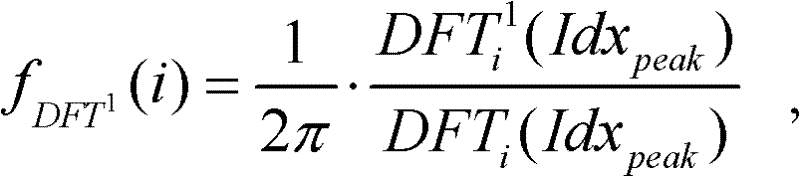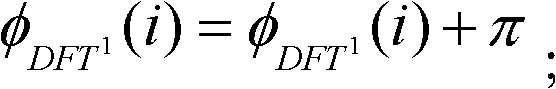Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
50results about How to "Implement integrity checks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
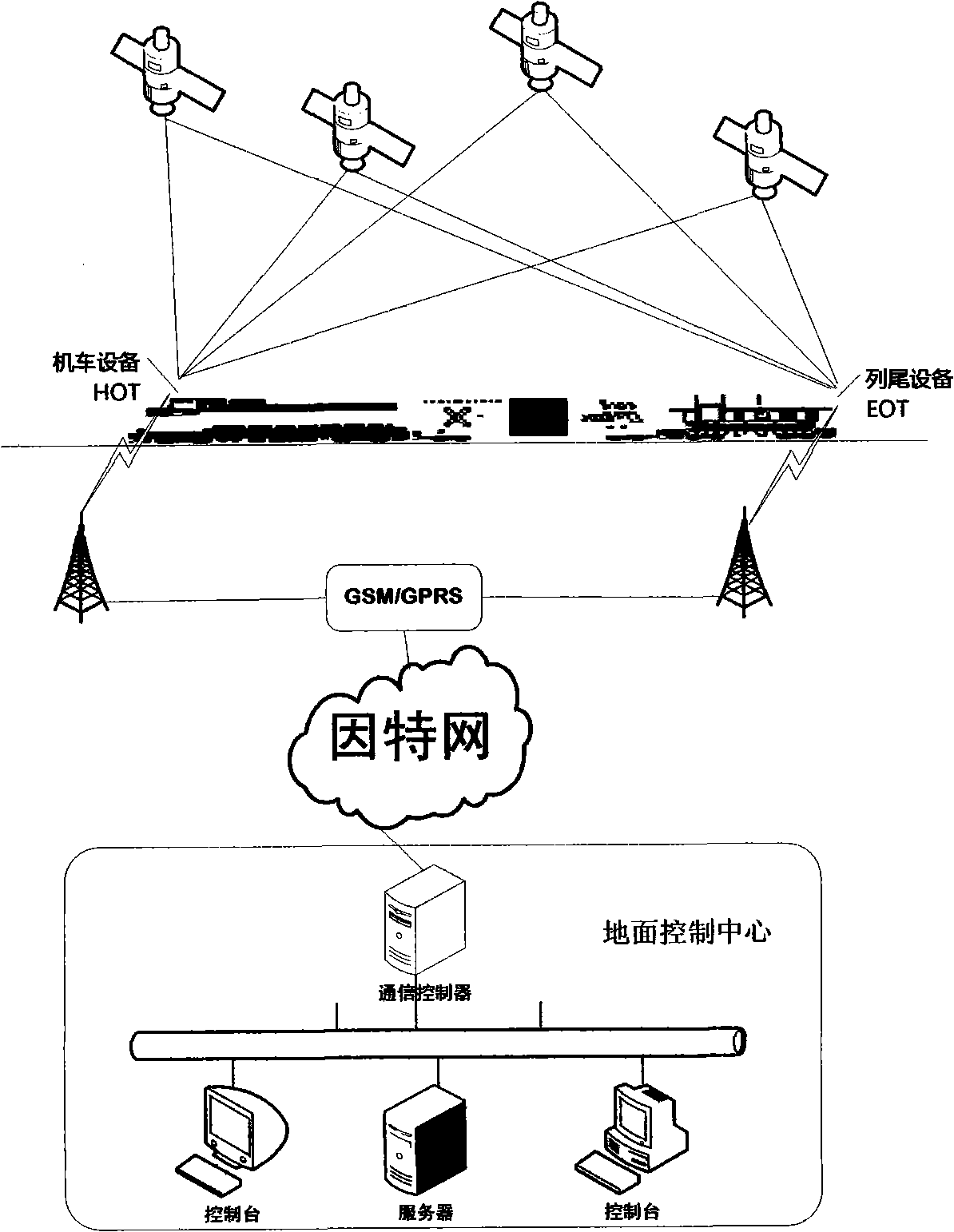
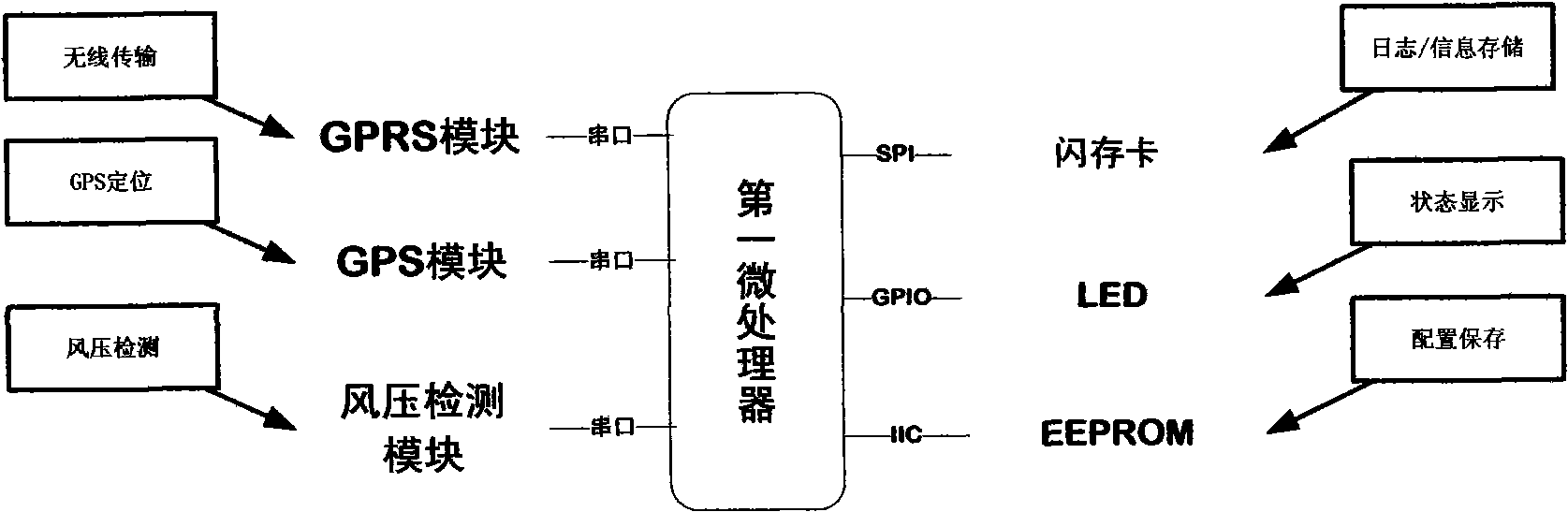
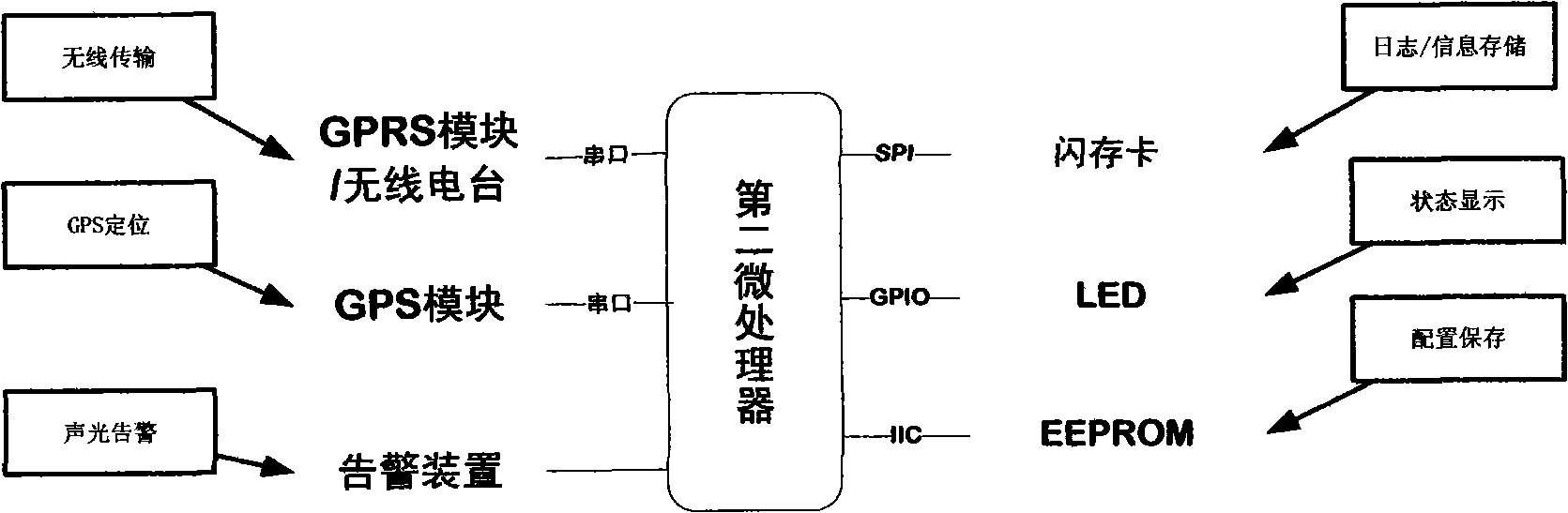
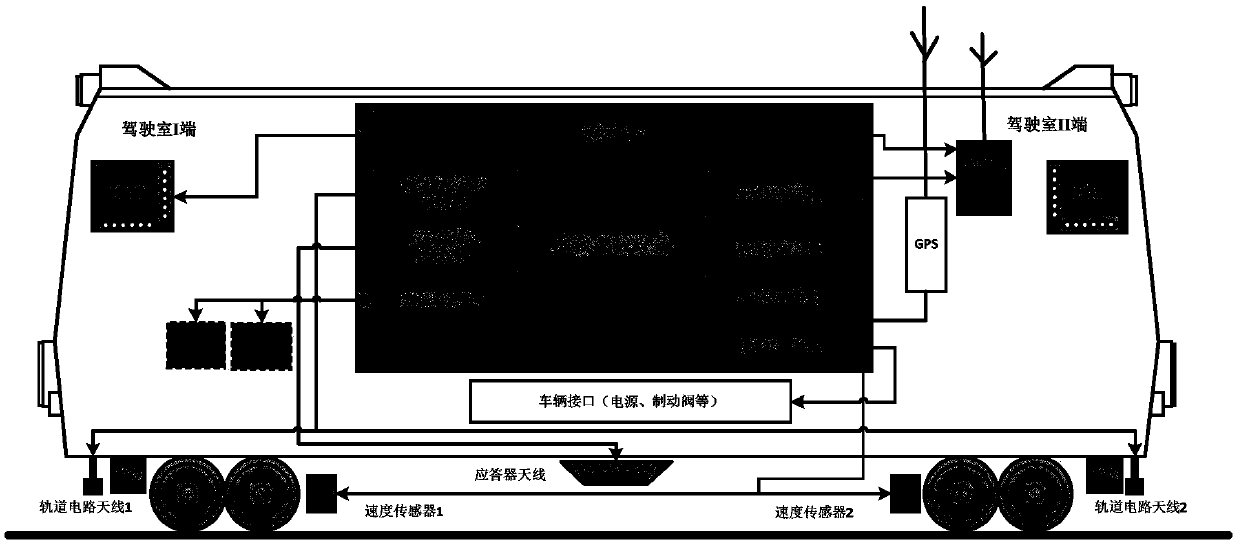
System for realizing remote monitoring of integrity of train and method
ActiveCN101554878AImplement integrity checksRealize remote monitoringRailway traffic control systemsEngineeringSafety monitoring
The invention relates to a system for realizing remote monitoring of integrity of a train and a method, and relates to an onboard device and a ground control center. The system comprises a train tail device and a locomotive device, a GPRS wireless communication module, a microprocessor, a GPS satellite positioning module, a safety monitoring module, a microprocessor, a GPS satellite positioning module, an alarm device, a communication controller and a ground database server. The train tail device is used for monitoring the working state and train tail position information of a train tail wind pressure detection device; the microprocessor is connected with a wireless communication device by an interface; the safety monitoring module comprises the wireless communication device; the communication controller is used for acquiring the data transmitted by the onboard device by GPRS and forwarding instructions sent by a console to the onboard device; and the ground database server stores the data received by the communication controller so as to supply data to user software of the console for use. The system can realize remote monitoring of integrity of the train, and also can utilize the GPS information to assist the integrity inspection of the train, thus achieving the purpose of guaranteeing driving safety.
Owner:BEIJING JIAOTONG UNIV
Light-weight train automatic control system orienting to heavy haul railway of China
PendingCN109677466AGet rid of the bondageGet rid of dependenceRailway traffic control systemsSignalling indicators on vehicleAutomatic controlAutomatic train control
The invention relates to a light-weight train automatic control system orienting to heavy haul railway of China. The system is connected equipment of a control center, interlocking equipment, equipment of a satellite positioning differential station, equipment of a transponder and track circuit equipment respectively; the train automatic control system comprises a ground control center ROC and vehicle-mounted equipment, wherein the ground control center ROC is connected with the equipment of a control center, interlocking equipment, equipment of a satellite positioning differential station andthe vehicle-mounted equipment respectively; the vehicle mounted equipment is connected with the equipment of the transponder, the ROC equipment and the track circuit equipment; the train automatic control system has a safety protection function, an operation plan management function, a temporary speed limitation management function and an automatic driving function on the basis of sufficiently reusing the achievements of existing heavy load train control system. Compared with the prior art, the system disclosed by the invention has the advantages of being light in weight, safe and efficient.
Owner:CASCO SIGNAL
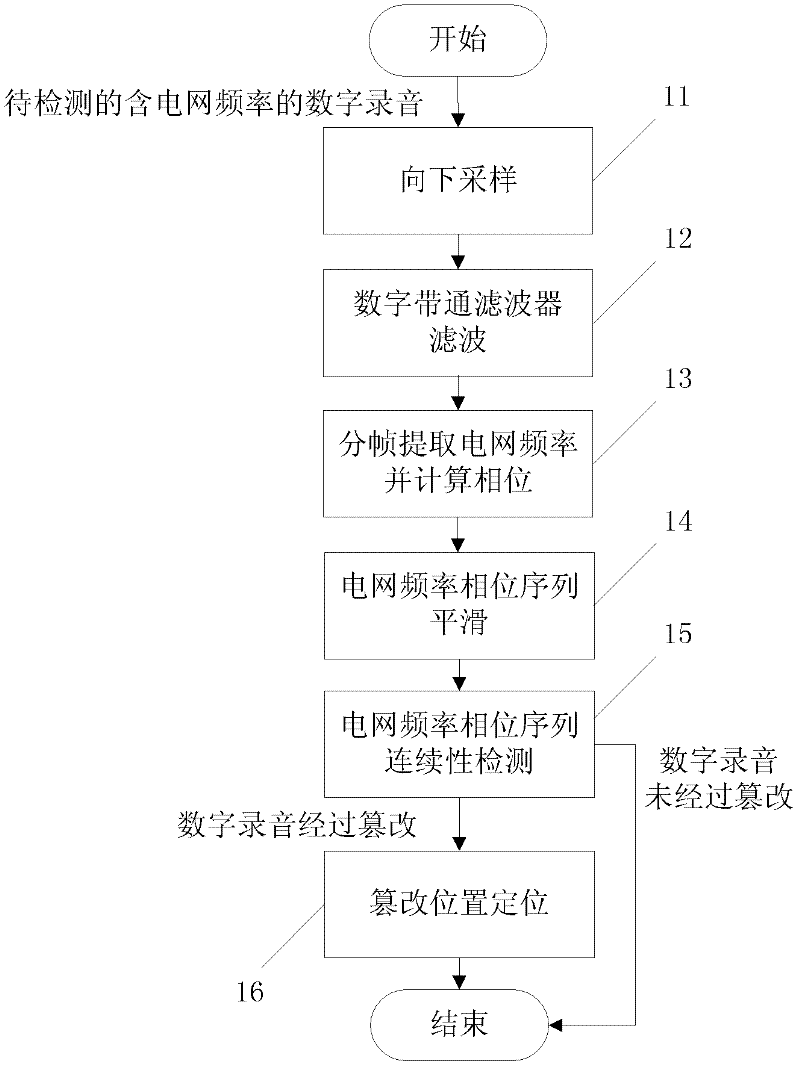
Digital audio record integrity detection method
The invention discloses a digital audio record integrity detection method, which comprises the following steps of: 1, performing down-sampling on a digital audio record which is to be detected and carries power grid frequency; 2, performing band-pass filtering on sampled data; 3, performing framing processing on a filtered audio sequence, extracting the power grid frequency frame by frame, and calculating corresponding power grid frequency phases to obtain a power grid frequency phase sequence; and 4, detecting the integrity of the digital audio record according to characteristic values of the power grid frequency phases. The phase characteristics of the digital audio record with the power grid frequency, whether the digital audio record is subjected to tampering such as insertion, deletion and replacement or not is judged, and a tampering position is determined to detect the integrity of the digital audio record. The method can be used for the integrity authentication of a digital audio record evidence in court evidencing.
Owner:TSINGHUA UNIV
Multi-parameter fused substation data integrity checking method
ActiveCN102798776AMaximize the useImplement integrity checksElectrical testingData integrityElectric capacity
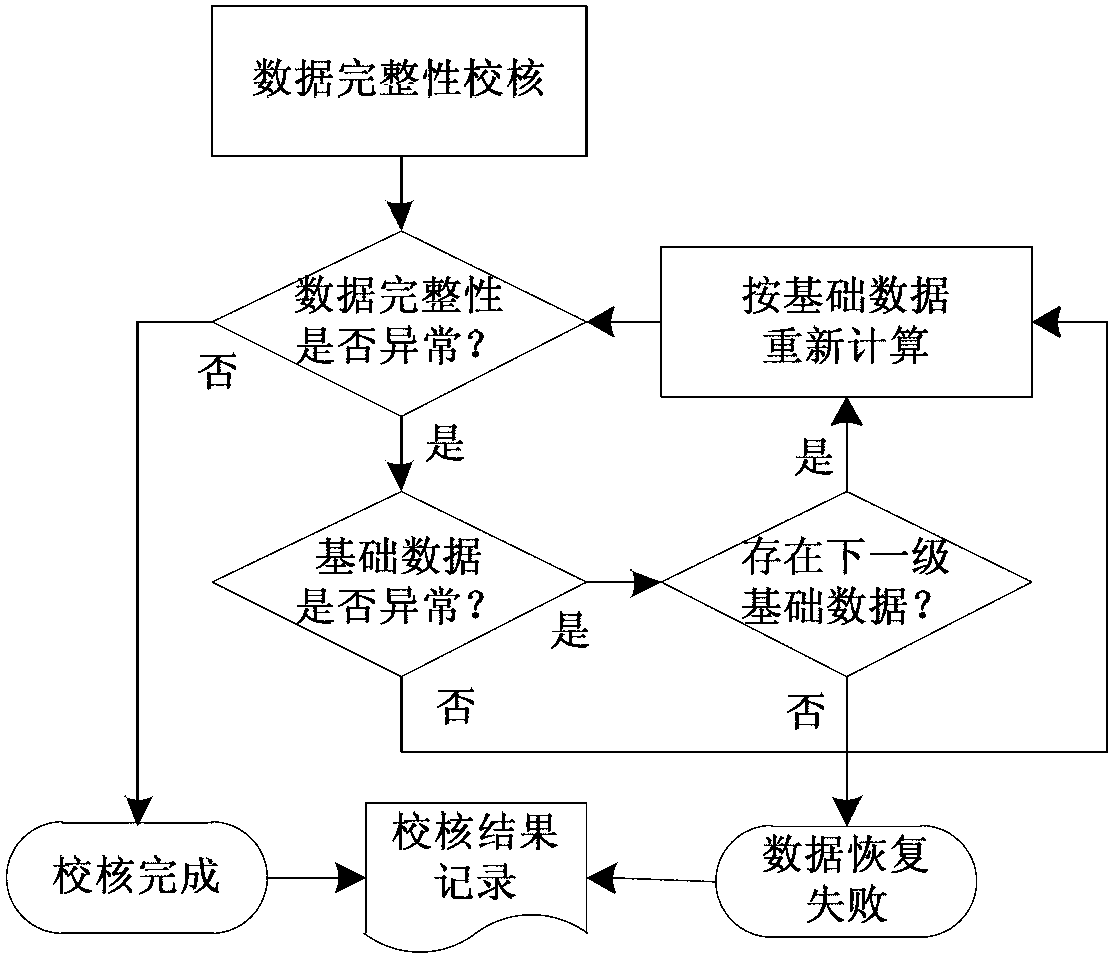
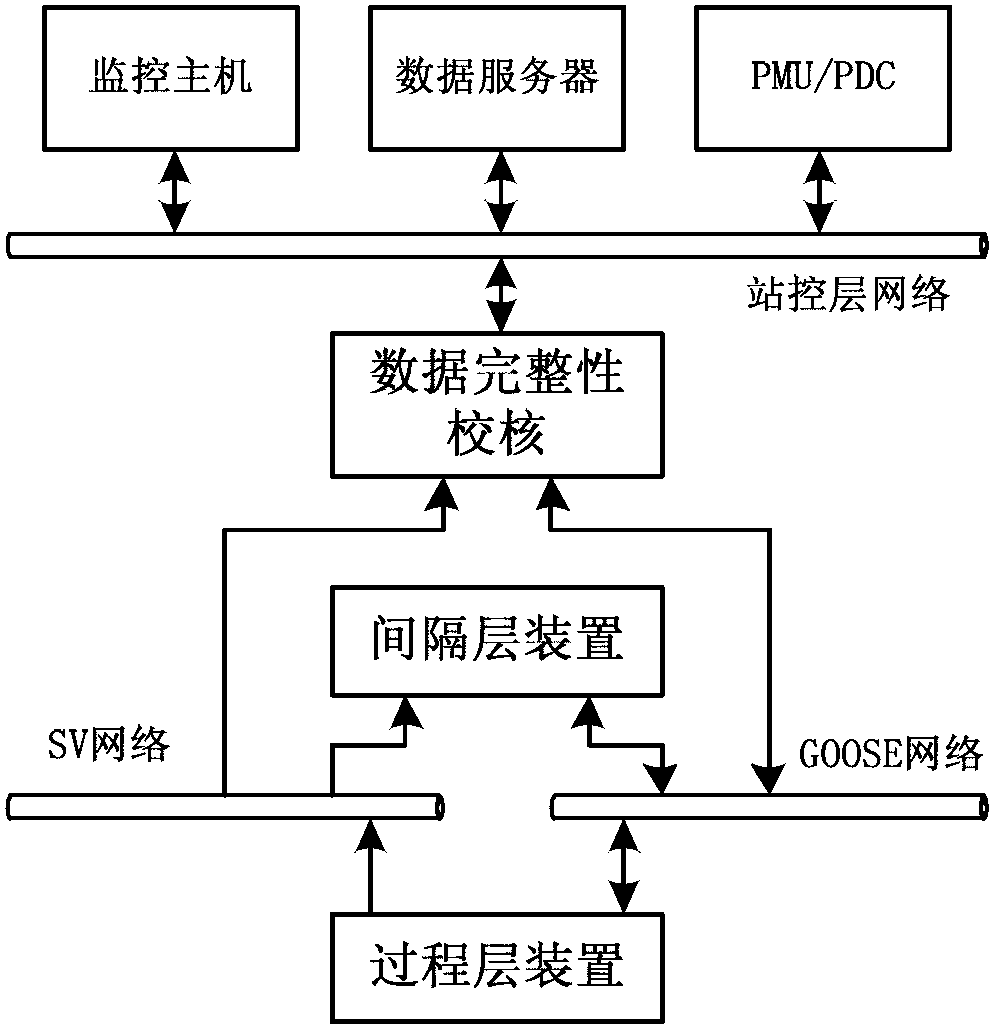
The invention provides a multi-parameter fused substation data integrity checking method, comprising the following corresponding checking steps according to a data incidence relation: checking data acquired from the same source by a weighted voting method; checking measurement data of the current flowing into a closed region by a current summation method; checking data having a constrained relationship by an equipotential searching method or a reasoning method based on the constrained relationship; checking different forms of the same data by a source-tracing computing method; checking the rationality of the sampled values and phasor values of an alternating-current electric capacity at two adjacent time points by a jumping detection method. The multi-parameter fused substation data integrity checking scheme provided by the invention performs integrity checking on the data in different forms from a plurality of dimensionalities of time and space, and systematically estimates and improves the quality of the basic data, thereby improving the reliability and usability of the substation data.
Owner:CHINA ELECTRIC POWER RES INST +1
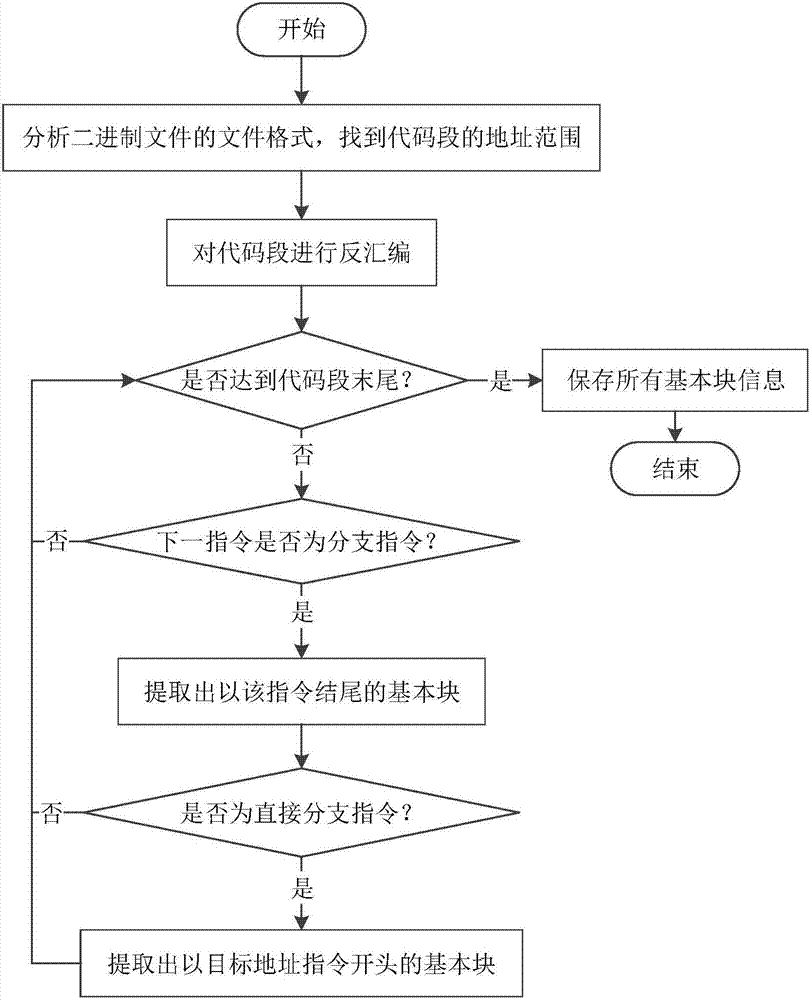
Full context-sensitive program control flow integrity protection method and system
ActiveCN107194252AImplement integrity checksHigh precisionPlatform integrity maintainanceProgram/content distribution protectionControl flowComputer module
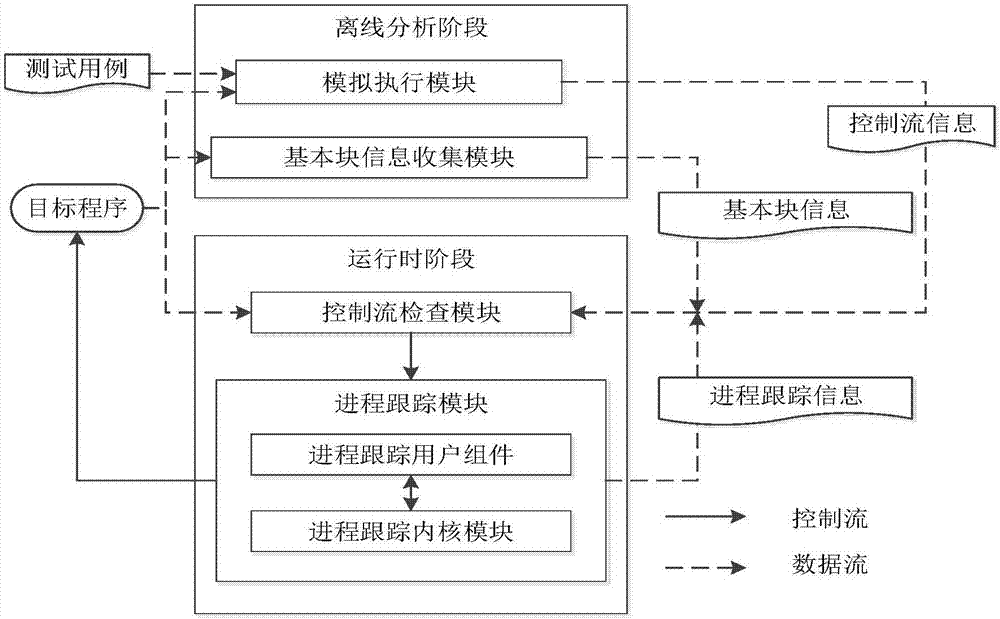
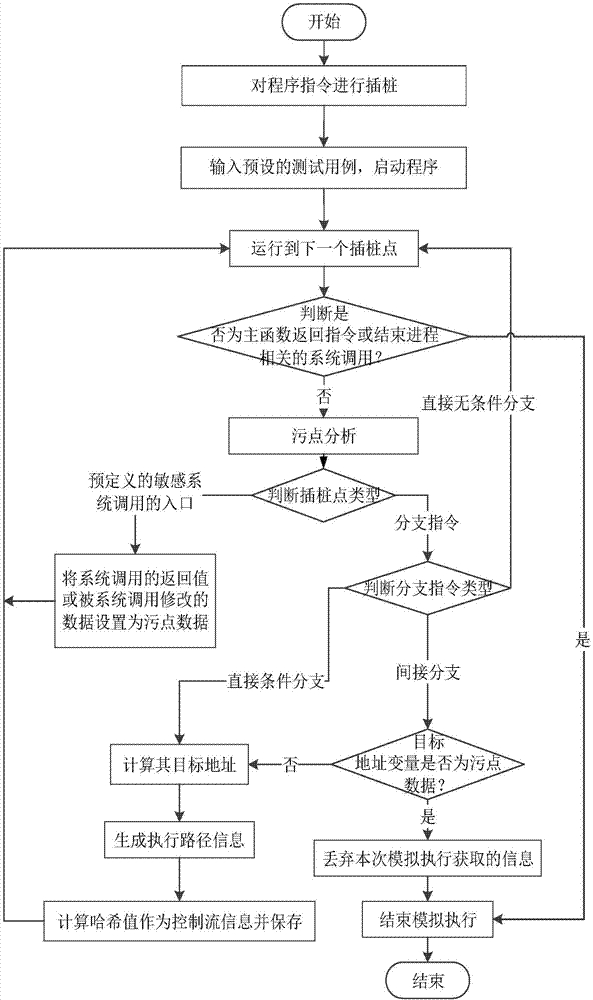
The invention discloses a full context-sensitive program control flow integrity protection method and system. According to the method, during an offline analysis stage, control flow information of a program is collected through simulative execution; an executive path is tracked during operation; the executive path, reaching a same indirect branch, of a process is tracked; path information is matched with the control flow information; if the matching succeeds, it is showed that a simulative executive path during offline analysis is the same as a real executive path during operation, and a subsequent legal target address can be judged according to the control flow information in the offline analysis; and if a target address during operation is different from the legal target address, it is judged that the program suffers from control flow hijack attack, so that a control flow check module notifies a process tracking module to stop the process. The invention furthermore discloses the full context-sensitive program control flow integrity protection system. The integrity protection is realized by tracking and checking executive path information, so that the program is prevented from being threatened by the control flow hijack attack.
Owner:HUAZHONG UNIV OF SCI & TECH
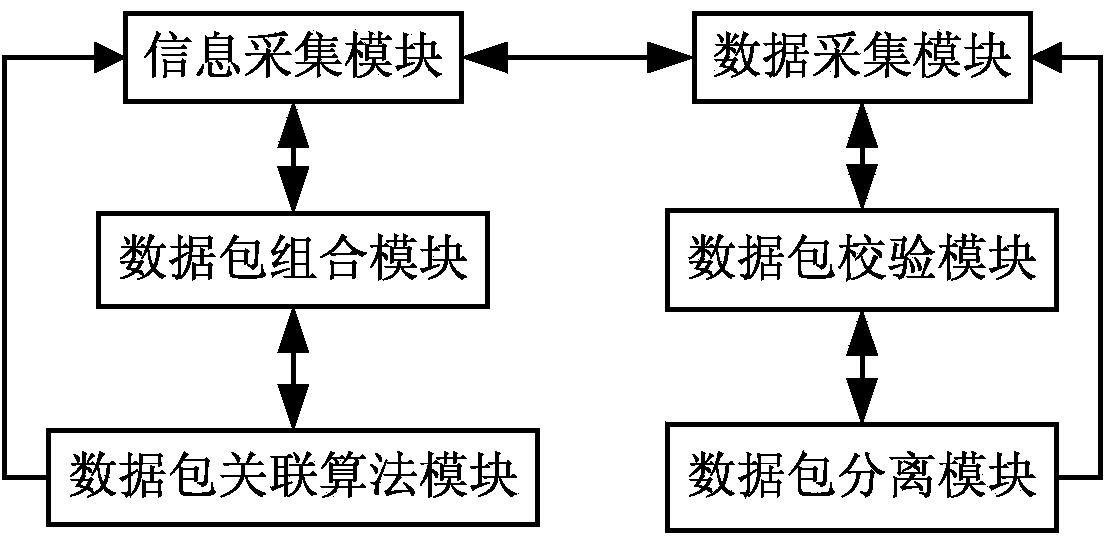
Supervision data acquisition system and method used for small loan company
ActiveCN104112228ASolve the lossImprove real-time performanceFinanceDigital data protectionNetwork packetData acquisition
The invention discloses a supervision data acquisition system and method used for a small loan company, and relates to the field of supervision data acquisition. The supervision data acquisition system comprises an information acquisition module, a data packet combination module, a data packet association algorithm module, a data acquisition module, a data packet verification module and a data packet separation module; the information acquisition module, the data packet combination module and the data packet association algorithm module are sequentially connected end to end; the information acquisition module is connected with the data acquisition module; the data acquisition module, the data packet verification module and the data packet separation module are sequentially connected end to end. The supervision data acquisition system and method used for the small loan company is relatively high in work efficiency, can efficiently place data loss during multiple-data-packet delivery, can improve the accuracy of a supervision conclusion, and is relatively safe to use and relatively wide in application range.
Owner:WUHAN FINANCIAL ASSETS EXCHANGE
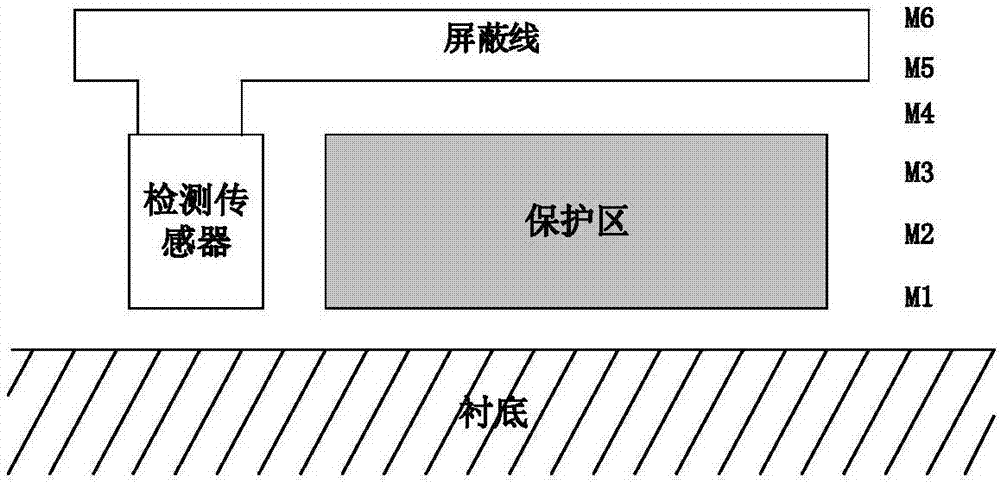
Chip top protection layer integrity detection apparatus
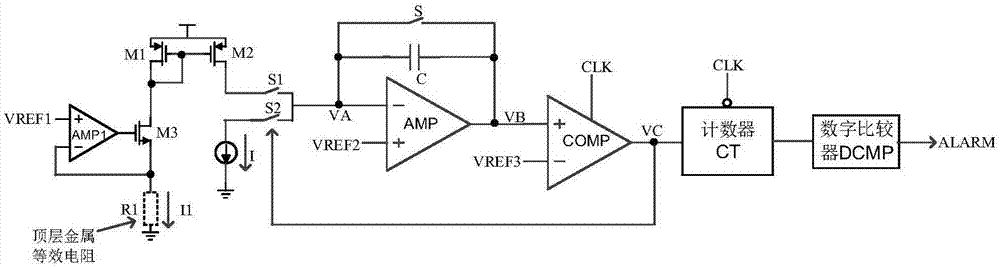
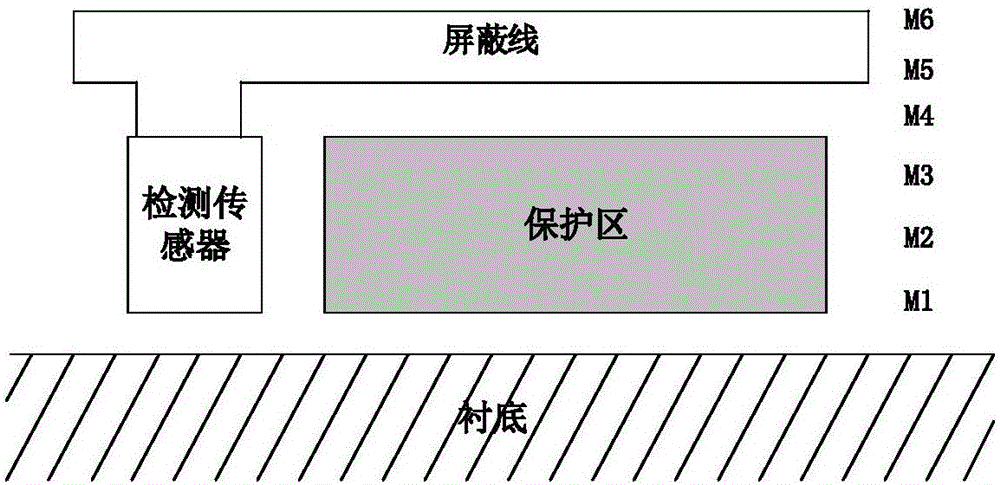
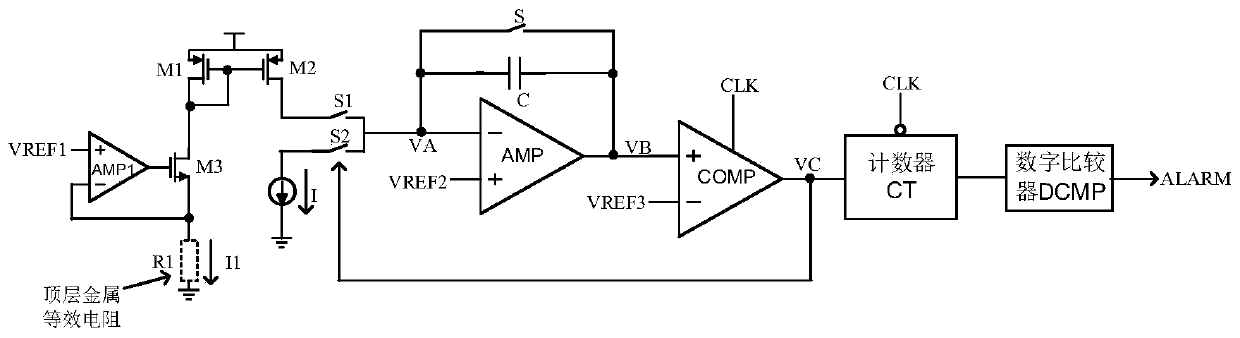
ActiveCN107329074AImprove detection accuracyImplement integrity checksElectronic circuit testingDelta modulationEngineering
The invention relates to the chip focusing resistance ion beam attack field and provides a top metal protection layer integrity detection method based on a sigma-delta modulator. In the method, through detecting whether a resistance value of a metal line is changed, whether a protection layer is complete is detected and then whether an attacker uses FIB to correct the protection layer is determined. A chip top protection layer integrity detection apparatus is formed by a top metal line AB, operation amplifiers AMP and AMP1, PMOS pipes M1 and M2, an NMOS pipe M3, switches S1 and S2, a reference current source I, a comparator COMP with a clock terminal, a counter CT and a digital comparator DCMP. The apparatus is mainly applied to a chip focusing resistance ion beam attack occasion.
Owner:TIANJIN UNIV
Data fusion method capable of ensuring confidentiality and integrity
InactiveCN104244236AUniqueness guaranteedGuaranteed confidentialitySecurity arrangementData integrityConfidentiality
The invention belongs to the technical field of sensor networks, and particularly relates to a data fusion method capable of ensuring confidentiality and integrity in a wireless sensor network. The method includes the steps of forming a node set structure with three nodes in one set in a network, encrypting data collected by source nodes through a privacy homomorphic encryption method, respectively verifying the data integrity of data in the fusion and transmission process by combining the message authentication code (MAC) authentication technology with the node set structure of the network, and recovering the data through the privacy hoomorphic encryption technology to obtain a correct fusion result after the data are completely transmitted to a base station. By means of the method, the confidentiality and the integrity in the data fusion process and the data transmission process of the data in the wireless sensor network are ensured, the data confidentiality, the data integrity and the node energy are comprehensively taken into consideration when the data fusion method is designed, wrong data existing in the network can be detected, and good performance can be achieved through the mechanism even under the condition that the number of the damaged nodes is fixed.
Owner:JIANGSU UNIV
A reversible information concealment framework with contrast pull-up utilizing histogram translation
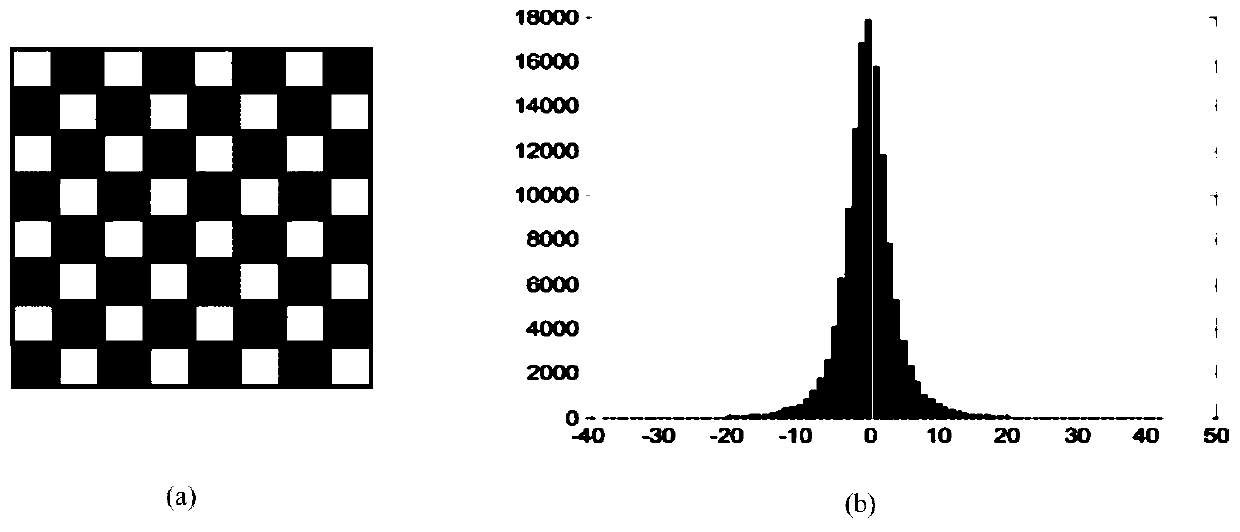
ActiveCN111464717AHigh embedding rateIncrease contrastImage enhancementDigital data protectionSteganalysisContrast level
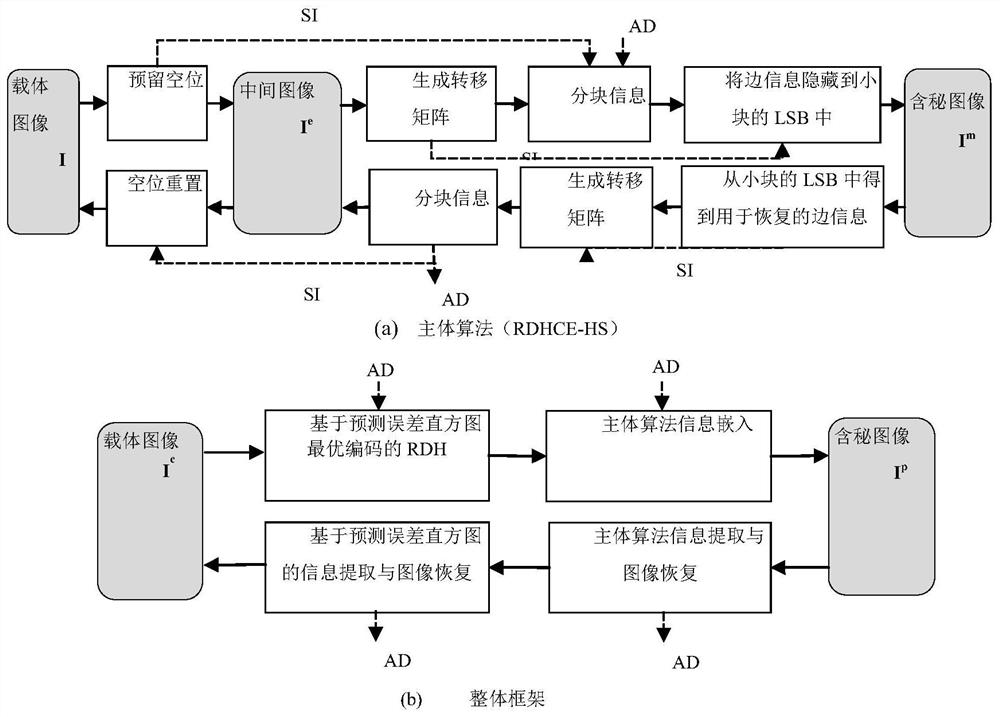
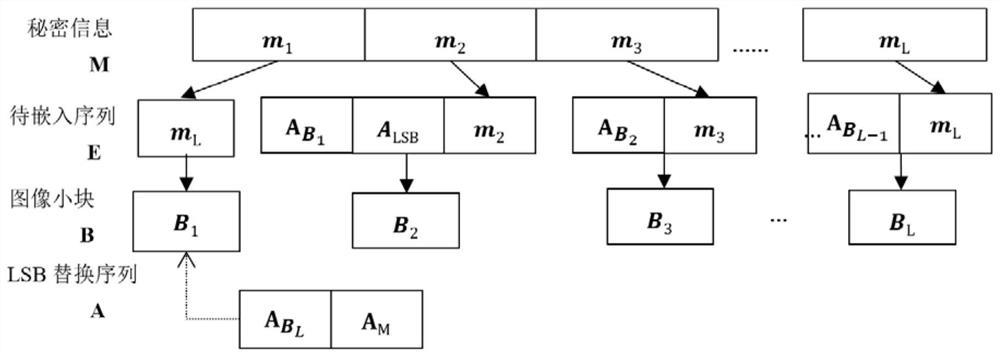
The invention discloses a reversible information hiding framework with contrast pull-up by using histogram translation, and designs an improved RDH based on prediction error histogram optimal coding to expand a main body algorithm into an efficient hiding framework with dual embedding capability. Compared with a plurality of previous RDH technologies based on contrast ratio pull-up, the frameworkprovided by the invention not only has higher information embedding rate, but also can generate a secret-containing image with higher quality, and in addition, the security test also proves that the framework can effectively resist a plurality of famous steganalysis technologies (such as Enable classifiers and the like). Moreover, the framework has a dual-embedding function, and can embed copyright information such as an image identifier, a serial number, characters and the like into the carrier on the premise of ensuring the original appearance of the digital carrier, so as to achieve the purposes of copyright protection, integrity check and the like of the carrier.
Owner:章劲松
Sensing original data safety protection method supporting data processing
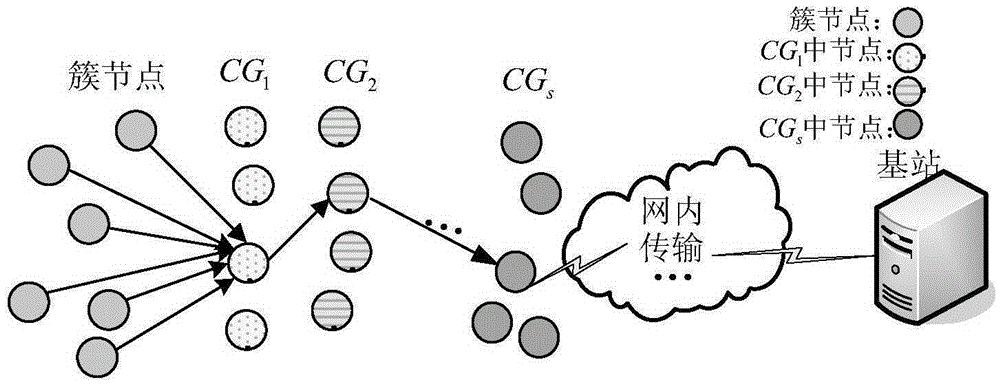
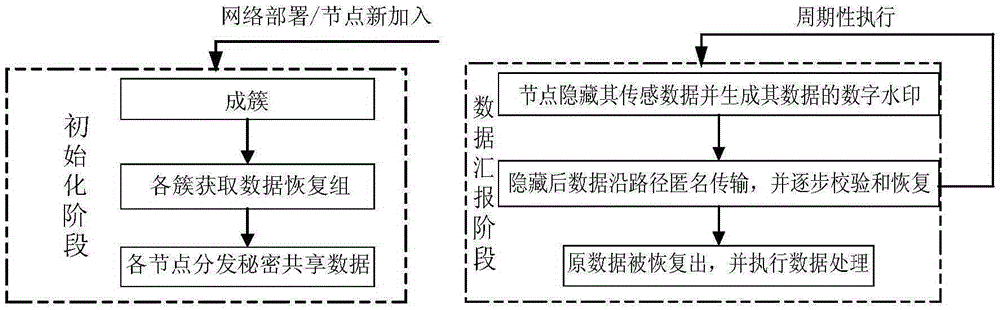
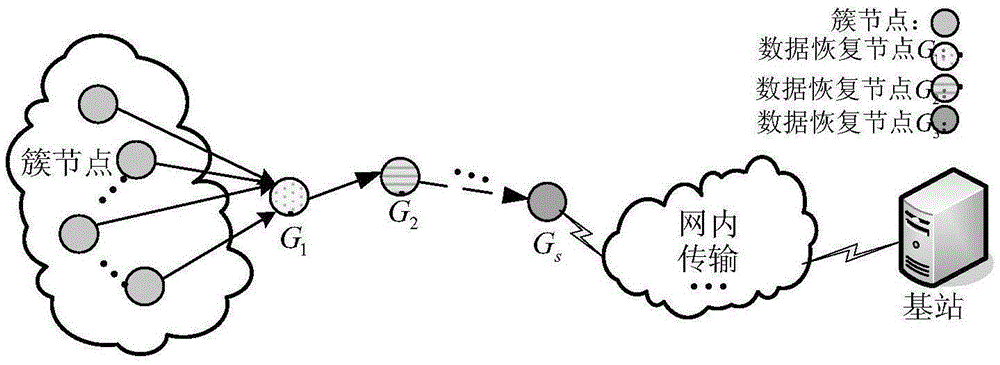
ActiveCN105407090AImplement integrity checksCo-EraseTransmissionHigh level techniquesSensing dataOriginal data
The invention discloses a sensing original data safety protection method supporting data processing. The method comprises an initialization stage and a data reporting stage executed repeatedly. The initialization stage comprises clustering nodes, obtaining data recovery groups by various clusters and distributing secret sharing data to the nodes. The data reporting stage comprises hiding sensing data of the nodes by the nodes, generating watermark data, and recovering the sensing data through cooperation of data recovery nodes. The method has good expansibility for the addition of the nodes and good robustness for node failures. Tolerance for the captured nodes is improved, good privacy protection effectiveness is provided, and energy consumption is reduced at the same time; and integrity of data can be identified, so filtering for tampered data is achieved, and a network communication resource is prevented from being wasted.
Owner:716TH RES INST OF CHINA SHIPBUILDING INDAL CORP
Locomotive video data integrity automatic detection method
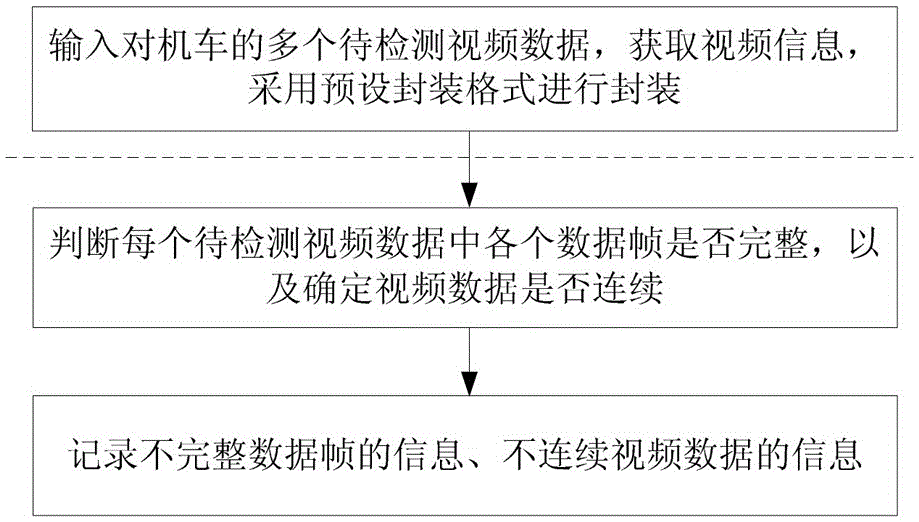
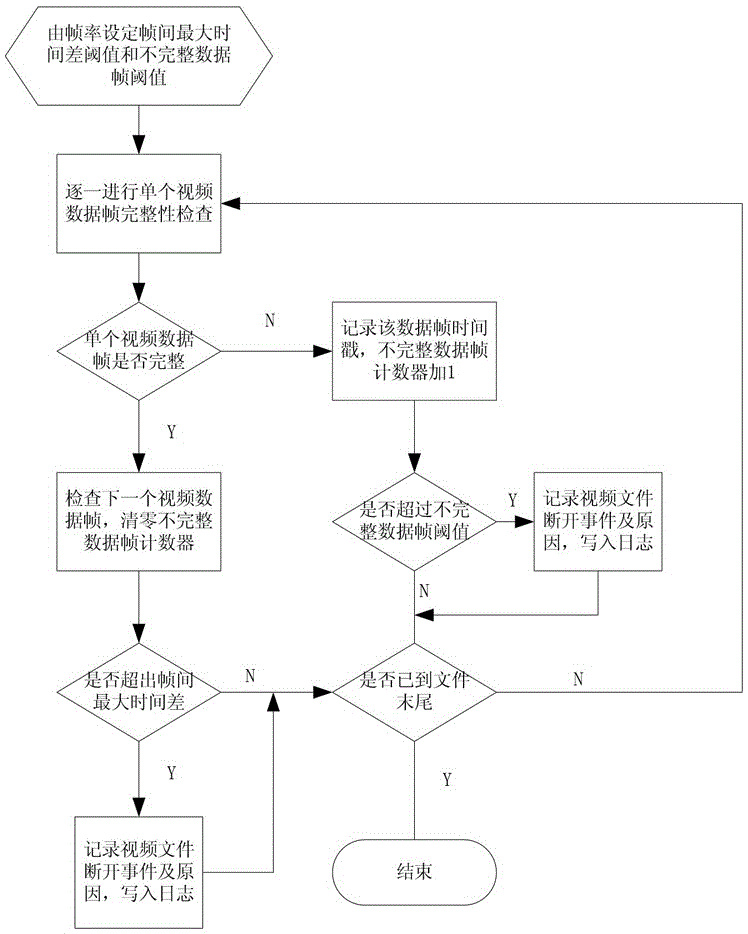
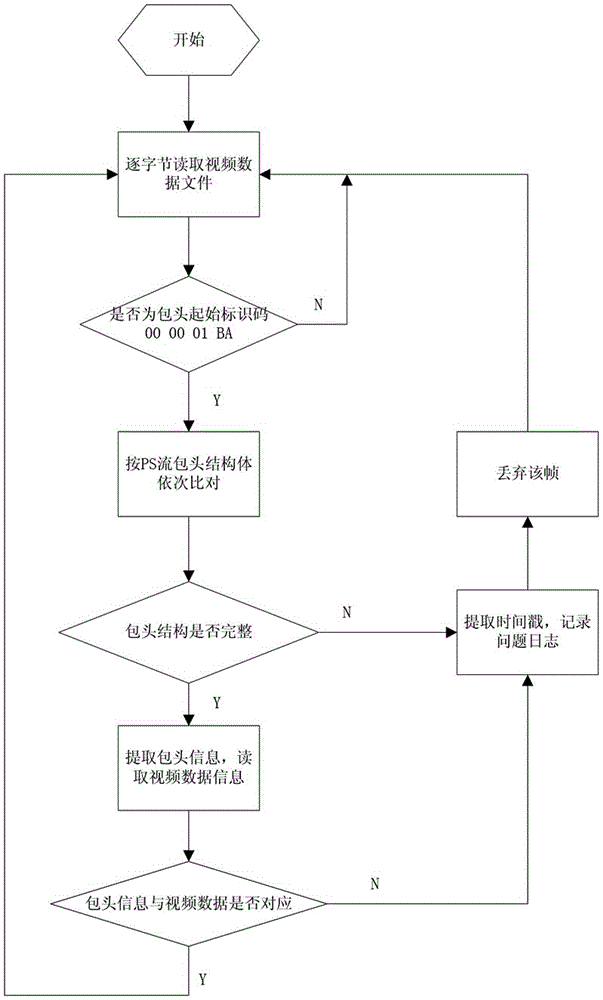
ActiveCN105049915AAutomated detection of completenessImprove detection efficiencyTelevision systemsSelective content distributionData integrityComputer vision
The invention discloses a locomotive video data integrity automatic detection method comprising the following steps: (1) inputting multiple pieces of to-be-detected video data of a locomotive, acquiring video information corresponding to each piece of to-be-detected video data, and encapsulating each piece of to-be-detected video data in a default encapsulation format; and (2) acquiring and detecting each piece of to-be-detected video data after encapsulation, judging whether each data frame is complete according to the default encapsulation format during detection of each to-be-detected video data, determining whether the corresponding to-be-detected video data is continuous according to the judgment result of each data frame, and recording information of the data frames judged as incomplete data frames and video information corresponding to video data determined as discontinuous video data. The locomotive video data integrity automatic detection method of the invention is advantageous in that implementation and operation are simple and convenient, automatic detection of the integrity of batch video data can be realized, and the efficiency and precision of detection are high.
Owner:ZHUZHOU CSR TIMES ELECTRIC CO LTD
Data processing method, system and equipment based on cloud platform
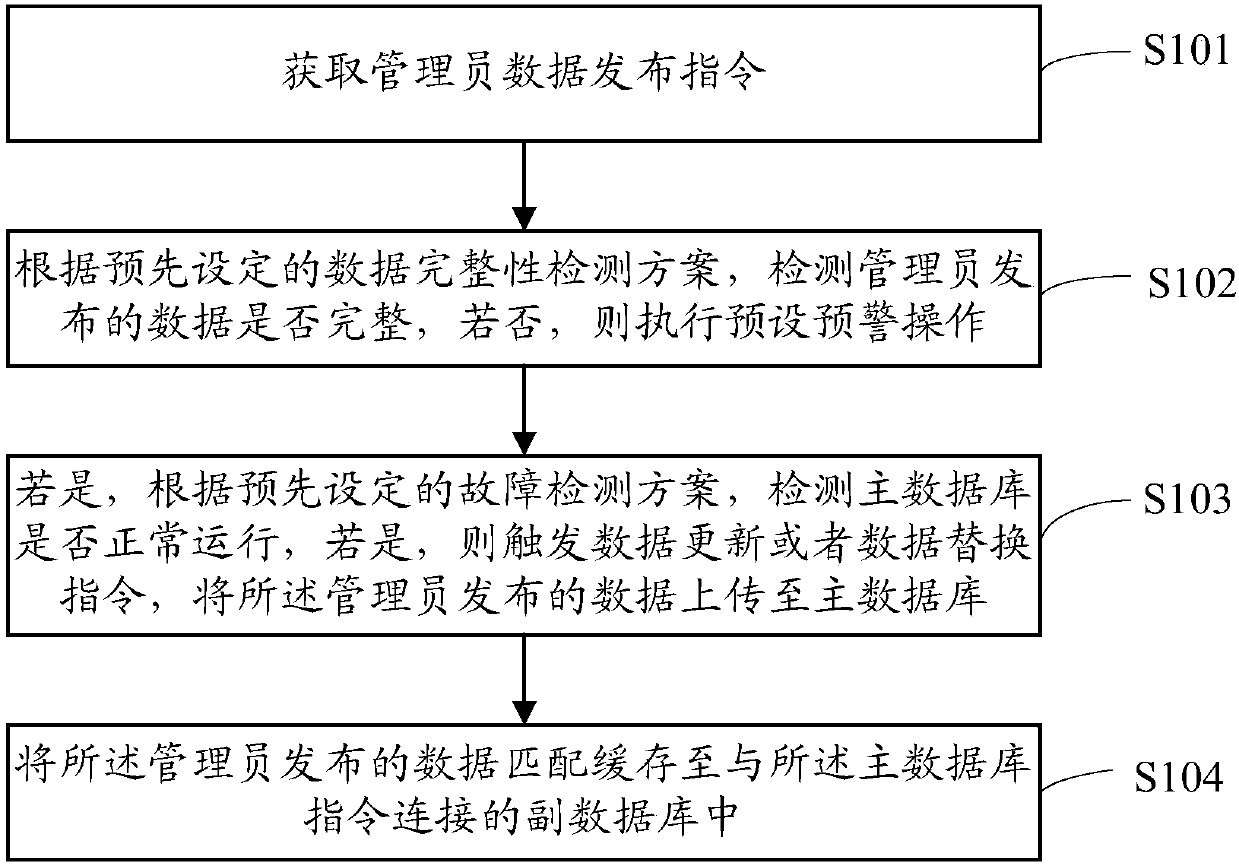
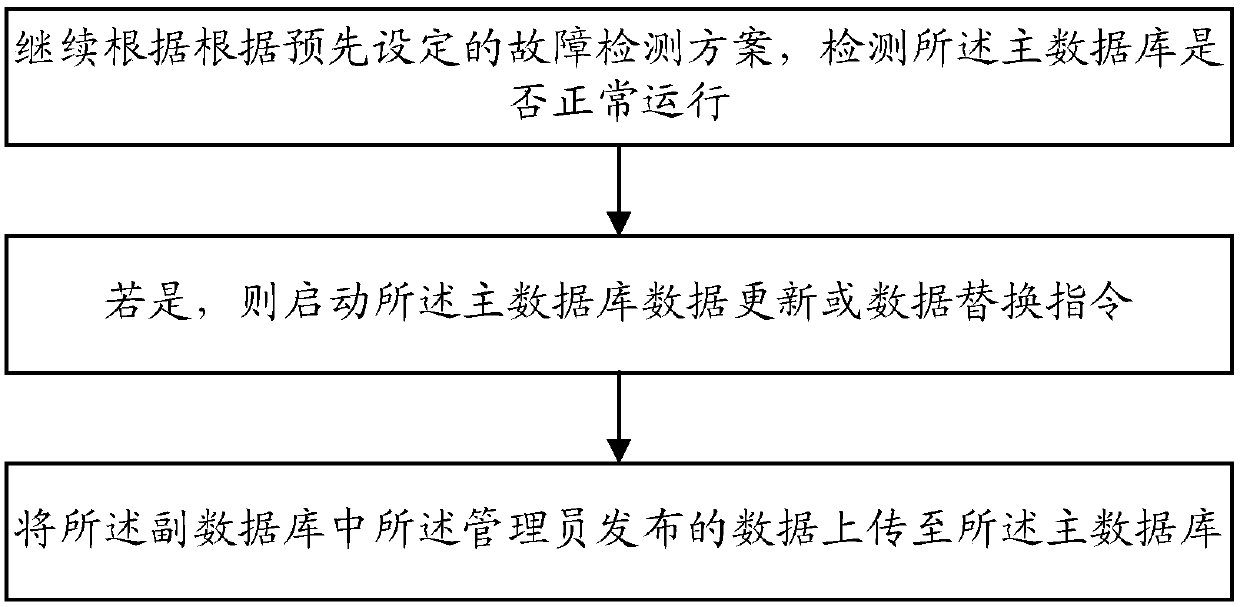
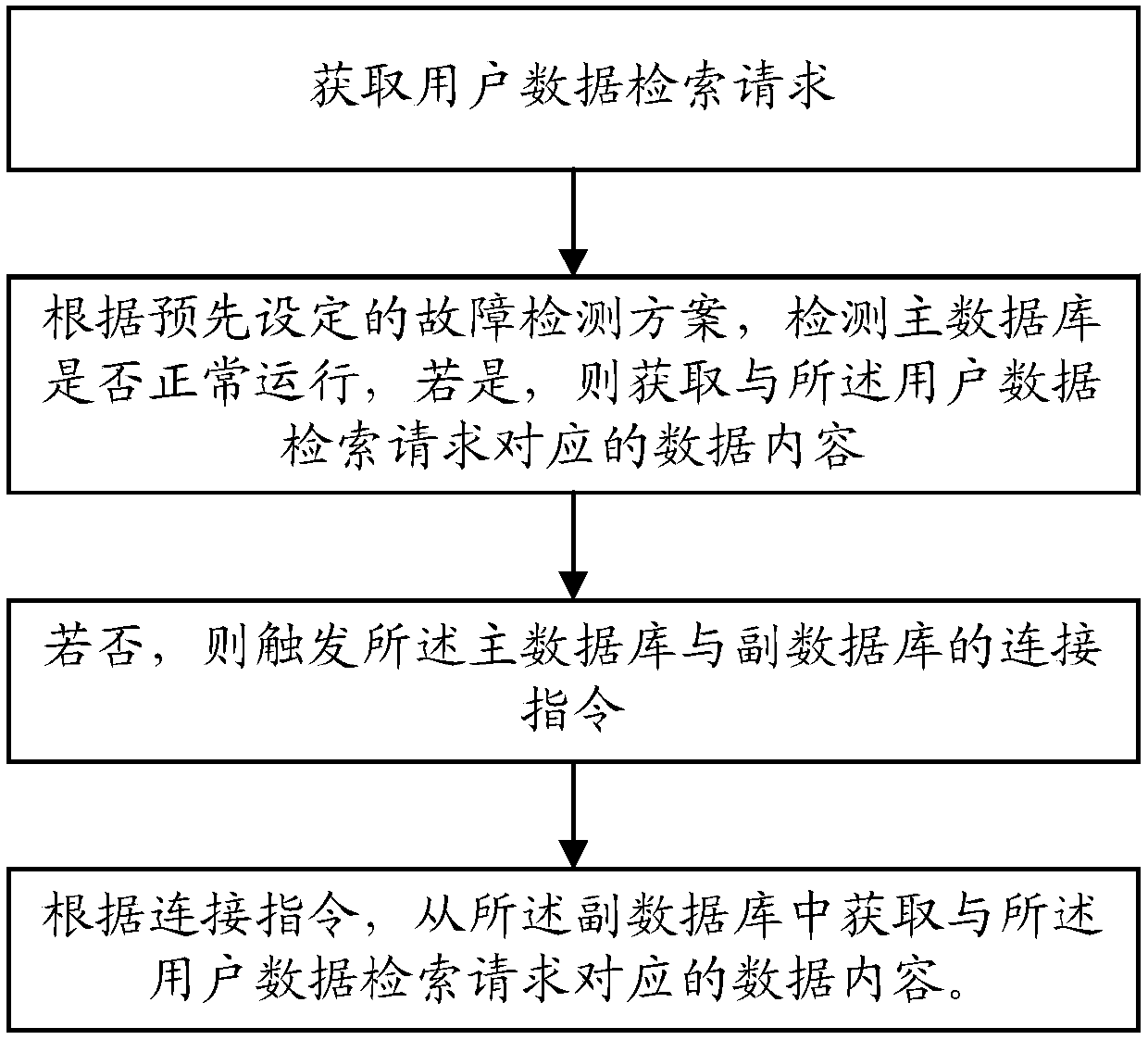
InactiveCN107786667AImplement integrity checksImprove accuracyDatabase management systemsDatabase distribution/replicationData matchingData loss
The invention discloses a data processing method, system and equipment based on a cloud platform. The data processing method comprises the following steps: acquiring an administrator data publishing instruction; detecting whether data published by an administrator are complete or not, if the data are incomplete, executing a preset early warning operation; if the data are complete, detecting whether a primary database is in normal operation or not; and if the primary database is in the normal operation, triggering a data updating or data replacing instruction, uploading the data published by the administrator to the primary database, and matching and caching the data into an accessory database connected with the primary database by virtue of an instruction. The data processing method disclosed by the invention has the advantages that whether the data published by the administrator are complete or not is detected, data processing integrity detection is realized, and precision ratio of the database is improved; further whether the primary database is in the normal operation or not is detected, a technical means of uploading to the primary database realizes a synchronous or asynchronous data uploading mode, data loss risk under abnormal condition is eliminated, and data security is improved; and finally a technology of matching and caching data into the accessory database preventsdata loss, and more importantly, user experience is improved.
Owner:八爪鱼在线旅游发展有限公司
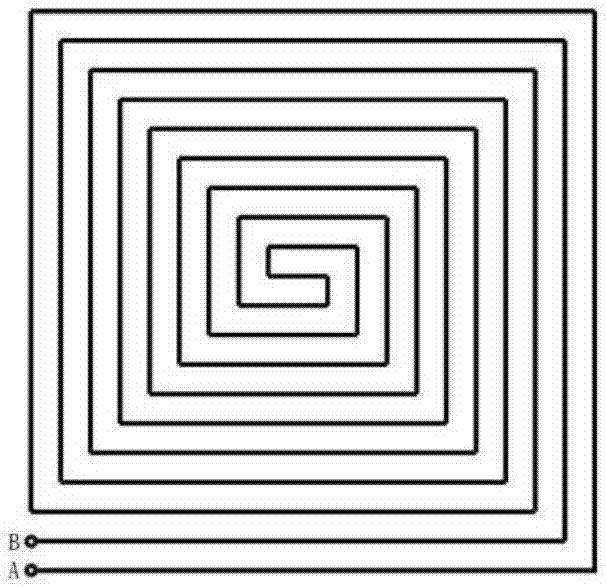
Integrity detection method and apparatus used for chip top metal protective coating
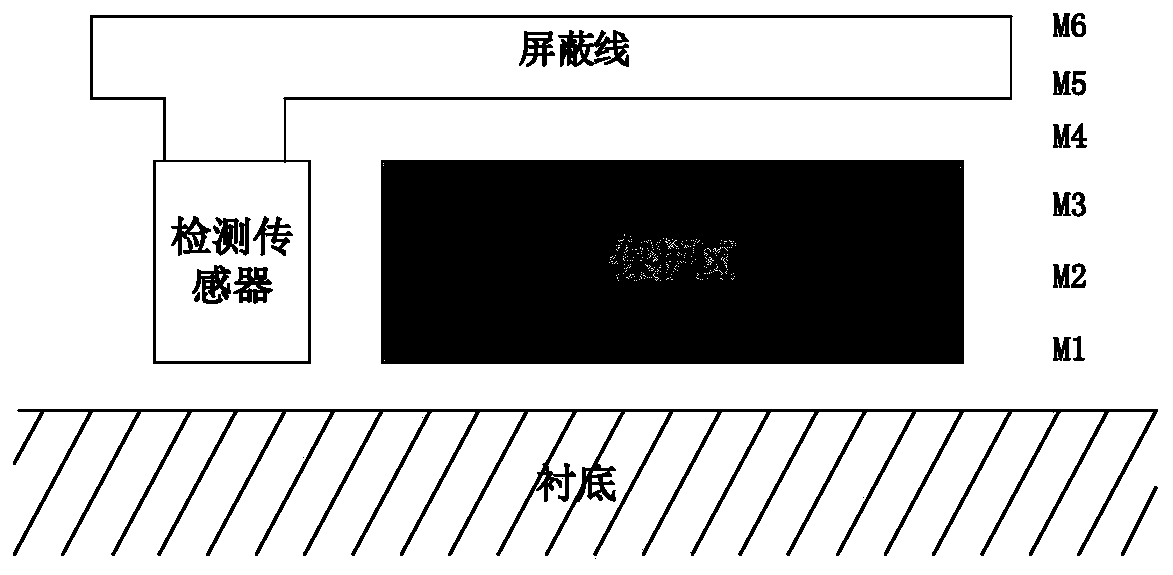
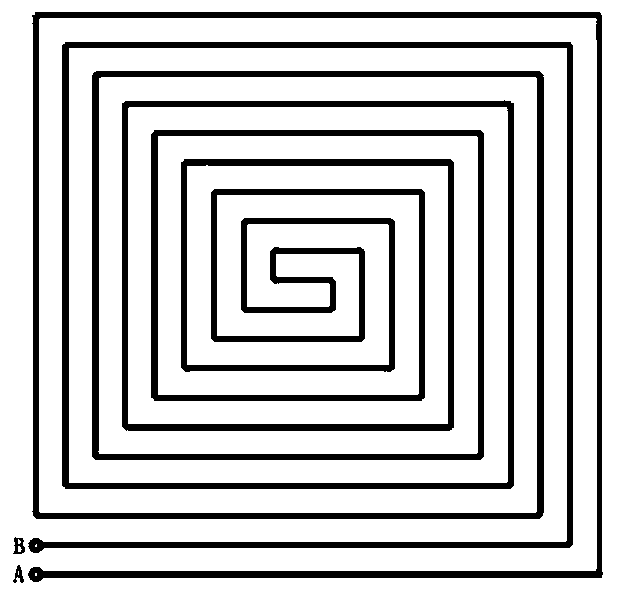
ActiveCN106503780AImprove the level of security protectionImplement integrity checksRecord carriers used with machinesEngineeringMetal
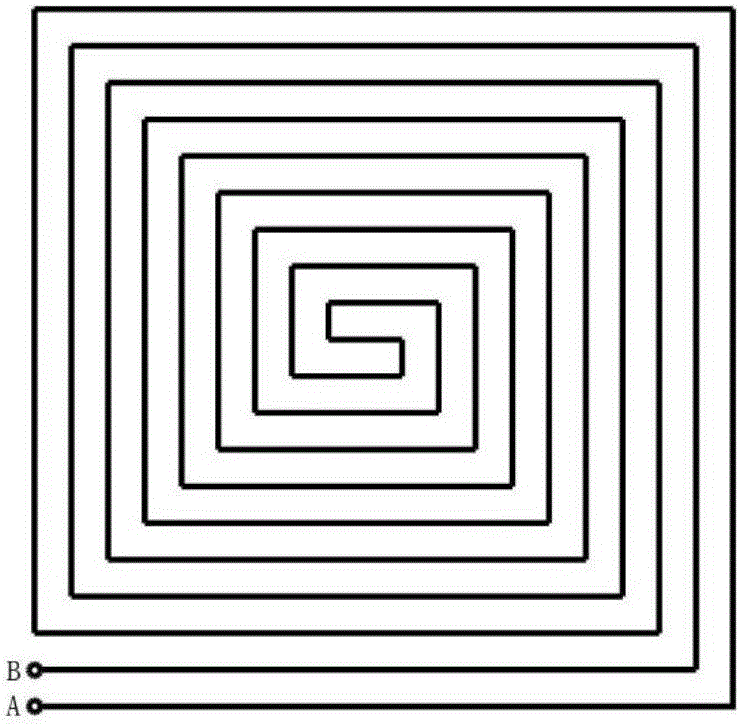
The invention relates to the field of chip security, and brings forward an integrity detection method suitable for a top metal protective coating. By use of the method, whether a metal wire of the protective coating is complete can be detected in real time, and accordingly, whether an attacker lunches a short-circuit or circuit-break attack on the protective coating by use of an FIB is determined. At the same time, the method can be applied to multiple wiring layer figure topology structures, enhances the detection sensitivity of the metal protective coating and improves the security protection level. The technical scheme is as follows: by use of the integrity detection method of the chip top metal protective coating, a spiral topology structure top metal protective coating wire, i.e., a metal wire AB is broken into four metal wires which are respectively a metal wire AC, a metal wire DH, a metal wire BE and a metal wire FG, each metal wire represents a sub protective coating, and all together, there are four sub protective coatings. The method and apparatus are mainly applied to a chip security occasion.
Owner:TIANJIN UNIV
Flexible cable process digital prototype construction system and method for spacecraft assembly
ActiveCN110162923AImplement compliance checksImplement integrity checksGeometric CADDesign optimisation/simulationComputer moduleFlexible cable
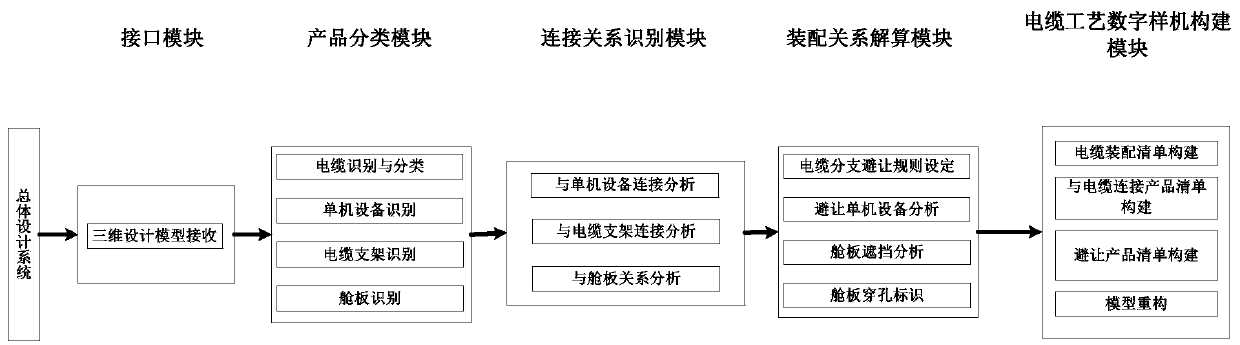
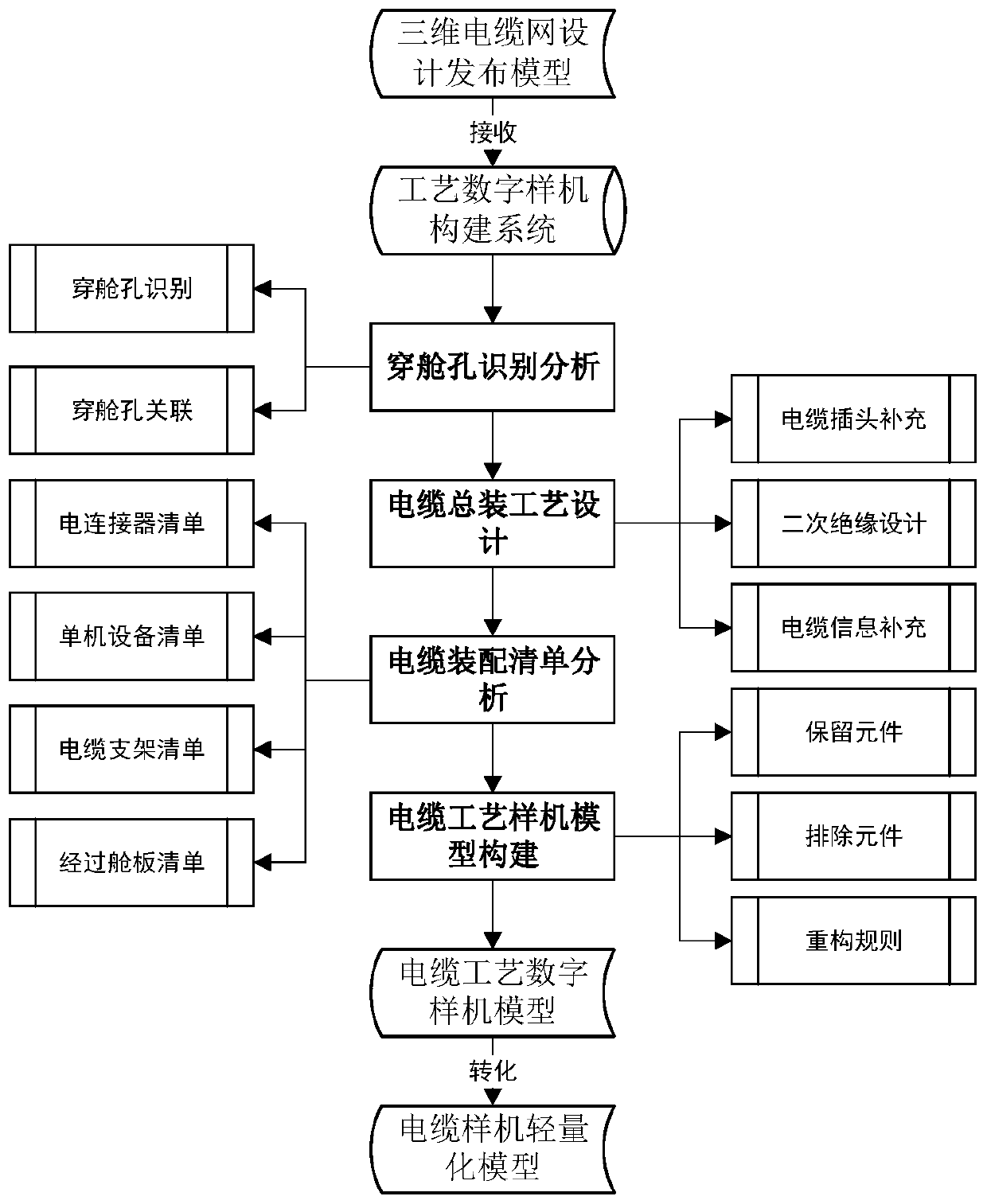
The invention discloses a flexible cable process digital prototype automatic construction system for spacecraft assembly. The flexible cable process digital prototype automatic construction system mainly comprises the following modules: an interface module, a product classification module, a connection relationship identification module, an assembly relationship resolving module and a cable process digital prototype construction module. According to the invention, rapid construction of the flexible cable process digital prototype is realized, and related requirements of cable laying are met; on the basis of simplifying an overall unit cable design model, complete information required by cable laying is reserved, and the probability of quality occurrence in the cable laying process in narrow spaces such as satellites is reduced.
Owner:BEIJING INST OF SPACECRAFT ENVIRONMENT ENG
Label based cross-domain data transmission protection method
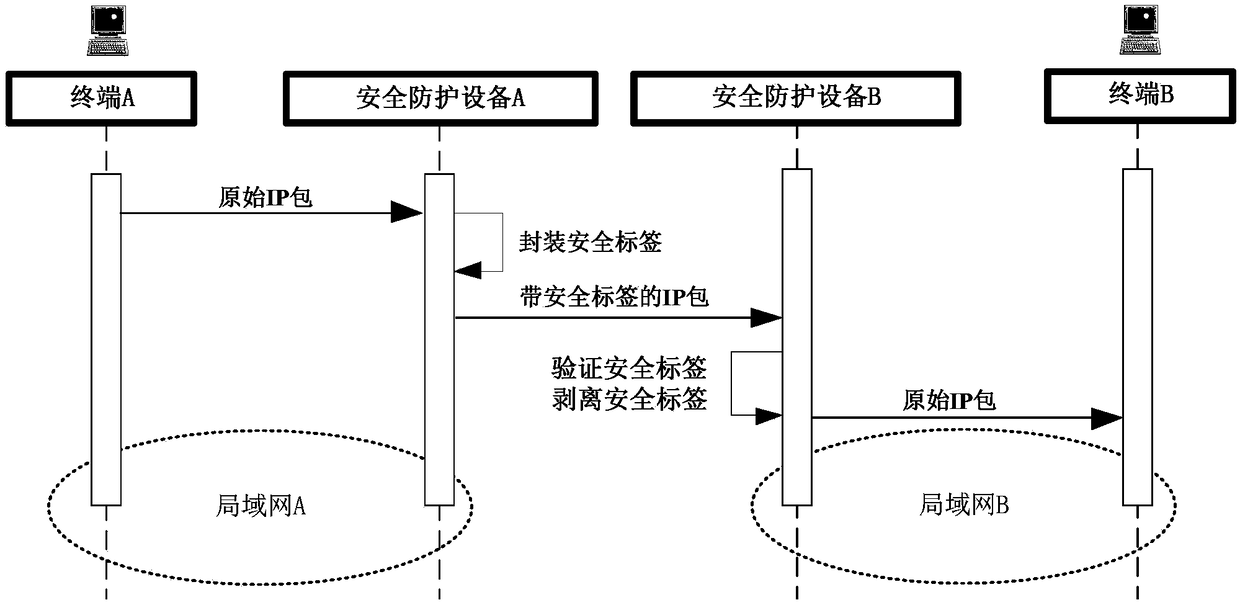
InactiveCN108234468AStrong scalabilityImplement anti-replay attackTransmissionData transmissionTelecommunications link
The invention discloses a label based cross-domain data transmission protection method. Safety protection devices are deployed at a network border and are connected in series in a communication link;a safety protection device at a transmitting terminal builds a safety label and adds the safety label to the tail of an original IP packet for transmission; and a safety protection device at a receiving terminal verifies the original IP packet by utilizing the safety label and sends out the original IP packet which passes verification. As the safety label is attached at the tail of the data message for transmission, so that identification and processing of a network device on a transmission path for data is not affected, and the label based cross-domain data transmission protection method hasa transparent transmission characteristic. Algorithm identifiers, label length and version number in the label have good expansibility. Safety label values designed in labels can be used for realizingcompleteness verification of data packets; serial number designed in the label can be used for realizing anti-replay attack of messages. The label based cross-domain data transmission protection method can be applied to a network safety product, and has the advantages of being safe, reliable and practical.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
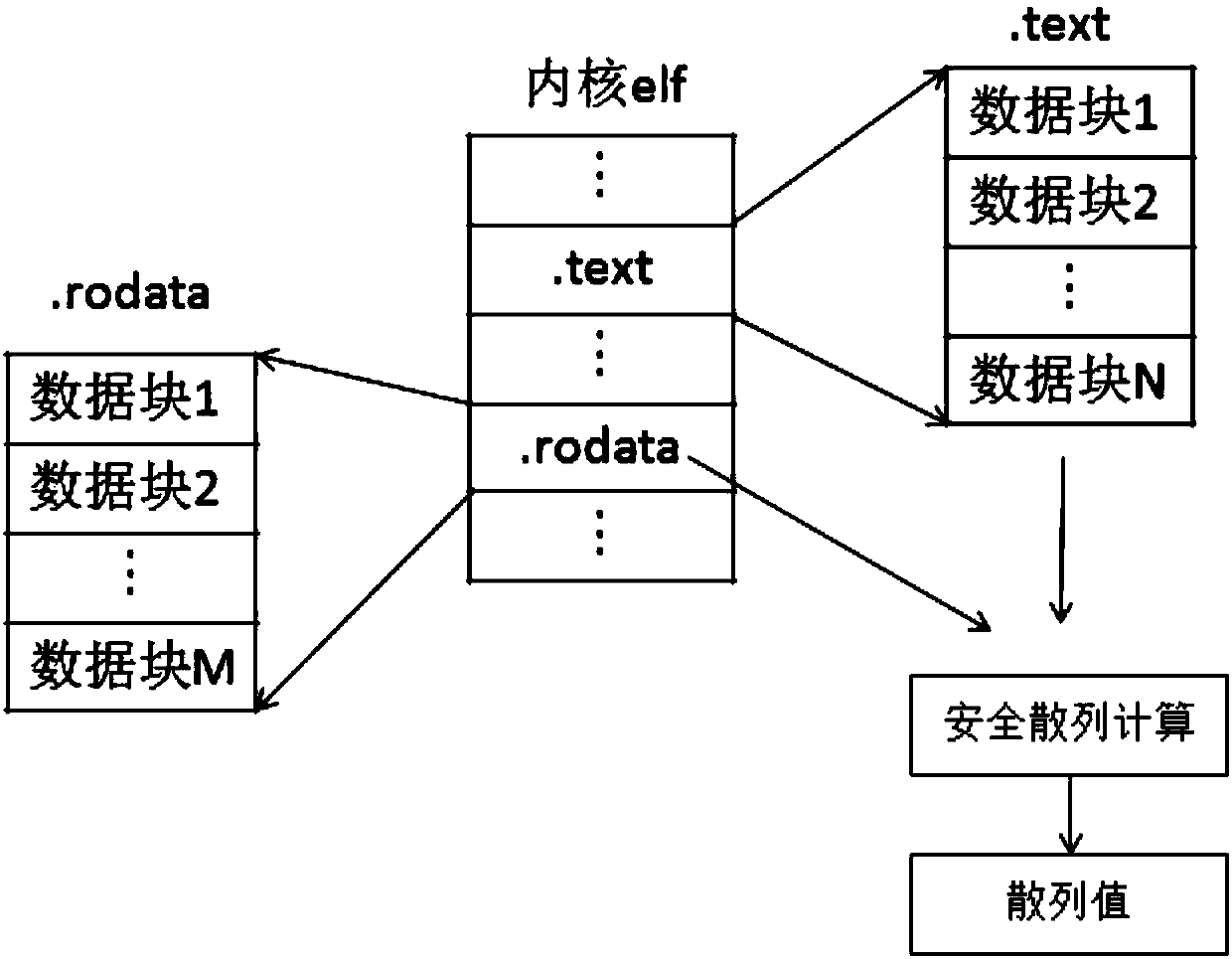
Integrity checking method during kernel running anda computer readable storage medium
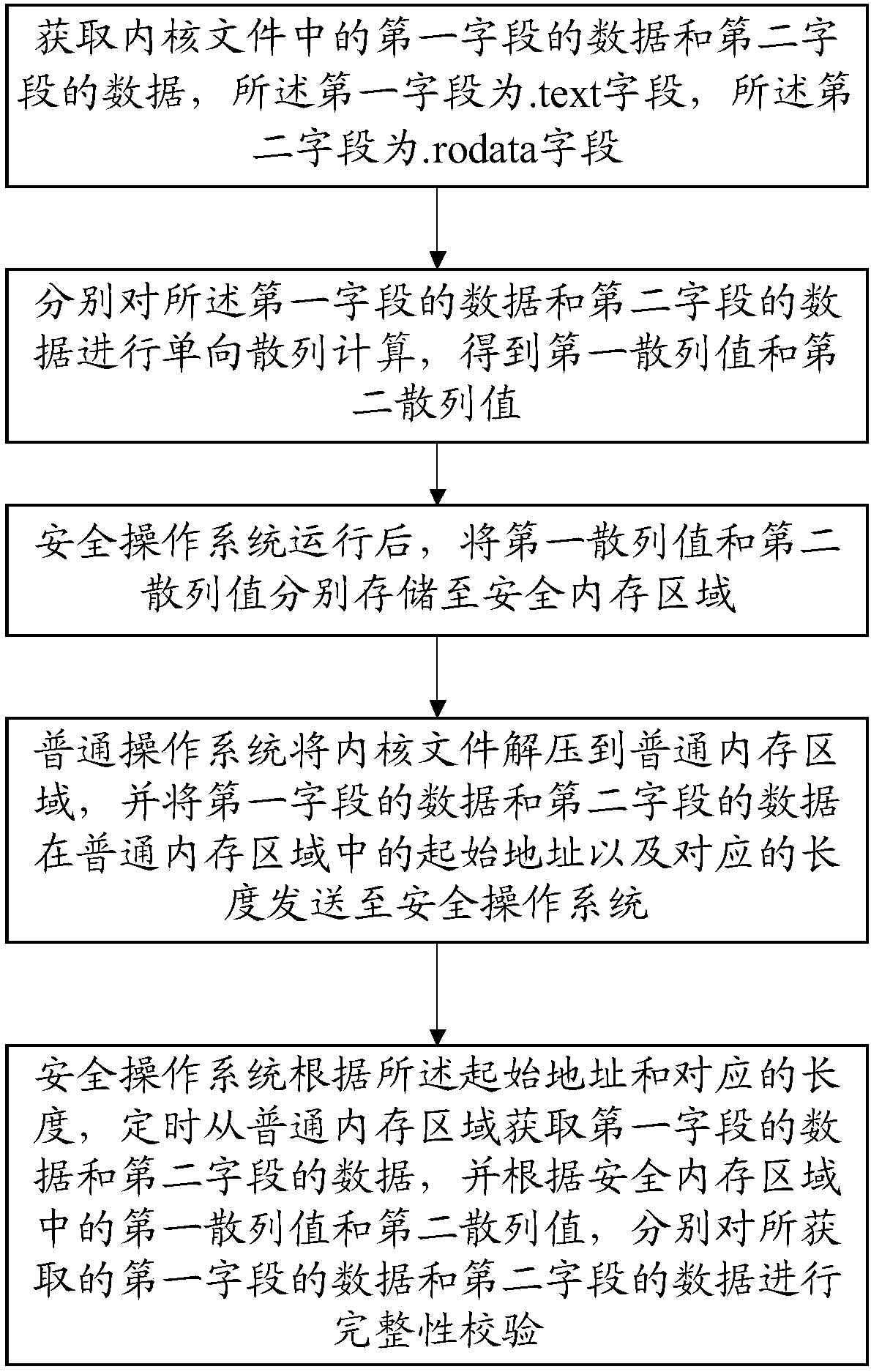
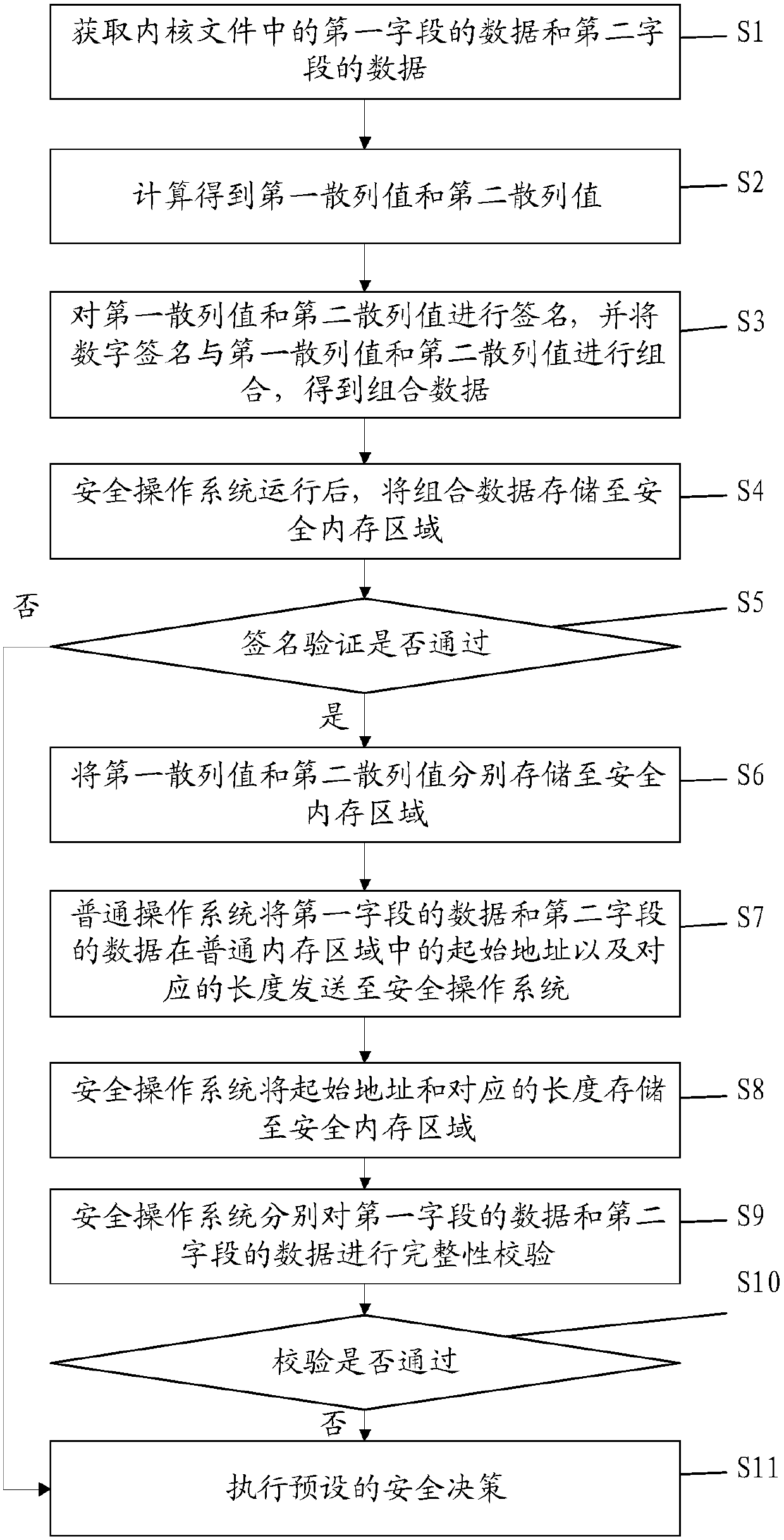
PendingCN109753788AEffective protectionImplement integrity checksPlatform integrity maintainanceComputer hardwareOperational system
The invention discloses an integrity checking method during kernel running and a computer readable storage medium, and the method comprises the steps: obtaining the data of a first field and the dataof a second field in a kernel file, and carrying out the one-way hash calculation of the data, and obtaining a first hash value and a second hash value; after the secure operating system runs, storingthe two hash values into a secure memory area; the common operating system sending the initial addresses and the corresponding lengths of the data of the first field and the data of the second fieldin the common memory area to the secure operating system; and the security operation system acquiring the data of the first field and the data of the second field from the common memory area at regular time, and performing integrity verification on the data according to the two hash values in the security memory area. According to the method, integrity verification can be performed on the runningkernel data, and it is ensured that when the corresponding region of the kernel is tampered, the corresponding region can be found in time and a corresponding security strategy is adopted.
Owner:XIAMEN YAXON NETWORKS CO LTD
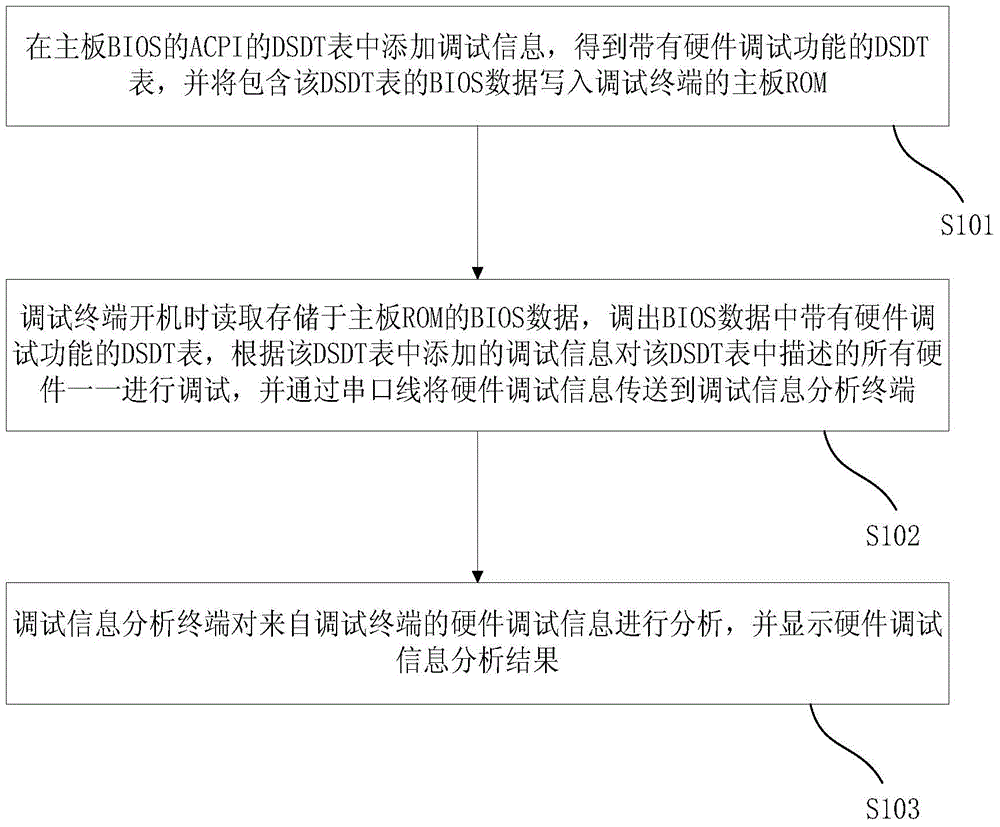
DSDT-based debugging method and debugging system
InactiveCN106201790AImplement integrity checksComprehensive hardware debugging resultsDetecting faulty computer hardwareSoftware testing/debuggingInformation analysisOperational system
The invention discloses a DSDT (Differentiated System Description Table)-based debugging method and debugging system. The system comprises a debugging terminal and a debugging information analysis terminal connected with the debugging terminal through a serial port line. The debugging terminal is used for reading BIOS (Basic Input Output System) data pre-stored in a mainboard ROM (Read Only Memory) during system startup, calling out a DSDT added with debugging information in the BIOS data, debugging all hardware described in the DSDT one by one according to the debugging information added in the DSDT, and generating hardware debugging information. The debugging information analysis terminal is used for receiving the hardware debugging information from the debugging terminal through the serial port line, analyzing the hardware debugging information, and displaying a hardware debugging information analysis result. The DSDT-based debugging method and debugging system can be suitable for different operation system environments, and can realize integrity detection of the hardware in the debugging terminal and obtain the quick, comprehensive, accurate and reliable debugging information analysis result.
Owner:SHENZHEN PRAFLY TECH
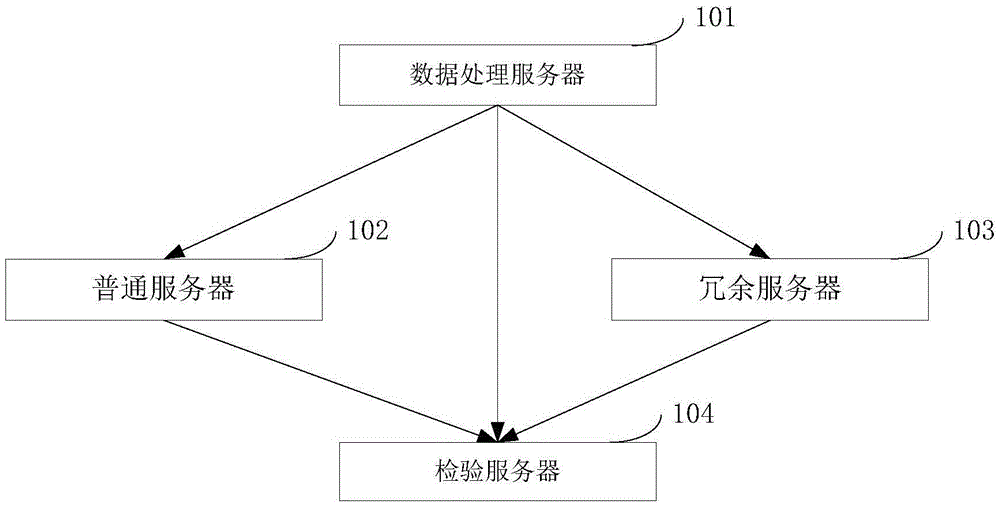
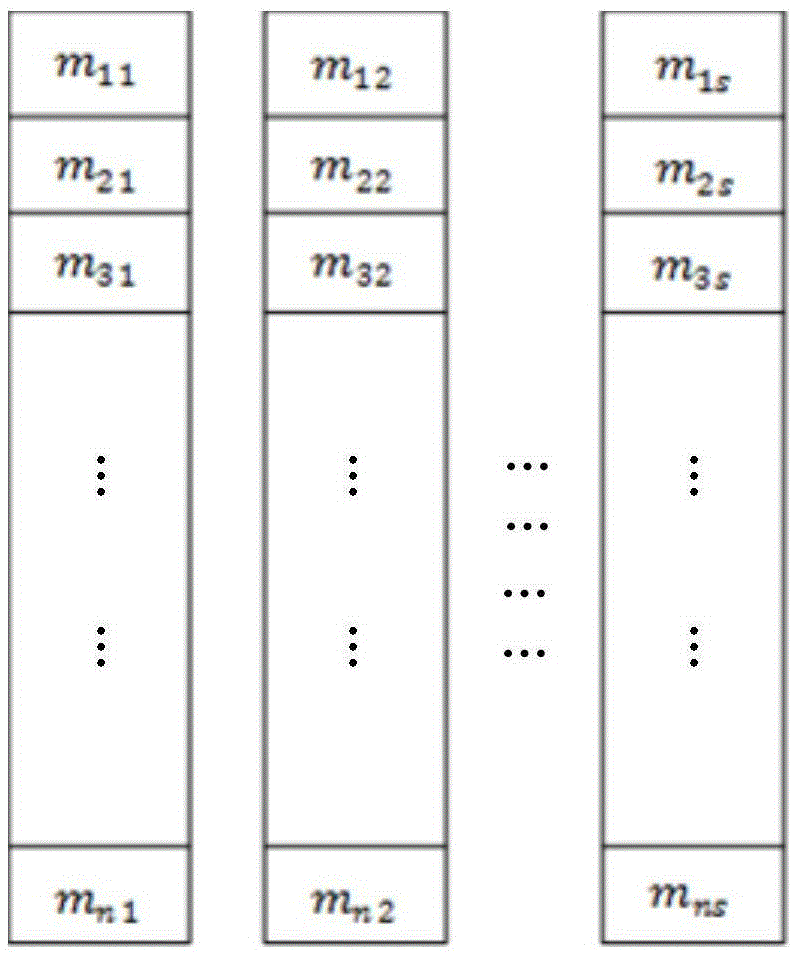
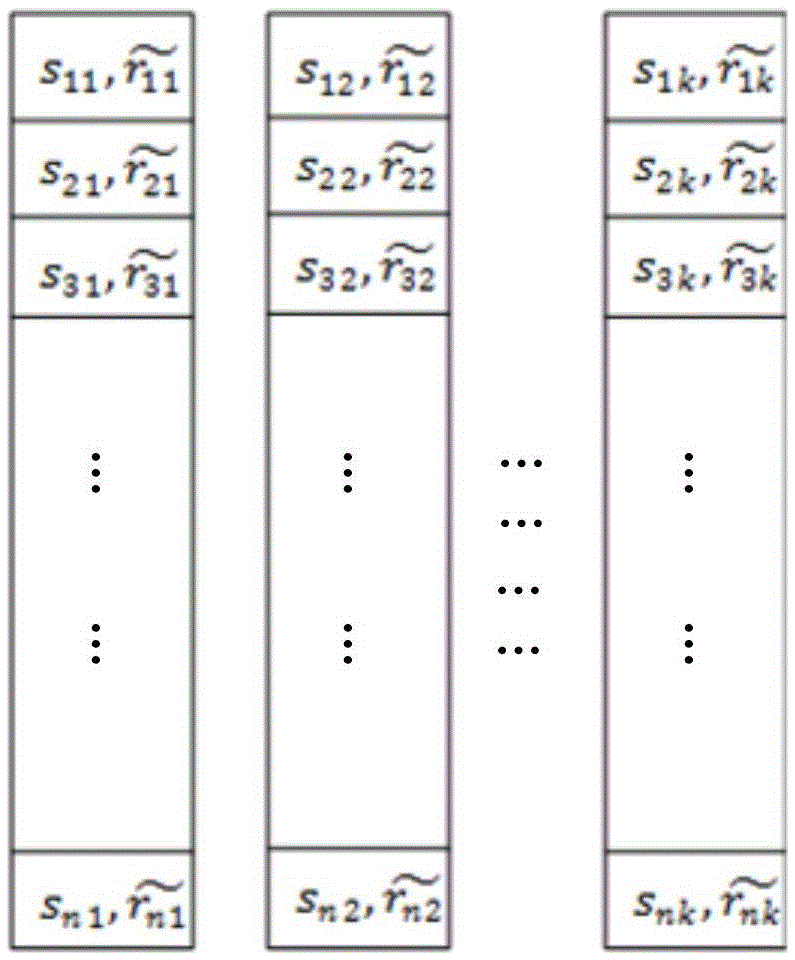
Data integrity testing system and method
The invention provides a data integrity testing system comprising a data processing server, for generating a matrix M according to data to be tested and storing the matrix in s ordinary servers, wherein the data processing server is also used for obtaining a matrix R according to a pseudorandom function f, a key kprf and seeds Sip<ver>, obtaining a matrix R<-> according to the matrix R and a generator g, obtaining a redundancy matrix S according to the matrix M, an s*k-order Cauchy matrix A and the matrix R, and storing the redundancy matrix S and the matrix R<-> in k redundant servers; the data processing server is also used for obtaining a matrix V according to the Cauchy matrix A and the generator g and transmitting the matrix V to a testing server; the testing server is used for testing the data to be tested and outputting test results. The method implements the testing for data integrity while protecting the privacy of information, and generates the redundancy matrix S and the matrix R<-> for data testing and restoration.
Owner:CHINA AGRI UNIV
Data integrity checking method for fine grain data on finite domain vector space
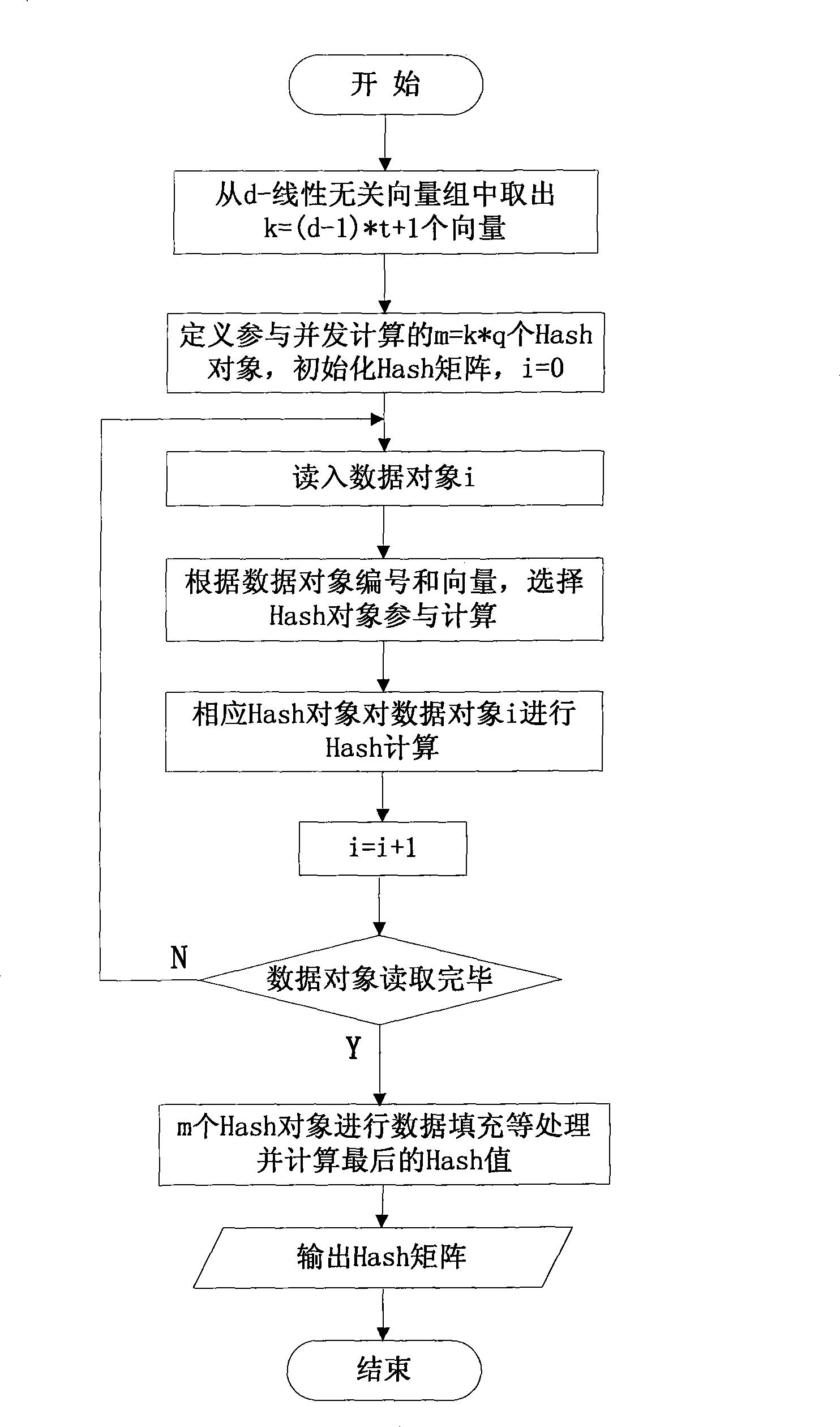
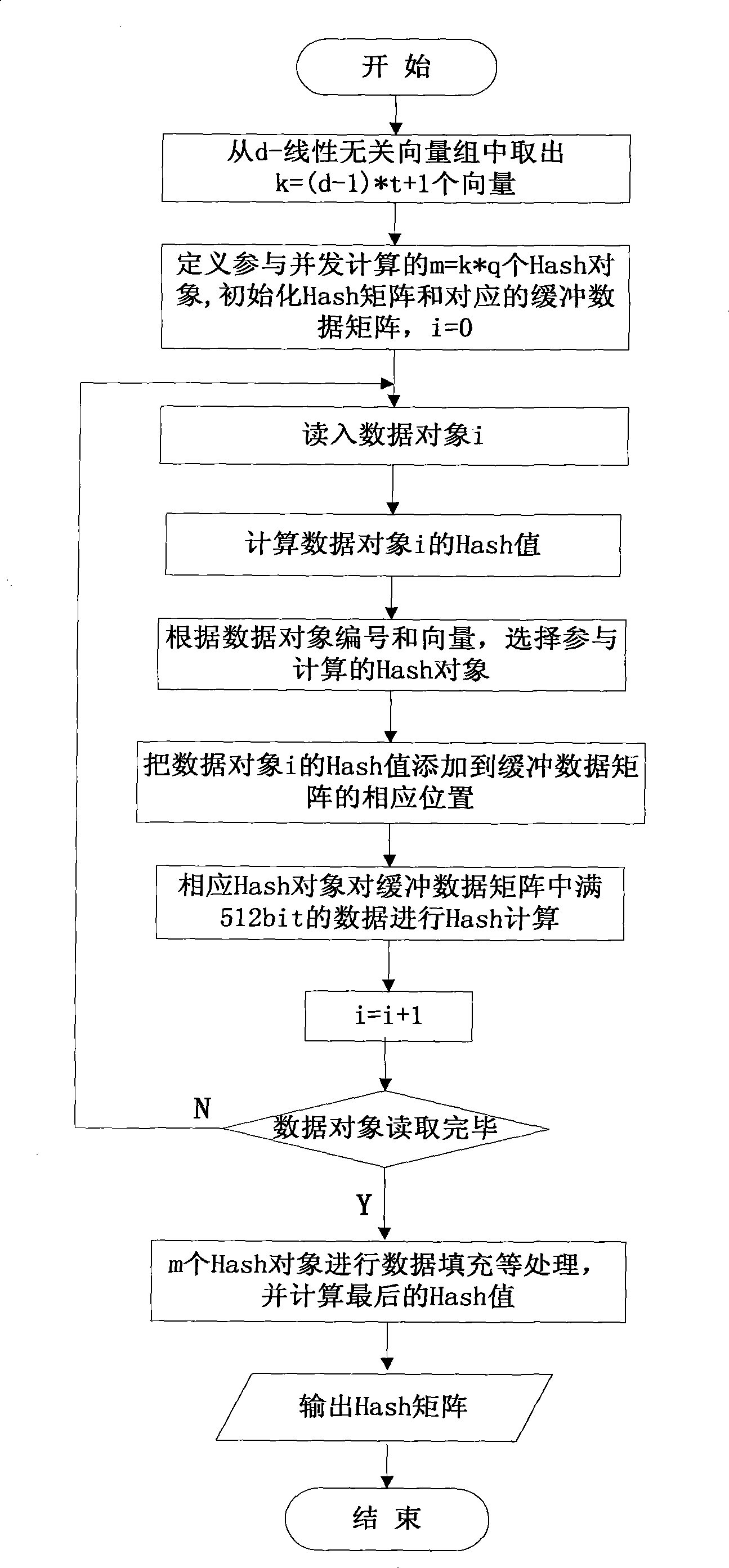
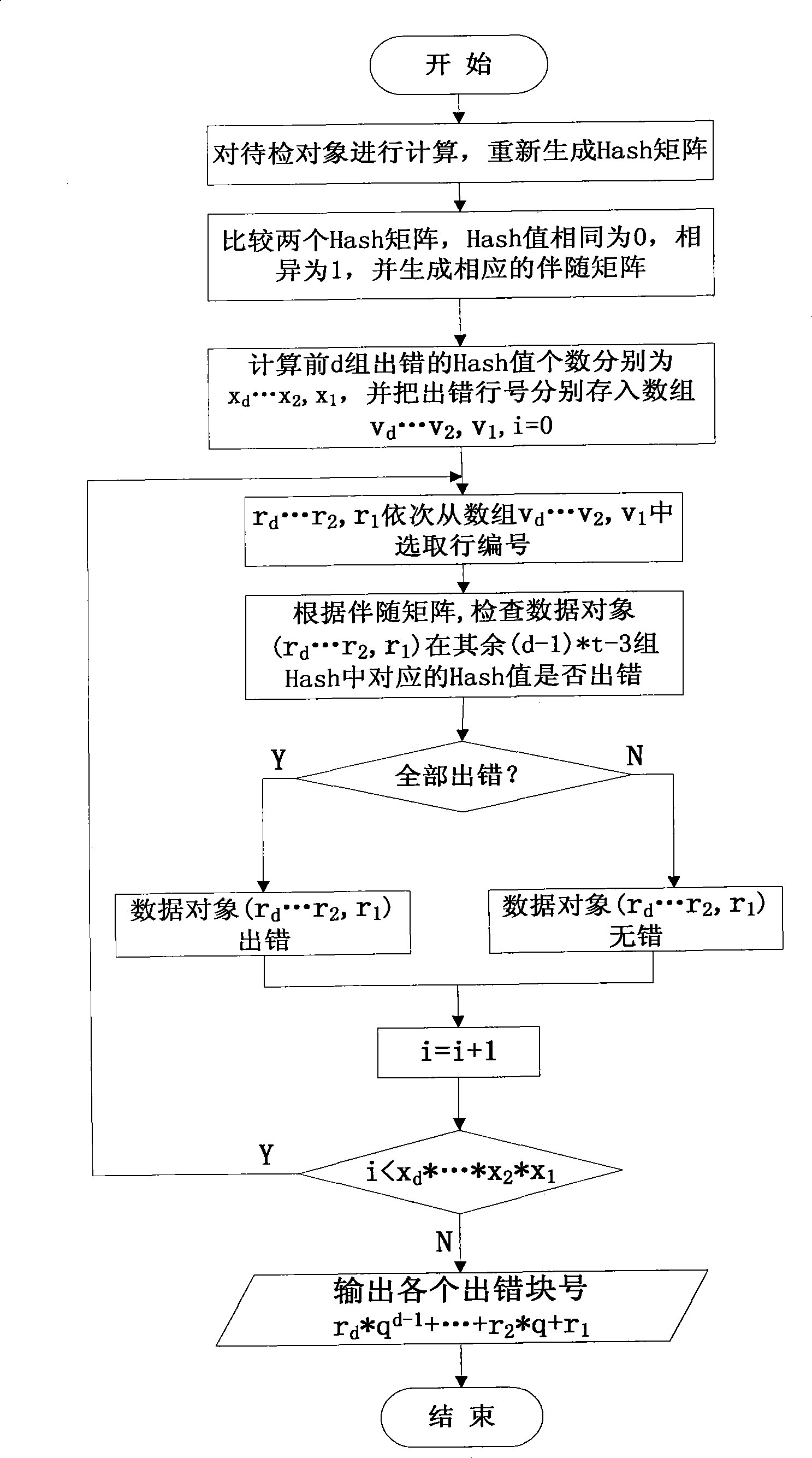
InactiveCN101477599AImplement integrity checksImplement data compressionDigital data protectionData integrityInformation security
The invention discloses a method for checking the integrity of fine-grained data in vector space of finite fields, which belongs to the field of computers and information security. That the integrities of more data objects are indicated by utilizing fewer testing data is realized at a fine-grained level; and squeezed degree can be set and quantity of error data object can be accurately indicated according to the requirements of the user. The method for checking the integrity of fine-grained data ensures that source data objects to be checked are mapped to d-dimension vector space on a finite field GF q; all data objects are uniformly divided; and uniform crossover is realized among different division. A group of Hash is formed by a division, and finally an all-round scheme for checking the integrity of data is obtained. The invention ensures that memory space for storing integrity check data and network bandwidth for transmitting the integrity check data are saved; and the method is applicable to occasions, such as mass data integrity check, data security verification in electronic data service, and original evidence obtaining integrity and electronic data evidence fix.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
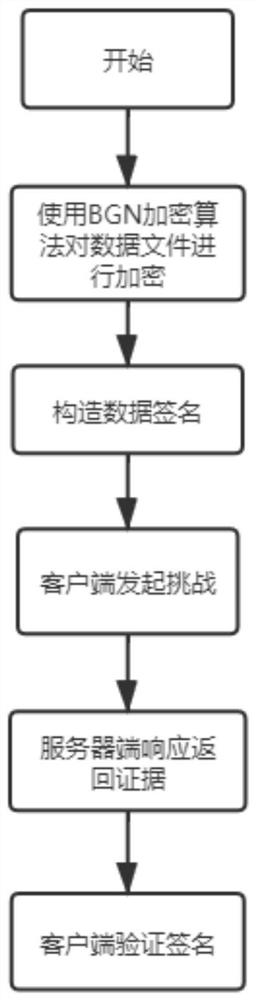
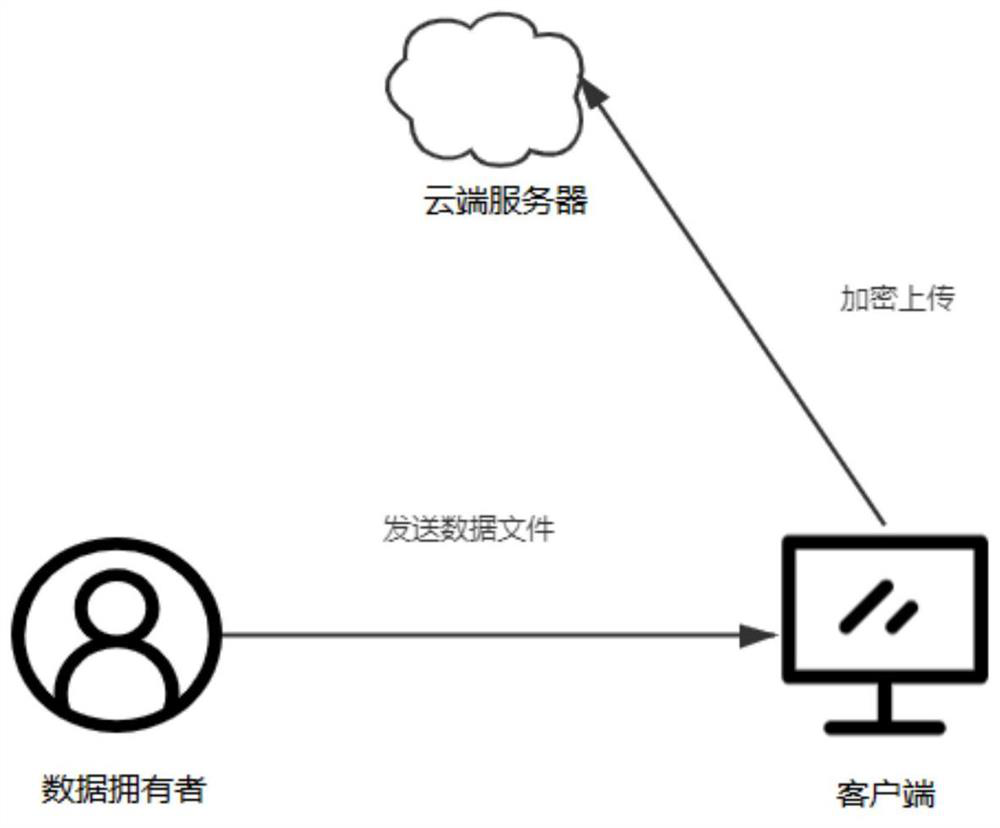
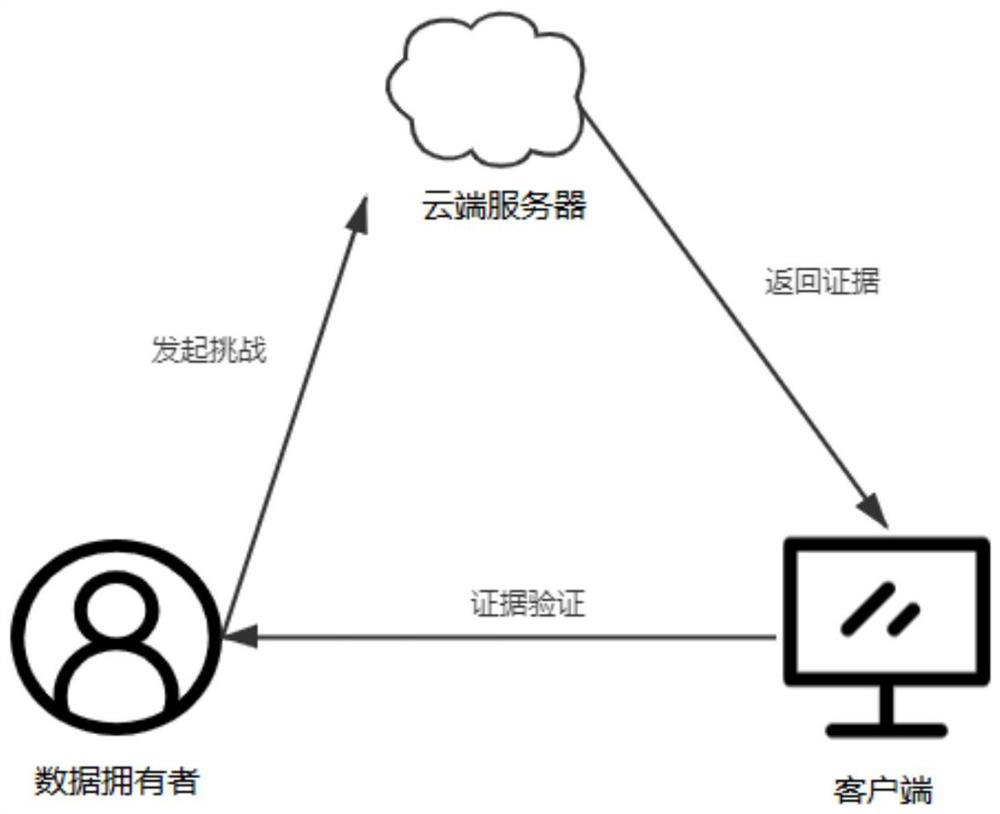
Data file encryption and integrity verification method and system for untrusted server environment
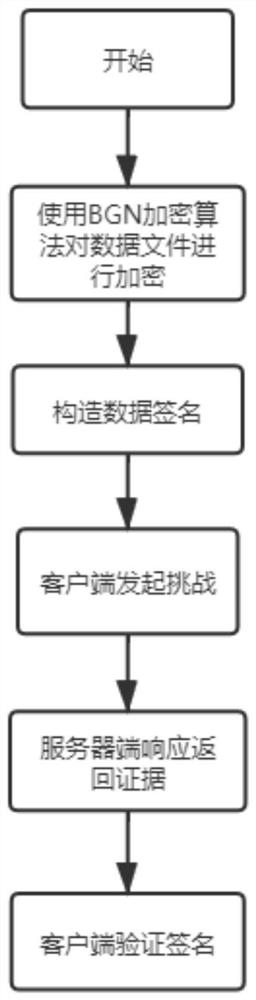
ActiveCN112491529AGuaranteed privacyGuaranteed availabilityKey distribution for secure communicationDigital data protectionData privacy protectionCiphertext
The invention provides a data file encryption and integrity verification method and system for an untrusted server environment, and relates to the technical field of data privacy protection, and the method comprises the steps: 1) initializing a system; 2) generating public and private keys of a BGN homomorphic encryption algorithm; 3) constructing public and private keys of the data signature; 4)encrypting the data file by adopting a BGN homomorphic encryption algorithm public key; 5) respectively constructing labels for all file blocks in the data file according to the private key of the data signature; 6) uploading the set of encrypted files and labels to a cloud server; 7) sending a file integrity challenge to the cloud server to return a label and a file block sum; 8) verifying the label sum by using the file block sum and the public key of the data signature so as to judge the integrity of the ciphertext file stored in the cloud server. According to the method, a BGN homomorphicencryption algorithm and a PDP data holding proof protocol are combined, data signatures are constructed to achieve integrity check of the encrypted files, and privacy protection and availability of the data files in an untrusted server environment are improved.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY +2
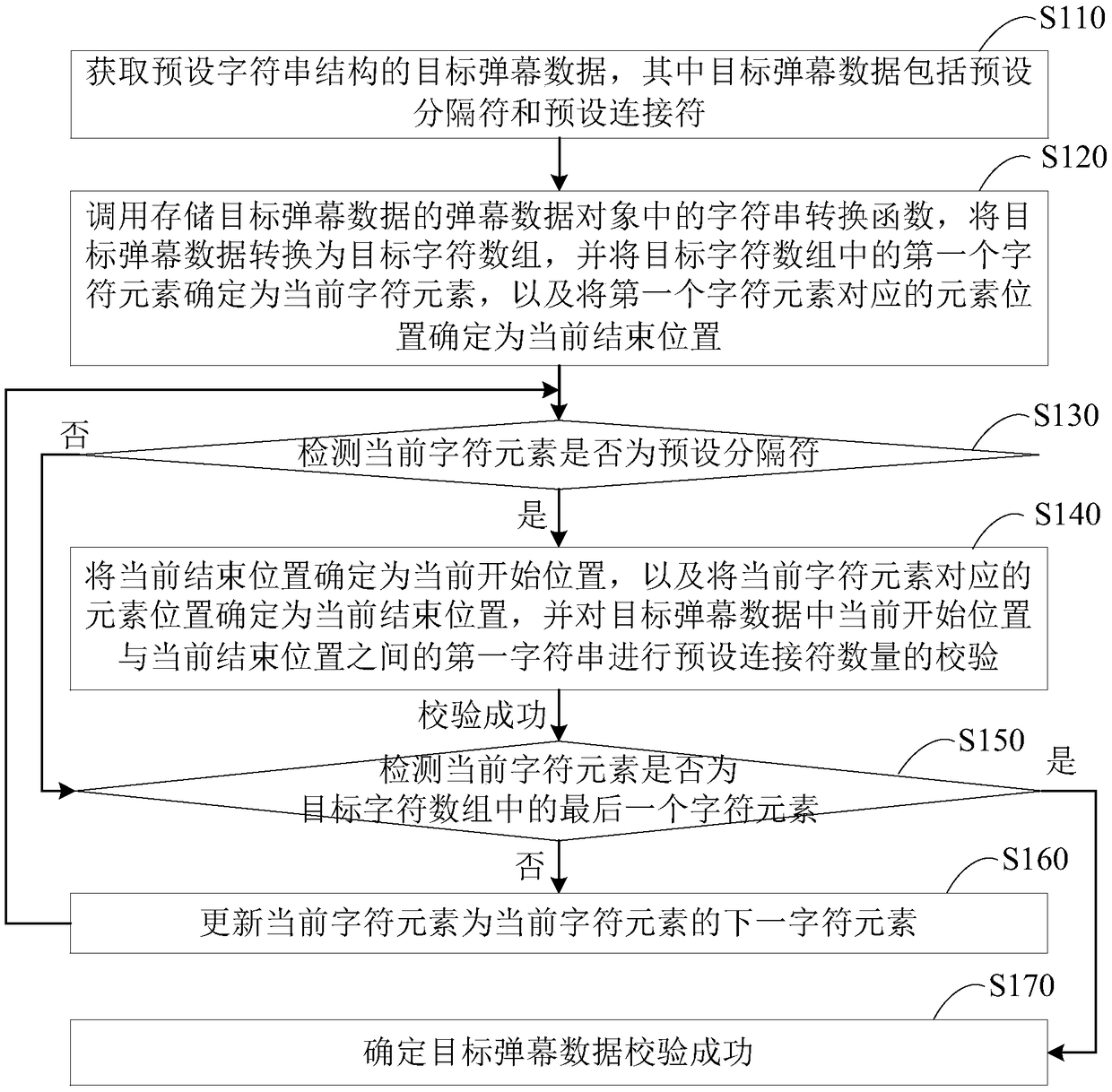
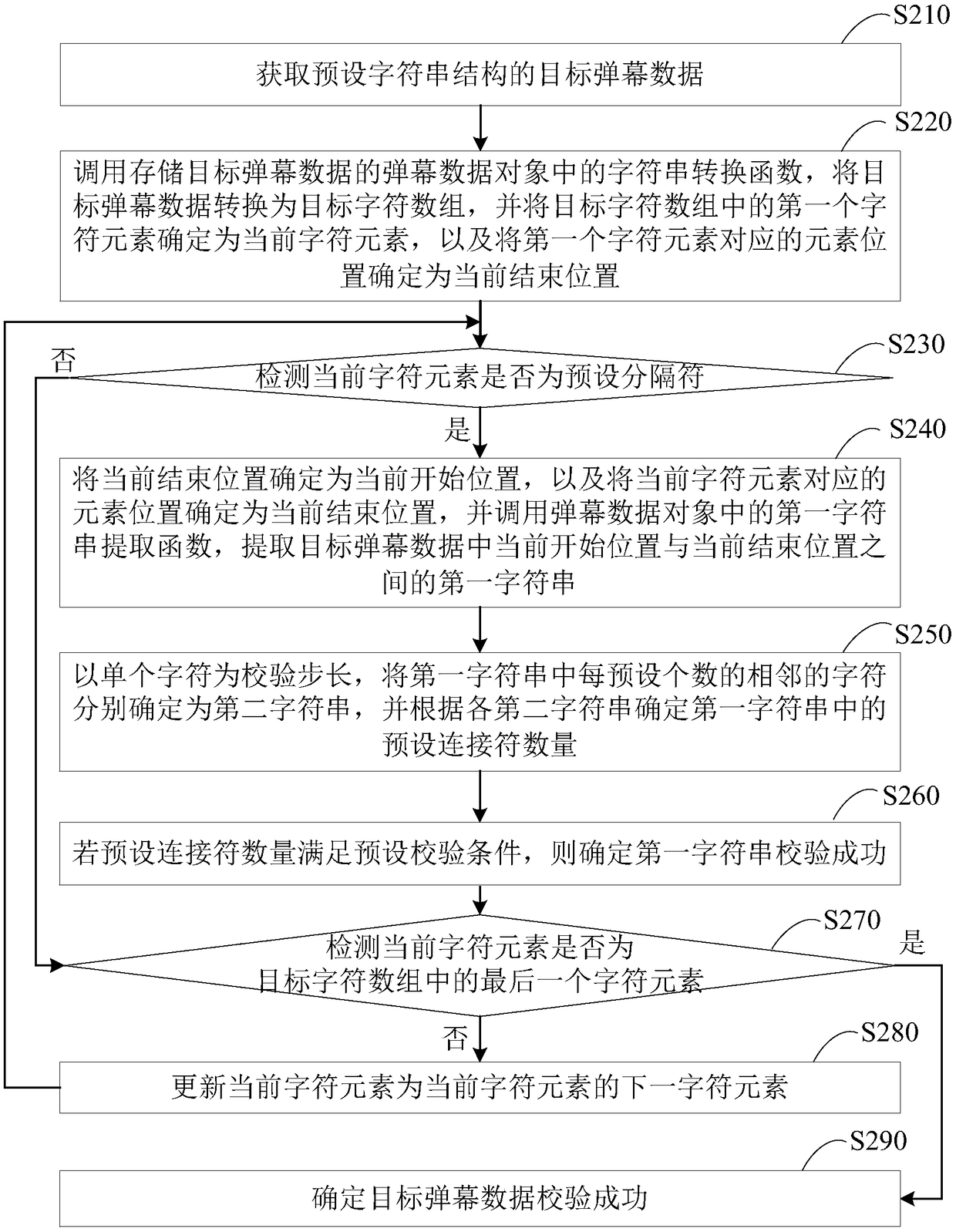
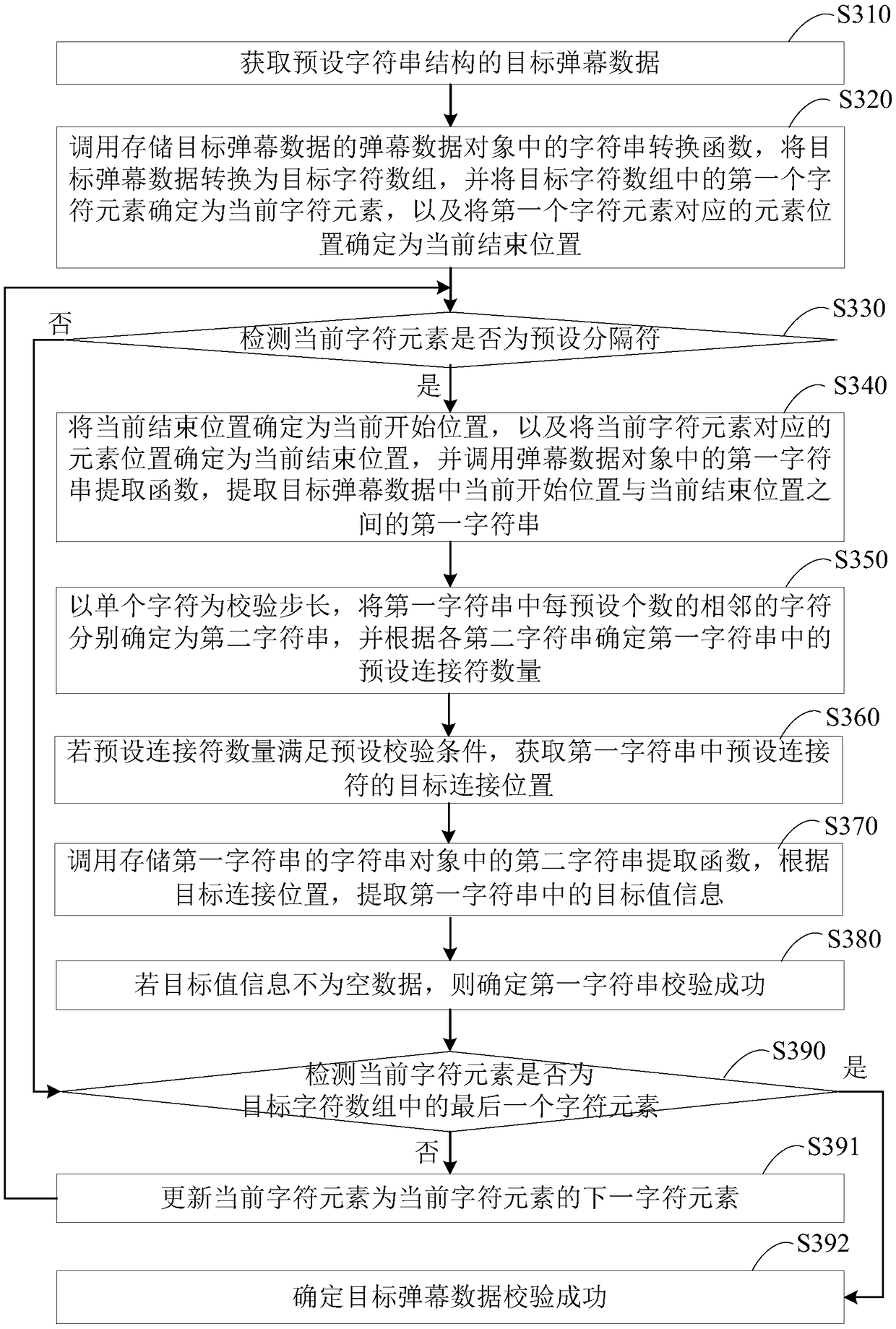
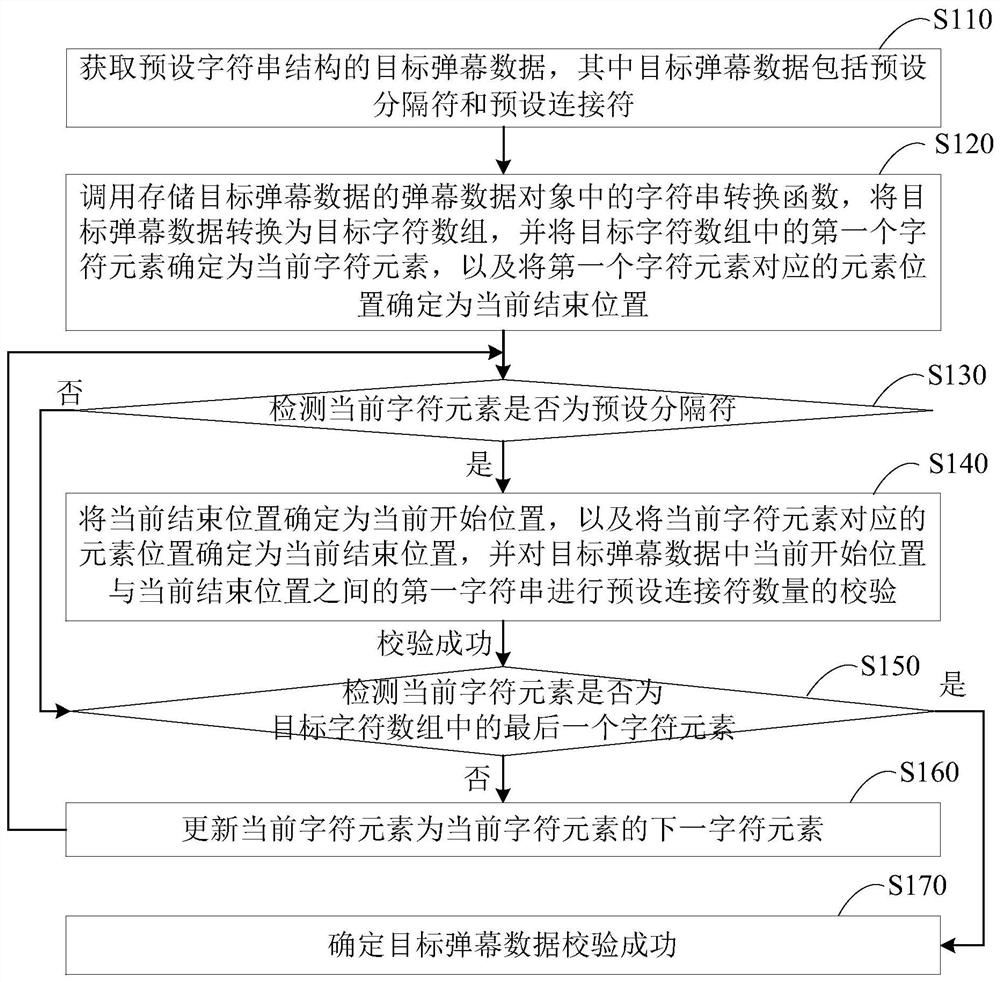
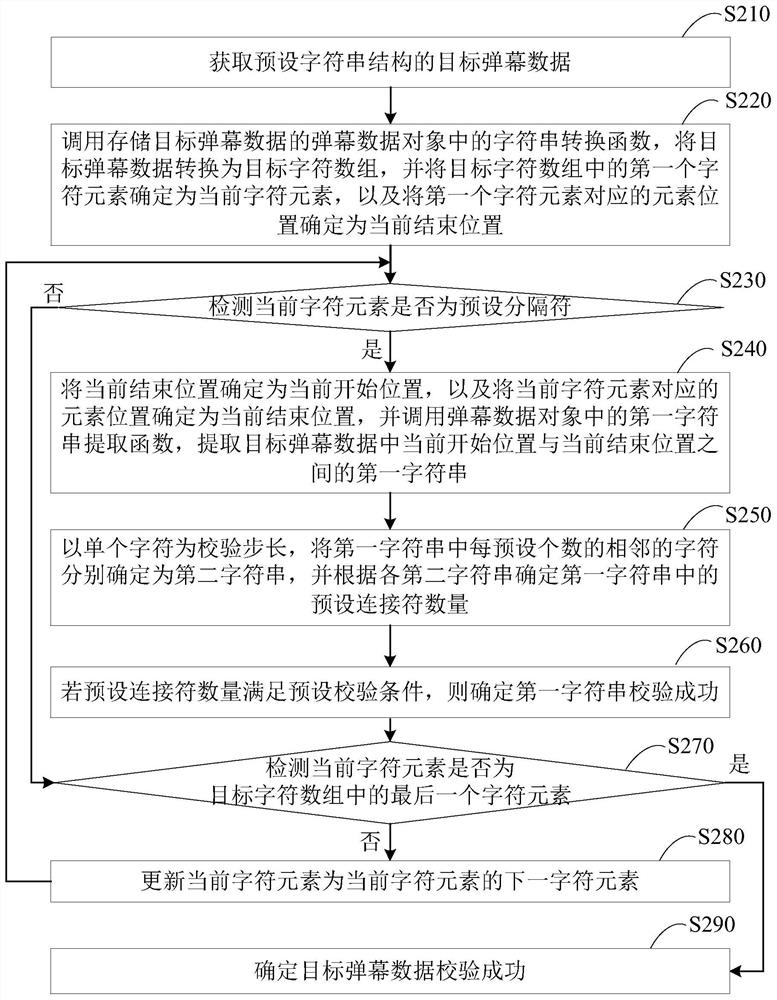
Integrity checking method and device for bullet screen data, terminal and memory medium
ActiveCN109413450AImplement integrity checksAvoid problems like crashesDigital data information retrievalSelective content distributionArray data structureComputer terminal
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Data storage method and device, data verification method and device, equipment and storage medium
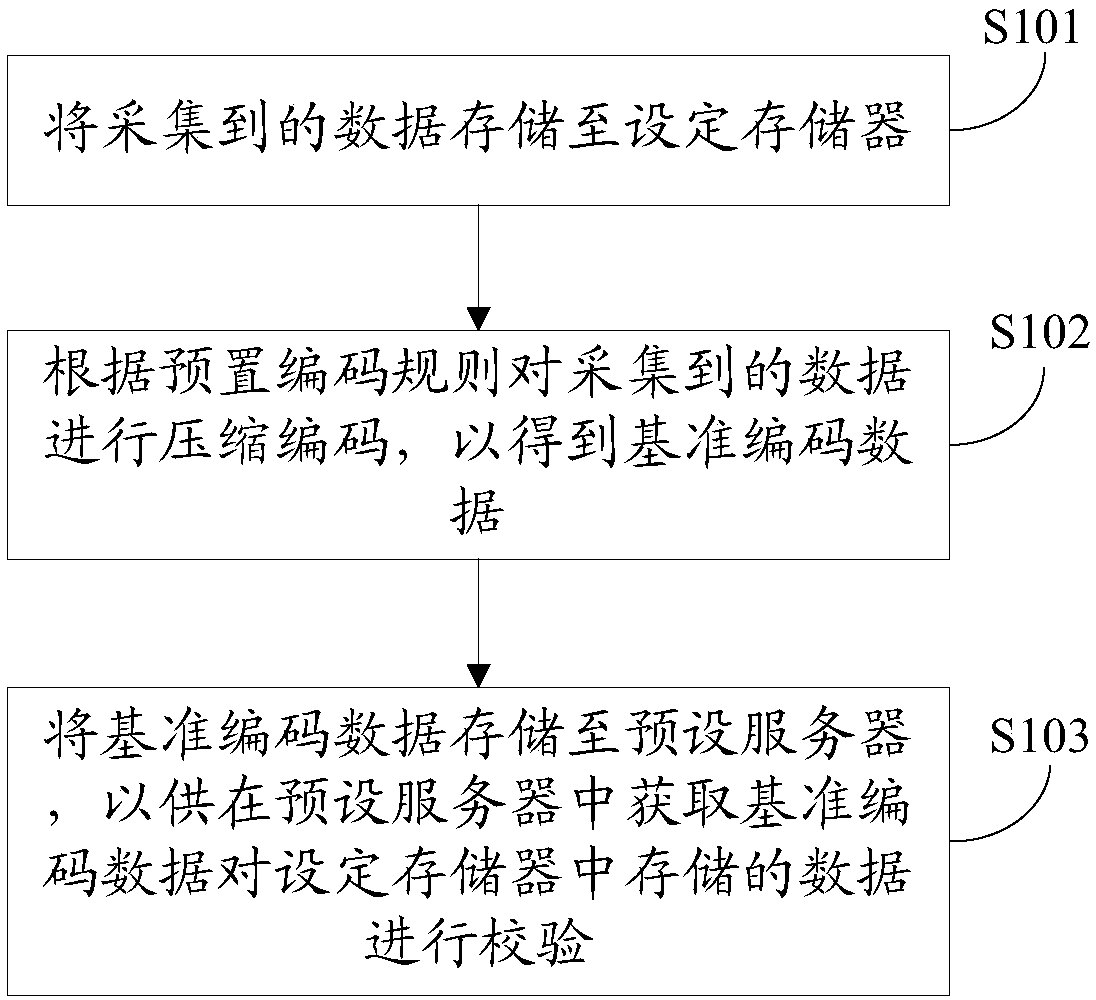
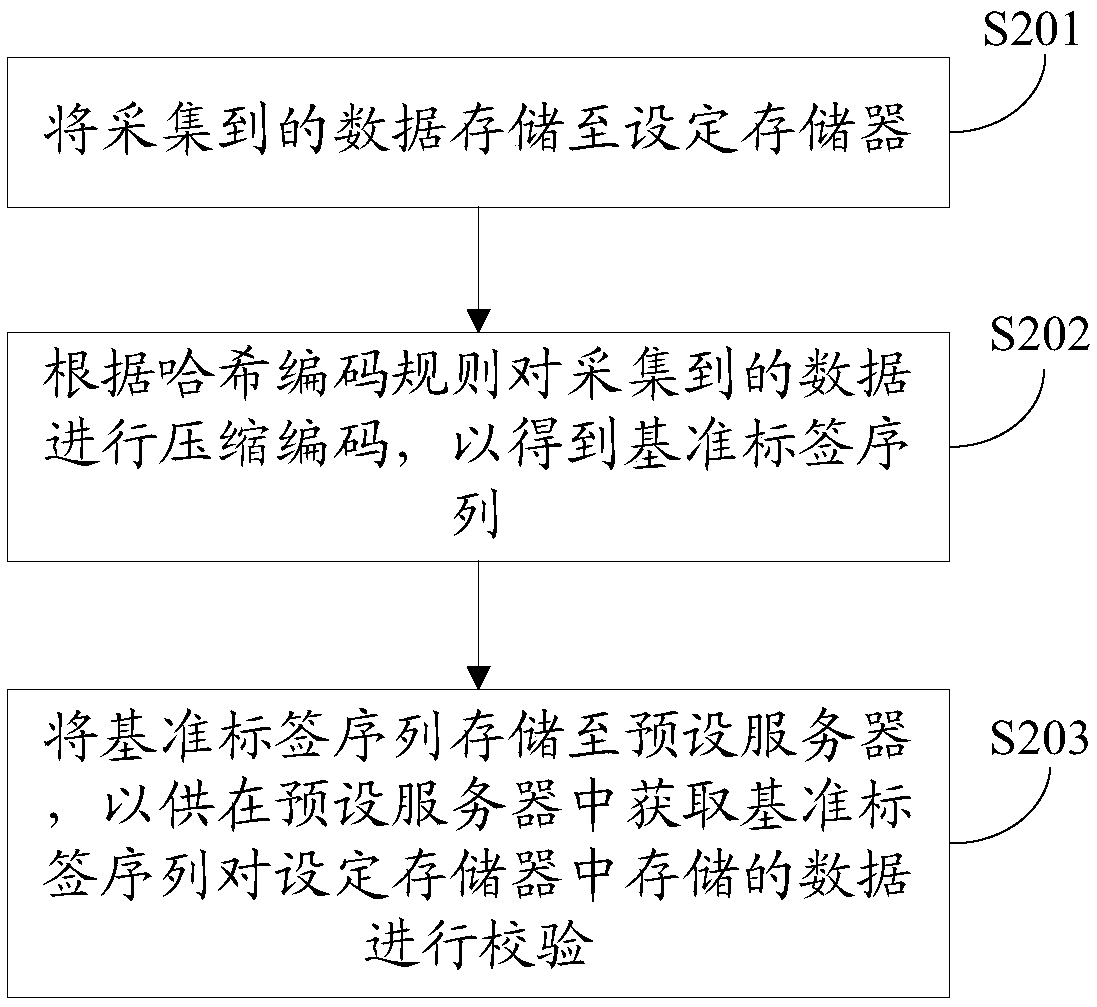
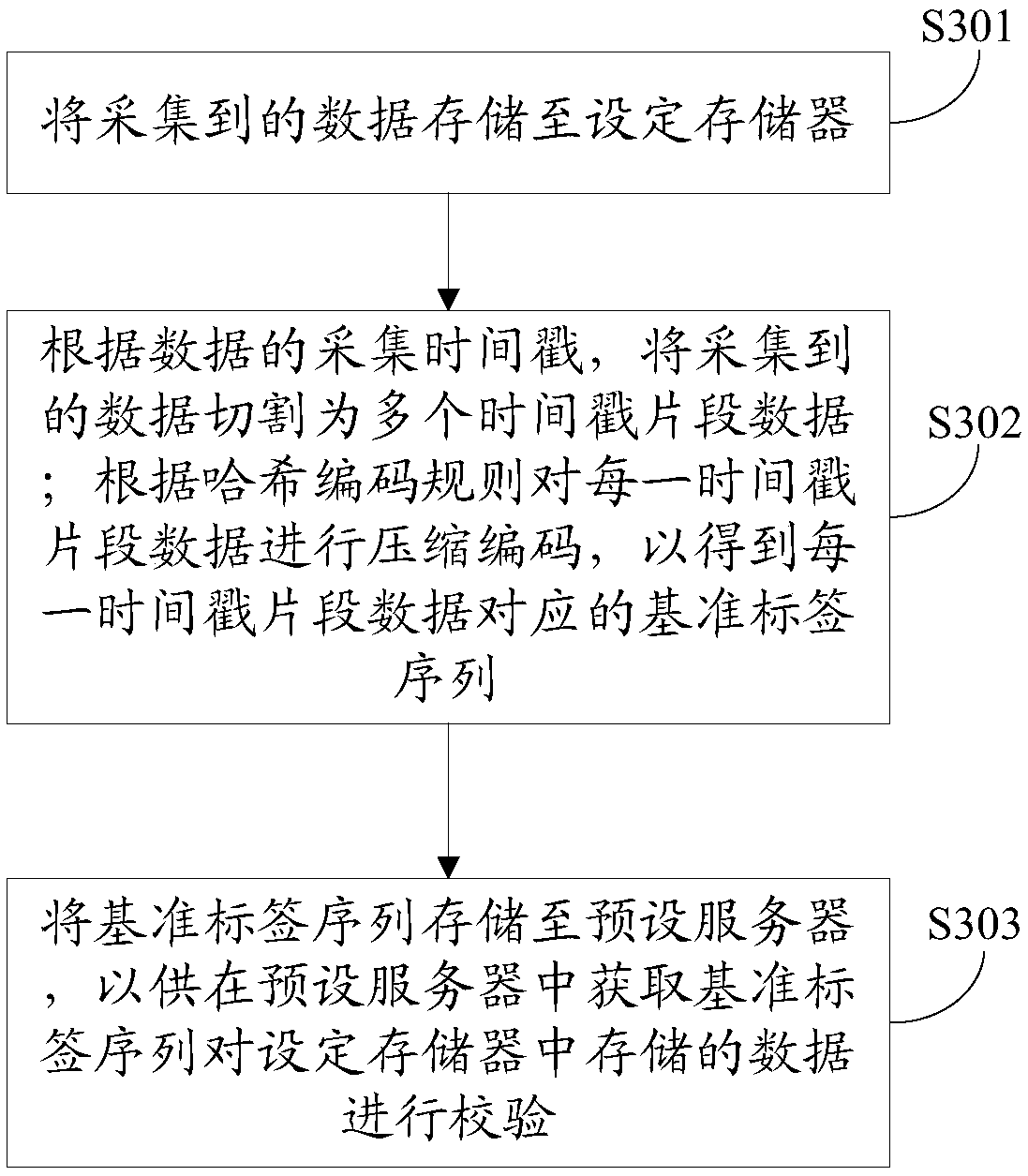
ActiveCN111161448AImplement integrity checksPrevent malicious tamperingInput/output to record carriersRegistering/indicating working of vehiclesData integritySource Data Verification
The invention provides a data storage method, which is applied to data acquisition equipment and comprises the following steps of storing acquired data into a set memory; performing compressed encoding on the acquired data according to a preset encoding rule to obtain reference encoded data; and storing the reference coded data to a preset server so as to obtain the reference coded data from the preset server to verify the data stored in the set memory. In addition, the invention also discloses a data verification method, device and equipment, and a computer readable storage medium, by implementing the above scheme, integrity verification of the collected data is effectively realized, and malicious tampering of the collected data is effectively avoided; the reference coded data for data integrity verification is stored in the server, so that the defect that the reference coded data stored locally is easy to tamper is avoided, and the security of the reference coded data is effectivelyimproved.
Owner:北京燧昀科技有限公司
Agricultural product traceability information storage method based on a block chain
ActiveCN109493045AAchieve compartmentalizationAchieve standardizationPayment protocolsCommerceData integrityProduct traceability
The invention discloses an agricultural product traceability information storage method based on a block chain, and the method comprises the steps: generating block data comprising the head part of ablock, a block body and other information, and achieving the streaked, normalized and persistent storage of the agricultural product traceability information; information such as a block number and forward Hash is added to the head part of the block, and information such as ontology Hash reality is added to the block body, so that all the blocks form a one-way linked list together. The invention discloses a traditional agricultural product tracing information storage technology. the storage of the tracing data can be realized; query and block-based data integrity verification can be realized;the prevention control, check control and recovery control capabilities of enterprises, consumers and administrative competent departments on agricultural product traceability information are improved, the transparency of the agricultural product traceability information is promoted, and the safety awareness and participation degree of all the society bounds on the quality of agricultural productsare enhanced.
Owner:HOHAI UNIV +3
Method and device for automatically checking fastening states of railway fasteners and spring fasteners
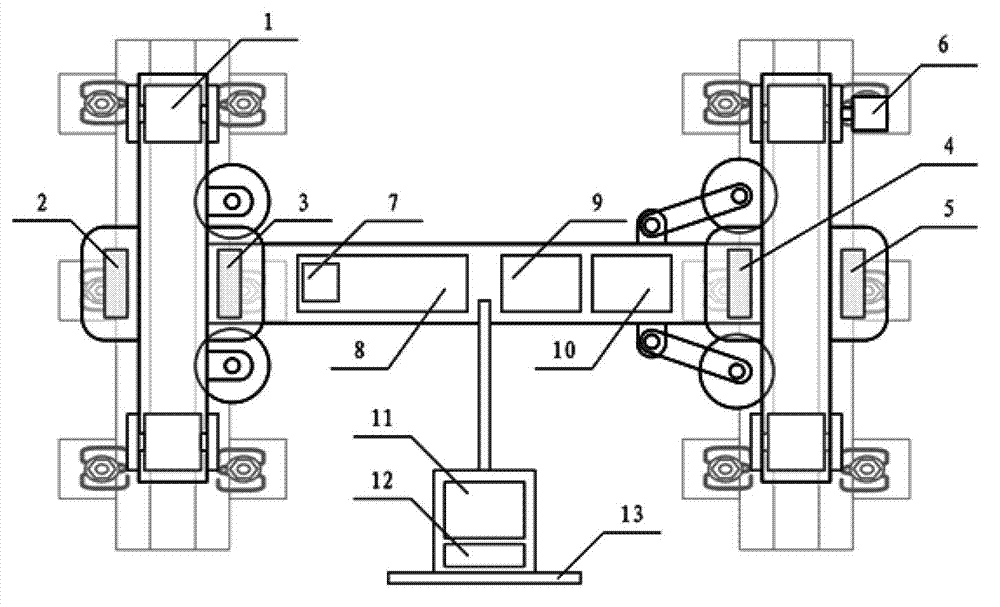
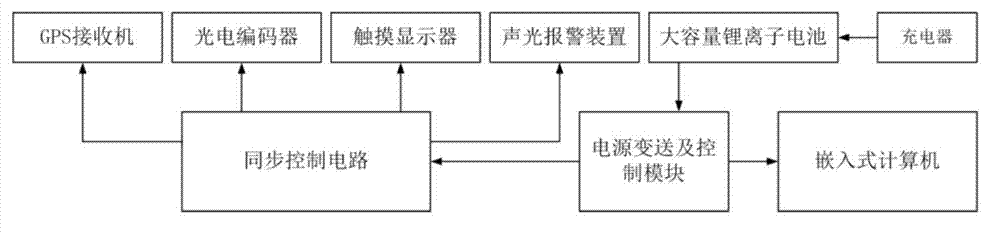
ActiveCN103061219BAchieve precise positioningImplement integrity checksUsing optical meansBogieSynchronous control
The invention relates to a method and a device for automatically checking fastening states of railway fasteners and spring fasteners. The method includes steps of acquiring positioning data of the railway fasteners, acquiring fastening state judgment data of the spring fasteners, combining the positioning data of the railway fasteners and the fastening state judgment data of the spring fasteners to complete checking the fastening states of the railway fasteners and the spring fasteners. The device comprises a railway bogie, a linear structure laser sensor, a photoelectric coder, a GPS (global positioning system) receiver, a synchronous control circuit, an embedded computer and a power source device, wherein the linear structure laser sensor, the photoelectric coder, the GPS receiver, the synchronous control circuit, the embedded computer and the power source device are arranged on the railway bogie. The method and the device for automatically checking the fastening states of the railway fasteners and the spring fasteners have the advantages that accurate positioning of the railway fasteners can be realized, completeness in checking of the railway fasteners and the spring fasteners is realized, the fastening states of the railway fasteners and the spring fasteners can be automatically checked, detail information of the railway fasteners can be recorded, and alarm for the fastening states of the railway fasteners and the spring fasteners is realized.
Owner:WUHAN HANNING TECH
Software delivery data checking method and device
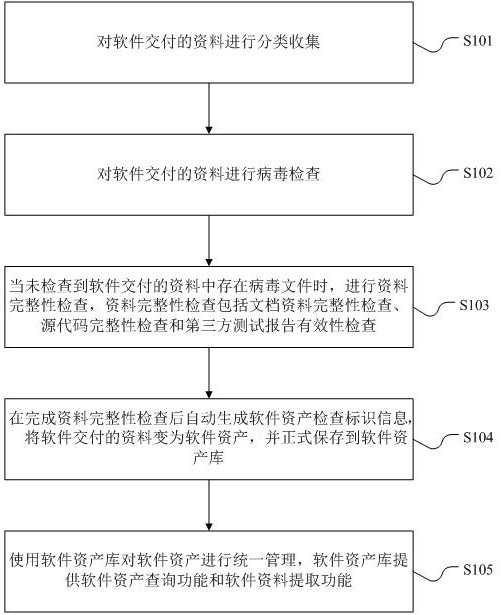
ActiveCN113448613AImprove efficiencyQuality improvementSoftware maintainance/managementPlatform integrity maintainanceThird partyData integrity
The invention provides a software delivery data checking method, which comprises the following steps of: classifying and collecting software delivery data, performing virus checking on the software delivery data, and performing data integrity checking when a virus file does not exist in the software delivery data. The data integrity checking comprises document data integrity checking, source code integrity checking and third-party test report validity checking, software asset checking identification information is automatically generated after the data integrity checking is completed, data delivered by software is changed into software assets, and the software assets are formally stored in a software asset library; the software asset library is used for managing software assets in a unified mode, the software asset library provides a software asset query function and a software data extraction function, the invention further provides a software delivery data checking device, the software delivery data are deeply and automatically inspected, and the efficiency and quality of software data checking are greatly improved.
Owner:湖南省佳策测评信息技术服务有限公司
Chip top protection layer integrity detection device
ActiveCN107329074BImplement integrity checksImprove detection accuracyElectronic circuit testingElectrical resistance and conductanceReference current
Owner:TIANJIN UNIV
Method and system for data file encryption and integrity verification in untrusted server environment
ActiveCN112491529BGuaranteed privacyGuaranteed availabilityKey distribution for secure communicationDigital data protectionData privacy protectionCiphertext
The method and system for data file encryption and integrity verification in an untrusted server environment provided by the present invention relate to the technical field of data privacy protection, and the method includes: 1) system initialization; 2) generating public and private keys of BGN homomorphic encryption algorithm; 3) ) Construct public and private keys for data signature; 4) Use BGN homomorphic encryption algorithm public key to encrypt data files; 5) Construct tags for all file blocks in the data file according to the private key of data signature; 6) Upload encrypted files and tags Gather to the cloud server; 7) Send the file integrity challenge to the cloud server to return the label sum and the file block sum; 8) Use the file block sum and the public key of the data signature to verify the label sum to judge the ciphertext stored in the cloud server File integrity: the present invention combines the BGN homomorphic encryption algorithm and the PDP data possession proof protocol to construct a data signature to realize the integrity check of the encrypted file, and improve the privacy protection and usability of the data file in an untrusted server environment.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY +2
A Reversible Information Hiding Method with Contrast Pulling Using Histogram Shift
ActiveCN111464717BHigh embedding rateIncrease contrastImage enhancementDigital data protectionSteganalysisAlgorithm
The invention discloses a reversible information hidden framework with a contrasting of the rechargeable diagram, and the RDH, which is an optimal encoded based on predictive errors, expands the main algorithm into an efficient hidden framework with dual embedded capabilities.Compared with the previous framework, the framework proposed by the present invention is not only a higher information embedded rate, but also a higher quality -containing image. In addition, the security test also proves that the present invention can effectively effectiveResist many famous hidden analysis technologies (such as Ensemble classifiers, etc.).Moreover, this framework has a dual embedded function. Under the premise of ensuring the original appearance of the digital carrier, the copyright information such as the image identity, serial number, text, and other copyright information is embedded in the carrier to achieve the purpose of copyright protection and complete verification of the carrier.Essence
Owner:章劲松
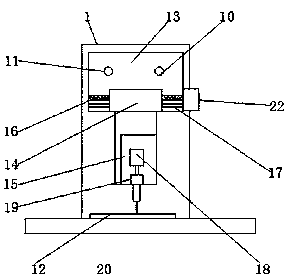
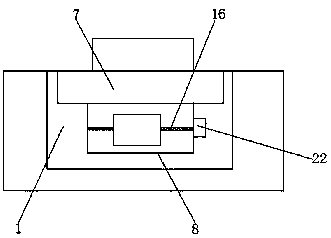
Hardware industry lateral tapping device and detecting method
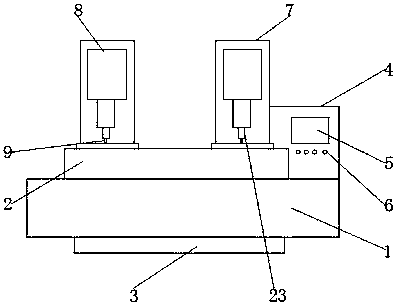
InactiveCN110064803ARealize three-axis adjustmentImplement integrity checksThread cutting machinesMeasurement/indication equipmentsComputer engineering
The invention discloses a hardware industry lateral tapping device and detecting method. The device comprises a machine body, a workbench, a base, a control cabinet, a display screen, a control button, a support plate, an adjusting device, a screw tap, an X-axis guiding column, an X-axis screw, a workpiece and the like; the bottom of the machine body is provided with the base; the workbench is arranged on the base; the control cabinet is arranged on one side of the workbench; the display screen is arranged on the control cabinet; the display screen is a touch display screen; the control buttonis arranged under the display screen; and the support plate is arranged on the upper portion of the workbench. According to the hardware industry lateral tapping device and detecting method, by arranging an X-axis adjusting device, a Y-axis adjusting device and a Z-axis adjusting device, three-axis adjustment of the tapping device is well achieved; and by arranging a workpiece detecting device and a screw tap detecting device, the integrity of a screw tap and the tapping yield of the workpiece are detected.
Owner:肖丽平 +1
Integrity verification method, device, terminal and storage medium for barrage data
ActiveCN109413450BImplement integrity checksAvoid problems like crashesDigital data information retrievalSelective content distributionData translationSoftware engineering
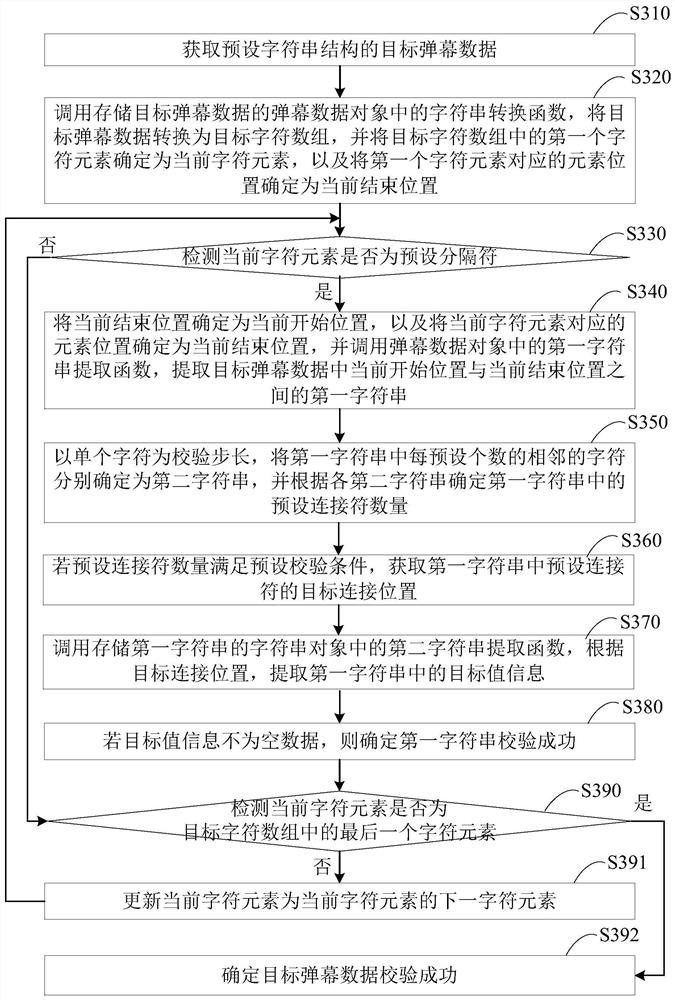
The embodiment of the present invention discloses a method, device, terminal and storage medium for checking the integrity of bullet chat data. The method includes: converting the target bullet chat data with a preset character string structure into a target character array, and The first character element in the array is used as the current character element; check whether the current character element is a preset delimiter, if so, use the current end position as the current start position, and use the position of the current character element as the current end position, for the current start Check the first character string between the position and the current end position; if not, or if the first character string is verified successfully, then if the current character element is not the last character element in the target character array, update the current character element, and Returns the operation of detecting whether the current character element is a preset separator; when the current character element is the last character element, it is determined that the verification of the target bullet chat data is successful, so as to perform an integrity check on the bullet chat data.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com