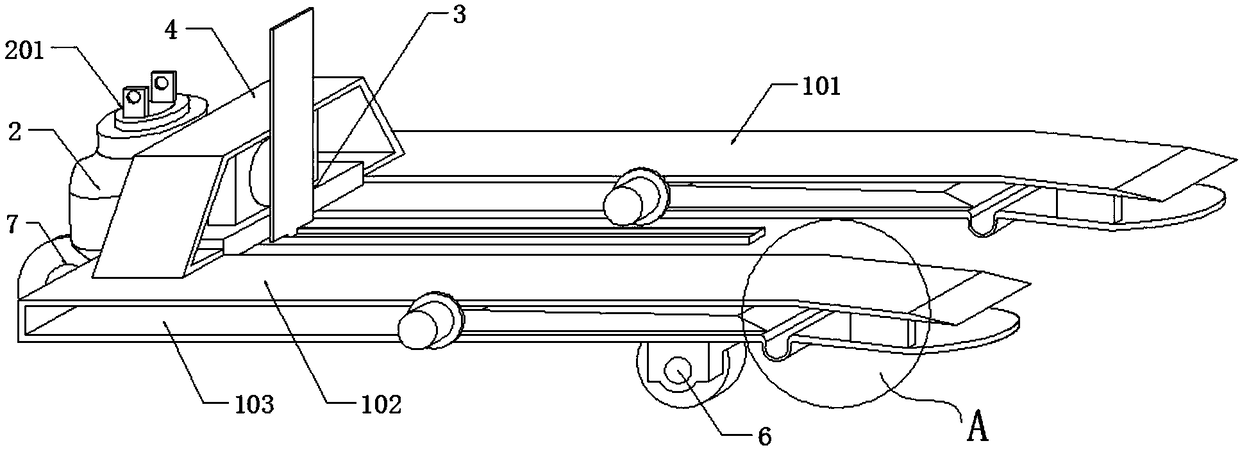
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
161results about How to "Effectively hide" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
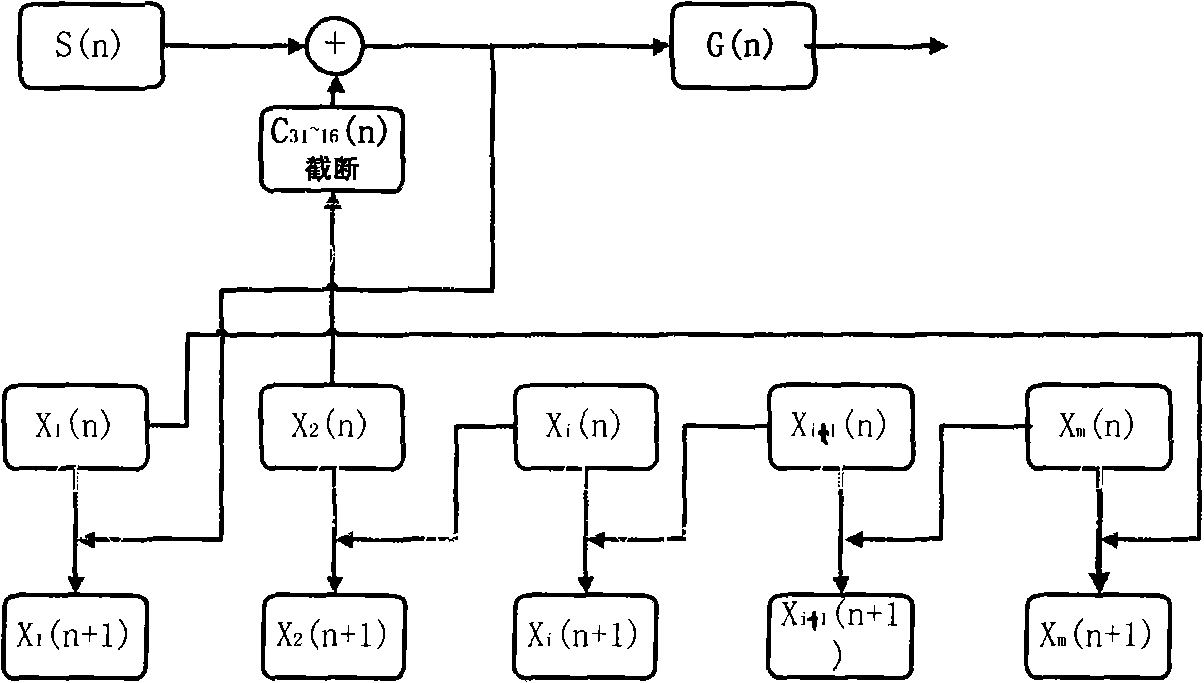
Online and intelligent optical cable monitoring and fault positioning system based on GIS platform
InactiveCN106788696AEasy storage and handlingSimple calculationElectromagnetic transmissionGeographical information databasesOptical powerOptical path
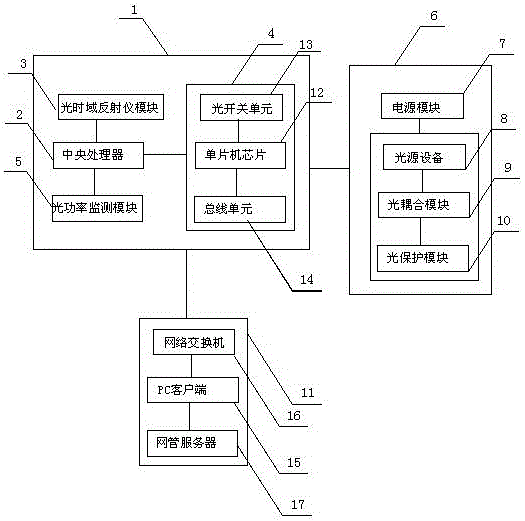
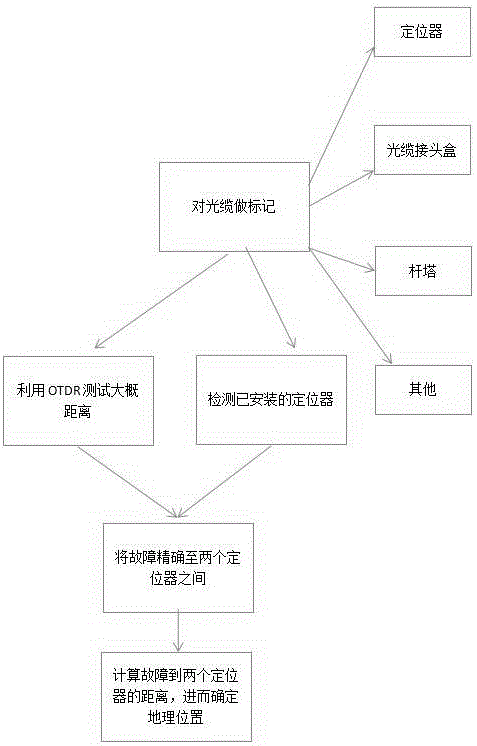
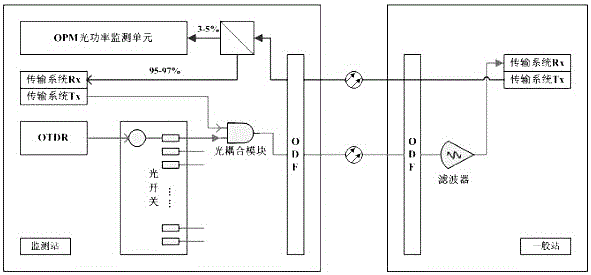
The invention provides an online and intelligent optical cable monitoring and fault positioning system based on a GIS platform. The online and intelligent optical cable monitoring and fault positioning system comprises a monitoring unit and a positioning unit, wherein the monitoring unit comprises an intelligent diagnosis mainframe, a diagnosis unit and a PC terminal display unit, the intelligent diagnosis mainframe comprises a central processing unit and an optical time domain reflectometer module, an optical path switching module and an optical power monitoring module connected with the central processing unit, the diagnosis unit comprises a power module and a light source device, an optical coupling module and an optical protection module connected with the power module, and the positioning unit comprises a fault locator arranged in an optical cable. Information is processed by calling optical cable information in time, and meanwhile the system can flexibly utilize a geographic information system (GIS) technology, adopts rack-type integration, and is high in integration level, good in stability and high in expandability. When breakdown occurs, the system can clearly display fault GPS points and fault types, maintainers can perform accurate positioning through a GIS map, and accordingly the maintenance efficiency is improved.
Owner:山西恒海创盈科技有限公司
Content distribution network based DDoS (distributed denial of service) attack protecting method and content distribution network based DDoS attack protecting system for cloud distribution platform
The invention discloses a content distribution network based DDoS (distributed denial of service) attack protecting method and a content distribution network based DDoS attack protecting system for a cloud distribution platform. The method and the system can effectively protect the cloud distribution platform from large-scale DDoS attacks. The technical scheme includes that the system comprises a plurality of content distribution network security nodes, an alarm component, a decision making component and a DNS (domain name server) component, wherein the content distribution network security nodes are used for detecting the DDoS attacks and executing protection strategies; the alarm component is connected with the content distribution network security nodes and is used for collecting and analyzing flow of the content distribution network security nodes and attack behavior characteristic matching and sending DDoS attack alarm information; the decision making component is connected with the alarm component and is used for analyzing the alarm information, generating the protection strategies aiming at the DDoS attacks, sending the protection strategies to the content distribution network security nodes and sending a switching instruction to the DNS component if the protection strategies include service switching nodes; and the DNS component is connected with the decision making component and is used for switching service nodes of a website according to the switching instruction.
Owner:CHINANETCENT TECH
Network video monitoring system based on FPGA chaotic encryption
InactiveCN101527823AFunction increaseConsider practicalityAnalogue secracy/subscription systemsClosed circuit television systemsPlaintextVideo monitoring
The invention relates to a network video monitoring system based on FPGA chaotic encryption, comprising a server terminal, a client terminal and a system configuration terminal. The server terminal comprises a plurality of cameras, a video server, an encryption module and a signal sending module; the client terminal comprises a signal receiving module, a decryption module and a client terminal player; video frequency collected by the plurality of cameras is coded by the server, then input into the encryption module via the Ethernet and sent to the client terminal via the signal sending module after encrypted; the signal receiving module of the client terminal receives the encrypted video data and then sends the data to the decryption module for processing and finally the client terminal player plays the video data; the encryption module and the decryption module are respectively an FPGA encryption board and a decryption board; the encryption process and the decryption process of the encryption module to video flow are as follows: the encryption module adopts a CPRS array which is cut and operates with a plain text data module 2, and then sent; and the receiving terminal of the decryption module obtains the same CPRS array, and then operates with a cryptograph module to realize decryption.
Owner:NANJING UNIV
Liquid crystal display device
ActiveCN103235432AGo borderlessSimple designStatic indicating devicesNon-linear opticsLiquid-crystal displayChip on film
The invention discloses a liquid crystal display device which is provided with a back plate, a light guide plate arranged on the back plate, an optical diaphragm arranged on the light guide plate, a rubber frame, a liquid crystal display panel, a driving chip and a flexible circuit board. The rubber frame is fixedly connected with the back plate so as to enable the optical diaphragm and the light guide plate to be fixed, the liquid crystal display panel is fixedly arranged on the rubber frame and comprises an upper glass substrate and a lower glass substrate, wherein the upper glass substrate and the lower glass substrate are arranged oppositely and comprise bottom surfaces, top surfaces and side surfaces for connecting the bottom surfaces and the top surfaces, and the flexible circuit board comprises metal leads and is connected to the liquid crystal display panel. The driving chip is connected with the flexible circuit board and connected to the liquid crystal display panel through the metal leads of the flexible circuit board in a coupling mode, a first wiring notch is arranged at the connecting position of the bottom surface and the side surface of the upper glass substrate, and the flexible circuit board connected to the liquid crystal display panel is wired through the first wiring notch. The liquid crystal display device enables chip on film (COF) to be hidden in the liquid crystal display device effectively and facilitates design of liquid crystal display panels without frames greatly.
Owner:CHANGSHA HKC OPTOELECTRONICS CO LTD
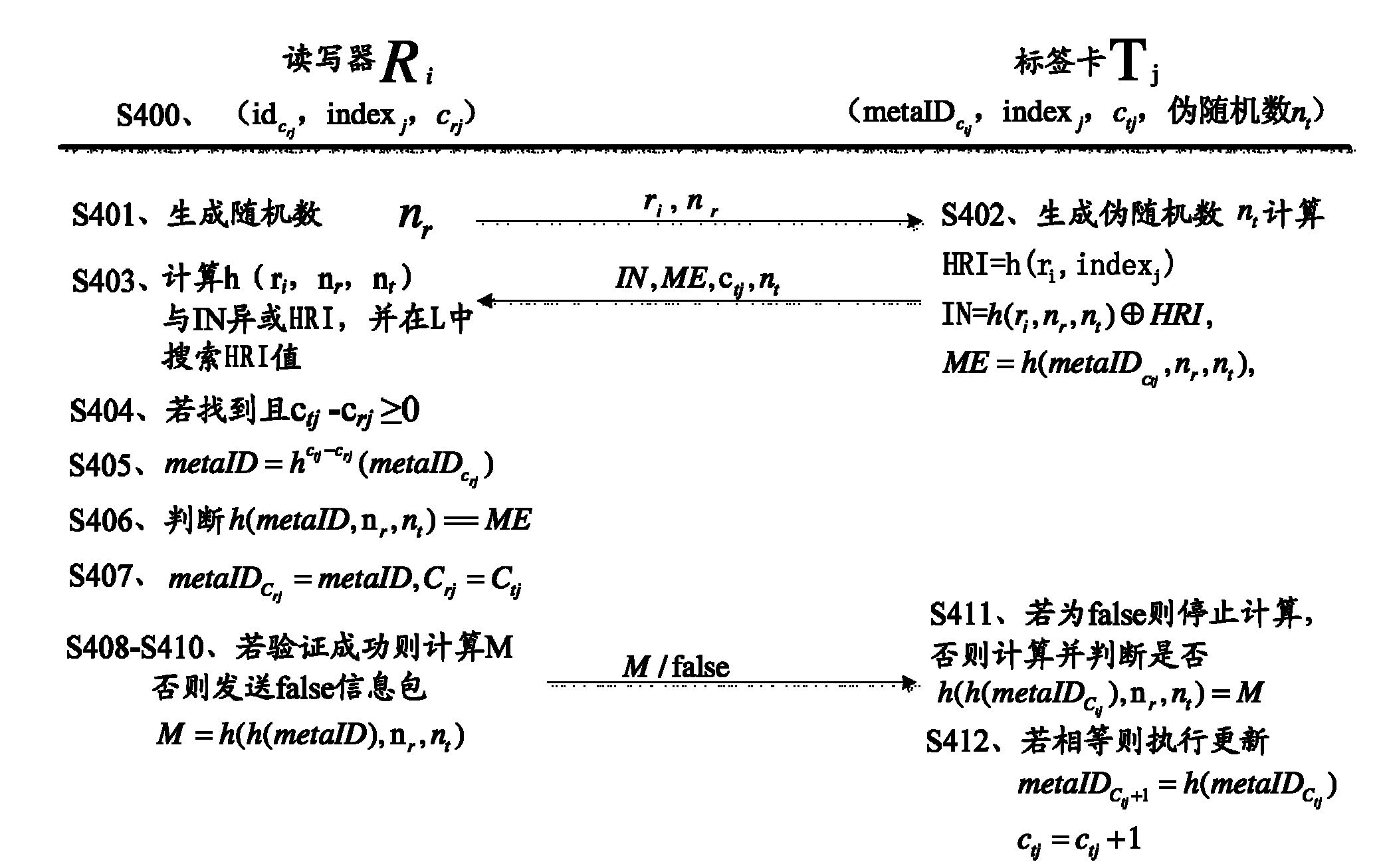
Dynamic authentication method between reader and tag card and implementing device thereof
InactiveCN102136079AEasy to useEffectively hideCo-operative working arrangementsDigital data authenticationComputer hardwareHash table
The invention discloses a dynamic authentication method between a reader and a tag card and an implementation device thereof for solving the technical problem that the traditional authentication method must depend on real-time online reliable and safe connection with a backstage database, and cannot authenticate the tag card with the reader autonomously at a high degree. In the method, only a legal reader can acquire corresponding tag authentication information from an authentication database to authenticate or update the state of the corresponding tag; only a legal tag can be processed by the legal reader; a dynamic updating mechanism is applied to the tag identification (ID) in the authenticating process to ensure the forward security, and the reader stores the tag card information by adopting a Hash table, thereby improving the authentication speed; and data synchronization is realized skillfully in an attribute value mode; and the use of random numbers ensures that different data packets can be used in each authentication, so that the position information of the tag is effectively concealed and high security characteristic is provided.
Owner:ZTE CORP
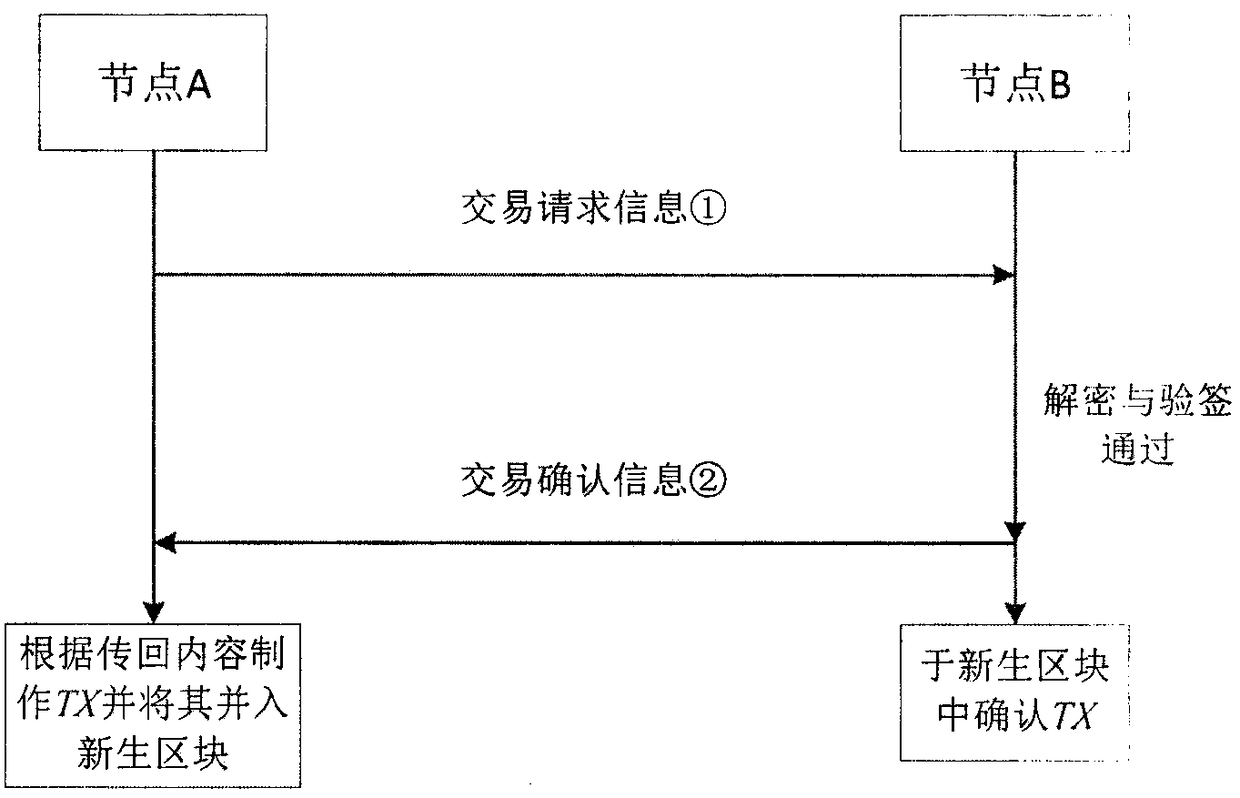
A block chain privacy protection scheme and system based on SM9 algorithm
InactiveCN109409884ASolve problems that are difficult to apply to real-world scenariosSolve application problemsDigital data protectionProtocol authorisationChain structurePrivacy protection
The invention discloses a block chain privacy protection scheme and a block chain privacy protection system based on an SM9 commercial cryptographic algorithm in China, belonging to the field of blockchain security and privacy protection. This invention provides an inter-node transaction platform based on federation chain, defines the permissions and functions of various nodes in the platform, and supports node transaction, information verification, parameter maintenance, block generation and other functions. This invention describes an improved SM9 multi-KGC (Key Generation Center) signaturealgorithm, which improves the working mode of single KGC in SM9 algorithm, adapts to the federation chain structure, and adopts this algorithm to determine the identity of the opposite party in the transaction between nodes. A group signature scheme based on SM9 algorithm is proposed. The identity verification of SM9 algorithm is improved to group signature verification, which effectively protects the identity privacy of the signatory. The transaction information is signed by the node through the algorithm and written into the block chain after the transaction, which can effectively hide theidentity information of both parties of the transaction, protecting the privacy of the node and ensuring the legitimacy of the transaction.
Owner:BEIJING ANRUSHAN CULTURE TECH
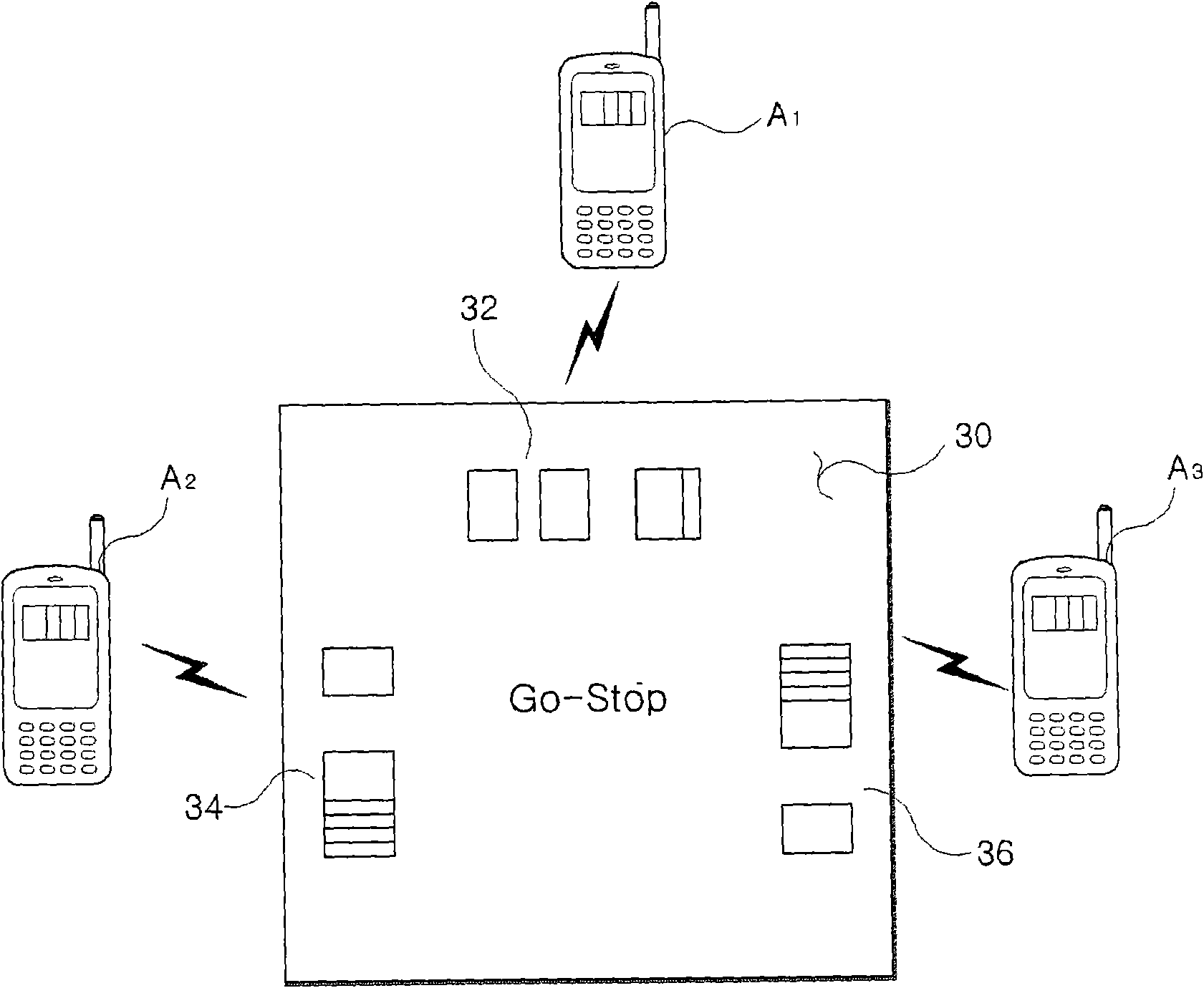
Game system and method in combination with mobile phones and a game console
InactiveCN101578619AEffectively hideEnhance interestOther printing matterFiling appliancesDisplay deviceLarge screen
A game system and method for enabling a mobile phone to interact with a user game console is disclosed. The game system enables a mobile phone and a user game console to interact with a game server, enables the user game console to interact with a video display, displays video data generated from the user game console on the video display in order to allow a user or gamer to play a desired game on a large screen, and allows a plurality of gamers to play the game using a single user game console over wireless communication for use of mobile phones. The game system can display different information on not only a common screen for all the game participants but also at least one screen for each gamer only, such that a plurality of gamers can participate in the game at the same time on a single screen image, resulting in the implementation of the simultaneous-participation games.
Owner:アルオンゲームズ
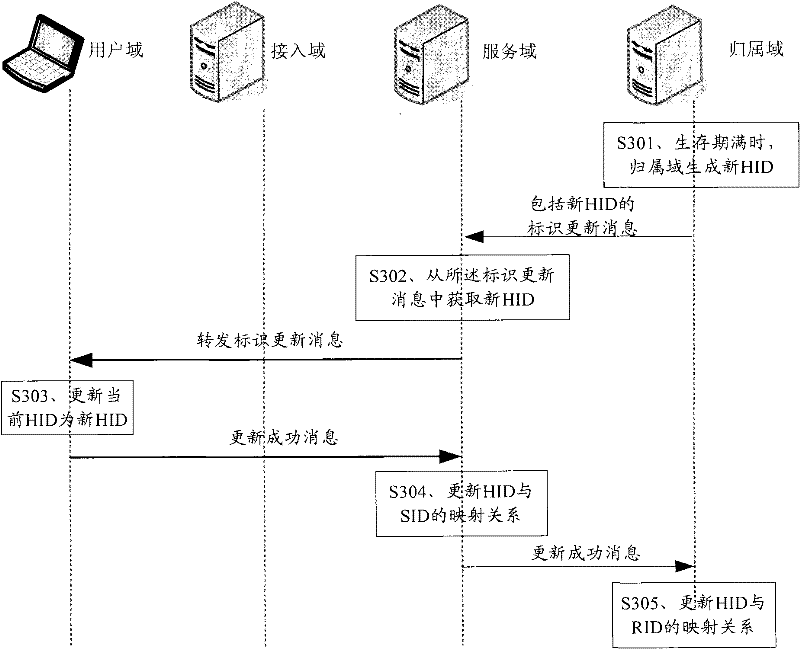
Identification distribution and separate-storage method, identification replacing transmission method and system
InactiveCN101754219AImprove the protective effectSupport mobilitySecurity arrangementTelecommunicationsService domain
The invention discloses an identification distribution and separate-storage method, an identification replacing transmission method and system, relating to the field of network safety. The identification distribution and separate-storage method comprises the following steps of: dividing a heterogeneous wireless network by function into a user domain, an access domain, a service domain and an attribution domain, wherein the service domain comprises at least one access domain, the access domain comprises at least one user domain, and the attribution domain and the service domain are the same network when in local service; and after the successful authentication of a terminal, allocating the attribution domain, the service domain and the access domain with domain identifications domain by domain. Based on the access authentication of the heterogeneous wireless network, the invention provides a mechanism of the identification distribution, the separate storage and the replacing transmission of the identification. In the transmission process of the domain identification in the user domain, the access domain, the service domain and the attribution domain, the real identity and the location information of a terminal can be effectively concealed through the retrieval and the replacement among domains and the dynamic update at different identification mapping servers, thereby enhancing the credible access of the heterogeneous wireless network and the safety protection capacity on mobility problems.
Owner:THE PLA INFORMATION ENG UNIV
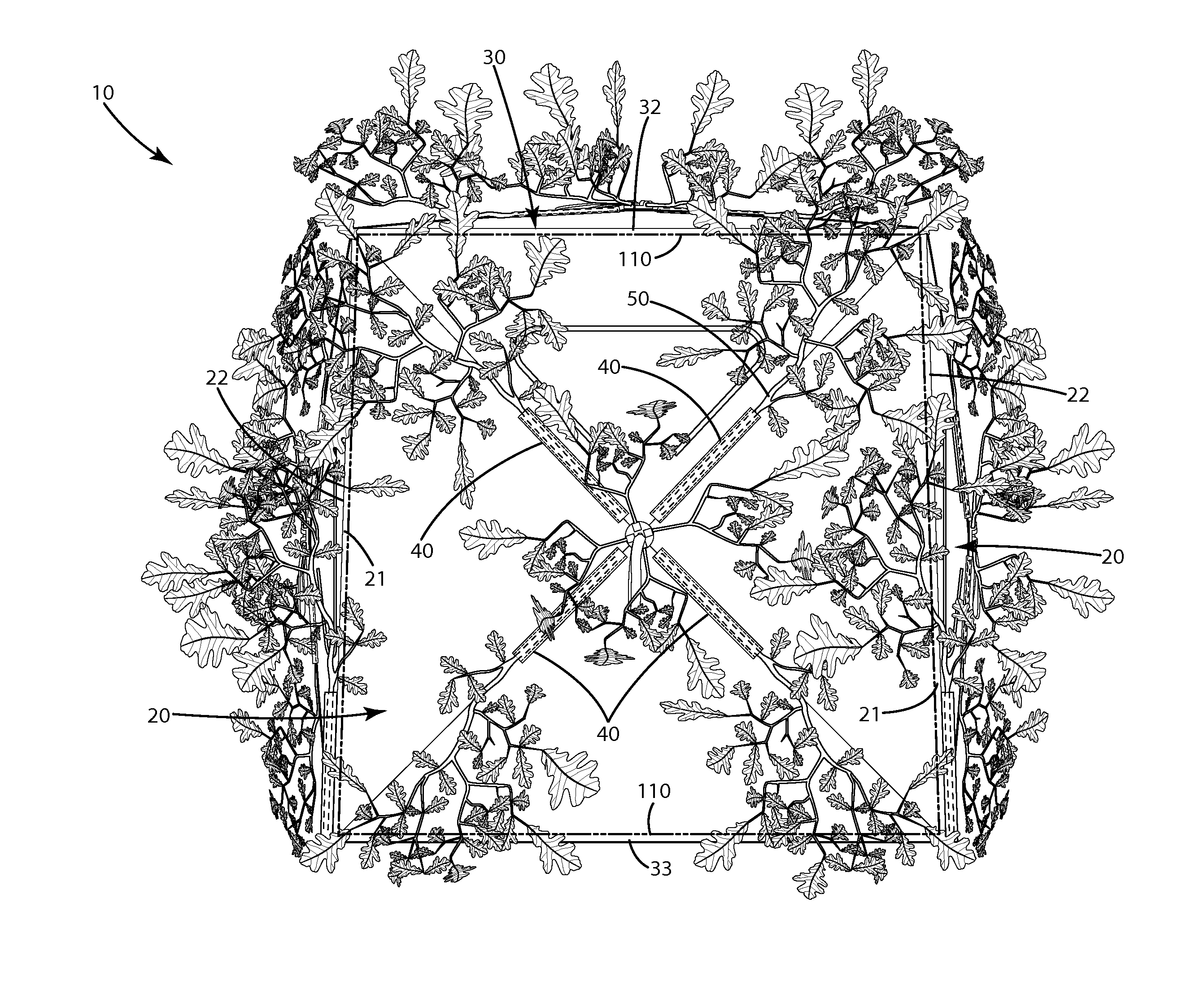
Portable blind and concealment system
ActiveUS8066022B2Effectively concealEffectively hideTents/canopiesWindow shutterBiomedical engineering
Owner:AMERICAN PRIDE OUTDOORS LLC
Method for realizing communication between IPv6 private network node and public network node and routing forwarding equipment
ActiveCN102932371AAchieve protectionRealize communicationData switching networksPrivate networkIp address
The application discloses a method for realizing communication between an IPv6 private network node and a public network node. The method comprises the following steps: receiving a message by routing forwarding equipment from the IPv6 private network node, and selecting one IPv6 address from the public IPv6 addresses configured for a corresponding interface of the routing forwarding equipment when the source IP addresses of the message are private network addresses and target IP addresses are public network addresses, wherein the prefix of the IPv6 address is used as the address prefix for the private network node to access to the public network, and the prefix of the IPv6 address is different from the address prefix used for the private network node to access to the public network last time; sending a router announcement (RA) which comprises the address prefix and the effective time to the private network node, wherein the RA is used for triggering the private network node to generate a polymerizable global unicast address with the address prefix in the RA, and the global unicast address is used for the communication between the private network node and the public network node. The application further discloses the routing forwarding equipment. Due to the adoption of the method and the routing forwarding equipment, the private network node can be effectively protected against the attack of the external network during the communication between the IPv6 private network node and the public network node.
Owner:XINHUASAN INFORMATION TECH CO LTD
Color moisture-absorbing article
Disclosed is a colored absorbent article to be attached to an inner side of an undergarment matching in color with the article. The absorbent article has a body surface for facing the skin of a wearer and a garment surface for facing the inner side of the undergarment. The absorbent article includes a topsheet appearing on the body surface. The topsheet is a nonwoven fabric formed of only colored fibers that are at least one kind of fibers selected from synthetic resin fibers, semi-synthetic fibers and regenerated fibers. When measured for the body surface of the absorbent article, a Munsell value is in a range of 5.7 to 9.3.
Owner:UNI CHARM CORP
Anti-counterfeiting ink with delayed fluorescence and application of ink
The invention discloses anti-counterfeiting ink with delayed fluorescence. The anti-counterfeiting ink is prepared from a delayed fluorescence material, a dispersion solvent, a water-soluble macromolecular polymer, water and the like. The delayed fluorescence material can emit visible light under ultraviolet excitation and emit delayed fluorescence after ultraviolet excitation. An information hiding and anti-counterfeiting method comprises the steps as follows: the anti-counterfeiting ink with delayed fluorescence forms a first mark containing confidential information; the first mark is coatedwith a second mark containing interference information formed by anti-counterfeiting ink with phosphorescence to form an anti-counterfeiting mark. The anti-counterfeiting mark displays the interference information under ultraviolet irradiation and after irradiation in a dry state and displays the interference information and the confidential information under ultraviolet irradiation and after irradiation in a moisture wet state. Decryption and encryption are realized by use of the principle that the delayed fluorescence material is insensitive to air and vapor and phosphorescence is quenchedunder the effects of air and vapor, operation is convenient, the cost is low, and the anti-counterfeiting performance is excellent and stable.
Owner:NINGBO INST OF MATERIALS TECH & ENG CHINESE ACADEMY OF SCI
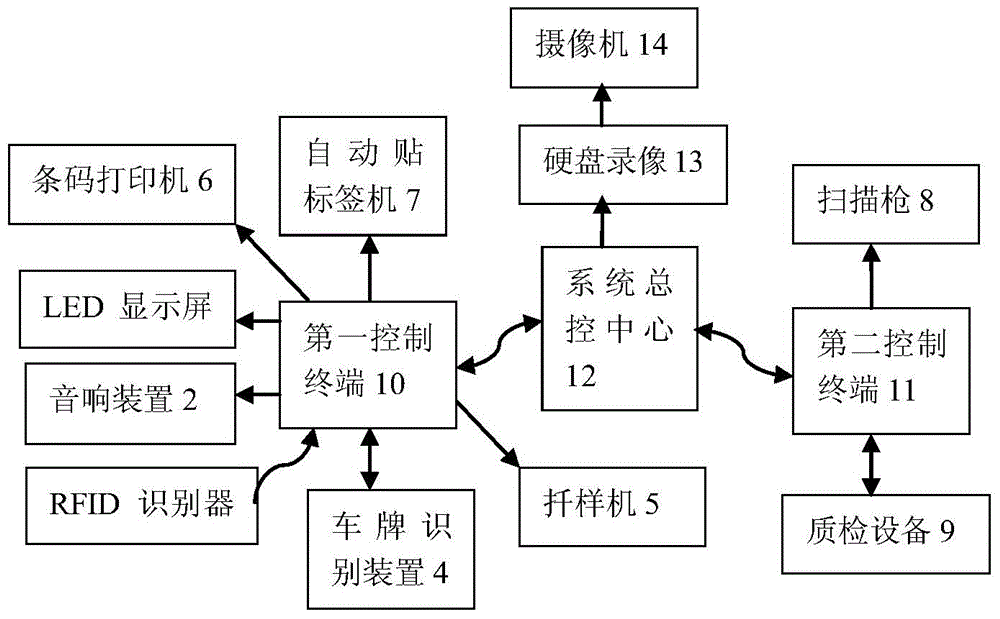
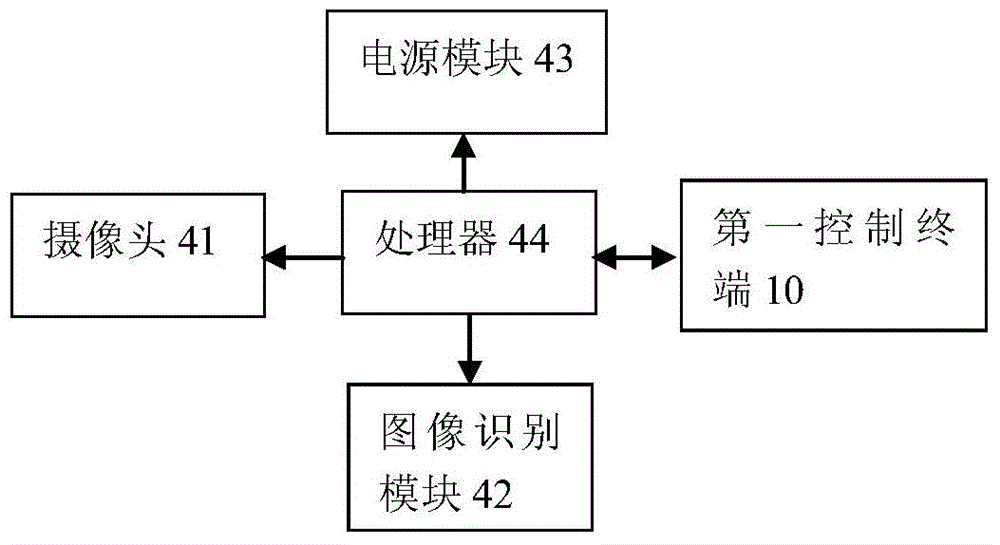
Intelligent sampling and quality testing system and method for grain depot
InactiveCN104537470ARealize integrated managementImprove work efficiencySensing record carriersResourcesIntelligent lightingWeb service
The invention provides an intelligent sampling and quality testing system and method for a grain depot. Integrated management of all processes of grain sampling and quality testing is achieved by comprehensively using technologies and methods of grain truck mechanical sampling, barcode information encoding, distributed web service, wireless bridging and the like, real-time transmission of sampling data and concealing of sample information are achieved, and the purposes of improving working efficiency, avoiding fraudulent practices and optimizing management are achieved.
Owner:ANHUI BOWEI CHANGAN ELECTRONICS
Traffic sign device
InactiveCN1460974AEasy to operateImprove structural strengthTraffic signalsRoad signsMechanical engineeringTraffic sign
Owner:HYNYANG FRAME CO LTD
Electric paying method based on trade code
The present invention provides an electronic payment method based on transaction codes. When a payer pays to a payee, the present invention comprises the following steps: the payer sends a payer identification code and payment amount to a payment platform; the payment platform generates a first transaction code; the payment platform sends the first transaction code to the payee; the payer calculates the first transaction code and a payer password to generate a second transaction code; the payer sends the second transaction code to the payee; the payee sends the payer identification code and the second transaction code to the payment platform; the payment platform sends payment success information to the payer and the payee. The method can be widely applied in the electronic payment field.
Owner:祁勇
Chaotic secret optical communication system based on double random phase encoding
PendingCN111314048ALarge key spaceImprove securityKey distribution for secure communicationSecuring communication by chaotic signalsTime domainPhase Code
The invention discloses a chaotic secret optical communication system based on double random phase encoding, and the system comprises a transmitting end which carries out the intensity modulation of achaotic optical signal and secret data; the double random phase encoding device comprises a first phase modulation module, a dispersion device and a second phase modulation module; the first phase modulation module is driven by a random key sequence A; different first phase codes are dynamically applied to the chaotic modulation signal in a time domain, then the chaotic modulation signal enters adispersion device and interacts with the dispersion device, through phase-intensity conversion of the dispersion device, intensity distribution of the chaotic modulation signal is disturbed in the time domain, and the waveform of the chaotic modulation signal is converted into a random-like noise signal; and the second phase modulation module is driven by the random key sequence B, performs second phase encoding on the chaotic modulation signal, and performs phase disturbance on the chaotic signal. According to the invention, the security of the secret data of the chaotic sending end is significantly enhanced.
Owner:GUANGDONG UNIV OF TECH
Vehicle-mounted head-up display system based on transparent imaging glass
ActiveCN106324839ASpecial three-dimensionalEffectively hideVehicle componentsOptical elementsHead-up display3d image
The invention relates to a vehicle-mounted head-up display system based on transparent imaging glass. The system comprises a vehicle head and a front windshield. A projector and a central processing unit used for controlling the projector are arranged in the vehicle head. The protector is connected with the central processing unit through a data line. The top of the vehicle head is provided with a light-pervious hole and a mirror outside a vehicle, the light-pervious hole can project an image in the projector, the mirror can reflect the image transmitted from the light-pervious hole to the front windshield, the front windshield is formed by stacking and fusing a transparent supporting layer and a nanoparticle thin film layer, and the nanoparticle thin film layer is a transparent material layer where nanoparticles are evenly distributed with a resin material as a carrier. Product investment cost is low, the projection image of the projector is reflected on the front windshield through light and can display a 2.5D or 3D image effect, light utilization efficiency reaches 24-30%, a clearer image can be represented, visual fatigue is effectively relieved, a projection device can be effectively hidden, and an optical path is corrected to prevent the vision in a cab from being sheltered.
Owner:SHANGHAI LANMOU MEDIA TECH CO LTD
Small desk type dish-washing machine
PendingCN108378800AEasy layout designImprove performanceTableware washing/rinsing machine detailsDeskEngineering
The invention relates to a small desk type dish-washing machine. The small desk type dish-washing machine comprises a machine body bottom plate, a base assembly, a liner assembly, a PCB, a door plateassembly, and a shell composed of a first side plate, a second side plate and a top plate, wherein an upper spray arm assembly is arranged on the top of the liner assembly, and a lower spray arm assembly is arranged on the base assembly; an air blowing assembly is arranged between the first side plate and the liner assembly, an air inlet of the air blowing assembly corresponds to and communicateswith a side plate air inlet in the first side plate, and an air outlet of the air blowing assembly corresponds to and communicates with a liner air inlet in the liner assembly; an air exhaust assemblyis arranged between the second side plate and the liner assembly, and an air inlet of the air exhaust assembly corresponds to and communicates with a first liner air outlet in the liner assembly. Thesmall desk type dish-washing machine provided by the invention is small and exquisite in structure size, the restricted problems including that the space of a kitchen is small, but users are in soreneed of a dish-washing machine, are solved, certain desire and demands of the users are fully satisfied, meanwhile, a fan drying system is configured, and thus the property of the machine is sufficiently improved.
Owner:中山市吉相电器有限公司
Portable blind and concealment system
ActiveUS20100269876A1Effectively concealEffectively hideTents/canopiesEngineeringBiomedical engineering
A portable collapsible blind is provided including positioning members and simulated arborescent structures to break-up the hard geometric shape and lines of the blind. The positioning members can position the simulated arborescent structures to extend beyond at least one of a sidewall, side edge, upper edge, sidewall corner, roof edge, roof corner and roof a preselected distance. The simulated arborescent structure can include a limb and a leafy part suspended by the limb at a location distal from the geometric shape of the blind. A concealment pod also can be provided. The concealment pod can include a base with a plurality of outwardly projecting simulated arborescent structures. The base can include the fastener element that joins with a corresponding fastener element of a joining element. The base and joining element can be pivotally joined so that the simulated arborescent structures can be oriented in a variety of configurations.
Owner:AMERICAN PRIDE OUTDOORS LLC
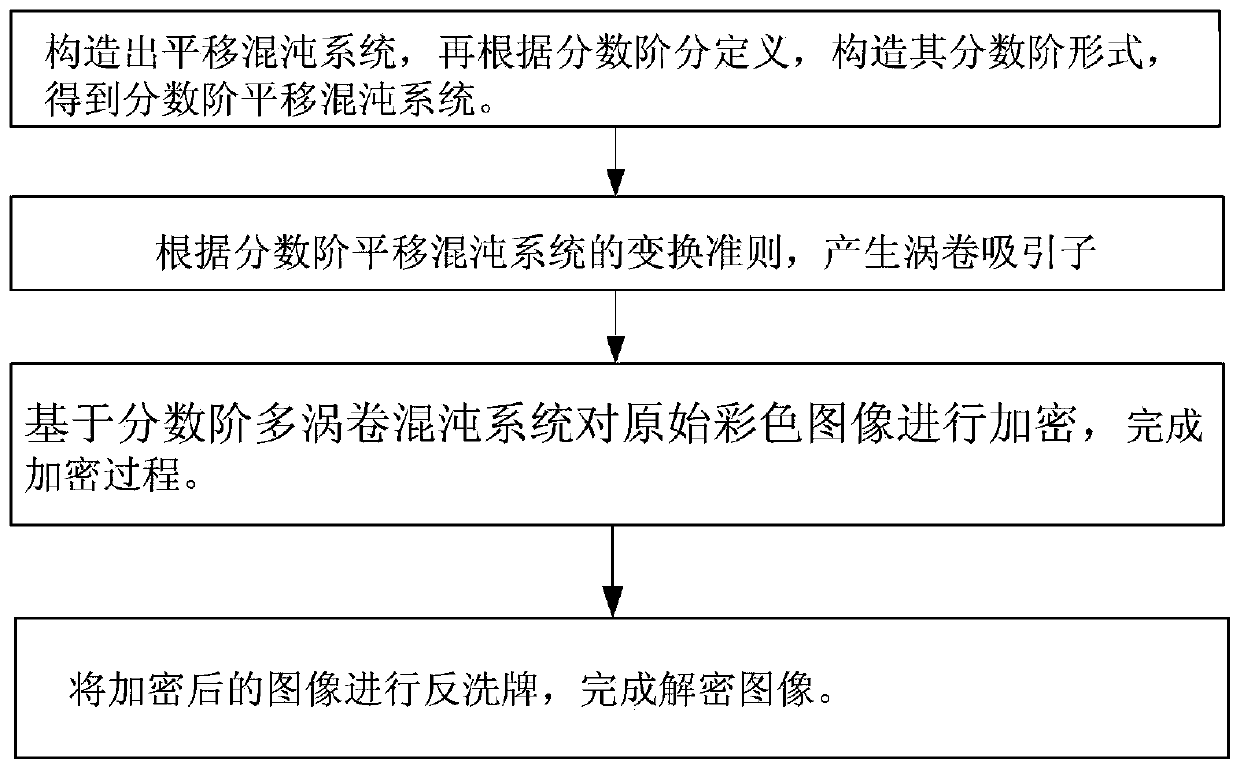
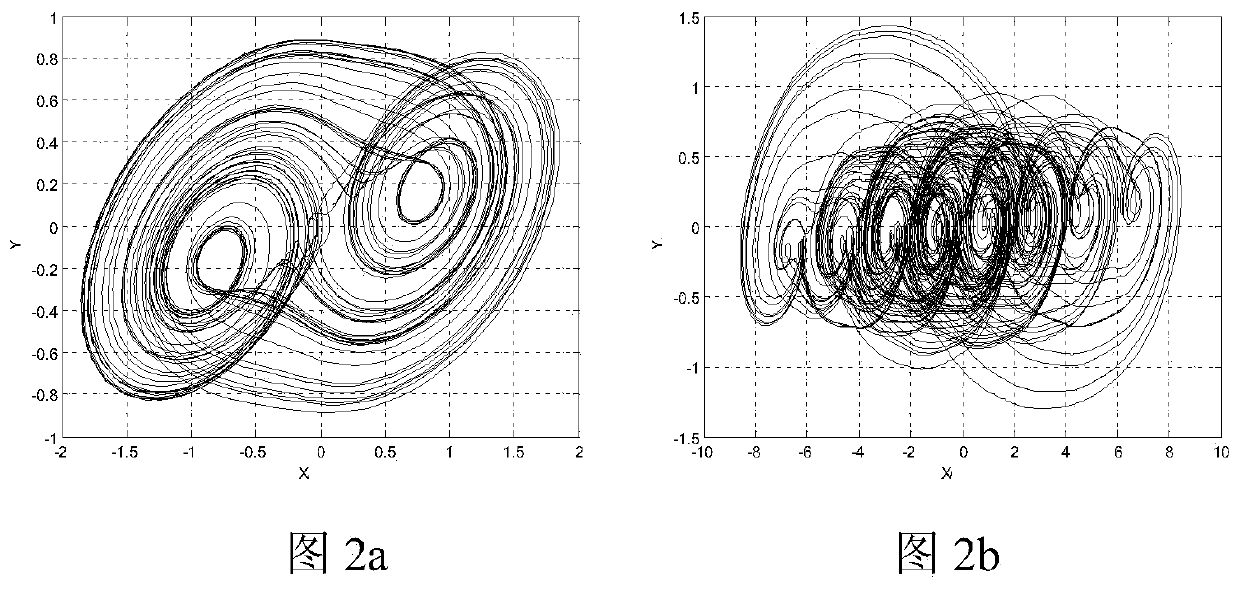
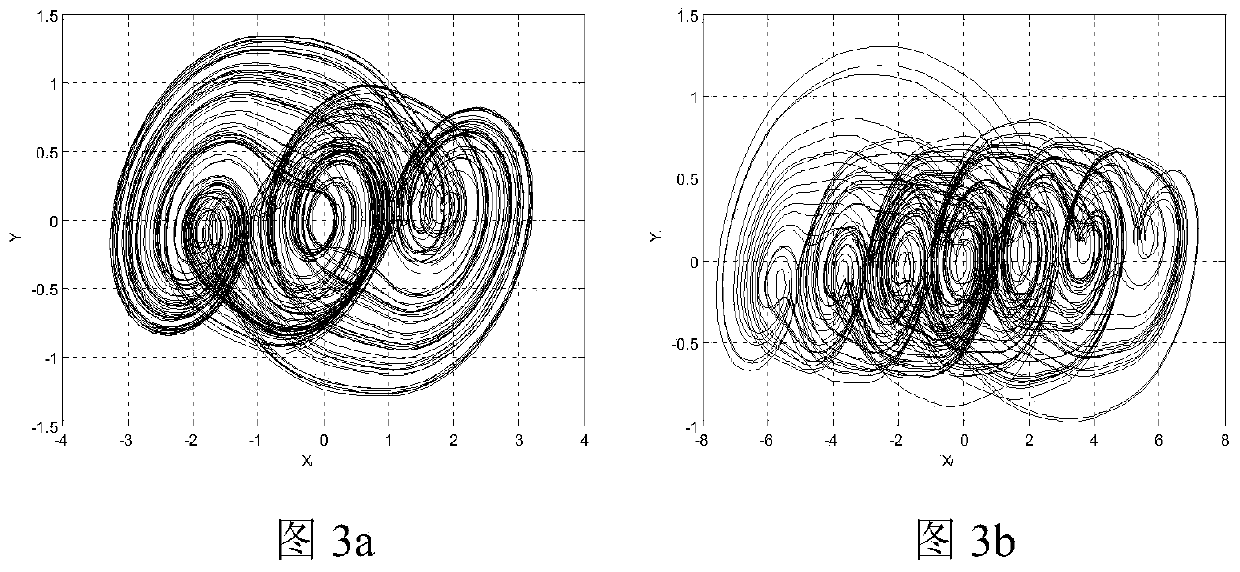
Image encryption and decryption method based on fractional order translation chaotic system
PendingCN110572252AHigh dimensional spaceStrong initial value sensitivityDigital data protectionSecuring communication by chaotic signalsComputer hardwarePlaintext
The invention discloses an image encryption and decryption method based on a fractional order translation chaotic system, and relates to the fields of computer cryptography, image encryption processing and communication and network engineering, which can solve the problems that initial conditions of an existing chaotic system are not associated with plaintexts, plaintext attacks cannot be resisted, and the safety is poor. According to themethod, translation transformation is conducted on the fractional order chaotic system by introducing a piecewise function, parameters are set, different numbers of scroll attractors can be generated, and the fractional order translation chaotic system perfects the field of fractional order chaotic systems composed of three-dimensional one-time autonomousconstant differential. Meanwhile, the fractional order multi-scroll chaotic system has higher dimension space and higher initial value sensitivity, the image encryption and decryption algorithm basedon the system is high in randomness and multiple in secret key parameters, a multi-iteration mode is adopted in the encryption process, an encrypted ciphertext matrix becomes very uniform, and therefore the purpose of effectively hiding original image information is achieved.
Owner:CHANGCHUN UNIV OF TECH
WEB dynamic security defense method and system
InactiveCN110381049AImplement virtualizationImplement one-shot transcodingTransmissionWeb applicationWeb service
The invention discloses a WEB dynamic security defense method and system. The method is based on a moving target defense technical thought. The invention provides an active dynamic defense mechanism for a WEB service system. When the protected WEB application service system is not attacked, the service entry or the resource address is actively transformed, so that the information of the backgroundof the server is effectively hidden and protected, the dynamics and uncertainty of the attacked surface of the system are realized in a randomized dynamic coding technical mode, the difficulty of network attack implementation is improved, and the anti-attack capability of the WEB application service system is effectively enhanced.
Owner:浙江智贝信息科技有限公司
Double U-groove and joint node structure using same
The embodiment of the present invention provides a double U-shaped groove and a joint structure using the double U-shaped groove. The double U-shaped groove includes: a first U-shaped groove and a second U-shaped groove; The first U-shaped groove includes a groove The top, the two side walls of the grooves, and the two groove edges, wherein the first ends of the side walls of each groove are respectively connected to opposite ends of the groove top, and the second ends of the side walls of each groove are located on the same side of the top of the groove and are respectively connected to each The first end of the groove edge and the second end of each groove edge extend in a direction away from the side wall of the groove, and a first flange and a second flange are provided on the opposite inner wall surfaces of the side walls of each groove; the second U-shaped The slot includes a cover plate and two support plates, wherein each support plate is located on the same side of the cover plate, and the first end of each support plate is respectively connected to the cover plate, and the second end of each support plate is respectively provided with limit hooks Correspondingly, a joint joint structure using double U-shaped grooves is provided, which has high strength and is not easily deformed, and the double-supporting and limiting technology of reverse hooks ensures the integrity and decoration of the double U-shaped grooves.
Owner:DUOWEI UNION GRP
Intelligent drum brake type anti-theft lock for electric vehicle
ActiveCN104372995AAvoid blockingEasy to useAnti-theft cycle devicesNon-mechanical controlsElectric vehicleMotor shaft
The invention discloses an intelligent drum brake type anti-theft lock for an electric vehicle. The intelligent drum brake type anti-theft lock for the electric vehicle comprises a remote control and a cylindrical drum body (22) installed on a motor shaft of the electric vehicle and a drum brake body (21), wherein a confined space of the drum brake body (21) is formed through a round decorative cover plate (37), an assembly lower shell (23) and an assembly upper cover (36) which are matched to form an assembly shell are installed on the brake drum main body (21), a circuit control board (24) is installed in the assembly shell and is electrically connected with a micro motor (25), a worm (251) is arranged on a shaft of the micro motor, and a locking mechanism is driven by the worm (251) through a transmission mechanism installed on the assembly lower shell (23) according to the rotating direction of the micro motor (25) to achieve unlocking and locking. According to the intelligent drum brake type anti-theft lock for the electric vehicle, electric power is supplied or cut off under the control of the remote control, the control circuit board is arranged, the electric vehicle can be locked automatically when a key is pulled out after parking, operation is convenient, and the degree of automation is high.
Owner:YUEQING LECHI HONGSHENG LOCK IND TECH CO LTD
Network video monitoring system based on FPGA chaotic encryption
InactiveCN101527823BEffectively hideImprove securityClosed circuit television systemsSelective content distributionVideo monitoringFpga implementations
The invention relates to a network video monitoring system based on FPGA chaotic encryption, comprising a server terminal, a client terminal and a system configuration terminal. The server terminal comprises a plurality of cameras, a video server, an encryption module and a signal sending module; the client terminal comprises a signal receiving module, a decryption module and a client terminal player; video frequency collected by the plurality of cameras is coded by the server, then input into the encryption module via the Ethernet and sent to the client terminal via the signal sending moduleafter encrypted; the signal receiving module of the client terminal receives the encrypted video data and then sends the data to the decryption module for processing and finally the client terminal player plays the video data; the encryption module and the decryption module are respectively an FPGA encryption board and a decryption board; the encryption process and the decryption process of the encryption module to video flow are as follows: the encryption module adopts a CPRS array which is cut and operates with a plain text data module 2, and then sent; and the receiving terminal of the decryption module obtains the same CPRS array, and then operates with a cryptograph module to realize decryption.
Owner:NANJING UNIV
Game data processing method, device and equipment and medium
The invention provides a game data processing method, a device and equipment and a medium, the method relates to rendering processing of game data such as cloud games, mobile games, end games and webgames, and the method comprises the steps of obtaining interface calling information for rendering function interfaces in a first process and to-be-rendered game data, transmitting interface calling information and to-be-rendered game data between the first process and the second process; wherein the first process refers to a process running in a black box and used for executing game logic, and the second process refers to a process running outside the black box and used for executing rendering logic; and when the second process obtains the interface calling information and the to-be-renderedgame data, calling a rendering function interface in the second process according to the interface calling information, and rendering the to-be-rendered game data according to the rendering function interface to generate a game interface for display. By adopting the embodiment of the invention, the safety of the game can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Smoke-cooker linked type air curtain extractor hood
InactiveCN110631076AReduce operational burdenIncrease authenticityDomestic stoves or rangesLighting and heating apparatusCookerSmoke
The invention discloses a smoke-cooker linked type air curtain extractor hood. The smoke-cooker linked type air curtain extractor hood comprises an air curtain device, a state obtaining device and a linking device, the air curtain device is used for forming an air curtain, the state obtaining device is used for obtaining the working state of the air curtain device, the working state of a cooker corresponding to the extractor hood, and the environment state around the extractor hood, and generating corresponding data, the linking device is connected with the air curtain device and the state obtaining device, and the working state of the air curtain device is adjusted according to the data obtained by the state obtaining device. According to the smoke-cooker linked type air curtain extractorhood, the linking device for controlling the air curtain device is additionally arranged, the working state of the air curtain device is controlled through the working state of the cooker within therange of a working area of the extractor hood, and the working state of the air curtain device is reasonably controlled.
Owner:QINGDAO HAIER WISDOM KITCHEN APPLIANCE CO LTD
Security management method for database information
InactiveCN103312518AEffectively hideEnsure safetyUser identity/authority verificationDigital data protectionInternet privacyEncryption
The invention relates to a security management method for database information, which aims to provide a method to realize effective management of security of the database information not only through user identity authentication, but also through information encryption and transcoding, prompt for dynamics of database information access and log recording. The method includes the steps of authenticating a user through a user platform, transcoding and encrypting the database information, prompting the dynamics of the database information access and recording the dynamics of the database information access.
Owner:NINGXIA XINHANG INFORMATION TECH
Transporting vehicle convenient to dismount
InactiveCN108715144AReduce the burden of feedingReduce frictionVehicle with rollersVehicle with loading rampBogieEngineering
The invention discloses a transporting vehicle convenient to dismount. The transporting vehicle comprises a first carrying plate, a second carrying plate, a steering frame, an unloading mechanism, a baffle frame, first rolling wheels and a second rolling wheel, wherein the first carrying plate and the second carrying plate are arranged side by side and are connected through a baffling frame; the steering frame is arranged on one side of the baffling frame and is fixedly connected with the baffling frame, the second rolling wheel is mounted at the bottom of the steering frame, and the first rolling wheels are respectively mounted at the bottoms of the first carrying plate and the second carrying plate; and the unloading mechanism is arranged on the inner side of the baffling frame and comprises a building plate, a hydraulic rod, a sliding chute plates and a pushing plate, the building plate is welded with the baffling frame, the sliding chute plate is connected to one side of the othersliding chute plate through screws, the hydraulic rod is fixedly mounted on the surface of the building plate, and a movable end of the hydraulic rod is fixedly connected with the pushing plate. Compared with an existing transporting vehicle convenient to mount and dismount, the transporting vehicle disclosed by the invention has the advantages that the constitution structure is simple, the operation is convenient, meanwhile, a mounting and dismounting mechanism can be folded, the labor can be effectively saved during the loading and unloading of the materials, the transporting vehicle is easyto popularize, and the like.
Owner:浙江杭力鼎盛机械有限公司
Counterweight arrangement structure in elevator traction system
PendingCN109665416ASmall form factorReduced size spaceElevatorsBuilding liftsTraction systemEngineering
The invention discloses a counterweight arrangement structure in an elevator traction system. The counterweight arrangement structure comprises an elevator car, a mounting platform and shaftway vertical columns which are arranged at four corners of the mounting platform, a traction machine and a traction wheel connected with the traction machine are arranged on the mounting platform, a first traction rope and a second traction rope are wound around the traction wheel, one end of the first traction rope is connected with the top of the elevator car, the other end of the first traction rope is connected with a first counterweight which is slidably arranged in the first shaftway vertical column, one end of the second traction rope is connected with the top of the elevator car, the other end of the second traction rope is connected with a second counterweight which is slidably arranged in the other shaftway vertical column, the first counterweight and the second counterweight are located on the two sides of the traction wheel correspondingly, and the four corners of the elevator car are in sliding connection with the corresponding shaftway vertical columns correspondingly. According tothe counterweight arrangement structure, multi-direction free setting of an elevator car door is facilitated, meanwhile, the overall impression of an all-transparent sightseeing elevator and a household elevator can be remarkably improved, and the safety of the elevator can be improved.
Owner:SHAANXI SIUSAI ELECTROMECHANICAL TECH CO LTD
Industrial internet terminal general security service system based on IBE
PendingCN112787806AReduce computing pressureGuaranteed normal transmissionKey distribution for secure communicationUser identity/authority verificationIndustrial InternetCommunications protocol
The invention discloses an IBE-based universal security service system for an industrial internet terminal. The system comprises an industrial internet terminal equipment layer, an access gateway layer and a management and control service layer; the industrial internet terminal equipment layer is used for transmitting the collected industrial data to a TCP port of the access gateway layer in an unvarnished manner; the access gateway layer is an industrial internet gateway, establishes mapping with an equipment management module according to configuration information such as a communication protocol of the terminal equipment layer, and initiates an IBE-XKMS service request to realize identity authentication access; and the management and control service layer is used for responding to a gateway equipment request through an IBE-XKMS module, completing gateway layer equipment authentication service, completing a user authority control module through key management, responding to a user data request, and completing real-time data acquisition and equipment management and control of terminal equipment accessed to the gateway through an HTTP API (Hyper Text Transport Protocol Application Program Interface). According to the invention, complex encryption and decryption operations are handed over to the gateway agent and IBE-XKMS service, so the computing pressure of the resource-limited terminal equipment is greatly reduced.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com