Method and device for identifying target user of service provider
A target user and identification method technology, applied in the computer field, can solve problems such as incomplete holding data of the unit and failure to identify the target user of the service provider
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
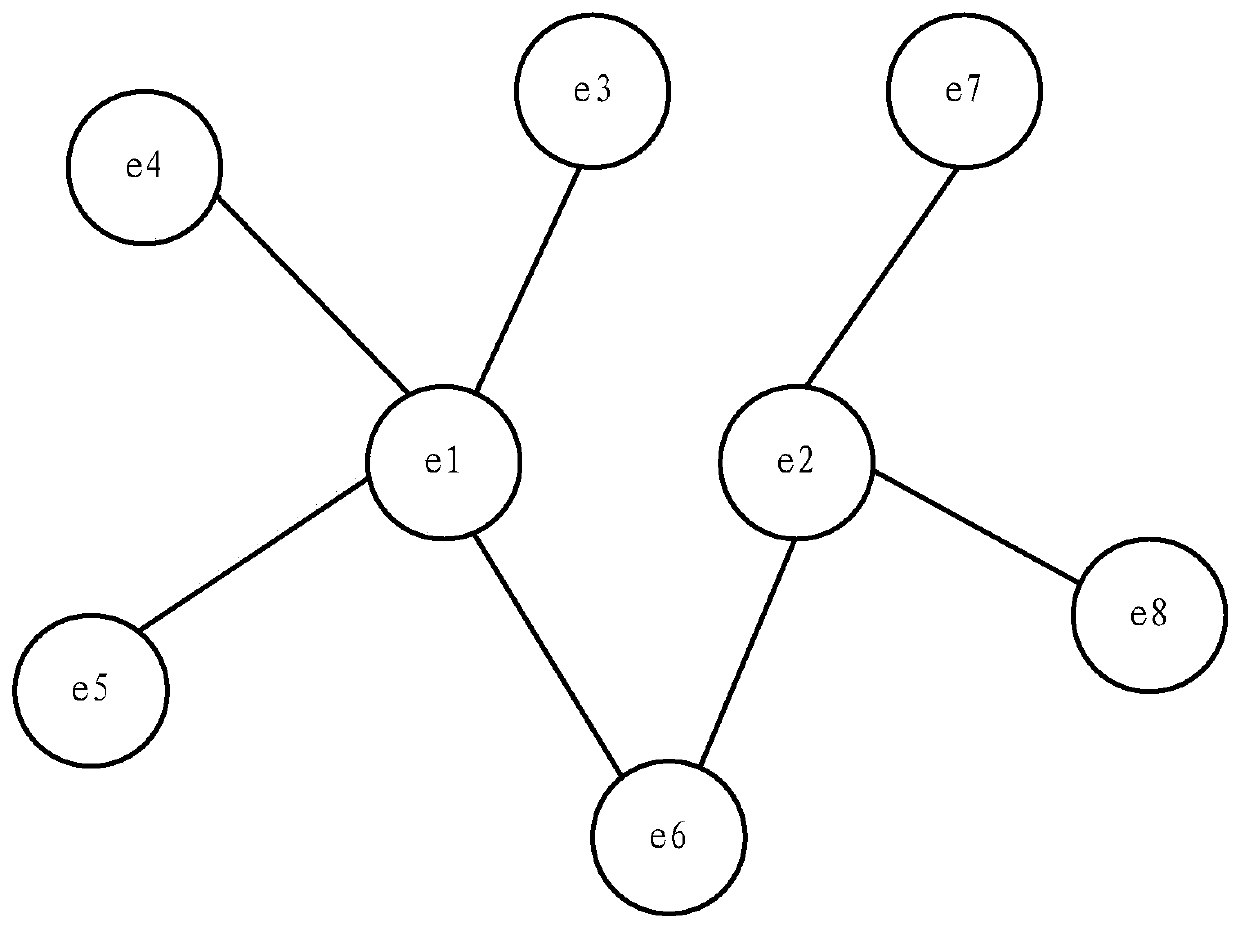
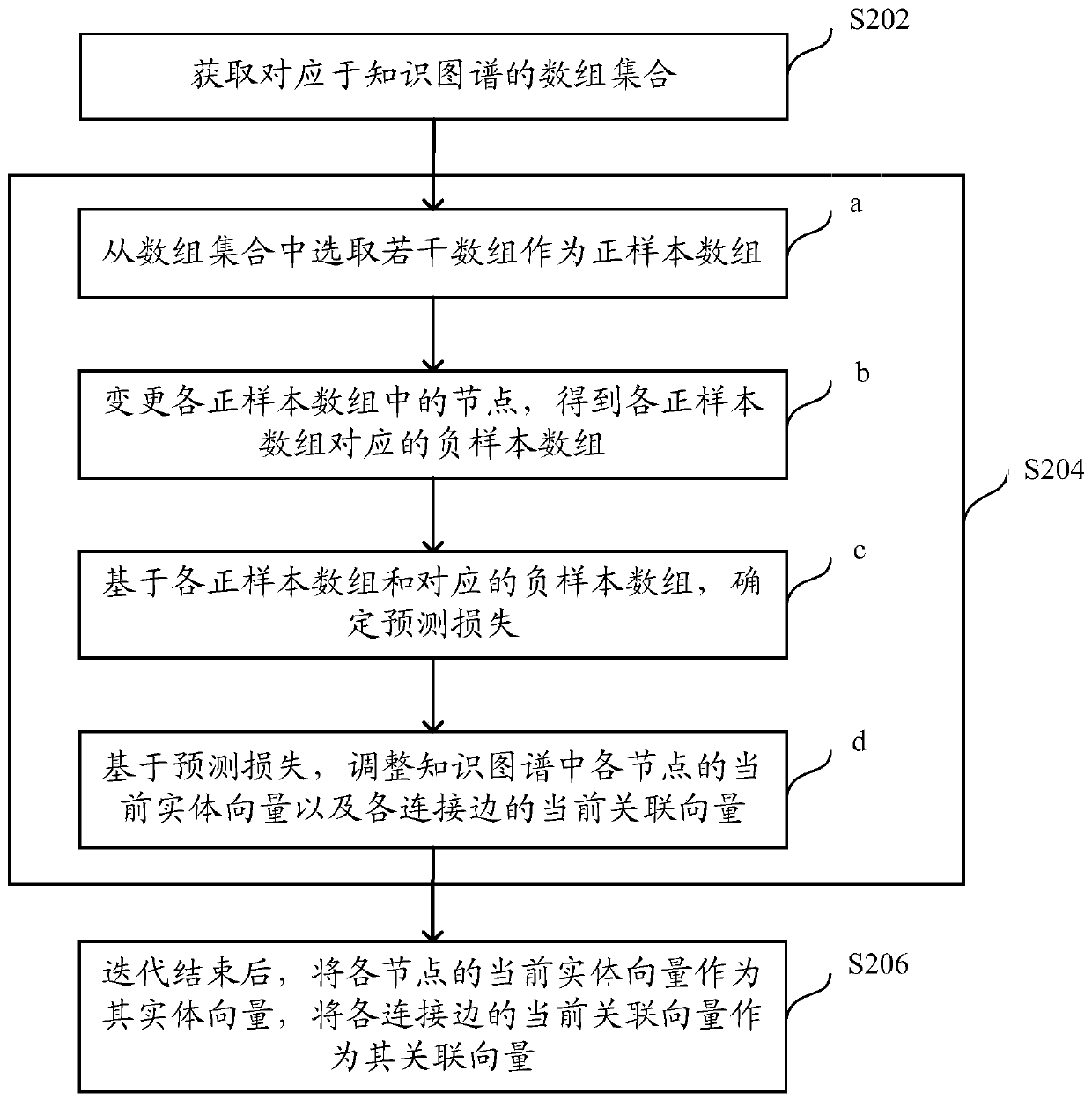
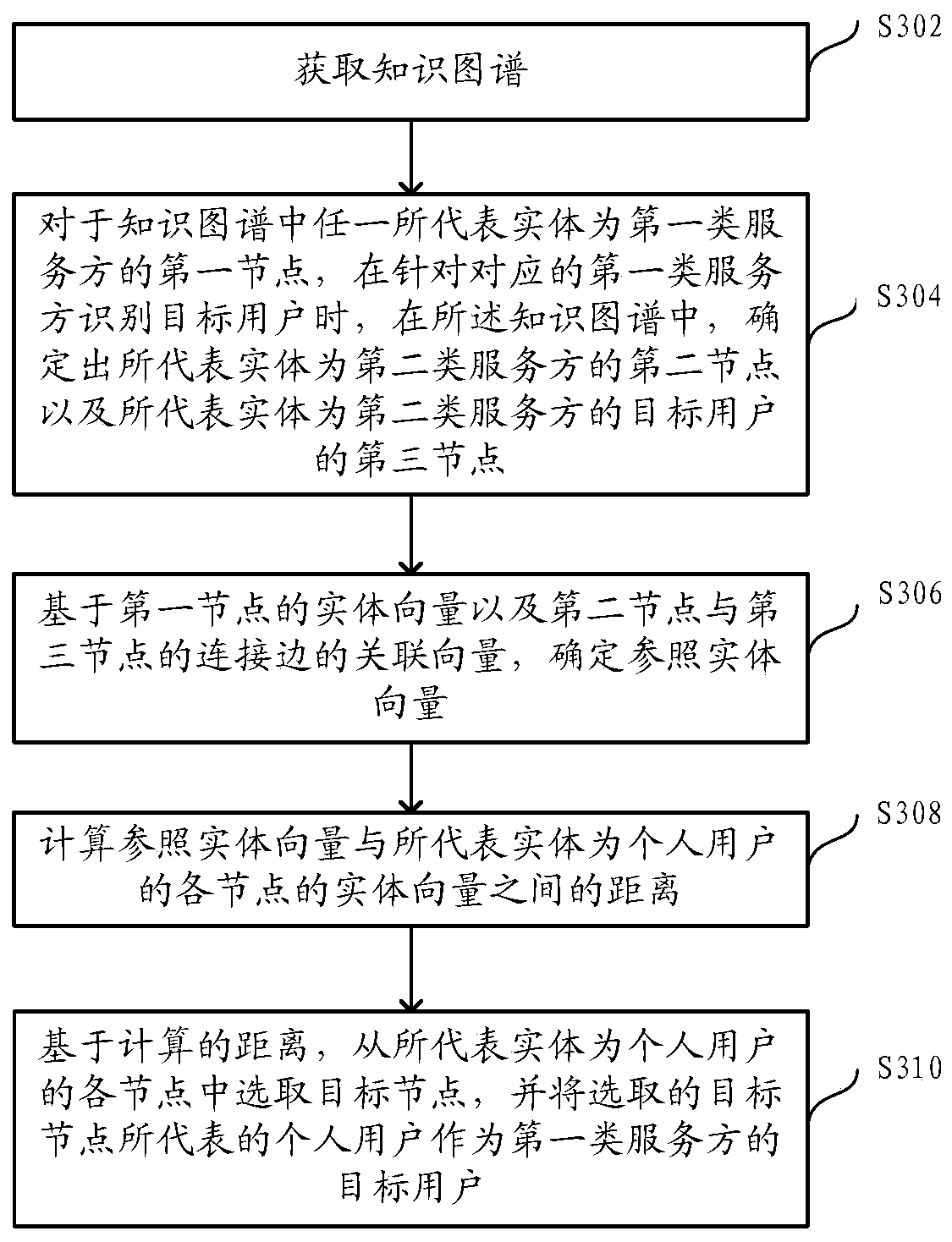
[0027] In order to effectively identify the target users of the service provider, the inventors of the present application propose to identify the target users of the service provider based on knowledge graphs. The service parties mentioned in this specification can be, for example, organizations such as enterprises, schools, and hospitals. The target users of the service party include but are not limited to the ultimate beneficiary.
[0028] The knowledge graph described in this specification can be constructed based on several service parties and the association relationship between each service party and their respective individual users. The service provider here may include, but not limited to, the first type of service provider that has not identified the target user and the second type of service provider that has identified the target user. In ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com