Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
105results about How to "Implement virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Cloud computing system, cloud computing method and cloud
ActiveCN102546735AAchieve integrationImplement virtualizationTransmissionVirtualizationComputing systems
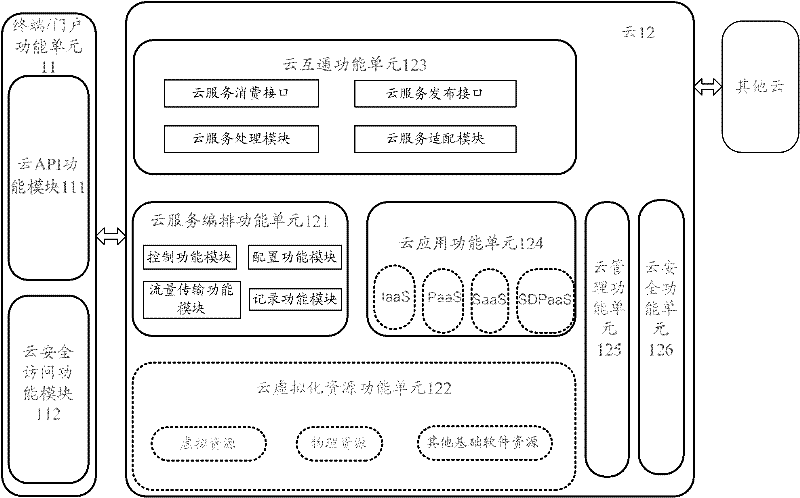
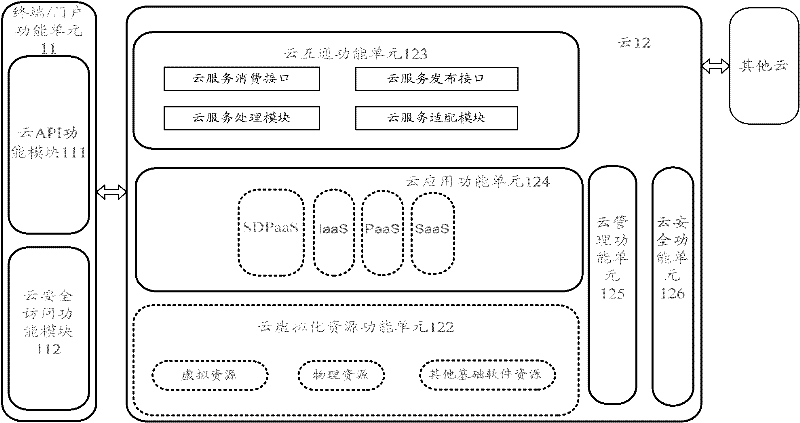
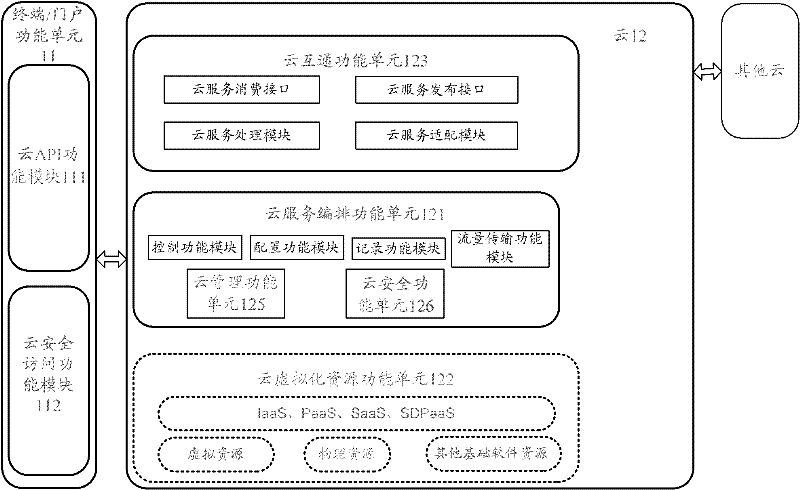
The invention discloses a cloud computing system. A terminal and / or a door function unit build / builds a safety mechanism with cloud and send / sends cloud service request to the cloud. After the cloud receives the cloud service request, other cloud is accessed by the cloud itself and / or through a cloud interworking function, cloud computing resource is arranged, and cloud service is provided for the terminal and / or the door function unit. The invention further discloses a cloud computing method and the cloud. By means of the technical scheme, integration, virtualization and automation of the cloud computing system can be achieved, the cloud can coordinate uniformly and arrange the cloud computing resource automatically, efficiency is improved, and defect that the existing cloud computing system can not arrange the cloud computing resource automatically is overcome.
Owner:ZTE CORP
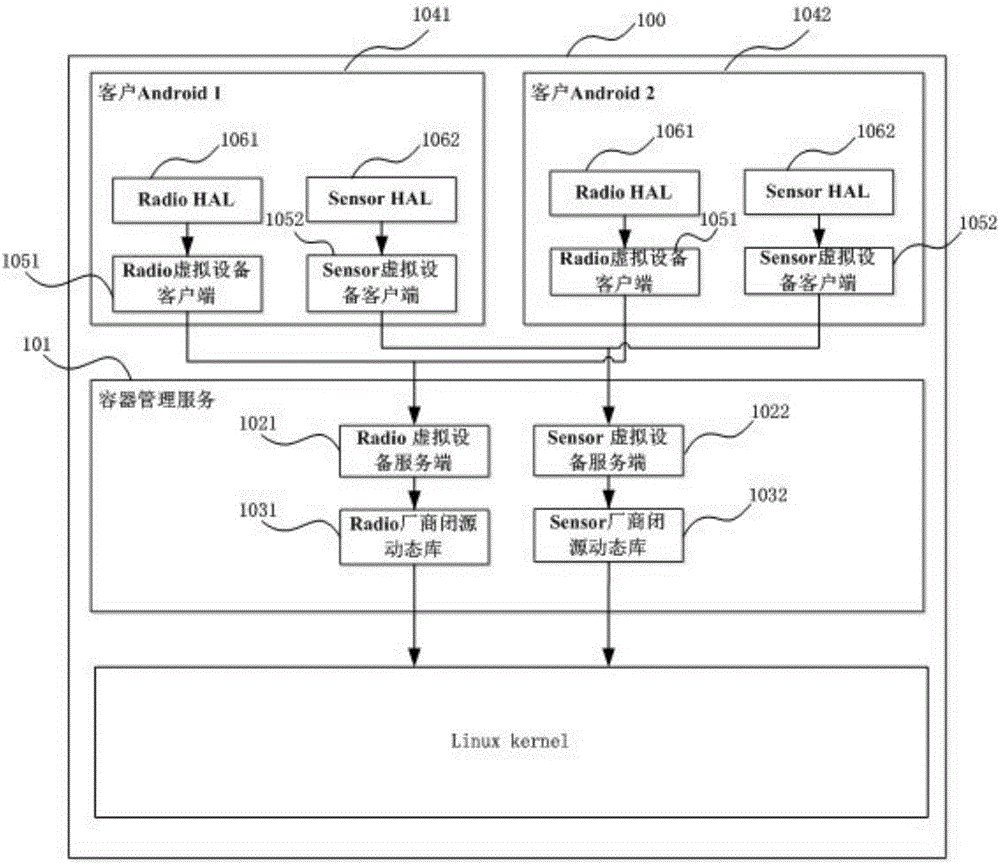
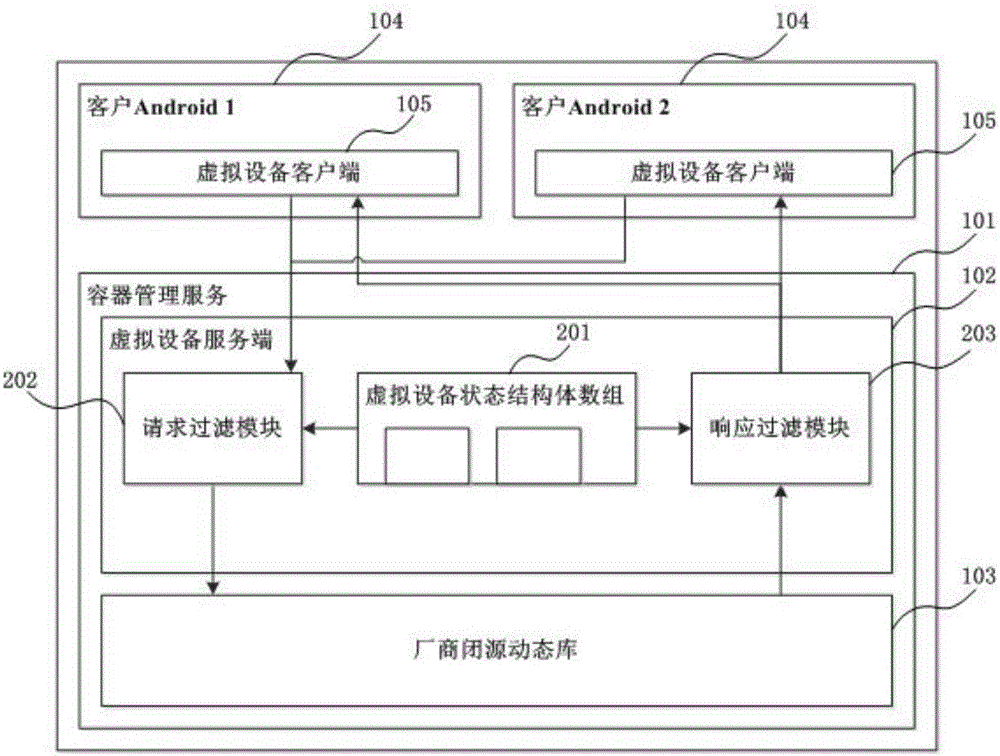
Device virtualization system and method based on Linux containers
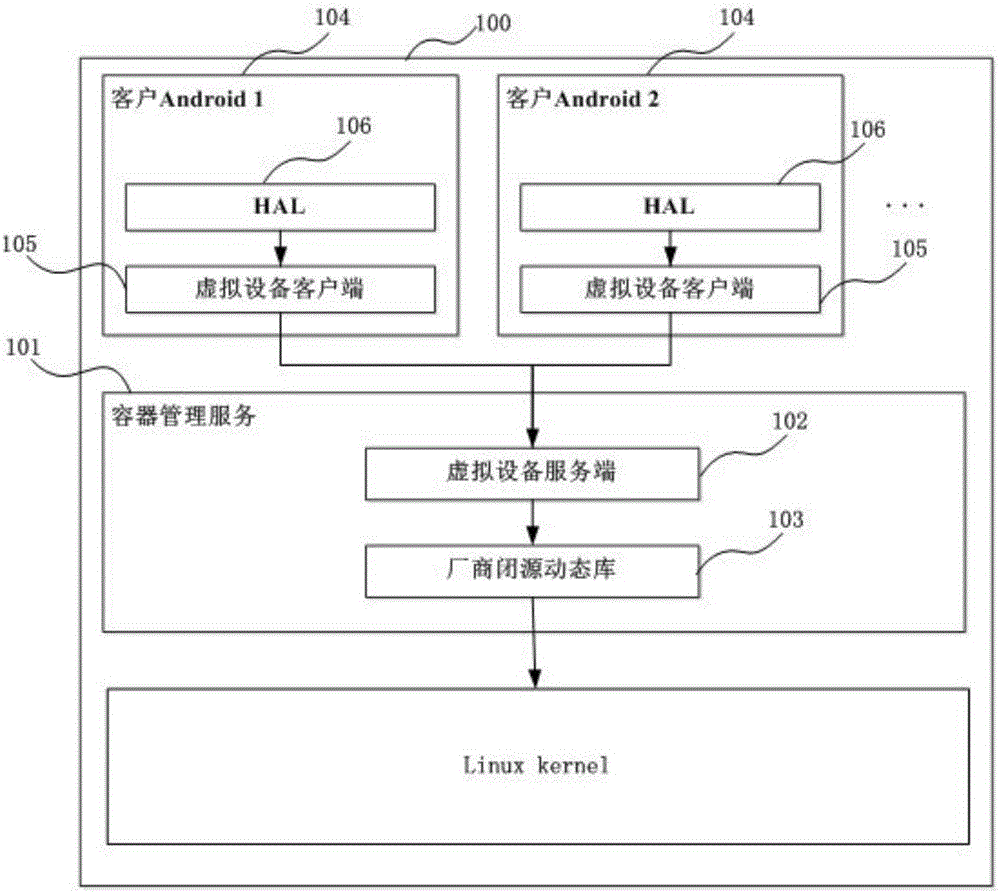
ActiveCN105808320ARealize multiplexingAvoid cumbersomeSoftware simulation/interpretation/emulationGNU/LinuxOpen source
The invention provides a device virtualization system and method based on Linux containers. Virtual device clients and a virtual device server are loaded between Android system HALs and a device subsystem; device operation requests are sent to the virtual device server through the virtual device clients; and then the virtual device server finishes function call in a manufacturer dynamic library, thus realizing agency for the device operations, or constructs device operation results, thus realizing reuse of the device subsystem. According to the device virtualization system and method provided by the invention, through loading the virtual device clients and the virtual device server in multiple Android systems and container management service in a Linux kernel, the agency for the device operations and the reuse of the device subsystem are finished, thus realizing virtualization of the device; a new method different from a traditional device virtualization method is provided; and the reuse of special devices (especially devices without open source code) such as Radios is realized in the multi-Android platform based on a Linux container technique.
Owner:杨霞
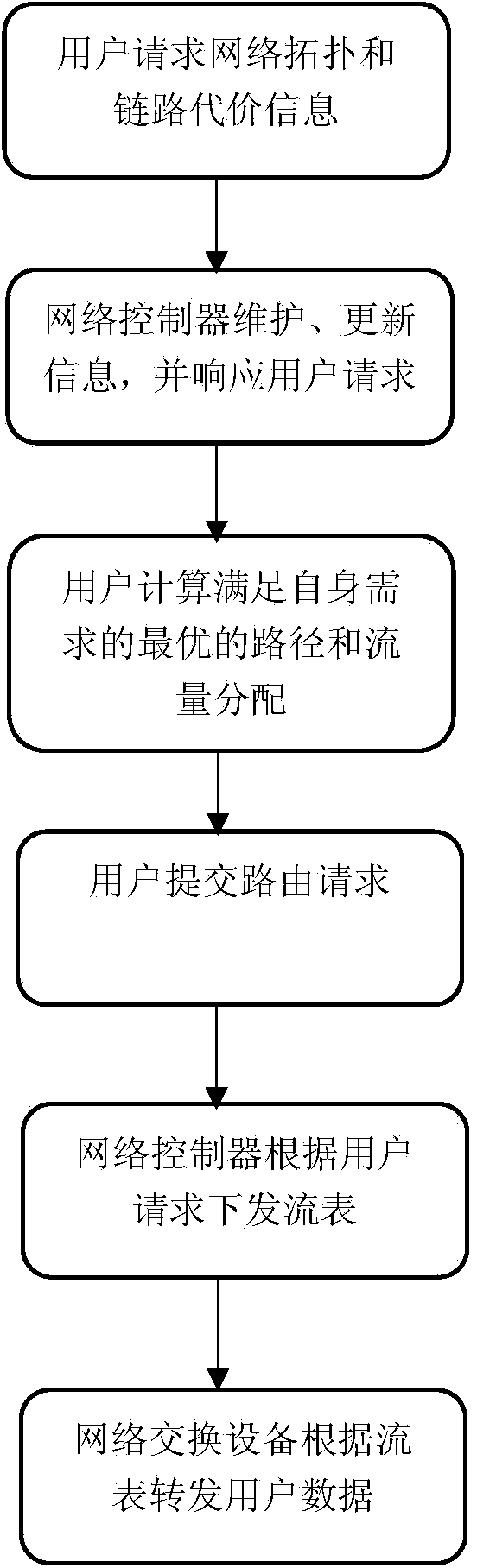
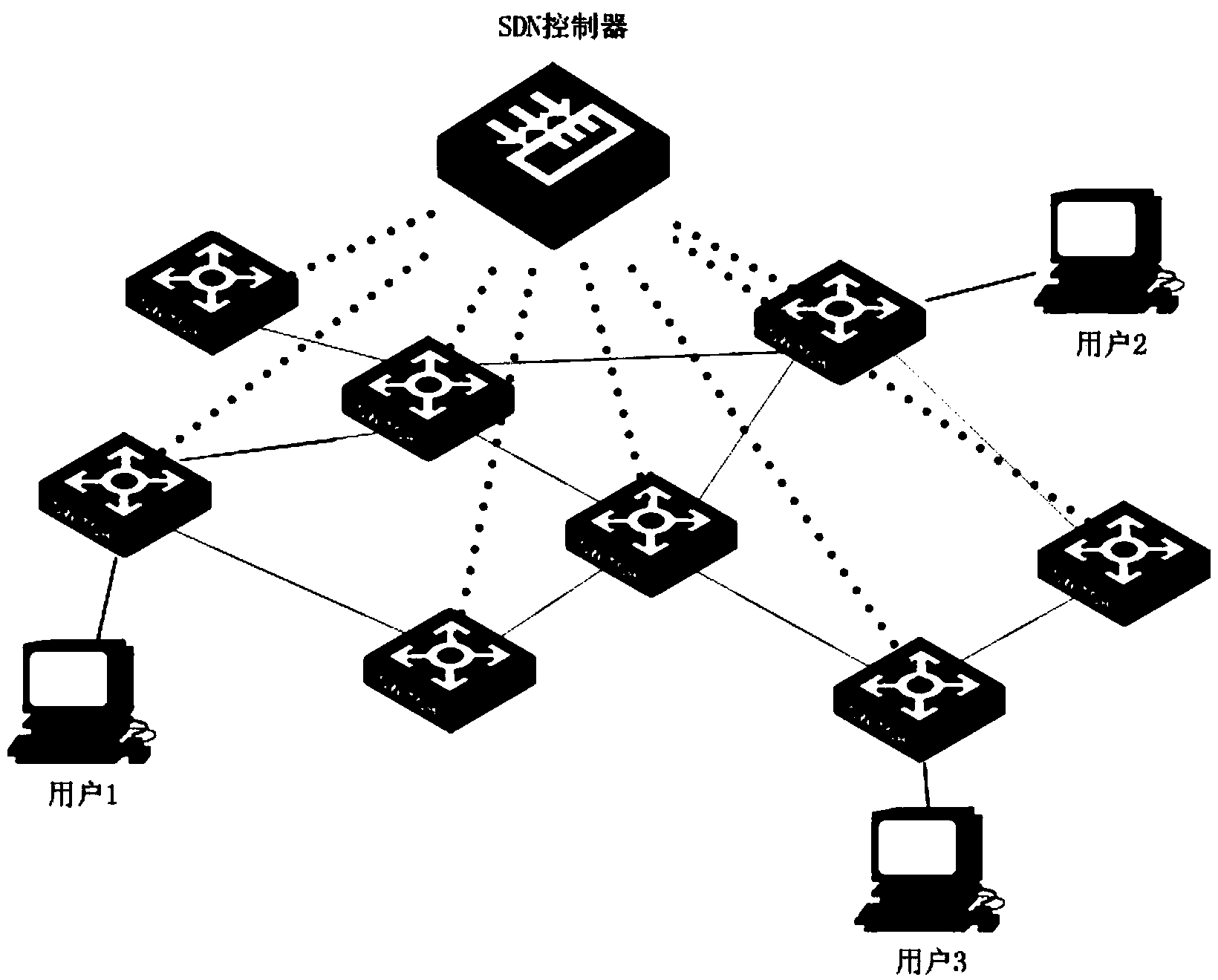
Client distributed path computation method based on software defined network architecture
ActiveCN104253749AChange limitationsHigh transparencyData switching networksPath computation elementNetwork architecture
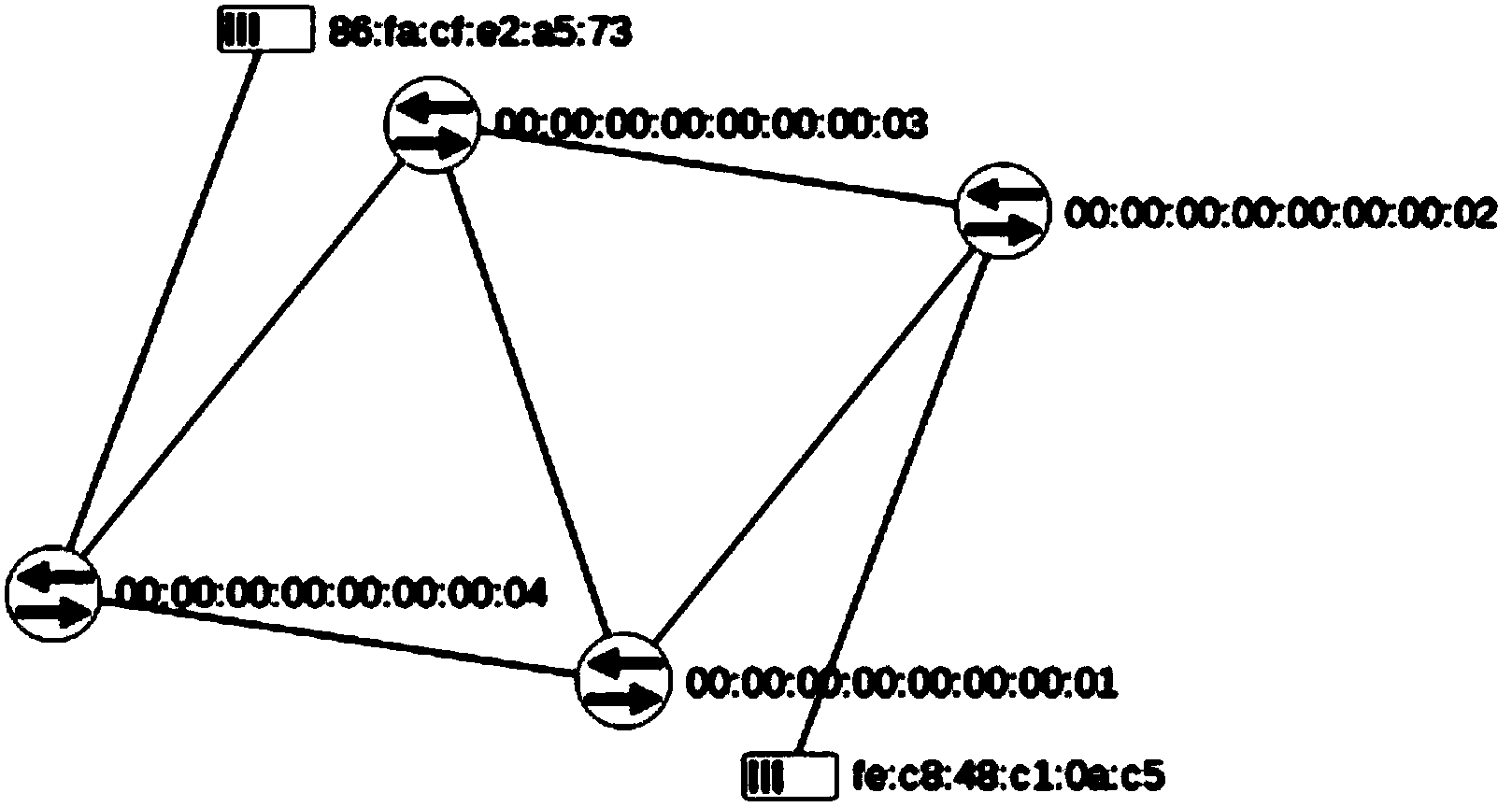
The invention discloses a client distributed path computation method based on a software defined network architecture. The client distributed path computation method comprises the following steps: a user obtains network topology and linkcost information from a network controller through a northbound interface of a controller, calculates the path on the basis, determines route and flow distribution, and submits a route request to the controller; the network controller is responsible for updating the network topology and link state, and issuing a flow statement to data forwarding equipment according to the route selection of the user. Through the route calculation, the user participates in the network control to achieve the distributed optimization during the use process of network resources; meanwhile, the controller provides network topology information for the user, and can achieve the virtualization of the network resources and functions for the user and the optimal configuration and the integrated use of the network resources. Through the application of the method, the user can get great rights within a network safety range, the network transparency is improved, and an SDN frame serves for the user.
Owner:SOUTH CHINA UNIV OF TECH
Multiple-path multiple-core server and its CPU virtualization processing method
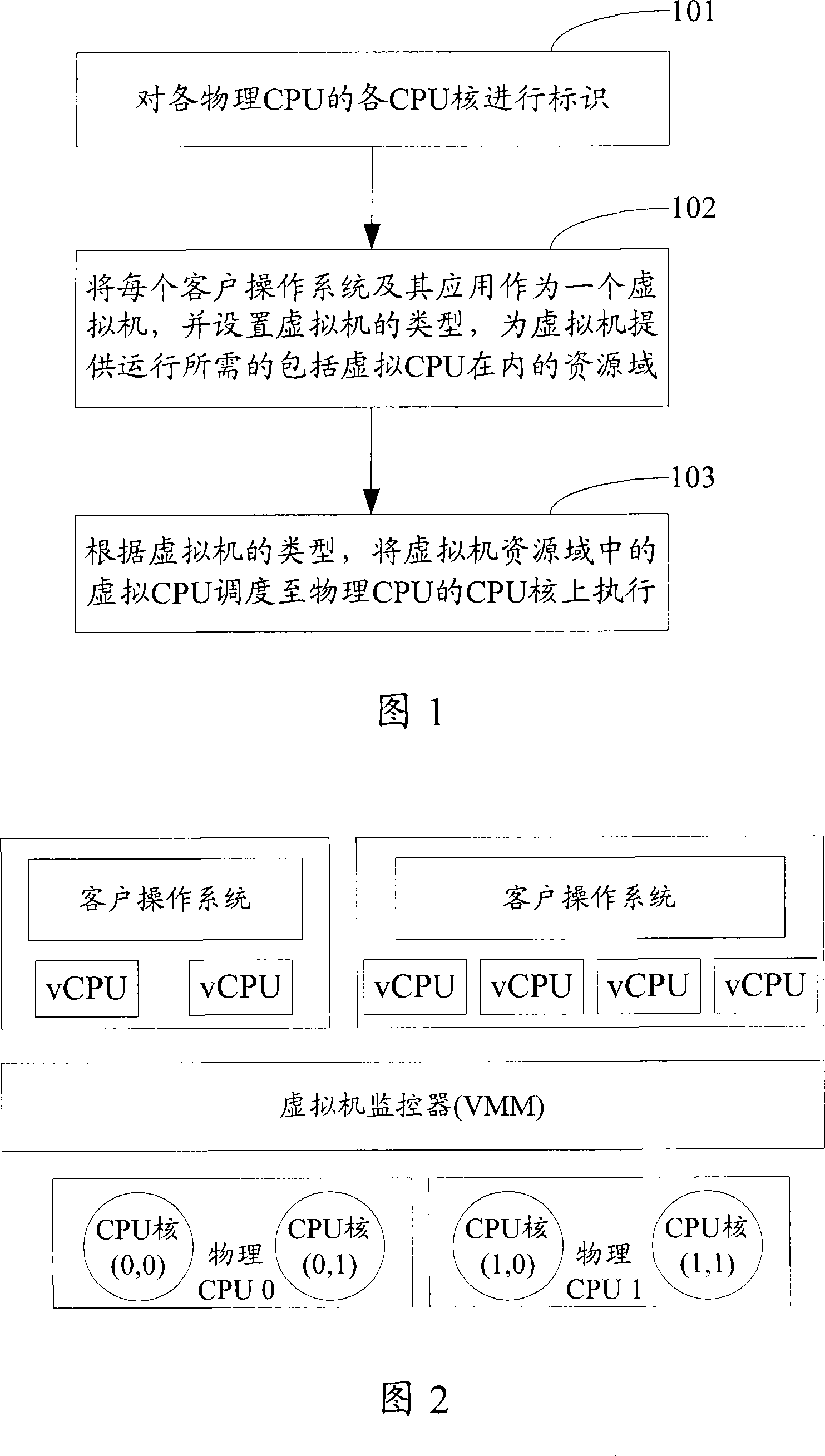
ActiveCN101169731AImplement virtualizationImprove performanceMultiprogramming arrangementsSoftware simulation/interpretation/emulationVirtualizationOperational system
The invention discloses a CPU virtualization method for a multiplex and multi-core server, which comprises using each customer operating system and application thereof as a virtual machine, setting the type of the virtual machine, and providing the virtual machine with the required resource domain including virtual CPU; and scheduling the virtual CPU in the resource domain of the virtual machine to a CPU core on a physical CPU to implement according to the type of the virtual machine. In addition, the invention also discloses a multiplex and multi-core server. The technical proposal disclosed in the invention can realize virtualization of the multiplex and multi-core server, and realize the performance and the efficiency by using the virtualization technique and the relations among the virtualization hardware, the physical hardware and the operating system.
Owner:XFUSION DIGITAL TECH CO LTD
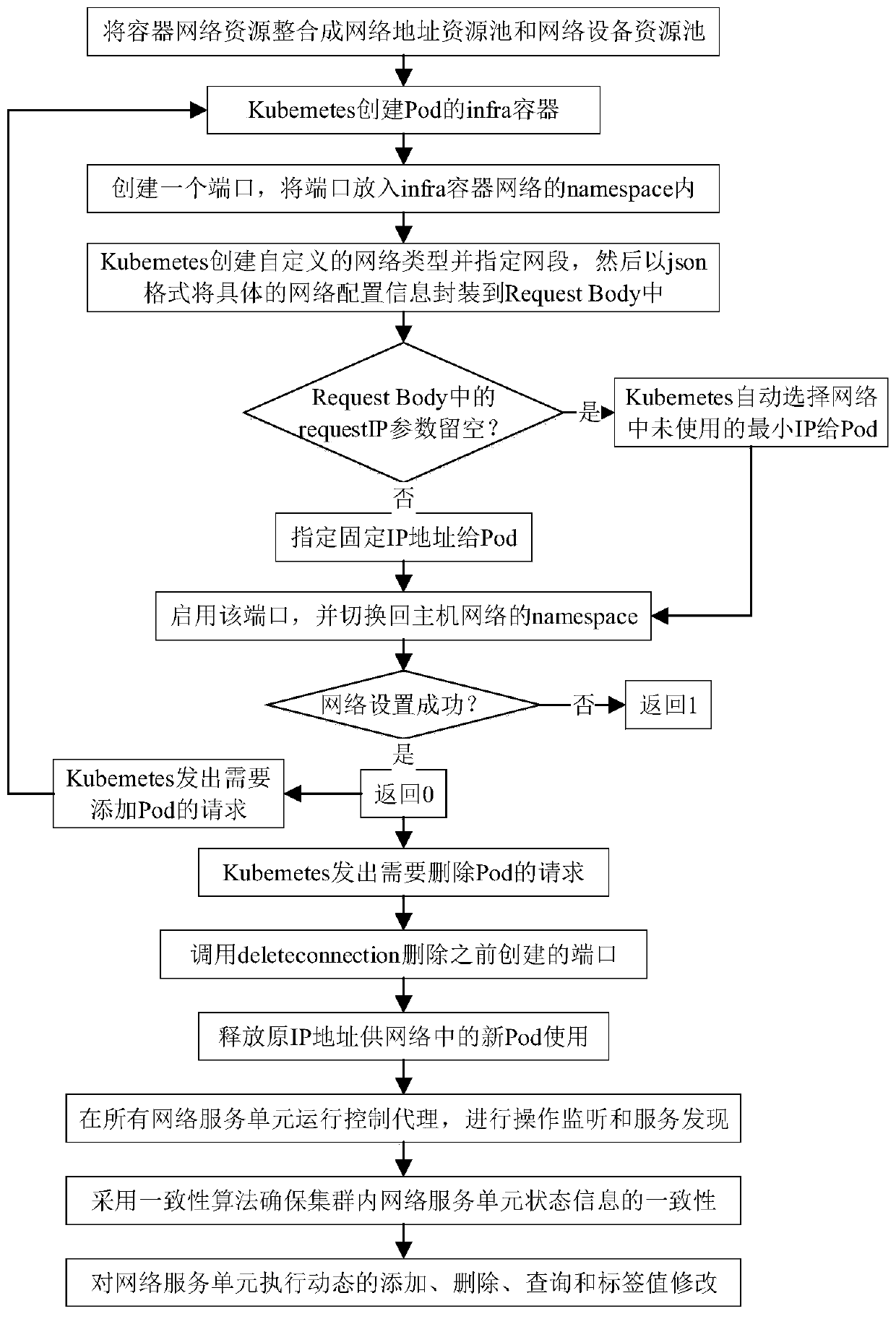
An SDN-based container network resource scheduling method
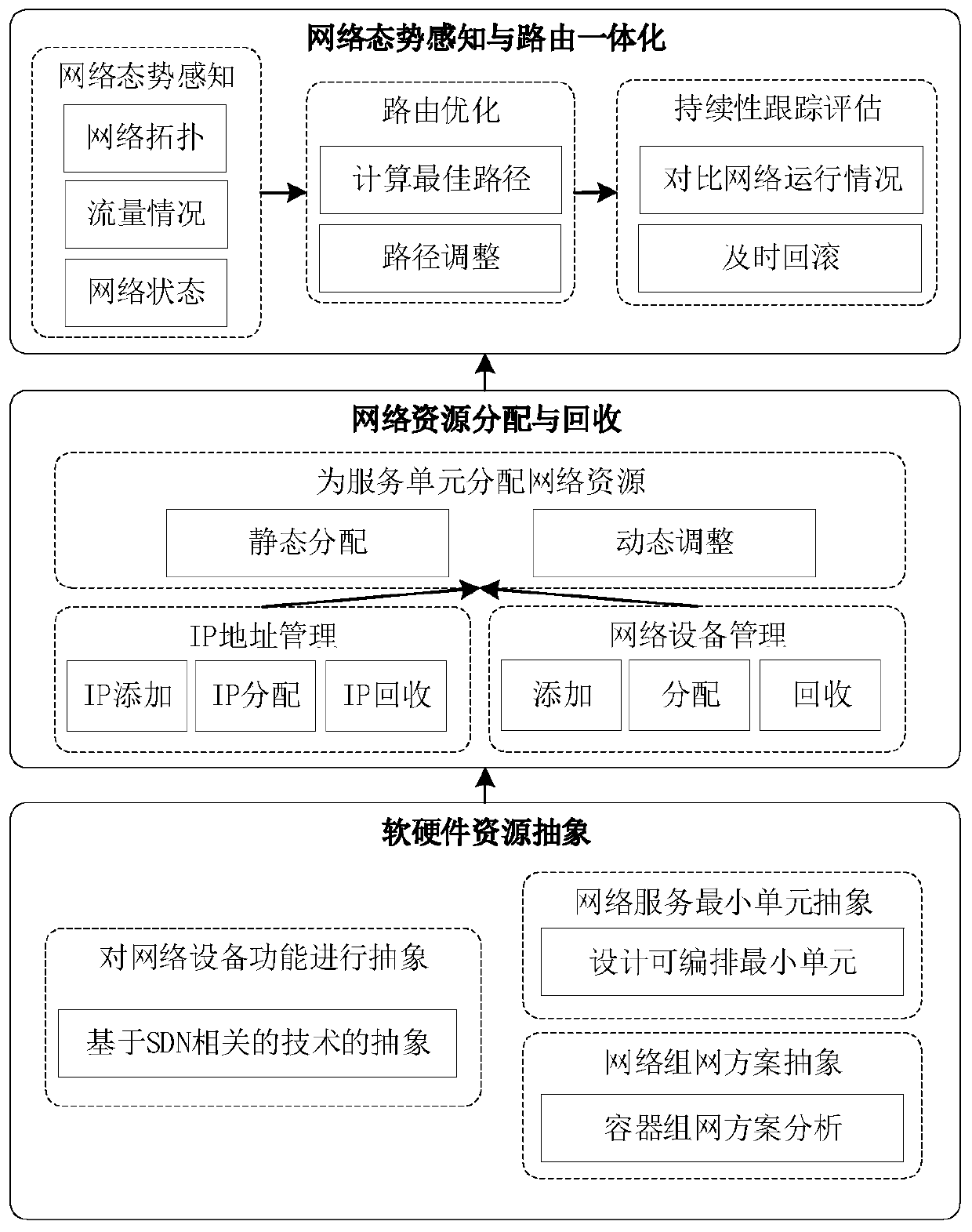
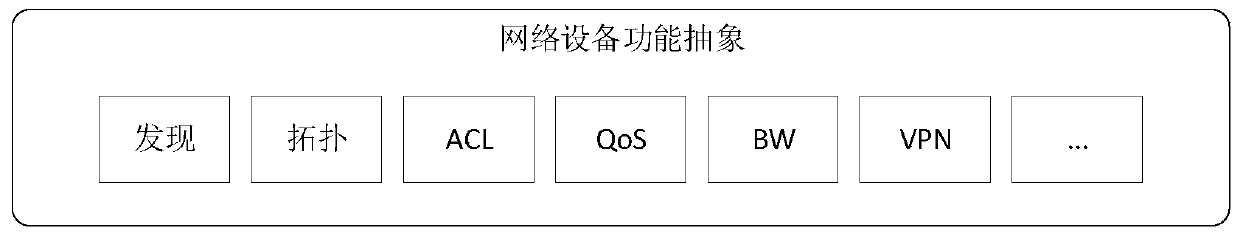
ActiveCN109743261AFully flexible sharingFlexible sharingData switching networksResource poolNetwork address
Aiming at the problem that resource segmentation and guarantee cannot be carried out according to requirements of a container network in the prior art, the invention provides an SDN-based container network resource scheduling method, which comprises the following steps of: 1, carrying out unified abstraction and description on network software and hardware resources based on an SDN / NFV technology;2, implementing resource allocation and recovery on the container network, integrating resources into a resource pool, establishing and managing a network address resource pool and a network equipment resource pool, providing network equipment resources as required, and recovering the network equipment resources in time when the network is destroyed; And step 3, based on the idea of SDN centralized control, deploying a centralized control server in the container network, and implementing network situation awareness and routing integration. The container network resource scheduling method integrates networking, routing and monitoring by intensively sensing the network situation and reasonably segmenting and recovering the container network resources in combination with the requirements oftasks, thereby realizing the optimal scheduling of the container network resources.
Owner:NAT UNIV OF DEFENSE TECH
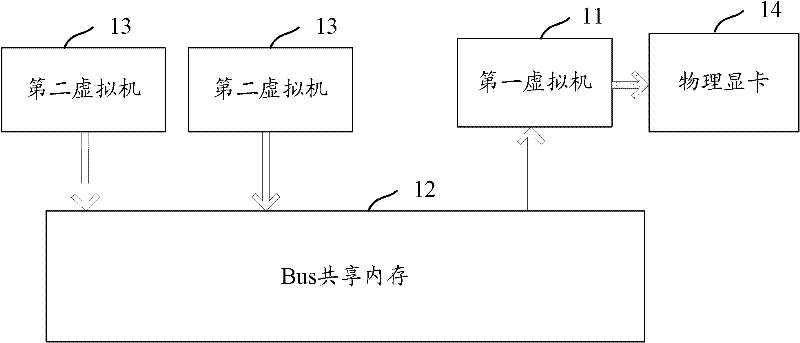
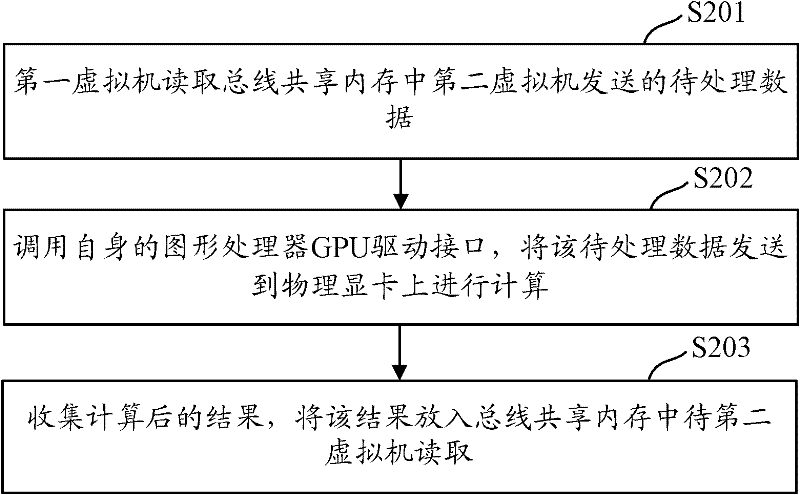
Implementation method, system and device for virtualization of universal graphic processor
ActiveCN102541618AImplement virtualizationProcessor architectures/configurationSoftware simulation/interpretation/emulationGeneral purposeGraphics
The invention discloses an implementation method, system and device for the virtualization of a GPGPU (General Purpose Graphics Processing Unit) to solve the problem that the virtualization of the GPGPU cannot be solved in the prior art. The implementation method comprises the following steps: a first virtual machine reads data to be processed in a shared memory of a bus, wherein the data to be processed is written by a second virtual machine; and the first virtual machine invokes a CPU (Central Processing Unit) driver interface, sends the data to be processed to a physical display card for calculation, collects calculated results, and inputs the results in the shared memory of the bus to be read by the second virtual machine. As the first virtual machine can visit the physical display card, and can realize information interaction with the second virtual machine, the virtualization of the GPGPU is realized.
Owner:CHINA MOBILE COMM GRP CO LTD
Virtualization method and device for accelerator and centralized resource manager
ActiveCN105159753AImplement virtualizationVirtualization is easyResource allocationSoftware simulation/interpretation/emulationResource poolVirtualization
The embodiment of the present invention discloses a virtualization method and device for an accelerator and a centralized resource manager. The method comprises: selecting a matched physical accelerator from a physical accelerator resource pool as a matched physical accelerator by the centralized source manager in accordance with virtual accelerator information to be created in a resource allocation command of a virtual machine; transmitting a first virtual machine creating command to a monitor of the virtual machine by the centralized source manager so that the monitor of the virtual machine creates a first virtual machine including a first virtual accelerator corresponding to the matched physical accelerator, or transmitting a second virtual machine creating command to the monitor of the virtual machine by the centralized resource manager, wherein the second virtual machine creating command comprises a description information acquisition identifier to make the monitor of the virtual machine create a second virtual machine after receiving the second virtual machine creating command, and make the second virtual machine generate a second virtual accelerator after acquiring a description information according to the description information acquisition identifier. The method of the present invention can realize the virtualization of the accelerator.
Owner:HUAWEI TECH CO LTD
GPU resource-based data processing method and system, and electronic equipment
ActiveCN110764901AGood abstractionEasy to packResource allocationSoftware simulation/interpretation/emulationParallel computingEngineering
The invention discloses a GPU resource-based data processing method and system, and electronic equipment. The GPU resource-based data processing method comprises the steps of creating N virtual GPU resources according to a resource configuration strategy and physical GPU resources; generating a resource mapping relationship between the physical GPU resources and the virtual GPU resources accordingto a resource configuration strategy; and enabling each resource application module to obtain a target virtual GPU resource in the N virtual GPU resources according to the resource mapping relationship.
Owner:ADVANCED NEW TECH CO LTD
File redirection technology based virtualized security desktop
InactiveCN104318179AOperational securityEasy to operate and controlDigital data protectionPlatform integrity maintainanceVirtualizationFile system
The invention discloses a file redirection technology based virtualized security desktop. Validity in using the security desktop is guaranteed through a login control module; operation behavior results of users can be reliably protected by an encrypted virtual storage file system; the operation behavior results of the users in the virtualized security desktop are 'internally' redirected to the encrypted virtual storage file system through a user operation middle layer and the whole redirection process is encrypted and monitored under a communication encryption module and a black and white list control module. The virtualized security desktop system is 'totally separated' from an original desktop, operations of adhering, copying, shifting and the like of the files cannot be performed between the virtualized security desktop system and the original desktop; the files on an original desktop system are mapped to the same catalog on the virtualized desktop; results (files, register lists, temporary cache and the like) generated from operation of the users in the virtualized desktop are encrypted for redirection treatment, and all the operations in the virtualized desktop are guaranteed to be safe, reliable and controllable.
Owner:中电科网络安全科技股份有限公司
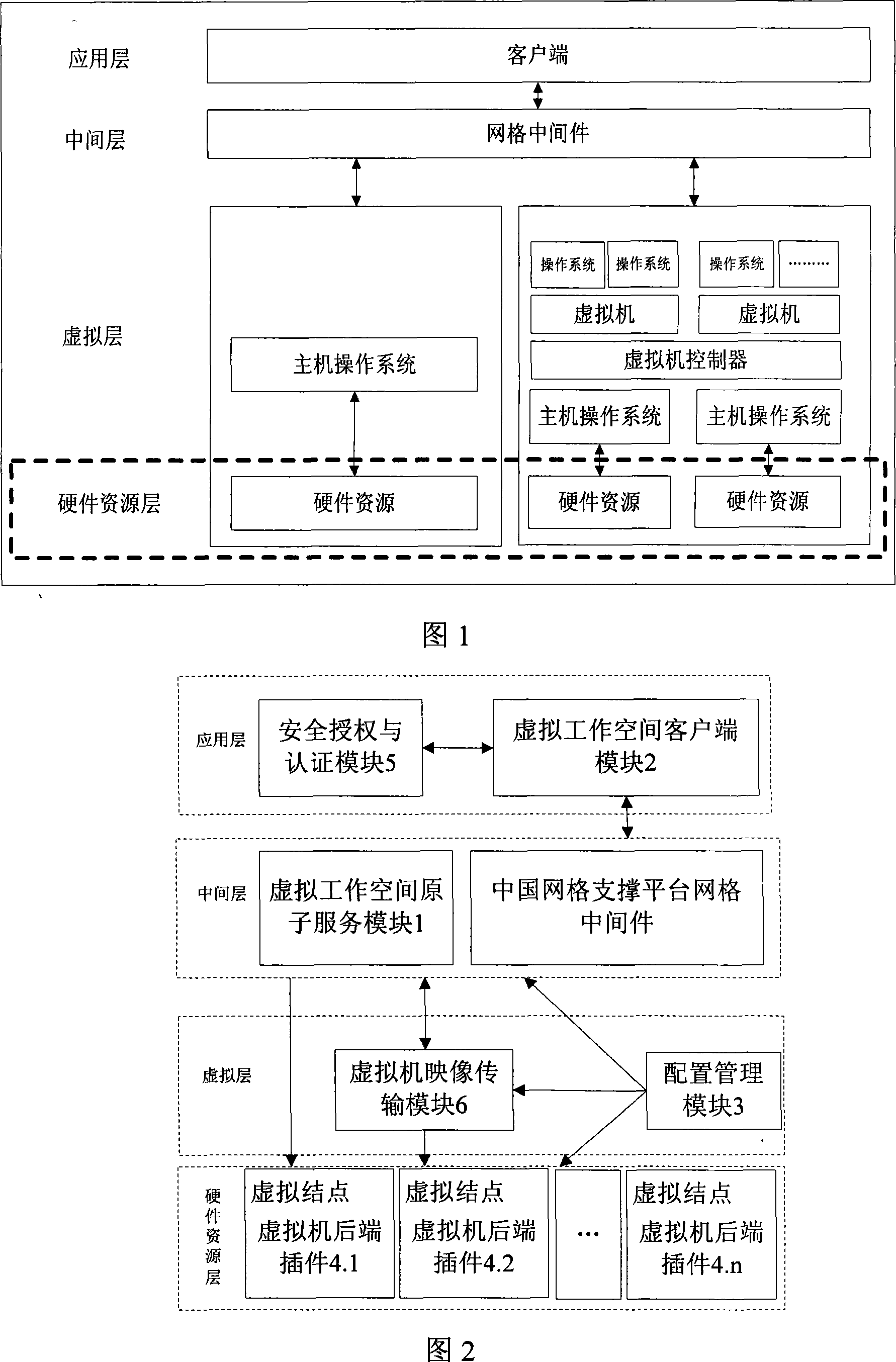
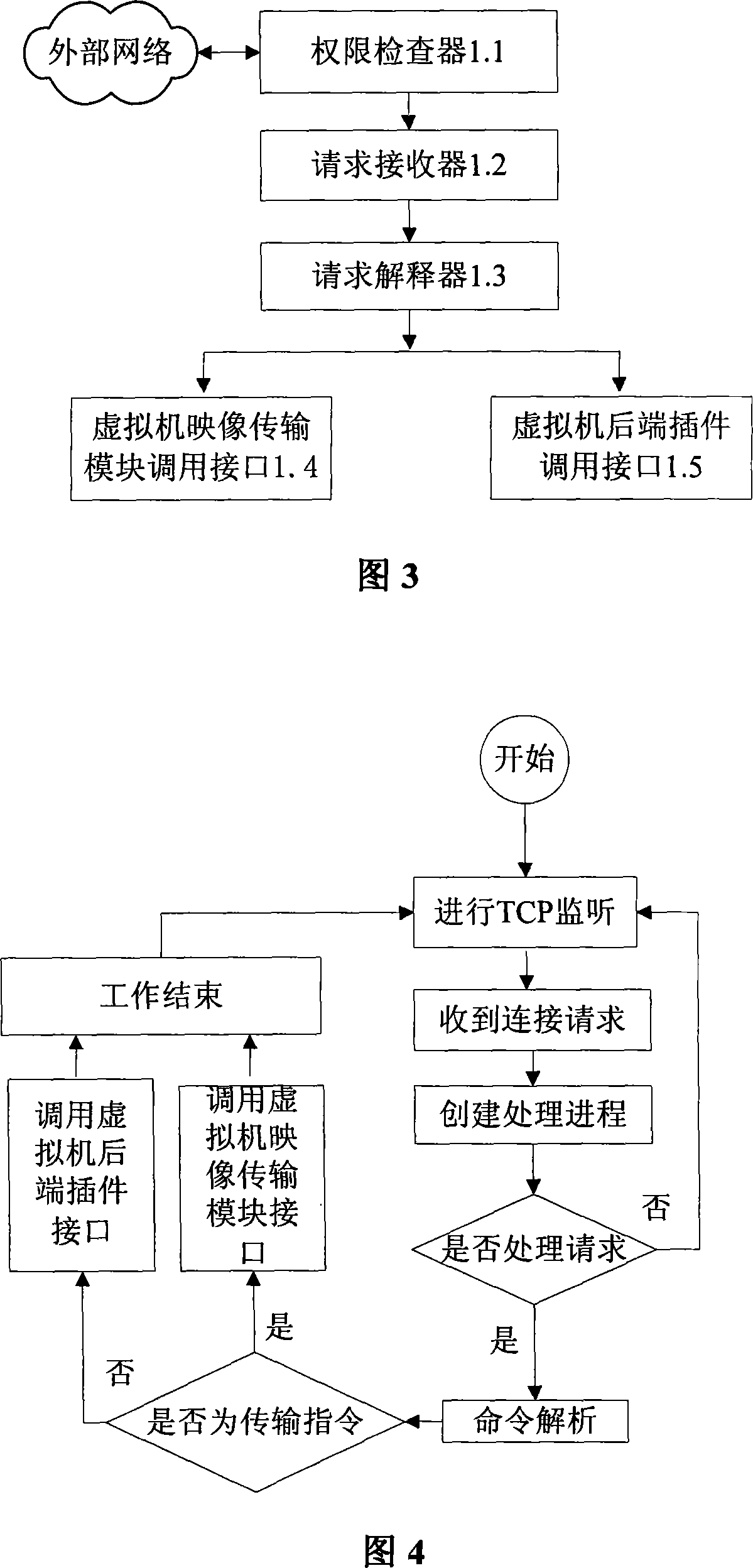
Grid middleware system based on virtual machine
InactiveCN101188624AImplement virtualizationIncrease flexibilityTransmissionSoftware simulation/interpretation/emulationMiddlewareVirtual machine
The invention discloses a graticule middle part system based on a virtual machine, which comprises safe authorization positioned in an application layer, a certification module and a virtual operating space client-side module, a virtual operating space atom service module positioned in a middle layer, a virtual machine mapping transmission module and configuration management module positioned in a virtual layer, and a plug-in package at the rear end of the virtual machine in each virtual node of a hardware resource layer. The invention not only realizes the virtualization of a great deal of deconcentrated resource, but also realizes the virtualization to a single system. The utility model utilizes the virtual machine to well overcome the defects in the prior graticule computing technology that the flexibility is not high, the efficiency is not high, and the secure is not high, but also effectively supports the transition of running environment and an application program under the graticule environment, and also supports the original network computation model.
Owner:HUAZHONG UNIV OF SCI & TECH
System and method for multi-tenant network stability monitoring based on cloud platform
ActiveCN107370642AImplement virtualizationGuaranteed stabilityData switching networksNetwork connectionResource virtualization
The invention discloses a system and a method for multi-tenant network stability monitoring based on a cloud platform. The system and the method ensure stability of an IPv4 network and an IPv6 network in a virtual machine. The method comprises: S1, establishing an OpenStack cloud platform; S2, integrating an SDN with the OpenStack cloud platform Neutron, to realize network resource virtualization; S3, acquiring IPv4 and IPv6 data, and converting the IPv6 data to IPv4 data through IVI; S4, through a Panabit device, identifying and monitoring and counting the IPv4 and IPv6 network data, and combined with a SDN controller of the SDN device, performing QOS regulation. The system and the method can solve problems of cloud platform multi-tenant network stability monitoring, ensure stability of the IPv4 network and the IPv6 network in the virtual machine, optimize network connection speed, improve network service quality monitoring, and improve network QOS and user experience.
Owner:CERNET CORP
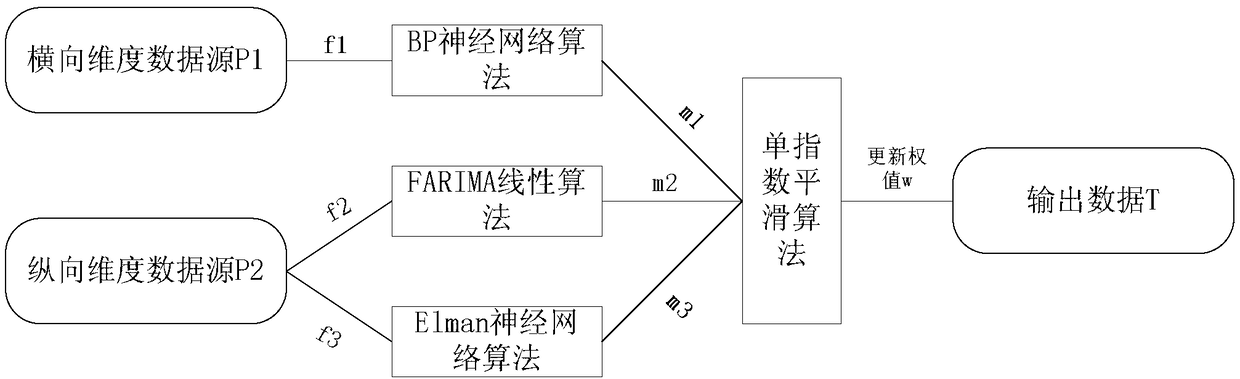
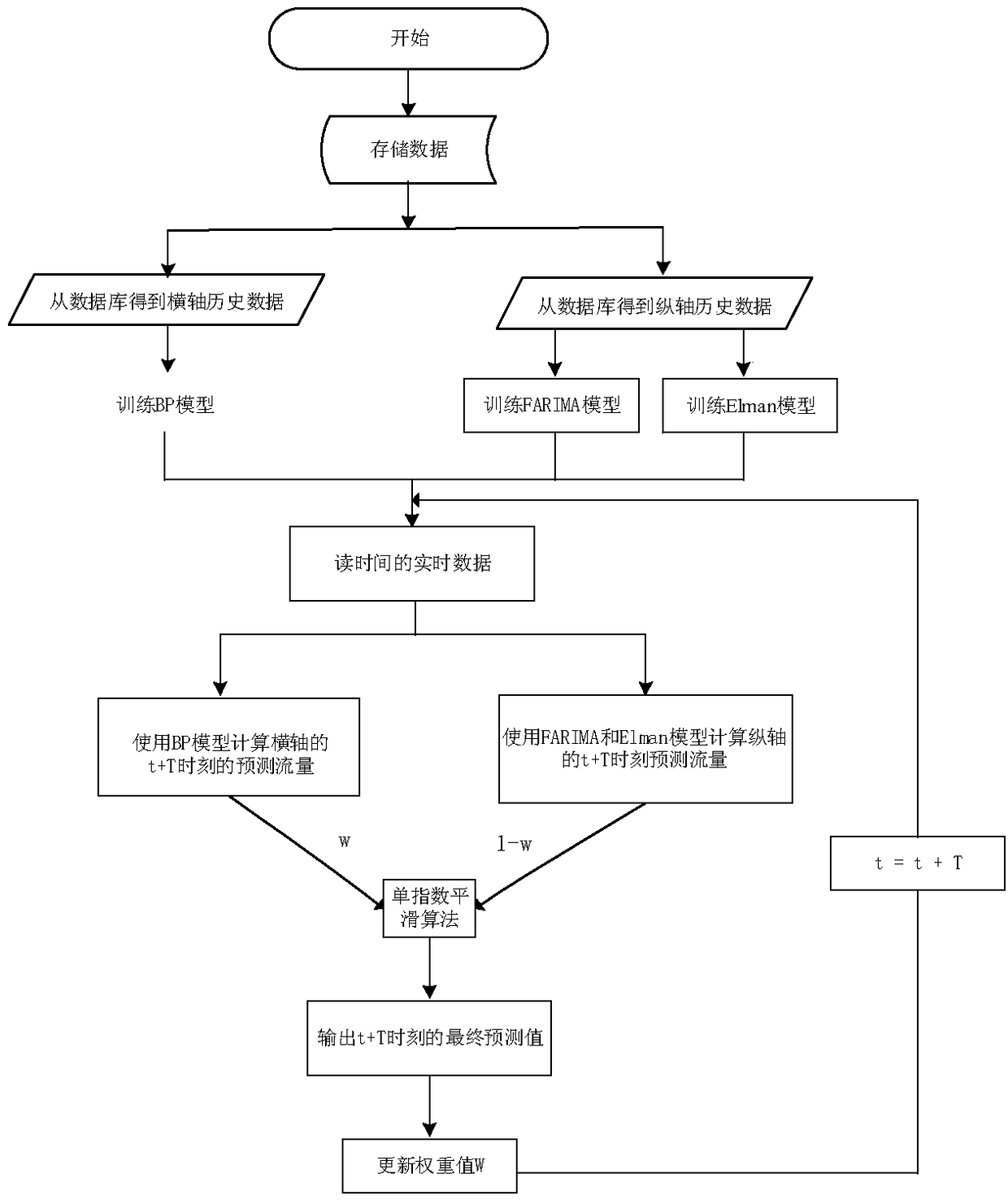
Multi-dimensional power communication network flow prediction method and system
PendingCN108199928AEasy to shareImprove collaborationData switching networksData acquisitionExponential smoothing
The invention discloses a multi-dimensional power communication network flow prediction method and system; the method comprises the following steps: step 1, network flow is collected; step 2, a multi-dimensional flow prediction method is carried out; step 3, a dynamic weight updating strategy is introduced into a single exponential smoothing algorithm; the system comprises application layer equipment, an interface module, an SDN controller, an SDN coordinator, an SDN device, an OTN device and an EOPN device. The method and the system have the advantages that a cloud service technology is introduced in the adopted data measurement method; an SDN technology is introduced into a data acquisition part; the collected transverse dimension data are trained through a BP neural network algorithm; and an algorithm combined with an FARIMA algorithm and an ELman algorithm is adopted for the collected longitudinal dimension data. The precision of the prediction algorithm is improved; and the singleexponential smoothing algorithm is adopted to update the weight output by the multi-dimensional prediction algorithm, so that the fluctuation dimension of errors is reduced.
Owner:STATE GRID HUBEI ELECTRIC POWER COMPANY INFORMATION & TELECOMM +2
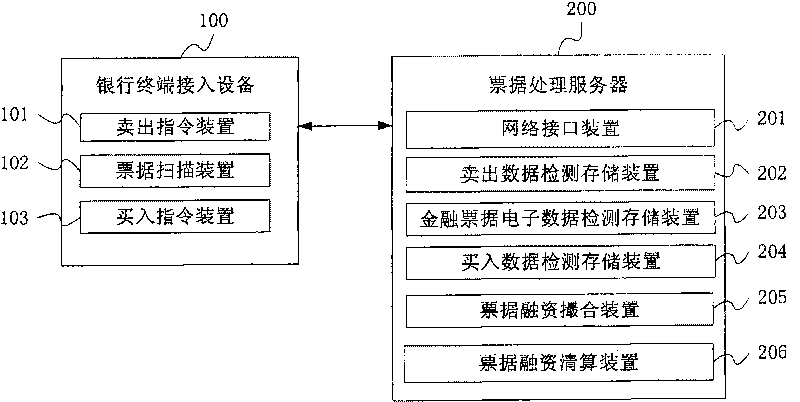
Device and method for realizing electronic trade of financial instruments
InactiveCN101763619ARealize electronicImplement virtualizationFinanceNetwork interface deviceElectronic data
The invention provides a device and a method for realizing electronic trade of financial instruments. The device comprises bank terminal access equipment and an instrument processing server; the bank terminal access equipment is used for inputting financial instrument financing-selling application data and scanning the financial instruments; the instrument processing server is used for receiving financial instrument financing-selling application data, financial instrument financing-buying application data and financial instrument electronic data, detecting and storing the received financial instrument financing-selling application data, financial instrument electronic data and the financial instrument financing-buying application data, and according to the financial instrument financing-buying application data and the financial instrument financing-selling application data, completing an instrument financing match and fund clearing to generate fund clearing result information; and the bank terminal access equipment is connected with the instrument processing server by a financial network, and the instrument processing server feeds the fund clearing result information back to the bank terminal access equipment through a network interface device. The device aims to solve the problem of electric treatment of the paper instruments.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Hardware counter virtualization-based performance analysis method for multiple virtual machines
InactiveCN102073535AImplement virtualizationEasy to analyzeSoftware testing/debuggingSoftware simulation/interpretation/emulationVirtualizationMessage passing
The invention discloses a hardware counter virtualization-based performance analysis method for multiple virtual machines. The method comprises the following steps of: when performance analysis is performed on multiple virtual machines at the same time and the multiple virtual machines need to occupy hardware counters, if the total number of central processing unit (CPU) events analyzed by multiple virtual machines surpasses the number of the hardware counters, virtualizing the hardware counters so as to meet requirements, otherwise, not virtualizing the hardware counters; and acquiring sampling information on the manager layer of an Xen virtual machine through a sampling mechanism, distributing the information to buffer zones which correspond to the virtual machines and analyzing and processing the information by using user layer programs of the virtual machines so as to obtain corresponding analysis result and detailed performance information. A request, which is used for starting or stopping performance analysis, of each virtual machine is monitored by a background daemon, Xenstore is taken as a message sending mechanism among the virtual machines, virtualization of the hardware counters is realized by time-sharing multiplexing technology, convenience is brought to program performance analysis in a virtual environment, and analysis accuracy is ensured well.
Owner:HUAZHONG UNIV OF SCI & TECH
Intelligent traffic system
InactiveCN103854473AAchieve sharingImplement virtualizationRoad vehicles traffic controlInter layerSoftware system
The invention discloses a bran-new intelligent traffic system which is never mentioned. The system comprises a sensing layer component, a middle part, a service layer component and an application layer component. The sensing layer component is connected with the service layer component through the middle part, the application layer component is connected with the service layer component, the sensing layer component is used for collecting various kinds of information relevant to traffic, the information relevant to the traffic comprises at least one of personal information, vehicle information, road information, environment information and traffic information, the middle layer component is used for being connected with all software systems of the sensing layer component and the service layer component, the service layer component is used for managing information collected by the sensing layer component, and conducts operation processing on the information collected by the sensing layer component, and the application layer component is used for conducting operation processing on the information collected by the sensing layer component based on the service layer component and provides corresponding application services for different traffic service objects.
Owner:CHINA MERCHANTS CHONGQING COMM RES & DESIGN INST
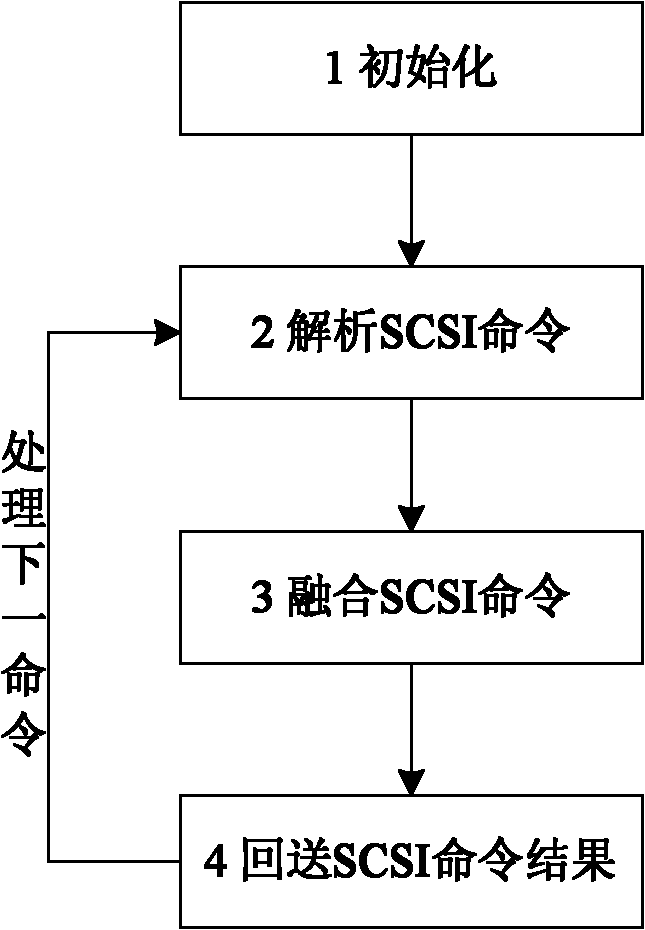
Convergence method of iSCSI (Internet Small Computer System Interface) and FCP (Fiber Channel Protocol) and application thereof to disaster recovery
InactiveCN101938523AImplement virtualizationIncrease flexibilityTransmissionRedundant operation error correctionFiberExtensibility
The invention relates to a convergence method of an iSCSI (Internet Small Computer System Interface) and an FCP (Fiber Channel Protocol). The method realizes the convergence of the iSCSI and the FCP through a convergence storage module and comprises the following steps of: (1) initializing the convergence storage module, establishing the mapping between a logical address space and physical storage equipment in a data storage system and recognizing the type of the physical storage equipment; (2) parsing an SCSI command; and (3) converging the SCSI command; and (4) returning an execution result of the SCSI command. The invention supports the exchange of an iSCSI data packet and an FCP data packet on an SCSI layer, realizes the visualization of a heterogeneous network storage system and effectively improves the deployment flexibility and the expandability of a disaster recovery system.
Owner:HUAZHONG UNIV OF SCI & TECH
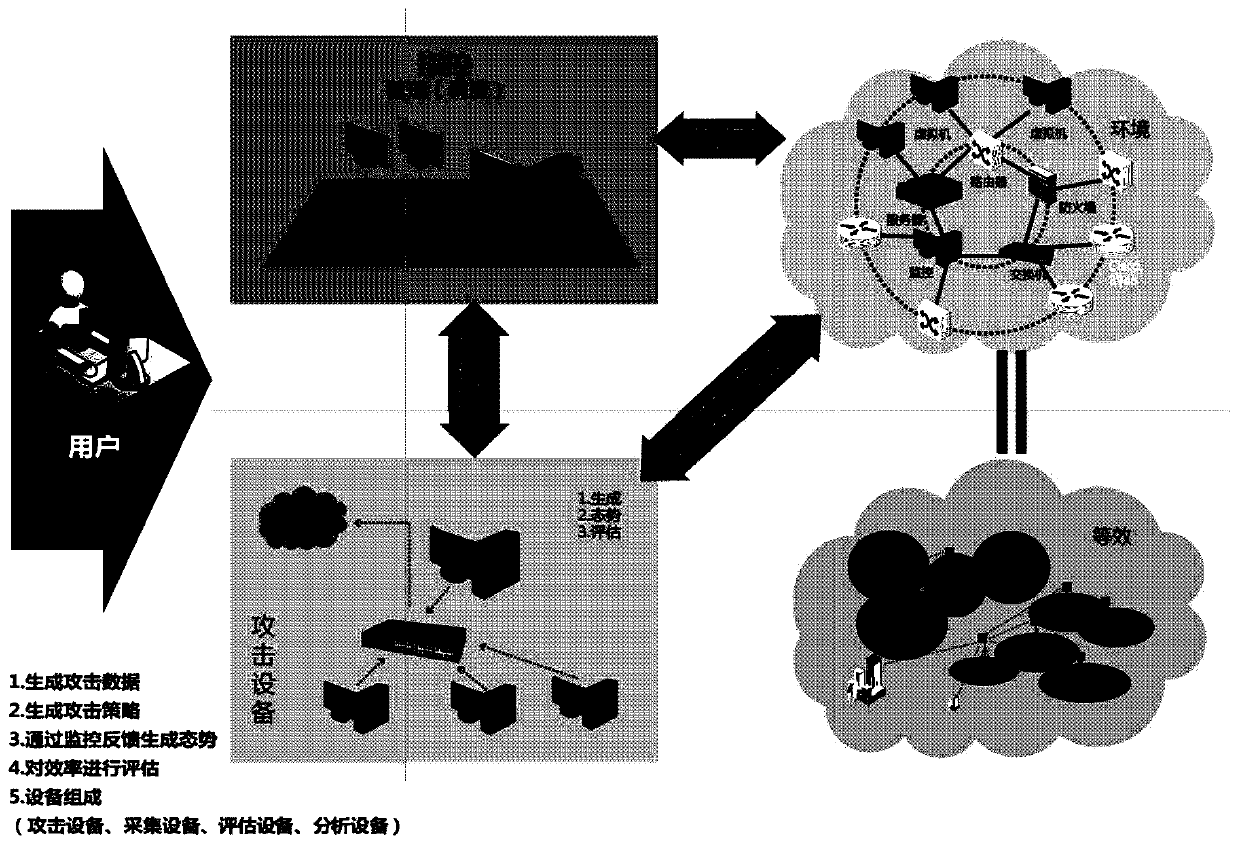
Cloud computing and big data based unmanned aerial vehicle task planning system and method
ActiveCN106776796ARealize unified managementImplement virtualizationArtificial lifeResourcesData informationOperation mode
The invention discloses a cloud computing and big data based unmanned aerial vehicle task planning system and method. The system comprises an information acquisition and data information management center and an output display system. The system has very powerful network management network management, is high in data processing speed and large in storage capacity and has good fault-tolerant capability. A big data technology is adopted, effective data can be rapidly and accurately looked up, and mass data is scientifically stored and managed. The whole system is easy to operate and manage, and an existing manual operation mode is completely changed. States of an unmanned aerial vehicle and combat teams can be checked and analyzed at multiple angles. Air lines and the like can be re-planned through real-time transmission of the unmanned aerial vehicle state and performance data and data information processing and analysis according to current state of the unmanned aerial vehicle and the emergency situation of a battlefield, and survival and task success rate are ensured. In addition, corresponding commanders and operators can make supervision and management by displaying the state and air lines of the unmanned aerial vehicle of the management system.
Owner:CENT SOUTH UNIV
Flow attack defense system based on SDN cloud security function service tree model
InactiveCN109617873ADefend and Defuse AttacksImplement virtualizationData switching networksExtensibilityVirtualization
The invention discloses a flow attack defense system based on an SDN cloud security service tree model. The system comprises a cloud security resource management module, a cloud security resource scheduling module, a security service tree policy customization module, a security service chain path customization module and a global security data monitoring module. By utilizing the flexibility of separation of a data plane and a control plane of an SDN, and easy extensibility provided by a virtual cloud environment, a cloud security service tree framework model is built. Flow to be detected is guided into an entry of a cloud security service tree; deep packet analysis of coarse granularity is carried out at the entry; if the flow is normal flow, the flow is rapidly forwarded to a destinationreceiver; and if the flow is abnormal flow, the flow is introduced into security service chains of subsequent tree branches to carry out fine granularity detection and processing. By utilizing massivecloud security resources and flexible resource scheduling, various granularities of network flow attacks of unknown types are detected and an attack elimination strategy capable of being flexibly customized is provided.
Owner:SUN YAT SEN UNIV
Gateway virtualization method and system
InactiveCN106161174AImplement virtualizationLarge capacityNetworks interconnectionNetwork connectionsVirtualizationNetwork service
An embodiment of the present invention discloses a gateway virtualization method. The method comprises the steps: receiving a network service request, and then requesting a software-defined network (SDN) controller to allocate resources according to the network service request. The network service request includes virtual network element requirements, and the virtual network element requirements include one or more virtual gateway forwarding requirements. Meanwhile, the embodiment of the present invention also discloses a gateway virtualization system.
Owner:ZTE CORP
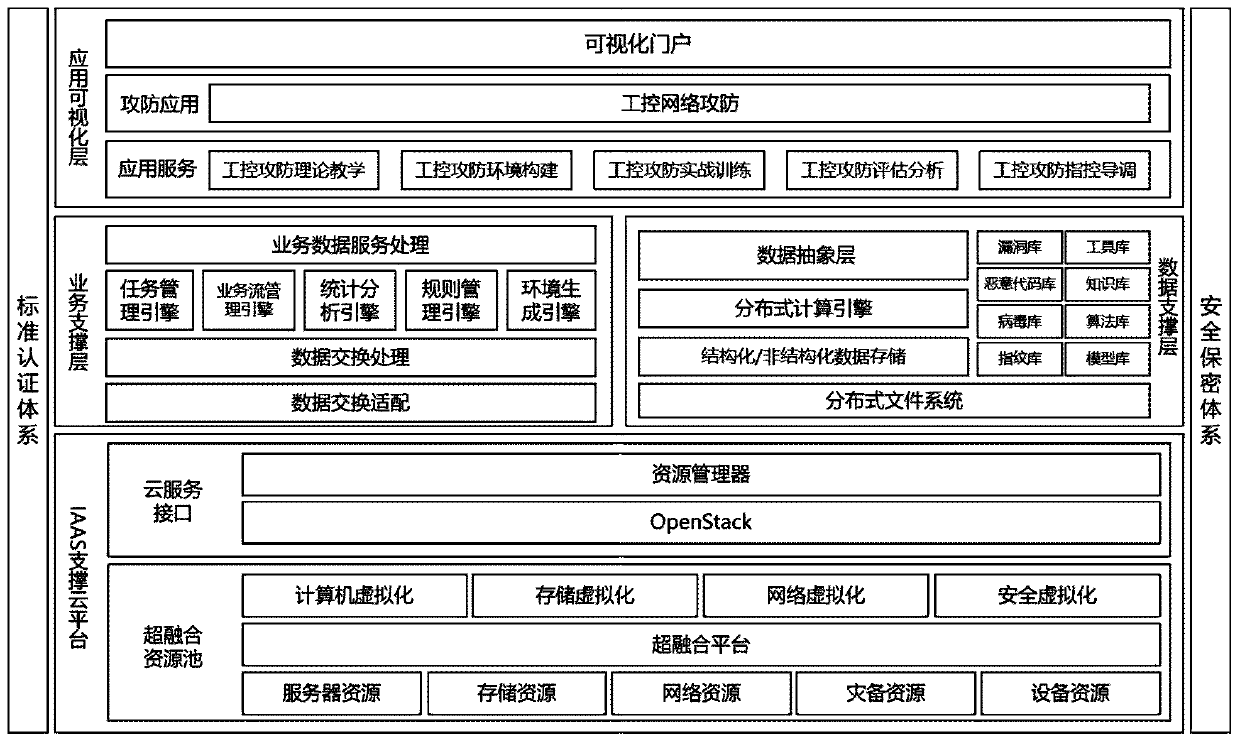
Industrial Internet security practical training platform based on virtualization
PendingCN111327463AFlexible configurationGuaranteed non-interferenceData processing applicationsData switching networksAttackIndustrial Internet
The invention discloses an industrial Internet security practical training platform based on virtualization. The invention belongs to the technical field of information security and industrial networksecurity. The system comprises an application visualization layer, a service support layer, a data support layer and a support cloud platform which are established under a standard authentication system and a security and secrecy system, a complete attack and defense teaching and practical training system is constructed; constructing a network attack and defense simulation environment based on the platform; software teaching and classroom teaching are combined, two links of classroom drilling explanation and student practice are provided, understanding and mastering of students on network attack and defense related basic knowledge are improved, teaching functions of practice, test and the like are provided, teaching and practice are combined, and the students have deeper understanding onnetwork attack and defense knowledge and technologies.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
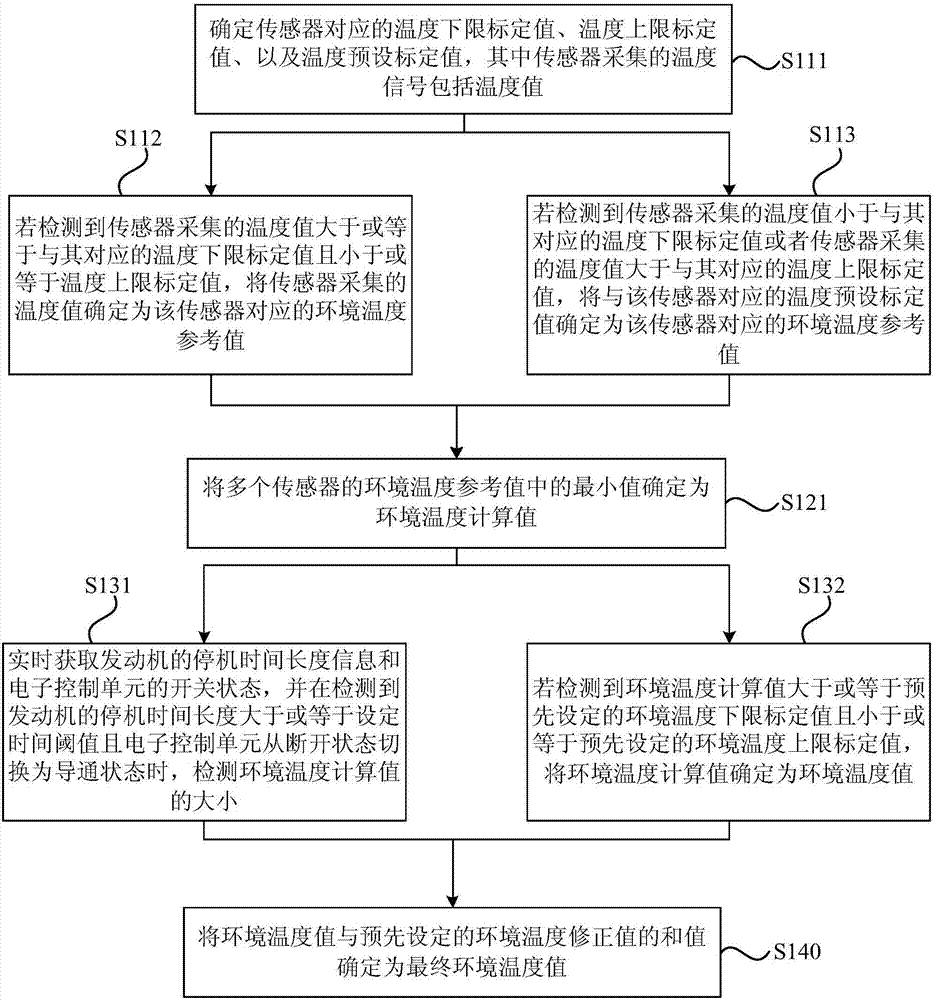
Control method, device and system of engine virtual environment temperature sensor
ActiveCN107965412AImplement virtualizationLow costInternal combustion piston enginesElectric motor startersVirtualizationElectricity
The embodiment of the invention disclsoes a control method, device and system of an engine virtual environment temperature sensor. An engine is electrically connected to an electronic control unit. The control method comprises the steps of starting the engine, obtaining temperature signals collected by a plurality of sensors integrated in the engine in real time, and determining the environment temperature reference value corresponding to the temperature signal of each sensor; calculating the environment temperature reference values of a plurality of sensors through the virtual environment temperature sensor to determine the environment temperature calculated values; and obtaining the downtime duration information of the engine and the on-off state of the electronic control unit in real time, and determining the environment temperature calculated values as the environment temperature values when it is detected that the downtime duration of the engine is longer than or equal to the settime threshold and the electronic control unit is switched on from off. According to the embodiment of the invention, the virtualization of the engine environment temperature sensor is achieved, and the cost is reduced; and the control method facilitates secondary development.
Owner:WEICHAI POWER CO LTD
Realization method for cross-physical-machine huge virtual machine
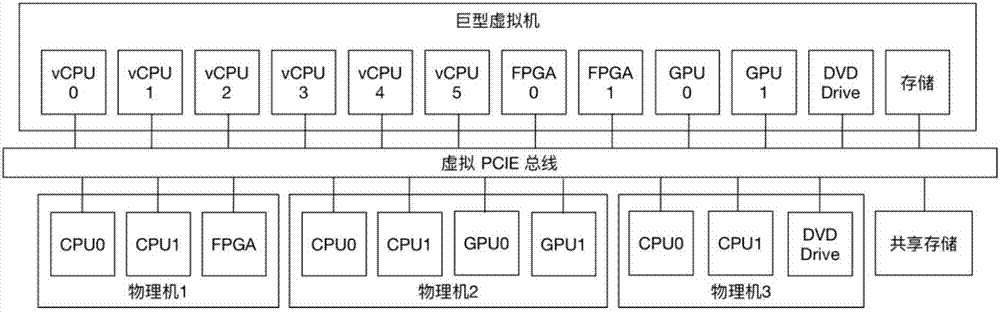
ActiveCN107491340AImplement virtualizationEnabling High Performance ComputingInterprogram communicationSoftware simulation/interpretation/emulationDirect memory accessRemote memory access
The invention provides a realization method for a cross-physical-machine huge virtual machine. The method comprises the steps that first, a huge virtual machine is created; second, interrupt processing is performed on the huge virtual machine; third, equipment interrupt processing is performed; and fourth, remote access based on a high-speed shared memory access technology is performed. Through the method, multiple physical machines provide computing resources, IO resources and other resources for one virtual machine; and the machines perform remote memory access through the remote high-speed memory access technology, so that a high-speed distributed shared memory is realized.
Owner:SHANGHAI JIAO TONG UNIV
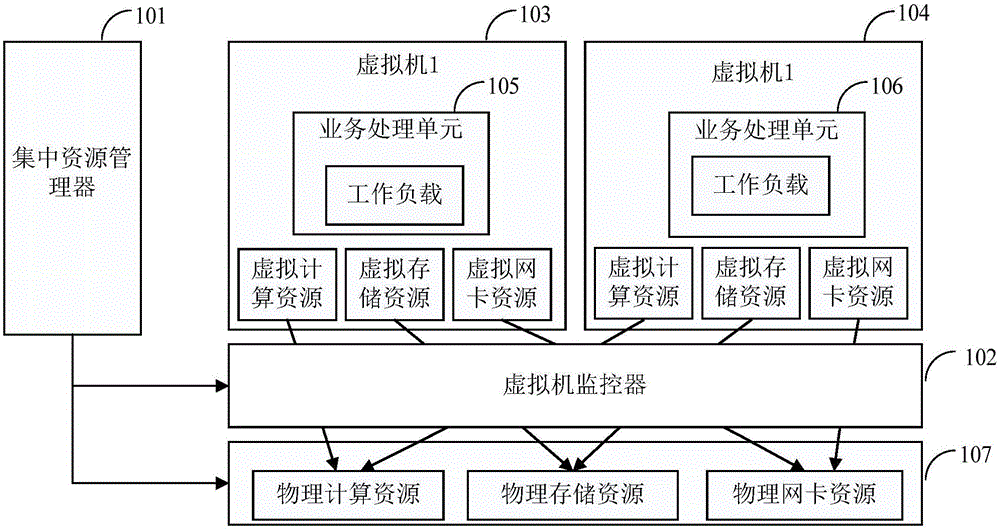
A resource scheduling method suitable for a cloud computing resource pool model of a hyperconverged IT infrastructure
InactiveCN109240795AEasy to manageImprove work efficiencyResource allocationSoftware simulation/interpretation/emulationResource poolArrival time
The invention discloses a resource scheduling method suitable for a cloud computing resource pool model of a hyperconverged IT infrastructure. A cloud computing resource scheduling system of the hyperconverged IT infrastructure is abstracted. Users send out task requests, and the tasks arrive at the cloud resource scheduling model in sequence, and are arranged into a global task queue; The scheduler schedules the tasks according to the load of each server, task type and task arrival time, and assigns the tasks to the virtual machine. If the virtual machine running on the server has idle resources, it can provide service for users immediately. After the task is executed, the virtual machine reclaims the allocated resources. If the virtual machine on which the server is running does not provide the resources required to perform the task, the task is discarded. The invention can better manage the resources of the cloud computing, improve the utilization rate of the whole resources, improve the integration performance of the super fusion structure, and effectively reduce the operation and maintenance cost of the cloud platform.
Owner:NANJING NARI GROUP CORP +2
Connection and management method of reconfigurable component in high performance computer
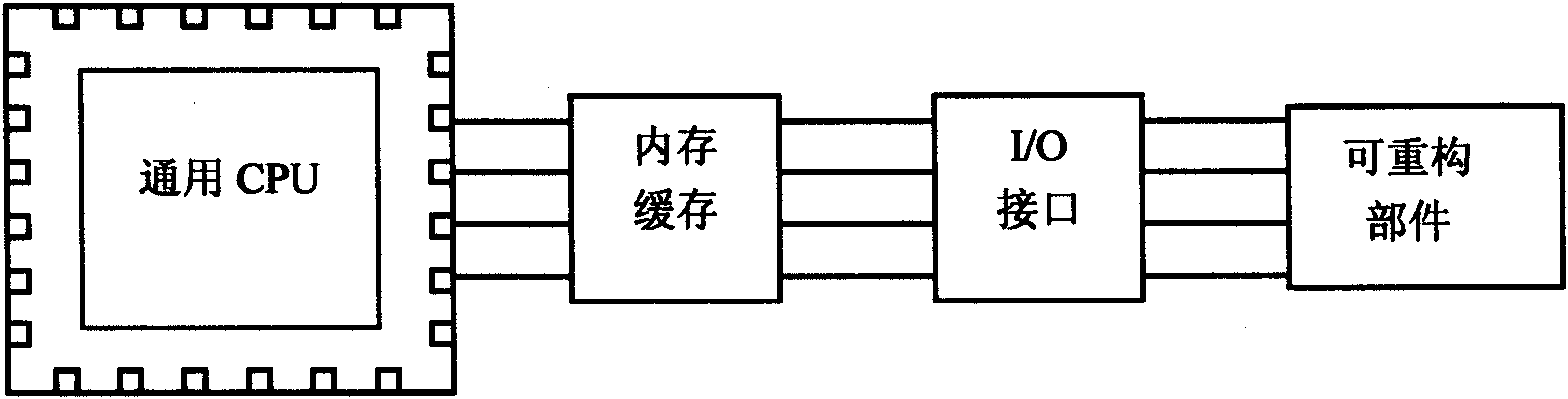
InactiveCN101620588AImplement virtualizationFully utilizeArchitecture with multiple processing unitsManagement unitNetwork connection
The invention relates to a connection method and a management method between a general CPU and a reconfigurable component in a high performance computer system. The high performance computer system of the invention contains a certain amount of computing nodes, and each computing node contains general CPUs and a certain amount of reconfigurable components as well as a reconfigurable component connection network and a management unit. All general CPUs, reconfigurable components and management units in the computing nodes can establish network connection by the reconfigurable components, and connections between all general CPUs and reconfigurable components in the computing nodes are disconnected under the default condition. The reconfigurable component connection method of the invention can cause the reconfigurable components to be no longer attached to any general CPU, and the general CPUs and the reconfigurable components can be arbitrarily combined, thus improving the flexibility of the system; the reconfigurable component management method realizes real-time monitoring and dynamic and flexible configuration of the reconfigurable components, thus being capable of giving full play to the reconfigurable components and the general CPUs in the high performance computer system.
Owner:THE PLA INFORMATION ENG UNIV
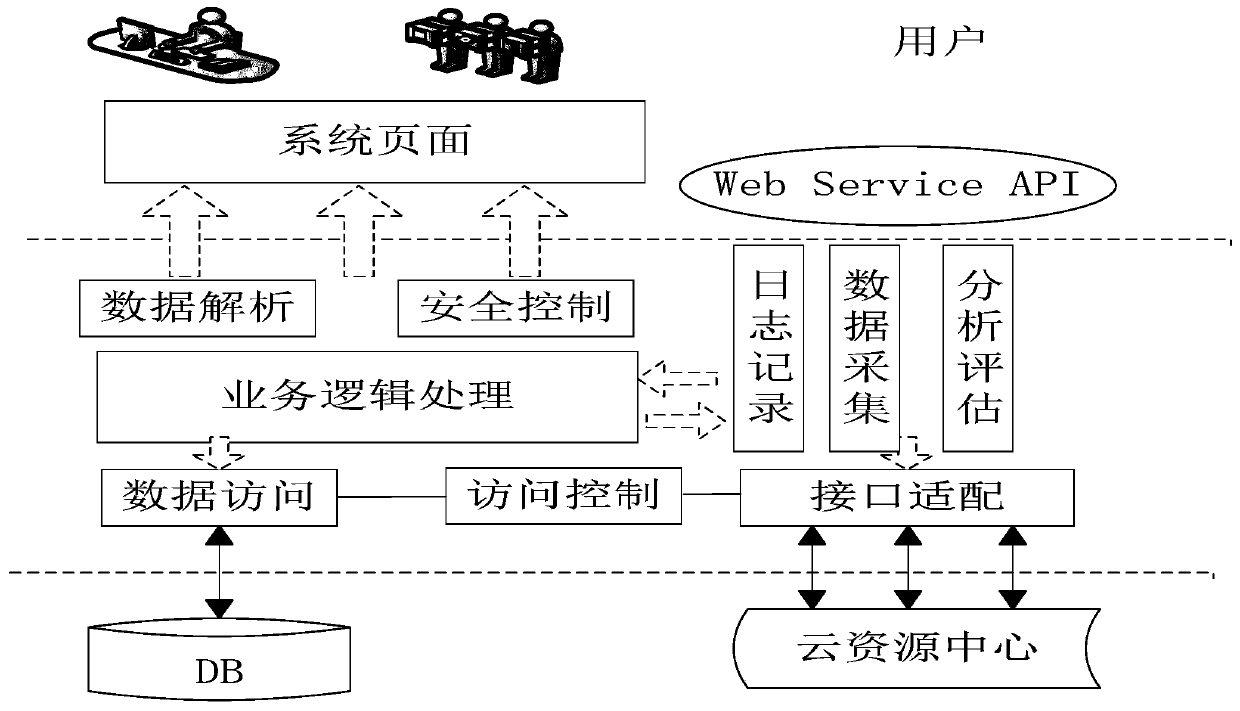
Cloud computing system based on KVM (Keyboard Video and Mouse) virtualization and media redirection
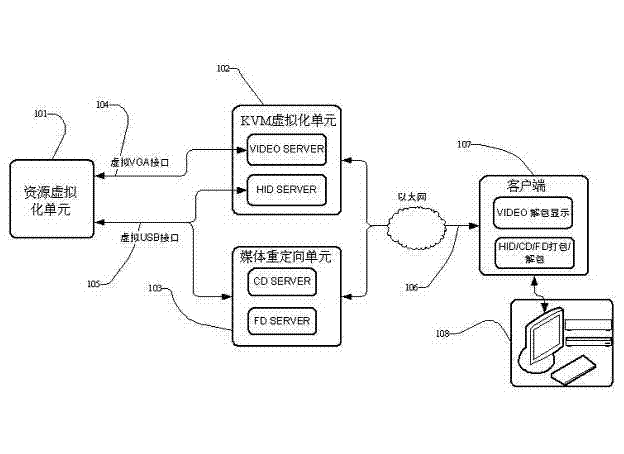
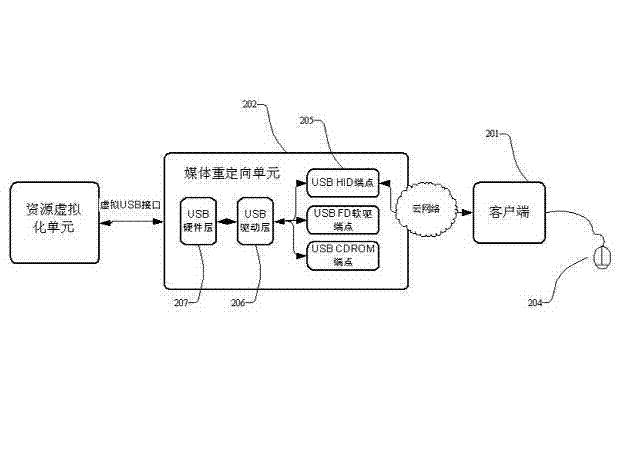
ActiveCN102368787ASave bandwidthImplement virtualizationInput/output for user-computer interactionTransmissionMemory virtualizationServer-side
The invention discloses a cloud computing system based on KVM (Keyboard Video and Mouse) virtualization and media redirection. The cloud computing system comprises two parts, namely, a cloud computing server side and a client side. The server side is used for realizing the KVM virtualization and the media redirection virtualization besides resource virtualization. A resource virtualization unit is used for providing a CPU (Central Processing Unit), a memory and other computing resources for a user; the KVM virtualization is used for providing VIDEO display, keyboard and mouse and other human-machine interaction modes to the user; and a media redirection unit can be used for mapping CD (Compact Disk) driver, a floppy disk, a USB (Universal Serial Bus) flash driver and other storage equipment of the client side to the server side so as to realize transmission of user data. Accordingly, for the client side, a complete set of computer virtualization equipment of the client side is constituted by means of the three virtualization parts, the requirements of the client side on hardware resources are reduced, and the construction of a cloud computing service of the server side is facilitated.
Owner:烟台浪潮云计算有限公司
WEB dynamic security defense method and system
InactiveCN110381049AImplement virtualizationImplement one-shot transcodingTransmissionWeb applicationWeb service
The invention discloses a WEB dynamic security defense method and system. The method is based on a moving target defense technical thought. The invention provides an active dynamic defense mechanism for a WEB service system. When the protected WEB application service system is not attacked, the service entry or the resource address is actively transformed, so that the information of the backgroundof the server is effectively hidden and protected, the dynamics and uncertainty of the attacked surface of the system are realized in a randomized dynamic coding technical mode, the difficulty of network attack implementation is improved, and the anti-attack capability of the WEB application service system is effectively enhanced.
Owner:浙江智贝信息科技有限公司
Window restoring method based on remote frame buffering
ActiveCN103049262AImplement virtualizationTransmissionSpecific program execution arrangementsVirtualizationComputer hardware
The invention discloses a window restoring method based on remote frame buffering. The method includes steps of extracting image frame buffering data from an X11 data generation layer of a server side; capturing application window information data from an X11 layer window manager of the server side, wherein the application window information data include identities (IDs), coordinates, states and types of all application program windows which are in operation on the server side; transmitting the image frame buffering data and the application window information data from the server side to a local client side; and restoring images of the application program windows which are in operation at a long distance according to the image frame buffering data and the application window information data in the local client side. By means of the window restoring method based on remote frame buffering, long-distance application windows can be checked and controlled on the local client side so that virtualization of application programs is achieved.
Owner:广州尚融云科技有限公司
Image imaging jitter compensation method, system and device
ActiveCN111614895AImprove accuracyEnable effective trackingTelevision system detailsColor television detailsComputer hardwareImaging processing
The invention relates to the technical field of image processing, and provides an image imaging jitter compensation method, system and device, and the method comprises the steps: installing a gravitysensor at a parallel position of a camera assembly, and obtaining the jitter acceleration data of the camera assembly in real time through the gravity sensor; adopting an SOC chip as a main control module, and utilizing the operation function of the SOC chip to perform logic operation on collected moving images and jitter acceleration data to obtain correction coordinates of a target object. According to the invention, the simple and low-cost gravity sensor is additionally arranged, so the shaking displacement of the target object is effectively detected; the SOC chip with highly integrated circuits and comprehensive functions is adopted to perform data operation, and direct output from moving images and jitter acceleration data to correction coordinates is realized, so the effective compensation of jitter displacement of a target object is realized on the basis of ultra-low manufacturing cost, and the accuracy of image imaging is greatly improved.
Owner:FORYOU GENERAL ELECTRONICS
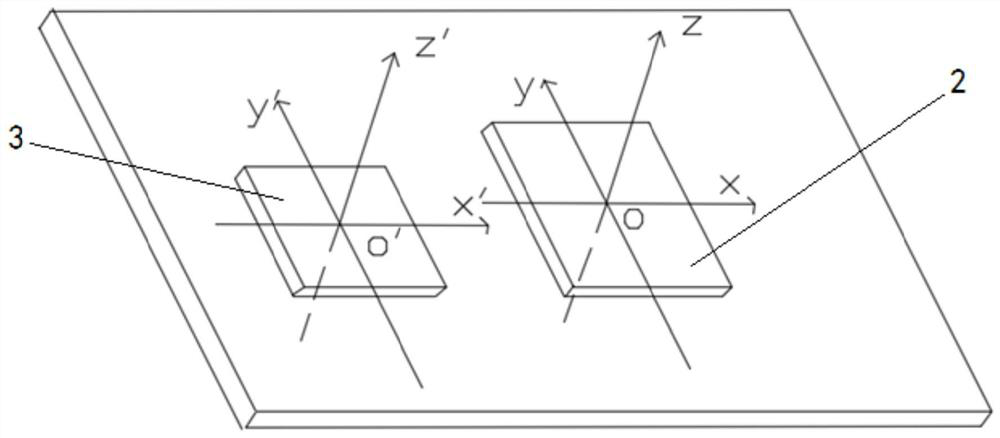
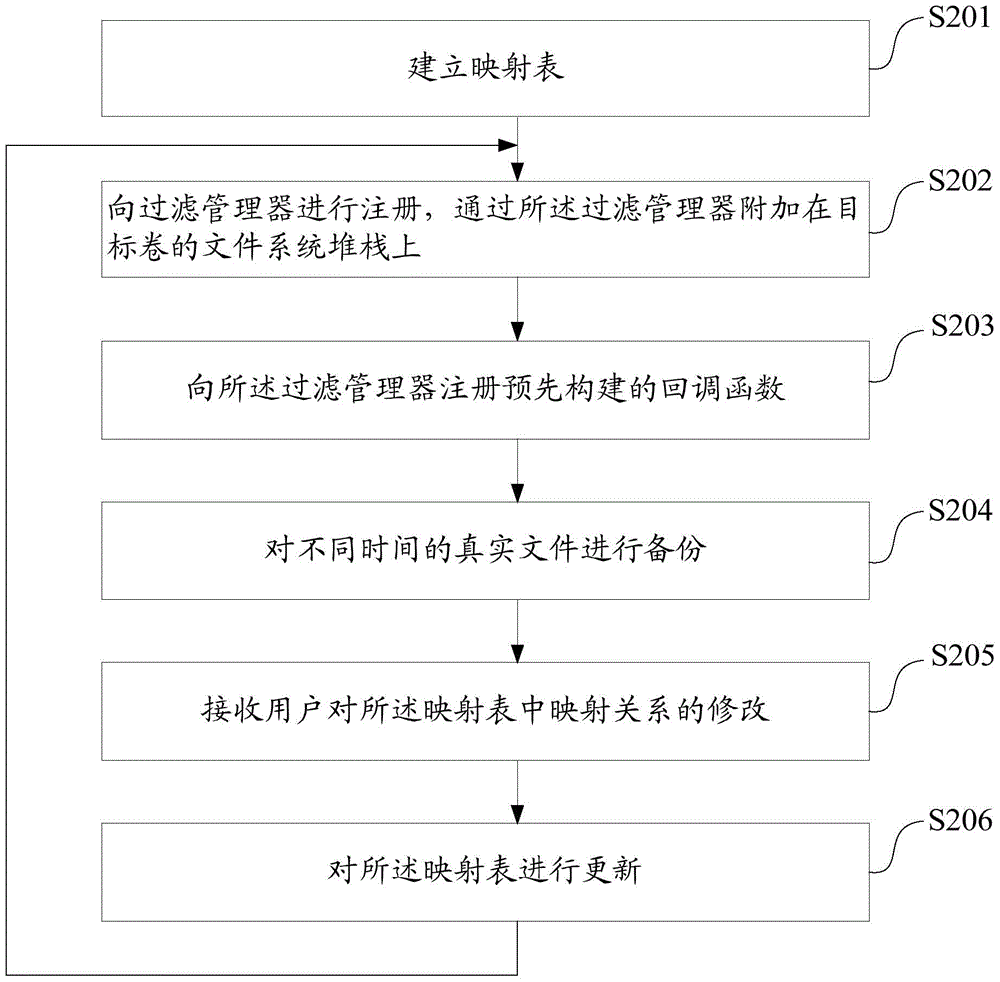
File virtualization implementation method and apparatus
ActiveCN105701409AImplement virtualizationImprove scalabilityDigital data protectionVirtualizationOperational system
Embodiments of the present invention disclose a file virtualization implementation method and apparatus, which are capable of solving the problem that the existing file virtualization is not stable enough and is not easy to be extended and efficiently implementing file virtualization. The method comprises: registering with a filtration manager, and attaching to a file system stack of a target volume by means of the filtration manager; registering a pre-constructed call back function with the filtration manager, wherein the callback function is used for responding to a call of the filtration manager and acquiring a file path corresponding to a to-be-opened file; and according to a pre-established mapping relationship, modifying the file path in the callback function into a target path, and modifying a return value in the callback function into a redirection state value and then returning the redirection state value, so as to enable the filtration manager to read the target path, and returning the target path to an operating system, so as to enable the operating system to open the file according to the target path. The apparatus comprises a module used for executing the method. The method and apparatus disclosed by the present invention are applicable to security protection of files.
Owner:ZHUHAI BAOQU TECH CO LTD
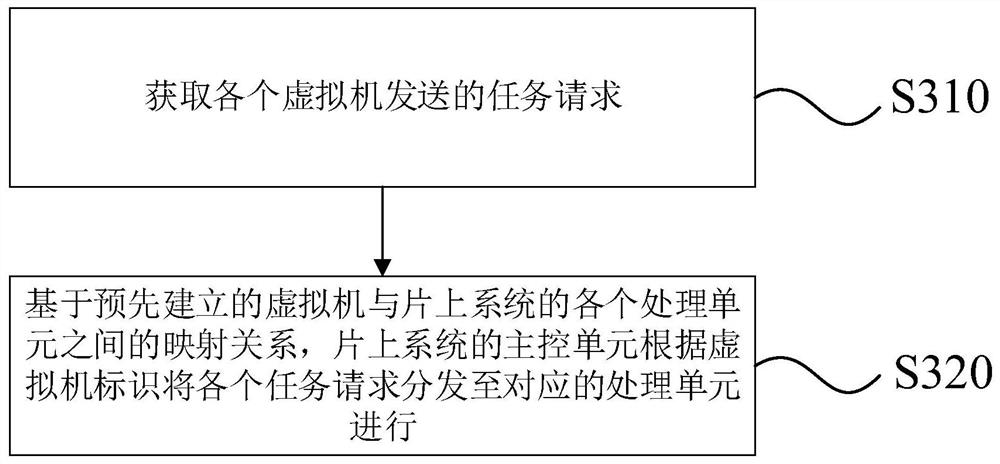
System-on-chip, virtual machine task processing method and device, and storage medium
PendingCN113821308AImprove performanceImplement virtualizationResource allocationArchitecture with single central processing unitComputer hardwareVirtualization
The invention relates to the technical field of computers, in particular to a system-on-chip, a virtual machine task processing method and device and a storage medium. The virtual machine task processing method is applied to a system on chip and comprises the steps that task requests sent by all virtual machines are obtained, and the task requests comprise corresponding virtual machine identifiers; and based on a pre-established mapping relationship between the virtual machine and each processing unit of the system-on-chip, the main control unit of the system-on-chip distributes each task request to the corresponding processing unit for processing according to the virtual machine identifier. In the method of the invention, the system-on-chip schedules and distributes the tasks based on the mapping relationship between the virtual machine and the hardware resource, so that the virtualization of the system-on-chip is realized, the virtualization cost is reduced, and the performance of the virtual machine is improved.
Owner:SHANGHAI POWERTENSORS INTELLIGENT TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com