Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
137 results about "Memory leak detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
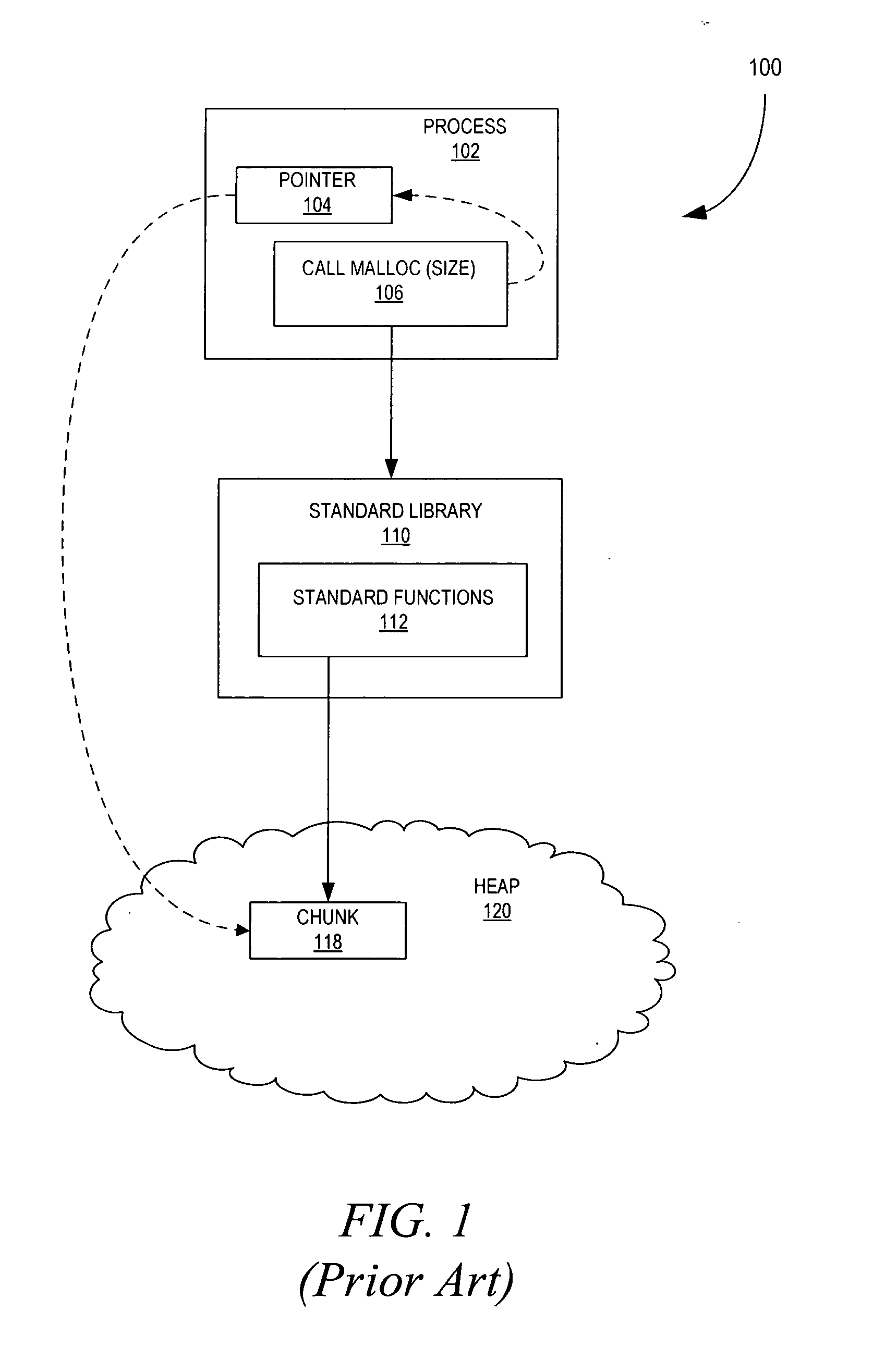
You can use some techniques in your code to detect memory leak. The most common and most easy way to detect is, define a macro say, DEBUG_NEW and use it, along with predefined macros like __FILE__ and __LINE__ to locate the memory leak in your code.
Method and system for memory leak detection
InactiveUS7487321B2Error detection/correctionMemory adressing/allocation/relocationParallel computingMemory leak detection
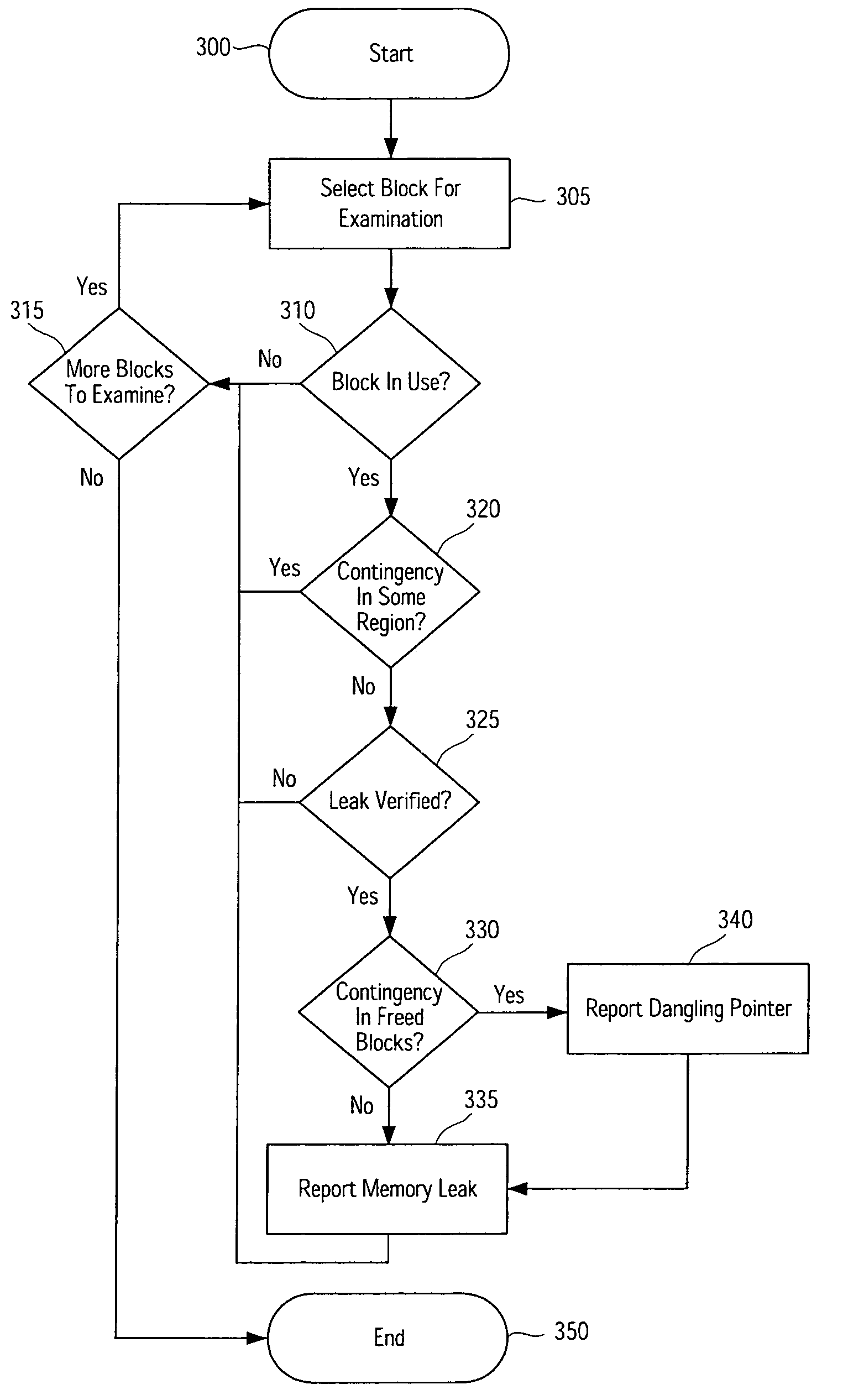
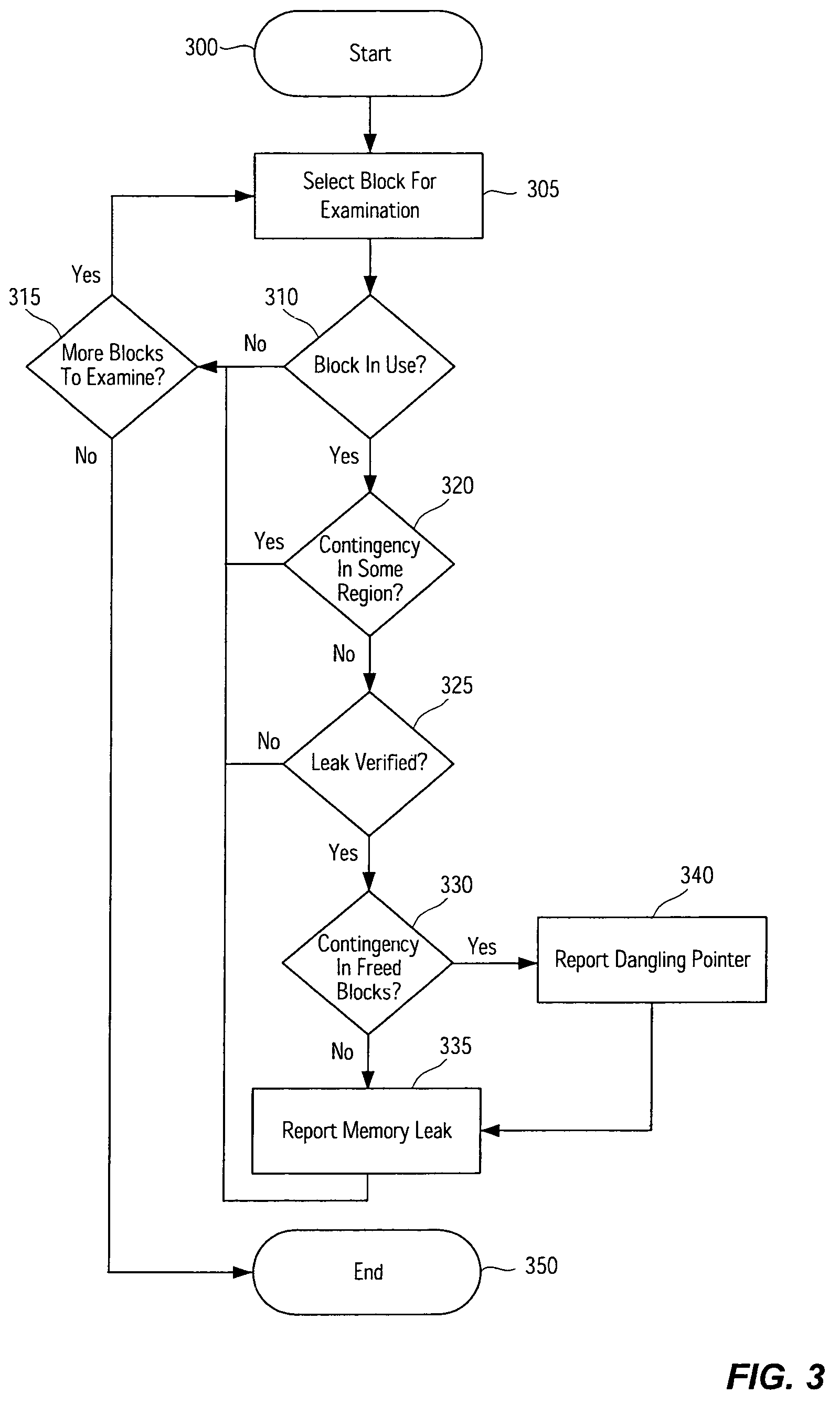
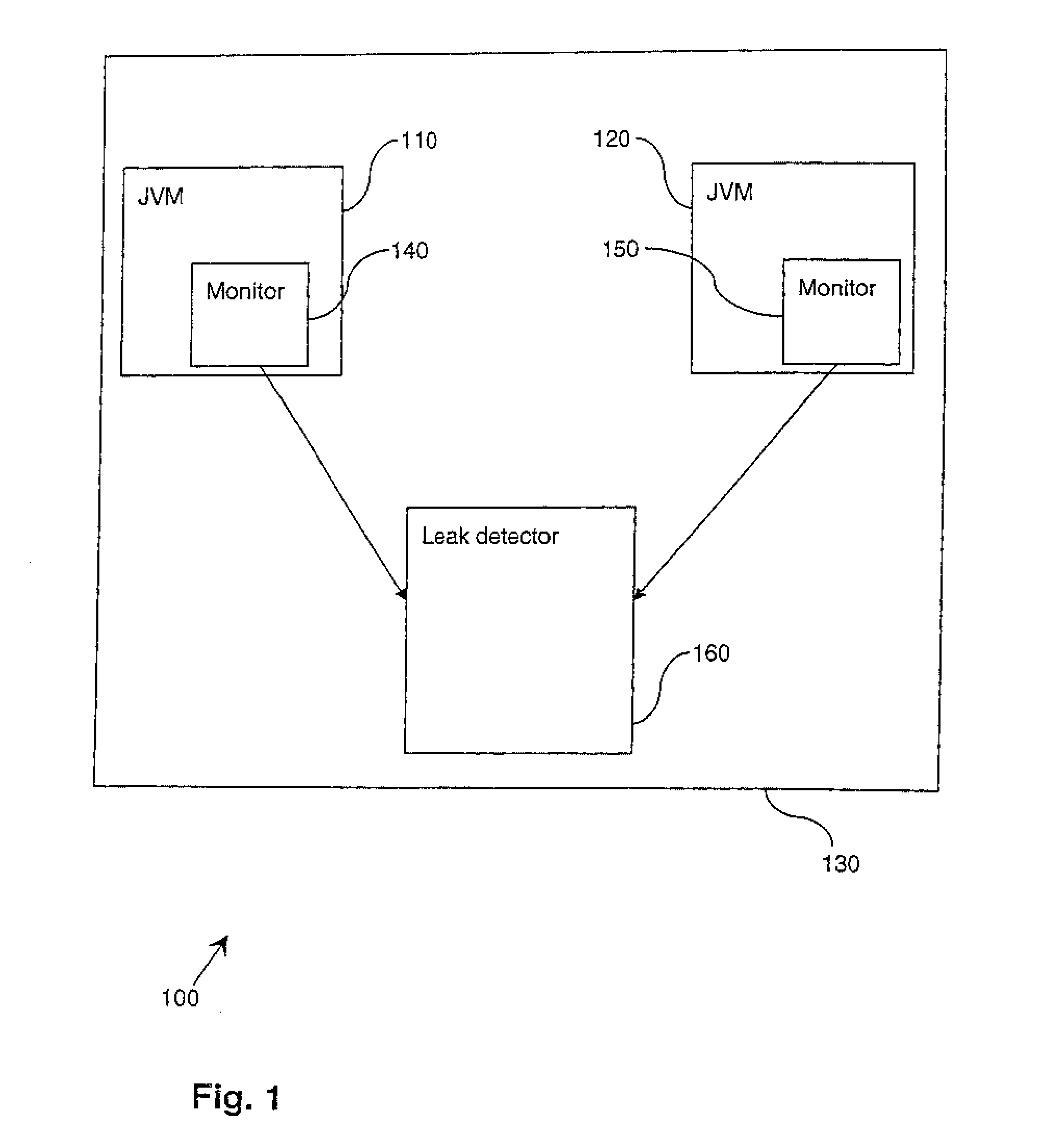
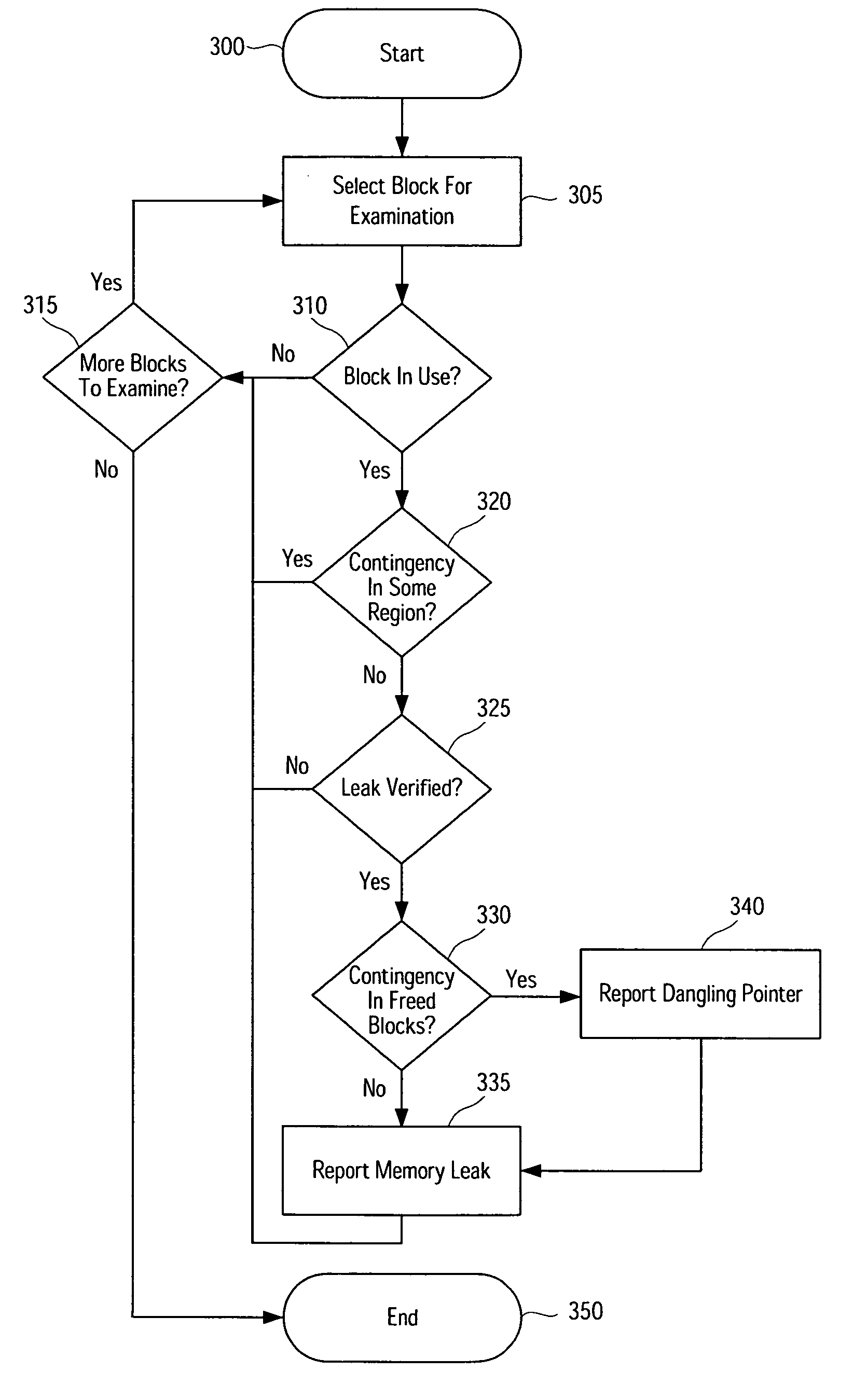
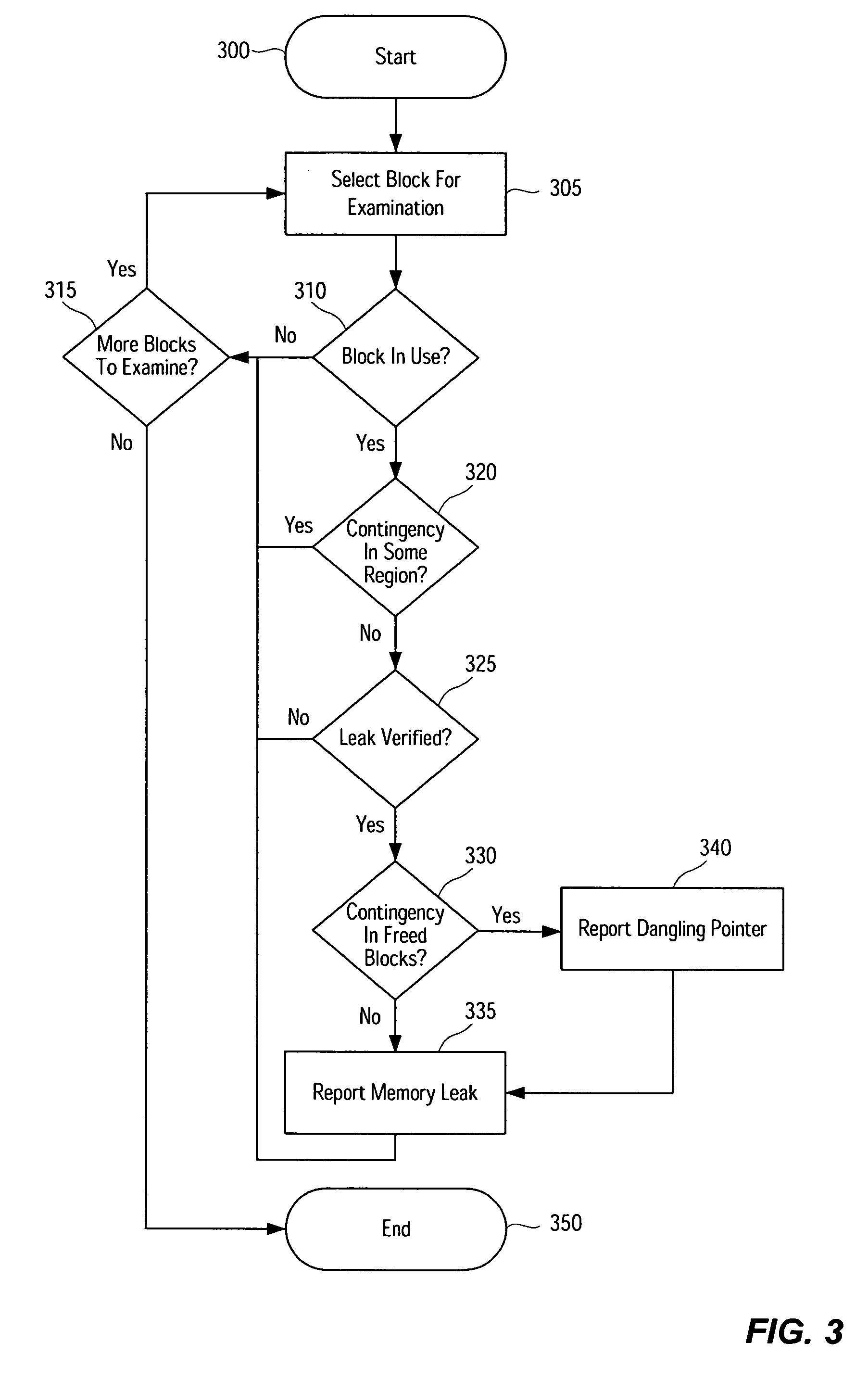
Systems, methods, apparatus and software can be implemented to detect memory leaks with relatively high confidence. By analyzing memory blocks stored in a memory, implicit and / or explicit contingency chains can be obtained. Analysis of these contingency chains identifies potential memory leaks, and subsequent successive verification confirms whether the potential memory leaks are memory leaks.
Owner:CISCO TECH INC
Method and system for memory leak detection
InactiveUS20050235127A1Error detection/correctionMemory adressing/allocation/relocationParallel computingTerm memory
Systems, methods, apparatus and software can be implemented to detect memory leaks with relatively high confidence. By analyzing memory blocks stored in a memory, implicit and / or explicit contingency chains can be obtained. Analysis of these contingency chains identifies potential memory leaks, and subsequent successive verification confirms whether the potential memory leaks are memory leaks.
Owner:CISCO TECH INC
Memory leak detection
InactiveUS20070027942A1Non-redundant fault processingSpecific program execution arrangementsParallel computingTerm memory
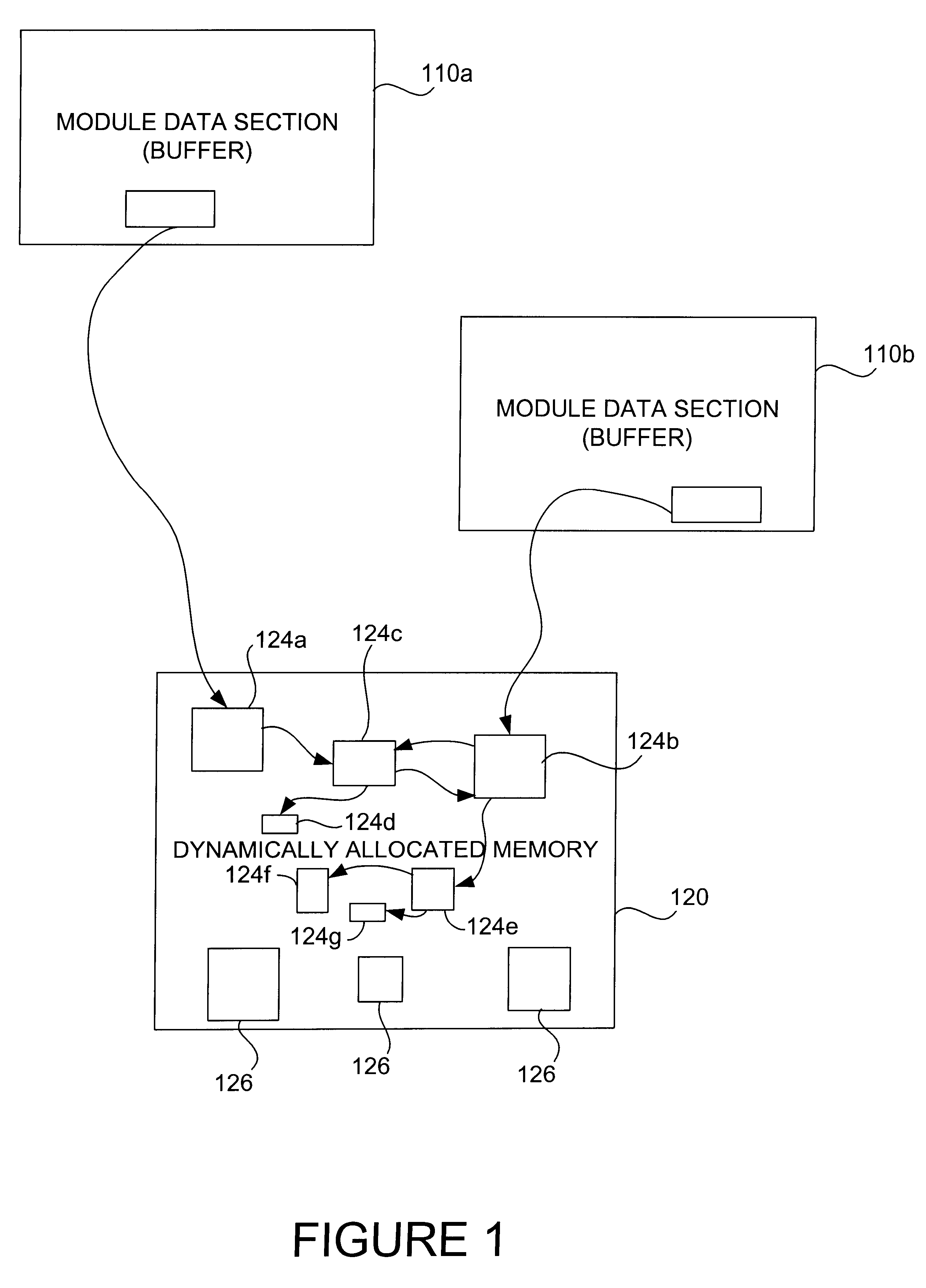
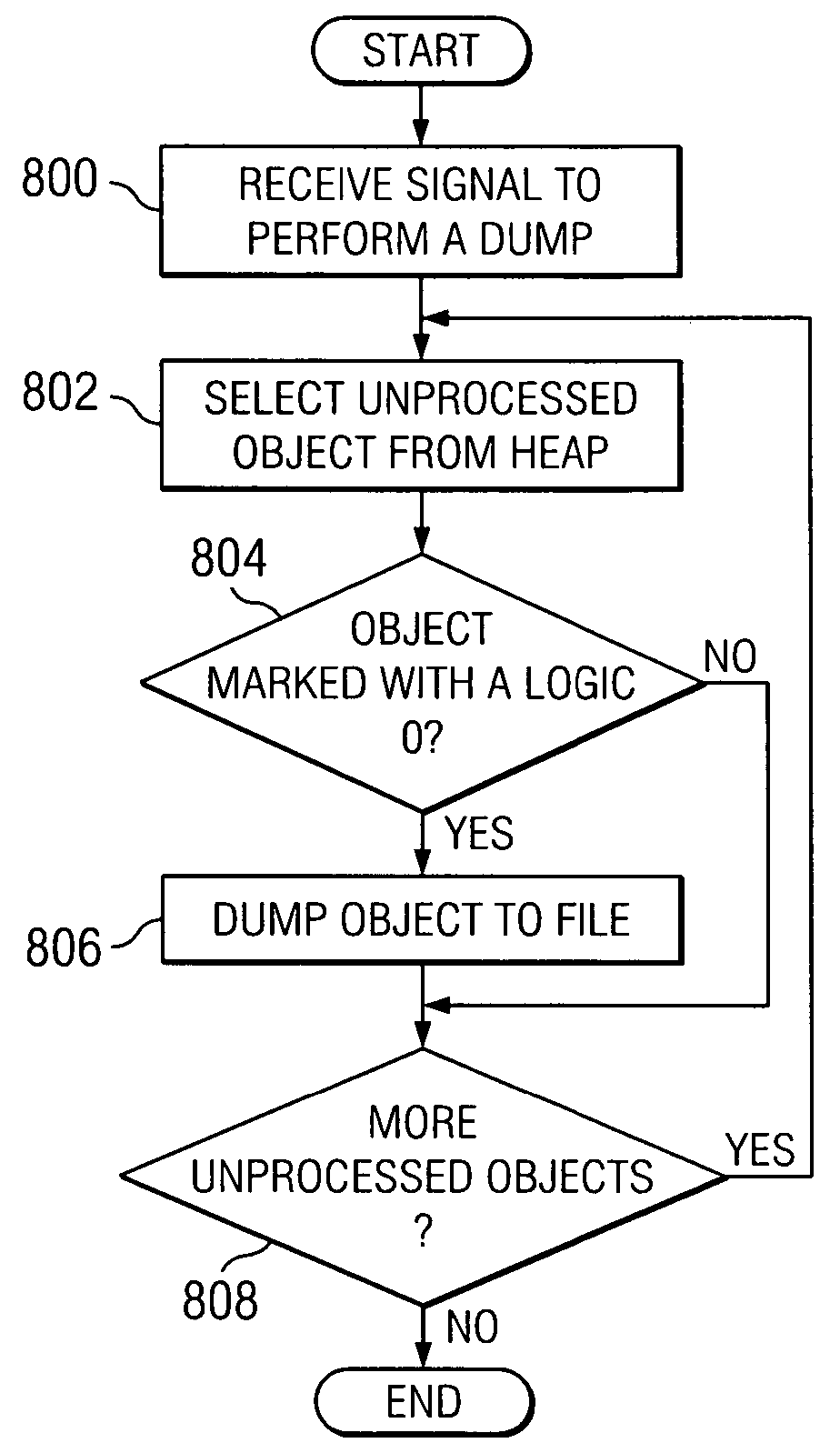
A memory leak detection scheme for use in a computer system (e.g., Java) by: finding an allocation site (410) which is responsible for allocating objects which accumulate in a memory heap (400); and monitoring memory activity related to the found allocation site to discover a memory leak related thereto. The technique can be entirely application independent and can be made fully automatic, running as a daemon process on a machine and detecting leakage in a number of client processes simultaneously.
Owner:LINKEDIN
Memory leak detection system and method using contingency analysis
ActiveUS7293142B1ConfidenceData processing applicationsError detection/correctionSurprisal analysisParallel computing
Systems, methods, apparatus and software can be implemented to detect memory leaks with relatively high confidence. By analyzing memory blocks stored in a memory, implicit and / or explicit contingency chains can be obtained. Analysis of these contingency chains identifies potential memory leaks, and subsequent verification confirms whether the potential memory leaks are memory leaks.
Owner:CISCO TECH INC
Method and apparatus for post-mortem kernel memory leak detection
InactiveUS6523141B1Data processing applicationsMemory adressing/allocation/relocationOperational systemMemory leak detection
Methods and apparatus for detecting and reporting memory leaks associated with an operating system are disclosed. In accordance with one aspect of the present invention, a method for identifying a section of dynamically allocated memory which may not be explicitly freed includes processing information associated with a failure of an operating system and identifying a call-site that is associated with the section of the dynamically allocated memory using the information. Once the call-site is identified, a report may be generated to identify the call-site as being associated with the section of dynamically allocated memory. In one embodiment, obtaining information associated with a failure of the operating system includes obtaining an image of the operating system which is created when a kernel associated with the operating system crashes.
Owner:ORACLE INT CORP
Memory leak detection
ActiveUS20110276949A1Error detection/correctionSpecific program execution arrangementsCorrelation coefficientArtificial intelligence
Embodiments of the invention provide systems and methods for detecting an analyzing memory leaks. According to one embodiment, a method of detecting a memory leak can comprise collecting instance count data for a number of instances of a plurality of classes in a memory heap. A correlation coefficient can be calculated for each of the plurality of classes in the memory heap. The correlation coefficient can represent a relevance of the class to a growth of the memory heap. Classes contributing to the growth of the memory heap can then be identified based on the correlation coefficient.
Owner:ORACLE INT CORP
Method and apparatus for generating data for use in memory leak detection
InactiveUS20050114844A1Data processing applicationsError detection/correctionParallel computingMemory leak detection
Owner:IBM CORP
Low-overhead run-time memory leak detection and recovery
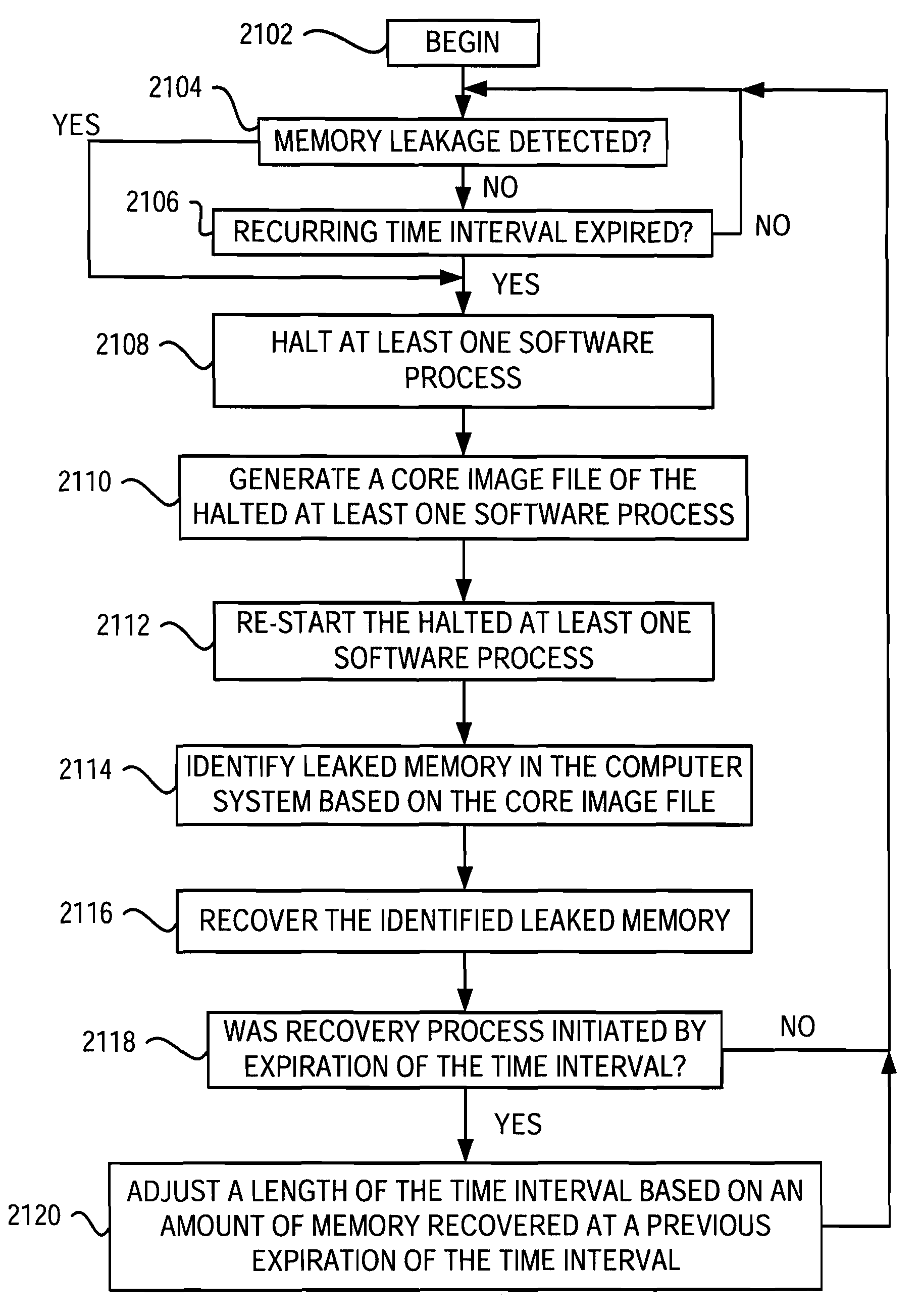
Leaked memory in a computer system is detected and recovered by first detecting memory leakage within the computer system based on nonlinear and non-parametric time-series regression analysis of software telemetry data generated by one or more software process running on the computer system. If existence of memory leakage is detected, then memory that has leaked is specifically identified and recovered. This is done by halting one or more of the software processes, generating a core image file or files of the halted software process(es), and re-starting the halted process or processes without waiting for analysis of the core image file(s). Then, the core image file is evaluated to specifically identify leaked memory in the computer system based on the core image file. Finally, the identified leaked memory is recovered.
Owner:ORACLE INT CORP
Memory leak detection method
InactiveCN101814049AExtensive coverageHardware monitoringSoftware testing/debuggingVirtualizationApplication software
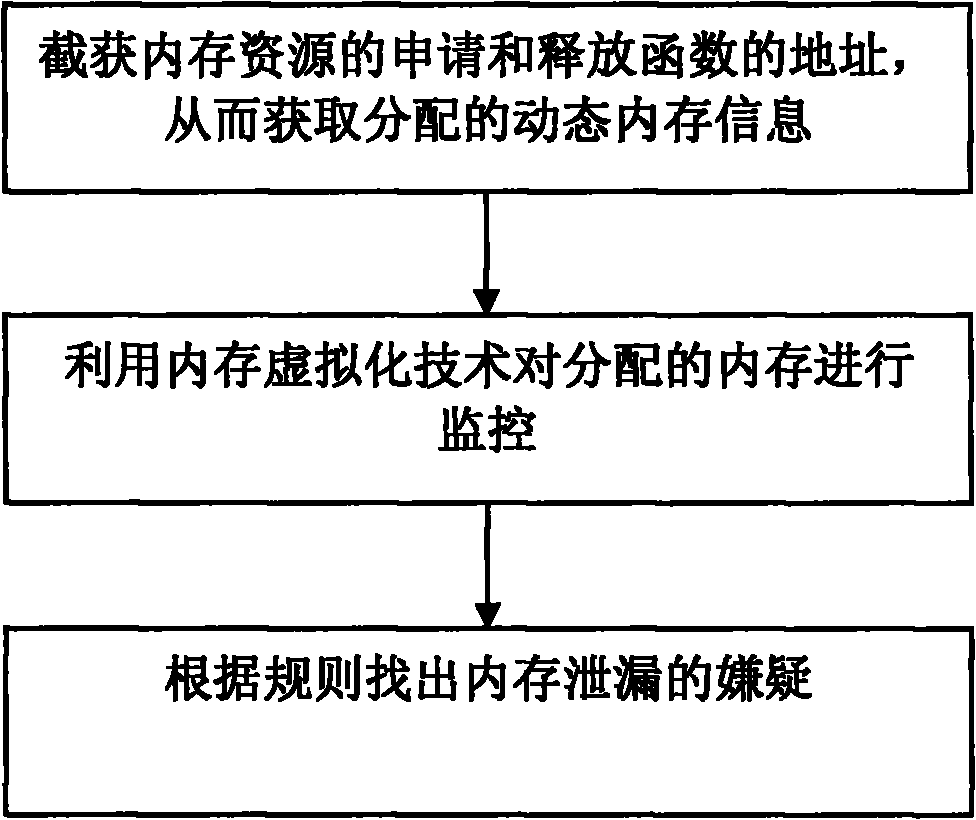
The invention discloses a memory leak detection method, and belongs to the technical field of virtualization. The method of the invention comprises the following steps that: 1) a virtual machine manager acquires addresses of an application function and a release function of a memory resource so as to acquire the allocated dynamic memory information; 2) calculating all the memory monitoring units crossed by a dynamic memory according to the start address and length of the dynamic memory; 3) a mapping relationship from the virtual address of the memory monitoring unit to the address of the machine is deleted from a shadow page table; 4) the virtual machine manager monitors whether the memory monitoring unit in the step 2) is accessed or not when a virtual machine is sunken; and 5) a monitoring strategy module regards the dynamic memory item where the memory monitoring unit is not accessed by an application program within a set time as the dynamic memory item on suspicion of memory leak. Compared with the prior art, the method can find out the potential memory leak without amending the source code of the detected program or newly encoding so as to provide transparency for the tested code.
Owner:PEKING UNIV
Device and method for detecting memory leak
InactiveCN101539870AEasy program adjustmentImprove stabilityResource allocationSoftware testing/debuggingComputer hardwareRelease time
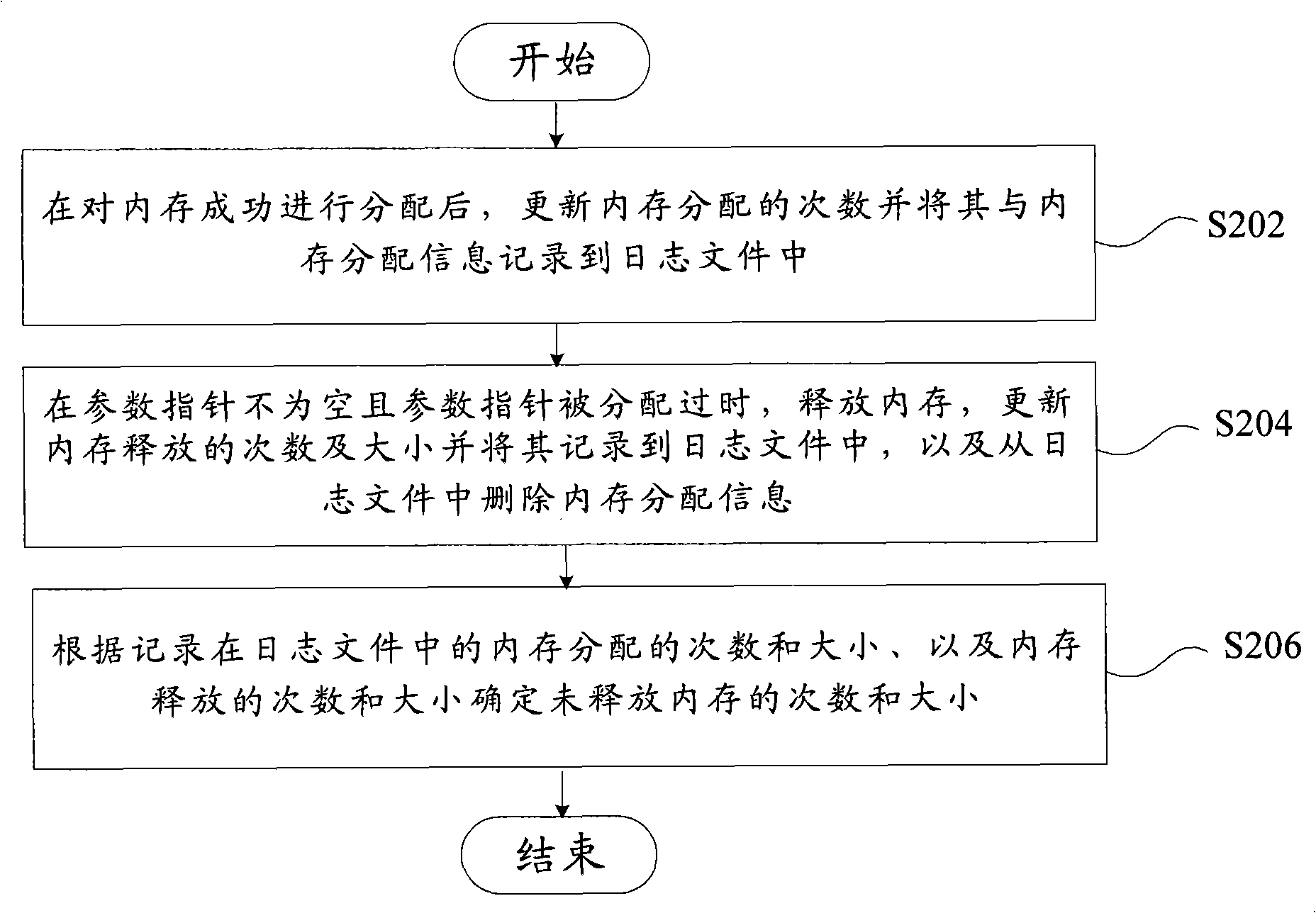
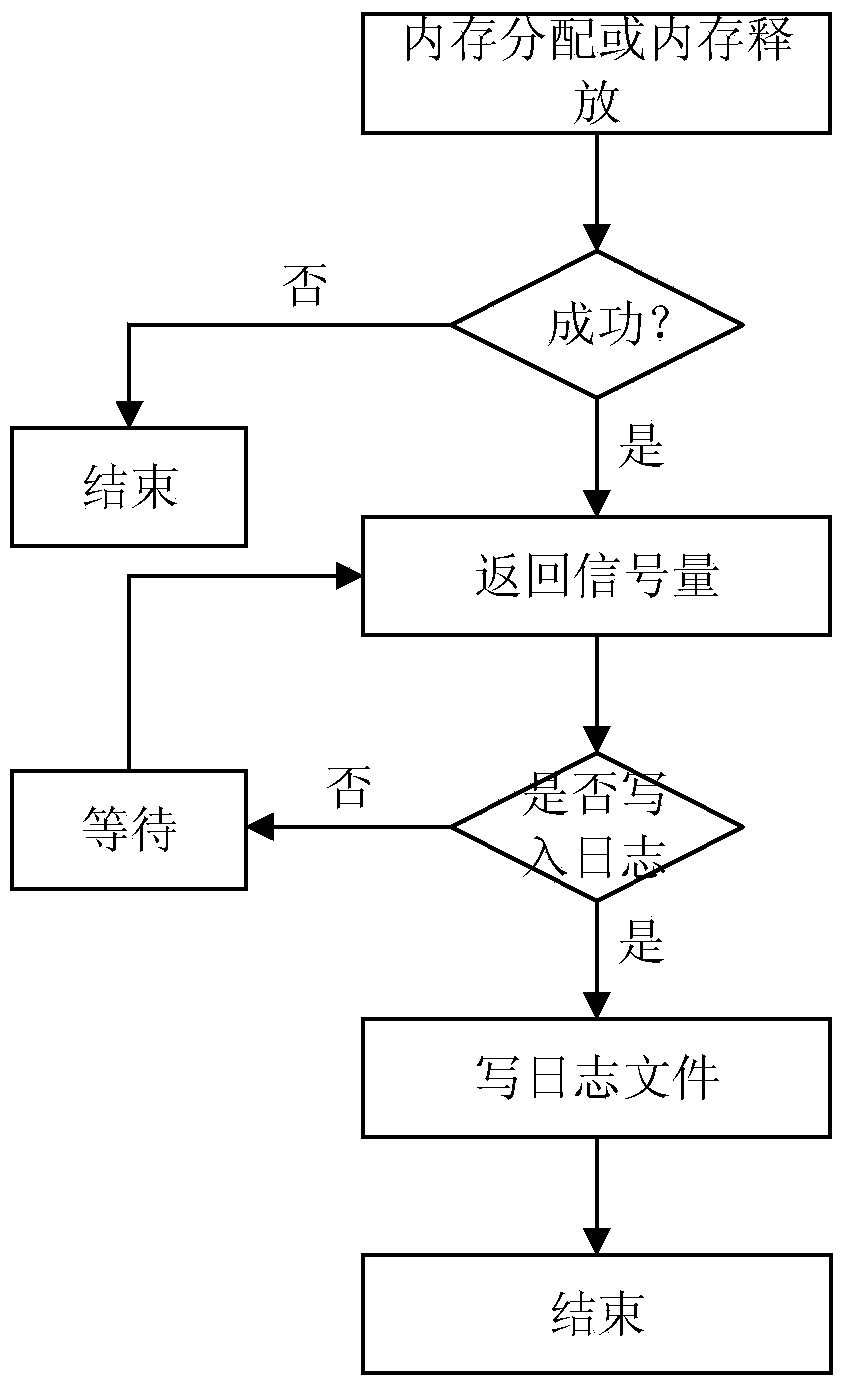
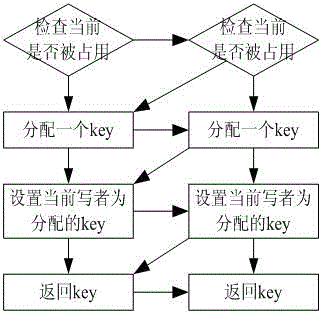
The invention discloses a device and a method for detecting memory leak. The method comprises the following steps: step S202, after a memory is successfully distributed, updating memory distribution times and recording the memory distribution times and memory distribution information into a log file; step S204, when a parameter pointer is not idle and has been distributed, releasing the memory, updating memory releasing times and size, recording the times and the size into the log file, and deleting the memory distribution information from the log file; and step S206, according to the memory distribution times and the size and the memory releasing times and the size in the log file, determining the times and size of the memory not released. The method can count memory using information, detect incorrect memory release and detect memory leak information, and is quite convenient for a programmer to adjust programs so as to enhance the stability of the programs.
Owner:ZTE CORP
Memory leak detecting method and device
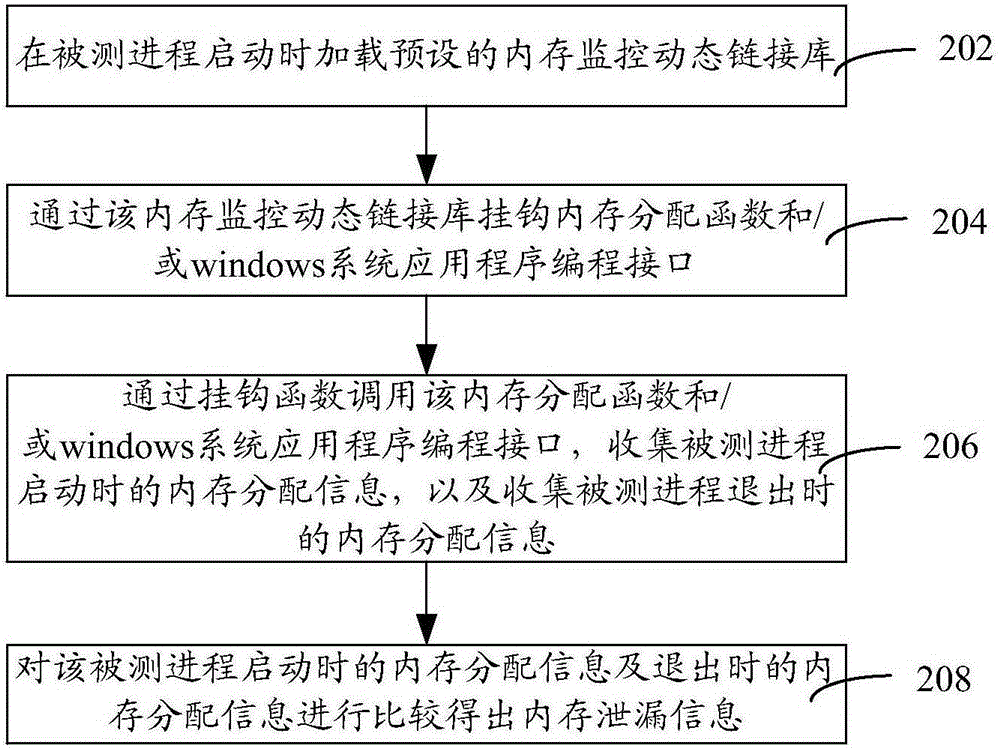
ActiveCN106610892AAccurate timeComprehensive dataMemory adressing/allocation/relocationSoftware testing/debuggingApplication programming interfaceMemory leak detection
The invention relates to a memory leak detecting method and device. The method comprises the following steps: loading a preset memory monitoring dynamic link library when a detected process is started; hooking a memory allocation function and / or a windows system application programming interface via the memory monitoring dynamic link library; calling the memory allocation function and / or the windows system application programming interface via a hook function, acquiring memory allocation information when the detected process is started, and acquiring memory allocation information when the detected process exits; and comparing the memory allocation information when the detected process is started with the memory allocation information when the detected process exits to obtain memory leak information. By adopting the memory leak detecting method and device, the memory allocation information of the detected process in the whole process from start to exit, so the monitoring time is accurate, the obtained data is comprehensive, the statistical result is not released all the time, and the obtained memory leak information is more accurate.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Test executive which provides heap validity checking and memory leak detection for user code modules
ActiveUS20060143537A1Improve executionImprove execution performanceError detection/correctionCode moduleTest execution
A system and method for automatically detecting heap corruption errors and memory leak errors caused by user-supplied code modules that are called by steps of a test executive sequence. The test executive sequence may first be created by including a plurality of test executive steps in the test executive sequence and configuring at least a subset of the steps to call user-supplied code modules. The test executive sequence may then be executed on a host computer under control of a test executive engine. For each step that calls a user-supplied code module, the test executive engine may perform certain actions to automatically detect whether the user-supplied code module causes a heap corruption error and / or automatically detect whether the user-supplied code module causes a memory leak error.
Owner:NATIONAL INSTRUMENTS
Memory leak detection
InactiveUS7827538B2Non-redundant fault processingSpecific program execution arrangementsParallel computingComputerized system
A memory leak detection scheme for use in a computer system (e.g., Java) by: finding an allocation site (410) which is responsible for allocating objects which accumulate in a memory heap (400); and monitoring memory activity related to the found allocation site to discover a memory leak related thereto. The technique can be entirely application independent and can be made fully automatic, running as a daemon process on a machine and detecting leakage in a number of client processes simultaneously.
Owner:LINKEDIN
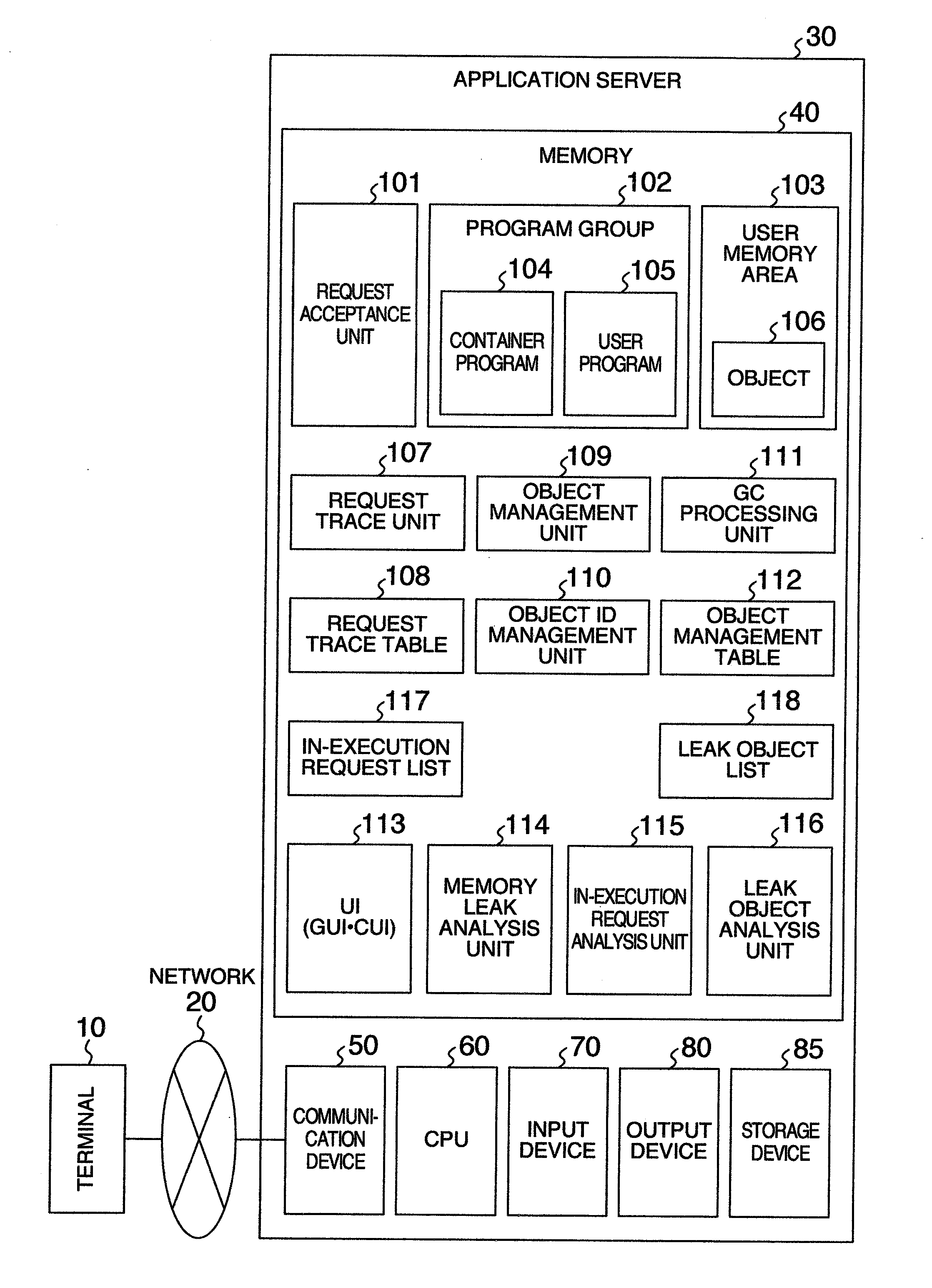
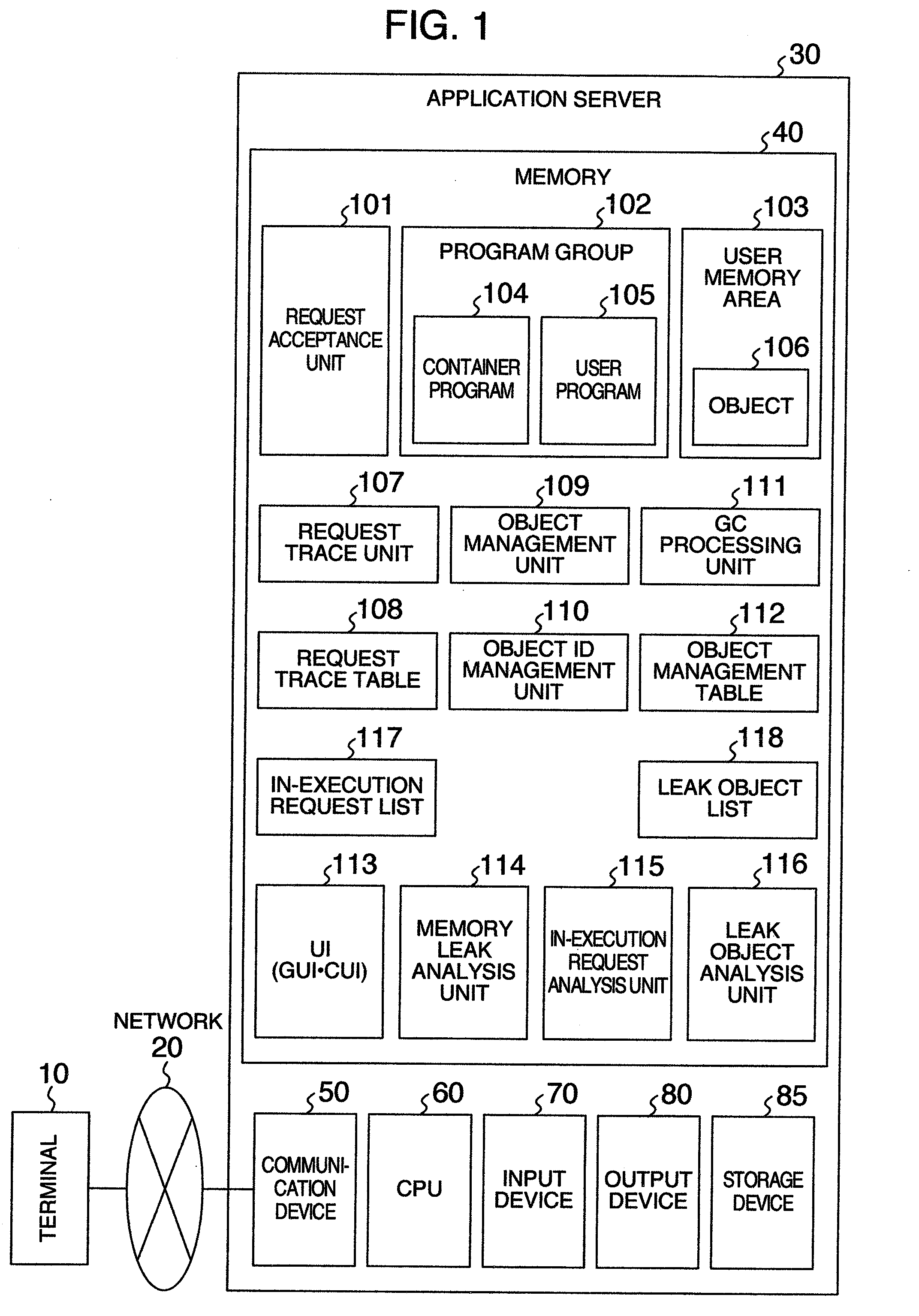
Memory leak detecting method, memory leak detecting device and memory leak detecting program
InactiveUS20080127212A1Easy to specifyMemory architecture accessing/allocationNon-redundant fault processingMemory leak detectionComputer science
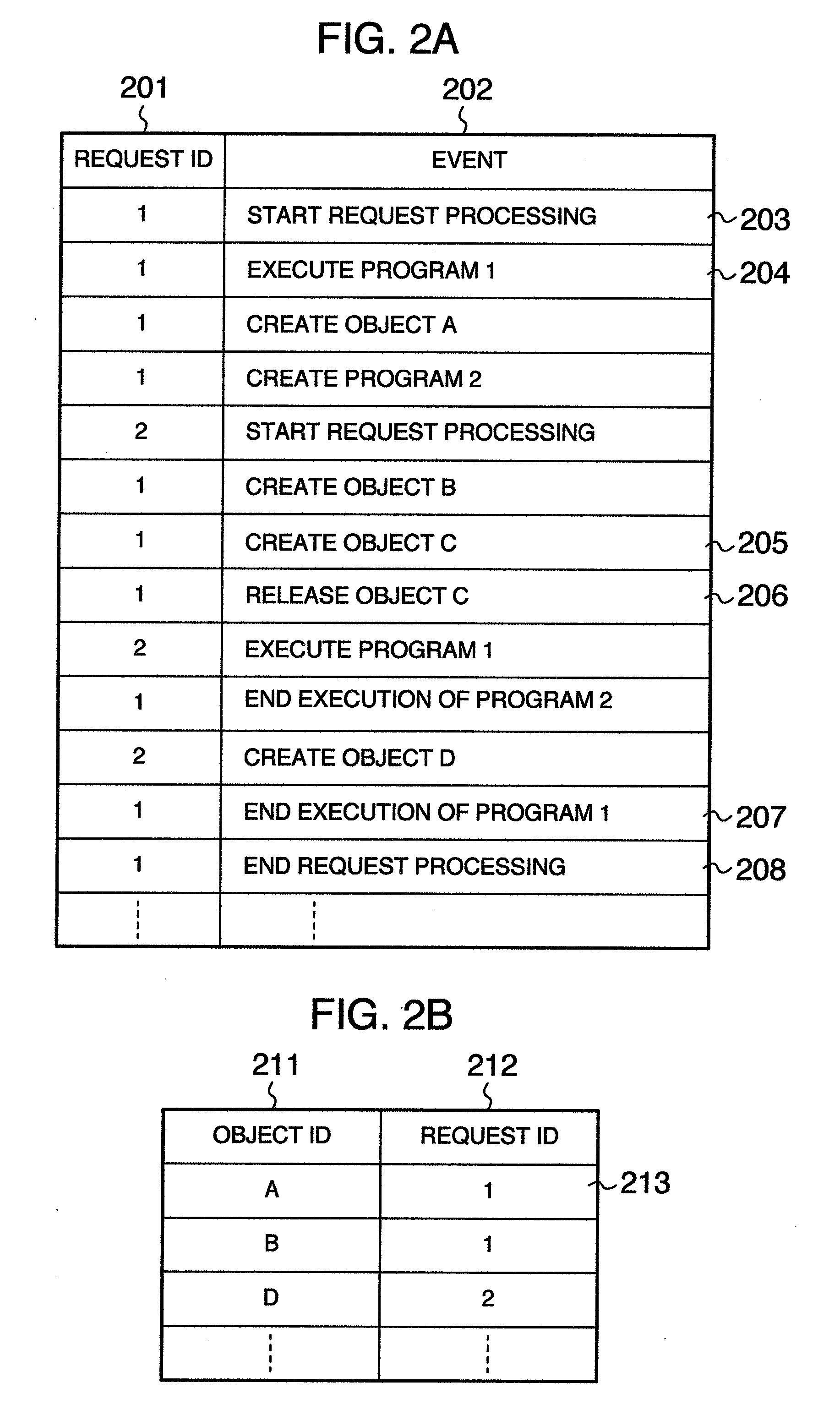
A memory leak detecting method includes steps of corresponding an accepted request with an identifier to be specified to the accepted request to store a history of an executed processing in request trace information; deleting correspondence information of the accepted request and an object to be created when the object is created in the processing of the accepted request and corresponding information of the request and object when trace information of an object creation is recorded and a use of the created object is ended; recording trace information of an object release; acquiring a list of the requests in execution from the request trace information in accepting an instruction for detecting a memory leak; and detecting an object corresponding to the request as a suspicion of memory leak, in which the object corresponding the request is not included in the request list and is included in the correspondence information.
Owner:HITACHI LTD
Method, system, and computer program product for light weight memory leak detection
InactiveUS20060277440A1Enable leak detectionData processing applicationsError detection/correctionParallel computingWaste collection
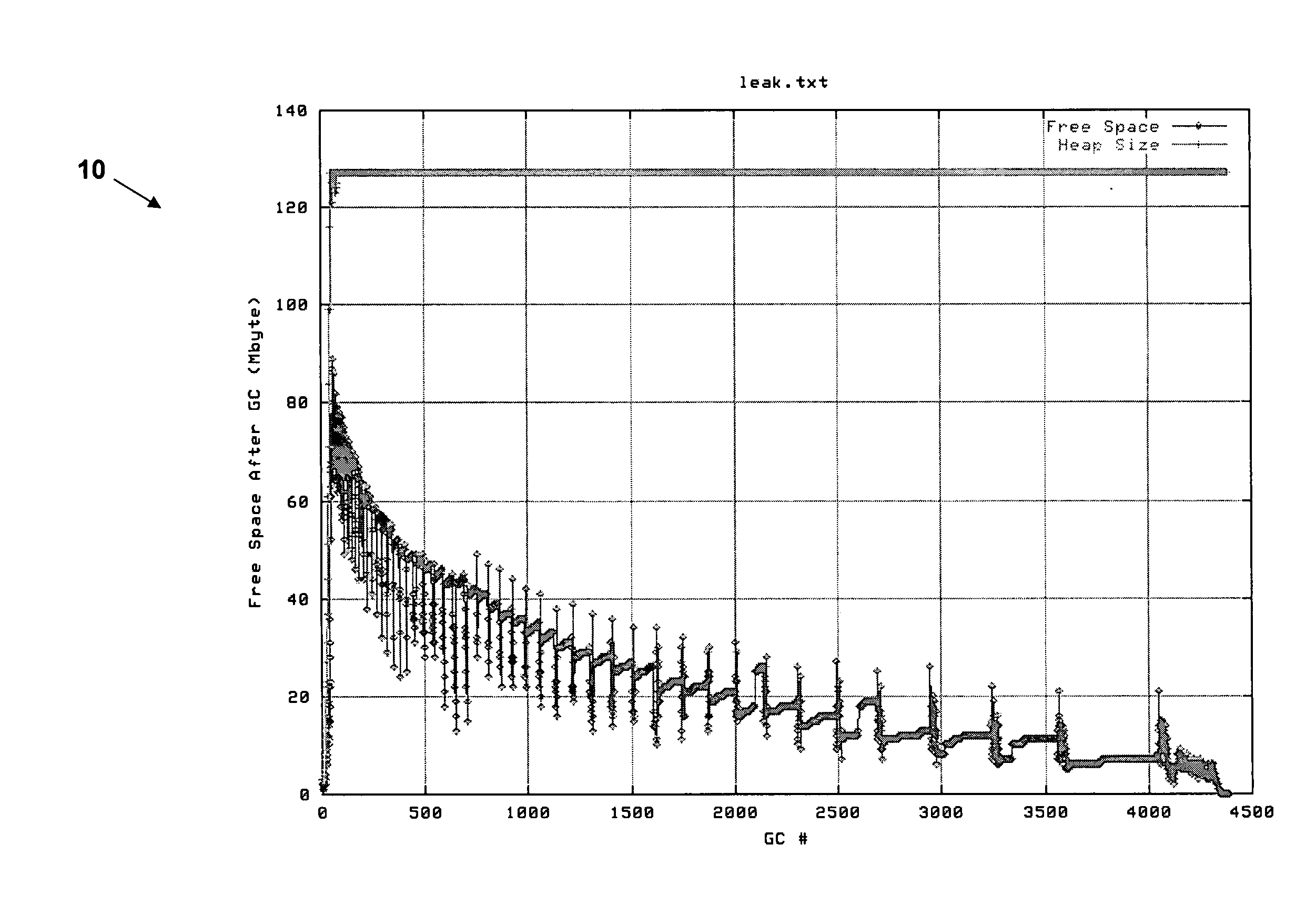
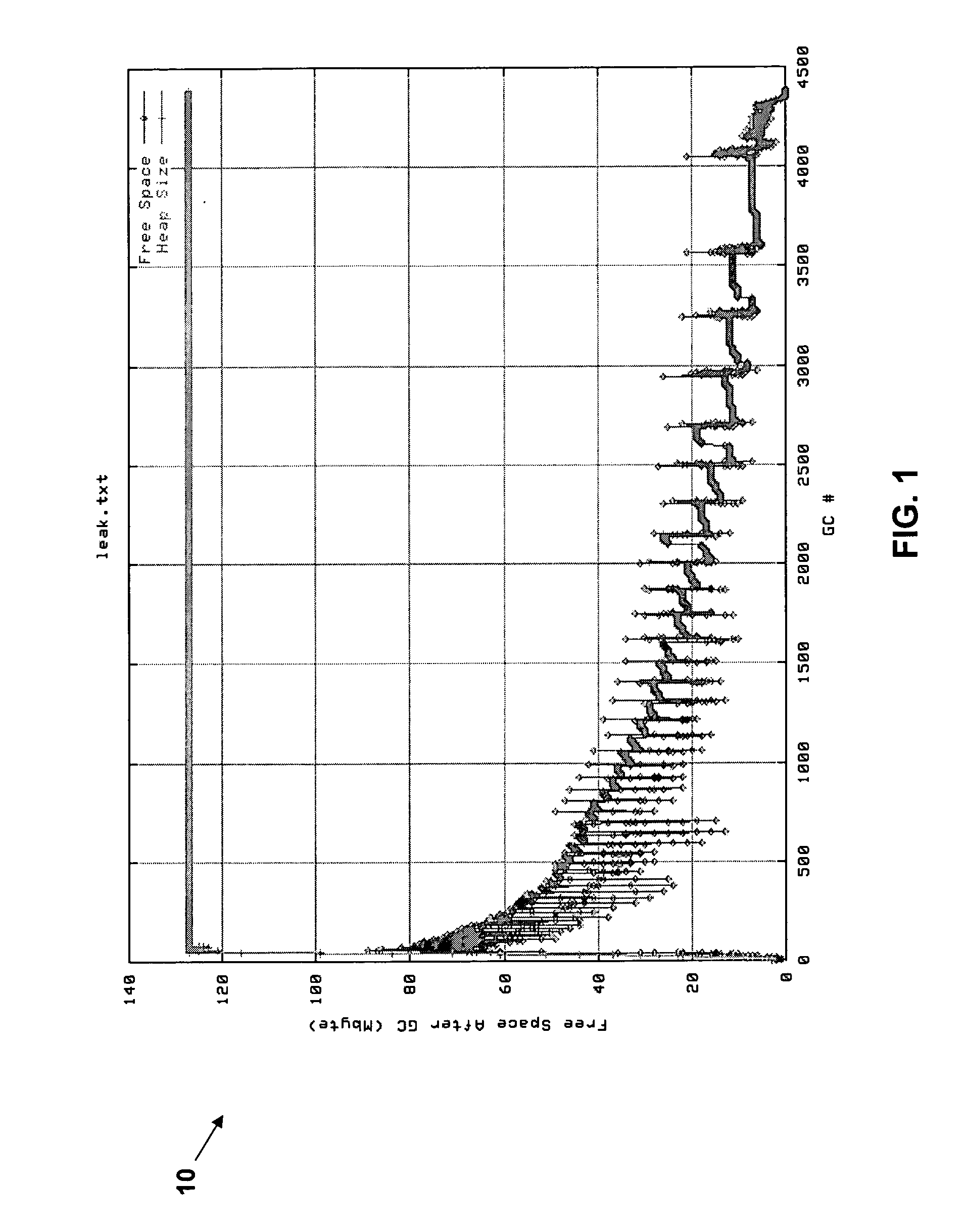
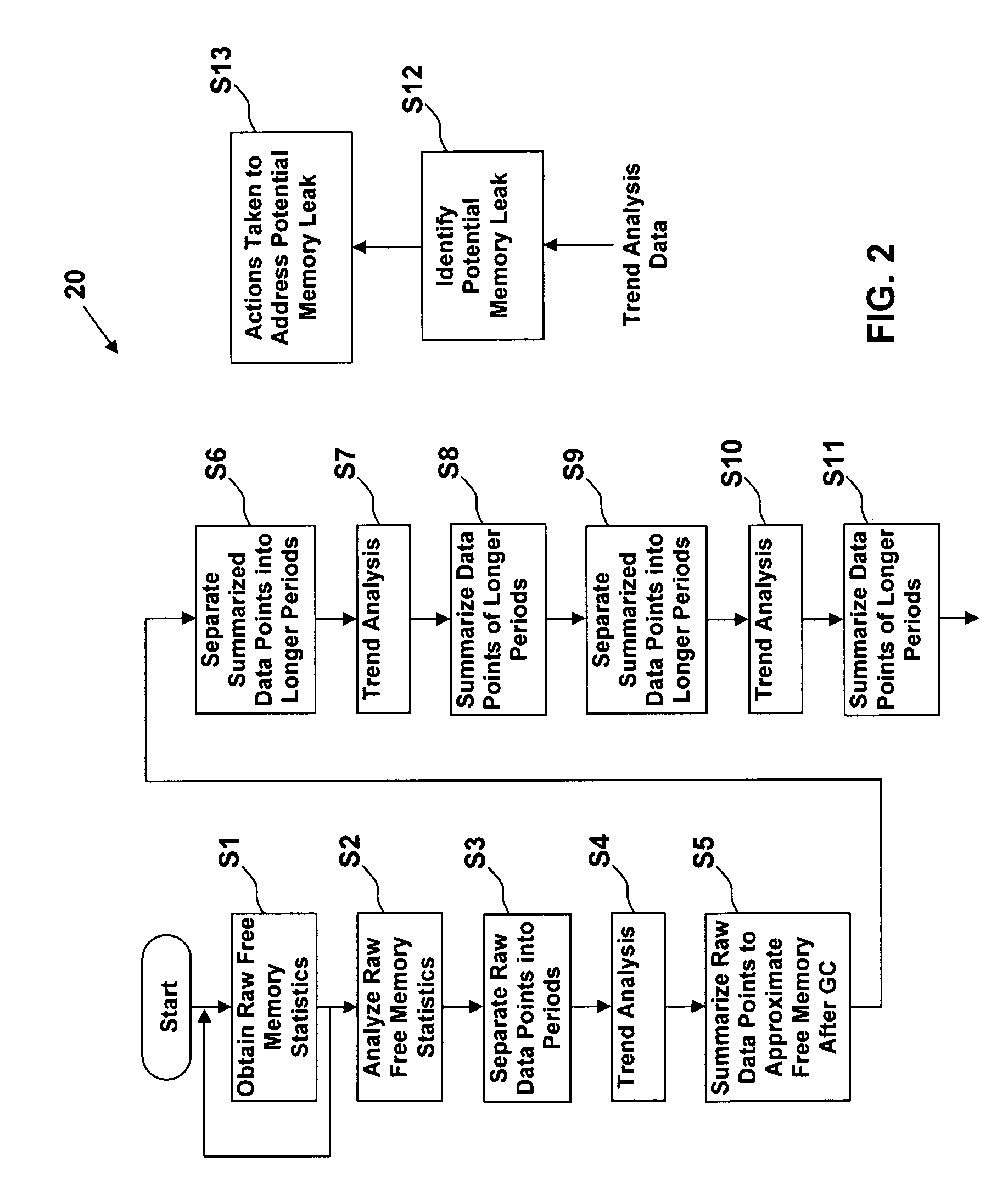
The present invention provides a method, system, and computer program product for light weight memory leak detection. A method in accordance with an embodiment of the present invention comprises: obtaining raw free memory statistics; approximating free memory after garbage collection from the raw free memory statistics; and analyzing the approximated free memory after garbage collection to identify a potential memory leak. A method in accordance with another embodiment of the present invention comprises the steps of: obtaining raw free memory statistics; generating a vector of memory leak indicators from the raw free memory statistics; comparing the vector of memory leak indicators against a plurality of vectors of the same memory leak indicators for known memory leak scenarios; and identifying a potential memory leak based on the comparison.
Owner:IBM CORP
Memory leak detection during dynamic memory allocation
ActiveUS20110145536A1Error detection/correctionMemory adressing/allocation/relocationDynamic storageMemory leak detection
A method to detect memory leaks during dynamic memory allocation comprises generating statistical information regarding allocated chunks in a memory heap during a dynamic memory allocation process, with the statistical information including same-sized chunk information related to the number of allocated chunks being identical in size. The statistical information is monitored to identify a potential memory leak based at least in part on the same-sized chunk information, in response to which an alert signal is generated.
Owner:SAP AG
Memory leak detection device and method and terminal
InactiveCN105204996AImprove accuracySoftware testing/debuggingComputer terminalMemory leak detection
The invention discloses a memory leak detection device. The device comprises a collection module used for collecting memory sampling information of a detected progress, a generation module used for generating the change trend of the memory occupation value of the detected progress, and a detection module used for judging whether memory leak happens to the detected progress or not according to the change trend of the memory occupation value of the detected progress. The memory sampling information includes the sampling time and the memory occupation value, at the sampling time, of the detected progress. The invention further discloses a memory leak detection method and a terminal. By means of the memory leak detection device and method and the terminal, the memory leak detection accuracy can be improved.
Owner:NUBIA TECHNOLOGY CO LTD
Dynamic internal memory leakage detecting method and device based on VxWorks operation system
ActiveCN103455424AImplement trackingImprove error detection efficiencyMemory adressing/allocation/relocationSoftware testing/debuggingInternal memoryOperational system
The invention discloses a dynamic internal memory leakage detecting method and device based on a VxWorks operation system, relates to dynamic internal memory leakage detecting methods and devices, and aims to solve the problem that current dynamic internal memory leakage detection is low in error detection efficiency and low in speed. The method includes: modifying an internal memory distribution function malloc () and an internal memory release function free () to obtain a function LC_malloc () and a function LC_free (), and recording distribution and releasing information in a form of log to realize dynamic internal memory tracking; using a data transmitting buffer queue to upload the log information from an industrial personal computer with the VxWorks operation system to an upper computer; in the upper machine, reading log events from the log files, comparing internal memory distribution and releasing, and analyzing and detecting internal memory leakage from the log files. The method is suitable for dynamic internal memory leakage detection.
Owner:HARBIN INST OF TECH
Memory leak detection method facing Xen environment during operation and implement system thereof
ActiveCN103064784ANo loss of efficiencyEfficient detectionSoftware testing/debuggingOperational systemParallel computing
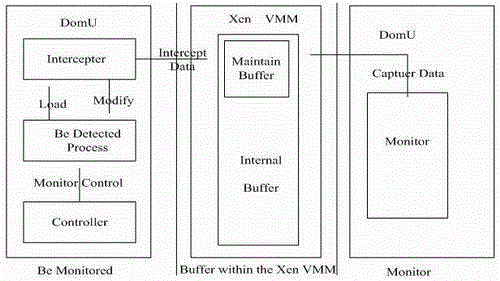
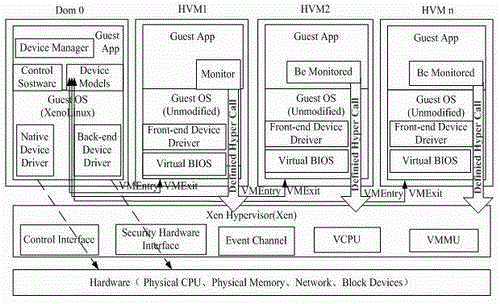
The invention relates to a method and system for detecting memory leak facing Xen virtualization environment during operation. The method for memory leak under Xen virtualization calculating environment during operation is provided. The method mainly includes: (1) performing dynamic analysis on memory usage action of a monitored program, grouping memory objects, and maintaining and updating related information on the memory objects; (2) detecting potential memory leak based on objected behavior characteristics; (3) and performing memory leak judgment according to related rules. Compared with the prior art, the method and system can detect the memory leak during operation in cross-operating system platform and cross-language development environment mode, is wide in application range, has good performance, can improve quality and development efficiency of a software development industry especially software products with limited memory, shortens period of software development, saves development cost directly, and can bring good economic benefit and social benefit.
Owner:FUJIAN NORMAL UNIV
Application memory leakage detection method and device, electronic equipment and storage medium
PendingCN109558308AImprove experiencePrecise positioningResource allocationSoftware testing/debuggingSecurity monitoringMemory leak detection
The invention discloses an application program memory leakage detection method. The method comprises the following steps of creating a weak reference monitor for each application program; when an application program runs, monitoring an Activity object of the corresponding application program through the weak reference monitor; packaging the Activity object as a weak reference object; detecting whether the weak reference of the Activity object exists or not; when it is determined that the weak reference of the Activity object exists, triggering a garbage collection mechanism, and marking the Activity object; detecting whether the Activity object is recovered or not; when it is detected that the Activity object is not recovered, obtaining a memory snapshot file of the application program; and analyzing memory leakage according to the memory snapshot file, generating an analysis report and reporting the analysis report. The invention further provides an application program memory leak detection device, electronic equipment and a storage medium. The invention belongs to the technical field of security monitoring, can accurately and quickly locate the memory leakage problem of an application program, and improves the efficiency and accuracy of application program memory optimization.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
Memory leak detection
ActiveUS20050240747A1Memory adressing/allocation/relocationSpecific program execution arrangementsComputer hardwareTerm memory
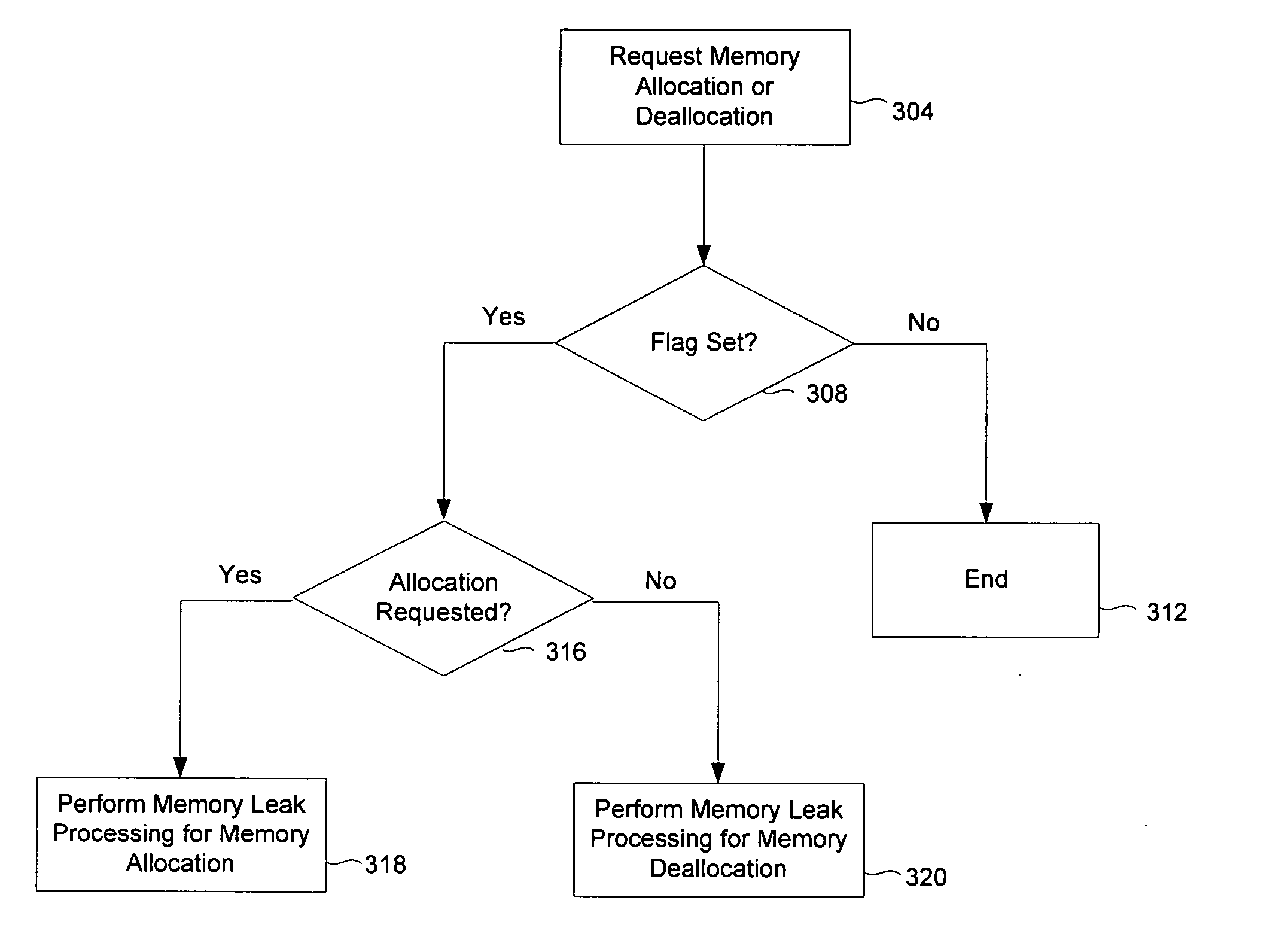
A technique is disclosed for detecting a memory leak. A request to allocate or deallocate memory is received. In a memory leak table that is bounded in size, an entry that is associated with a call path with which the request is associated is accessed. The entry in the memory leak table is updated.
Owner:ALCATEL IP NETWORKS
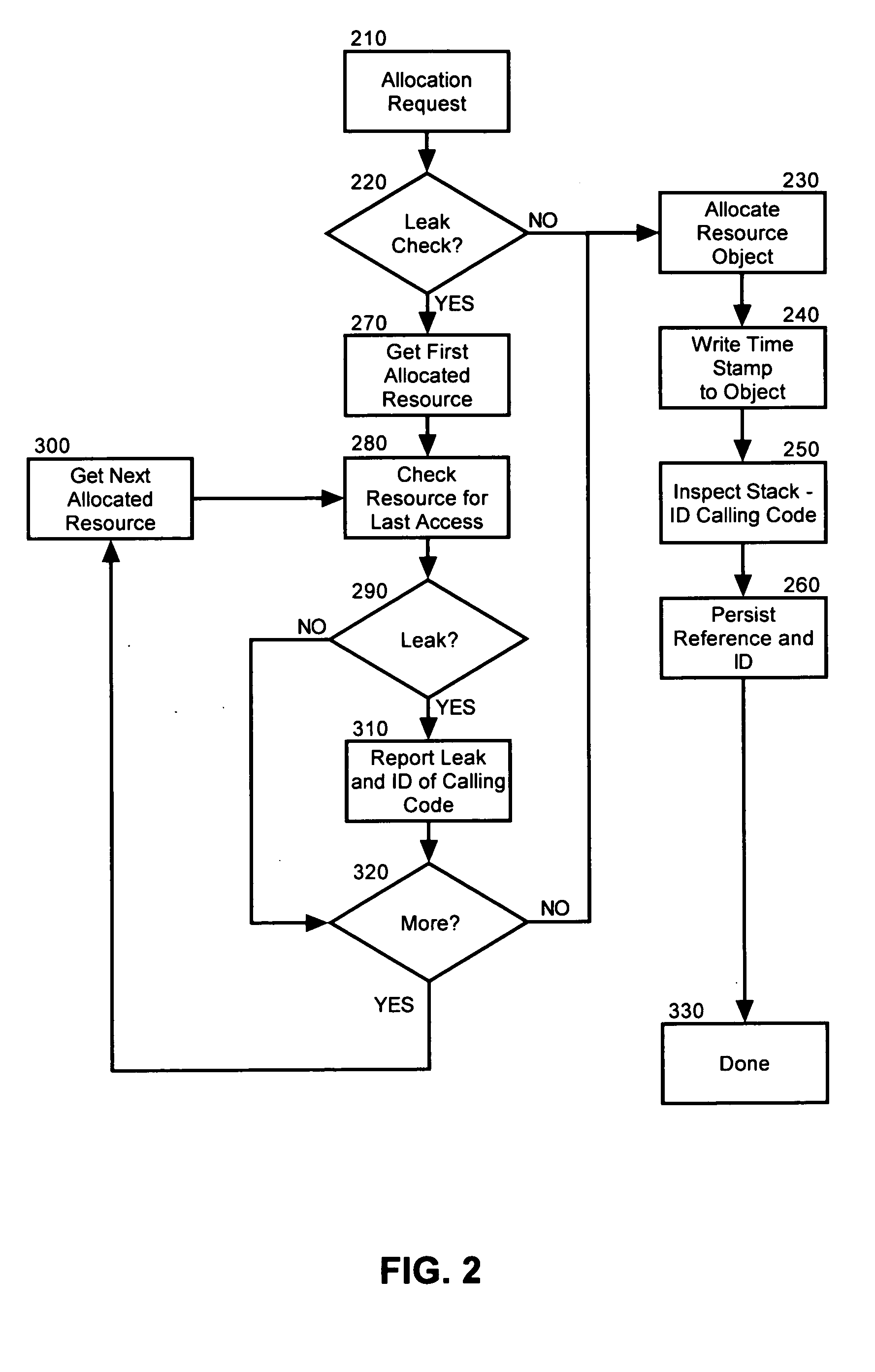
Fast detection of the origins of memory leaks when using pooled resources
InactiveUS20050114843A1Resource allocationSpecific program execution arrangementsResource poolCall stack
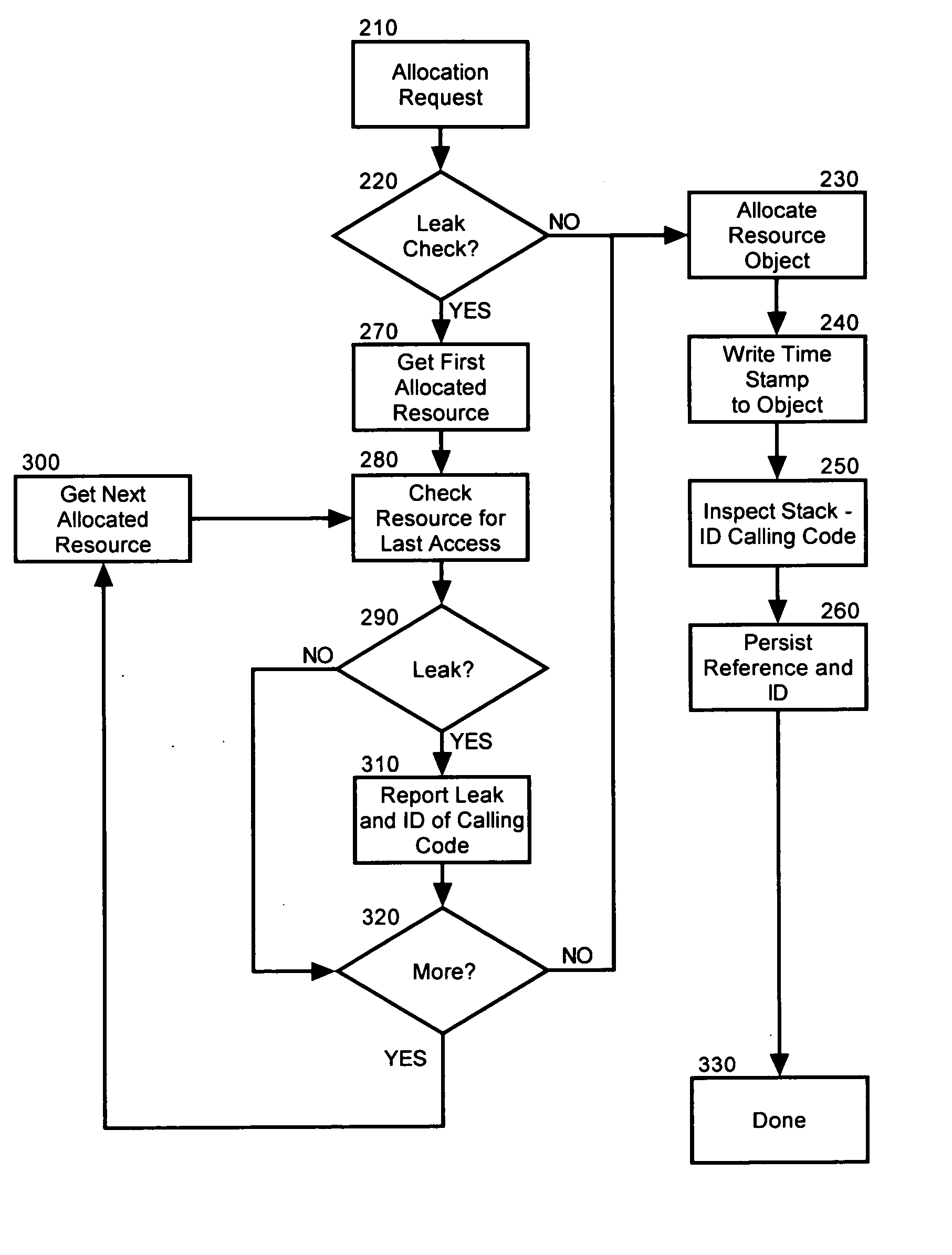
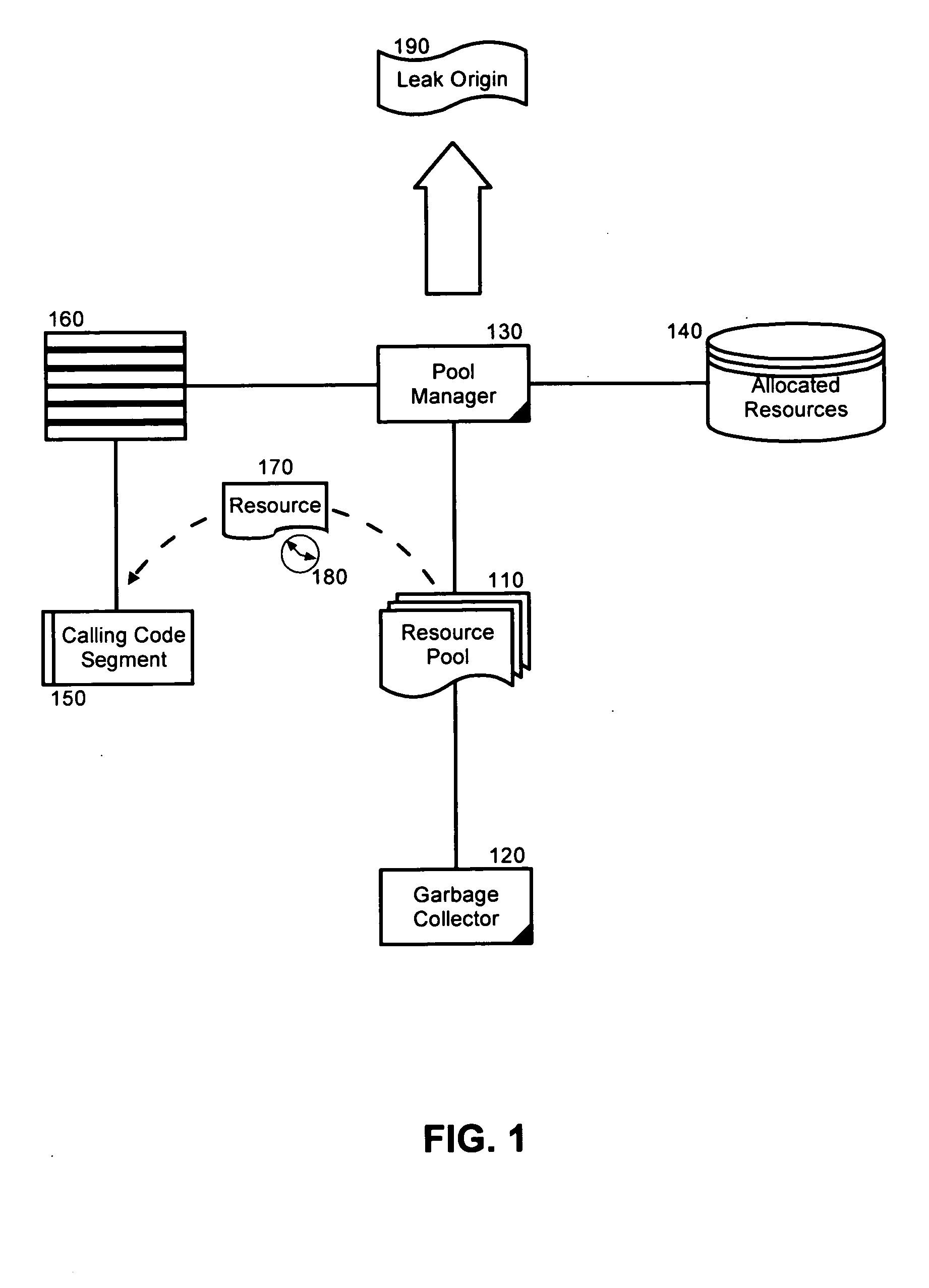
The present invention is a method, system and apparatus for memory leak detection and reporting. In a preferred method of the invention, allocated ones of resources in a resource pool can be time stamped upon allocation and calling code segments receiving the allocated resources can be identified. Memory leaks can be detected by inspecting individual timestamps for the allocated resources to determine whether the allocated resources have become overly idle. Notably, the identifying step can include the step of retrieving identities for individual ones of the calling code segments from an associated calling stack when the individual ones of the calling code segments acquire one of the allocated resources. In any case, for each allocated resource determined to have become overly idle, an identity of a corresponding one of the calling code segments can be reported.
Owner:LINKEDIN
System and method for memory leak detection
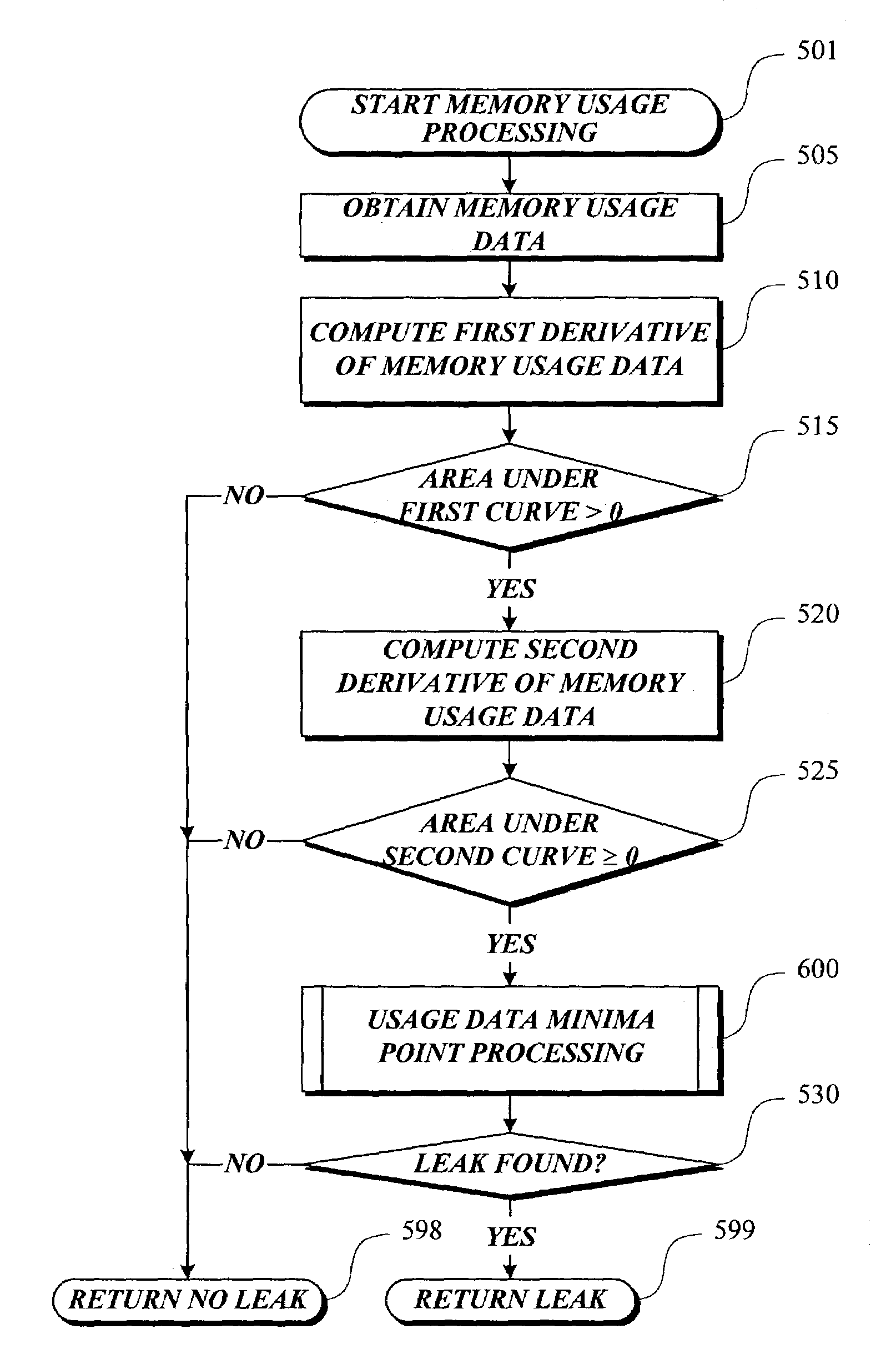
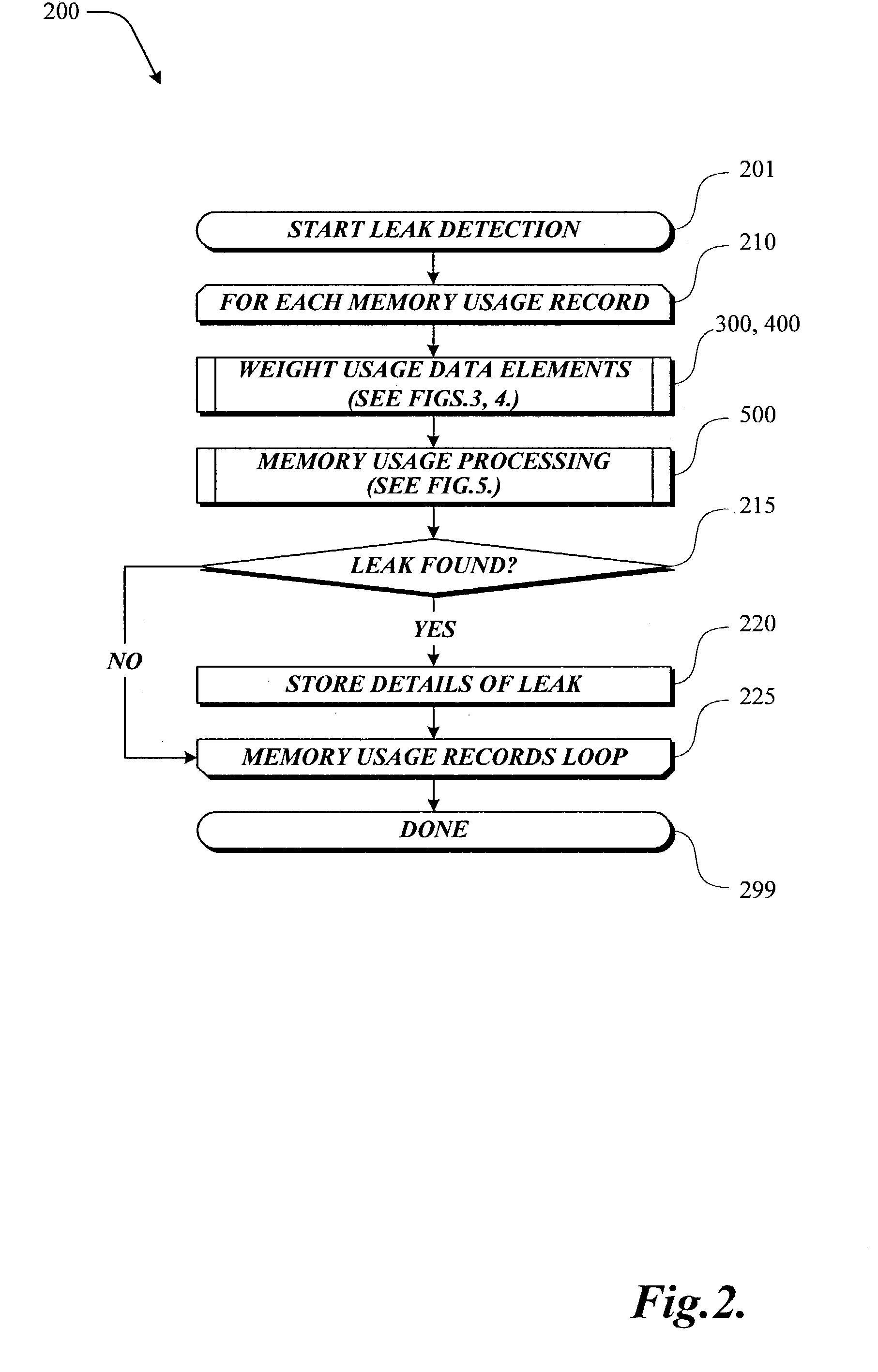
InactiveUS7089460B2Reduce the impactAccumulate usage dataData processing applicationsNon-redundant fault processingComputer hardwareComputer memory
The present invention is directed to detecting leaks in computer memory. Memory leaks are detected by analyzing computer component memory usage records. The first derivative of the memory usage data is computed. If the area under a curve created by a plot of the first derivative of the memory usage data is greater than zero, the second derivative of the memory usage data is computed. If the area under a curve created by a plot of the second derivative of the memory usage data also is greater than or equal to zero, the memory usage data is analyzed to determine how many minima points are present in the memory usage data. If less than four memory usage data minima points are present, a memory leak exists. If four or more minima points are present in the memory usage data, the minima points are further processed to determine if a memory leak exists.
Owner:MICROSOFT TECH LICENSING LLC
Method for detecting memory leakage of heap operational program
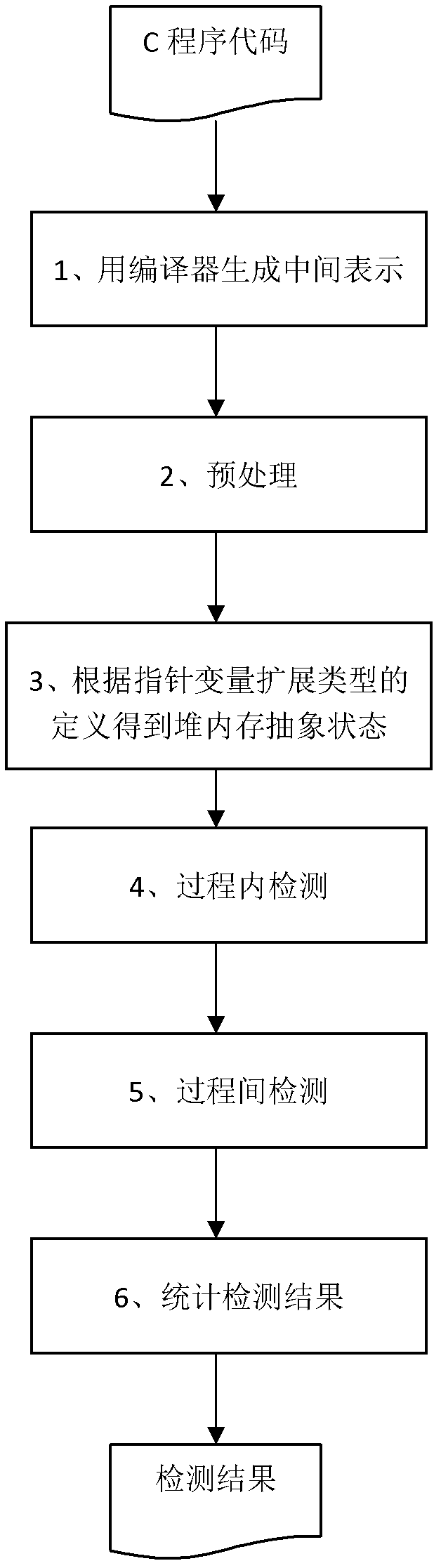
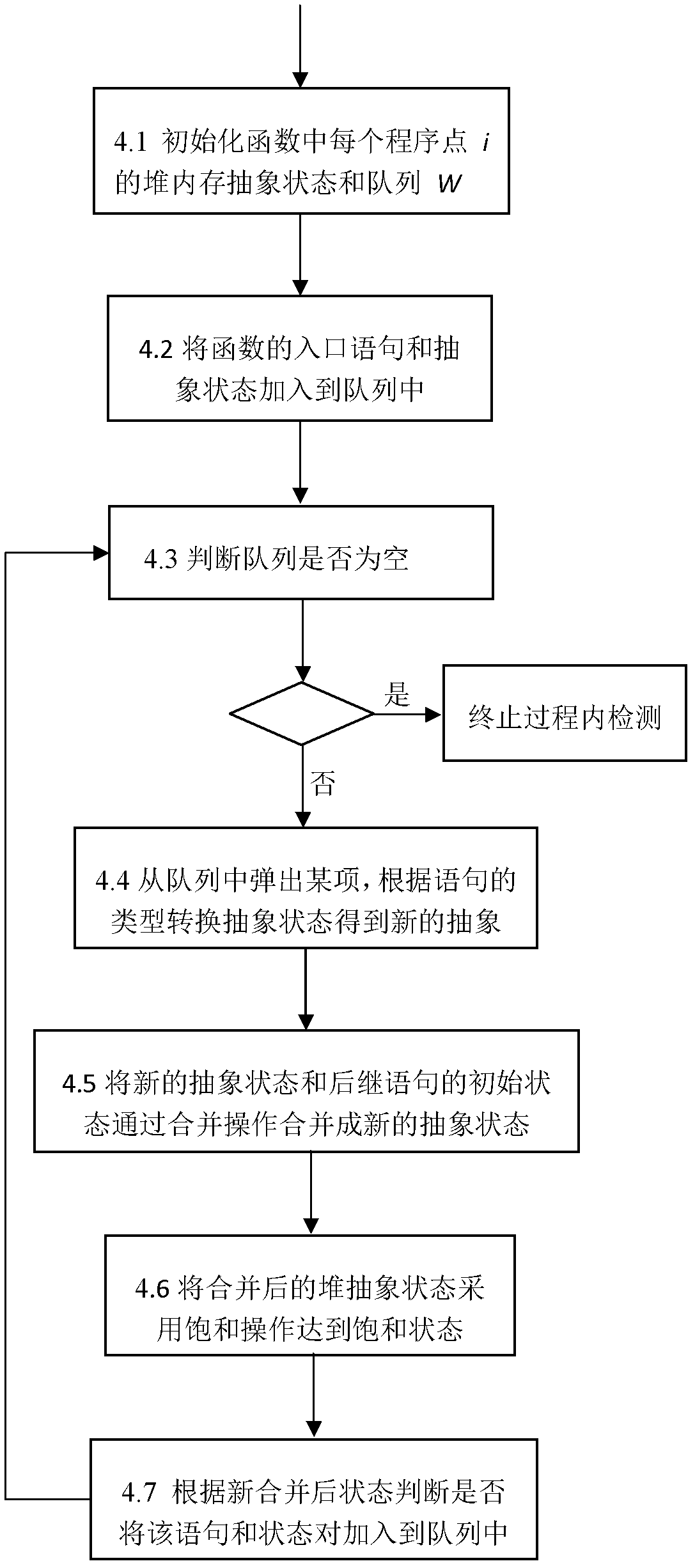
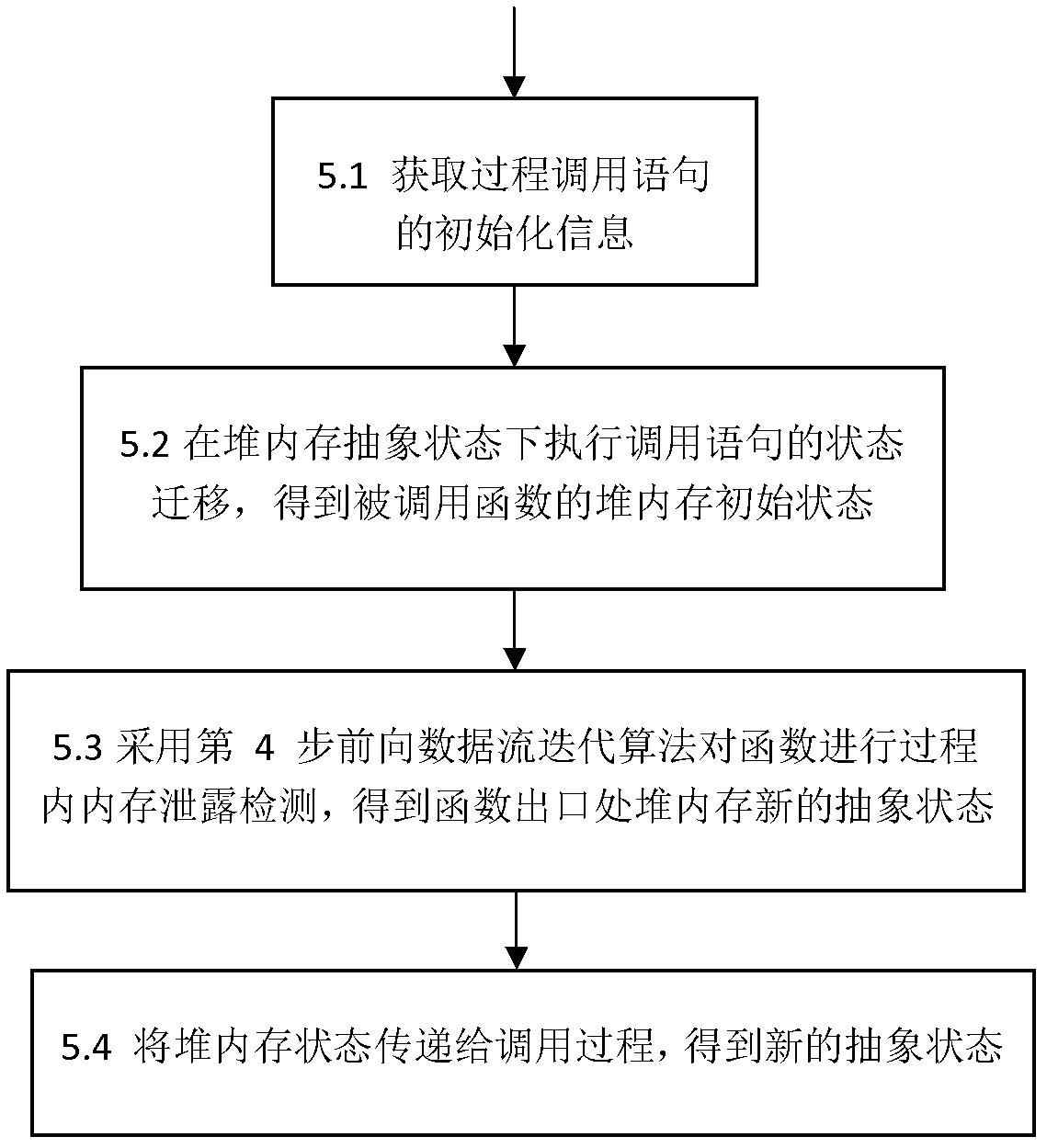
ActiveCN102662825ATaking into account efficiencyImprove balanceSoftware testing/debuggingSource codeMemory leak detection
The present invention discloses a method for detecting the memory leakage of a heap operational program, is directed to solving a technical problem of the memory error detection of the heap operational program in terms of precision and efficiency, and provides a novel memory leakage detection method with improved precision and efficiency of the detection. The technical scheme comprises analyzing a source code of the program in terms of statement and morphology at first and generating an intermediate file; carrying out a pretreatment which includes slicing and transformation; obtaining an abstract state of a heap memory based on the definition of an extension type of a pointer variable in the program; employing a forward data flow iteration method to implement an in-process detection and an inter-process detection; and finally inspecting and counting results of the memory leakage detection. The method finds a good equilibrium point between precision and efficiency of a static analysis, accelerates the termination of an iterative algorithm, improves the precision and the efficiency of the detection, and has a strong scalability and a low storage overhead.
Owner:NAT UNIV OF DEFENSE TECH
Memory leakage detection and prevention method
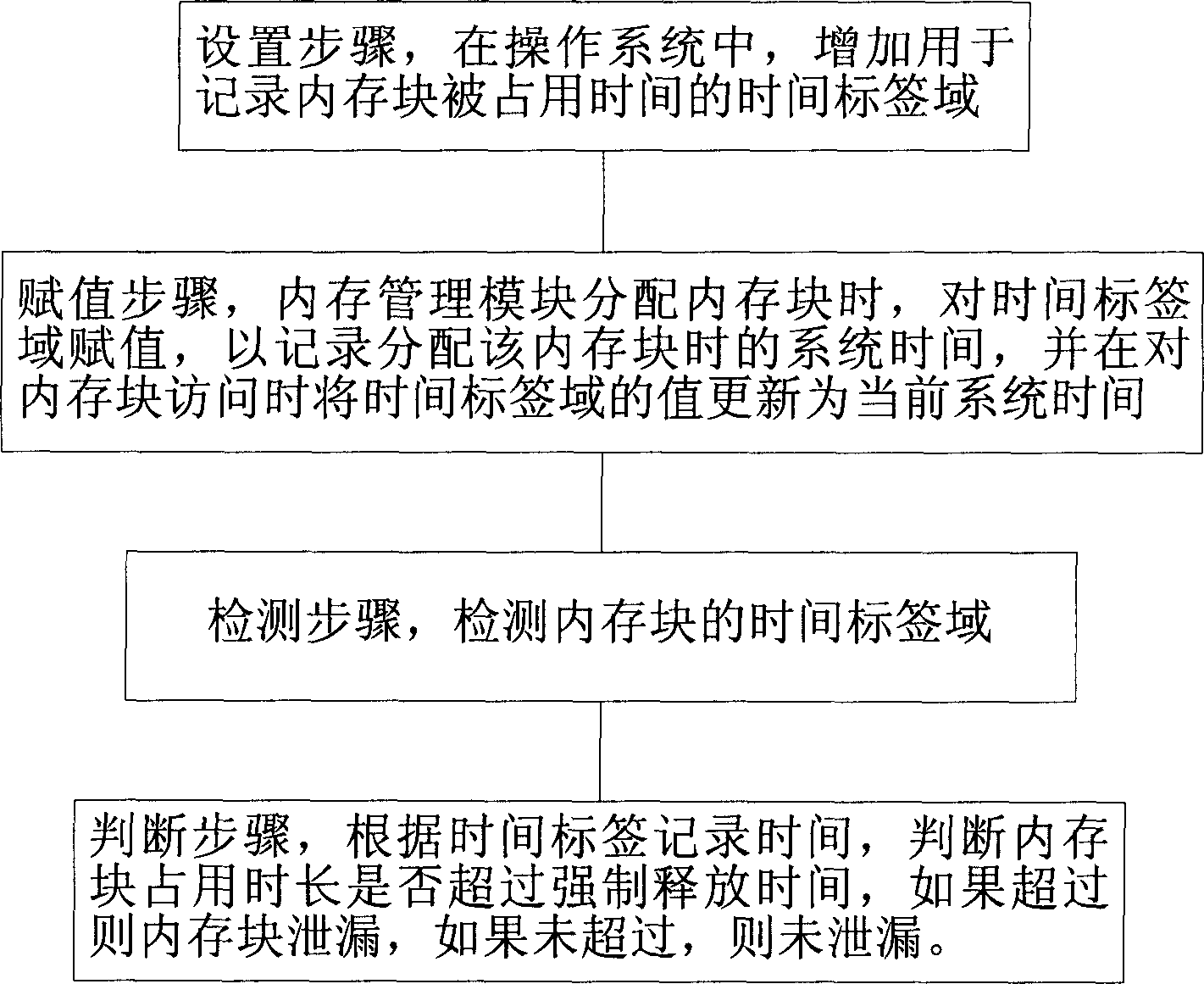
InactiveCN1845080AEasy to check for tightnessPrevent leakageSoftware testing/debuggingMemory leak detectionDistributed memory
The invention relates to a method for detecting and avoiding memory leakage, which comprises: setting step that increasing a time label in the operation system to record the time that memory is occupied; evaluating step that memory manage module evaluates the time label when distributing memory blocks to record the system time that distributing said memory block and refreshing the value of time label into present system time when accessing the memory block; checking step that checking the time label of memory block; judging step that judging if the memory block occupy time is longer than the forced release time according to the time recorded in time label, and if it is longer, the memory block is leaked, or else, the memory block is not leaked. The invention can effectively judge if the memory block should be released, and directly release memory block when the leakage is detected.
Owner:HUAWEI TECH CO LTD
Memory leakage detecting method and device
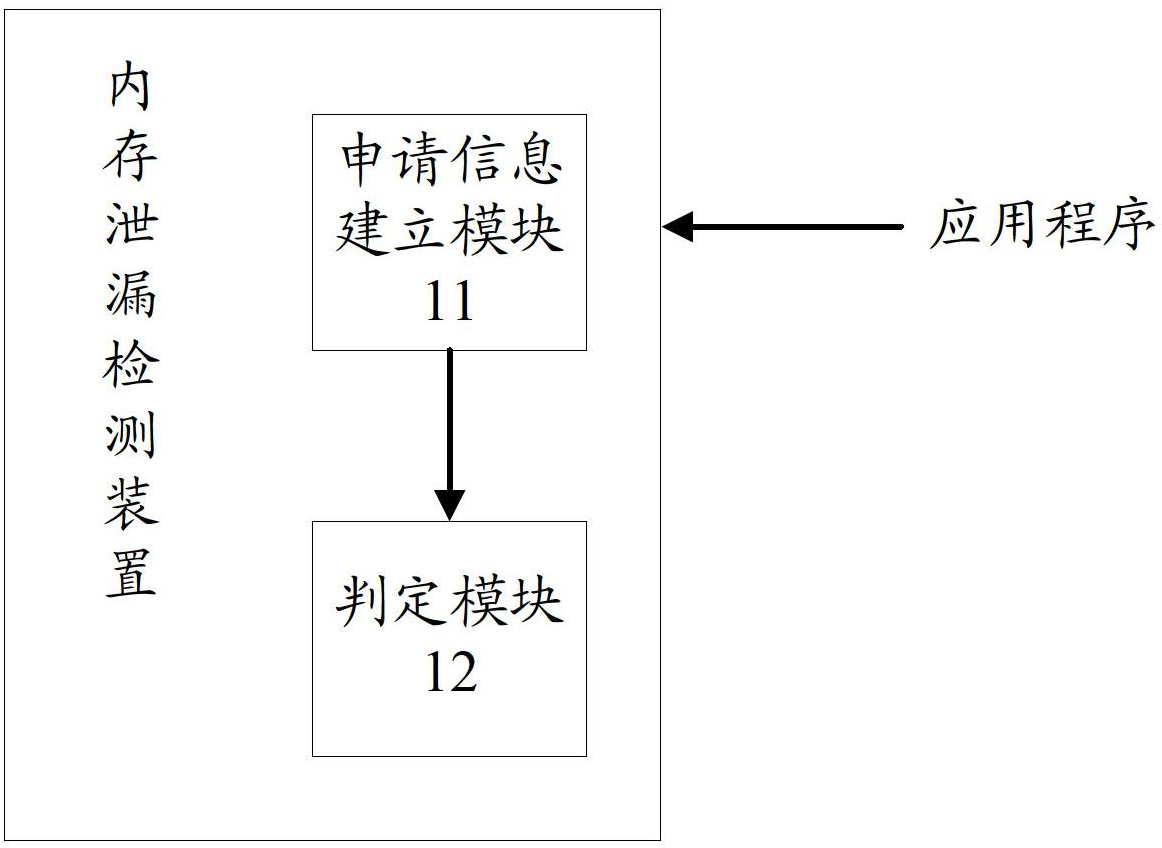
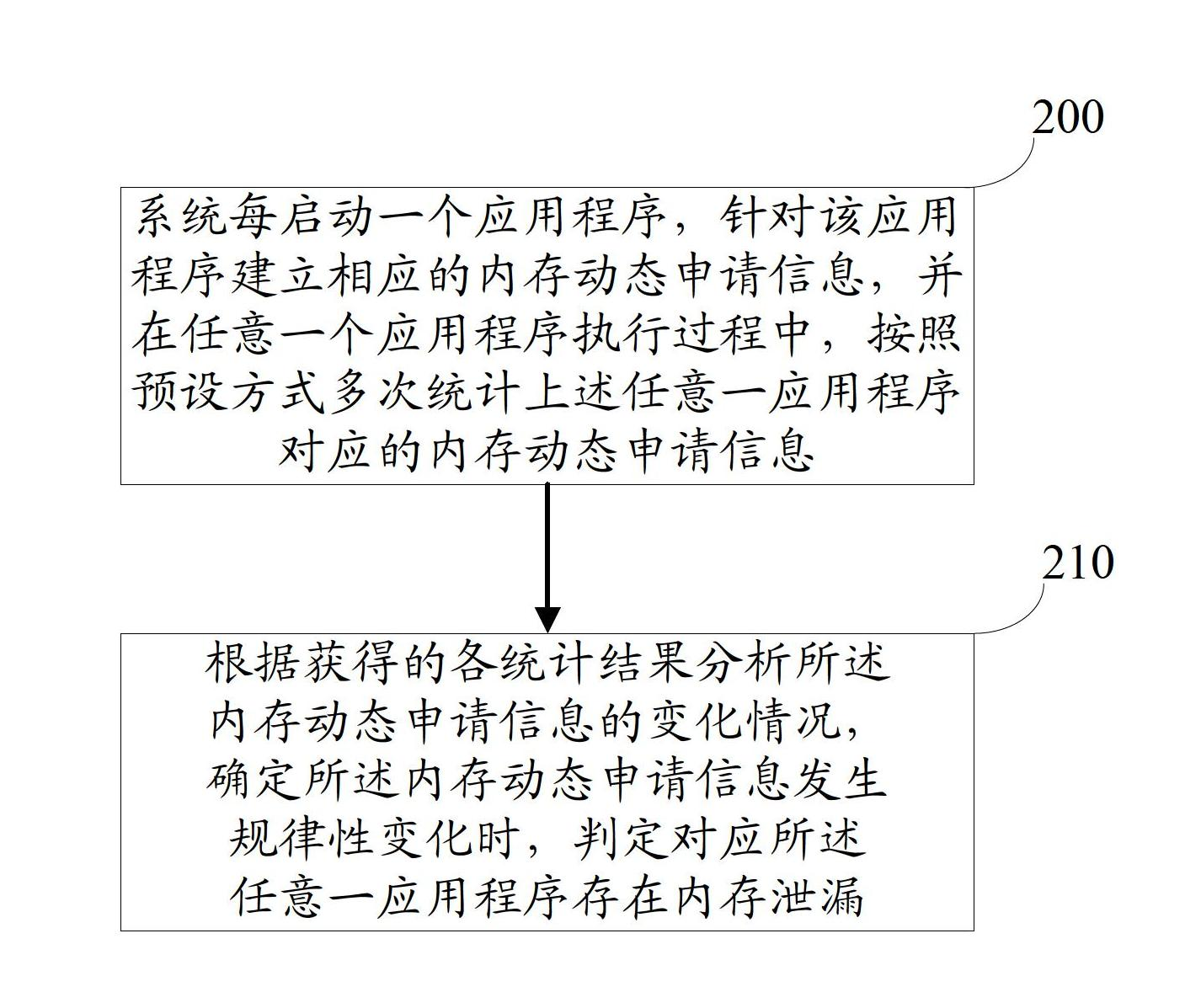
ActiveCN102681938AEasy to judgeEasy to debugSoftware testing/debuggingSystem testingMemory leak detection
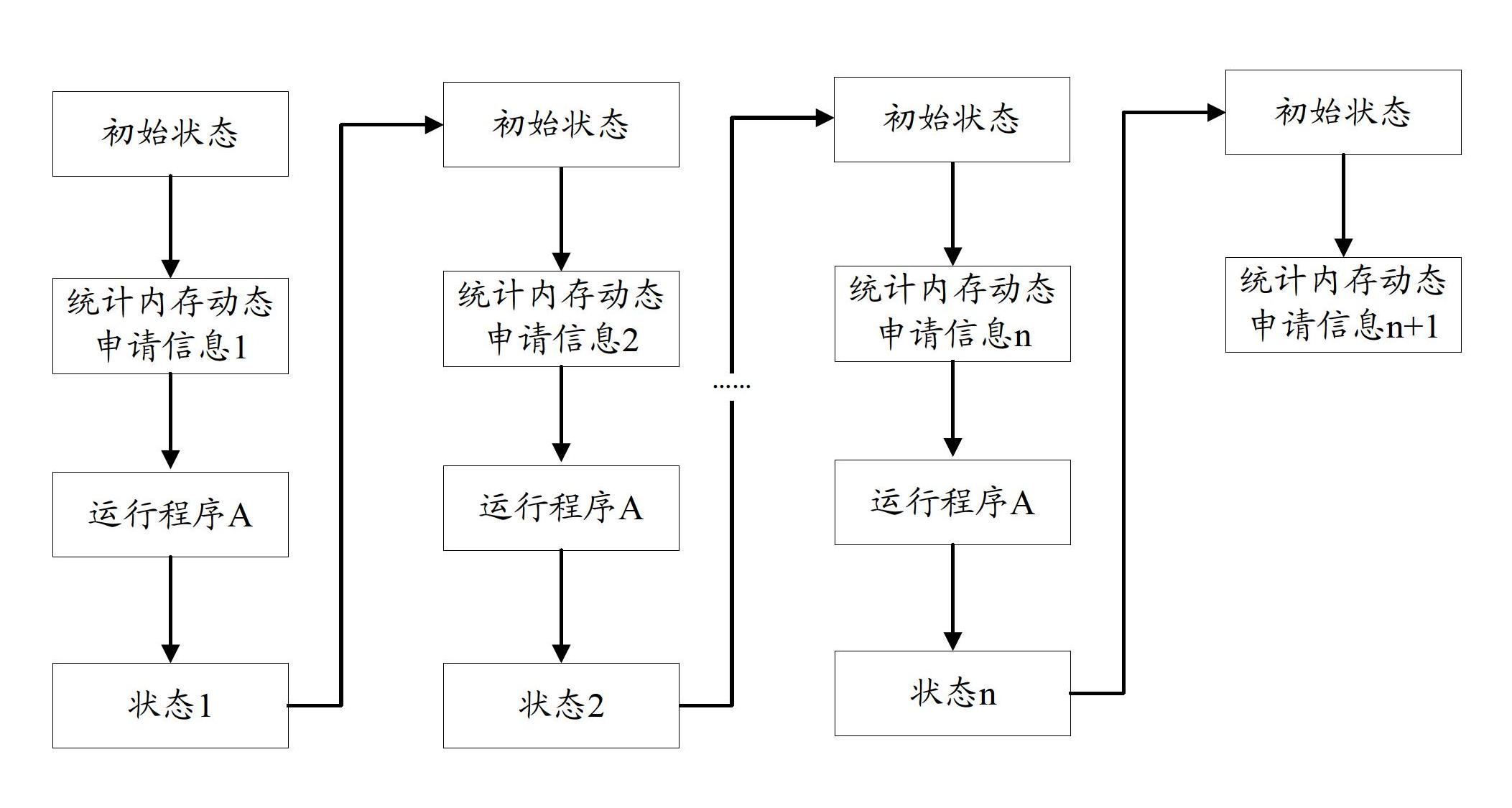
The invention discloses a memory leakage detecting method and a memory leakage detecting device. The method comprises the following steps of: after a system starts one application program each time, establishing corresponding memory dynamic applying information aiming at the application program, and carrying out statistic on the memory dynamic applying information corresponding to any one application program for many times according to a preset way in the execution process of the any one application program; and analyzing the variation condition of the memory dynamic applying information according to each obtained statistic result, and judging that the memory leakage exists corresponding to the any one application program when the memory dynamic applying information is determined to generate regular variation. In such way, the memory leakage can be conveniently judged whether to exist or not; the position of the memory leakage in a code is accurately positioned; and a system tester can conveniently debug the system aiming at a memory leakage problem.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
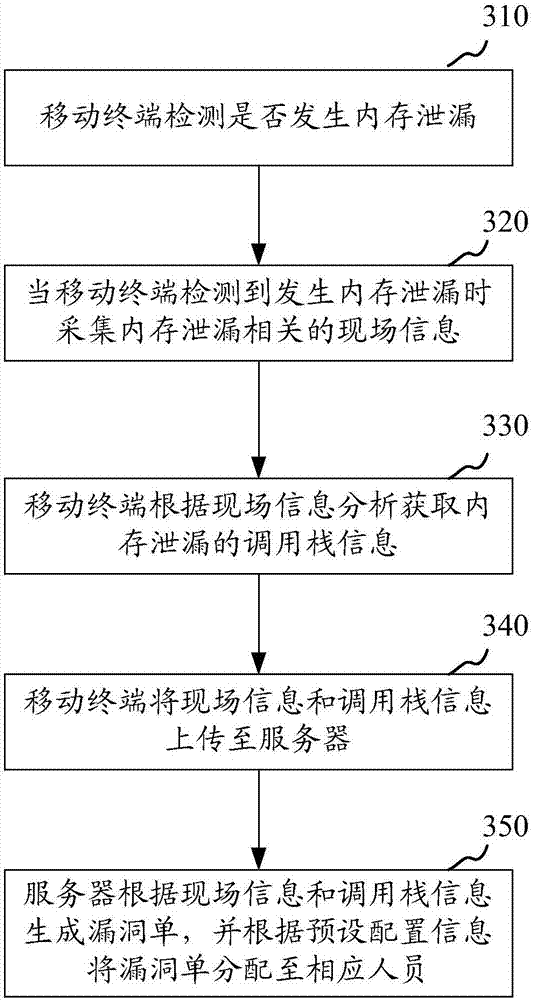
Mobile terminal memory leak processing method and device
The present invention provides a mobile terminal memory leak processing method comprising the following steps: detecting whether a memory leak occurs or not through a mobile terminal; when the memoryleak is detected by the mobile terminal, collecting field information related to the memory leak; obtaining call stack information of the memory leak according to the field information analysis through the mobile terminal; reporting the field information and the call stack information to a server through the mobile terminal; and generating a vulnerabilities list according to the field informationand the call stack information and assigning the vulnerabilities list to the corresponding personnel according to the preset configuration information through the server. The mobile terminal memory leak processing method provided by the invention has the advantages that the automatic operation of the processes of memory leak detecting, collecting, analysis, reporting, and assigning and the like isrealized; and the efficiency of detecting and processing the mobile terminal memory leaks is increased. The invention also provides another mobile terminal memory leak processing method and device.
Owner:TENCENT TECH (SHENZHEN) CO LTD
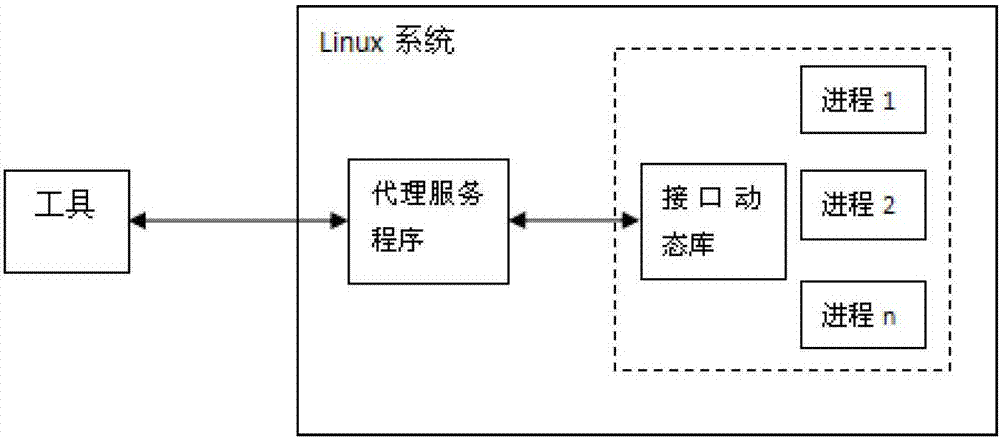
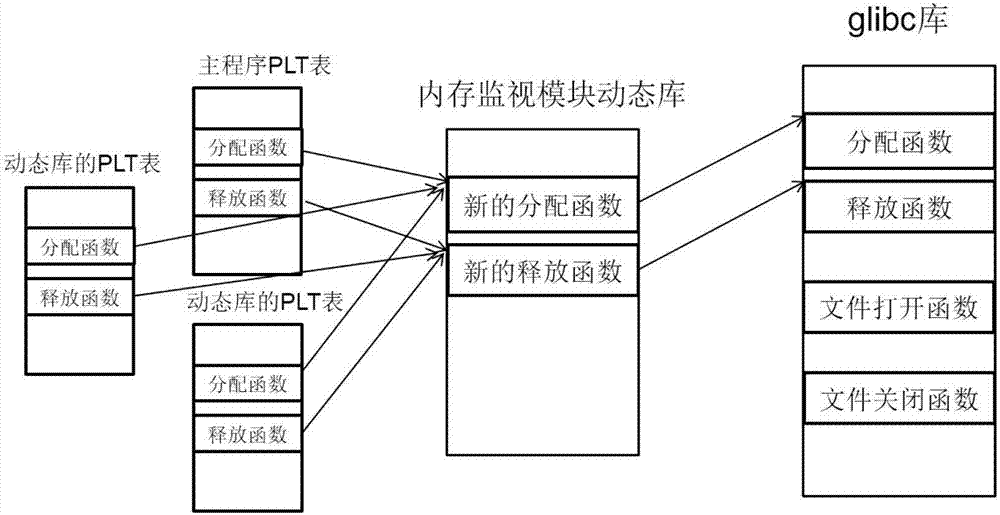
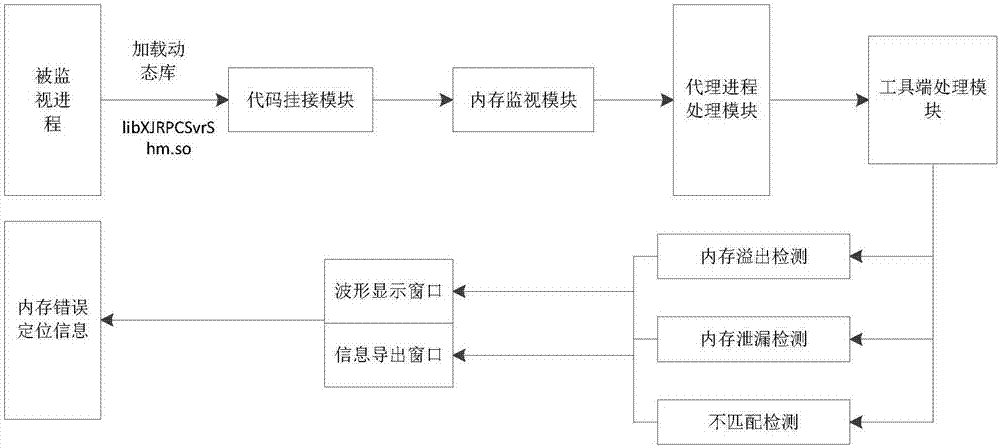
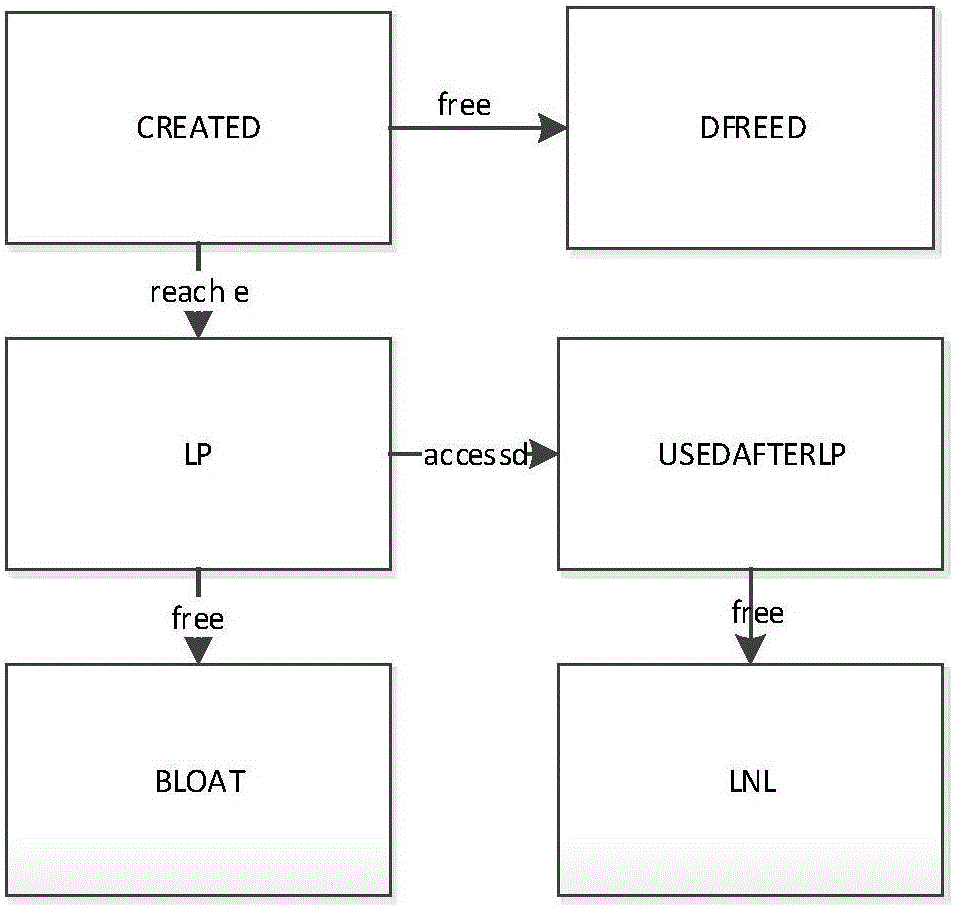
Dynamic memory leak detection method and system
The invention relates to a dynamic memory leak detection method and system. The method comprises the following steps of: dynamically mounting a memory monitoring module in a dynamic link library into an address space of a monitored process by a tool side so as to ensure that the monitored process has a memory leak detection function; recording memory operation behaviors by the monitoring module, putting the messages into a message queue and sending the message queue to an proxy server side; and uniformly managing memory information in the message queue by the proxy server side and sending the memory information to the tool side. According to the method and system provided by the invention, the memory leak conditions in process spaces can be monitored in real time without interrupting target processes, so that real online monitoring is realized; and the memory leak detection can be remotely controlled through the tool side, and the memory information of the monitored processes can be harmlessly read and written by the proxy server side, so that practical value is brought to position memory errors and diagnose problems, and the method and system are suitable for different scenes such as Linux system C / C++ programs, electric power system programs and the like.
Owner:XUJI GRP +3
Memory leak detection method based on symbolic execution
InactiveCN105808369ANarrow down the scope of monitoringImprove the efficiency of dynamic executionFault responseTest executionSource code
The invention aims at overcoming the memory leak defect and providing a memory leak detection method based on symbolic execution. Firstly, tested source codes are processed by using a static analysis tool to obtain static memory leak alarms; then, the source codes and the memory leak alarms are simultaneously input into a pile inserting device to obtain pile-inserted codes; then, the pile-inserted codes are input into a test case generating module to generate a large number of test cases and execute all test cases; the target memory leak situation is reported after operation of each test case finishes, finally all test execution outputs are summarized, and memory leak testing results are judged. The memory leak detection method solves the false alarming problem of static memory leak analysis and neglected alarming problem of dynamic testing, utilizes a symbolic execution technology to generate test cases, decreases artificial verification works of static analysis of memory leak results and improves dynamic execution efficiency.
Owner:北京系统工程研究所 +1
Method and apparatus for generating data for use in memory leak detection
InactiveUS7100003B2Data processing applicationsError detection/correctionParallel computingMemory leak detection
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com