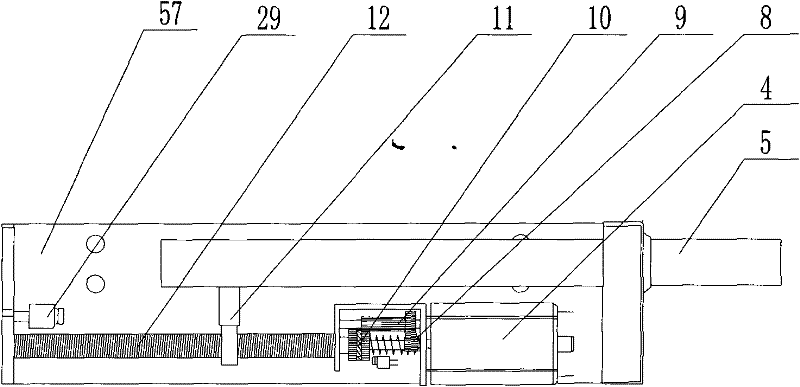
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
99results about How to "Strong security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
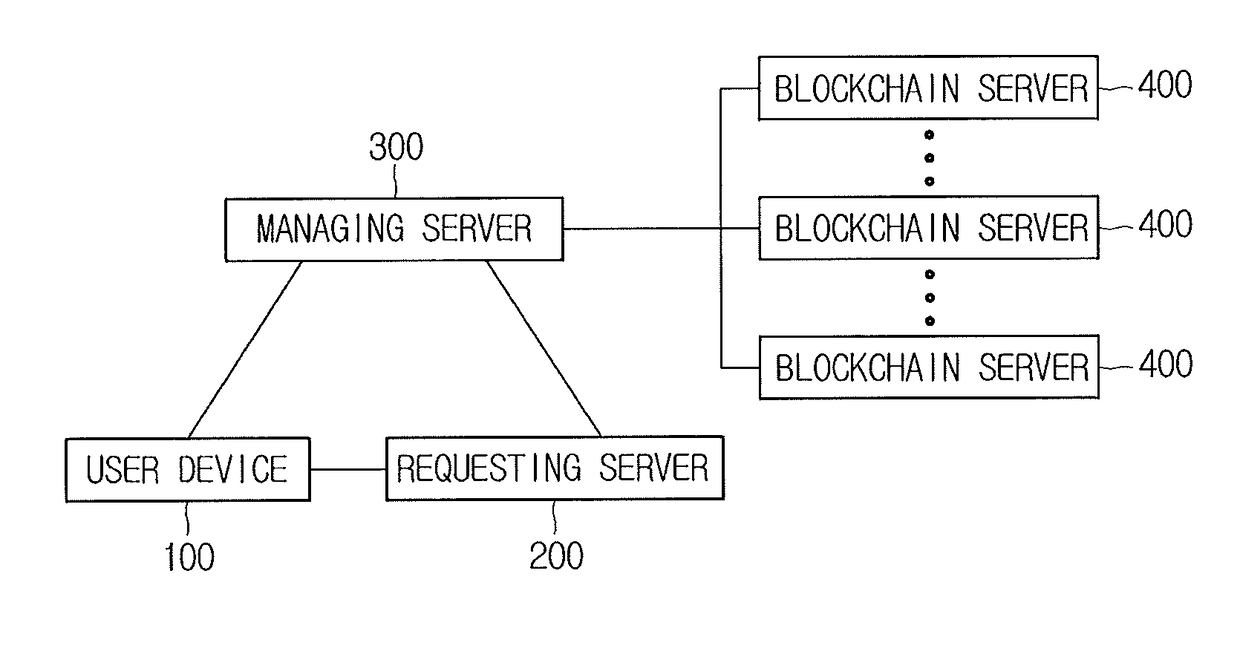
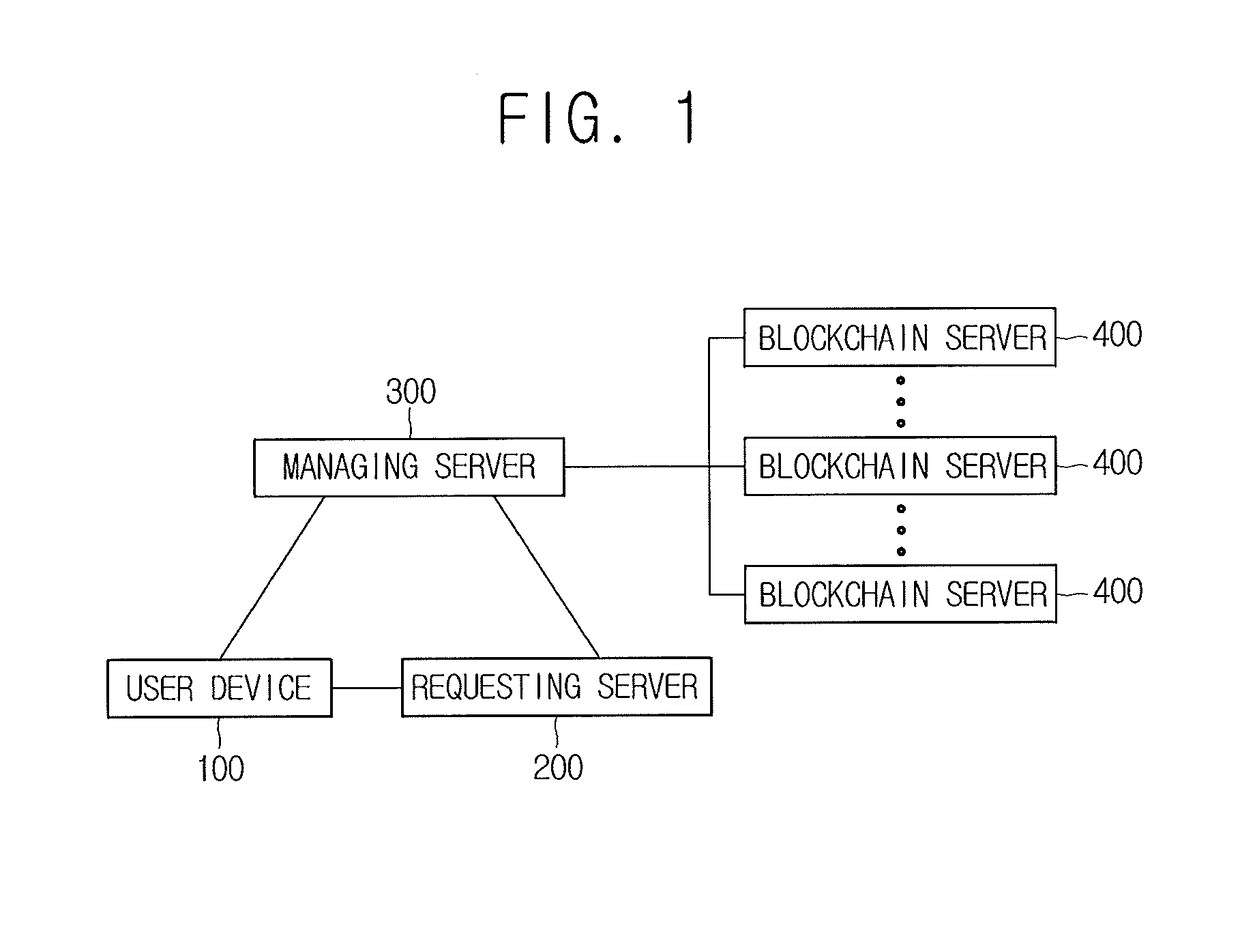
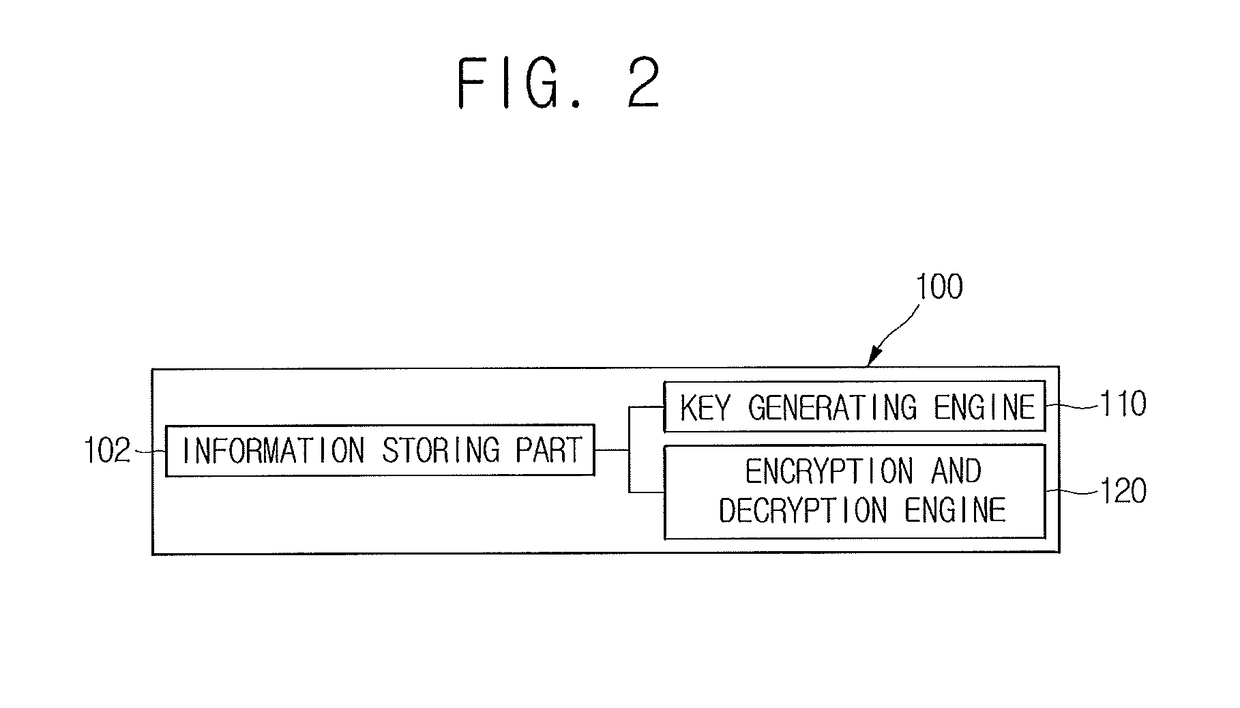
Method for using and revoking authentication information and blockchain-based server using the same
ActiveUS20170330180A1Strong securityEffective usabilityCryptography processingDigital data authenticationRevocationBlockchain
A method for using authentication information is provided. The method includes steps of: (a) a managing server, if a request for using the authentication information is acquired, acquiring a transaction ID corresponding to a specific user's identification information; (b) the managing server acquiring an output of a specific transaction corresponding to the transaction ID from a blockchain; (c) the managing server determining revocation of the authentication information by referring to the output of the specific transaction; and (d) the managing server supporting a communication by providing the specific user's public key in the output of the specific transaction, if the authentication information is not revoked, and if (i) a hash value of the specific user's identification information included in the output of the specific transaction or its processed value corresponds to (ii) a hash value of the specific user's identification information pre-stored in a certain database or its processed value.
Owner:COINPLUG LNC
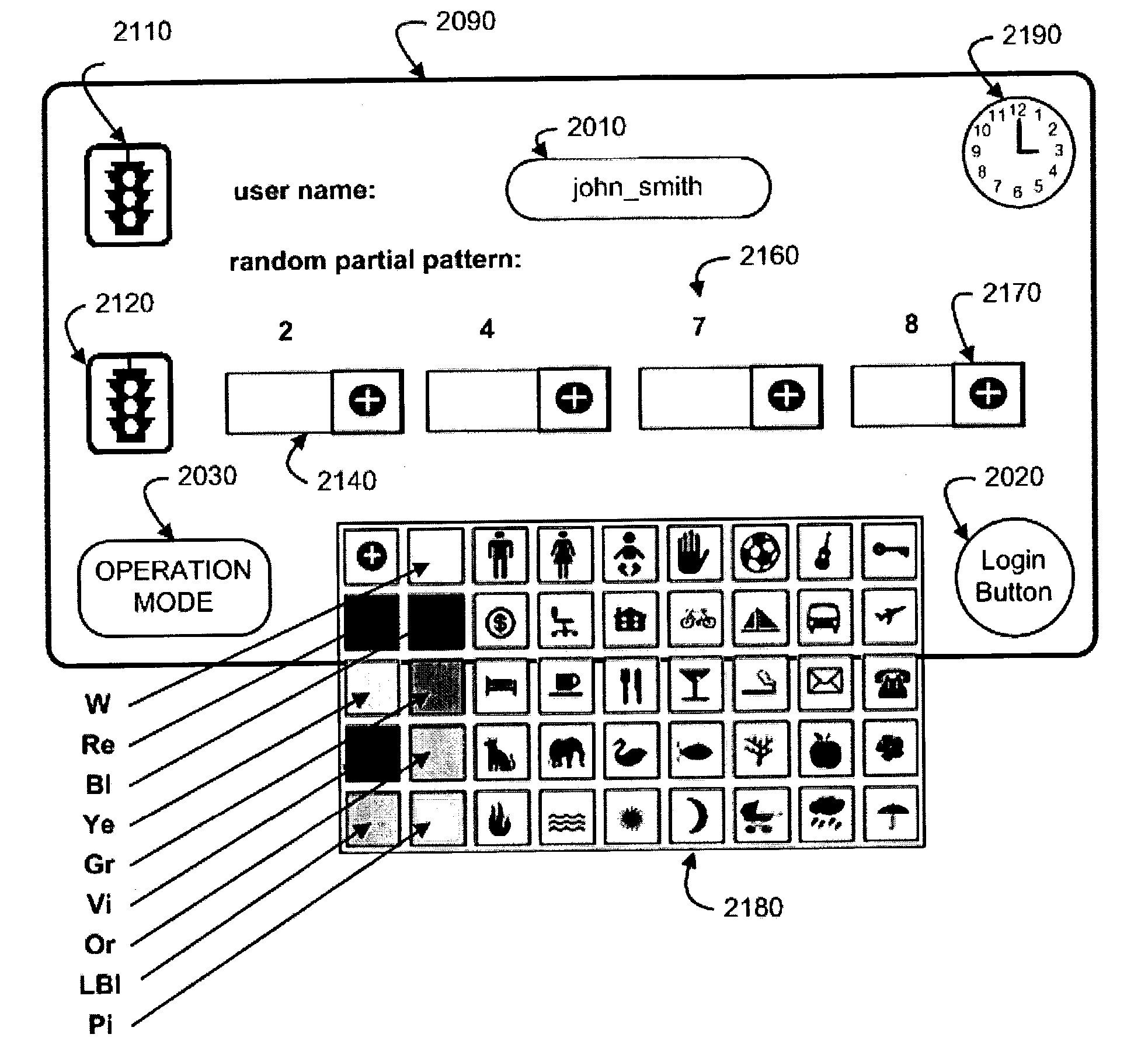
System and method for user authentication interface
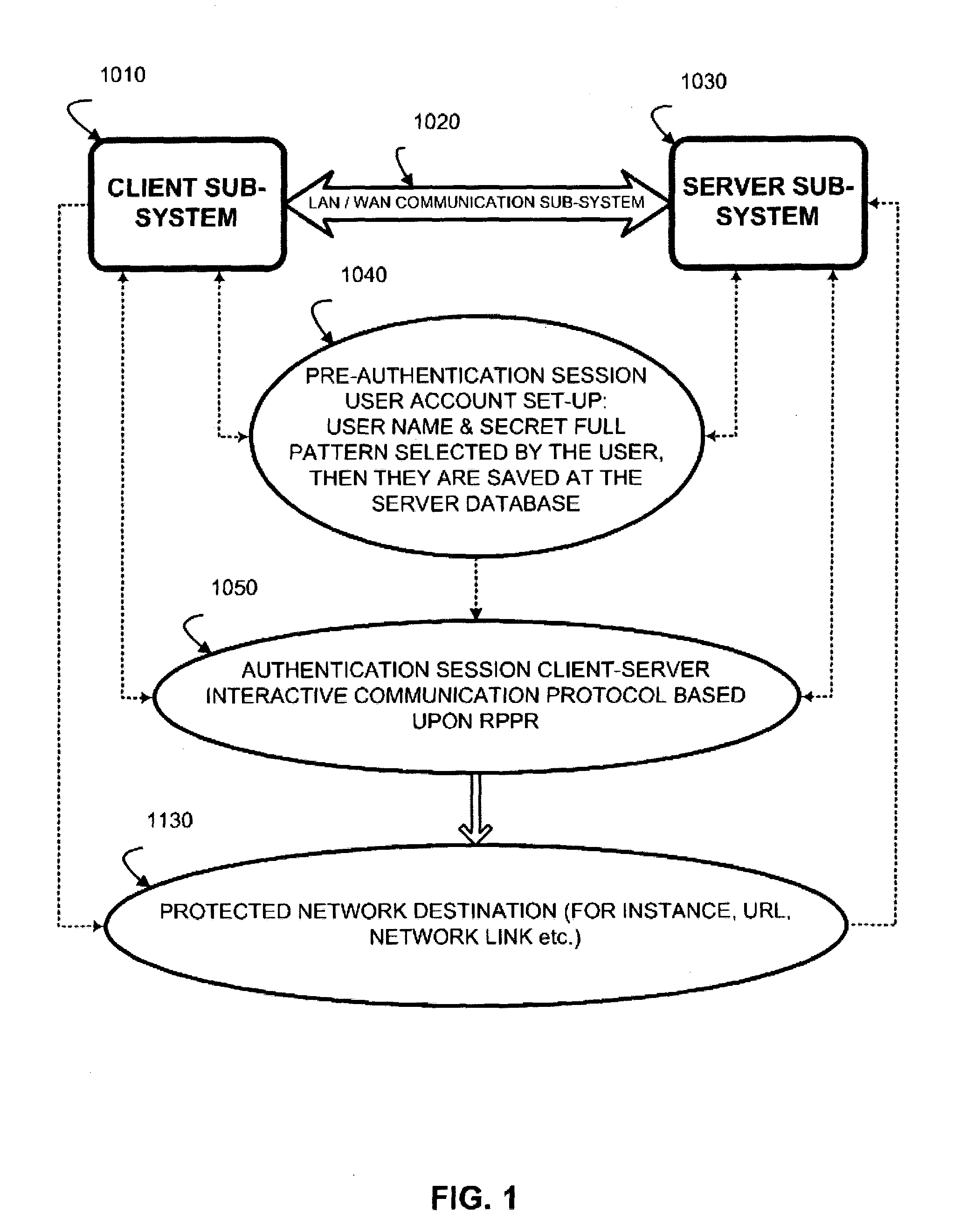
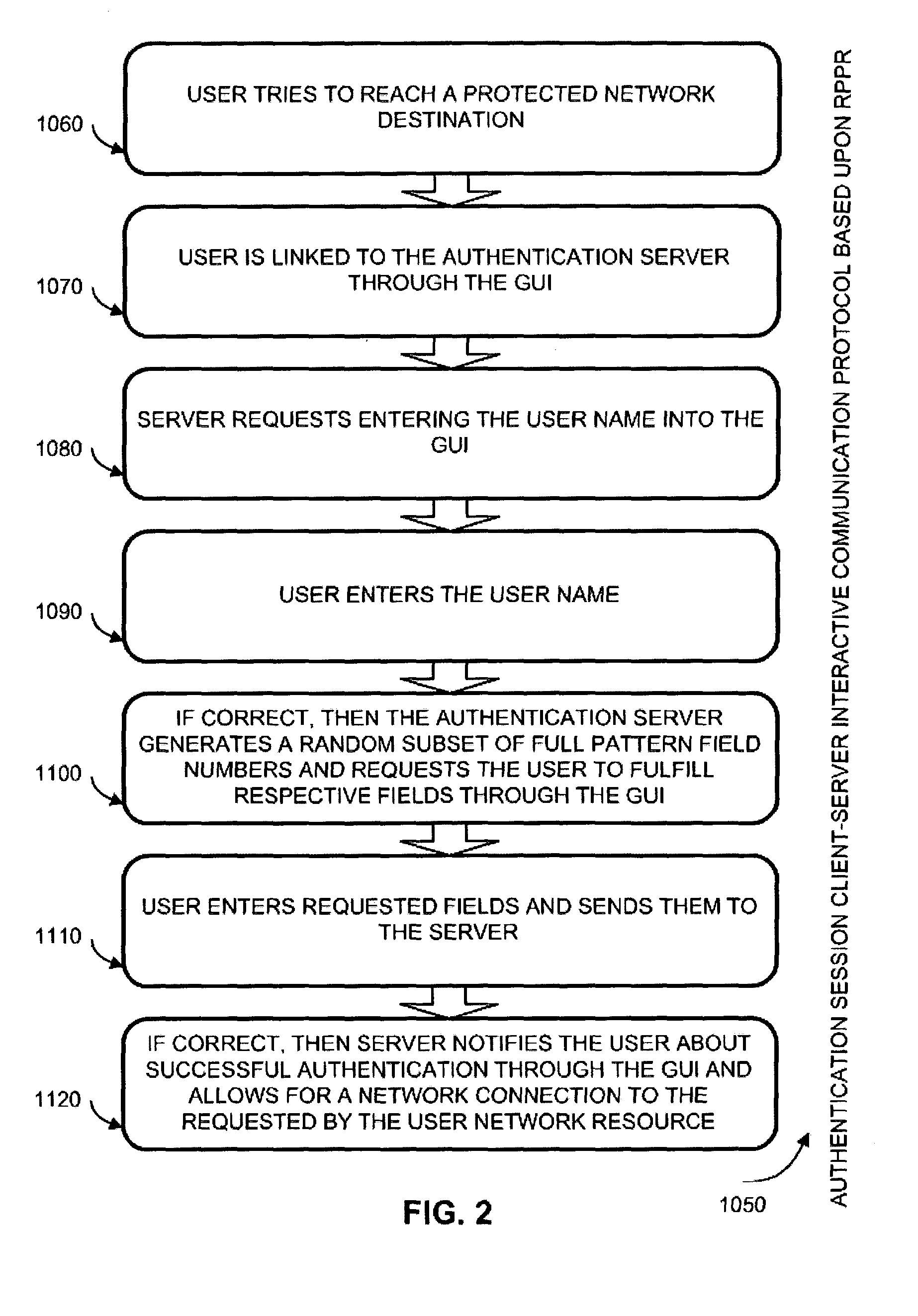
ActiveUS7188314B2Enormous combinatorial capacityStrong securityDigital data processing detailsUser identity/authority verificationUser authenticationOrder set
A graphical user interface supports an interactive client-server authentication based on Random Partial Pattern Recognition algorithm (RPPR). In RPPR, an ordered set of data fields is stored for a client to be authenticated in secure memory on the server side. A graphical user interface presents a clue generated at the server to the client, such positions in the ordered set of a random subset of data fields from the ordered set. The client enters input data in multiple fields of the interface according to the clue, and the server accepts the input data from the client. The input data includes storage units representing alpha-numeric characters, images and colors corresponding to the field contents for the data fields. The interface includes indicators for elapsed time and status of the authentication session.
Owner:AUTHERNATIVE INC
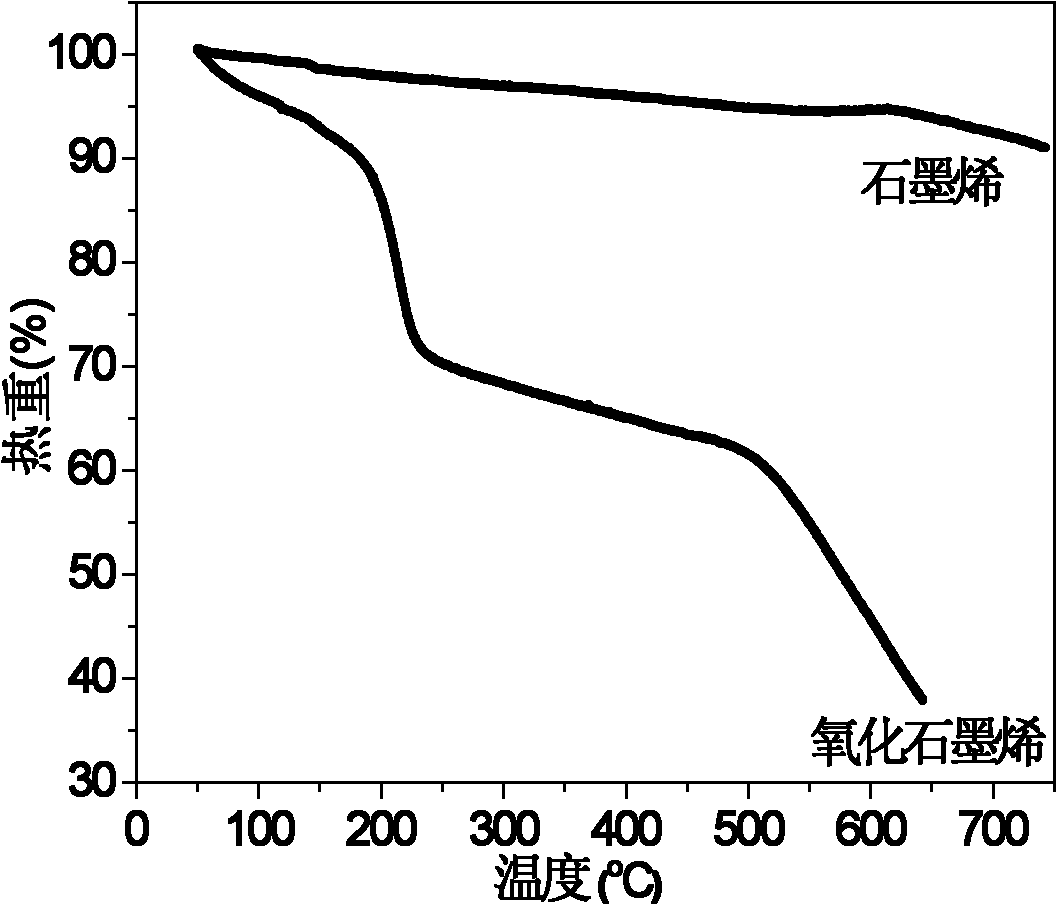
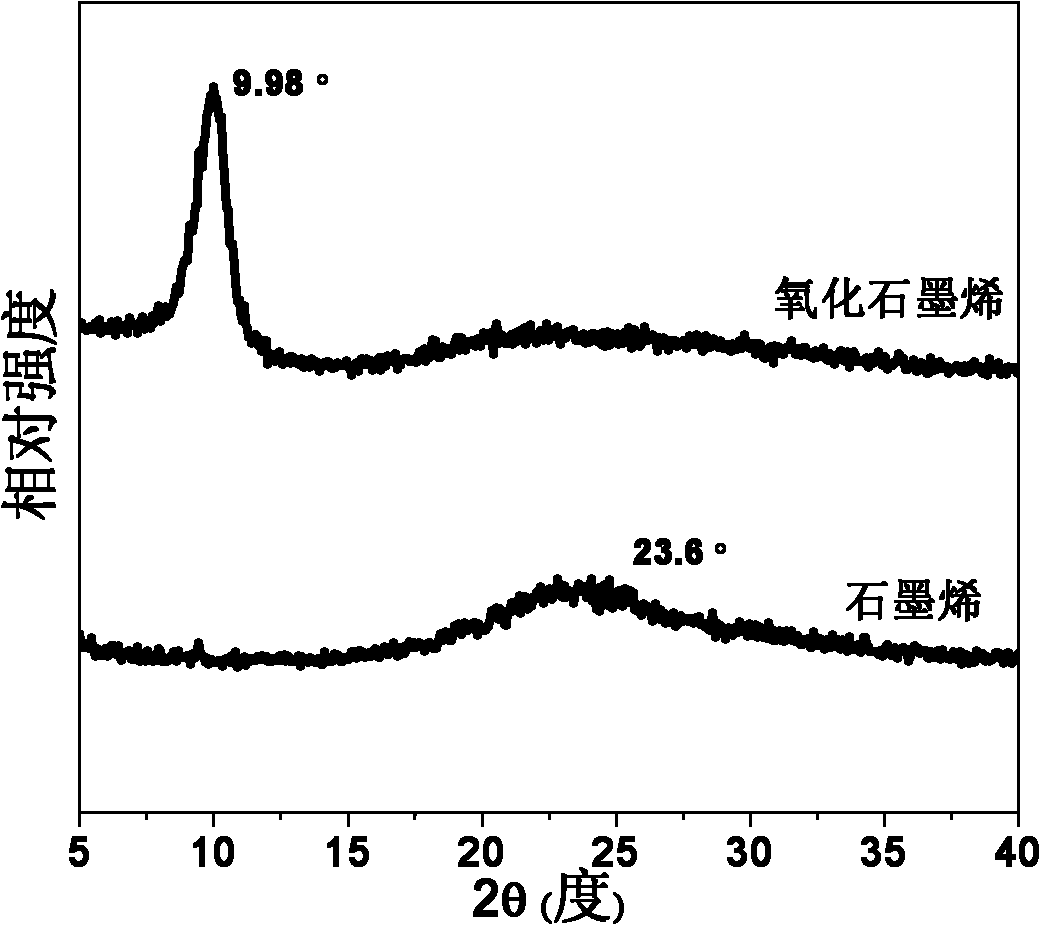
Method for preparing graphene by chemical oxidation reduction
The invention discloses a method for preparing graphene by chemical oxidation reduction, which comprises the following steps: preparing a graphene oxide water solution according to the concentration of 1-6 mg / ml from graphene oxide which is prepared from graphite by the existing chemical oxidation method; then, uniformly coating the graphene oxide water solution on a substrate by using a spin coating method or pouring method, and carrying out vacuum drying to form a graphene oxide film; and immerging the substrate coated with the graphene oxide film in a reducer water solution which is prepared from sodium hydrosulfite and sodium hydroxide according to the mass ratio of (1:2)-(1:6), carrying out reducing reaction at 50-80 DEG C for 12-20 minutes, washing with water to neutral, and drying to obtain a black graphene film. The sodium hydrosulfite used in the method disclosed by the invention is a mild, nontoxic and efficient reducer, is harmless to people and does not pollute the environment, thus the sodium hydrosulfite has the advantages of high safety and high reduction efficiency; and in addition, the sodium hydrosulfite has the advantages of low price and wide sources, thus the sodium hydrosulfite has wide industrial prospects and can be used for large-scale production of graphene products.
Owner:SICHUAN UNIV
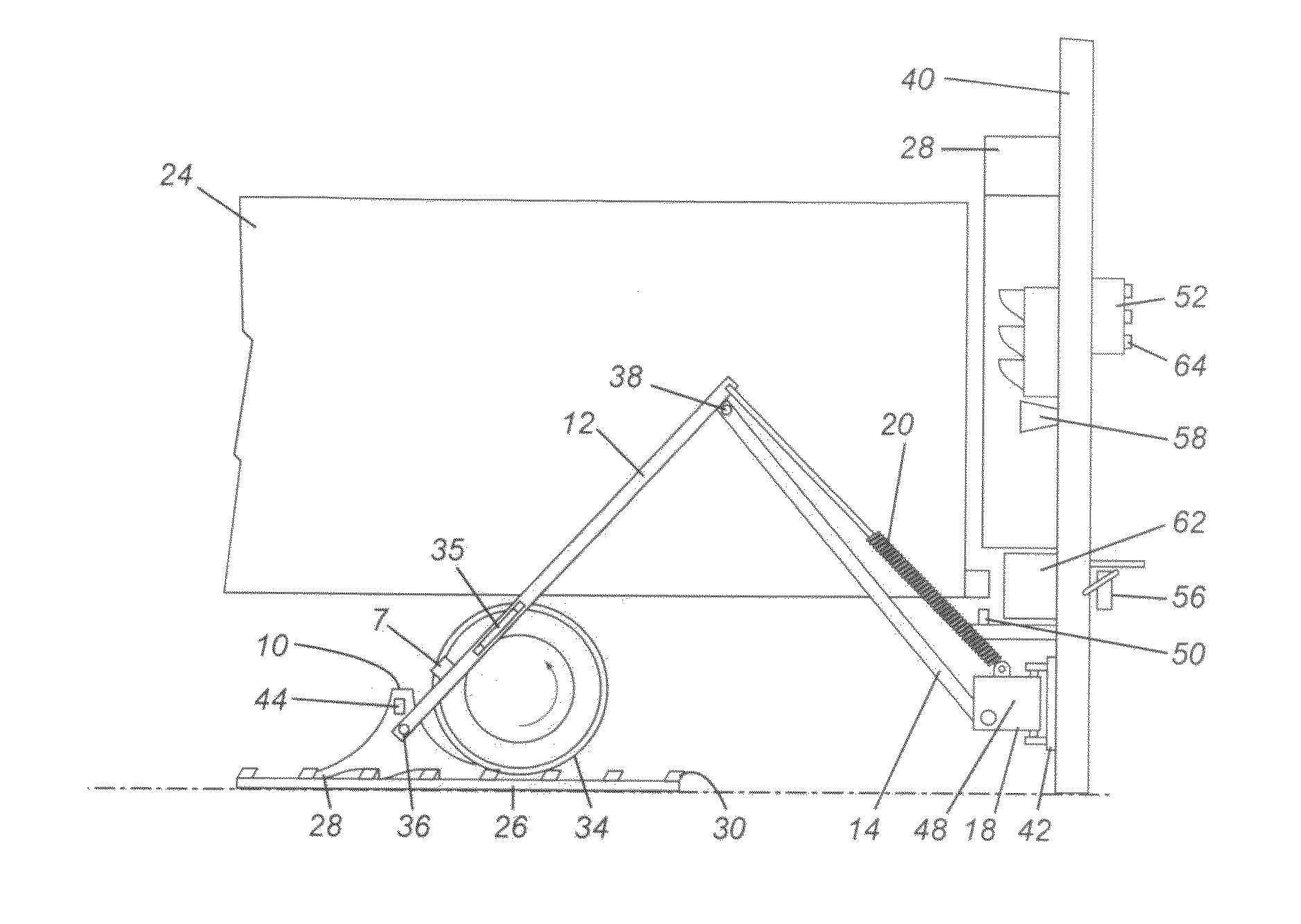
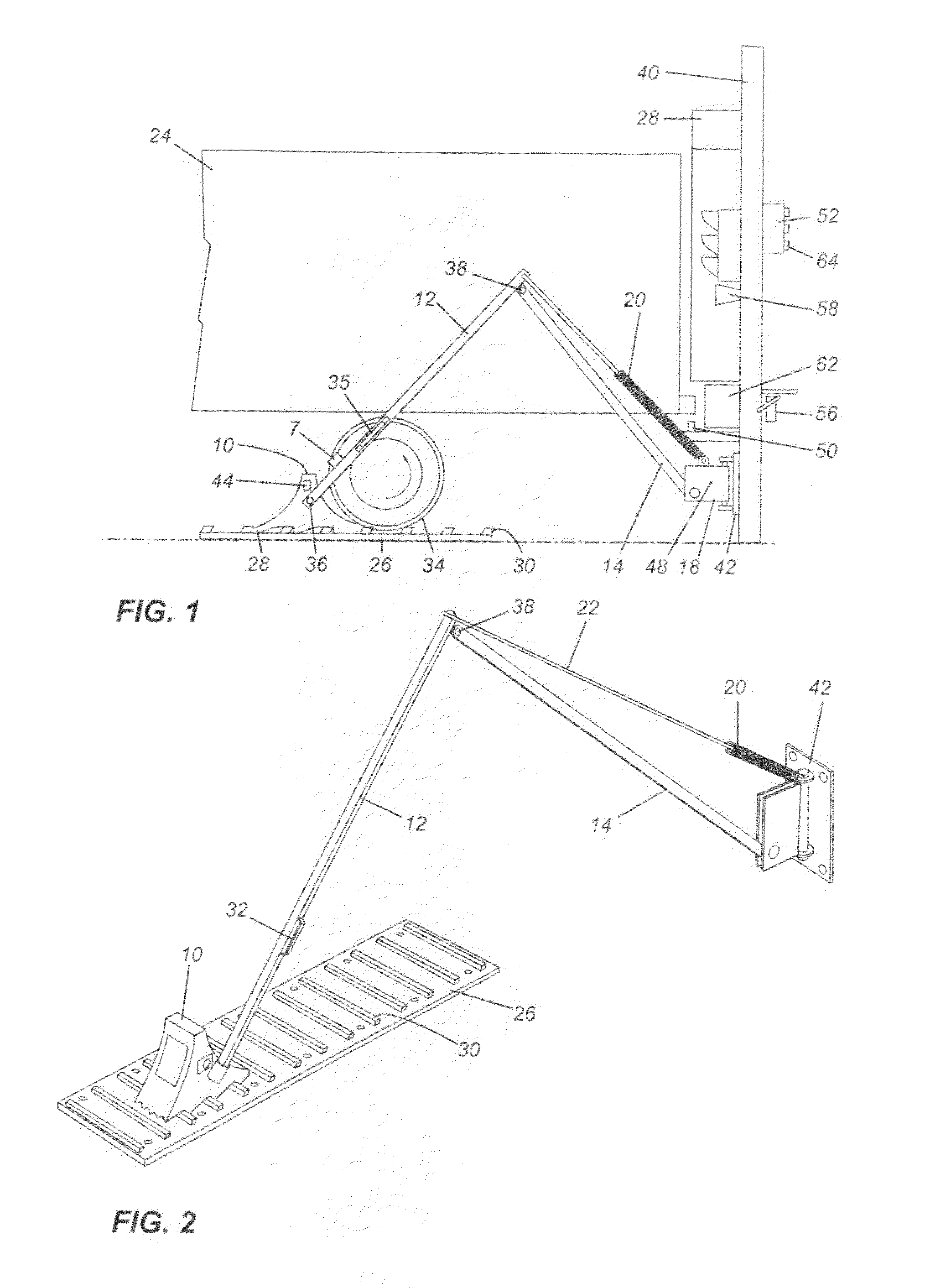
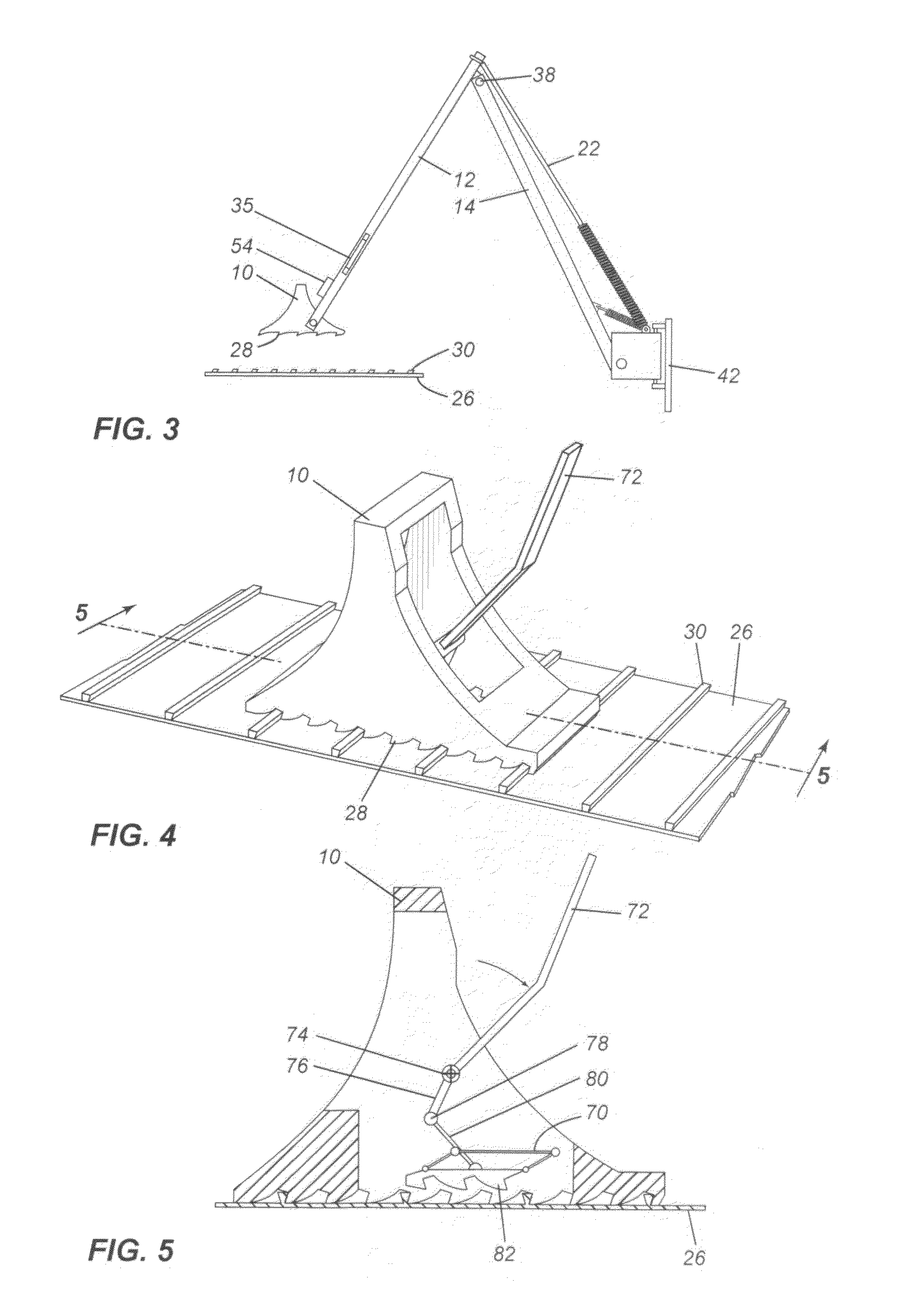
Chock system
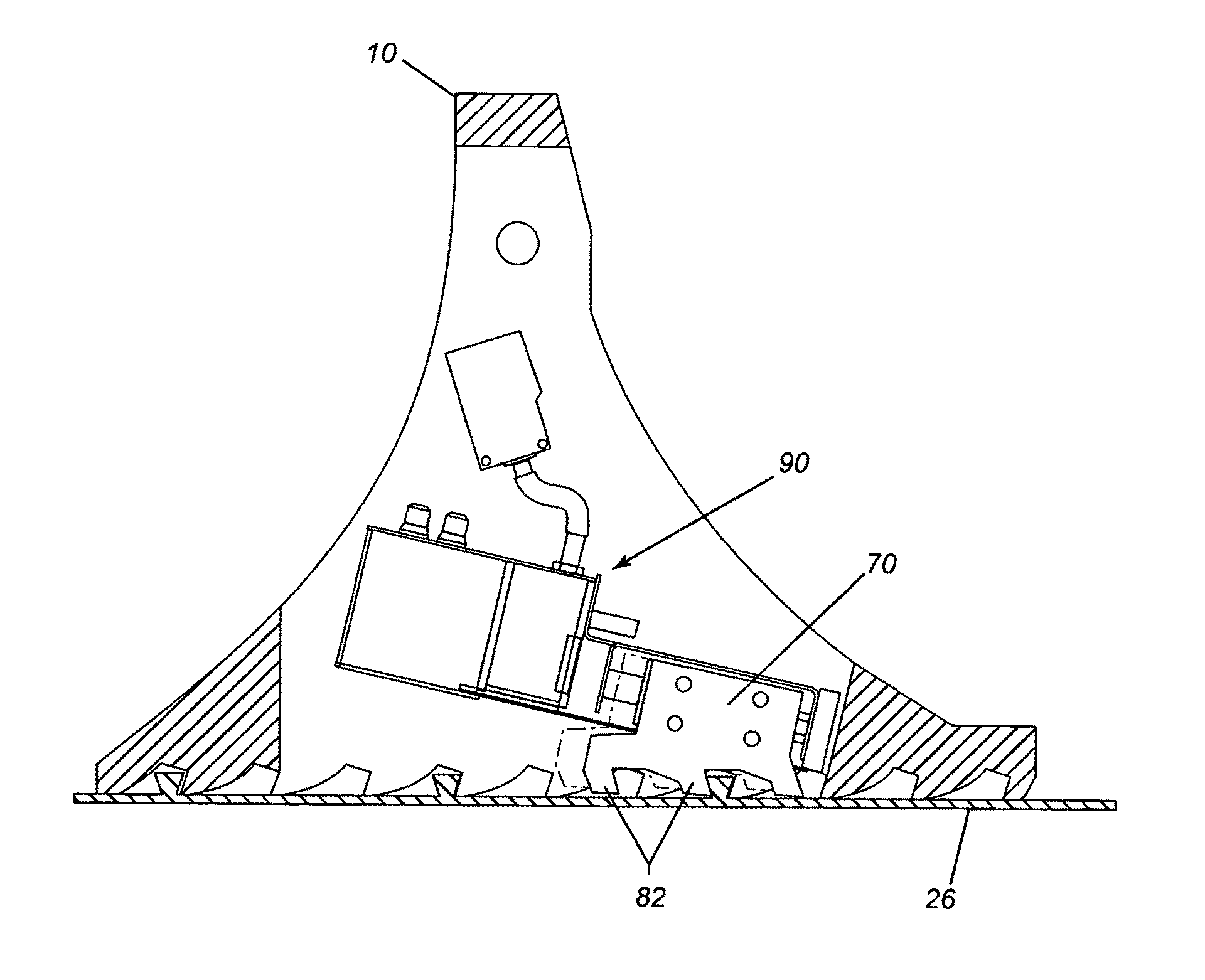
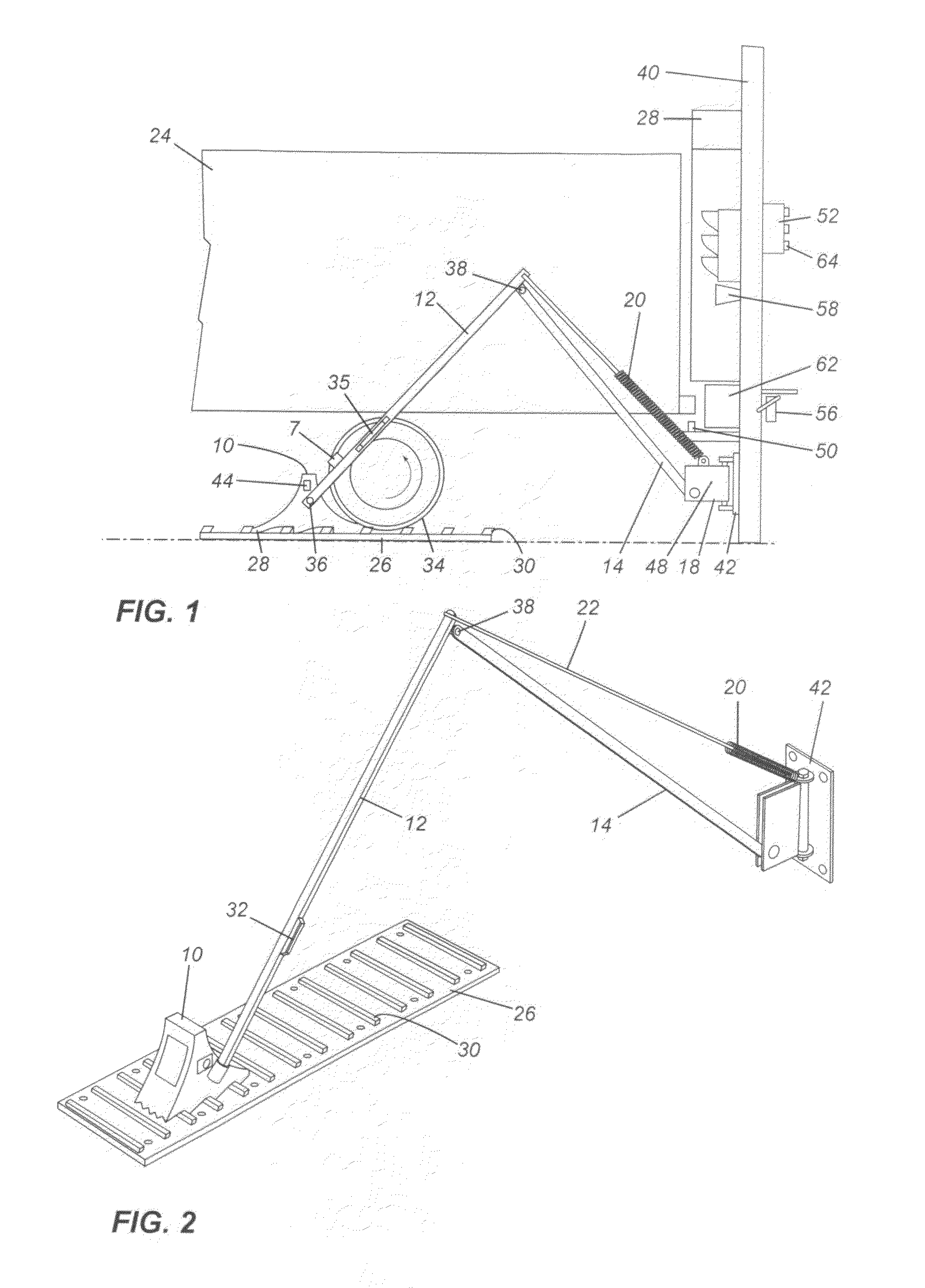
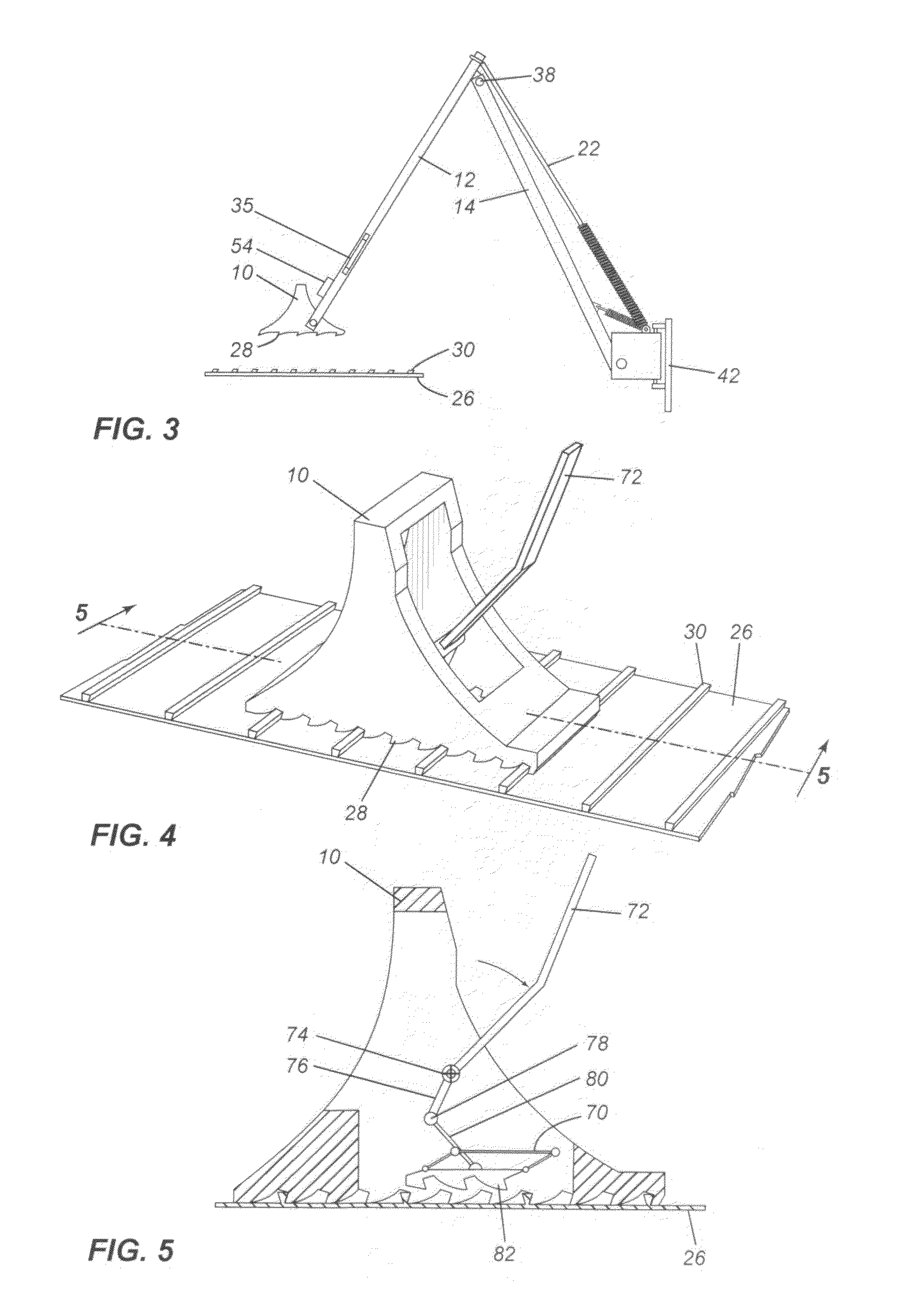
ActiveUS8590674B2Strong securityPrevent movementBraking element arrangementsPortable braking systemMechanical engineeringWheel chock
A wheel chock restraint system which comprises a wheel chock having a base, a plurality of teeth extending outwardly from the base, the teeth extending in a first direction, and a locking member mounted within the chock, the locking member having a plurality of locking member teeth extending from a bottom thereof, the locking member teeth extending in a second direction generally opposed to the first direction, and an arrangement for moving the locking member in a generally vertical direction.
Owner:9172 9863 QUEBEC
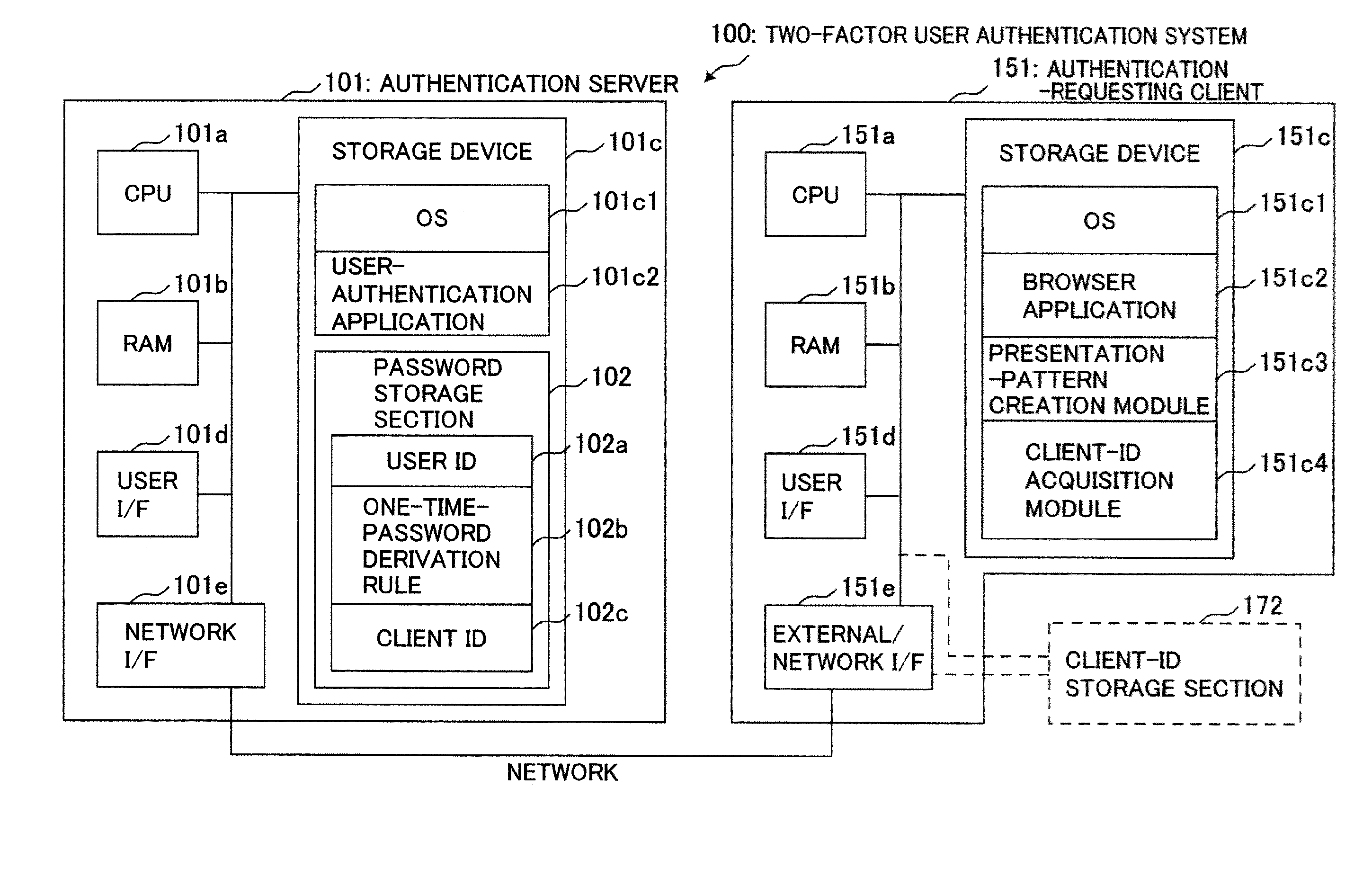
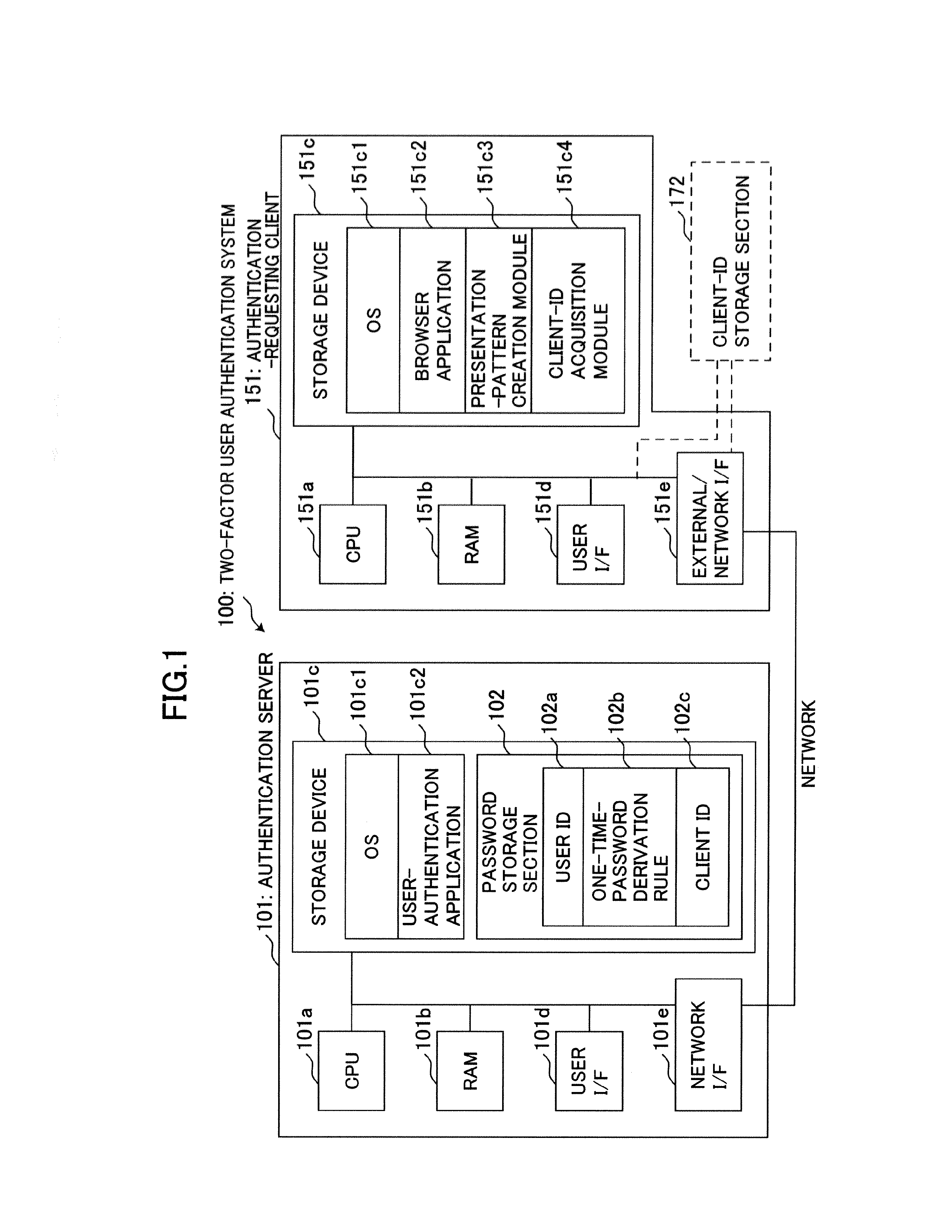
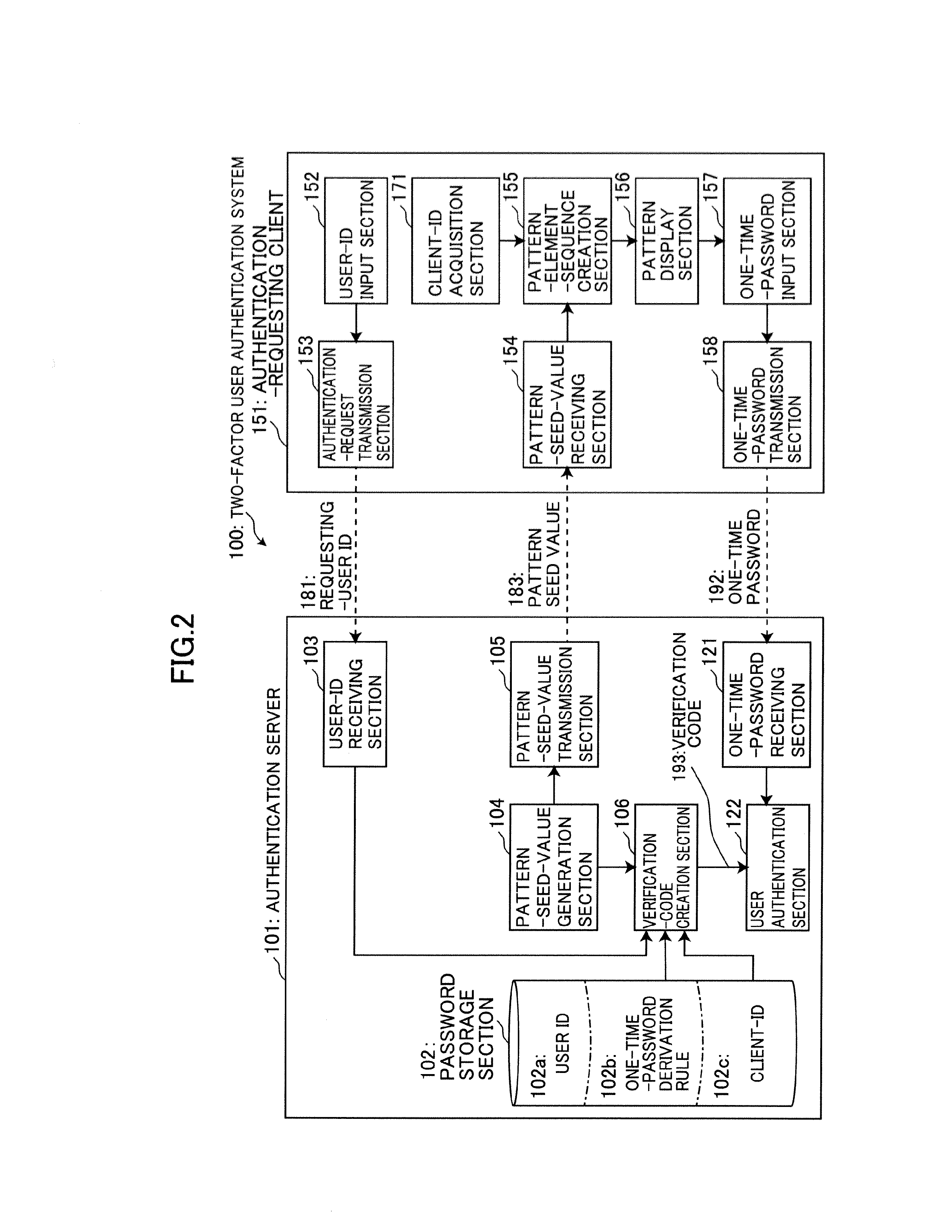
System and method for two-factor user authentication
ActiveUS20130185779A1Strong securityMinimize costDigital data processing detailsMultiple digital computer combinationsUser authenticationReduced risk
Provided is a two-actor user authentication system with a reduced risk of leakage of authentication information.The two-factor user authentication system is designed to use, as a password, a one-time-password derivation rule to be applied to certain pattern elements included in a presentation pattern at specific positions so as to create a one-time password, and further use, as a second authentication factor, information identifying a client to be used by a user. An authentication server is operable to generate a pattern seed value adapted to uniquely specify a presentation pattern in combination with a client ID, and transmit the pattern seed value to an authentication-requesting client. The authentication-requesting client is operable to create a presentation pattern based on a client ID acquired therefrom, and display the presentation pattern to allow a user to enter thereinto a one-time password based on the presentation pattern.
Owner:CSE CO LTD
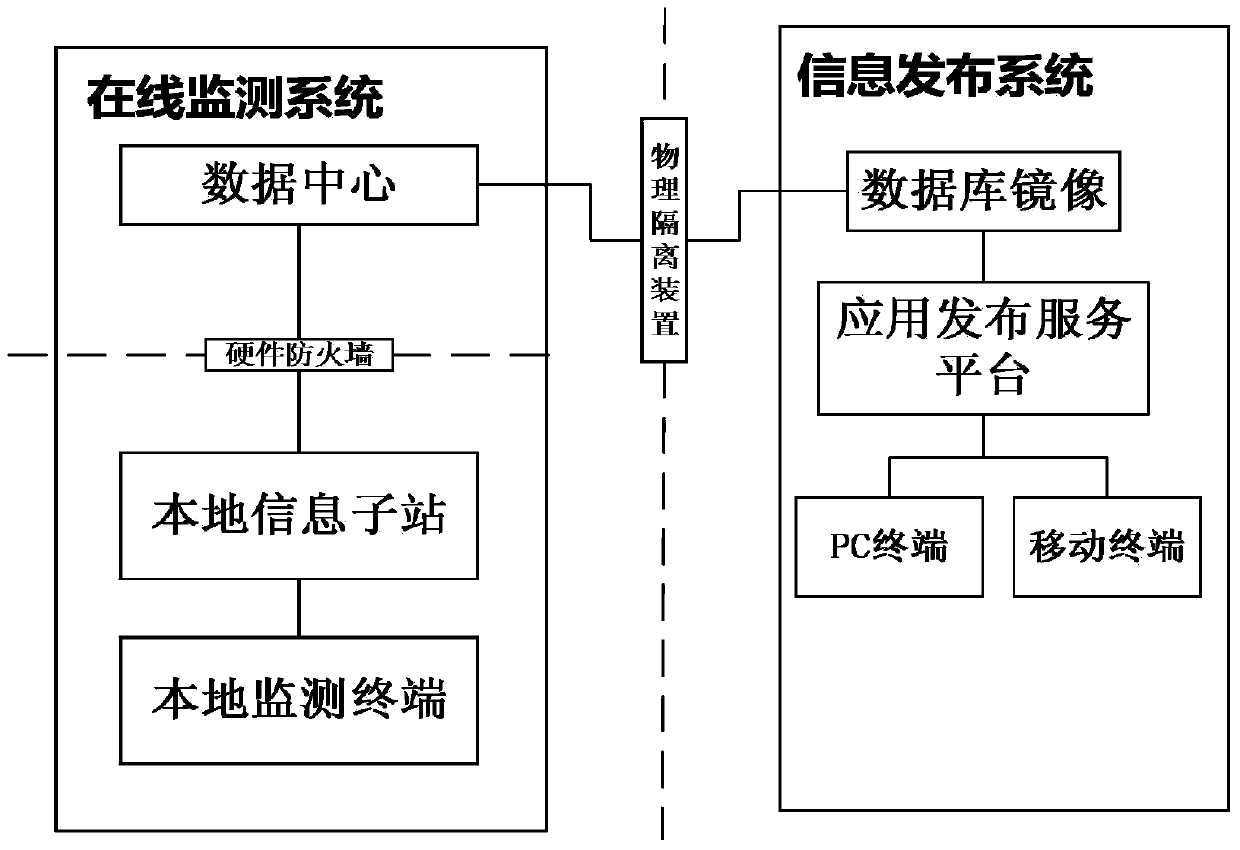
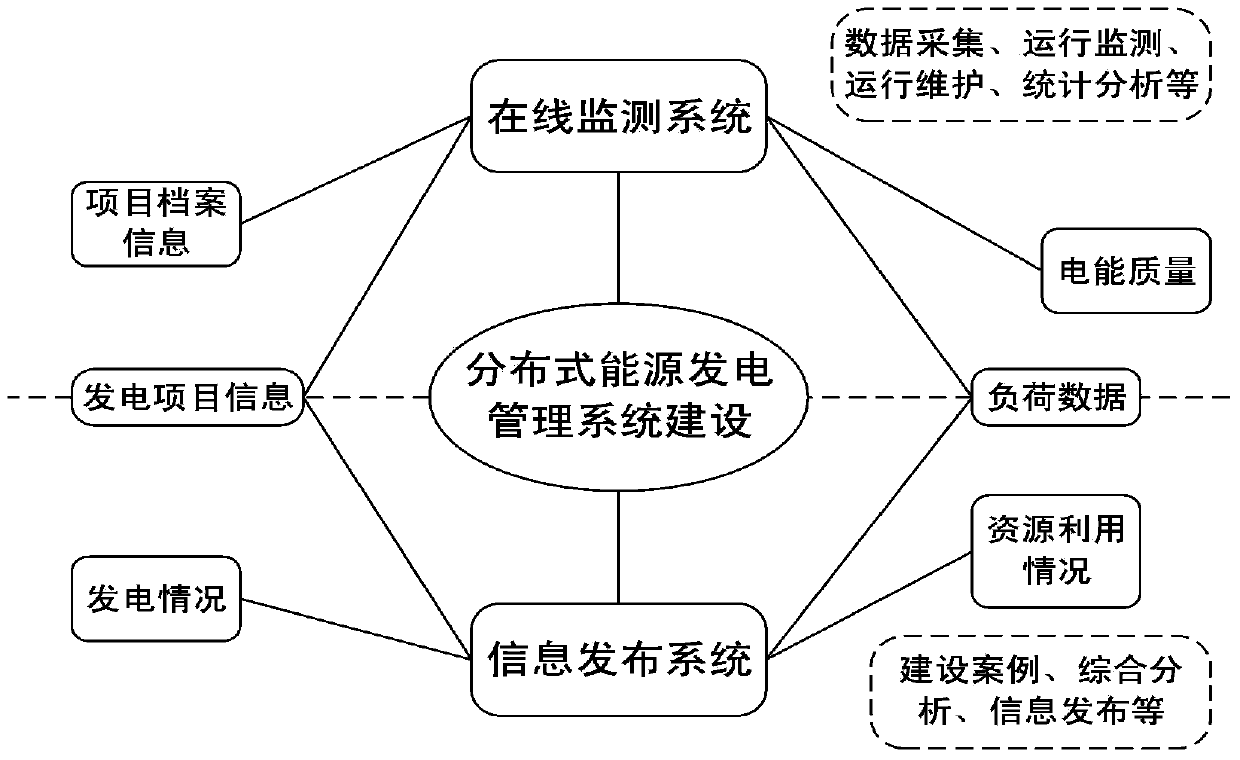
User-side distributed energy power generation management system
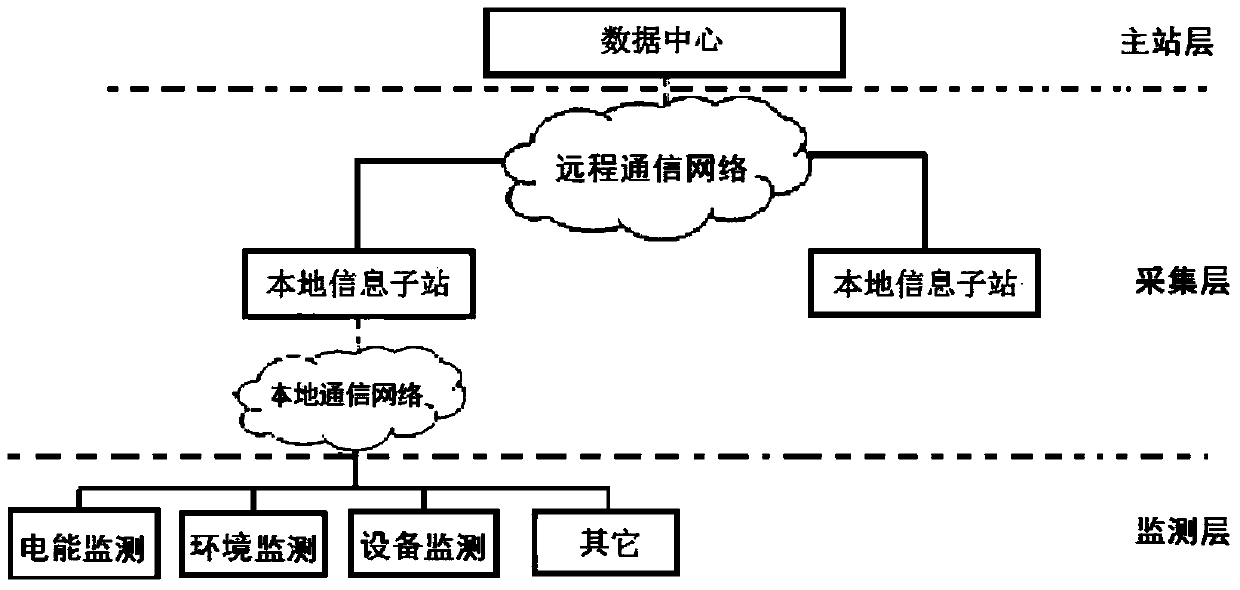
The invention provides a user-side distributed energy power generation management system. The user-side distributed energy power generation management system comprises an online monitoring subsystem and an information publishing subsystem which are connected through an isolation device. The information publishing subsystem is mainly used for Web displaying for relevant enterprises and the societal public. The online monitoring subsystem is responsible for acquisition, collection, monitoring and analysis of real-time data such as electric energy data, electric energy quality, environmental data, equipment working conditions and the like of distributed power generation projects. The system can acquire real-time power generation data of the distributed energy power generation projects within a certain range, provide technical services such as monitoring, analysis, evaluation, grid connection, information publishing and the like for users, achieve concentrated digital supervision of the distributed energy power generation projects, and provide technical support and data support for the government to carry out the low-carbon and energy-saving strategy and make and implement the clean energy development plan and related policies.
Owner:STATE GRID CORP OF CHINA +1
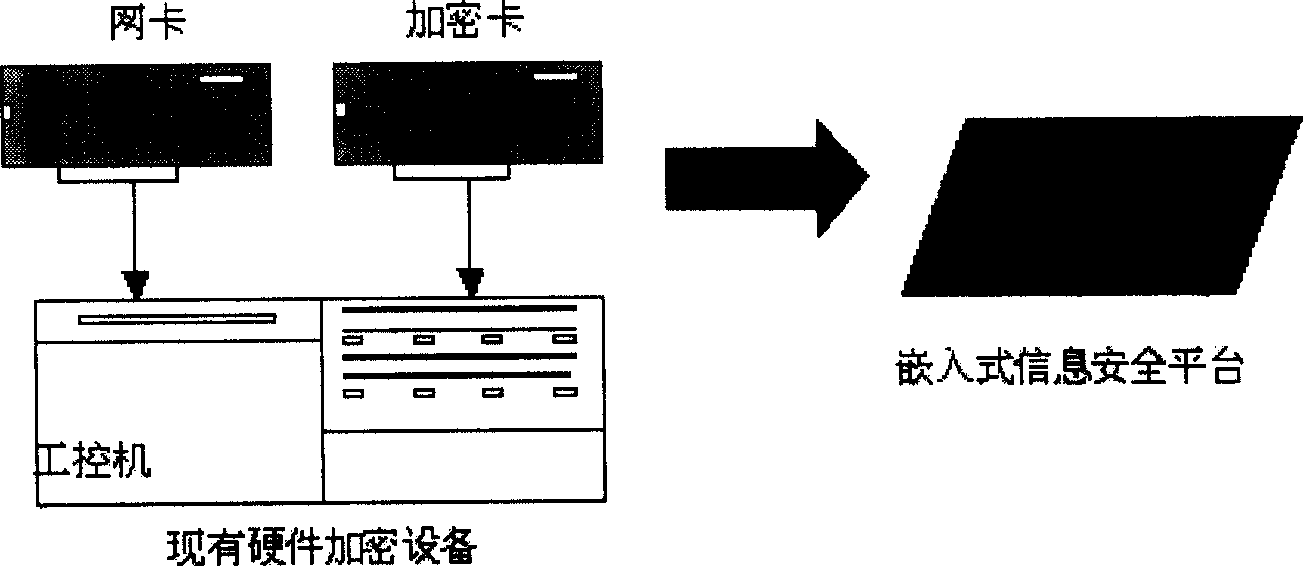
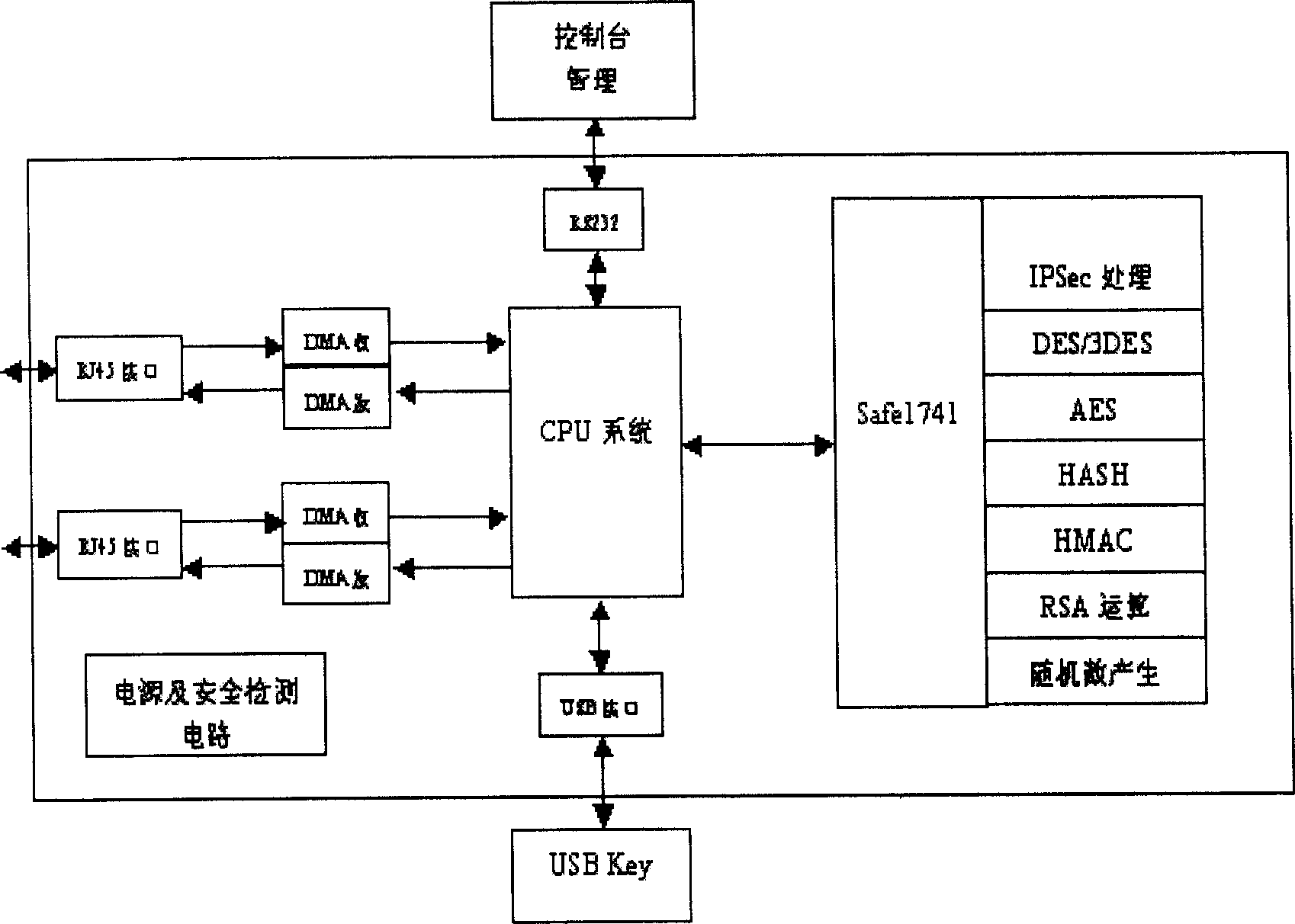
An embedded information security platform
InactiveCN1622517ALow costStrong securityData switching networksSecuring communicationSerial digital interfaceApplication Context
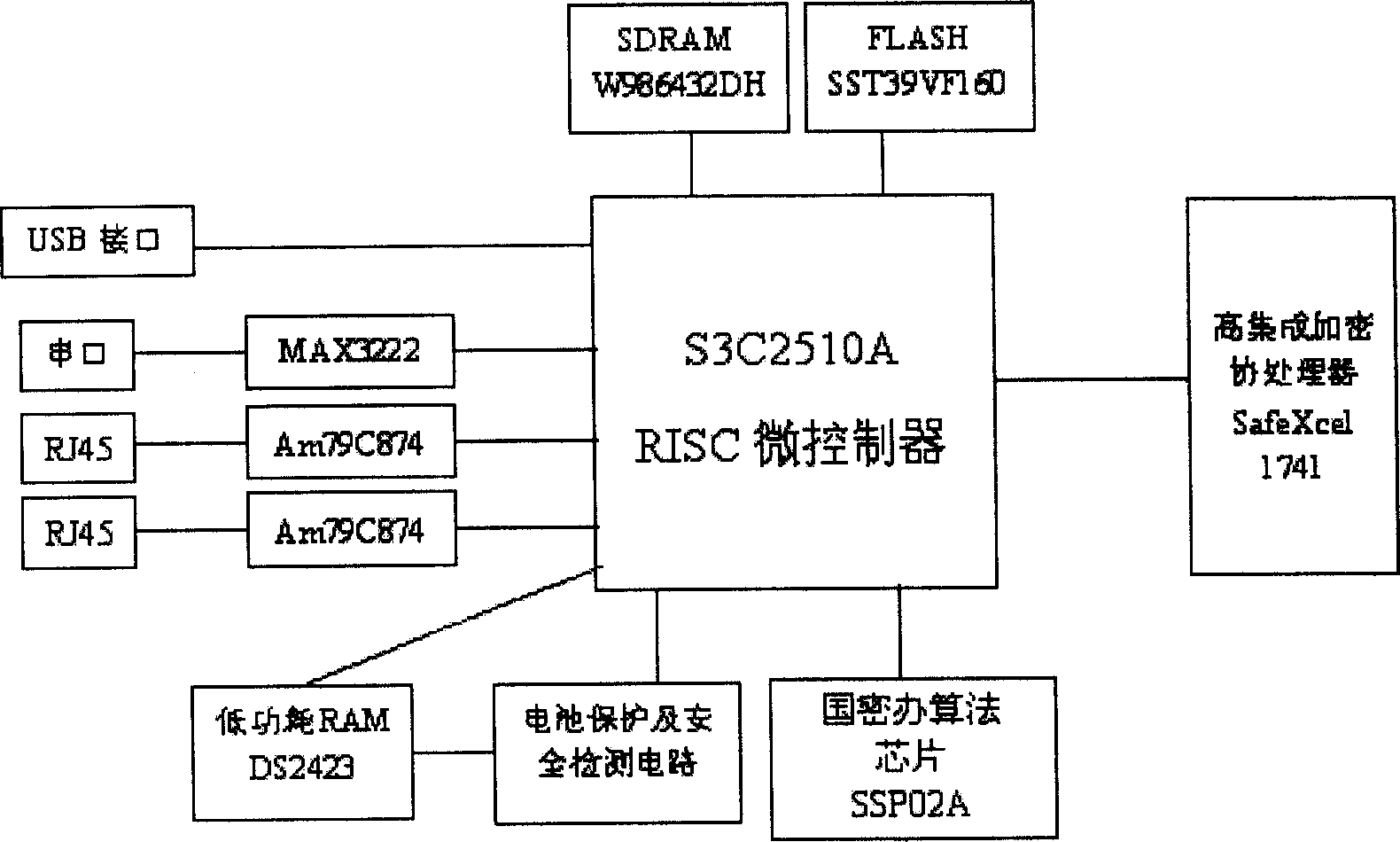
The embedded information safety platform features the CPU micro controller as one network processing chip with ARM940T kernel containing real-time embedded operation system; enciphering and deciphering hardware chip comprising IPSec algorithm chip and symmetric algorithm chip; I / O interface including two 10 / 100 M adaptive Ethernet interfaces, one USB main control interface and one serial interface. The present invention is one opening hardware safety platform enclosed inside one casing and with relaxed application environment, powerful attack resistance and high reliability. The present invention has several enciphered algorithms, supports several kinds of application service, has high versatility, and may be used also in ciphering server, VPN ciphering gateway, SSL safety gateway, safety router, hardware fire wall and other safety devices.
Owner:上海极毅信息科技有限公司
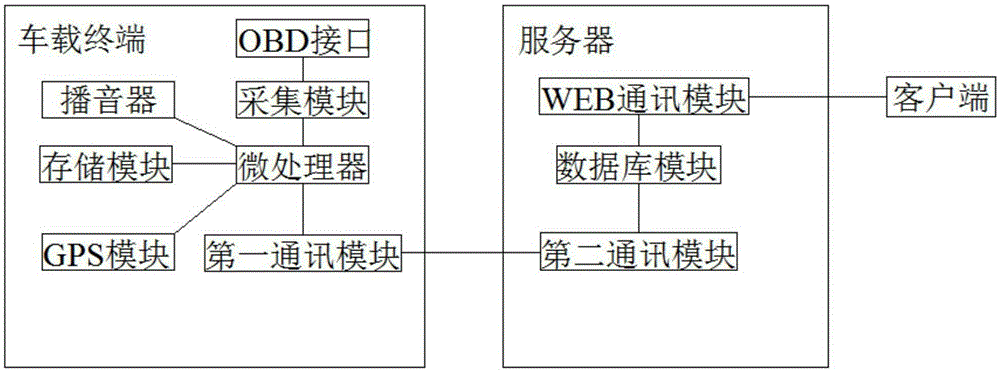
Remote diagnosis method for vehicle
InactiveCN106814724AImprove securityStrong securityElectric testing/monitoringStart signalElectronic control unit
The invention discloses a remote diagnosis method for a vehicle, and the method comprises the following steps: S1, transmitting a vehicle diagnosis triggering start signal to a server through a client; S2, transmitting a vehicle diagnosis triggering signal to a vehicle-mounted terminal after the server receives the vehicle diagnosis triggering start signal; S3, reading fault codes of a vehicle body electronic control unit one by one after the vehicle-terminal receives the vehicle diagnosis triggering signal, generating vehicle diagnosis raw data through all read fault codes of the vehicle body electronic control unit, transmitting the vehicle diagnosis raw data to the server, and transmitting the vehicle diagnosis raw data to a client after the receiver receives the vehicle diagnosis raw data. The method is simple and practical, and is high in safety.
Owner:SHENZHEN SEG SCI NAVIGATIONS CO LTD
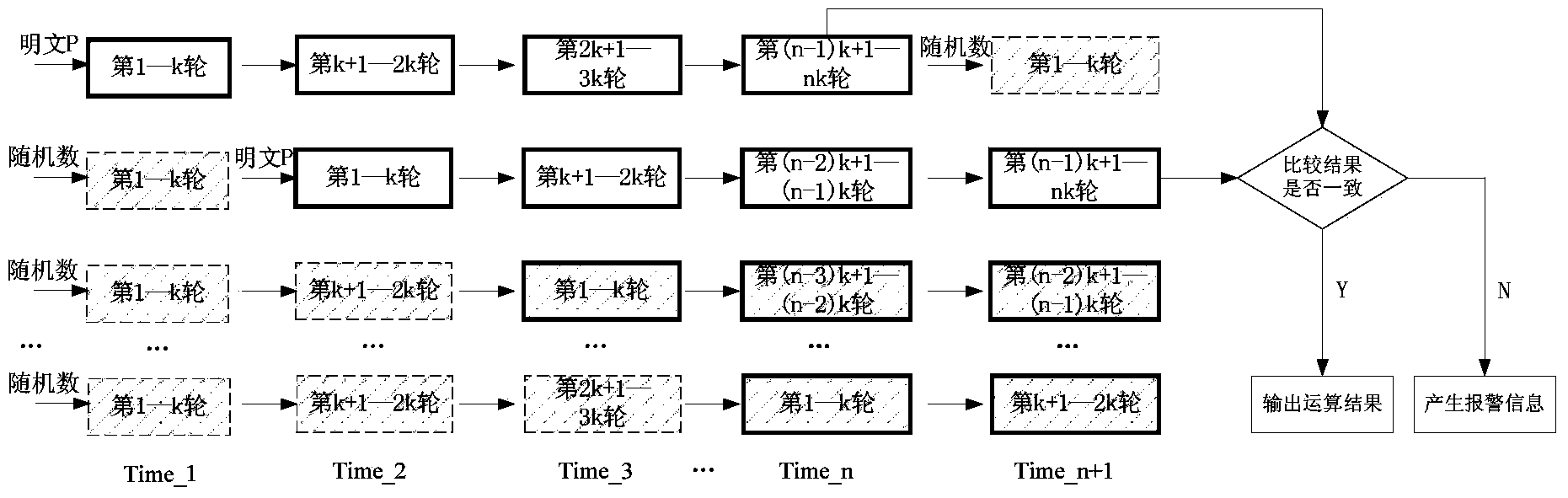
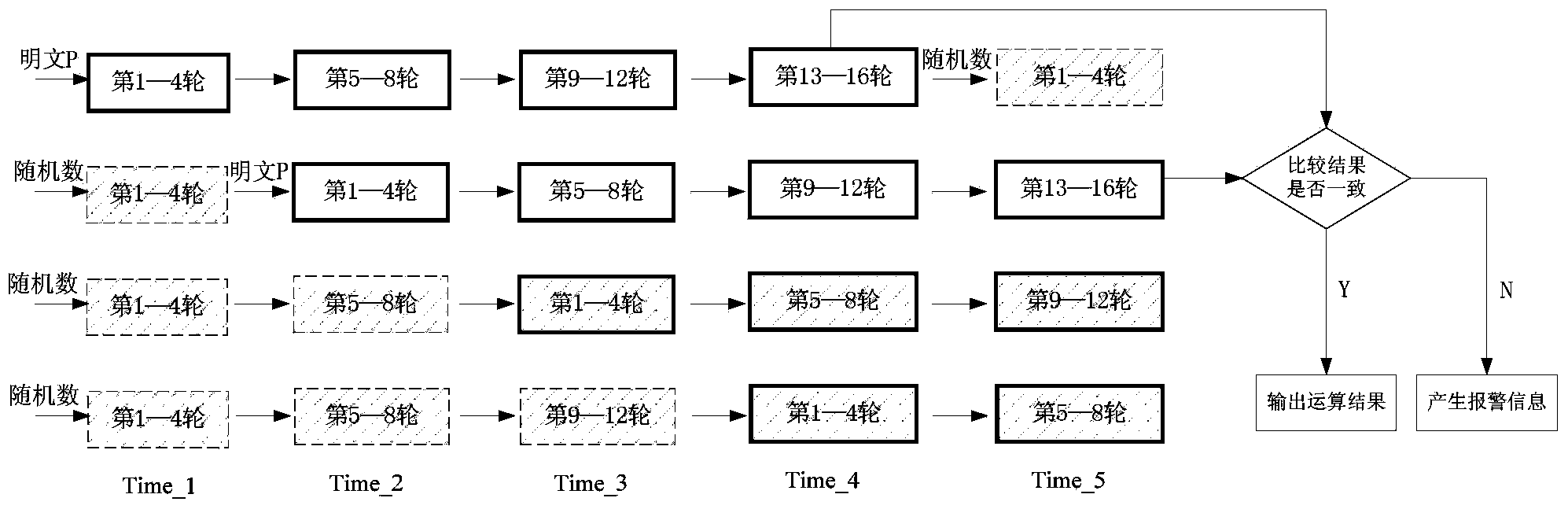
Protection method for side channel attack and fault attack
ActiveCN103634102AStrong securityImprove execution efficiencyEncryption apparatus with shift registers/memoriesSide channel attackPlaintext
The invention provides a protection method for side channel attack and fault attack. The protection method comprises the following steps of I. dividing operation of block cipher algorithm into a plurality of stages of pipelines; II. inputting real plaintext into two stages of pipelines selected at random, and inputting random number into other stages of pipelines; III. carrying out operation, and then comparing whether the operation results of the two real data are consistent after the operation is finished. The protection method can resist both side channel attack and fault attack, and has strong safety and high execution efficiency.
Owner:STATE GRID CORP OF CHINA +4
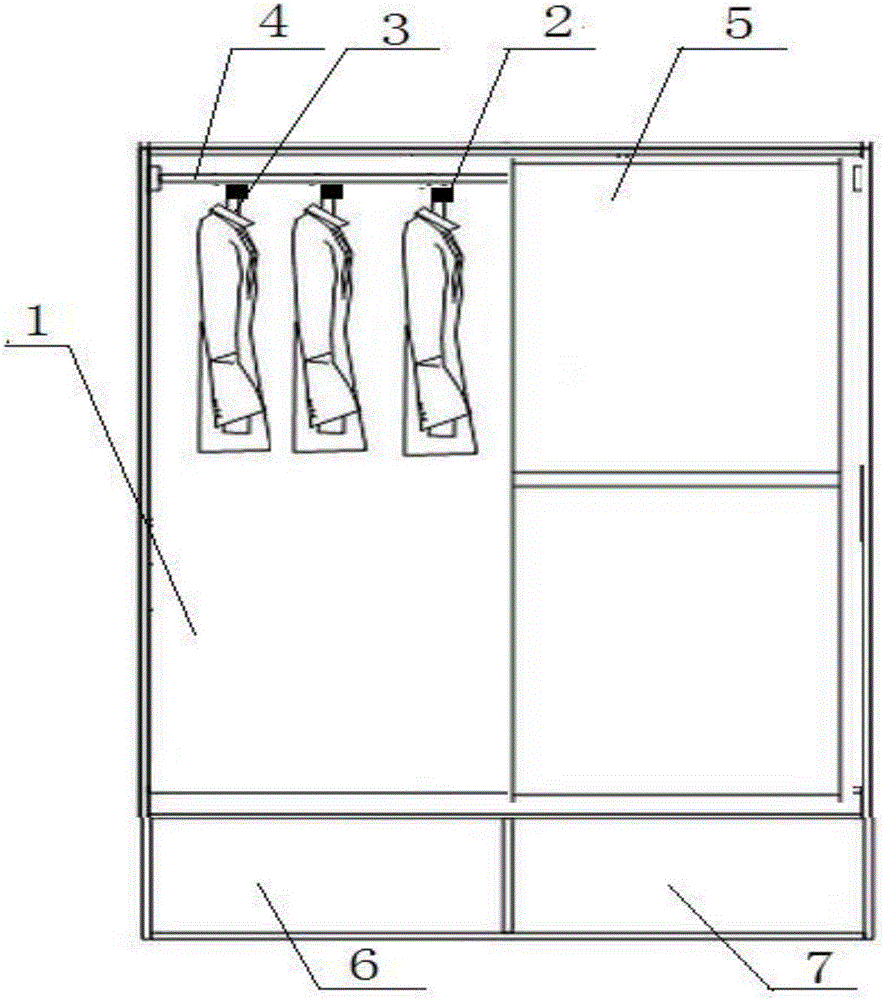
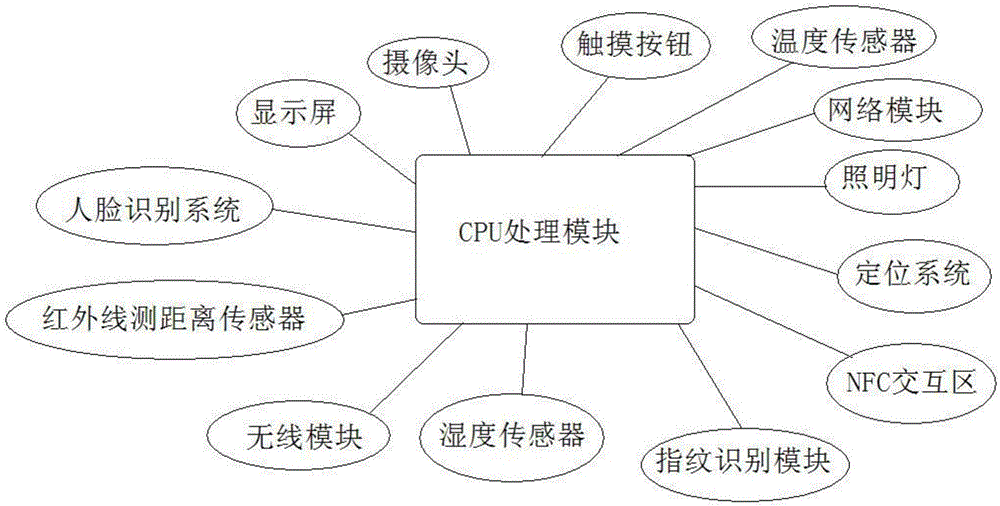
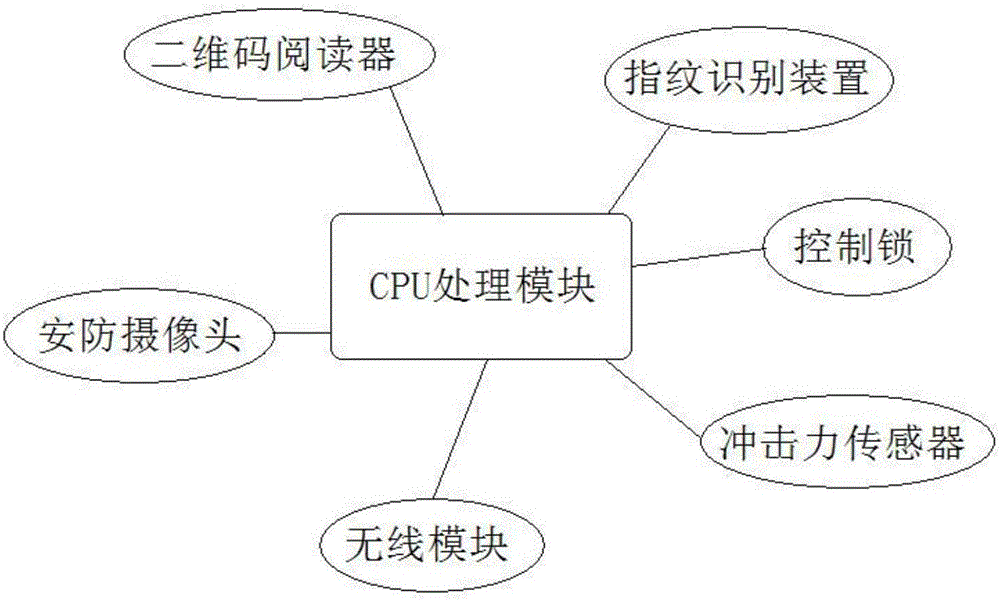
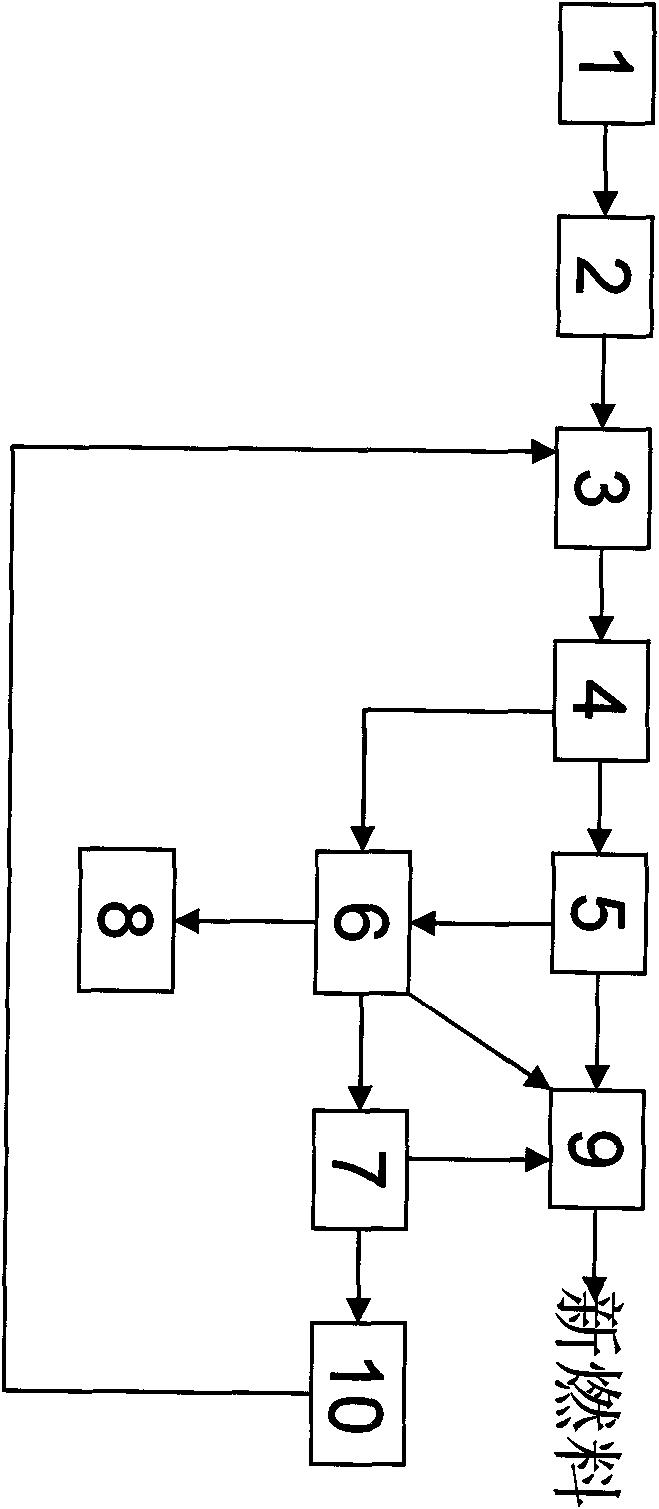
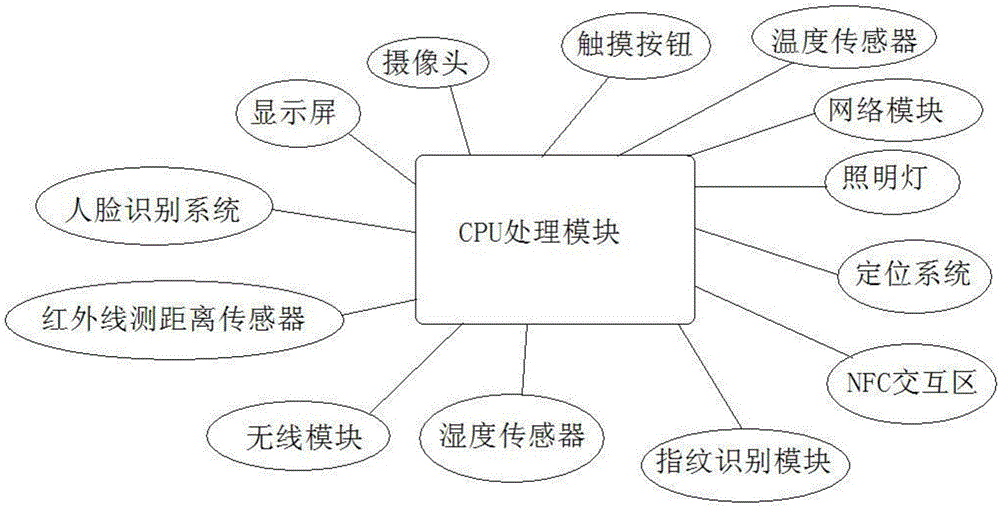
Home intelligent wardrobe and control method therefor
The invention discloses a home intelligent wardrobe. The home intelligent wardrobe comprises a clothes storage space, an accommodation space and a privacy space, wherein a clothes hanger transverse rod and clothes hangers are arranged in the clothes storage space; a push-pull panel is arranged outside the clothes storage space; the accommodation space and the privacy space are arranged at the bottom of the clothes storage space; the wardrobe also comprises an intelligent control system and an anti-theft control system for the privacy space; the intelligent control system comprises a display screen; and the display screen comprises a main display screen and a secondary display screen, a touch button, a camera, a human face identification system, a positioning system, a network module, a temperature sensor, a humidity sensor, an illumination lamp, a wireless module, a fingerprint identification module, and an NFC interaction region.
Owner:GUANGDONG LOCKA FURNITURE LIMITED
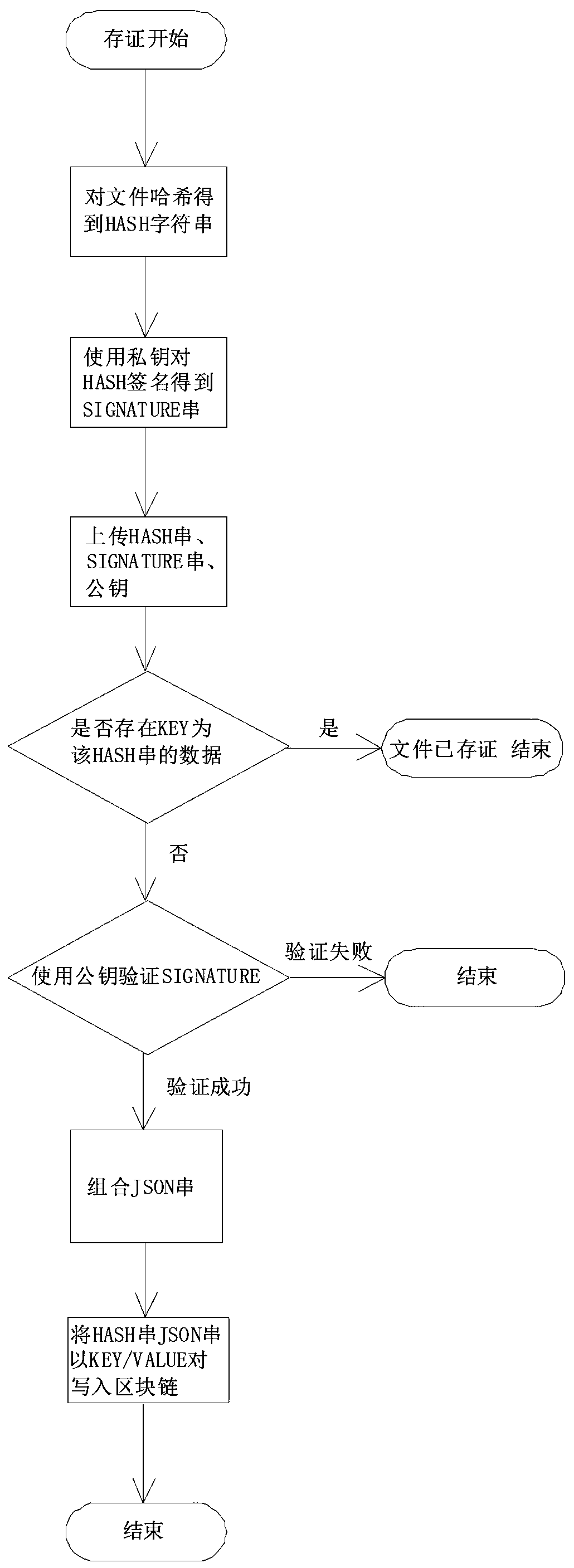
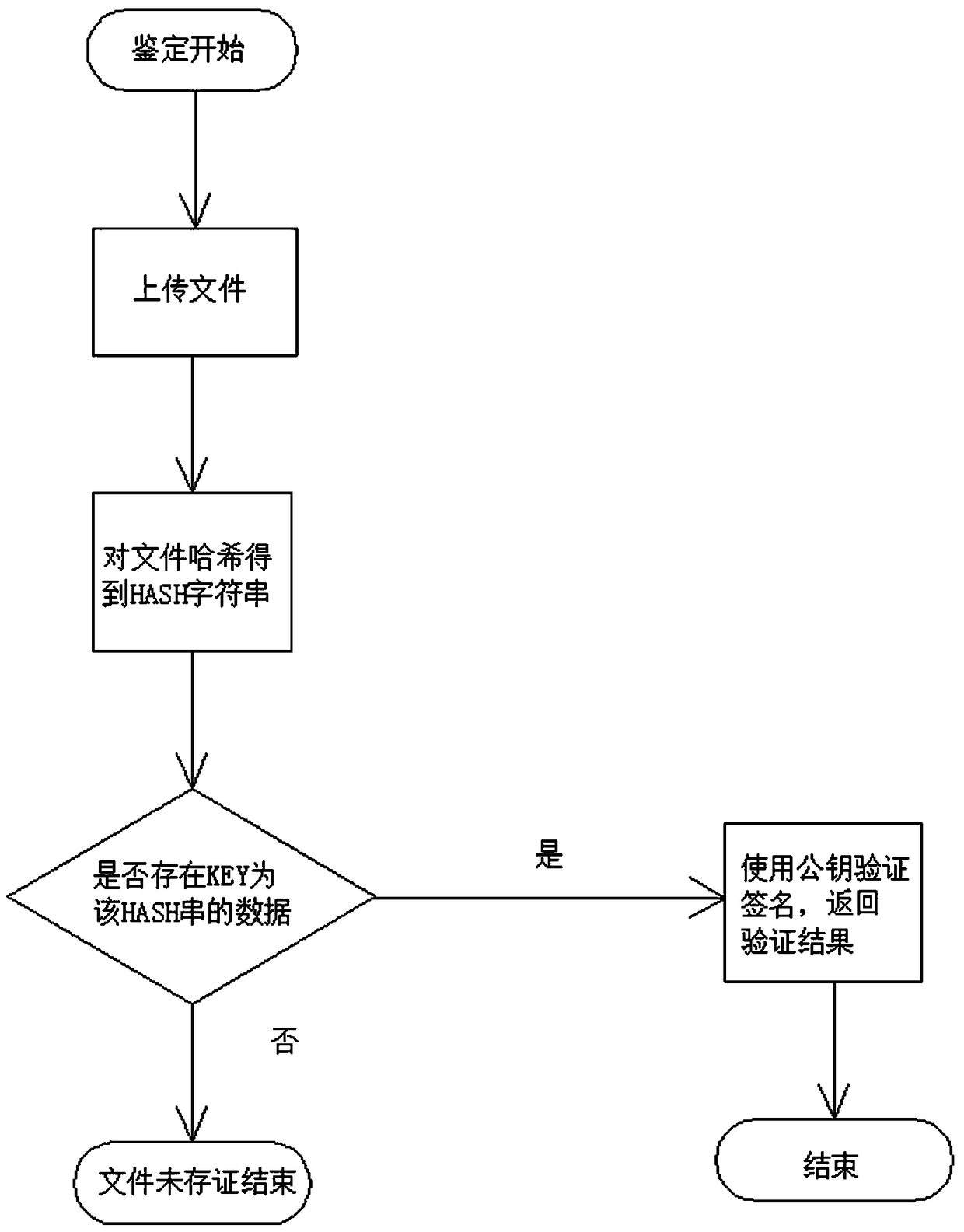
Method for implementing file evidence storage and authentication based on blockchain
InactiveCN108833111AIncrease credibilityStrong securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationBlockchainInformation extraction
The invention discloses a method for implementing file evidence storage and authentication based on a blockchain. The implementation process is as follows: firstly, configuring a blockchain network; then, performing evidence storage: performing hash on an evidence storage file by using a hash algorithm to obtain a hash value, encrypting the hash value by using an asymmetric encryption algorithm, extracting evidence storage information as a data model, assembling an evidence storage data structure according to the data model, and writing the assembled data into the blockchain network; and finally, performing authentication: performing hash on the file by using the hash algorithm to obtain a hash value, querying evidence storage data on the blockchain according to the hash value, and verifying the signature. Compared with the prior art, the method for implementing file evidence storage and authentication based on the blockchain disclosed by the invention has the advantage of high security, and has the characteristics of data disclosure and prevention of tampering based on the blockchain technology; and the privacy is good, a source electronic file is not uploaded to the network andis only stored at a file owner.
Owner:INSPUR QILU SOFTWARE IND
Beamforming-based dynamic direction modulation method
ActiveCN106888045AStrong securityReduce computational complexitySpatial transmit diversityMultiple carrier systemsRound complexityLow complexity
The present invention belongs to the array signal processing field in communication technologies and relates to a beamforming-based dynamic direction modulation method. According to the beamforming-based dynamic direction modulation method, one-time integration is performed on an antenna through an algorithm, so that a group of antenna weights is obtained; antenna weights are not required to be re-calculated in different symbol periods, and it only needs to randomly change the sequence of the antenna weight data, and a group of antenna weights is selected from the antenna weight data so as to be subjected to integration, and therefore, low-complexity dynamic direction modulation is realized; and a direction modulation method is adopted to update array element weights so as to replace base band modulation. With the algorithm provided by the invention adopted, the security of dynamic direction modulation can be realized under a low-complexity condition.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Chock system
ActiveUS20110226565A1Strong securityPrevent movementBraking element arrangementsPortable braking systemEngineeringMechanical engineering
A wheel chock restraint system which comprises a wheel chock having a base, a plurality of teeth extending outwardly from the base, the teeth extending in a first direction, and a locking member mounted within the chock, the locking member having a plurality of locking member teeth extending from a bottom thereof, the locking member teeth extending in a second direction generally opposed to the first direction, and an arrangement for moving the locking member in a generally vertical direction.
Owner:9172 9863 QUEBEC
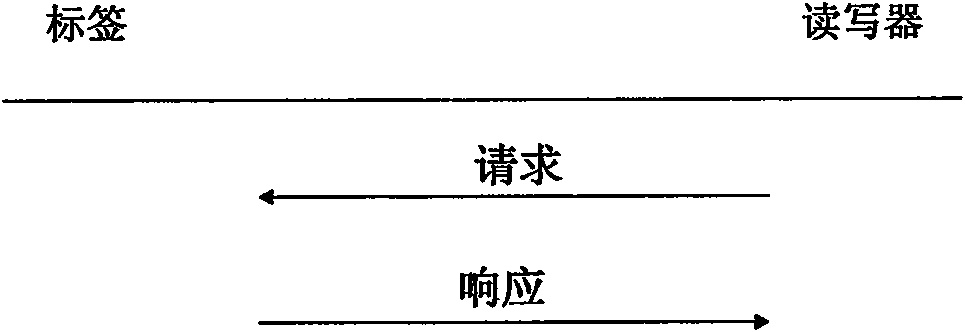
Radio frequency identification (RFID) privacy authenticating method
InactiveCN101645138AReduce storage and computing overheadStrong securityCo-operative working arrangementsRadio frequencyReader writer
The invention discloses a radio frequency identification (RFID) privacy authenticating method which comprises the following steps: system initialization: a reader-writer stores secret keys and indexesof all labels and a summary value of an index space; label recognition: the reader-writer transmits an authenticating request to the labels, the labels calculate and transmit authenticating information to the reader-writer, and reader-writer recognizes the labels after receiving the authenticating information; updating: after the labels are authenticated, the reader-writer updates the secret keysand the indexes of the labels and transmits updated information to the labels, and the labels update the stored secret keys and the indexes; and system maintenance: when the labels enter or depart from an RFID system, the reader-writer maintains the secret keys and the indexes of the labels. The invention can effectively resist various prior passive and active attacks; compared with an RFID authenticating method based on a balanced tree structure, the invention greatly reduces the storage and calculation cost at the label ends.
Owner:XI AN JIAOTONG UNIV
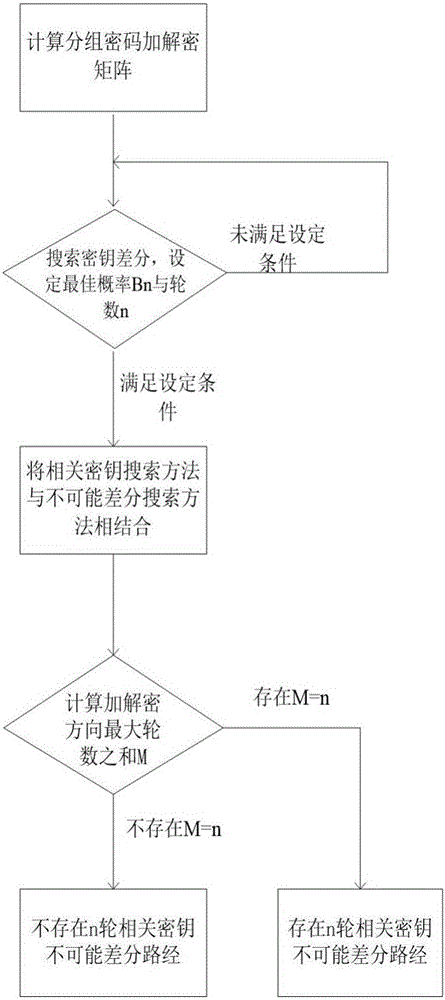
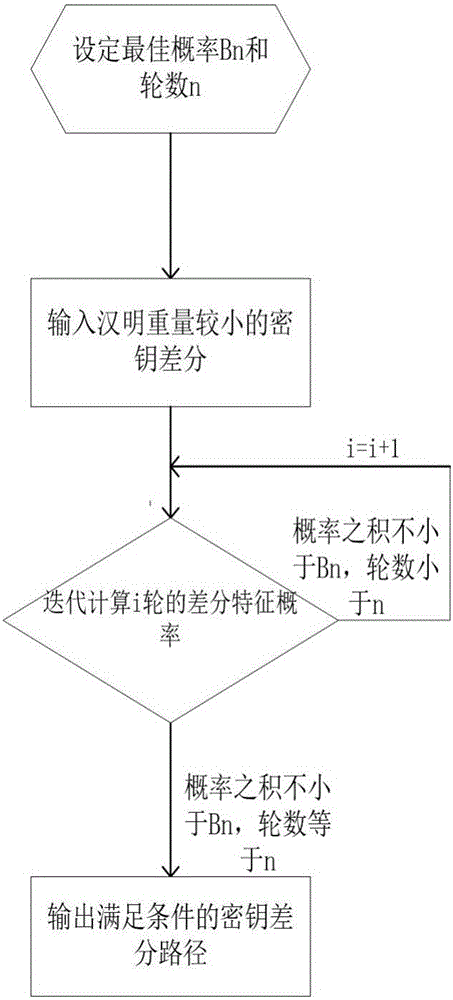
Searching method for impossible differential path of related key of block cipher
ActiveCN106027226ASolve the problem of findingIn-depth analysisEncryption apparatus with shift registers/memoriesRelated-key attackTheoretical computer science
The invention discloses a searching method for an impossible differential path of a related key of a block cipher. As an impossible differential attack method and a related key attack method are combined, the problems of automatic searching of the impossible differential path of the related key and searching of a longest analysis path in cryptanalysis are solved, and deeper and more thorough analysis for a cryptographic algorithm can be carried out. According to the searching method for the impossible differential path of the related key of the block cipher, the method for searching the impossible differential path of the related key is upgraded from the traditional manual analysis to computer automatic searching, the disadvantages that an existing manual analysis method is fussy and error-prone when being used for analyzing the cryptographic algorithm are avoided, the maximum length of the impossible differential path of the related key of the block cipher algorithm can be calculated rapidly and accurately, and the cryptanalysis efficiency is improved. The searching method for the impossible differential path of the related key of the block cipher realizes transformation of the cryptographic algorithm from a non-generalized Feistel structure to a generalized Feistel structure, can be widely applied to automatic search of the impossible differential paths of related keys of various cryptographic algorithms in different structures.
Owner:XIDIAN UNIV
Web3D encryption method based on dongle
The invention relates to a Web3D encryption method based on a dongle, in particular to a data encryption method through the USB (Universal Serial Bus) dongle under the condition of low costs. According to the encryption method, the whole Web3D operation interface is subjected to encryption protection by utilizing the USB dongle, namely, a user can perform a three-dimensional interactive operation on a browser only when the dongle is inserted into a client server, as long as no dongle is detected, the interface is locked, so that illegal embezzlement and access of data is prevented. Compared with other specialized dongles, ordinary dongles has low price. Besides, the Web3D encryption method based on the dongle is applicable to Web3D files of different formats and flexible.
Owner:FUZHOU UNIV
Method for manufacturing fuel through straw quick thermal cracking and fuel product thereof
InactiveCN101602954AEasy to operateStrong securityBiofuelsLiquid carbonaceous fuelsBoiling pointEngineering
The invention relates to a method for manufacturing fuel through straw quick thermal cracking and a fuel product thereof. The method comprises the following steps: crushing straw materials; drying the crushed materials; carrying out thermal cracking of the dried materials; completing gas-solid separation of the thermal cracking products; condensing gaseous biomass oil; collecting low-boiling point biomass oil; and mixing and grinding biomass carbon obtained after gas-solid separation, condensed biomass oil, water and surfactant. The fuel product comprises the following components in percentage: 30 to 60 percent of the biomass carbon, 2 to 15 percent of the heavy biomass oil, 0.2 to 1 percent of the surfactant, and the balance of water. The method converts straw through quick thermal cracking and makes straw into the novel fuel product of the biomass oil, the biological carbon and the water; moreover, the method has the advantages of lower production cost, higher yield of biomass fuel and better control of quick thermal cracking conditions. The fuel product has the advantages that the product has high thermal value and low sulphur content and does not block up pipelines and burner nozzles frequently during combustion; moreover, the product has stable performance and is convenient for transportation and storage. Therefore, the fuel product can be widely used in thermal power plants, heating boiler rooms, and the like.
Owner:BEIJING YIMINBAO ENERGY TECH CO LTD
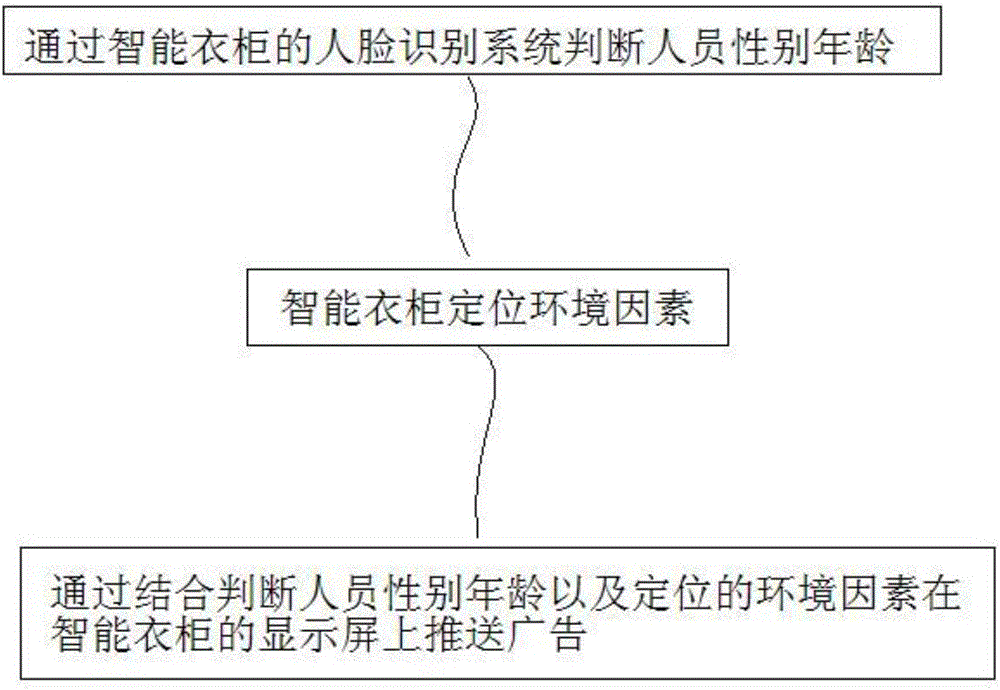
Advertisement pushing and intelligent screening intelligent wardrobe control method
ActiveCN106843028ASecurity GuaranteeStrong securityProgramme controlWardrobesComputer scienceRecognition system
The invention discloses an advertisement pushing and intelligent screening intelligent wardrobe control method. The advertisement pushing and intelligent screening intelligent wardrobe control method comprises the steps of (1) determining the age and gender of a user through a face recognition system of an intelligent wardrobe, (2) positioning environmental factors through the intelligent wardrobe, (3) by combining the age and gender of the user with the positioned environmental factors, pushing advertisement on the display screen of the intelligent wardrobe.
Owner:上海如晶新材料科技有限公司
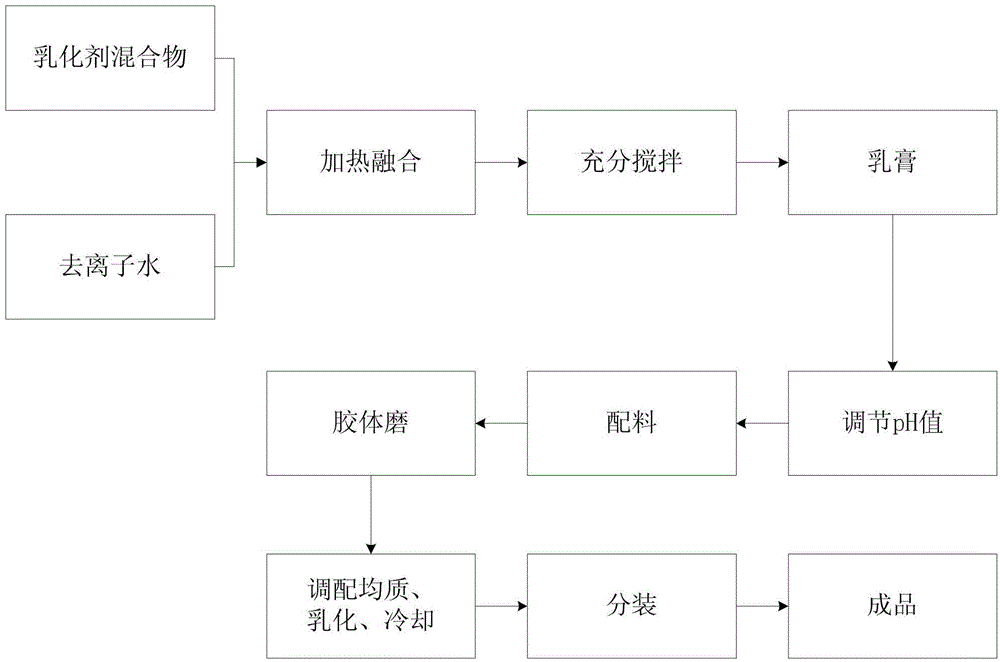
Preparation method and application of novel edible moisturizing nutritional ointment
The invention discloses a preparation method and application of a novel edible moisturizing nutritional ointment, and belongs to the technical field of cosmetic processing. The preparation method comprises the following steps: treating abelmoschus esculentus, treating propolis, preparing a liquorice root extract, extracting ginkgo leaf flavonoids, preparing fibroin protein, preparing perilla oil, preparing pine seed oil, and preparing an emulsifying agent. The preparation method specifically comprises the following steps: by taking an emulsion matter as a basic emulsion material, adding deionized water, fully stirring, and then adding 1-5% of an abelmoschus esculentus polysaccharide refined product in percentage by volume, 0.1-1.0% of a propolis viscous substance in percentage by volume, 0.1-1.0% of the liquorice root extract in percentage by volume, 0.1-1.0% of ginkgo leaf flavonoids in percentage by volume and 0.1-2.0% of fibroin protein in percentage by volume to obtain the moisturizing nutritional ointment. According to the preparation method and application disclosed by the invention, the safe and edible novel moisturizing ointment can be prepared by using abelmoschus esculentus, propolis, liquorice root, ginkgo leaves, fibroin, perilla oil, maize embryo oil, wheat embryo oil and pine seed oil, and the moisturizing ointment is suitable for being applied to the exposed skin which easily contacts with foods.
Owner:JILIN BUSINESS & TECH COLLEGE
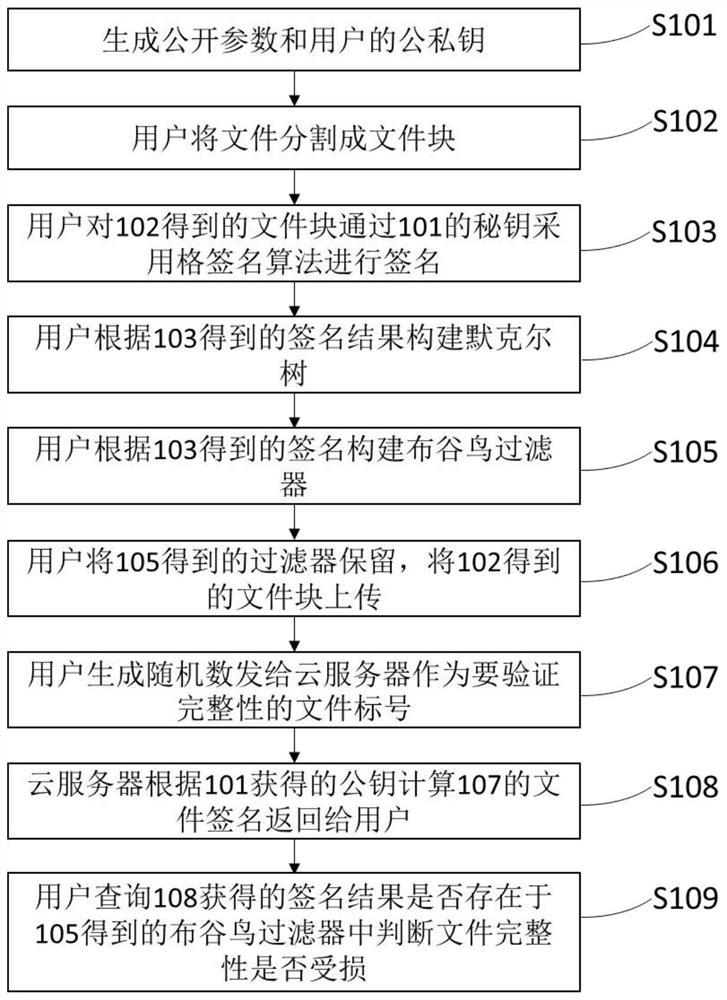
Cloud storage data integrity detection method and system based on blockchain
ActiveCN112565264AStrong securityImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesChain networkBlockchain
The invention discloses a cloud storage data integrity detection method and system based on a blockchain, and the method mainly employs a lattice signature algorithm to sign a file at a user side, caneffectively resist the threat of quantum computing, and guarantees that a signature is not cracked. According to the method, the Merkel tree is constructed, the signature value of the file is aggregated into the Merkel tree and combined with the cuckoo filter, on one hand, the requirement of dynamic operation of the file can be met, on the other hand, a complex signature verification process is simplified into a simple cuckoo filter query process, and the verification efficiency is remarkably improved. And meanwhile, the block chain network is introduced to replace the traditional TPA, so that the situation that the TPA colludes with the other party can be effectively avoided, the transparency of the information is improved, and the security of the scheme is further improved.
Owner:亿海兰特科技发展(长沙)有限公司
Conductive heating ceramic tube and preparation method
InactiveCN1499898AGood waterproof and insulation performanceStrong securityHeating element shapesElectric heatingChina clay
Two or more electric heating electrodes are arranged orderly and in interval along axial line or in annular along cross section inside ceramic tube. Material of the ceramic tube is evenly mixed china clay and stuffing of current conducting fine particle. Preparing an insulated surface according to conventional method for manufacturing ceramic tube and embedding bus bar in advance or posting bus bar after makes electric heater unit. The electric heater unit could be solid rod shaped. The invention has advantages of good water resistance and insurability, high safety and high conversion efficiency of electric heating.
Owner:黄加玉 +1
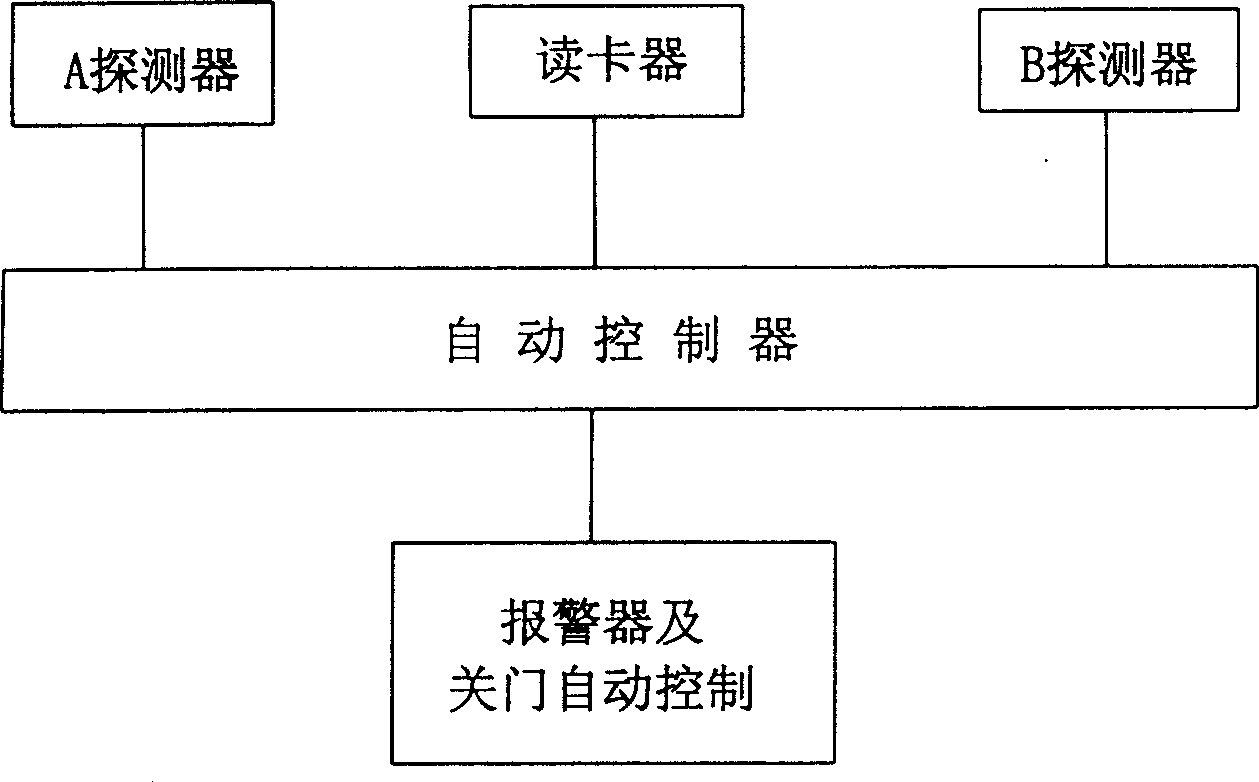
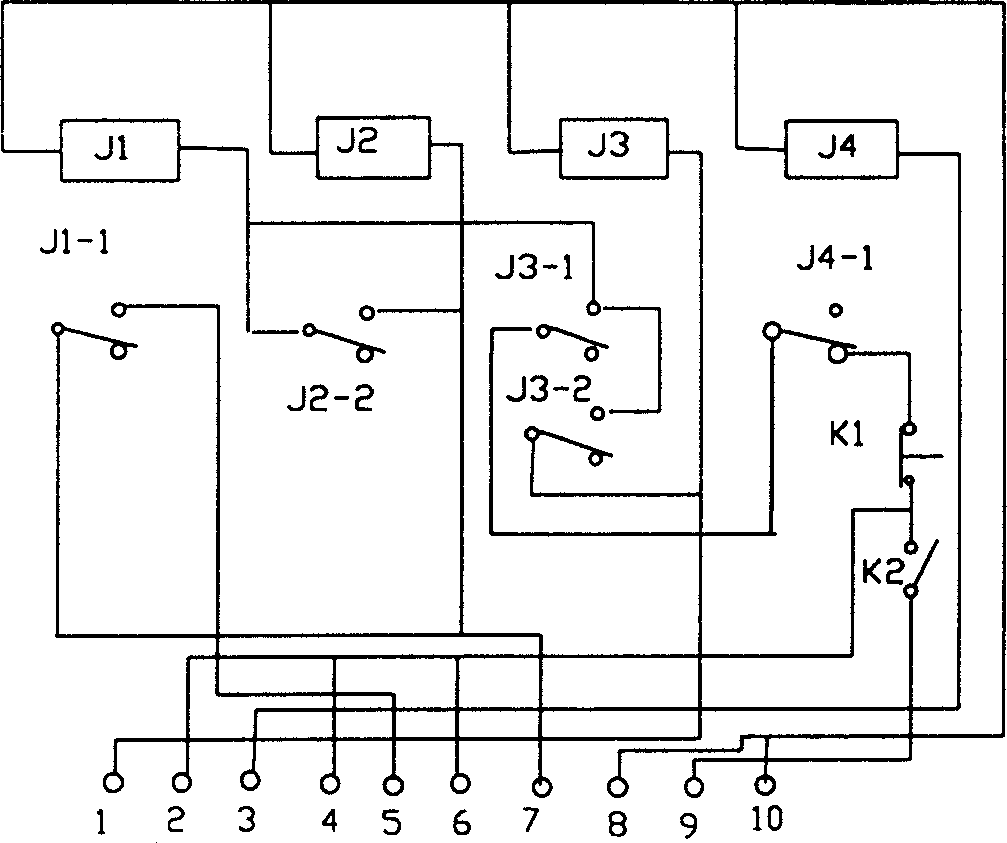
Open type gate inhibition unlawful penetration alarm device
The invention relates to an open type gate inhibition illegal accessing alarm device. It posits first explorer at channel porch and posits card reader at channel's middle parts and posts second first explorer at channel exit. It also has a auto controller circuit which interlocks the reference power of second explorer and makes it at pre-alert state when first explorer has tested the signal of people entering at the porch, and makes it at armed state when card reader receives the legal ID signal, or keeps the armed state when card reader receives the illegal ID signal. The alarm or auto closed driving control end sends signal when second explorer identifies the signal of people entering and works to achieve the function of auto alarm or auto interception.
Owner:锐意视觉科技(北京)有限公司
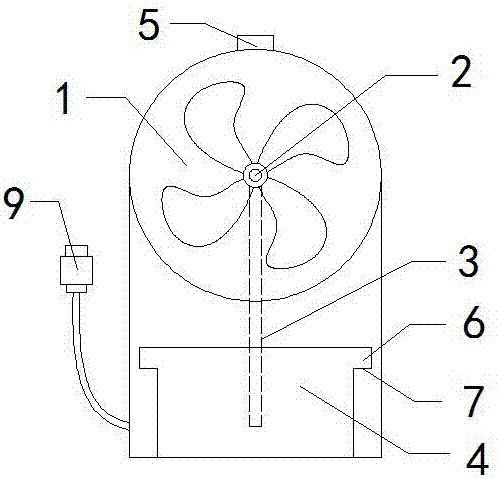
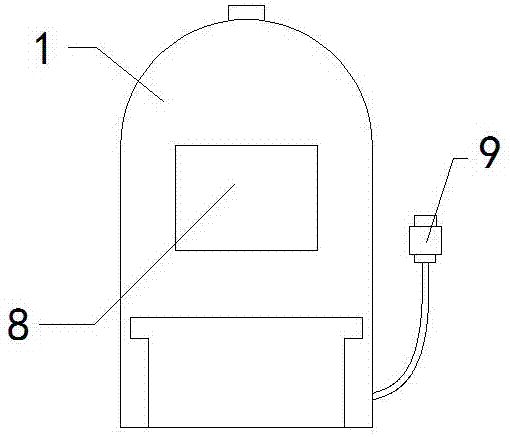
USB water supplementing fan
InactiveCN107575404AKeep moistStrong securityPump componentsLighting and heating apparatusEngineeringMoisture
The invention belongs to the field of fan articles, and particularly relates to a USB water supplementing fan. The USB water supplementing fan comprises a fan body 1, and is characterized in that an atomizing port 2 is formed in the middle of the fan body 1 and is connected with a water storage box 4 at the bottom of the fan body 1 through a water guiding pipe 3, the top of the fan body 1 is connected with an atomizing button 5, and guiding plates 6 are arranged on the left side and the right side of the water storage box 4 and matched with a guiding groove 7 in the bottom of the fan 1. According to the USB water supplementing fan in the claim 1, the USB water supplementing fan is characterized in that the fan body 1 is provided with a USB wire inserting head 8, and a battery bin 9 is arranged on the back. The provided USB water supplementing fan has the beneficial effects that water in air can be effectively supplemented, moisture of the skin is kept, an air blowing system and an atomizing system are independent of each other, safety is high, USB and battery power supply is provided, and practicability is good.
Owner:黄妙珊
Electric burglar-proof lock
InactiveCN101748937AStrong anti-theft performanceStrong securityAnti-theft cycle devicesAnti-theft devicesEngineeringMotorized vehicle
The invention relates to a lockset of a motor vehicle, in particular to an electric burglar-proof lock of a vehicle. The technical problem to be solved is to provide a safe anti-dismantling electric burglar-proof lock. The electric burglar-proof lock comprises a mechanical lock part and a circuit lock part which are controlled by each other, wherein the mechanical lock part has an anti-dismantling match-box-type structure, a bolt penetrates through a lock case from the inside and is connected with the screwed holes of a lock head and a lock catch; and a lock shaft, a lock shaft transmission structure and an electric motor which are used as the drawer of the match-box-type structure to be fixed in the lock case by the lock head and constitute an anti-dismantling covering structure of the bolt. The electric burglar-proof lock of the technical scheme of the invention is safe and anti-dismantling, is convenient to use and can lock the electronic start circuits of wheels and the vehicle at the same time.
Owner:廖祥能
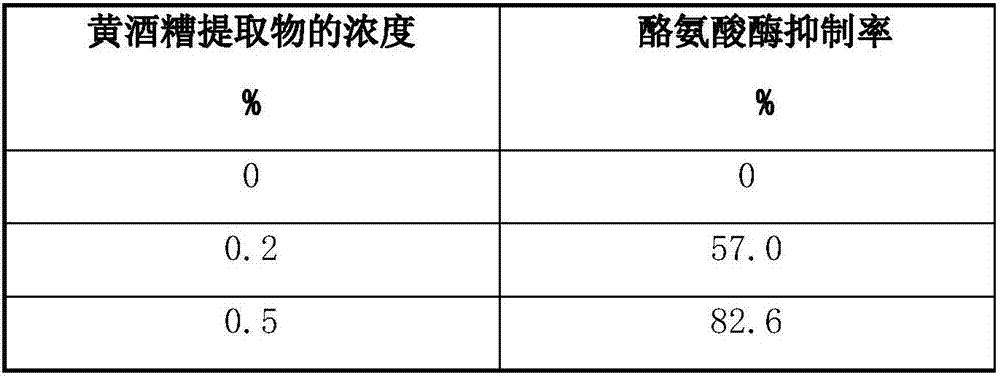
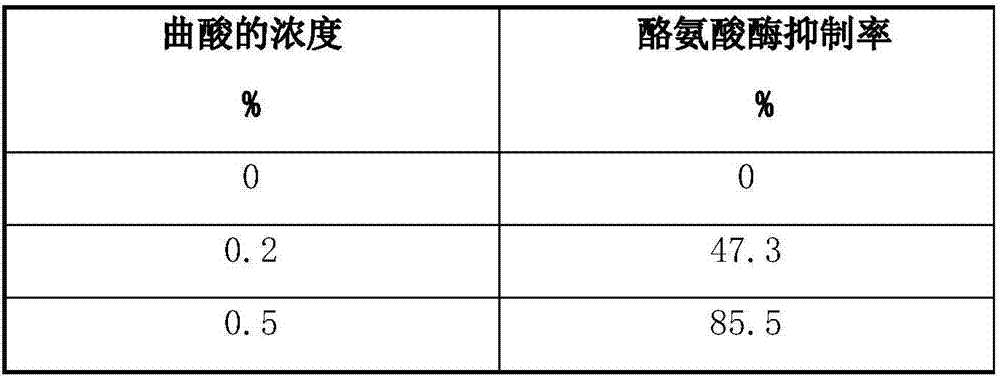
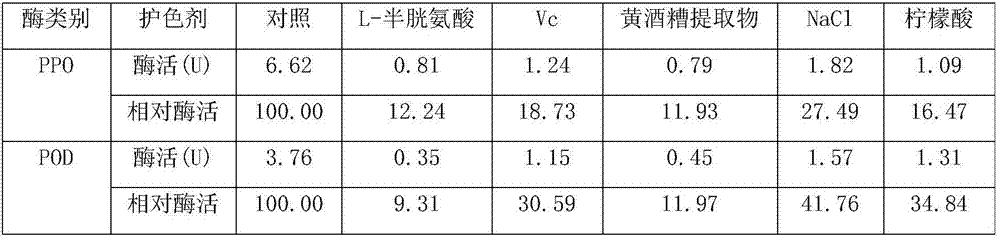
Tyrosinase inhibitor extracted from yellow wine lees and preparation method of tyrosinase inhibitor
ActiveCN107569433AWide variety of sourcesStrong securityCosmetic preparationsToilet preparationsWater contentPulverizer
The invention belongs to the technical field of food processing and particularly relates to a tyrosinase inhibitor extracted from yellow wine lees and a preparation method of the tyrosinase inhibitor.The method comprises the following steps: 1) obtaining fresh yellow wine lees from a production line of yellow wine produced through normal fermentation or obtaining fresh frozen yellow wine lees; 2)drying the yellow wine lees with a drying machine, so that the water content is less than 10%; pulverizing the yellow wine lees with a pulverizer, so as to obtain uniform fine powder with the particle size of less than 40 meshes; 3) extracting the fine powder of the lees with a volatile solvent with no residual toxicity, so as to obtain solution containing fat-soluble extract; volatilizing remaining alcohol under a pressure reduction condition, so as to obtain light yellow paste extract. The tyrosinase inhibitor has important application value in the fields of food process and cosmetics and has the functions of saving resources and protecting environment.
Owner:湖州老恒和酒业有限公司
Energy-saving environment-friendly flame-retardant architectural paint
The invention discloses an energy-saving environment-friendly flame-retardant architectural paint which comprises the following components in parts by weight: 30-50 parts of cement, 20-50 parts of paste ash, 10-25 parts of coal slag powder, 10-35 parts of POE (polyolefin elastomer), 10-36 parts of halogen-free expanded flame retardant, 10-14 parts of crystal II type ammonium polyphosphate, 11-16 parts of smoke suppressor, 11-21 parts of compatibilizer, 1-3 parts of hollow glass microsphere, 1-4 parts of graphite powder, 1-6 parts of kaolin, 1-9 parts of wood fiber (80-200 meshes), 3-8 parts of kieselguhr (80-180 meshes), 1-9 parts of film-forming assistant, 2-8 parts of acrylic emulsion, 3-7 parts of network interpenetrating emulsion, 1-6 parts of water-based dispersing agent BPS, 1-7 parts of magnesium hypophosphite and 1-3 parts of talcum powder. The invention has the advantages of high safety, high strength, favorable elasticity, light weight, heat preservation, heat insulation, sound absorption and radiation resistance, shortens the building cycle, improves the working environment, enhances the safety coefficient, and reduces the environmental pollution around the building area.
Owner:QINGDAO JIZHI ENERGY SAVING ENVIRONMENTAL PROTECTION
Mounting assembly for vehicle roof-box
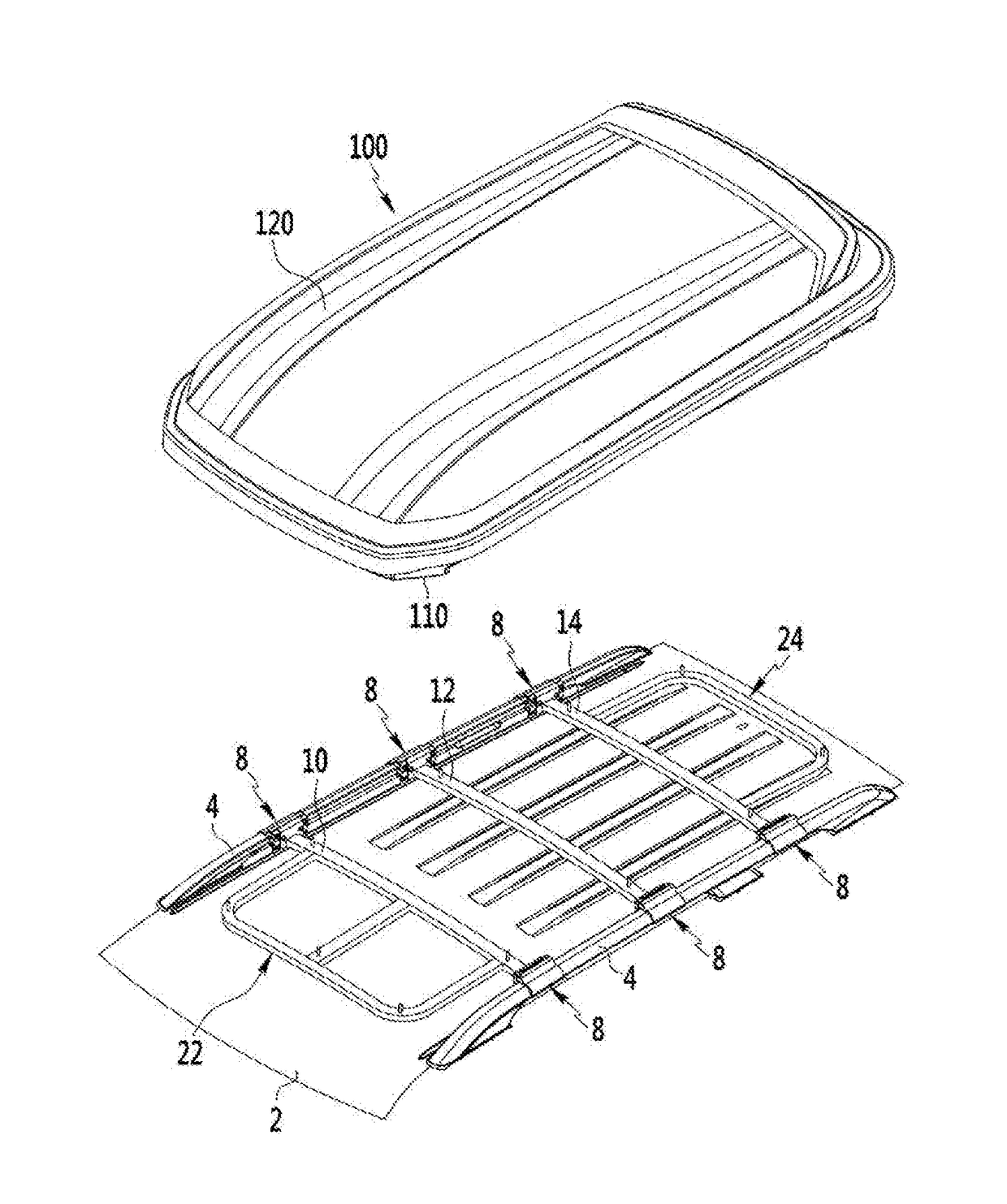
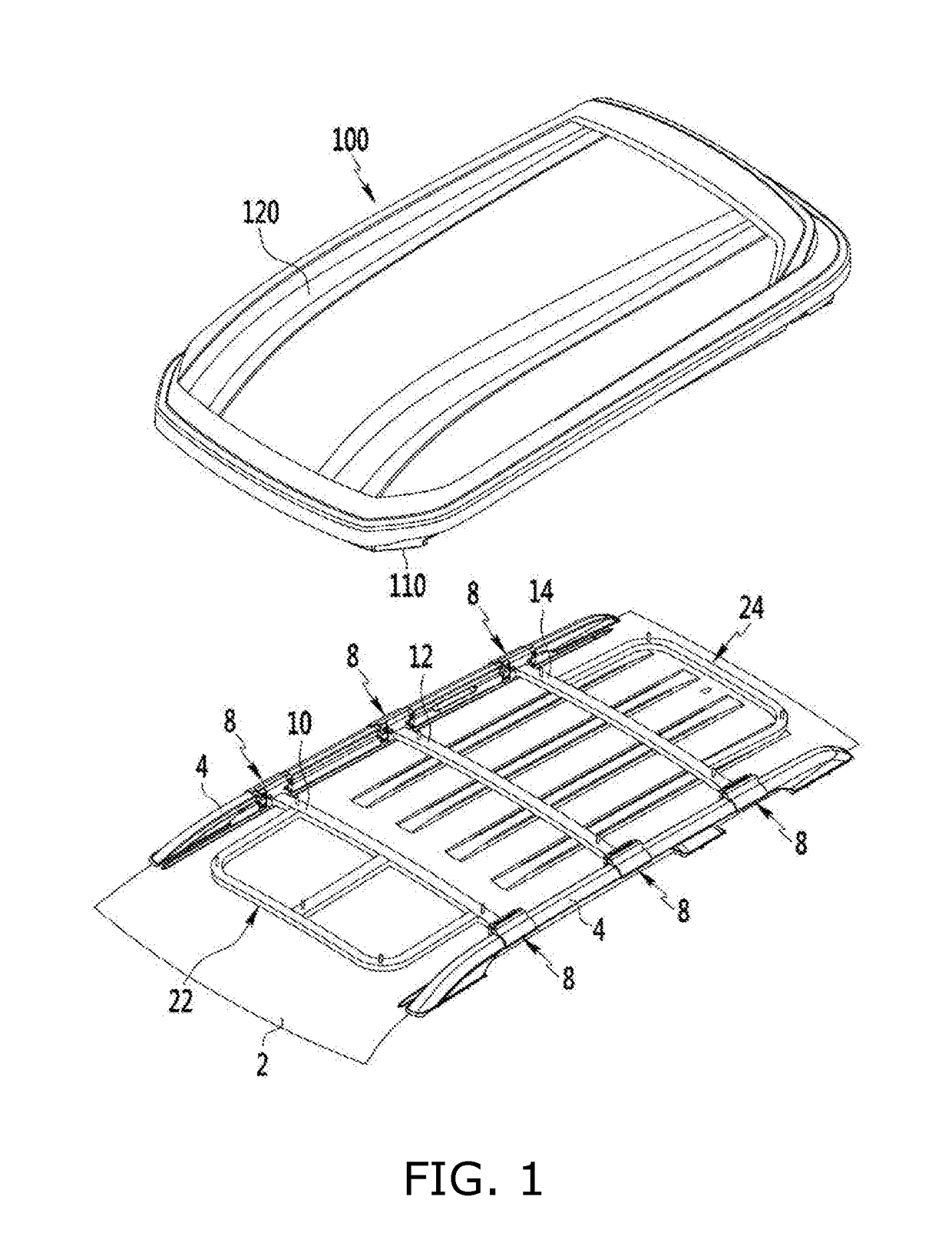
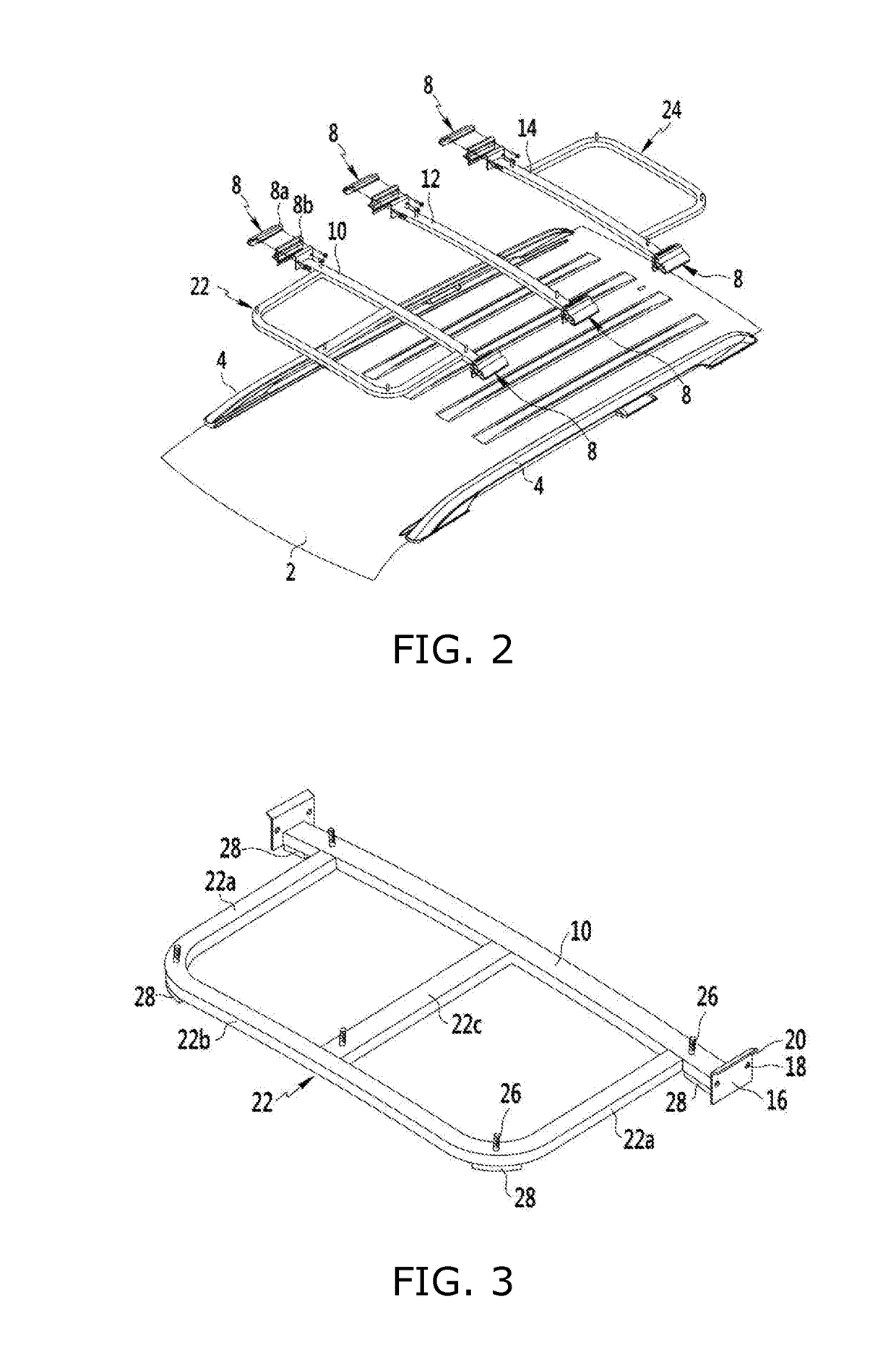
ActiveUS20170203698A1Easy to installReduced strengthSupplementary fittingsStampingEngineeringMechanical engineering
An assembly for mounting a vehicle roof-box on a vehicle roof panel comprises a pair of roof rails disposed on the vehicle roof panel at both sides thereof respectively in a front-rear direction of the vehicle roof panel; a plurality of cross-bars spacedly arranged in the front-rear direction, wherein each cross-bar has two opposing ends removably coupled to the roof rails respectively, wherein the vehicle roof-box is mounted to the cross-bars; and a plurality of securing means configured to removably secure the cross-bars to the roof rails, wherein each of the plurality of securing means includes a first bracket movable along each of the roof rails, and a second bracket screw-coupled to the first bracket to secure the first bracket to each of the roof rails, wherein an end of each of the cross-bars is fixed to the second bracket.
Owner:KH TECH
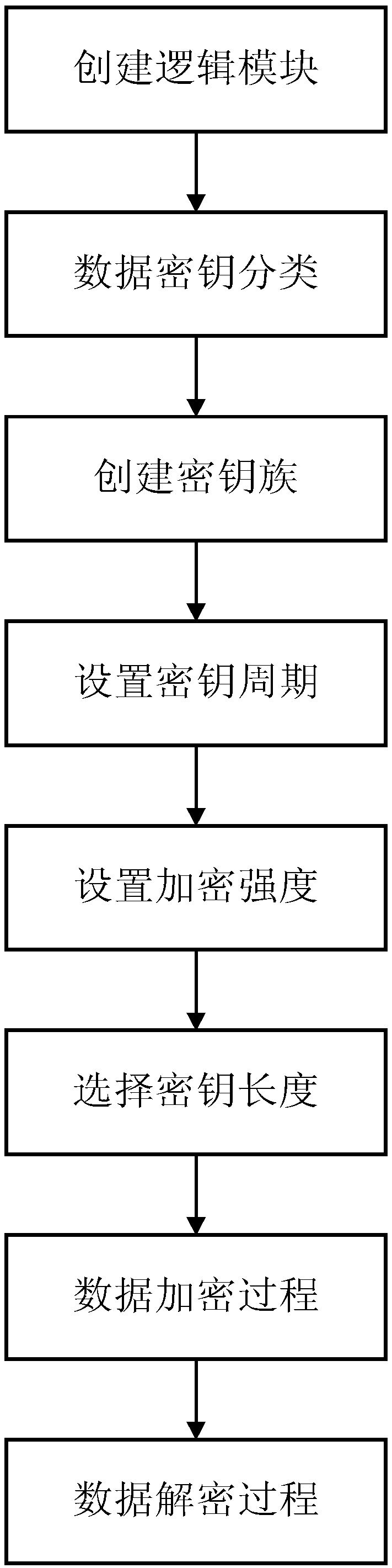
A database encryption method based on an AES algorithm
InactiveCN109376543AStrong securityIncrease the difficulty of crackingDigital data protectionDatabase encryptionKey size
The invention relates to a database encryption method based on AES. Firstly, aiming at the database encryption problem, the shortcomings of the present database encryption such as low security, easy to crack, information leakage and the like are analyzed. Then, according to the encryption strength of AES encryption algorithm, the key length and key period can be set flexibly according to the attributes, which is difficult to crack. Finally, the method is used in database encryption to establish a set of database encryption method with strong security and great difficulty to crack. The invention provides a database encryption method based on an AES algorithm which is strong in security and difficult to crack. The encryption strength, the key length and the key period are set according to the data attribute by using the AES algorithm.
Owner:ZHEJIANG UNIV OF TECH
Well lid with safety warning device
ActiveCN106759511APrevent stray entrySimple structureArtificial islandsUnderwater structuresEngineeringSlide plate
The invention relates to the field of municipal public facilities, in particular to a well lid with a safety warning device. The well lid with the safety warning device comprises the well lid, the warning device and a support device; connecting rods connected with a well wall are arranged on two sides of the support device; the warning device is mounted between the well lid and the support device; the warning device includes a warning box; a compressed gas box is arranged at the bottom of the warning box; a separation plate for stopping gas leakage is arranged at the upper part of the compressed gas box; a through hole connected with the compressed gas box is formed in the middle position of the separation plate; extension springs are arranged on two sides of the upper part of the separation plate; a slide plate is arranged at the upper parts of the extension springs; a lifting rod matched with the through hole is arranged in the middle position of the slide plate; and an exhaust port is formed in the outer side between the separation plate and the slide plate, and is connected and provided with a warning airbag. The device prevents loss of the well lid and accidental falling of pedestrians and vehicles into a pit, and reduces the danger.
Owner:TIANJIN CHENGJIAN UNIV
Folding structure of saddle supporting seat
The invention discloses a folding structure of a saddle supporting seat. The saddle supporting seat is formed by symmetrically wedging a left cover plate and a right cover plate; a placing hole is formed in the cover plate; a spanner is arranged in the placing hole; a rotary fulcrum support at the lower part of the spanner is arranged at the bottom of the cover plate; the middle part of the spanner is provided with a steel wire rope hole; a plunger seat is arranged on a disc where the cover plate is rotationally connected with a cross beam; plungers are held in positioning holes of the plunger seat; the heads of the plungers are exposed out of the cover plate and can be inserted into fixed holes in a cross beam shaft seat; the two plungers distributed left and right on the saddle supporting seat are connected by a spring; the plungers are provided with traction holes; and after one end of a steel wire rope passes through the steel wire rope hole and is fixed on the spanner, the other end of the steel wire rope passes through the traction holes of the plungers and is fixed. The saddle supporting seat has the advantages of strict structure, strong safety, practicability and reliability; and a practical outfit is provided for production and use of a folding electric bicycle.
Owner:WUXI SHANGGE IND DESIGN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com