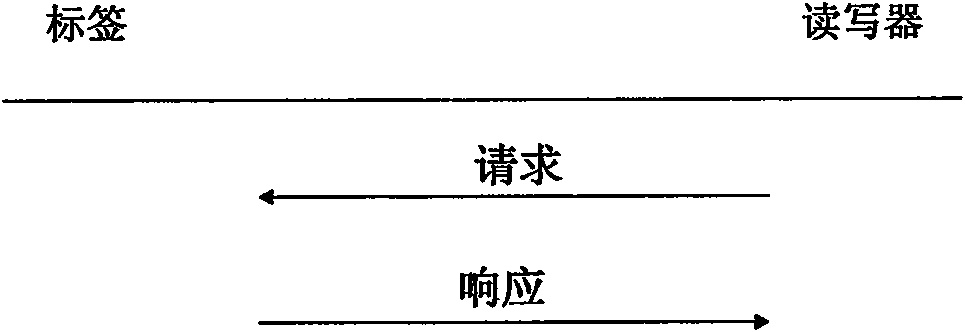
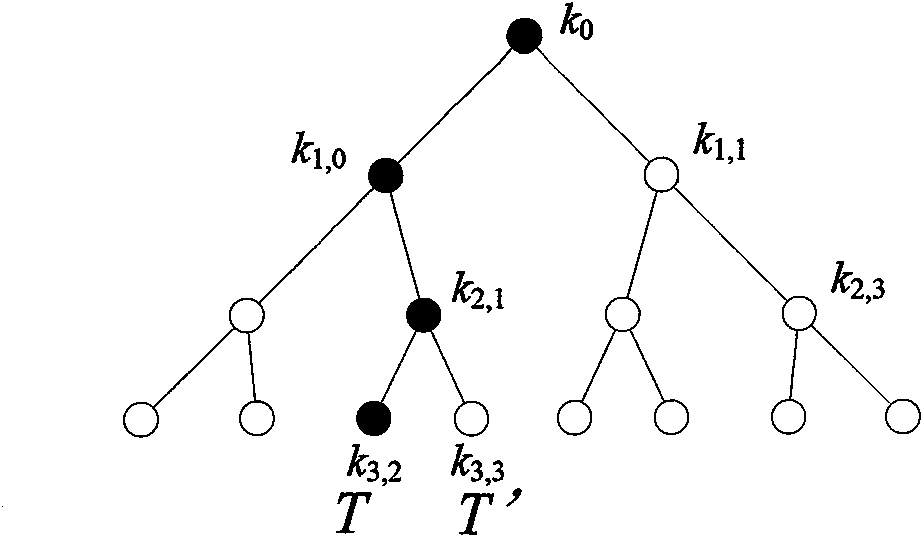
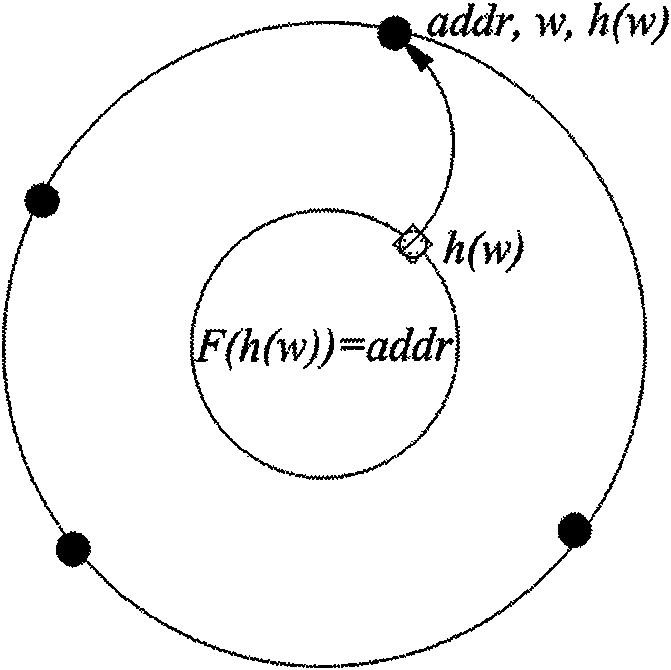
Radio frequency identification (RFID) privacy authenticating method
An authentication method and radio frequency identification technology, applied in the security technology field related to radio frequency identification tag authentication, can solve problems such as inability to meet forward security, affect tag privacy, lack of update mechanism, etc. Security, the effect of ensuring forward security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the purpose, technical scheme and advantages of the present invention clearer, the following will be combined with the attached image 3 , 4 The present invention is further described in detail.
[0026] Let h(·), F(·) be the digest function {0, 1} in the sense of cryptography * → {0, 1} l , where l is the security parameter of the RFID system, here is the security strength of the tag. Suppose there are n tags T in the system i , 1≤i≤n, and reader R. Reader R organizes the keys of all tags according to the tags' indexes.
[0027] When the RFID system is initialized, select the security parameters of the system and the index length b. Reader for each tag T i Randomly specify a key key i and index index i . And use the summary function h( ) to calculate the index i The digest value {h(s)} corresponding to all elements s in the domain S of . The tuple (h(s), s) is stored at physical address F(h(s)). The function F(·) is a processing of the out...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com