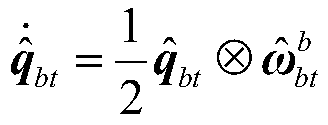Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31results about How to "Ensure safe execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Navigation apparatus and access method to map data therein
InactiveUS7171305B2Ensure safe executionAvoid failureInstruments for road network navigationRoad vehicles traffic controlAccess methodDisplay device
A navigation apparatus is provided for ensuring safe execution of a navigation function even when a vehicle travels high altitude areas. The navigation apparatus has a function of searching for a route to a destination, and comprises the following structure: a memory device 30 for storing map data or the like, a data memory 70 for being capable of storing part of the map data or the like stored in the memory device 30, a position detector 500 for detecting positional information on a vehicle position, a controller 80 for causing the map data stored in the memory device 30 to be stored in a backup memory area 74 of the data memory 70 when the vehicle reaches a predetermined altitude based on the positional information, and a display controller 50 for displaying the map data read from the data memory 70 on a display device 51.
Owner:ALPINE ELECTRONICS INC
Technique for dynamically restricting thread concurrency without rewriting thread code
ActiveUS8245207B1Easy to scaleReduce the amount requiredSoftware engineeringDigital computer detailsParallel computingWorkload
Owner:NETWORK APPLIANCE INC
Safe communication method and device
ActiveCN105307163AEnsure safe executionPrevent eavesdroppingSecurity arrangementSecure communicationSecure channel
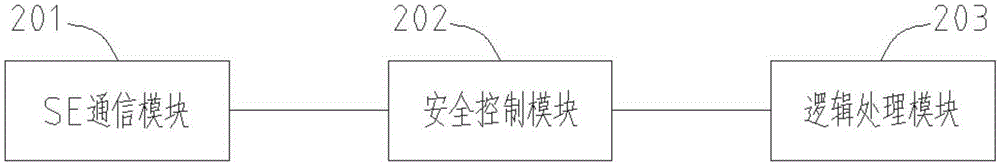
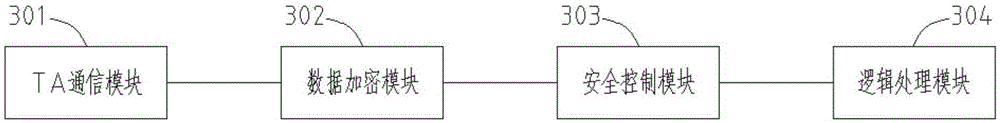
The invention provides a safe communication method and device. The method comprises steps of performing basic information authentication, external authentication and secondary authentication on a security chip and a trusted application, so as to establish a connection between the security chip and the trusted application; performing basic information authentication, external authentication and secondary authentication on the trusted application and a user application, so as to establish a connection between the trusted application and the user application; and establishing a logic connection between the security chip and the user application. A safe channel is established before business communication, and all data communicated in the safe channel is encrypted and transmitted, so that the data in the link is not transparent any longer. The method can effectively prevent interception, guarantees the business to be executed safely, needs no external equipment, and increases user experience.
Owner:HENGBAO
Block level encryption method in cloud storage and multi-granularity deduplication method
ActiveCN106603561ADe-duplicationReduce overheadDigital data protectionTransmissionGranularityCloud storage
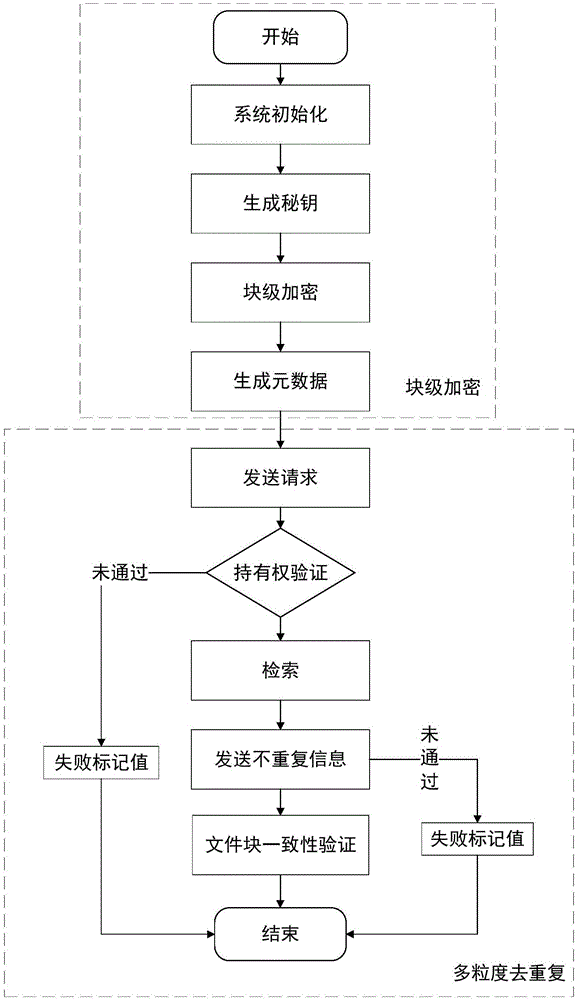
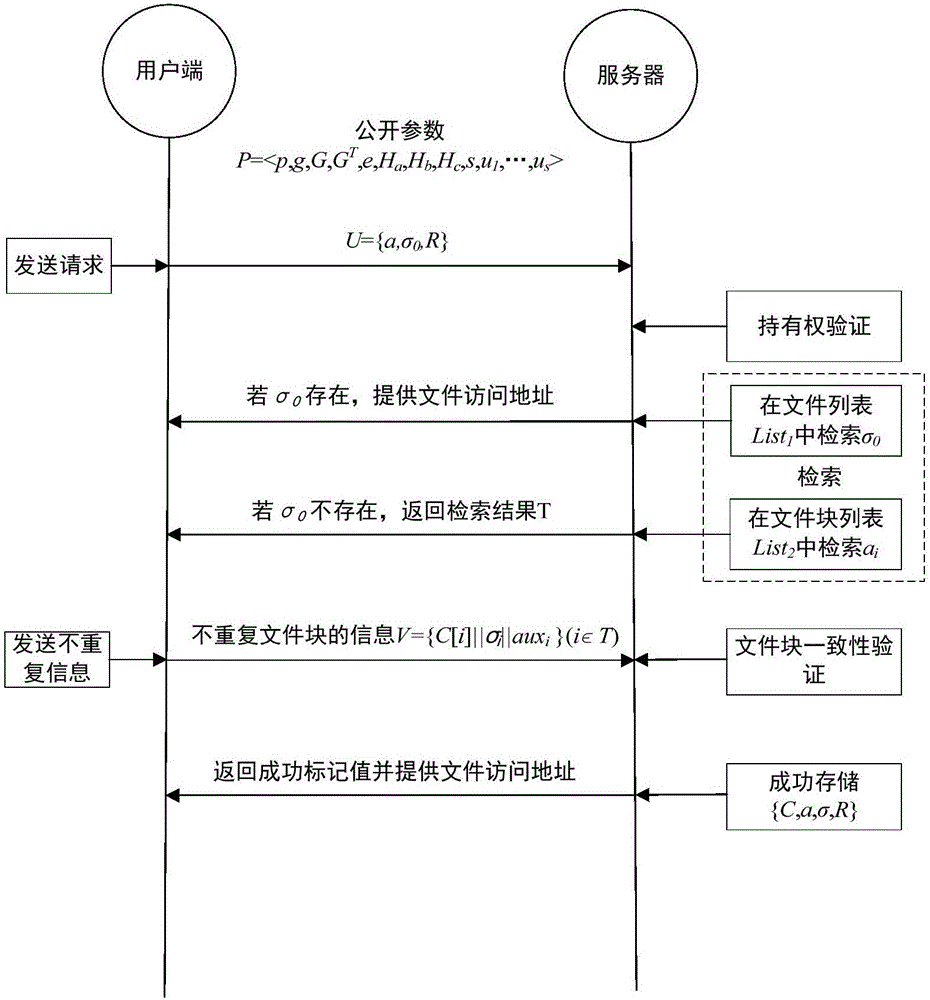
The invention discloses a block level encryption method in cloud storage and a multi-granularity deduplication method, belonging to the technical field of network security. The block level encryption method comprises the steps that a system public parameter is set, a user end calculates a key and encryptes a file, and metadata is calculated; and the user end selects a part of metadata as a deduplication request and sends the request to a server, the server verifies the file ownership of a user according to the request and retrieves a file in a storage list, if the file exists, access is provided directly, otherwise the server asks the user end to upload non-repeat information, the server carries out consistency verification on received data, and the server allows the user end to access the file if the verification is passed. The method is suitable for the cloud storage with security and efficiency of data and aims to safely and reliably carry out deduplication on the user data, and the data storage efficiency is high.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Indoor wall-buried wire non-destructive detection instrument
InactiveCN101539637AEnsure safe executionExcellent usabilityElectric/magnetic detectionAcoustic wave reradiationNon destructiveMicrocontroller
The invention relates to an indoor wall-buried wire non-destructive detection instrument which comprises a sensor module (1), a multistage amplifying circuit module (2), a singlechip module (3) and a display module (4), wherein the output terminal of the sensor module (1) is connected with the input terminal of the multistage amplifying circuit module (2), the output terminal of the multistage amplifying circuit module (2) is connected with the input terminal of the singlechip module (3), and the output terminal of the singlechip module (3) is connected with the display module (4). The indoor wall-buried wire non-destructive detection instrument adopts a non-destructive detection technology, does not destruct a wall surface, has low cost, high sensitivity, remarkable strength variance when closing to a live wire, accurate positioning, small error between an indicative position and a practical wire position in a range from -0.5cm to 0.5cm, easiness and simplicity, maneuverability without any professional knowledge, simple structure, firmness, durability, safety, reliability, no ray release, no ultrasonic wave release, and the like and does not need to mount an instrument on the wire, thereby being convenient and practical.
Owner:GUANGDONG UNIV OF TECH
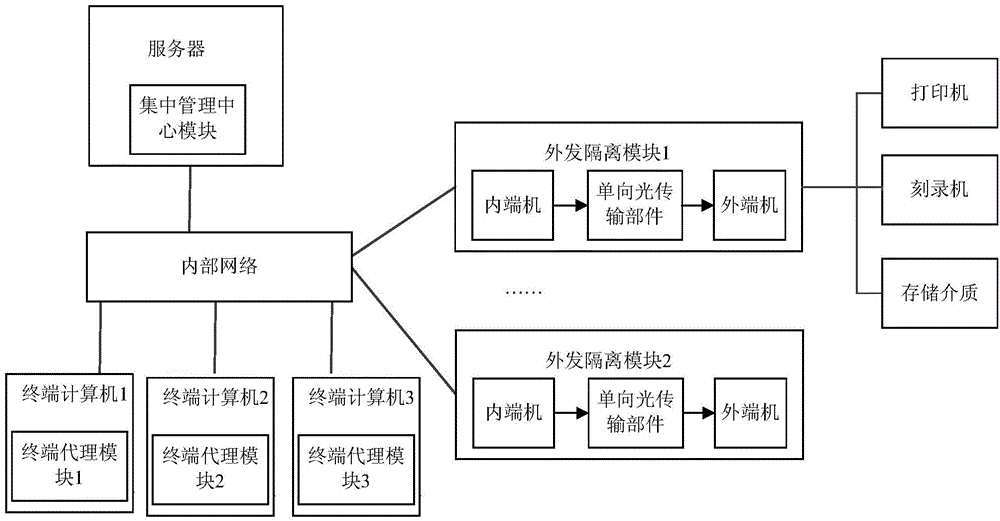
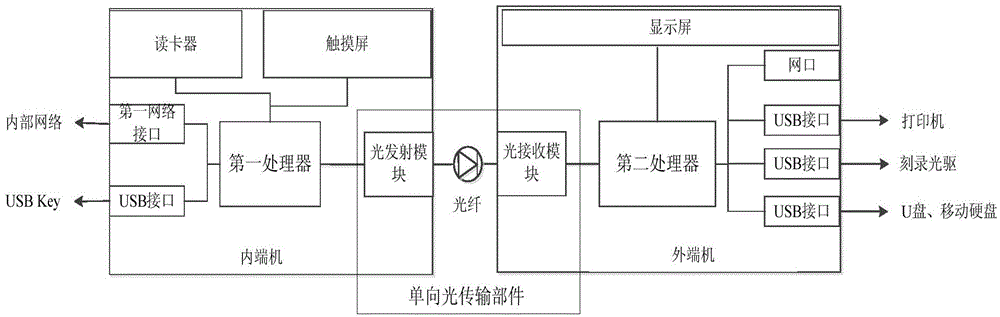
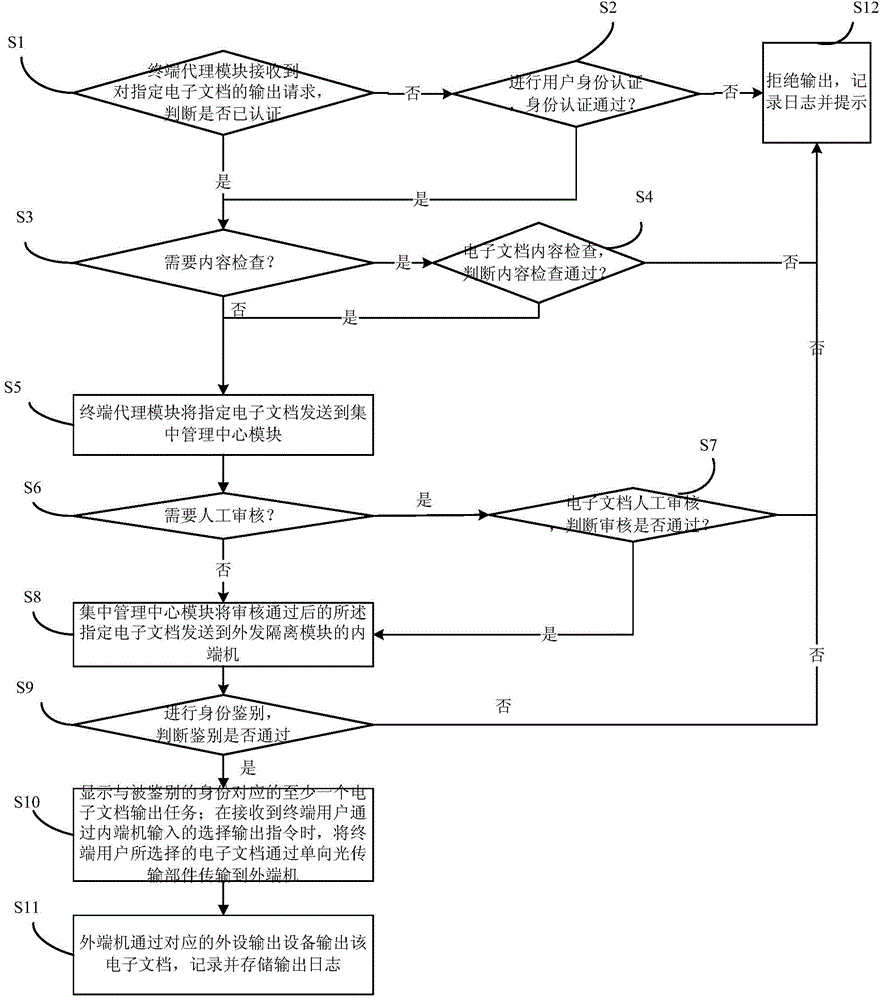
Unidirectional transmission based electronic document output management and control system and method
ActiveCN104579626AEffective isolationAvoid accessDigital data protectionPlatform integrity maintainanceElectronic documentControl system
The invention provides a unidirectional transmission based electronic document output management and control system and method. The system comprises a terminal proxy module, a centralized management center module and an outgoing isolation module, wherein both-way communication is performed between the terminal proxy module and the centralized management center module and between the centralized management center module and the outgoing isolation module. The system has the following advantages: (1) through the unidirectional transmission technology, an in-house network is connected with peripheral output device through the outgoing isolation module, so that unidirectional output of an electronic document can be ensured, and effective isolation between peripheral output risk devices such as a printer and the sensitive in-house network is realized; (2) safe identity authentication ensures credibility of an outgoing source of the electronic document, security check ensures content controllability and manageability of the outgoing electronic document, and execution of a security policy ensures that only authorized electronic document can be sent outward; (3) multiple output modes such as printing output, optical disk burning output, storage medium output and the like are supported, and the system can be widely applied to various security output occasions of the electronic document.
Owner:ZHONGTIE XINAN BEIJING INFORMATION SECURITY TECH
Internet-based communication method and communication terminal
InactiveCN102932565AReduce use costNo forwarding delayInterconnection arrangementsData switching networksThird partyAddress book
The invention provides an internet-based communication method and an internet-based communication terminal and aims to solve the problems of forward time delay and complexity in communication process. The method comprises the following steps of: generating a first number which is used for uniquely identifying each terminal for the terminal, and generating a second number which is used for communicating the terminal with other terminals; acquiring an address book by two communicating terminals from each other, and storing the address book which contains opposite information; searching a network link address and a port number, which are matched with the second number of a called terminal in the address book by a calling terminal, and calling the called terminal through the network link address and the port number, which are searched; after the called terminal is called, connecting the called terminal and the calling terminal according to the network link address and the port number of the calling terminal; and communicating the calling terminal and the called terminal. Third-party equipment is not required to participate in the communication process, and the communication process is self-completed by the terminals, so the forward time delay is avoided, and the communication process is simplified.
Owner:DATANG MOBILE COMM EQUIP CO LTD
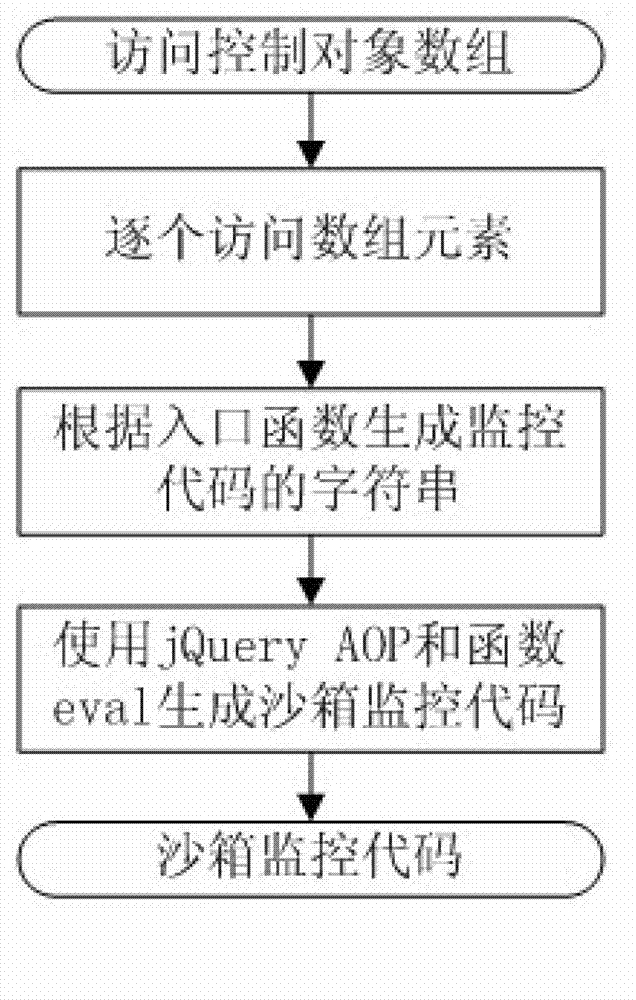
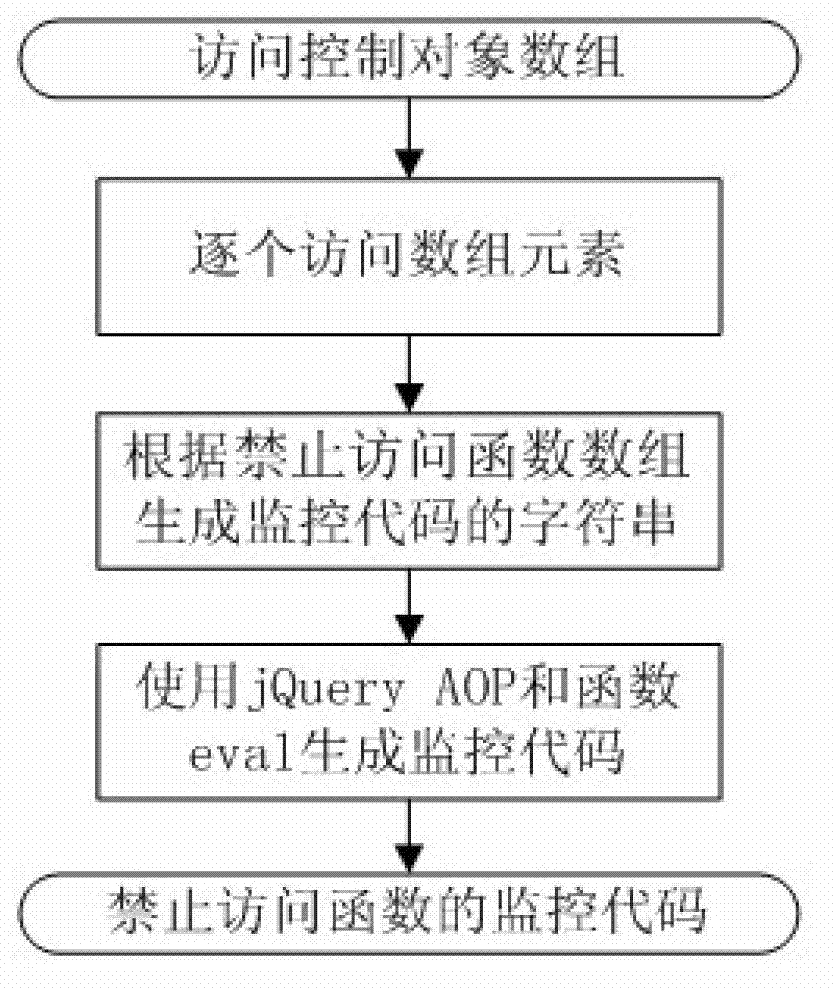
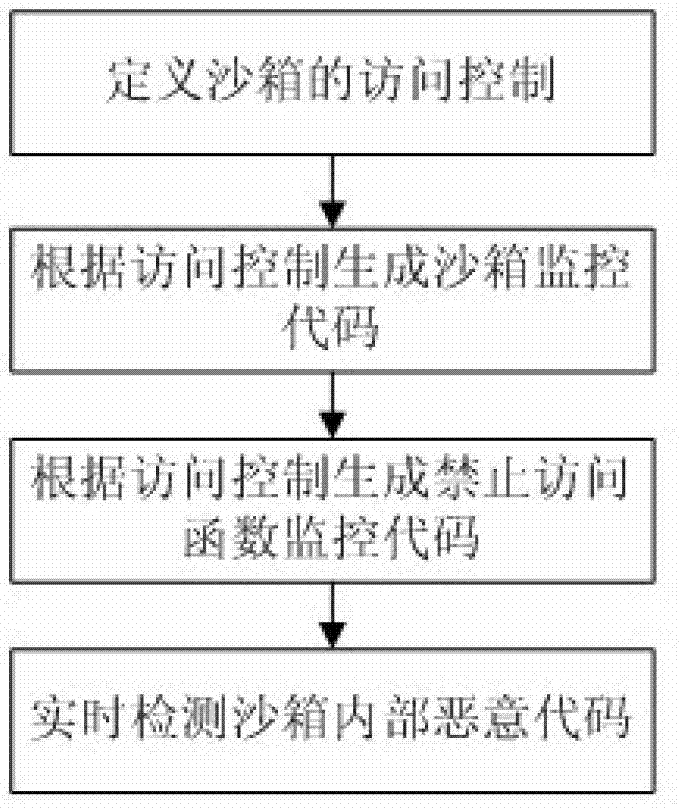
Method for realizing lightweight class JavaScript sandbox
ActiveCN102930203AEasy to implementEasy to masterPlatform integrity maintainanceSoftware engineeringProgram behavior
The invention discloses a method for realizing a lightweight class JavaScript sandbox. The method comprises the following steps of: S10, defining access control inside the sandbox; S11, automatically generating a sandbox monitoring code according to the defined access control; S12, automatically generating a monitoring code for stopping an access function according to the defined access control; and S13, detecting a malicious code inside the sandbox in real time, and stopping calling a dangerous function. The method for realizing the lightweight class JavaScript sandbox provided by the invention is simple and effective; a programmer can conveniently grasp and operate the method for realizing the lightweight class JavaScript sandbox; the JavaScript program code is safely executed inside the sandbox; and no dangerous program behavior is generated.
Owner:ZHEJIANG UNIV CITY COLLEGE
Automatic driving lane changing track optimization model, lane changing track optimization method and system
ActiveCN110936958AEnsure safe executionEasy to adjustInternal combustion piston enginesControl devicesInformation processingSimulation
Owner:RES INST OF HIGHWAY MINIST OF TRANSPORT +2
A method and system for extending high-performance encryption and decryption computing capability
ActiveCN109190407AEnsure safe executionDigital data protectionArchitecture with single central processing unitComputer hardwareEncryption
The invention discloses a method and system for extending high-performance encryption and decryption computing capability. The method comprises the following steps: a main processor transmits data tobe encrypted and decrypted and program calls of encryption and decryption operations to an FPGA main controller through system communication; the FPGA master resolves the program calls from the main processor and decomposes them into a series of sub-processes. The FPGA master sends the corresponding command call and related data to the security chip. The security chip generates the secondary key required for the current encryption and decryption operation according to the root key stored in the FPGA master and the input data from the FPGA master, and feeds the operation result back to the FPGAmaster. According to the secondary key fed back by the security chip, the FPGA master calls the high-performance encryption and decryption circuit to complete the corresponding encryption and decryption operation, and sends the final operation result to the main processor. The invention adds a high-performance encryption and decryption circuit into the FPGA main controller to ensure the safe execution of the high-performance encryption and decryption operation.
Owner:网御安全技术(深圳)有限公司
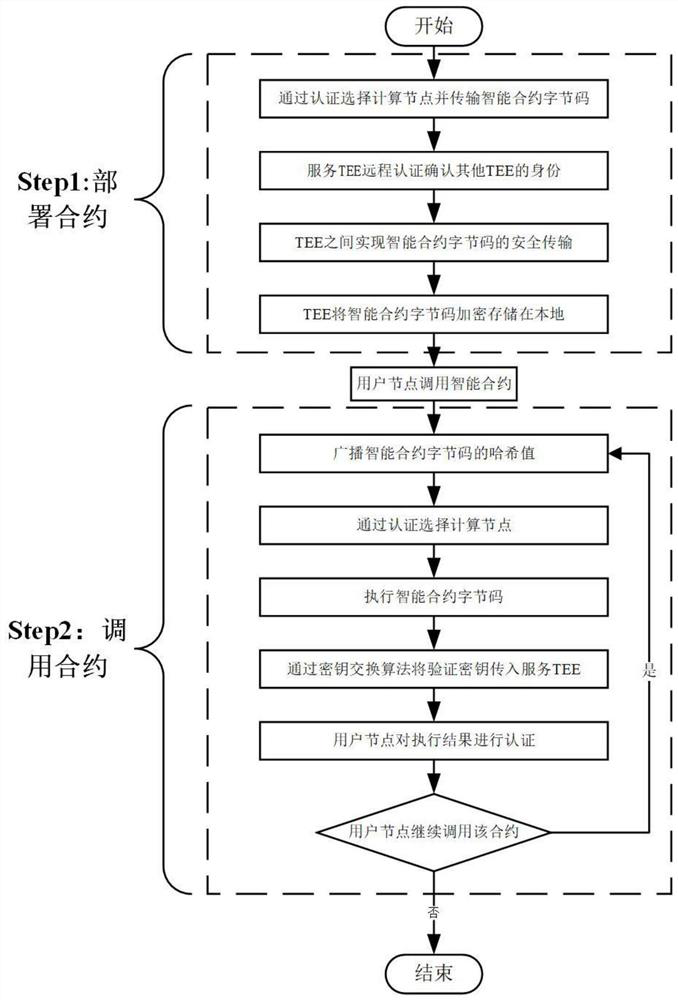
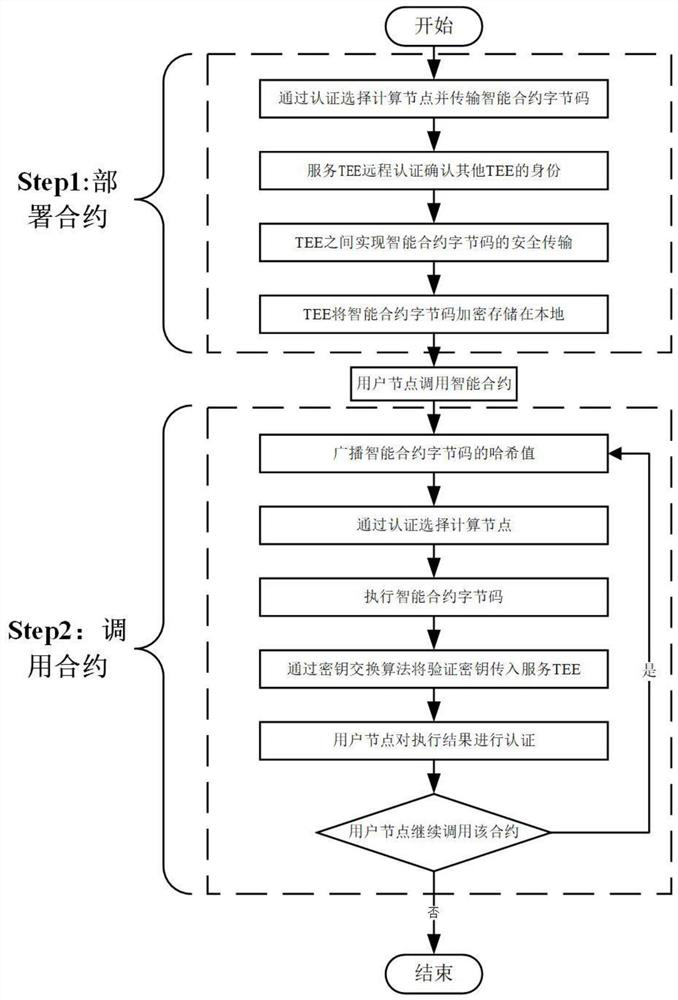
Encrypted smart contract privacy protection method based on trusted execution environment
ActiveCN113726733APrivacy protectionEnsure safe executionUser identity/authority verificationDigital data protectionKey exchangeSecure transmission
The invention discloses an intelligent contract privacy protection method based on a trusted execution environment and encryption. The method comprises two steps of contract deployment and contract calling. The method comprises the following steps: according to the confidential and non-tampering characteristics of a trusted execution environment, completing encryption deployment of an intelligent contract byte code through the trusted execution environment, confirming whether identities of the trusted execution environments on different computing nodes are legal or not through an authentication center, and realizing the safe transmission of the byte code of the intelligent contract between two legal trusted execution environments; performing the execution of the byte code of the intelligent contract in the trusted execution environment, realizing the secure transmission of a verification key between the user node and the trusted execution environment through a key exchange algorithm, enabling the trusted execution environment to use the verification key to sign an execution result, and enabling the user node to ensure the correctness of contract execution through the signature. According to the scheme, the problems that the privacy of the smart contract code is leaked and the identity of the TEE carried by the computing node is illegal in the previous scheme are solved.
Owner:SOUTHEAST UNIV
Microwave ablation needle provided with water cooling sleeve tube and applied under bronchofiberscope
PendingCN109247984AImprove puncture strengthExcellent water cooling cycle designSurgical needlesEndoscopesEngineeringMicrowave
The invention discloses a microwave ablation needle provided with a water cooling sleeve tube and applied under a bronchofiberscope. The microwave ablation needle comprises a handle, a sheathing canal, a guide wire and a control mechanism. The handle is provided with a water injecting guide tube and a water drain guide tube. The guide wire comprises a cable, an ablation electrode, a water coolingguide tube, a sealing part, a syringe needle and an inner sleeve. A backflow opening is formed in the front end of the water cooling guide tube, a water injecting cavity and a water drain cavity are formed in an inner cavity, and the ablation electrode and the syringe needle are arranged at the front end of the cable. The microwave ablation needle provided with the water cooling sleeve tube and applied under the bronchofiberscope can achieve needle insertion and ablation at a controllable distance in a channel of the bronchofiberscope. The microwave ablation needle has excellent water coolingcirculating design, the sealing property and supporting performance in the microwave ablation needle are considered from multiple aspects, and it is guaranteed that microwave treatment emitting high heat can be safely executed in the body of a patient.
Owner:NANJING ECO MICROWAVE SYST
Distributed power supply comprehensive analysis and safety management and control system
PendingCN114372594ARealize power supply analysisRealize functionCircuit arrangementsTechnology managementControl systemGraphical query
The invention provides a distributed power supply comprehensive analysis and security management and control system. A distributed power supply data processing module is used for acquiring distributed power supply information; the distributed power supply equipment management module is used for providing a distributed power supply equipment adding, deleting, modifying and checking interface for a user; the distributed power supply equipment query statistics module is used for configuring an equipment tree query interface, an equipment account attribute query interface and a graphic query interface; the distributed power supply maintenance management module is used for providing a management interface for compiling annual, monthly and weekly maintenance plans, displaying the maintenance plans by using a Gantt chart, and providing a maintenance plan time adjustment operation interface; pre-balancing, repeated power failure analysis, risk analysis and safety early warning functions can be performed; the distributed power supply data analysis display module is used for displaying system operation information; the system realizes the functions of safety early warning and reminding of maintenance work including the distributed power supply, power supply analysis of the distributed power supply, safety management and control and the like, and guarantees the personal safety of maintenance personnel.
Owner:YANTAI POWER SUPPLY COMPANY OF STATE GRID SHANDONG ELECTRIC POWER +1
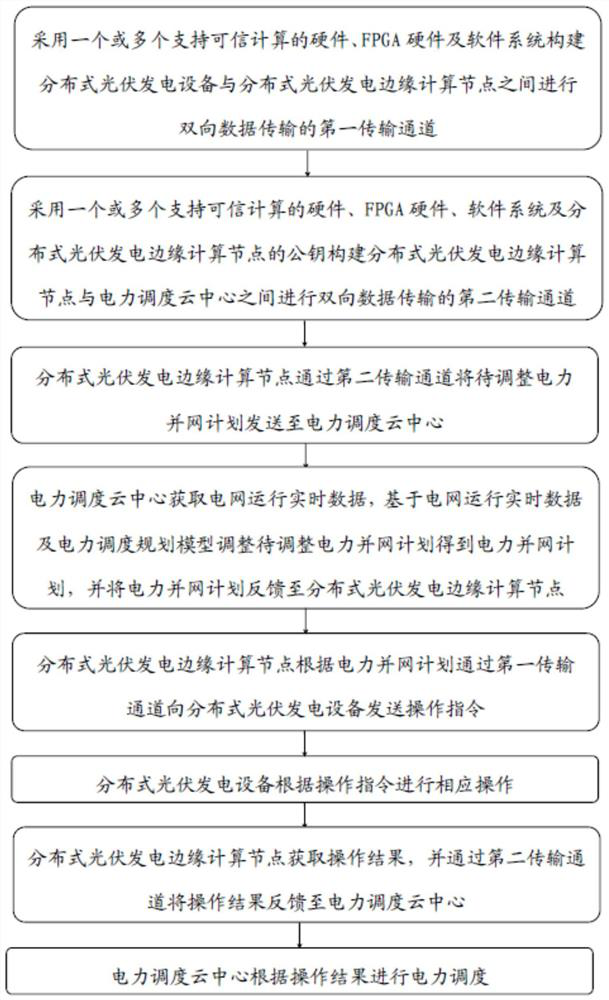
Distributed photovoltaic power generation power grid-connected system, method and equipment based on trusted computing, and medium
ActiveCN113792934AGuaranteed safe operationAccurate responseForecastingSingle network parallel feeding arrangementsSoftware systemEdge computing
The invention discloses a distributed photovoltaic power generation power grid-connected system and method based on trusted computing. The system comprises distributed photovoltaic power generation equipment, distributed photovoltaic power generation edge computing nodes and a power dispatching cloud center, wherein the distributed photovoltaic power generation equipment comprises a power generation device and a grid connection device; the distributed photovoltaic power generation edge computing nodes comprise a hardware system and a software system, the hardware system comprises hardware supporting trusted computing, FPGA hardware and data network transmission hardware, and the software system is constructed based on a container technology; the power dispatching cloud center is constructed based on cloud infrastructure; and the distributed photovoltaic power generation edge computing nodes perform data transmission with the distributed photovoltaic power generation equipment and the power dispatching cloud center through a first transmission channel and a second transmission channel respectively. By arranging the edge computing node, safe and reliable data exchange can be ensured, and the photovoltaic power generation equipment is controlled to timely and accurately respond to an instruction of the power dispatching cloud center to perform operations such as grid connection, power generation output increase and decrease and cut-out.
Owner:SHANDONG INSPUR SCI RES INST CO LTD
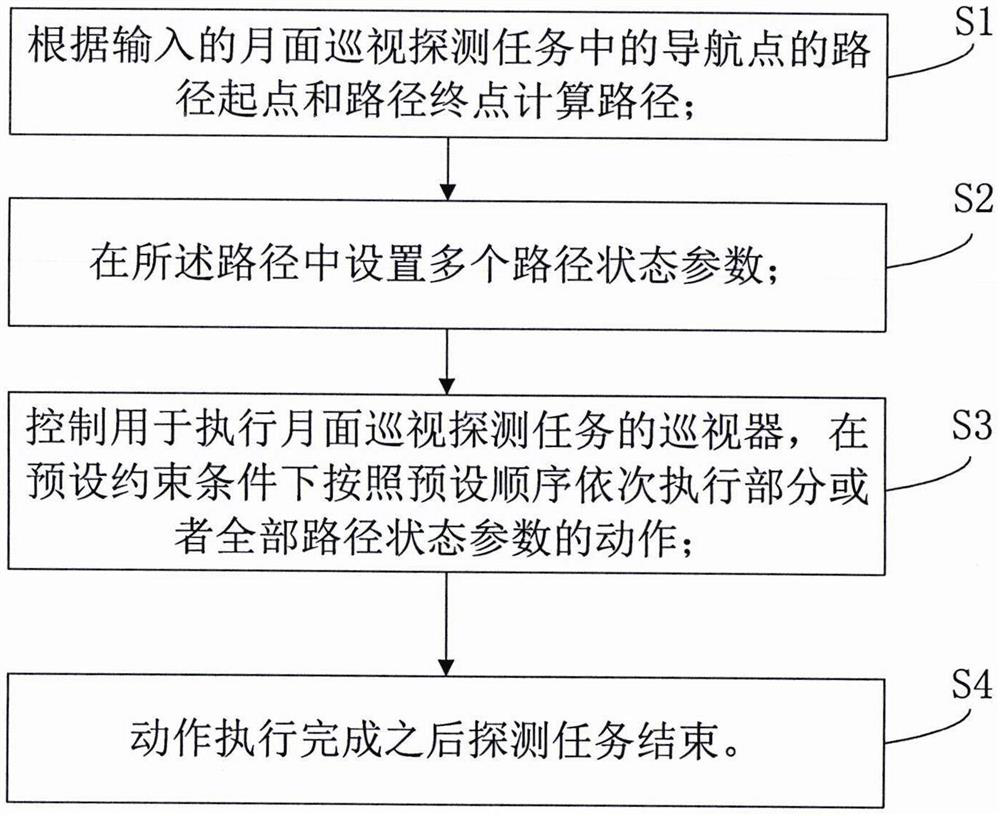
Planning method and system for lunar surface inspection and detection task
PendingCN114111761AIncrease flexibilityImprove practicalityNavigation by astronomical meansTerrainSimulation
The invention discloses a method and a system for planning a lunar surface inspection and detection task, and relates to the field of lunar surface detection. The method comprises the following steps: calculating a path according to a path starting point and a path ending point of a navigation point in an input lunar surface patrol detection task, setting a plurality of path state parameters in the path, and controlling a patrol device for executing the lunar surface patrol detection task, according to the method, actions of partial or all path state parameters are executed in sequence according to a preset sequence under a preset constraint condition, a detection task is finished after the actions are executed, and when a specific planning problem is described, lunar surface patrol task planning can be realized only by appointing a detection point without determining an action sequence in an intermediate process, so that the method is simple and convenient. The method has good flexibility and practicability, can cope with a terrain environment with complex constraint, can gradually perceive the surrounding environment in the detection process, and selects a detection target and an inspection route.
Owner:BEIJING AEROSPACE CONTROL CENT
An electronic document output control system and method based on one-way transmission
ActiveCN104579626BEffective isolationAvoid accessDigital data protectionPlatform integrity maintainanceTransmission technologyOutput device
The invention provides an electronic document output control system and method based on one-way transmission. The system includes: a terminal agent module, a centralized management center module, and an outgoing isolation module. The terminal agent module communicates with the centralized management center module in two directions; the centralized management center module Two-way communication with the outgoing isolation module; the advantages are: (1) Through the one-way transmission technology, the internal network is connected to the peripheral output device through the outgoing isolation module, ensuring the one-way output of electronic documents, and realizing the output of peripheral devices such as printers Effective isolation from sensitive internal networks; (2) Ensure the credibility of the outgoing source of electronic documents through secure identity authentication, ensure that the content of outgoing electronic documents is manageable and controllable through security checks, and ensure that only authorization is granted through the implementation of security policies (3) It supports multiple output methods such as print output, CD burning output, and storage medium output, and can be widely used in various electronic document security output occasions.
Owner:ZHONGTIE XINAN BEIJING INFORMATION SECURITY TECH
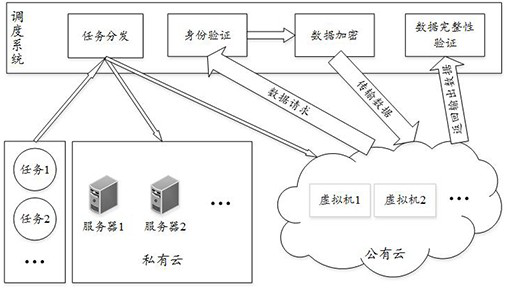
Hybrid cloud security scheduling method and hybrid cloud security scheduling system
The present invention provides a hybrid cloud security scheduling method, comprising: after obtaining the task request information sent by the user, based on the task request information, judging to assign the task to the target private cloud server or the target public cloud virtual machine; When the task is assigned to the target public cloud virtual machine, the task performed by the target public cloud virtual machine is authenticated; after the authentication of the task is passed, the input data requested by the task is encrypted, and the encrypted data is transmitted To the task; receive the output data transmitted by the task, and verify the integrity of the output data transmitted by the task, and feed back the output data to the user when the completion verification is passed. Through the technical solution of the present invention, it is possible to optimize the use efficiency of hybrid cloud resources on the premise of satisfying the security of task execution.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Lane-changing trajectory optimization method and system for automatic driving
ActiveCN110936958BEnsure safe executionEasy to adjustInternal combustion piston enginesDesign optimisation/simulationInformation processingSimulation
Owner:RES INST OF HIGHWAY MINIST OF TRANSPORT +2
A lightweight javascript sandbox implementation method
ActiveCN102930203BEasy to implementEasy to masterPlatform integrity maintainanceSoftware engineeringMedia access control
The invention discloses a method for realizing a lightweight class JavaScript sandbox. The method comprises the following steps of: S10, defining access control inside the sandbox; S11, automatically generating a sandbox monitoring code according to the defined access control; S12, automatically generating a monitoring code for stopping an access function according to the defined access control; and S13, detecting a malicious code inside the sandbox in real time, and stopping calling a dangerous function. The method for realizing the lightweight class JavaScript sandbox provided by the invention is simple and effective; a programmer can conveniently grasp and operate the method for realizing the lightweight class JavaScript sandbox; the JavaScript program code is safely executed inside the sandbox; and no dangerous program behavior is generated.
Owner:ZHEJIANG UNIV CITY COLLEGE
Power-frequency feeble-current electromagnetic signal sensor of non-current transformer type
InactiveCN101539636ALow costHigh sensitivityElectric/magnetic detectionAcoustic wave reradiationMagnetic coreInstrumentation
The invention relates to a power-frequency feeble-current electromagnetic signal sensor of a non-current transformer type, comprising a bottom liner (11) and at least two sensors (12) mounted on the bottom liner (11). Axial geometric axes of the sensor modules (12) are mutually staggered, and either sensor (12) comprises a magnetic core (121) and a lacquered wire (122) which is wound outside the magnetic core (121) and used for inducing a magnetic field and generating electromotive force; one end of either lacquered wire (122) of either sensor (12) is connected with the input end of a multistage amplifying circuit module (2), and the other end of one lacquered wire (122) of one sensor (12) and the other end of the other lacquered wire (122) of the other sensor (12) are mutually connected together to form a sensor pair. The power-frequency feeble-current electromagnetic signal sensor of non-current transformer type adopts a non-destructive detection technology, does not destruct a wall surface, has low cost, high sensitivity, remarkable strength variance when closing to a live wire, accurate positioning, small error between an indicative position and a practical wire position in a range from -0.5cm to 0.5cm, easiness and simplicity, maneuverability without any professional knowledge, simple structure, firmness, durability, safety, reliability, no ray release, no ultrasonic wave release, and the like and does not need to mount an instrument on the wire, thereby being convenient and practical.
Owner:GUANGDONG UNIV OF TECH
A privacy protection method for encrypted smart contracts based on trusted execution environment
ActiveCN113726733BPrivacy protectionEnsure safe executionUser identity/authority verificationDigital data protectionKey exchangePERQ
The invention discloses a smart contract privacy protection method based on a trusted execution environment and encryption, which includes two steps of contract deployment and contract invocation. First, according to the confidential and non-tamperable characteristics of the trusted execution environment, the encrypted deployment of the smart contract bytecode is completed through the trusted execution environment, and the authentication center is used to confirm whether the identity of the trusted execution environment on different computing nodes is legal. Secure transmission of smart contract bytecodes between legitimate trusted execution environments. Secondly, the execution of the smart contract bytecode also occurs in the trusted execution environment. The key exchange algorithm is used to realize the secure transmission of the verification key between the user node and the trusted execution environment. The trusted execution environment uses the verification key to execute the execution. The result is signed, and the user node ensures the correctness of the contract execution through the signature. This solution solves the problems of the smart contract code privacy leakage and the illegal identity of the computing node hosting the TEE in the previous solution.
Owner:SOUTHEAST UNIV
A security communication method and device
ActiveCN105307163BEnsure safe executionPrevent eavesdroppingSecurity arrangementSecure communicationInternet privacy
The present application proposes a secure communication method and device, wherein the method includes establishing a connection between the security chip and the trusted application through basic information authentication, external authentication, and secondary authentication, and the trusted application and the user application pass basic information authentication, external authentication, and secondary authentication To establish a connection, the security chip establishes a logical connection with the user application. By establishing a secure channel before business communication, all communication data in the secure channel is encrypted and transmitted, making the data in the link no longer transparent. This method can effectively prevent eavesdropping and ensure The secure execution of services without additional external devices enhances user experience.
Owner:HENGBAO
Method for configuring system audit service, information processing device and readable storage medium
ActiveCN107707410BEnsure safetyEnsure safe executionDigital data protectionPlatform integrity maintainanceInformation processingEngineering
The present disclosure provides a method for configuring a system audit service on a server side, the method comprising receiving a first instruction to establish at least one blockchain; and sending a second instruction to instruct a node communicatively connected to the server to install a blockchain smart contract, The blockchain smart contract includes a system audit smart contract. The present disclosure also provides a method for configuring a system audit service on the node side of the block chain, the method includes receiving a second instruction and installing a block chain smart contract. Finally, the present disclosure provides an information processing device and a corresponding tangible computer-readable storage medium for realizing the above method. According to the solution disclosed in this disclosure, the smart contract running on the block chain is used to realize the system audit function, so that the unique advantages of the block chain technology can be used to ensure the safe execution of the system audit function, thereby effectively ensuring the integrity of the audit log. Security, thereby ensuring the security of important data stored on the nodes of the enterprise-level blockchain.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
Method and system for rapid personalization of smart card
ActiveCN105337995BGet personalized resultsShort response timeDigital data protectionTransmissionPersonalizationSmart card
The invention provides a rapid personalization method and system for a smart card. The method comprises the steps that multiple personalization data in a database are compiled to be a personalization instruction, the personalization instruction is sent to the smart card, the smart card decompiles the instruction to obtain personalization parameters, the smart card carries out continuous processing on the personalization parameters, and therefore the personalization process of the smart card is achieved. Compared with the prior art, according to the technical scheme, the response transmission time and processing intervals of multiple instructions are saved, the personalization speed is increased, and the possibility that personalization fails when mistakes are made in the personalization process is reduced.
Owner:HENGBAO
A method and system for autonomous control of spacecraft approaching operations based on online learning
ActiveCN111596677BAchieving motion avoidanceEnsure safe executionAutonomous decision making processAttitude controlDynamic modelsOnline learning
Owner:BEIHANG UNIV
Face payment security method based on security unit and trusted execution environment
PendingCN113902446AProtect data accuracyImprove integrityProtocol authorisationCiphertextConfidentiality
The invention provides a face payment security method based on a security unit and a trusted execution environment, and the method comprises the steps: obtaining a living body percentage through the calculation of face living body detection data and face image data collected by a face recognition trusted application and a face recognition camera, and the trusted execution environment, and then calling the security unit to obtain a percentage signature result and ciphertext data; and enabling the payment application to judge whether the living body percentage is larger than a preset living body percentage threshold value or not, and if yes, carrying out user identity authentication and remaining transactions in combination with a password keyboard in the rich execution environment. In the scheme, the security unit provides a secure cryptographic algorithm service and a face recognition data protection key, the trusted execution environment ensures secure execution of a face living body detection algorithm, and through direct connection with the face recognition camera, protection of integrity, authentication and confidentiality of data in the face payment process is ensured.
Owner:北京银联金卡科技有限公司
A block-level encryption method and multi-granularity deduplication method in cloud storage
ActiveCN106603561BDe-duplicationReduce overheadDigital data protectionTransmissionGranularityCloud storage
The invention discloses a block-level encryption method and a multi-granularity deduplication method in cloud storage, and belongs to the technical field of network security. The invention includes: setting the system public parameters, calculating the key and encrypting the file at the user end, and calculating the metadata; the user end selects part of the metadata as a deduplication request and sends it to the server, and the server verifies the user's file ownership according to the request, and stores Search the file in the list, if the file already exists, provide access directly, otherwise the server requires the client to upload non-repetitive information, the server will verify the consistency of the received data block, if the verification passes, the server will allow the client to access the file . The present invention is suitable for cloud storage that requires data security and efficiency at the same time, and aims to deduplicate user data safely and reliably, and has high data storage efficiency.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Resource processing method and system based on block chain
PendingCN114493568AEnsure safe executionImprove operational efficiencyProtocol authorisationResource transferResource Provider
The embodiment of the invention provides a resource processing method and system based on a block chain, the resource processing method based on the block chain is applied to the resource processing system, the system comprises a first decision module, a second decision module and a task storage module of a resource processing party, under the condition that a resource transfer task sent by an off-chain resource provider is received, the current state information of the off-chain resource provider and an on-chain resource receiver is determined, and under the condition that the current state information is determined to meet a preset task interruption condition, the resource transfer task is stored in a task storage module; the task storage module sends the resource transfer task to the second decision module based on a preset task sending rule; and the second decision module responds to the current state information of the under-chain resource provider and the on-chain resource receiver of the resource transfer task, and executes the resource transfer task under the condition that the current state information determines that a preset task execution condition is met.
Owner:ALIPAY LABS SINGAPORE PTE LTD
Hybrid cloud security scheduling method and hybrid cloud security scheduling system
The invention provides a hybrid cloud security scheduling method, which comprises the following steps of: when request information of a task sent by a user is obtained, judging whether to distribute the task to a target private cloud server or a target public cloud virtual machine based on the request information of the task; when it is determined that the task is allocated to the target public cloud virtual machine, performing identity verification on the task executed by the target public cloud virtual machine; after the identity verification of the task is passed, performing encryption processing on input data requested by the task, and transmitting the encrypted data to the task; and receiving the output data transmitted by the task, performing integrity verification on the output datatransmitted by the task, and feeding back the output data to the user when the integrity verification is passed. Through the technical scheme of the invention, on the premise of meeting the task execution security, the use efficiency of the hybrid cloud resources can be optimized.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Spacecraft proximity operation autonomous control method and system based on online learning
ActiveCN111596677AAchieving motion avoidanceEnsure safe executionAutonomous decision making processAttitude controlOnline learningDual quaternion
The invention relates to a spacecraft proximity operation autonomous control method and system based on online learning. In order to solve practical engineering problems of sight field constraint, proximity corridor constraint, real-time online optimization of control performance and the like of a spacecraft in a proximity operation task, the invention provides a proximity operation autonomous control technology method based on online learning. The method comprises the following steps: firstly, establishing a pose integrated kinetic model of a spacecraft based on dual quaternions, and describing pose motion constraints into an inequality form by utilizing the dual quaternions; secondly, designing a return function of online learning control based on the property of the dual quaternion fortask requirements of spacecraft approaching operation autonomous control; and finally, under a dual quaternion framework, designing an online learning method is designed to enable the controller to begradually improved from a simple control strategy to a suboptimal controller by utilizing online data. The task execution capability of the spacecraft is improved.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com