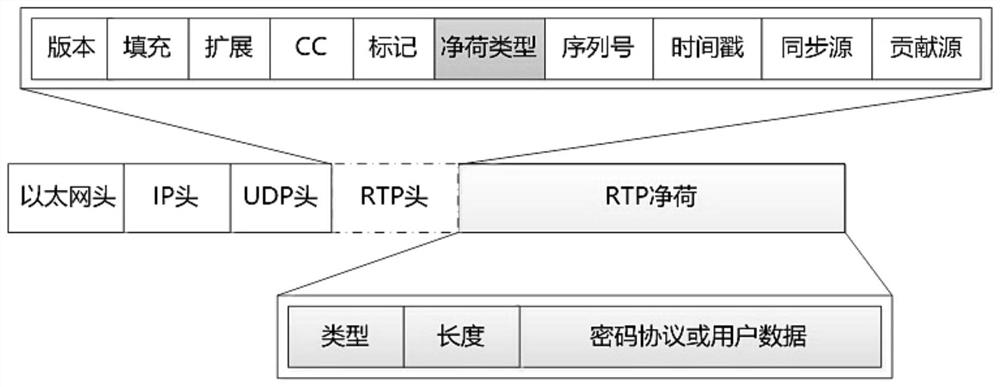
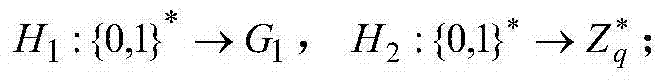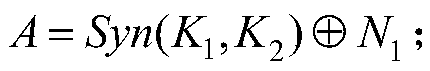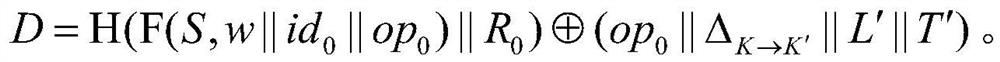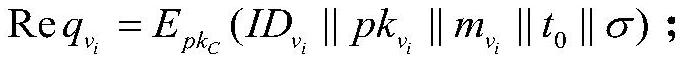Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38results about How to "Guaranteed forward security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Certificate-based forward security signature method and system thereof
InactiveCN102420691APrevent leakageHigh utility valueKey distribution for secure communicationUser identity/authority verificationPasswordKey generation
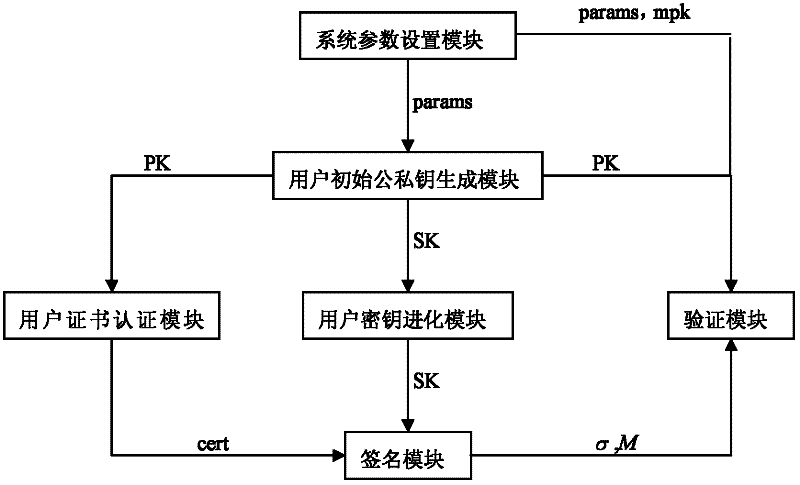
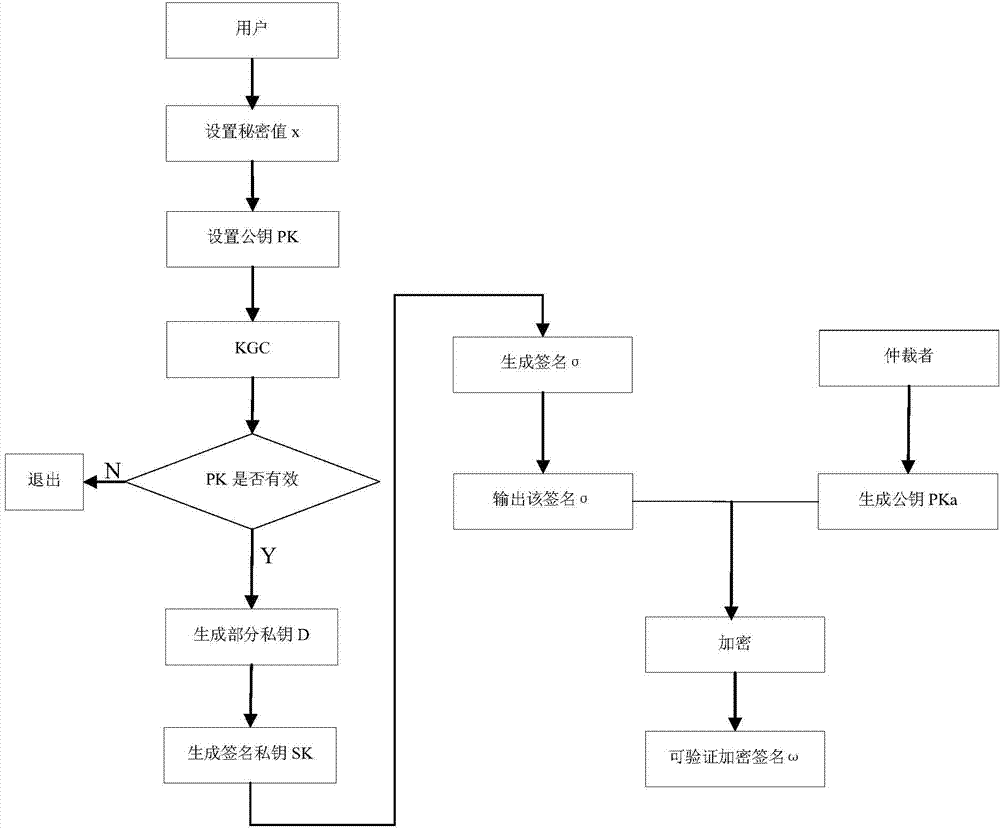
The invention discloses a certificate-based forward security signature system. The system comprises: a system parameter setting module, a user initial public or private key generation module, a user certificate authentication module, a user secret key evolution module, a signature module and a verification module. The system parameter setting module generates a system main secret key and a public system parameter and sends to the other modules. The user initial public or private key generation module generates the public key and the initial private key of the each user. The user certificate authentication module issues the certificate to the valid user and sends to the signature module. The user secret key evolution module evolutes the private key of the user and sends to the signature module. The signature module generates the signature to any messages and sends to the verification module. The verification module verifies validity of the signature. By using the system, partial secret key leakage problems based on a certificate password system can be solved. A practical value is high. The invention also discloses a certificate-based forward security signature method.
Owner:HOHAI UNIV
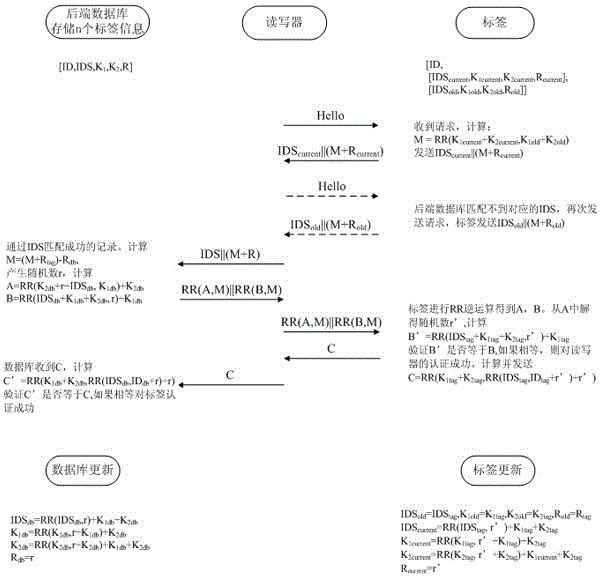
RFID (radio frequency identification) mutual authentication protocol method
ActiveCN103078741AReduce computing needsReduce storage requirementsUser identity/authority verificationCo-operative working arrangementsThree stageExclusive or
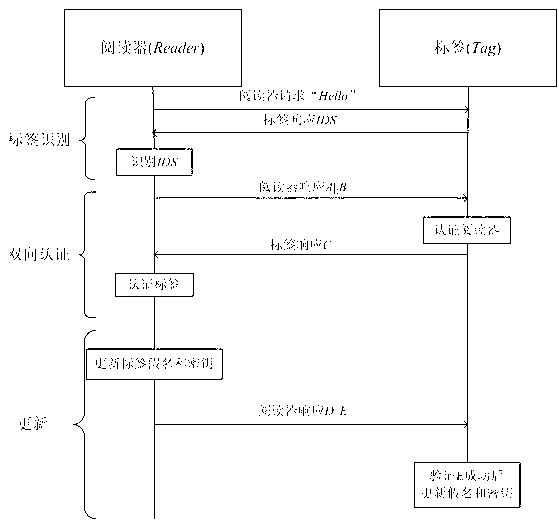
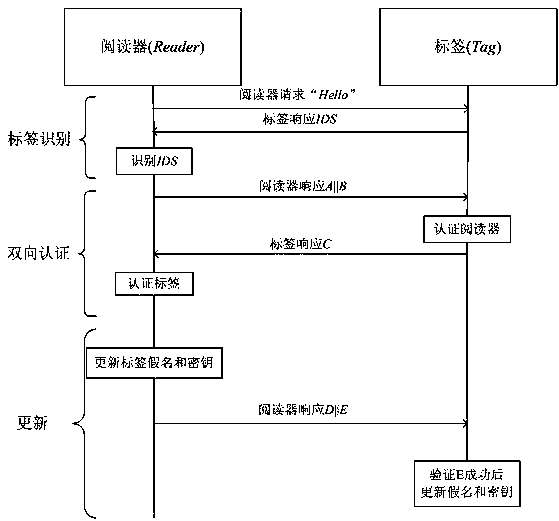
The invention relates to an RFID (radio frequency identification) mutual authentication protocol method, which comprises the following three stages: a tag identification stage, a mutual authentication stage and an update stage, wherein at the tag identification stage, a reader sends a request to a tag, and the tag returns an identification section (IDS) to the reader after receiving the request; at the mutual authentication stage, after the IDS is identified by the reader, an exclusive-or operation related to a digital synthetic operation is conducted to obtain A and B, A and B are sent to the tag, after the reader is identified by the tag through received A||B, related calculation is conducted to obtain C, C is sent to the reader, and the tag is identified by the reader; and at the update stage, after C is successfully identified by the reader, IDS and secret keys (K1 and K2) in C are updated, then D and E are calculated and sent to the tag, and after E is successfully identified by the tag, IDS and secret keys of E are updated. Only the simple digital synthetic or exclusive-or operation exists in the RFID mutual authentication protocol method. Therefore, the RFID mutual authentication protocol method has the beneficial effects that the calculation amount and storage space of the tag can be effectively reduced, various attacks such as impersonation, retransmission, tracking and denial of service can be resisted, and forward security is provided.
Owner:上海诚扬信息科技有限公司
Dynamic authentication method between reader and tag card and implementing device thereof
InactiveCN102136079AEasy to useEffectively hideCo-operative working arrangementsDigital data authenticationComputer hardwareHash table
The invention discloses a dynamic authentication method between a reader and a tag card and an implementation device thereof for solving the technical problem that the traditional authentication method must depend on real-time online reliable and safe connection with a backstage database, and cannot authenticate the tag card with the reader autonomously at a high degree. In the method, only a legal reader can acquire corresponding tag authentication information from an authentication database to authenticate or update the state of the corresponding tag; only a legal tag can be processed by the legal reader; a dynamic updating mechanism is applied to the tag identification (ID) in the authenticating process to ensure the forward security, and the reader stores the tag card information by adopting a Hash table, thereby improving the authentication speed; and data synchronization is realized skillfully in an attribute value mode; and the use of random numbers ensures that different data packets can be used in each authentication, so that the position information of the tag is effectively concealed and high security characteristic is provided.
Owner:ZTE CORP
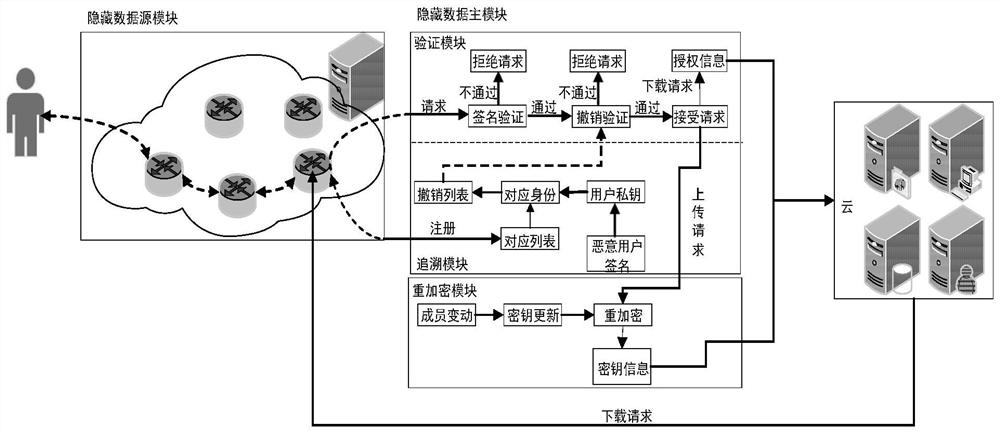
Anonymous data sharing method and system based on data source and data main hiding
ActiveCN111600875APrivacy protectionReduce overheadKey distribution for secure communicationIp addressData source
The invention discloses an anonymous data sharing method and system based on a data source and data main hiding. In the stages of registration and request initiating, effective access control is achieved through group signature, anonymous authentication is completed to protect user identity privacy, and meanwhile the problem that the user identity is associated due to leakage of the user IP address is solved by hiding the user IP address through onion routing. In the file uploading stage, the group administrator re-encrypts the uploaded file by using a re-encryption technology and generates key information; in the file downloading stage, after revocation verification and signature verification are completed, a group administrator generates authorization information for a user, so that theuser can obtain a decryption and re-encryption key from key information, and the forward security of the scheme is ensured; and in the group dynamic stage, the group administrator performs key updating and updates encryption of the cloud file, so that the expenditure of the user side is greatly reduced.
Owner:JIANGSU UNIV
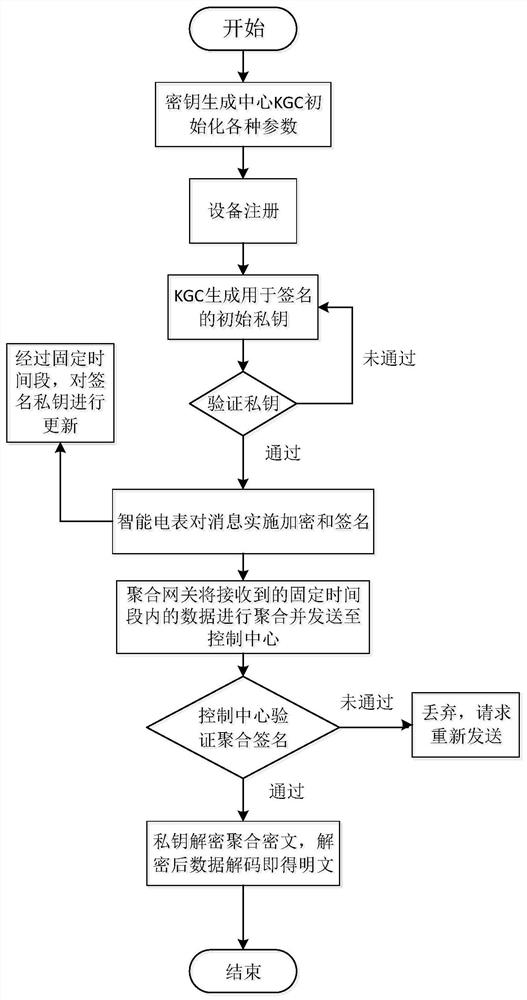
Intelligent power grid data encryption method and decryption method with forward security
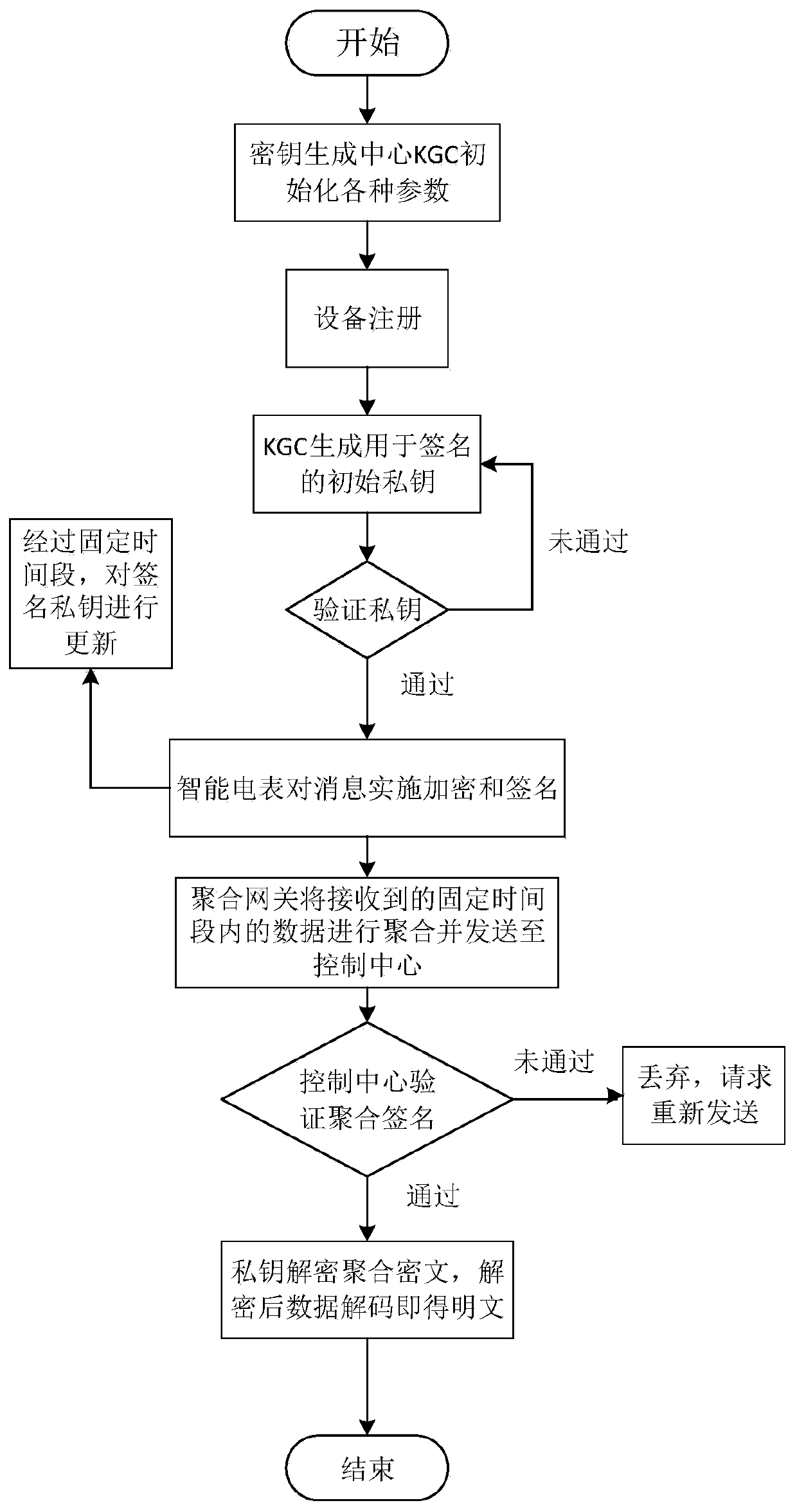
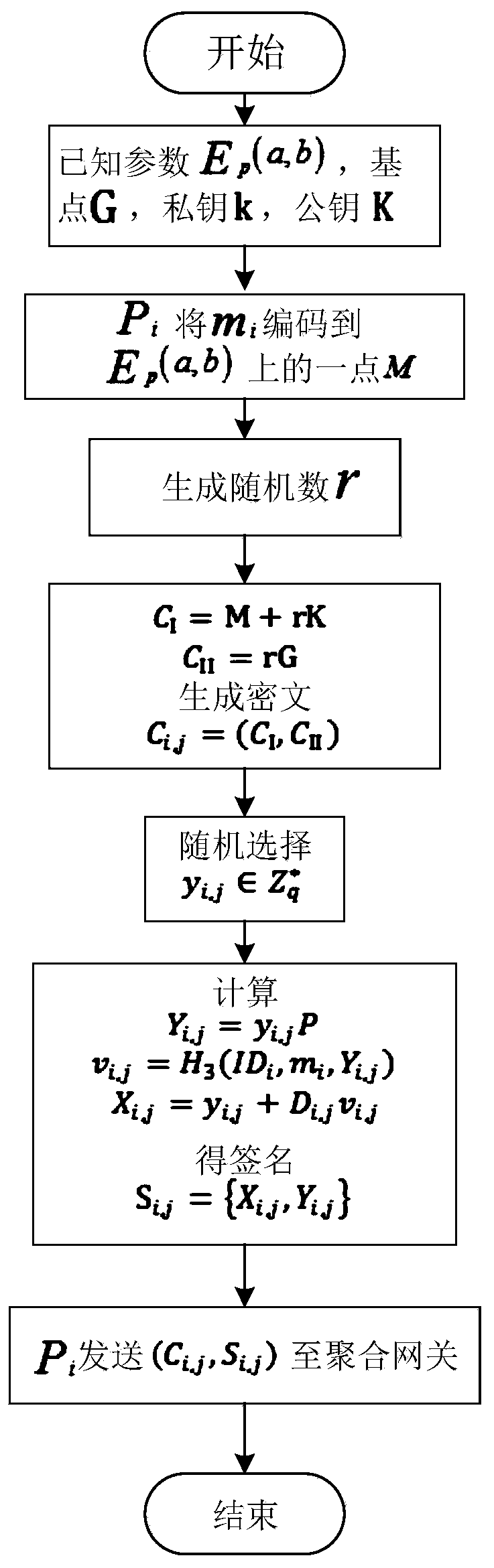
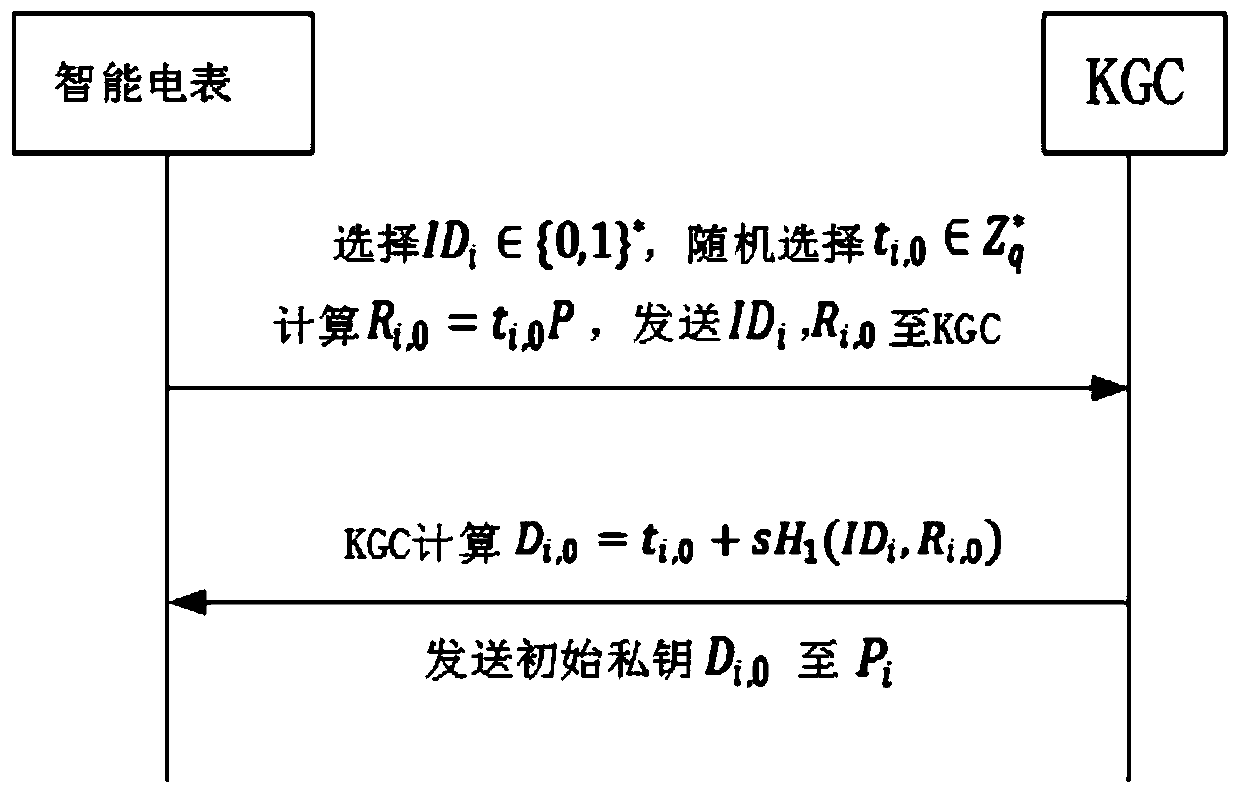
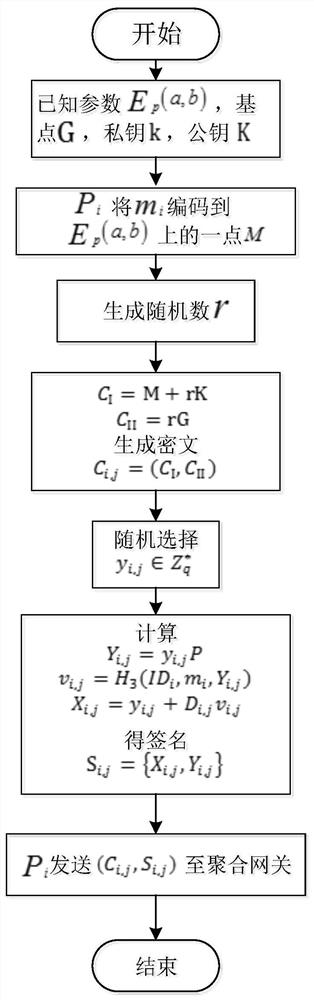
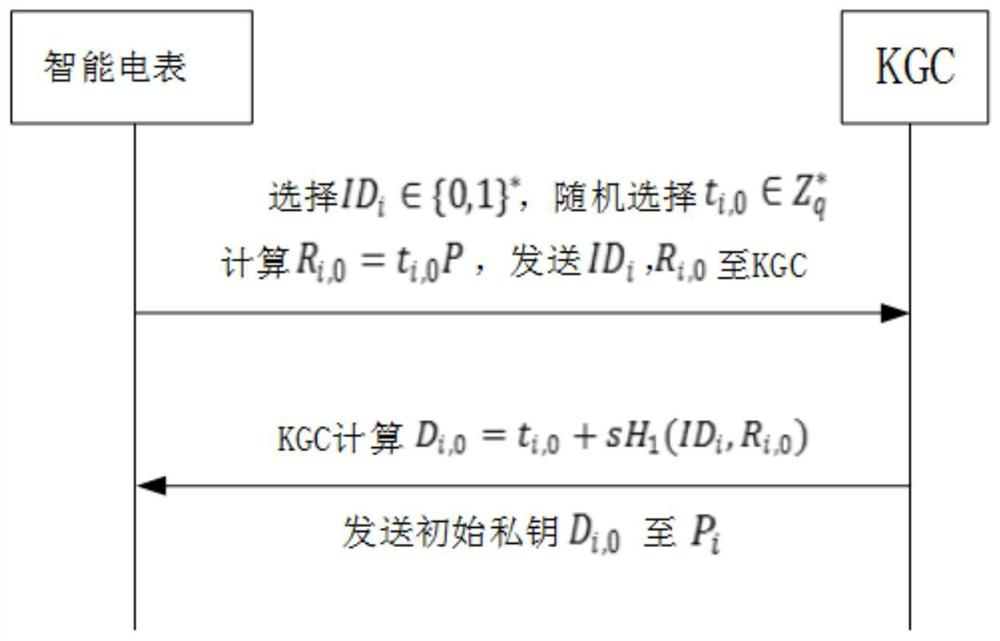
ActiveCN110460570AGuaranteed forward securitySmall amount of calculationData processing applicationsPublic key for secure communicationPlaintextDigital signature
The invention discloses an intelligent power grid data encryption method with forward security. The method comprises the following steps: a control center registers an aggregation gateway after receiving a registration request sent to the control center by the aggregation gateway, a public key K used for encrypting plaintext data is sent to the aggregation gateway; the aggregation gateway registers the intelligent electric meter after receiving a registration request sent to the aggregation gateway by the ith intelligent electric meter Ii, sends a public key K to the intelligent electric meter; a counter j=0 is set, whether j is less than or equal to a time period T is judged; and if yes, the ith intelligent electric meter Ii selects the ID number of the ith intelligent electric meter Ii and generates a random number ti,j, calculates and discloses a time reference variable Ri,j according to the random number ti,j, and sends the random number ti,j, the ID number IDi of the ith intelligent electric meter Ii and the time reference variable Ri,j to the control center. According to the invention, the signature private key is updated in a fixed time period, the forward security of signature information is ensured, and the aggregation and verification of digital signatures are completed without using bilinear pairs.
Owner:湖南匡安网络技术有限公司
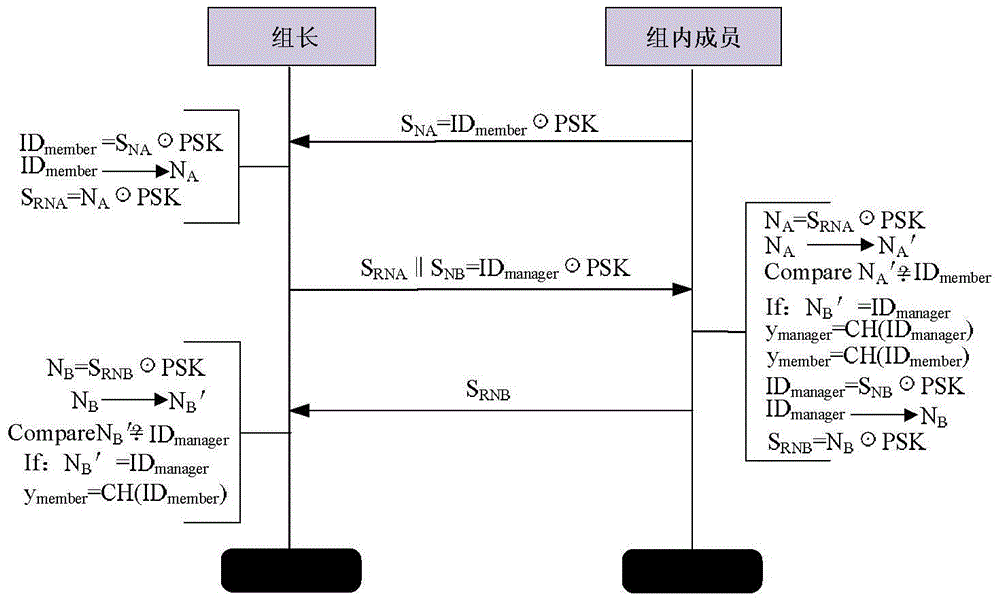
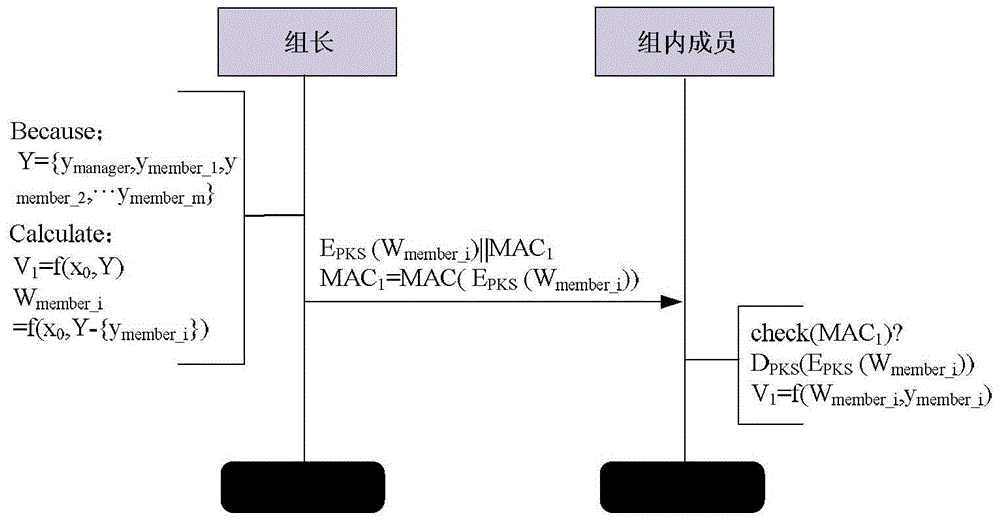
Group key management method applicable to heterogeneous sensor network
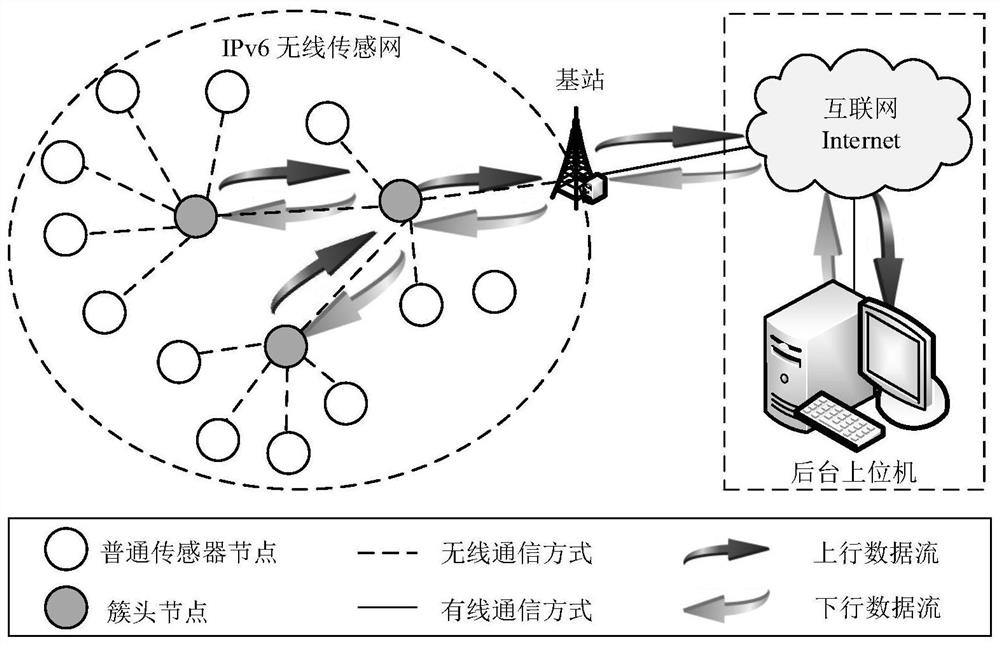
ActiveCN104618090AEnsure safetyReduce storage overheadKey distribution for secure communicationHeterogeneous networkWireless sensor networking
The invention provides a group key management method applicable to a heterogeneous sensor network. The method is that the distributive key management mode is performed; key materials of nodes in the group are dynamically distributed by a leader of each group; when networking, the leader and the nodes in the group are identified according to an exclusive NOR identification mechanism; when constructing the group key, the leader generates a witness for members in each group through an one-way accumulator; when updating the group key, three key update mechanisms are provided, namely, the mechanism of timely updating the group key, the mechanism of updating the group key while adding a new node, and the mechanism of updating the group key when repealing the old nodes; the nodes in the group utilize the concealed witness in a group key update message to identity a group key update instruction. With the adoption of the method, the calculation cost and storage cost of the whole network can be reduced; the real distributive management mode can be achieved; in addition, the forward security and the backward security of the whole network can be ensured; the safety and reliability of the wireless sensor network in operation can be improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
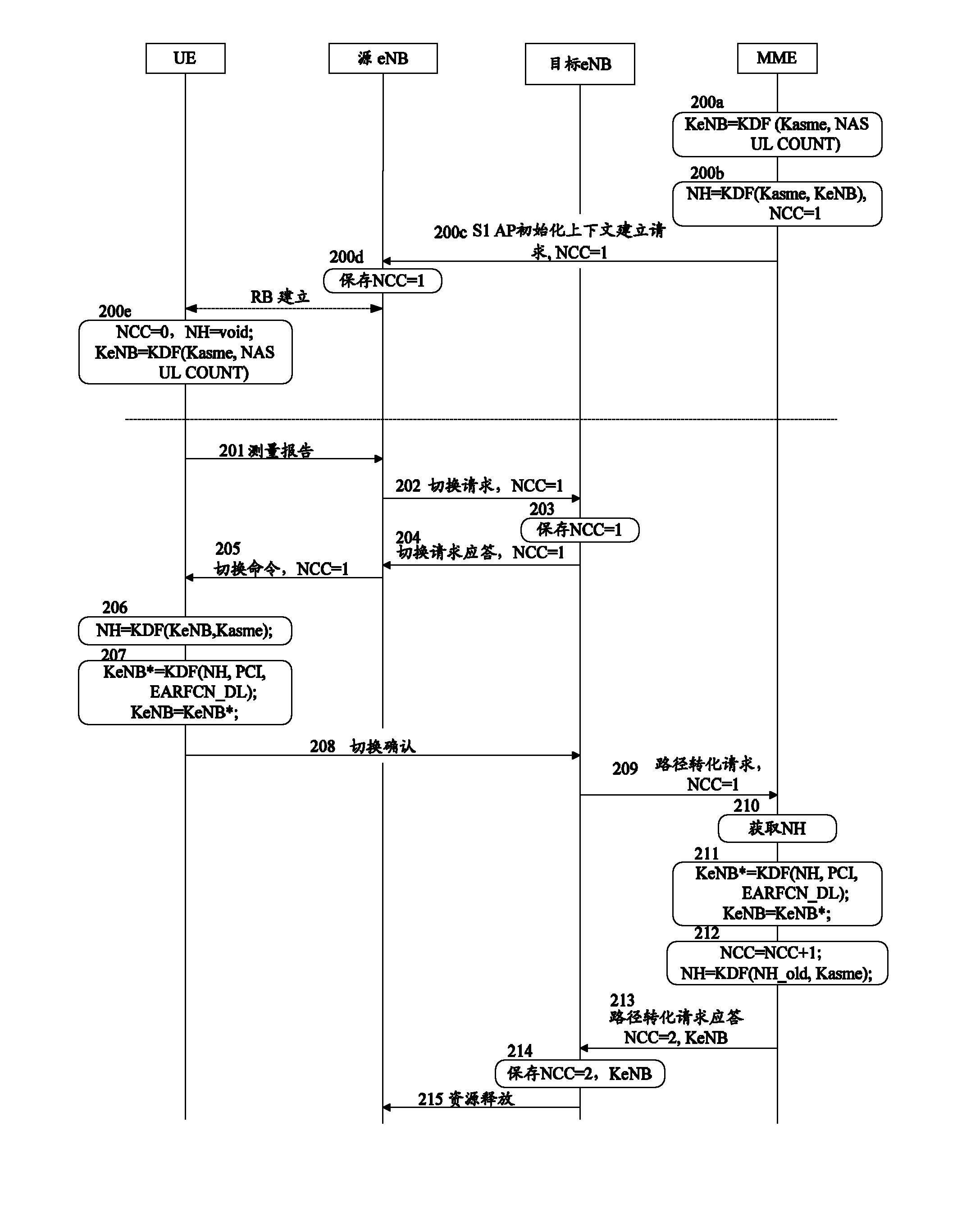
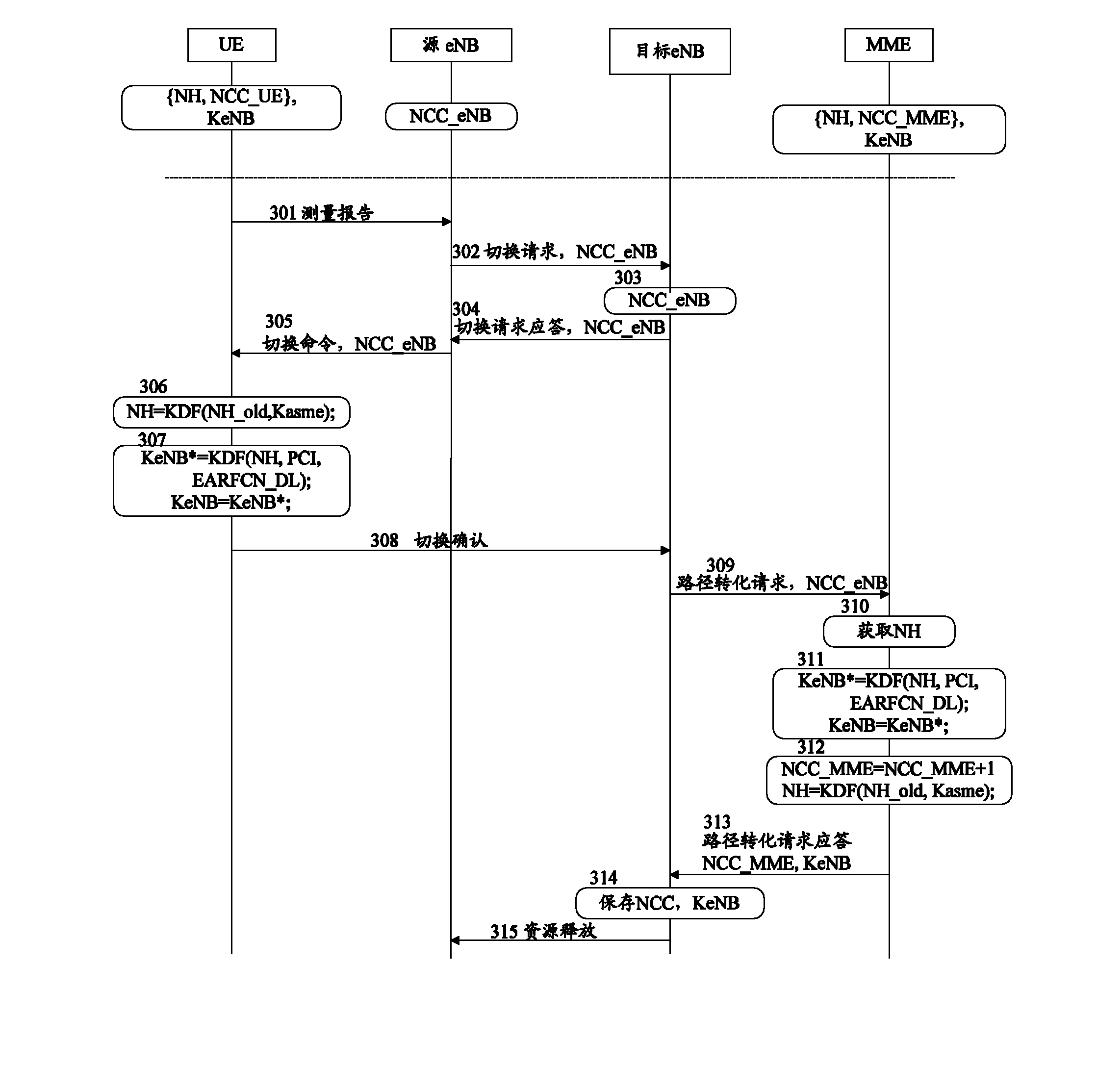
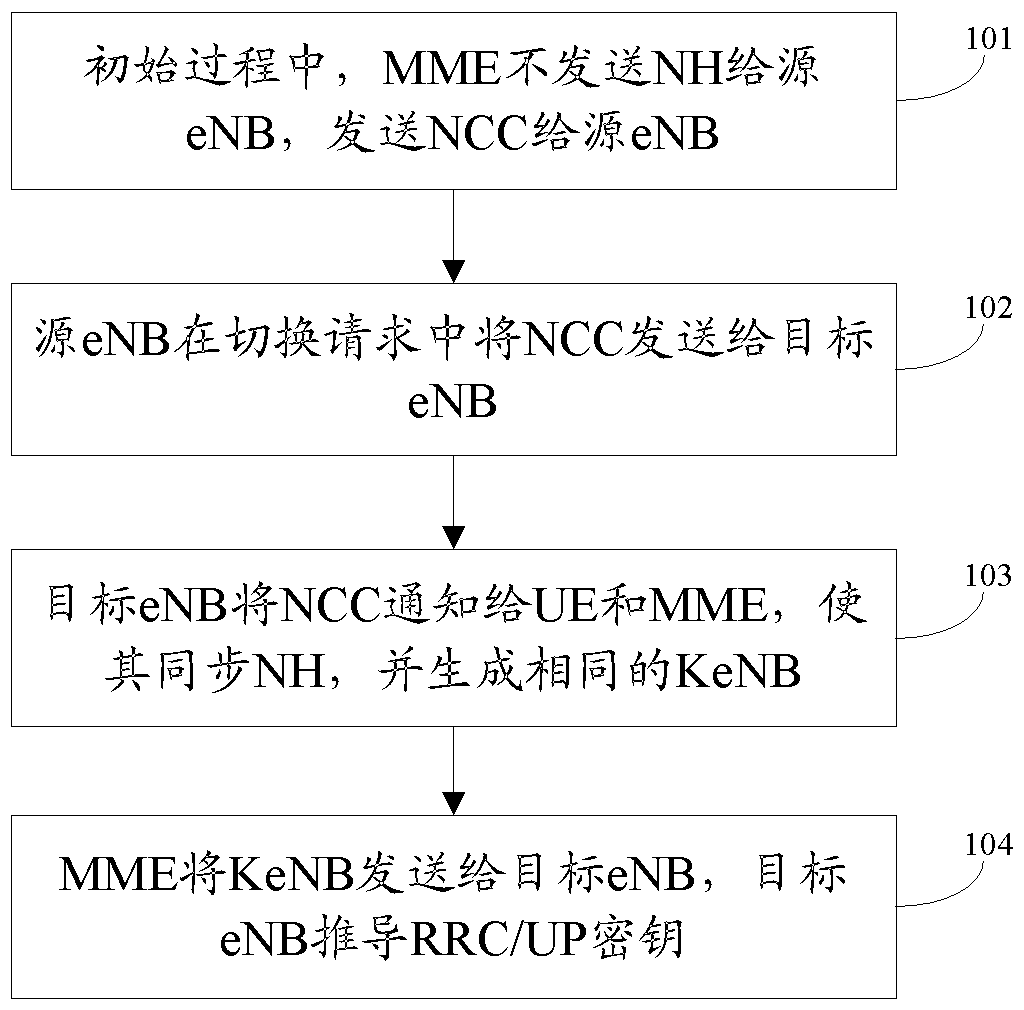
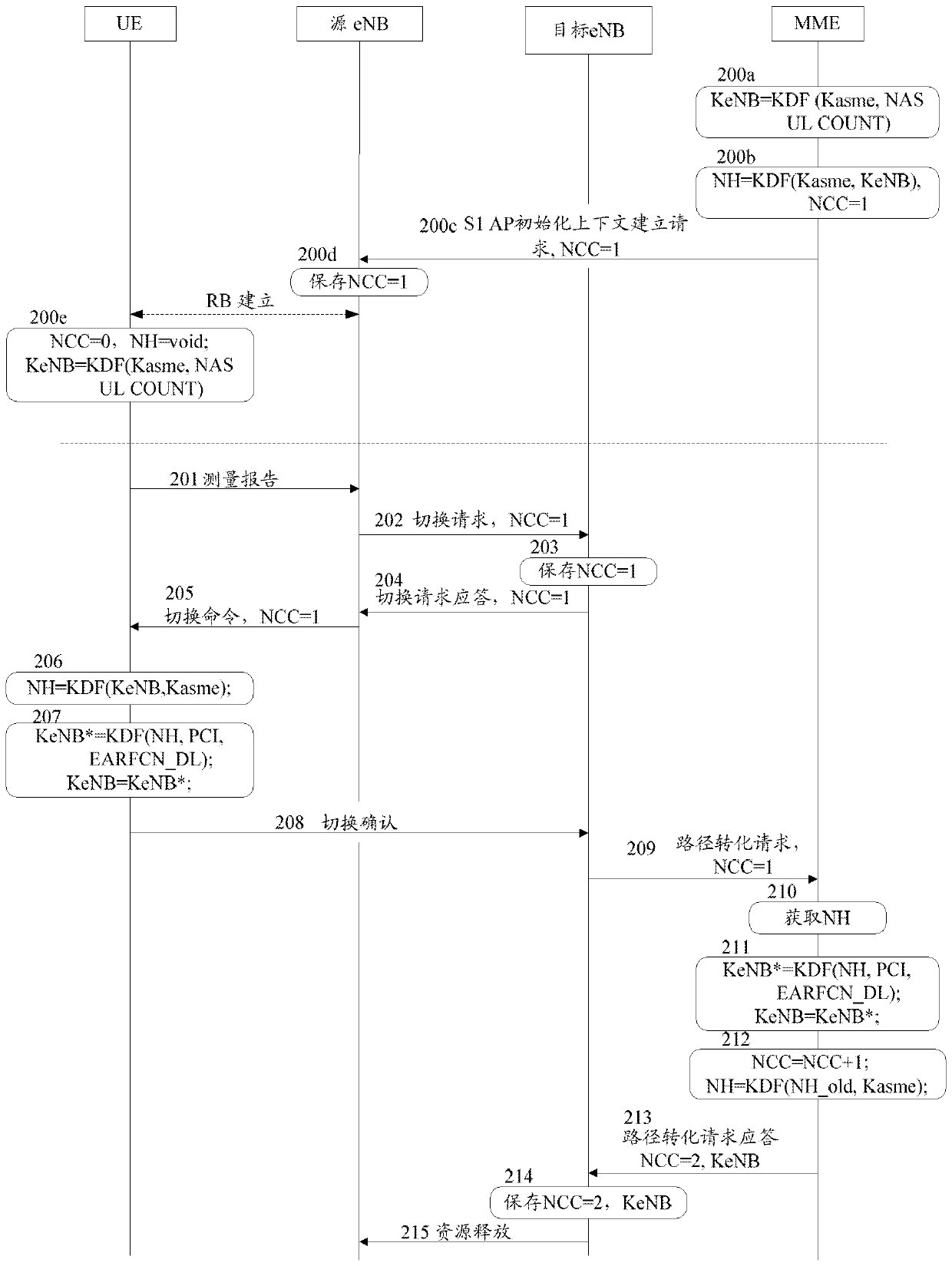
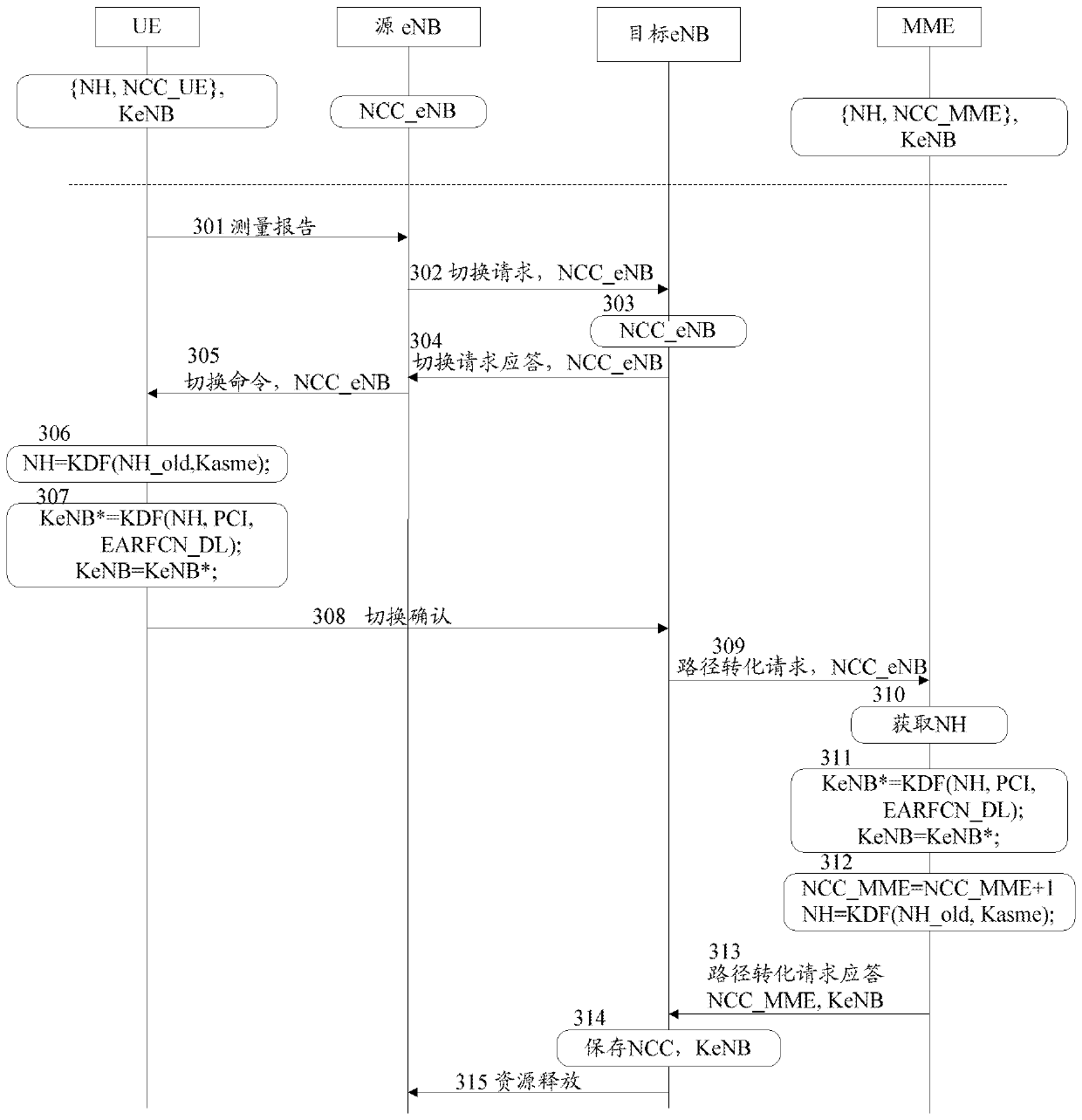
Key generation method and system in switching process
InactiveCN103139771APut an end to the possibilityImprove securitySecurity arrangementCommunications systemKey generation
The invention discloses a key generation method and system in a switching process. The method includes that a network side uses next hop parameter NH to generate next hop secret key evolved node B (KeNB) in user equipment (UE) switching process; a base station is not informed of the NH generated by the network side; the network side and the UE side respectively use next hop chaining counter (NCC) values informed by a target base station to synchronize with next hop KeNB; and the target base station is informed of the next hop KeNB generated by the network side. The base station can not acquire NH, so that the next hop KeNB can not be generated, the possibility of illegally acquiring next hop KeNB is reduced, and the forward security is guaranteed. By means of the method and the system, the safety of a communication system is greatly improved.
Owner:ZTE CORP
Symmetric searchable encryption method, device, equipment and medium
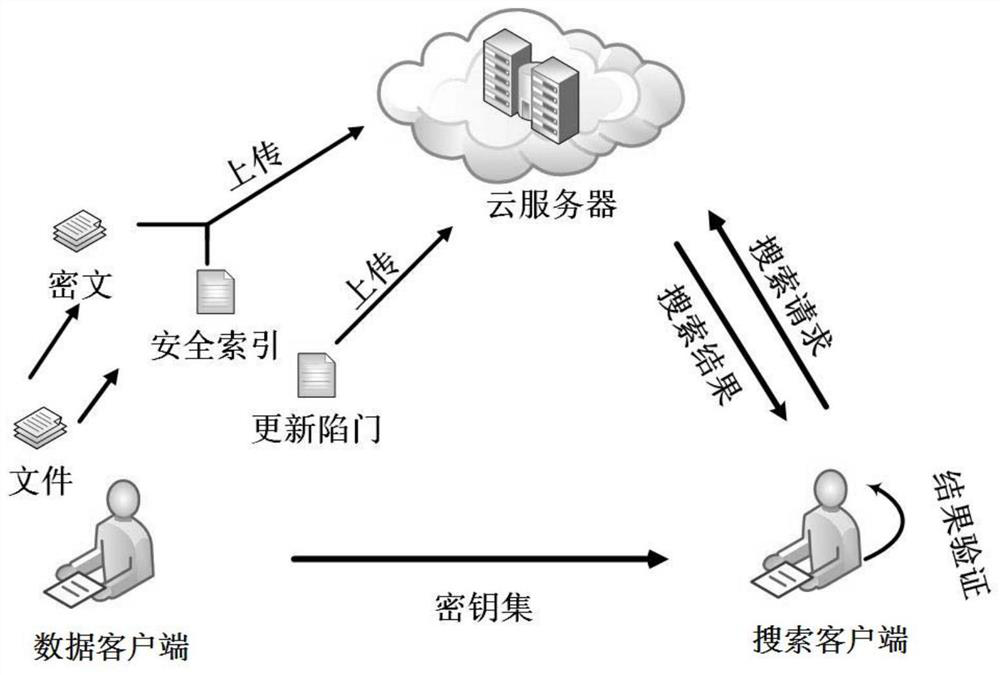
ActiveCN112182630AGuaranteed forward securityAchieving verifiabilityDigital data protectionFile access structuresPlaintextCiphertext
The invention discloses a symmetric searchable encryption method and device, equipment and a medium. The method comprises the following steps: encrypting a target plaintext file to obtain a ciphertextfile; creating a file index table based on the target plaintext file and a hash chain structure, wherein the file index table comprises an accumulative verification label and a continuously updated search trap door; and uploading the ciphertext file and the file index table to a cloud server, so that the cloud server feeds back the ciphertext file and the verification label corresponding to the search trap door to the search client based on the file index table after receiving the search trap door sent by the search client, wherein after the search client receives the ciphertext file and theverification label, the correctness of the ciphertext file is verified based on the verification label. According to the invention, the forward security and the complete verifiability of data search can be realized at the same time by creating the obtained file index table containing the accumulative verification label and the search trap door which is continuously updated.
Owner:QINGDAO UNIV
Intelligent power grid data aggregation and encryption method with forward security
ActiveCN110489982AGuaranteed forward securitySmall amount of calculationData processing applicationsDigital data protectionPlaintextData aggregator
The invention discloses an intelligent power grid data aggregation and encryption method with forward security. The method comprises: a key generation center KGC generating an initial private key andsending the initial private key to an intelligent electric meter through a secret channel; the intelligent electric meter verifying the initial private key, encrypting and signing the data of the userto generate a signature private key, sending the signature private key to the aggregation gateway, and updating the signature private key; the aggregation gateway aggregating the received signature private keys to generate an aggregation signature and sending the aggregation signature to the control center; and the control center verifying the aggregated signature, and decrypting and decoding theaggregated signature by using the private key k encrypted by the public key to obtain a plaintext m after successful verification. The problems of plaintext transmission of user power consumption information data and the like, data transmission congestion from the intelligent electric meter to a control center and expenditure in an existing aggregation encryption algorithm in an existing intelligent power grid are solved. The method is suitable for encrypting and aggregating the transmission data of the intelligent power grid, and the purpose of safely and efficiently transmitting the data isachieved.
Owner:北京珞安科技有限责任公司
Certificateless verifiable encrypted signature method with forward security
InactiveCN104780047AResistant to Substitution AttacksHigh degree of associationUser identity/authority verificationHash functionTimestamp
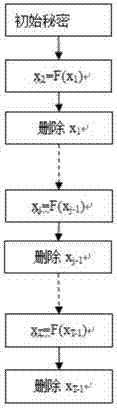
The invention provides a certificateless verifiable encrypted signature method with forward security, and belongs to the technical field of computer network and information security. According to the method, the timestamp is embedded into secret values of a certificateless signature algorithm, secret values which are not used is safely deleted, and signature key evolution and digital signature are really combined; a traditional certificateless signature algorithm sequence is changed, the set secrete values are generated before part of private keys are generated, meanwhile, public keys are bound to a Hash function, the parameter correlation degree in the signature algorithm is increased, and two types of enemy attacks of the certificateless environment are resisted; a generated verifiable encrypted signature comprises the user secret values and has the forward security; the computation burden of a signature scheme is small, the signature is short, and the whole performance is advantageous. The certificateless verifiable encrypted signature method with the forward security has very high security and fairness.
Owner:NANJING UNIV OF POSTS & TELECOMM
Pair secret key management method suitable for clustering wireless sensor network model
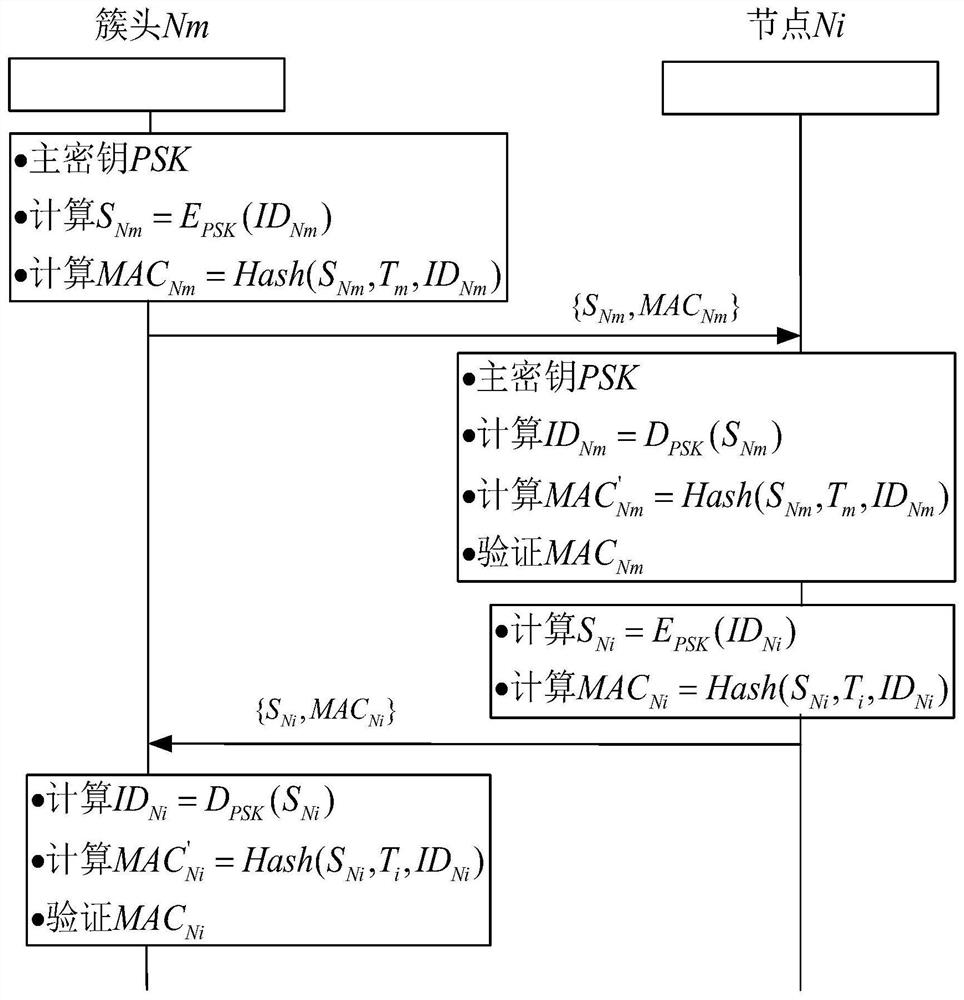
ActiveCN111447615AReduce storage overheadEnsure safetyPublic key for secure communicationNetwork topologiesCiphertextWireless sensor networking
The invention relates to a pair secret key management method suitable for a clustering wireless sensor network model, and belongs to the technical field of wireless communication. The method employs acombined public key-based algorithm to generate a pair secrete key. In the process of mutually authenticating identity identifiers of two parties, identity identification authentication between a cluster head and an intra-group node is completed by utilizing a combined private key generated by the identity identifiers, a ciphertext formed by encrypting the identity identifiers and an authentication code generated by system time; in secret key updating, updating of the combination matrix of the intra-group nodes is dynamically distributed by each group of cluster head nodes. The intra-group node completes the identification of the legality of the key updating command by utilizing the hidden witness in the key updating message. According to the method, the calculation overhead and the storage overhead of the whole network are reduced, the pair secret key management of the clustering wireless sensor network model in the true sense is realized, the forward security and the backward security of the whole network are ensured, and the security and the reliability of the wireless sensor network during operation are improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Information leakage preventing method and system based on internet of things
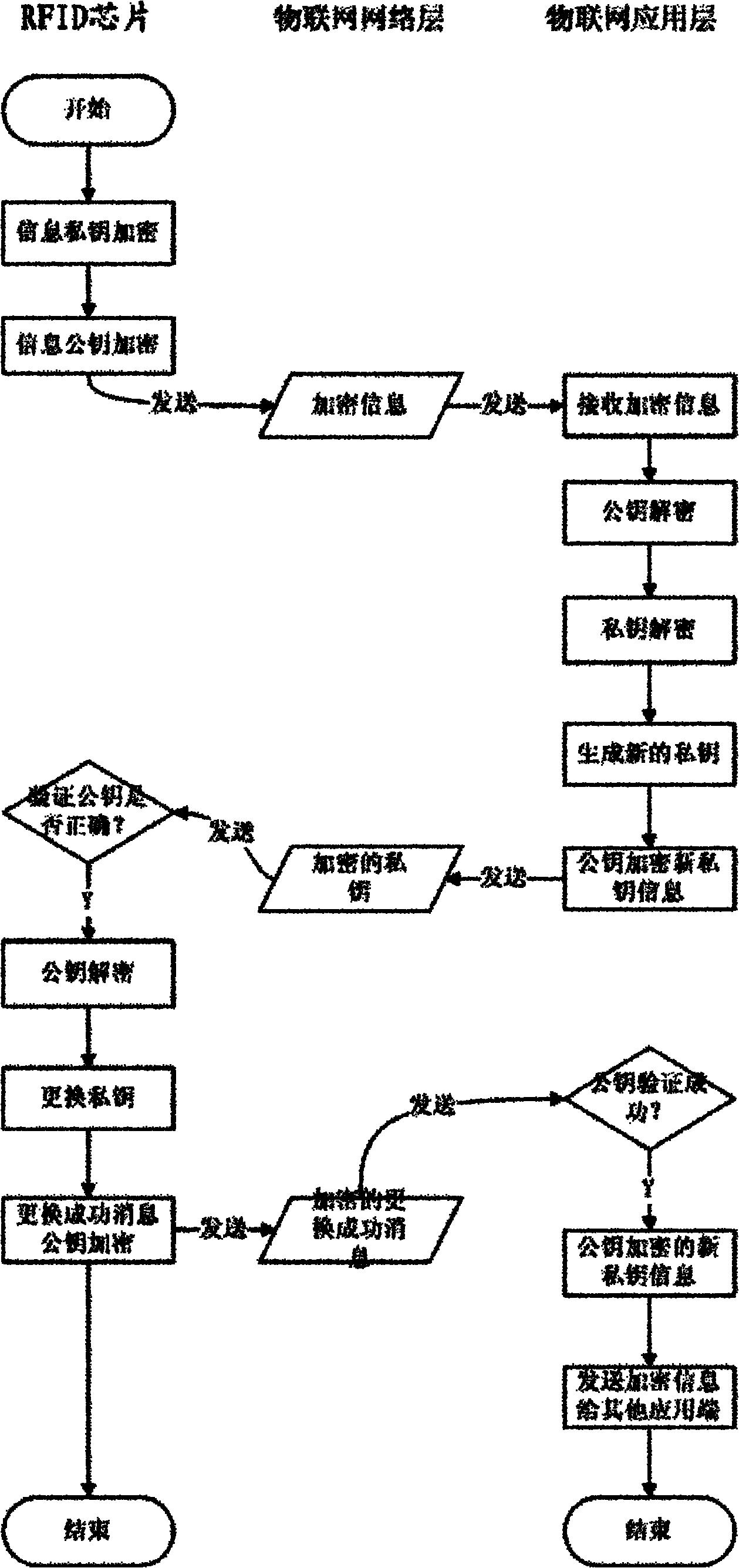
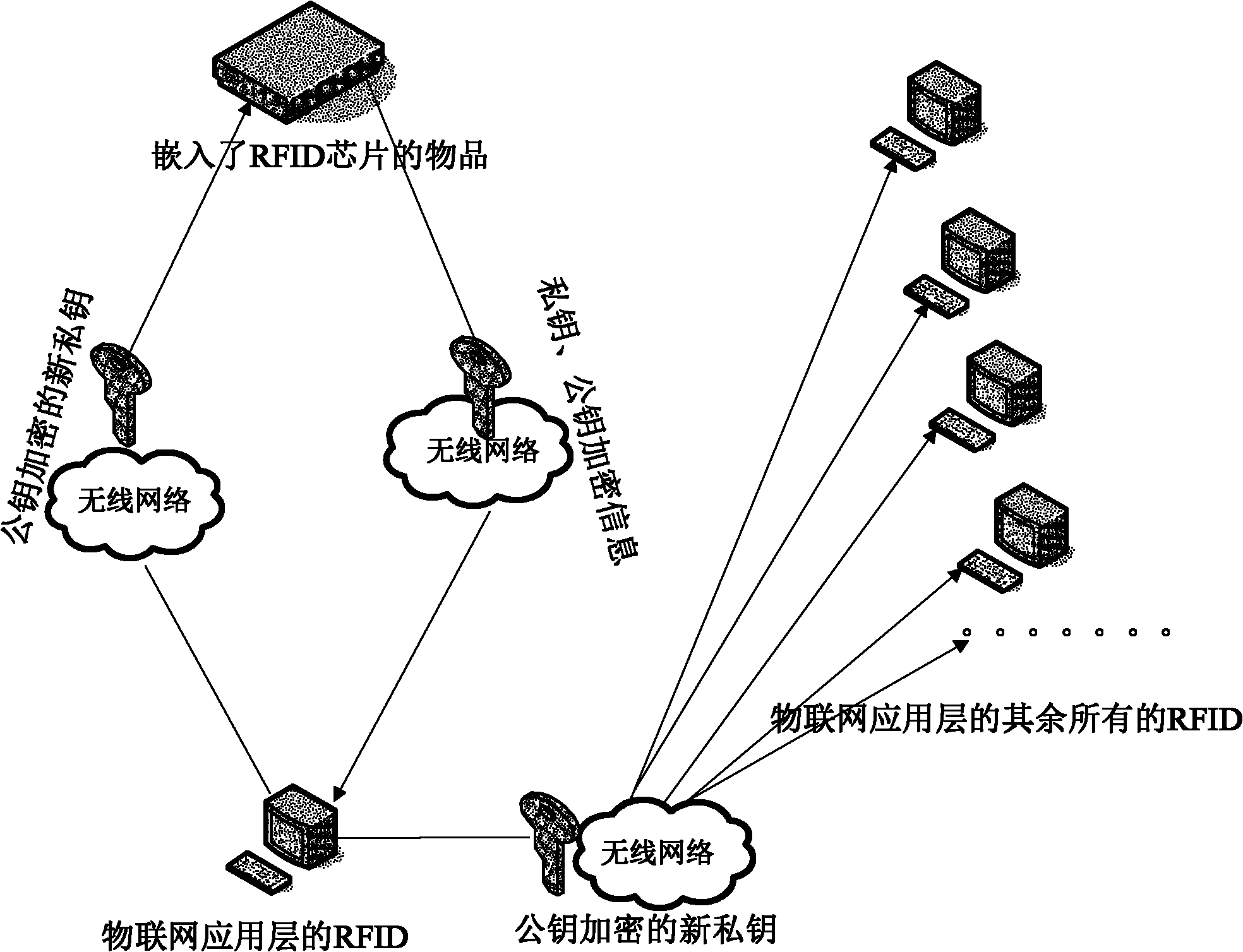
ActiveCN102065094APrevent leakageProtection securitySensing record carriersTransmissionPasswordThe Internet
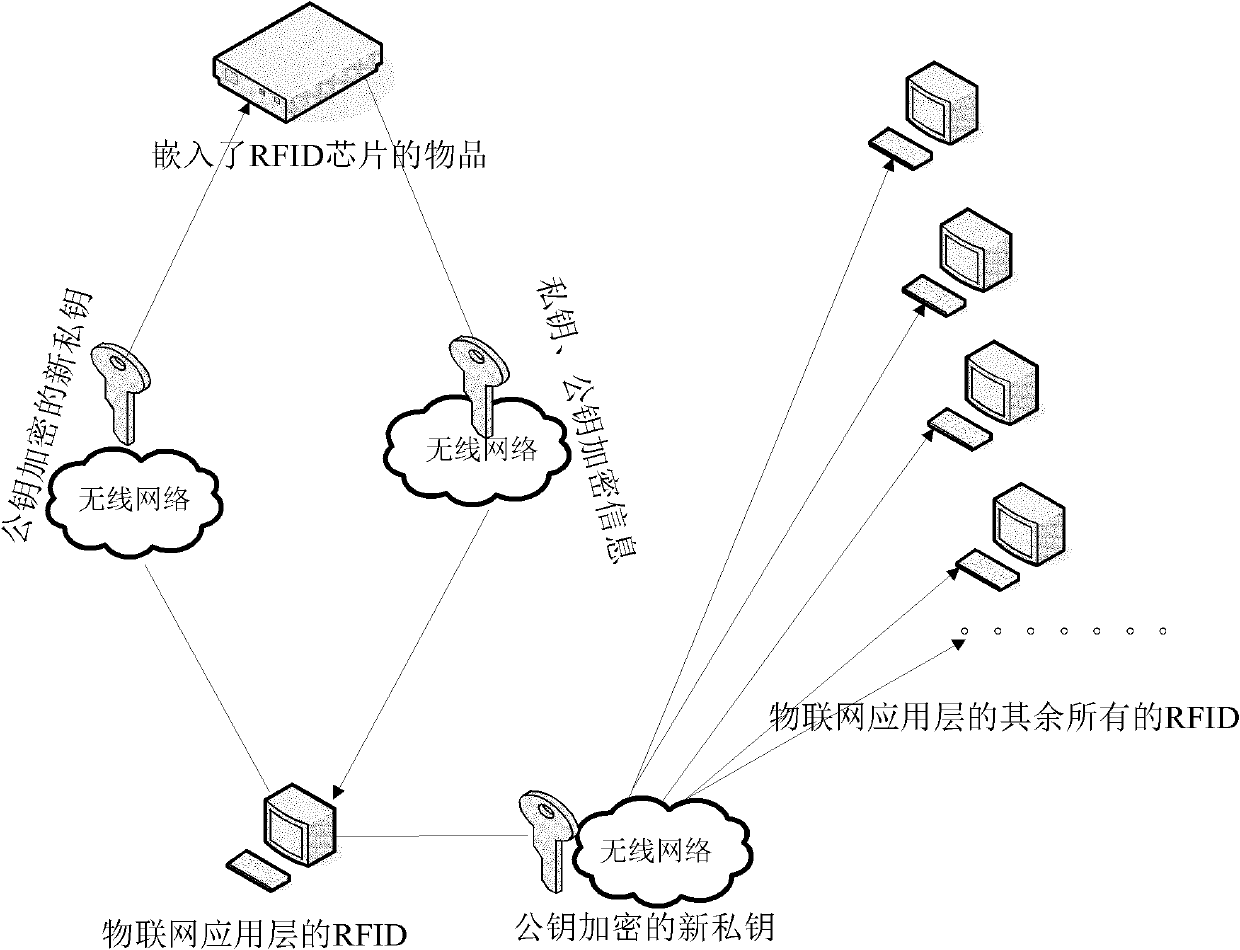
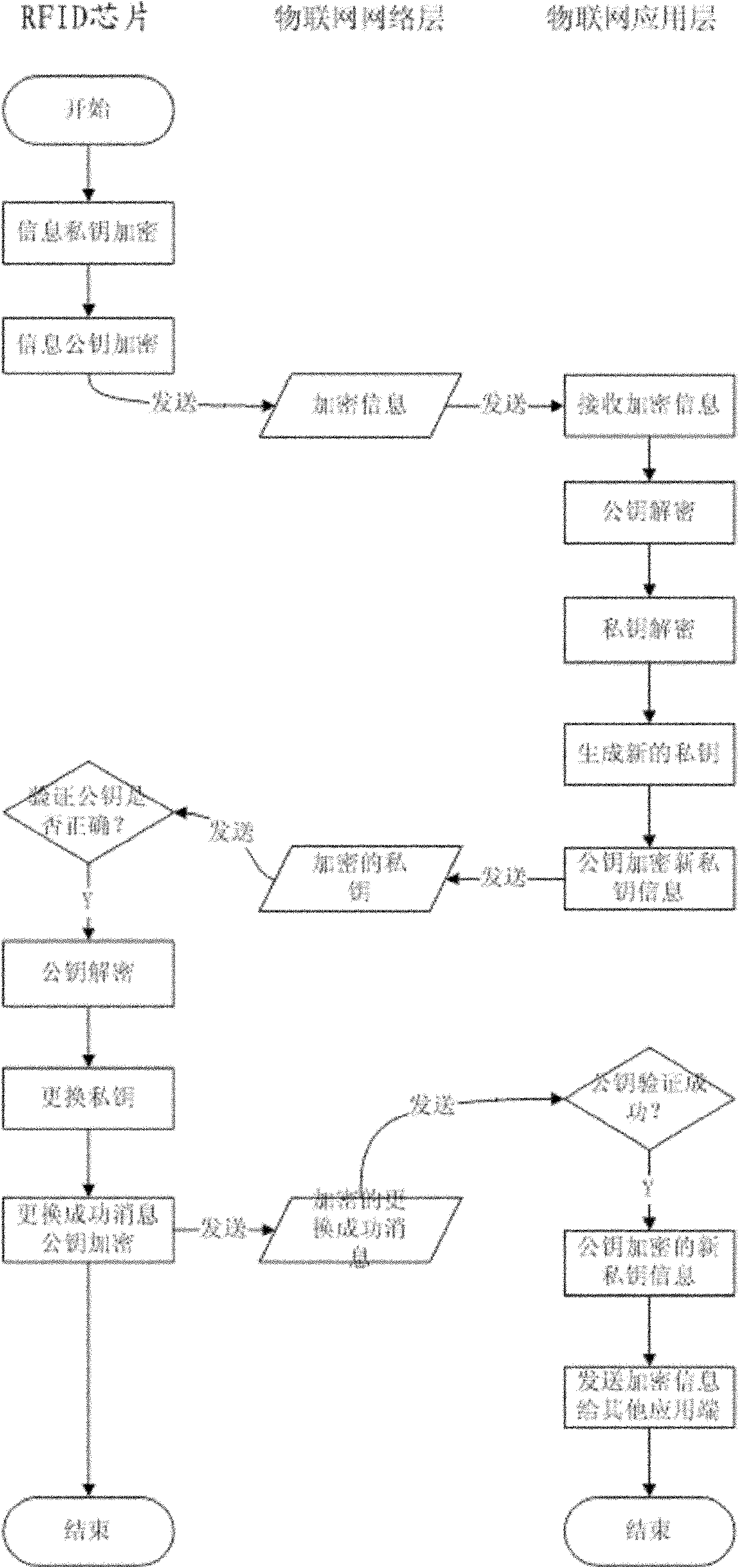
The invention discloses an information leakage preventing method and system based on the internet of things. An RFID (Radio Frequency Identification Device) chip responder and a reader of an application layer of the internet of things, which are mutually communicated and arranged in the internet of things; and the RFID chip responder stores an electronic carrier of identifying information of things in the internet of things. The method comprises the following steps that the RFID chip responder encrypts a private key and a public key and then transmits encrypted information to the reader of the application layer of the internet of things by a network layer of internet of things; the reader of the application layer of the internet of things decrypts the public key and the private key and generates a new private key every time; and the reader of the application layer of the internet of things encrypts and forwards the new generated private key to the RFID chip responder and readers of other application layers of the internet of things by using the public key. The invention protects the safety of data in the internet of things and prevents the leakage of information by a public key and private key encrypting mechanism. In the whole process of realization, the dynamic replacement of the private key not only further protects information safety but also improves the difficulty of password cracking.
Owner:WUXI CINSEC INFORMATION TECH
Anonymous privacy protection authentication protocol method based on wireless sensor system in smart medical treatment
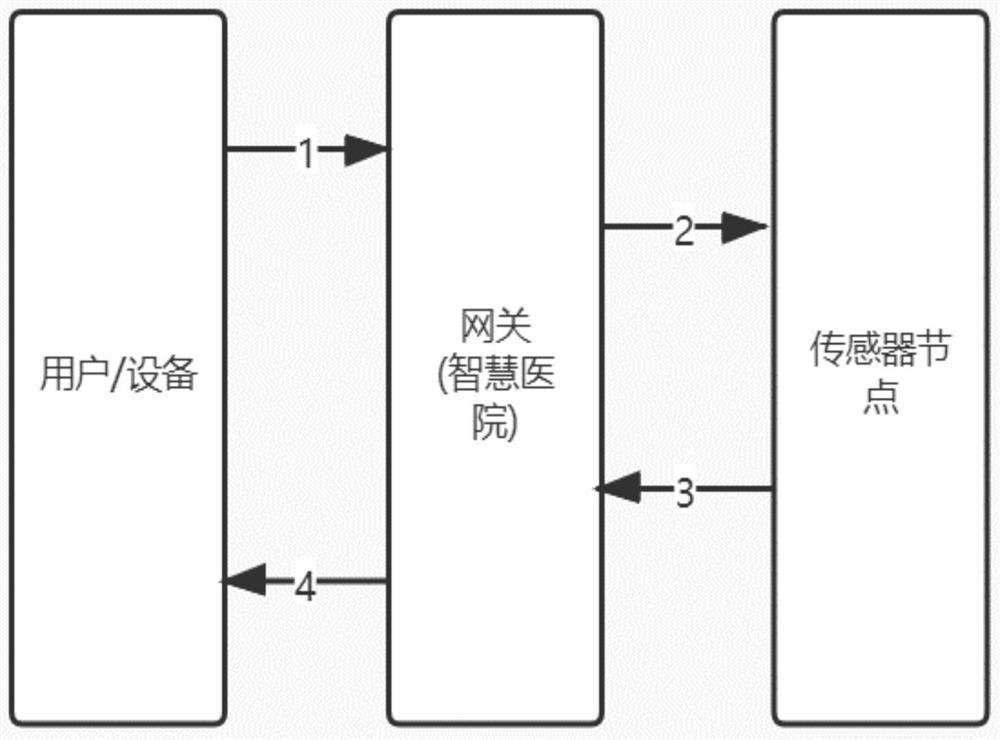
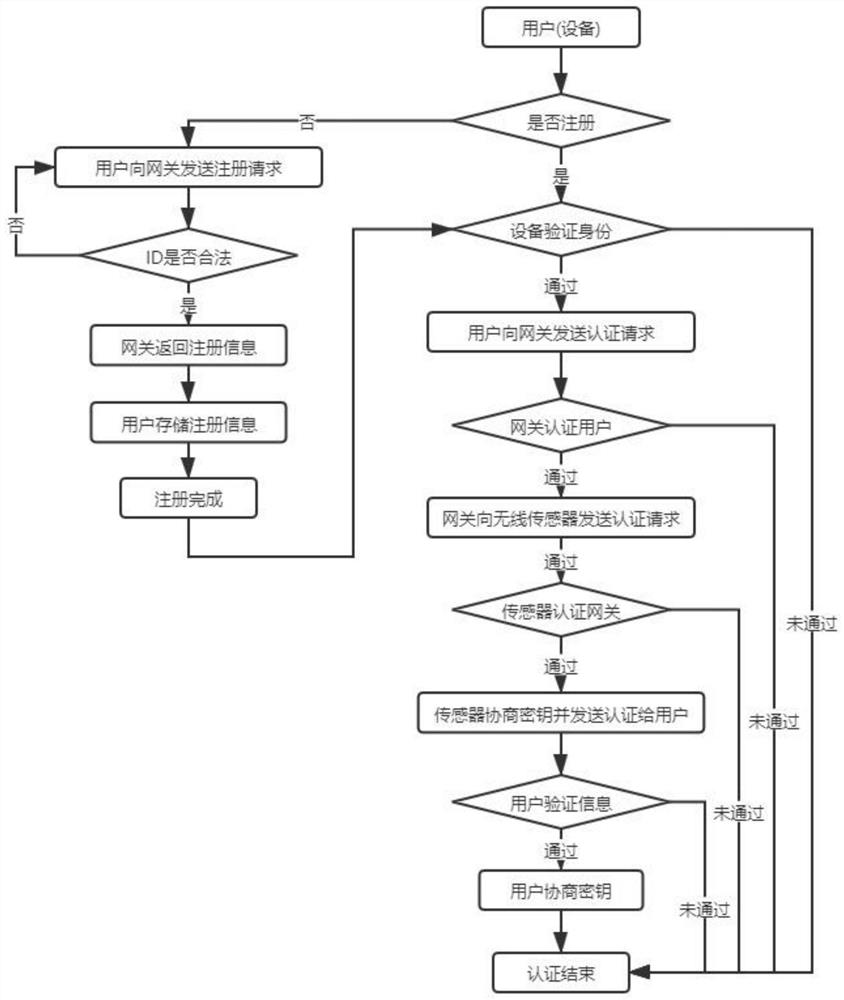
PendingCN113727296AReduce storage requirementsReduce computing pressureParticular environment based servicesSecurity arrangementAttackPrivacy protection
The invention discloses an anonymous privacy protection authentication protocol method based on a wireless sensor system in smart medical treatment, and belongs to the field of information security. The invention relates to an anonymous privacy protection authentication protocol method based on a wireless sensor line in wisdom medical treatment, which comprises three entities of a user, a gateway and a sensor node, the sensor node collects real-time data of a patient, wherein the sensor node is connected to the Internet through the credible gateway, the user accesses the data collected by the node through the Internet, and the user, the gateway and the sensor node are mutually authenticated to generate a session key for communication. By means of the anonymous privacy protection authentication protocol method, off-line password guessing attacks, known key attacks and desynchronization attacks can be effectively resisted, and the whole authentication process is safe and efficient, so that the method has very high application value in an intelligent medical scene.
Owner:HANGZHOU NORMAL UNIVERSITY
Authentication method, reader and label
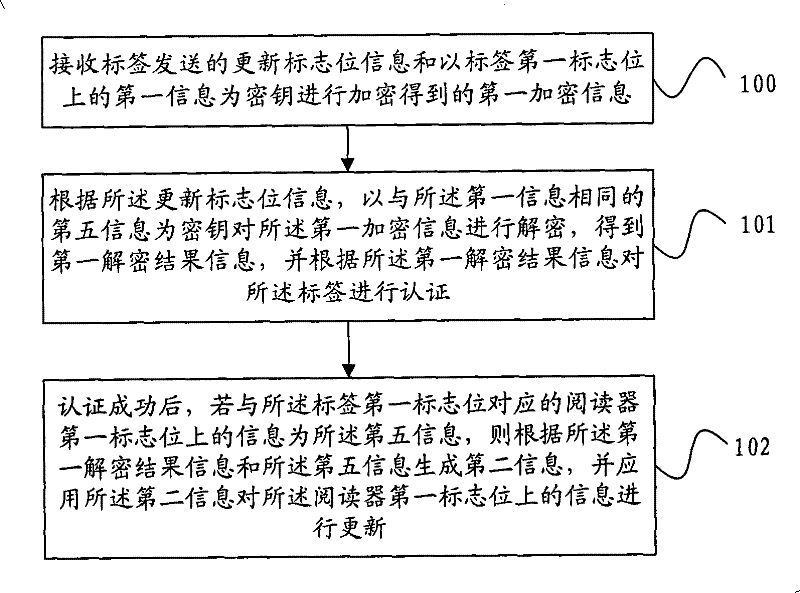
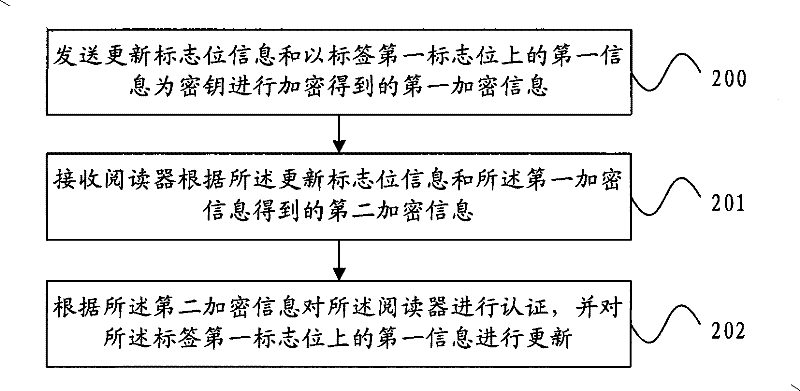
InactiveCN101599829BGuaranteed forward securityKey distribution for secure communicationMultiple keys/algorithms usageComputer scienceSynchronism
The embodiment of the invention provides an authentication method, a reader and a label. The method comprises the steps: receiving an updated mark bit message sent by the label and a first enciphered message; deciphering the first enciphered message according to the updated mark bit message and authenticating the label according to the deciphering result. The reader authenticates the label by applying corresponding deciphered and enciphered messages of an encryption key according to the updated mark bit message sent by the label; and the adopted encryption key is relevant to a cipher code adopted before, therefore, an attacker cannot calculate a symmetric key used in previous communication, and the forward security can be ensured; the encryption key is updated and the updated encryption key is synchronized with the label after the communication is successful; and if the updated mark bit message applied by the label is updated successfully or not can ensure the data synchronism.
Owner:BEIJING BAILETU TECH CO LTD
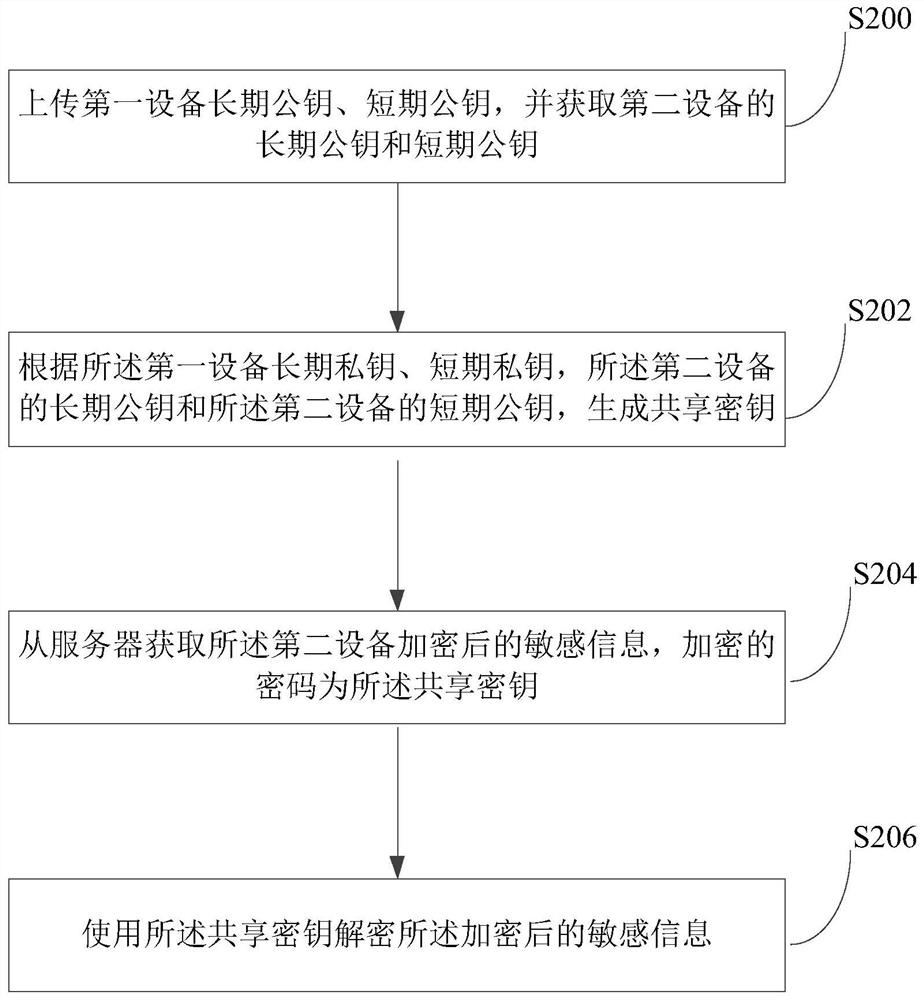
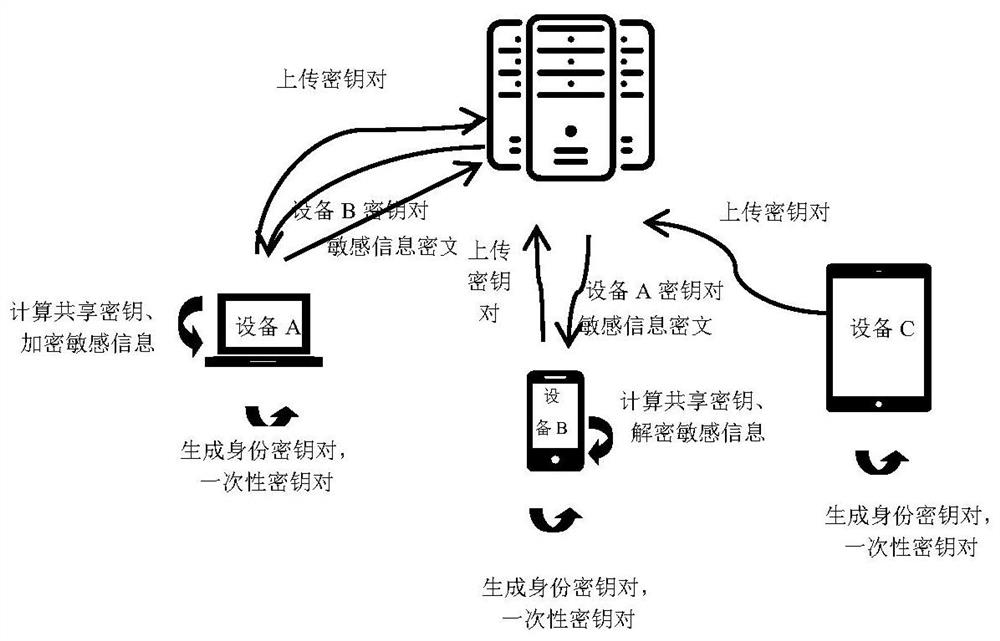
Sensitive data synchronization method, device and system, computer equipment and computer readable storage medium
PendingCN112468291AWon't leakGuaranteed forward securityKey distribution for secure communicationPublic key for secure communicationData synchronizationPassword
The embodiment of the invention discloses a method, device and system for synchronizing sensitive data, computer equipment and a computer readable storage medium. The method comprises the following steps: uploading a first equipment long-term public key and a short-term public key, and obtaining the long-term public key and the short-term public key of second equipment; generating a shared key according to the first equipment long-term private key, the short-term private key, the long-term public key of the second equipment and the short-term public key of the second equipment; acquiring the encrypted sensitive information of the second device from a server, wherein the encrypted password is the shared key; and decrypting the encrypted sensitive information by using the shared key. Therefore, in the sensitive information synchronization process, the transmission of the sensitive information is always in an encrypted state, and the sensitive information is ensured not to be leaked to anintermediate server or other attackers. The newly generated shared key is used for the encryption key of the sensitive information each time, so that the forward security is ensured, and an attackercannot decrypt the previously encrypted information even if the attacker breaks through the latest encryption key.
Owner:深圳依时货拉拉科技有限公司
A kind of rfid two-way authentication protocol method
ActiveCN103078741BReduce computing needsReduce storage requirementsUser identity/authority verificationCo-operative working arrangementsThree stageExclusive or
The invention relates to an RFID (radio frequency identification) mutual authentication protocol method, which comprises the following three stages: a tag identification stage, a mutual authentication stage and an update stage, wherein at the tag identification stage, a reader sends a request to a tag, and the tag returns an identification section (IDS) to the reader after receiving the request; at the mutual authentication stage, after the IDS is identified by the reader, an exclusive-or operation related to a digital synthetic operation is conducted to obtain A and B, A and B are sent to the tag, after the reader is identified by the tag through received A||B, related calculation is conducted to obtain C, C is sent to the reader, and the tag is identified by the reader; and at the update stage, after C is successfully identified by the reader, IDS and secret keys (K1 and K2) in C are updated, then D and E are calculated and sent to the tag, and after E is successfully identified by the tag, IDS and secret keys of E are updated. Only the simple digital synthetic or exclusive-or operation exists in the RFID mutual authentication protocol method. Therefore, the RFID mutual authentication protocol method has the beneficial effects that the calculation amount and storage space of the tag can be effectively reduced, various attacks such as impersonation, retransmission, tracking and denial of service can be resisted, and forward security is provided.
Owner:上海诚扬信息科技有限公司
Information leakage preventing method and system based on internet of things
ActiveCN102065094BPrevent leakageProtection securitySensing record carriersTransmissionPasswordThe Internet
The invention discloses an information leakage preventing method and system based on the internet of things. An RFID (Radio Frequency Identification Device) chip responder and a reader of an application layer of the internet of things, which are mutually communicated and arranged in the internet of things; and the RFID chip responder stores an electronic carrier of identifying information of things in the internet of things. The method comprises the following steps that the RFID chip responder encrypts a private key and a public key and then transmits encrypted information to the reader of the application layer of the internet of things by a network layer of internet of things; the reader of the application layer of the internet of things decrypts the public key and the private key and generates a new private key every time; and the reader of the application layer of the internet of things encrypts and forwards the new generated private key to the RFID chip responder and readers of other application layers of the internet of things by using the public key. The invention protects the safety of data in the internet of things and prevents the leakage of information by a public key and private key encrypting mechanism. In the whole process of realization, the dynamic replacement of the private key not only further protects information safety but also improves the difficulty of password cracking.
Owner:WUXI CINSEC INFORMATION TECH
WSN group key management method suitable for multicast communication
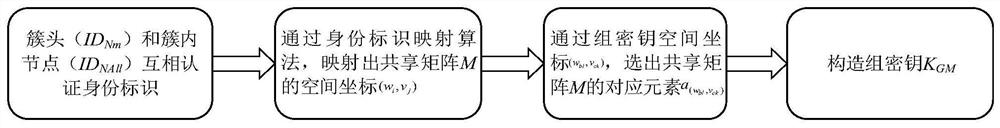
ActiveCN112383390AReduce storage overheadLarge key spaceKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey spaceEngineering
The invention relates to a WSN group key management method suitable for multicast communication, and belongs to the field of network security and communication, and the method comprises the followingsteps: S1, initializing system parameters; S2, enabling the two communication parties to mutually authenticate identities; S3, constructing space coordinates of the shared matrix M; s4, enabling the two communication parties to establish a group key; and s5: updating the group key. According to the method, on the basis of reducing the storage overhead of each node, the establishment of the group key and the updating of the group key are completed, and the key space of the group key is increased compared with the same type of group key management scheme. Meanwhile, the method ensures the forward security and backward security in the whole network operation process, that is, only legal nodes can update the group key, and nodes cannot be removed to obtain the updated group key.
Owner:刘中亚
Anonymous data sharing method and system based on data source and data master hiding
ActiveCN111600875BPrivacy protectionReduce overheadKey distribution for secure communicationIp addressData source
Owner:JIANGSU UNIV
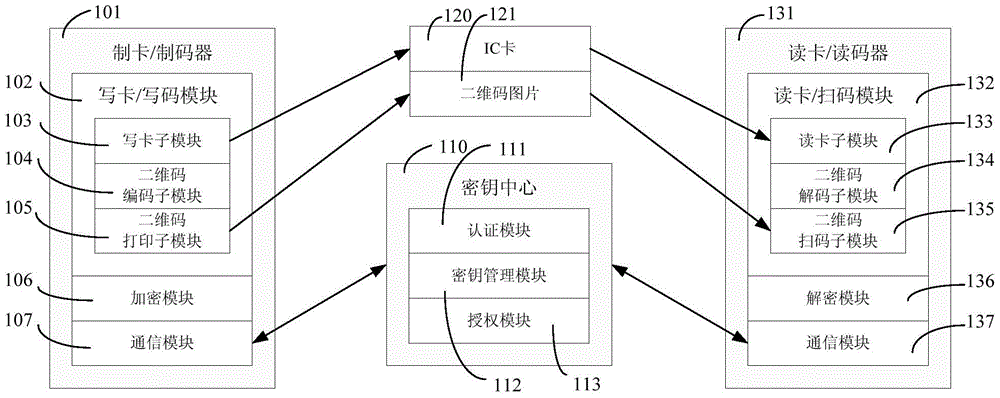
A data security storage method applicable to IC cards and two-dimensional codes
ActiveCN104463016BNot limited to typesGuaranteed forward securityAutomatic card filesDigital data protectionSoftware systemComputer terminal
The invention relates to IC cards and two-dimension codes and discloses a data safety storing method suitable for IC cards and two-dimension codes. The method comprises the steps of (1) terminal registering, (2) authentication, (3) card / code generating and (4) card / code reading. A symmetric key and an asymmetrical key are combined for use, only the data storing function of the IC cards and the two-dimension codes is used, a data encryption function is completely completed by an upper layer software system, accordingly, limiting from the types and inner achieving of the IC cards is avoided, and limiting from the types of the two-dimension codes is avoided. Each card / code generator and each card / code reader are provided with unique identity keys, a key center is used for distributing different encryption keys during each-time encryption, and the key center carries out decryption authorization on the card / code reader. The forward safety of the keys can be well guaranteed, right control particle size is well refined, and accordingly data safety is enhanced.
Owner:XIAMEN UNIV
A Smart Grid Data Aggregation and Encryption Method with Forward Security
ActiveCN110489982BGuaranteed forward securitySmall amount of calculationData processing applicationsDigital data protectionData aggregatorEngineering
The invention discloses a smart grid data aggregation and encryption method with forward security. The key generation center KGC generates an initial private key and sends it to a smart meter through a secret channel; the smart meter verifies the initial private key, and the user's data Implement encryption and signature to generate a signature private key, send it to the aggregation gateway, and update the signature private key at the same time; the aggregation gateway aggregates the received signature private key to generate an aggregate signature and send it to the control center; the control center verifies the aggregate signature, After the verification is successful, the aggregate signature is decrypted and decoded with the private key k encrypted with the public key to obtain the plaintext m. The invention solves the problem of plaintext transmission of user electricity information data in the existing smart grid, data congestion in the transmission from the smart meter to the control center, and overhead problems in the existing aggregation encryption algorithm, and is suitable for data transmission in the smart grid. Encryption and aggregation to achieve the purpose of safe and efficient data transmission.
Owner:北京珞安科技有限责任公司
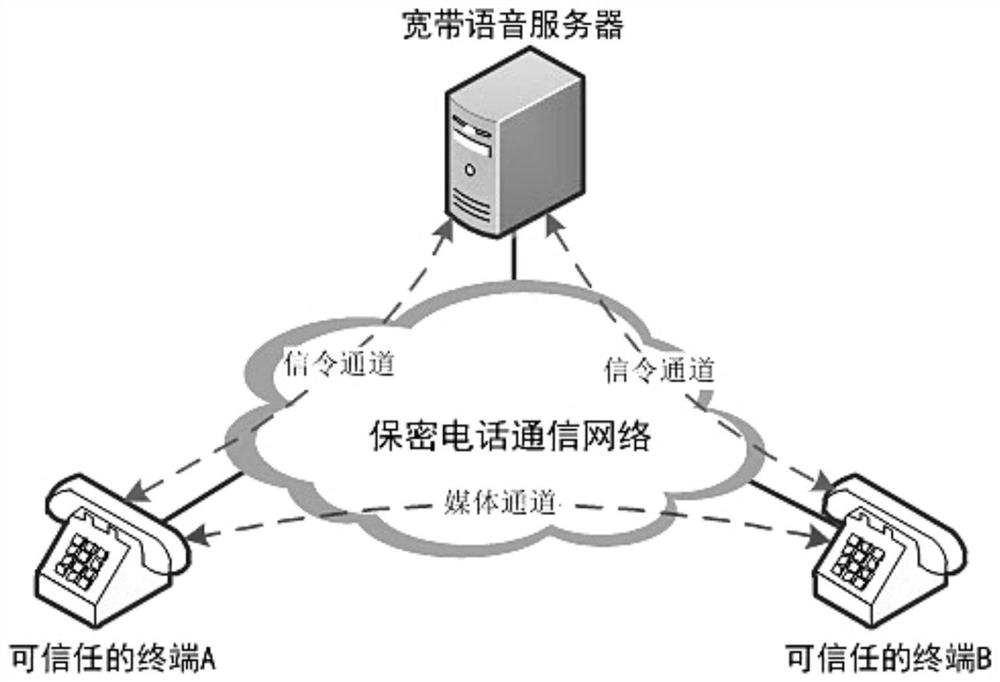
Method for realizing secure migration of user data based on voice channel
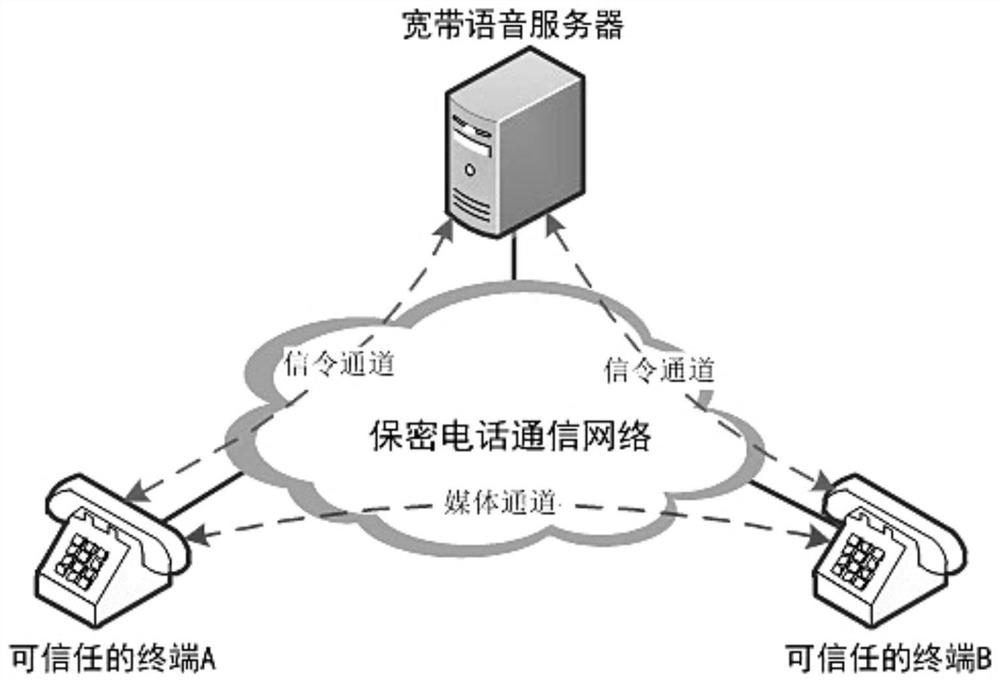
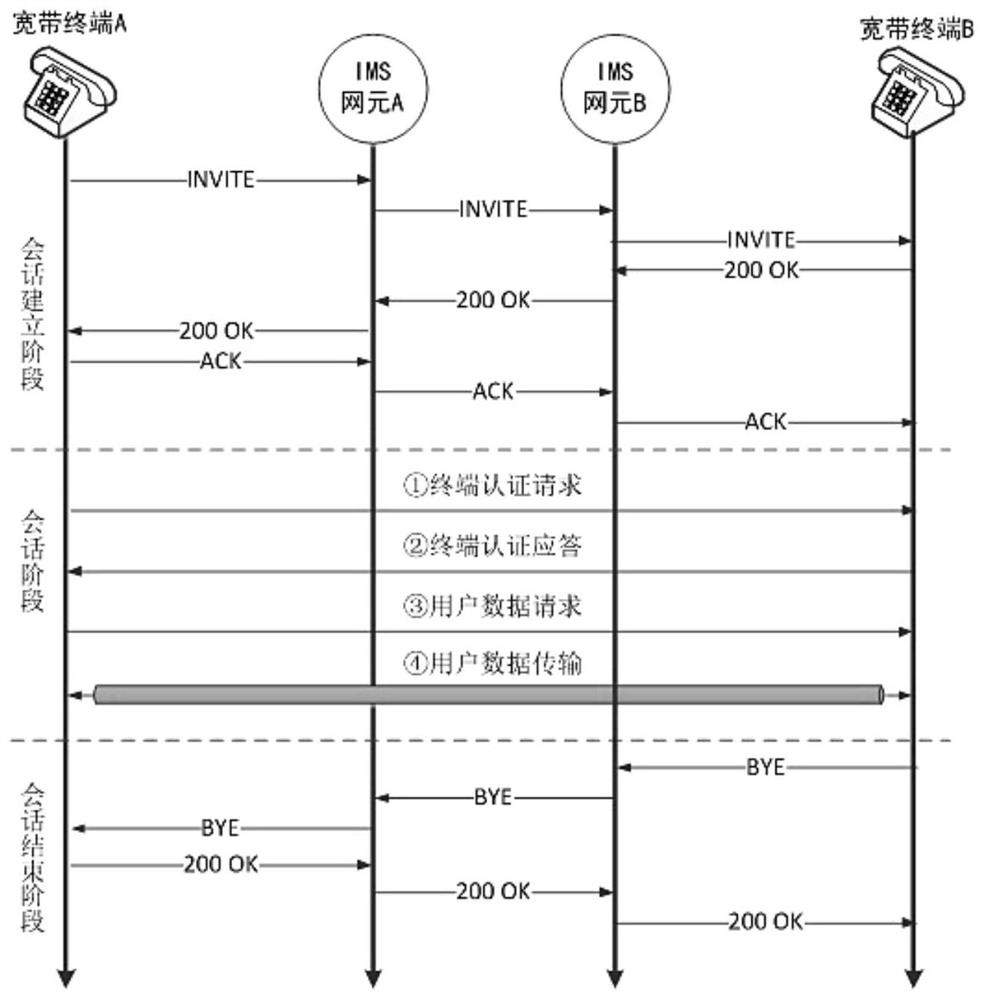
ActiveCN112737784AAccelerateImprove computing efficiencyKey distribution for secure communicationPublic key for secure communicationDiscrete logarithmUser information
The invention discloses a method for realizing safe migration of user data based on a voice channel, which comprises the following steps of: deploying a cryptosystem combining a symmetric password and an asymmetric password on a trusted terminal of a secret telephone communication network; confidentiality protection of the user information being completed by utilizing the characteristics of high encryption and decryption speed, high calculation efficiency and less resource occupation of the symmetric password; identity authentication of two communication parties being realized by utilizing calculation difficulty of discrete logarithms of asymmetric passwords in a finite field, and meanwhile, sharing factors of the two communication parties being obtained through point multiplication of temporary public and private keys by means of composite characteristics of an elliptic curve algorithm, so that a one-time pad service data protection key being generated, and forward security of user data is ensured; and finally, respectively utilizing the calculation determinacy of the hash algorithm and the uncertainty of the random sequence to solve the problems of integrity protection of the user data in the transmission process and the anti-replay performance of the cryptographic protocol.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Anti-leakage forward security cloud data integrity remote verification method and system
InactiveCN111935091AGuaranteed validityIntegrity verification is validUser identity/authority verificationData integrityData file
The invention discloses an anti-leakage forward security cloud data integrity remote verification method and system. A data owner generates a public and private key pair of the data owner by using security parameters; the data owner generates authentication information of the outsourcing data by using a private key of the data owner, and uploads the outsourcing data and the authentication information to a cloud storage server; the data owner generates challenge information and sends the challenge information to the cloud storage server; the cloud storage server generates verification certification information by utilizing the public key of the data owner, the challenge information, the outsourcing data file and the authentication information set, and returns the verification certificationinformation to the data owner; the data owner verifies the integrity of the outsourcing data file by using the own public key, challenge information and verification certification information to obtain a verification result. The data owner obtains the current time period and updates the current time period to the next time period; the data owner acquires the key representing the node in the current time period, updates the key into a random new key and covers the original key.
Owner:SHANDONG UNIV
Method for Realizing User Data Security Migration Based on Voice Channel
ActiveCN112737784BGuaranteed forward securityAddressing Integrity ProtectionKey distribution for secure communicationPublic key for secure communicationConfidentialityCryptosystem
The invention discloses a method for realizing safe migration of user data based on a voice channel. A cryptographic system combining symmetric cipher and asymmetric cipher is deployed on a trusted terminal of a secure telephone communication network. Utilize the characteristics of fast encryption and decryption speed, high computing efficiency, and less resource occupation of symmetric ciphers to complete the confidentiality protection of user information; use asymmetric ciphers to calculate the difficulty of discrete logarithms in finite fields to realize the identity authentication of both parties in communication, and at the same time With the help of the complex characteristics of the elliptic curve algorithm, the shared factor of the two parties in the communication is obtained through the point multiplication of the temporary public and private keys, and a one-time secret service data protection key is generated to ensure the forward security of user data; finally, the hash algorithm is used respectively The calculation determinism of the random sequence and the uncertainty of the random sequence solve the integrity protection of the user data during transmission and the anti-replayability of the cryptographic protocol.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method and system for key generation during handover
InactiveCN103139771BPut an end to the possibilityImprove securitySecurity arrangementCommunications systemKey generation
The present invention discloses a key generation method and system in the handover process. The method includes: in the UE handover process, the network side uses the next hop parameter NH to generate the next hop key KeNB; wherein, the network side The generated NH does not notify the base station; the network side and the UE side respectively use the next hop counter NCC value notified by the target base station to synchronize the next hop key KeNB; the network side uses the generated next hop The changed key KeNB notifies the target base station. Since the base station cannot obtain the NH, it cannot generate the next-hop key KeNB, which avoids the possibility of illegally obtaining the next-hop key KeNB and ensures forward security. The invention greatly improves the security of the communication system.
Owner:ZTE CORP
An Efficient and Robust Dynamically Searchable Symmetric Encryption Method and System
ActiveCN110765469BImprove robustnessGuaranteed forward securityDigital data protectionTransmissionCiphertextTheoretical computer science
The invention discloses an efficient and robust dynamically searchable symmetric encryption method and system, belonging to the field of cloud storage security, including: for any keyword w, obtain the key used in the latest operation associated with it at the retrieval client Information and the corresponding ciphertext index L' and trapdoor T' to generate the ciphertext of the current operation and send it to the retrieval server, so as to store it in the ciphertext database; the ciphertext meta information of the generated ciphertext includes L ’ and T’; the ciphertext meta-information of the deletion operation ciphertext also includes the deletion credential; the key information is updated when the retrieval ciphertext is generated, and the ciphertext meta-information also includes the difference between the previous retrieval operation and the key used in the current retrieval operation To update the credentials between, send L' and T' while sending the retrieval ciphertext; at the retrieval server, obtain all the ciphertexts associated with the keyword w, delete the ciphertexts that need to be deleted, and send the result set to the retrieval client. The invention can improve the robustness of the searchable symmetric encryption method.
Owner:HUAZHONG UNIV OF SCI & TECH +1
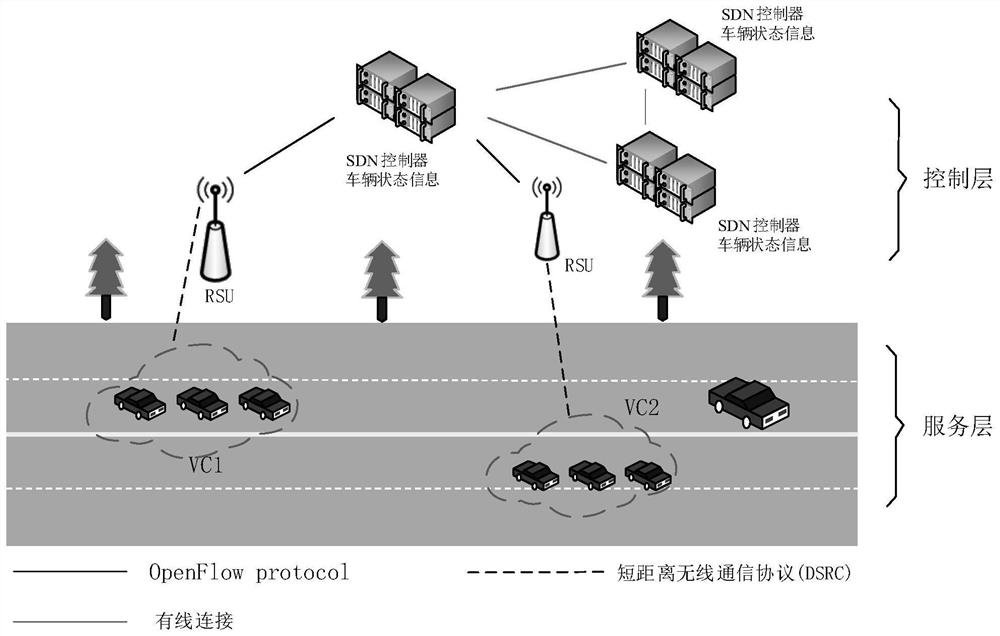
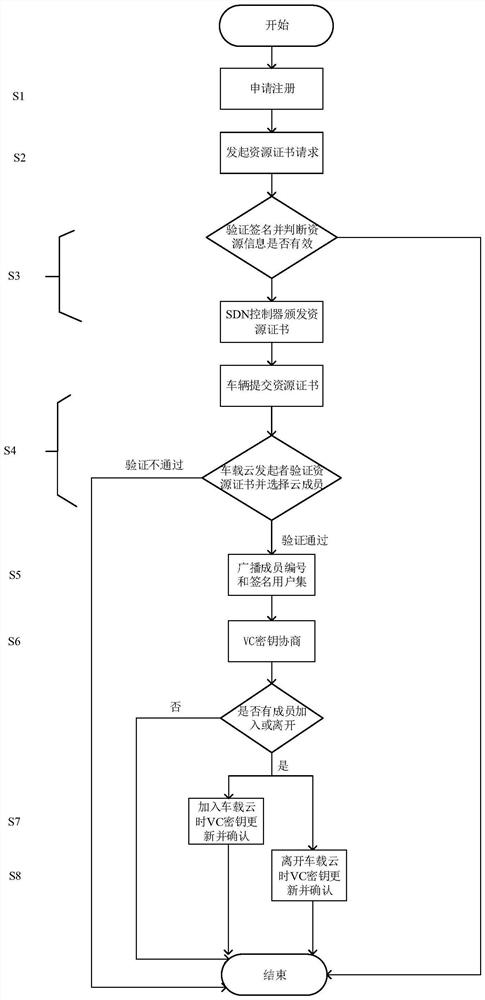
SDN (Software Defined Network)-based vehicle-mounted cloud computing method with privacy protection
PendingCN114389836AGuaranteed privacy and securityDisrupt normal executionKey distribution for secure communicationParticular environment based servicesCommunications securityIn vehicle
The invention relates to the technical field of vehicle-mounted network communication security, in particular to an SDN-based vehicle-mounted cloud computing method with privacy protection, which comprises the following steps: constructing an SDN-based vehicle-mounted cloud computing system, and applying for registration in the system and obtaining a resource certificate by a new vehicle; the vehicle-mounted cloud initiator selects the verified vehicles from the vehicles to form a vehicle-mounted cloud, numbers the selected vehicles and the vehicle, and negotiates vehicle-mounted cloud keys for all the vehicles in the vehicle-mounted cloud; when other new vehicles want to join the vehicle-mounted cloud, the vehicle-mounted cloud initiator verifies the validity of the resource certificate of the new user and then numbers the vehicles, and negotiates the vehicle-mounted cloud key again; when a member in the vehicle-mounted cloud leaves, the member leaving the vehicle-mounted cloud sends a leaving message to a neighbor vehicle of the member, and the key of the vehicle-mounted cloud is negotiated again; according to the invention, all vehicle nodes cannot confirm the real identity of the sender through the message and cannot track the position information of the vehicle through the link message.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
An ultra-lightweight RFID two-way authentication method
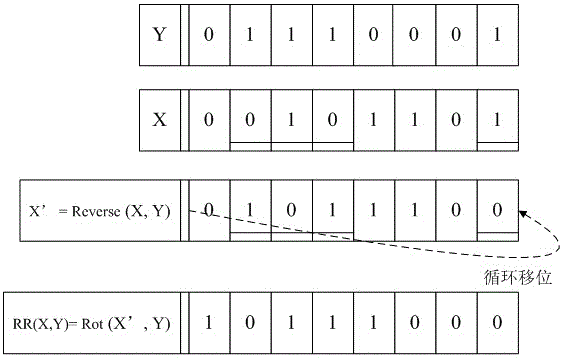
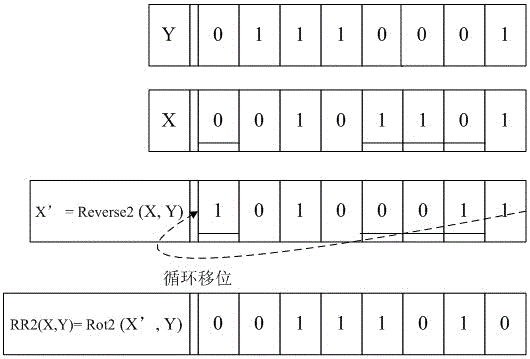
ActiveCN103716164BEasy to hideGuaranteed forward securityUser identity/authority verificationCo-operative working arrangementsNegationElectronic tagging
The invention discloses an ultra-lightweight RFID mutual authentication method, and belongs to the technical field of RFID. With a negation cyclic displacement operation processing tag and data stored by a rear-end database, secret data are greatly hidden. According to the authentication method, tag authentication is firstly performed, then a stage of mutual authentication is performed, and information stored by a reader-writer and an electronic tag is updated after success of mutual authentication so that forward security is guaranteed. New and old authentication information stored by the electronic tag is combined with resistance replay aggression data M which are designed in the authentication process by utilizing secret key information of the new and old authentication information so that non-synchronous aggression and replay aggression are effectively resisted.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
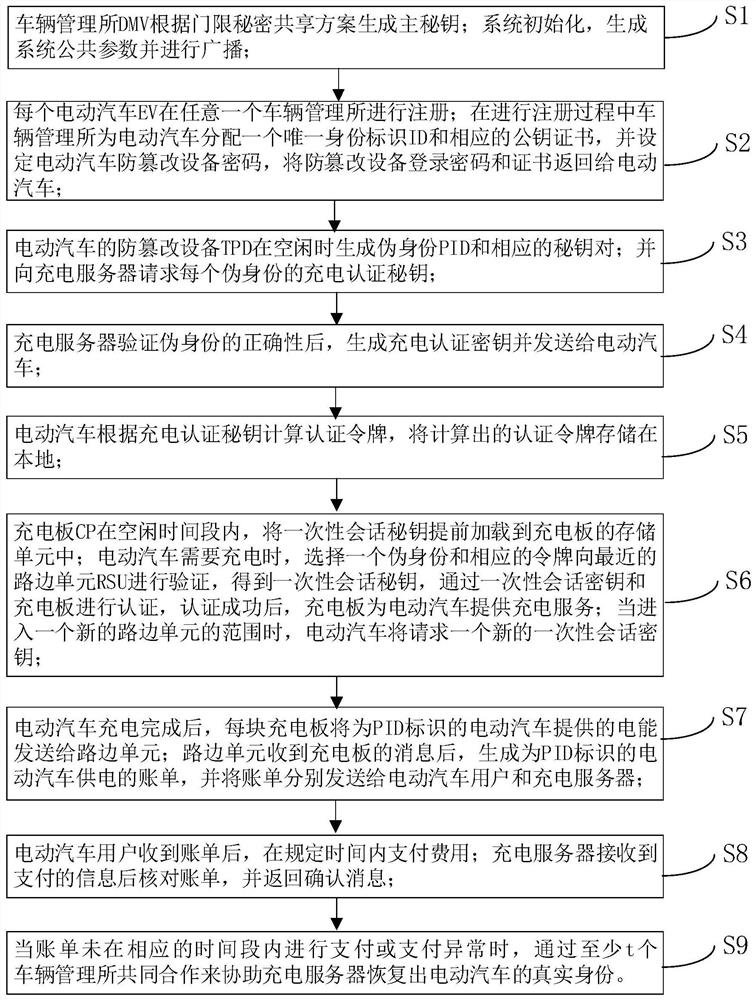
An authentication method and system for privacy protection of dynamic wireless charging of electric vehicles
ActiveCN113114630BImplement anonymous authenticationProtect identity privacyCircuit authenticationCharging stationsThird partyPrivacy protection
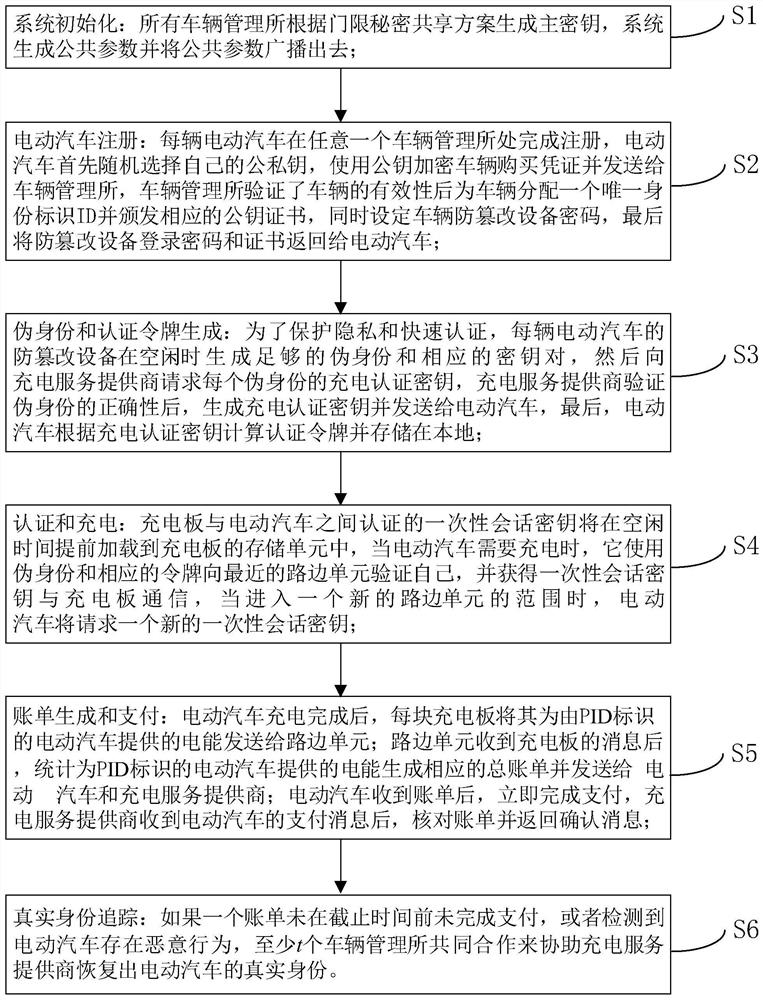
The invention belongs to the field of security authentication in the discipline of cyberspace security, and specifically relates to an authentication method and system for privacy protection of dynamic wireless charging of electric vehicles, including: registering an electric vehicle with a vehicle management office, obtaining a login password for an anti-tampering device of the vehicle, Log in to the anti-tampering device afterwards to generate a false identity and request an authentication token from the charging service provider, which enables the electric vehicle to pass the authentication of the roadside unit and obtain a one-time session key for authentication with the charging board; the present invention guarantees It improves the efficiency, identity privacy and location privacy of electric vehicles during charging authentication, and in case of disputes, with the assistance of multiple vehicle management offices, charging service providers can recover the true identity of the vehicle, ensuring the identity of the vehicle Not in the hands of any trusted third party.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
A method and system for security authentication of mobile terminal equipment based on chaotic mapping
ActiveCN112804680BEnsure safetyPrevent impersonation attacksUser identity/authority verificationSecuring communication by chaotic signalsWeb authenticationAttack
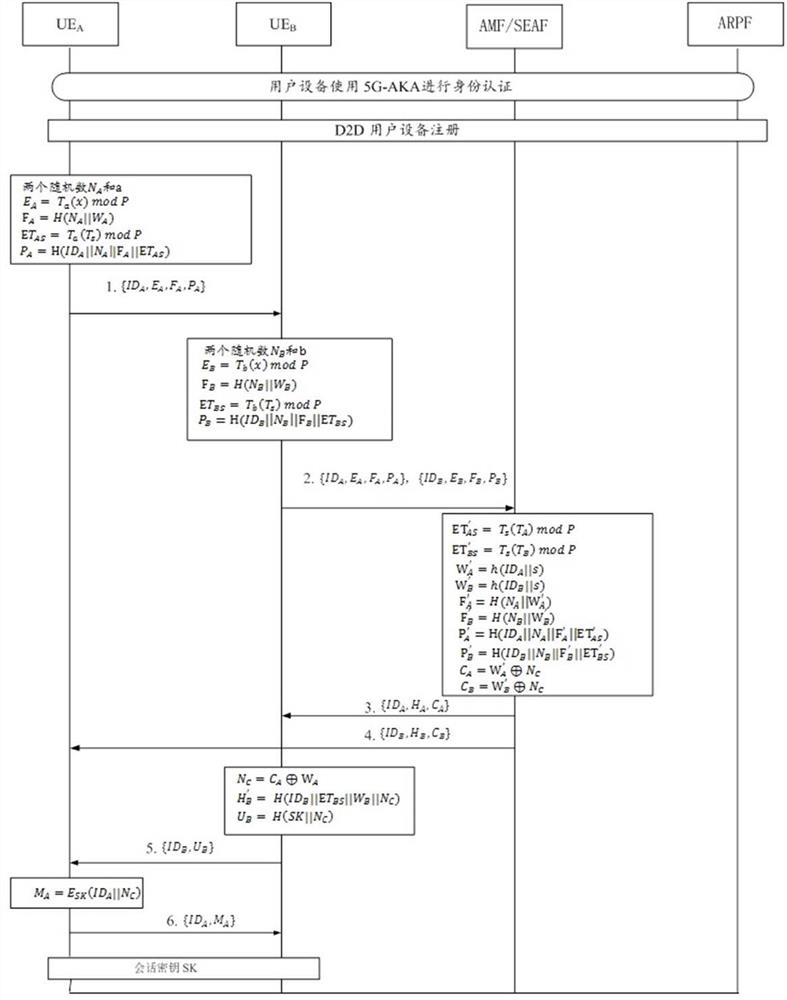
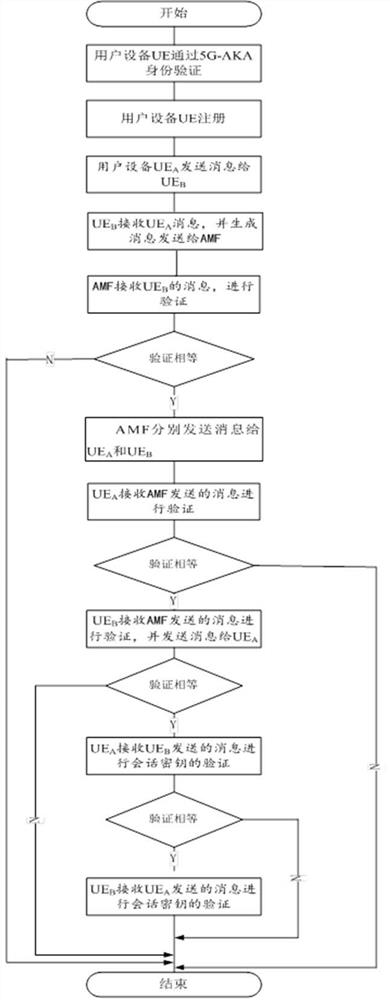
The present invention provides a method and system for security authentication of mobile terminal equipment based on chaotic mapping. For the device-to-device D2D communication on the wireless channel in the fifth-generation mobile network 5G, it is vulnerable to various passive or active attacks, such as eavesdropping and data tampering. and invasion of privacy, for one-to-one device communication, the UE first performs identity authentication through the 5G network authentication protocol 5G-AKA, and establishes a secure channel between the UE and the 5G network; when the user equipment UE performs D2D communication, the user equipment The UE performs authentication and key agreement with neighboring devices through the chaotic mapping algorithm. The present invention provides secure device discovery, mutual authentication, and key agreement mechanisms for adjacent terminals under the same 5G network. , Efficiently perform D2D communication.
Owner:北京电信易通信息技术股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com