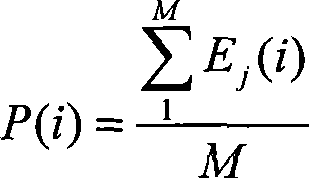Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1276results about How to "Not lost" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Vehicle license plate recognition method based on video
InactiveCN104050450AReduce sizeLow costCharacter and pattern recognitionFeature vectorTemplate matching
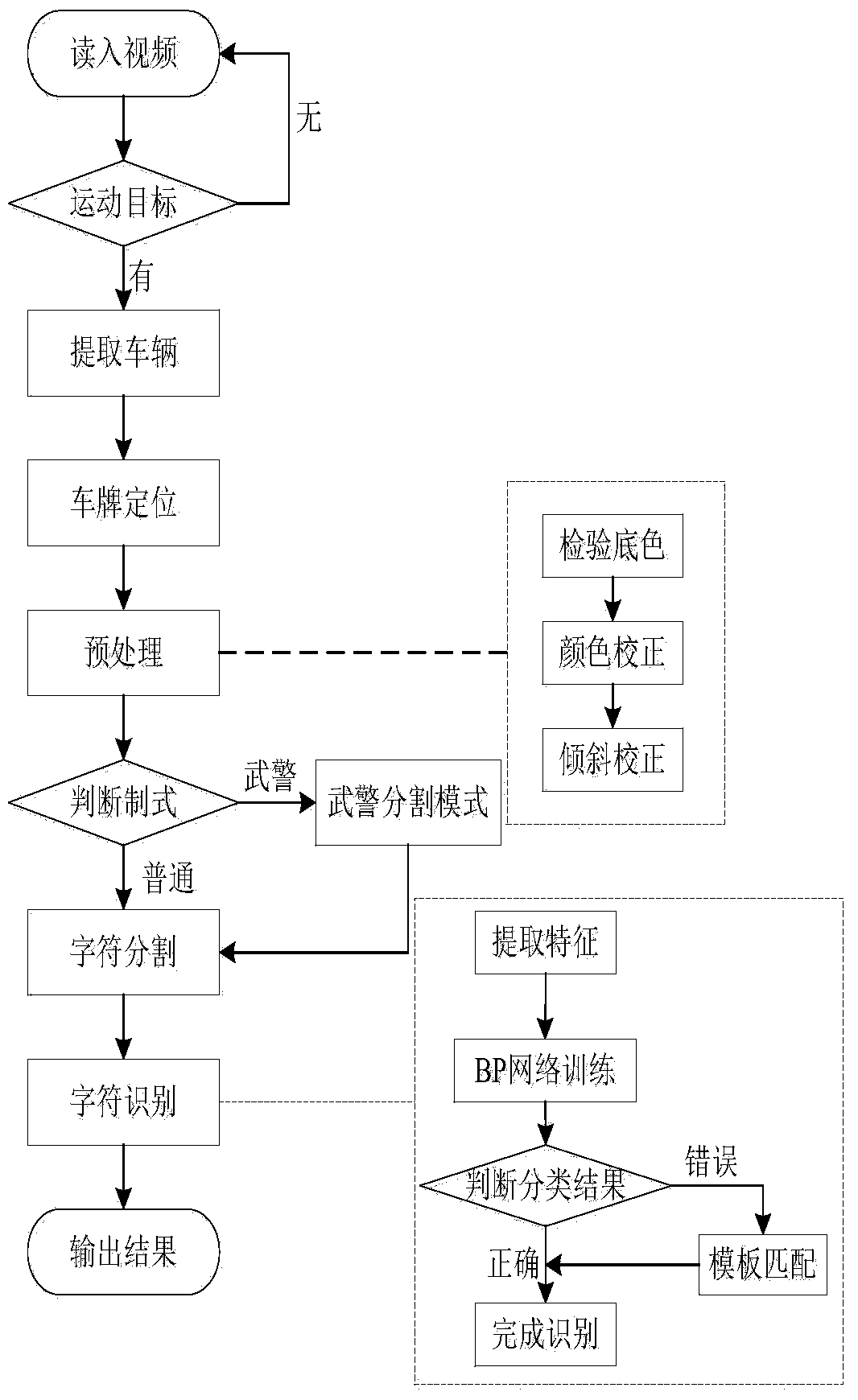
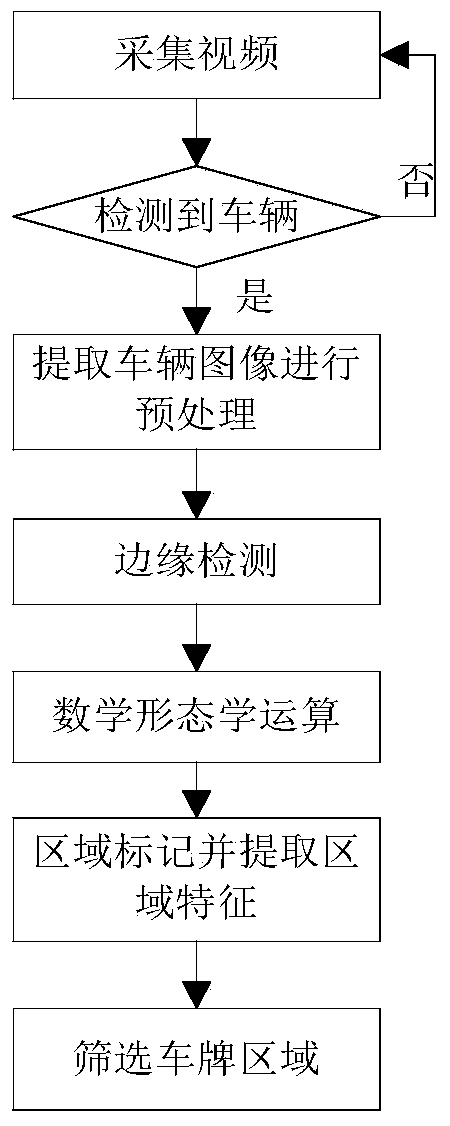
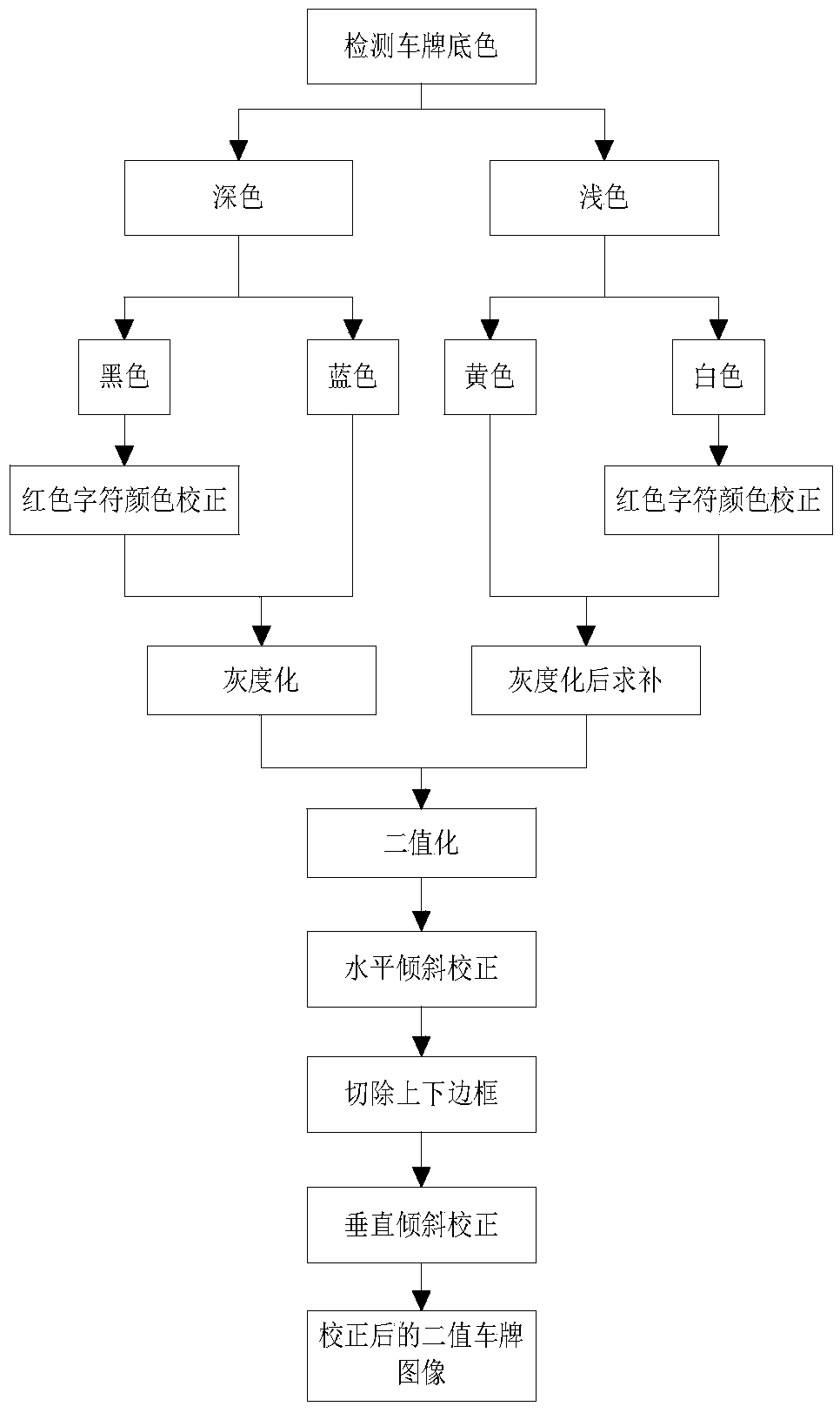
The invention provides a vehicle license plate recognition method based on a video. According to the vehicle license plate recognition method based on the video, moving vehicles are detected and separated out with the vehicle video which is obtained through actual photographing by means of a camera serving as input, the accurate position of a vehicle license plate area is determined by conducting vertical edge extraction on a target vehicle image obtained after pre-processing, a vehicle license plate image is separated out, color correction, binaryzation and inclination correction are conducted on a vehicle license plate image, each character in the positioned vehicle license plate area is separated to serve as an independent character, feature extraction is conducted one each character, obtained feature vectors are classified through a classifier which is well trained in advance, a classification result serves as a preliminary recognition result, secondary recognition is conducted on the stained vehicle license plate characters according to a template matching algorithm imitating the visual characteristics of human eyes, and then a final vehicle license plate recognition result is obtained. The vehicle license plate recognition method based on the video has the advantages that hardware cost is reduced, the management efficiency of an intelligent transportation system is improved, the anti-jamming performance and the robustness are high, the recognition efficiency is high, and the recognition speed is high.
Owner:XIAN TONGRUI NEW MATERIAL DEV
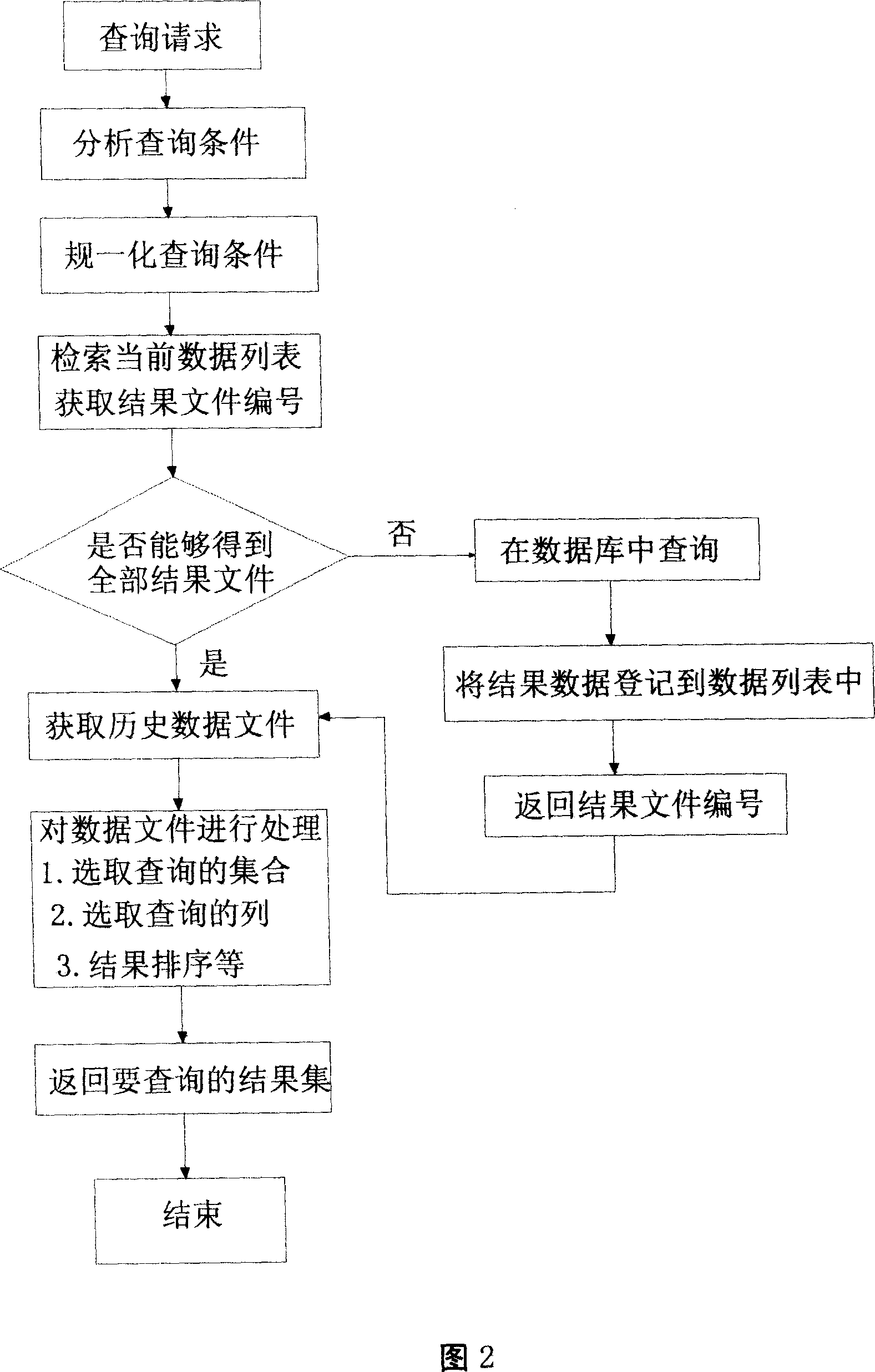
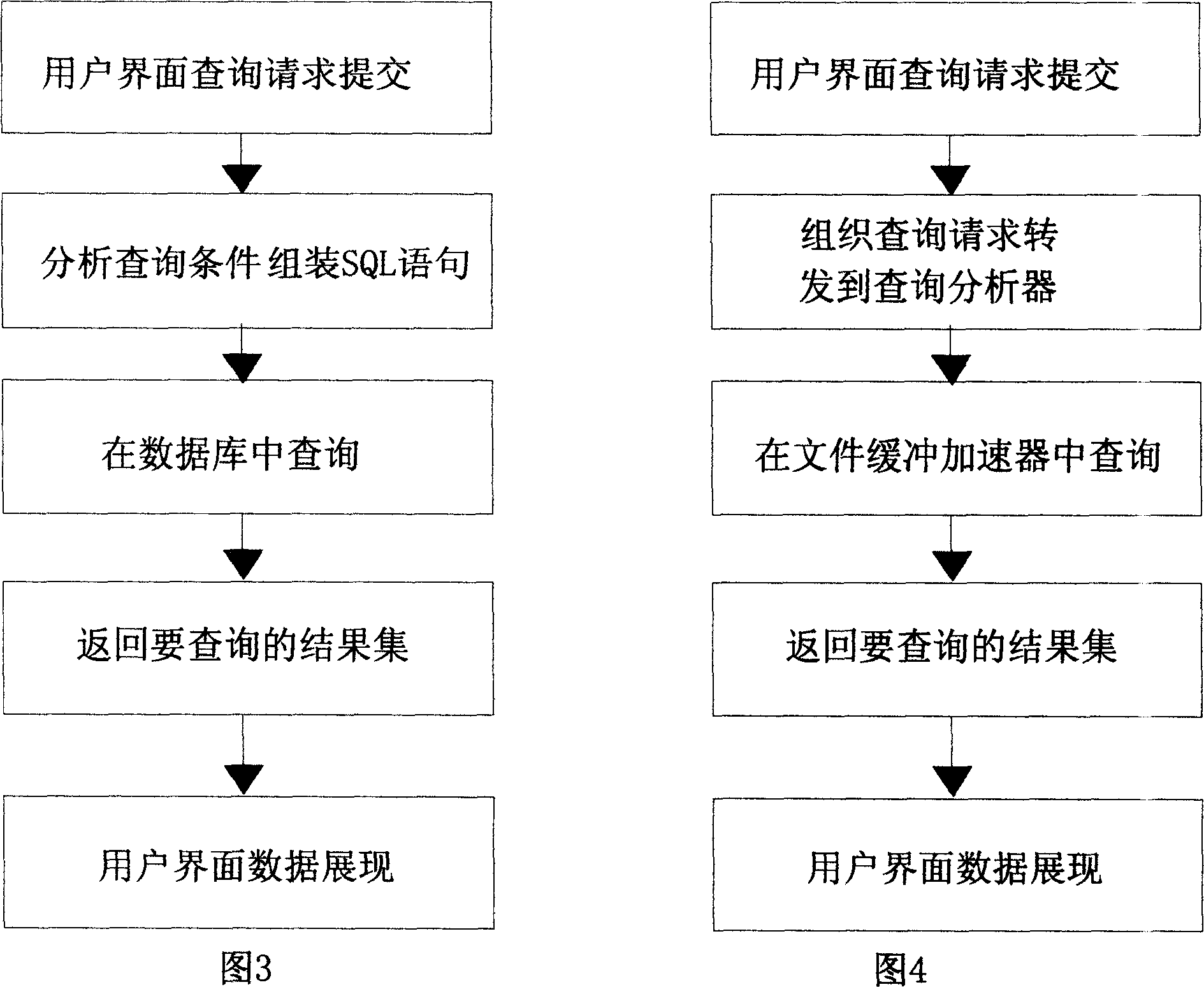
Data speedup query method based on file system caching
InactiveCN101110074AImprove hit rateIncrease in inquiriesSpecial data processing applicationsQuery analysisFile system
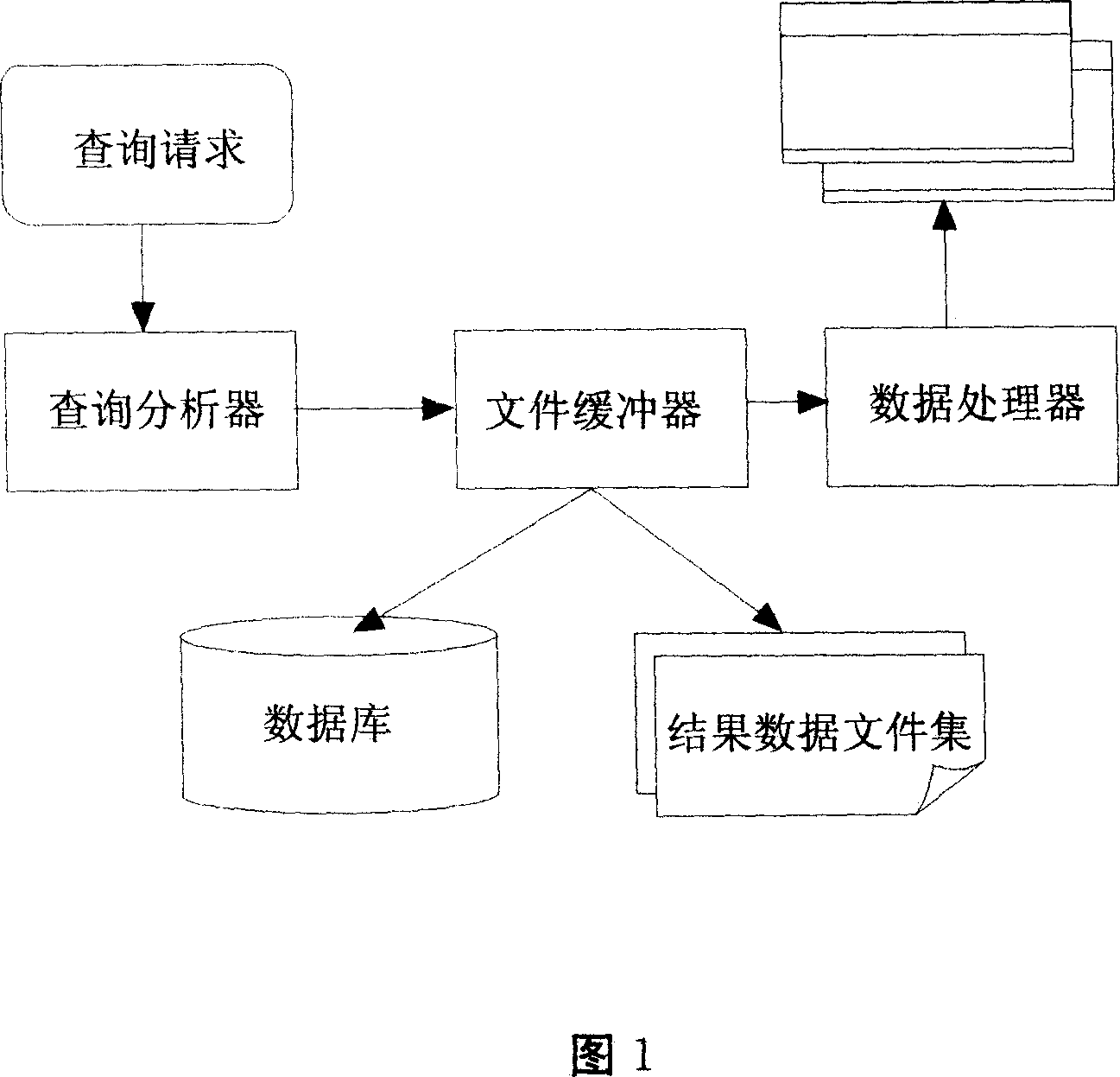
The invention relates to an accelerated data query method in a query system, which provides an accelerated data query method based on a cache of document system according to the features of unchanged saved historical data and frequent query of same data. The invention saves the historical query data and takes it as the cache data for query, so as to accelerate the query. Upon receiving the query quest from user, the system will first of all turn to the query analyzer; the principal function of the query analyzer is to analyze and plan the query condition; then, after passing through a document buffer, the system analyzes whether the data document in the result satisfies the present query need; if not, the query will be carried out in the database and the final result will be fed back to a data processor; then, the data processor will filter and sort the data according to the final query demand and finally feed back the result document to a super stratum application system. Therefore, without increasing the investment on hardware, this query method is able to greatly reduce the occupation of database and system resource, so as to improve the query speed.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
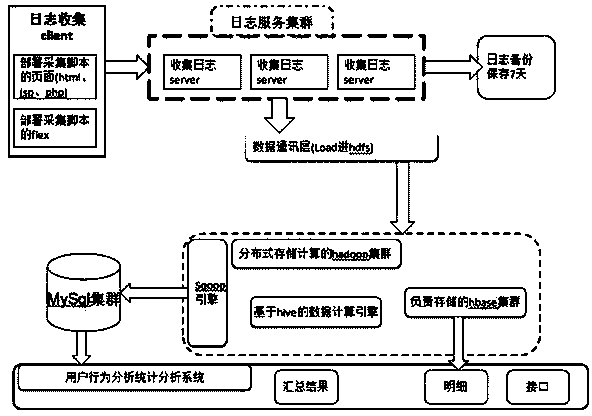
Method for monitoring and analyzing website user behaviors
The invention relates to a method for monitoring and analyzing website user behaviors. The method includes the steps of analysis object determination, page point insertion, log collection, HDFS storage, distributed summary calculation and result display. The method can be applied to websites with large page views (a hundred million page views per day), data such as website page views and click views can be accurately displayed in real time, and millisecond-level search of detail data can be achieved as well. The method is designed completely based on open source software development, a common pcserver and a common sata hard disk are adopted, redundant design is adopted in system architecture, and data will not be lost if any data node or the hard disk is damaged. All links can be automatically carried out, graphic monitoring can be achieved, and the method is easy to implement.
Owner:INSPUR SOFTWARE CO LTD
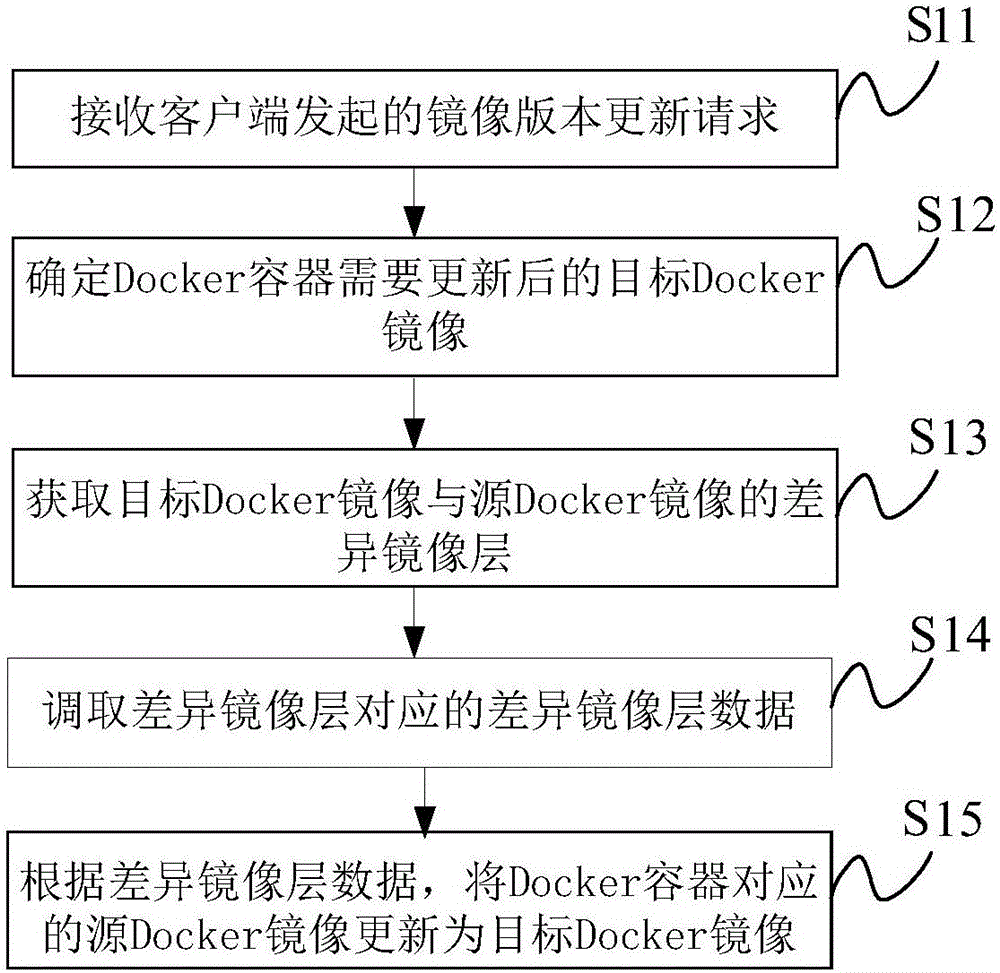
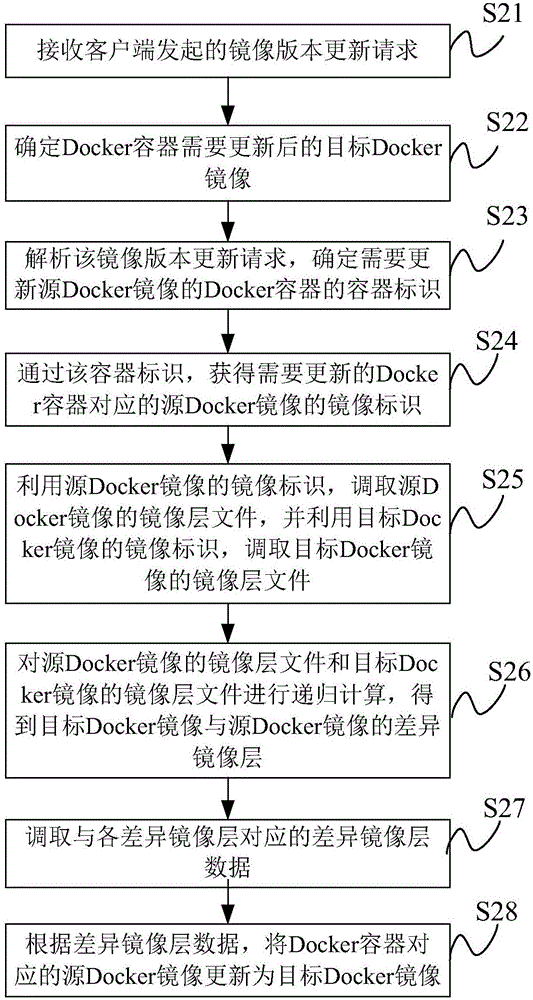
Content updating method and system for Docker container, and server
ActiveCN106528224ARealize online updateNot lostProgram loading/initiatingSoftware deploymentData lossMirror image
The invention provides a content updating method and system for a Docker container, and a server. When a Docker mirror image of a new version of a network product needs to be released, a developer can perform corresponding triggering operation at a client; the client initiates a corresponding mirror image version updating request to the server; and the server determines that the Docker container needs an updated target Docker mirror image according to the updating request, obtains a differential mirror image layer of the target Docker mirror image and a source Docker mirror image, and calls differential mirror image data corresponding to the differential mirror image layer from a mirror image warehouse. According to the method and the system, the source Docker mirror image corresponding to the Docker container is directly updated to the target Docker mirror image according to the differential mirror image layer data, the Docker container does not need to be restarted, namely, memory data in the Docker container is not lost, and normal external services of businesses are not influenced, so that online updating of the Docker container is realized.
Owner:TENCENT TECH (SHENZHEN) CO LTD
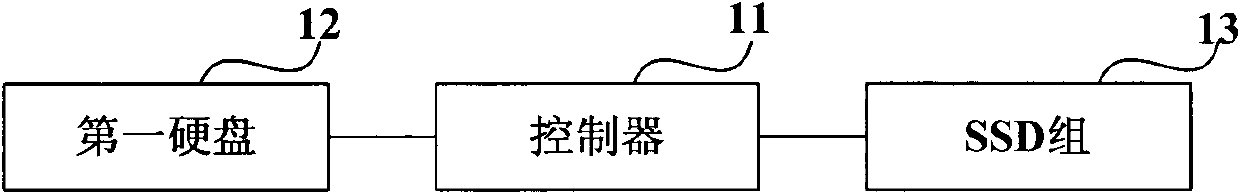
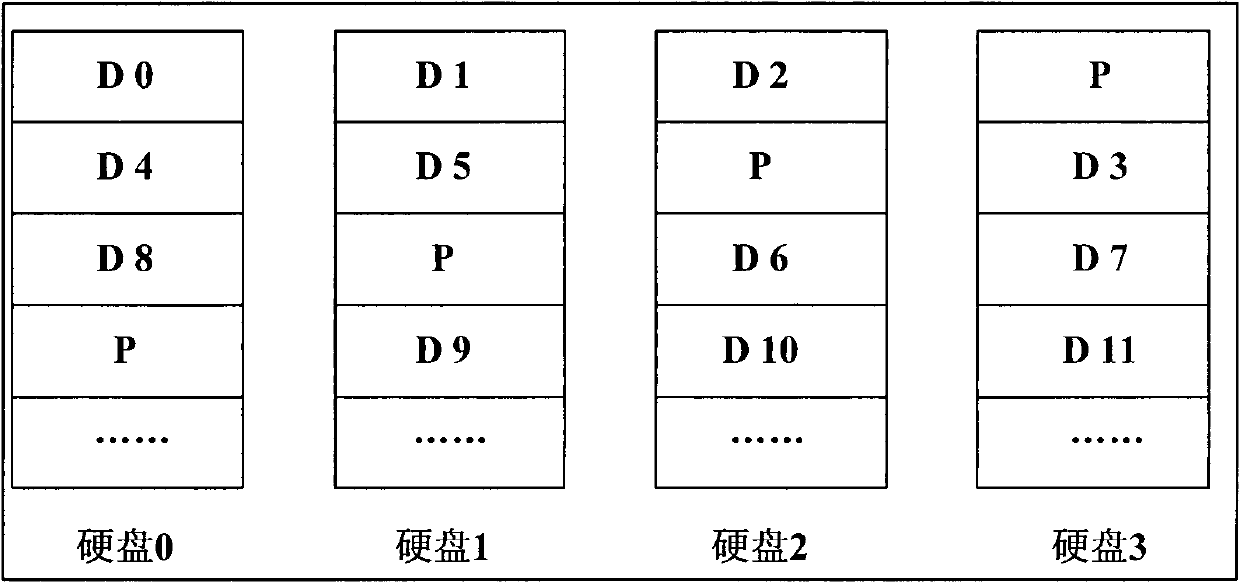
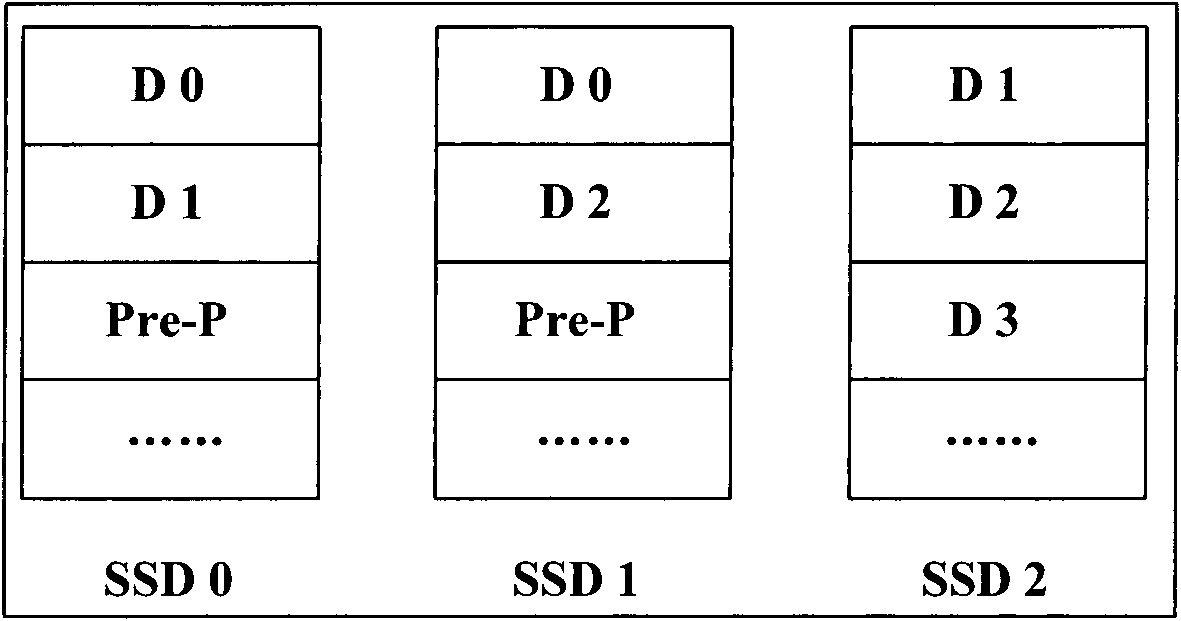
Storage system, method for reading data from storage system and method for writing data to storage system
InactiveCN102023809AReduce complexityImprove responsivenessInput/output to record carriersMemory adressing/allocation/relocationLogic cellSolid-state drive
The invention relates to a storage system, a method for reading data from the storage system and a method for writing data to the storage system. The system comprises a controller, a first hard disk divided with strips of redundant arrays of inexpensive disks and also a solid state disk set. The solid state disk set is assigned as the storage space corresponding to a logic unit number of the first hard disk, and is classified as a set of strips of redundant arrays of inexpensive disks. The strips of the redundant arrays of the inexpensive disks of the solid state disk set and those of the first hard disk have the same strip depth and the same strip size. The controller preserves Hash mapping tables used for expressing the mapping relation between the storage space and the solid state disk set. Hash mapping table items include indexes, pointer domains and bitmap domains. The controller also preserves analytic functions which are used for resolving an initial address of read-write requests to the indexes of the Hash mapping tables.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
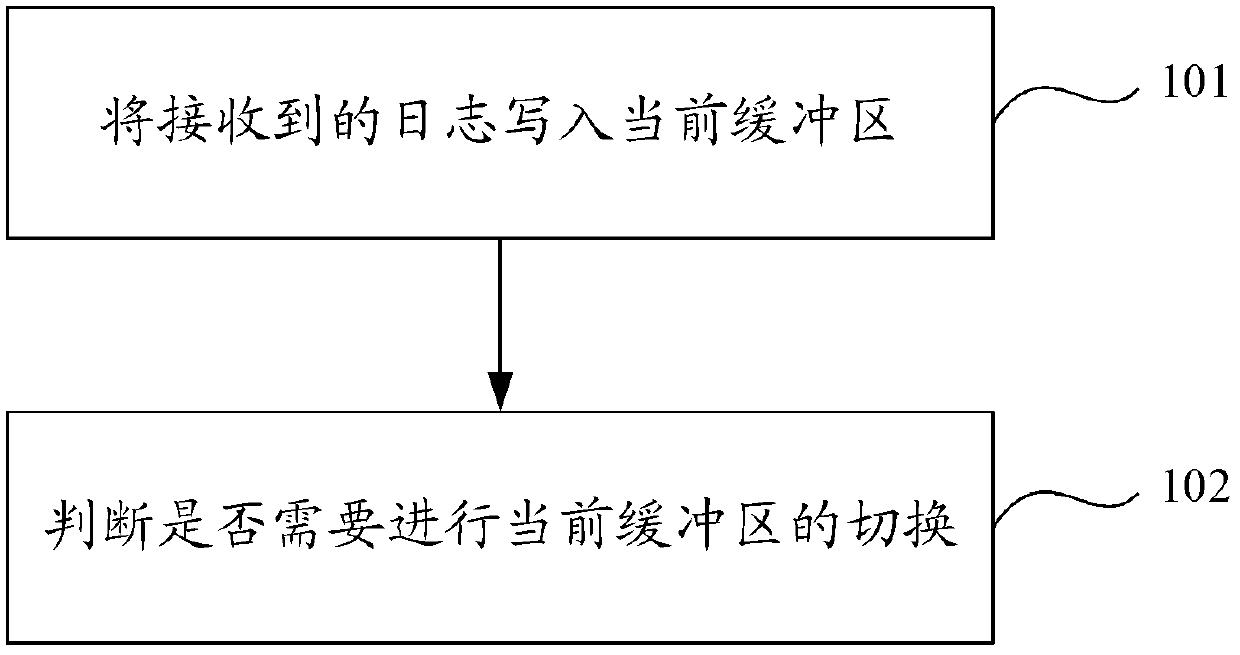
Method and device for processing client log
ActiveCN103309767AEnsure safetyData lostMemory loss protectionRedundant operation error correctionMmapInternal memory
The embodiment of the invention provides a method and a device for processing a client log. The method comprises the following steps of adopting a double buffering mechanism, previously setting two MMAP (map files or devices into memory) internal memories to be respectively used as a current buffering area and a standby buffering area, switching the standby buffering area to be the current buffering area when the current buffering area is filled, and transmitting a log stored in the filled buffering area to a distributed file system to be stored, so that the problem that the log processing capacity is limited because the quantity of the processed logs is limited by the limit space of the existing disk can be solved. Due to the characteristics of the MMAP technology, in the operation process, the data in the buffering area can be forcedly outputted to the disk by the system, so that even if a server is restarted or collapsed, the data stored in the buffering area can be restored through the disk without being lost, and the safety of the log stored in the buffering area can be guaranteed.
Owner:TAOBAO CHINA SOFTWARE
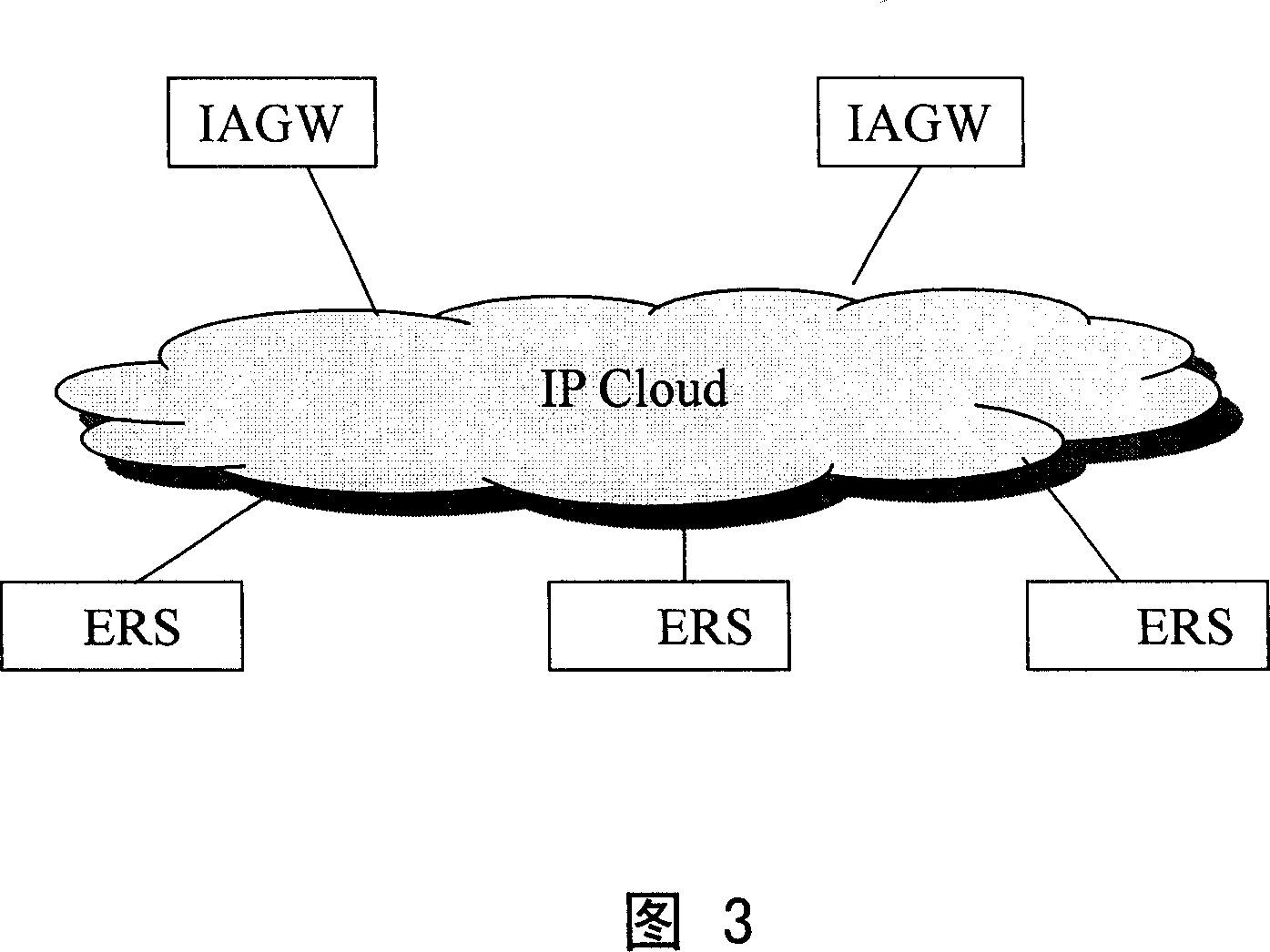
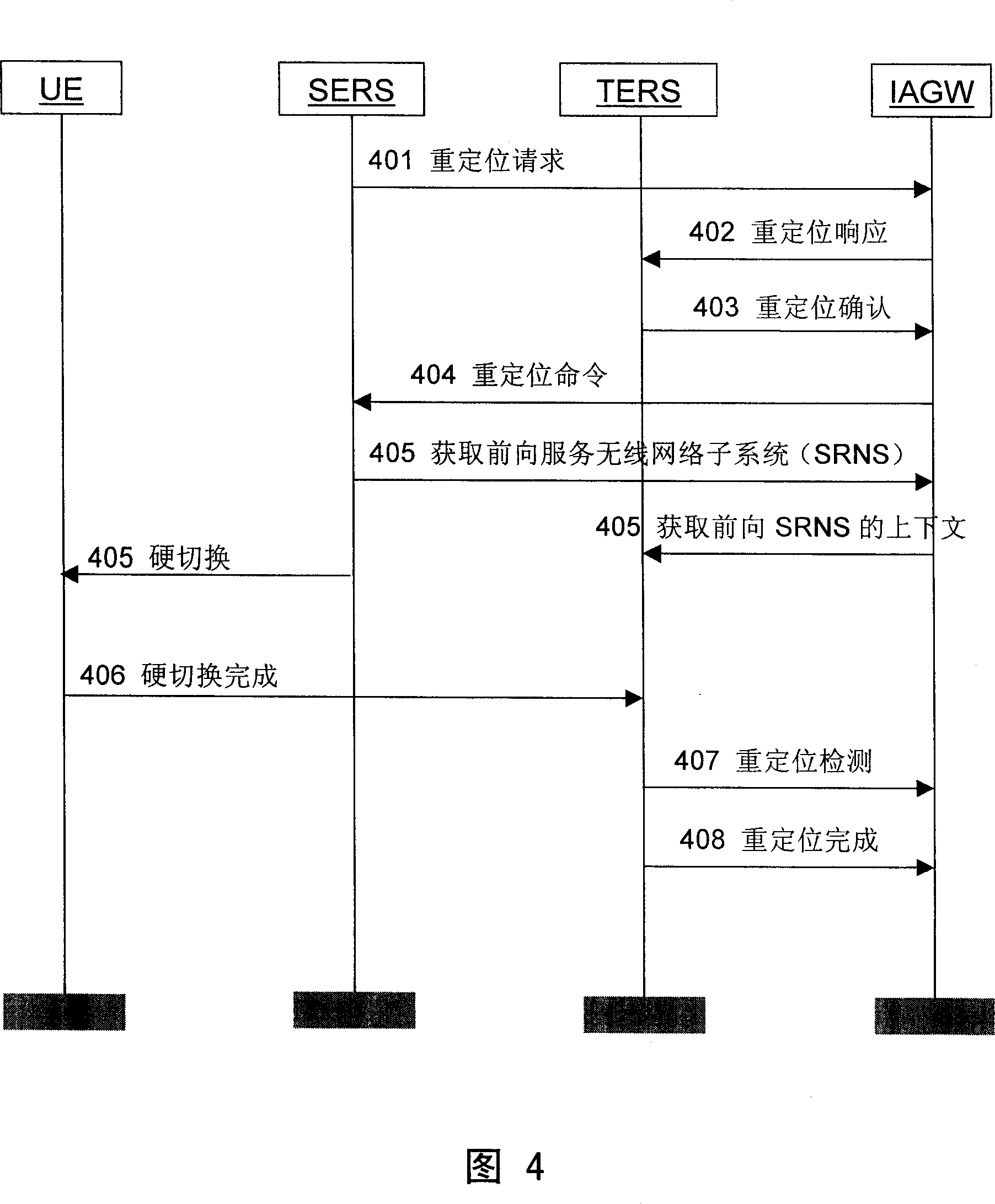
A method for switching among cells
ActiveCN1997204ANot lostIntegrity guaranteedNetwork traffic/resource managementRadio/inductive link selection arrangementsMaterials preparationInformation transmission
This invention discloses one method to realize area switching, which comprises the following steps: setting control panel and user panel agreement in base station and network gate; after receiving message, network gate processes buffer on sent data for materials preparation by aim base station; aim base station preserves materials to establish new user interface and establishing materials to fulfill UE area switching and the gate execution path and sending the data to aim station for information transmission between aim base station and UE.
Owner:HUAWEI TECH CO LTD
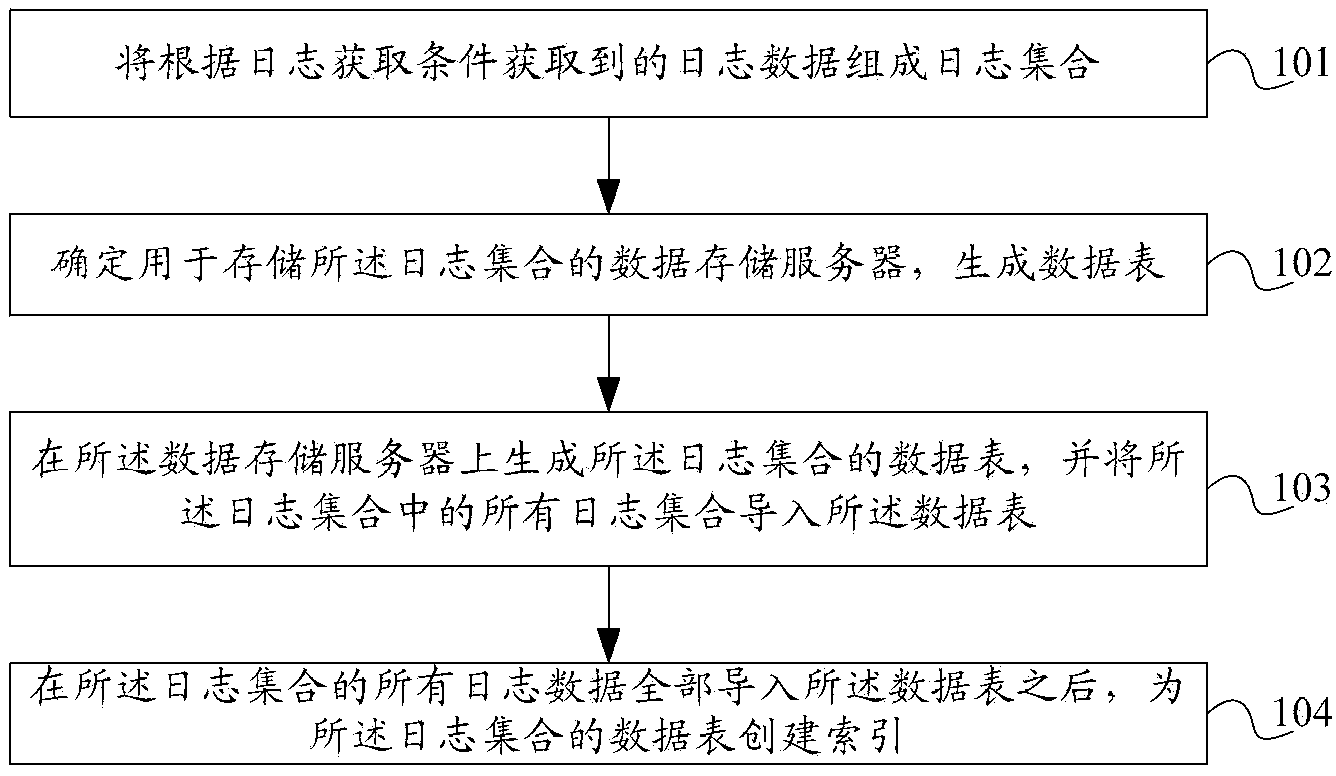
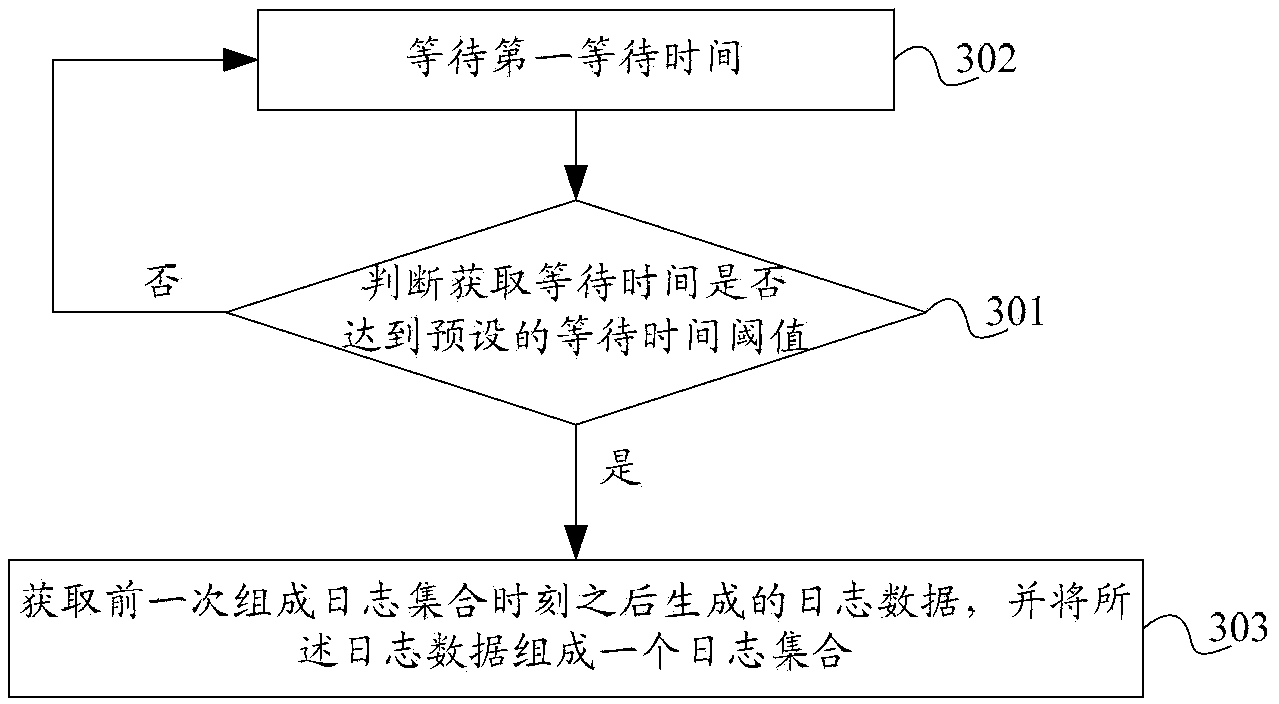
Method, log server and system for recording log data
The invention discloses a method, log server and system for recording log data. The method comprises that log data obtained according to the log obtaining condition forms a log set; a data storage server for storing the log set is determined; the log set is stored in the data storage server, and a data sheet of the log set is generated in the data storage server; and after all log data of the log set is introduced into the data sheet, an index is created for the data sheet of the log set. According to the method, log server and system, the storage speed of log data can be improved, a network platform can timely record a lot of log data that is generated in a short time, data loss is prevented, and delayed query time can be shortened.
Owner:ALIBABA GRP HLDG LTD
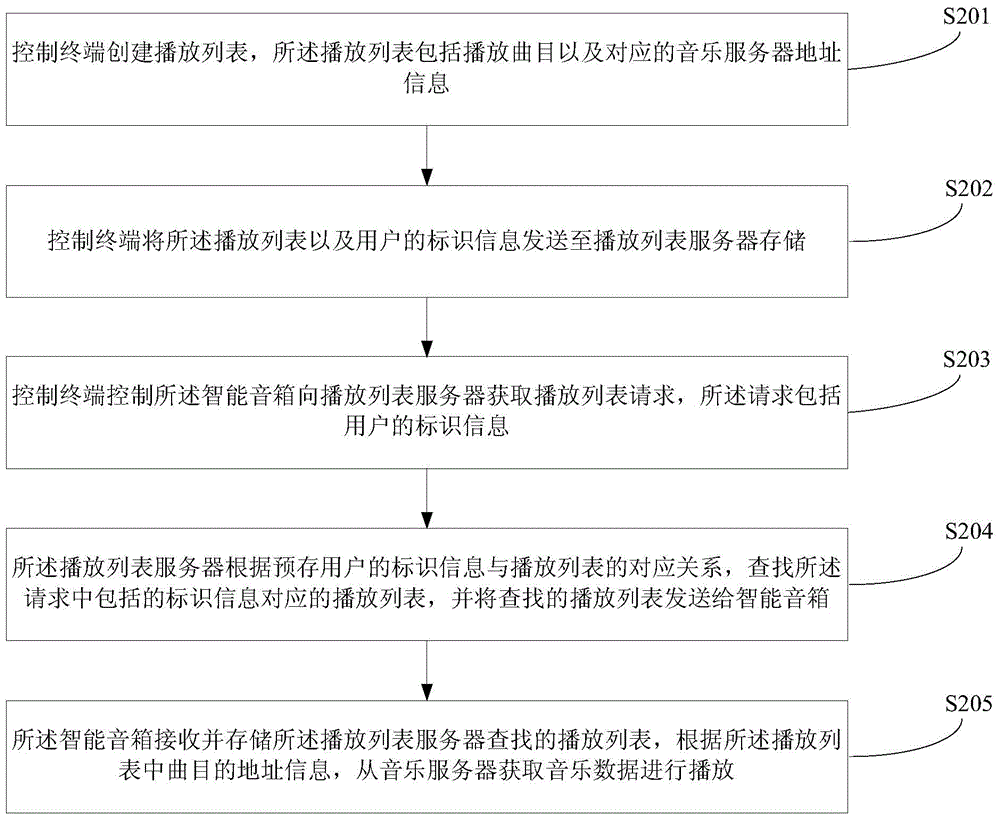
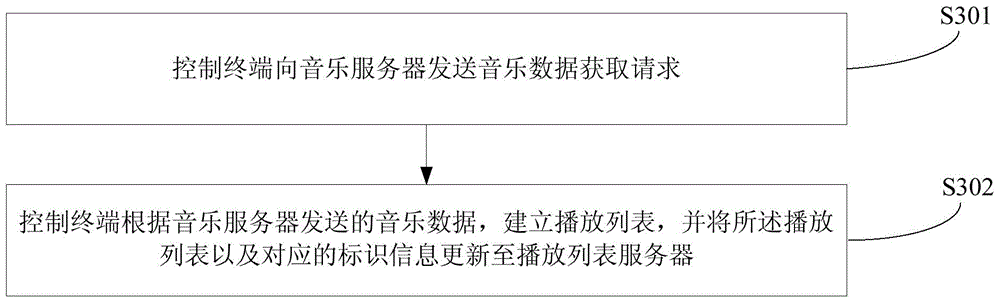
Music playing method and device of smart sound box
ActiveCN104601685AImprove securityEasy to controlTransmissionSpecial data processing applicationsThe InternetComputer terminal
The invention applies to the internet field, and provides a music playing method and a music playing device of a smart sound box. The music playing method of the smart sound box includes that a control terminal controls the smart sound box to obtain a playlist request for a playlist server, and the playlist request includes identification information of a user; the playlist server checks a playlist corresponding to the identification information included in the playlist request, and sends the playlist checked out to the smart sound box; the smart sound box receives and stores the playlist request checked by the playlist server, and obtains music data from a music server for playing according to address information of programs in the playlist. The music playing method and the music playing device of the smart sound box can conveniently control the playing of the programs in the playlist at different control terminals, can not lose the playlist when the control terminals or the smart sound box is damaged, and improve safety of the playlist data.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
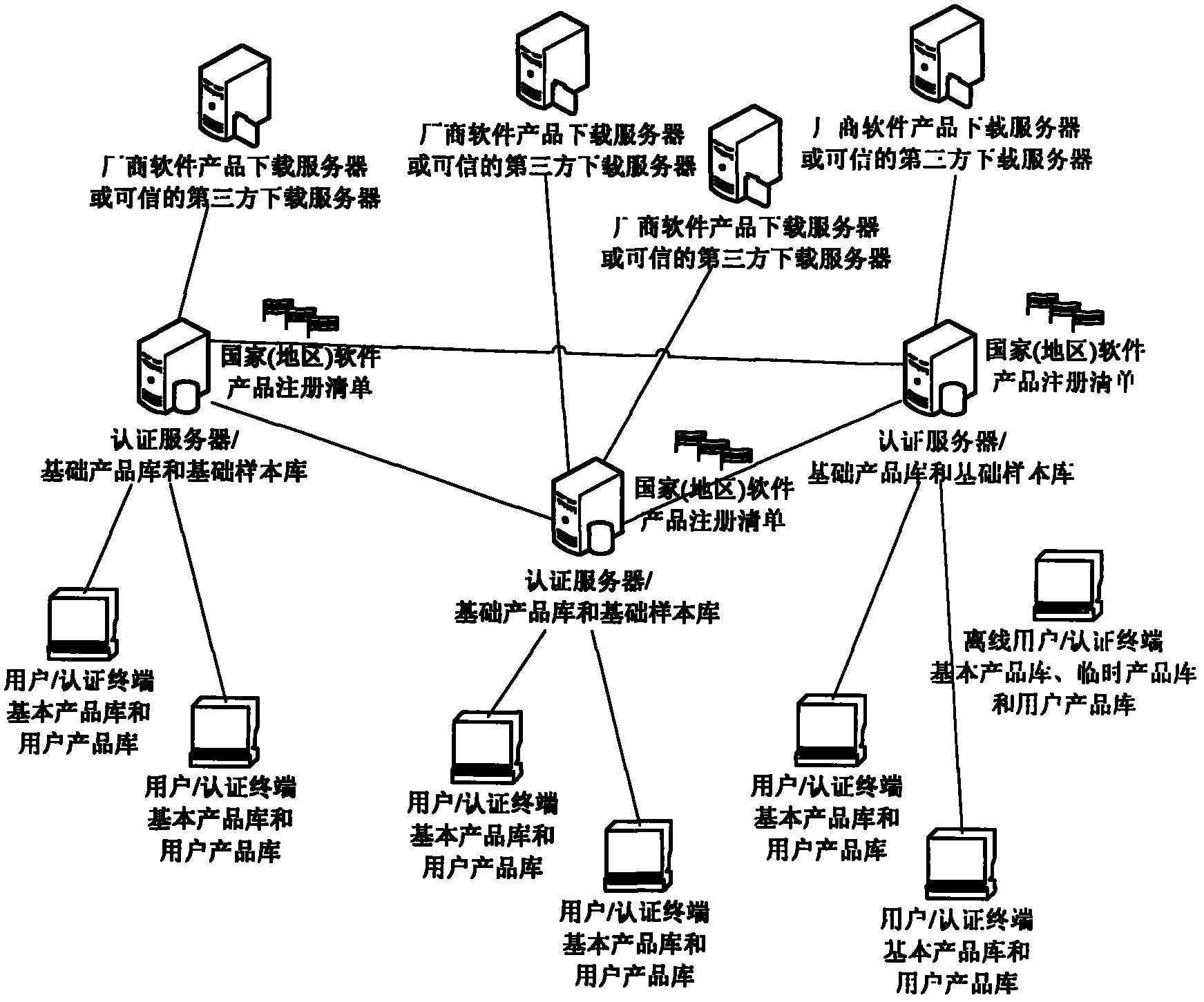
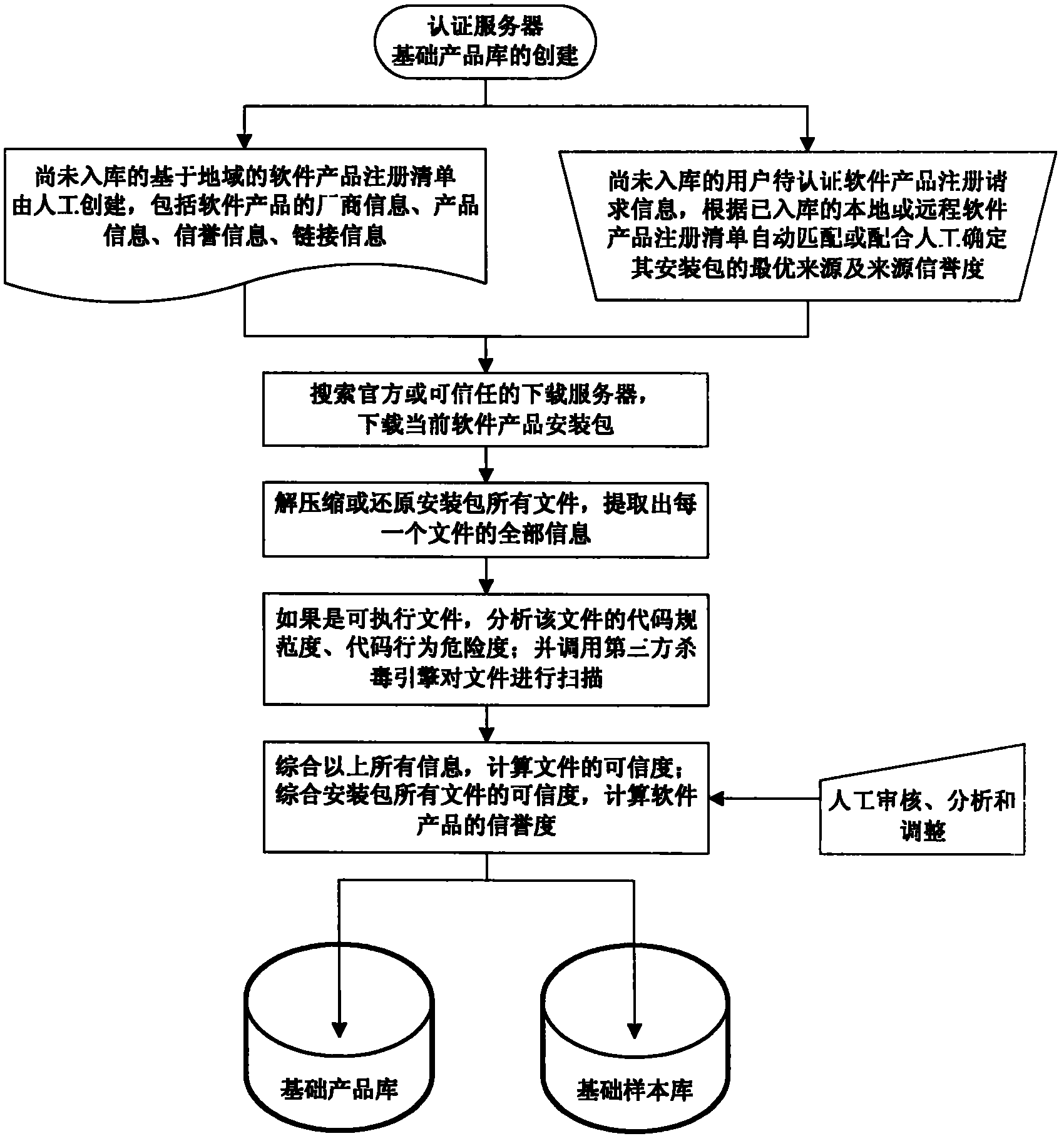
Distributed credibility authentication method and system thereof based on software product library
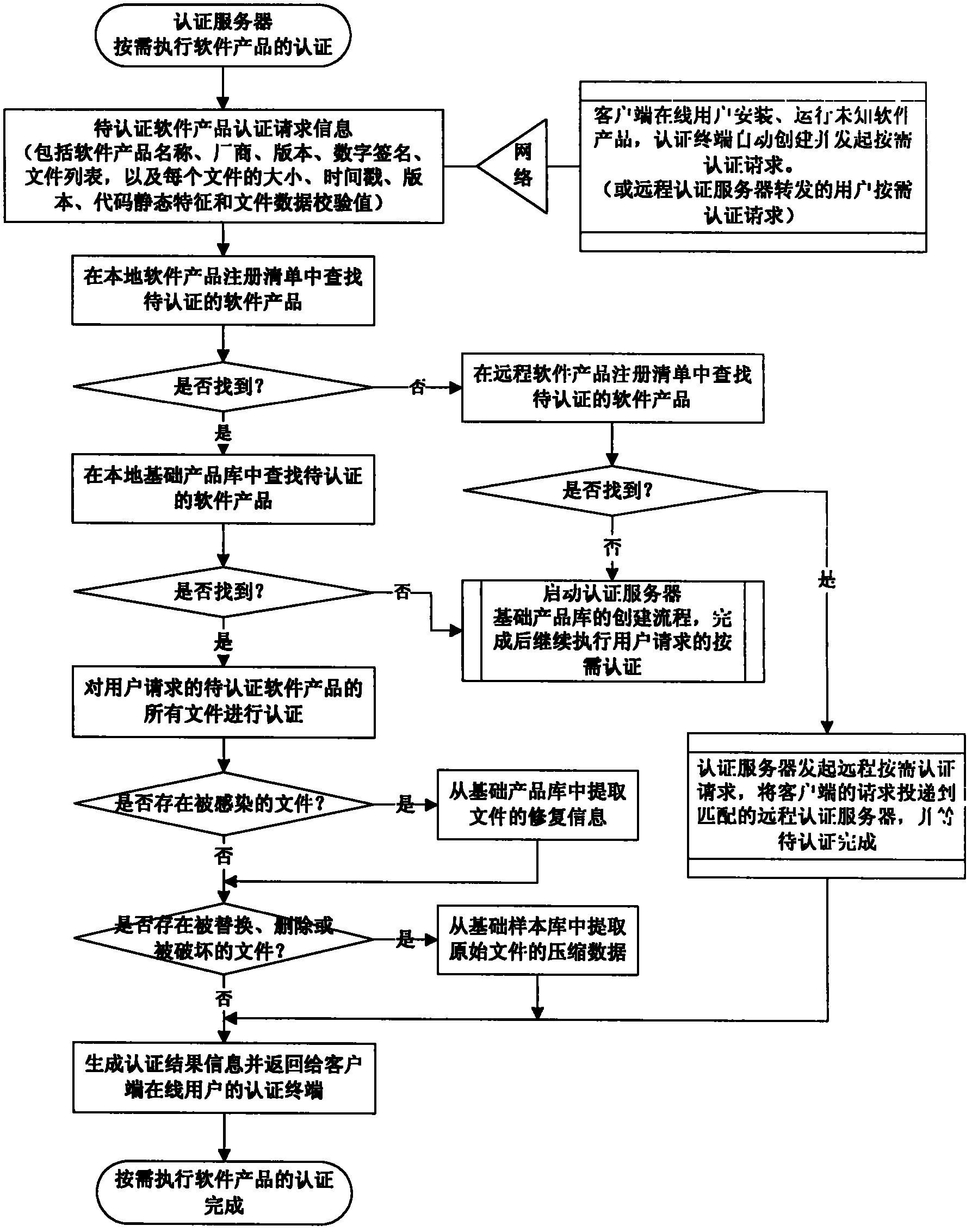
ActiveCN102195987AGuarantee data securitySolve practical problemsUser identity/authority verificationComputer security arrangementsOnline and offlineSecurity authentication
The invention relates to the technical field of security authentication, particularly to a distributed credibility authentication method and a system thereof based on a software product library. An on-line user initiates an authentication request to an authentication server through an authentication terminal, and the authentication server provides credibility for performing software product authentication as required or authenticating the user software product in distributed form to the on-line user according to the authentication request, and finally returns back the authentication result; an off-line user directly authenticates the credibility of the software product through the authentication terminal, and protects data security and information security of the user by switching among different security levels according to the authentication result or the user choices. In the method and the system provided by the invention, a software credibility authentication mechanism created by two ways of on-line and off-line can implement the credibility authentication of a plurality of security levels for the user so as to ensure the application security and the information security of user computers, and the user is allowed to run any software product at different security levels without any trouble, even the product contains real virus codes, the data security and the system stability of the user computer cannot be destroyed.
Owner:CHENGDU QIQIAO SOFTWARE
Failure diagnosis method and apparatus of hydroturbine based on acoustic emission technology
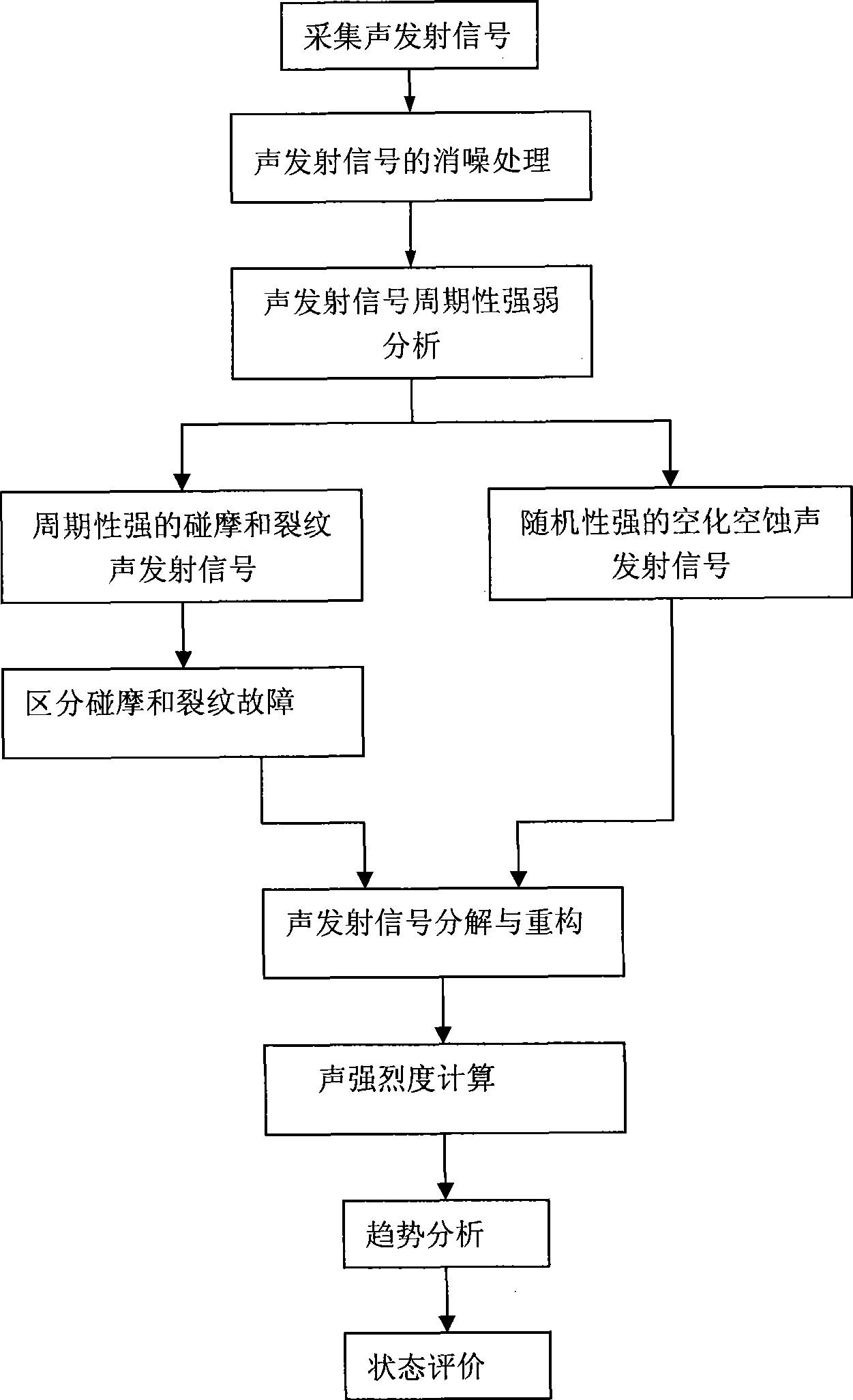
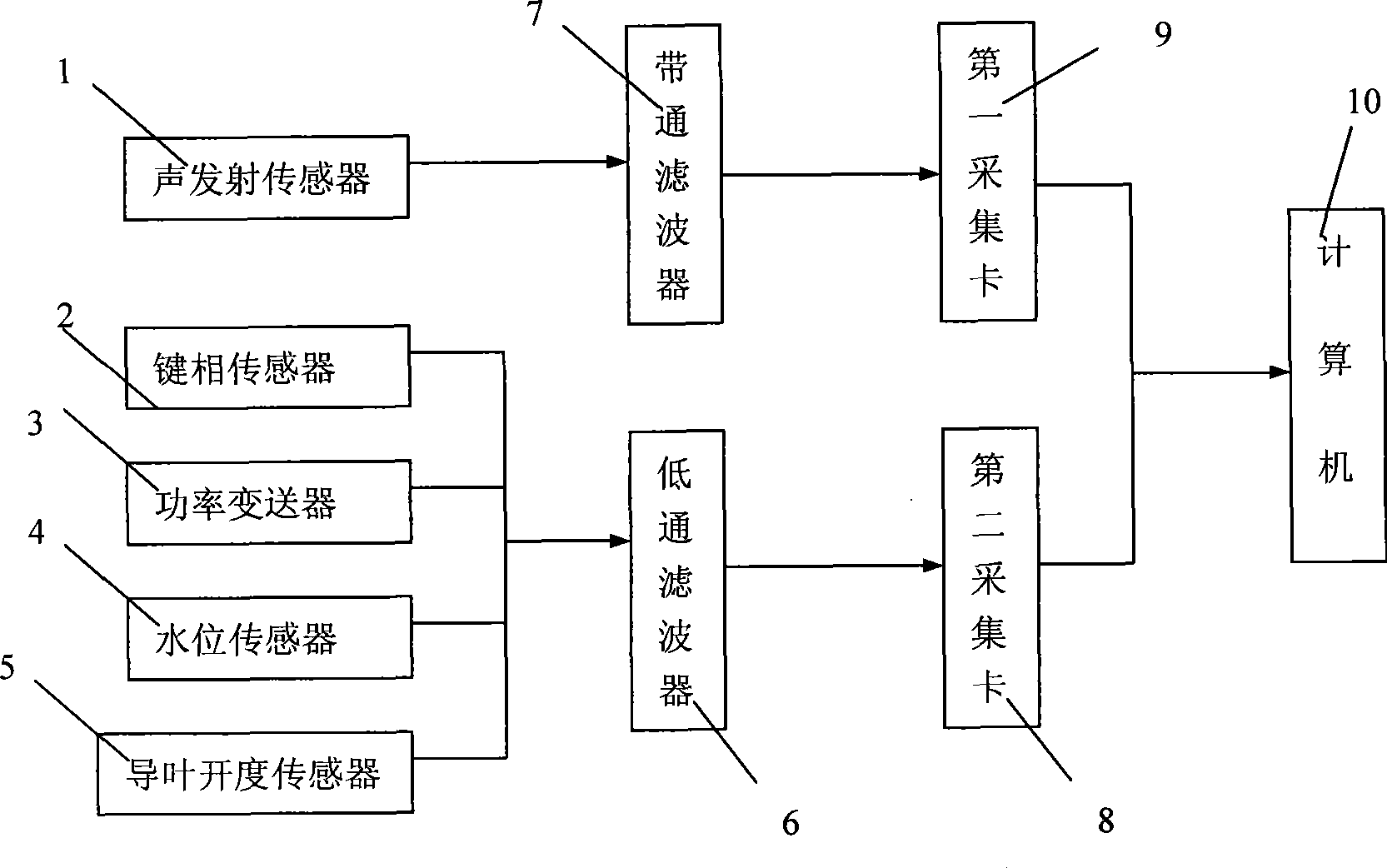
InactiveCN101435799AAvoid Low Frequency Noise InterferenceContinuous acquisitionAnalysing solids using sonic/ultrasonic/infrasonic wavesFrequency spectrumCavitation
The invention discloses a hydroturbine fault diagnosis method and a hydroturbine fault diagnosis device based on acoustic emission technology. The method applies the acoustic emission technology to the fault diagnosis of a hydroturbine set, obtains acoustic emission signals on a hydroturbine draft tube and guide vanes of a watermill chamber through an acoustic emission sensor, eliminates noise by adopting morphological filtering technology, adopts the pulse repetition rate to analyze the intensity of the periodicity of the acoustic emission signals, combines spectrum analysis and waveform nearness analysis to identify common rub impact, cracks as well as cavitation and cavitation erosion states, and applies wavelet packet technology for the decomposition and reconstruction of the signals to calculate the acoustic intensity of acoustic emission and perform the trend analysis of parameters of the acoustic intensity along with the working condition such as active power, water head and guide vane opening, further to comprehensively know the operation state and performances of a hydroturbine generator set and guide the operation of a hydroturbine.
Owner:TSINGHUA UNIV
Message transmission method and device for message middleware MQ
ActiveCN104731912AImprove reliabilityAvoid lossTransmissionSpecial data processing applicationsMessage queueMiddleware
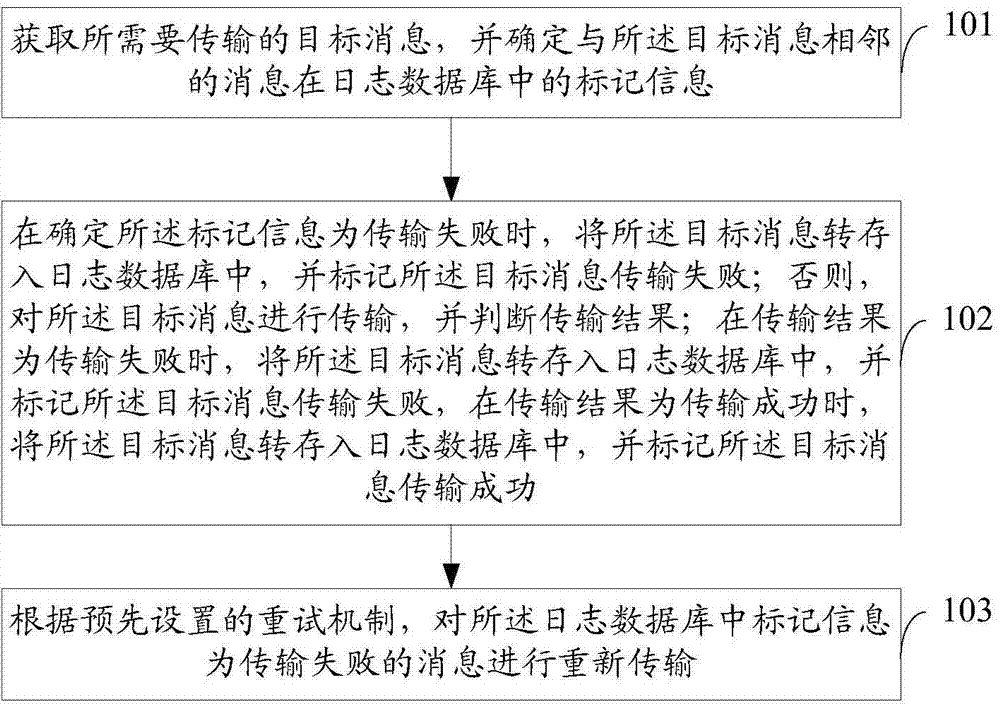
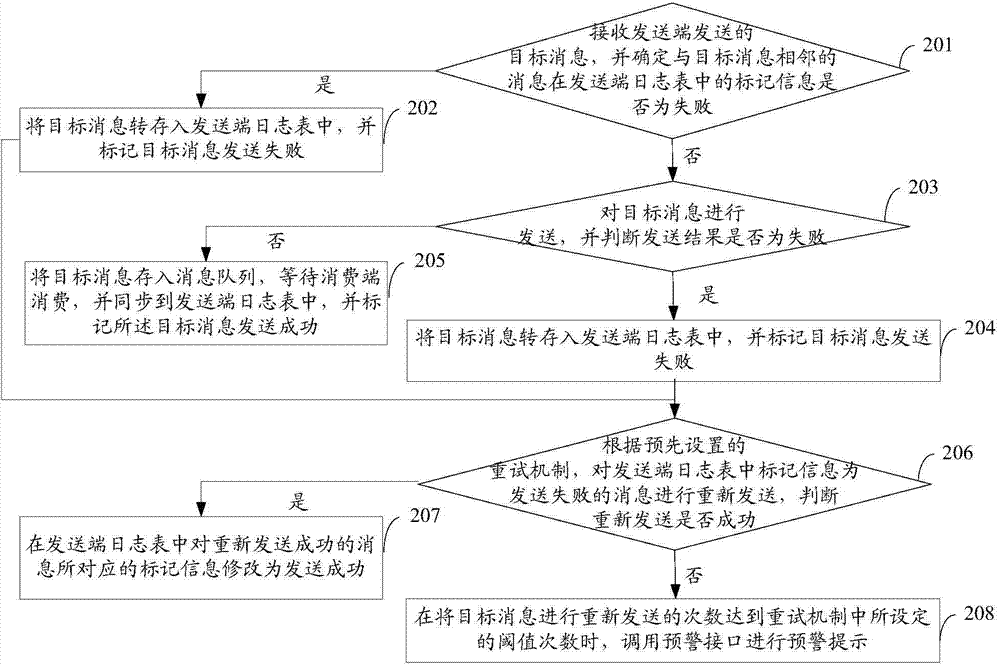
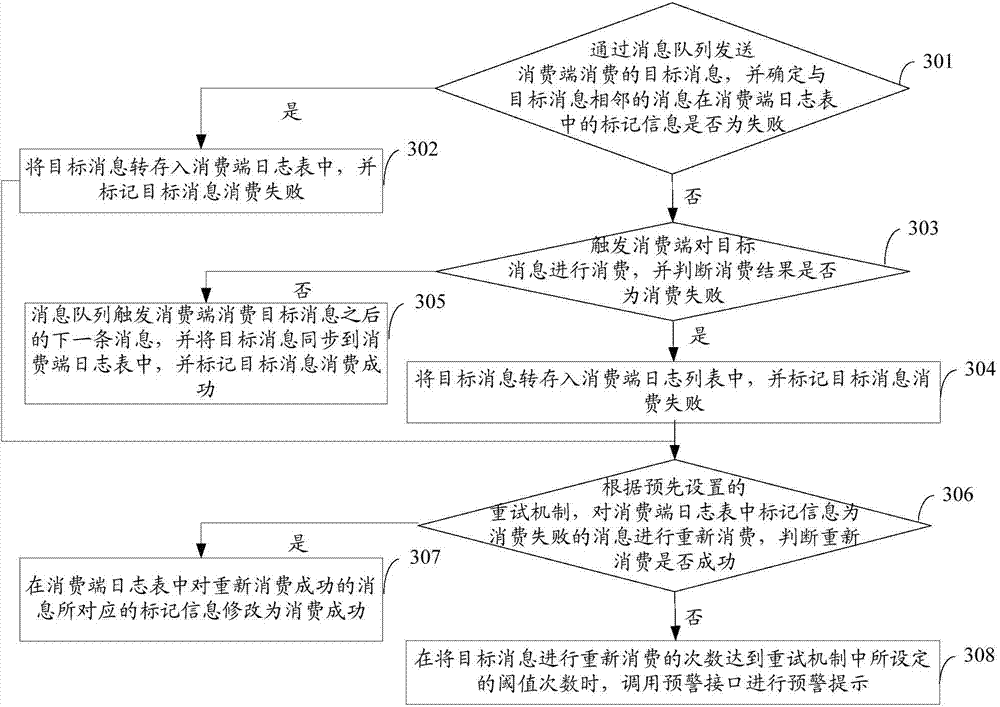
The invention provides a message transmission method and device for message middleware MQ. The method comprises the steps that a target message which needs to be transmitted is obtained, and whether marking information of a message which is adjacent to the target message in a log database is failed to transmit is confirmed; if yes, the target message is transferred to the log database; if no, the target message is transmitted, and a transmission result is judged; when the transmission result is that the transmission is unsuccessful, the target message is transferred to the log database, and the transmission of the target message is marked to be unsuccessful; when the transmission result is that the transmission is successful, the target message is stored in a message queue and synchronized in the log database, and the transmission of the target message is marked to be successful; according to a preset retry mechanism, the marking information marked as a message which is failed to transmit in the log database is transmitted again, so that the reliability of messages is improved.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Defect detecting method and defect detecting device
ActiveCN104616275ANot lostReduce contrastImage enhancementImage analysisVertical projectionProjection image
The invention provides a defect detecting method and a defect detecting device. The method comprises the steps of acquiring an image of a region of interest (ROI); setting two threshold values, performing binarization processing on the ROI image according to normal pixel points of the ROI image with the pixel value within the two threshold values and defect pixel points of the ROI image with the pixel value beyond the two threshold values, so as to obtain a binarization image; performing vertical projection and / or horizontal projection on the defect pixel points of the acquired binarization image so as to obtain projection images of the defect points; and detecting the defects from the projection images. The method can realize detection of low contrast defects.
Owner:BEIJING C&W ELECTRONICS GRP +1
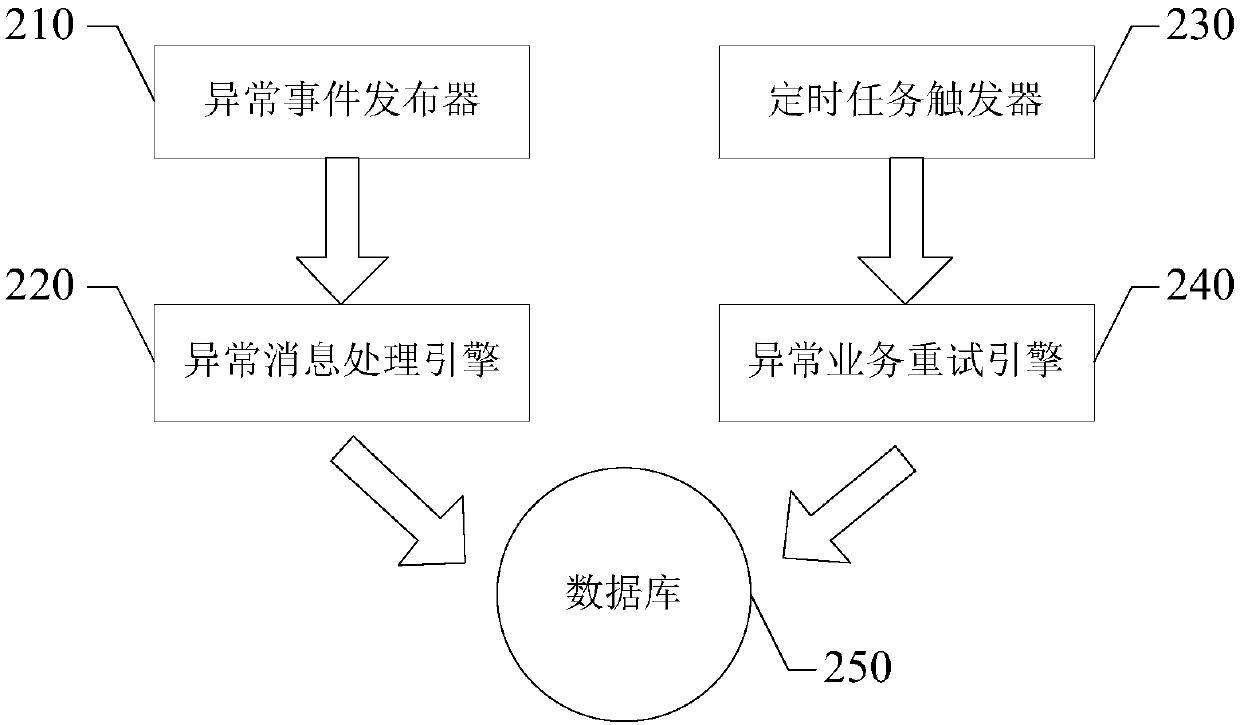
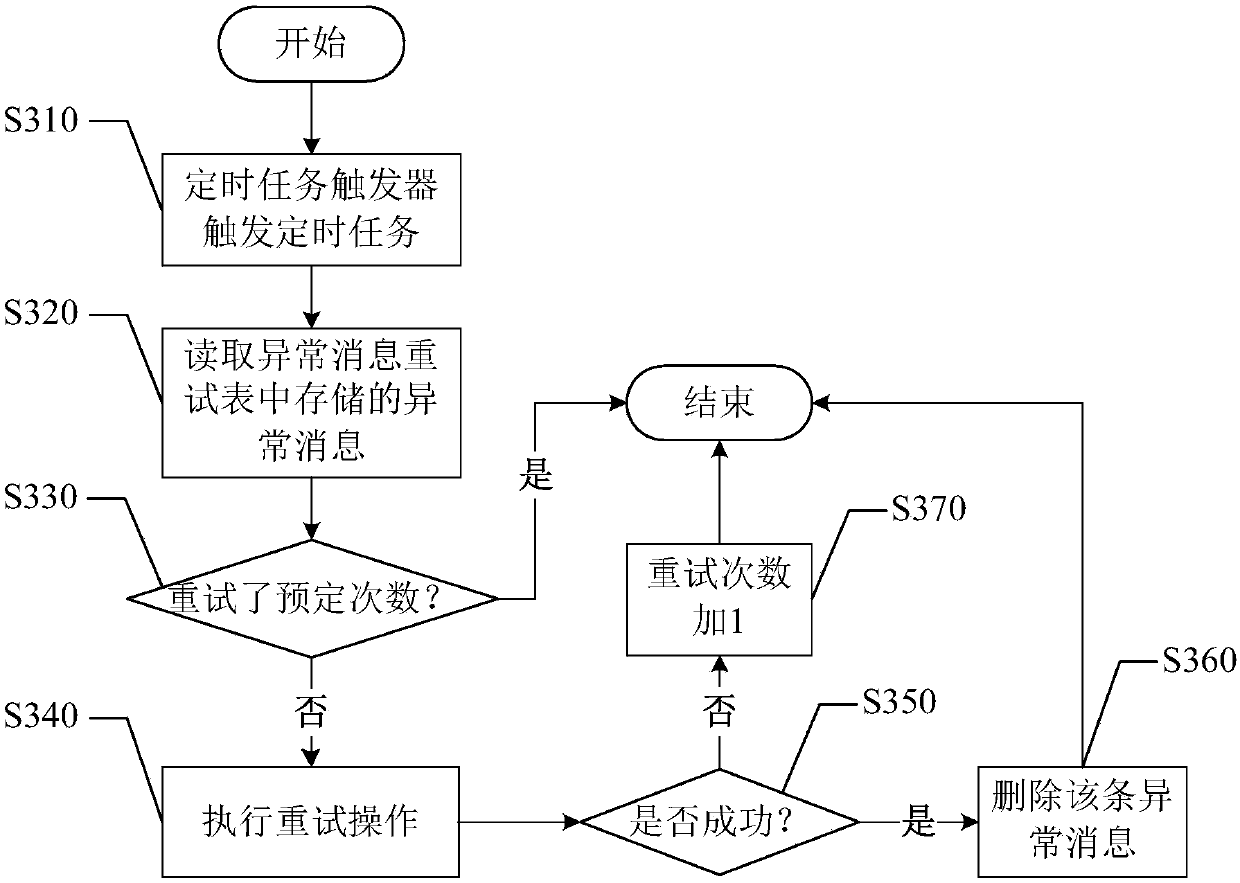
Abnormal event processing method and apparatus, electronic device and storage medium
ActiveCN107908494AImprove processing efficiencyNot lostNon-redundant fault processingComputer hardwareMaterial resources
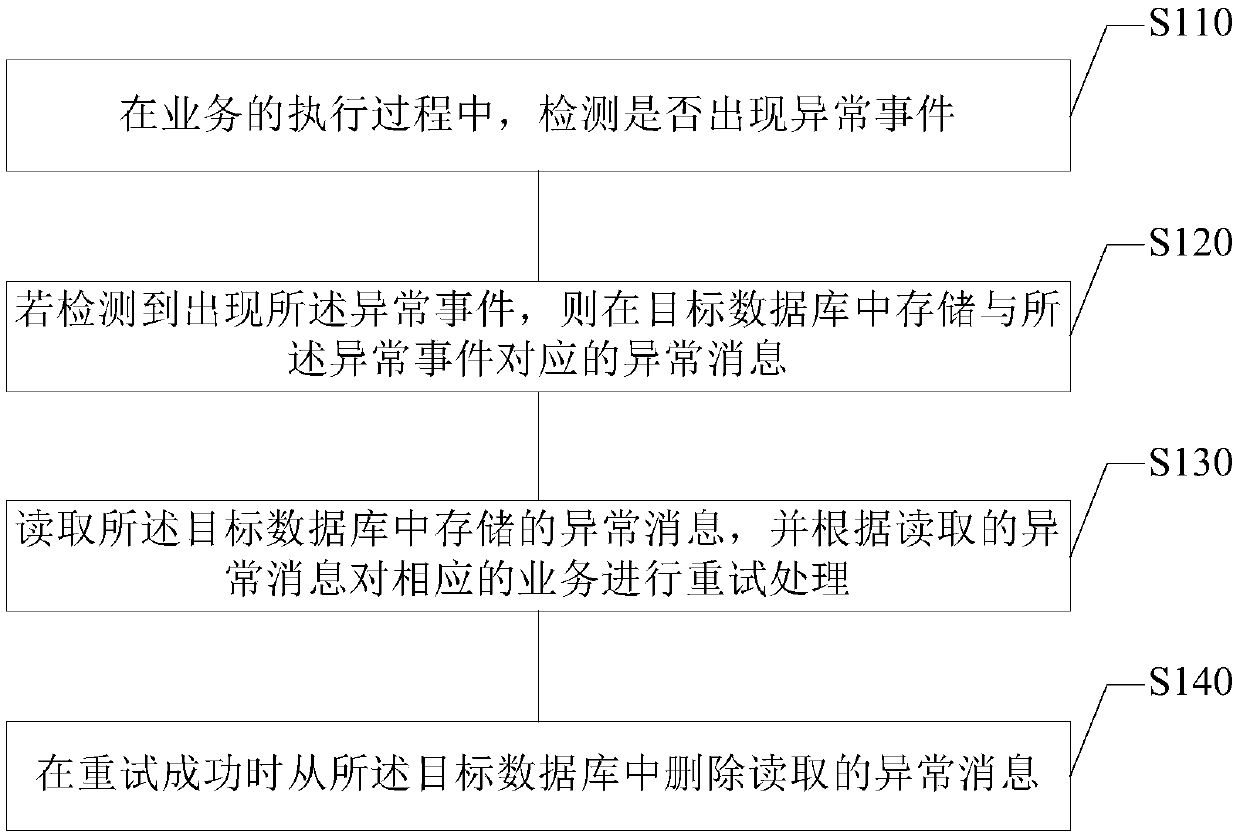
Embodiments of the invention provide an abnormal event processing method and apparatus, an electronic device and a storage medium, and relate to the technical field of data processing. The method comprises the steps of detecting whether an abnormal event occurs or not in a business execution process; if it is detected that the abnormal event occurs, storing an abnormal message corresponding to theabnormal event in a target database; reading the abnormal message stored in the target database, and according to the read abnormal message, performing retry processing on corresponding businesses; and when the retry succeeds, deleting the read abnormal message from the target database. According to the technical scheme, the abnormal businesses can be automatically retried without manual intervention, so that the manpower and material resource input is greatly reduced and the abnormal event processing efficiency can be improved.
Owner:TAIKANG LIFE INSURANCE CO LTD
Security attack alarm positioning system based on Spark big data platform of Tachyou
InactiveCN105207826AEfficient use ofImprove good performanceData switching networksReal time analysisData platform
The invention discloses a security attack alarm positioning system based on a Spark big data platform of Tachyou and belongs to the field of big data and information security. The system comprises an acquisition module, a security attack alarm positioning module and a view module. The acquisition module gathers log information in an enterprise information system, preprocesses and pushes the log information to the security attack alarm positioning module in real time, the security attack alarm positioning module performs real-time analysis to generate alarm information, and sends the alarm information to a view front end page. Compared with the prior art, the security attack alarm positioning system can solve the problem that a large number of logs are difficult to analyze in real time and has excellent practicality and value of popularization and application.
Owner:NANJING LIANCHENG TECH DEV
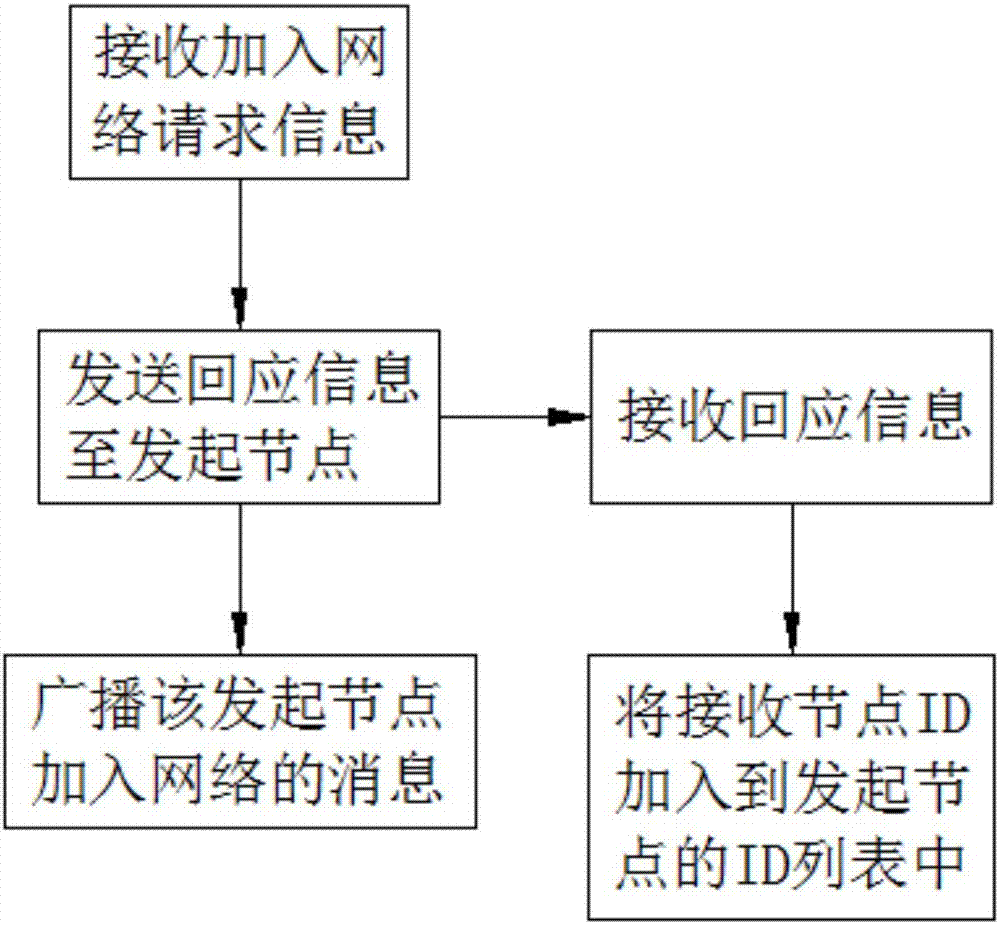
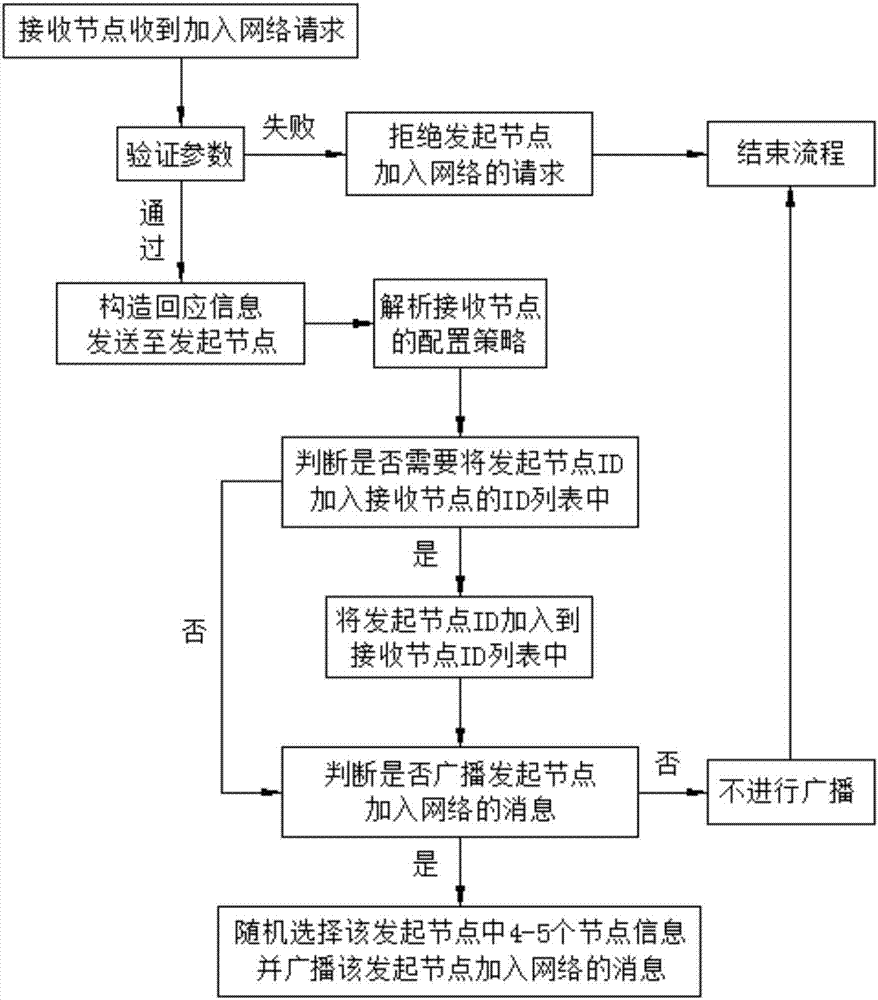
Method for realizing distributed file storage based on block chain
InactiveCN107995270AEnsure safetyGuaranteed integrity and securityUser identity/authority verificationSpecial data processing applicationsBlockchainNetwork architecture
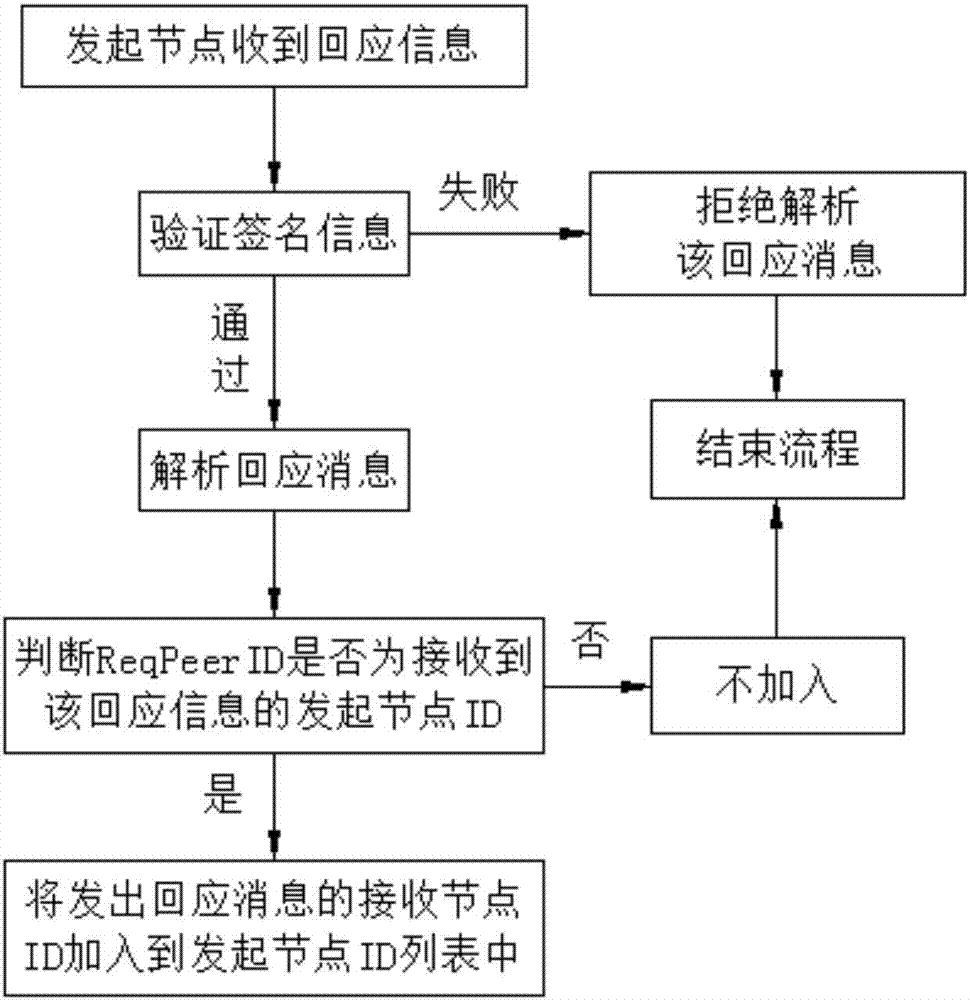
The invention discloses a method for realizing distributed file storage based on a block chain. The method comprises the following steps: setting a node sending network access request information as an initiating node, and setting a node receiving the network access request information as a receiving node; constructing, by the receiving node receiving the network access request information, response information, sending the response information to the initiating node, and broadcasting a message indicating that the initiating node accesses the network; and adding, by the initiating node receiving the response information, the ID of the receiving node to an ID list of the initiating node. According to the method disclosed by the invention, the P2P network architecture based on the Internet is adopted, each node located in the same network is mutually equivalent and jointly provides and jointly enjoys the network service, there is no special node, the topology between the nodes is organized not based on geographical positions, the nodes interconnected with a certain node may be far away from each other on the geographical positions; and the nodes interactively coordinate and cooperatively handle services, and the method has the advantages of reliability, decentralization and openness.
Owner:成都赤乌软件技术有限公司
Secondary door access system adopting biological character identification technology and control method
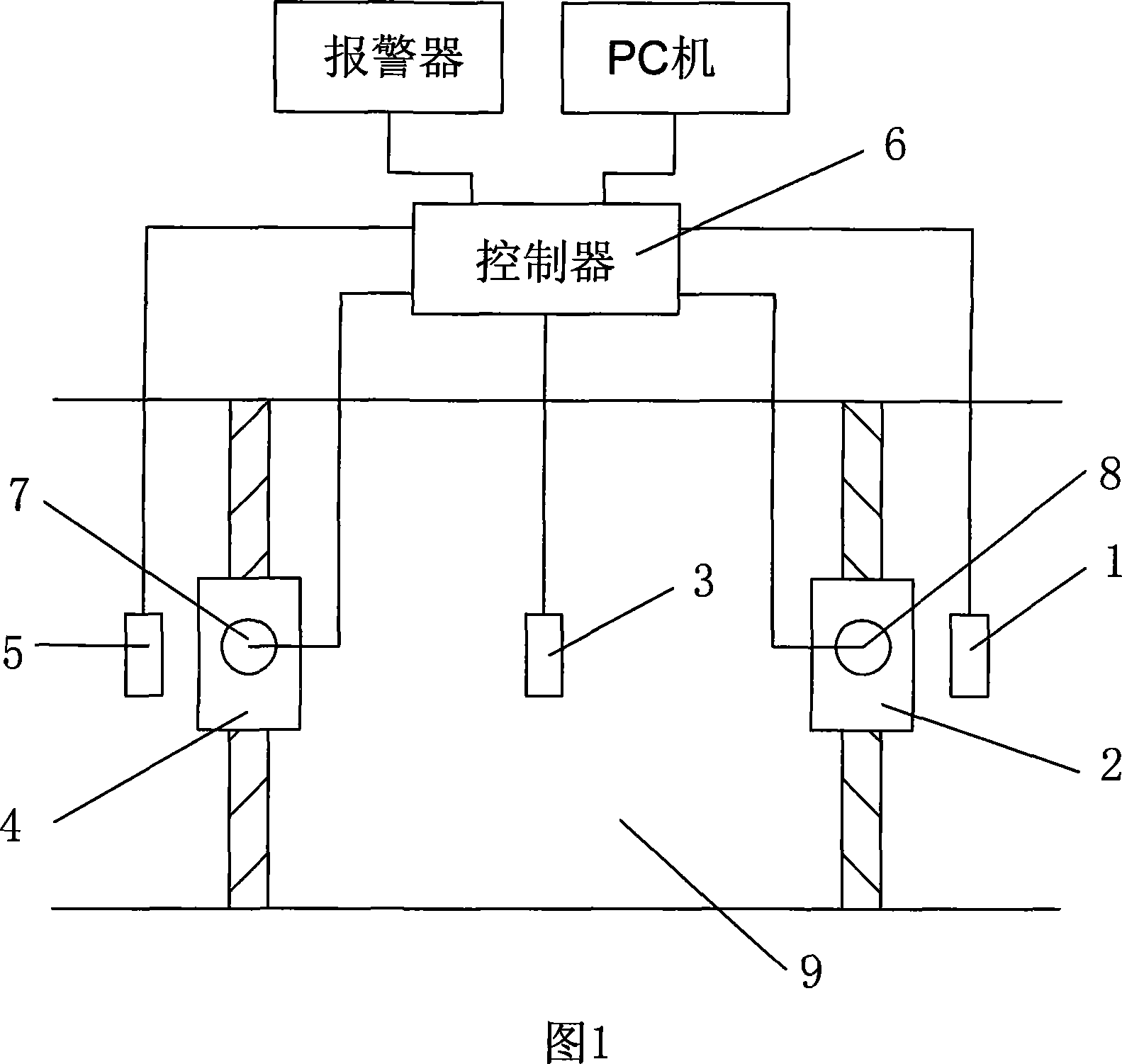
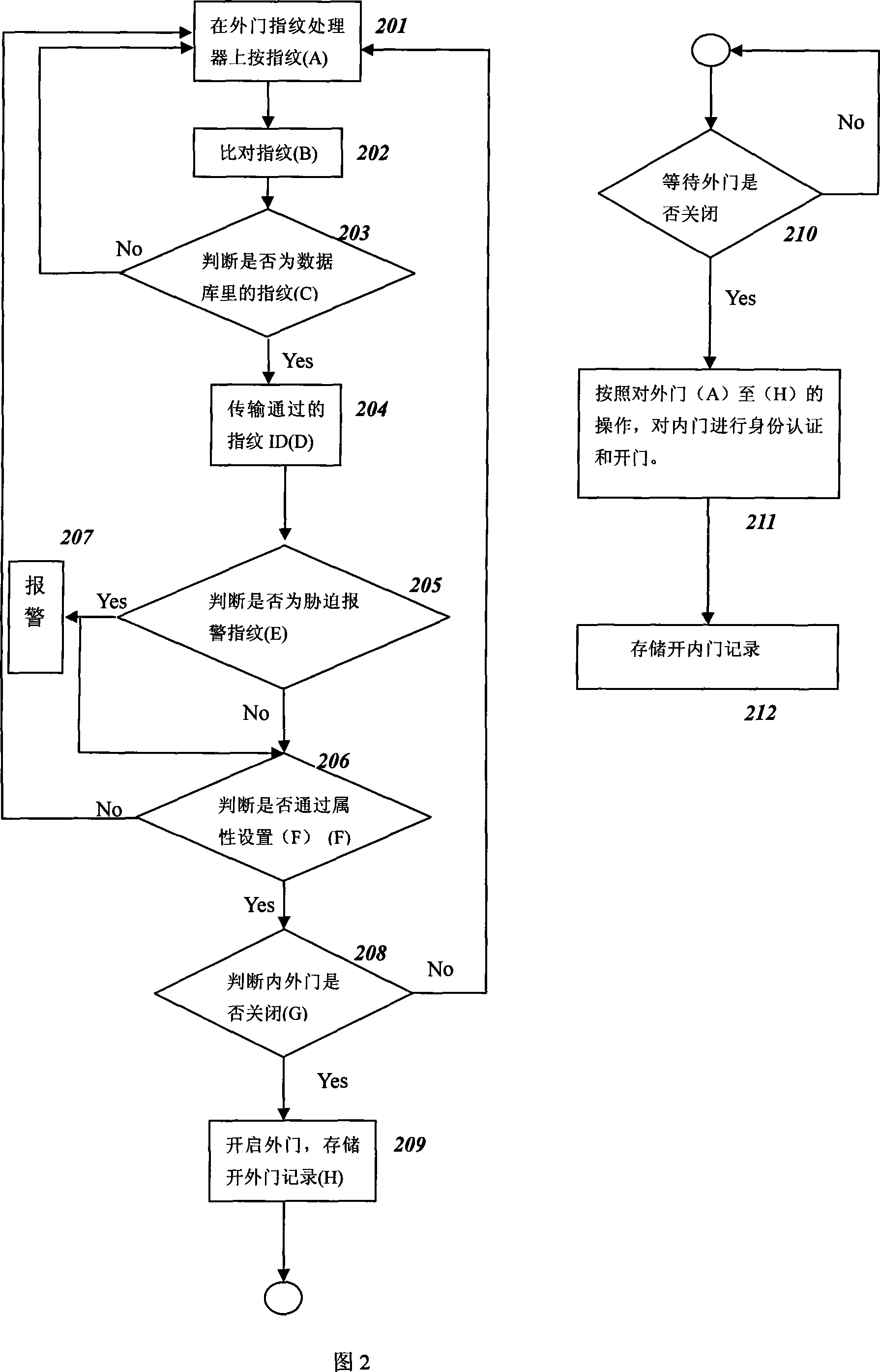
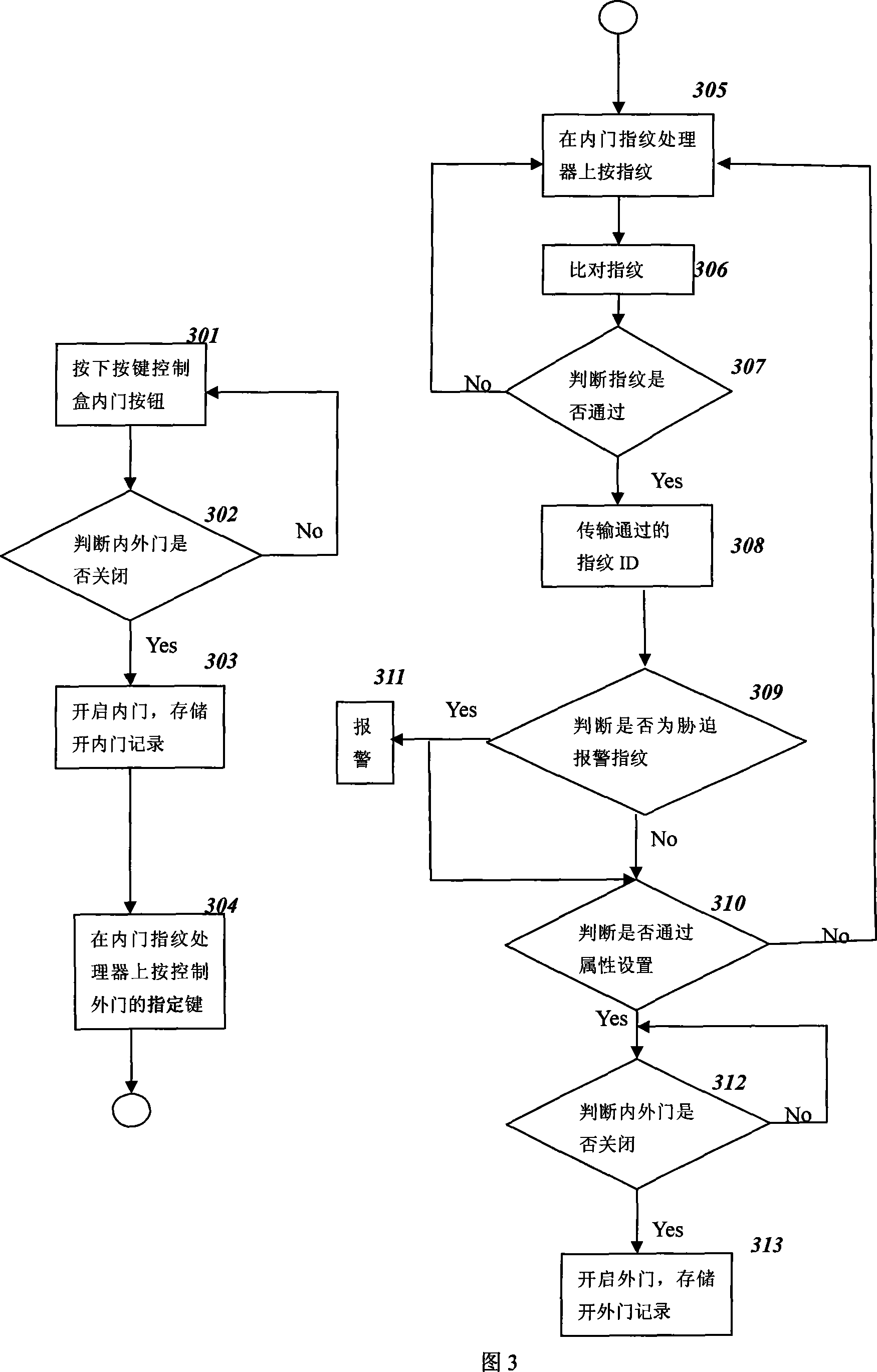
InactiveCN101059878AEnsure safetyGuaranteed accuracyCharacter and pattern recognitionIndividual entry/exit registersGeneral biologySwitch box
The invention relates to a two-door gate inhibition system and a control method, based on biology character recognize technique, comprising a biology character gate inhibition device, a controller, an electric lock, a switch box, a biology character register terminal, and a gate inhibition system server, wherein the biology character register terminal registers the biology character information, to record and build database for general biology character and alarm biology character, when passes two doors, the gate inhibition device checks and receives biology character, to extract and compare the biology character information, and when the biology character information is authorized one, to send an outer door open request to the controller, and when the biology character information is alarm biology character, send out an outdoor door open request and an alarm signal. The invention provides forced alarm method, to open door with starting alarm response, to alarm on time and protect owner.
Owner:ZHEJIANG MIAXIS TECH CO LTD
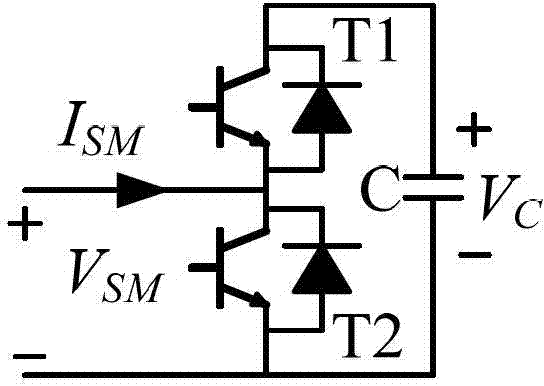
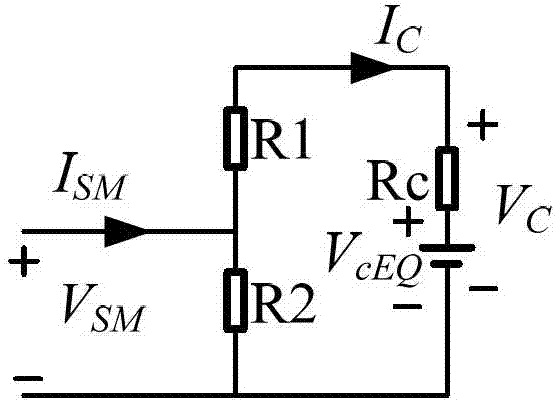
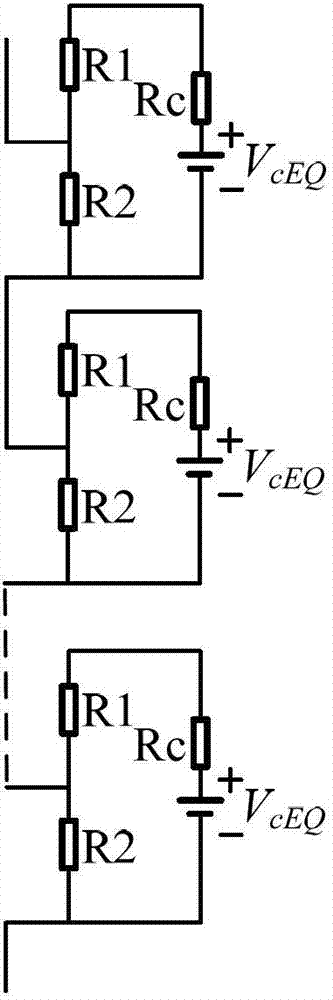
Modular multilevel converter (MMC) topology converter efficient electromagnetism transient state simulation method
ActiveCN103116665AReduce interface callsImprove Simulation EfficiencySpecial data processing applicationsTransient stateComputer Aided Design
The invention discloses a modular multilevel converter (MMC) topology converter efficient electromagnetism transient state simulation method. The method comprises the following steps: (1) building a thevenin equivalent circuit of a submodule and acquiring the hevenin equivalent circuit of a series subnodule, (2) opening power system computer aided design (PSCAD) and operating Fortran script editing user-defined module, (3) replacing at least one submodule by using the user-defined module, (4) using status bit to show insulated gate bipolar transistor (IGBT) status in the user-defined module of the PSCAD, (5) and figuring submodule capacitor voltage and submodule current by using a difference equation. The method reduces the number of nodes of a MMC topology converter model, and is quick in simulation speed and high in efficiency.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
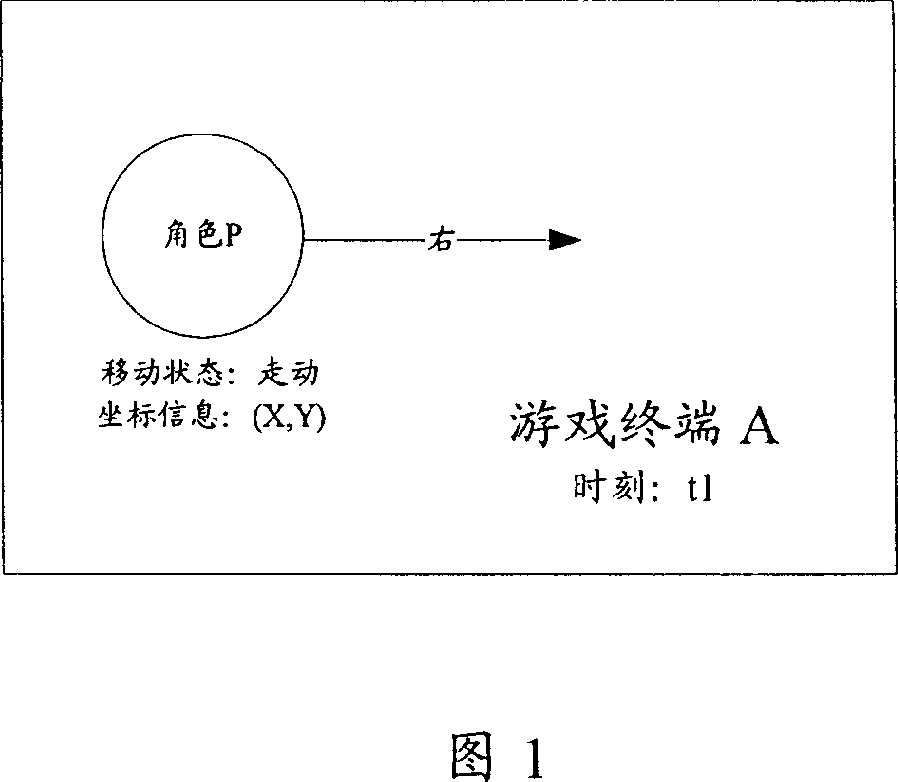
Method for shifting roles in netowrk games
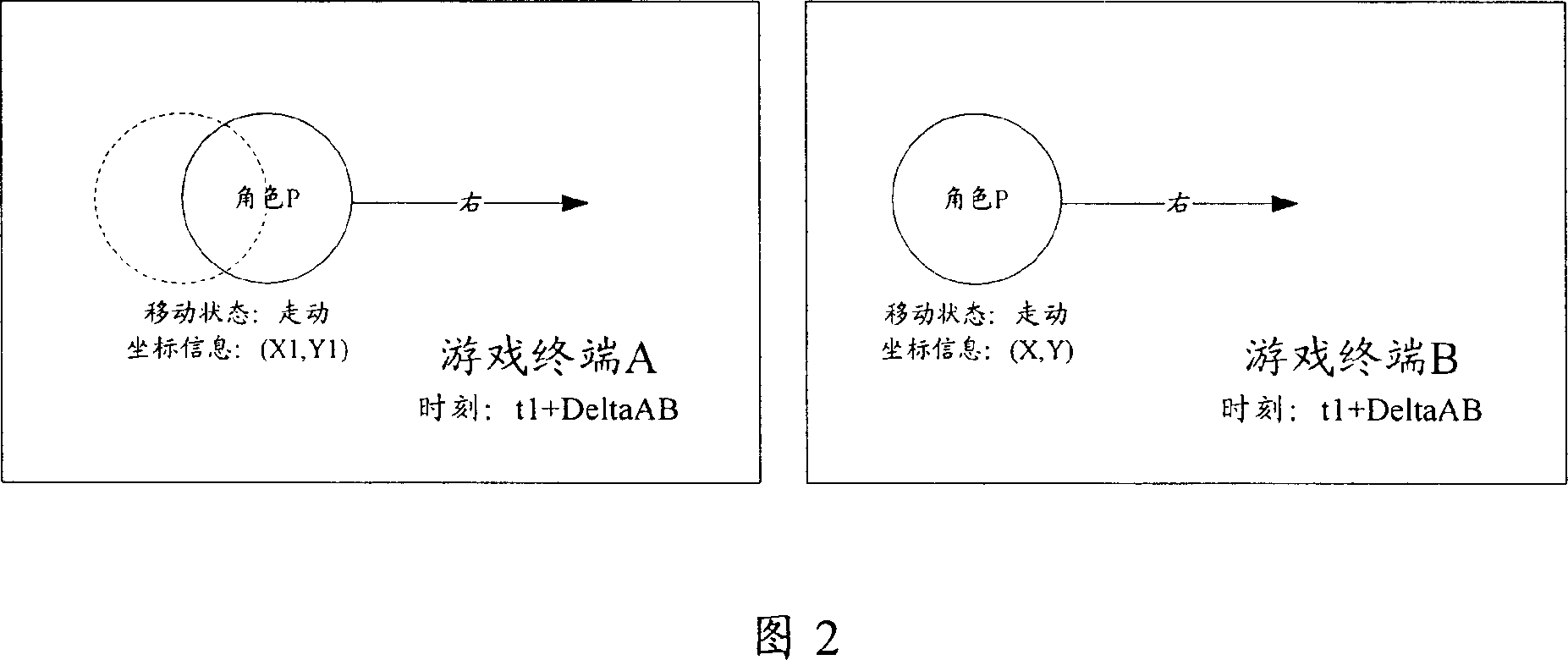
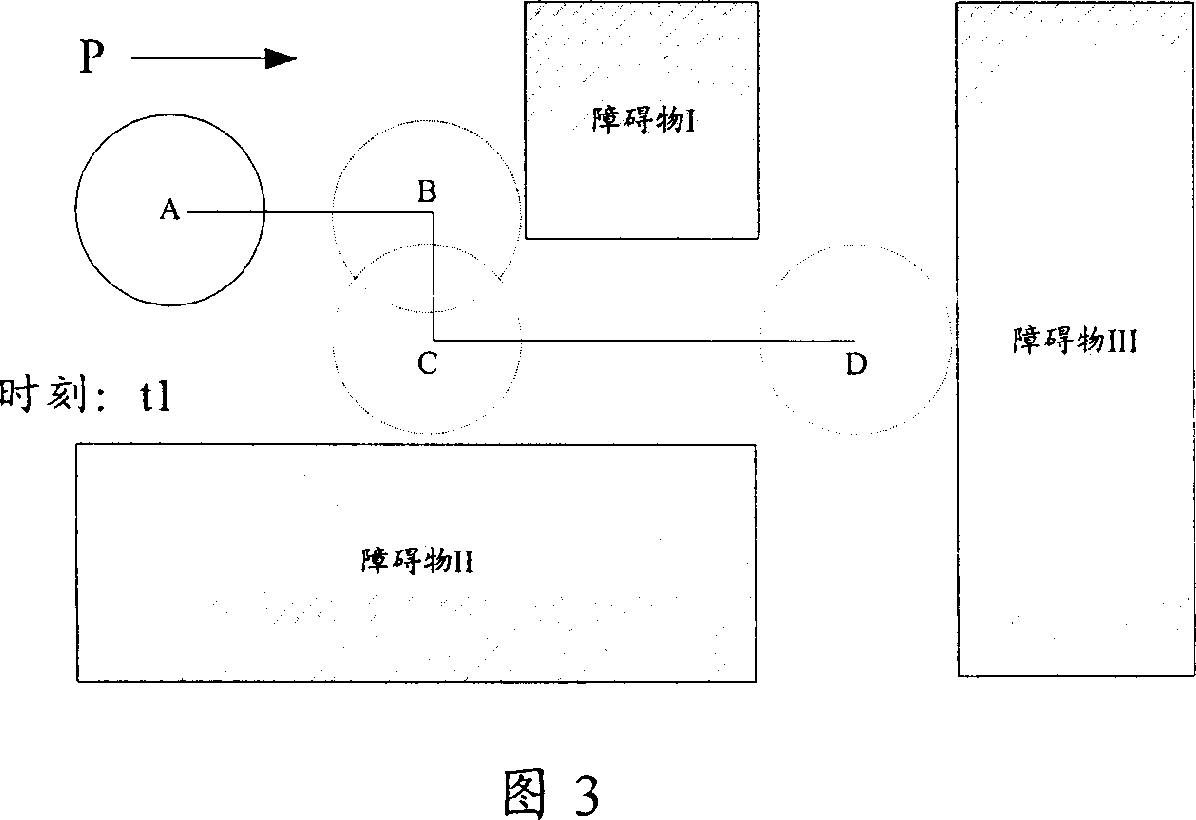
ActiveCN1941788ASend less frequentlyReduce trafficData switching networksSpecial data processing applicationsTraffic capacityNetwork reduction
The method comprises: a) the local game end real-time decides if the moving route of local role varies; if yes, then determines the moving route of local role, and sends the moving message carrying the moving state and moving route of local role to the remote game terminal; b) the remote game end controls the remote role corresponding to the local role to move according to the moving state and moving route in the received moving message. By the invention, the network traffic flow for on-line game can be reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for managing data in flash storage medium
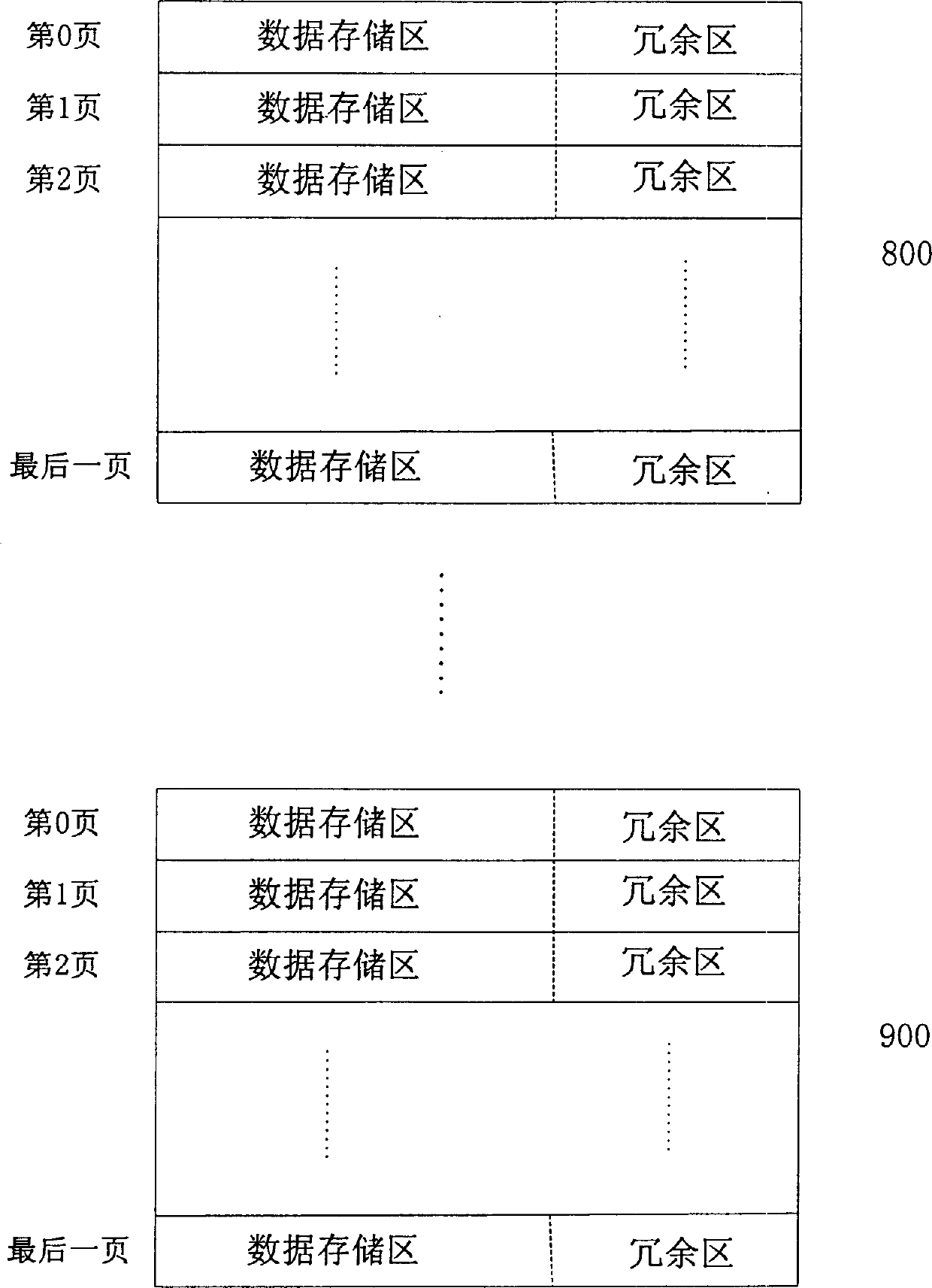
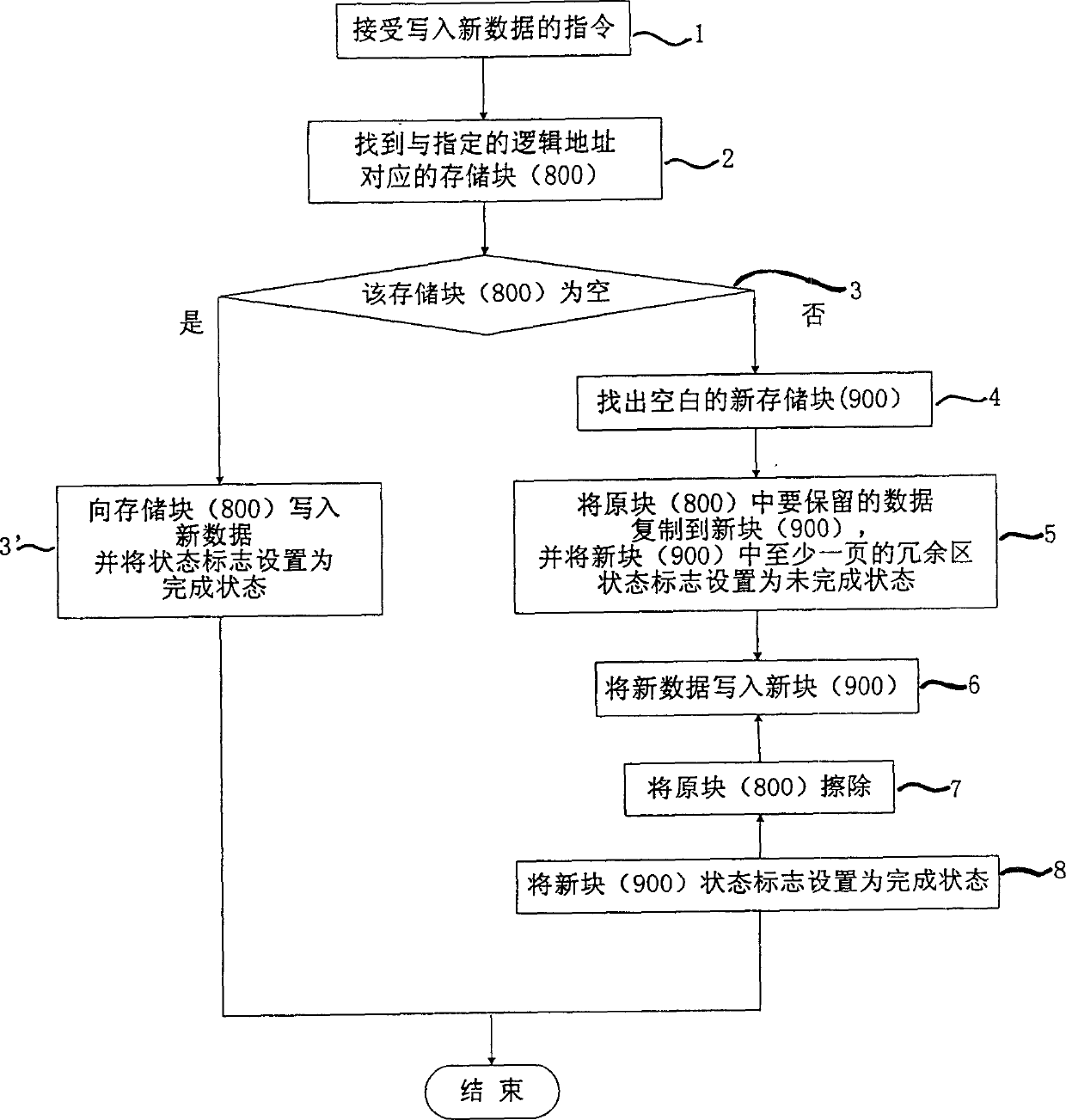
InactiveCN1518000ANot lostAvoid reading and writing errors againRead-only memoriesDigital storageOriginal dataSoftware engineering
A method for managing the data in flash memory medium features that when the memory block is operated, its state flag is set up to a unfinished state, and when its operation is finished, the state flag is set up to finished state. If an exception accurs during data writing to the flash memory medium, the original data in the flash memory medium can not bo lost. Its data writing method and data restoring method are also disclosed.
Owner:NETAK TECH KO LTD
Application message display control method and application message display control device
ActiveCN105183307ANot lostReduce distractionsTransmissionSpecific program execution arrangementsApplication procedureApplication software
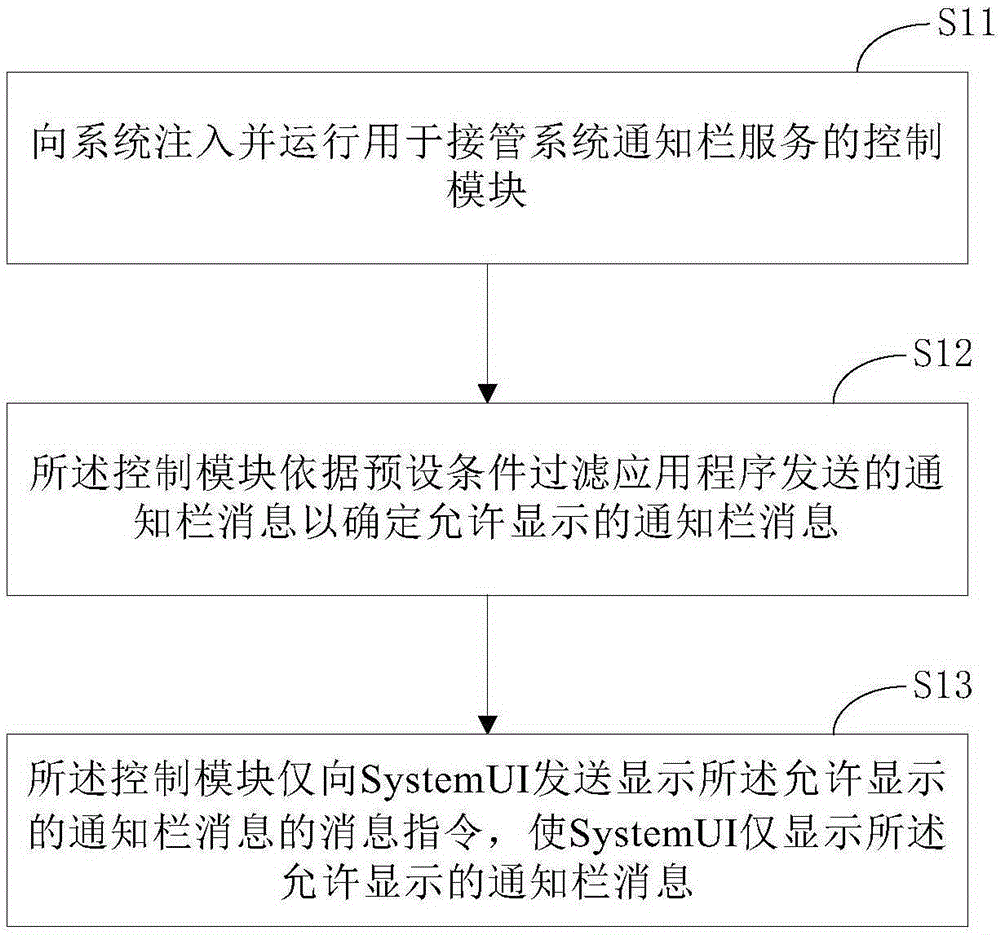
The invention provides an application message display control method which comprises the steps of inputting a control module which is used for controlling a system notification service into a system and operating the control module; filtering notification messages which are transmitted by the application by the control module according to a preset condition for determining the notification message that is allowed to be displayed; and only transmitting a message instruction for displaying the notification message that is allowed to be displayed by the control module to a SystemUI so that the SystemUI only displays the notification message that is allowed to be displayed. Correspondingly, the invention further provides an application message display control device. The application message display control method can make the application selectively display the notification message for hiding useless notification message and displaying useful notification message, thereby preventing an interference caused by a large number of useless notification messages to a user, and preventing loss of important messages.
Owner:北京鸿享技术服务有限公司
Method and device for equalizing histogram based on sub-regional interpolation
ActiveCN101739672ANot lostRich in detailsTelevision system detailsImage enhancementSource imageHistogram equalization
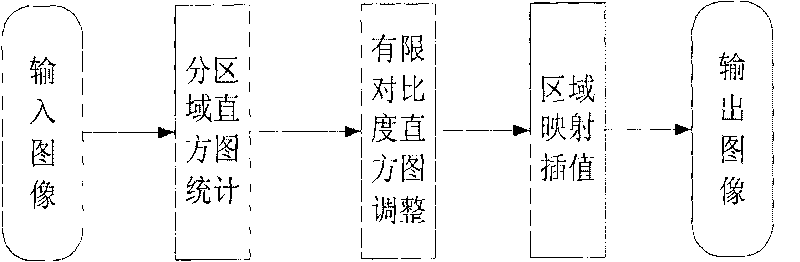
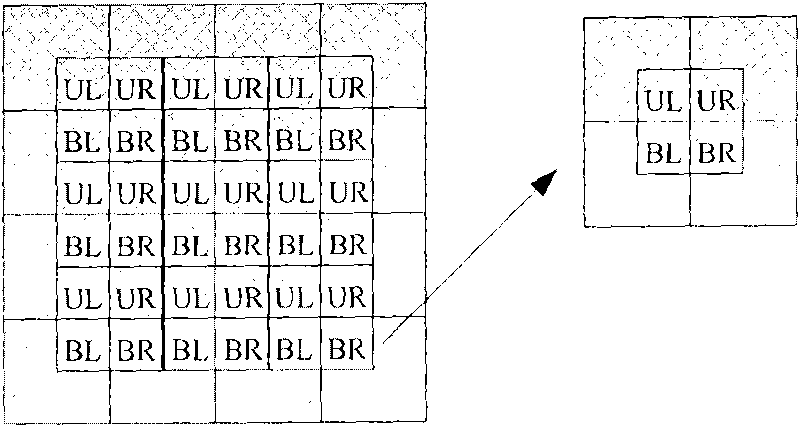
The invention relates to a method and a device for equalizing a histogram based on sub-regional interpolation. The method and the device are used for: acquiring and digitalizing an image; preprocessing the image; dividing data input by an image input module into a plurality of regions; performing histogram statistics on each region; performing contrast limited adjustment on histogram data and an input image; changing histogram distribution of the histogram data and the input image; redistributing overflow pixels to each histogram interval; performing histogram equalization on a result of the contrast limited histogram adjustment; dividing an image region into a plurality of sub-blocks; and performing interpolation processing on adjacent sub-blocks positioned in different regions. The idea of the invention is to analyze the histogram of an input source image on the basis of contrast limited histogram equalization technology, brighten the dark part in the source image through adaptive histogram specification technology and the processes of regional interpolation and the like, highlight more details, and prevent the brighter part from overexposure to lose an image detail at the same time.
Owner:北京中星天视科技有限公司
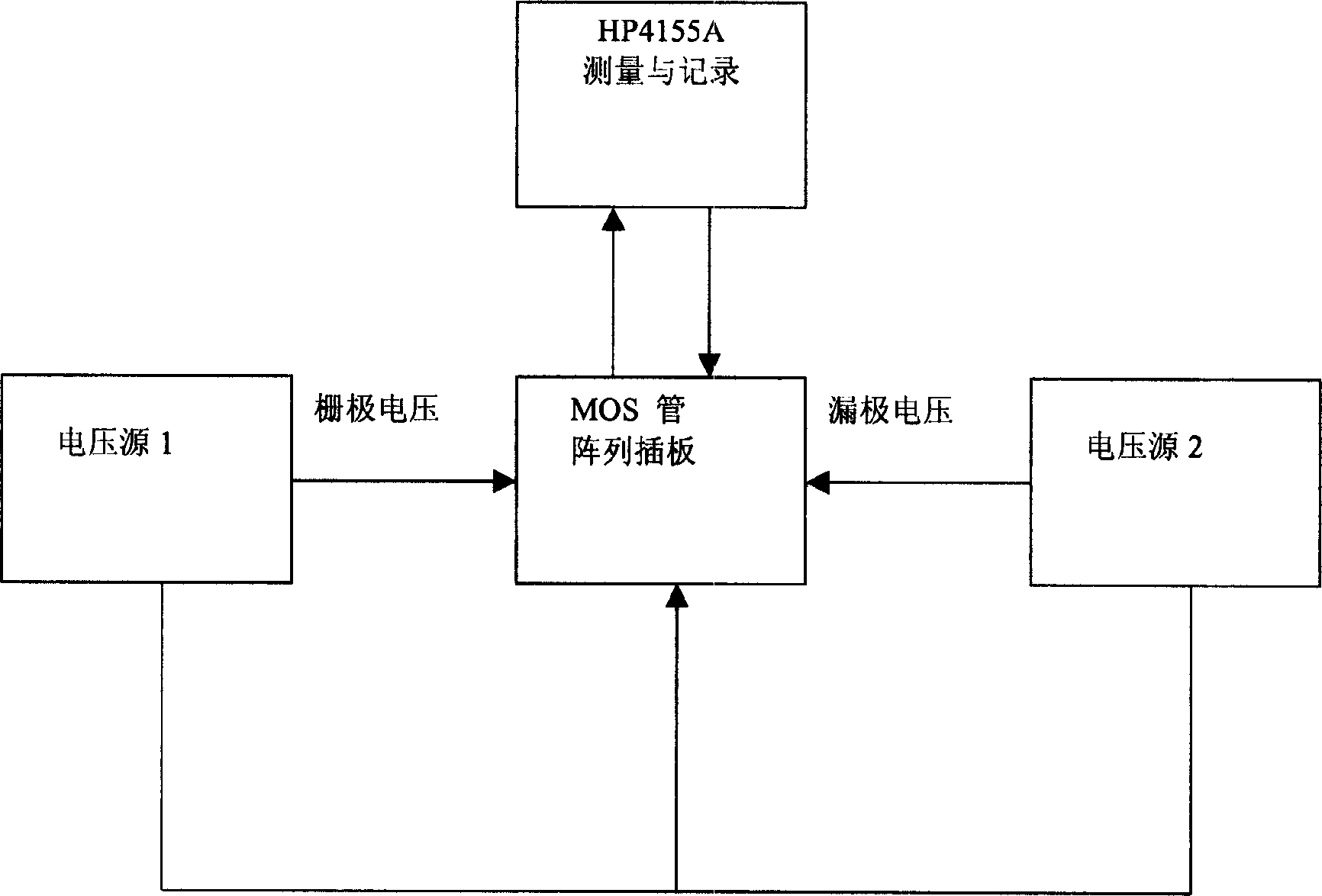
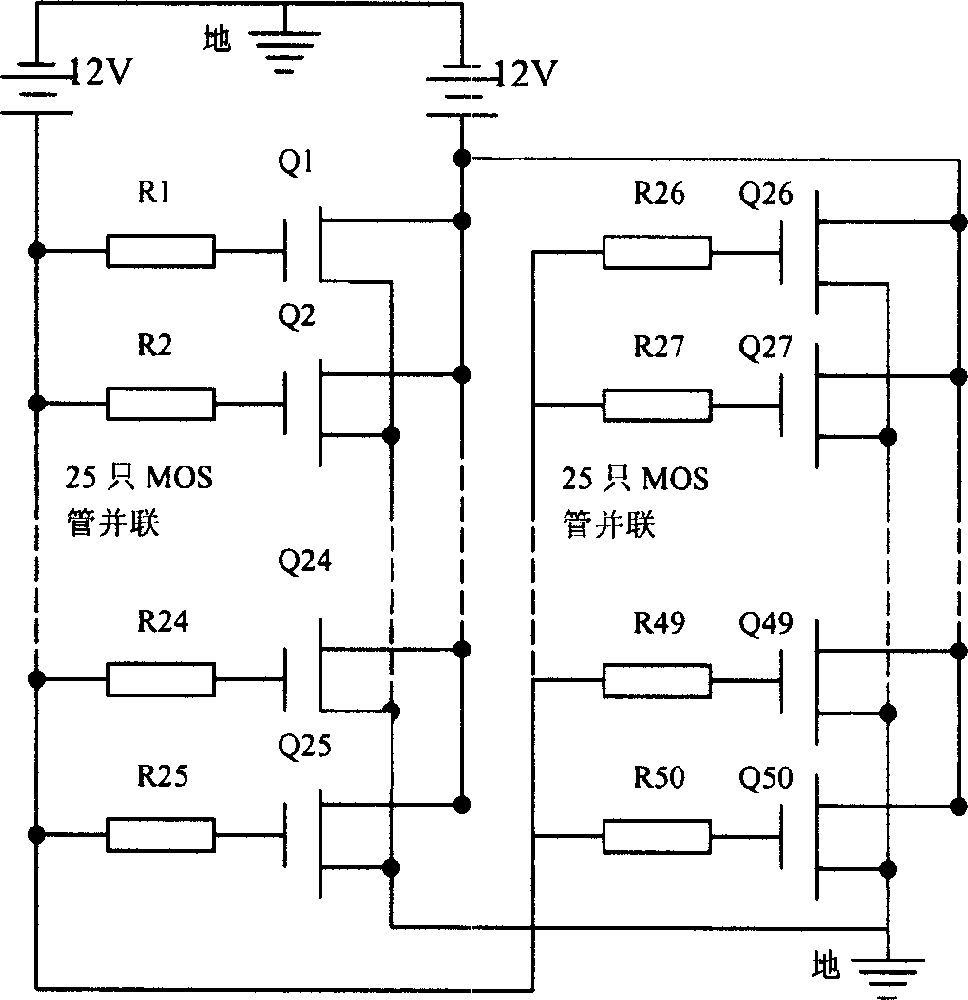
MOS device hot carrier injection effect measuring method
InactiveCN1588104ALow costNot lostSemiconductor/solid-state device testing/measurementIndividual semiconductor device testingFast measurementHeat carrier
The invention is a measuring method for MOS device heat carrier injecting effect. At first, the stress voltage value of drain and grid electrode of the device needed to be measured are determined according to the standard measuring device, and records the initial data through the data recording program; then the device needed to be measured is placed into the socket of the circuit board, at the same time, supplies voltage to the drain and grid electrode; shuts off the stress voltage at time point after 10, 20. and 50 seconds, the MOS is pulled out form the circuit board, and the degeneration quantity of designated parameter measured by the device are recorded; after the first time of data recording, all the MOS tubes are inserted into the original socket of the circuit board, then carries on correspondent voltage stress to the next time point, then stops the stress, then pulls out the MOS tubes form the circuit board, records the measured degeneration data, repeats the above mentioned steps until the degeneration quantity accords to the demands.
Owner:信息产业部电子第五研究所
Dynamic symbol executing method for relieving path explosion
ActiveCN102708045AEliminate explosionIncrease the lengthSoftware testing/debuggingPathPingSoftware engineering
The invention belongs to the field of security tests for computer software, and provides a dynamic symbol executing method for relieving path explosion. The method aims to solve the problem of path explosion and can remove redundancy constraining conditions generated during circulation of an executing process of a program by means of a mapping and acquiring process for the constraining conditions generated by execution of symbols on a static decision diagram of the program, so that the problem of path explosion caused by the circulation of execution of the dynamic symbols is eliminated. The dynamic symbol executing method is applied to tests for software.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
Method and system for backing up mobile phone short messages
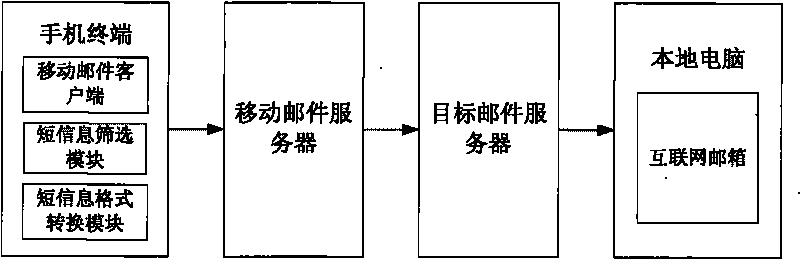
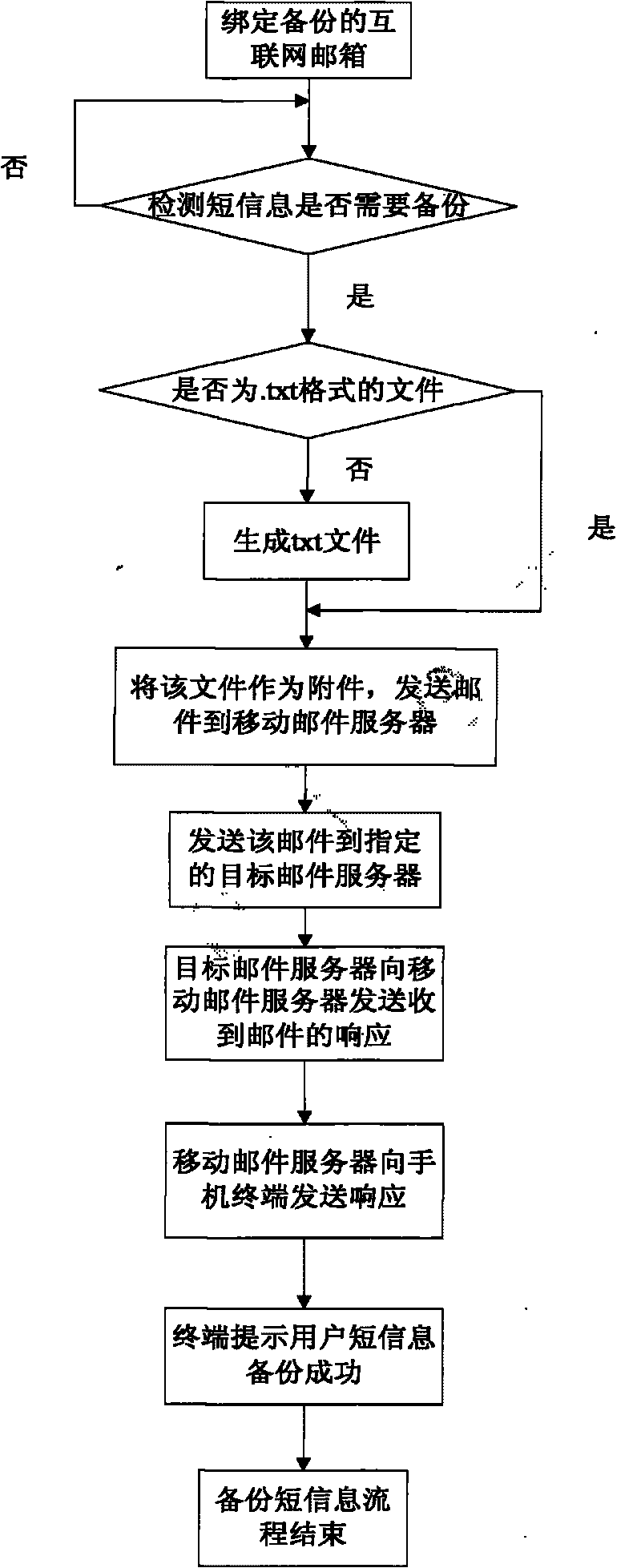
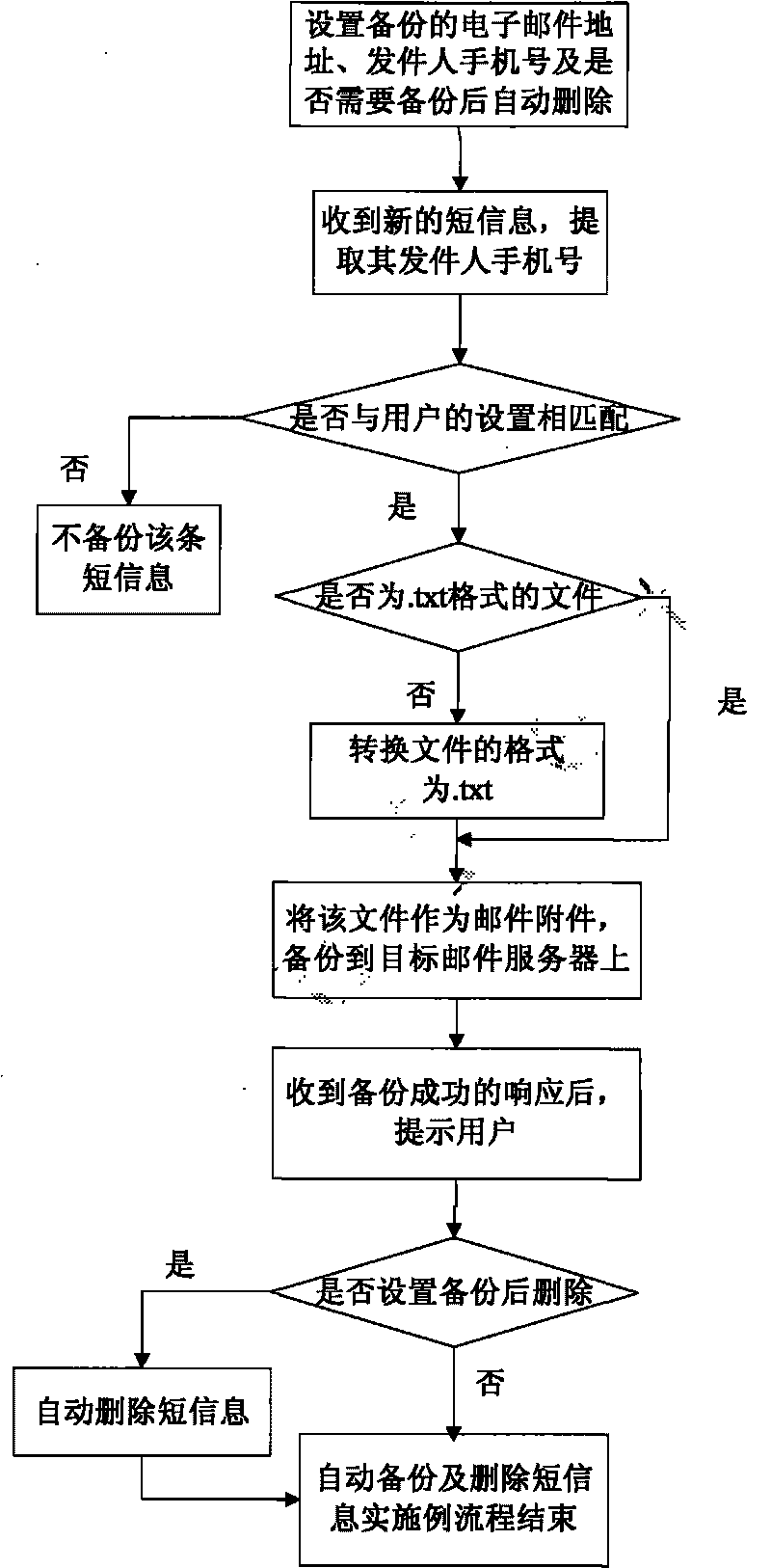
InactiveCN101765068ANot lostWon't leakInformation formatContent conversionShort Message ServiceThe Internet
The invention relates to a method and a system for backing up mobile phone short messages. The method comprises the following steps that: a user selects the short messages needing to be backed up; a mobile phone converts the short messages needing to be backed up into files of formats suitable for multimedia service transmission; and the files of the converted formats serving as an email are sent to a specified Internet mailbox by using a mobile multimedia email service. The system comprises the mobile phone, mobile email client software, a short message filtering module, a short message format converting module, a mobile email server, a target email server and a terminal computer capable of logging in the Internet mailbox, wherein the short message filtering module is used for screening the short messages needing to be backed up according to the setting of the user; and the short message format converting module is used for uniformly converting short message files of different formats into the formats suitable for the multimedia service transmission.
Owner:ZTE CORP
Method and device for protecting power failure data of solid state disk
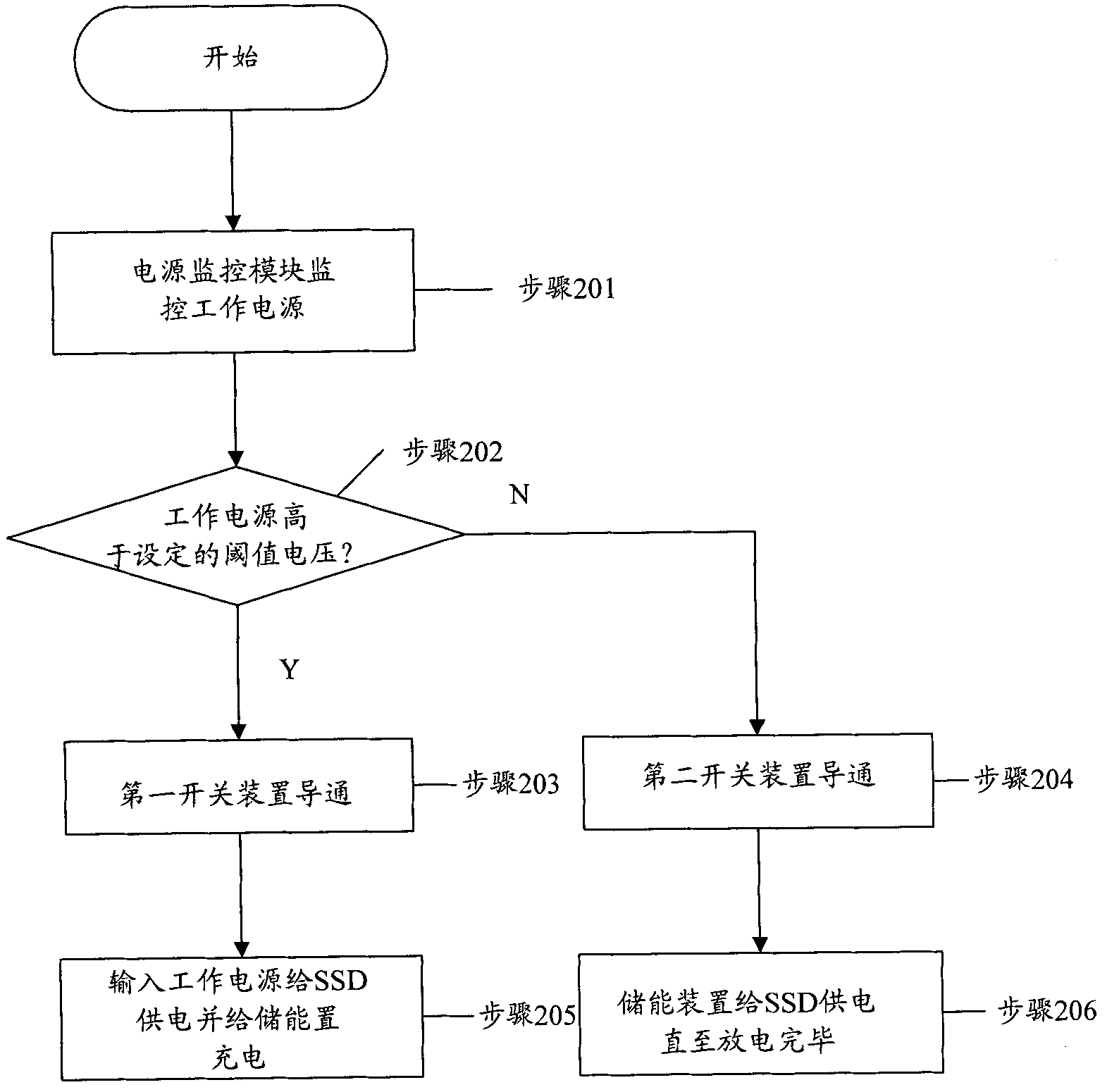
InactiveCN101826060AEasy to implementLow costMemory loss protectionPower supply for data processingSolid-stateFailure data
The invention discloses a method and a device for protecting power failure data of a solid state disk. The method comprises the steps of: detecting power failure of the solid state disk, and switching a working power supply to a preset energy storing device to provide power for the solid state disk; in a period for providing power for the solid state disk by the energy storing device, storing data being read and writted by the solid state disk to a disk; and detecting the working power supply and restoring power, and switching into the working power supply from the energy storing device to provide the power for the solid state disk. By the processing, when the solid state disk is in abnormal power failure, the data being read and written by the solid state disk can not be lost.
Owner:ZTE CORP
Method for implementing magnanimity broadcast data warehouse-in
InactiveCN101277272ATimely processingSolve the unstable operation of the systemSpecial service provision for substationClient-sideData file
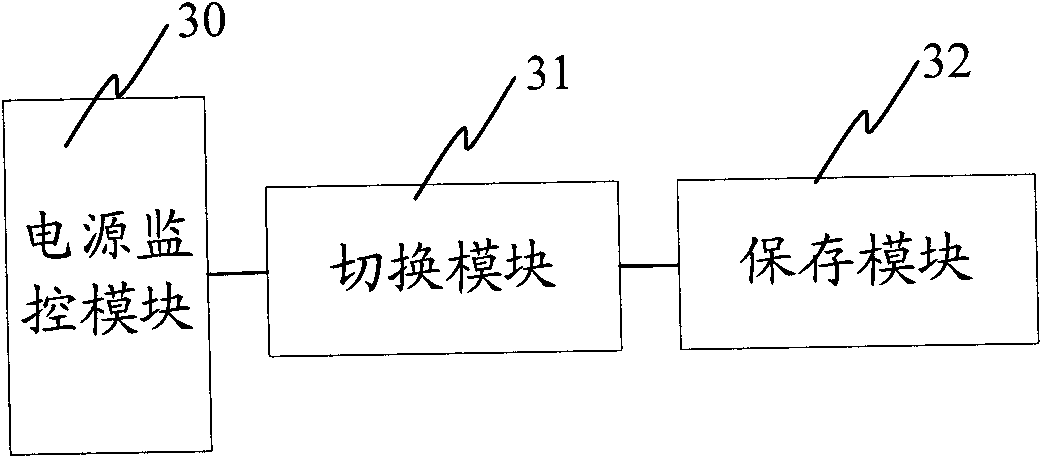
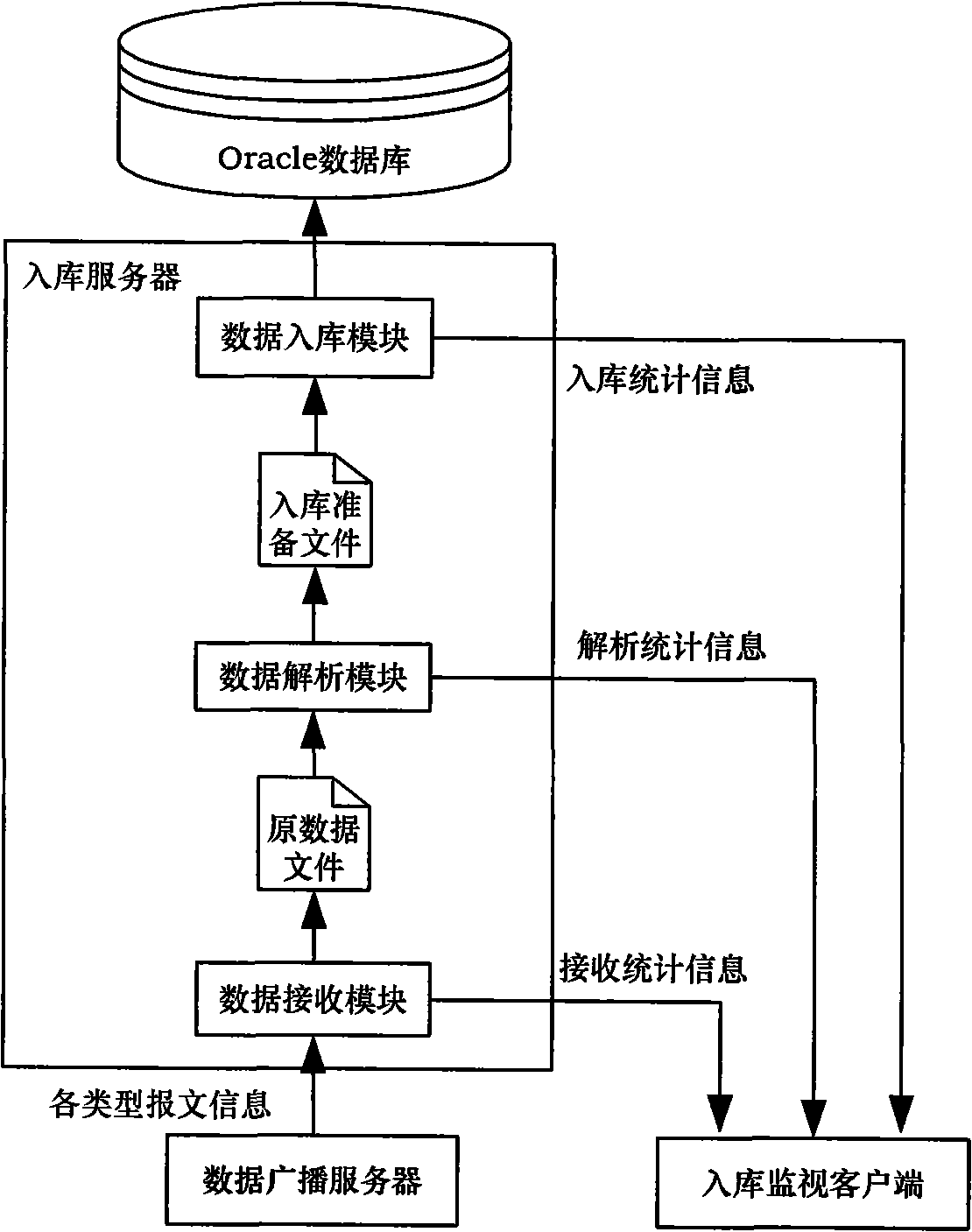
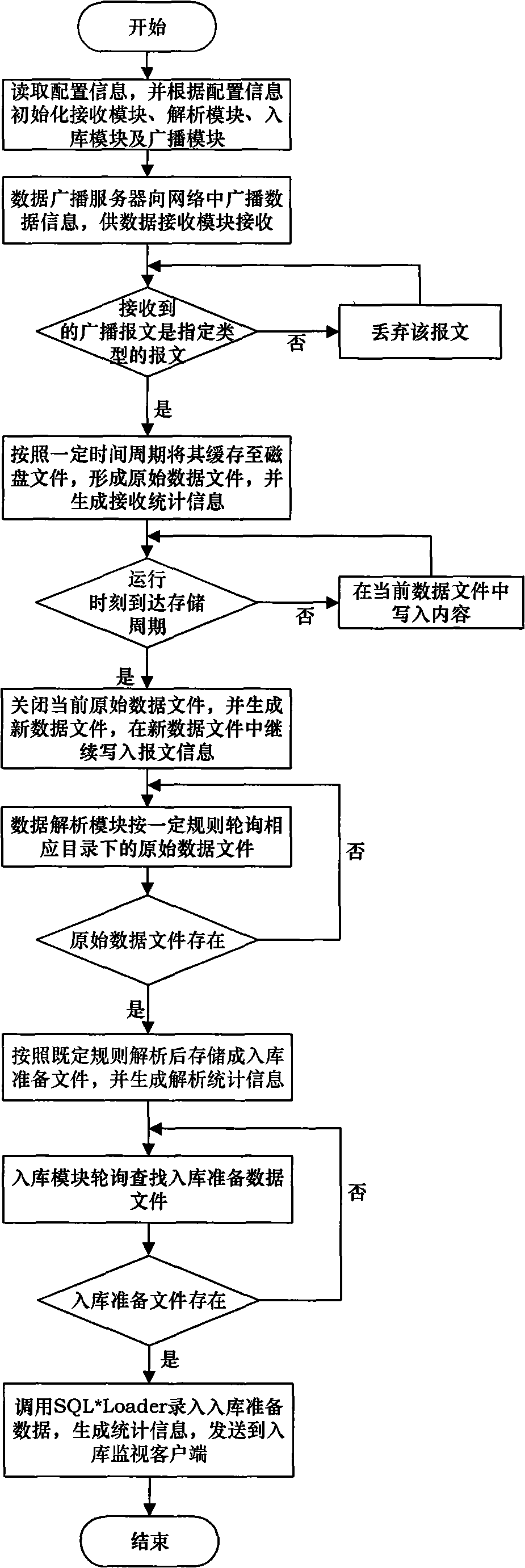
The invention provides a realizing method for warehousing mass broadcast data, comprising the steps of: receiving the broadcast data according to certain period, caching the data information in a manner of data file in terms of types, time, and columns, and accomplishing data parsing and warehousing process in the way of polling, generating relevant receiving statistics information in the process of receiving, parsing and warehousing to send to a warehousing monitor client so that users can monitor the information in real time, thus achieving the stable and punctual processing to the mass broadcast data, improving processing ability to the mass data in practical application through double-machine thermal backup technology, multi-course technology, file storage technology and SQL*Loader technology, ensuring stability of application and data integrality, and enhancing performances of the application system.
Owner:BEIHANG UNIV
Nonvolatile memory system and management method thereof
ActiveCN103810112ASolve protection problemsPromote recoveryMemory adressing/allocation/relocationEnergy efficient computingDram memoryHost memory
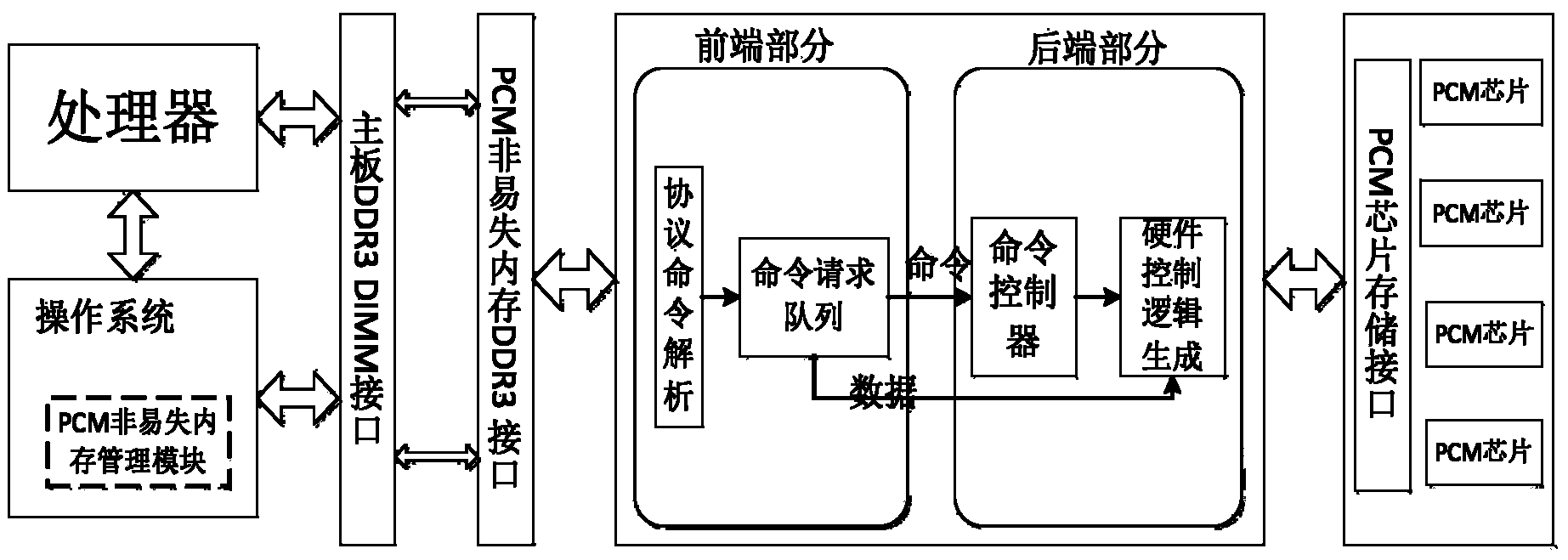
The invention discloses a nonvolatile memory system and a management method of the nonvolatile memory system. A nonvolatile memory is constructed by adopting a nonvolatile PCM storage device, management on the nonvolatile memory is added to a host memory management module, unified management on the nonvolatile memory and a traditional DRAM is achieved, and the nonvolatile memory and the traditional DRAM can be fused to form a unified memory for the access of a host processor. According to the nonvolatile memory system and the management method of the nonvolatile memory system, the problem that power failure data of the traditional DRAM are lost and the problem of data consistency can be solved, and meanwhile energy consumption of the host memory can be lowered.
Owner:HUAZHONG UNIV OF SCI & TECH
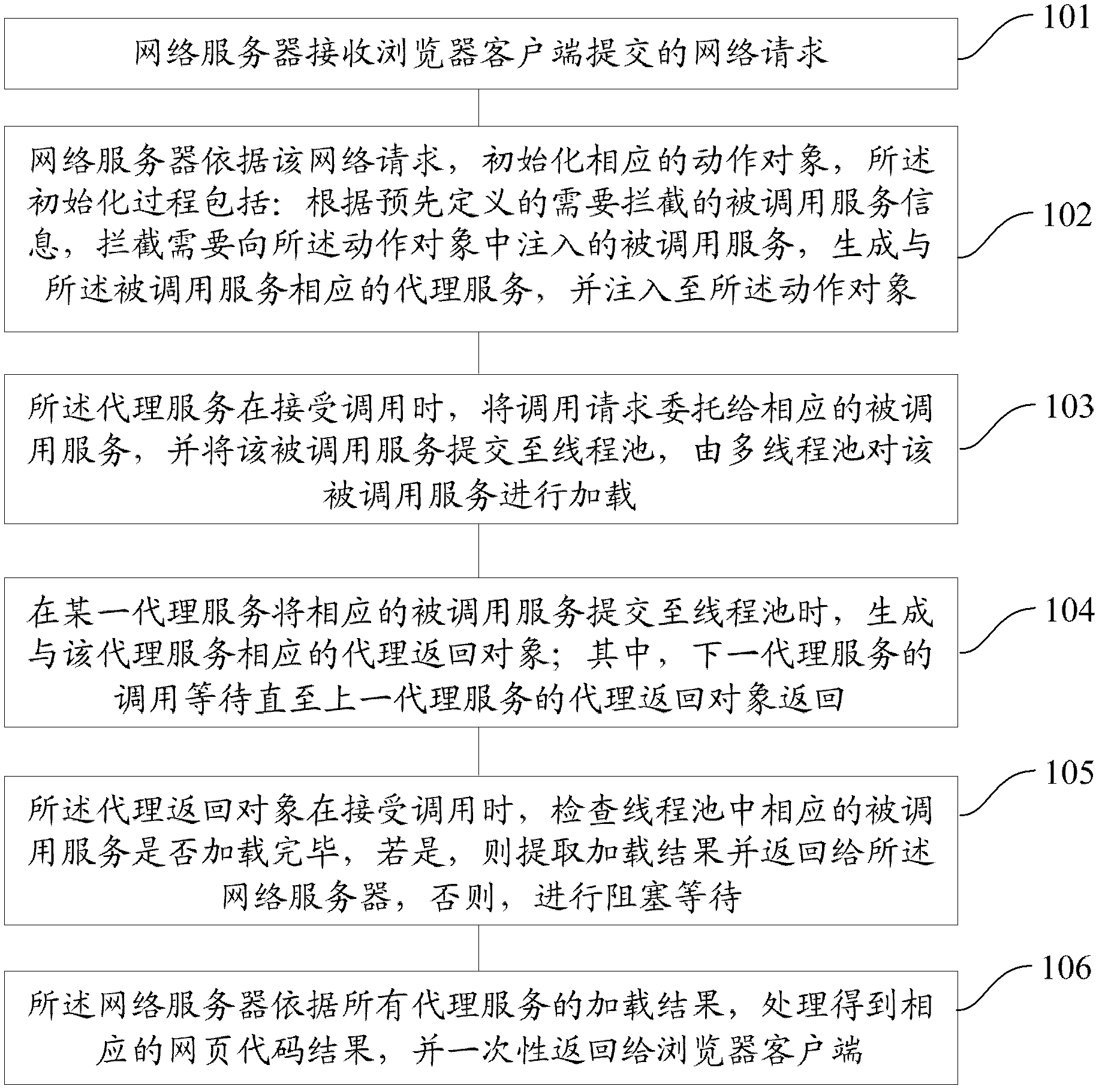
Network request processing method and system, and network service providing device
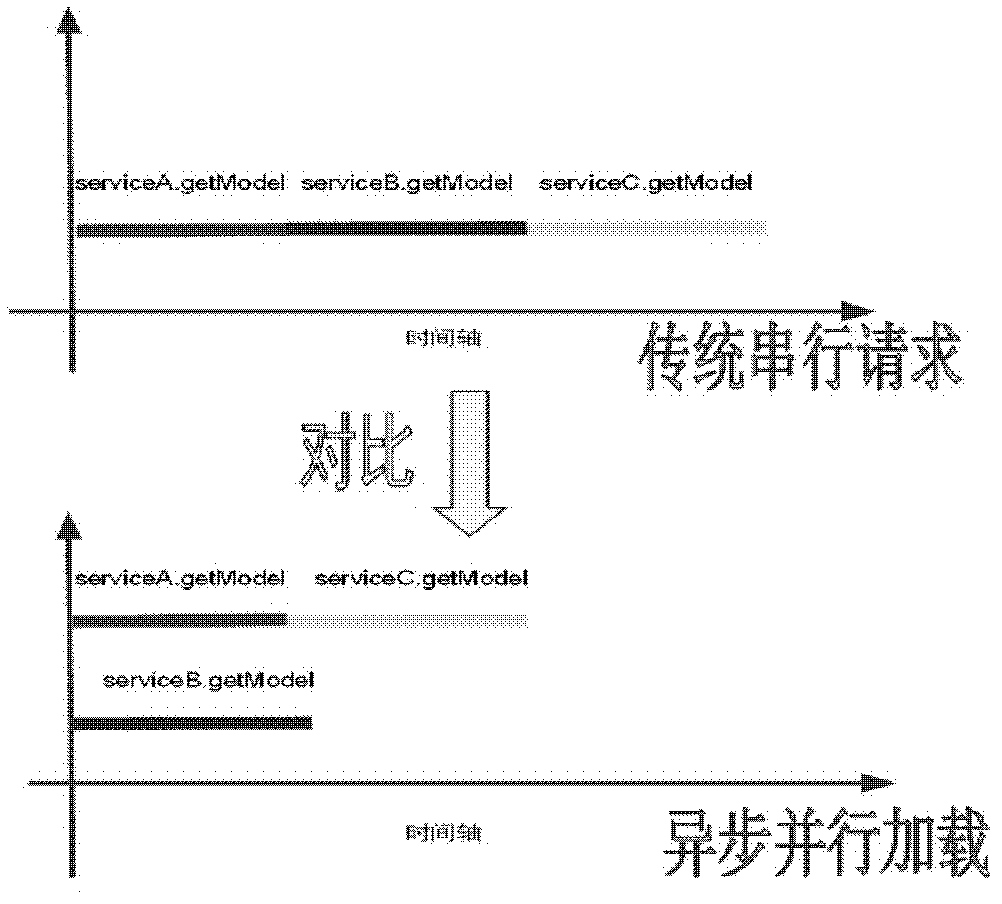
The invention provides a network request processing method, a network request processing system and a network service providing device. The network request processing method comprises the following steps of: receiving a network request which is submitted by a browser client; initializing a corresponding motion object according to the network request; when proxy service is called, consigning a call request to corresponding called service, submitting the called service to a thread pool, and loading the called service by a multi-thread pool; when certain proxy service submits the corresponding called service to the thread pool, generating a proxy return object which corresponds to the proxy service; when the proxy return object is called, checking whether loading of the corresponding called service in the thread pool is finished; and processing by a network server according to loading results of all pieces of proxy service to obtain corresponding webpage code results, and returning the webpage code results to the browser client at one time. By the invention, the response time of the network request can be greatly shortened.
Owner:ALIBABA GRP HLDG LTD
Streaming time series data dimensionality reduction and simplified representation method based on piecewise linear representation
InactiveCN106960059AGuaranteed Dimensionality Reduction ResultsImprove fitting accuracySpecial data processing applicationsMaximum errorStreaming data
The invention relates to a streaming time series data dimensionality reduction and simplified representation method based on piecewise linear representation. The method comprises the following steps that: S1: presetting data segments and compression parameters; S2: carrying out data scanning on streaming time series data in a slide window way, and entering a streaming data buffer zone; S3: judging whether the fitting error of an initial segmented data segment exceeds an ME_ES (Maximum Error for Entire Segment) or not, carrying out reservation if the fitting error of the initial segmented data segment exceeds the ME_ES, and marking the initial data segment as "inseparable", and if the fitting error of the initial segmented data segment does not exceed the ME_ES, carrying out secondary optimal segmentation; and S4: moving the data segment which is marked as "inseparable" in the streaming data buffer zone out of the streaming data buffer zone, judging whether the streaming time series data to be processed is in the presence or not, if the streaming time series data to be processed is in the presence, returning to the S2, and otherwise, ending. By use of the method, data dimensionality reduction execution efficiency is guaranteed to a high limit, the fitting accuracy of data simplified representation is optimized to a certain range, and accuracy and the execution efficiency of data representation can be improved.
Owner:SHANDONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com