Method and system for key generation during handover
A technology for handover process and key generation, which is applied in electrical components, security devices, wireless communications, etc., can solve problems such as hidden dangers of communication system security, improve security, and avoid illegally obtaining the key KeNB of the next hop. Possibilities, Effects of Guaranteed Forward Safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
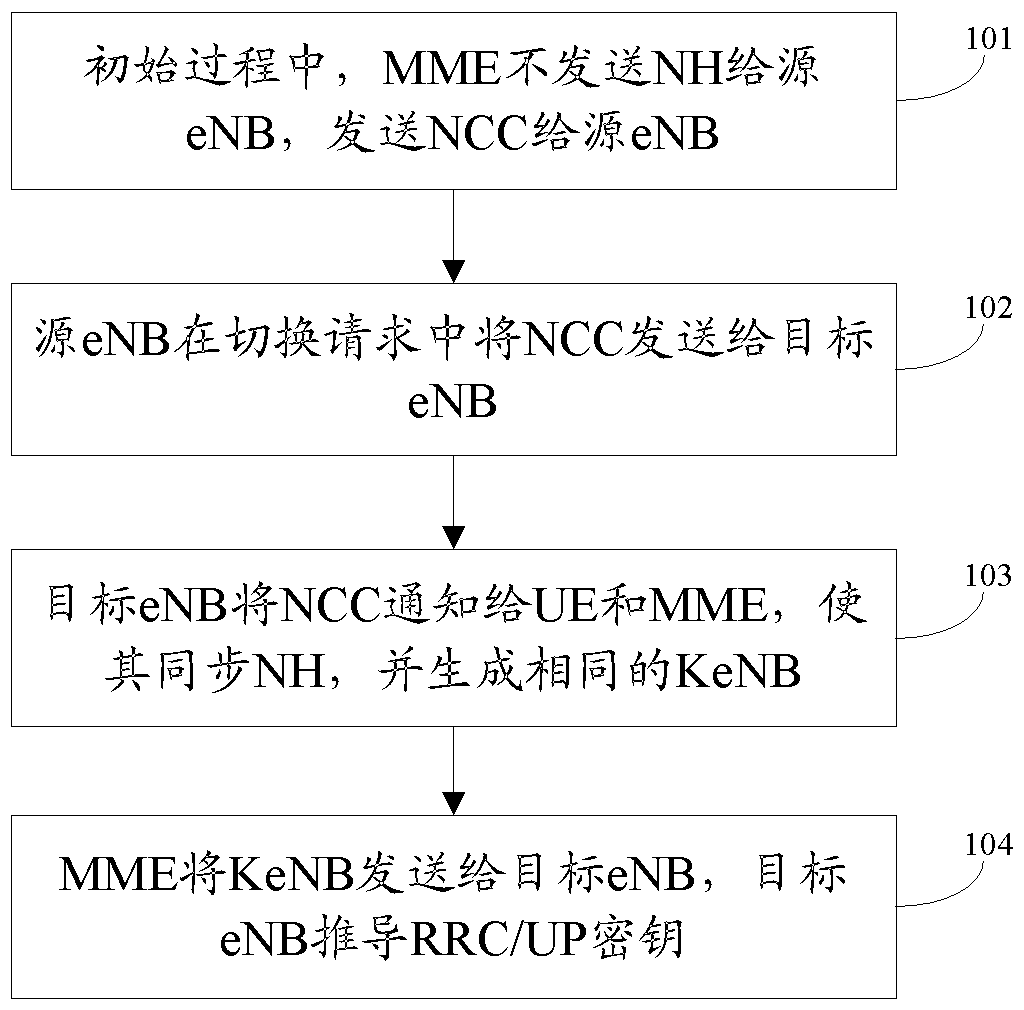
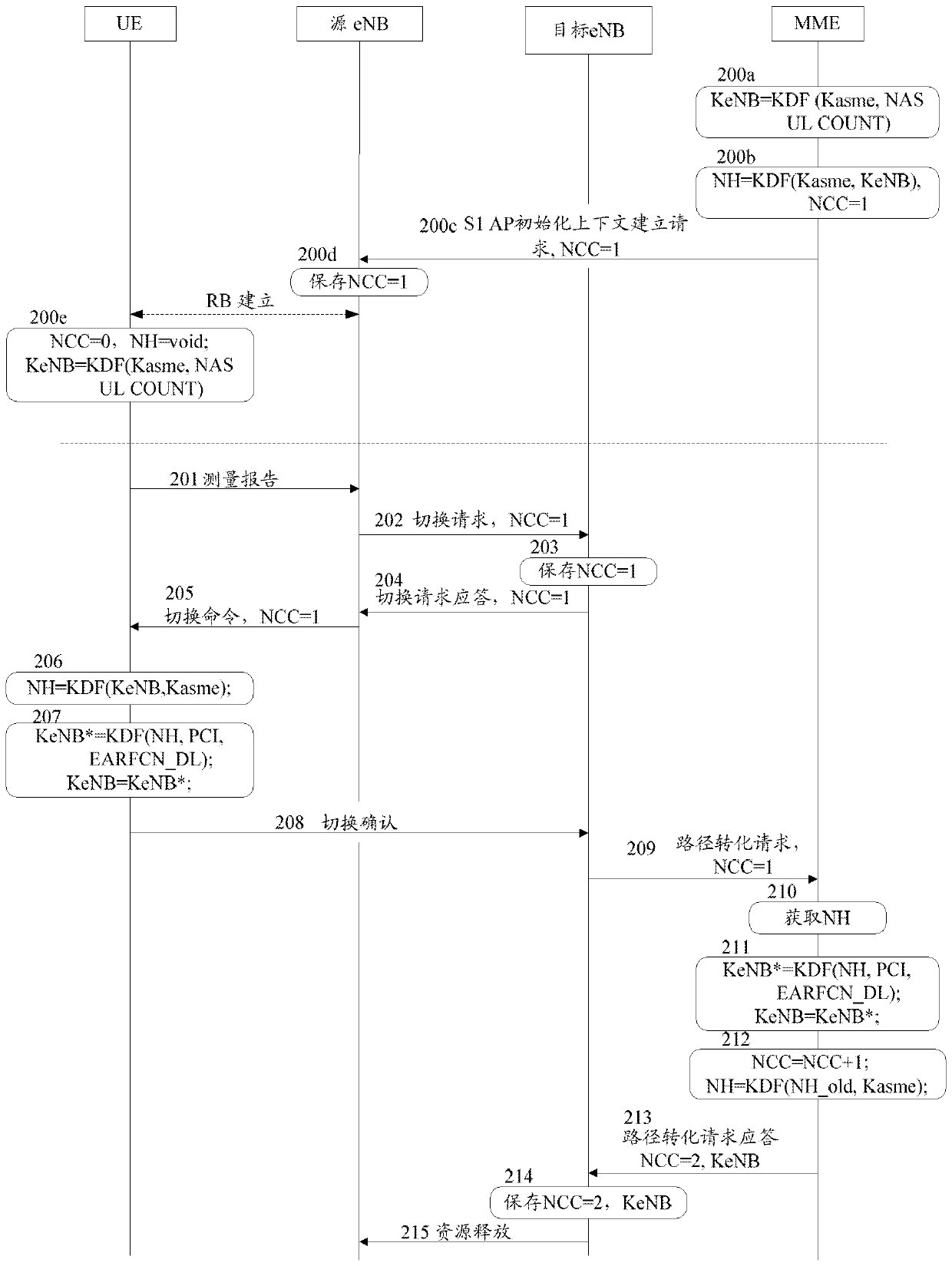
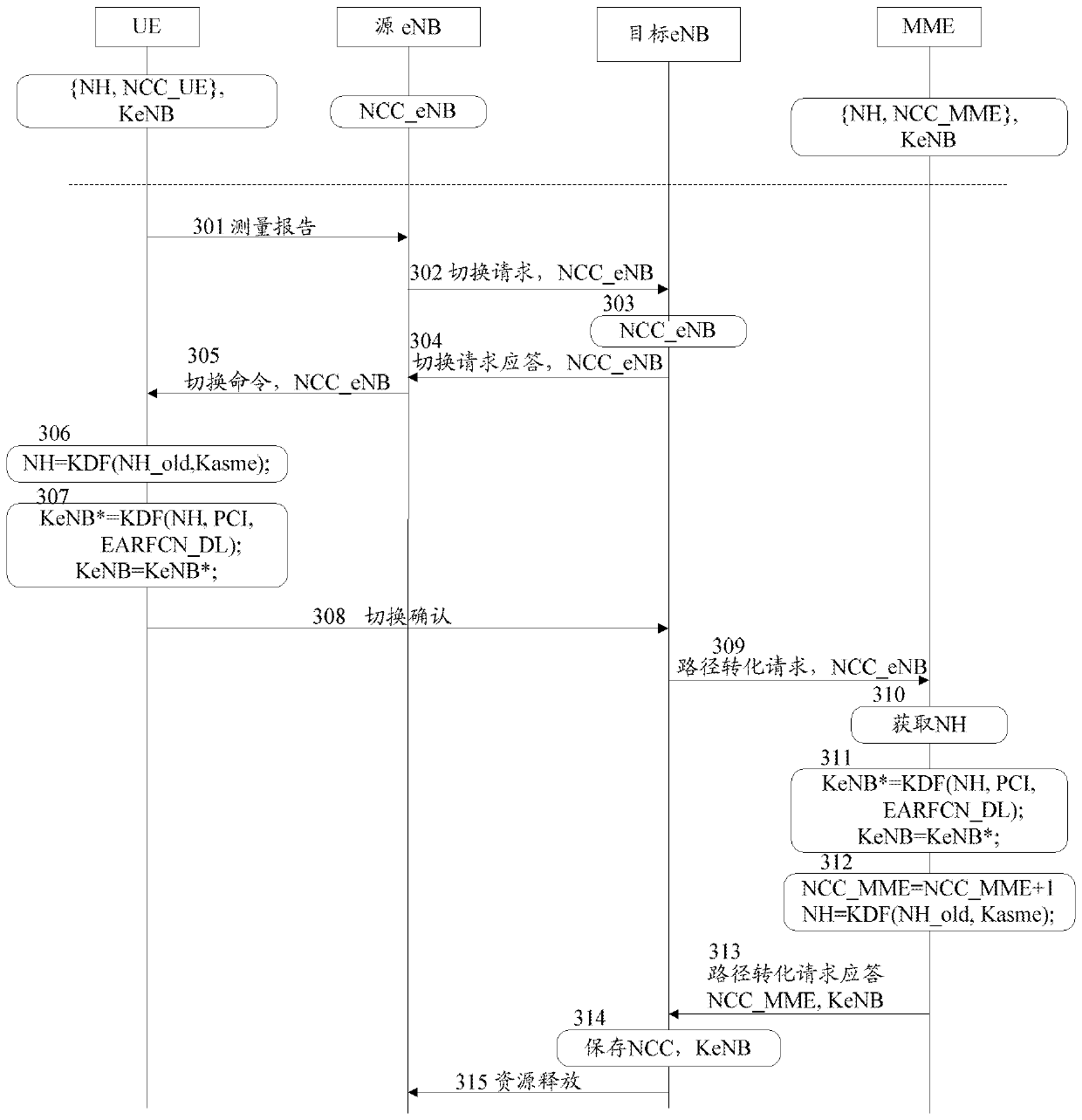
[0056] The basic idea of the present invention is: during the X2 handover process, the source eNB no longer derives the next hop key for the target eNB, and the source eNB only provides the next hop counter NCC value for the target eNB. The target eNB uses the NCC value to keep the NHs in the UE and MME entities synchronized, so that the same KeNB is saved in the UE and the MME. The target eNB uses the NCC value to apply to the MME for the same KeNB as the UE, so as to keep its own KeNB consistent with the UE's KeNB. During the handover process, the NH no longer leaves the MME, the eNB cannot obtain the NH, and the eNB has no ability to deduce the NH (the calculation of the NH must have Kasme), so the source eNB cannot obtain the KeNB of the target eNB in the next hop transition, which solves the forward security question.
[0057] In order to make the purpose, technical solutions and advantages of the present invention more clear, the following examples are given and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com