Insurance claim settlement system based on block chain
A block chain and subsystem technology, applied in the information field, can solve problems such as difficulty in ensuring the authenticity of relevant documents and bills, and achieve the effect of eliminating the possibility of forging business files, improving security, and ensuring authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
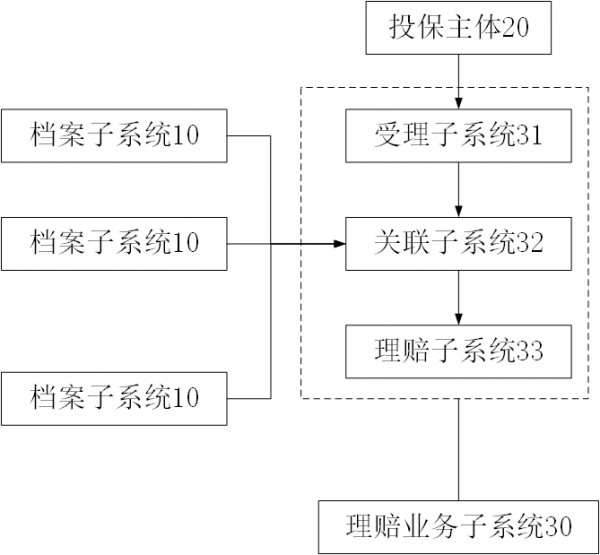
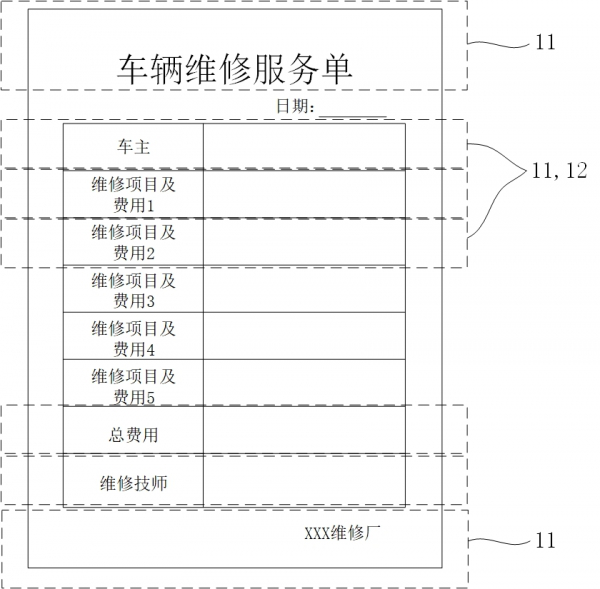
[0020] Blockchain-based insurance claims system, please refer to the appendix figure 1 , including the file subsystem 10 and the claim settlement business subsystem 30. The claim settlement business subsystem 30 includes an acceptance subsystem 31, an association subsystem 32 and a claims settlement subsystem 33. When a claim settlement event occurs in the insured subject 20, the insured subject 20 sends a claim settlement request To the acceptance subsystem 31, the acceptance subsystem 31 creates a new claim settlement task, assigns a task number, and extracts the hash value of the identification of the insurance applicant 20 as an identification code. The acceptance subsystem 31 publishes a smart contract on the blockchain, and the smart contract publishes the identification code. and the public key of the associated subsystem 32, the file subsystem 10 is deployed on the service subject that provides services for the insurance subject 20, collects and manages the service subj...
Embodiment 2
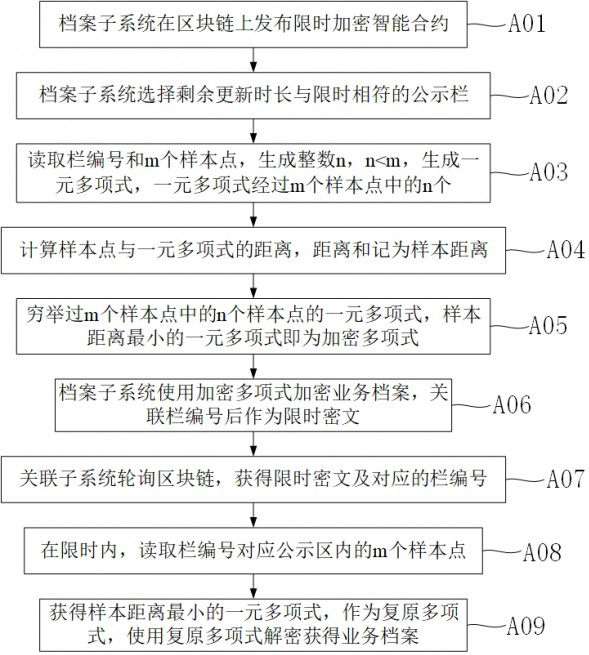
[0034] Based on the blockchain-based insurance claim settlement system, this embodiment further improves the time-limited encryption algorithm on the basis of the first embodiment.
[0035] In the time-limited encryption algorithm scheme described in the first embodiment, if the correct n value is not obtained, m univariate polynomials can be recovered through m sample points. In order to improve the security of time-limited encryption, the bulletin board should disclose multiple sample points, such as 512 or 1024 sample points. But even if the number of sample points is increased, the encryption polynomial is easy to be cracked by exhaustive attempts.
[0036] Please see attached Figure 5 , in this embodiment, the time-limited encryption algorithm includes: step C01) the file subsystem 10 exhaustively enumerates the univariate polynomials of n sample points in the m sample points; step C02) arranges the univariate polynomials in ascending order of sample distance; step C03)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com