Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
52results about How to "No need to consume resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
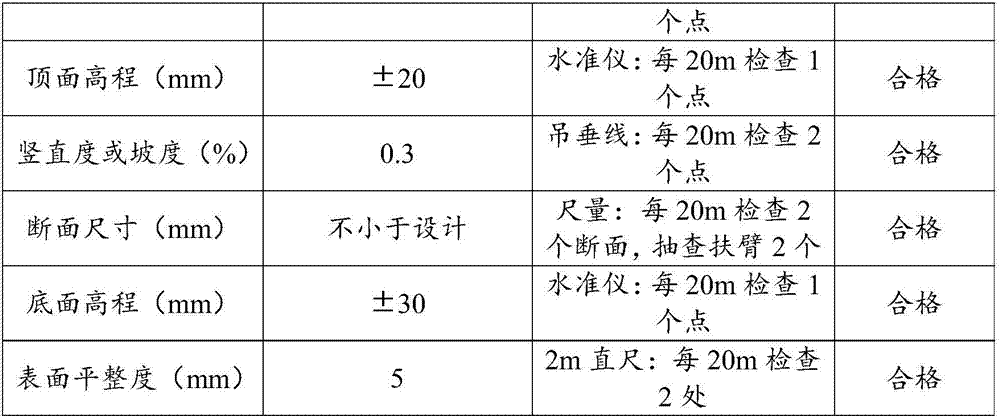
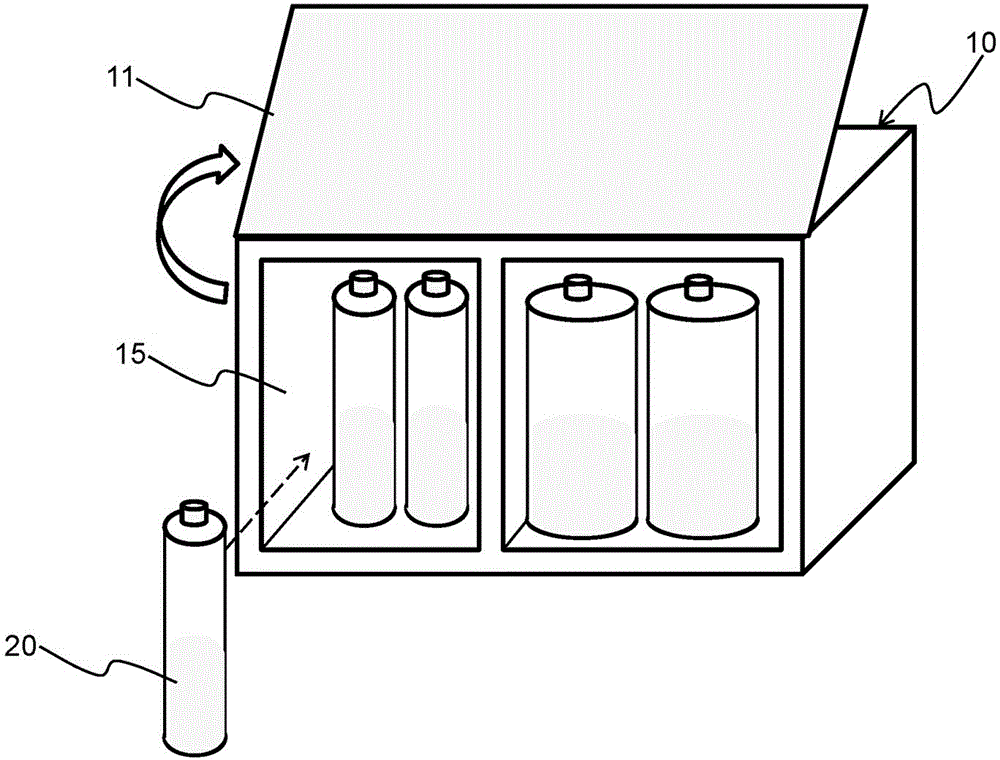
Key point positioning method and terminal
ActiveCN105512627AHigh precisionReduce processing difficultyCharacter and pattern recognitionComputer terminalFace perception
The embodiment of the invention discloses a key point positioning method and a terminal. The method comprises the steps of detecting a target object as a face image during the collecting process of the target object; generating a target detecting region on the face image of the i frame for human face recognition and location according to a preset configuration and annotating the target detecting region, wherein i is larger than or equal to 1; when i is larger than 1, estimating the key point information of a human face based on the face image of the i frame according to the similarity matching strategy between a previous frame and the current frame so as to obtain the category of the human face for the face image of the i frame; according to the category of the human face for the face image of the i frame, determining a first initial shape out of a plurality of preset candidate initial shapes; and calculating the position of an initial face key point in the face image of the i frame according to the target detecting region and the first initial shape.
Owner:TENCENT TECH (SHENZHEN) CO LTD
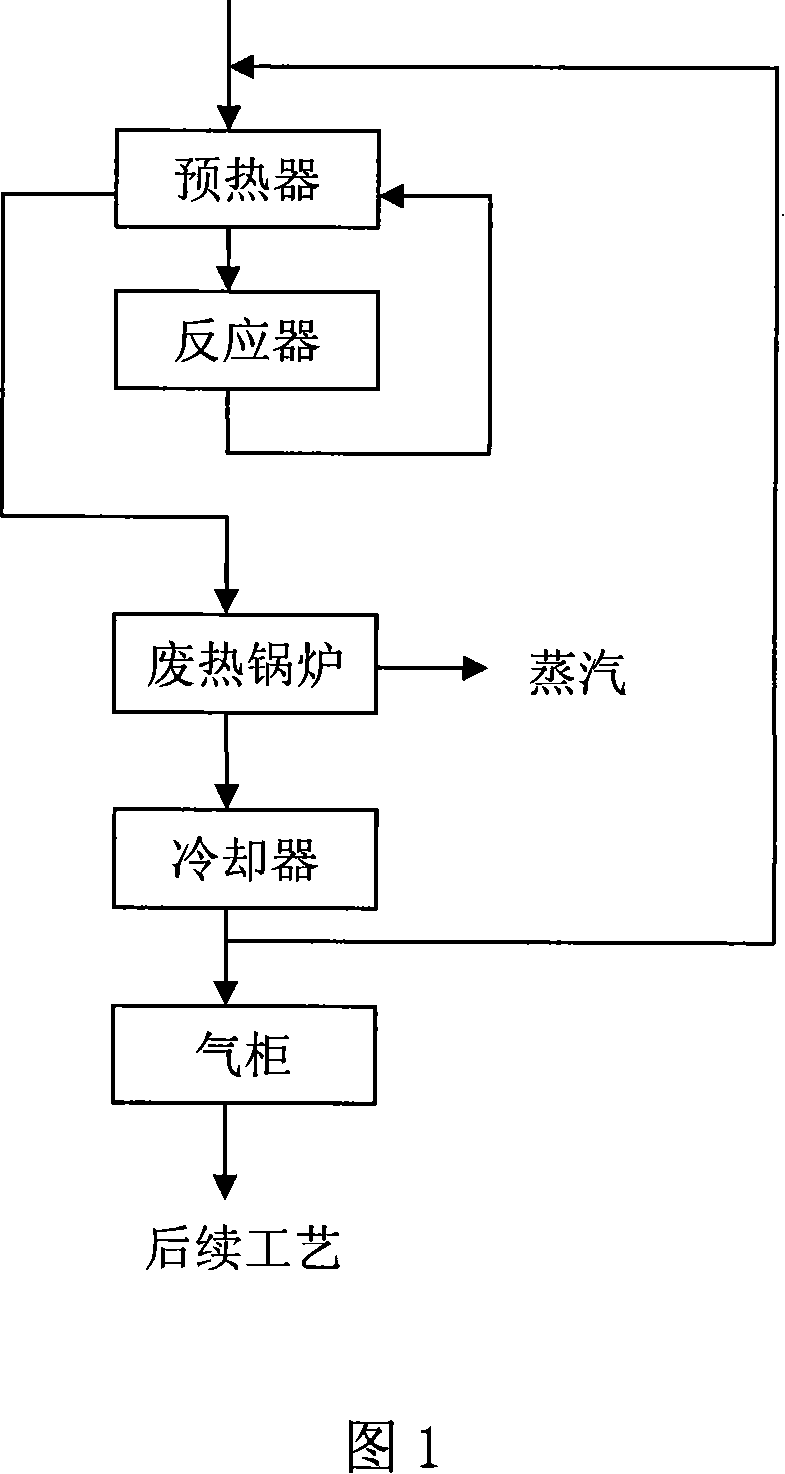
Sulfur-resistant catalytic deoxidization process for methane-rich gas
InactiveCN101139239ALow priceSulfur resistanceMetal/metal-oxides/metal-hydroxide catalystsChemical modification purification/separationReaction temperatureManganese
The present invention discloses a sulfur wearable and catalyzing and oxidizing method for gas abundant of firedamp; the raw material gas abundant of firedamp such as coal bed gas firstly passes through a preheater for preheating, and then enters a oxidizing reaction device; under the condition of 0-0.5MPa of pressure, 500-750 DEG C of reaction temperature, 1000-3000h-1of reaction air speed, the firedamp in the air is reacted with oxygen to produce carbon dioxide and water in manganese base sulfur wearable and catalyzing and oxidizing bed; at the same time, a small quantity of firedamp is decomposed to produce carbon and hydrogen gas; the carbon and the hydrogen after being decomposed are also reacted with oxygen so as to reach the purpose of getting rid of oxygen in the airs abundant of firedamp effectively. The present invention adopts much newer and more economical new catalyzer, which does not need to desulfurize firstly for the air; the air can directly enter the oxidization reaction device for oxidization. So the present invention can decrease the cost and simplify the technics process.
Owner:HAO HUA CHENGDU TECH
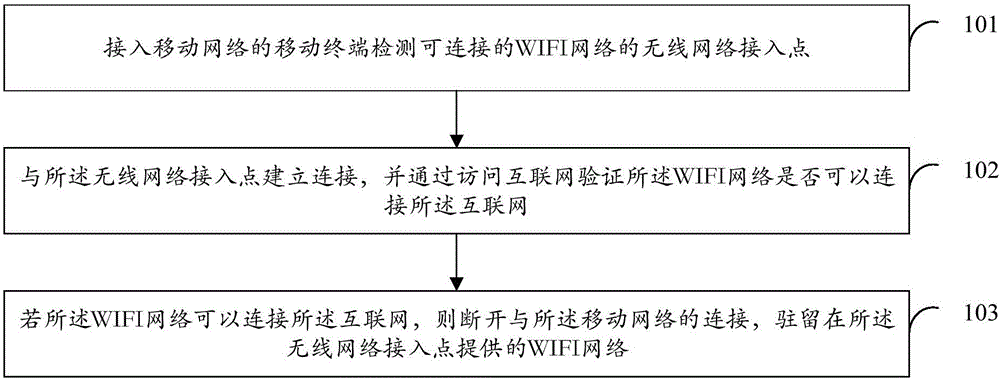
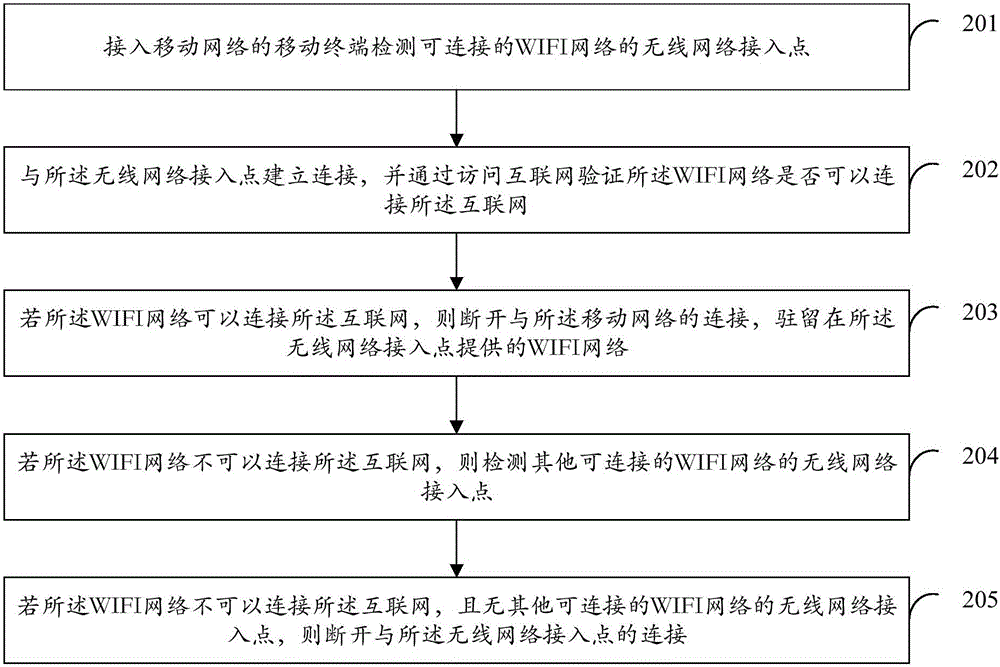
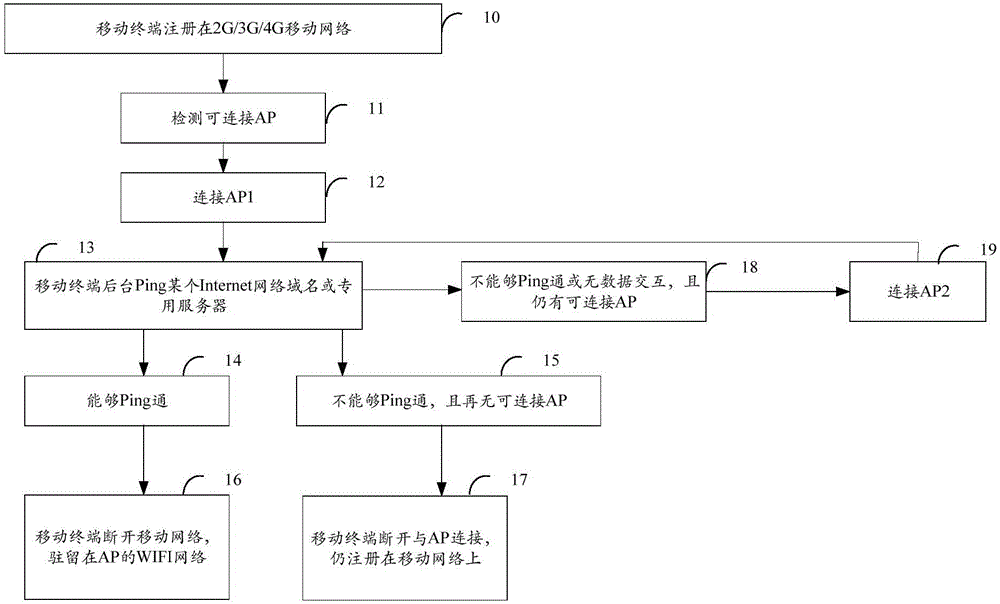
Method and device of WiFi adaptive selection and connection
InactiveCN105828395AOvercoming problems with real-time interactive dataAvoid the operation of manually switching networksAssess restrictionReal-time dataTTEthernet
The present invention discloses a method and device of WiFi adaptive selection and connection. The method comprises the steps that: an access mobile which connects a mobile network detects a wireless network access point which can be connected to a WiFi network; the connection with the wireless network access point is established, and whether the WiFi network can be connected to the Internet is verified through visiting the Internet; if the WiFi network can be connected to the Internet, the connection with the mobile network is disconnected, and the mobile terminal stays at the WiFi network provided by the wireless network access point. According to the invention, the condition of network disconnection after the connection of the WiFi network from a mobile network when the WiFi network of the Internet can not be connected can be avoided, the problem of affecting network real-time data exchange by the network disconnection is overcome, and the operation of manually switching a network by a user after the WiFi can not be connected to the Internet is avoided at the same time.
Owner:VIVO MOBILE COMM CO LTD
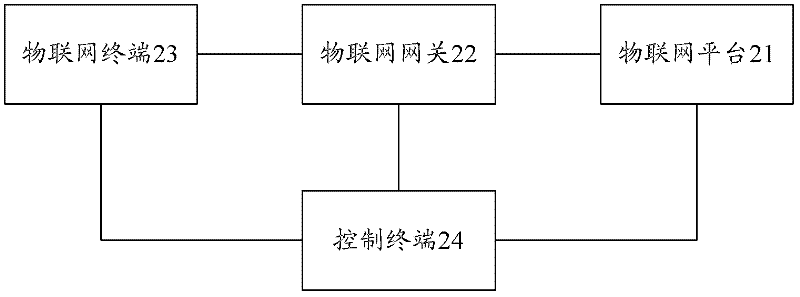
Method and system for combining Internet of things capability with terminal
ActiveCN102378177AExpand the scope of servicesAdequate serviceNetwork topologiesSecurity arrangementIot gatewayThe Internet
The invention claims a method for combining Internet of things capability with a terminal. The method comprises the steps: an Internet of things platform opens terminal capability of the Internet of things published by an Internet of things gateway; a control terminal sends a request for obtaining capability information to the Internet of things gateway; and the control terminal uses capability corresponding to the Internet of things terminal according to the Internet of things terminal capability information returned by the Internet of things gateway after a notification of successful authorization or authentication is received. Meanwhile, the invention also claims a system for combining the Internet of things capability with the terminal. Through the proposal of the invention, the capability of the Internet of things terminal can be shared, combined services are provided, service range is expanded, more sufficient service is provided for users without consuming too many resources of operators, and service cost is reduced.
Owner:ZTE CORP
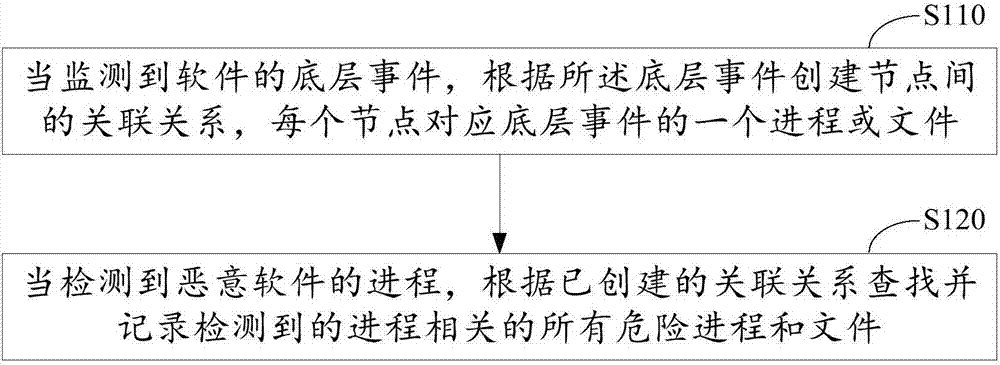
Threat tracing method and device of malware
ActiveCN107292169AAvoid secondary attacksQuick Threat TracingPlatform integrity maintainanceMalwareComputer science
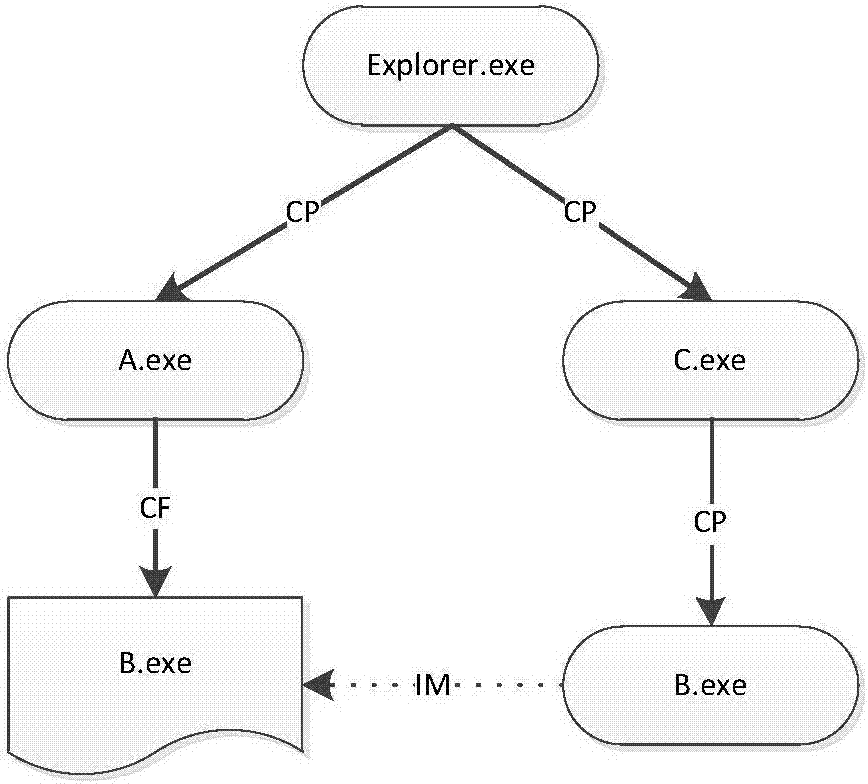
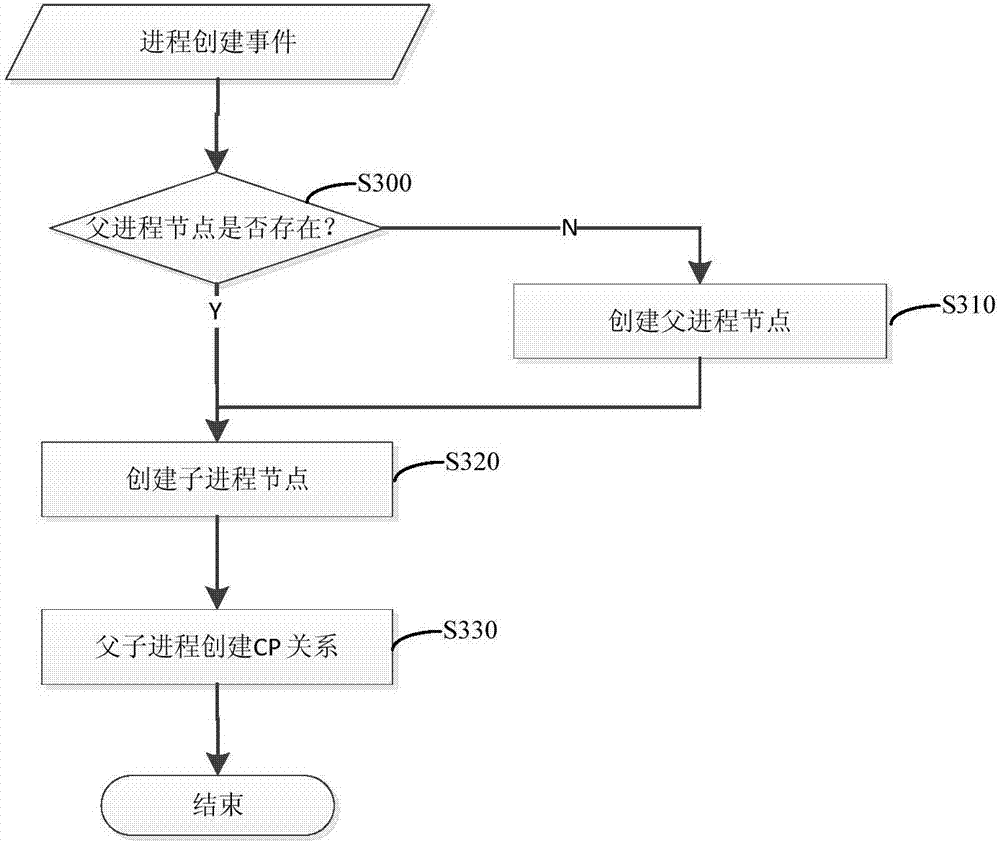
The invention provides a threat tracing method and a threat tracing device for malware. The method comprises the following steps of building an association relation between nodes according to a bottom-layer event when the bottom-layer event of software is monitored, wherein each node is corresponding to a progress or a file of the bottom layer event; and when the progress of the malware is detected, searching and recording all dangerous progress and files related to the detected progress according o the built association relation. An association relation network between the nodes is built and updated in real time, so that a threat can be quickly traced based on the association relation network; compared with a big data analysis network tracing mode, the threat tracing method is reduced in consumption of network resources and even does not consume the network resources, and processing efficiency is high.
Owner:ALIBABA GRP HLDG LTD
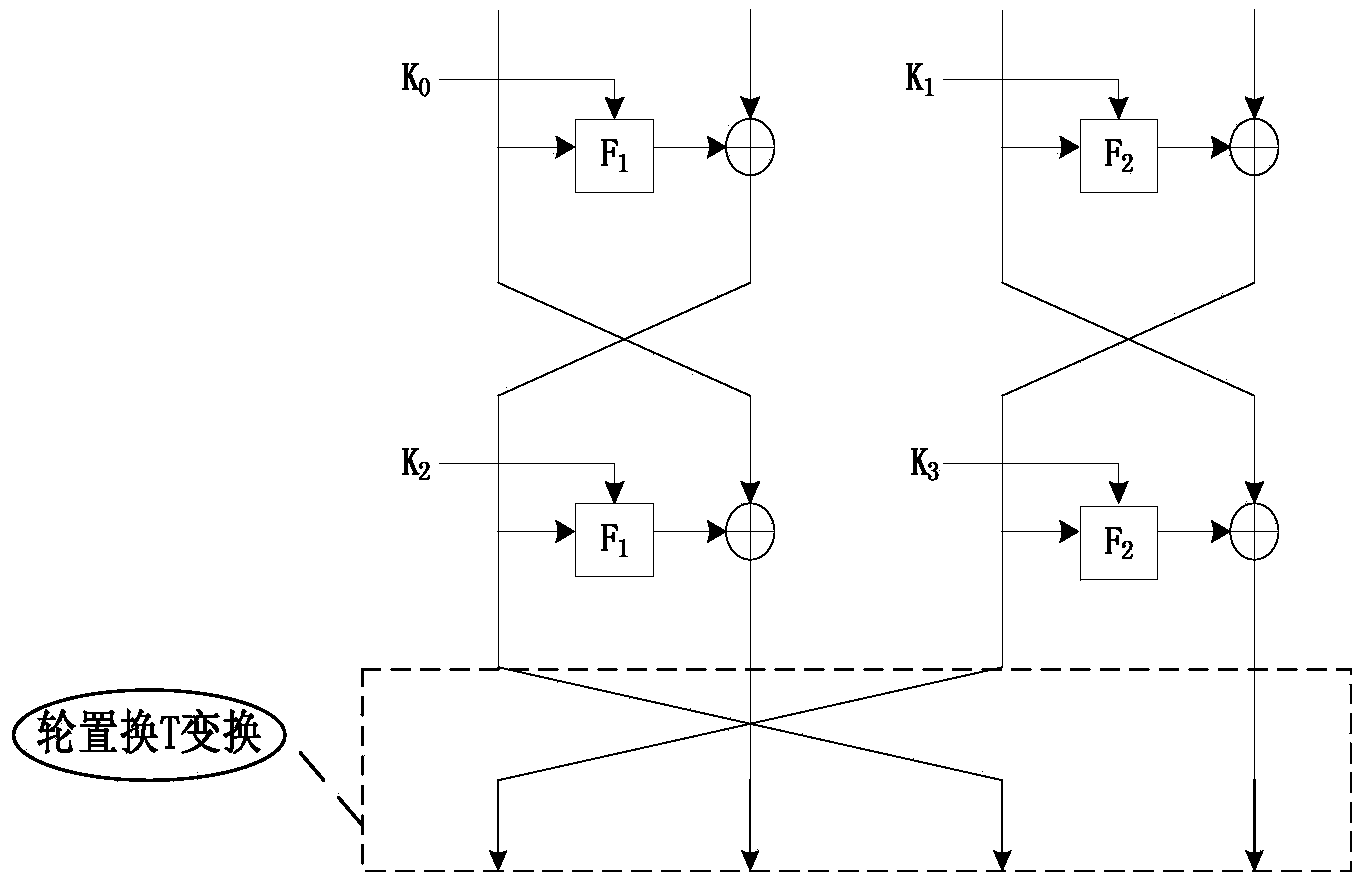
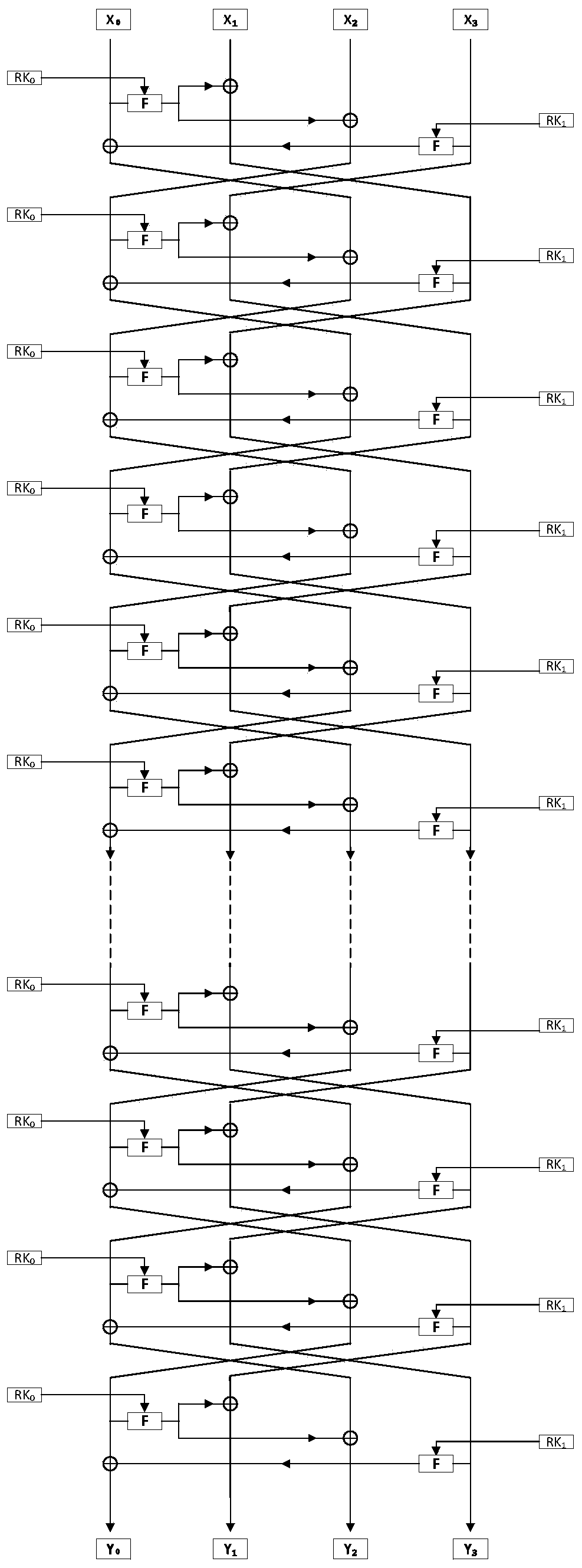
Novel ultra-lightweight QTL (Quasi-Transmission Line) block cipher implementation method
ActiveCN104333446AImprove diffusivitySimple and fast operationEncryption apparatus with shift registers/memoriesComputer hardwareS-box
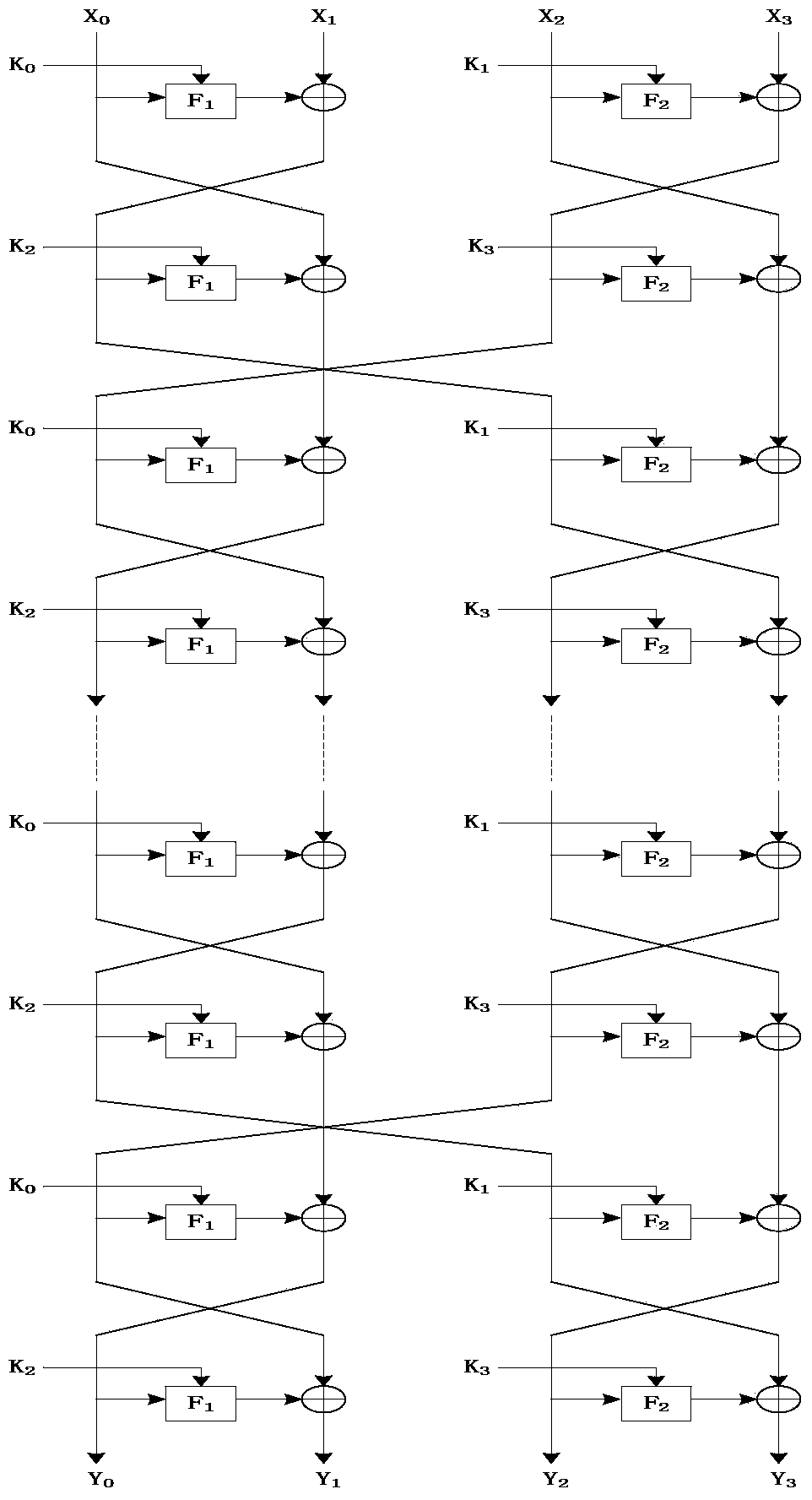
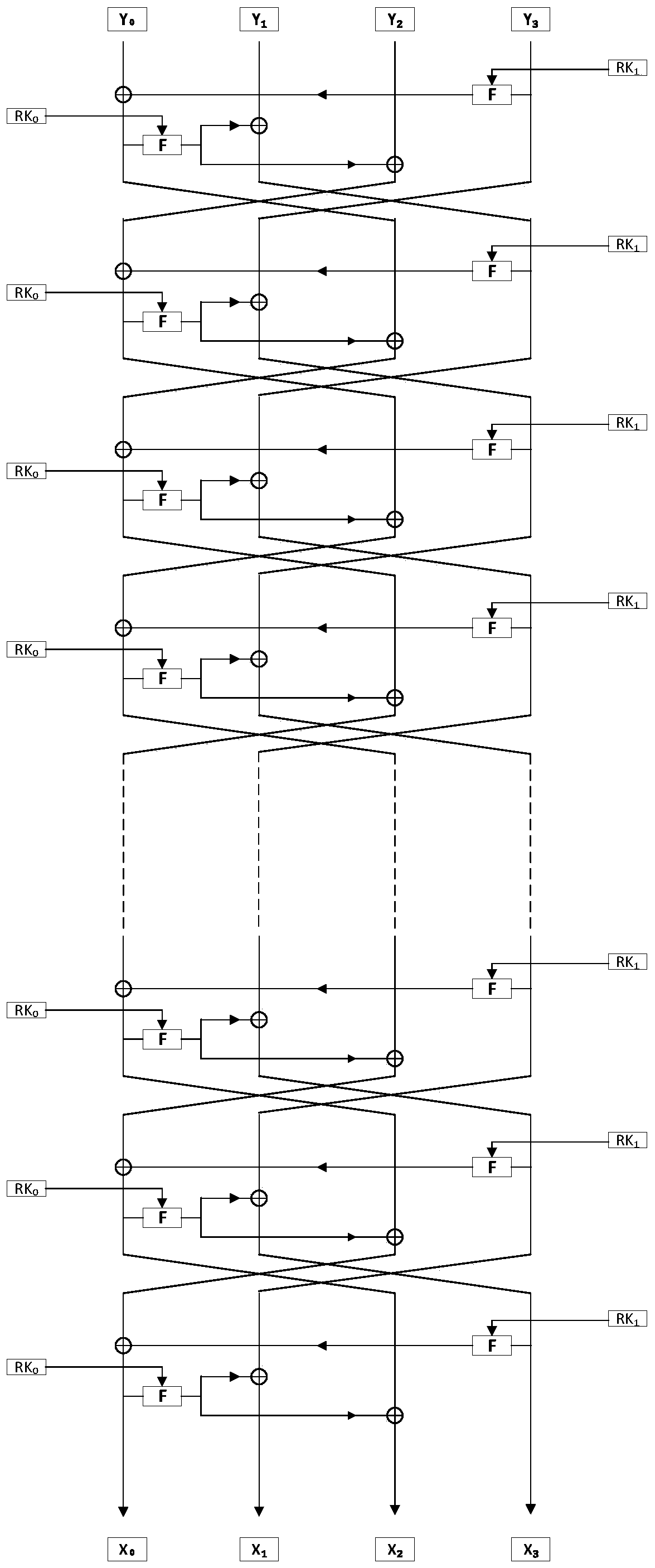
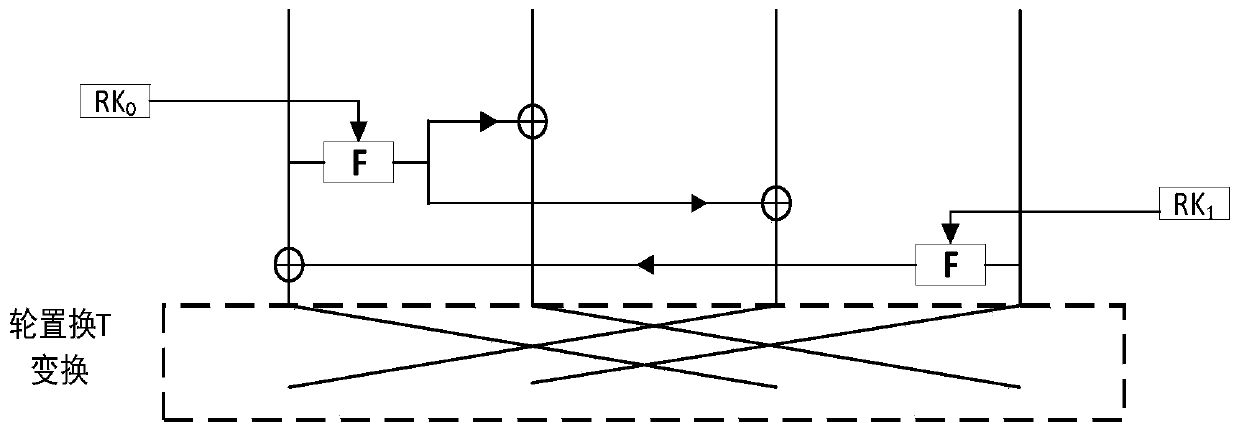
The invention discloses a novel ultra-lightweight QTL (Quasi-Transmission Line) block cipher implementation method. According to the method, a novel generalized Feistel network structure is designed; the structural algorithm overcomes the defect that only a half of grouped data is changed during one-round iterative operation of the conventional Feistel network structure, and realizes that all grouped data is changed by the one-round iterative operation. F functions in the round operation of the algorithm comprise an F1 function and an F2 function; S1 and S2 boxes are adopted respectively; the conversion process of the F functions comprises round key add, S box substitution, P replacement and S box substitution; different S box and P replacement only requires hardware connection; the F function of the light super S box is constructed. The algorithm structure is highly symmetric, an encryption module is decrypted and multiplexed by the algorithm, decryption can be performed by exchanging an encryption round key use sequence, the operation is easy and convenient, and extra resource is not required to be consumed by the decryption. Compared with the current lightweight password, the occupied resource is smaller, the encryption performance is high, and known attack can be resisted.
Owner:HENGYANG NORMAL UNIV
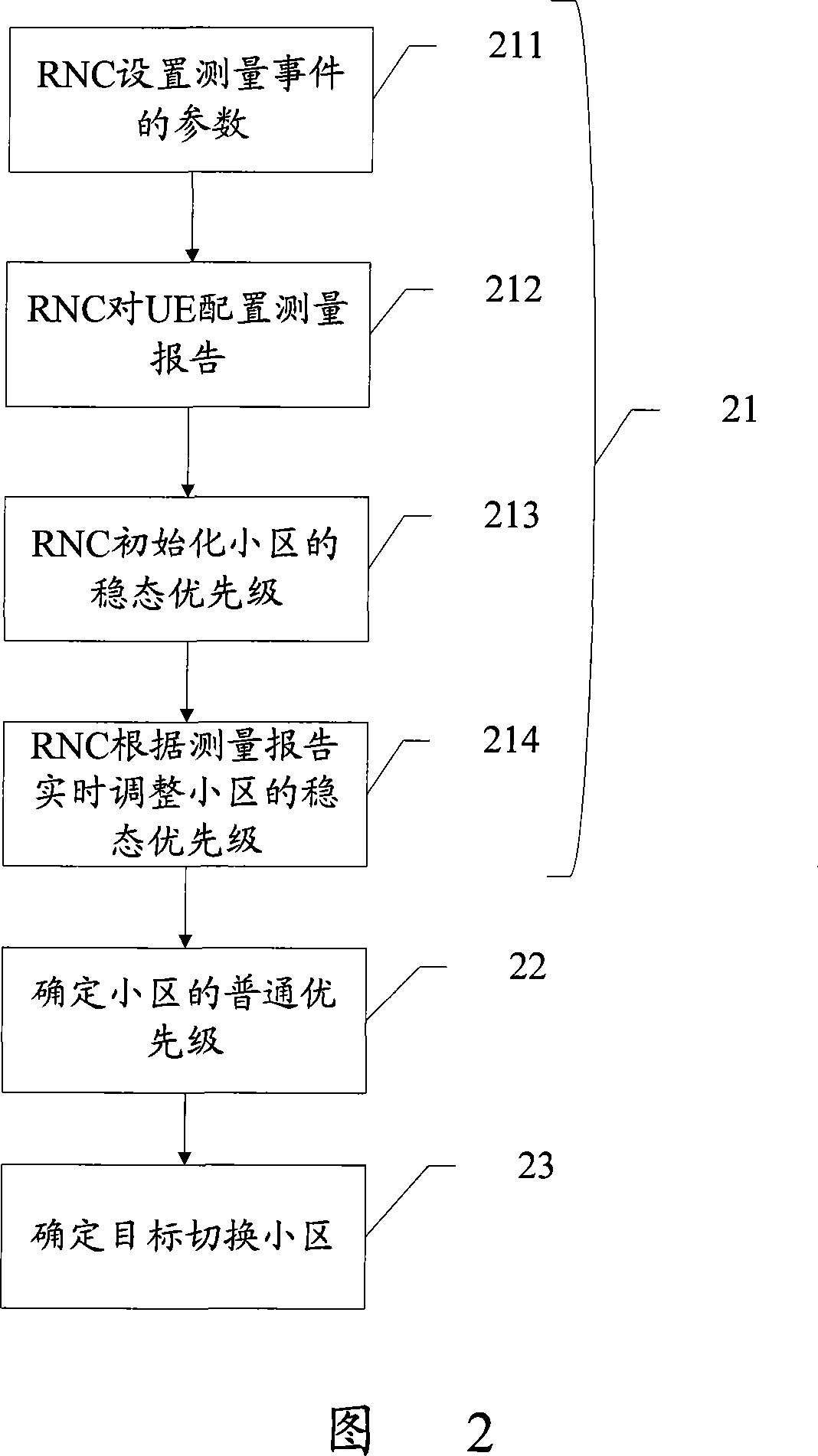
An identification method for destination switching cell
InactiveCN101128059APriority adjustments in real timeImprove switching too frequentlyRadio/inductive link selection arrangementsWireless communicationSurvey resultRadio Network Controller
The utility model discloses a determination method of target switching districts, comprising a radio network controller (RNC), which is characterized in that the RNC utilizes the survey report events in the wideband code division multiple assess (WCDMA) system to determine the steady-state priority of the districts, the common priority of the districts is determined; at least two districts with higher common priority are selected, and the district with the highest steady-state priority is selected from the districts as the target switching district. The determination method of target switching districts of the utility model combines the steady-state priority of the districts to determine the target switching districts based on determining common priority, improves the problems of excessively frequent district switching and unstable district switching, real-time adjusts the priority of the districts according to survey reports, stores the historical survey results without using a great deal of resources, and is convenient in calculation.
Owner:ZTE CORP
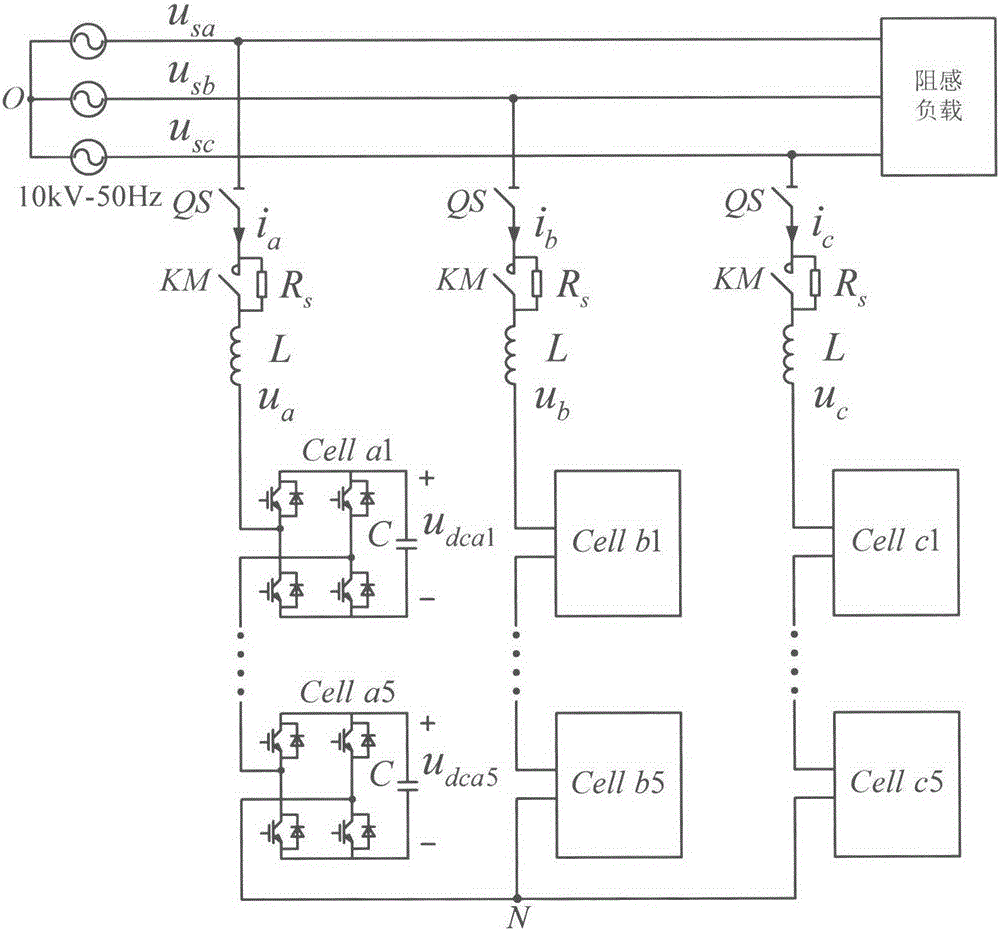
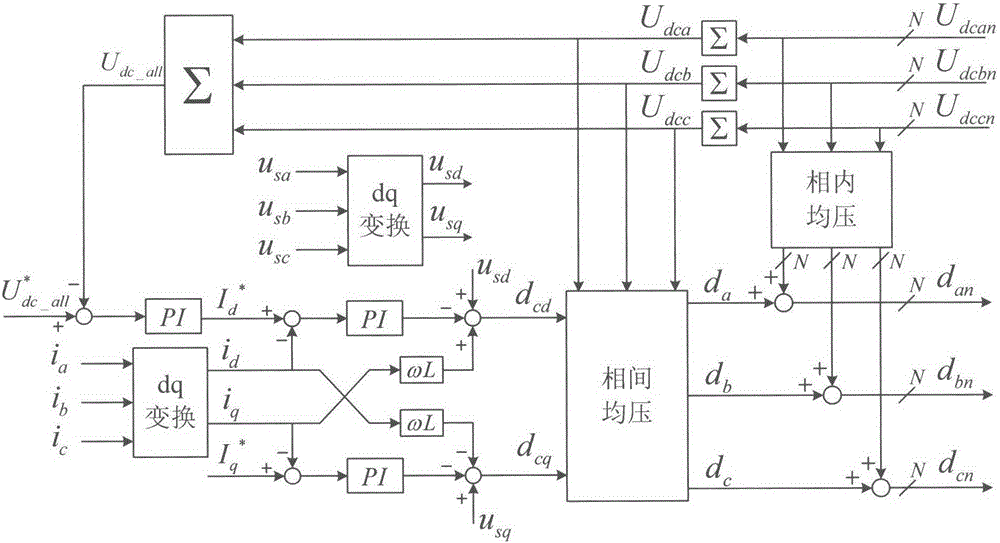
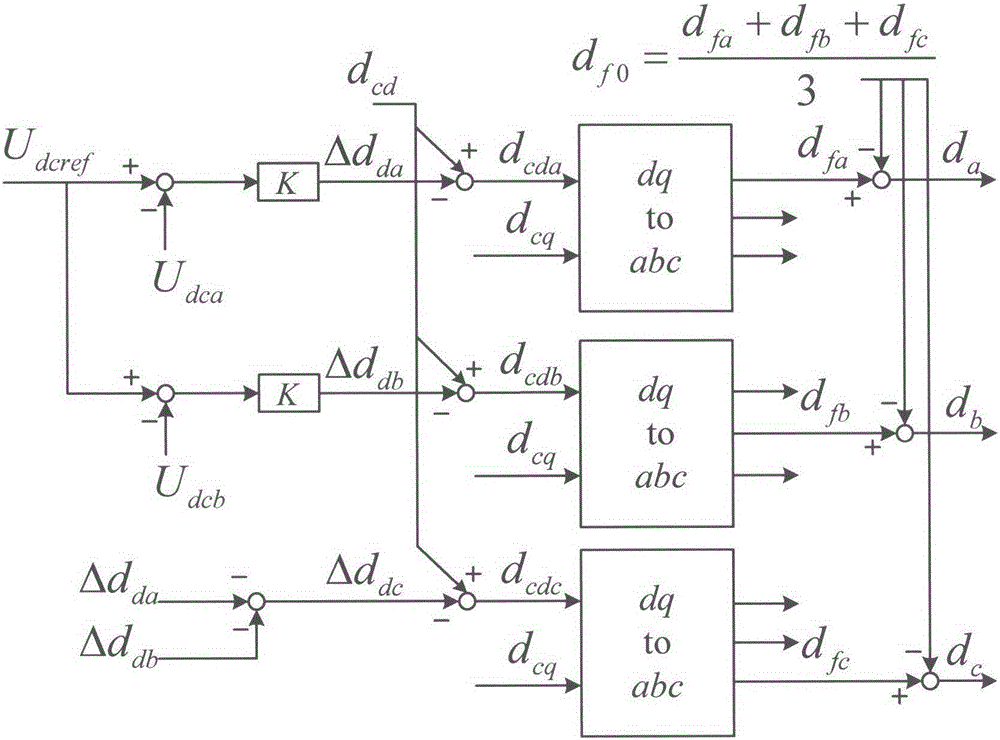
Inter-phase voltage-sharing control method for DC bus of cascaded star-connected static synchronous compensator (STATCOM)
InactiveCN105720587ANo need to consume resourcesSimple calculationFlexible AC transmissionReactive power adjustment/elimination/compensationPower flowEngineering
The invention discloses an inter-phase voltage-sharing control method for a DC bus of a cascaded star-connected static synchronous compensator (STATCOM). The voltage-sharing control method comprises the following steps of regulating a d-axis component of a modulation wave output from a current ring according to the deviation between DC voltages of a phase A and a phase B and a reference value; converting dq-abc conversion on the modulation, wherein a negative-sequence component is overlaid with the modulation wave, so that the output of the STATCOM generates the negative-sequence voltage. The negative-sequence voltage is used for generating a negative-sequence current, the negative-sequence voltage, the negative-sequence current, positive-sequence current and positive-sequence voltage are separately used for changing allocation of three-phase power flow, and the balance among three phase DC voltages is achieved. In the voltage-sharing method proposed by the invention, a mode of overlaying the negative-sequence modulation wave is simple and is easy to implement, the stability of the current ring is not affected, meanwhile, the introduced modulation wave zero-sequence component is also removed, over-modulation caused by the zero-sequence component is avoided, and the reliability of STATCOM running is improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Implementation method of novel lightweight block cipher CORL
ActiveCN111431697AImprove diffusivitySave resourcesEncryption apparatus with shift registers/memoriesAlgorithmControl signal
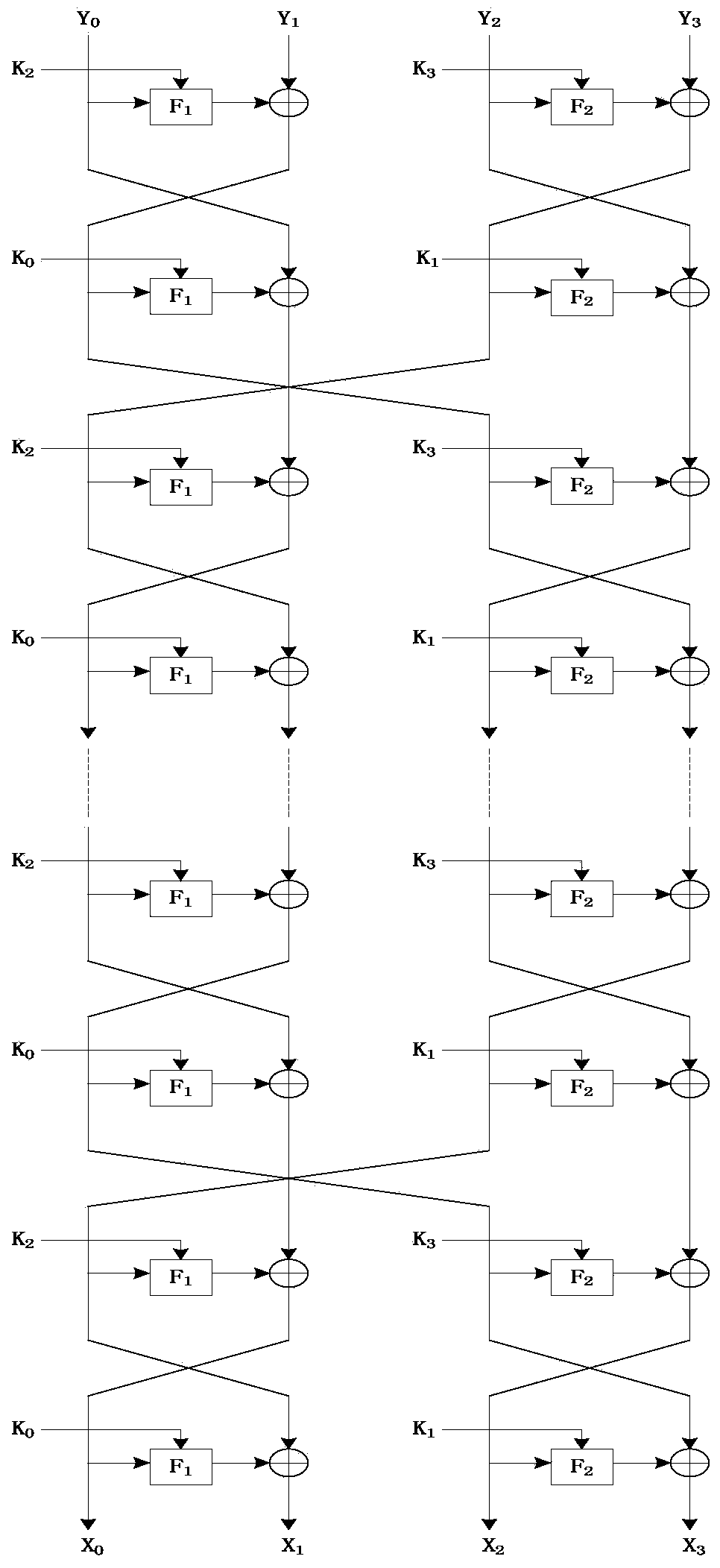
The invention discloses an implementation method of a novel lightweight block cipher CORL. According to the method, a novel generalized Feistel network structure is designed, the structural algorithmoptimizes the defect that a round of iterative operation of a traditional Feistel network structure only changes a half of data packet data, and achieves an effect that three fourths of packet data ischanged through a round of iteration. An algorithm round function comprises an F function, and the conversion process of the F function sequentially comprises row shifting, round key addition, S boxreplacement, row shifting and column confusion. The algorithm structure is convenient for software and hardware realization, the algorithm decryption basically multiplexes the encryption module, decryption can be performed only by adding some control signals, the operation is simple, and decryption is realized without consuming more resources. Compared with the current block cipher, the occupied resource is small, the encryption performance is high, and the known attack can be resisted.
Owner:HENGYANG NORMAL UNIV
Video image matting processing method, video image matting processing client and readable storage medium
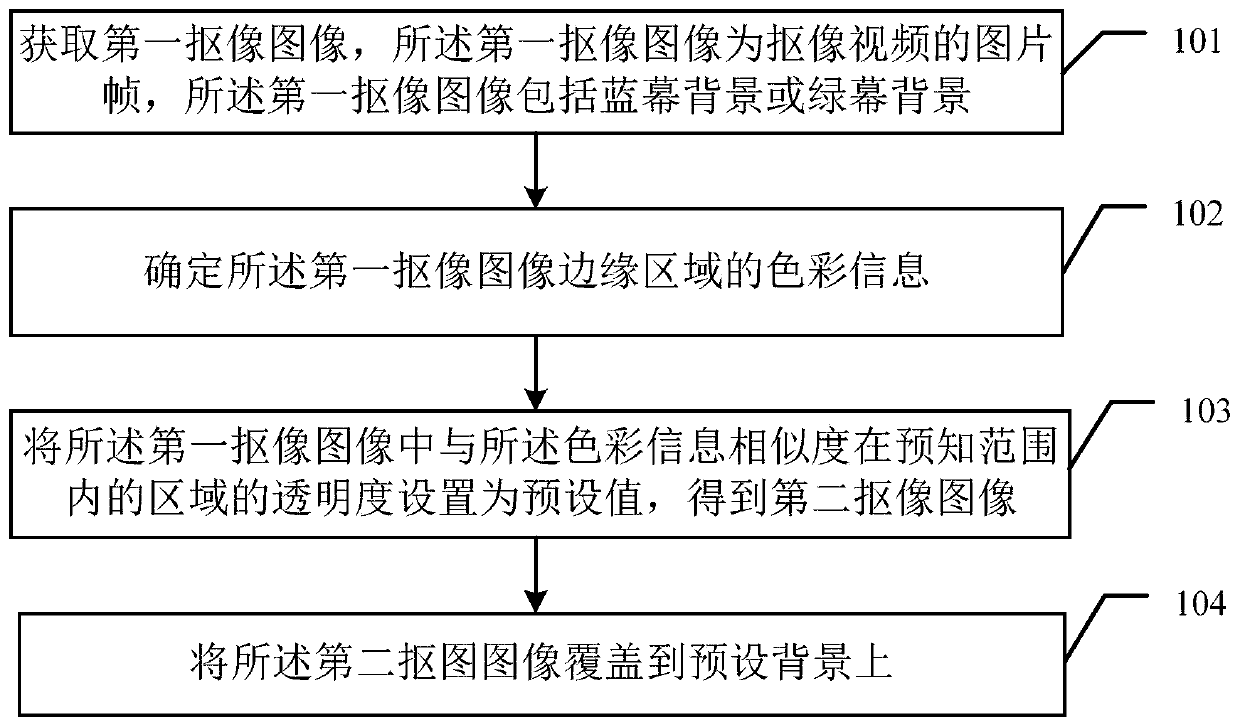
InactiveCN109919836ANo need to consume resourcesImprove real-time performanceTelevision system detailsImage analysisComputer graphics (images)Video image
The embodiment of the invention discloses a video image matting processing method, a video image matting processing client and a readable storage medium, and the method comprises the steps that the video image matting processing client obtains a first image matting image, and the first image matting image is a picture frame of an image matting video; The video image matting processing client determines color information of an edge area of the first image matting image; The video image matting processing client sets the transparency of an area with the color information similarity within a preset range in the first image matting image as a preset value to obtain a second image matting image; And the video image matting processing client covers the second matting image on a preset backgroundto obtain a synthesized image. By means of the mode, a video does not need to be uploaded to a server, server decoding, image matting and video synthesis are not needed, a user does not need to consume any server resource in the embodiment, image matting operation can be completed at a browser end, and the real-time performance of image matting and synthesis is improved.
Owner:广州方硅信息技术有限公司
Intelligent apparatus and communication method with outside and device
ActiveCN101169652AReduce volumeTo achieve interoperabilityTelephonic communicationData switching by path configurationThird partyApplication server
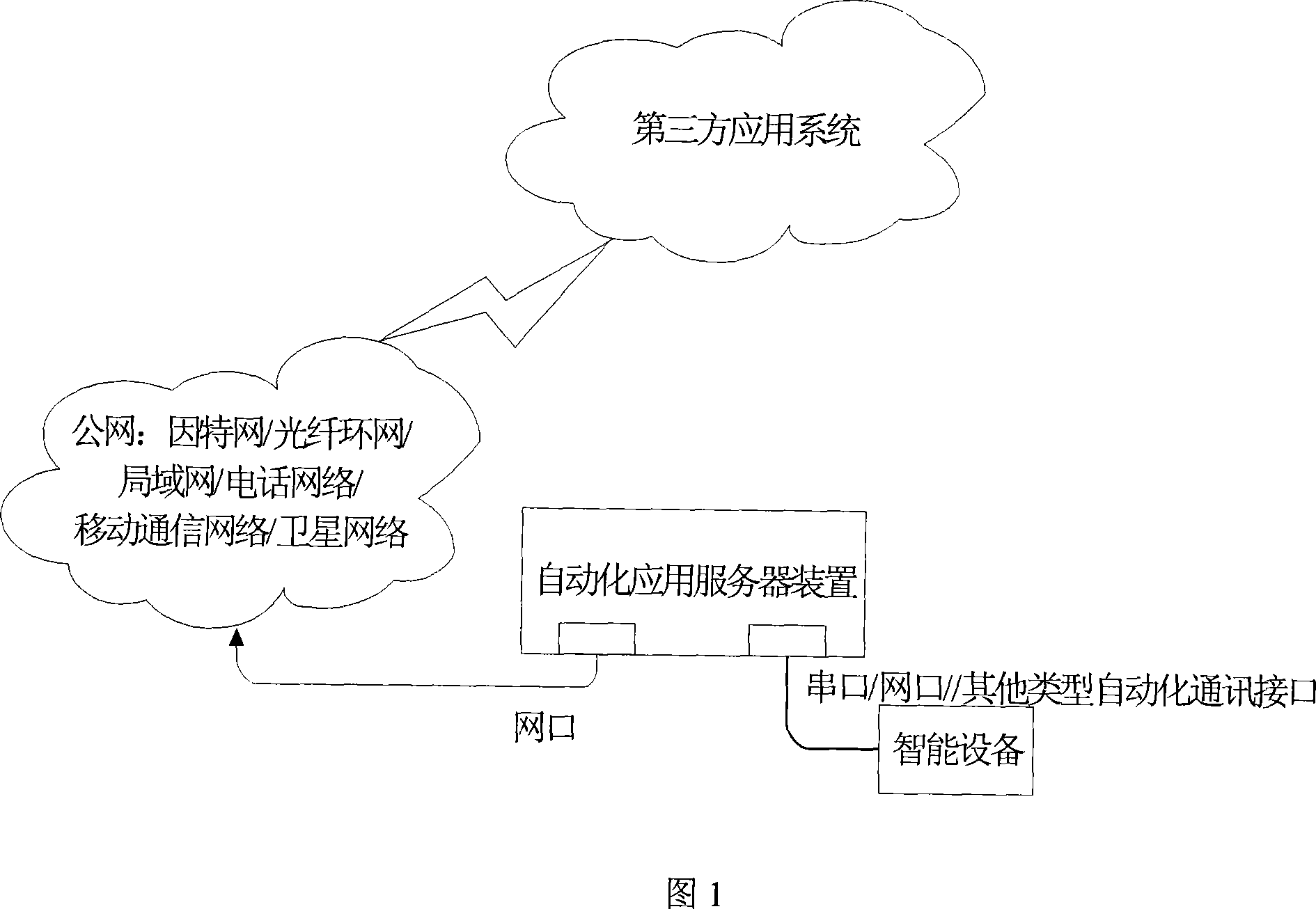
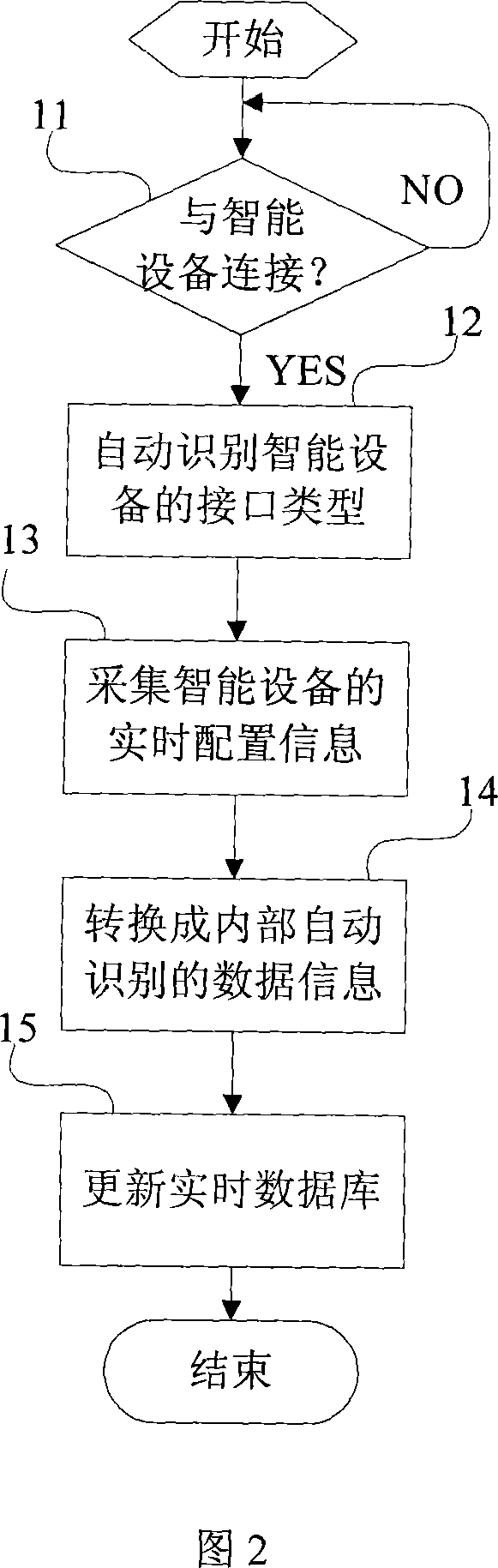
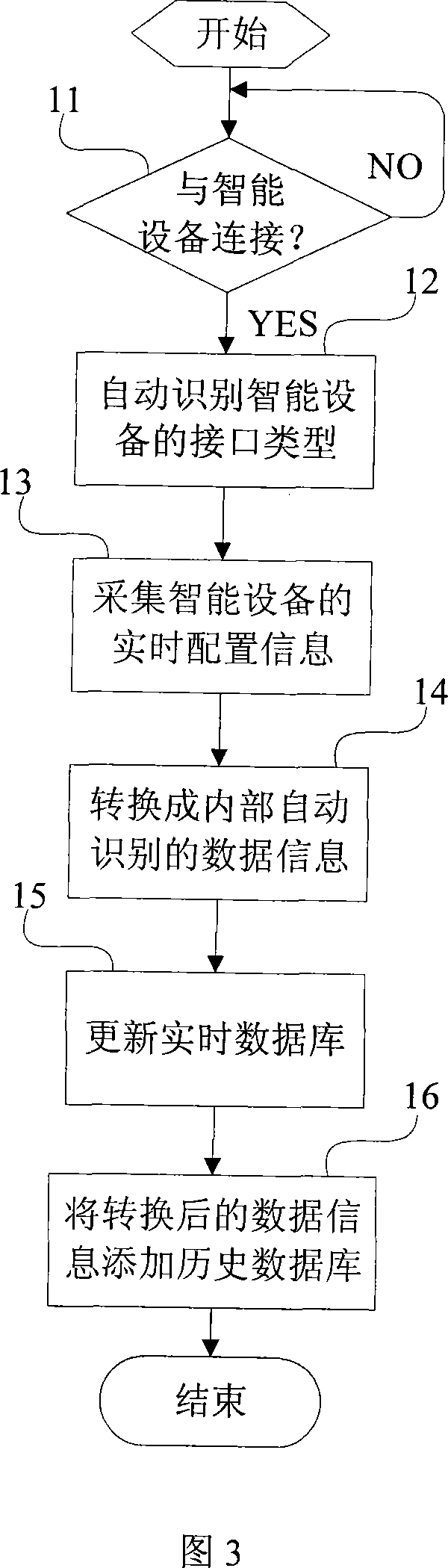
The invention relates to a communication method of the intelligent equipment with the outside and a device to achieve the method. An automation application server device firstly receives control orders from a third-party application system through a network; wherein, the control orders are converted into communication data that the intelligent equipment can identify under real-time configuration information in the real-time database thereof, and then transmitted to the intelligent equipment. Compared with the prior art, the invention has advantages that: the communication of the intelligent equipment with the outside is realized through the automation application server device that stores the real-time database with real-time configuration information in the intelligent equipment, and automation application server device can timely realize the communication of the intelligent equipment with the third-party of outside, thereby not only allowing the fault information of the intelligent equipment to timely feedback the third-party application system, but also transmitting maintenance instructions sent by the third-party application system to the intelligent equipment, thereby achieving timely, efficient and safe communication.
Owner:ASAT CHINA TECH
Multi-user co-vibrating system and method realized by mobile core network
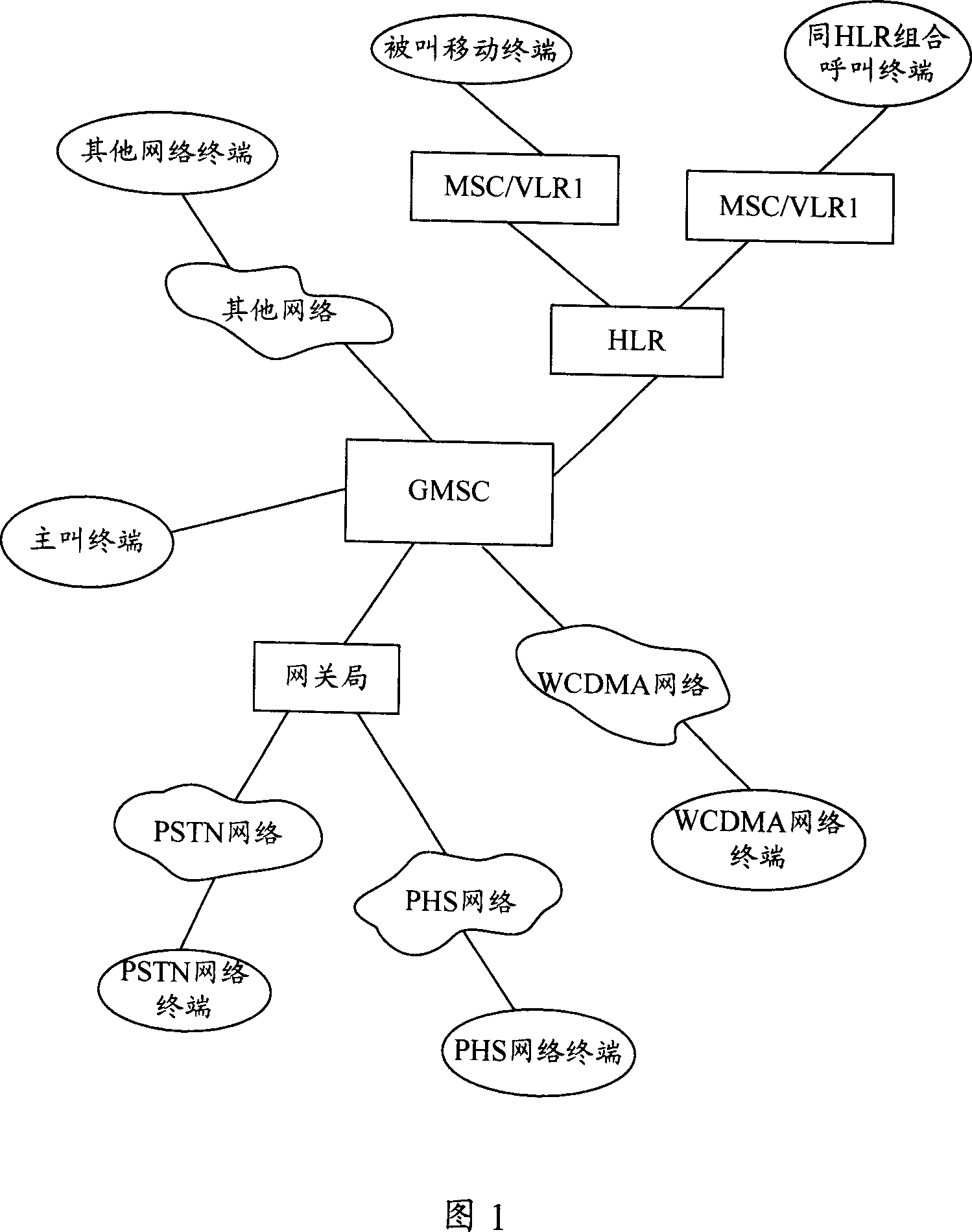
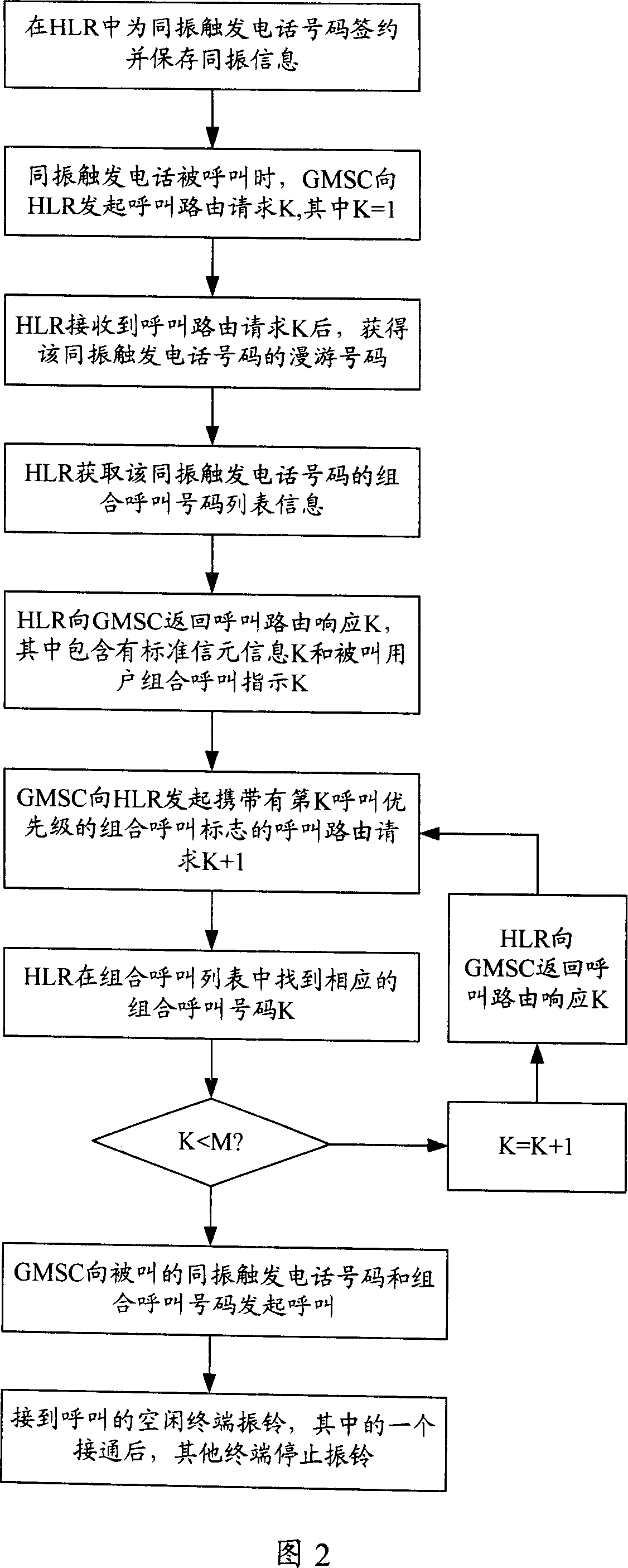
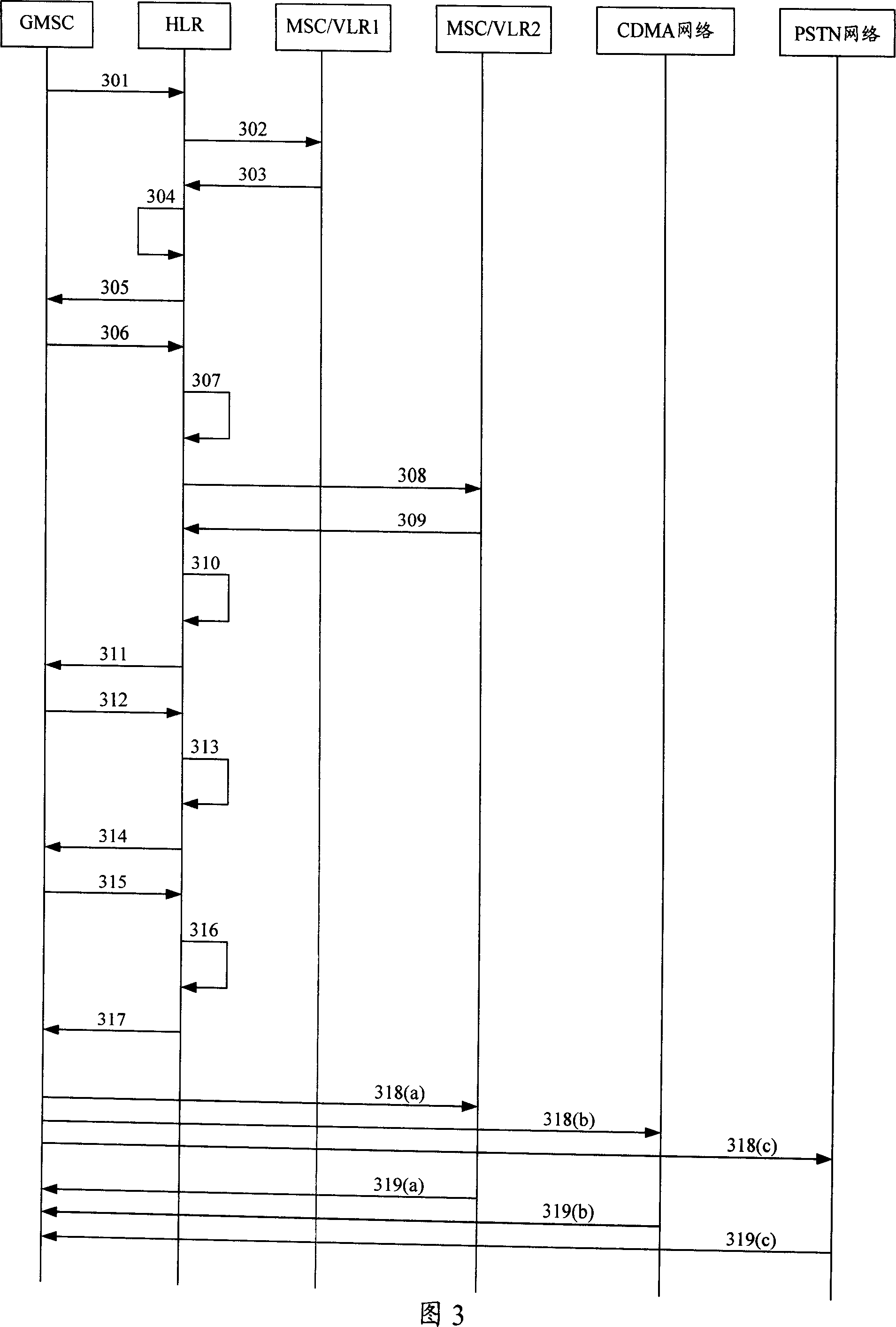
InactiveCN101026790AConducive to maintenanceRealize simultaneous vibration businessSpecial service for subscribersConnection managementReal-time computingCore network
Without need of consuming resources of intelligent network, the invention can be implemented by net element device of mobile core network. The system upgrades functions of GMSC and HLR devices, and expands route request and response message in calling flow. The method includes steps: storing together vibrant information signed by target mobile user in HLR; when the target mobile user is called, MSC / GMSC initiates request of call route to HLR; HLR returns route response message of together vibrant information with signing target mobile user back to MSC / GMSC; based on together vibrant information in route response message, MSC / GMSC executes together ringing. Managing and maintaining data of together vibrant service signed by users in HLR, the invention realizes the service only through mobile core network.
Owner:ZTE CORP
Solvent for anti-vacuum casting of chromium zircomium copper
The invention relates to a preparation method of a solvent for anti-vacuum casting of chromium zircomium copper, comprising the following steps: mixing 60-65 weight portions of boric acid, 7-10 weight portions of sodium chloride, 15-25 weight portions of cryolite and 8-10 weight portions of fluorite; carrying out heat fusing to obtain a mixture with the temperature of 850-900 DEG C, and then naturally cooling to room temperature; and crushing to obtain the solvent for anti-vacuum casting of chromium zircomium copper. By covering the solvent on the liquid surface of the casting crystallizer, the liquid surface can be sealed without oxidation by contacting with atmosphere, the activity of the protective layer is good, harmful gas in the copper liquid can be effectively discharged, and oxides in the copper liquid can be kept on the surface of the solvent, so that the brightness and clean of the surface of the ingot casting can be guaranteed, the defects of oxide inclusion and pores are avoided, and the qualified rate of the ingot casting reach more than 97 %. The solvent has the advantages of easy obtainment and convenient purchase of raw materials, simple preparation, and low cost.
Owner:JIANGSU LONGDA SUPERALLOY MATERIAL CO LTD
Protocol-independent forwarding network rapid fault detection and flow protection switching method
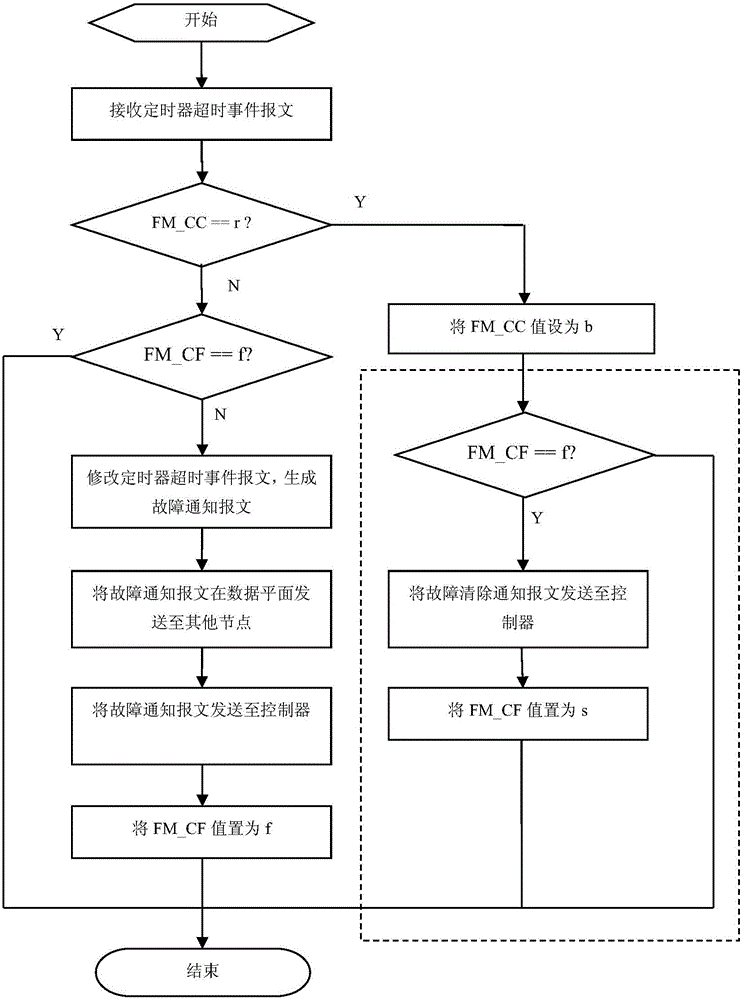
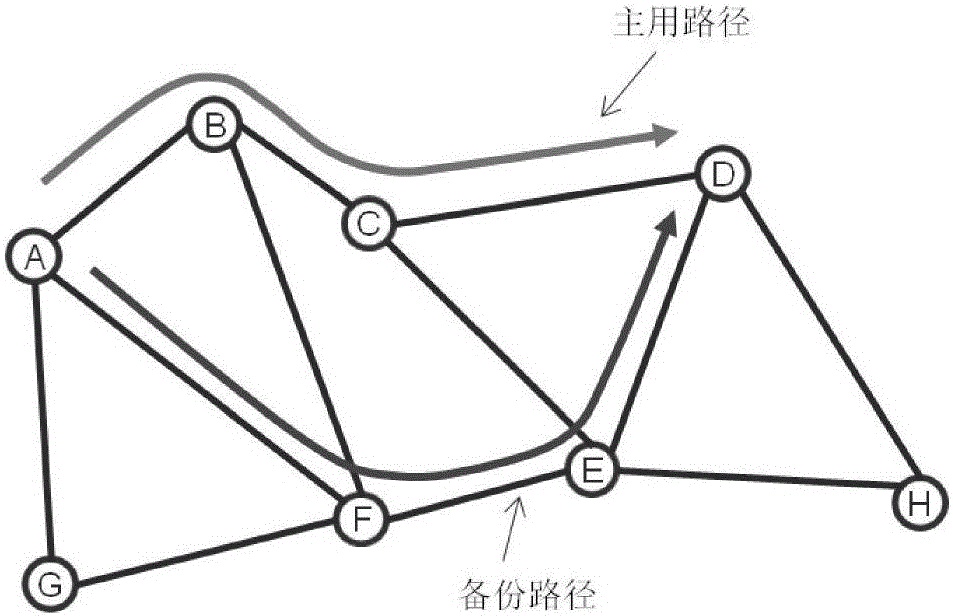
ActiveCN105897580AImprove acceleration performanceImprove adaptabilityData switching networksTraffic volumeData transmission
The invention discloses a protocol-independent forwarding network rapid fault detection and flow protection switching method which includes following steps. A controller notifies that each pair of switches S1 and S2 start a timer respectively. When a transmission timer on the S1 is overtime, a connectivity inspection message is generated and sent to S2, and S2 sets a stream metadata unit FM_CC as r. When an inspection timer on S2 is overtime, the FM_CC value is detected. If the FM_CC value is r, then the FM_CC value is set to b; if the FM_CC value is b, a fault notice message is generated and sent to switch that has to respond to the fault event, and S1 is notified of the fault. S1 sends the fault notice to a switch that has to respond to the fault event. When a source node sends data to a target node through a flow switching node, the flow switching node checks the availability of a main path. If the main path is available, the data are transmitted through the main path; otherwise, a standby path is selected for data transmission.
Owner:INST OF INFORMATION ENG CAS
Data processing method and system for risk weighted asset calculation
ActiveCN102393945AAvoid duplicate storageImprove processing efficiencyFinanceData ingestionApplication server
The invention discloses a data processing method and a data processing system for risk weighted asset calculation. The system comprises a data extraction module, a field value calculation module, a risk weighted asset value calculation module and a report display module. In the method and the system, a data storage model for the risk weighted asset calculation is divided into four layers; data processing for the risk weighted asset calculation is realized among the layers by extracting, converting and loading data according to respective mapping documents of the four layers, so repeated data storage is avoided, a large quantity of application server resources is not required, and the processing efficiency of the system is improved on the premise of realizing the function of the system. Furthermore, uniform processing for a large amount of readily available data can be realized by splitting a logic of the risk weighted asset calculation according to asset classification, calculating risk weighted asset values respectively and finally integrating calculated results; and therefore, the processing efficiency of the system can be improved and the cost of the system can be reduced.
Owner:CHINA CONSTRUCTION BANK
Construction method with aluminum alloy formworks as gravity type highway retaining wall formwork and retaining wall
InactiveCN107366303AMeet construction quality requirementsHigh strengthArtificial islandsUnderwater structuresForest resourceRetaining wall
The invention discloses a construction method with aluminum alloy formworks as a gravity type highway retaining wall formwork and a retaining wall and relates to the technical field of building construction. The technical problems that according to traditional formworks, the construction quality requirements of the gravity type retaining wall built at a mountain highway section adjacent to a cliff or a river cannot be meet, in addition, potential safety hazards exist, and forest resources are excessively consumed are relieved. According to the construction method with the aluminum alloy formworks as the gravity type highway retaining wall formwork, the aluminum alloy formworks are adopted to be assembled into the retaining wall formwork in a sectioned mode on a spacious site firstly, then the retaining wall formwork is hoisted to the designed position and fixed, and then concrete is poured; the construction quality requirements of the gravity type retaining wall built at the mountain highway section adjacent to the cliff or the river can be meet, besides, safety accidents can be reduced to the maximum limit, the construction speed can be also improved, and the constriction period is shortened; and meanwhile, the collapse phenomenon can be avoided, wood resources do not need to be consumed, and thus the energy-saving and environment-friendly beneficial effects are achieved. The retaining wall can take the effects of slope protection and edge protection for a long time.
Owner:江苏燕宁工程科技集团有限公司
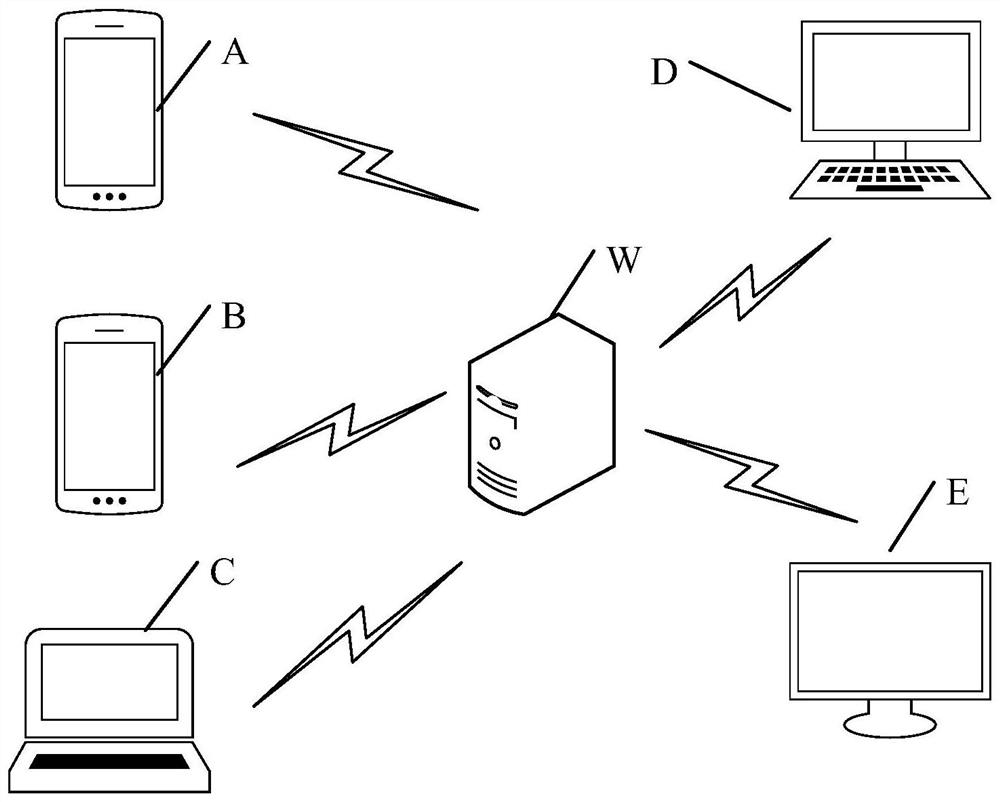
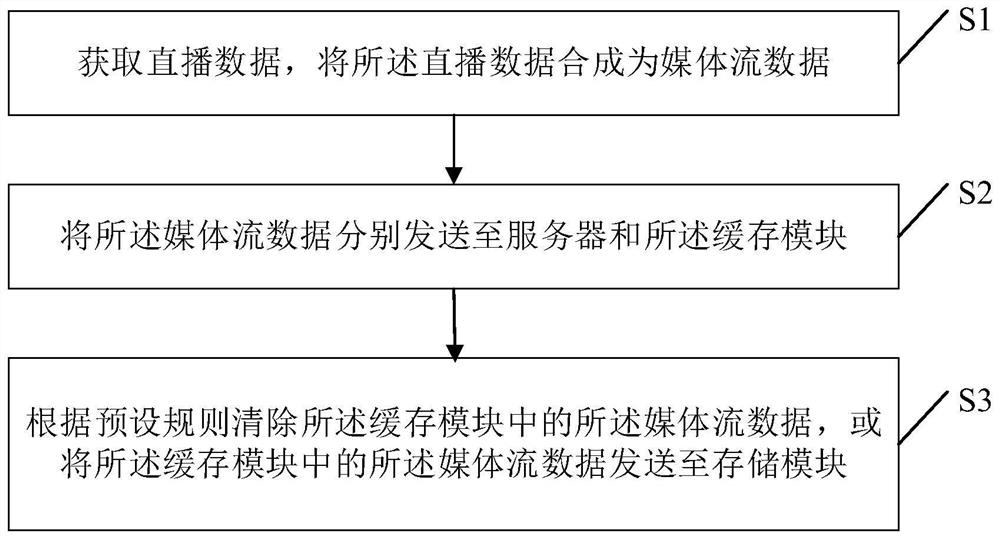
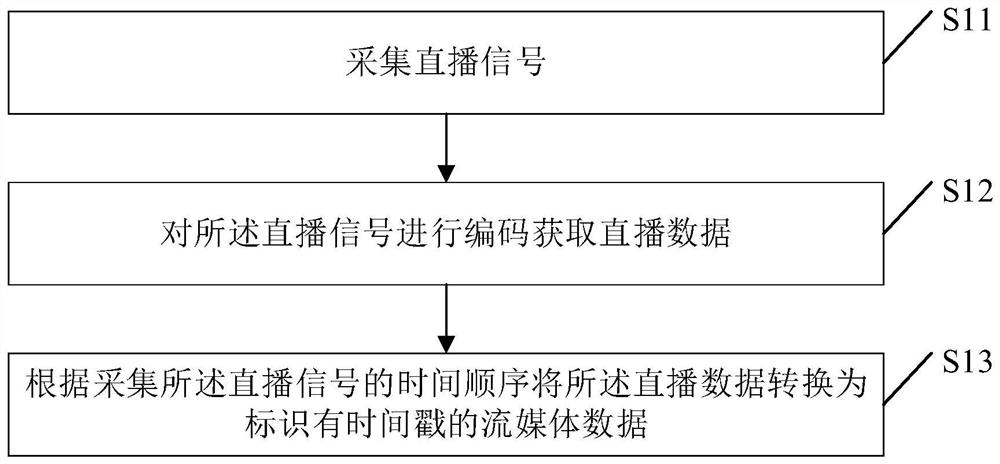
Live broadcast playback method, computer equipment and readable storage medium
PendingCN112019905ANo need to consume resourcesAvoid taking up memory spaceSelective content distributionStreaming dataComputer network
The invention discloses a live broadcast playback method, computer equipment and a readable storage medium, and belongs to the technical field of the Internet. According to the invention, the obtainedlive broadcast data is synthesized into the media stream data, the media stream data is sent to the server and the local cache module, the media stream data can be cached locally by adopting the cache module, and when a local live broadcast end user wants to obtain a video, the media stream data stored in the cache module can be extracted; the cache module can be periodically cleared according toa preset rule so as to avoid occupying the memory space of a local client, and the playback video can be independently generated without consuming server resources.
Owner:SHANGHAI BILIBILI TECH CO LTD
Personnel unconventional behavior rapid identification method based on inertial sensor
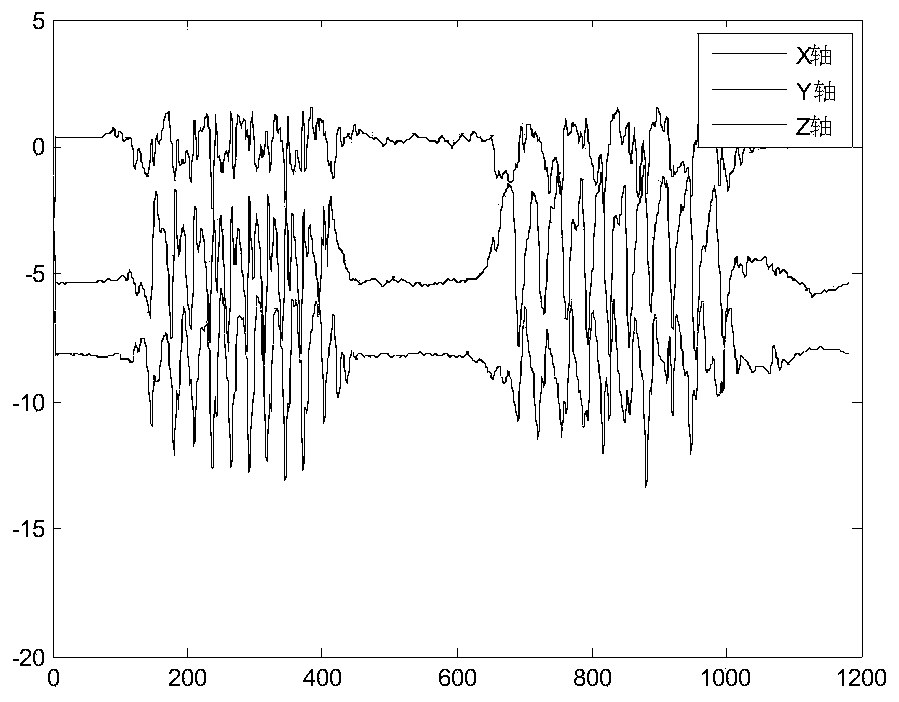
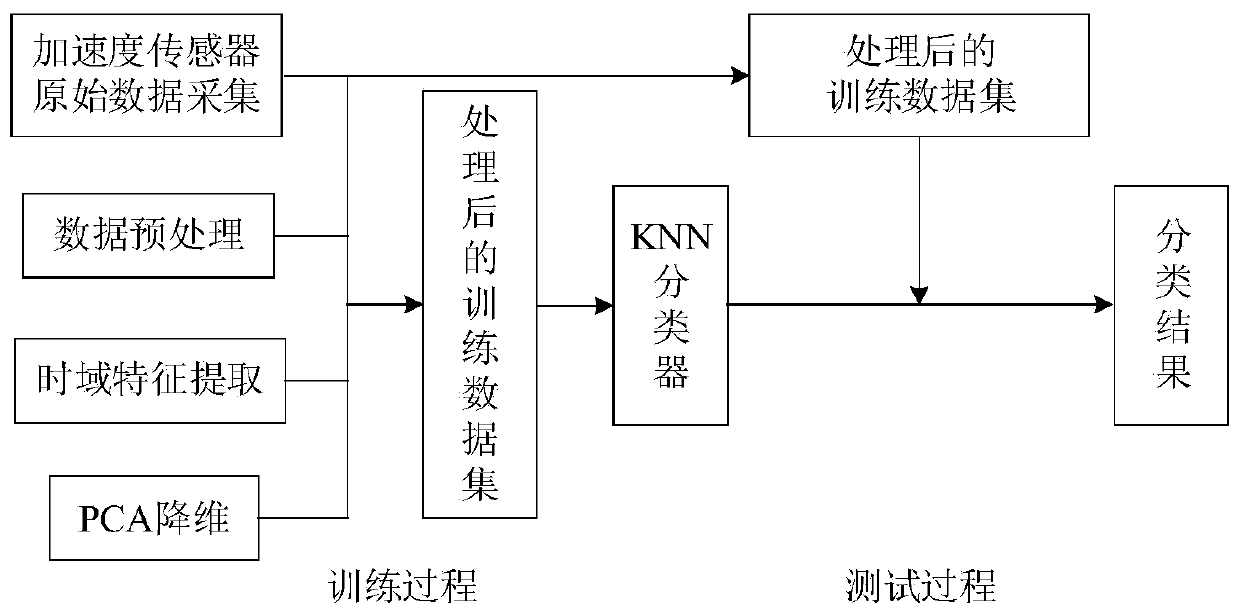
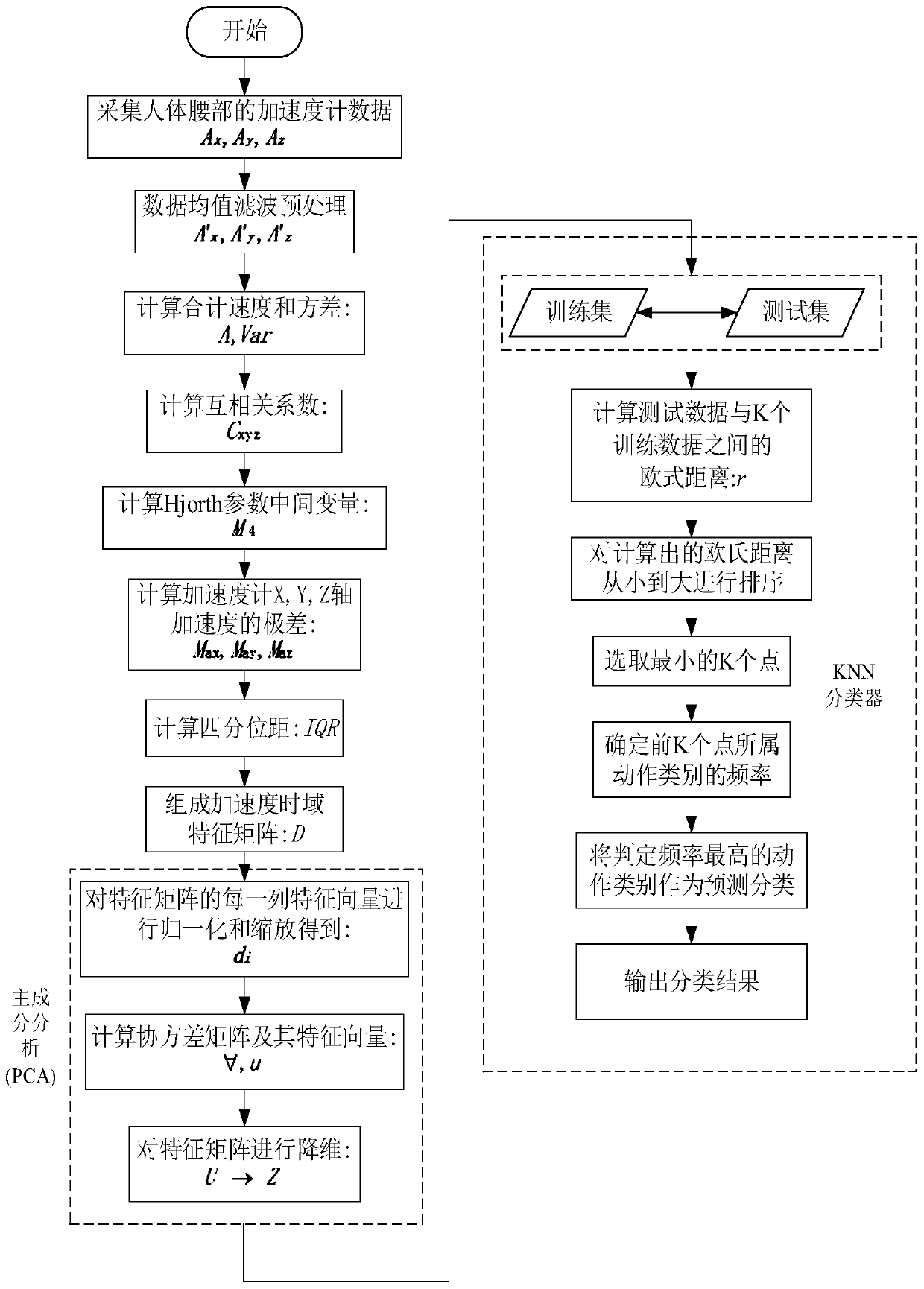
ActiveCN111259956ALow costReduce power consumptionAcceleration measurement using interia forcesCharacter and pattern recognitionTime domainAccelerometer
The invention discloses a personnel unconventional behavior rapid identification method based on inertial sensor, and belongs to the field of mode identification. According to the method, an individual soldier positioning module is installed on the waist of a pedestrian, a gyroscope, an accelerometer and other sensing devices are arranged in the individual soldier positioning module, and the accelerometer is used for measuring real-time X-axis, Y-axis and Z-axis acceleration information of the waist of the pedestrian. After acceleration time domain characteristic parameters are calculated, dimensionality reduction is performed on a time domain characteristic matrix by adopting PCA (Principal Component Analysis); and finally, the time domain feature matrix obtained through dimension reduction compression is input into a K nearest neighbor (KNN: k-NetworstNetwork) classifier, so that an effect of behavior pattern recognition is achieved. According to the method, measurement and calculation can be carried out in real time for unconventional behaviors in a special application scene, the calculation efficiency can be improved, and a mode recognition result can be quickly obtained.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Efficient filtering equipment for sewage treatment
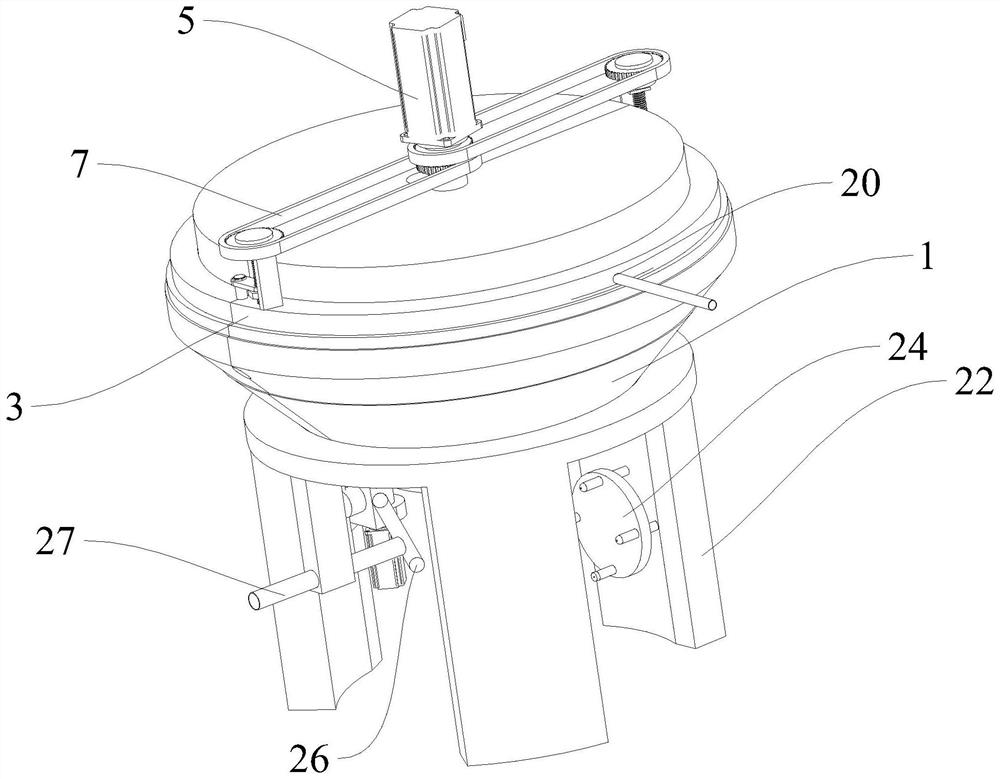
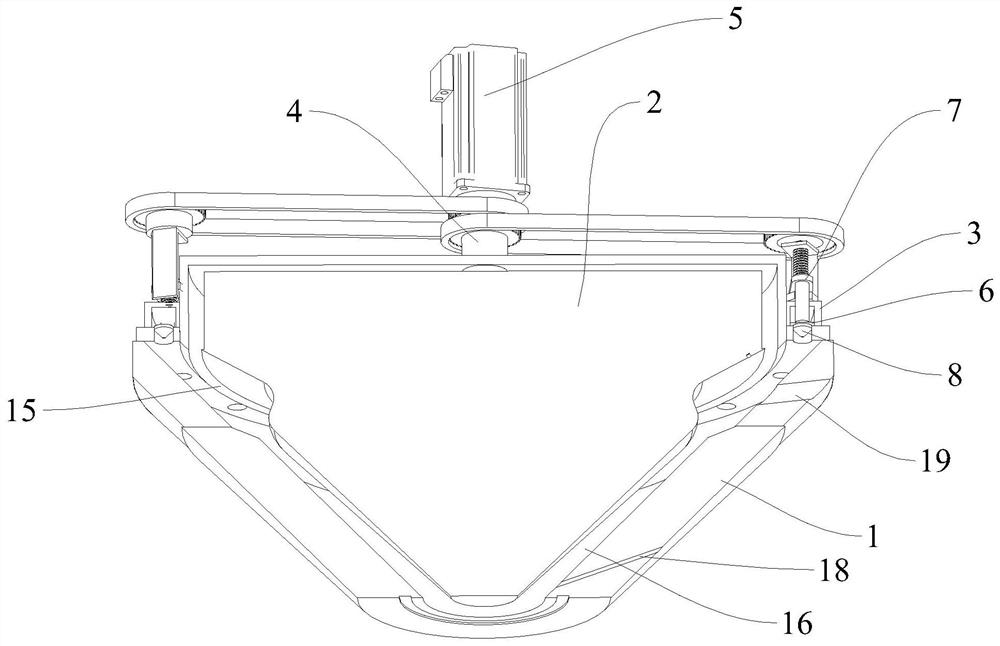
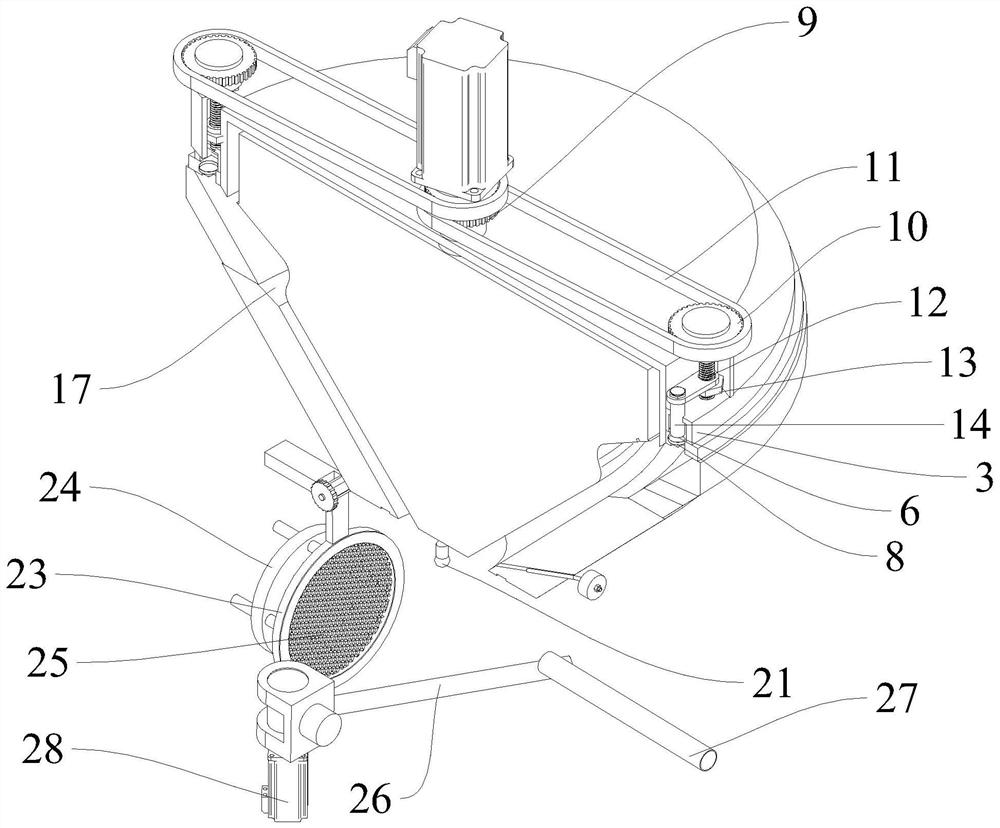
ActiveCN111450611AImprove processing efficiencyImprove permeabilityStationary filtering element filtersWater wheelOutfall
The invention discloses efficient filtering equipment for sewage treatment. The equipment comprises an equipment base body, a water inlet is formed in the upper end of the equipment base body; a circular groove communicated with the water inlet is formed in the side wall of the equipment base body; a rotary disc is coaxially, hermetically and rotatably connected into the circular groove; a plurality of through holes with different sizes are formed in the side wall of the rotary disc, a water wheel is coaxially and fixedly connected to the side wall of the rotary disc, a water outlet communicating with the interior of the circular groove is formed in the side wall of the equipment base body, a filter screen is embedded in the water outlet, and a buoyancy scraper matched with the filter screen is slidably connected into the water outlet. Sewage flows out through the through holes with different sizes, and the liquid level in the water outlet can continuously fluctuate up and down, so that the buoyancy scraper in the water outlet moves up and down along with the liquid level, garbage and impurities adhered to the filter screen can be scraped into a storage tank under the filter screenin time, good permeability of the filter screen is kept, and the sewage treatment efficiency is further improved.
Owner:中节能(西安)生态环保有限公司
Deployment method of unmanned aerial vehicle base station based on undirected graph
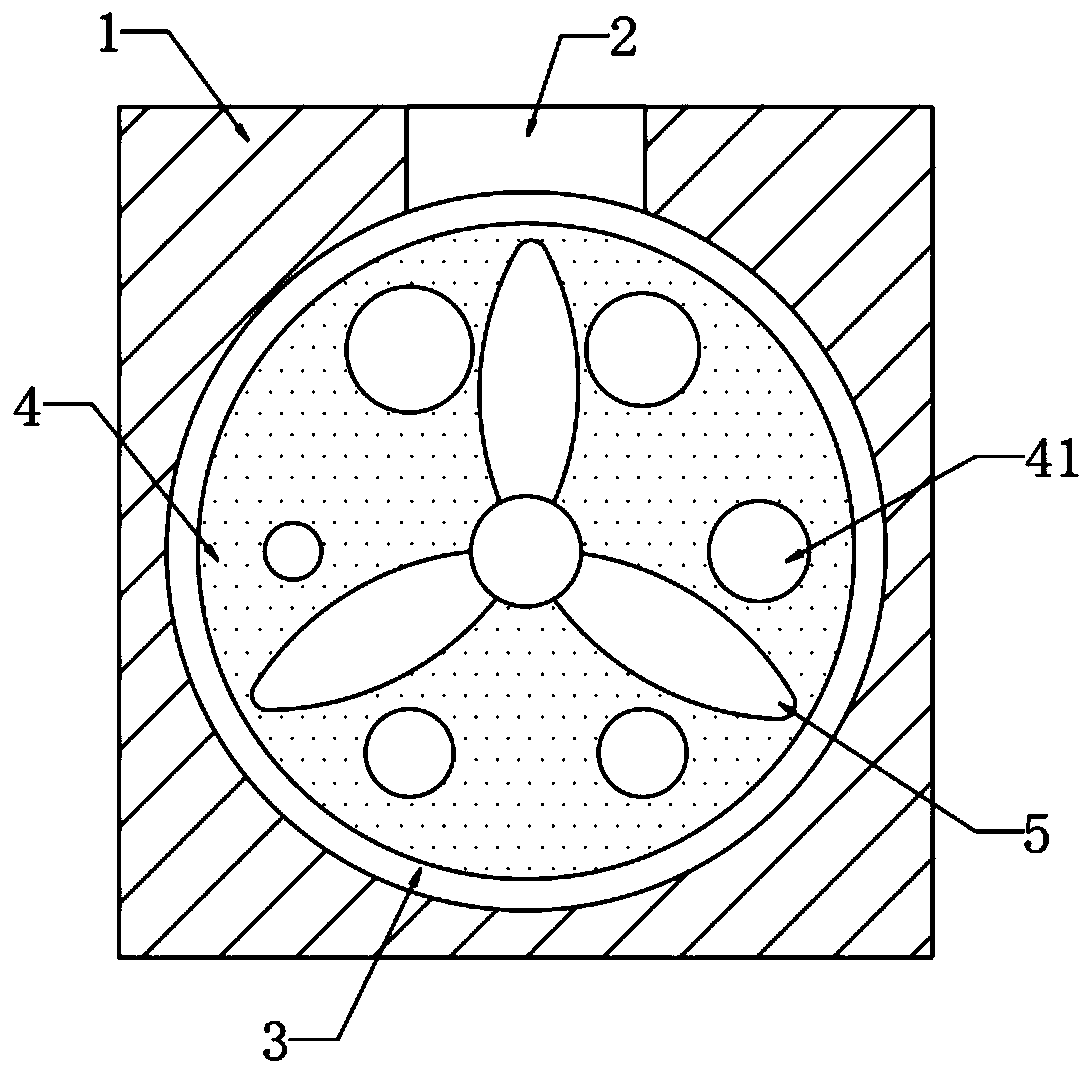
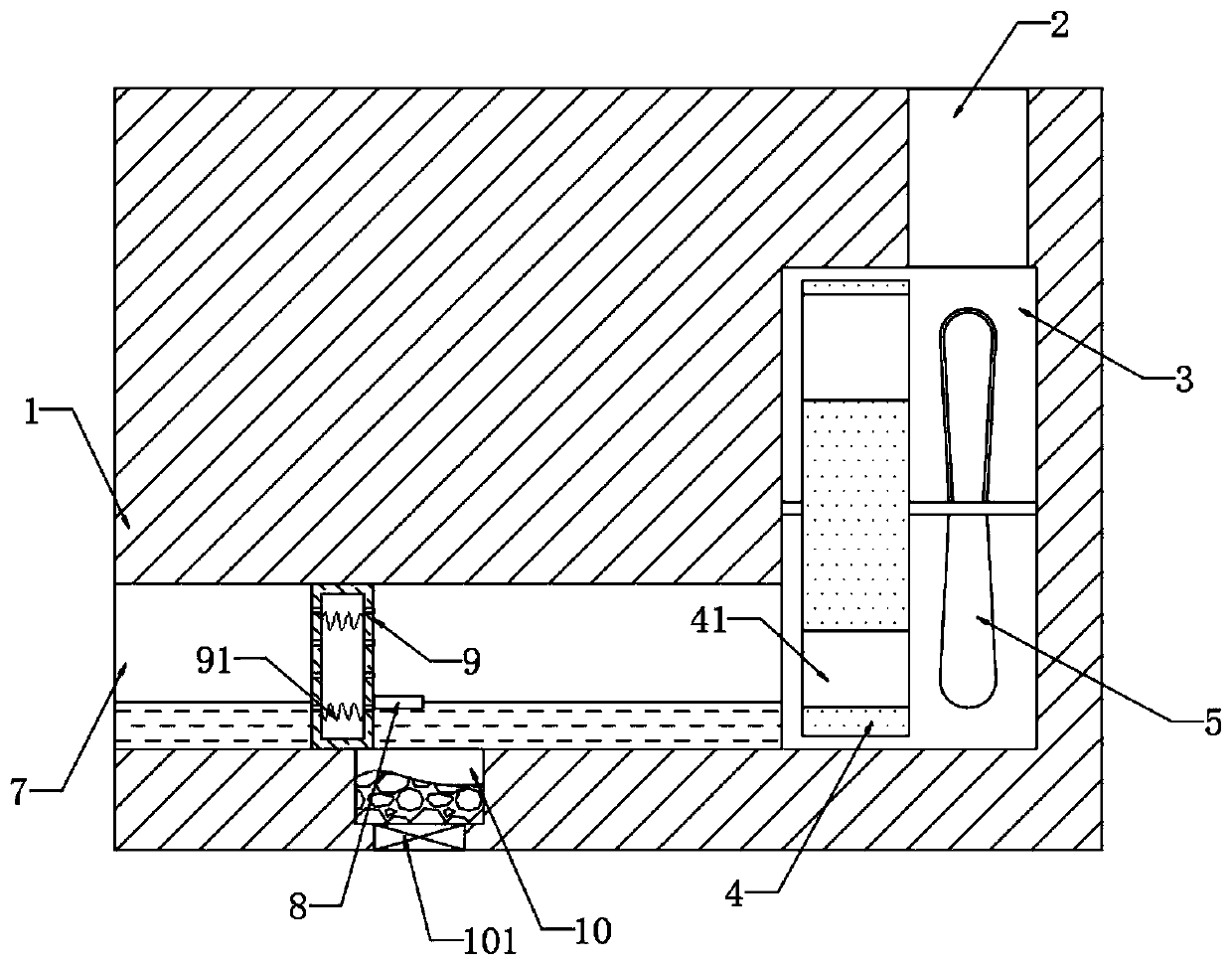
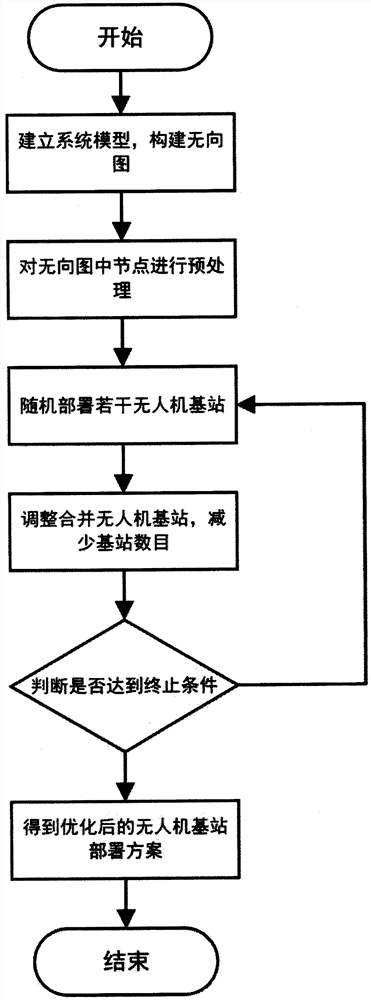
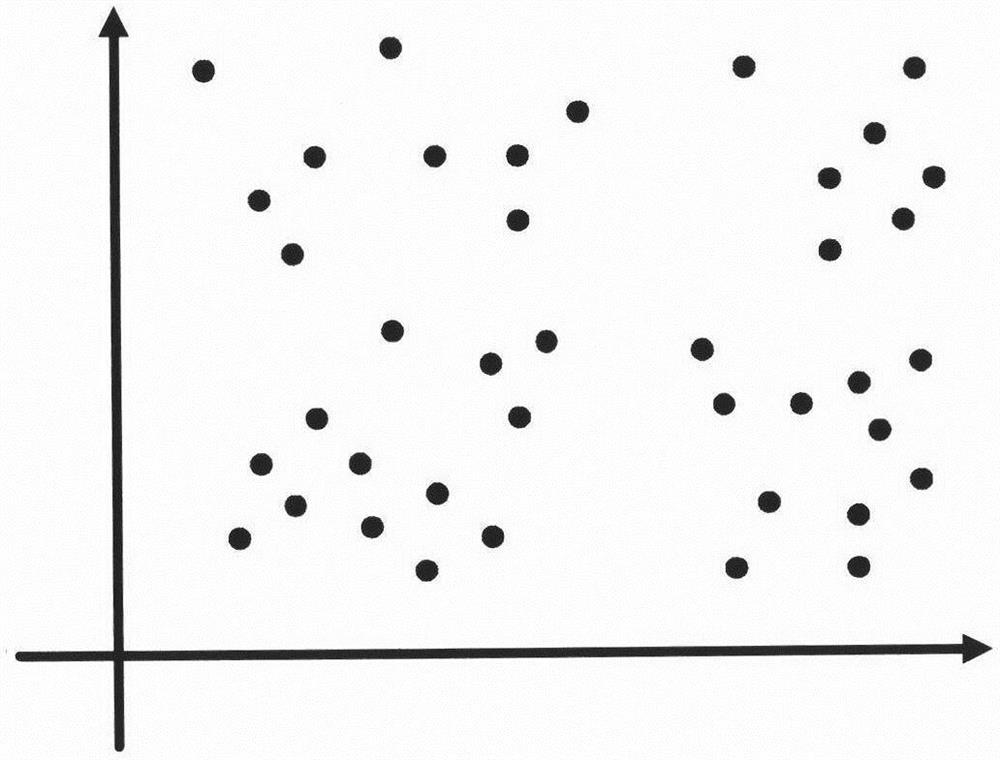
ActiveCN112351438AImprove layout efficiencyNo need to consume resourcesRadio transmissionNetwork planningUndirected graphReal-time computing
The invention provides an deployment method of unmanned aerial vehicle base station based on an undirected graph, and mainly solves the problem of optimal deployment of base stations for unmanned aerial vehicles. The method comprises the following steps of: 1) drawing the undirected graph according to distance information between ground terminals; 2) based on the undirected graph, preprocessing nodes with degrees of 0 and 1 in the undirected graph; and 3) dividing the undirected graph into a plurality of first-order or second-order complete sub-graphs, and deploying the base station of the unmanned aerial vehicle based on the first-order or second-order complete sub-graphs; 4) continuously adjusting the coverage area of the base stations according to the degree information of the vertexesand the adjacent information of the vertexes in the undirected graph, combining the base stations, and reducing the number of the base stations. and 5) repeating the processes 3) and 4) for multiple times to optimize the deployment scheme until the termination condition is reached. The invention can be deployed efficiently at low cost, and applied to area monitoring, temporary communication and the like.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
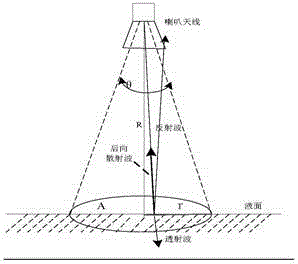
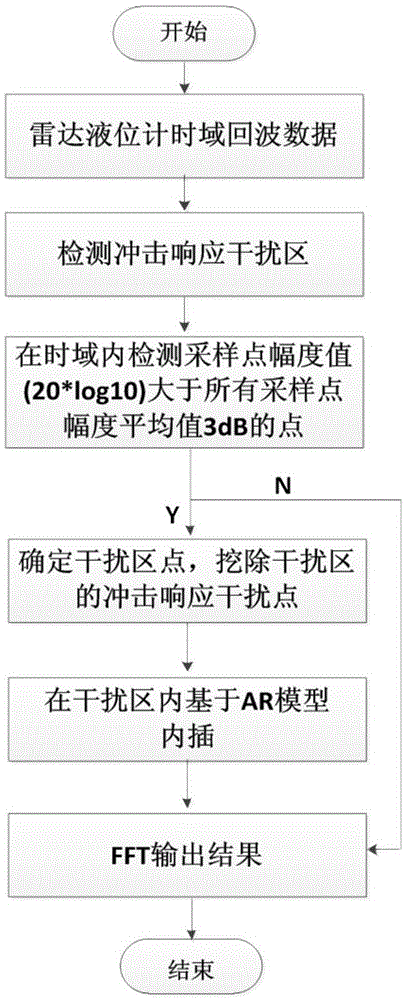
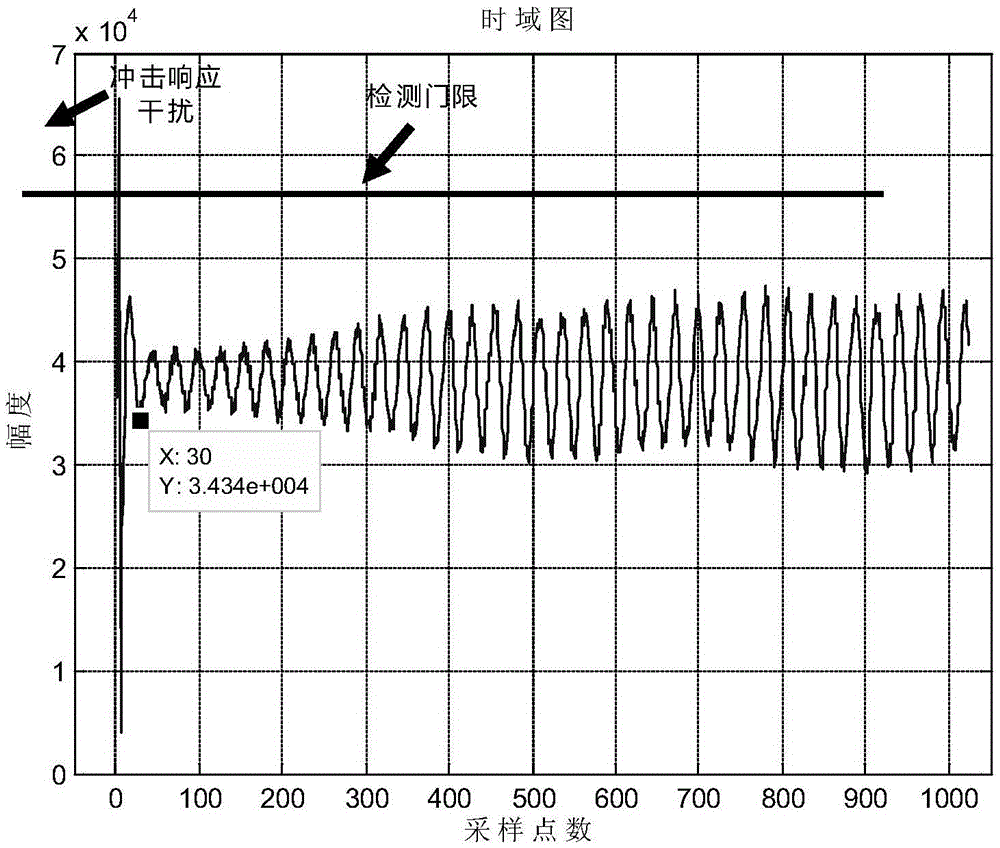
Method for suppressing interference of echo-impact response of frequency modulated continuous wave(FMCW) radar fluid-level meter
InactiveCN106842145AGood effectSuppression of impulse response disturbancesWave based measurement systemsMachines/enginesFluid levelModulated continuous wave
The invention provides a method for suppressing interference of echo-impact response of a frequency modulated continuous wave(FMCW) radar fluid-level meter. The method is characterized by including the following steps of detecting impact response interference zone, analyzing measured detecting sampling points in a way of x<0>,x<1>,...x<N-1>; detecting detecting sampling points which are satisfied with the formula (1)(the formula is as shown in the description) in time-domain, wherein the x,(i=0, 1, 2...N-1) represents the ith sampling point; taking fifteen points of the left side and the right side of an amplitude maximum point in the detecting sampling points respectively as the impact response interference zone, and if points on the left side of the detecting sampling points are less than fifteen points, taking all sampling points from the first point on the left side to the amplitude maximum point; drugging out detecting sampling points in the impact response interference zone in the original signal of time-domain and compensating zero; predicting and interpolating based on auto regressive(AR) model.
Owner:LEIHUA ELECTRONICS TECH RES INST AVIATION IND OF CHINA
Preparation device for ceramic bond of ceramic diamond grinding wheel
ActiveCN113477375AKeep dryImprove grinding effectGlass recyclingDrying gas arrangementsReciprocating motionMachining
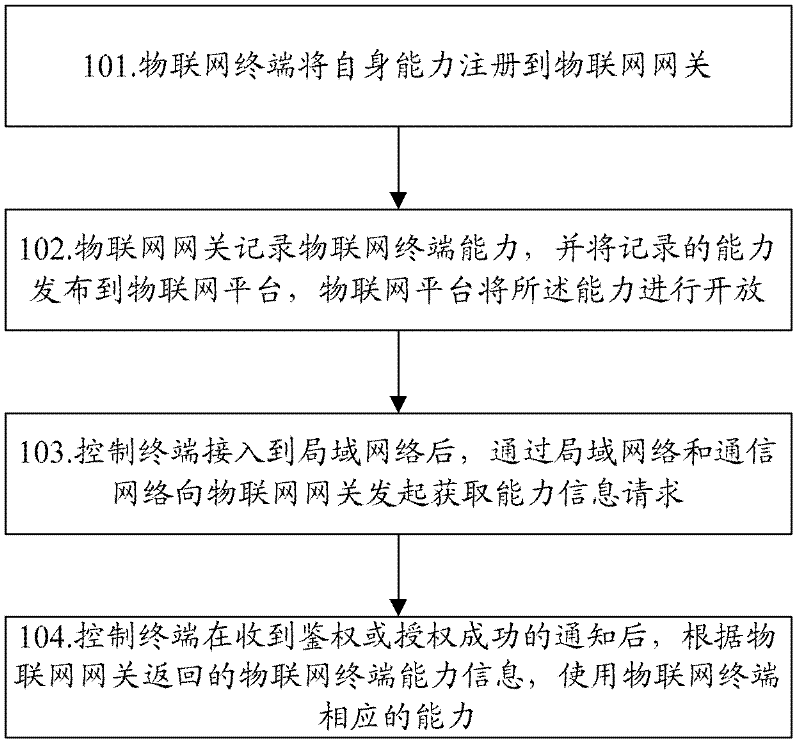
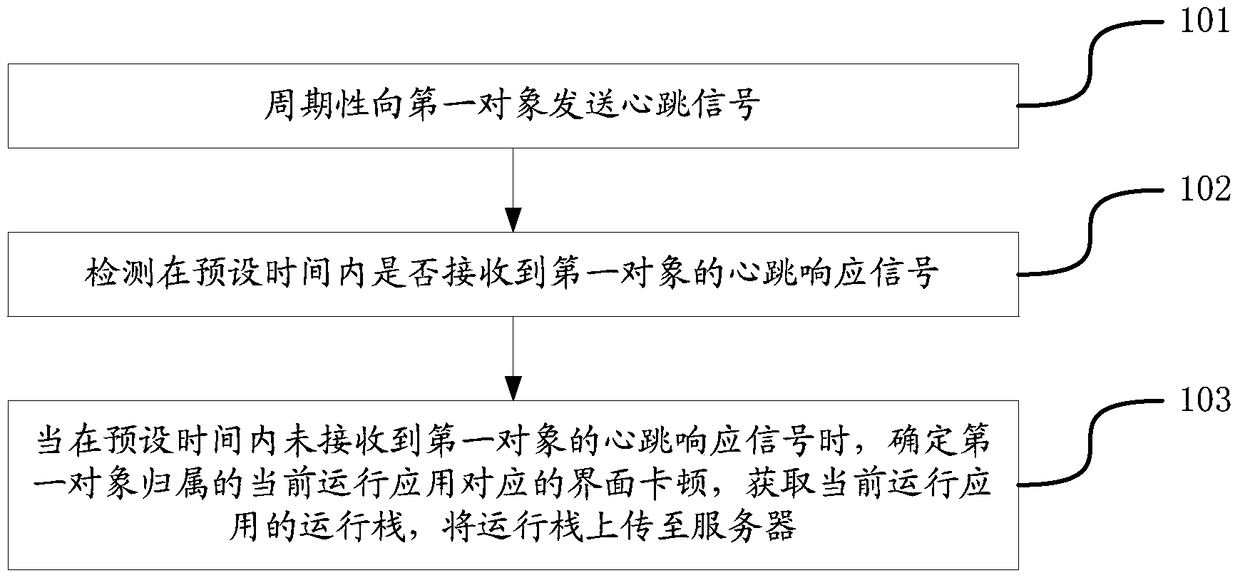
The invention relates to the technical field of grinding wheel machining, in particular to a preparation device for a ceramic bond of a ceramic diamond grinding wheel. The preparation device comprises a shell, a grinding disc and an annular groove; the grinding disc is arranged in the shell; a rotating shaft is fixedly arranged at an eccentric position of the top of the grinding disc; the annular groove is coaxially and fixedly arranged on the shell in a sleeving mode; an annular piston plate is arranged in the annular groove; a plurality of control mechanisms for driving the annular piston plate to reciprocate are fixedly arranged at the top of the annular piston plate; the control mechanisms penetrate through the annular groove, extend out of the annular groove and are finally rotationally connected with the rotating shaft; and a plurality of uniformly distributed vent holes are formed in the junction of the annular groove and the shell. According to the preparation device, the grinding disc, the rotating shaft, the annular piston plate and the control mechanisms are arranged, so that when the rotating shaft rotates, the grinding disc can be driven to rotate eccentrically to grind materials, the annular piston plate can be driven to reciprocate, the function of indirect air leakage is achieved in the reciprocating process of the annular piston plate, and the drying and grinding effects on the ceramic bond are improved.
Owner:南通尚东磨具有限公司
Solar power bank structure
InactiveCN104953632ANo need to consume resourcesFew transmission linesBatteries circuit arrangementsElectromagnetic wave systemElectric power systemEngineering
A solar power bank structure is disclosed. A power bank housing comprises a plurality of charging battery receiving slots in different specifications and at least one external connecting interface. After the external of the housing is provided with a solar reception plate for receiving solar energy, the solar energy is converted into working power and transmitted to the external connecting interface so as to be used by other devices. The work power can charge charging batteries of various types through the charging battery receiving slots without consuming any resources. If no light source is available, the power bank provides electric power to other devices through the charging batteries in the charging battery receiving slots, and can receive external electric power from the external connecting interface during charging. The external electric power after being converted by a working unit is transmitted to the charging battery receiving slots to charge the charging batteries of various types. The charging batteries can be taken out from the housing to serve as common household batteries. The structure is convenient and portable, and the use convenience of the power bank is improved.
Owner:吴铭远
User access method and device
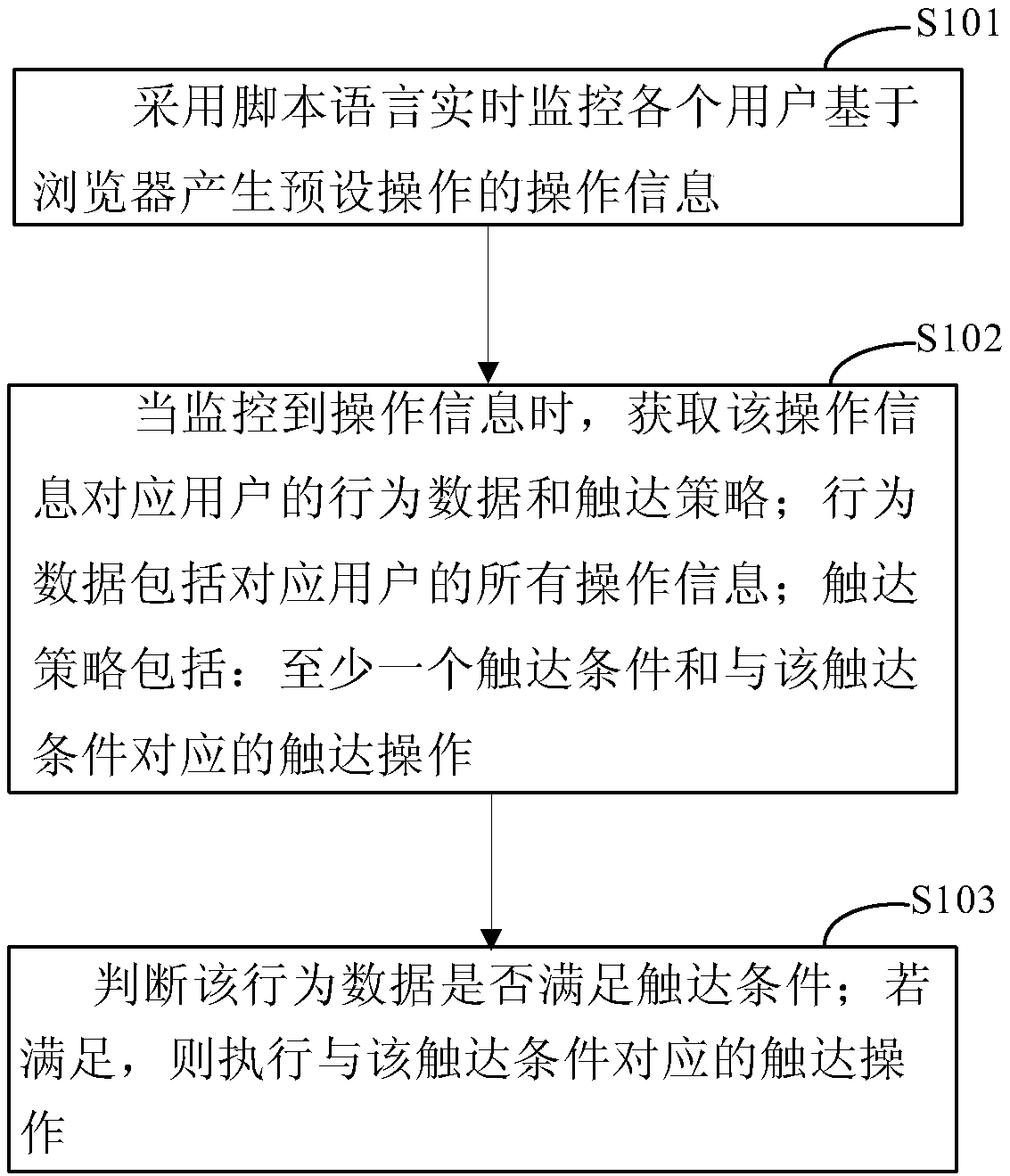
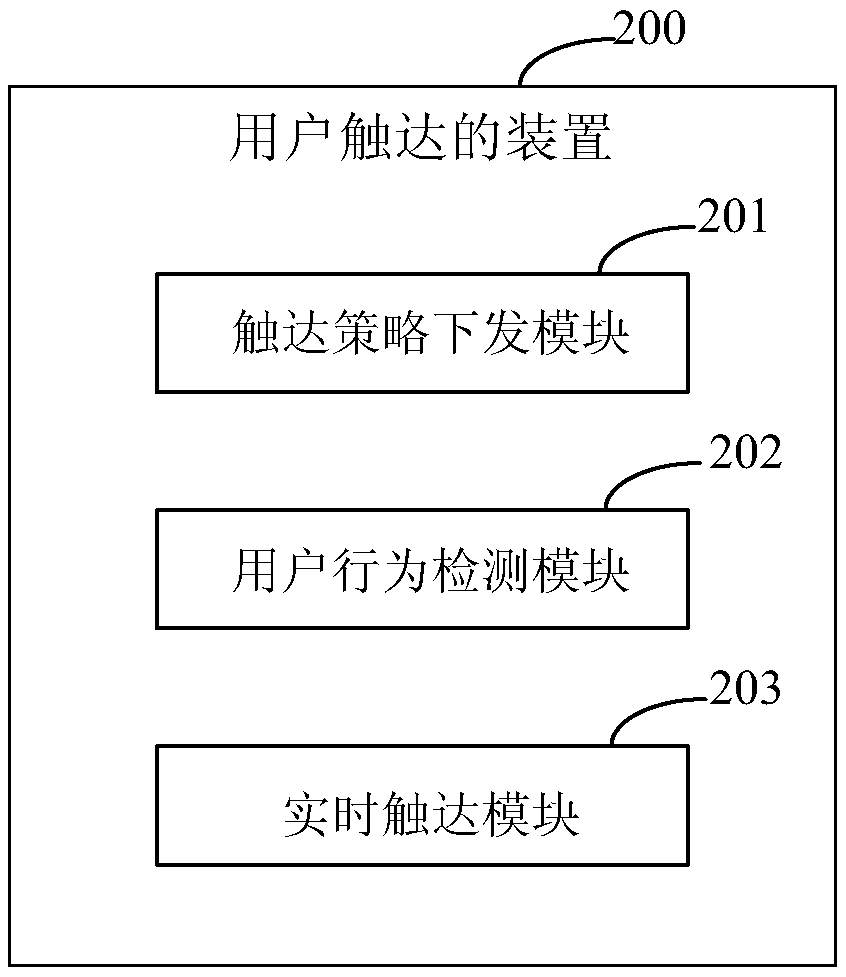
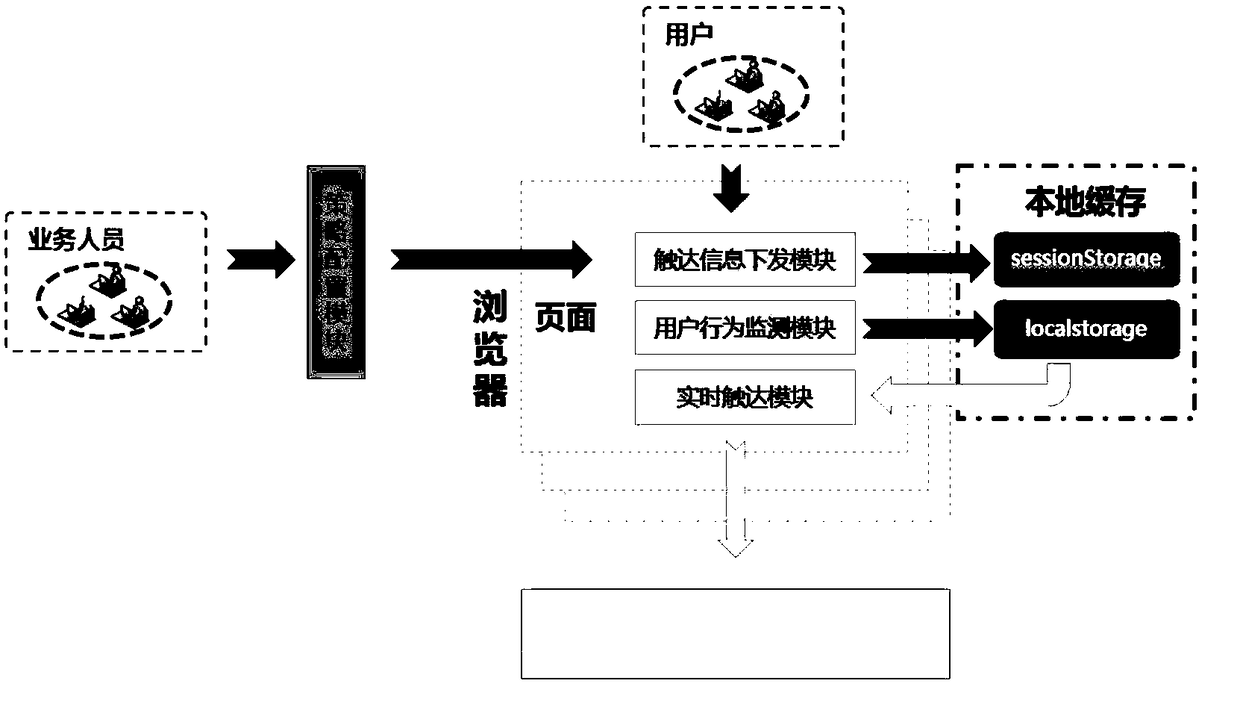
ActiveCN108933823ANo need to consume resourcesAvoid hysteresisTransmissionScripting languageAccess method
The invention discloses a user access method and device, and relates to the field of computer technologies. One specific embodiment of the method comprises the implementation of the following steps ata client: a script language is adopted to monitor operation information of each user for generating a preset operation based on a browser in real time; when the operation information is monitored, behavior data and an access strategy of the user corresponding to the operation information are obtained, wherein the behavior data includes all operation information of the corresponding user, and theaccess strategy includes at least one access condition and an access operation corresponding to the access condition; whether the behavior data meets the access condition or not is judged; and if so,the access operation corresponding to the access condition is executed. In the embodiment of the invention, the whole computing process of user access is carried out at the client without a need of consuming server resources; and the script language is adopted to monitor the operation information of each user, thereby being capable of calculating user behaviors in real time more comprehensively, avoiding the lag, and saving tedious steps and workload of a butt-joint interface.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Large fluidized bed system and device for drying and upgrading lignite
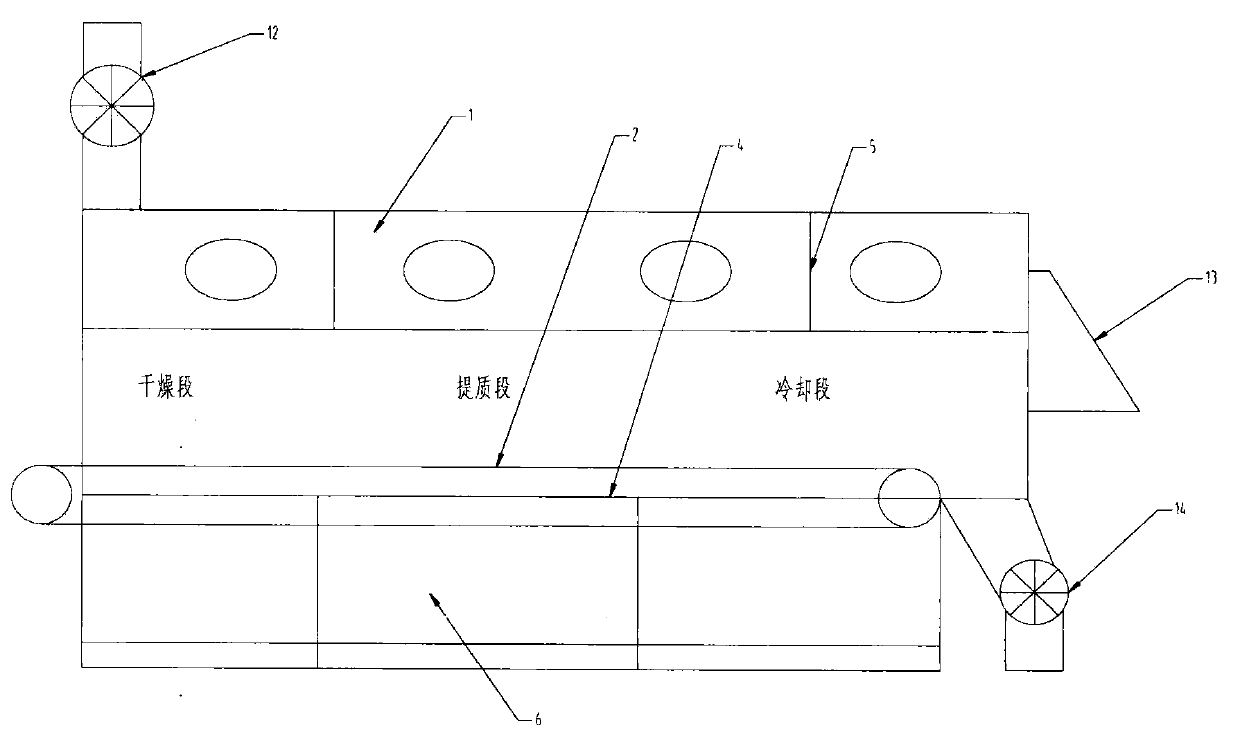
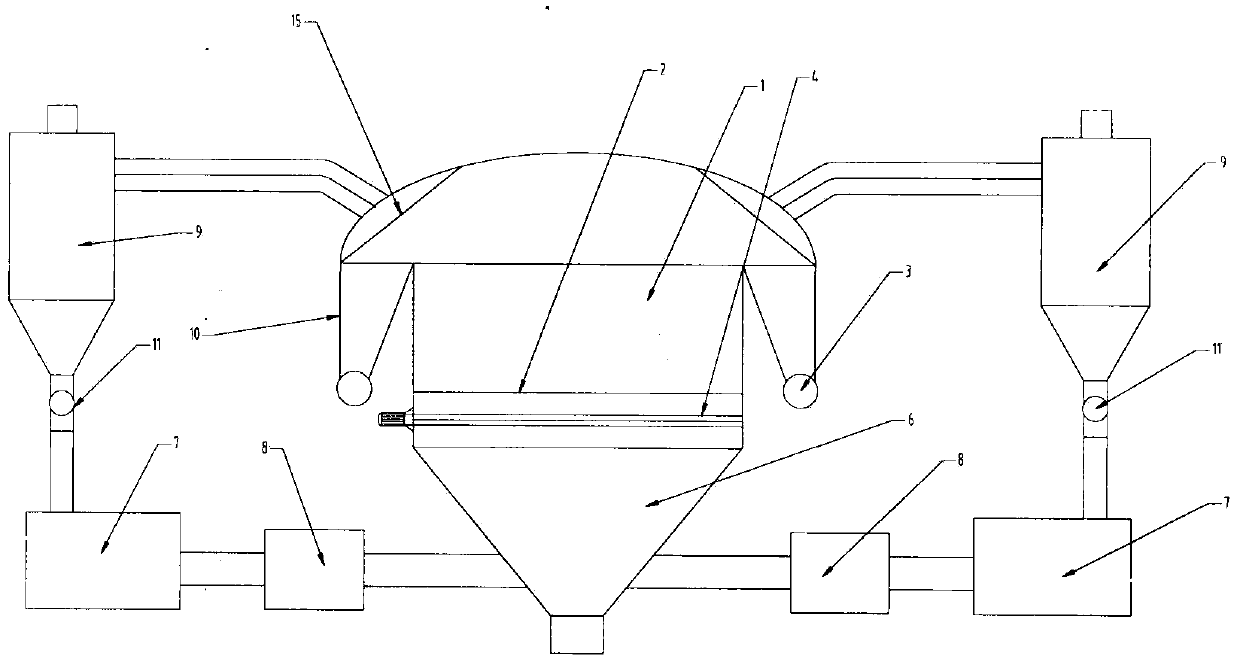
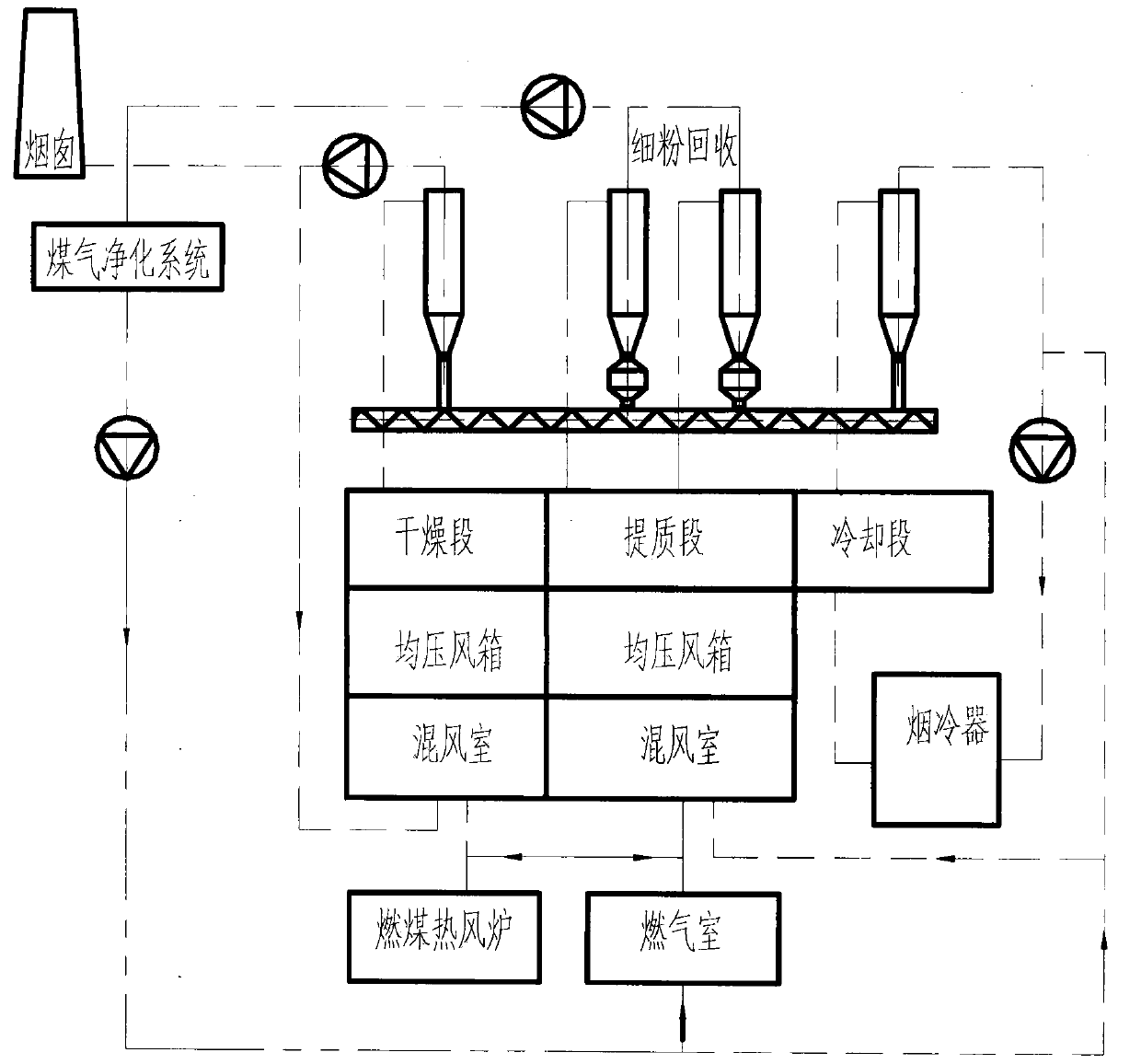
InactiveCN104180609AEnsure quality improvementMove fastDrying solid materials with heatDrying gas arrangementsFluidized bedEngineering
The invention relates to a fluidized bed system for grading, drying and upgrading lignite. The fluidized bed system comprises a fluidized bed, coal-burning hot air furnaces and a hot air recycling system, and the hot air recycling system hermetically connects the coal-burning hot air furnace with the fluidized bed. The fluidized bed system is characterized in that broken lignite entering the fluidized bed is divided into upgrading coal granules and fine coal powder, the fine coal powder is sent into the coal-burning hot air furnaces for burning to provide heat for the fluidized bed system, the fluidized bed system further comprises a lignite grading and upgrading system, and the upgrading coal granules are graded according to granular size in the fluidized bed under action of the lignite grading and upgrading system and subjected to upgrading of different degrees according to difference in granular size of the coal granules. By the fluidized bed system, industrialized grading, drying and upgrading of lignite can be realized, and utilization rate of lignite is increased.
Owner:赵建勋
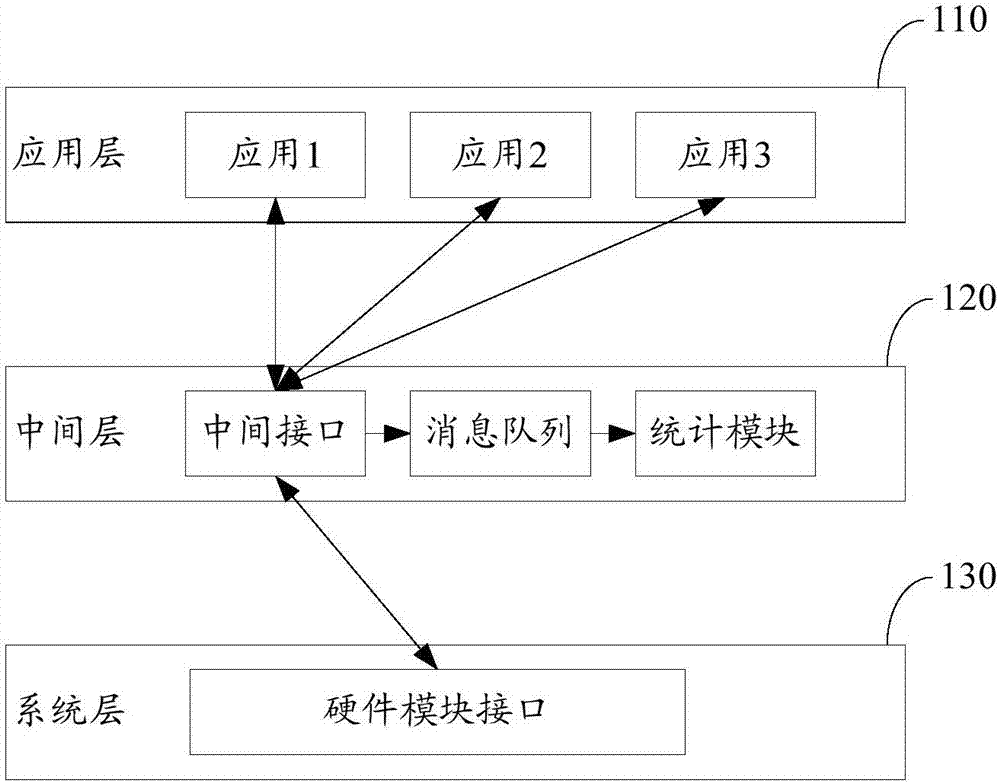
Information statistical method and device
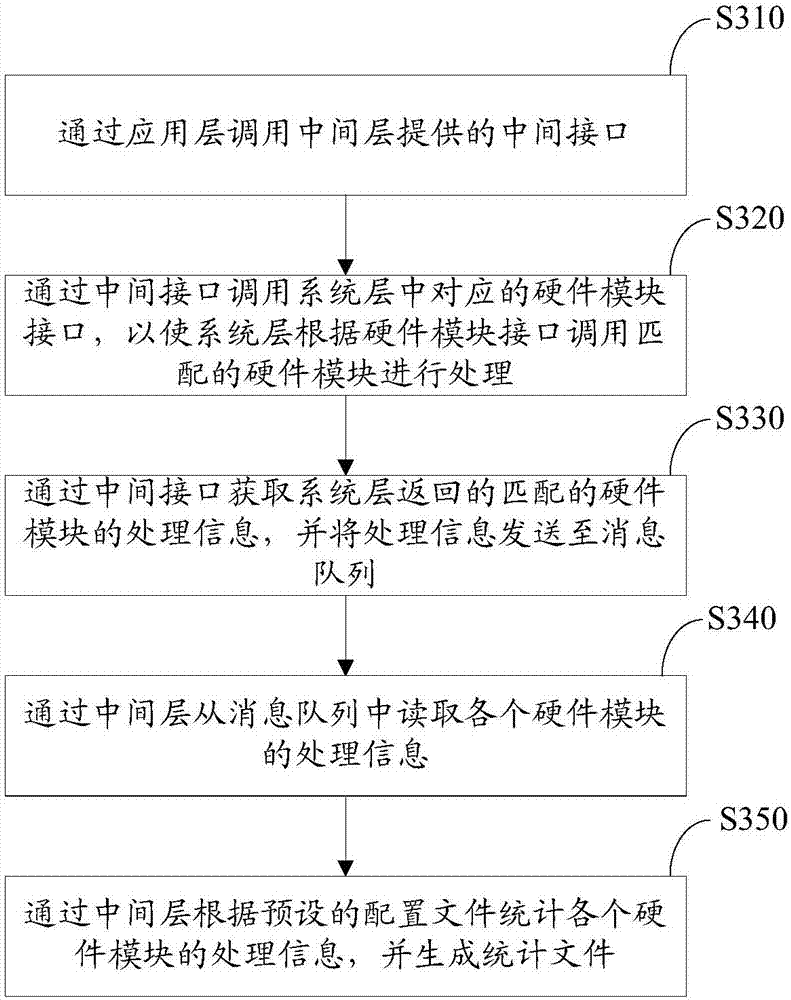
ActiveCN106919385AStatistical method is simpleNo need to consume resourcesSoftware designSpecific program execution arrangementsMessage queueComputer terminal
The invention relates to an information statistical method and device. The method comprises following steps: calling an intermediate interface provided by a middle layer through an application layer; calling a corresponding hardware module interface of a system layer through the intermediate interface so that the system layer calls matched hardware module to process according to the hardware module interface; obtaining processing information of the matched hardware module returned by the system layer through the intermediate interface and sending the processing information to a message queue; reading processing information of each hardware module from the message queue through the intermediate layer; performing statistics on the processing information of each hardware module according to a preset configuration file through the intermediate layer and generating a statistics file. By means of the above information statistical method and device, the use condition of each hardware module of payment terminals can be flexibly computed; the statistics method is simple and there is no need to consume a large number of resources for application development.
Owner:PAX COMP TECH SHENZHEN
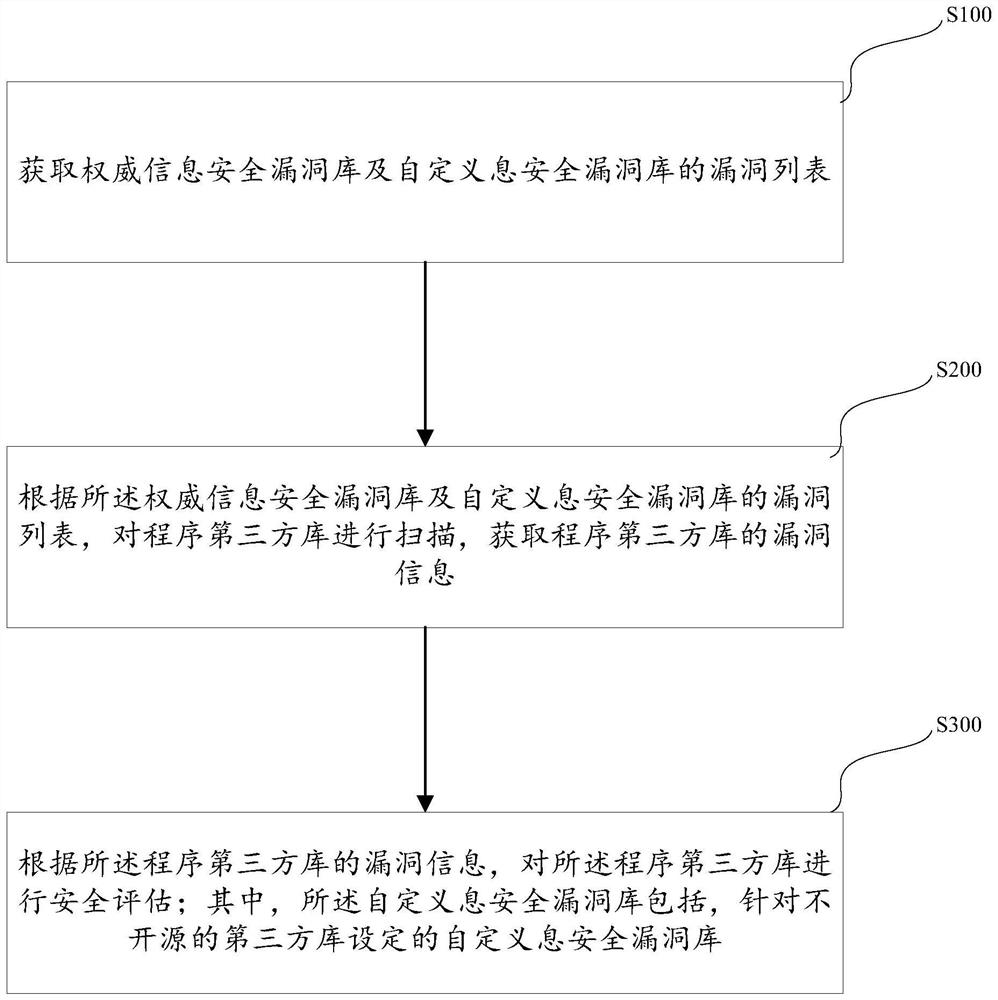
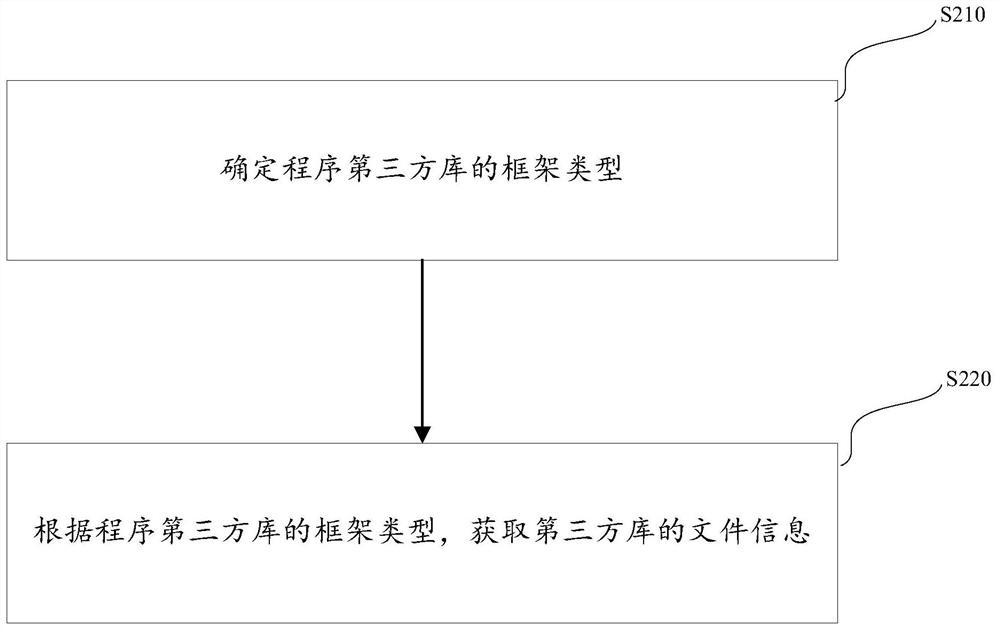
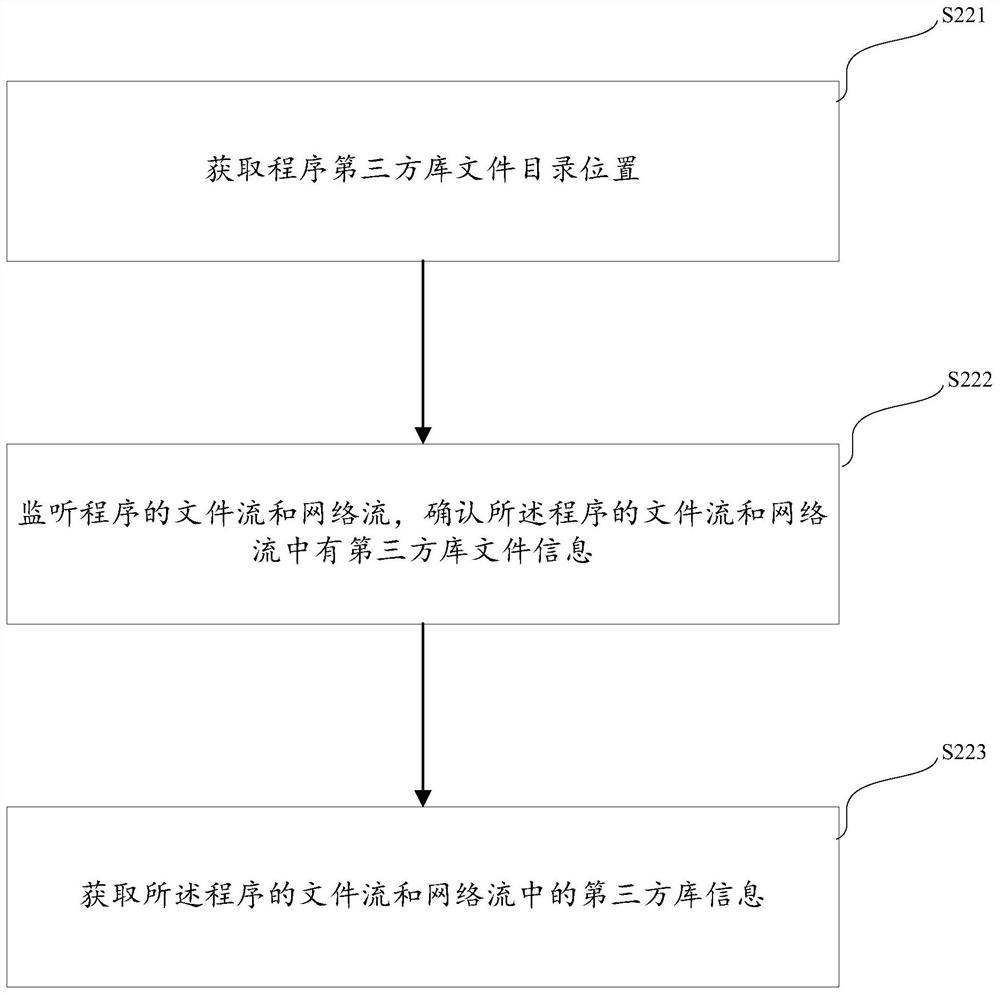
Method and system for dynamically detecting program third-party library and performing security assessment
ActiveCN111046386BImprove targetingEasy to set upPlatform integrity maintainanceThird partyInternet privacy
The invention provides a method for dynamically detecting a program third-party library and carrying out security evaluation. The method specifically comprises the following steps: obtaining vulnerability lists of an authority information security vulnerability library and a custom information security vulnerability library; scanning the program third-party library according to the authority information security vulnerability library and the vulnerability list of the custom information security vulnerability library to obtain vulnerability information of the program third-party library; performing security assessment on the program third-party library according to the vulnerability information of the program third-party library, wherein the custom information security vulnerability librarycomprises a custom information security vulnerability library set for a non-open-source third-party library. The pertinence of the vulnerability list can be enhanced through the vulnerability list obtained by the custom information security vulnerability library; meanwhile, an interface can be set at will in the vulnerability list of the custom information security vulnerability library, so thatthe method is combined with user behaviors, convenient to expand, good in expansibility and high in flexibility; and the detection efficiency of the third-party library security evaluation based on the file system software review is improved.
Owner:SECZONE TECH CO LTD
Cutting device and method for building materials used in construction site
InactiveCN108527680ANeat cutting edgeFast cutting speedWorking accessoriesStone-like material working toolsArchitectural engineeringWater pipe
The invention discloses a cutting device and method for building materials used in a construction site. The cutting device comprises a water collecting tank, a vertical plate I and a vertical plate II. The vertical plate II is arranged on the side, away from the vertical plate I, of the water collecting tank. The cutting device and method for the building materials used in the construction site has the beneficial effects that a pressuring machine, a water lance head, a water quantity valve and a water proof cover are arranged, so that the cutting edges of the building materials are more orderly, the cutting speed is accelerated, and the cutting efficiency is improved; a first filter plate and the water collecting plate are arranged, the dust produced by the building materials during cutting can be eliminated and collected, the health damage from the dust to workers is reduced, and the pollution of dust to the environment is reduced; a rolling device, a sliding device, a data interfaceand a controller are arranged, so that the pattern cutting process of the building materials is automatically completed, and the cutting efficiency is greatly improved; and a water pump, a water pumping opening, a water inlet pipe and a telescopic water pipe are arranged, so that the cutting tools of the building materials can be recycled without the need for consuming more resources.
Owner:GUANGXI JIAZHIBAO NETWORK TECH CO LTD
Three-layer phishing website detection system based on hybrid method
ActiveCN110784462BStrong representativeDiscovered in timeCharacter and pattern recognitionNeural architecturesWeb siteHybrid approach
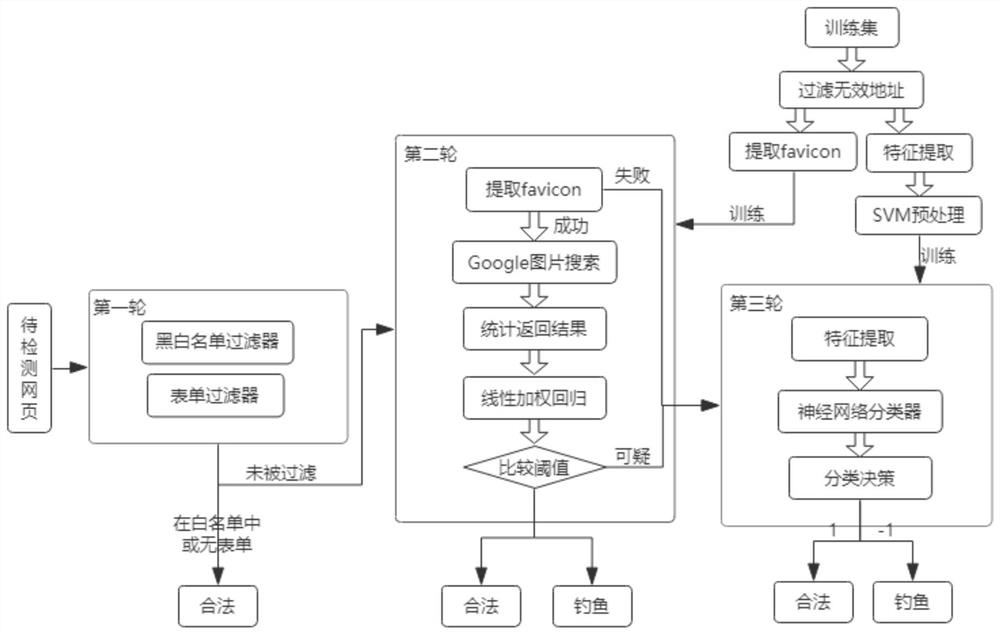
The invention discloses a three-layer phishing website detection system based on a hybrid method. The detection system is composed of three layers: a first layer of black and white list, a form filtering layer, a second layer of favicon detection layer and a third layer of machine learning detection layer; Layers of black and white lists and form filtering layers can detect known phishing websites in time and reduce the cost of detection. The second layer of favicon detection layer can identify the real identity of the website through faviocn to detect phishing websites, which is faster and does not need to consume too many resources. The third layer of machine learning detection layer can accurately identify the websites judged as suspicious by the second layer, and obtain more accurate judgment results. The three levels of detection not only ensure the accuracy of recognition results, but also reduce the detection time as much as possible.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Interface stuck processing method and device
Owner:广州方硅信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com