Power service message attack identification method and system based on service logic
A technology for power business and attack identification, applied in transmission systems, electrical components, data processing applications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
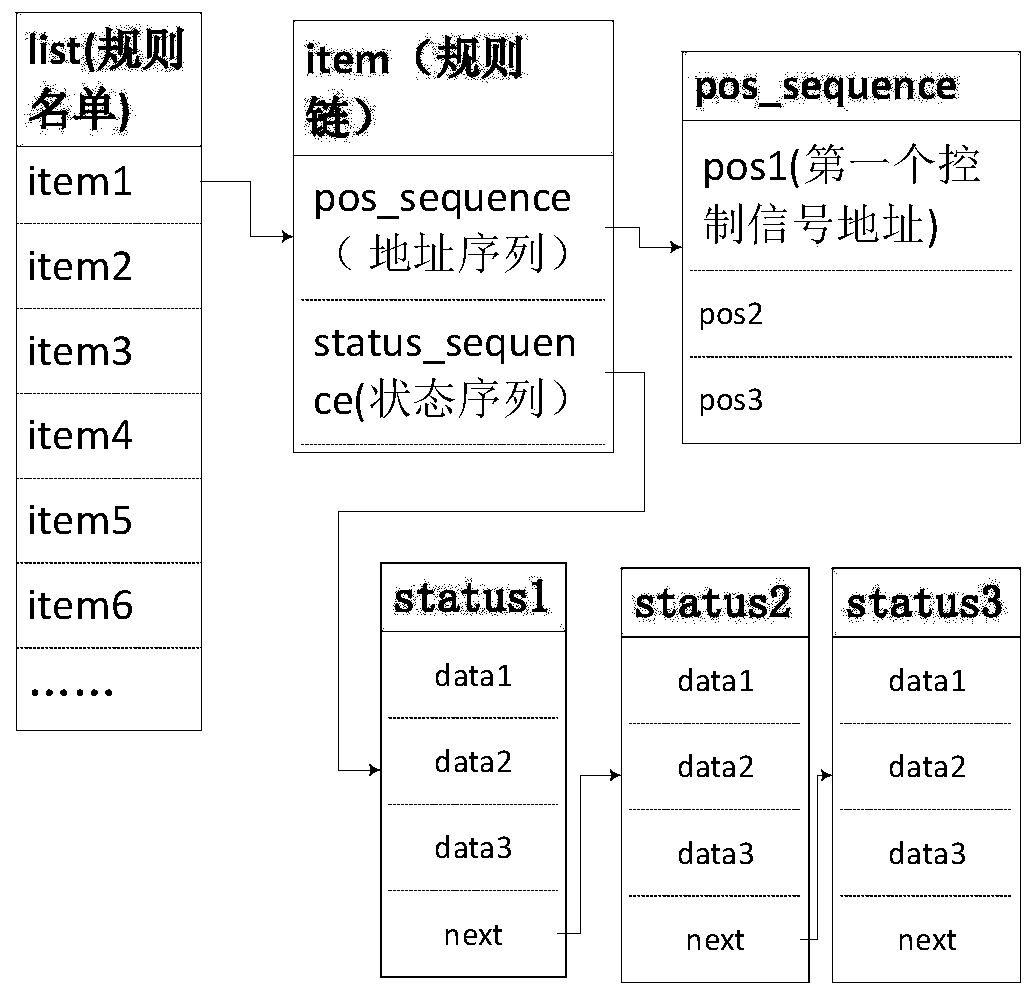
[0128] Suppose the state block attacked by the attacker has three FCDAs, and the address information of each FCDA is as follows:
[0129] pos 1 ="(APPID=0x0001)-(dataset=DeviceF001 / LLN0$GOOSE1)-(alldata.1)",
[0130] pos 2 ="(APPID=0x0001)-(dataset=DeviceF001 / LLN0$GOOSE1)-(alldata.2)",
[0131] pos 3 ="(APPID=0x0001)-(dataset=DeviceF001 / LLN0$GOOSE1)-(alldata.3)",
[0132] The corresponding control block status is: status 1 =(0,0,0) T , status 2 =(0,0,1) T ,...,status 8 =(1,1,1) T . Set the security risk threshold X for the intrusion detection method safe is 0.25.
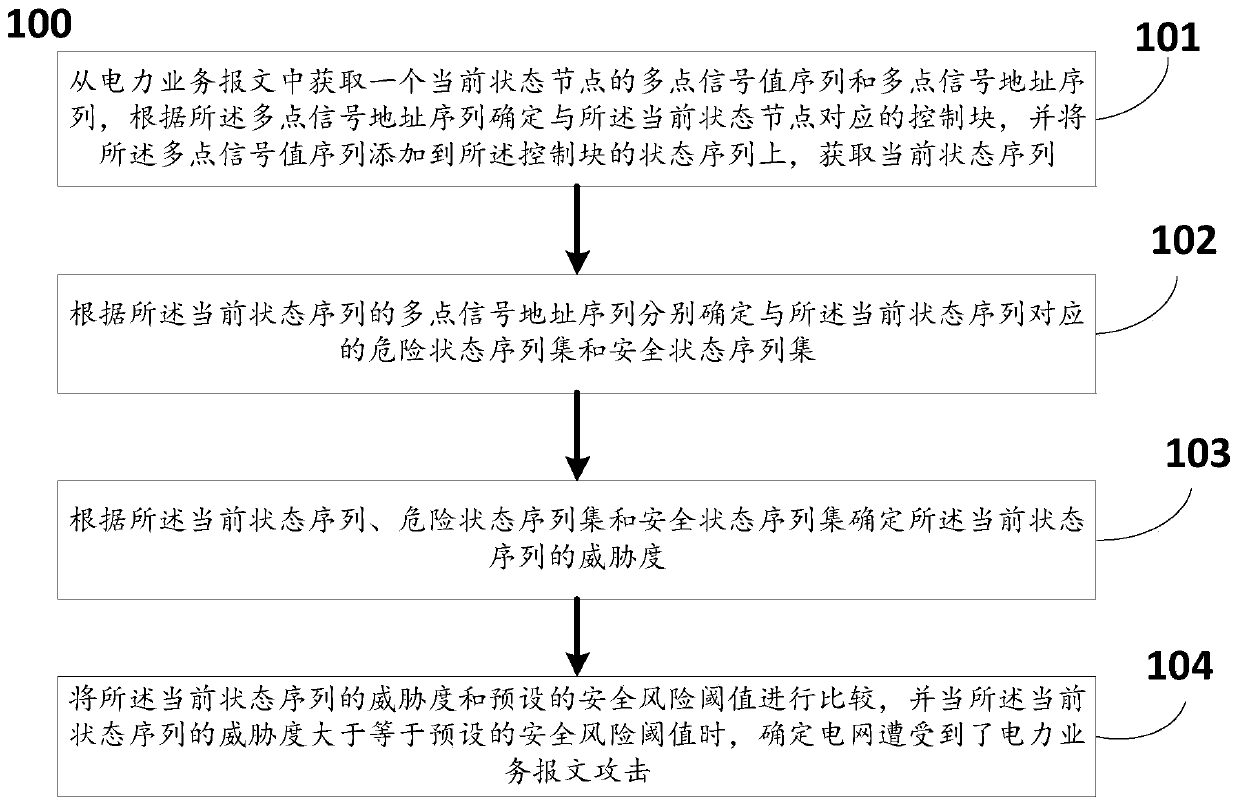
[0133] When it is determined that the power grid is attacked by power service packets, the specific implementation method is as follows:
[0134] Step (1), status chain entry: assume that the entered status sequence is status_sequence 1 =(S 1 , pos_sequence), where S 1 =(status 1 , status 2), pos_sequence=(pos 1 ,pos 2 ,pos 3 ) T , now extract a state node Node from the application layer messag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com