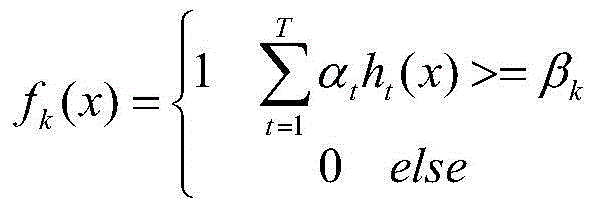Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
411results about How to "Taking into account efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
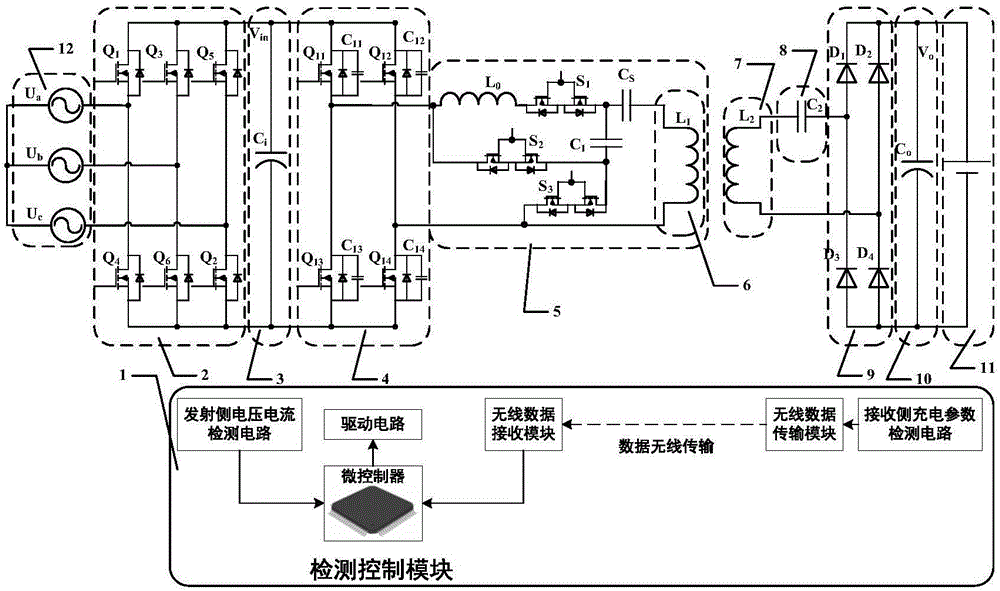
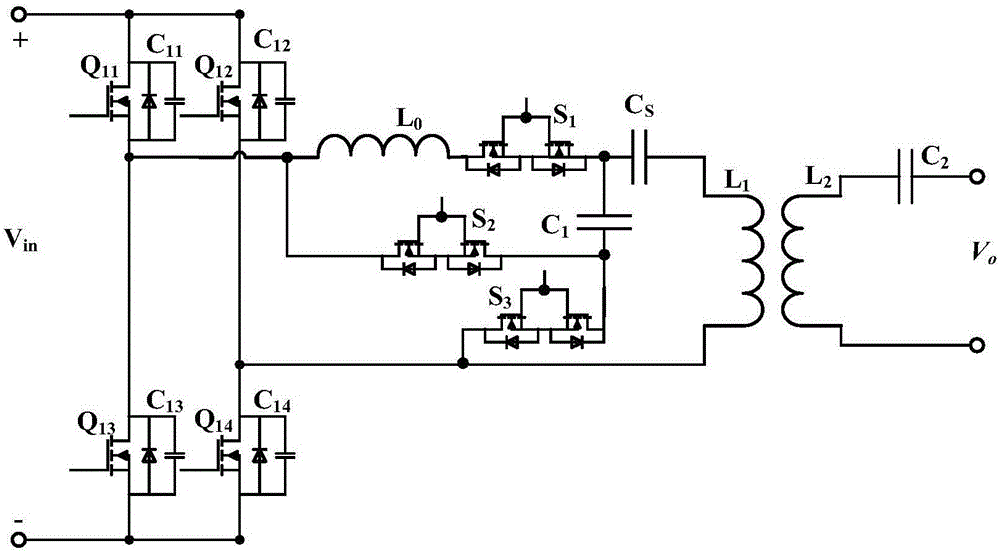
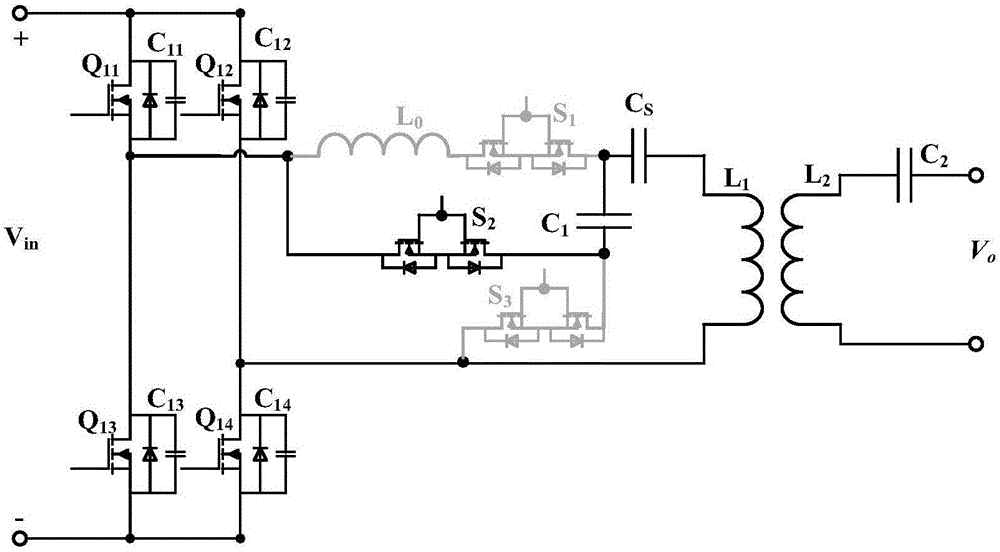
Resonant compensation topology variable magnetic coupling resonant wireless electric energy transmission device and method
InactiveCN106849299ATaking into account efficiencyReduce control difficultyBatteries circuit arrangementsElectric powerCouplingComputer module
The invention discloses a resonant compensation topology variable magnetic coupling resonant wireless electric energy transmission device and method. The transmission device comprises a rectification module, an emitting end voltage stabilization module, a high-frequency inversion module, an emitting end coupling resonant coil, a receiving end coupling resonant coil, a receiving end resonant circuit capacitor, a receiving end rectification module, a receiving end voltage stabilization module, a variable resonant compensation circuit module and a detection control module, wherein the input end of the variable resonant compensation circuit module is connected with the output end of the high-frequency inversion module; the output end of the variable resonant compensation circuit module is connected with the emitting end coupling resonant coil; the detection control module is used for detecting charging parameter and input parameter information, and driving the on-off of an MOS (metal oxide semiconductor) tube and the on-off of a controllable switch. At a constant current charging stage, the series / series resonant compensation topology is used; at a constant voltage charging stage, the LCC / series resonant compensation topology is used; on the premise of not changing an electric automobile side receiving end device, the unique requirements of electric automobile charging are effectively met; the efficiency and power optimization of a wireless electric energy transmission system is considered.
Owner:SHANDONG UNIV
Projection full-convolution network three-dimensional model segmentation method based on fusion of multi-view-angle features
ActiveCN108389251AImproving the effect of semantic segmentation annotationTaking into account efficiencyNeural architectures3D-image renderingData setAlgorithm
The invention discloses a projection full-convolution network three-dimensional model segmentation method based on fusion of multi-view-angle features, and the method comprises the steps: 1, collecting data of a data set inputted into a three-dimensional network model; 2, carrying out the sematic segmentation of a model projection rendering map through a FCN (full-convolution network) integrated with multi-view-angle features, and obtaining the probability that the pixels of the projection rendering map of a model in all view-point directions are predicted as labels; 3, carrying out the back projection of a projection rendering map sematic segmentation probability graph of the model in each view-point direction, employing the maximum view-angle pooling, and obtaining the probability that amodel patch is predicted as each label; 4, carrying out the optimization through employing a Graph Cut image segmentation algorithm, and obtaining a final prediction label of the model patch.
Owner:NANJING UNIV
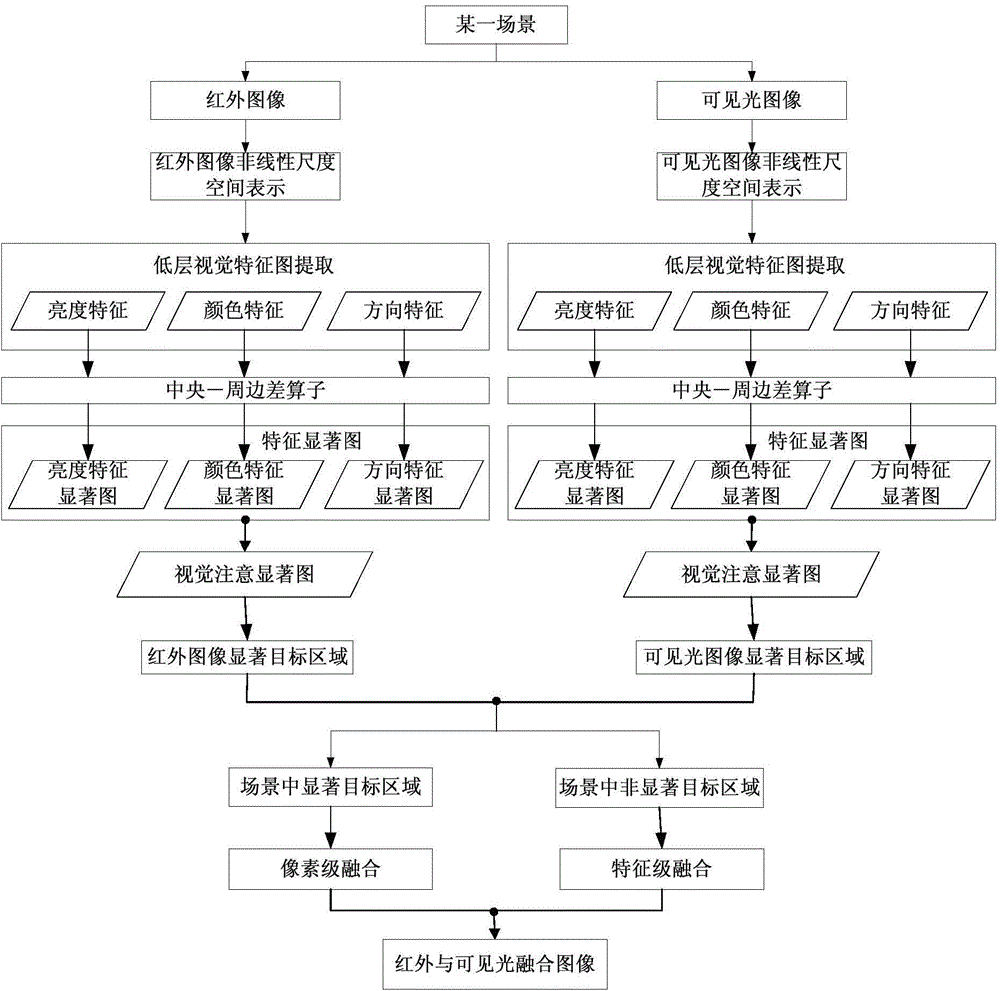
Infrared and visible light image fusion method based on salient objects
ActiveCN104700381AGuarantee the quality of fusionData volume reductionImage enhancementSalient objectsComputational model
The invention provides an infrared and visible light image fusion method based on salient objects. The infrared and visible light image fusion method based on the salient objects includes following steps: building nonlinear scale space representation for an infrared image and a visible light image which respectively comprise a plurality of objects in a given scene; using a visual attention computational model to compute visual attention salient maps of the infrared image and the visible light image based on the nonlinear scale space representation of the images; using a return inhibition mechanism to select salient object areas from the infrared image and the visible light image based on the visual attention salient maps of the infrared image and the visible light image, and computing all salient object areas in the whole scene; performing rectification operation on the infrared image and the visible light image, using a pixel level fusion algorithm to perform fusion treatment on the salient object areas, and using a feature level fusion algorithm to perform fusion treatment on non-salient object areas; generating a fusion image of the infrared image and the visible light image of the whole scene by synthesizing results.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
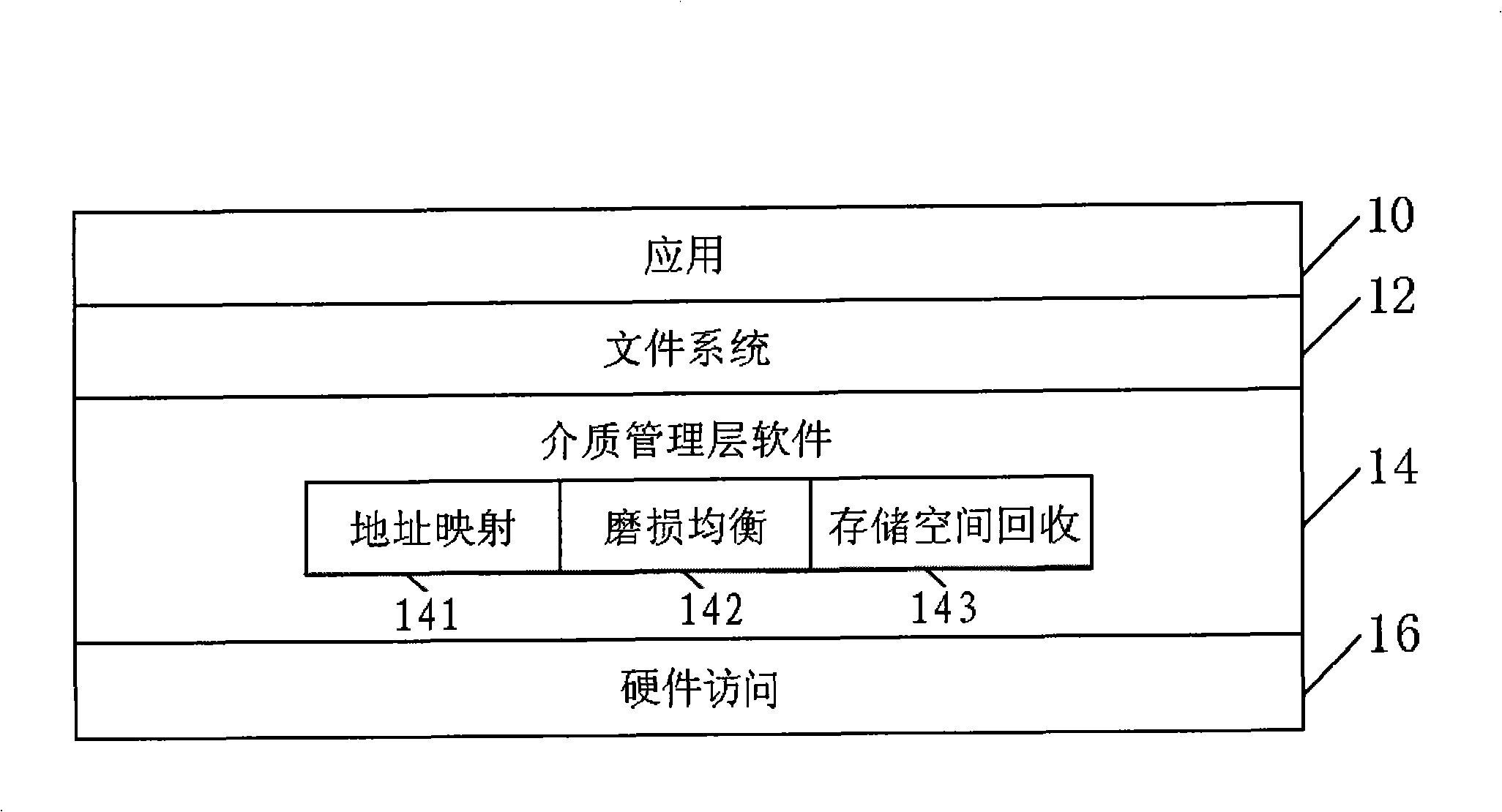
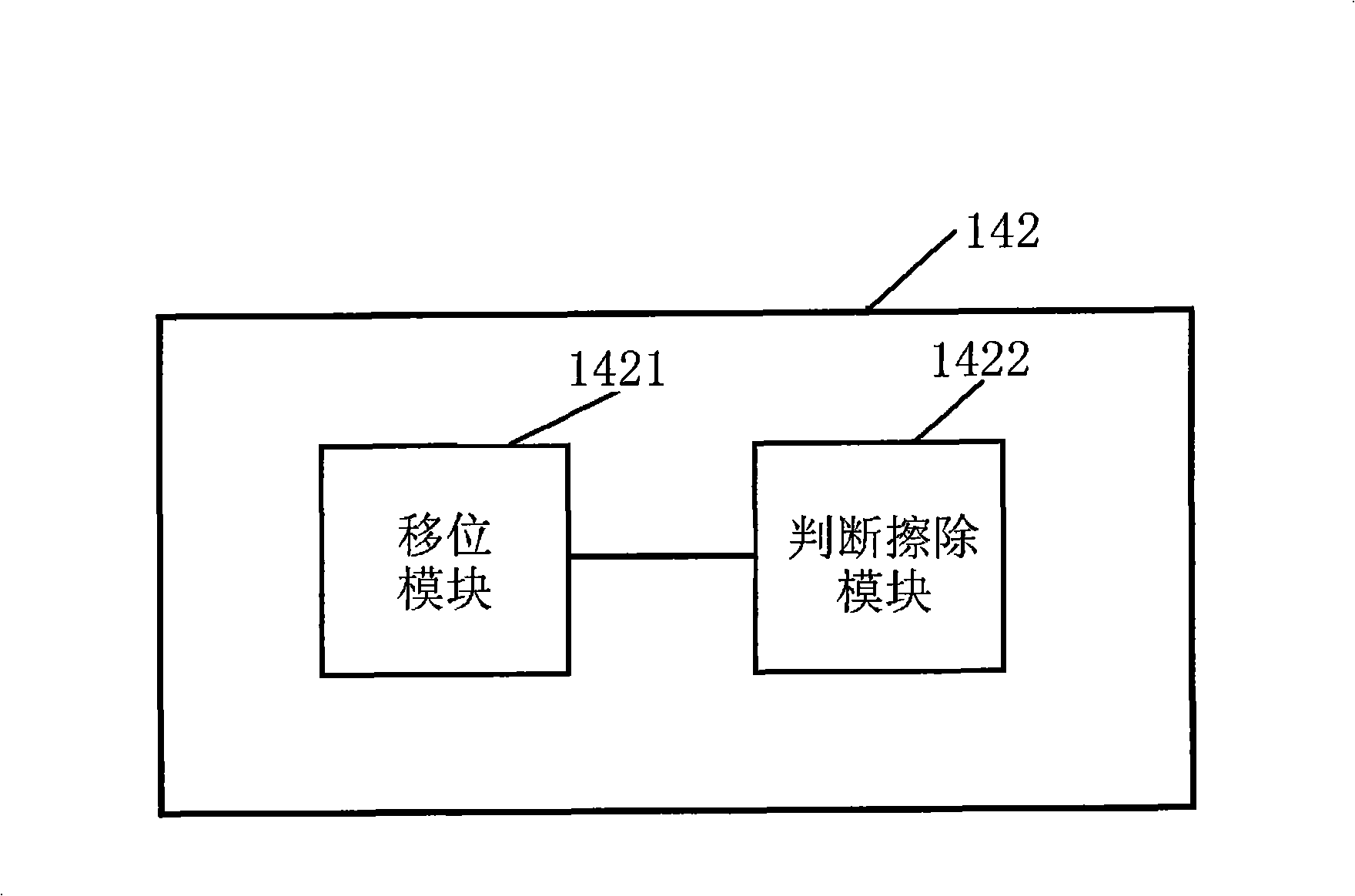
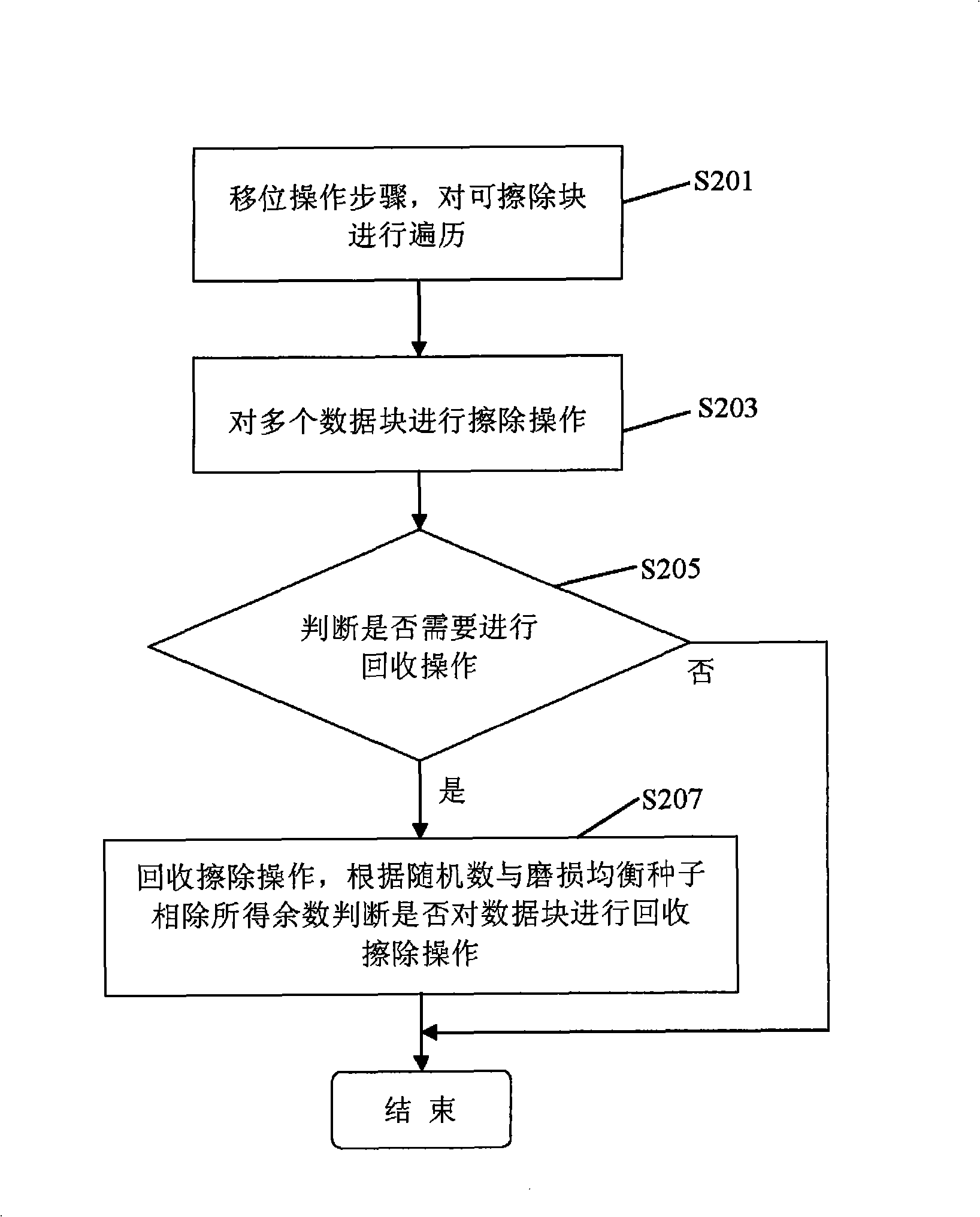
Memory system, abrasion equilibrium method and apparatus of non-volatile memory
ActiveCN101354681ATaking into account efficiencyMemory architecture accessing/allocationMemory adressing/allocation/relocationLeveling effectEmbedded system
The invention provides a wear-leveling method and a wear-leveling device for a memory system and a non-volatile memory, wherein the non-volatile memory comprises a plurality of data blocks and a linked list which is formed by the plurality of data blocks. The wear-leveling method comprises the following steps: firstly, a step of shift operation, namely the plurality of data blocks are arranged in order according to time values respectively corresponding to the plurality of data blocks and according to the time order of the time values, so as to form the linked list; and secondly, a step of erasure judgment, namely judgment is made whether to erase the plurality of data blocks, and when the plurality of data blocks are erased, corresponding data blocks are selected for erasure according to the time order of the time values of the plurality of data blocks in the linked list. The wear-leveling method and the wear-leveling device can simultaneously give attention to the system efficiency and the wear-leveling effect while really reflecting the service life of the erasable blocks in a system.
Owner:INTEL CORP
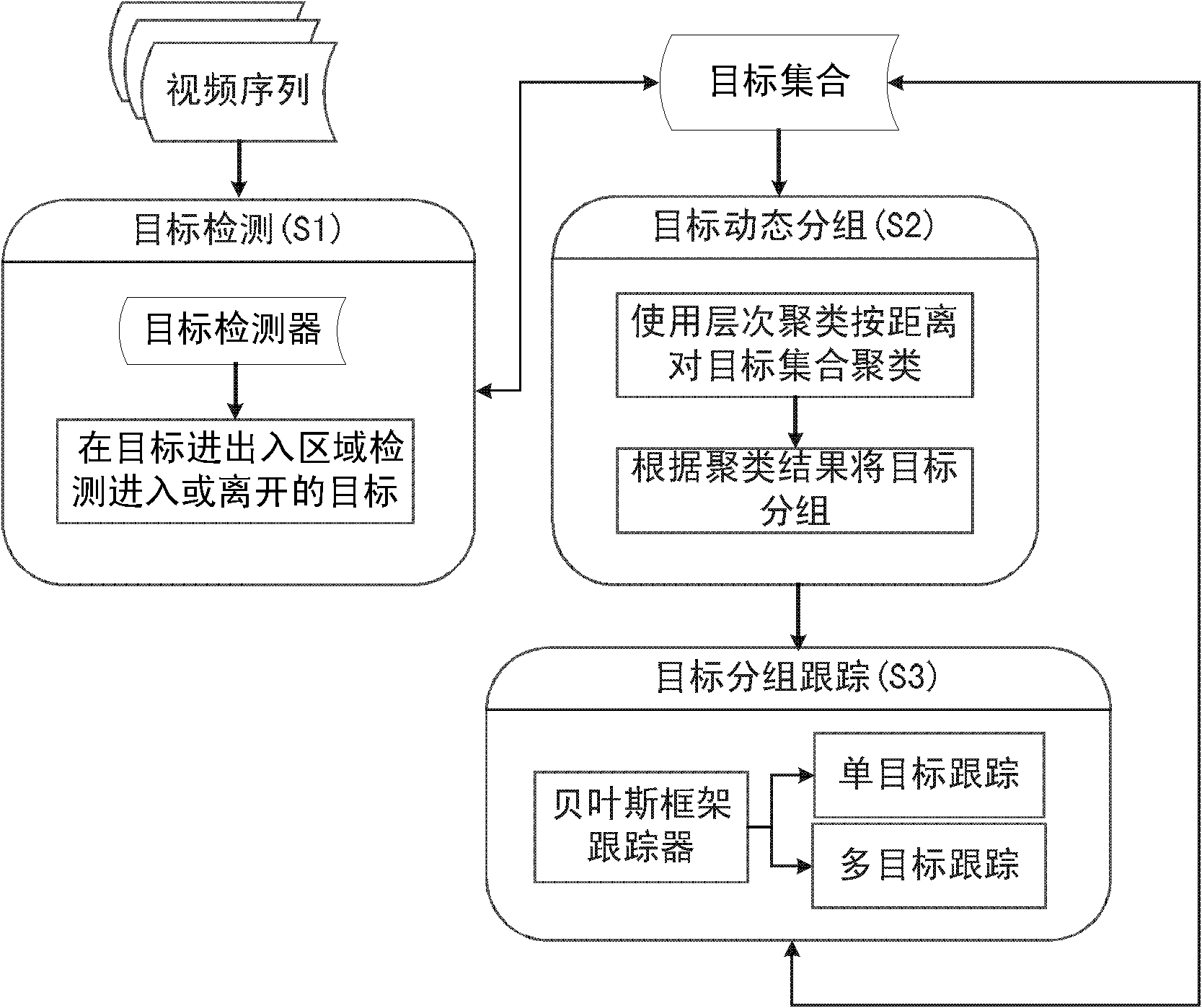
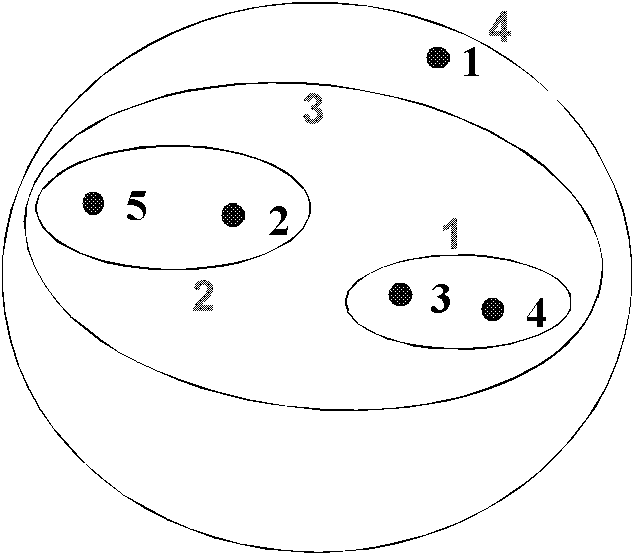
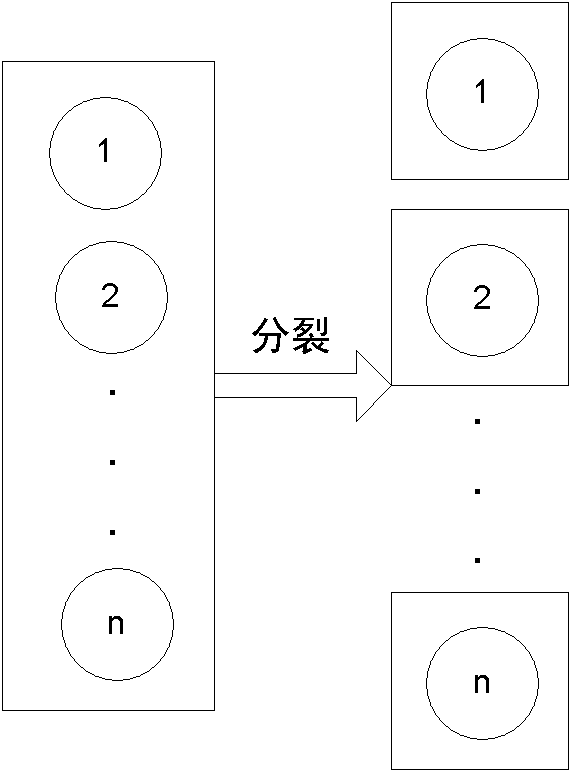
Multi-target tracking method based on dynamic group division
InactiveCN102148921AImprove efficiencyFix bug prone to target mergingTelevision system detailsColor television detailsPattern recognitionMulti target tracking
The invention relates to a multi-target tracking method based on dynamic group division, which comprises the steps as follows: S1, for a certain time in a video scene, whether a target enters or leaves a scene area or not is judged firstly and a target set is updated according to a detection result; S2, a grouping threshold of the target set is set and hierarchical clustering is used to cluster the target set at last time by distances, and then a target position at last time is divided into different groups according to a clustering result at last time; S3, each group in the target set is provided with a tracker; the trackers use a Bayesian framework to deduce the optimal value of each target at a current time position according to the position state of each target at last time and the observation value of each target on an image at the current time in the groups; and the optimal value of each target at the current time position is used for updating the position state of each target in the target set so as to prepare deducing the position of each target at next time.
Owner:江苏瑞奥风软件科技有限公司
Trust assessment-based adaptive trust negotiation system and method
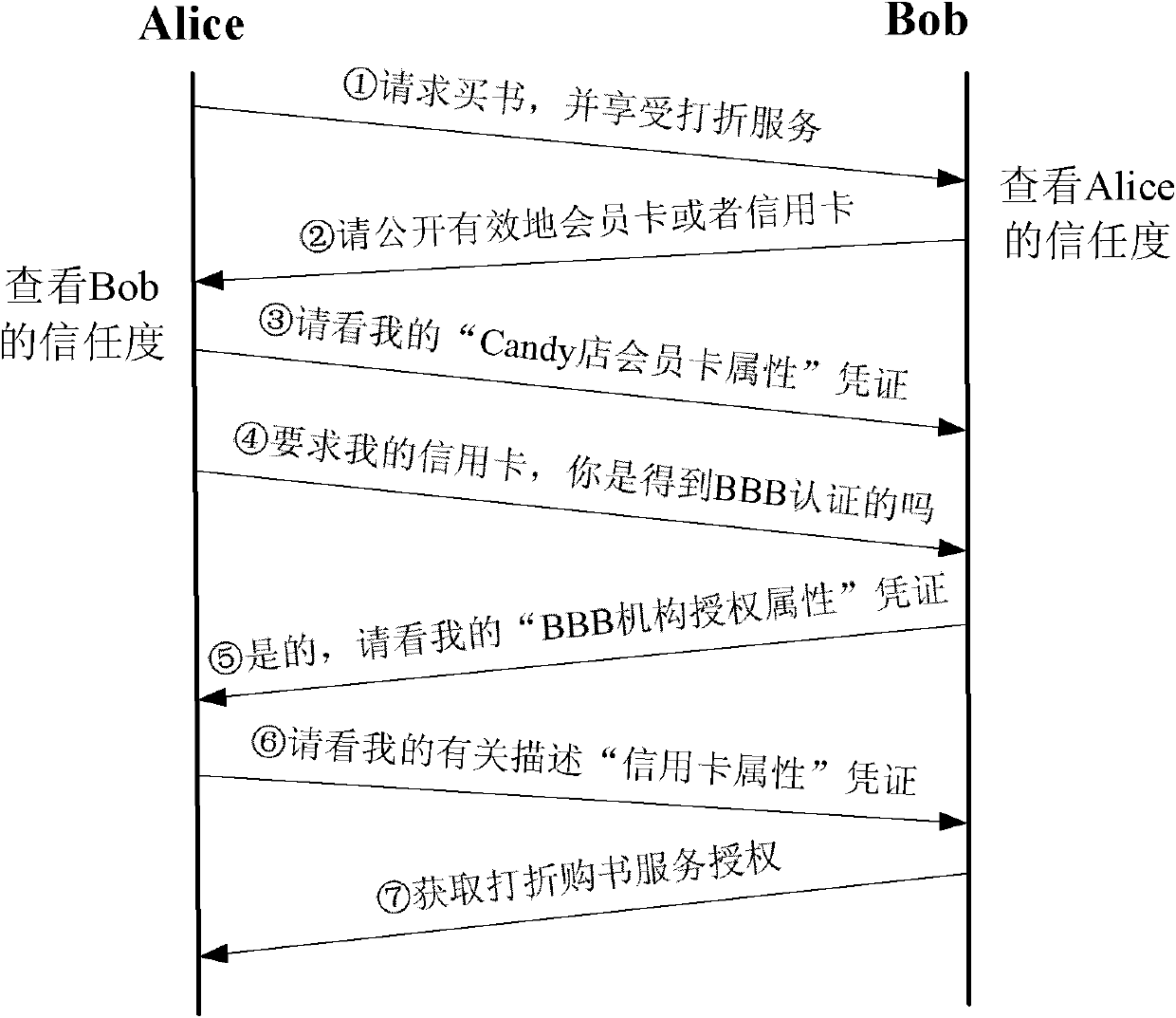
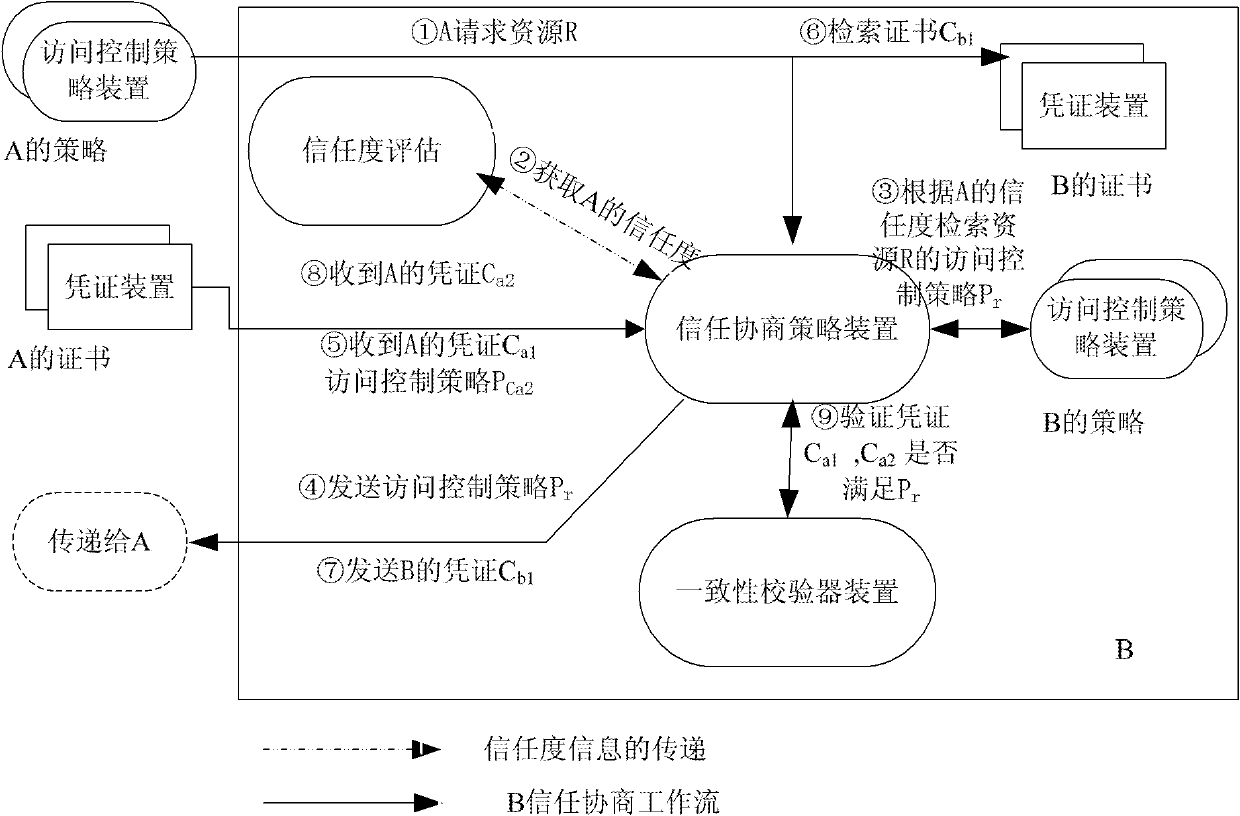
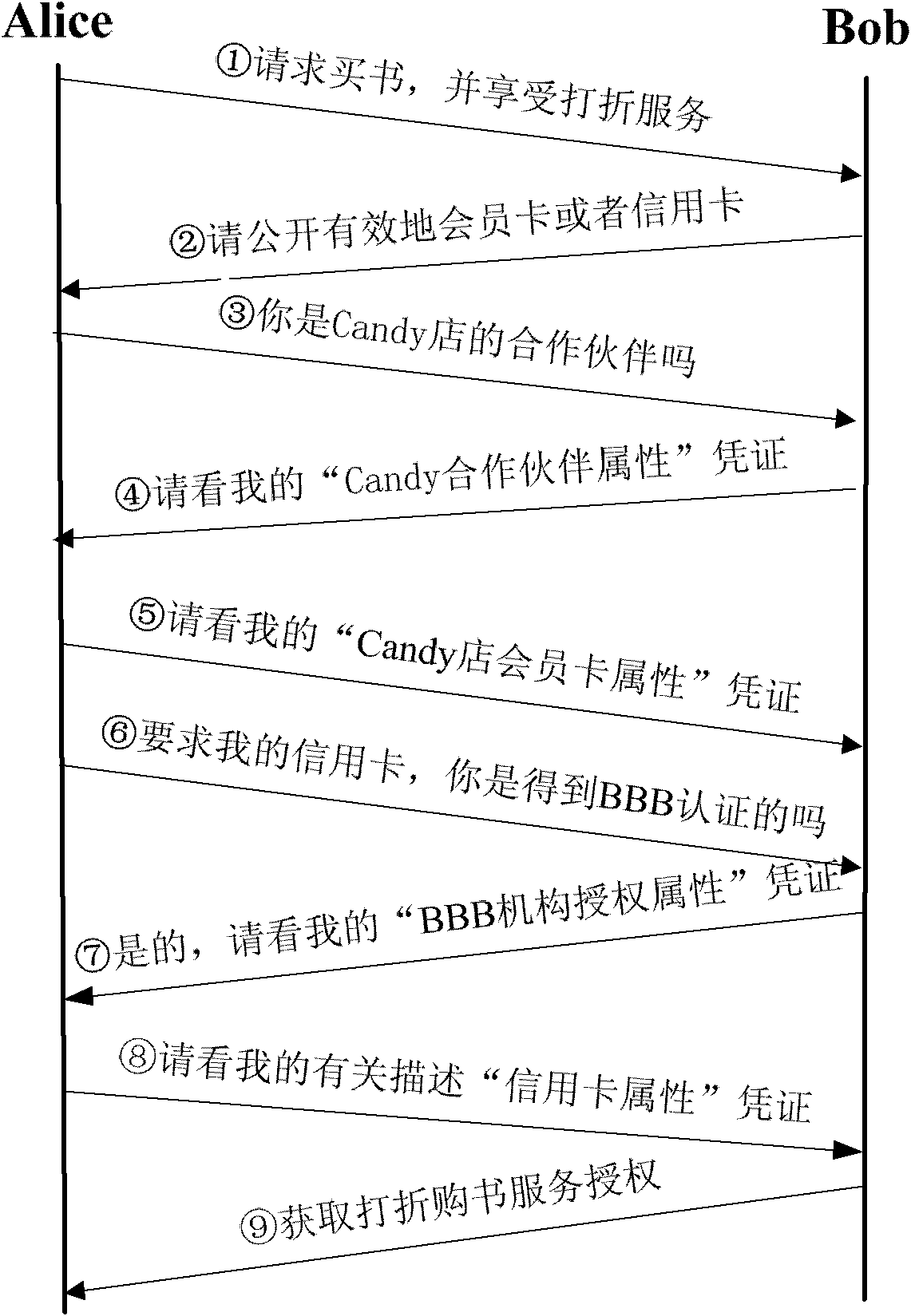
ActiveCN101951375ABalance safety and efficiencyTaking into account efficiencyData switching networksInternet privacyEngineering
The invention discloses a trust assessment-based adaptive trust negotiation system and a trust assessment-based adaptive trust negotiation method. The system comprises a plurality of trust negotiation devices, wherein the trust negotiation devices comprise a requesting party trust negotiation device and a requested party trust negotiation device; the trust negotiation devices also comprise a certificate device, an access control strategy device, a trust assessment device, a consistency checker device, a trust negotiation strategy device, a negotiation protocol device and a security interaction device; and the trust negotiation strategy device performs trust negotiation control on each device based on the trust level provided by the trust assessment device. Therefore, the invention provides the trust assessment-based adaptive trust negotiation system and the trust assessment-based adaptive trust negotiation method, which can dynamically adjust the access control strategy and the negotiation strategy according to the trust assessment result so as to effectively meet the demands of efficiency and security in the trust negotiation.
Owner:BEIJING INFORMATION SCI & TECH UNIV
Precision matching method for multiple depth image
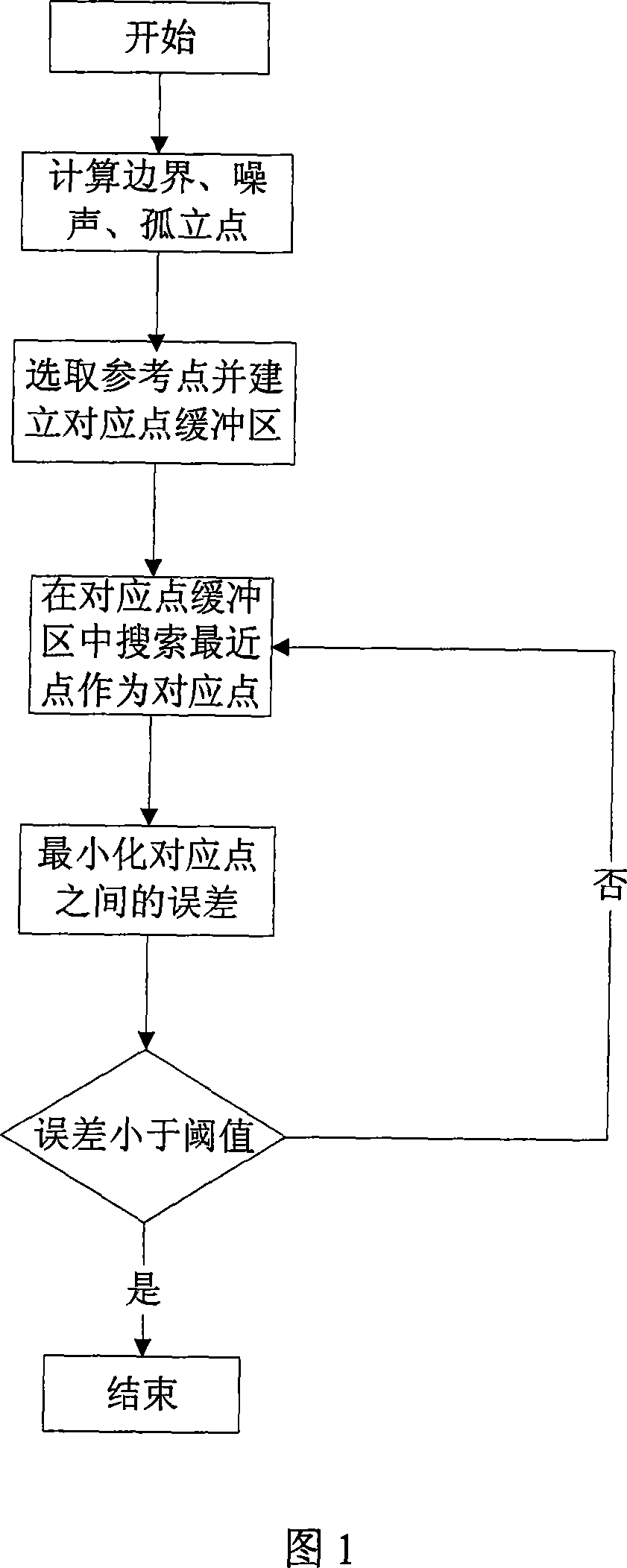
InactiveCN101051386AQuality improvementImprove registration efficiencyImage analysisThresholdingDepth map
The present invention relates to an accurate registration method of multi-frame depth image. Said method includes the following steps: (1), judging boundary point, noise point and isolated point so as to remove point whose noise is large; (2), selecting reference point in overlay area of different depth images, creating correspondent point buffer zone for every reference point so as to search correspondent point in buffer zone; and (3), adopting iteration method to progressively optimize whole registration accuracy. Said invention also provides the concrete steps of said iteration method.
Owner:BEIHANG UNIV
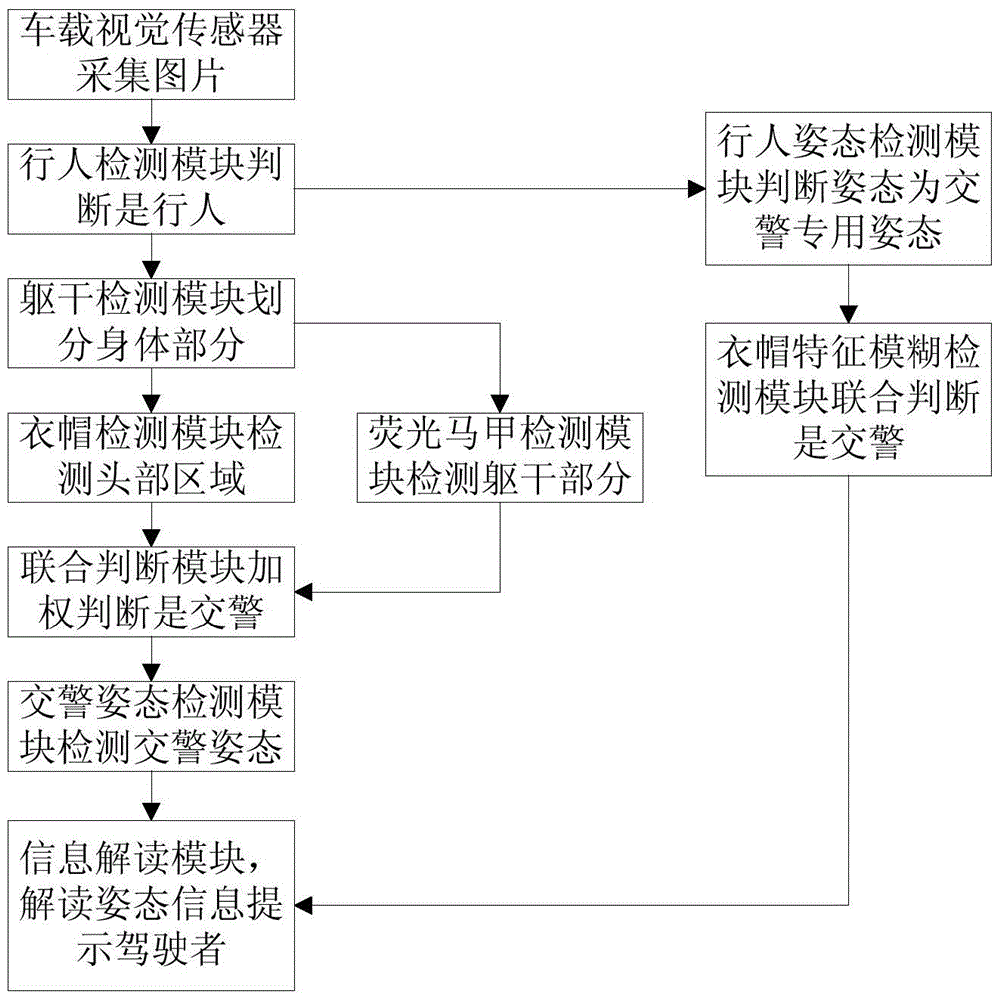
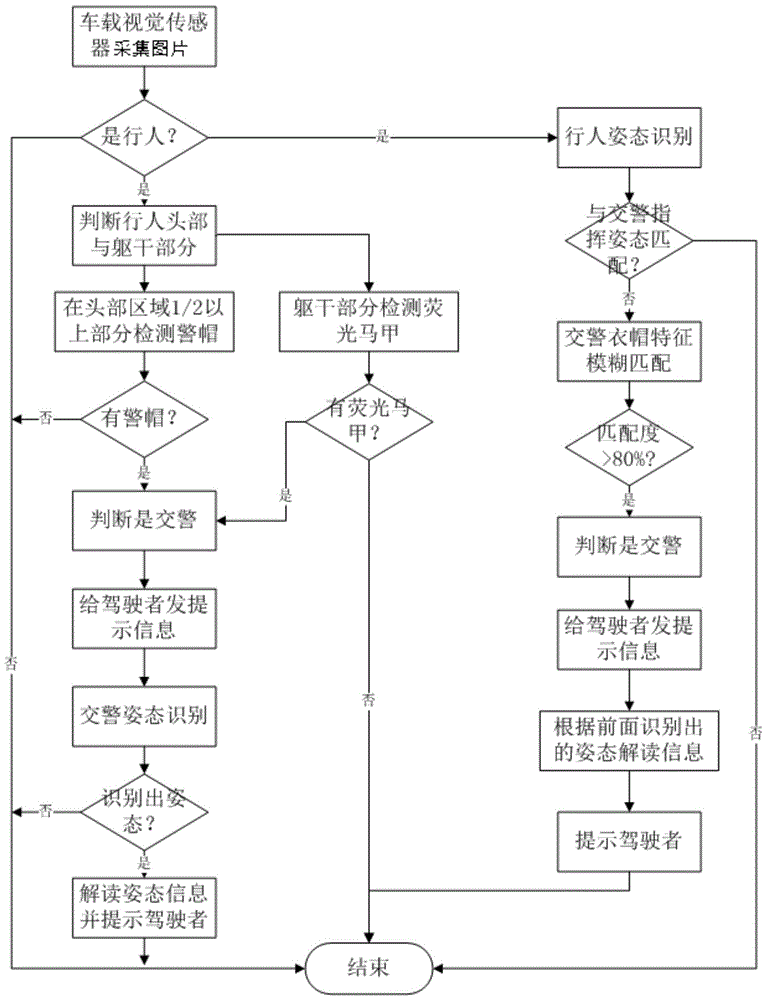
Coat and cap characteristics and attitude detection-based traffic police detection method and system
ActiveCN105740776AImprove accuracyImprove detection efficiencyBiometric pattern recognitionSample imagePedestrian
The invention relates to a coat and cap characteristics and attitude detection-based traffic police detection method and system. The system comprises an offline training construct classifier, an online real-time detection traffic police and an attitude thereof, wherein an offline part extracts a pedestrian hog characteristic, a cap hog characteristic, a fluorescent clothes hog characteristic, a construct pedestrian classifier, a cap classifier and a fluorescent clothes classifier through a lot of collected sample images respectively; and an online part collects an original image in real time and judges whether a pedestrian, namely the traffic police who wears the cap and fluorescent clothes at the same exists in the original image or not by the pedestrian classifier, the cap classifier, the fluorescent clothes classifier and various combinations, then judges the attitude of the traffic police, and prompts a driver to help the driver correctly understand the attitude of the traffic police. The detection method is broadly divided into two processes of accurate matching and fuzzy matching; the two processes can be corroborated by each other; the traffic police and the attitude thereof can be accurately and quickly detected; and the coat and cap characteristics and attitude detection-based traffic police detection method and system have important guiding significance in active driving.
Owner:DALIAN ROILAND SCI & TECH CO LTD
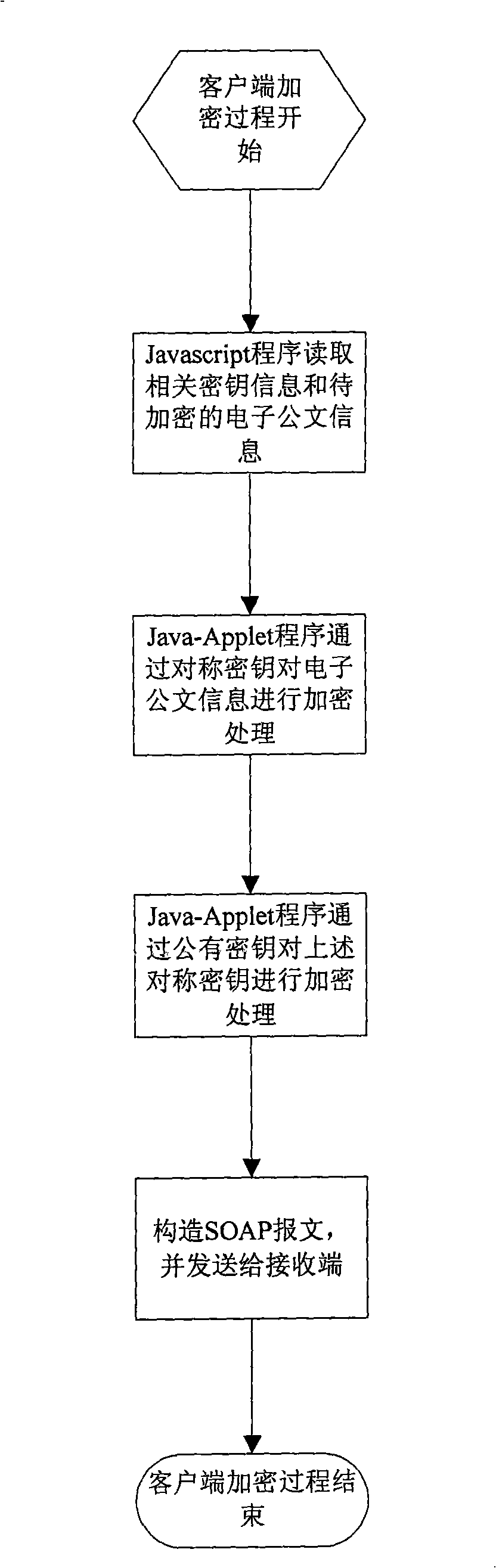
Electronic official document safety transmission method based on Web service
InactiveCN101321057AEnsure safety featuresSolve security issues such as confidentialityPublic key for secure communicationUser identity/authority verificationWeb serviceSOAP
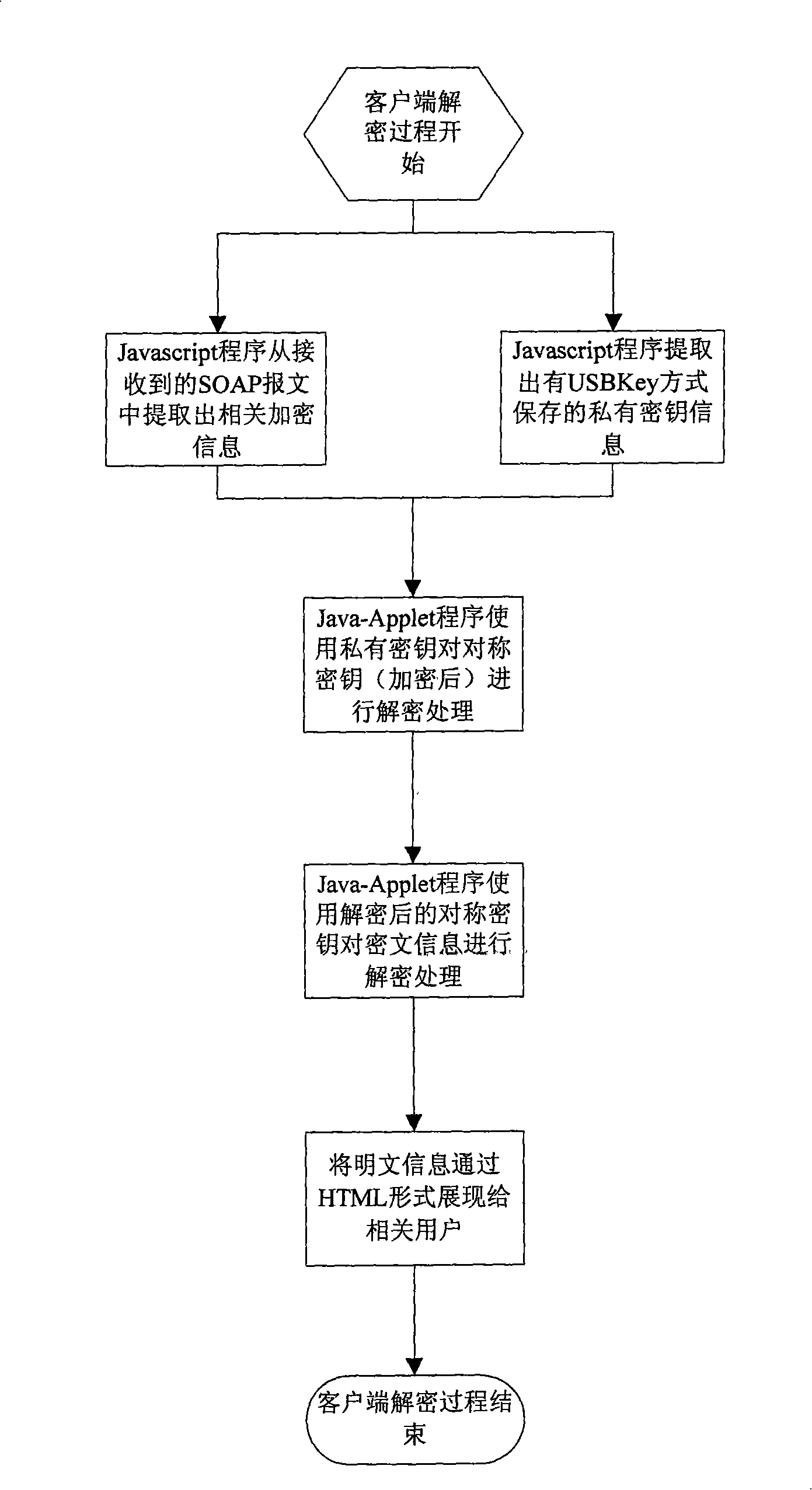
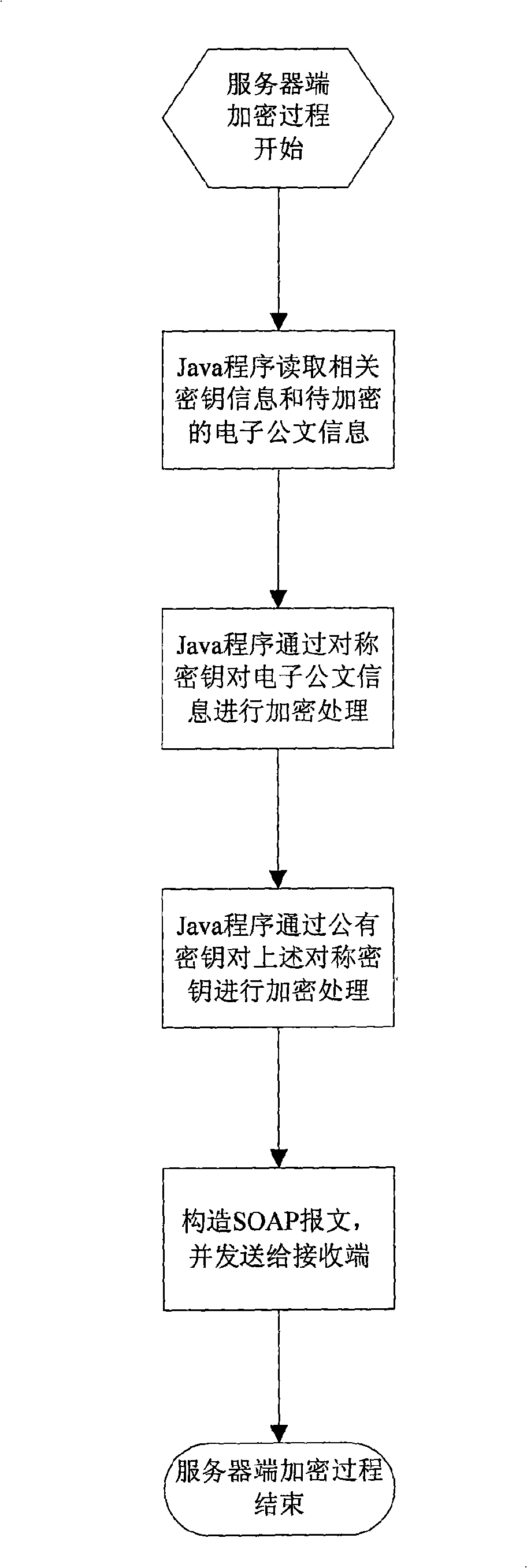
An electronic document secure transmission method based on the Web service is disclosed, comprising: encrypting by the client-end and reading the electronic document information and the related cipher key by the Javascript, performing the encryption by the Java-Applet program; finally constructing the SOAP information, transmitting to the receiver; decrypting the by the client-end, receiving the SOAP information by the Javascript and extracting the electronic document information and the encrypted information, then performing the decrypting process by the Java-Applet program, exhibiting to the user through the HTML form. The encryption of the server end is the same to that of the client-end, with the difference in that, the JAVA program is used in the encrypting process on the electronic document information, rather than the Java-Applet program; the server directly uses the Java program on the server to search the private cipher key information, rather than on the USBKey, and in the decrypting process, the server end uses the Java program to perform the decrypting process rather than the Java-Applet program. According to the invention, the transmission safety between the end to end transmission and the multipoint is ensured.
Owner:BEIHANG UNIV
Peripheral target geographic information acquiring and searching method for position service
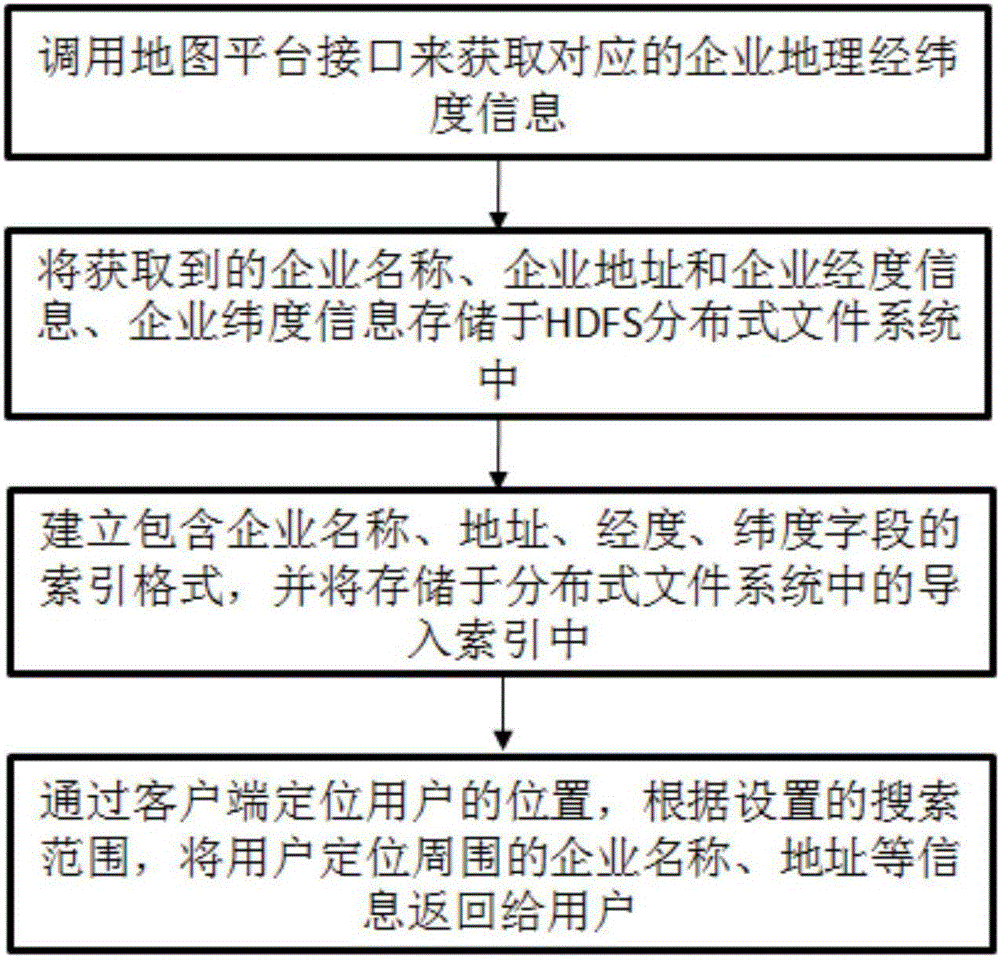
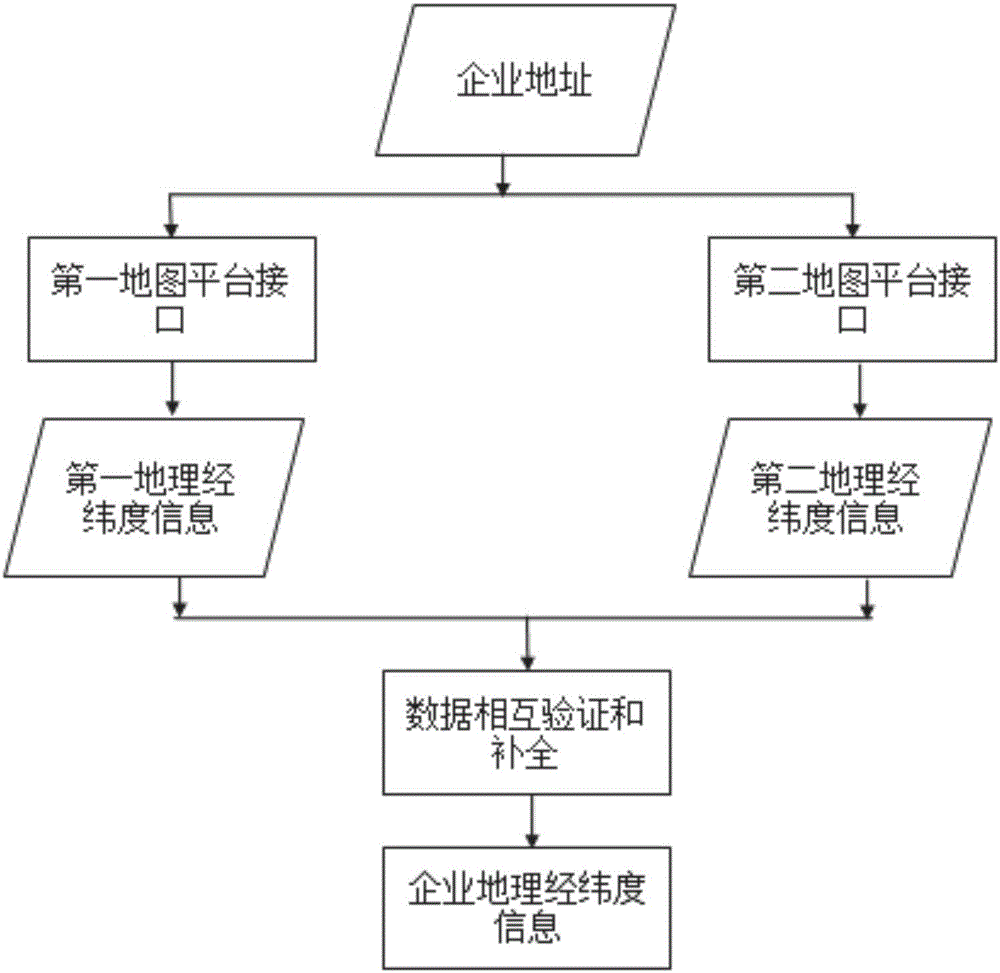
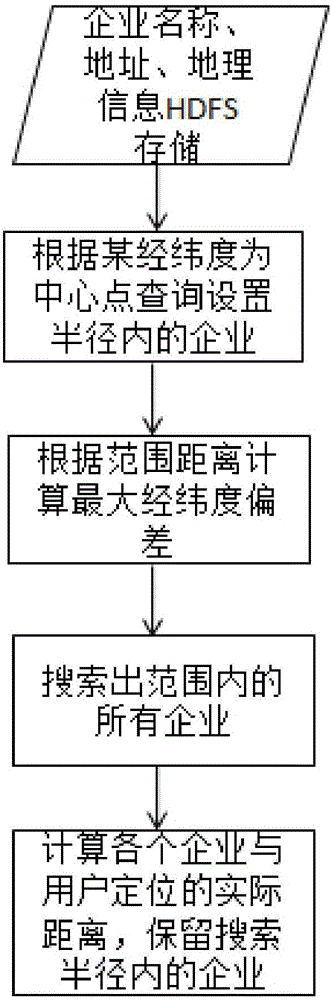
InactiveCN106341471AGuaranteed accuracySmall amount of calculationGeographical information databasesLocation information based serviceInformation processingLongitude
The invention relates to the Internet information processing field and particularly relates to a peripheral target geographic information acquiring and searching method for position service. The location position of a user is positioned through a client, the enterprise information within a set user positioning surrounding scope is returned to the user. According to the method, data analysis, integration and display is carried out for enterprises, based on that the full basic enterprise information is established and the latitude / longitude data is stored, the enterprise information near the user is returned to the user through combining a field search function of a positioning and index system of the user, a problem of insufficient enterprise searching existing in position service in the prior art is solved, and technical support is provided for related business application and analysis, moreover, when peripheral enterprise searching is carried out, to-be-displayed enterprises are searched in a largest longitude / latitude deviation scope acquired through preselected distance conversion, actual distances between the enterprises and the user are calculated on the basis of the searched enterprises, the enterprises within a search radius is remained, efficiency and accuracy requirements are satisfied in a pre-screening mode.
Owner:成都数联铭品科技有限公司
Full-automatic material piling operation method
ActiveCN107010425AIncrease profitTaking into account efficiencyLoading/unloadingEngineeringOperation safety
The invention discloses a full-automatic material piling operation method. The method comprises the steps that a material piling machine firstly executes material piling operation on the first line in a block, a path from front to back is adopted to pile materials from a first material piling point on the head portion, and when the height of a material pile reaches a set height H, the material piling machine backs up to a second material piling point to repeat the material piling process, till last material piling point operation on the line is finished; the material piling machine moves to the next line to repeat the material piling process, if the line is an odd number line, the path from front to back is adopted to pile the materials, if the line is an even number line, a path from back to front is adopted to pile the materials, till material piling operation on all the N lines of the block is finished; and after operation of the last material piling point in the current block, the tail end of the material piling machine moves to a first material piling point of a next block along a reverse L-shaped path to repeat the material piling operation process in the block, till material piling of all the blocks is finished. The utilization rate of piling filed space is increased through blocking material piling, and through the designed paths in the blocks and among the blocks, operation safety is guaranteed, and efficiency is combined.
Owner:SHANGHAI ZPMC ELECTRIC +1
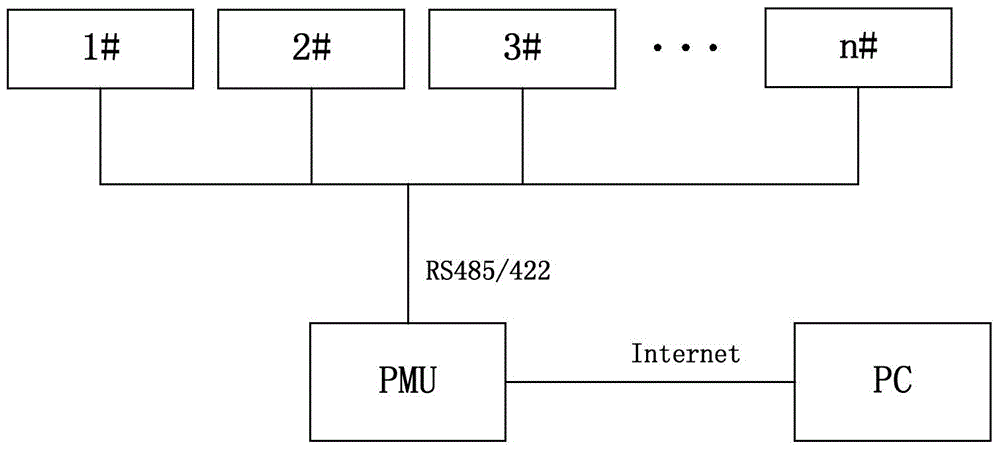
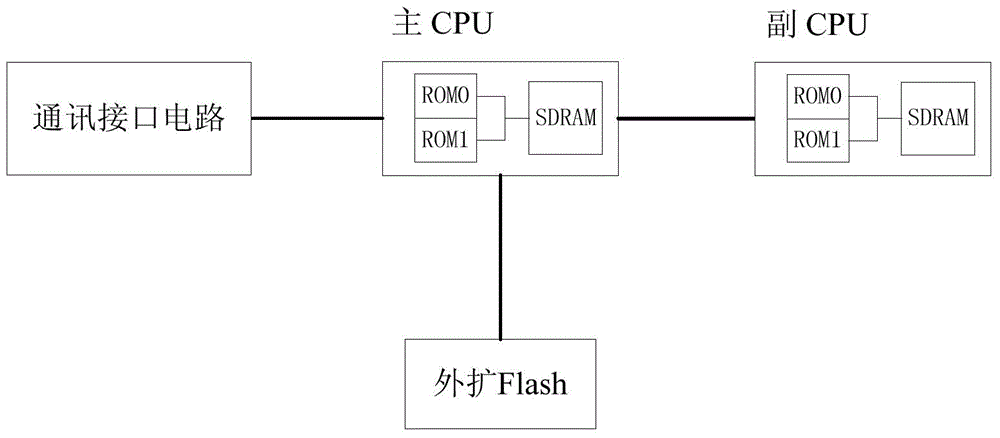
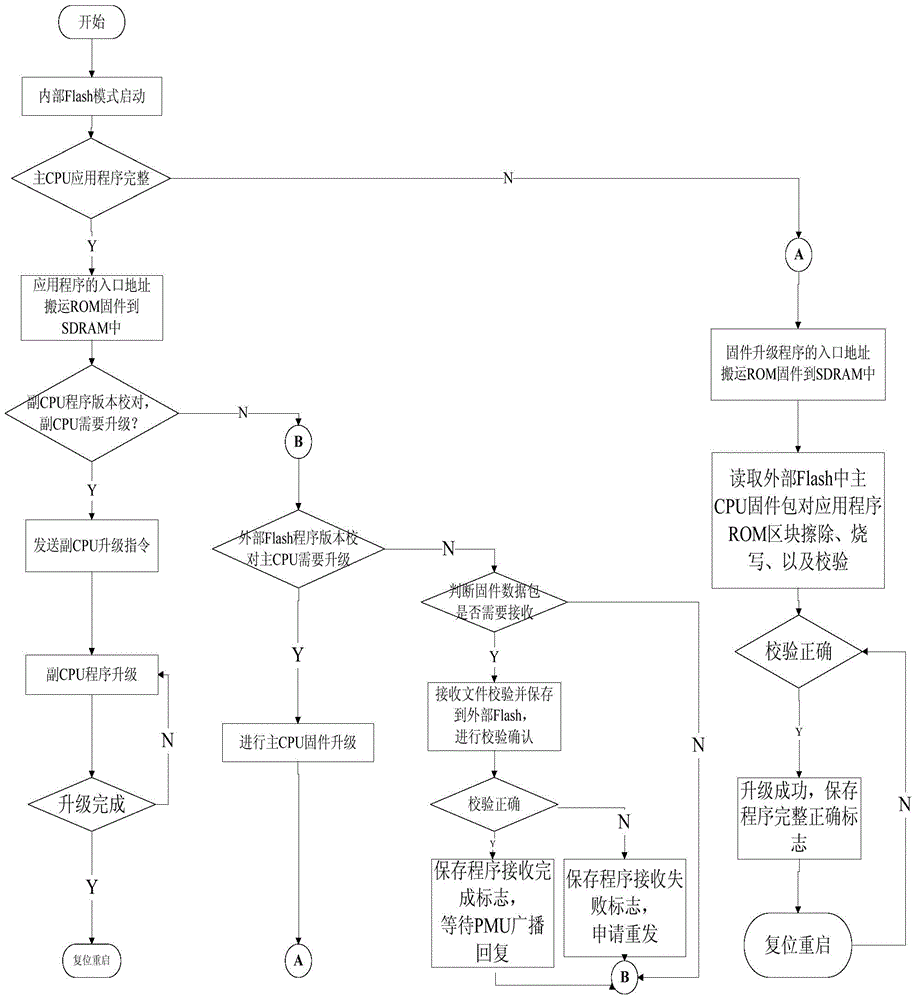
Double-CPU system and program updating method thereof
ActiveCN104102518ASafe and correct storageEnsure correct and reliableProgram loading/initiatingInterface circuitsOperating system
An embodiment of the invention provides a double-CPU system and a program updating method thereof. The method has the advantages that correct and complete transmission and saving of an updating file can be guaranteed, and synchronous updating of multiple computers can be achieved; by using communication between a main CPU and an auxiliary CPU, a program updating function of the main CPU to the auxiliary CPU is achieved, the switching interface circuit of an original design is simplified, and cost is lowered; in consideration of randomness of abnormality in updating, the method can guarantee that self-rebooting can be performed for continuing updating after system updating is interrupted by abnormality, actual reliable updating is achieved, the method is compatible with a field manual updating function, product updating and maintenance are facilitated to the maximum extent, good transportability is achieved, and updating success rate and efficiency are both considered comprehensively, and certain practical and reference value in the field of remote program updating are achieved.
Owner:JIANGSU EVER SOLAR NEW ENERGY CO LTD
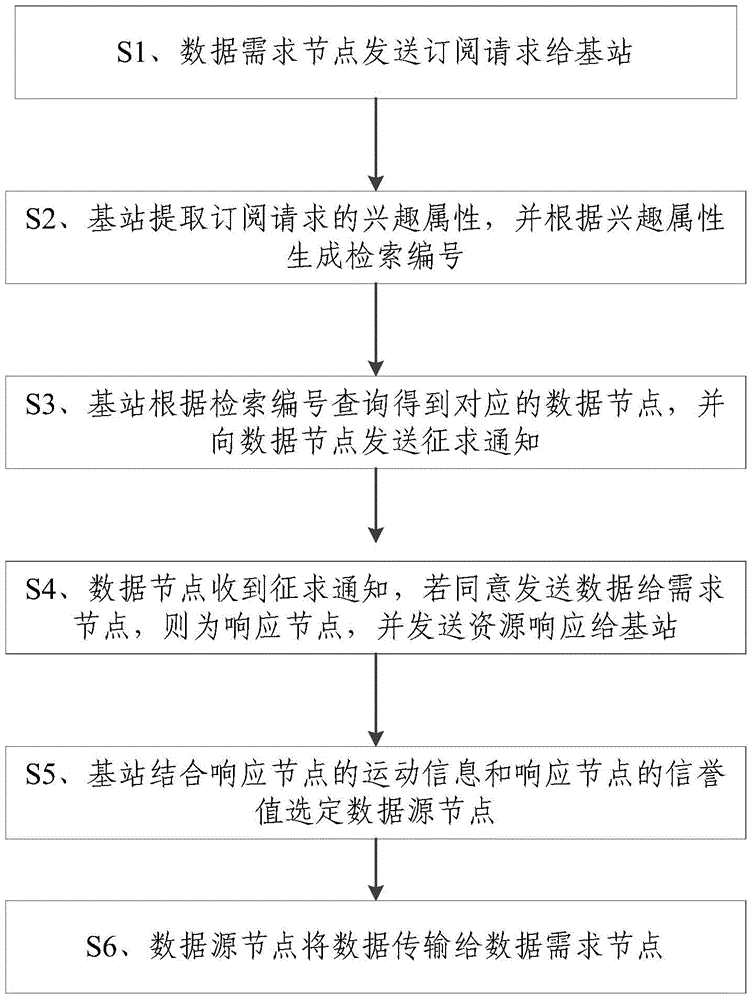
Method for transmitting data in opportunity network
ActiveCN104661275AReduce consumptionIncrease the probability of encountering opportunitiesNetwork topologiesData informationResource consumption
The invention discloses a method for transmitting data in an opportunity network. The method comprises the following steps: adding a base station in the opportunity network to acquire, process and analyze data information, designing a source node recommendation strategy based on geographic positions, motion features and reputation values, dynamically regulating the quantity of resources shared by a data demand node sending a resource request through reputation feedback and updating node reputation values according to the document similarity, so that the decay rate of edge node reputation values is retarded on one hand, and higher matching requirements are provided for a community active node on the other hand. According to the method disclosed by the invention, the resource utilization rate and the transmission efficiency are effectively improved, and the transmission efficiency and the success rate are greatly improved on the premise of reducing the time delay and the resource consumption.
Owner:BEIJING UNIV OF POSTS & TELECOMM
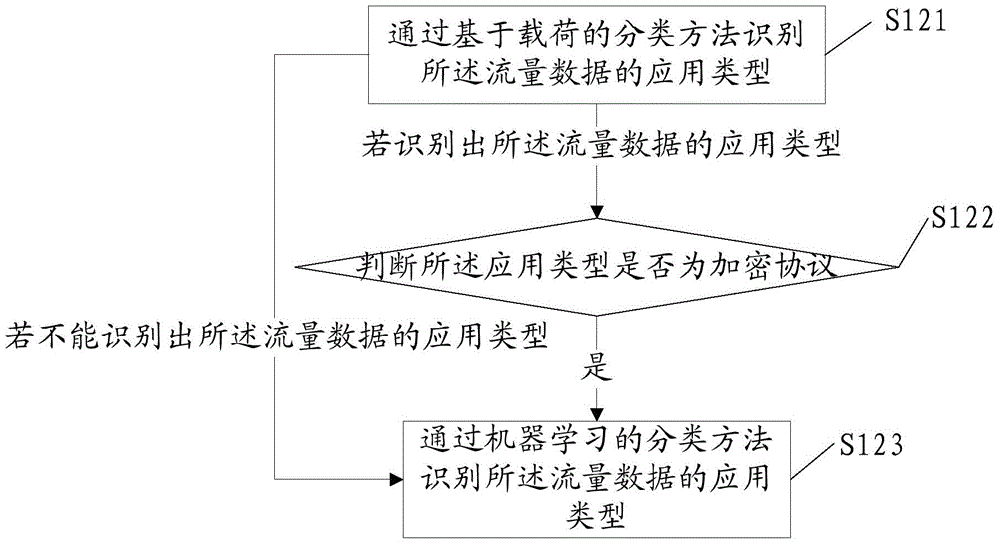
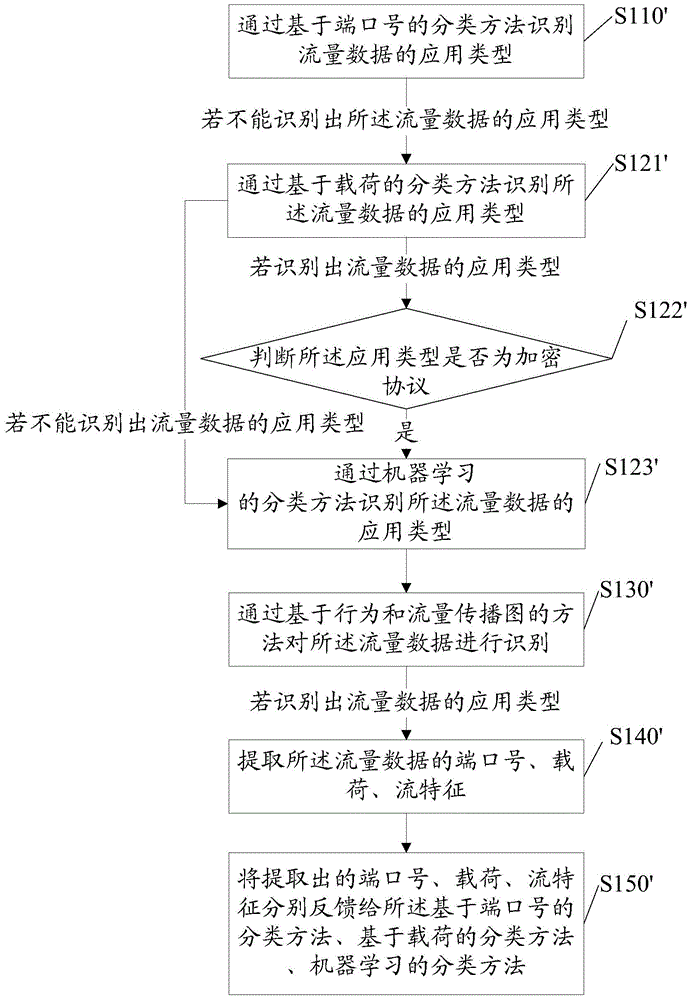
Method and system for recognizing application type of flow data
InactiveCN104468273ATaking into account efficiencyTaking into account the accuracyData switching networksClassification methodsData mining
The invention provides a method and system for recognizing the application type of flow data. The method comprises the steps that a coarse-grained classification method is used for recognizing the application type of the flow data; if the application type of the flow data cannot be recognized, a fine-grained classification method is used for recognizing the application type of the flow data. By the adoption of the method and system for recognizing the application type of the flow data, the application type of the flow data can be recognized with both high efficiency and high precision.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
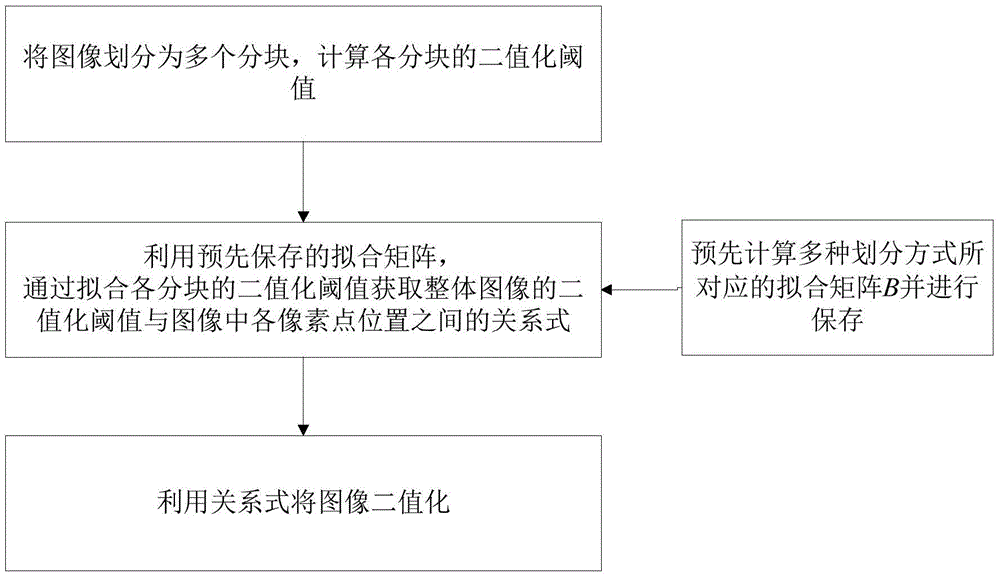
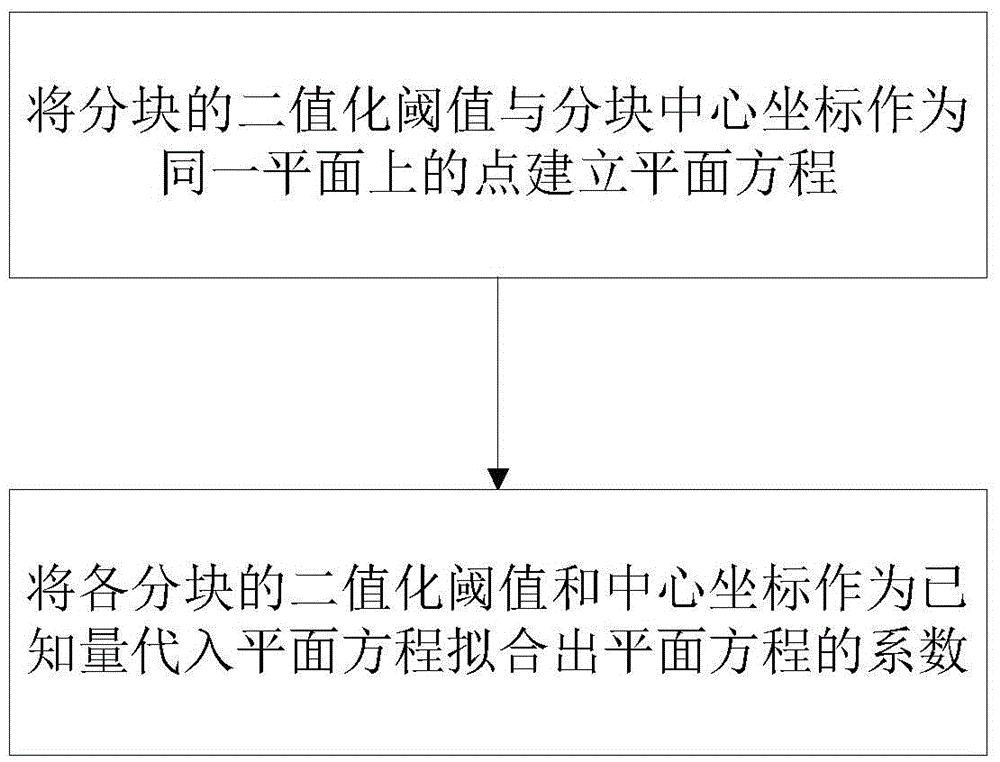
Block plane fitting-based image binaryzation method and device
InactiveCN105608708AGood robustnessBalance efficiency and accuracyImage enhancementImage analysisNon uniform illuminationPattern recognition
The invention discloses a block plane fitting-based image binaryzation method, comprising: dividing an image into many blocks; calculating the binaryzation threshold of each block; obtaining a relation expression about the binaryzation threshold of the whole image and the location of each pixel point in the image by fitting the binaryzation threshold of each block; and conducting image binaryzation by using the relation expression. The invention also discloses a device corresponding to the method. The invention has the prominent advantages that both local and global binaryzation information is considered, good robustness is achieved both for images with uniform illumination and images with non-uniform illumination, the threshold can be accurately obtained even when there are few blocks, and accuracy and efficiency are balanced.
Owner:ZHEJIANG UNIVIEW TECH
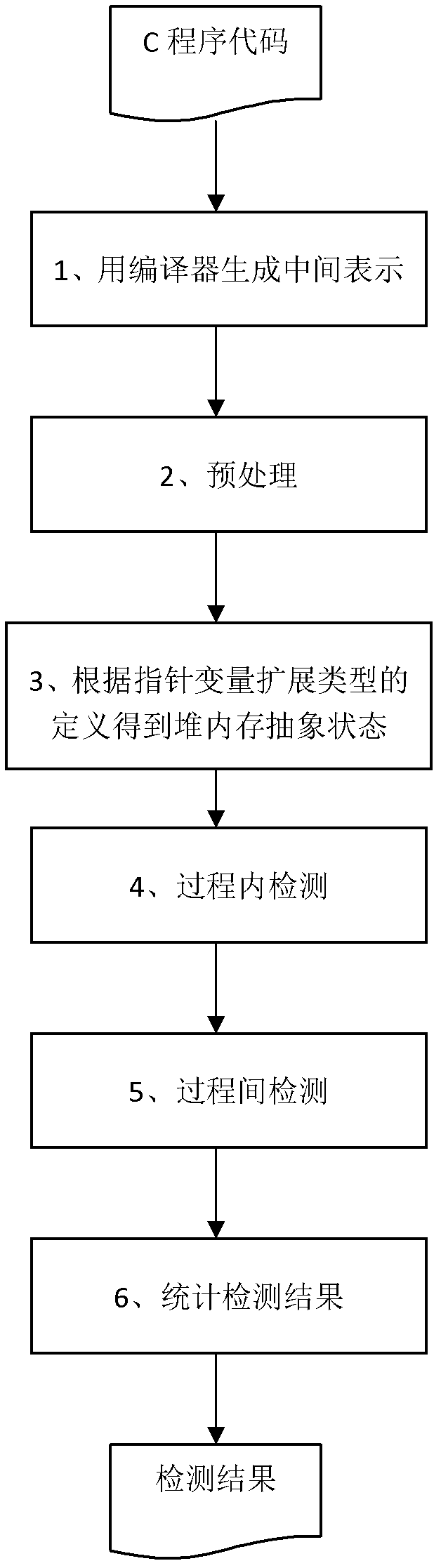
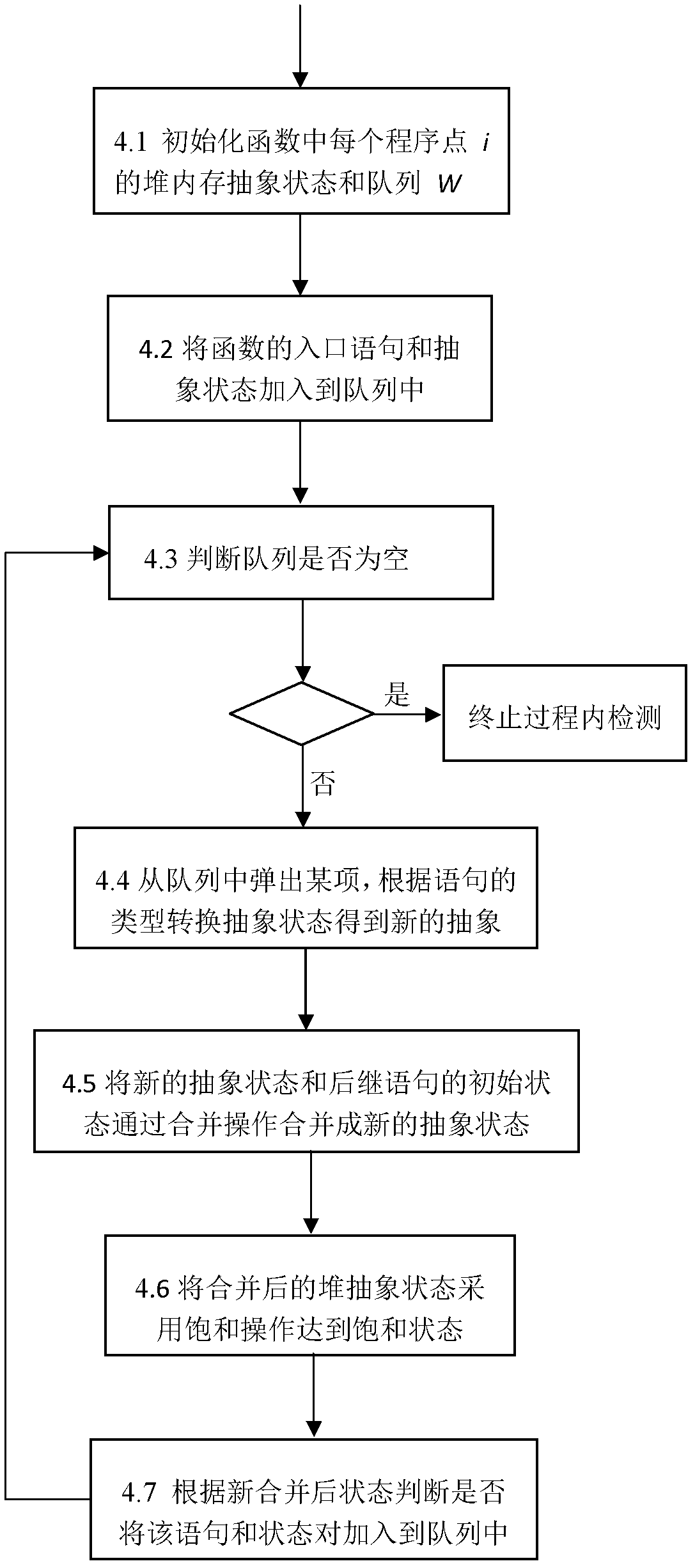
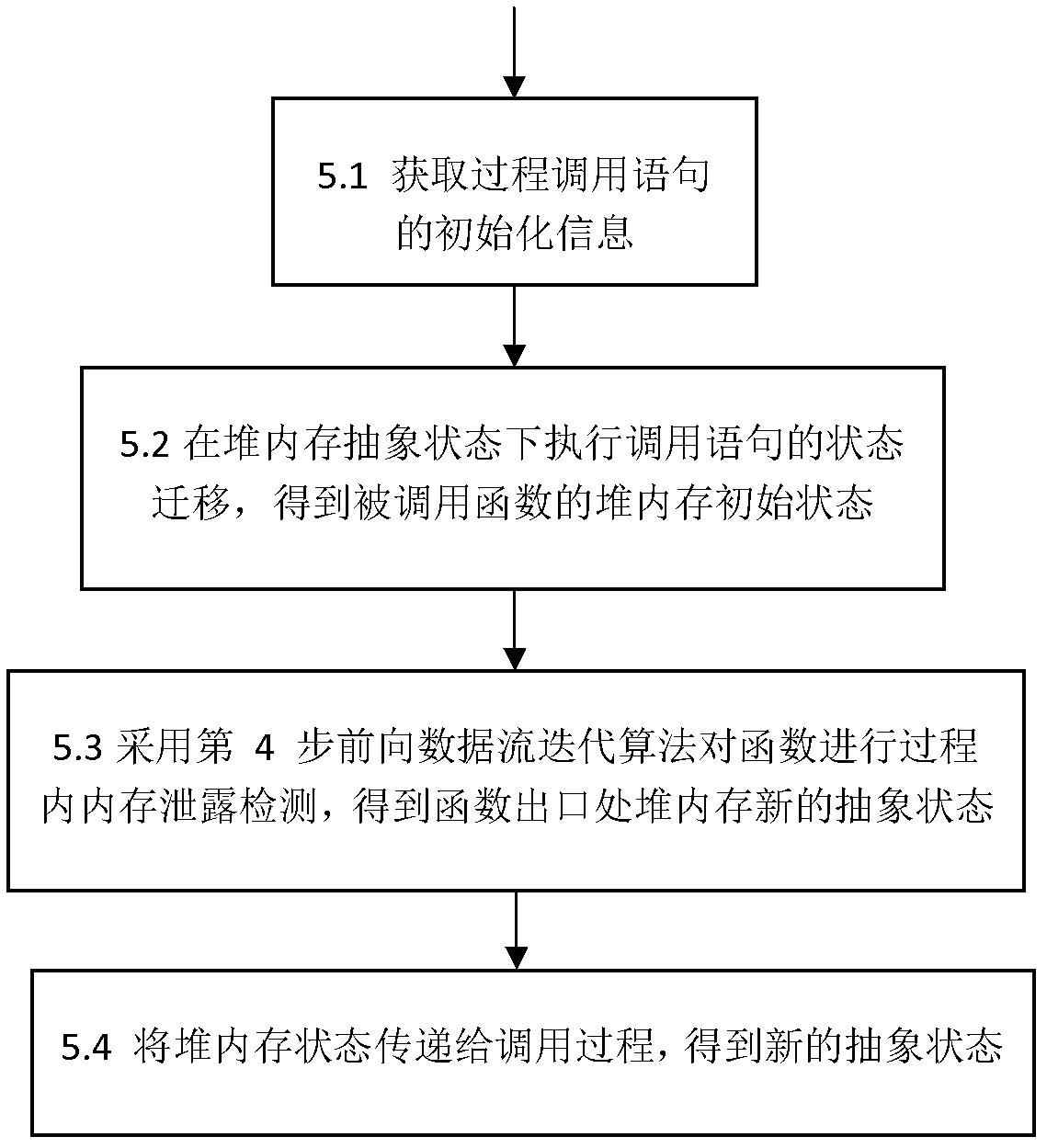
Method for detecting memory leakage of heap operational program
ActiveCN102662825ATaking into account efficiencyImprove balanceSoftware testing/debuggingSource codeMemory leak detection
The present invention discloses a method for detecting the memory leakage of a heap operational program, is directed to solving a technical problem of the memory error detection of the heap operational program in terms of precision and efficiency, and provides a novel memory leakage detection method with improved precision and efficiency of the detection. The technical scheme comprises analyzing a source code of the program in terms of statement and morphology at first and generating an intermediate file; carrying out a pretreatment which includes slicing and transformation; obtaining an abstract state of a heap memory based on the definition of an extension type of a pointer variable in the program; employing a forward data flow iteration method to implement an in-process detection and an inter-process detection; and finally inspecting and counting results of the memory leakage detection. The method finds a good equilibrium point between precision and efficiency of a static analysis, accelerates the termination of an iterative algorithm, improves the precision and the efficiency of the detection, and has a strong scalability and a low storage overhead.
Owner:NAT UNIV OF DEFENSE TECH
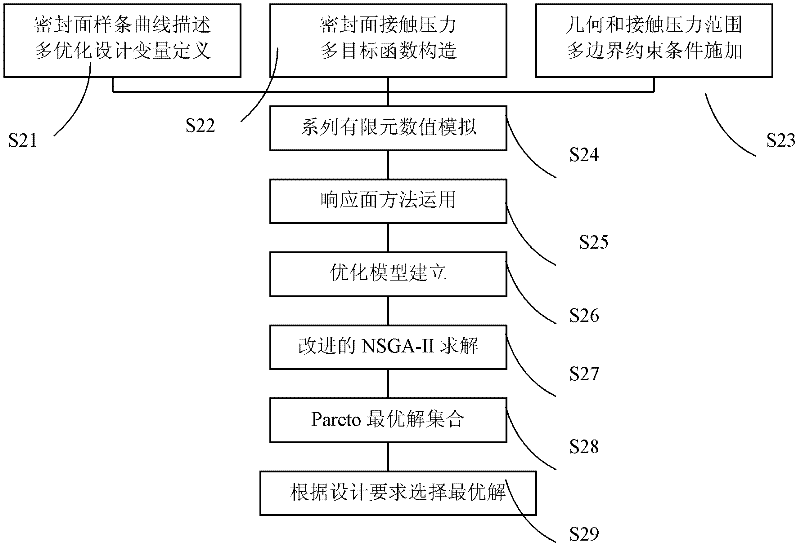
Optimization design method for non-API (American petroleum institute) thread sealing face
ActiveCN102609566ATaking into account the accuracyTaking into account efficiencySpecial data processing applicationsGenetic algorithmEngineering
The invention relates to an optimization design method for a non-API (American petroleum institute) thread sealing face. The method includes: constructing an optimization objective function according to the sealing quantity requirement of a plurality of limited condition loading points; describing the shape of the sealing face of an internal thread and an external thread with non-uniform B-spline curves; using control vertex coordinates of characteristic polygon of the non-uniform B-spline curves as variables of the optimization design; determining constraint conditions of the variables of the optimization design according to diameter parameter range requirements of oil bushing sealing face and upper limit requirements of contact interference of the sealing face; using numerical simulation of finite element to build the objective function of sealing of the sealing face and connection among different shape design variables of the sealing face; constructing test data points used for evaluating response function via numerical simulation; constructing an optimization model; using non-dominated sorting genetic algorithm modifier based on robust design method to implement multi-object optimization; and determining Pareto optimal solution collection. By the method, targeted and precise control of sealing integrity of threaded connectors is achieved.
Owner:BC P INC CHINA NAT PETROLEUM CORP +1
Device compatible with three SHA standards and realization method thereof
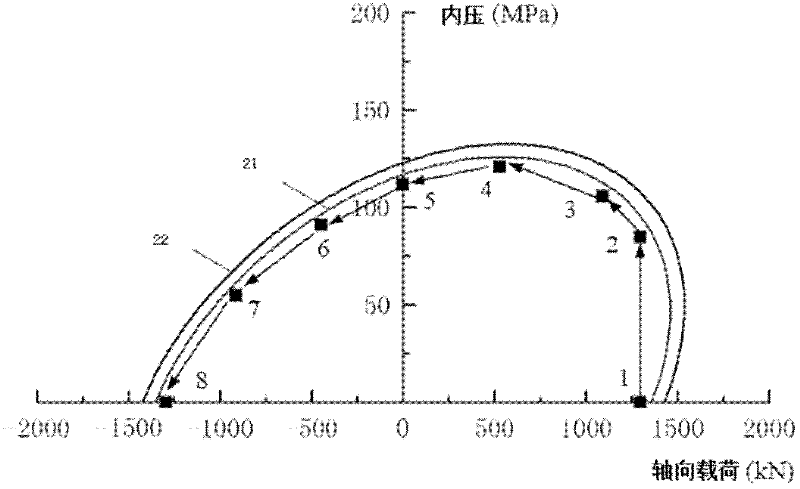
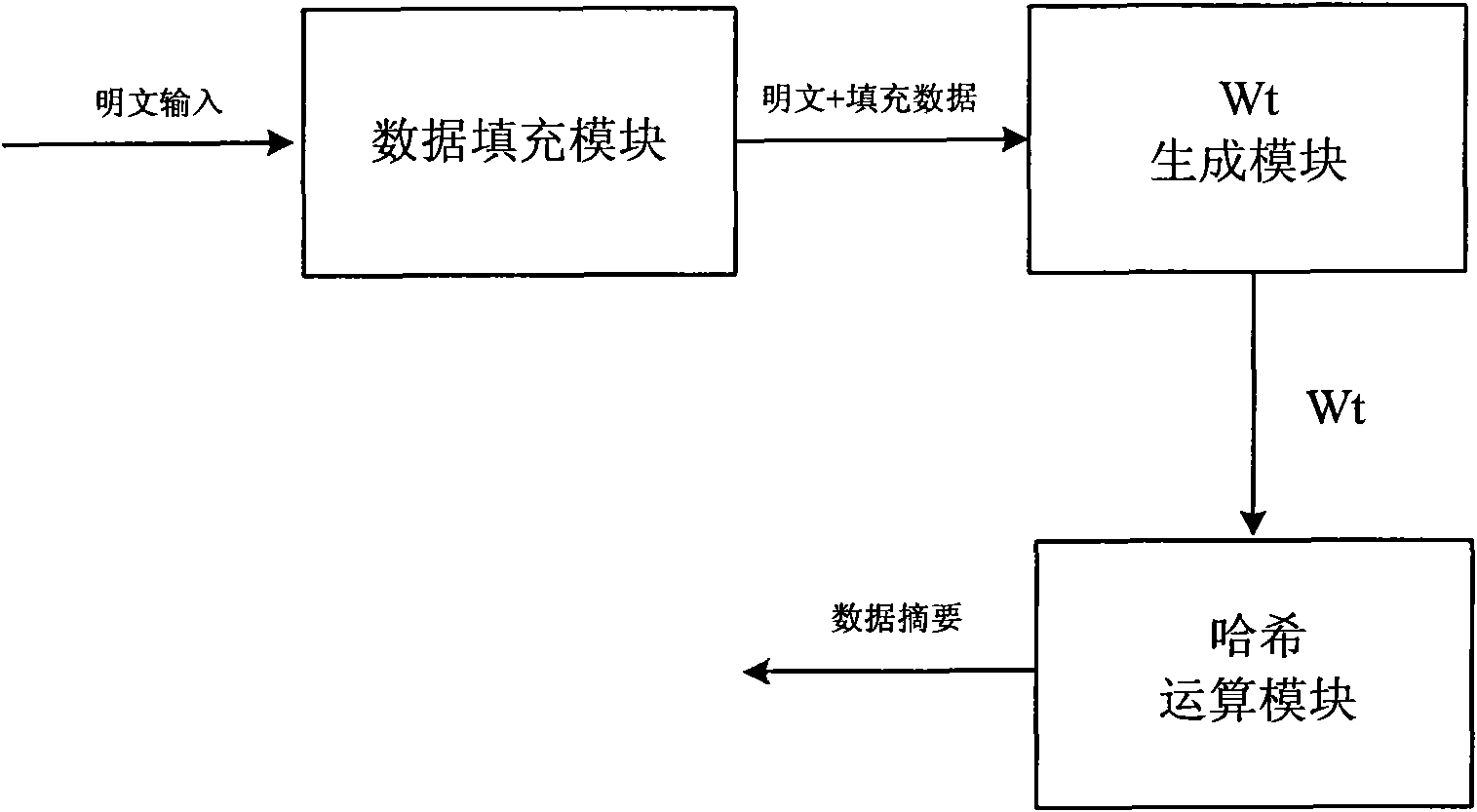
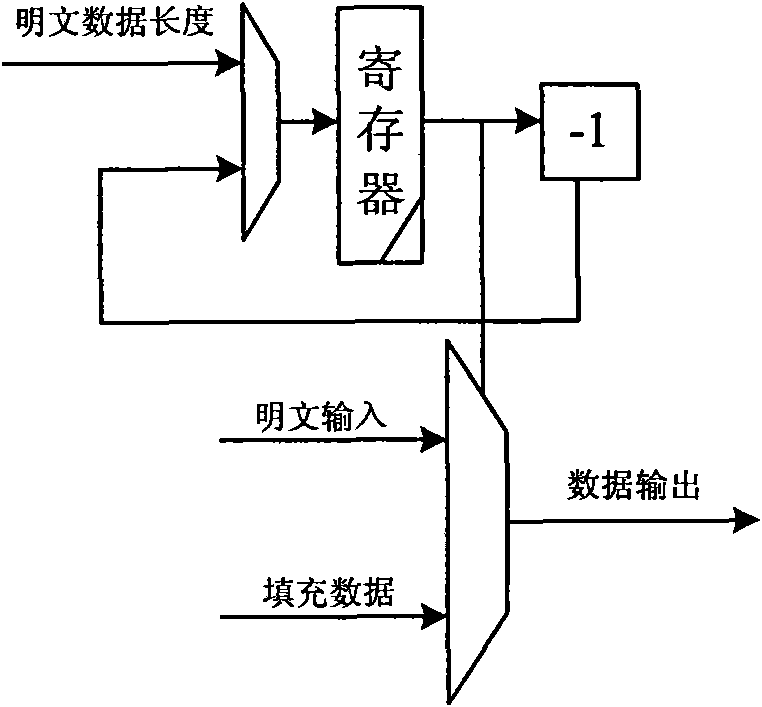
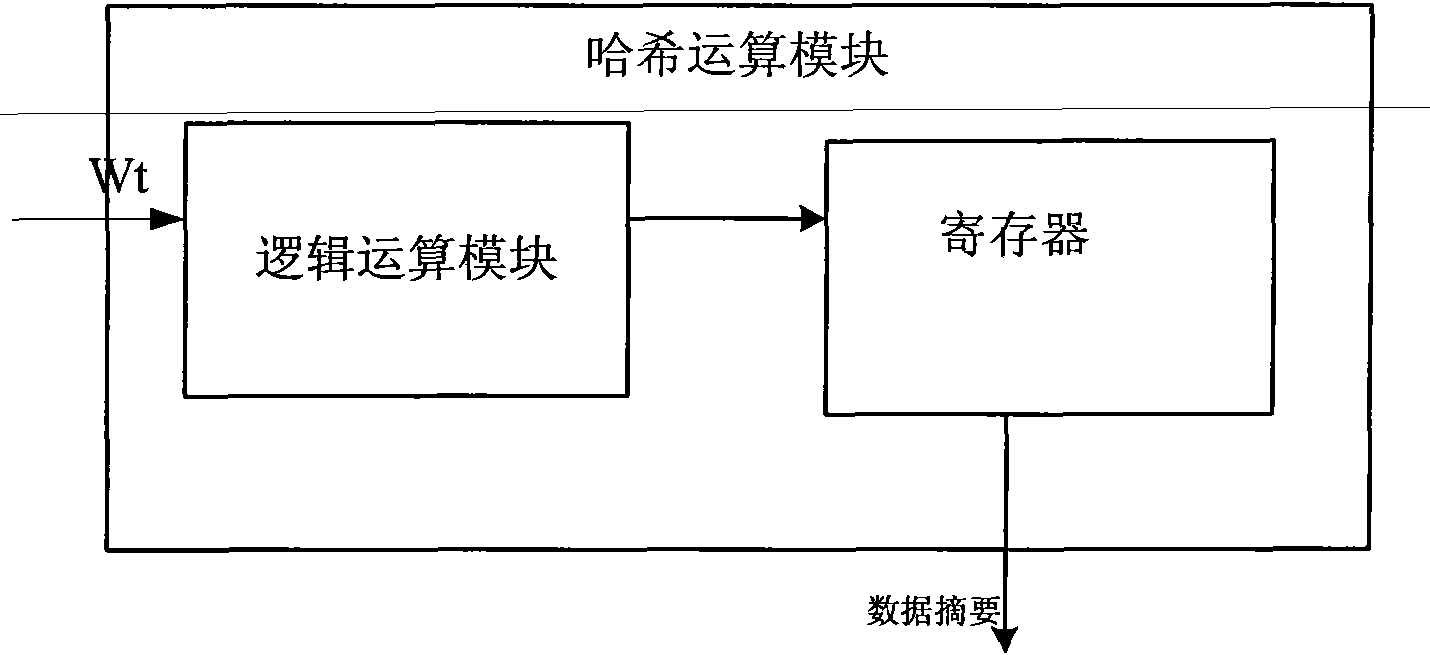
InactiveCN101894229AImprove compatibilityReduce consumptionInternal/peripheral component protectionComputer compatibilityData filling
The invention discloses a device compatible with three SHA standards, which comprises a data filling module, a Wt generation module and an Hash operation module, which are connected in order. The invention also discloses a realization method of the device compatible with three SHA standards, which comprises the following steps: (I) receiving cleartext data by the data filling module to generate filling data and outputting the data to the Wt generation module; (II) generating new Wt operators by the Wt generation module and inputting the new Wt operators into the Hash operation module; and (III) generating a data abstract with 160 bits under an SHA-a mode, generating a data abstract with 256 bits under SHA-256 mode or generating a data abstract with 512 bits under an SHA-512 mode by the Hash operation module. The invention has the advantages of common practicality, good compatibility, low power consumption, less occupation of extra resources and the like.
Owner:SOUTH CHINA UNIV OF TECH
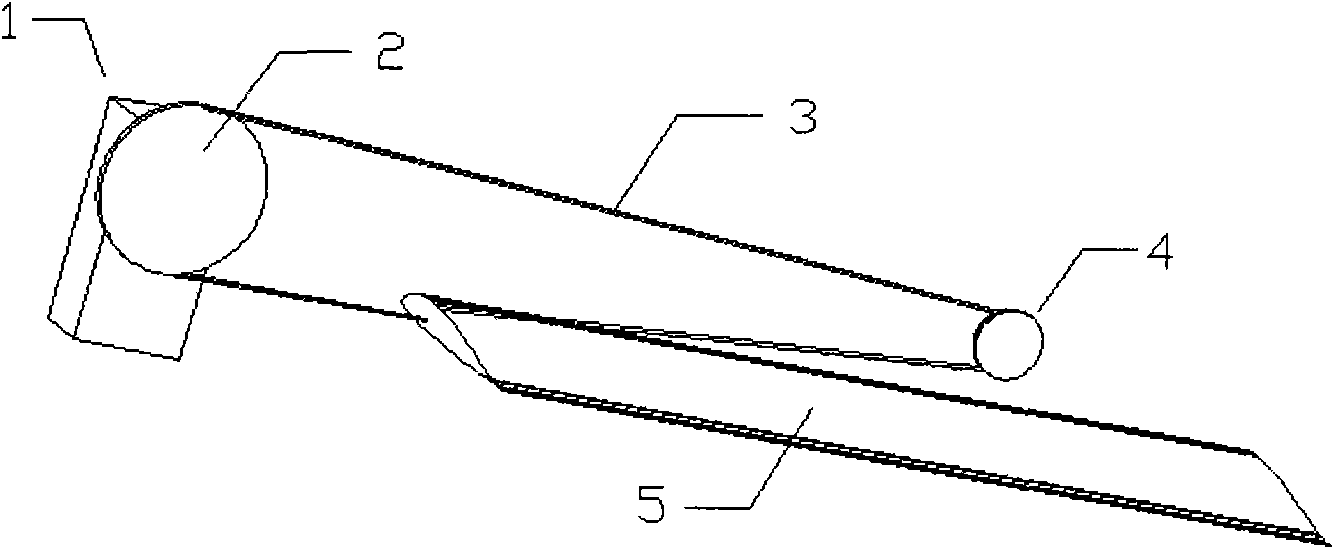
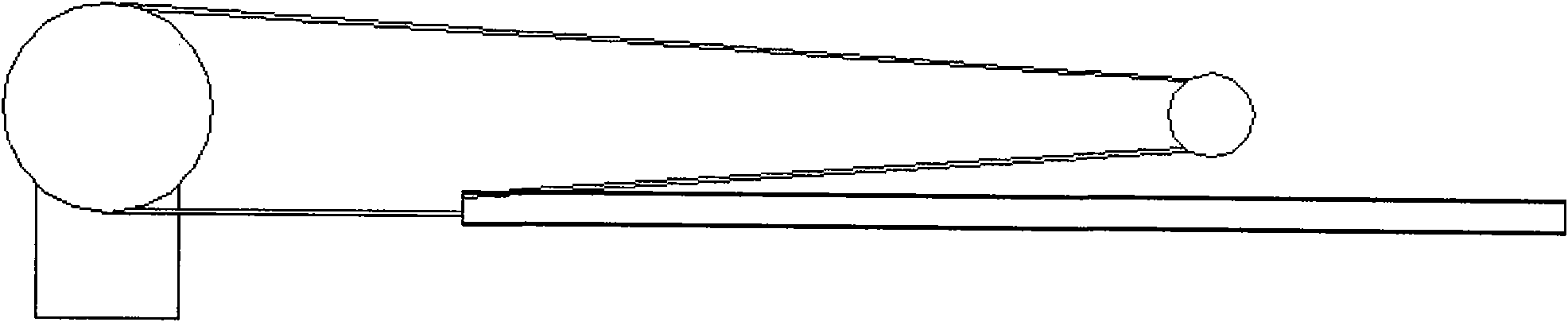
Transmission mechanism of telescopic morphing wing
The invention discloses a transmission mechanism of telescopic morphing wing, which comprises a speed reducing motor, a steel cable, a winch and a pulley and is characterized in that: the speed reducing motor drives the winch to unwind and wind the steel cable wound on the winch; a telescopic section of the wing, the steel cable, the winch and the pulley are embedded in a main wing; the pulley is positioned at the tail end of a girder under a wing face skin on the wing tip of the main wing; and steel cable controls the telescopic change of the telescopic section of the wing in real time through the pulley. The transmission mechanism of the telescopic morphing wing has the advantages of simple structure, light weight, safety, reliability and the like, can relatively better meet the requirements on the structure of an aerocraft, takes efficiency and weight into account and fulfils the aim of the telescopic change of the wing.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
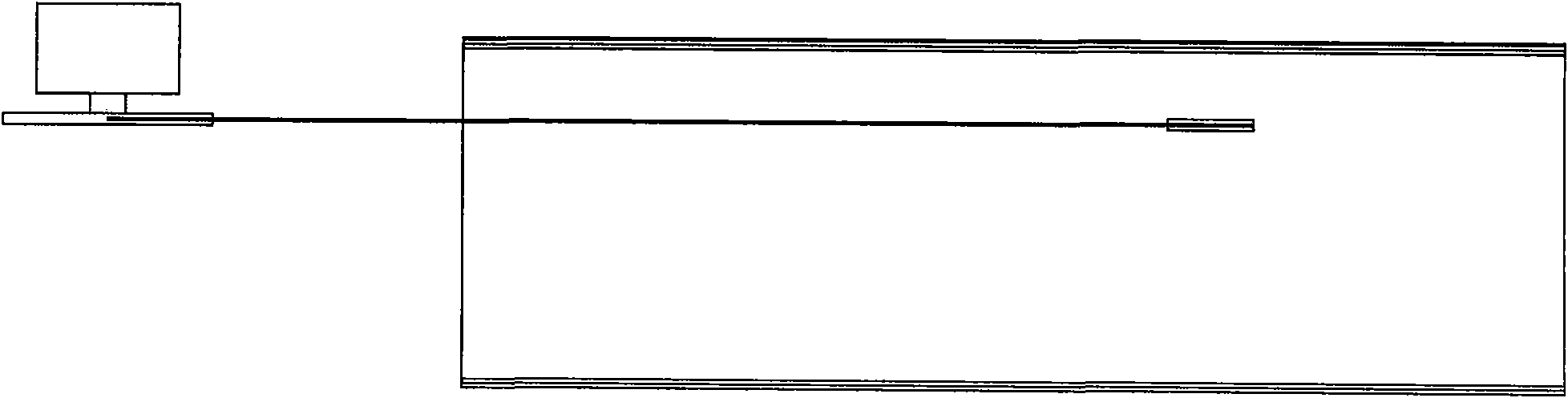
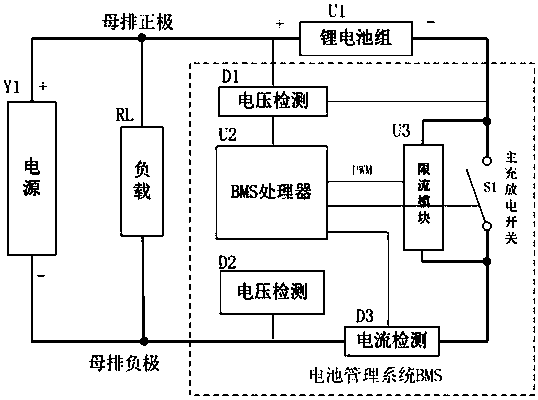
A battery management system and circuit for charging and discharging a battery pack
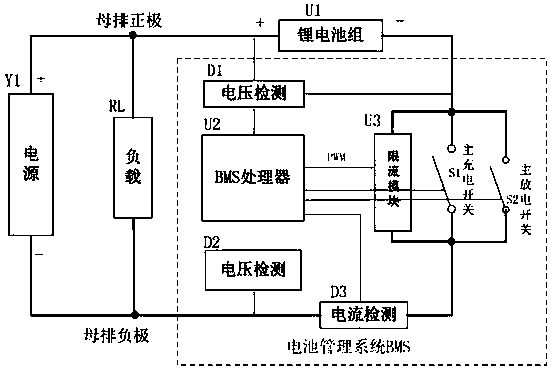
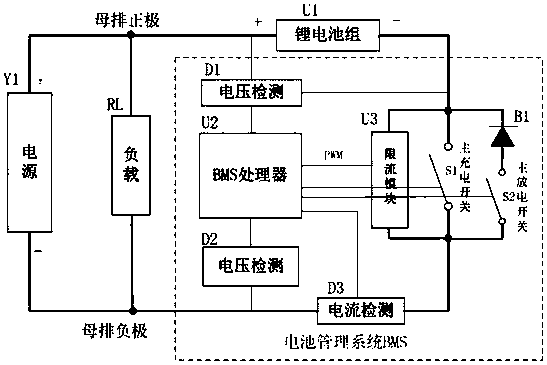
PendingCN109245189AImprove charge and discharge efficiencyBoth safety and efficiencyCircuit monitoring/indicationDifferent batteries chargingElectrical batteryCharge and discharge
The embodiment of the invention discloses a battery management system and a circuit for charging and discharging a battery pack. The circuit may include at least one voltage detection module D, a battery management system BMS processor, a current limiting module U3, a current detection module I, and at least one switch S1. The current limiting module U3 is connected in parallel with the switch S1,and is connected in series with the current detecting module I after being connected in parallel; A voltage detection module D, configured to detect a voltage value of the power supply Y1 and the charging battery pack U1; A current detection module I, configured to detect the current value of the loop in which the current detection module I is located; BMS processor, D for control that voltage detection module, Current limiting module U3, The current detection module I and the switch S1 can solve the problem of low charging and discharging efficiency under the condition that the charging of the rechargeable battery does not exceed the current in the related art, realize the improvement of the charging and discharging efficiency of the rechargeable battery under the condition that the charging of the rechargeable battery does not exceed the current, and achieve the beneficial effect that both the safety and the efficiency of the rechargeable battery are taken into account.
Owner:ZTE CORP
Modular integrated multi-stage and multi-drive chamber partially non-coaxial dry type vacuum single pump
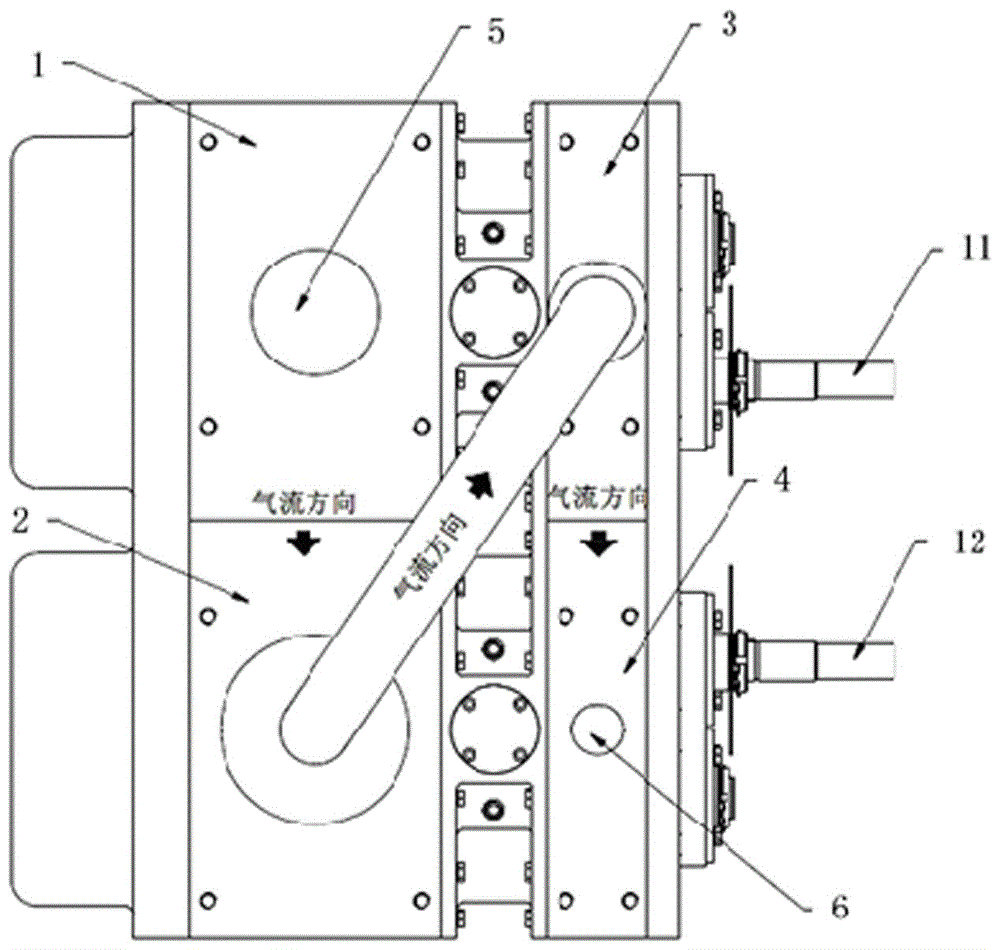
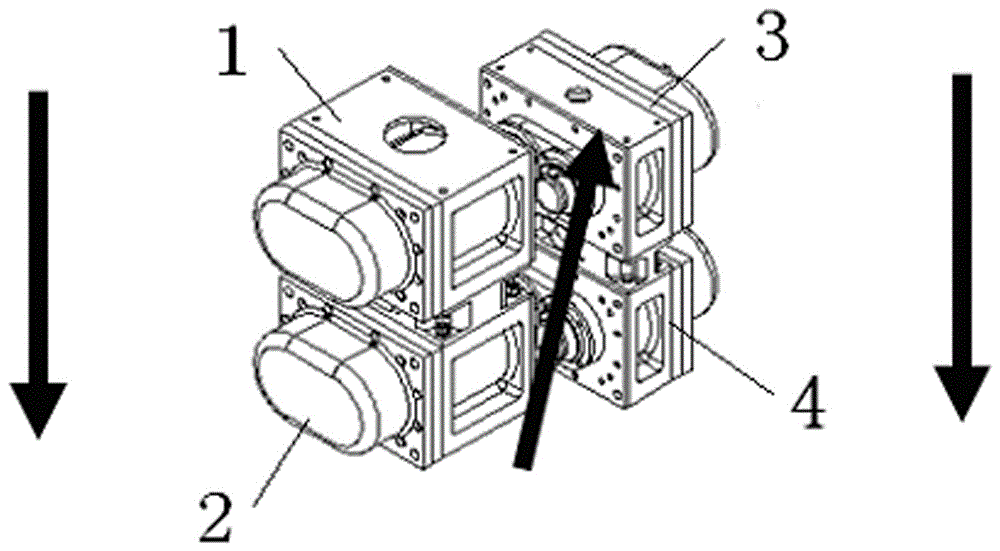
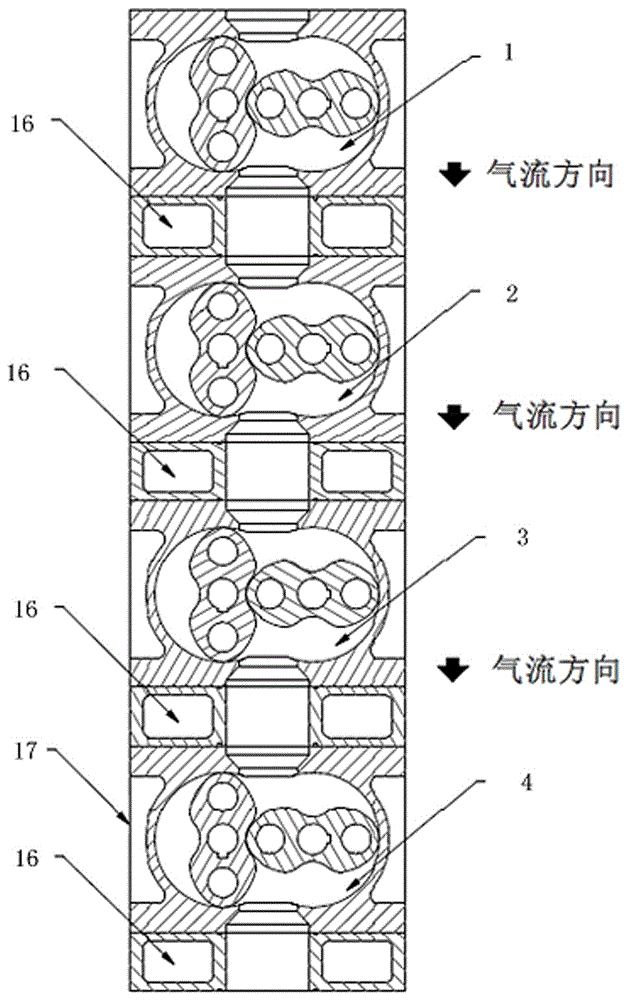
InactiveCN106438365AIncrease mass flowHigh calorific valueRotary/oscillating piston combinations for elastic fluidsRotary piston pumpsDrive shaftAtmospheric air
The present invention discloses a modular integrated multi-stage and multi-drive chamber partially non-coaxial dry type vacuum single pump, which comprises a plurality of modular vacuum drive chambers. The dry type vacuum single pump is characterized in that the plurality of modular vacuum drive chambers are integrated as an overall single pump. The plurality of modular vacuum drive chambers are connected in series to form a multi-stage vacuum single pump. At least two vacuum drive chambers, among the above plurality of modular vacuum drive chambers, are associated in the two non-coaxial manner, wherein the gas mainstream direction is perpendicular to the drive shaft of a rotor. The inlet of a first-stage vacuum chamber is directly introduced to the atmosphere. According to the technical scheme of the invention, the plurality of modular vacuum drive chambers are non-coaxial, so that the compression ratio of each vacuum drive chamber is adjustable. In this way, in the high-vacuum environment, the compression ratio is large. In the rough vacuum environment, the compression ratio is small. Therefore, both the safety and the efficiency are given consideration to, and the optimized control is enabled. The differential pressure sharing and the heat sharing at each stage are more uniform.
Owner:ELIVAC CO LTD +2
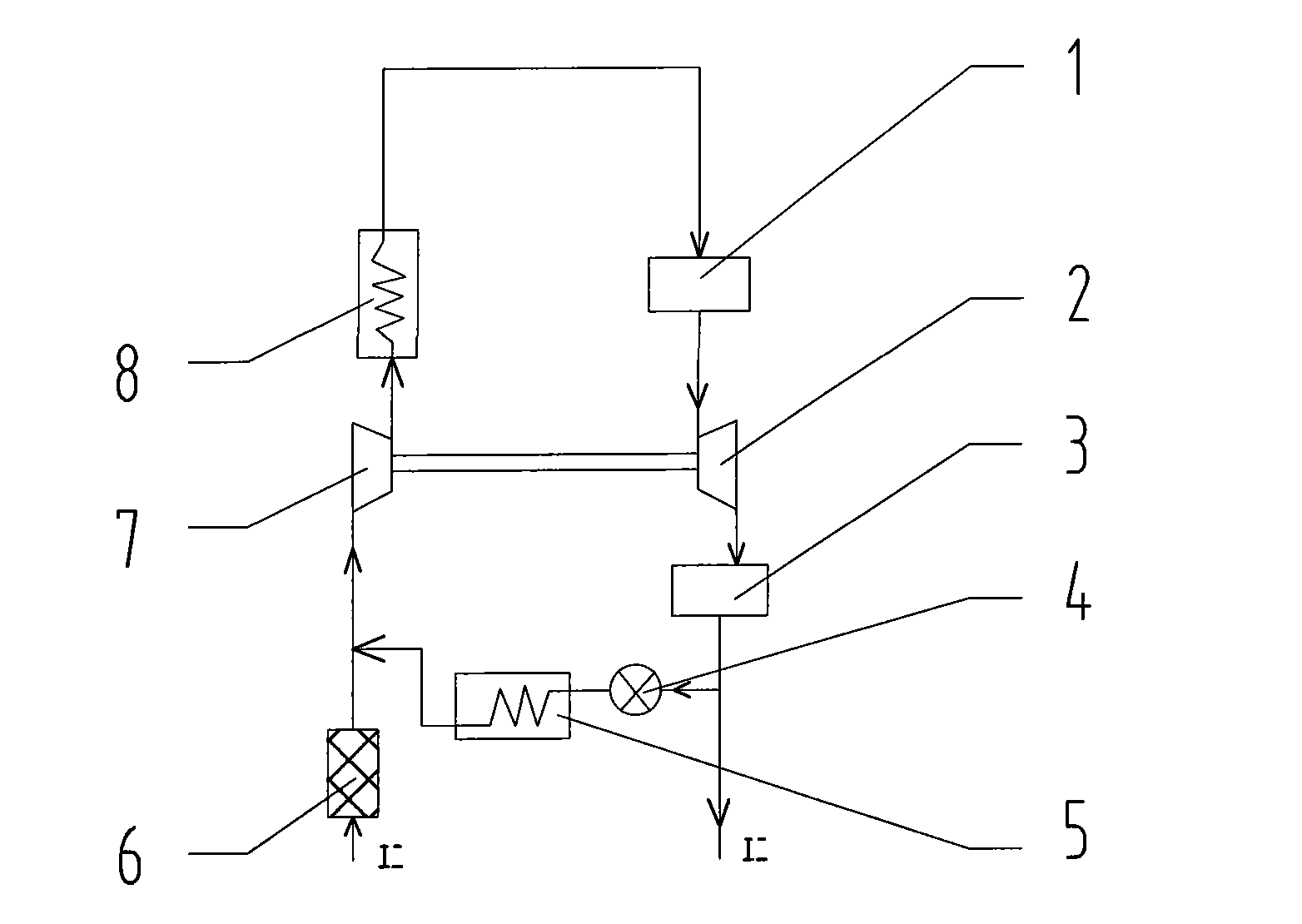
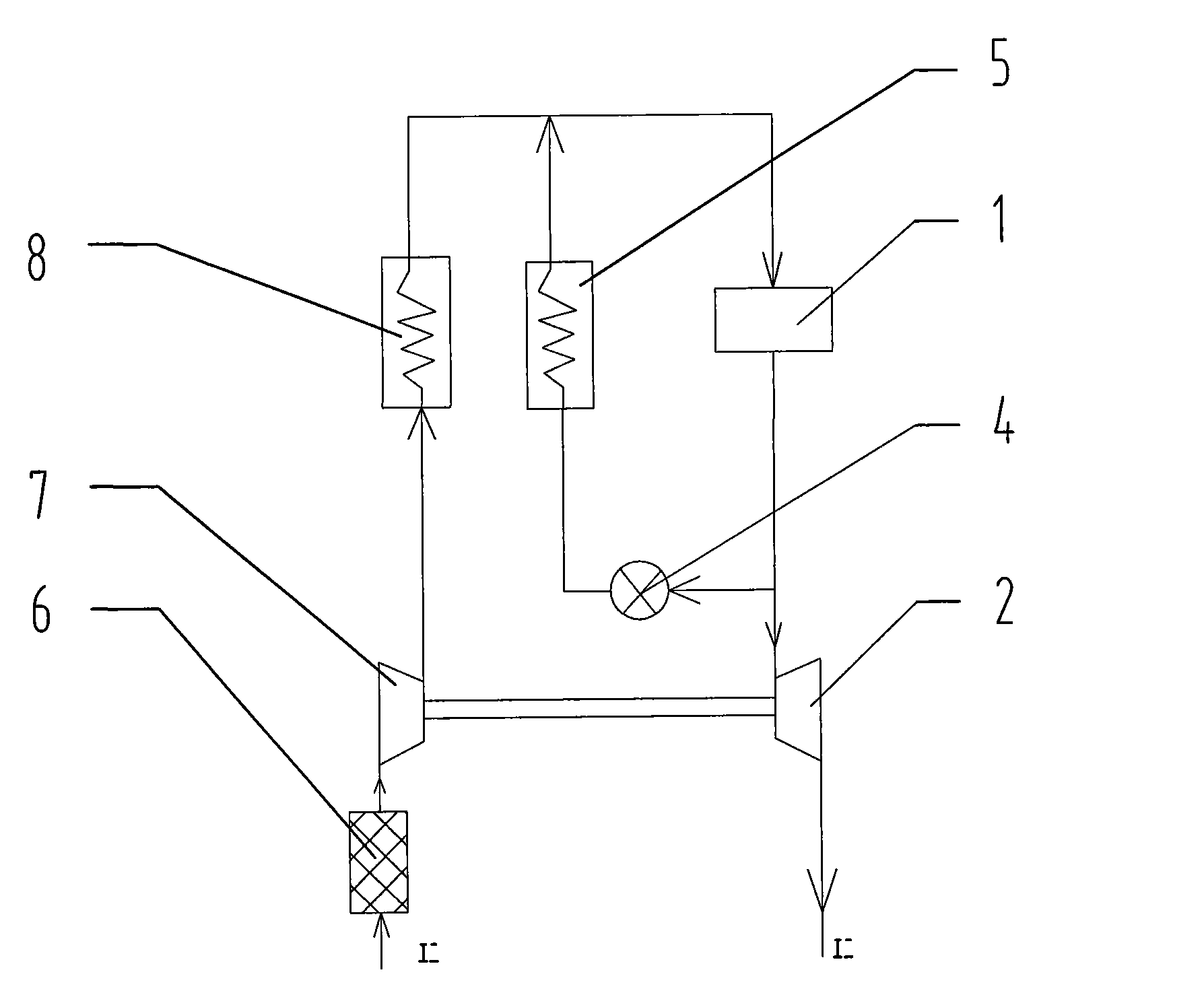
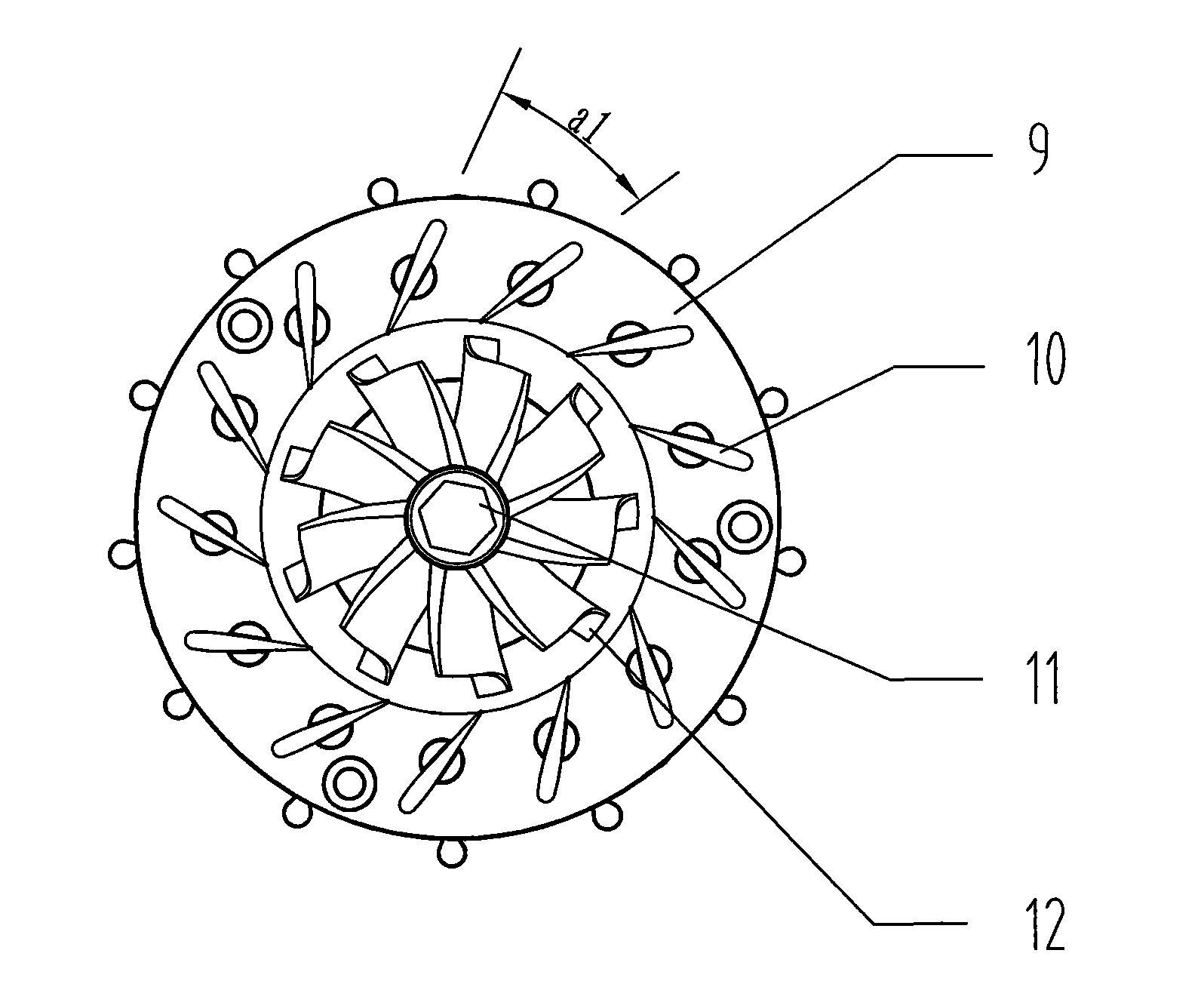
Asymmetric split turbine of turbocharger
ActiveCN101634244AAddressing High Discharge Pressure RequirementsReduce control difficultyNon-fuel substance addition to fuelInternal combustion piston enginesTurbochargerEngineering
The invention discloses an asymmetric split turbine of a turbocharger, comprising an engine. The engine is provided with an exhaust tube of the engine, a turbine casing and a turbine rotor, wherein, the turbine casing is provided with a casing high pressure flow channel and a casing low pressure flow channel, the exhaust tube of the engine is provided with a high pressure exhaust manifold and a low pressure exhaust manifold, the high pressure exhaust manifold is connected with the casing high pressure flow channel, the low pressure exhaust manifold is connected with the casing low pressure flow channel, and the A / R value of the casing high pressure flow channel is less than that of the casing low pressure flow channel. By adopting the asymmetric split structure, the two flow channels of the turbine casing have different A / R values and are respectively connected with different exhaust pipelines of the engine, thus effectively lowering the exhaust back pressure of part of engine cylinders and reducing the influence of EGR operation process on the pressurizing unit. The asymmetric split turbine has good succession, simple structure, easy upgrade and switch of products, low cost and easy and fast realization of engineering.
Owner:康跃科技(山东)有限公司
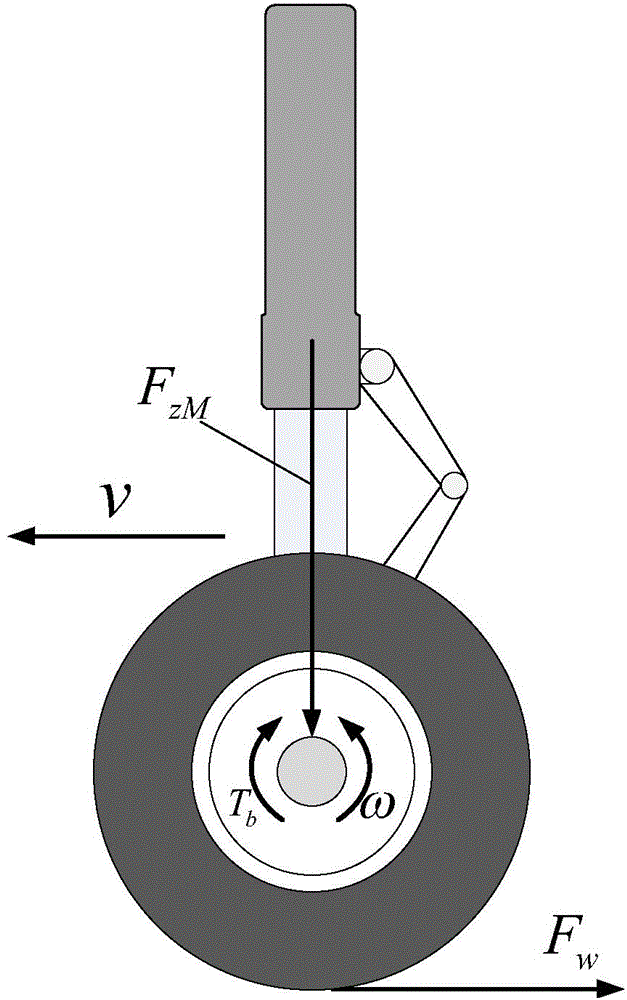
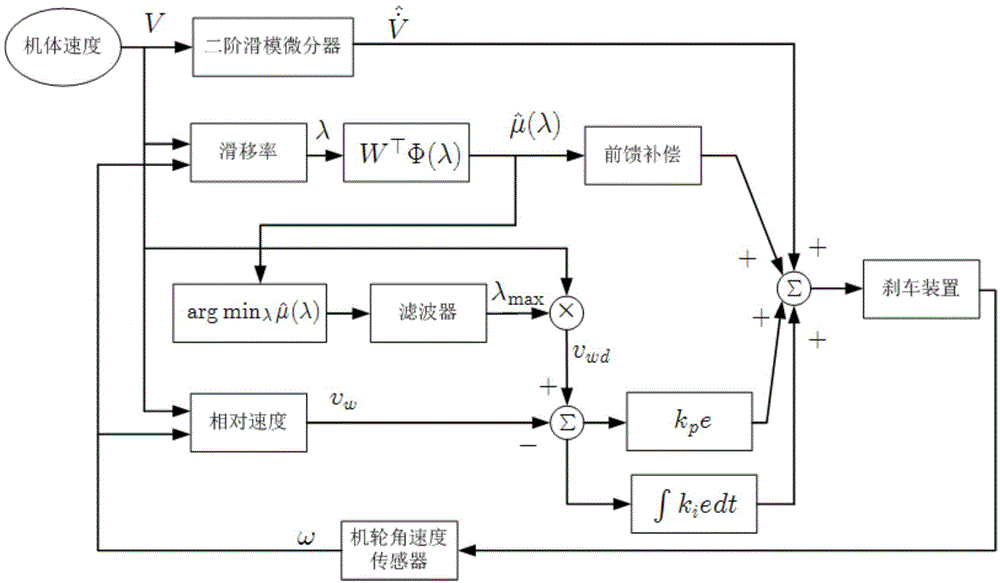
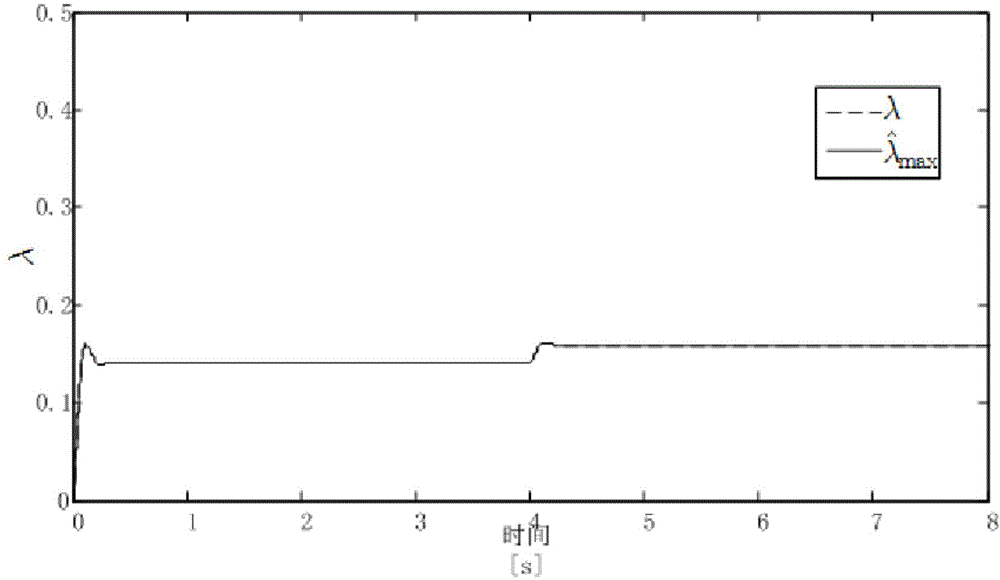
Aircraft anti-skid brake control method
InactiveCN103552685AAvoid learning to identifyTaking into account efficiencyAircraft braking arrangementsBraking systemsReduction rateDifferentiator
The invention relates to an aircraft anti-skid brake control method. According to the aircraft anti-skid brake control method, an aircraft reduction rate signal is constructed by means of the robustness and anti-interference characteristics of a tracking differentiator or a second-order sliding mode differentiator, and is used for calculating slip force, and learning identification in a longitudinal dynamics process is avoided. According to the method, braking longitudinal force does not need to be assumed to be uniformly distributed, and the method can be used for a multi-wheel brake system. In addition, a safety operation range of the brake system is considered, the brake pressure is constrained, the anti-skid brake efficiency and anti-lock safety are considered simultaneously, and the method has certain advancement.
Owner:渭南高新区晨星专利技术咨询有限公司
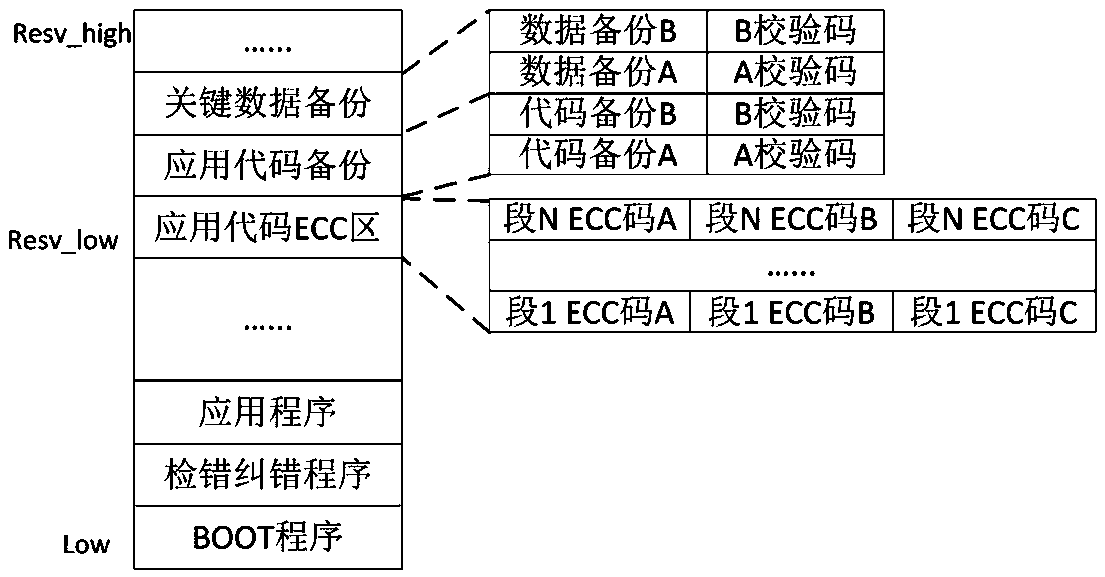
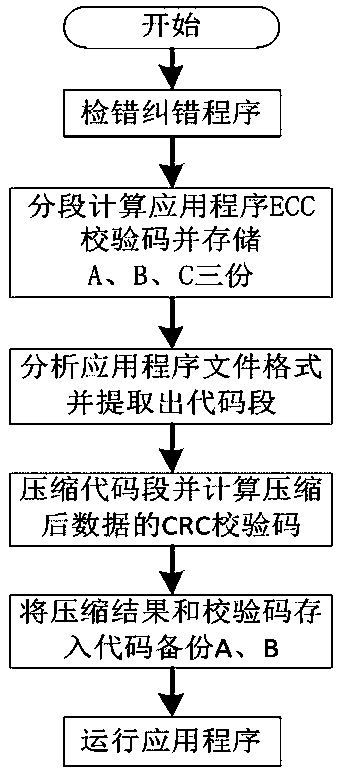
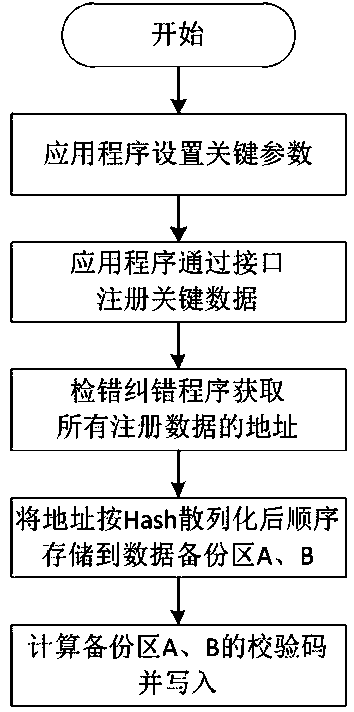
Method and system for detecting and recovering memory bit flipping of power secondary equipment
ActiveCN111552590AQuick Position RecoveryGuaranteed uptimeHardware monitoringNon-redundant fault processingProgramming languageCheck digit
The invention discloses a method and a system for detecting and recovering memory bit flipping of power secondary equipment in the technical field of memory error correction, and aims to solve the technical problem of abnormal equipment function or result caused by memory bit flipping of the power secondary equipment in the prior art. The method comprises the following steps that ECC check code calculation is conducted on an application program running area when an application program is loaded according to the preset ECC segment length, and ECC check codes of segment data of the application program when the application program is loaded are obtained; ECC check code calculation is performed on the segment data of the application program when the application program runs according to a preset ECC segment length to obtain an ECC check code of the segment data of the application program when the application program runs; the ECC check code is compared with the ECC check code; and if it isjudged that the segment data of the application program has a single-bit error during running of the application program according to the comparison result, the bit with the error is corrected.
Owner:NARI TECH CO LTD +1
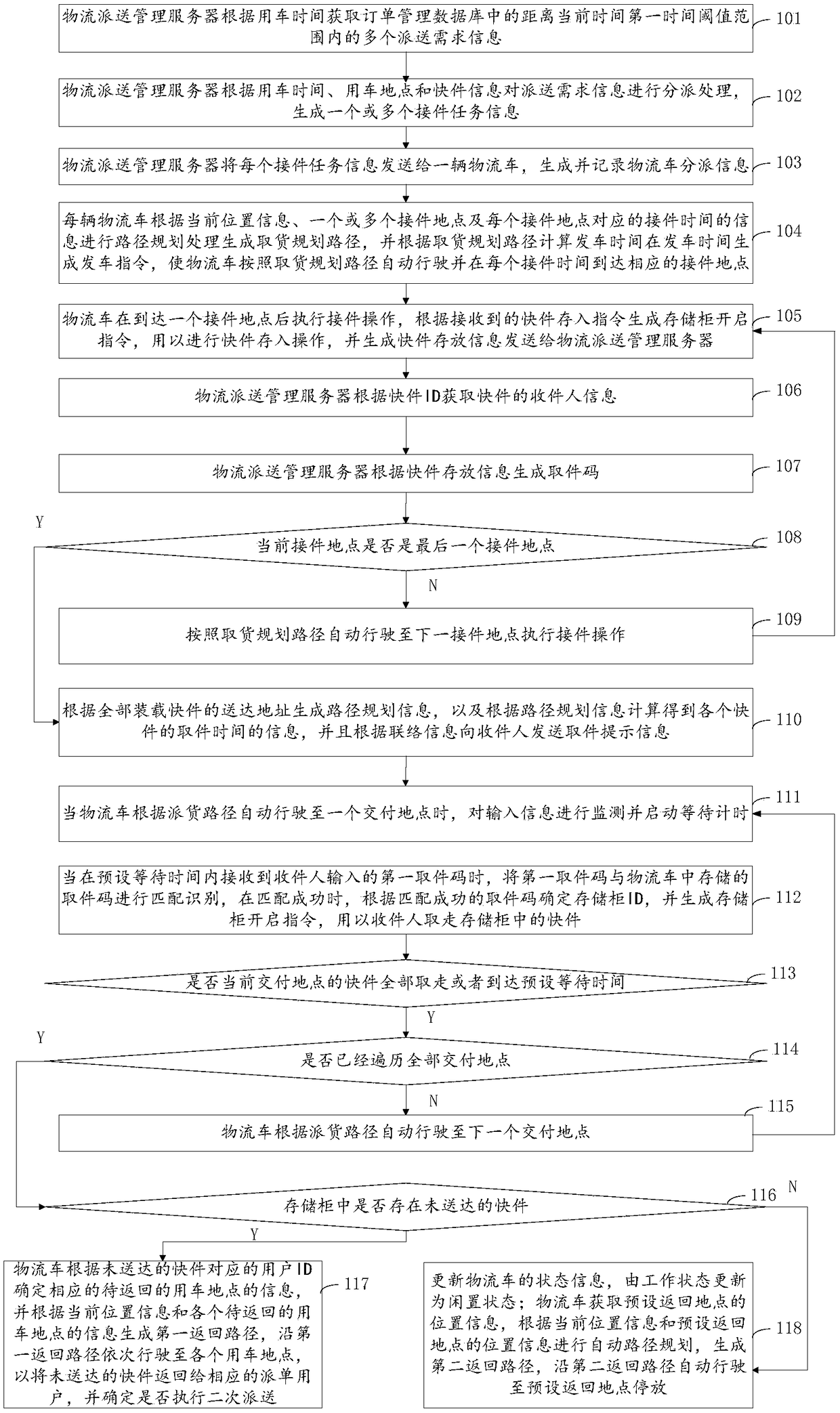
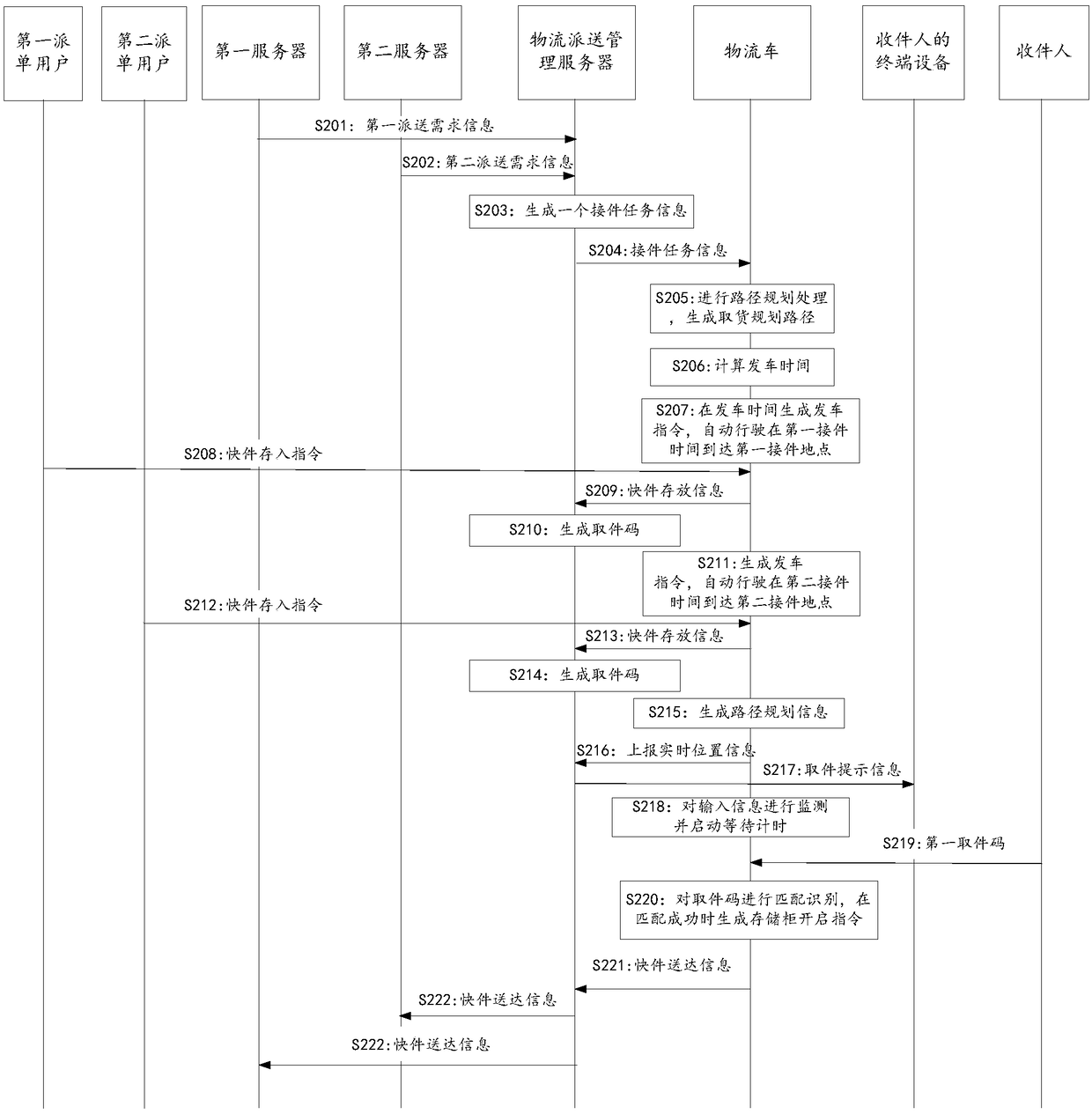
Full-automatic logistical overall delivery service method
The invention provides a full-automatic logistical overall delivery service method. The method comprises the following steps of: obtaining delivery demand information of a plurality of users in an order management database according to car using time, carrying out delivery task distribution according to the delivery demand information of the users so as to generate one or more pieces of receptiontask information, and enabling each logistical car to carry out automatic path planning according to one piece of reception task information, automatic run according to a planned pickup path and arrive at appointed places to receive to-be-delivered expresses before the car using time; generating path planning information according to service addresses of all the loaded expresses, recognizing pickup codes input by recipients and carrying out matching when the car automatically and sequentially arrives at each delivery place according to the delivery path, and after the matching succeeds, generating storage cabinet opening instructions so that the recipients can take away expresses in storage cabinets; and when the fact that all the expressed at the current deliver place is taken away or a preset waiting time expires, automatically running to the next deliver place by the logistical car according to the delivery path.
Owner:BEIJING ZHIXINGZHE TECH CO LTD
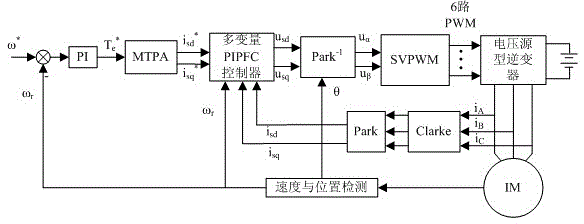
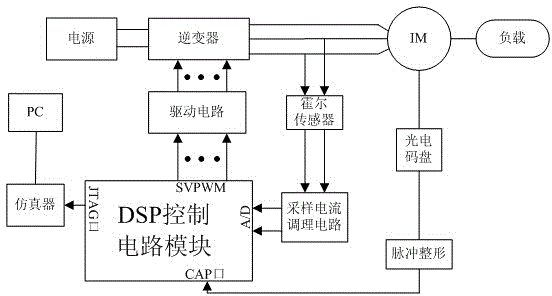
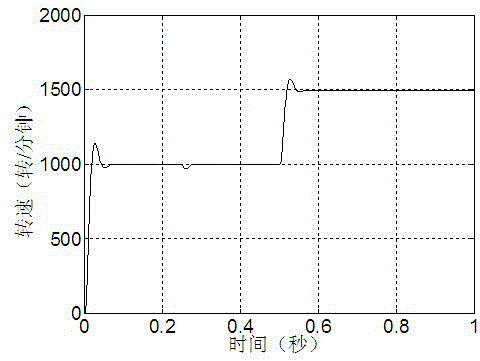
Control method for maximum torque current rate of induction motor
ActiveCN104135205ATaking into account efficiencyImprove operational efficiencyElectronic commutation motor controlVector control systemsMulti inputMaximum torque
The invention discloses a control method for maximum torque current rate of an induction motor, belonging to the technical field of induction motor control. According to the control method, when the induction motor is at a working condition of light load running, PI (Proportional-Integral) and forecasting function control are combined so as to obtain a novel control method which can be applicable for a multi-input-multi-output system, control quantity output from a forecasting function controller serves as an input signal of an inverter circuit to change output voltage of an inverter, so that motor rotation speed is controlled, and tracking control on the rotation speed of the induction motor is achieved. The control method has the advantages of high control accuracy, fast tracking speed, low steady-state error and high interference resistance, the induction motor can be guaranteed to be endowed with high stability and dynamic performance, and the running efficiency of the motor at a dynamic condition can be improved.
Owner:邳州市景鹏创业投资有限公司
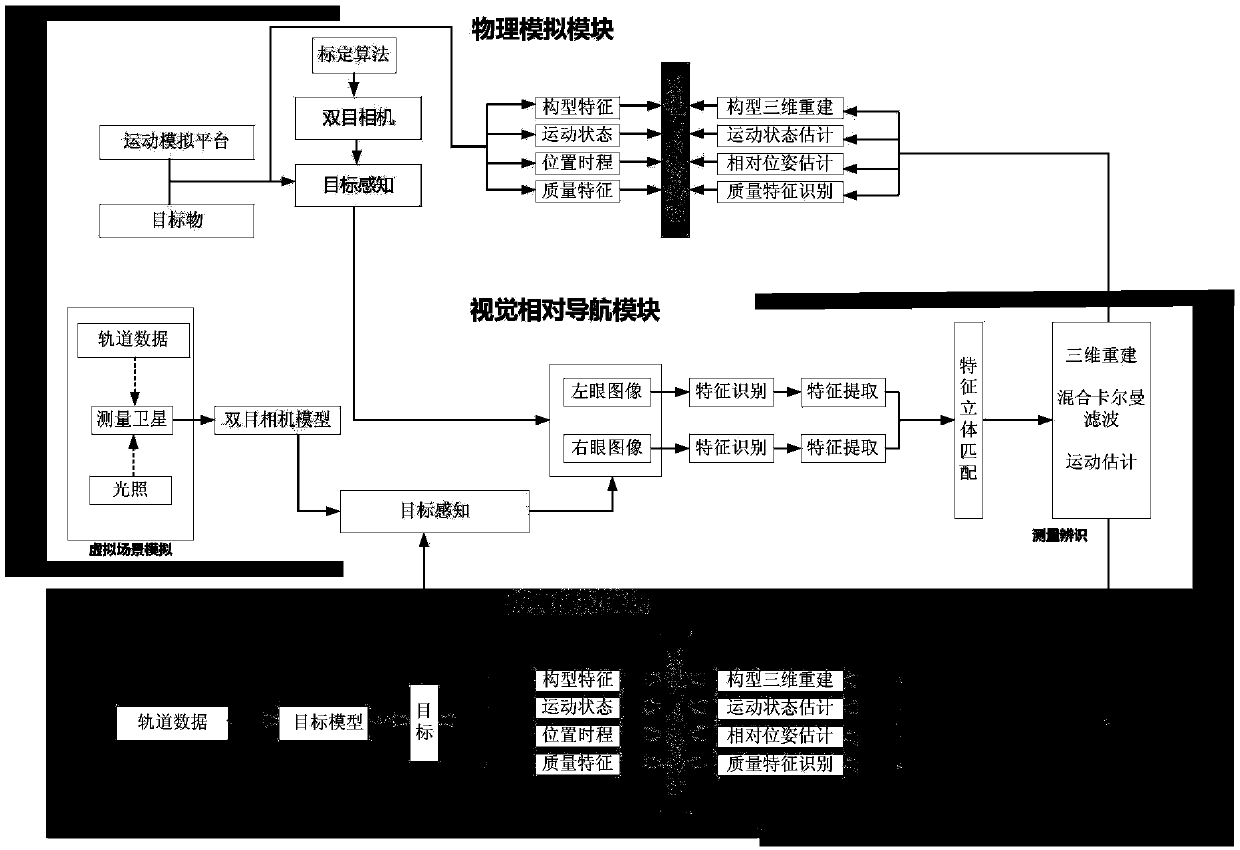
Vision measurement system for non-cooperative target relative navigation simulation verification, and method thereof
ActiveCN108645416ATaking into account efficiencyEasy to useInstruments for comonautical navigationSimulationPattern perception
The invention discloses a vision measurement system for non-cooperative target relative navigation simulation verification, and a method thereof. The system includes a physical simulation module, an analogue simulation module and a visual relative navigation module; the physical simulation module and the visual relative navigation module form a semi-physical semi-simulation verification subsystem,and the visual relative navigation module and the analogue simulation module form a full-simulation verification subsystem; and the physical simulation module and the analogue simulation module construct a non-cooperative target, and the visual relative navigation module realizes the perception, feature recognition, feature extraction, feature matching, state measurement and parameter identification of the non-cooperative target by a binocular camera.
Owner:BEIJING INST OF SPACECRAFT SYST ENG
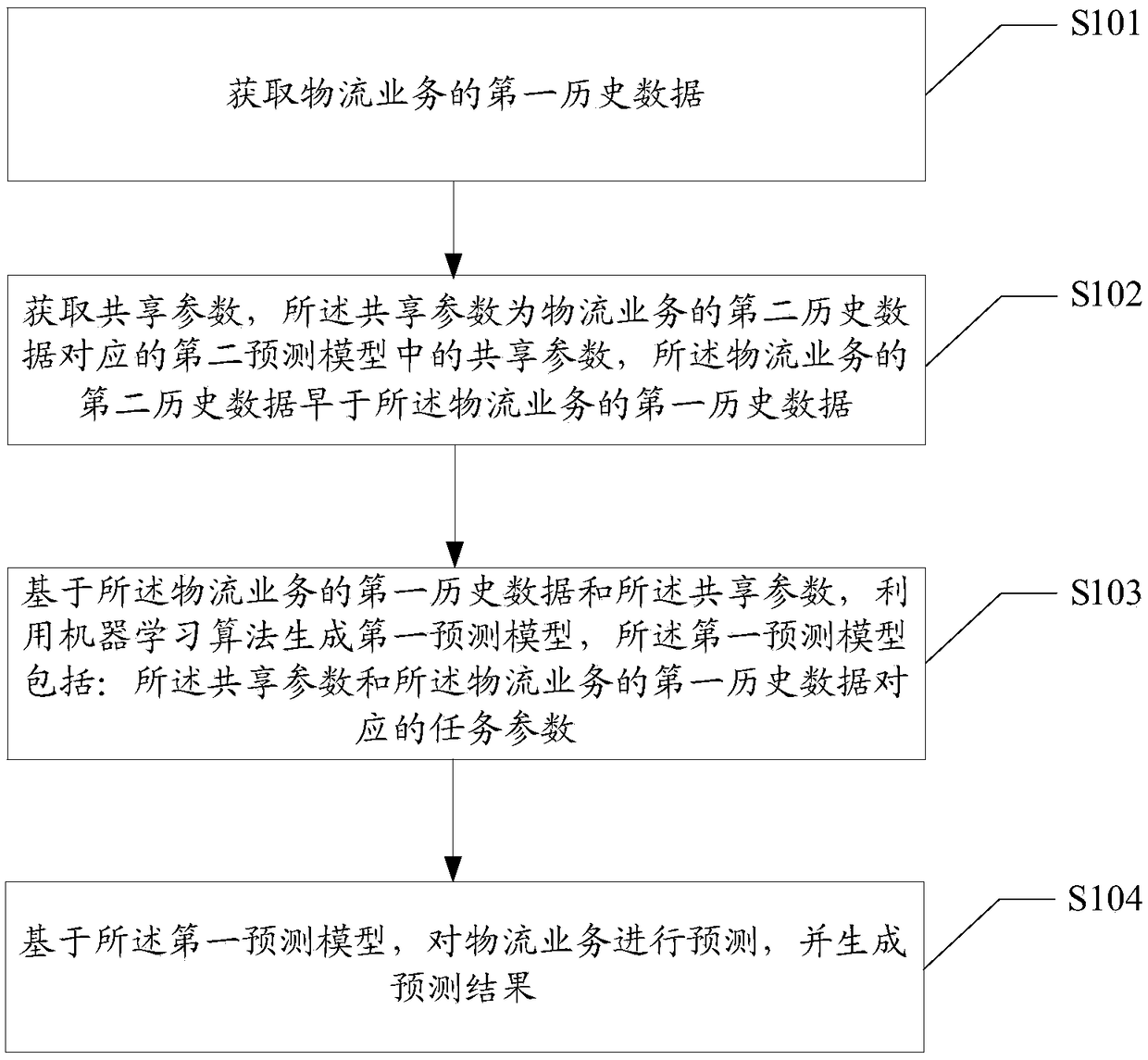
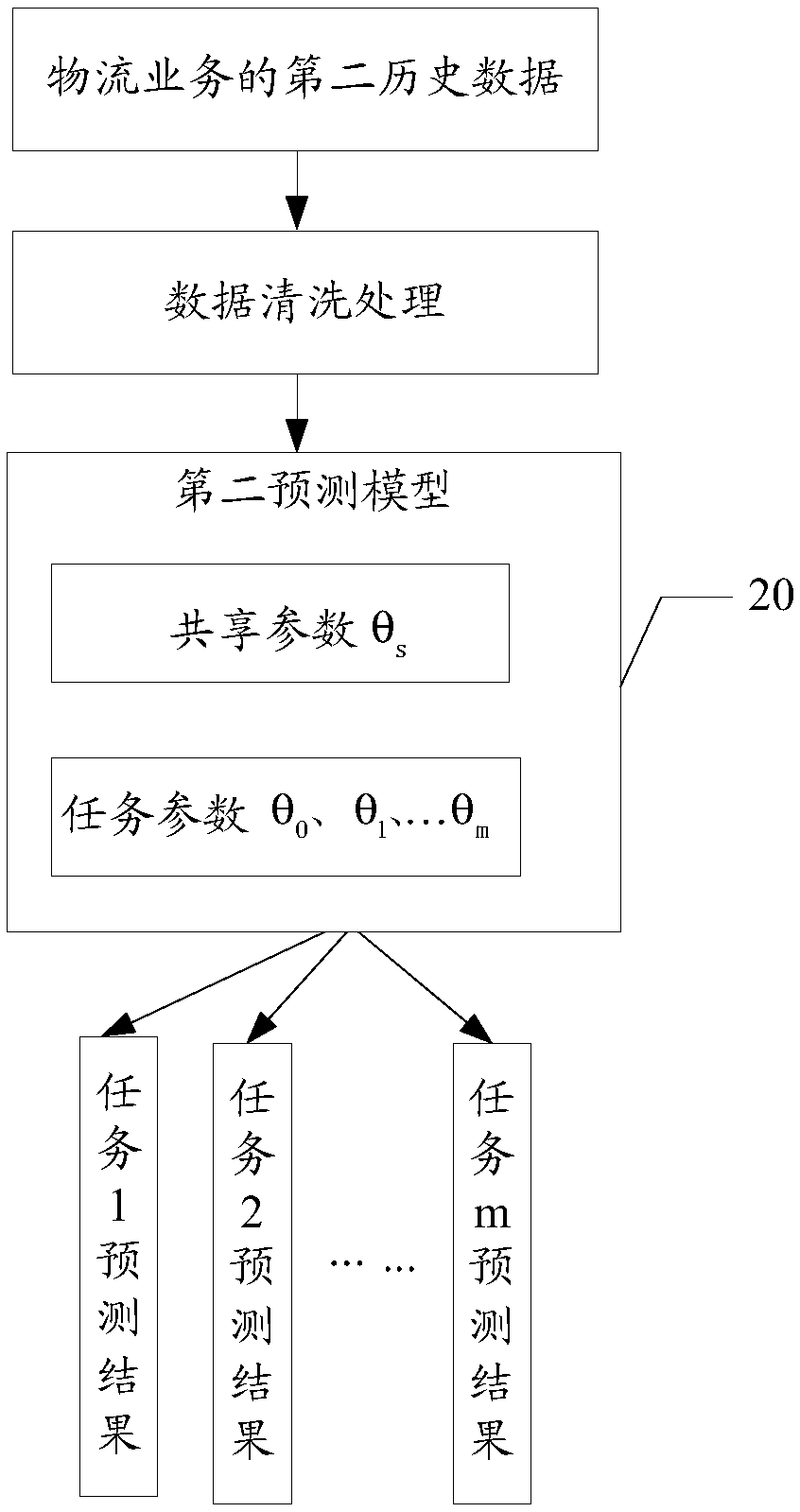
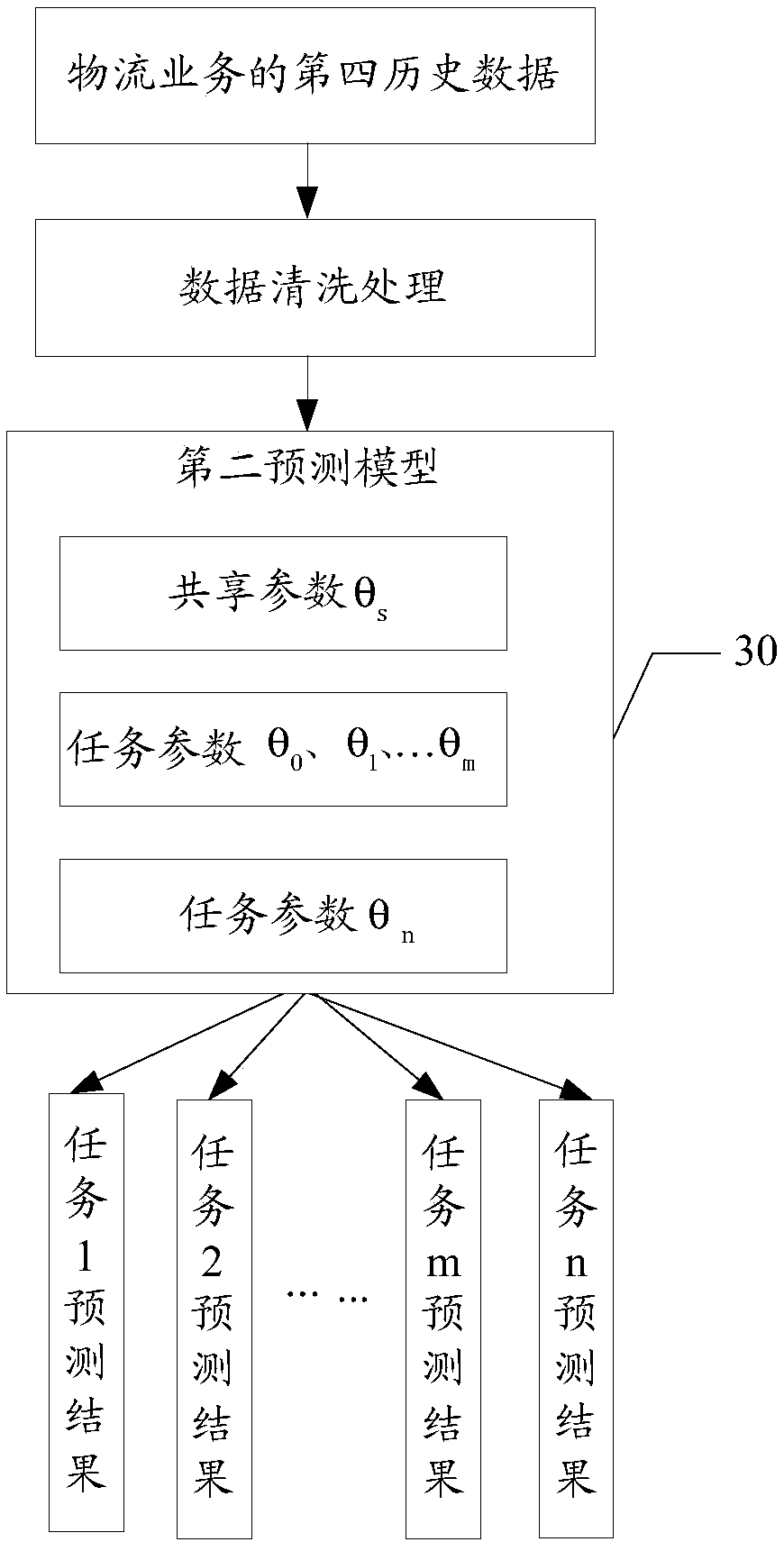
Logistics service prediction method and device, and readable storage medium
ActiveCN109214559AImprove forecasting efficiencyImprove predictive performanceForecastingMachine learningLogistics managementBusiness forecasting
A method and apparatus for predicting logistics services, a readable storage medium, the predicting apparatus for logistics services comprising: acquiring first historical data of logistics services;acquiring a shared parameter, the shared parameter being a shared parameter in a second prediction model corresponding to a second historical data of a logistics service, the second historical data ofthe logistics service being earlier than the first historical data of the logistics service; generating a first prediction model using a machine learning algorithm based on the first historical dataof the logistics service and the shared parameters, the first prediction model comprising: task parameters corresponding to the shared parameters and the first historical data of the logistics service; predicting a logistics service based on the first prediction model, and generating a prediction result. Applying the above scheme, the effect and efficiency of logistics business forecasting can betaken into account simultaneously.
Owner:ANJI AUTOMOTIVE LOGISTICS +1
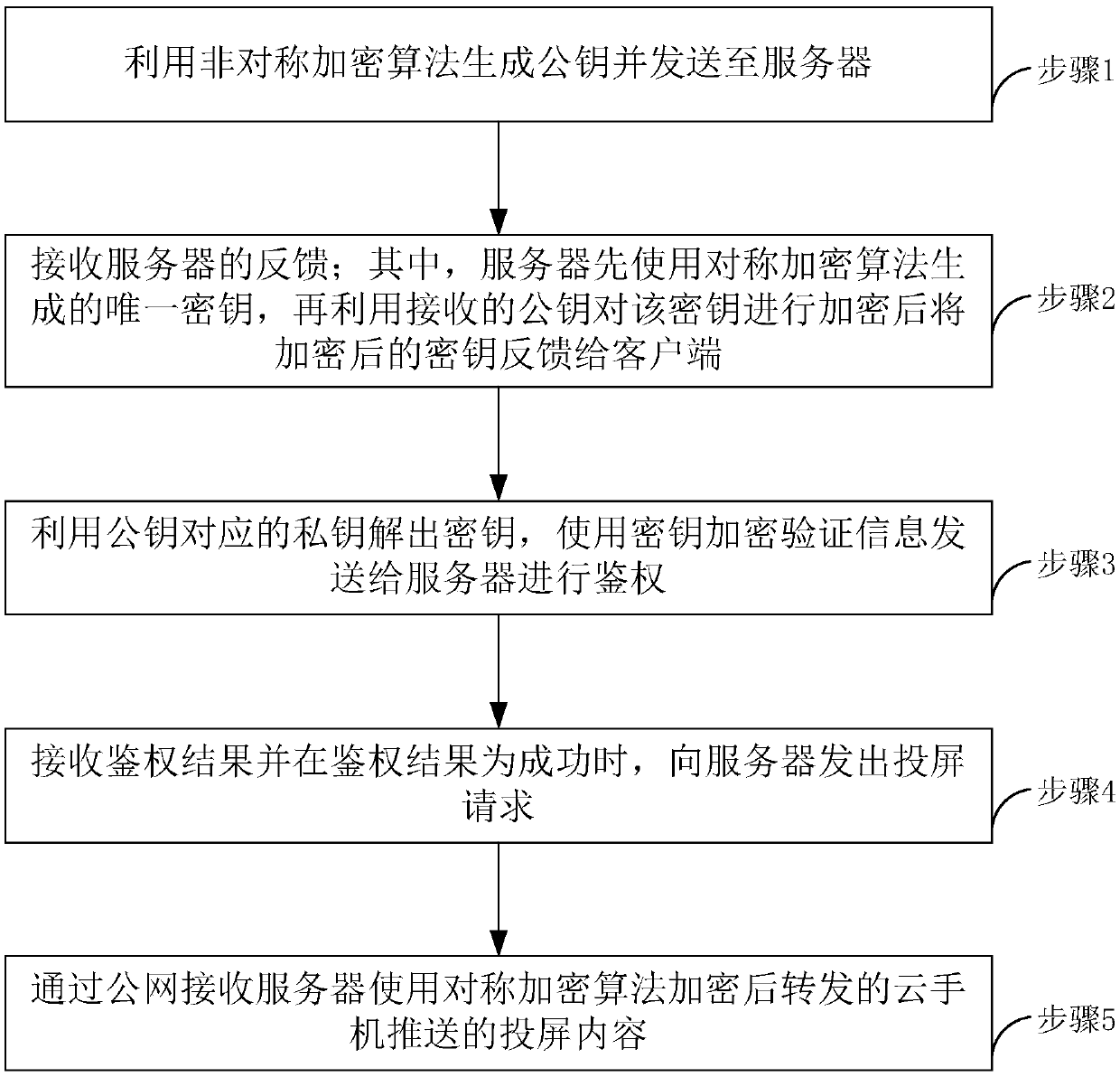
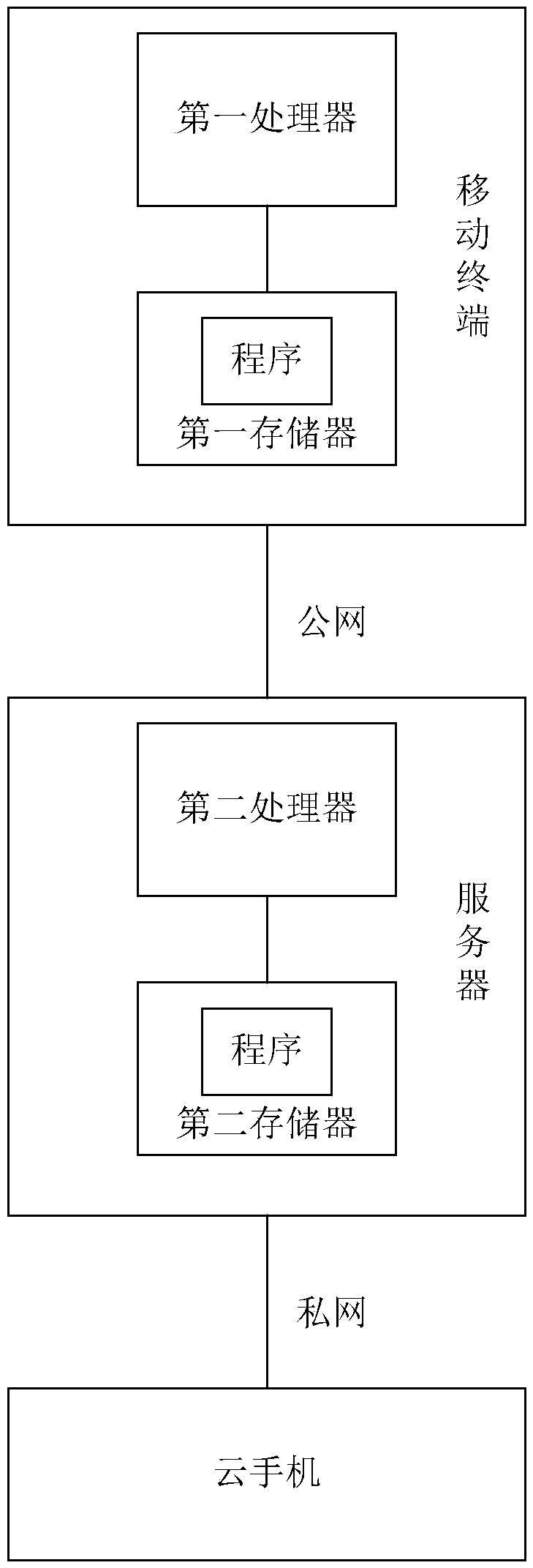
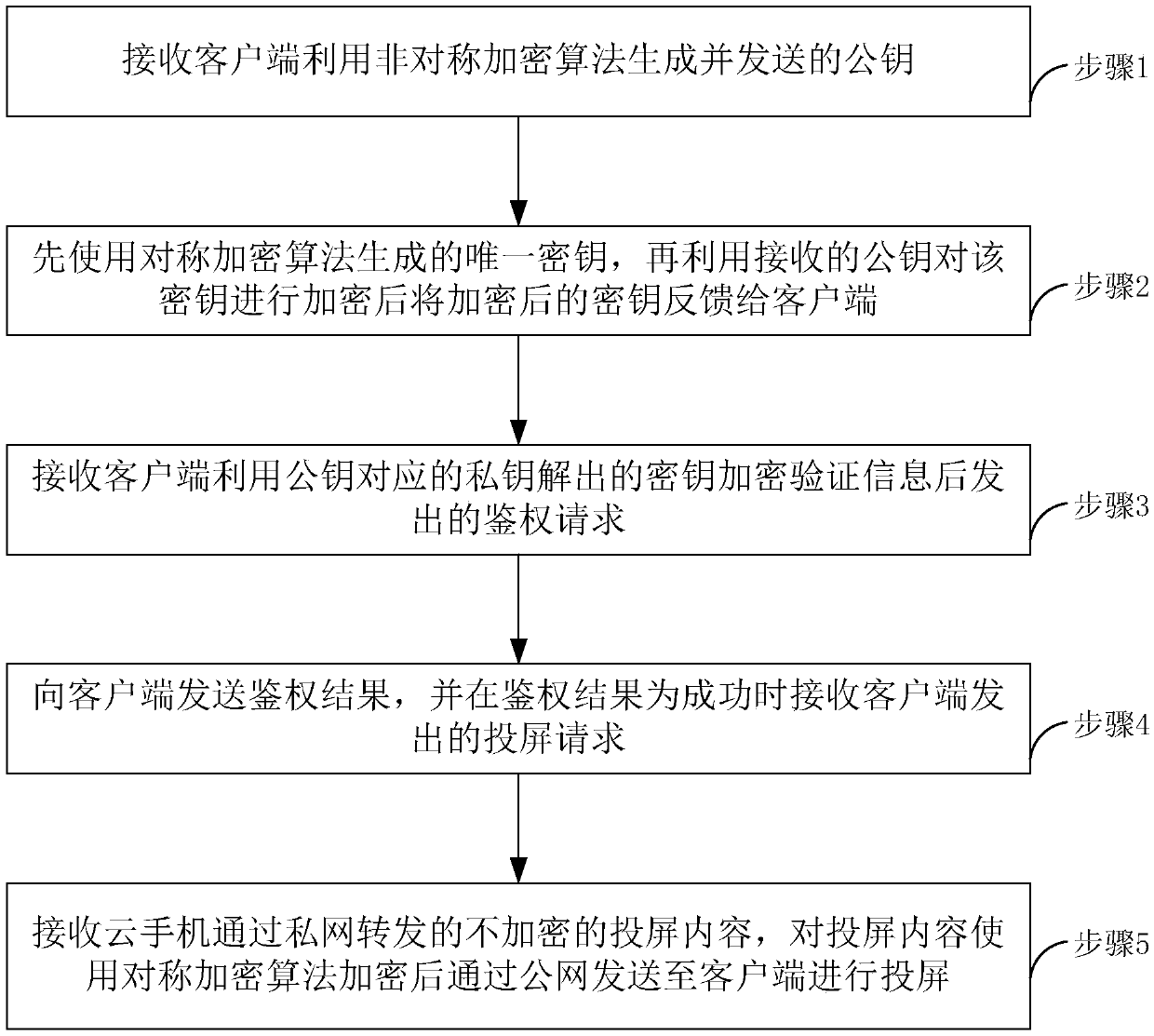
Safe screen projection method of cloud mobile phone, mobile terminal and server
InactiveCN109639697AEnsure safetyTaking into account efficiencyKey distribution for secure communicationMultiple keys/algorithms usagePrivate networkClient-side
The invention relates to the technical field of networks, and relates to a safe screen projection method of a cloud mobile phone, a mobile terminal and a server. The method includes the following steps: generating a public key by using an asymmetric encryption algorithm and sending the public key to the server; receiving feedback from the server, wherein the server firstly uses a symmetric encryption algorithm to generate a unique key, then encrypts the key with the received public key, and then feeds the encrypted key back to the client; decrypting the key by a private key corresponding to the public key, and encrypting verification information by using the key, and sending the verification information to the server for authentication; receiving an authentication result and sending a screen projection request to the server when the authentication result is successful; and using a public network to receive projection content forwarded after being encrypted by the server using the symmetric encryption algorithm and pushed by the cloud mobile phone. The method firstly uses the asymmetric encryption algorithm to realize authentication. After successful authentication, the screen projection is performed and screen projection content transmitted by the private network is not encrypted, while screen projection content transmitted by the public network is encrypted by the symmetric encryption algorithm, so that security is ensured and some links are encrypted with efficiency.
Owner:广州微算互联信息技术有限公司
Adaptive plane layering method based on additional material remanufacturing point cloud model
ActiveCN108022307ASkip the resurfacing processImprove efficiencyAdditive manufacturing apparatusImage data processingPoint cloudInter layer
The invention relates to an adaptive plane layering method based on an additional material remanufacturing point cloud model. The method comprises: step one, a layering direction is determined; step two, a layering height is determined; to be specific, traverse of point cloud coordinates is carried out to obtain a zmin and a zmax, difference processing is carried out on the zmin and the zmax to obtain a layering height; step three, an inter-layer point cloud mapping relationship is constructed; step four, a surface error is defined; to be specific, a surface error P is defined to express a surface difference degree between two slices, wherein sigma is equal to Rmax and the Rmax expresses a maximum value a radial width R of a projection point cloud; and step five, a layering thickness is determined. According to the adaptive plane layering method, the maximum value of the radial width R of the projection point cloud is used as a surface error and thus an adaptive layering height is determined by iteration; the algorithm implementation process is clear; and both efficiency and precision are considered.
Owner:ARMOR ACADEMY OF CHINESE PEOPLES LIBERATION ARMY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com