Web3D encryption method based on dongle
An encryption method and dongle technology, applied in the direction of digital data authentication, etc., can solve the problems of inability to modify, poor flexibility, resource misappropriation, etc., to shorten the development cycle, prevent misappropriation and cracking, and enhance security strength.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
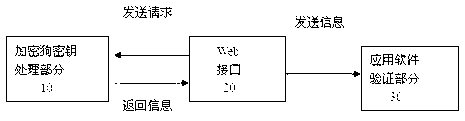
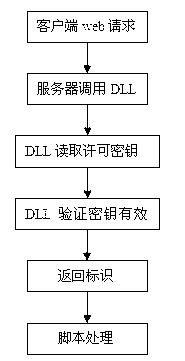
[0039] Such as figure 1 As shown, the main structure of the scheme may include three parts: dongle key processing part 10, web interface part 20, and application software verification part 30.
[0040] Among them, in order to prevent illegal copying of the program and the theft of dongle information, the dongle key processing part 10 of this solution encrypts key data by combining software and hardware.
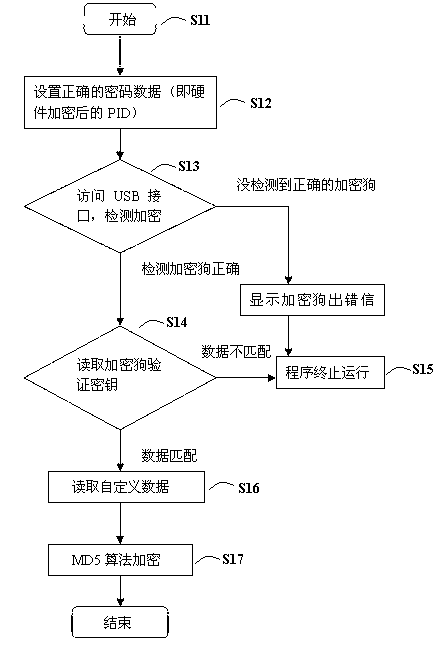
[0041] 1. In terms of hardware, software developers must first understand the internal settings and usage methods, reading and writing tools and drivers of the dongle. You can directly use the API interface provided by the dongle manufacturer and the corresponding dynamic link library file DLL to carry out a new design for the seed and product identification number (PID). Finally, use the HAMC-MD5 key (seed) in the dongle hardware The HMAC-M...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com