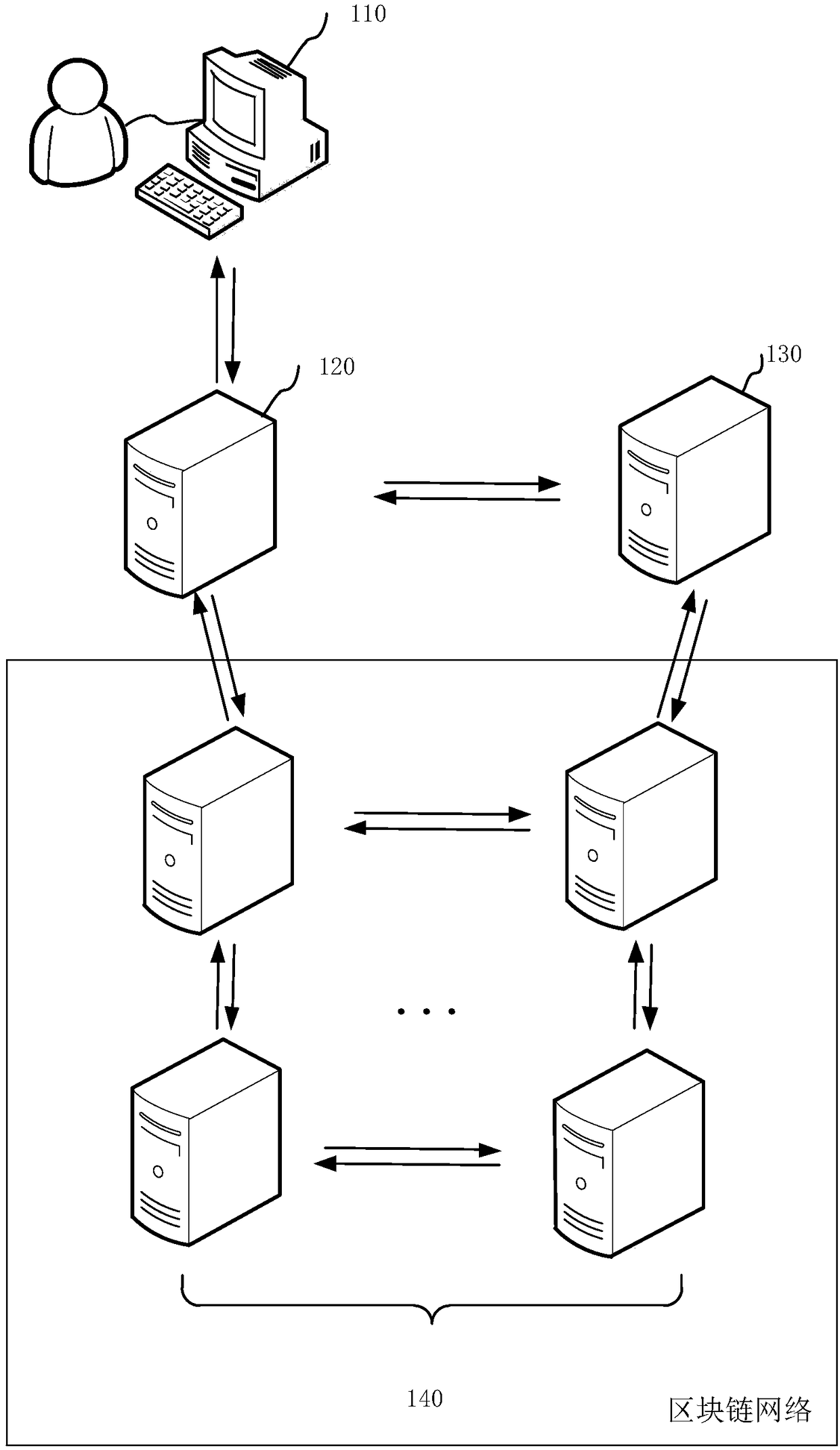
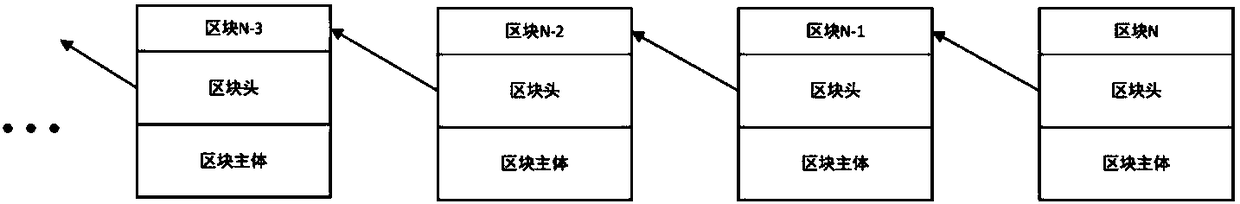
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
584results about How to "Guarantee data security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security cloud storage system based on increment synchronization
InactiveCN104023085AImprove user experiencePrevent leakageTransmissionTransmission protocolFile synchronization
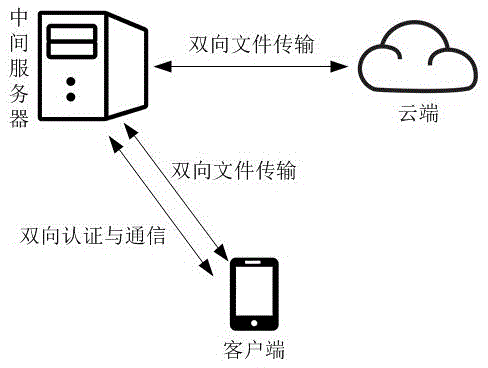
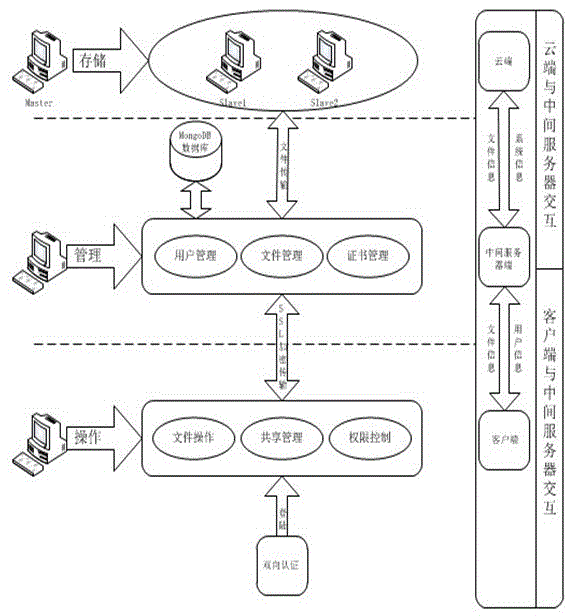
The invention discloses a security cloud storage system based on increment synchronization. A three-tier architecture of client-intermediate server-private cloud terminal is adopted, and data security is guaranteed by multiple security protection technology. After being blocked and encrypted, a user file is transmitted to a cloud terminal through an SSL (security socket layer) security transmission protocol; after finishing the work of user management and key management, the intermediate server terminal adopts a mutual authentication mechanism and an access control mechanism to realize the safe data share so as to completely prevent original data from leaking from the server terminal; the binding of the file and a mobile device is realized at a client, the specific file can be only opened on a specific device, and even though the file is leaked by an insider, a leaking device can be traced; moreover, the unique increment synchronization technology is realized, and the file can be synchronized by only synchronizing modified file blocks, so that the flow consumption in the file transmission process is reduced, the transmission efficiency is improved, the system usability is enhanced, and user experience is promoted.
Owner:WUHAN UNIV
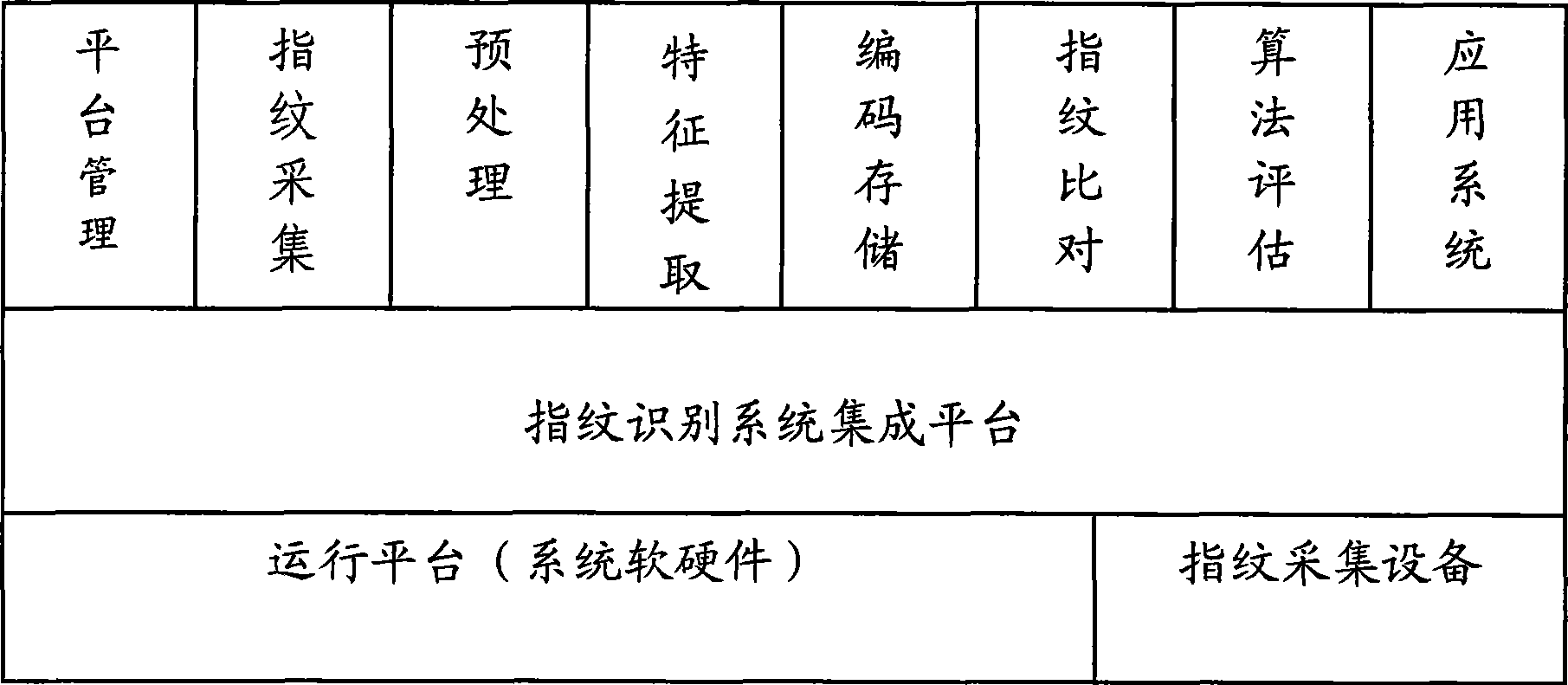
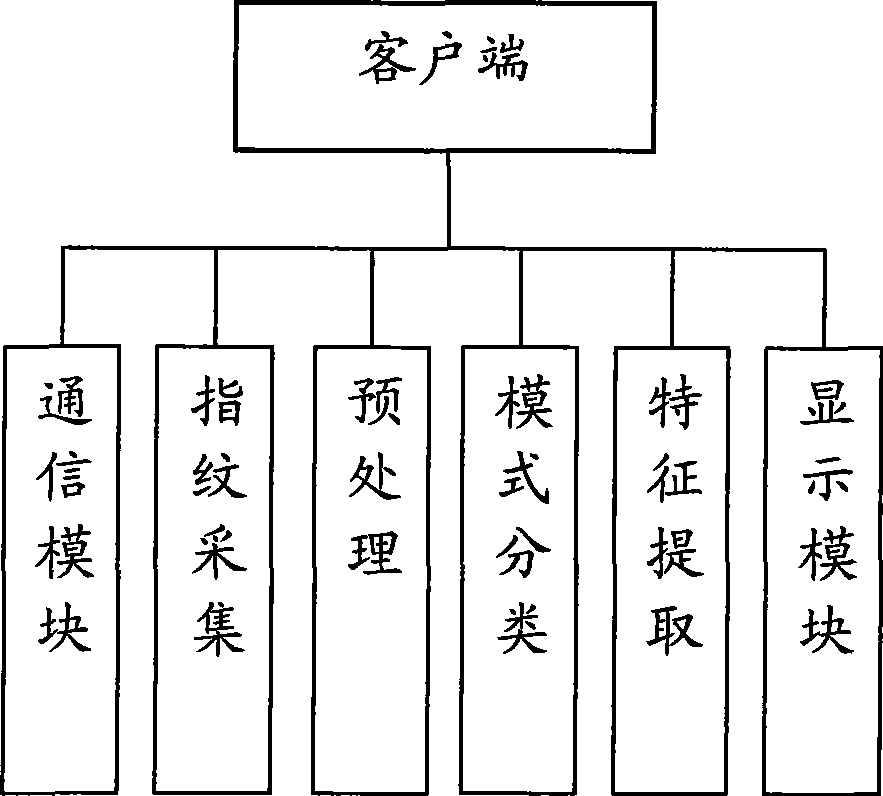
Fingerprint recognition system and control method
InactiveCN101414351AAvoid accessEasy constructionUser identity/authority verificationCharacter and pattern recognitionCapital investmentFingerprint database
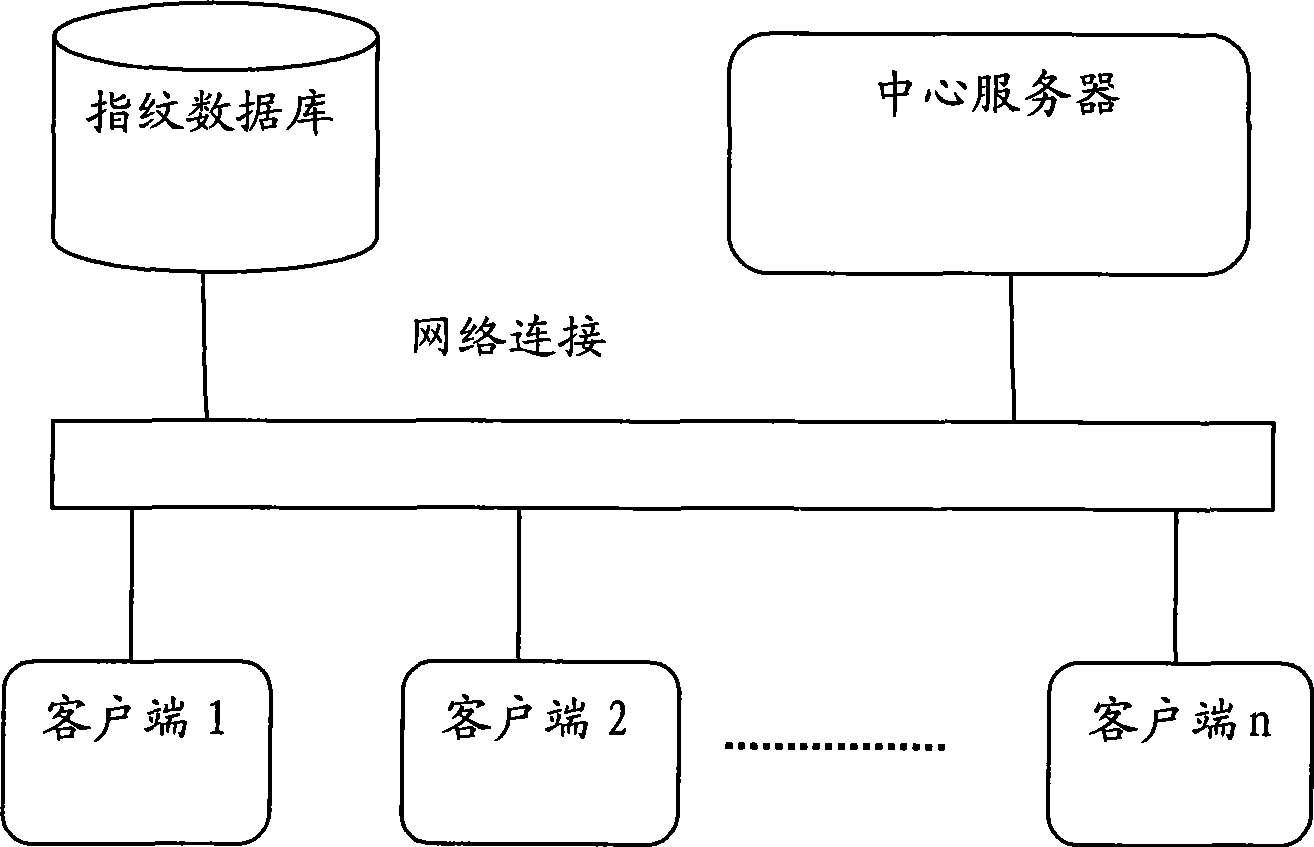
The invention discloses a fingerprint identifying system which comprises three large parts of a fingerprint database, a central server and a client terminal; the fingerprint database is mainly used for memorizing the fingerprint characteristic information after digital coding; the central server is mainly responsible for validating the validity of the client terminal, receiving the fingerprint characteristic data, comparing the characteristics and returning the fingerprint identifying result; the client terminal is mainly responsible for collecting the fingerprint, extracting and uploading the fingerprint characteristic data. The system overcomes the defects of the prior art, can provide an online / offline fingerprint identifying system the basic algorithm library of which can be seamlessly expanded and the functions of which can be selected and matched. The fingerprint identifying system can lead a user to obtain the ID identification and authentication services with high quality under the situation of not needing a great amount of capital investment.
Owner:章毅 +2
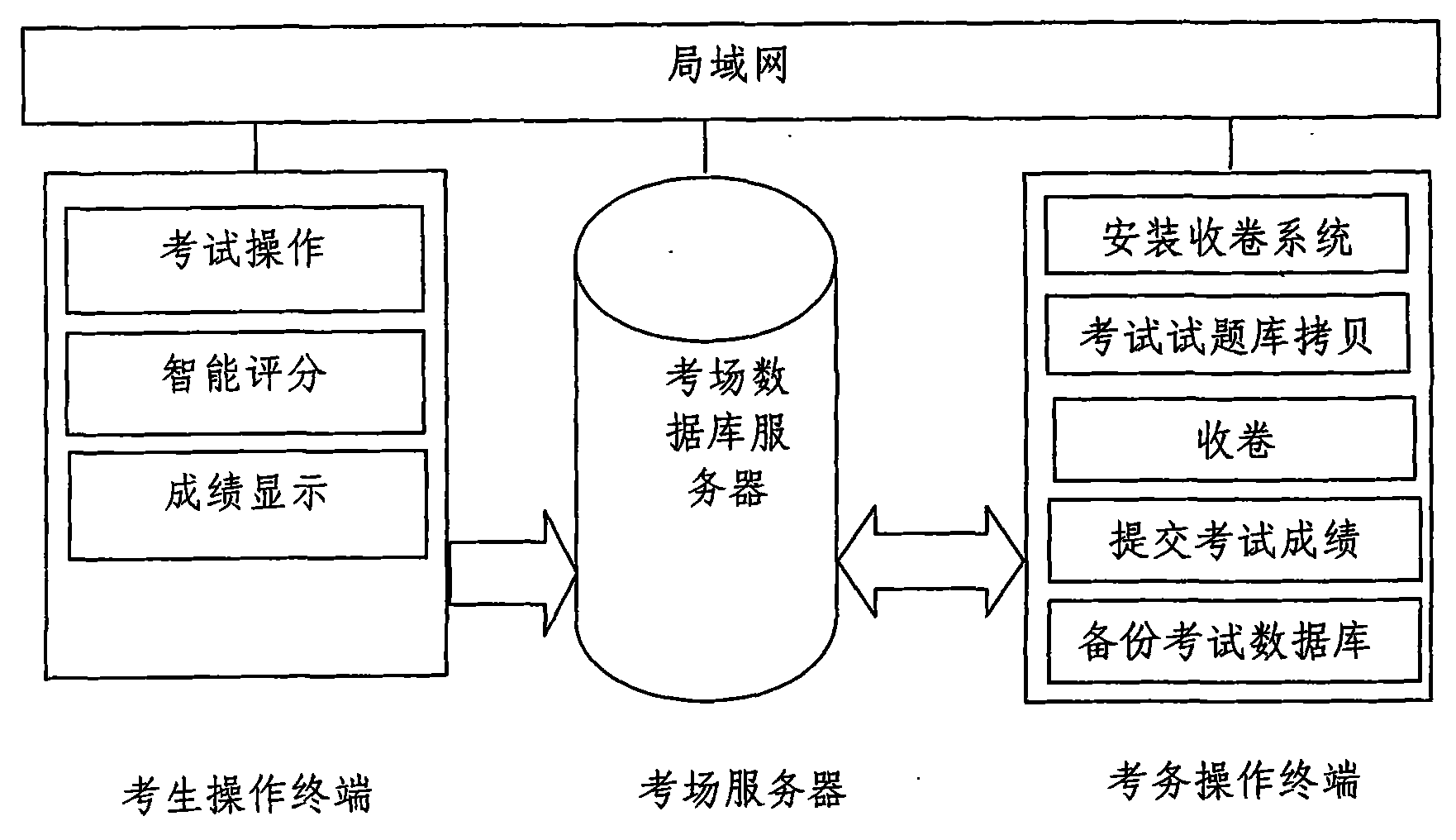
Local area network-based network examination system and implementation method thereof
InactiveCN101964152AReduce investmentGuarantee data securityData switching by path configurationElectrical appliancesArea networkBody area network
The invention discloses a local area network (LAN)-based network examination system and an implementation method thereof. The LAN-based network examination system adopts a client / server (C / S) mode framework; an examination room server, an examination affair operating terminal and examinee operating terminals form a local are network; and examination test questions in the examination room server are decrypted by the examination affair operating terminal and then converted into a data format which can be identified by the examinee operating terminals. The examination affair operating terminal classifies and collects data files of problems worked by examinees and archives examination data. The examinee operating terminals display the identified data and provide an examination environment for examinees. The LAN-based network examination system has lower requirements on network and hardware configurations, stronger adaptability and high compatibility, and only each examinee operating terminal is communicated with a twisted pair cable and is connected with each other by using an exchanger to form the local area network, thereby greatly saving the input of network equipment. The examination data are transferred in the local area network and has no physical contact with the internet, thereby guaranteeing data security and stability of the examination system.
Owner:KUNMING METALLURGY COLLEGE
Web three dimensional (3D) synchronous conference system based on rendering cloud and method of achieving synchronization
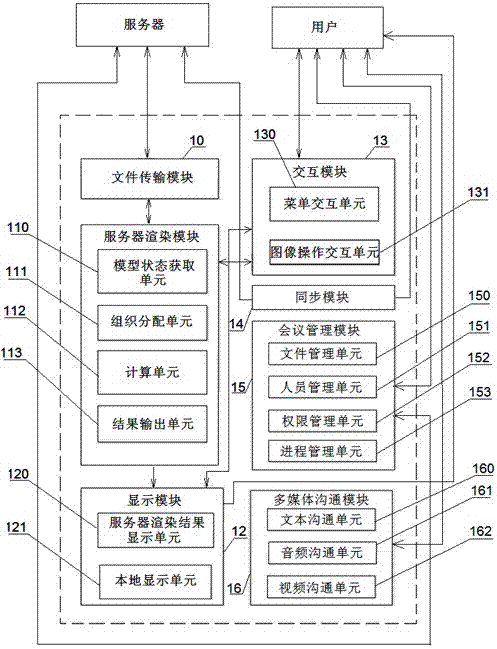
The invention relates to a Web three dimensional (3D) synchronous conference system based on rendering cloud and a method of achieving synchronization. The Web three dimensional (3D) synchronous conference system based on the rendering cloud and the method of achieving synchronization comprise a file transmission module, a server rendering module, a display module, an interaction module, a synchronization module, a conference management module and a multi-media communication module. Rendering technology is adopted by the system. Various kinds of large-scale or ultra-large type three-dimensional models can be browsed synchronously controlled, directly and fluently through a browser, thus any plug-in module is not needed to be installed. Due to the fact that a manipulation model can be synchronously browsed by multiple users of different places movable cross platform (such as a mobile phone terminal and a personal computer terminal) is supported, thus synergic operation is achieved. Due to the fact that only rendered pictures can be obtained by the client terminal, model data can not be obtained, thus data safety of a user is guaranteed. The problem that communication difficulties of a traditional multi-user network conference caused by the fact that data size of transmitting graphic images is large is solved.
Owner:SHANGHAI UNIVERSITY OF ELECTRIC POWER
Multi-source electronic commerce data processing platform and method for heterogeneous data
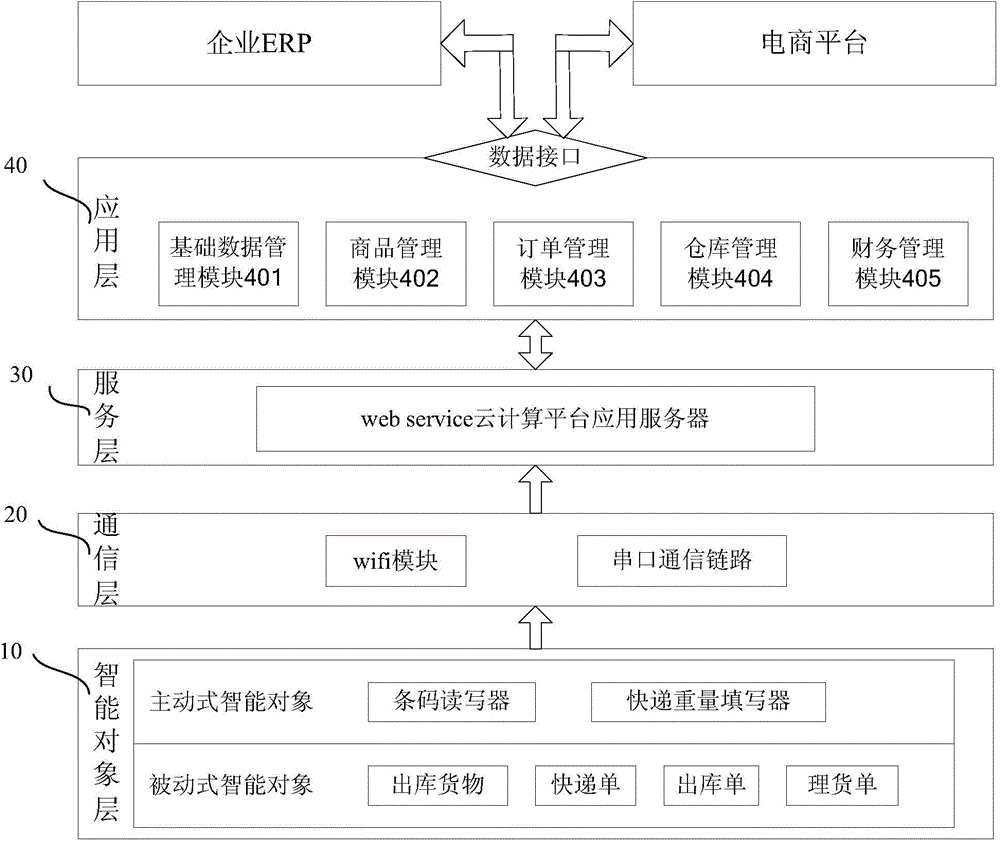
InactiveCN104809553AGuarantee data securityProtect critical data securityBuying/selling/leasing transactionsResourcesEnterprise resource planningData management
The invention discloses a multi-source electronic commerce data processing platform and method for heterogeneous data. The platform comprises an intelligent object layer for collecting a large number of goods data through an intelligent object, a communication layer for transmitting the large number of goods data collected by the intelligent object, a service layer for receiving and storing the large number of goods data transmitted by the communication layer, processing the large number of goods data and providing storage services for an application layer, and the application layer for providing enterprise ERP (Enterprise Resource Planning) and a multi-source electronic commerce platform with an unified data interface to access the application layer and providing basic data management application, order management application, merchandise management application, warehouse management application and financial management application. By means of the multi-source electronic commerce data processing platform and method for heterogeneous data, goods information and sales orders of ERP, the multi-source electronic commerce platform and the multi-source electronic commerce data processing platform are synchronized, so that enterprise financial management is performed easily.
Owner:GUANGDONG UNIV OF TECH
Entrance guard controlling method and system based on bidirectional authentication
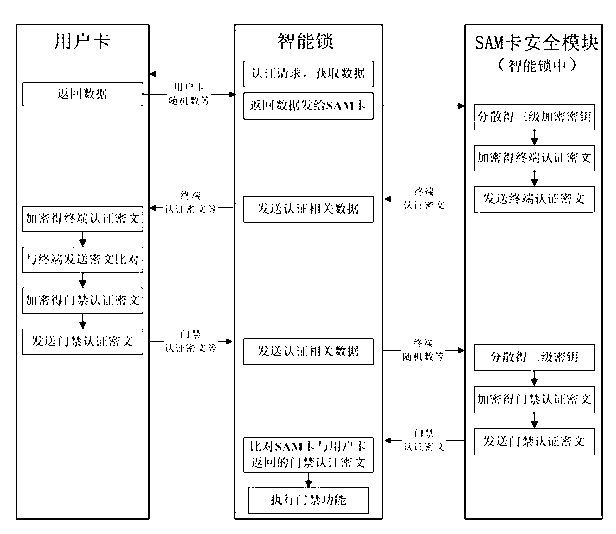
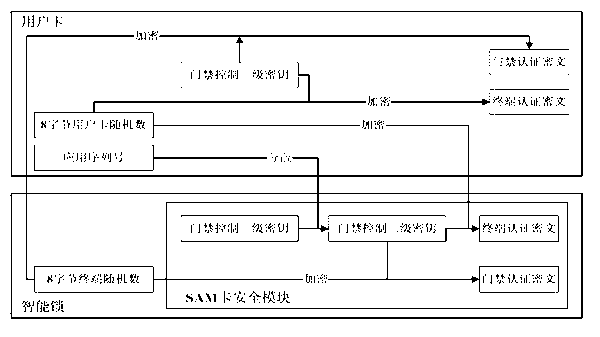
InactiveCN102800141AEnsure safetySolving Security Authentication IssuesIndividual entry/exit registersControl systemSecure access module
The invention provides an entrance guard controlling method and system based on bidirectional authentication. The core of the entrance guard controlling method and system is that a secure access module (SAM)-card safety module which is connected with an intelligent lock control system signal in an intelligent lock is added, can be embedded into the intelligent lock and be separated from the intelligent lock, and is used for storing a secret key and performing encryption / decryption operation. The SAM-card safety module is taken as a medium to realize the bidirectional authentication between a subscriber card and the intelligent lock, therefore, the safe authentication problem between a locket and the subscriber card in the entrance guard system is solved, the safety of the lockset is improved, the lockset or the subscriber card is prevented from being decrypted and cloned, the safety of data storage and data transmission is guaranteed, and further, the safety of the entrance guard system is guaranteed.
Owner:EASTCOMPEACE TECH +1
Data storage access method and device
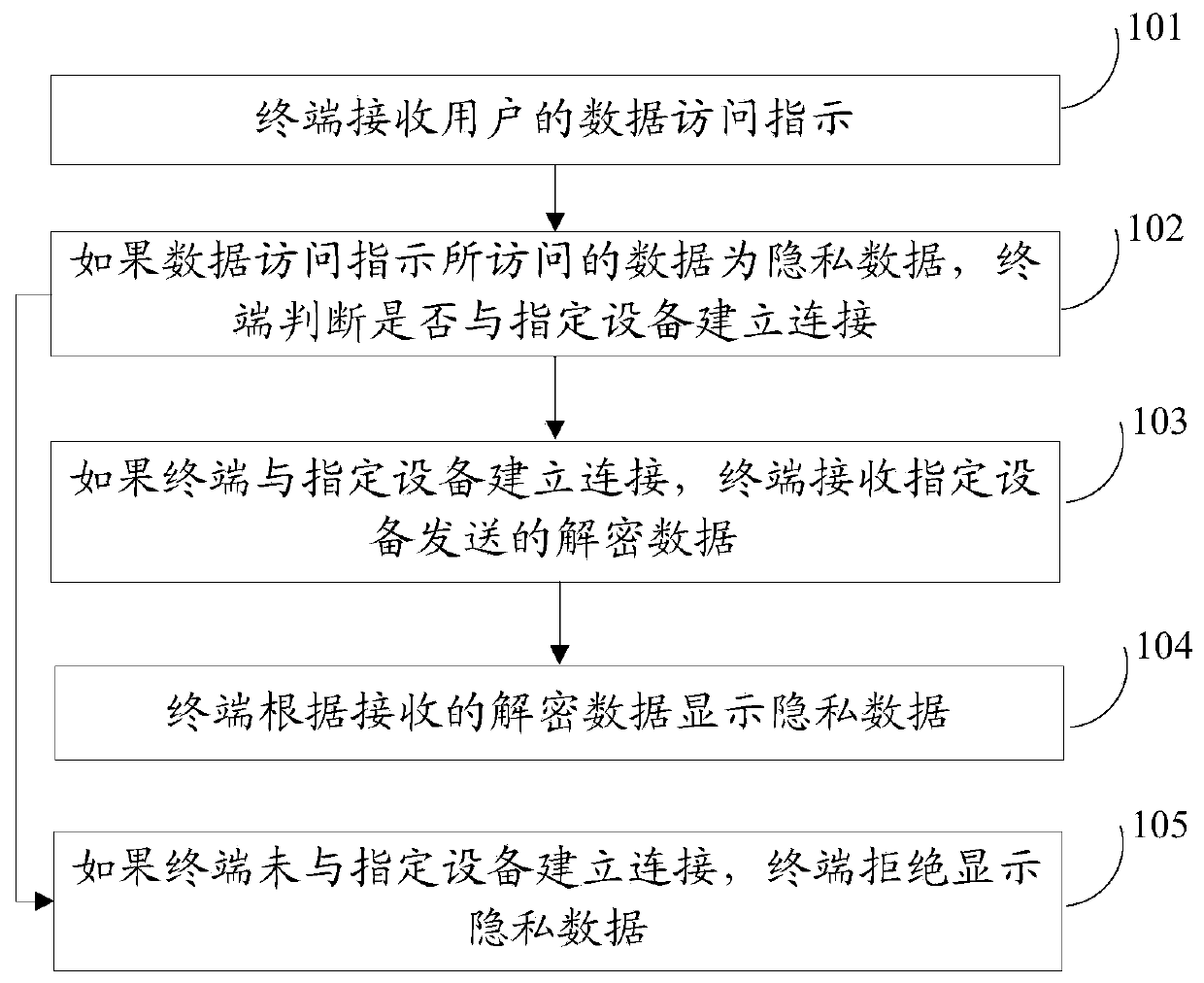
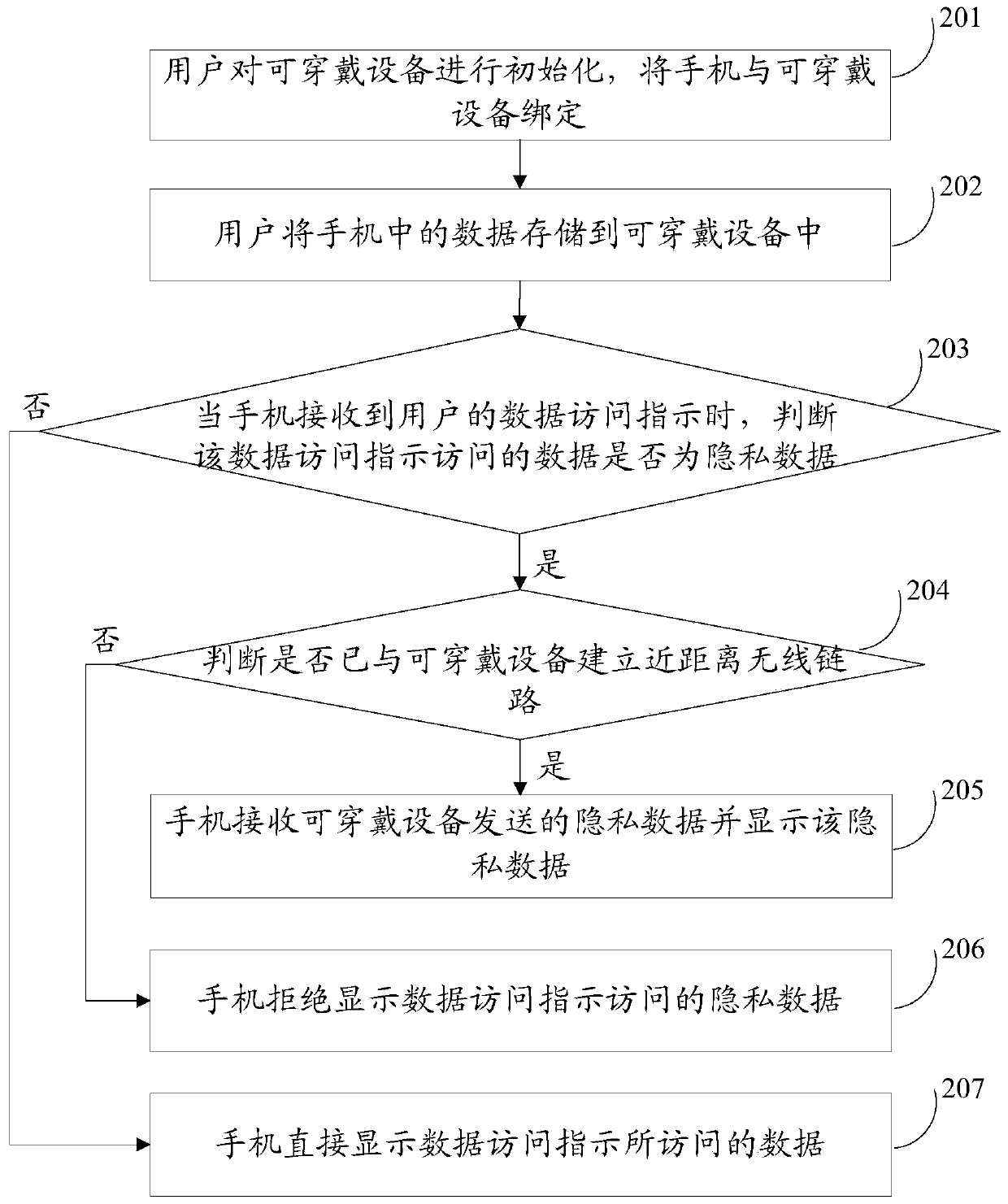
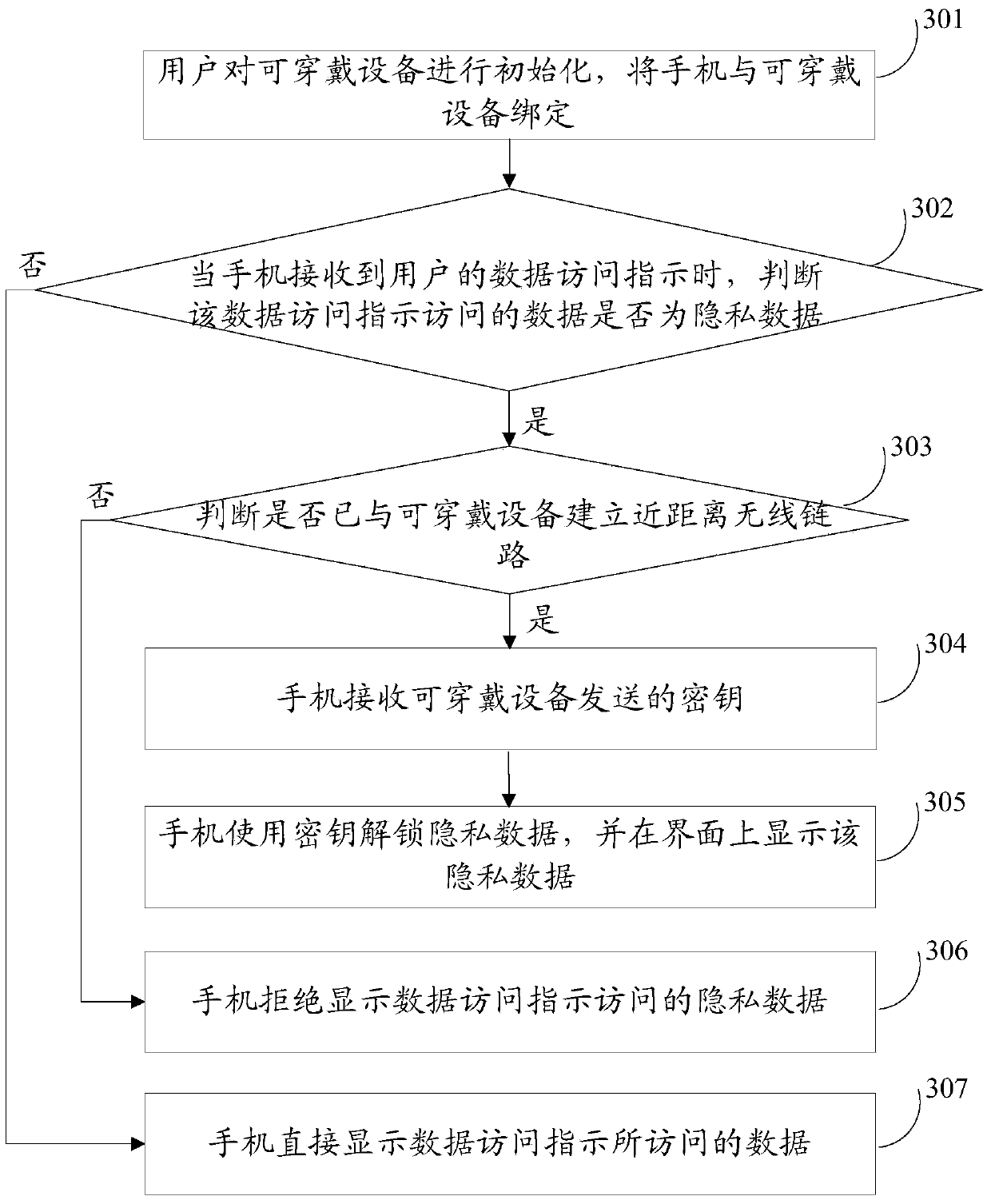
InactiveCN103473514ARefuse to display private dataGuarantee data securityDigital data protectionAccess methodData access
An embodiment of the invention discloses a data storage access method and device. The data storage access method includes that a terminal receives data access instructions of users; if data accessed through the data access instructions are private data, then the terminal judges whether to establish connection with appointed devices or not; if the terminal establishes connection with the appointed device, then the terminal receives decoded data sent from the appointed devices; the terminal displays the private data according to the decoded data; if the terminal does not establish connection with the appointed devices, then the terminal refuses establishing the private data. The data storage access method is applied to mobile terminals.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Electronic invoice data processing method, device and system, medium and apparatus
ActiveCN108961030AGuarantee data securityAvoid manpower consumptionFinanceSpecial data processing applicationsInvoiceBlockchain
The present invention relates to an electronic invoice data processing method, device and system, a medium and an apparatus. The method comprising: obtaining drawer characteristic data associated witha drawer identifier; setting an electronic invoice issuing condition corresponding to the drawer identifier according to the drawer characteristic data, wherein the electronic invoice issuing condition corresponding to the drawer identifier is configured to control an electronic invoice issuing behavior performed through the drawer identifier; and correspondingly uploading the electronic invoiceissuing condition and the drawer identifier to a blockchain node, wherein the electronic invoice issuing condition and the drawer identifier correspondingly uploaded are configured to instruct the blockchain node to associate the electronic invoice issuing condition and the drawer identifier correspondingly uploaded and write the same in a data block. The solution provided by the application improves the electronic invoice issuing efficiency.
Owner:深圳市智税链科技有限公司
Energy internet trusted service management system and method based on block chain
InactiveCN108234456AAchieve transparencyAchieve decentralizationFinanceTransmissionTransaction managementDigital signature
The invention discloses an energy internet trusted service management system and method based on a block chain. The system comprises a trust establishment module, a transaction management module and an attack defense module. The trust establishment module establishes trusted service interaction between different objects by using the block chain and a digital signature method, and provides a trustworthy environment for the service interaction by using the block chain technology; the transaction management module provides transaction management between a service provider and a server requester by using the transaction between an intelligent contract and block chain management service provider and the server requester; and the attack defense module is used for defending against external attacks, preventing network attacks and malicious node spoofing, and ensuring the credibility and security of the transaction. According to the energy internet trusted service management system and method,by adoption of the block chain technology, the transparency and decentralization of the energy internet trusted service management can be realized, the maintenance cost is greatly reduced, fast response can be made to the network change of the energy internet, and the data security of the block chain and the whole network security are protected.
Owner:NANJING UNIV OF POSTS & TELECOMM
Computer intelligent energy-conserving method
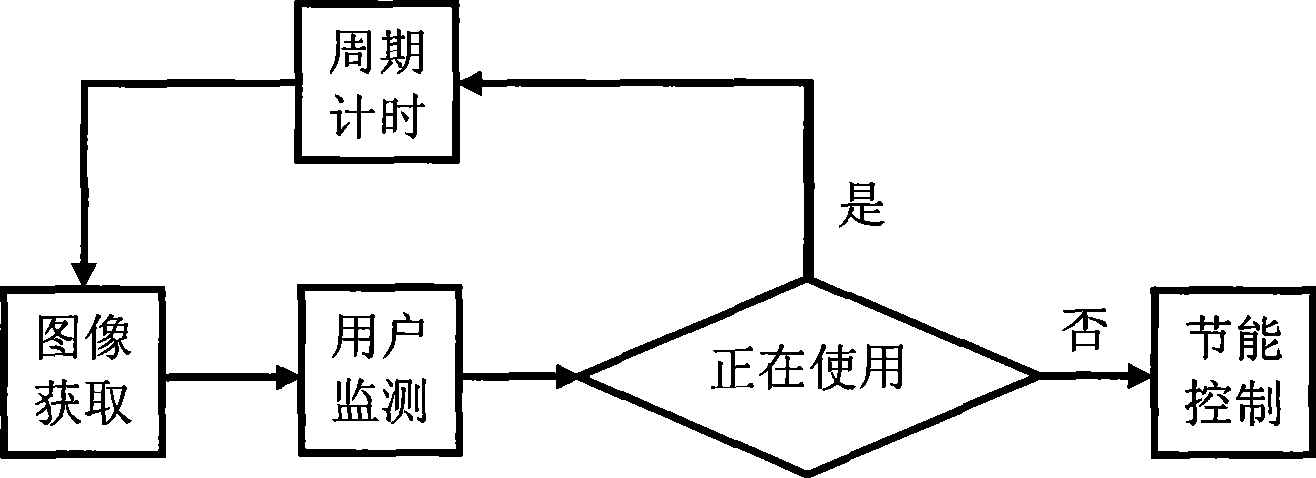
ActiveCN101458560AMonitor usage statusRealize smart energy savingEnergy efficient ICTCharacter and pattern recognitionSleep timePower management system
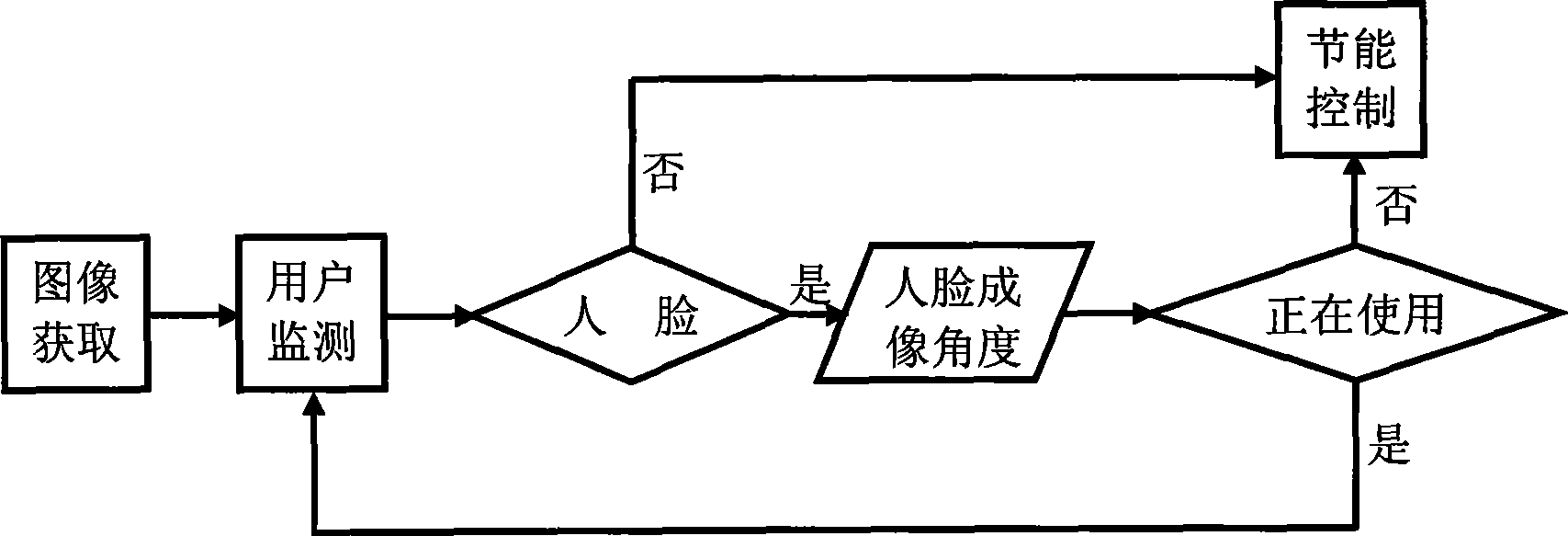
The invention relates to a computer save energy method. The method includes steps as follows: an image information collected by an image obtaining module is sent to a user monitor module, the user monitor module scans the image information and sends result to an energy saving control module, if no facial image, the energy saving control module processes energy saving control to computer, if facial image being, the energy saving control module keeps normal working state of computer. The method solves problem that computer consumes energy still when a user is disturbed by something and the computer is not turned off or is adjusted to waiting, sleeping modes in computer power management system with existing technique, and waiting or sleeping time interval is overlong, and inconvenient using caused by user using manual switching energy saving mode. The method has energy saving function with human-computer communication mode, the computer is controlled to enter energy saving mode when no people is ahead on the computer or people does not operate computer, and can realize energy saving control when user leaves and using computer when user comes, the method is convenient and can save energy efficiently.
Owner:NANJING UNARY INFORMATION TECH
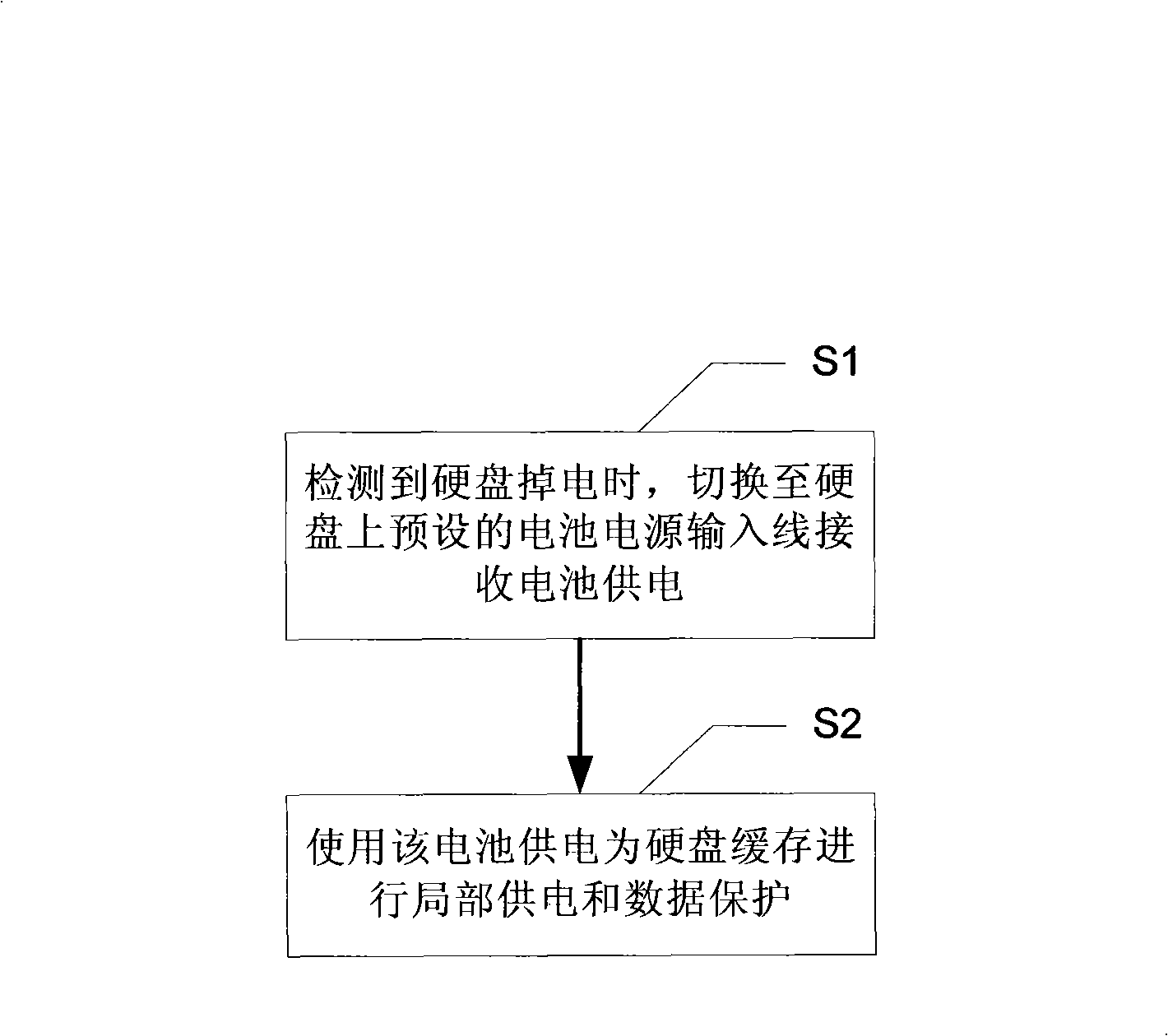
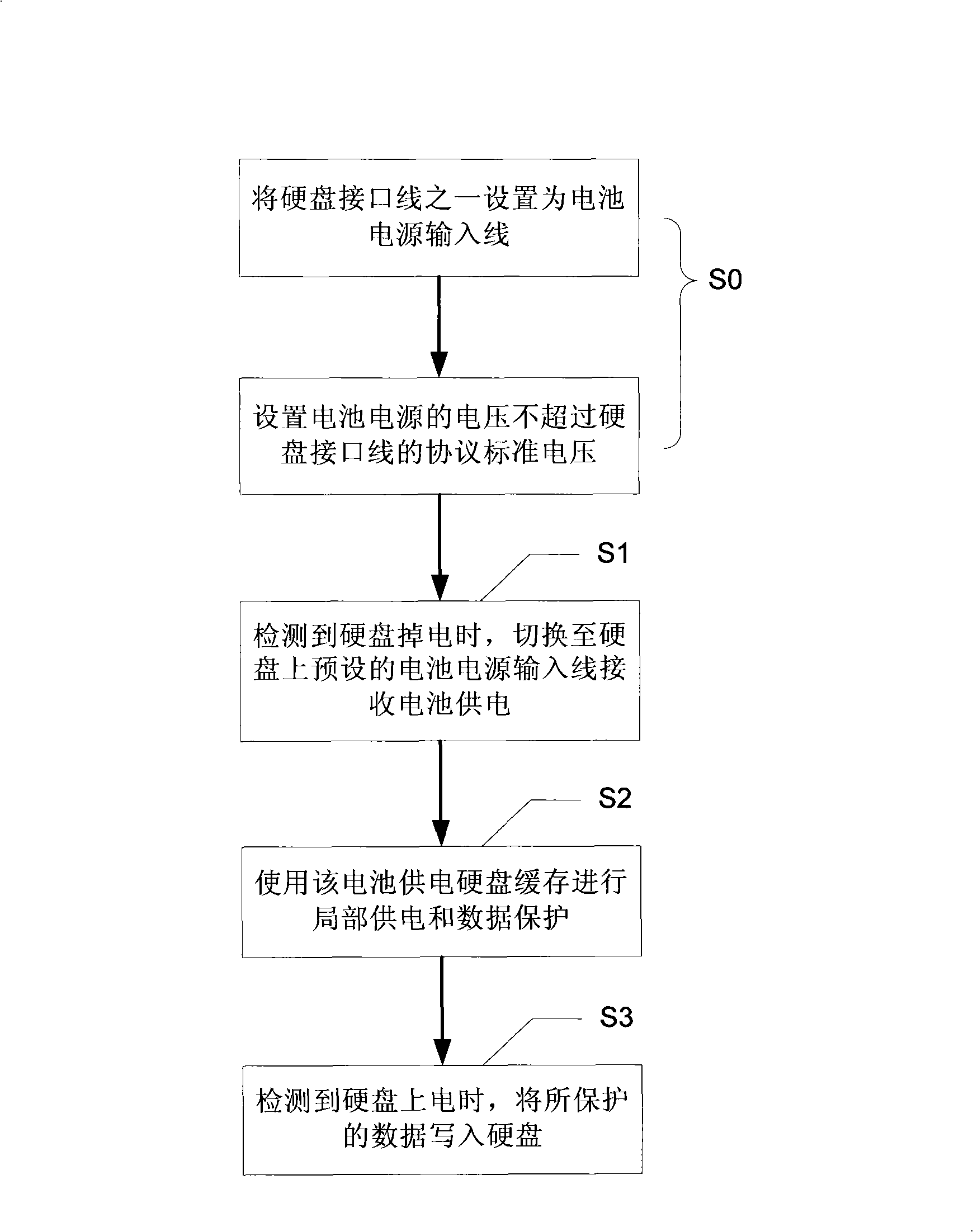
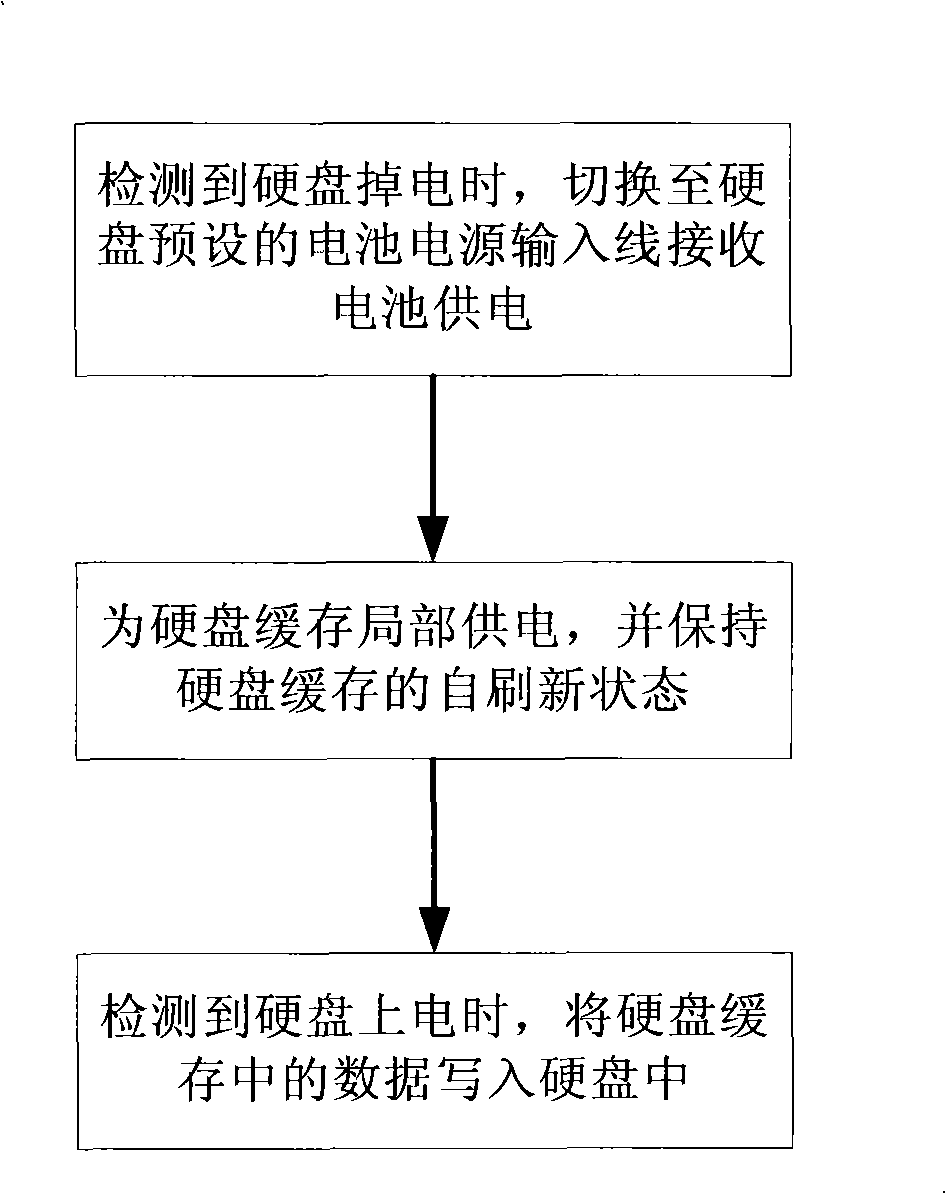
Hard disk power down protection method, device and hard disk, and hard disk power down protection system
InactiveCN101286086AGuarantee data securityLow costInput/output to record carriersRecord information storageElectricityElectrical battery
Owner:NEW H3C TECH CO LTD
Multi-place multi-center data center dual-enabling method and system
InactiveCN106506588AGuarantee data securityAvoid wastingDatabase distribution/replicationTransmissionData exchangeFibre Channel switch
The invention provides a multi-place multi-center data center dual-enabling method and a multi-place multi-center data center dual-enabling system. The system comprises a data switch used for achieving interconnection of two layers of a data center and achieving an OTV technology; an intelligent DNS multi-site selector used for achieving load balance of multiple data centers by accessing through domain names; an application load balancer used for achieving application load balance of the multiple data centers; and an MDS optical fiber channel switch used for achieving SAN extended storage among the multiple data centers.
Owner:BEIJING XJ ELECTRIC +1
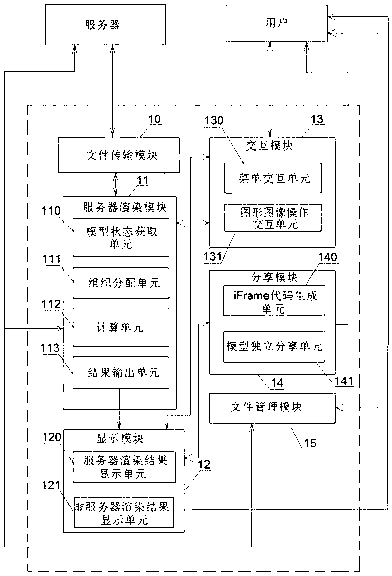
IFrame embedded Web3D (Web three-dimensional) system based on cloud rendering
InactiveCN103077239ASupport concurrent accessGuarantee data securityImage data processingSpecial data processing applicationsWeb siteFile transmission
The invention relates to an iFrame embedded Web3d (Web three-dimensional) system based on cloud rendering. The iFrame embedded Web3D system comprises a file transmission module, a server rendering module, a display module, an interactive module, a sharing module and a file managing module, wherein the server rendering module comprises a model state acquiring unit, an organizing and distributing unit, a calculating unit and a result output unit. According to the system, various large or extra-large three-dimensional models can be directly and smoothly browsed, operated and controlled on webpages through browsers without installing any plugin; hardly any requirement is made on a display terminal, and various mobile intelligent terminals can be supported to view the models smoothly; the generation of iFrame codes can be supported, and models are embedded into various different platforms or websites; multiuser concurrent access can be supported; and since clients only can acquire rendered pictures instead of model data, so that the data security of users is well guaranteed.
Owner:SHANGHAI UNIVERSITY OF ELECTRIC POWER
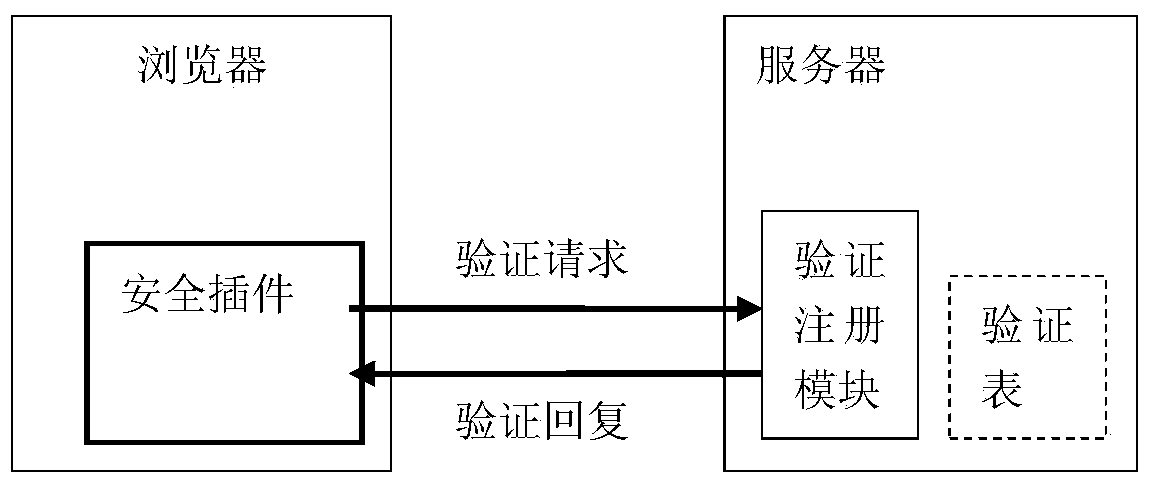
Safety protection system and method for webpage access through browser
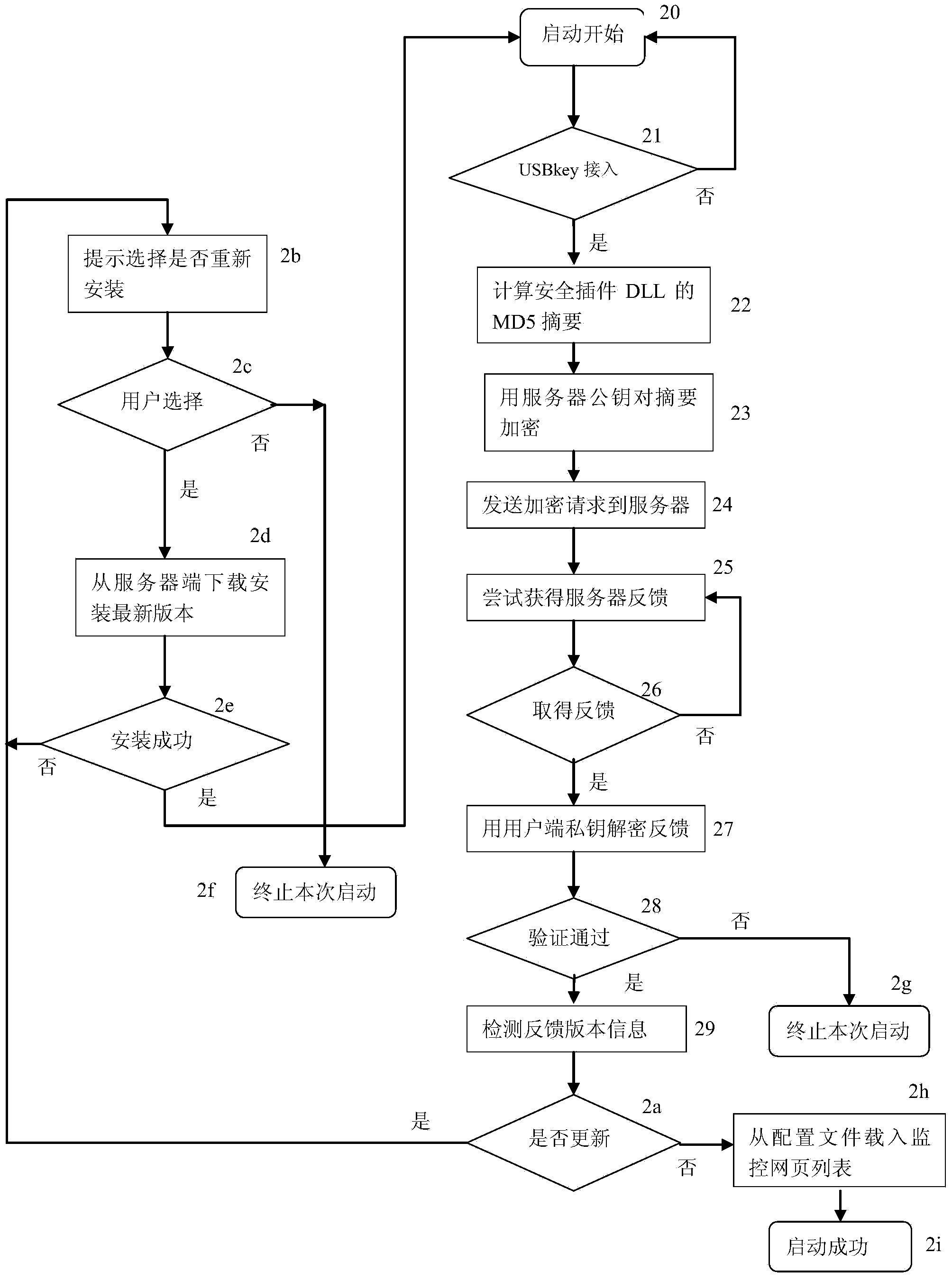
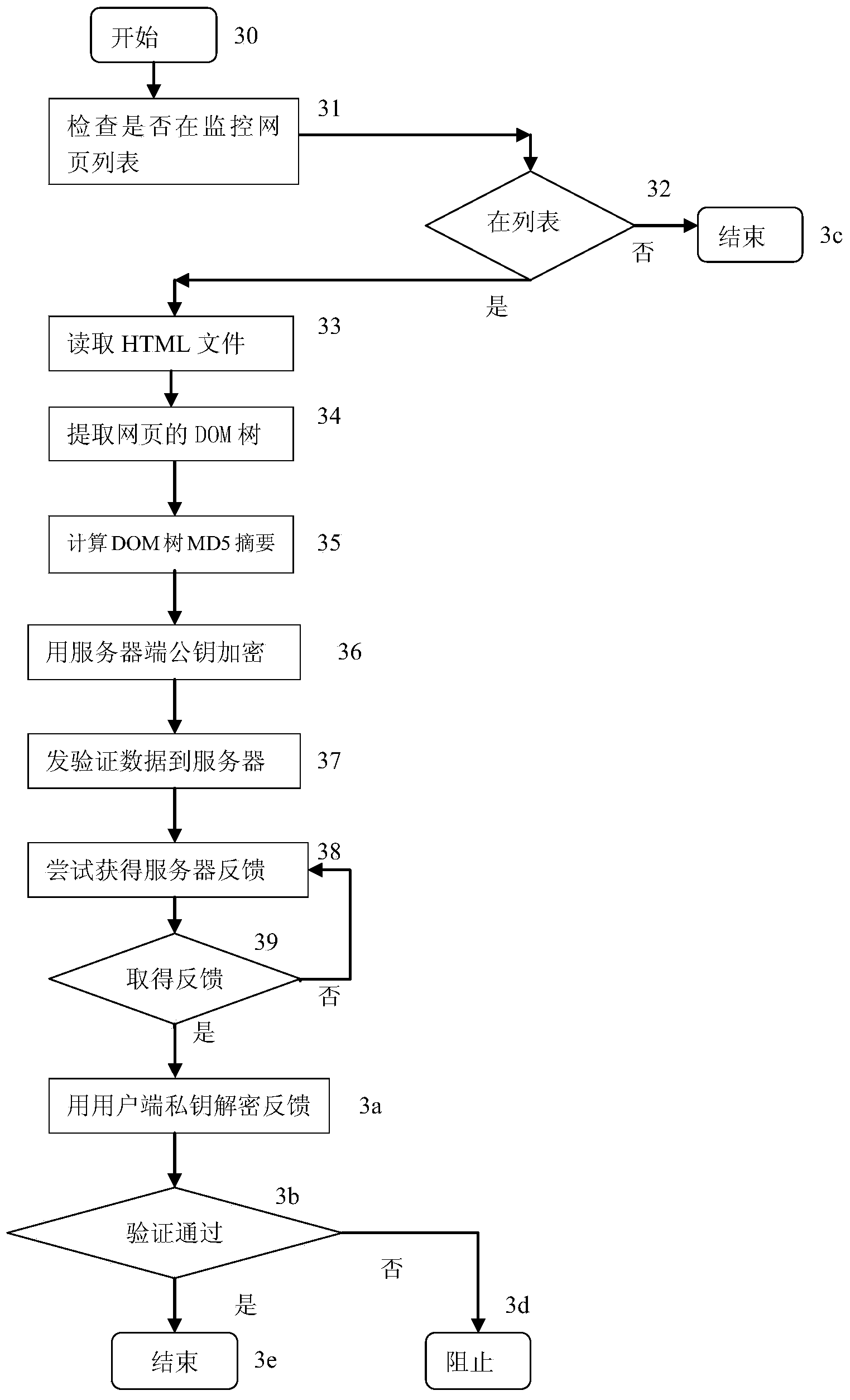
ActiveCN103685277APrevent cheatingGuarantee data securityTransmissionSpecial data processing applicationsTransaction serviceWeb page
The invention discloses a safety protection system for webpage access through a browser. The system comprises a user side, the browser, security plug-ins of the browser, a server side, a verification and registration module and a verification table. The invention further provides a safety protection method for webpage access through the browser. The method includes the steps that the security plug-ins are initialized and installed; the security plug-ins and important web pages are registered, and registration information is stored in the verification table of the server side; the browser starts the security plug-ins, and whether the kernel of the browser and the security plug-ins are corrected or not are verified; abstract information of DOM trees of the important web pages are calculated, and webpage verification requests are sent to the server side; the server side receives the webpage verification requests sent by the security plug-ins and extracts registered corresponding webpage abstract information, the registered corresponding webpage abstract information is verified, and verification feedback information is sent back; the browser is driven to continue executing and displaying web pages or to stop having access to web page operations according to the verification feedback information. Accordingly, safety protection is provided for accessing the important web pages, and data and fund security of users in network transaction service is guaranteed.
Owner:NANJING UNIV
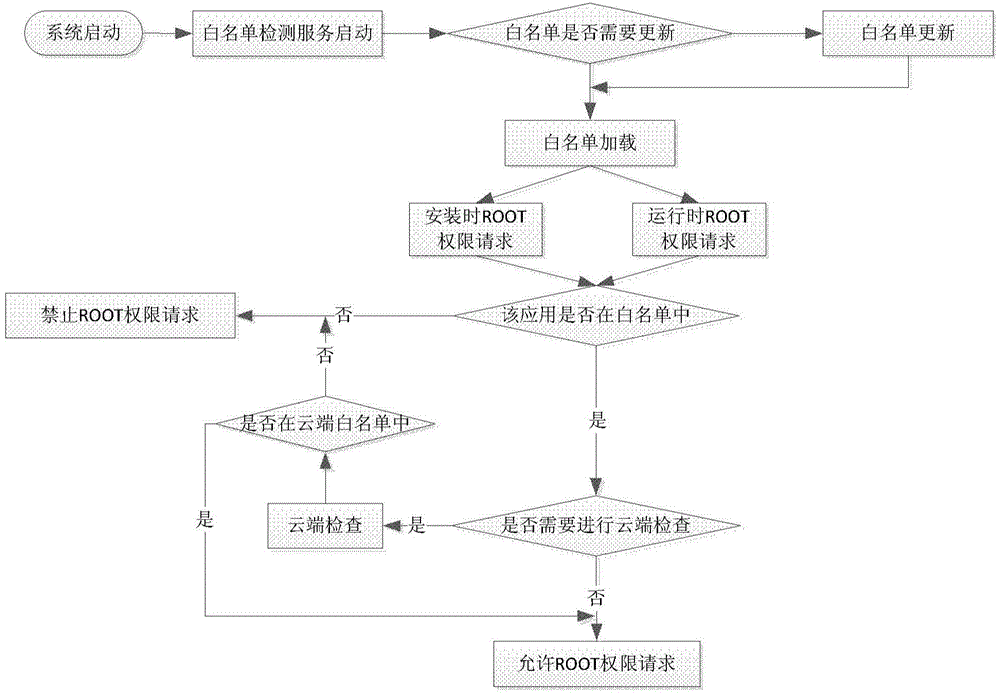
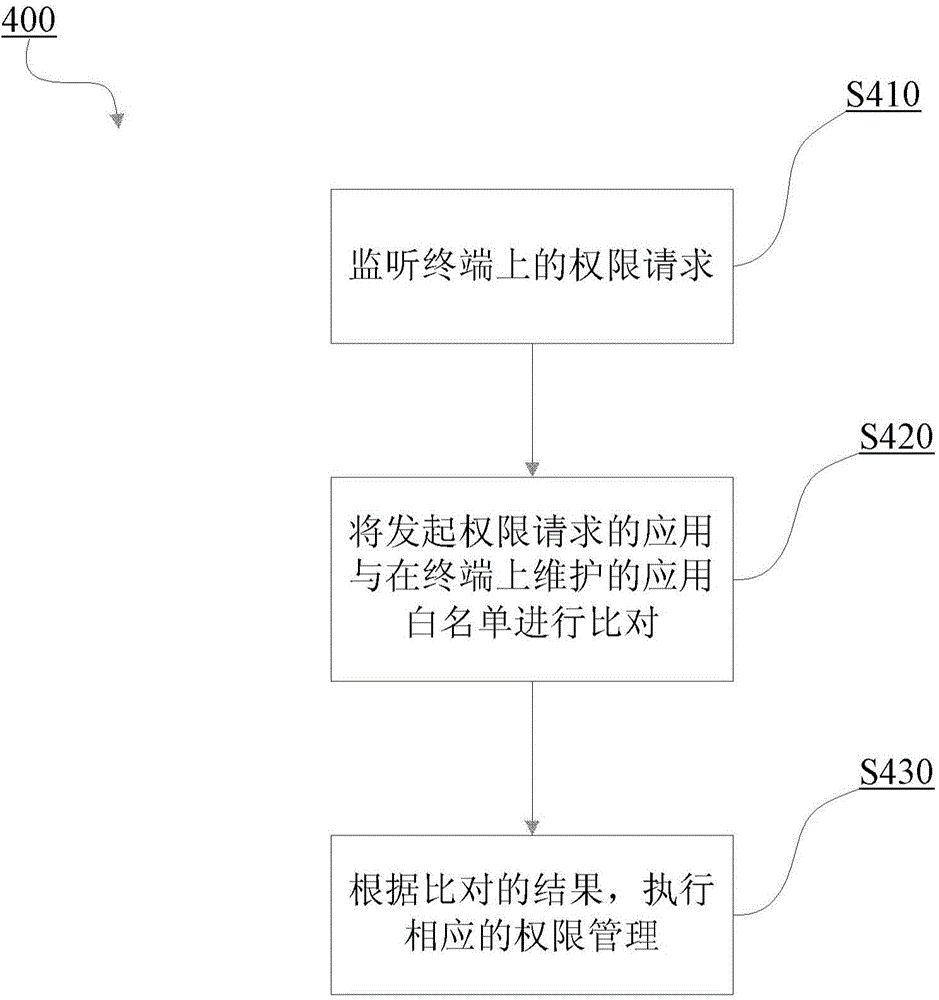
Method for terminal authority management and terminal
InactiveCN104573435AReduce instances of misauthorization by malicious applicationsGuarantee data securityDigital data authenticationComputer terminalDatabase
The invention provides a method for terminal authority management and a corresponding terminal. The method comprises the following steps: a) monitoring an authority request on the terminal; b) comparing an application which initiates the authority request with an application white list which is maintained on the terminal; c) executing corresponding authority management according to a comparison result.
Owner:BEIJING NETQIN TECH
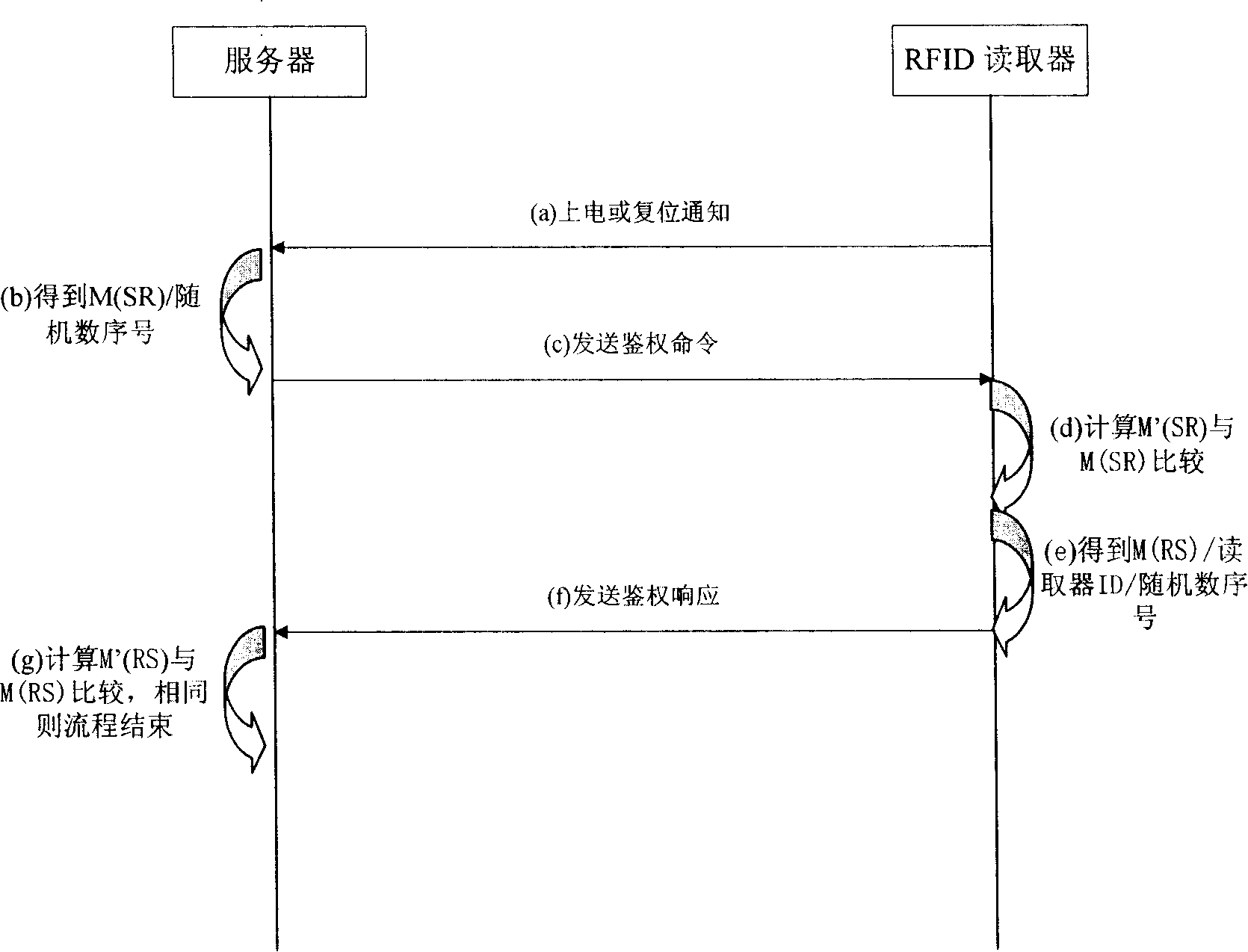
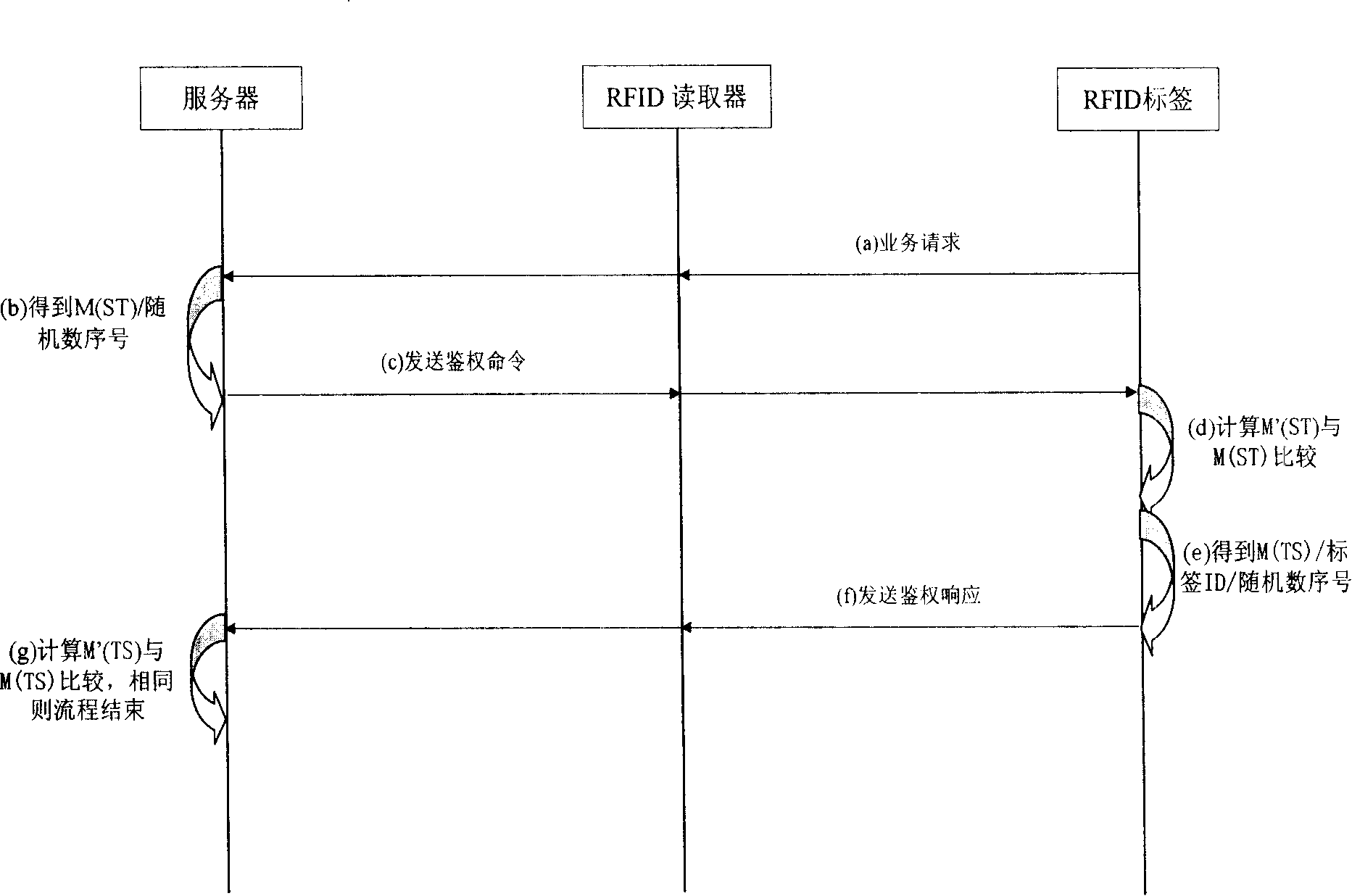
Method and system for protecting radio frequency identification tag and reader data safety
ActiveCN101211401APrevent illegal theftGuarantee data securityUser identity/authority verificationSensing record carriersTelecommunications networkRadio frequency
The invention relates to a method and system to protect data safety of RF identification (RFID) tags and acquisition devices, so as to fulfill bidirectional authority verification between a network server and RFID tags and acquisition devices; therefore, the invention can effectively prevent illegal access on RFID tags and acquisition devices that have not passed safety certification. When effectively using a matured and simple arithmetic structure, the RFID system has no higher requirement for system hardware, so as to effectively lower composition cost between the RFID system and prior telecom network.
Owner:CHINA TELECOM CORP LTD
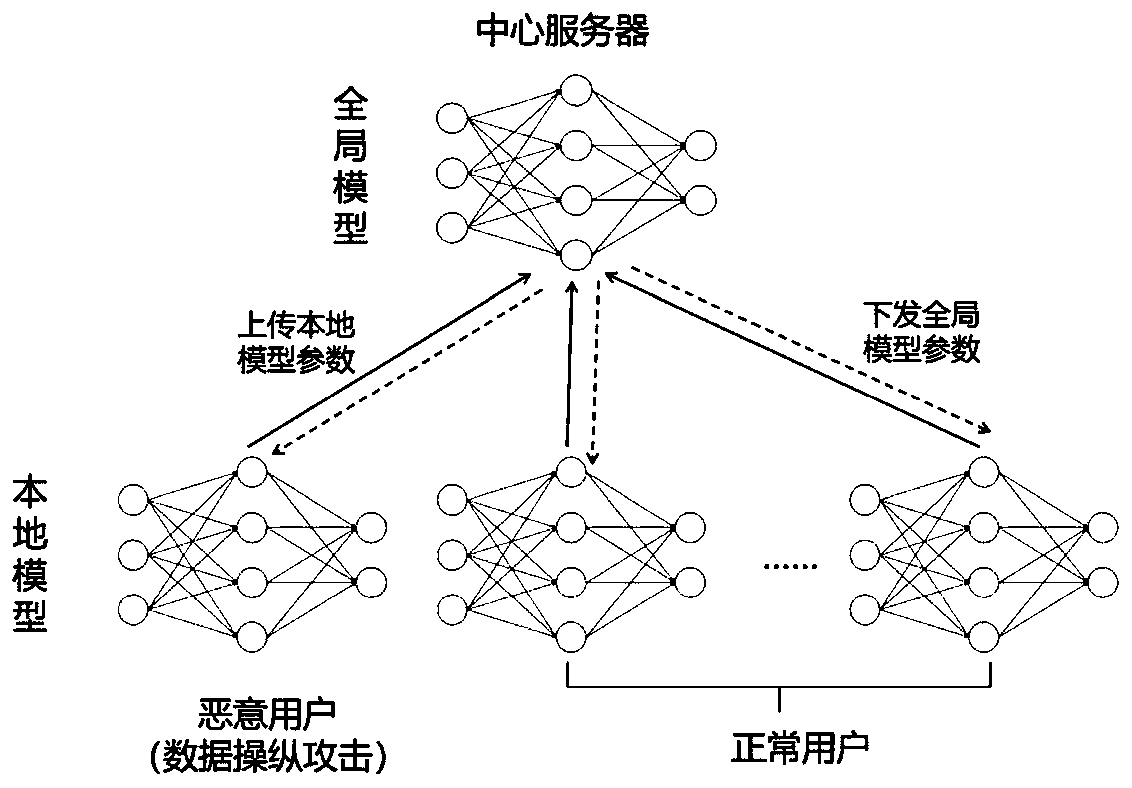
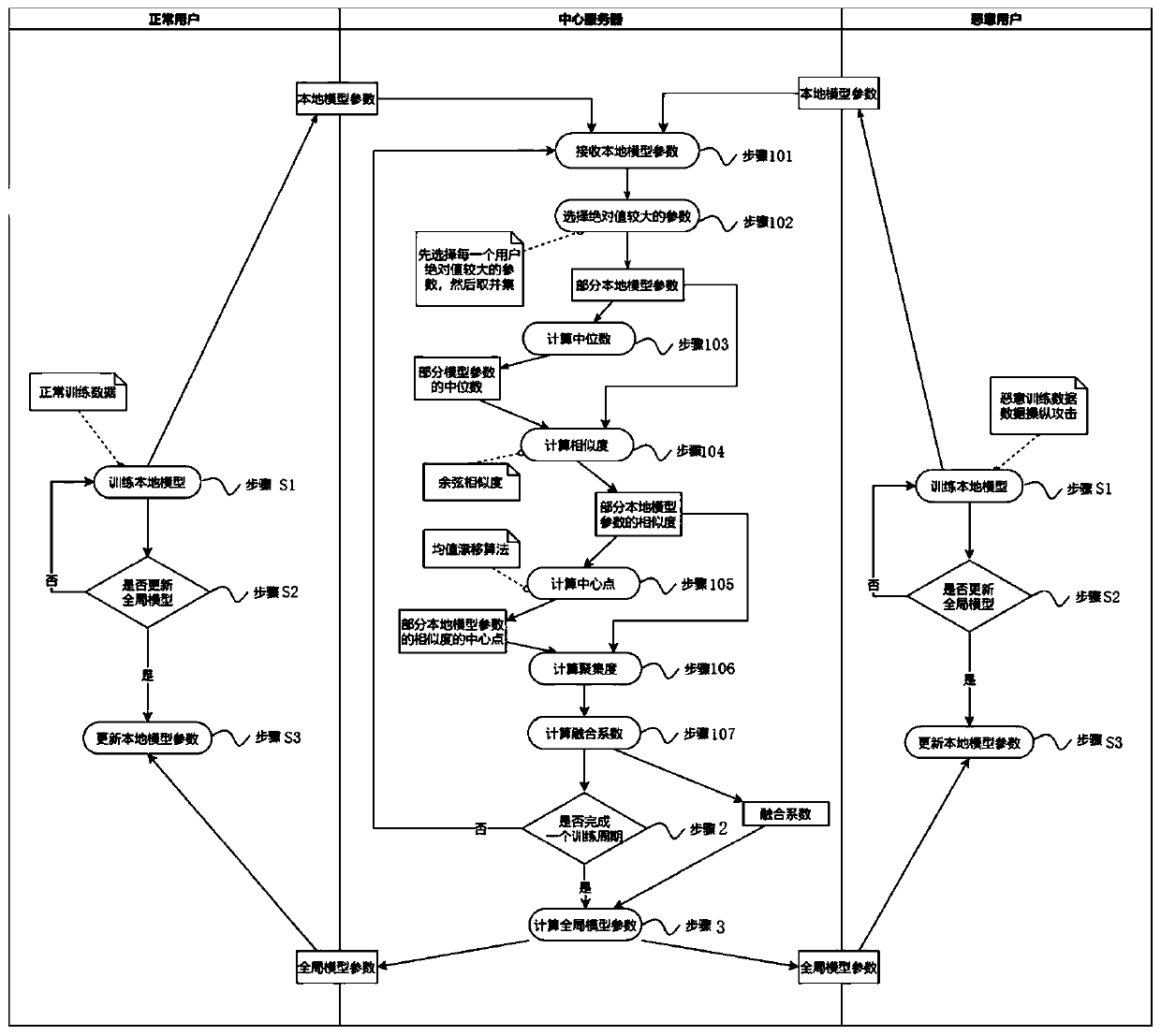
Security defense method for data manipulation attacks in federated learning
ActiveCN111460443AProtection securityGood effectCharacter and pattern recognitionDigital data protectionAttackEngineering
The invention discloses a security defense method for data manipulation attacks in federated learning. The method comprises the following steps: 1, enabling a central server to receive local model parameters uploaded by users, and calculating the similarity degree of the local model parameters uploaded by each user and a fusion coefficient corresponding to each user, wherein the local model parameters are local model parameters obtained after the users adopt private training data to train for one round; 2, after the central server receives the local model parameters of the local users in one period, enabling the central server to calculate a weighted average value of the local model parameters of each user according to the fusion coefficient to obtain global model parameters, wherein the period is a preset local model parameter updating round number; 3, issuing the global model parameters to the corresponding users, and enabling the users to update the local model parameters after receiving the global model parameters.
Owner:NANJING UNIV
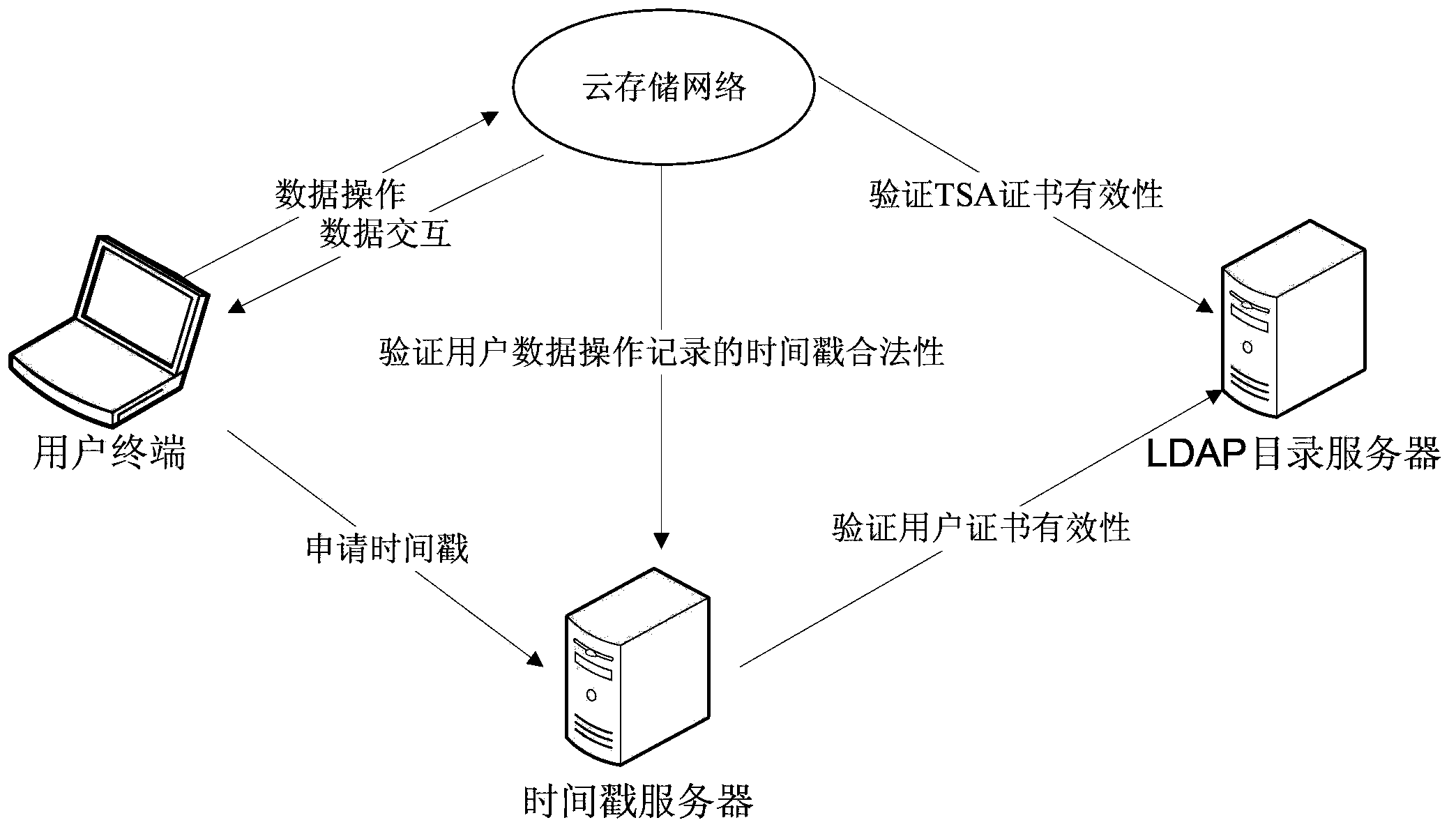
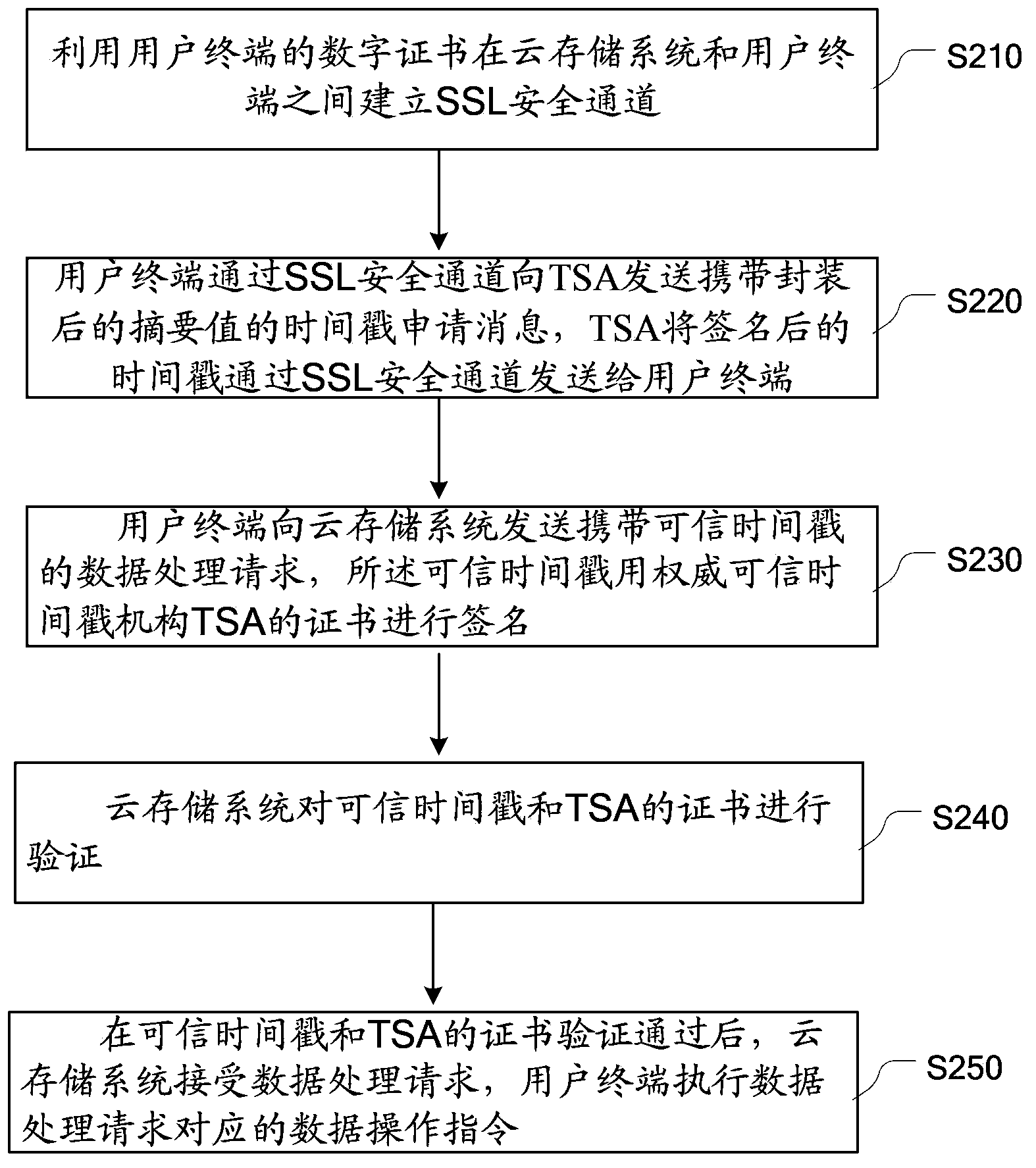
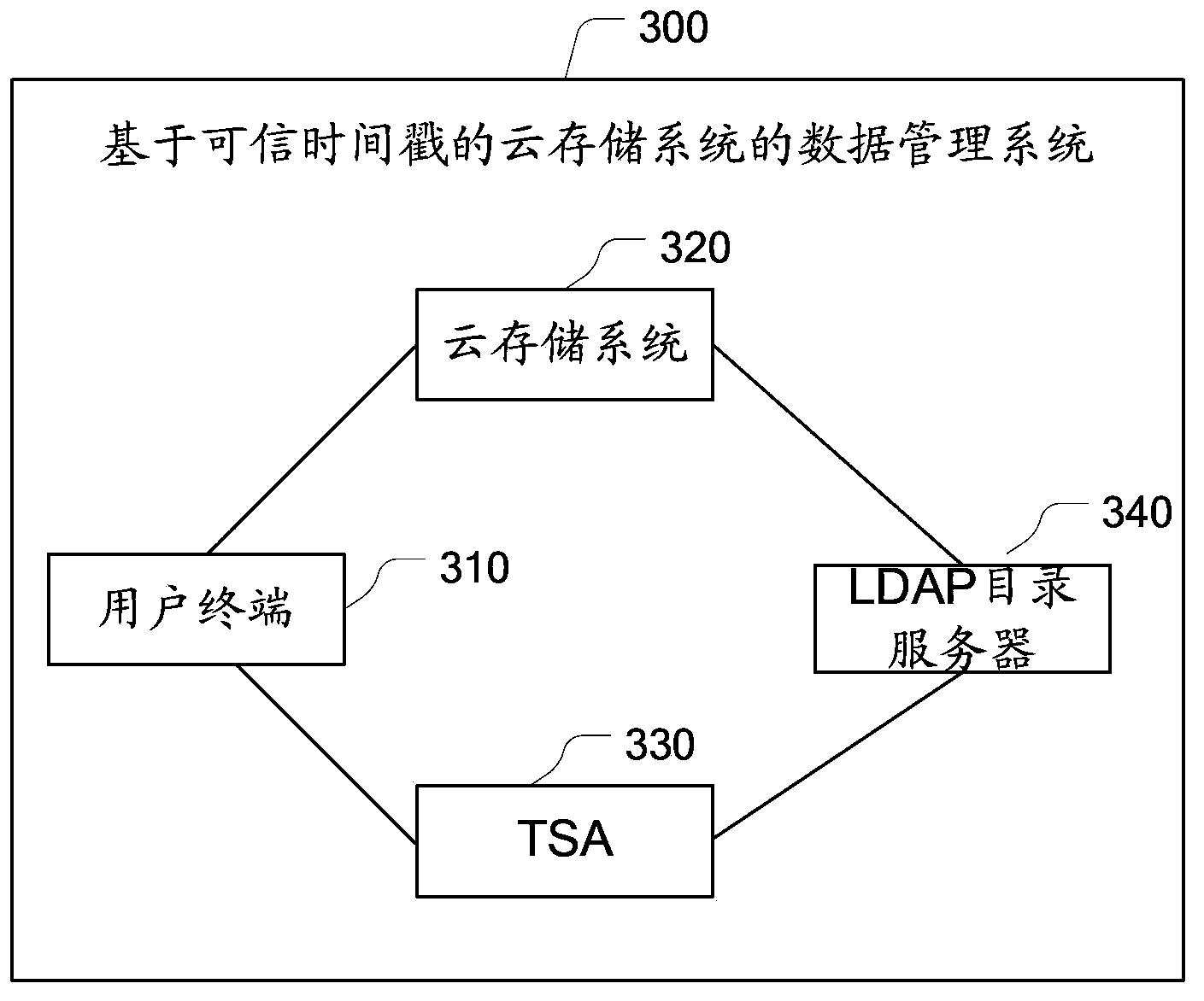
Data management method and system of cloud storage system based on trusted timestamp
InactiveCN104348870ADoes not increase the complexity of the service processGuarantee data securityUser identity/authority verificationThird partyTimestamp
The embodiment of the invention provides a data management method and system of a cloud storage system based on a trusted timestamp. The method mainly includes the following steps: the cloud storage system receives a data processing request which is sent by a user client and carries the trusted timestamp signed through use of a TSA certificate; and the cloud storage system verifies the trusted timestamp and the TSA certificate and after the trusted timestamp and the TSA certificate pass the verification, the cloud storage system receives the data processing request and the user client executes a data operation instruction corresponding to the data processing request. Through the third-party trusted timestamp, the cloud storage system is capable of carrying out effective management and audit on user data and carrying out verification and recording and filing on data operation records of a user so that the security of user operations and the authenticity of cloud storage data are guaranteed and it is achieved that the data security of the user is guaranteed while the complexity of the service procedure of the cloud storage system is not increased.
Owner:AEROSPACE INFORMATION
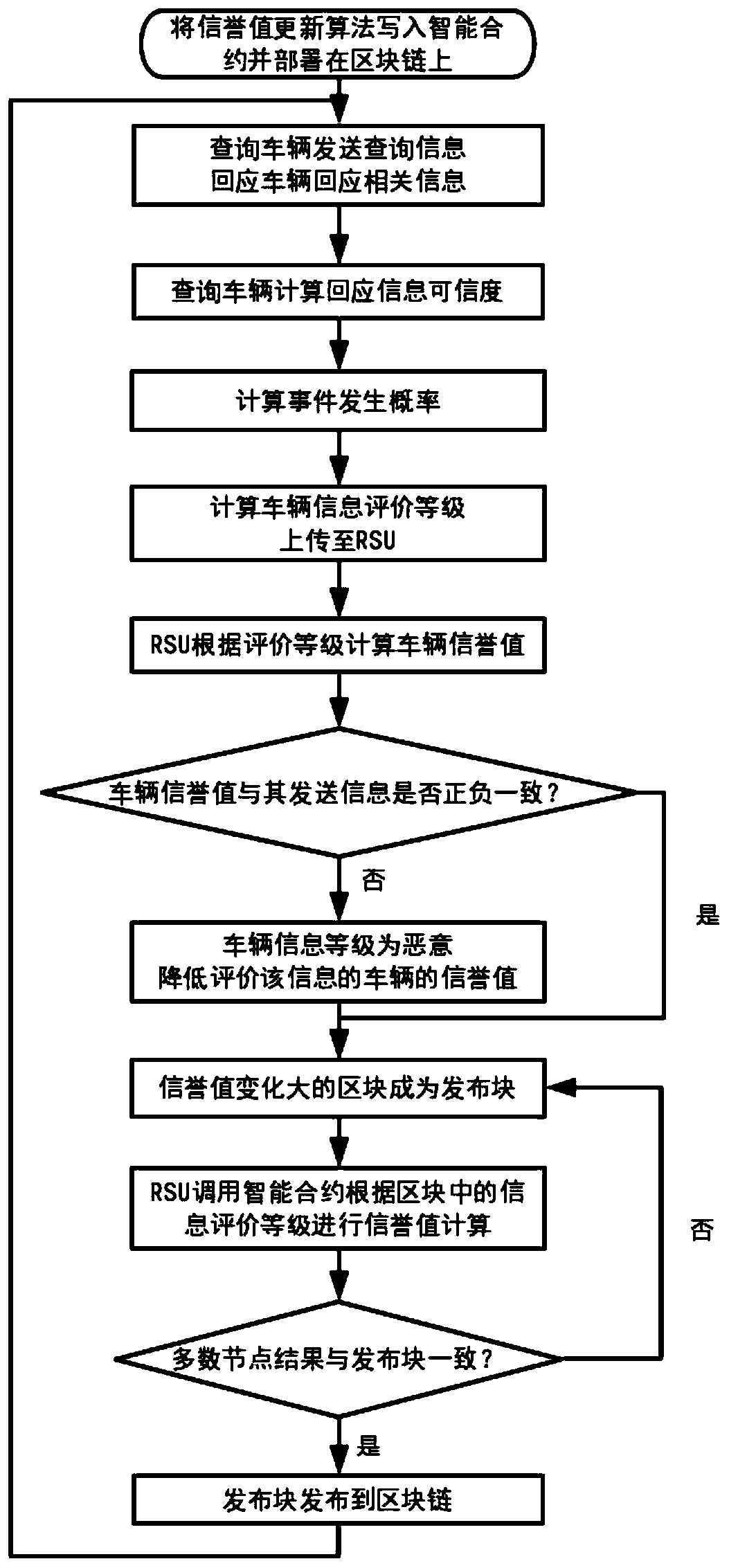
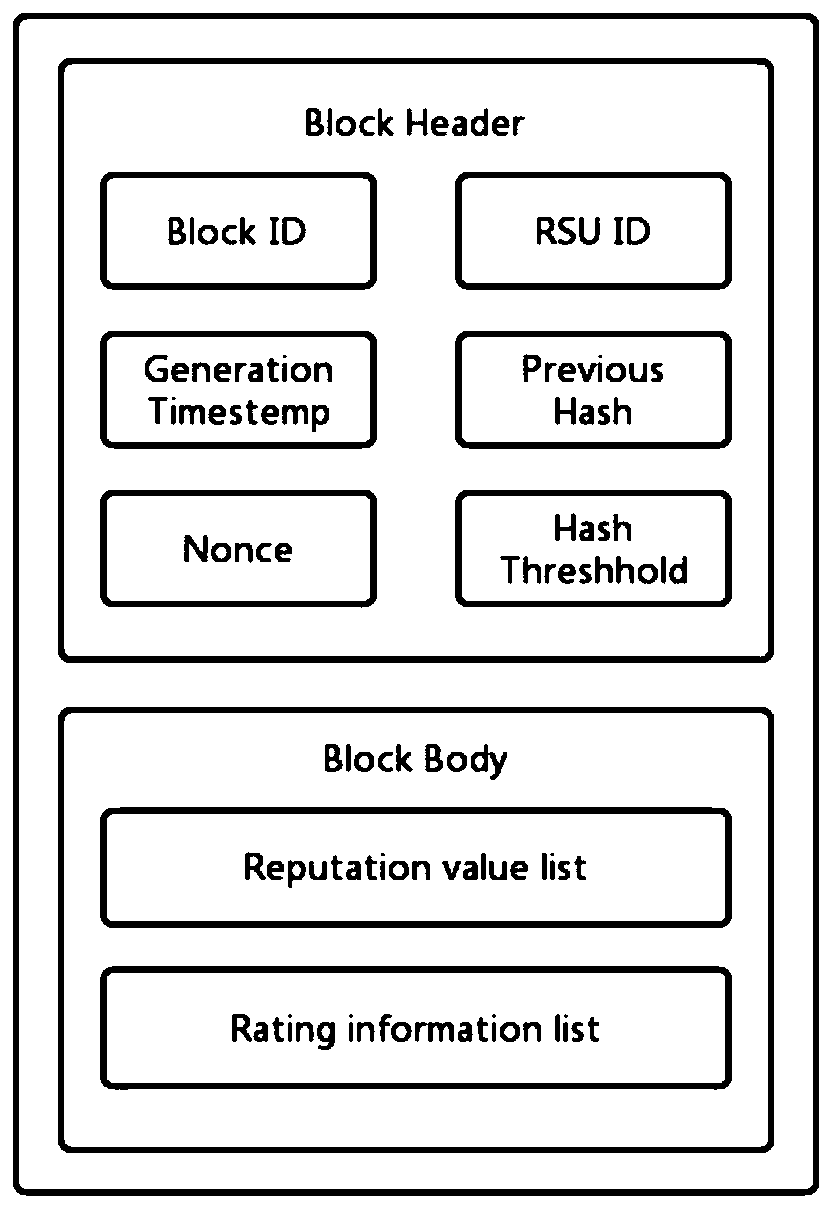
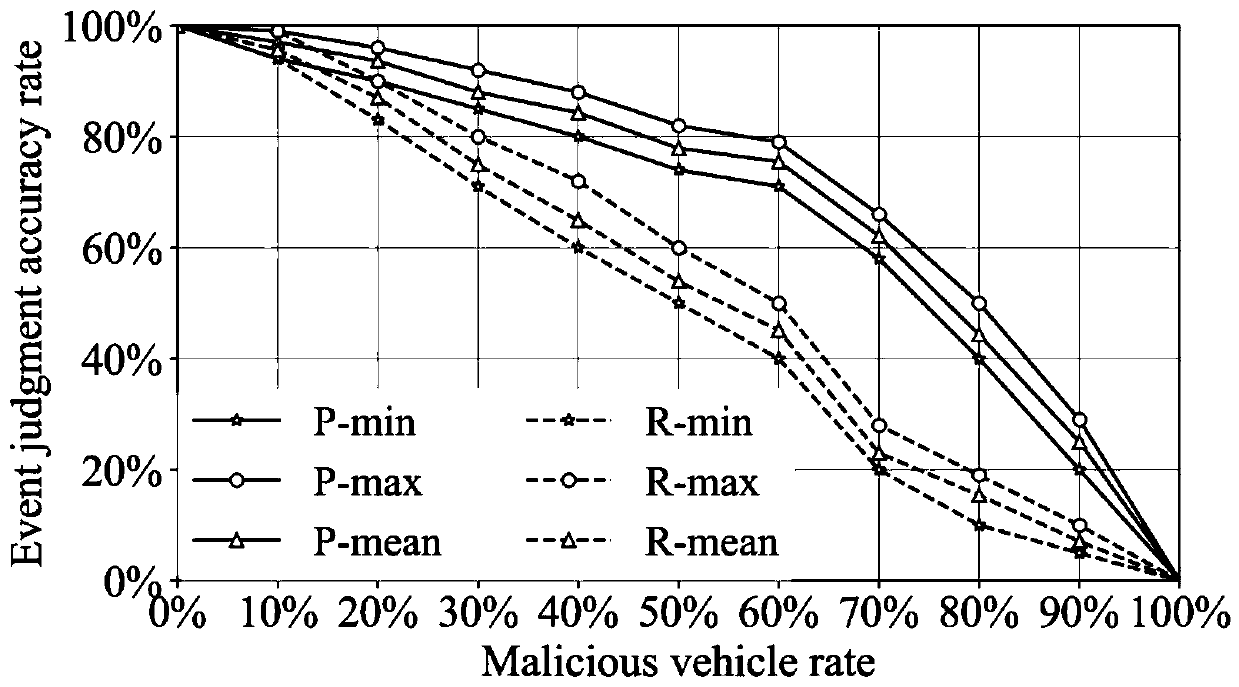
Internet-of-Vehicles trust management method based on block chain
ActiveCN111447177ASecurityInformation judgment is accurateDatabase distribution/replicationDigital data protectionBlockchainData security
The invention discloses an Internet-of-Vehicles trust management method based on a block chain, and the method comprises the steps: firstly calculating the credibility of received vehicle informationrelated to an event, judging the occurrence probability of each event through the credibility of the vehicle information, generating a rating for transmitted information, and uploading the rating of the vehicle information to nearby RSUs; enabling the RSU to call a reputation value updating method in an intelligent contract deployed on a block chain to calculate a vehicle reputation value, whereinthe calculated vehicle reputation value and the collected rating information are all packaged into a block; through a consensus mechanism combining PoW and PoS, ensuring RSUs with larger change of vehicle reputation values to serve as miner nodes to publish blocks; and enabling other RSUs to re-use the reputation value updating method of the smart contract to re-calculate the rating in the release block, and if the calculation results of most nodes are consistent with the data in the release block, releasing the release block to the block chain to realize Internet-of-Vehicles trust management. According to the invention, the data security is ensured, and the accuracy of event judgment in the Internet of Vehicles is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Access control system and access control method of fine-grained privacy security
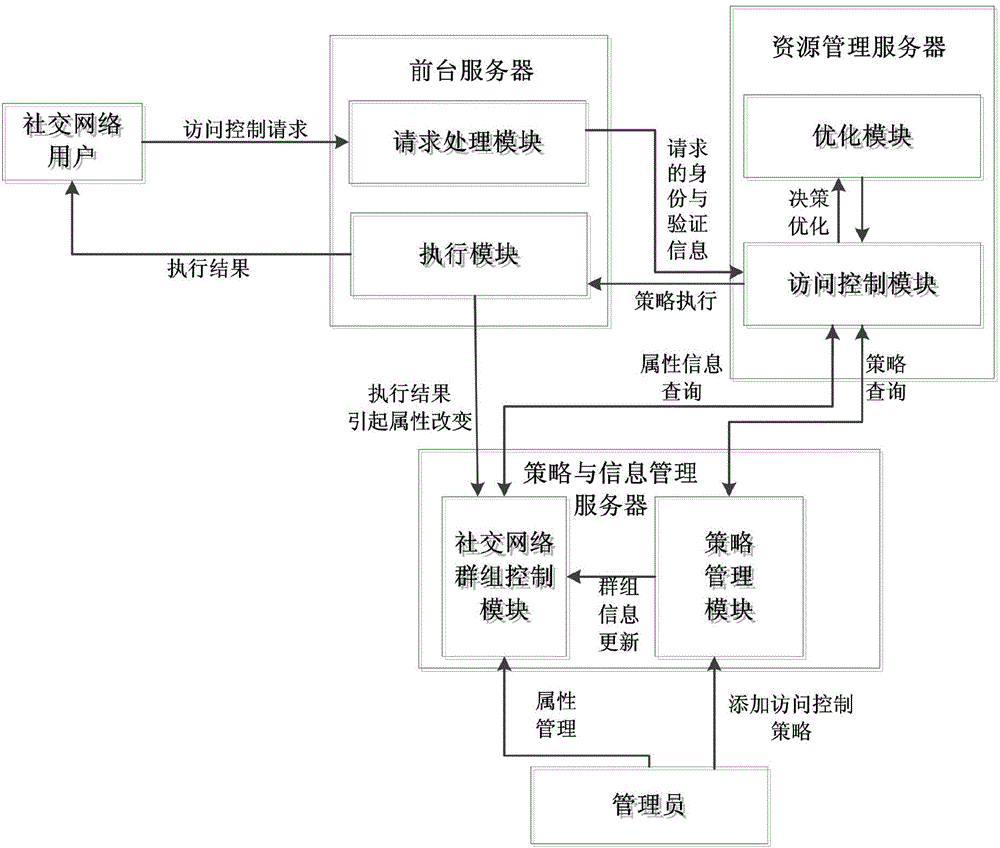
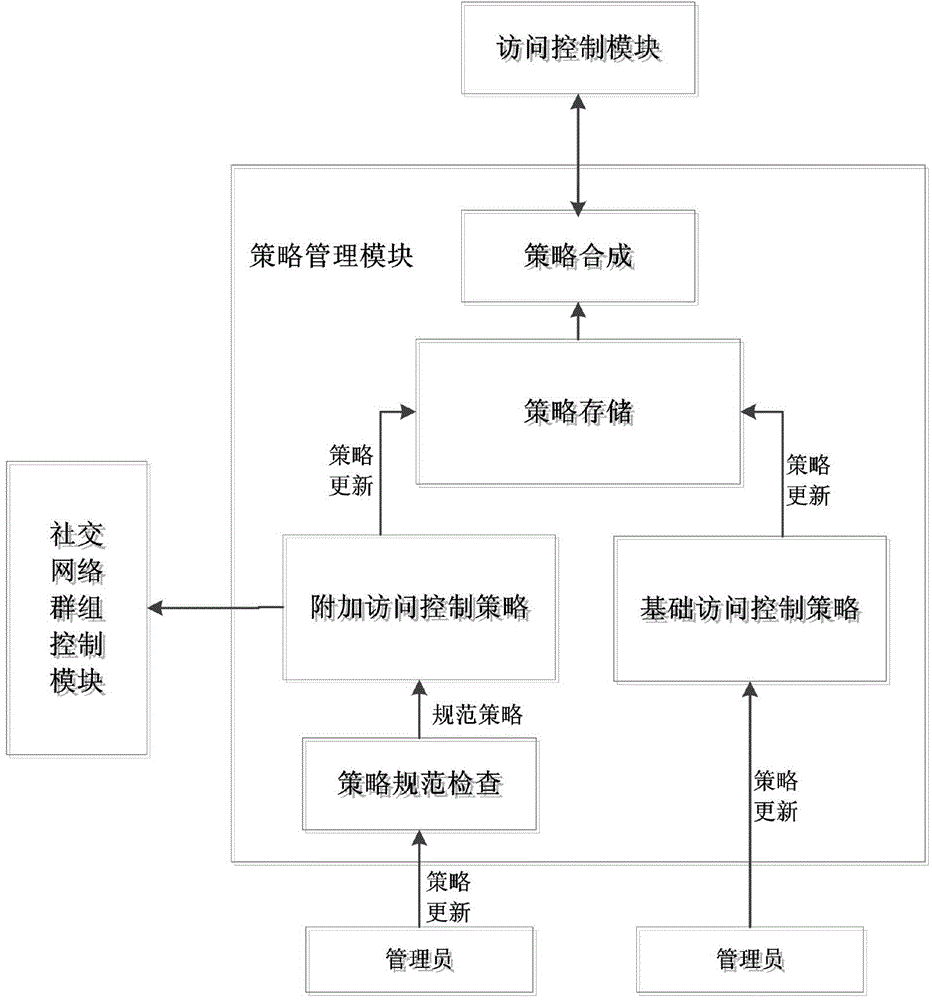
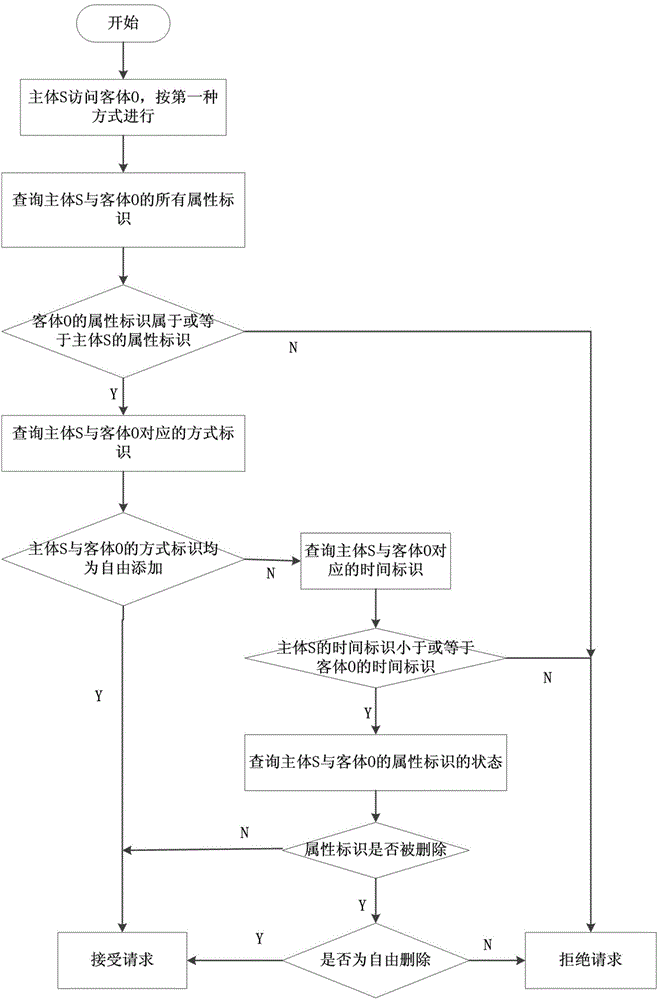
ActiveCN104683362AGuarantee data securityMeet fine-grained privacy protection requirementsTransmissionUser privacyMedia access control
The invention discloses an access control system and an access control method of the fine-grained privacy security. The access control system of the social networking service fine-grained privacy security comprises a strategy management module, a social networking service group control module, a request processing module, an access control module, an optimizing module and an execution module. The strategy management module is used for maintaining and combining access control strategies; the social networking service group control module is used for maintaining all attribute sets; the request processing module is used for verifying identification; the access control module is used for carrying out the decision for the access request to obtain a decision result; the optimizing module is used for carrying out the exclusiveness processing on the decision result; the execution module is used for executing the decision result. The access control system is used for controlling the security of data flow in the social networking service, a more fine-grained access control mechanism is provided for a user, the user privacy can be protected, and the application requirement of the social networking service can be met.
Owner:HEFEI UNIV OF TECH
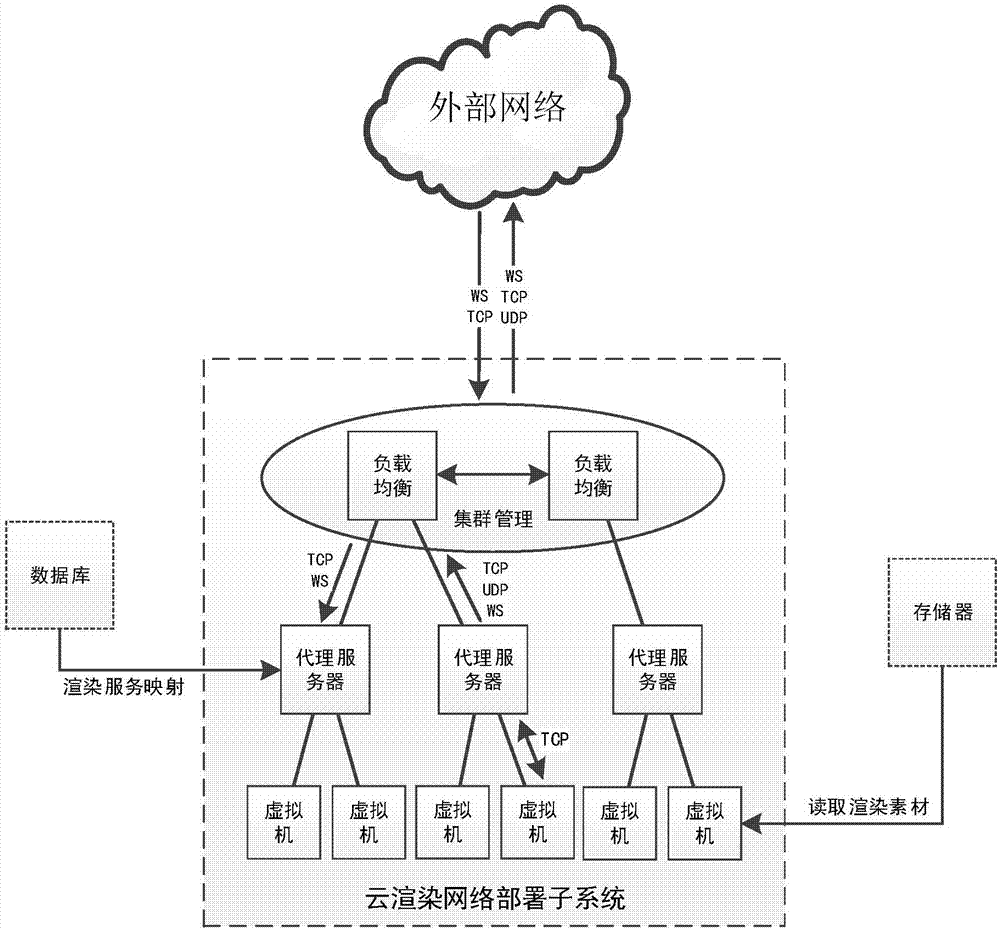
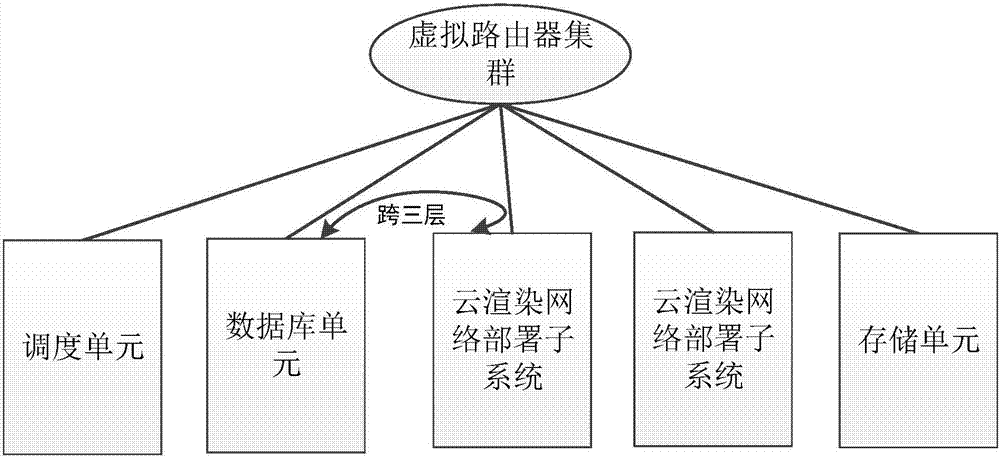
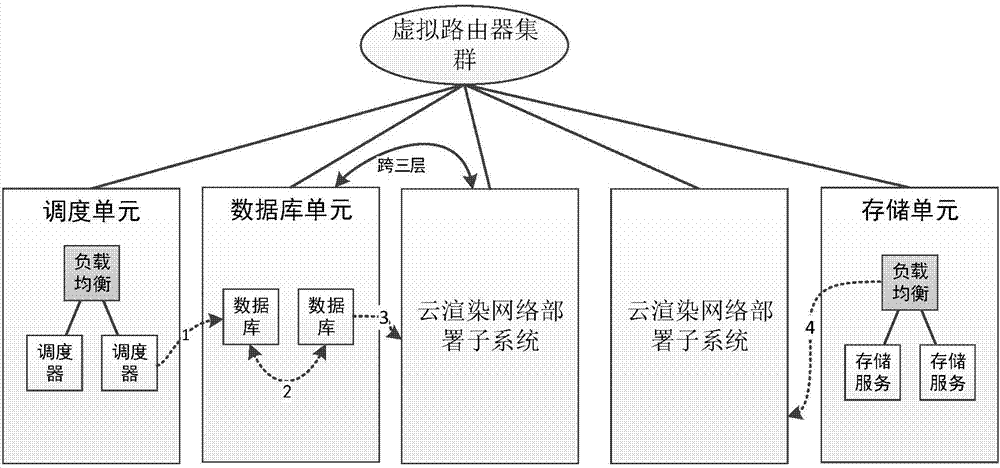
Cloud rendering network deployment sub-system, system and cloud rendering platform
The invention discloses a cloud rendering network deployment sub-system. The cloud rendering network deployment sub-system comprises a proxy server connected with an external network; the proxy server is further connected with at least one virtual machine; the proxy server comprises a control information processing unit and a data information processing unit; the control information processing unit is used for receiving the control information sent by the external network, analyzing the control information, converting the control information into the TCP protocol encapsulated information, and sends the TCP protocol encapsulated information to the corresponding virtual machine; the data information processing unit is used for receiving the data information sent by the virtual machine, converting the data information into the protocol encapsulation way corresponding to the external network, and sending the corresponding protocol encapsulation way to the external network. Through the above-mentioned adaption, the cloud rendering network deployment sub-system disclosed by the invention can support the data transmission among multiple network protocols and facilitate the different clients to access a cloud server, and the user experience is good.
Owner:成都云创互联信息技术有限公司
Cloud storage method and system
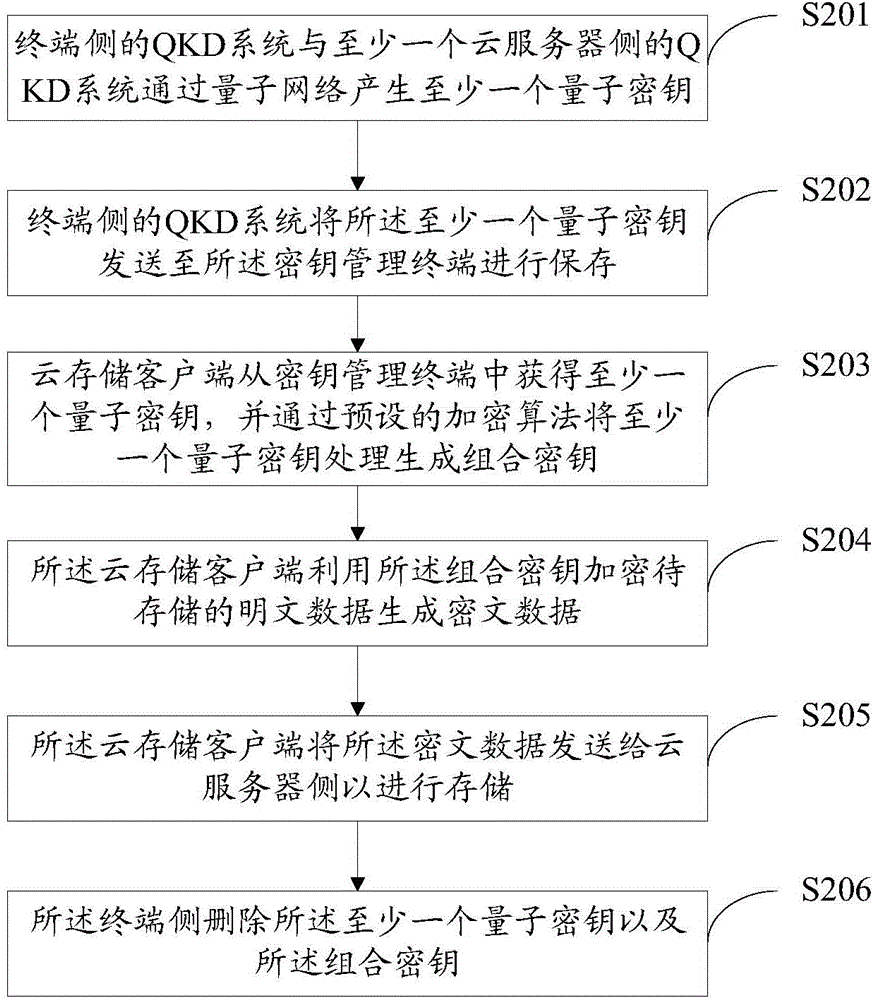
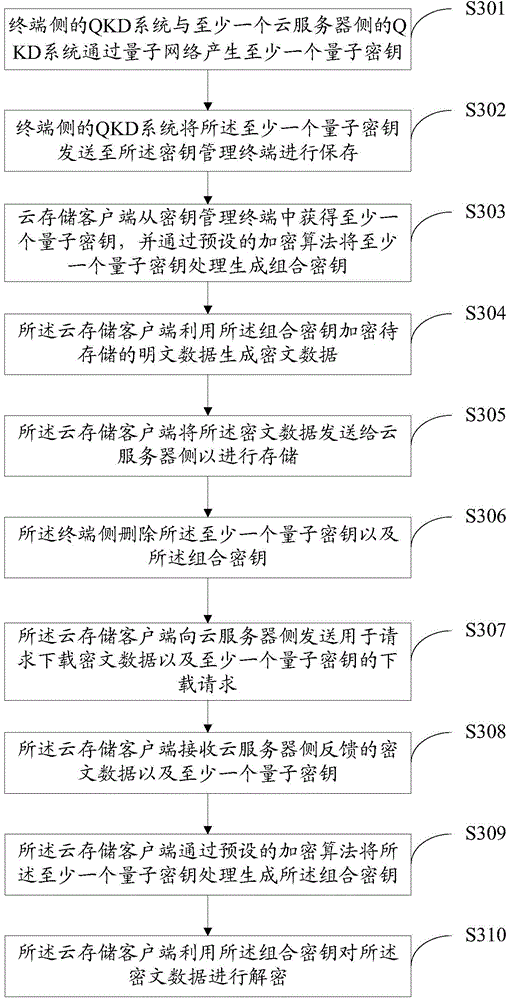
ActiveCN106209739AGuarantee data securityQuantum computersComputer security arrangementsQuantum networkKey distribution
The invention discloses a cloud storage method and system. At least one quantum key is generated through a quantum network by a QKD system at a terminal side and at least one QKD system at a cloud server side; and a cloud storage client side processes the at least one quantum key through a pre-set encryption algorithm so as to generate a combined key. By means of the method, a quantum key distribution technology and a cloud storage technology are combined; because natural advantages that a lot of random keys can be easily generated through distributed characteristics of cloud storage and quantum key distribution and the keys are difficultly eavesdropped are utilized, a malicious attacker cannot obtain the quantum keys, and cannot crack the combined key; and thus, the data security of cloud storage is greatly ensured.
Owner:QUANTUMCTEK
Network security isolation and information exchange method and system based on one-way channel
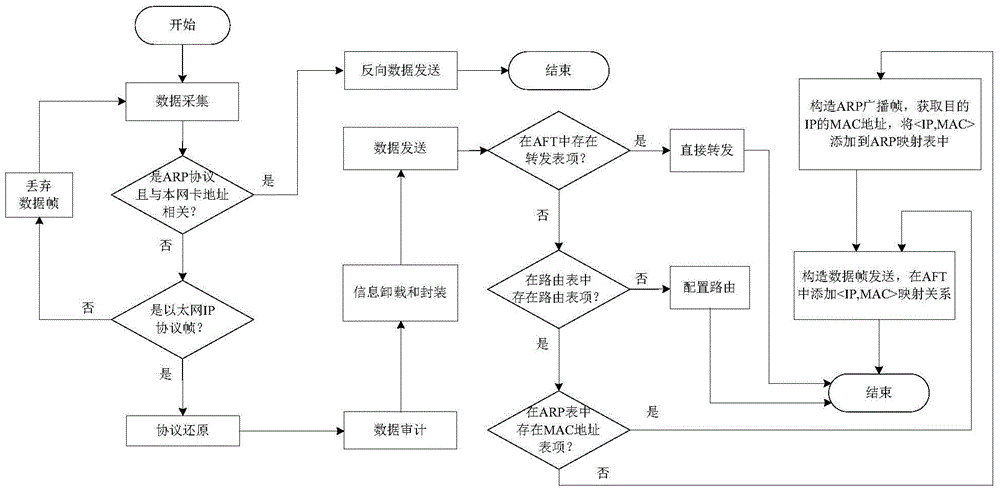
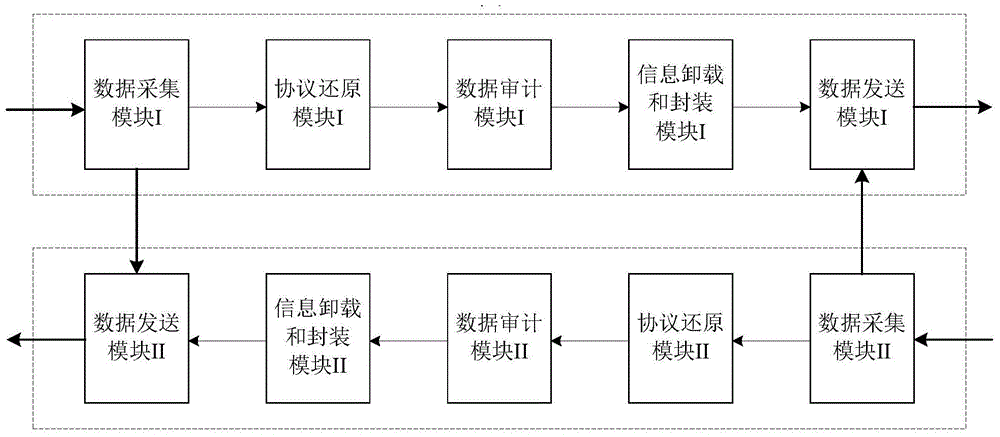
ActiveCN104363231AImprove data throughputGuarantee data securityTransmissionHigh level techniquesData acquisitionNetwork security policy
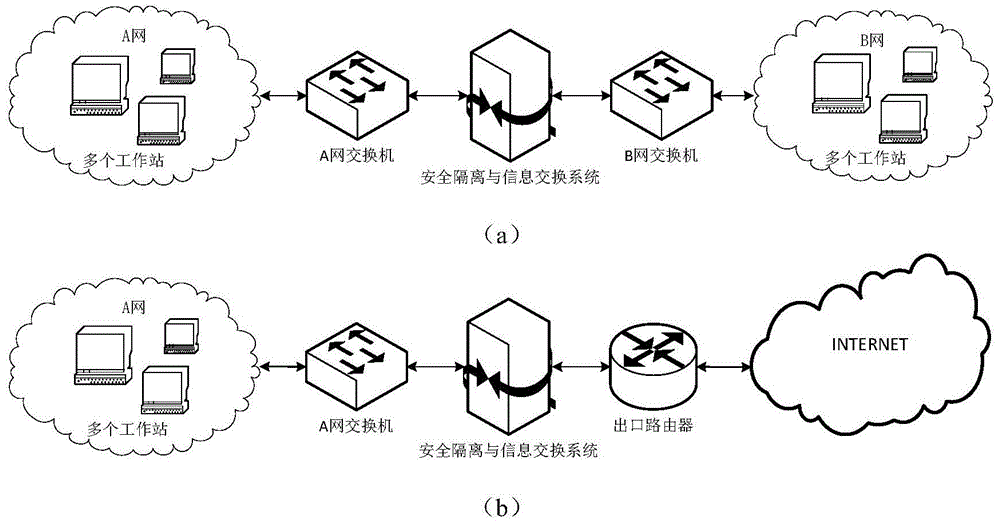
The invention provides a network security isolation and information exchange method and system based on a one-way channel and belongs to the field of computer network security. The network security isolation and information exchange system comprises a data acquisition module, a protocol reassembling module, a data audition module, an information unloading and packaging module and a data transmission module. Each module can be acquired through hardware or / and software. The network security isolation and information exchange method includes the steps of data acquisition, protocol reassembling, data audition, information unloading and packaging, data transmission and the like. The one-way channel is adopted for transmitting data, the transmitted data are audited and unloaded through a special data package processing method, and when a fault occurs, physical isolation is formed. According to the network security isolation and information exchange method and system, the data throughput rate can be remarkably increased, data security between different networks can be effectively protected, illegal user intrusion and control are avoided, and system cost is reduced.
Owner:BEIJING RUICHI XINAN TECH
Method and system for killing mobile terminal viruses
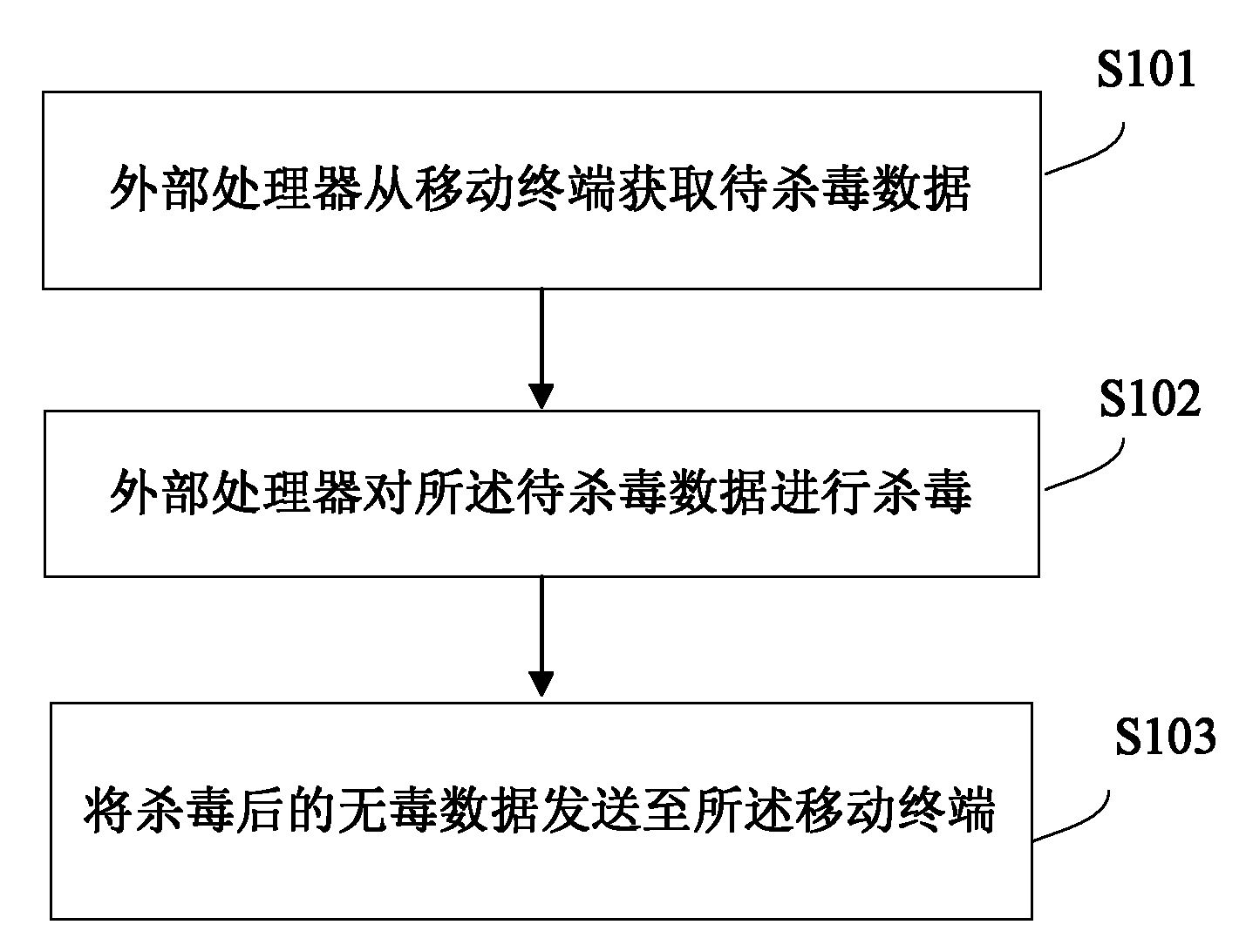
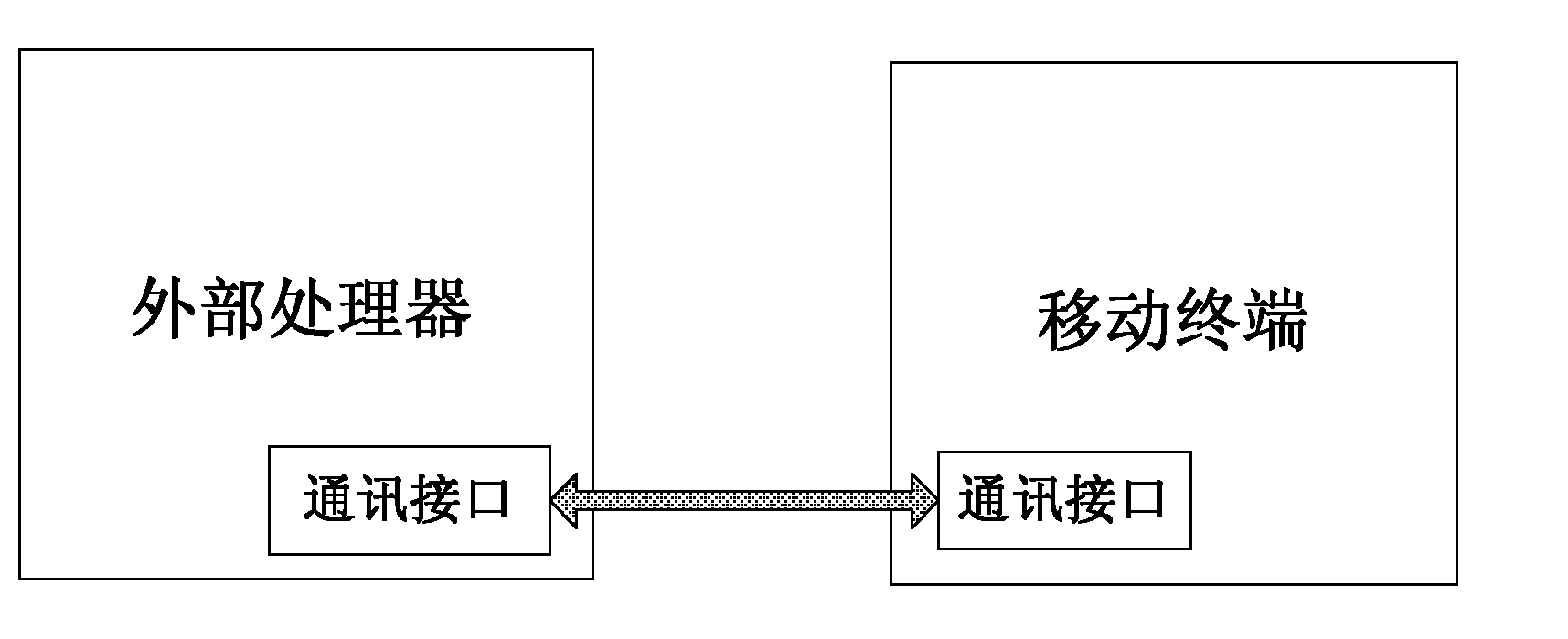
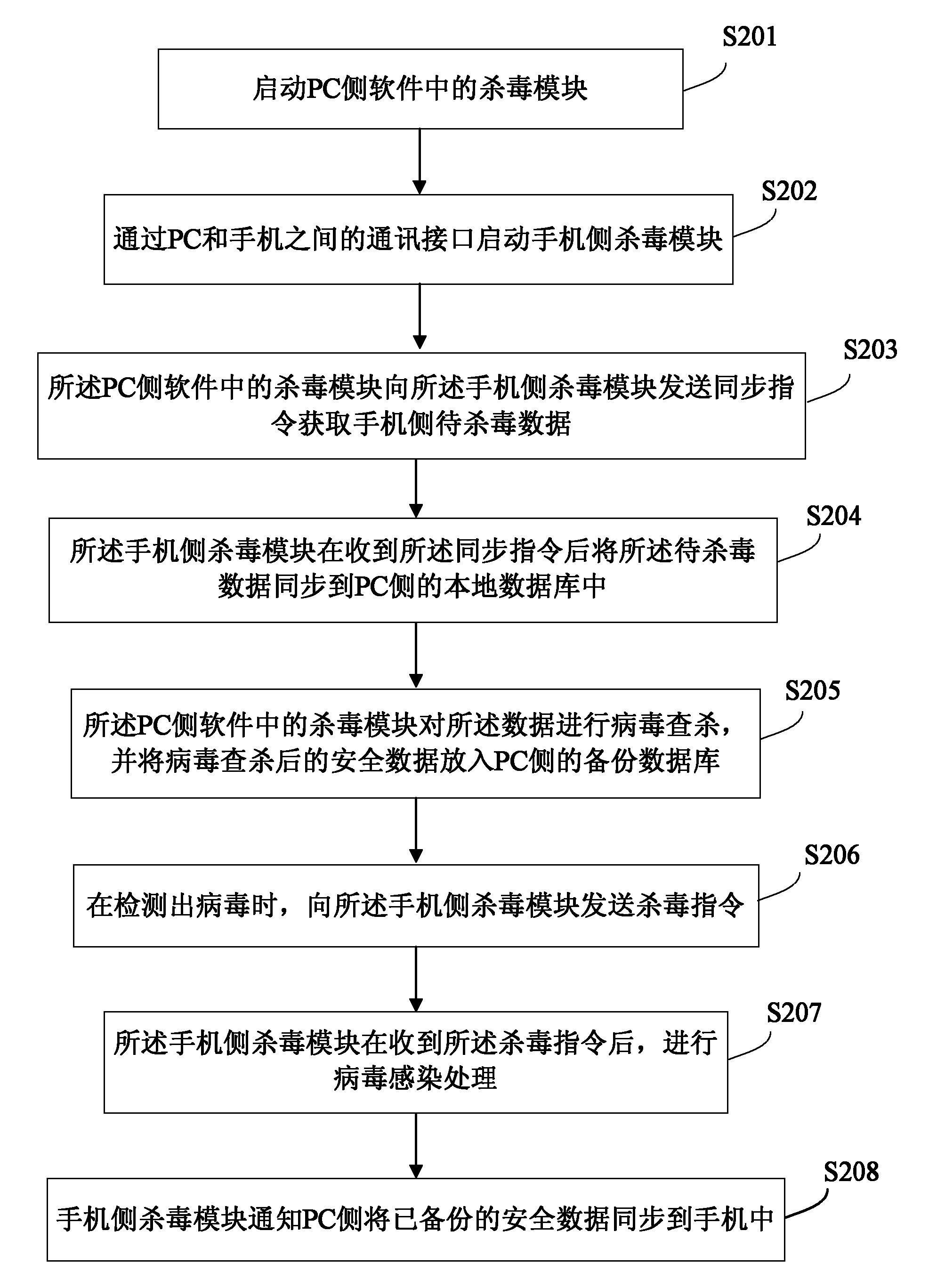
InactiveCN102222184AGuarantee data securityAvoid bad consequencesPlatform integrity maintainanceCommunication interfaceVirus
The invention discloses a method and a system for killing mobile terminal viruses. The system comprises an external processor and a mobile terminal which are connected through communication interfaces. The method comprises the following steps that the external processor acquires data to be subject to virus killing from the mobile terminal; and after the data is subject to the virus killing, non-virus data after the virus killing is transmitted to the mobile terminal. The method and the system can make up the defect that mobile terminal virus-killing software has limit space and processing capability so that the virus check and killing is not complete, can avoid the serious consequences caused by virus check leakage to a user, improves the capability of killing viruses of the mobile terminal, and better protects the data safety of the mobile terminal.
Owner:ZTE CORP
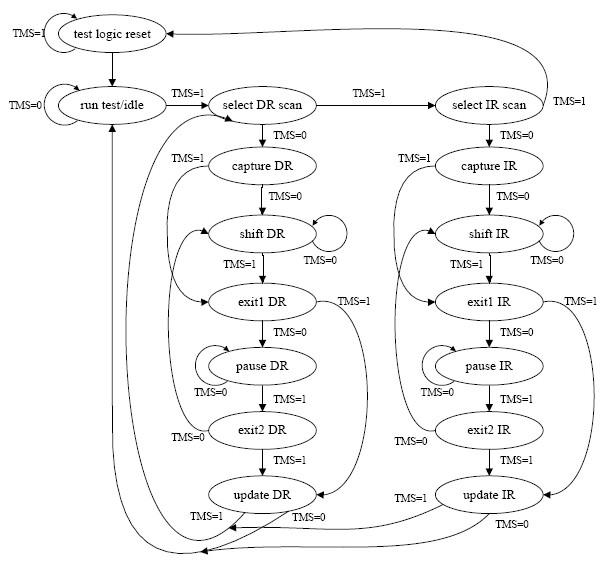
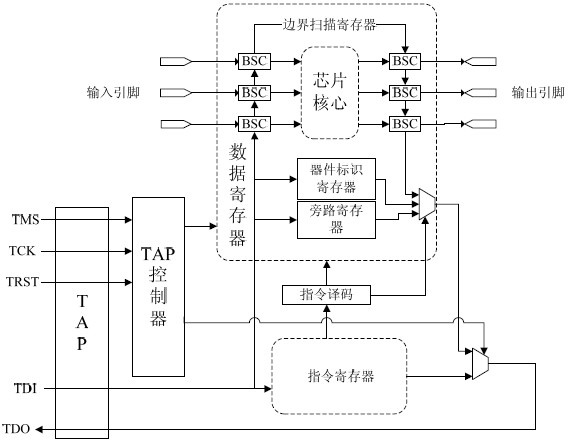
System chip JTAG (Joint Test Action Group) debugging control method based on chip flash memory
ActiveCN102073009AGuarantee data securityEnsure safetyElectrical testingTransport Driver InterfaceProcessor register
The invention discloses a system chip JTAG (Joint Test Action Group) debugging control method based on a chip flash memory. A JTAG realizes control on a boundary scanning chain through a TAP (Test Access Port), a TCK (Test Clock) interface, a TMS (Time Multiplexed Switching) interface and a TDI (Transport Driver Interface) are respectively controlled by an alternative datum, two inputs of a data selector are respectively used as a normal signal and a fixed low level or high level, the data selector is controlled through a register REG 1 with a bit width of a bit in a system chip, when the value of the REG1 is 1, the low level is connected to the TCK interface, the TMS interface and the TDI through signals and used for shielding an JTAG interface; when the value of the REG1 is 0, the normal signal is connected to the TCK interface, the TMS interface and the TDI and enters a normal debugging mode; and the value of the REG1 is determined according to the data of the chip flash memory. The invention ensures the data security and improves the security while the debugging is convenient.
Owner:C SKY MICROSYST CO LTD
Equipment charging method and system, and charger
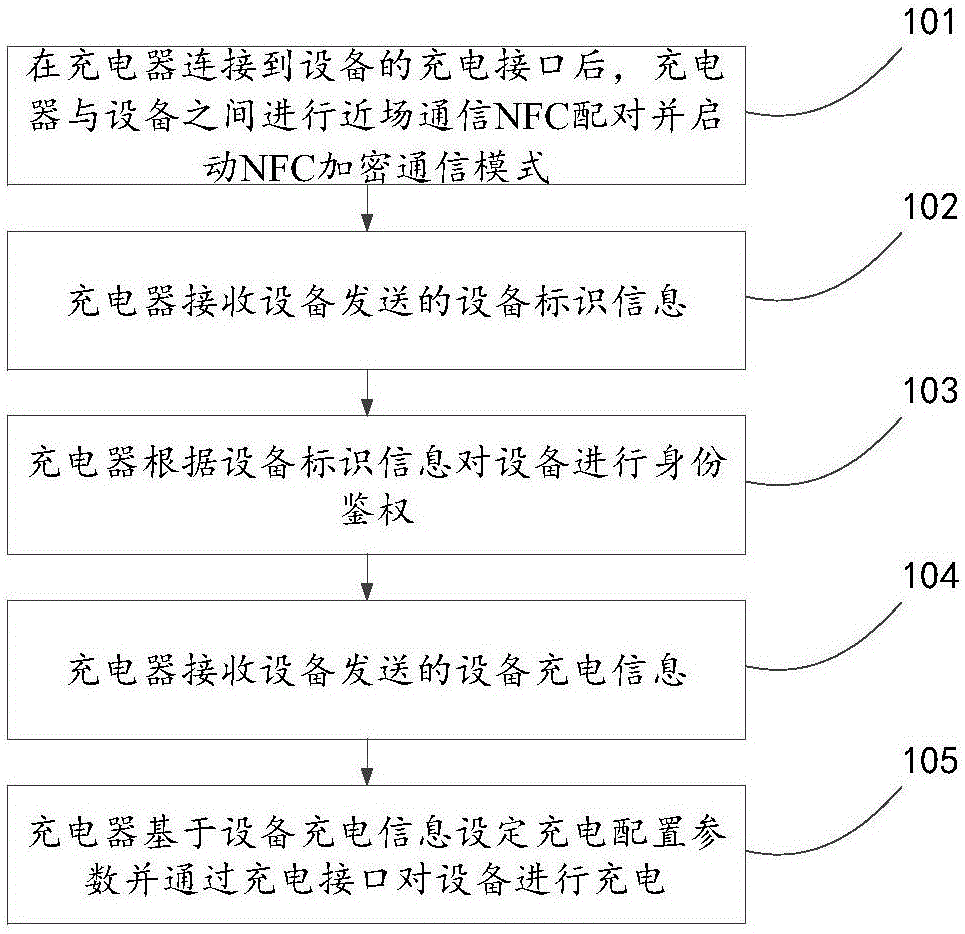
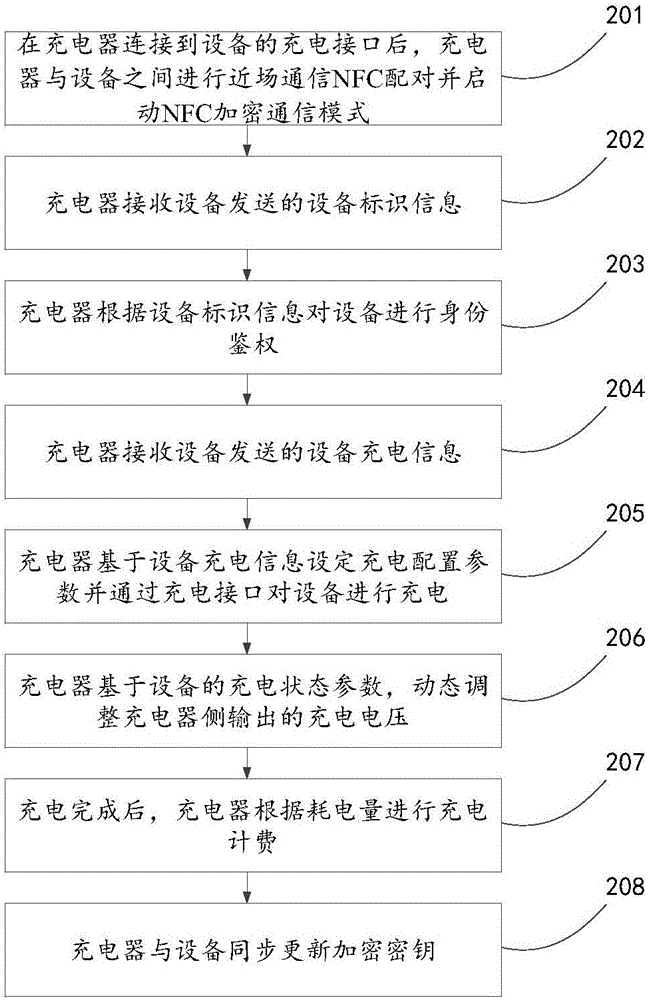
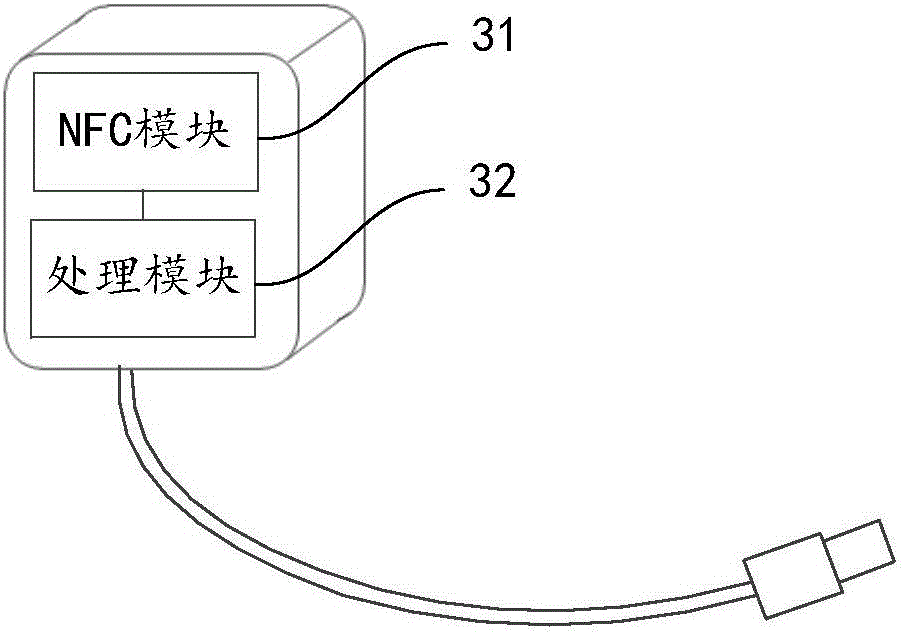
InactiveCN106487072AGuarantee data securityProtection of legitimate rights and interestsCircuit authenticationElectric powerData informationIntelligent equipment
The invention discloses an equipment charging method, an equipment charging system and a charger, which relate to the field of intelligent equipment, and are invented to solve the problem that the existing charging method is prone to cause charging configuration parameter disclosure. The equipment charging method comprises the steps that: near field communication NFC pairing is carried out between the charger and equipment and an NFC encrypted communication mode is initiated after the charger is connected to a charging interface of the equipment; the charger receives equipment identification information sent by the equipment; the equipment is subjected to identity authentication according to the equipment identification information; equipment charging information sent by the equipment is received; and charging configuration parameters are set based on the equipment charging information, and the equipment is charged by means of the charging interface. The equipment charging method, the equipment charging system and the charger can protect the security of data interaction between the equipment and the charger, and prevent data information from being detected and cracked.
Owner:NEUSOFT CORP
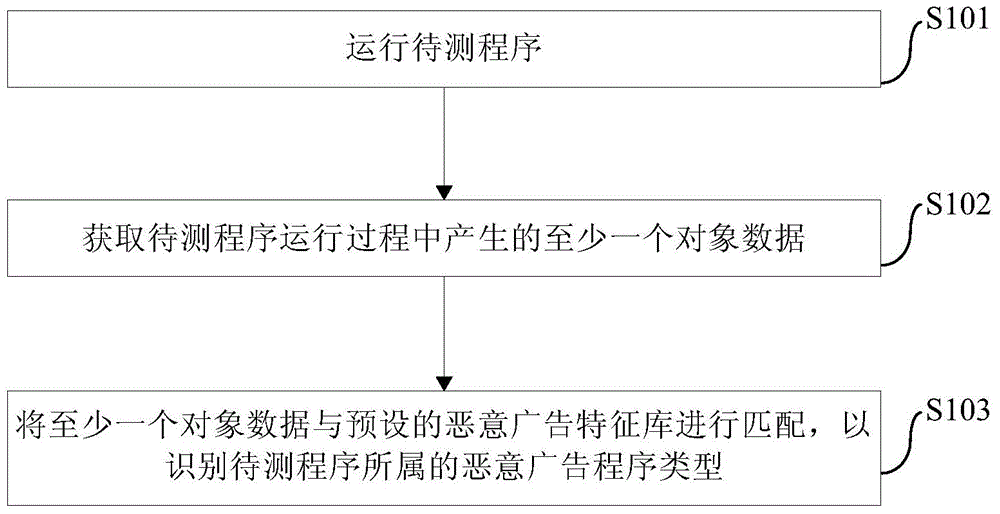
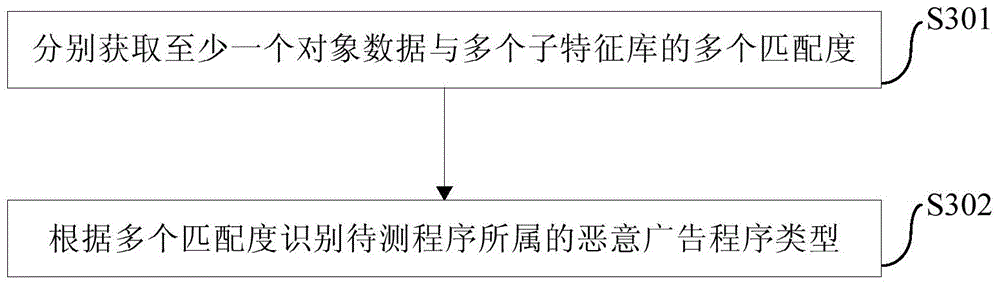
Identification method and device of malicious advertisement program and client side
ActiveCN104598815AType accurate judgmentEffective interceptionPlatform integrity maintainanceObfuscationSoftware engineering
The invention provides an identification method and device of a malicious advertisement program and a client side. The method comprises the following steps: operating a program to be tested; obtaining at least one piece of object data generated in an operation process of the program to be tested; and matching at least one piece of object data with a preset malicious advertisement feature library to identify a malicious advertisement program type to which the program to be tested belongs. According to the method of the embodiment of the invention, program variants can be subjected to continuous tracking and classification and are free from the restriction of code obfuscation rival and program encryption, the type of the program to be tested is accurately judged so as to effectively intercept a malicious program to guarantee the data safety of a user.
Owner:BEIJING CHEETAH MOBILE TECH CO LTD +1
Format-preserving data desensitization method
InactiveCN105426445AAvoid loading errorsEnsure safetySpecial data processing applicationsProcess mechanismChinese characters
The invention discloses a format-preserving data desensitization method, which relates to a data desensitization method, in particular to a format-preserving data processing method. The method aims to solve the problems that data accuracy is seriously affected since data missing happens when a traditional protection method of client sensitive data carries out a data association operation, an algorithm is easy in cracking since the adopted algorithm is too simple and no effective historical data processing mechanism is provided after a key is exposed. A GB2312 Chinese character set is divided into 72 isometric unit intervals on the basis of the coding structure of the GB2312 Chinese character set within a range of B0A0, and the code distribution of each unit interval is the same. The method comprises the coding structure of the GB2312 Chinese character set, a GBK (Guo-Biao Kuozhan) isometric encryption algorithm, a GBK isometric decryption algorithm, a number scrambling algorithm and a number descrambling algorithm. The method belongs to the field of computer software.
Owner:TIANJIN JIANING KUNXIANG TECH CO LTD
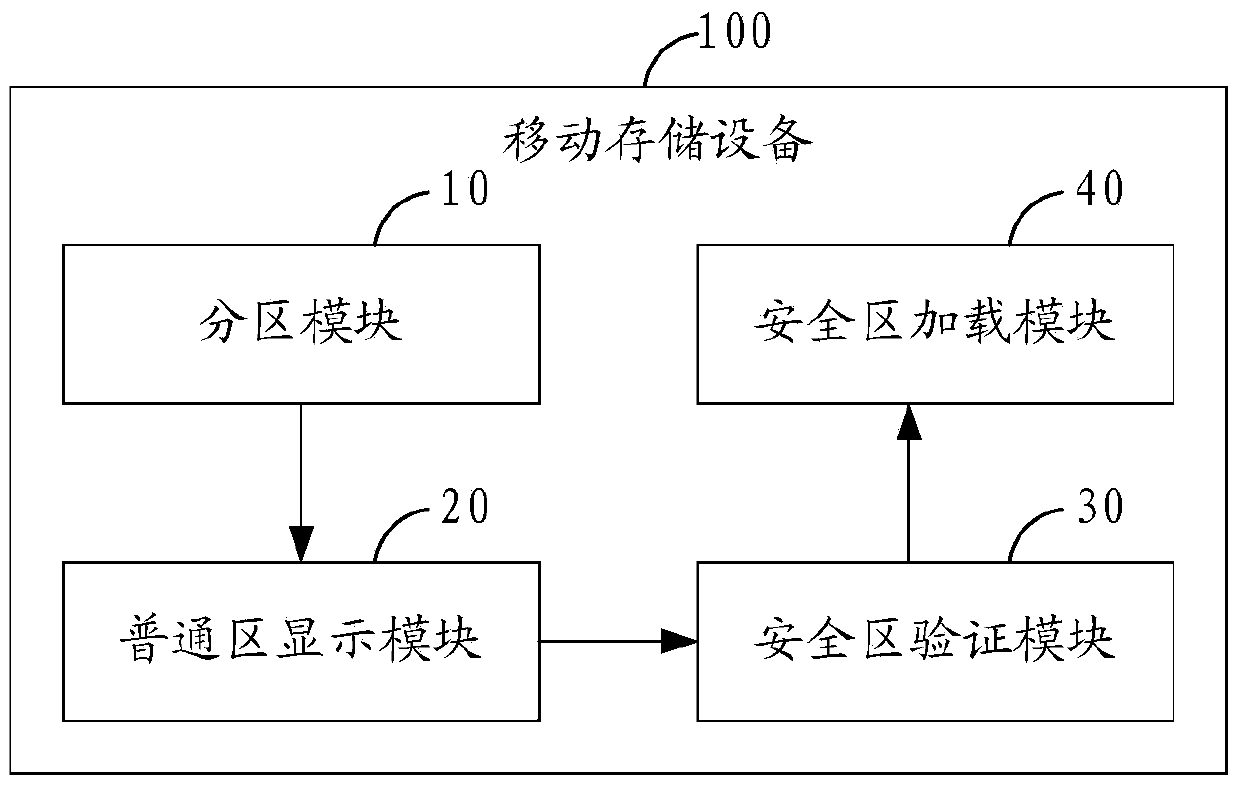
Mobile storage device based data protecting method and mobile storage device
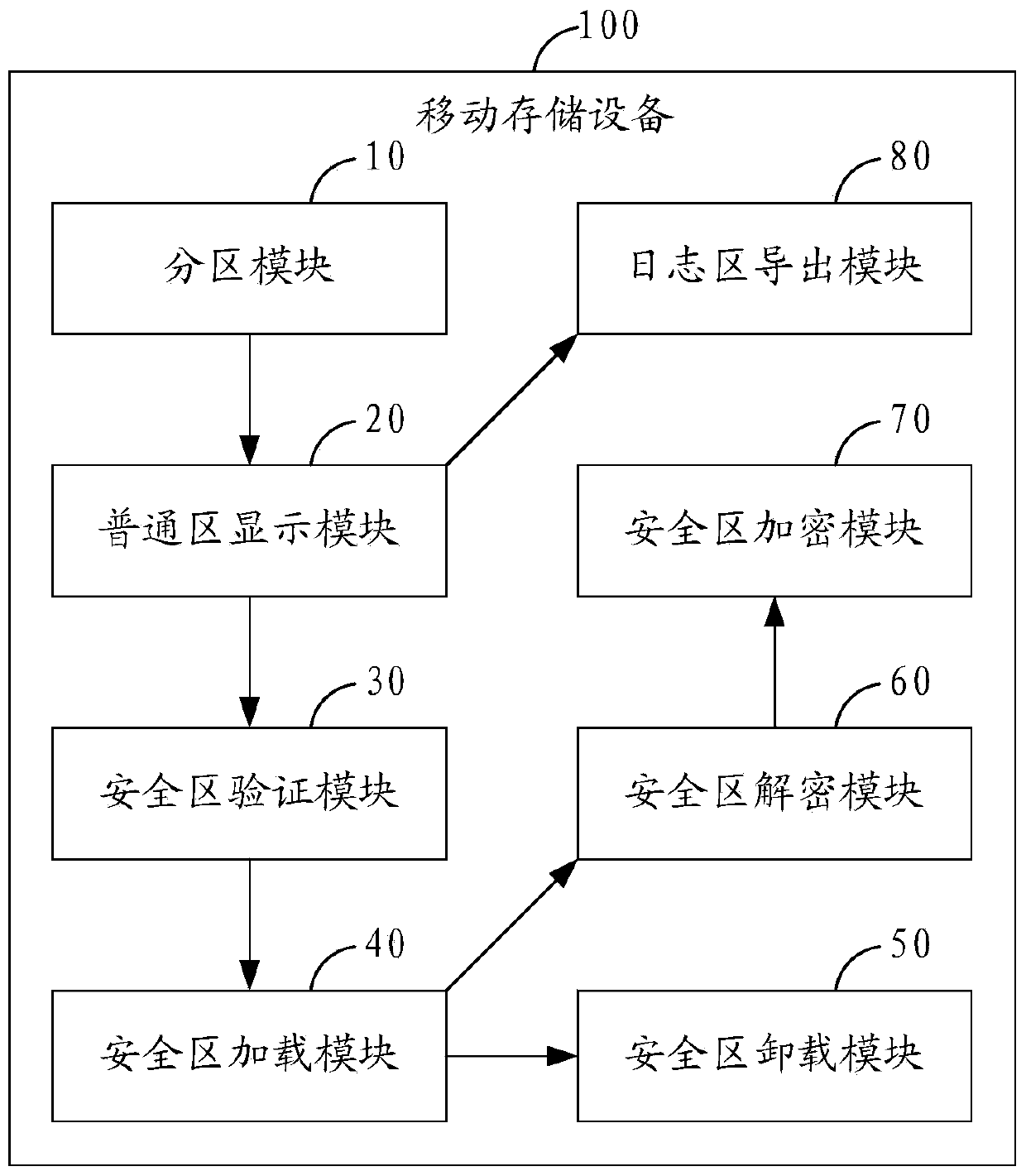
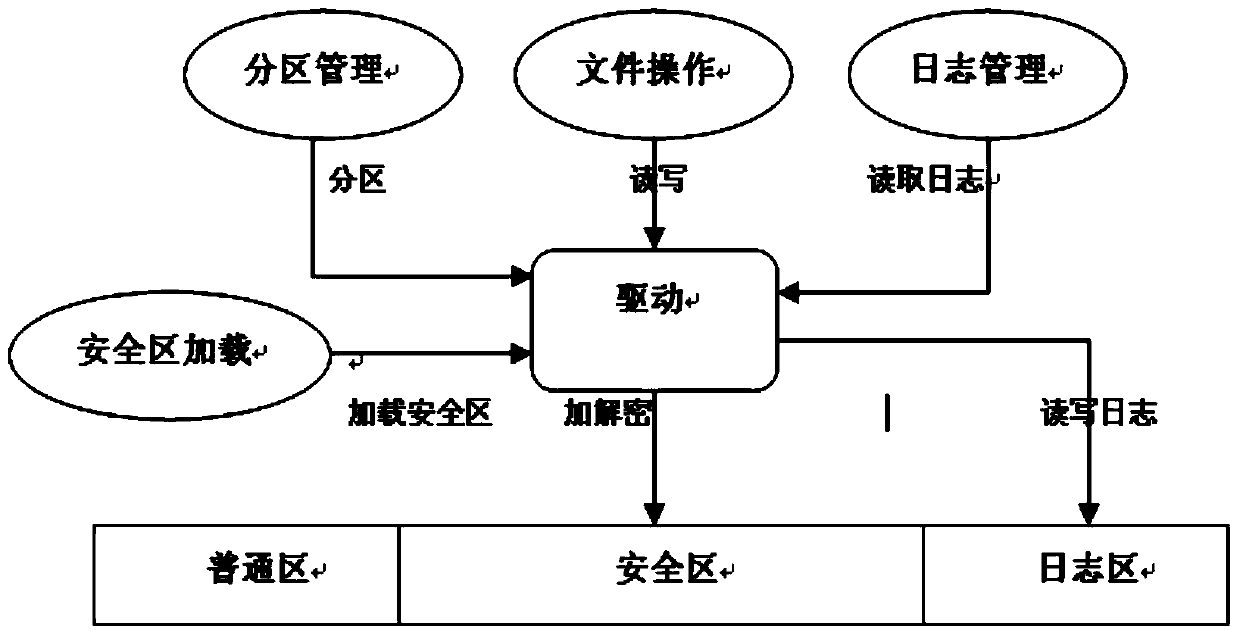
InactiveCN103793334AGuarantee data securityPrevent leakageUnauthorized memory use protectionRemovable media
The invention is applicable to the technical field of mobile storage and provides a mobile storage device based data protecting method. The mobile storage and provides a mobile storage device based data protecting method includes: dividing a storage region of mobile storage device into a normal region and a safe region; displaying the normal region when a first access request of the mobile storage device is received; verifying a second access request when the second access request of the safe region is received; and if the second access request passes the verification, loading and displaying the safe region. The invention further provides the mobile storage device correspondingly. Data in a whole mobile memorizing process is guaranteed to be quite safe, and the problem of data leakage caused by device loss, cross use, vicious stealing and the like can be prevented effectively.
Owner:SUNINFO INFORMATION TECH
Cross-equipment input method, processing device, input equipment and intelligent display equipment
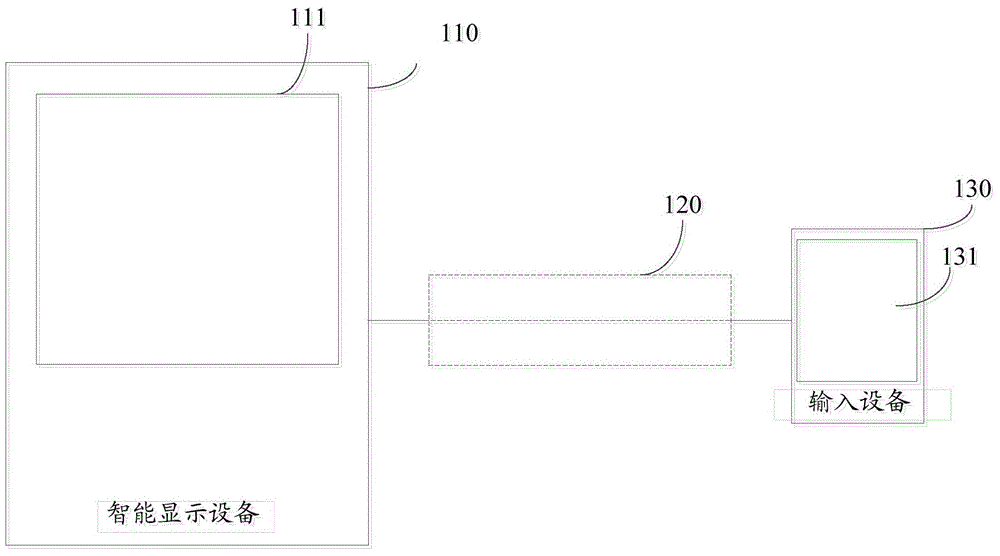
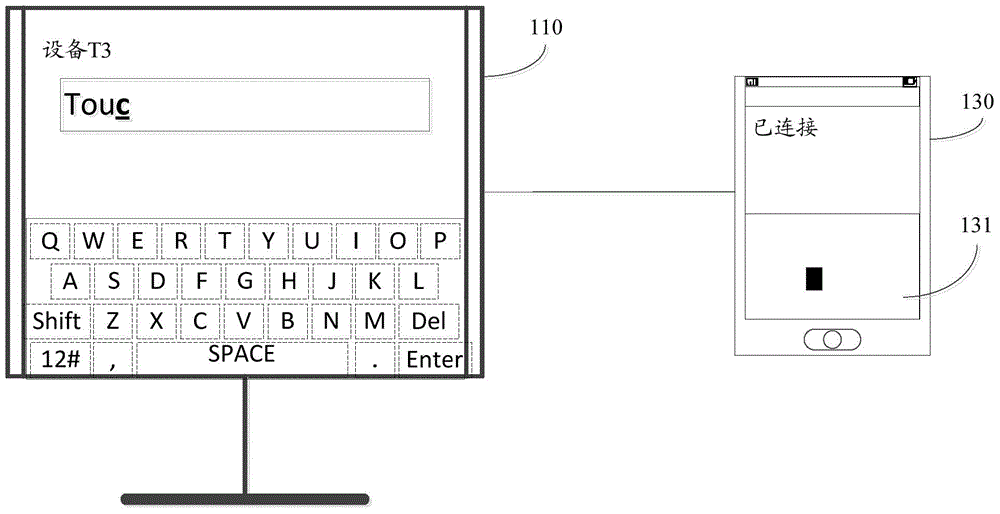
ActiveCN104375666AIncrease typing speedAvoid eye movementInput/output processes for data processingInput deviceInput method
Disclosed are a cross-equipment input method, a processing device, input equipment and intelligent display equipment. The cross-equipment input method includes acquiring input interface information from the intelligent display equipment; adjusting keyboard layout according to the input interface information; detecting an input signal corresponding to input operation of a user, and transmitting information of the keyboard layout after being adjusted, input setting information and the input signal to the intelligent display equipment to enable the same to perform operation processing and display. By the above technical scheme, cross-equipment input speed can be increased, and user experience can be improved.
Owner:SHANGHAI CHULE (COOTEK) INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com