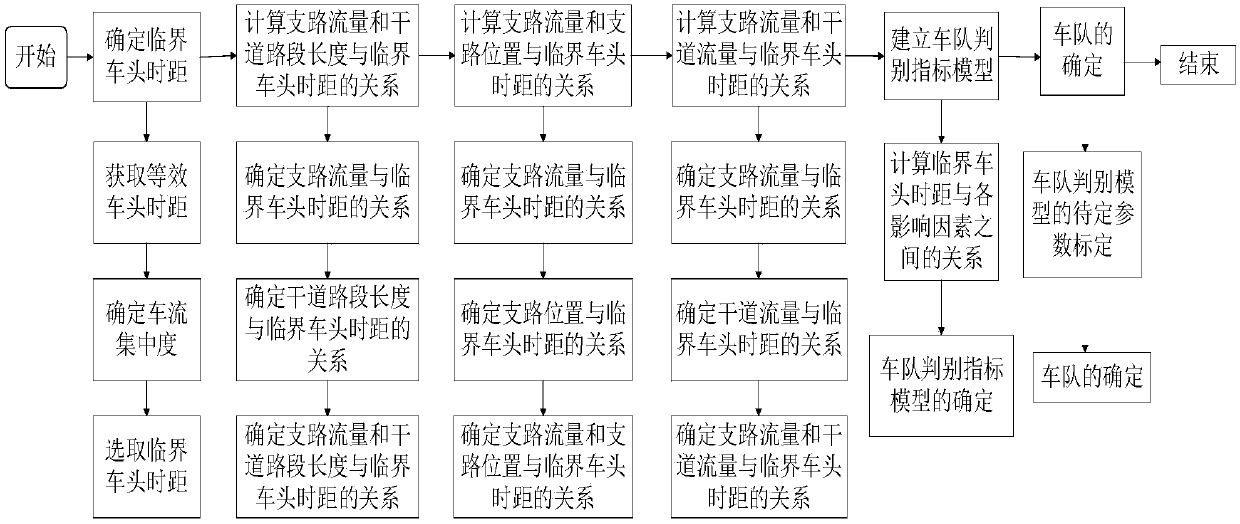
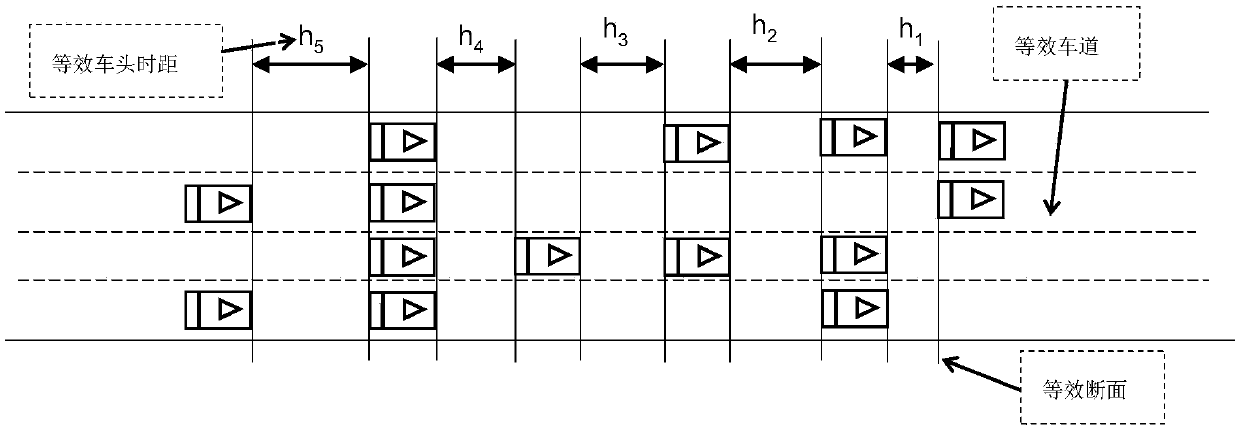
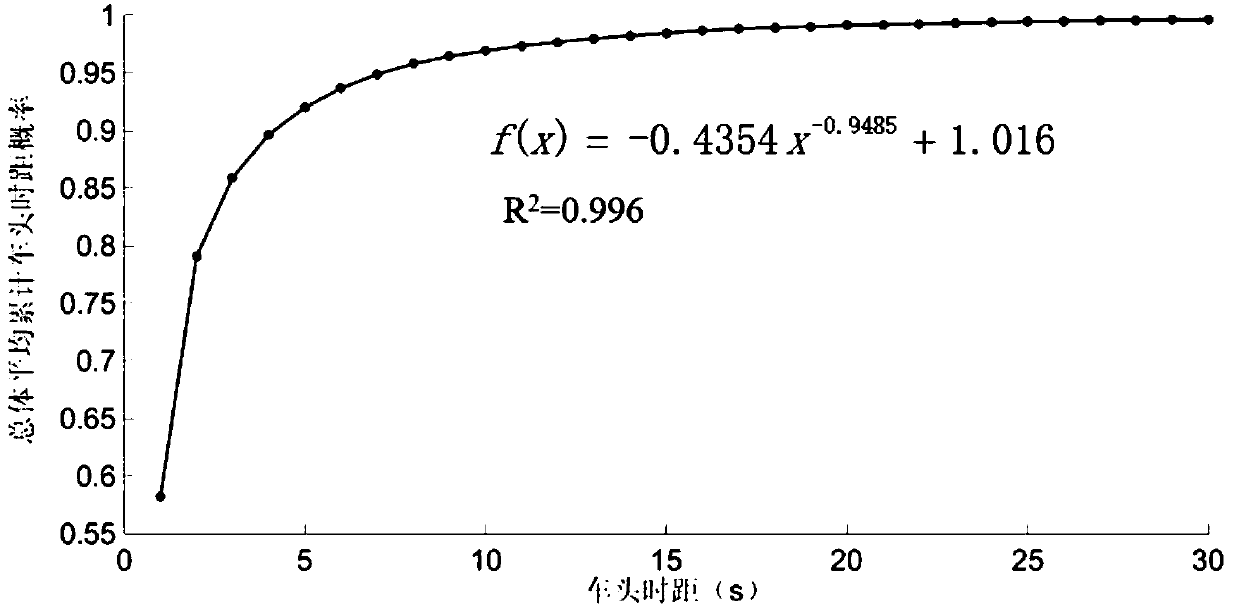
Incoming traffic flow-considered trunk motorcade judgment method
ActiveCN107665581AAvoid congestionAvoid wastingControlling traffic signalsDetection of traffic movementTraffic flowInfluence factor
The invention discloses an incoming traffic flow-considered trunk motorcade judgment method. In order to overcome the defect that the influence of the traffic flow of a branch on the discrete characteristics of the traffic flow of a trunk is not taken into consideration for an existing motorcade judgment model in the prior art, the invention provides the above method. The incoming traffic flow-considered trunk motorcade judgment method comprises the following steps of 1, determining a critical head time interval; 2, calculating the relation among the traffic flow of the branch, the length of atrunk road section and the critical head time interval; 3, calculating the relation among the traffic flow of the branch, the position of the branch and the critical head time interval; 4 calculatingthe relation among the traffic flow of the branch, the traffic flow of the trunk and the critical head time interval; 5, establishing a motorcade judgment index model: 1) calculating the relation between the critical head time interval and each influence factor; 2) determining a motorcade judgment model: (img file = 'DDA 0001425314000011.TIF 'wi = '1166 'he = '135 ') in the formula, HK is the critical head distance with the unit thereof to be s; q0 is the traffic flow of the trunk with the unit thereof to be veh / h; q1 is the traffic flow of the branch with the unit thereof to be veh / h; a, b,c, d and e are undetermined parameters and are obtained through the prameter calibration according to actual data; 6) determining a motorcade.
Owner:JILIN UNIV
A key target identification method for automobile cruise system
InactiveCN106114511BRealize online real-time estimationAccurately identify and trackExternal condition input parametersGoal recognitionSlip angle
The invention discloses a key target identification method for an automobile cruising system. Based on the fuzzy control theory, a multi-target automobile lane changing fuzzy logic controller is designed, a dangerous lane changing automobile is prejudged, and effective identification of a straight lane key target is determined. The tilting motion influence of automobile bend running is considered, an extension Kalman filtering on-line real-time estimation of an automobile mass center side slip angle and a road curvature is achieved, the bend key target identification method is provided, a key target judgment basis is given, and effective identification of the bend key target is achieved.
Owner:LIAONING UNIVERSITY OF TECHNOLOGY
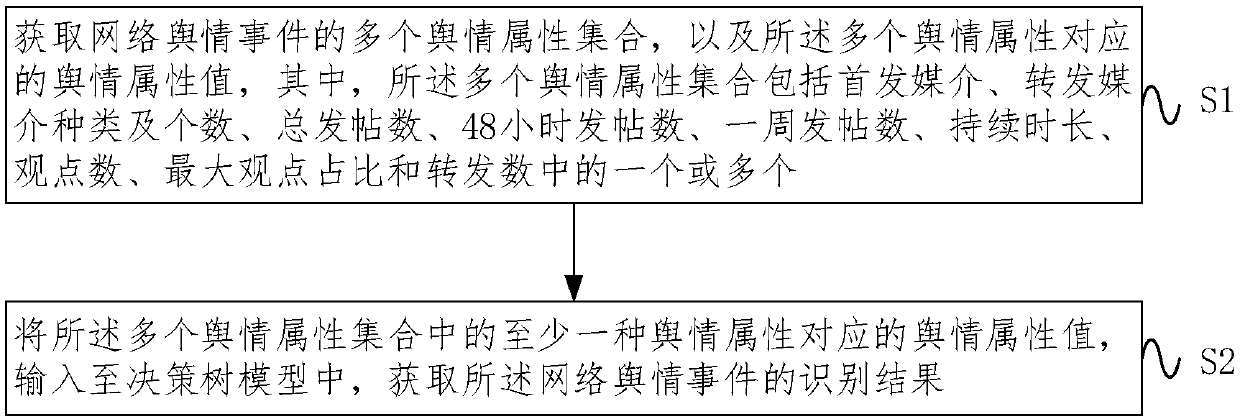
Network pseudo public opinion identification method based on combined optimization decision tree
InactiveCN107742256AAccurate identificationQuick identificationData processing applicationsWeb data indexingViewpointsDecision model
The invention provides a network pseudo public opinion identification method based on a combined optimization decision tree. The method comprises the following steps that S1, a public opinion attribute set of a network public opinion event is obtained, wherein the public opinion attribute set comprises one or more of the variety and number of first publish media and forwarding media, the total posting number, the number of posting within 48 hours, the number of posting within a week, duration, the number of viewpoints, the largest opinion ratio and the forwarding number; S2, public opinion attribute values corresponding to at least one public opinion attribute in the public opinion attribute set are input into a decision tree model, and an identification result of the network public opinion event is obtained. According to the method, the public opinion attribute values corresponding to at least one public opinion attribute in the public opinion attribute set are input into the decisiontree model, and network pseudo public opinions are more accurately and rapidly identified through the decision tree model.
Owner:CHINA AGRI UNIV
Secure bank card comprehensive prevention and control system on basis of big data application technology
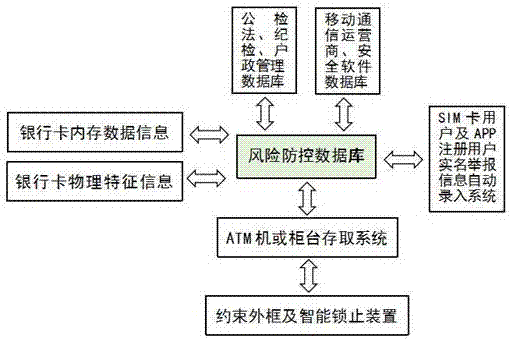
InactiveCN107578574ATo achieve effective identificationAvoid property damageComplete banking machinesRisk preventionControl system
The invention relates to a secure bank card comprehensive prevention and control system on the basis of a big data application technology. The system comprises an ATM, a bank counter depositing and withdrawing system, a cloud risk prevention and control database for integrating big data information, an intelligent image recognition system for integrating image recognition functions and a card reading system which contains bank card physical characteristic scanning and recognition. Latest data of multiple organizations are integrated by the risk prevention and control database and comprises data of head portrait, fingerprints and irises and bank card physical characteristic data reserved by a bank; by means of the system, through a comprehensive detection means, a rule-breaking operator ora cloned bank card can be eliminated, and the suspect is locked in an operating chamber, so that the suspect operational process saving and evidence solidification are synchronously conducted. According to the system, through software and hardware upgrading and function extension, recognition of the cloned bank card and the card holder is achieved, and operation of withdrawing and transferring ofthe suspect is prevented in time, so that property loss of a large cheated population is avoided, the measure efficiency is extremely high, and criminal activities of bank card fraud and money laundering are effectively struck and frightened.
Owner:贵州千寻科技有限责任公司
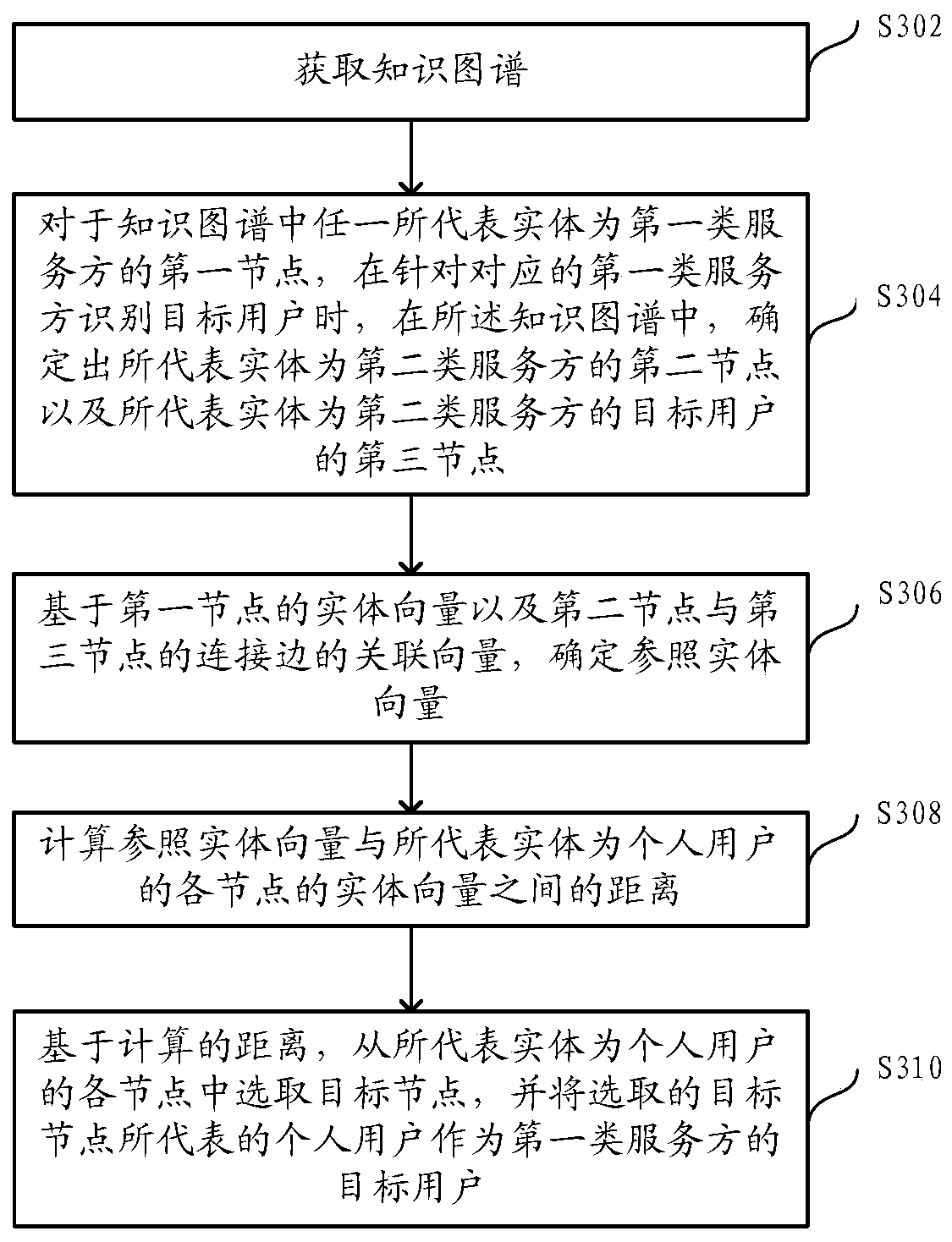
Method and device for identifying target user of service provider
ActiveCN111460171ATo achieve effective identificationFinanceSpecial data processing applicationsTheoretical computer scienceEngineering
The embodiment of the invention provides a method and device for identifying a target user of a service provider, and the method comprises the steps: obtaining a knowledge graph which comprises a plurality of nodes, wherein each node represents one entity and corresponds to one entity vector; and in the plurality of nodes, connecting the nodes with the association relationship through connecting edges, wherein each connecting edge corresponds to one association vector; for the first node of any first type of service party in the knowledge graph, when a target user is identified, determining asecond node of the second type of service party and a third node of the target user of the second type of service party in the knowledge graph; determining a reference entity vector based on the entity vector of the first node and the association vector of the connection edge of the second node and the third node; calculating distance between the reference entity vector and an entity vector of a node of each person user;. based on the distance, selecting a target node, and taking a personal user represented by the target node as a target user of the first type of service provider.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
License authentication method and device, electronic equipment and storage medium
ActiveCN109743330ATo achieve effective identificationUser identity/authority verificationUser inputChain network
The embodiment of the invention provides a license authentication method and device, electronic equipment and a storage medium, and the method comprises the steps: obtaining an authentication instruction input by an authentication user, wherein the authentication instruction comprises a copy license, an identifier of an original license and an authentication type, and the authentication type comprises content authentication and file authentication; Determining an original certificate and an authentication type according to the authentication instruction; When the authentication type is contentauthentication, determining first authentication information in a copy certificate corresponding to the content authentication; When it is judged that the authentication user is allowed to check theoriginal certificate corresponding to the identifier of the original certificate, determining first authentication information of the original certificate corresponding to the content authentication in the regional block chain network by utilizing a preset smart contract; Comparing whether the first authentication information in the copy certificate is consistent with the first authentication information in the original certificate or not; And if yes, determining that the copy certificate and the original certificate are certificates with the same content. According to the invention, the certificate is authenticated according to the authentication instruction of the authentication user.
Owner:BEIJING UNIV OF POSTS & TELECOMM
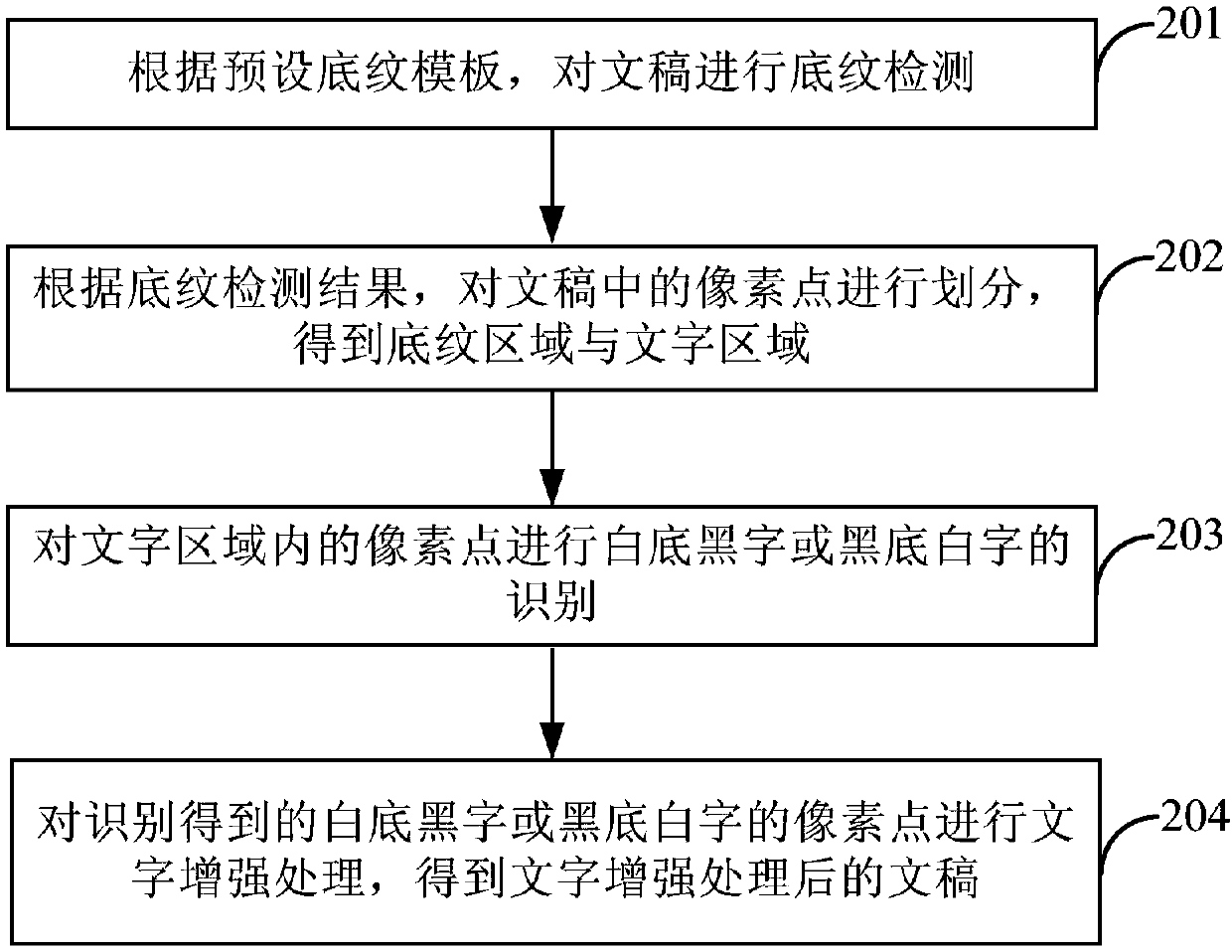
Character enhancement method and device
ActiveCN107766014ATo achieve effective identificationImprove clarityDigital output to print unitsPattern recognition
The invention provides a character enhancement method and device. The method comprises the steps of conducting shading detection on a document according to a preset shading template; dividing pixel points in the document according to a shading detection result to obtain a shading area and a character area; conducting recognition in a black-character-on-a-white-background mode or a white-character-on-a-black-background mode on the pixel points in the character area; conducting character enhancement processing on the pixel points in the black-character-on-a-white-background mode or the white-character-on-a-black-background mode obtained through recognition, and obtaining a document after character enhancement processing. According to the character enhancement method and device, effective recognition of shading in the document is achieved, through character enhancement processing on characters in the black-character-on-a-white-background mode or the white-character-on-a-black-background mode of which the shading is removed or weakened, the presentation definition of the characters in a printed document is improved.
Owner:ZHUHAI PANTUM ELECTRONICS
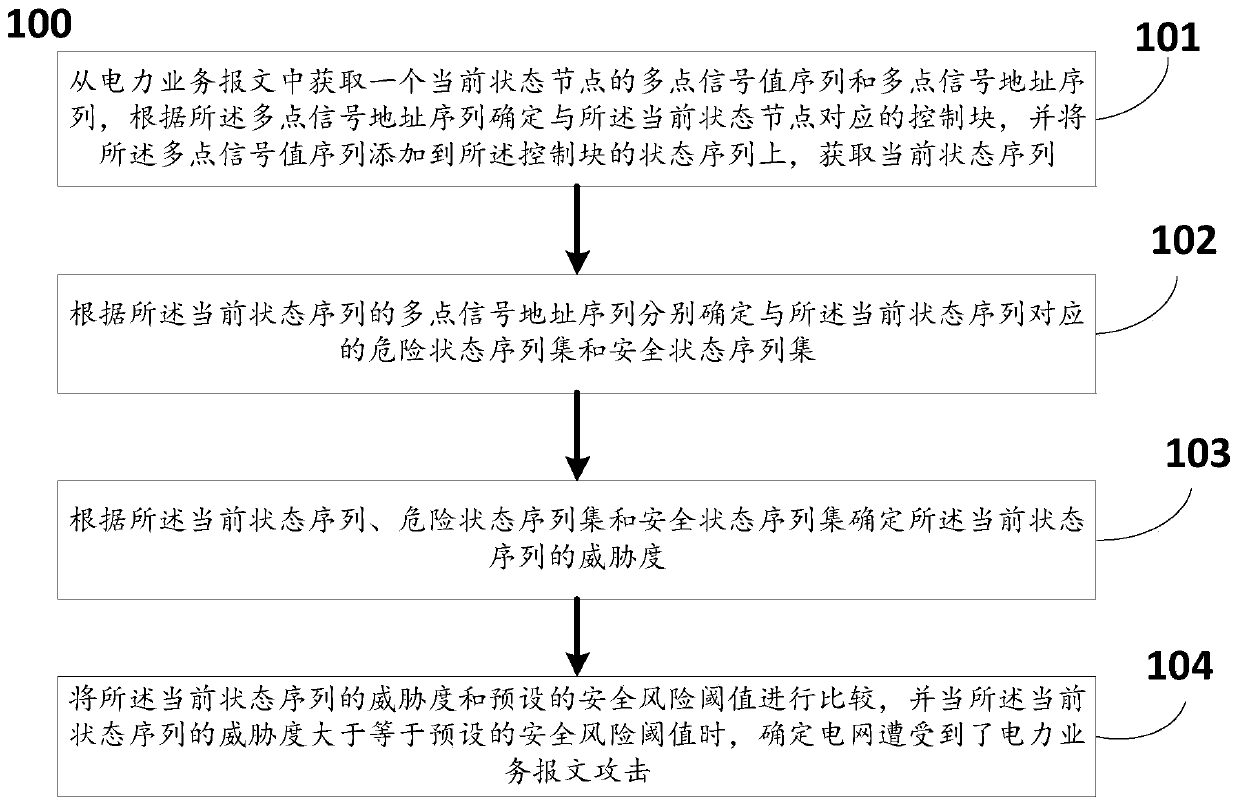
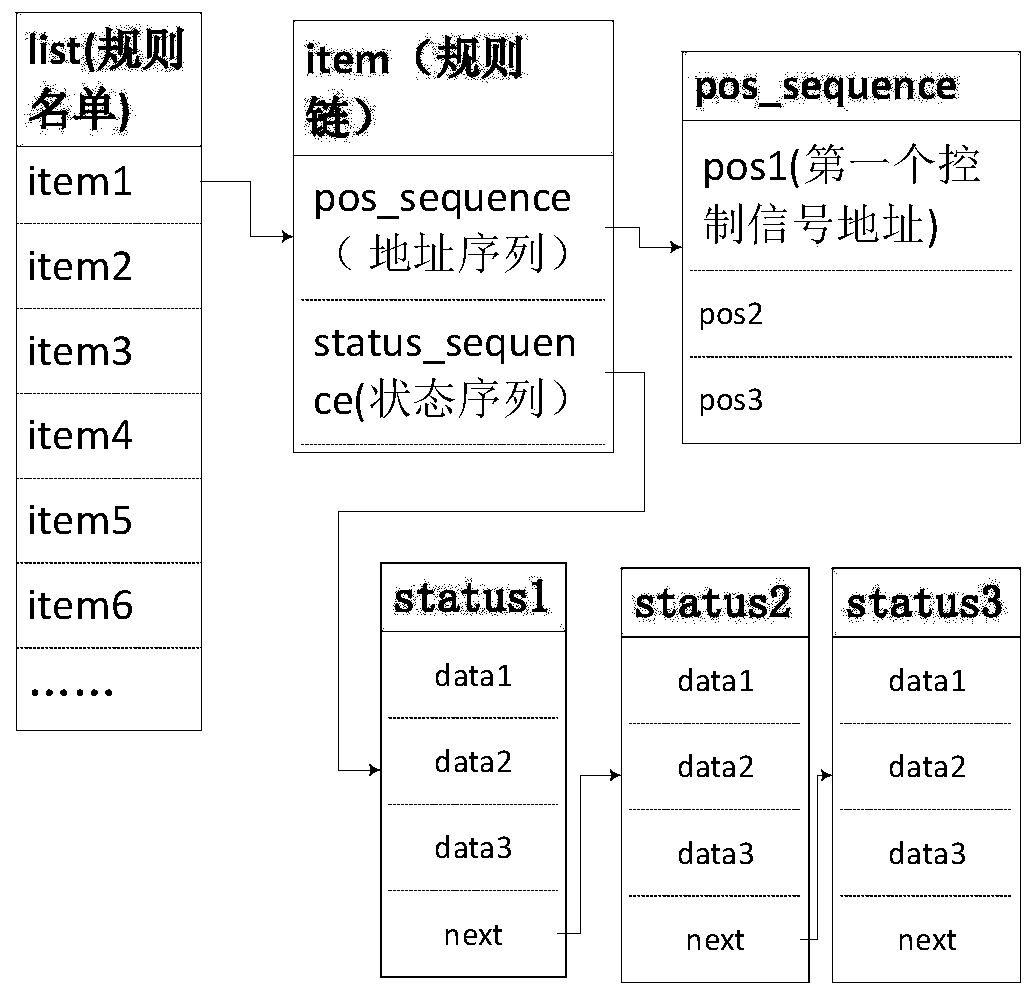
Power service message attack identification method and system based on service logic
PendingCN110751570ATo achieve effective identificationGuaranteed uptimeData processing applicationsTransmissionAttackAnomaly detection
The invention discloses a power service message attack identification method and system based on service logic. The method comprises the following steps: determining a current state sequence of a power service; respectively determining a dangerous state sequence set and a safe state sequence set corresponding to the current state sequence according to the multi-point signal address sequence of thecurrent state sequence; determining the threat degree of the current state sequence according to the current state sequence, the dangerous state sequence set and the safe state sequence set; and whenthe threat degree of the current state sequence is greater than or equal to a preset security risk threshold, determining that the power grid is attacked by the power service message. According to the invention, a dangerous state sequence set and a safe state sequence set of power business logic are defined; according to the method, misuse detection and anomaly detection methods are combined, thethreat degree of the power service is evaluated, and whether the power grid is attacked by the power service message is determined according to the threat degree, so that the power service message attack is effectively identified, and the safe and reliable operation of a power industrial control system is guaranteed.
Owner:CHINA ELECTRIC POWER RES INST +3
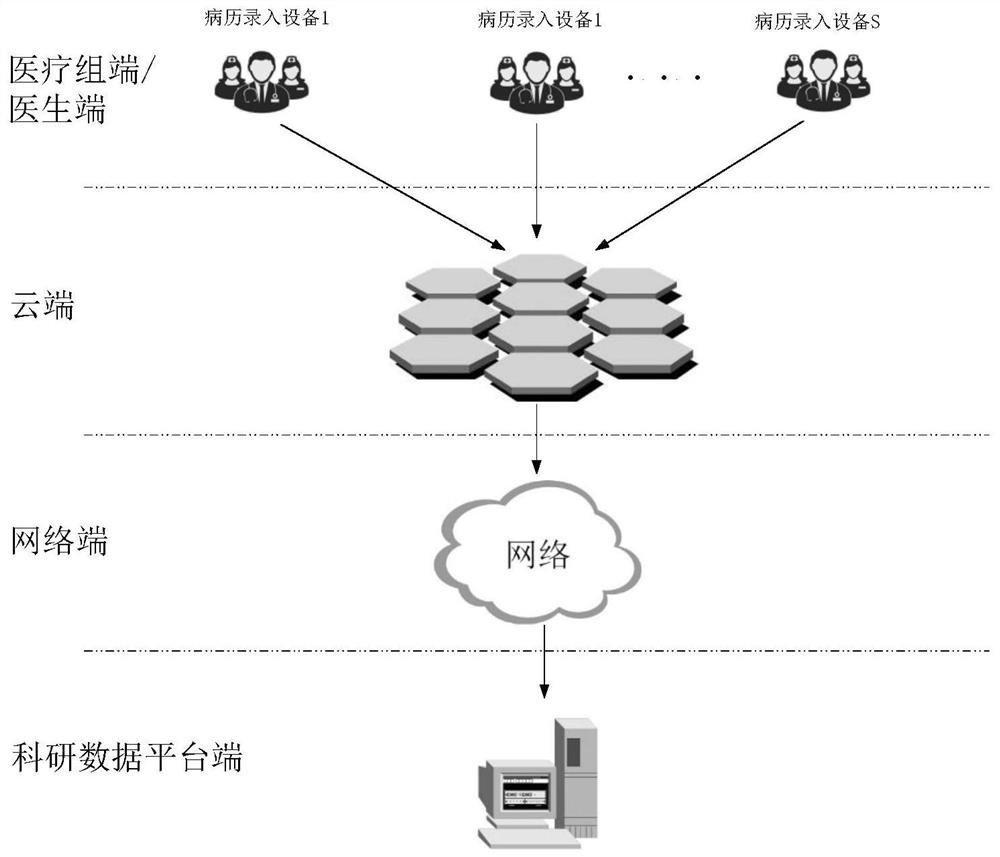
Electronic medical record medication structural processing system based on multiple models
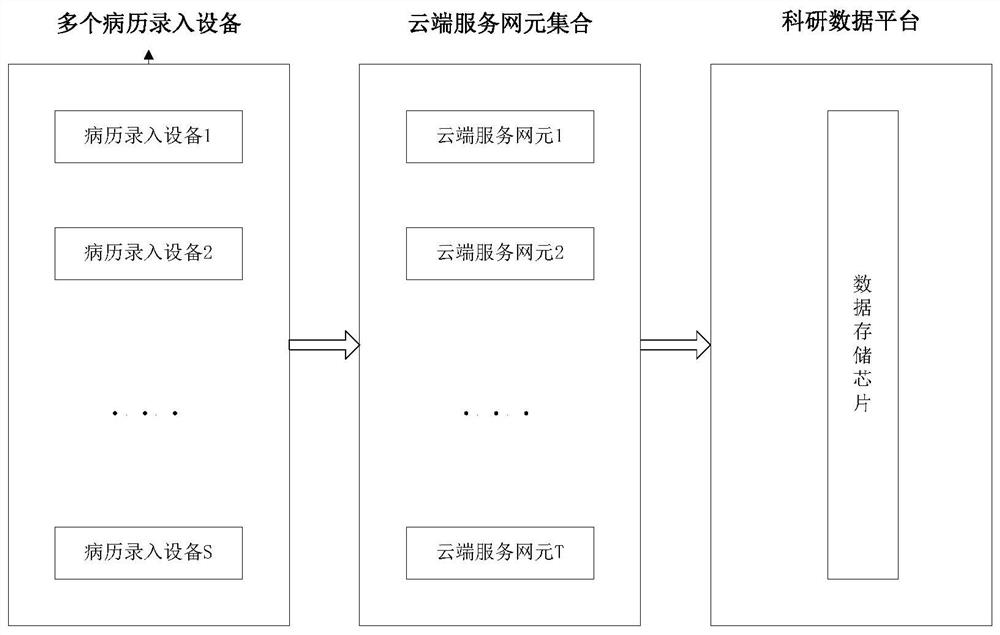
ActiveCN112309519AReliable data baseEnsure that the model achieves effective identificationDrug and medicationsNatural language data processingMedical recordNerve network
The present invention relates to an electronic medical record medication structural processing system based on multiple models. The system comprises: a plurality of medical record input devices, wherein each medical record input device is used for inputting each piece of electronic medical record information of a medical group / doctor corresponding to the medical record input device, and each pieceof electronic medical record information comprises a course paragraph; and a cloud service network element set which is used for selecting a corresponding deep neural network model according to the received source medical group / doctor of each piece of electronic medical record information so as to execute deep neural network identification processing on the disease course paragraph and obtain a patient medication structured file taking a medication name as a main index word. The electronic medical record medication structural processing system based on multiple models is intelligent in operation and timely in response. On the basis that a computer adopts a deep neural network model to read electronic medical record data mainly including texts, medical record writing habits of different medical groups / different doctors in the same medical institution are recognized, and effective structured medical basic data are provided for a scientific research data platform of the medical institution.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com