Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
203results about How to "Improve the level of security protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
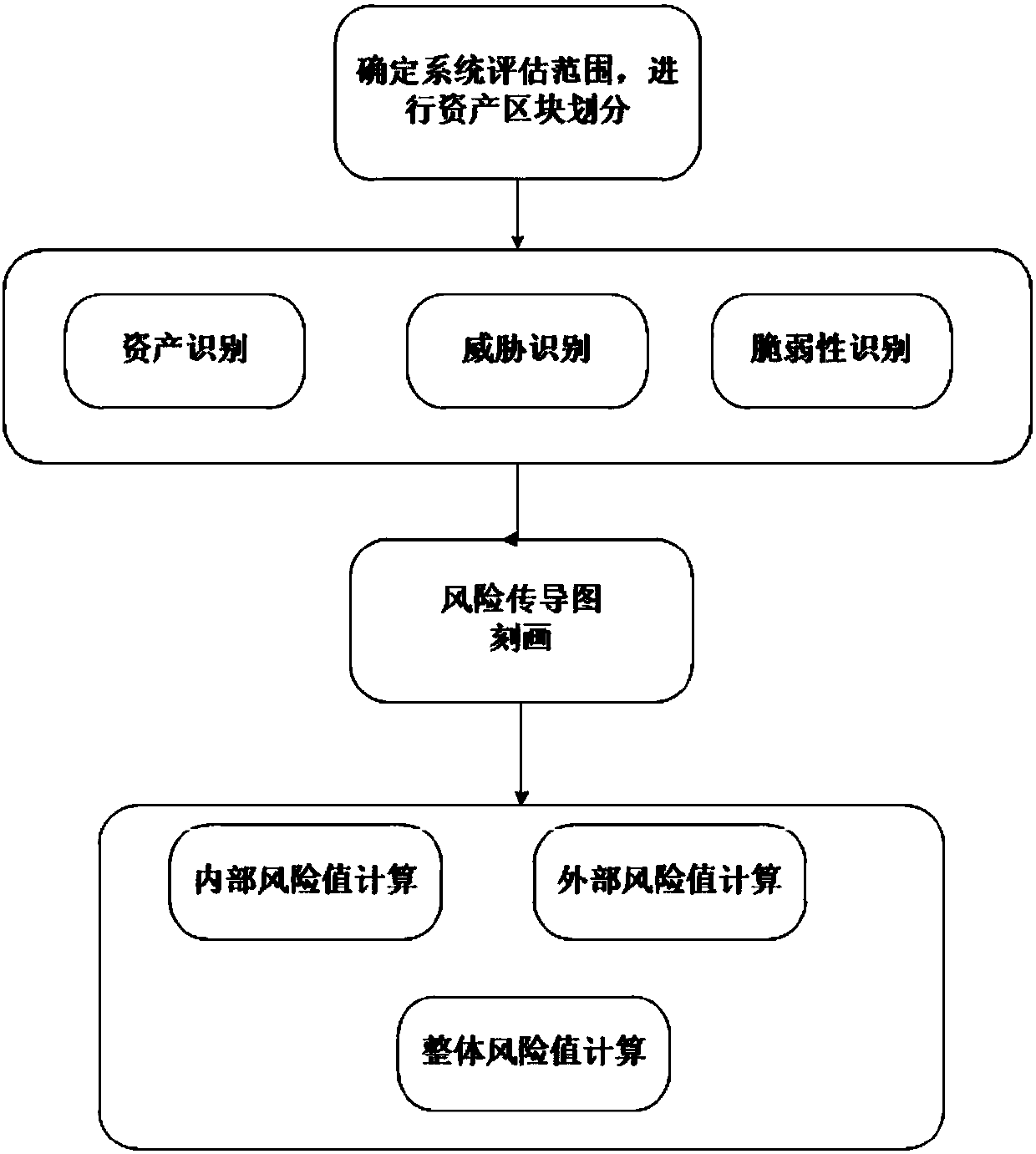
Asset dependence relation-based information security risk evaluation method and system
The invention discloses an asset dependence relation-based information security risk evaluation method and system. The method comprises the following steps of acquiring an asset range in a to-be-evaluated information system, and dividing the asset into blocks; identifying threats, vulnerability and asset significance of the to-be-evaluated information system, and acquiring significance value of the asset, threat value of the threat, and a vulnerability value of the vulnerability; calculating to build a security dependence relation matrix of assets by using a dependence structure matrix, determining a risk conduction coefficient of the assets by using a Delphi method and building a risk conduction relation; and calculating interior risk value and an exterior risk value of each block and overall risk value of the to-be-evaluated information system according to the risk conduction relation and asset significance, threat value and vulnerability value. The method can acquire a weak link ofthe system more accurately, and acquire more reliable information security risk evaluation results.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
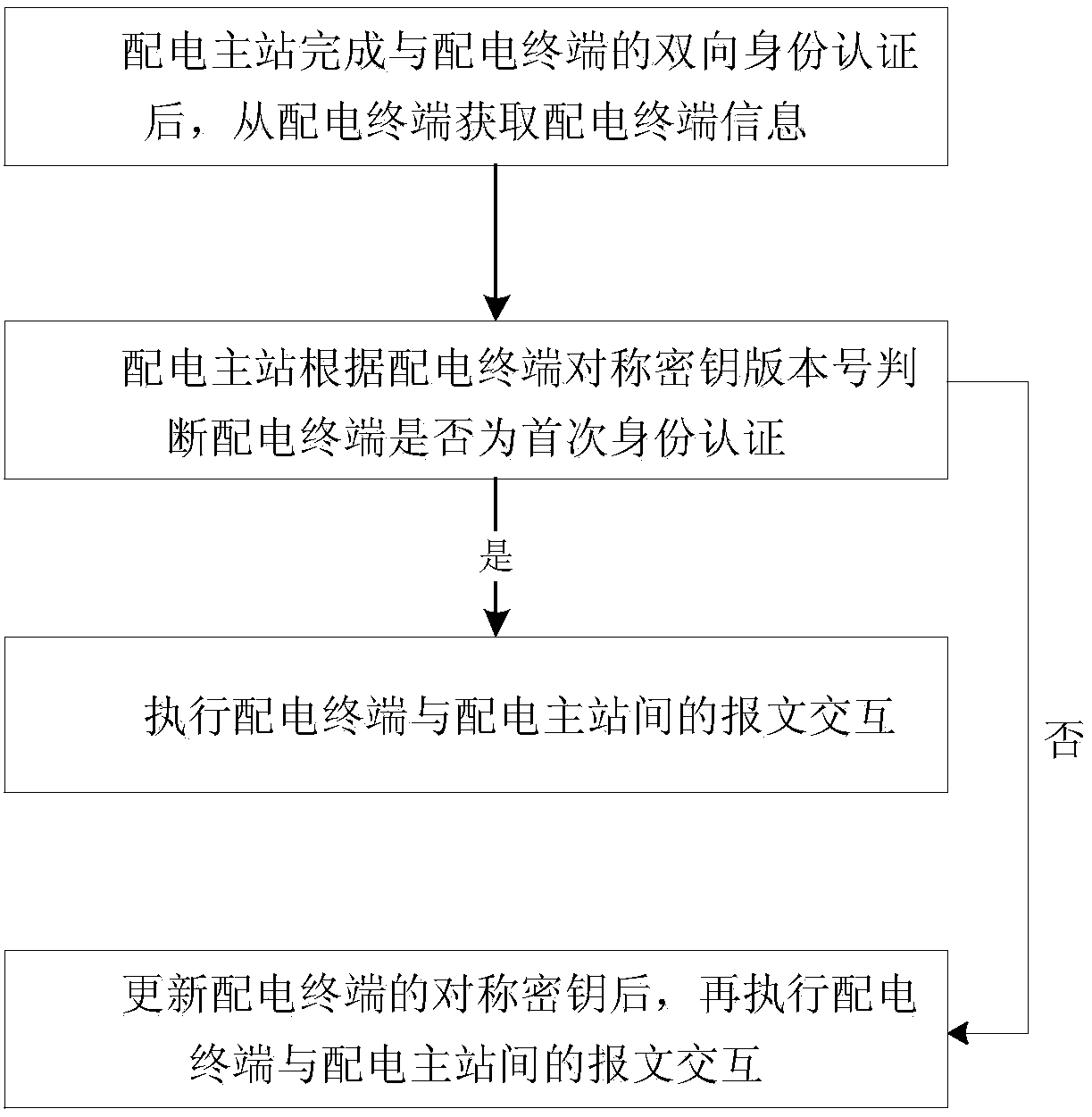
Communication message security interaction method and device of distribution automation system
ActiveCN109257327AImprove the level of security protectionAvoid safety hazardsKey distribution for secure communicationCircuit arrangementsRemote controlConfidentiality
The invention provides a communication message security interaction method and a device of a distribution automation system. After completing two-way identity authentication between a distribution master station and a distribution terminal, a main distribution station obtains distribution terminal information from the distribution terminal. The main distribution station judges whether that distribution terminal is the first identity authentication according to the version number of the symmetrical key of the distribution terminal, if not, the message exchange between the distribution terminaland the main distribution station is carried out; otherwise, after the symmetric key of the distribution terminal is updated, message exchange between the distribution terminal and the distribution master station is performed. The scheme makes up for the shortcomings that the distribution master station can not identify the distribution terminal in the distribution automation system security protection system, and the confidentiality and integrity of the communication message can not be guaranteed, and improves the security protection level of the vertical communication between the distribution master station and the distribution terminal in the distribution automation system. At that same time, the problem that the remote control / parameter set message has the hidden trouble of the replayattack and the like are sol.
Owner:CHINA ELECTRIC POWER RES INST +1
Resin-formed flexible puncture-proof fabric and preparation method thereof
The invention relates to a resin-formed flexible puncture-proof fabric and a preparation method of the resin-formed flexible puncture-proof fabric. The fabric consists of garment fabric and thermosetting resin condensates, wherein a gap exists between the thermosetting resin condensates. The preparation method comprises the following steps of: uniformly dispersing the thermosetting resin in each mesh of a screen plate so that each mesh is filled with resin; scraping residual resin on the surface of the screen plate; spreading the garment fabric on the screen plate filled with resin; applying pressure to the garment fabric, and drying; solidifying the thermosetting resin condensate on the surface of the garment fabric; and finally removing the thermosetting resin condensate from the screen plate to obtain the resin-formed flexible puncture-proof fabric. According to the invention, the thermosetting resin is a good binder before solidification, has a good binding effect with the garment fabric and relatively high strength and hardness after solidification, and can resist the puncture of a conventional tool needle tube; and the shortcomings and defects of the prior art are overcome, and the needs of the military field and civil field are met.
Owner:DONGHUA UNIV +1
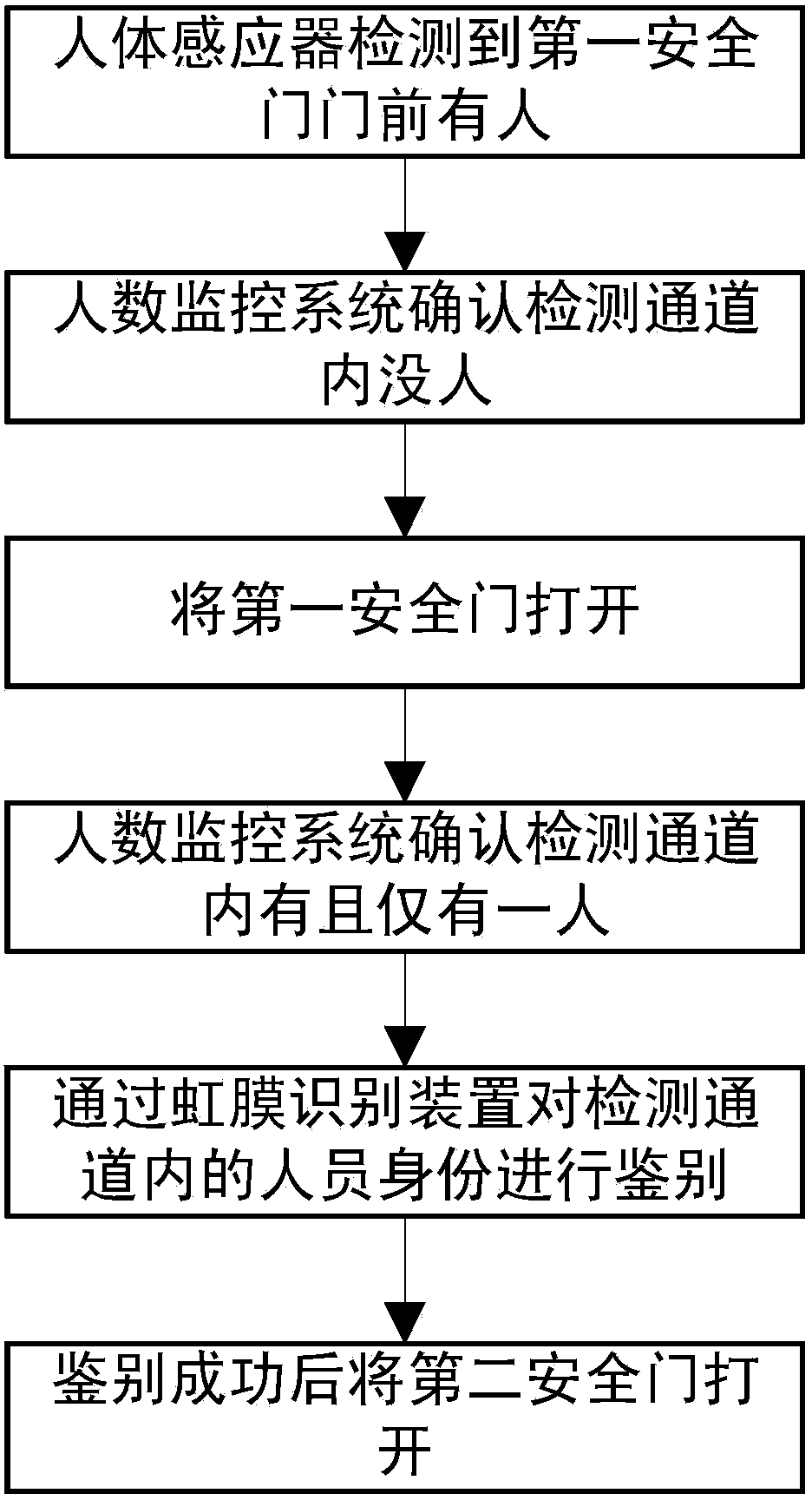
Safety detection method for personnel passing
InactiveCN104361661AAvoid tailgating into buildingsImprove the level of security protectionIndividual entry/exit registersHuman bodyIdentification device
The invention discloses a safety detection method for personnel passing and belongs to the field of personnel passing. According to the method, a detection channel, a first automatic door, a second automatic door, an iris identification device, a human body sensor, a control unit, a number-of-people monitor system and a remote server are arranged; the identities of personnel entering the detection channel are identified through the iris identification device, the number of people in the detection channel is analyzed through the number-of-people monitor system, and an alarm is given when the number of people in the detection channel is more than 1, so that the situation that illegal personnel enters a building by following legal personnel is effectively avoided and the safety protection level of the building is improved.
Owner:SUZHOU YOURUI TESTING TECH
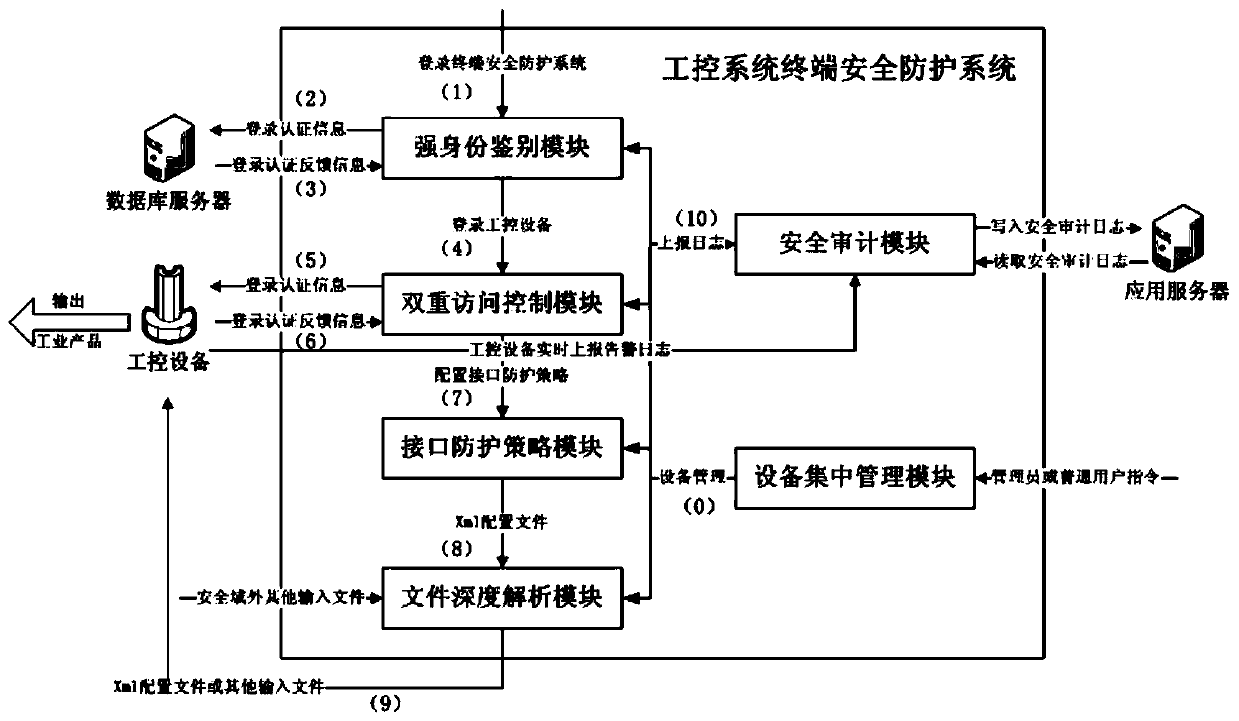
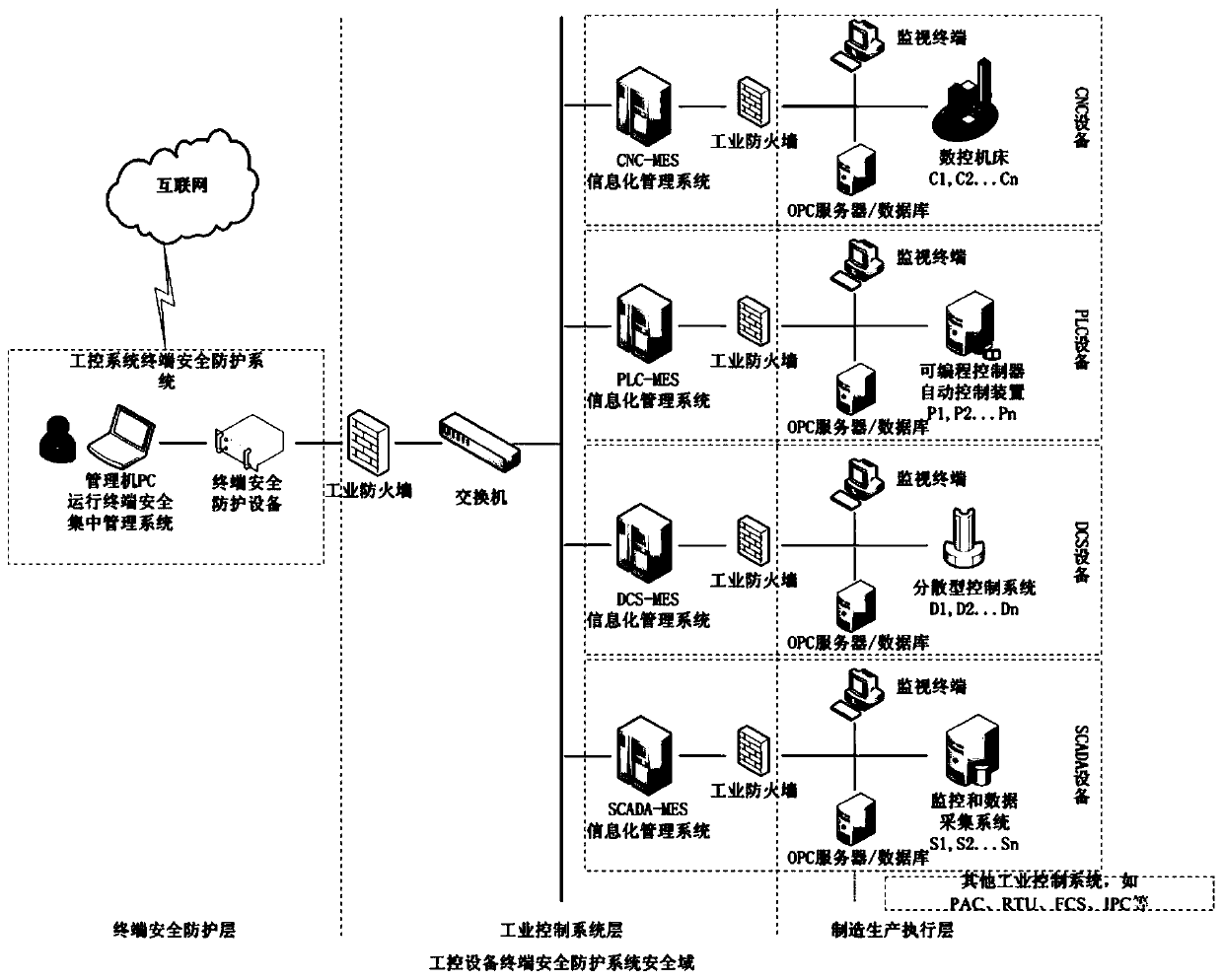
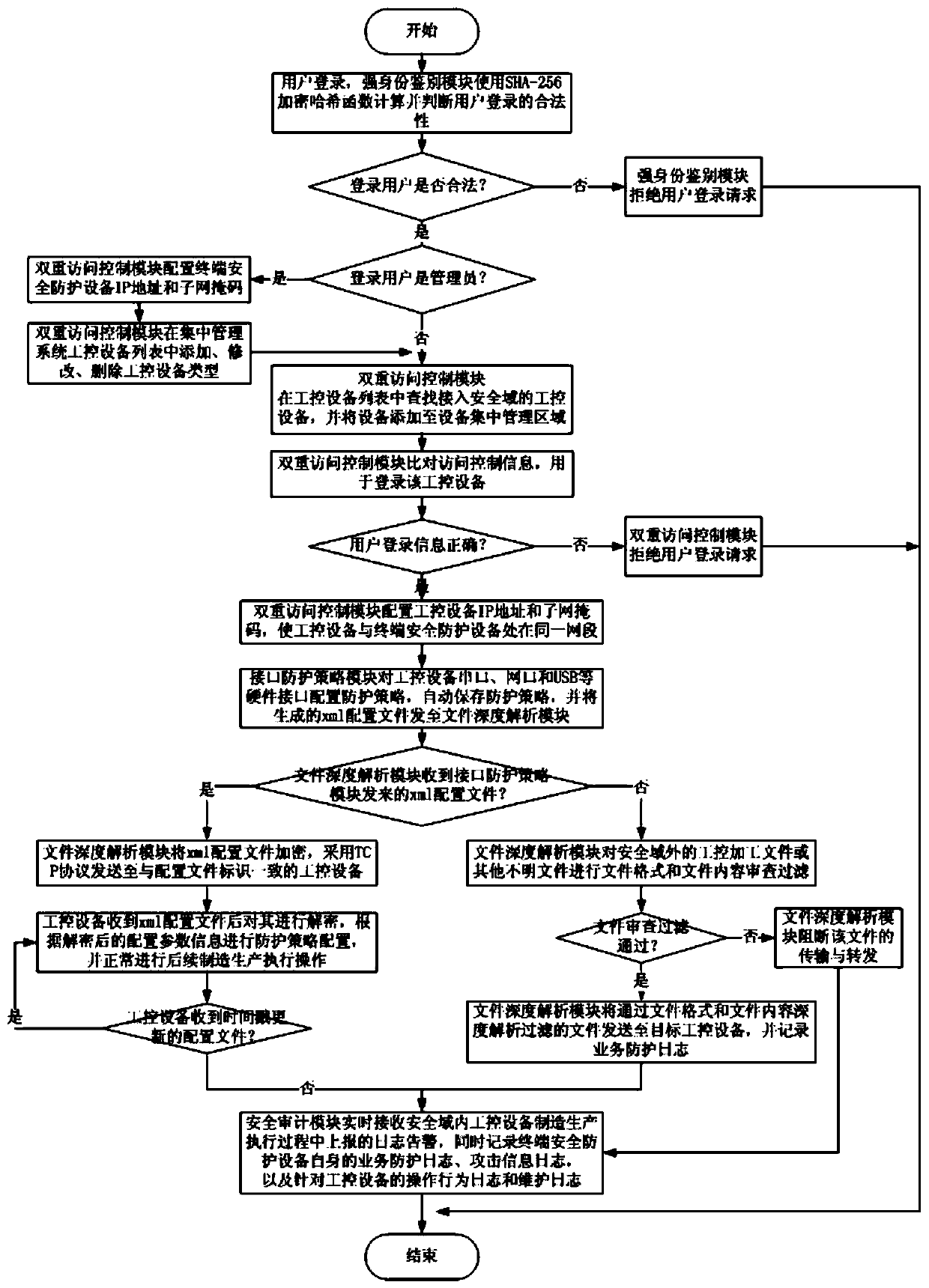
Industrial control system terminal safety protection method
ActiveCN109995796AImprove the protective effectImprove the level ofEncryption apparatus with shift registers/memoriesComputer compatibilityEngineering
The invention belongs to the technical field of industrial control system terminal safety protection, and particularly relates to an industrial control system terminal safety protection method. The method is implemented based on an industrial control system terminal safety protection system, and the system comprises terminal safety protection equipment and a terminal safety centralized managementsystem. According to the scheme, a series of technical means of strong identity authentication, dual access control, an interface protection strategy, file deep analysis, security audit and equipmentcentralized management are comprehensively applied; malicious behaviors such as network attack and illegal access in operation of industrial control system equipment are effectively blocked, and centralized configuration and management of security protection strategies of a plurality of industrial control system equipment terminals of the same type or different types are realized at the same time.The scheme has the advantages that the safety protection level of the industrial control equipment terminal is high, centralized and unified management of multiple pieces of equipment is supported, and the centralized management platform is suitable for multiple application environments and multiple industrial protocols, good in compatibility, flexible in protection strategy configuration, efficient in alarm reporting and equipment management and the like.
Owner:北京京航计算通讯研究所
Fluorescent inflaming-retarding multifunctional double-layer fabric and preparing method thereof
ActiveCN105483898AFlame retardant hasHigh temperature resistantFibre typesMulti-ply fabricsYarnSurface layer
The invention discloses a fluorescent inflaming-retarding multifunctional double-layer fabric. The surface layer of the fabric is woven from inflaming-retarding yarn capable of being dyed with fluorescence color, and the inner layer of the fabric is woven from non-melting inflaming-retarding yarn incapable of being dyed with fluorescence color. The warps of the inner layer are lifted to be interwoven with the wefts of the surface layer to form a binding texture so that the two layers can be connected. The fabric is prepared in the way that the warps of the inner layer are lifted to be interwoven with the wefts of the surface layer to form the binding texture so that the two layers can be connected, and then dyeing treatment is conducted to generate the fluorescent inflaming-retarding multifunctional double-layer fabric. Specifically, the two layers of the fabric are connected in the way that when surface wefts are put in for surface layer weaving, all inner warps must sink to the space below a shed and can not be interwoven with surface wefts; when inner wefts are put in for inner layer weaving, all surface warps must be lifted and can not be interwoven with inner wefts. The double-layer fabric can have different spaces and can be used for making protection garments in a plurality of fields.
Owner:SHAANXI YUANFENG TEXTILE TECH RES
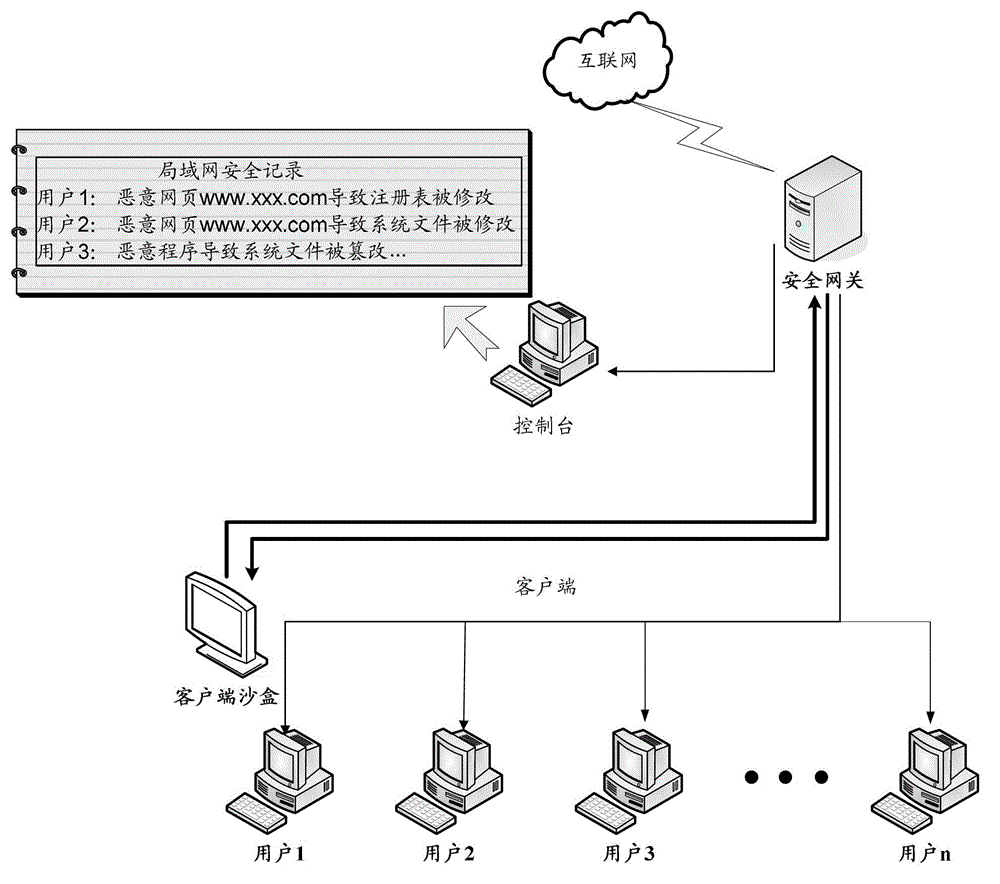
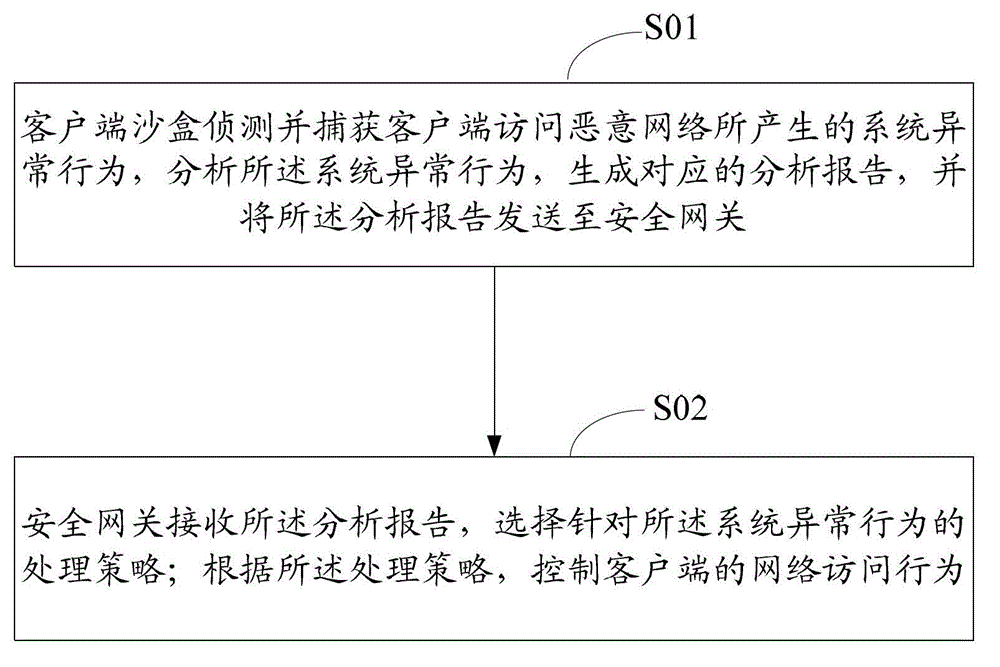
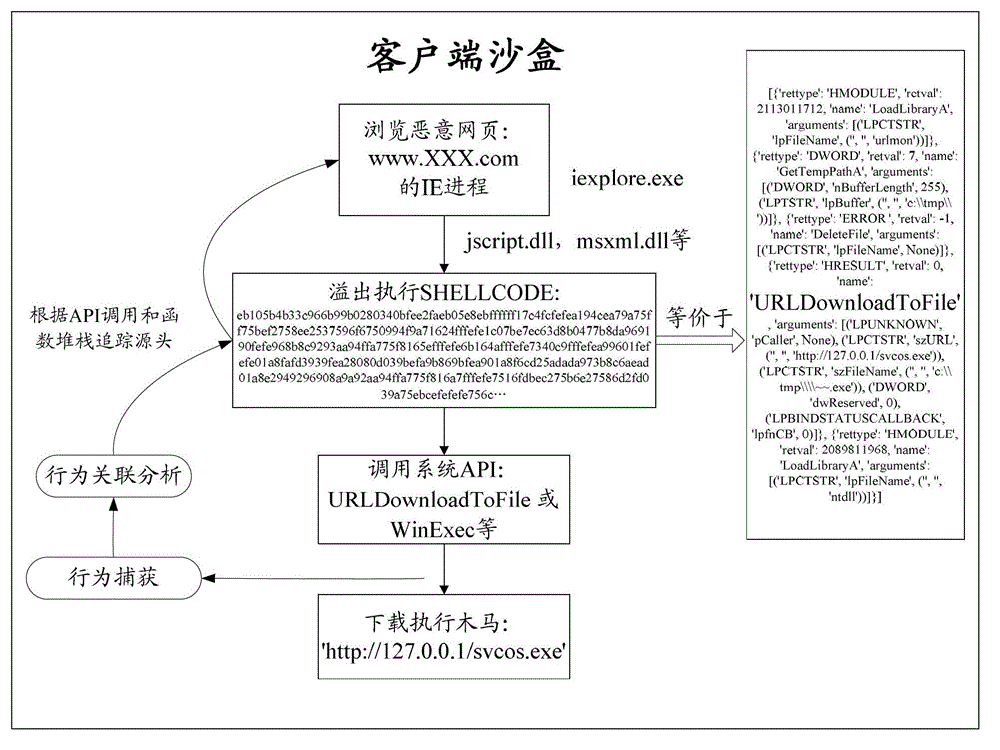
Method and system of controlling access behaviors of client network
ActiveCN103152323AImprove the level of security protectionHigh transparencyTransmissionClient-sideNetwork security
The invention discloses a method and a system of controlling access behaviors of client network. The method comprises the following steps: a step of detecting client sandbox, capturing system abnormal behaviors caused by visiting malicious network done by the clients, analyzing the system abnormal behaviors, generating a corresponding analysis report and sending the analysis report to a security gateway; a step of receiving the analysis report by the security gateway, choosing a strategy used for dealing with the system abnormal behaviors; a step of controlling the network-visiting behaviors of the clients according to the dealing strategy. The method has the advantages of common protection to the network-visiting behaviors of the clients by the combination of the client sandbox and the security gateway so as to improve safety protection degree of client visiting the network, meanwhile, when the clients visit the network, transparency of network safety state is improved.
Owner:SANGFOR TECH INC
Waterproof and dustproof structure of outdoor equipment cabinet and outdoor equipment cabinet with waterproof and dustproof structure
ActiveCN103327776AImprove the level of security protectionExtended service lifeCasings/cabinets/drawers detailsCooling/ventilation/heating modificationsEngineeringElectrical equipment
The invention discloses a waterproof and dustproof structure of an outdoor equipment cabinet and the outdoor equipment cabinet with the waterproof and dustproof structure. According to the waterproof and dustproof structure of the outdoor equipment cabinet and the outdoor equipment cabinet with the waterproof and dustproof structure, more than two ventilation holes are vertically formed in one lateral wall of a cabinet body at intervals, a louver is arranged outside each ventilation hole in a covering mode, an air duct is arranged between each ventilation hole and a corresponding louver in an enclosing mode, each louver is provided with vertically arranged openings which are lower than a corresponding ventilation hole, and the lower edge of the bottommost opening of each louver is flush with the lower wall surface of a corresponding air duct. The outdoor equipment cabinet with the waterproof and dustproof structure is simple in structure. According to the waterproof and dustproof structure of the outdoor equipment cabinet and the outdoor equipment cabinet with the waterproof and dustproof structure, the service life of the equipment cabinet is effectively prolonged, electrical equipment installed in the equipment cabinet is made to rotate in a sound internal environment all the time, the level of safety protection of the outdoor equipment cabinet is further improved, and the problem that drainage is unavailable at interlayer positions of an air inlet and an air outlet of an existing equipment cabinet is solved.
Owner:STATE GRID CORP OF CHINA +2
Universal type automatic-butt-joint charging apparatus applicable to indoor mobile robot
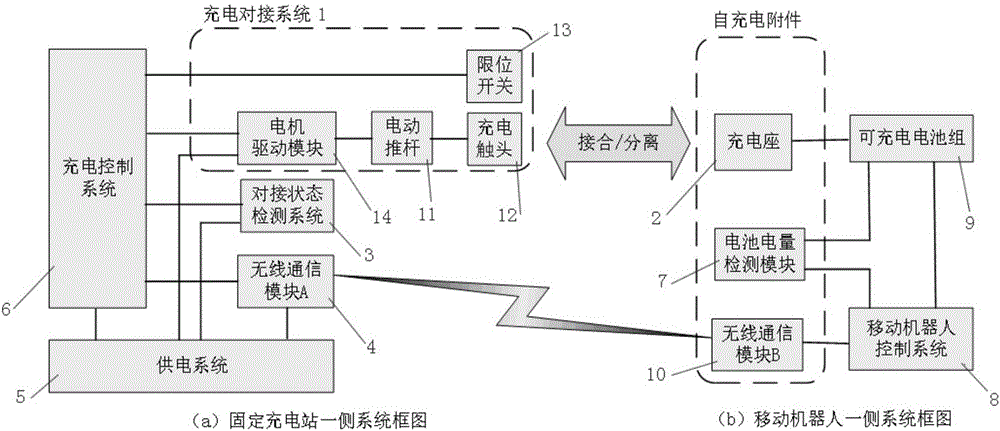
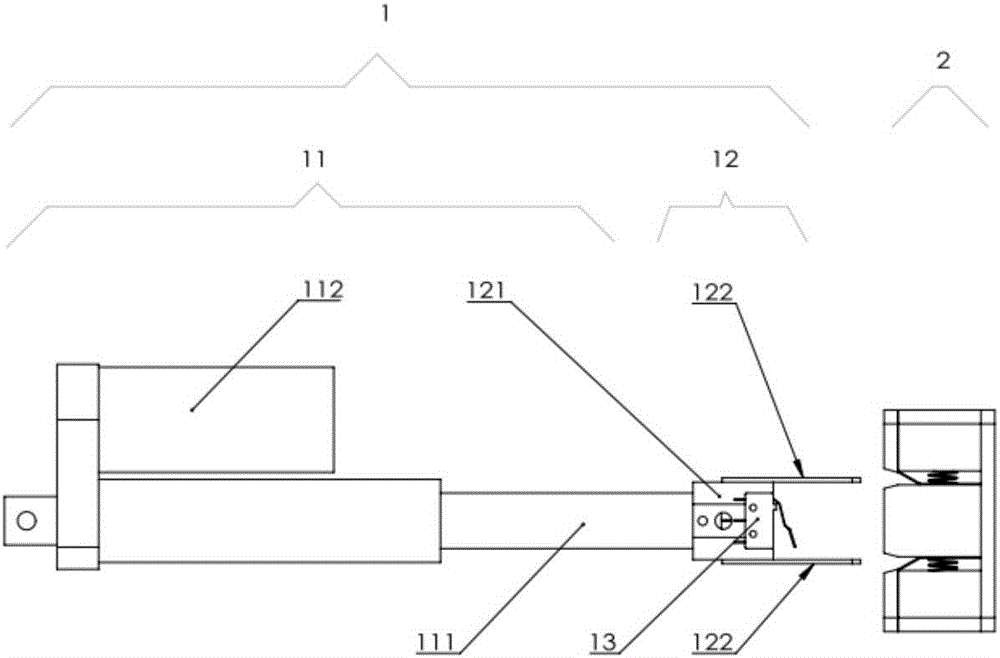
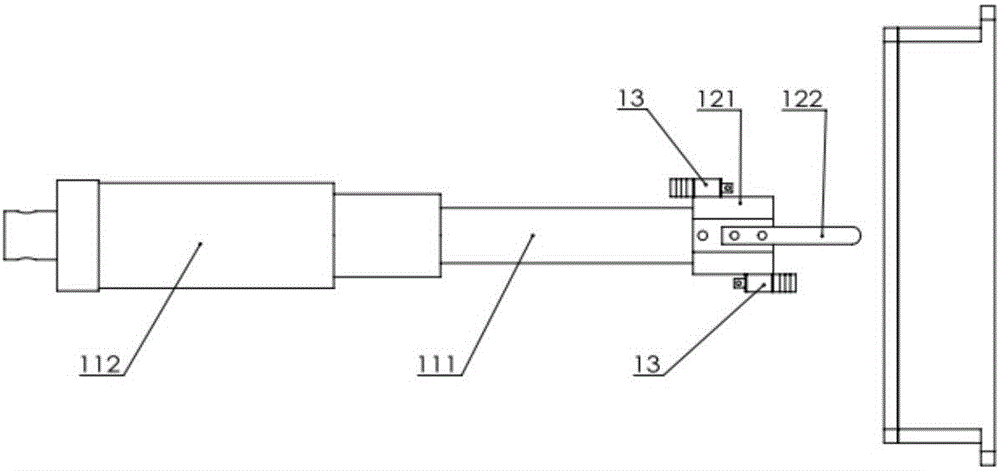
ActiveCN106786882AReduce the precision requirements for docking operationsLow costElectric powerExchanging data chargerMobile robotSingle degree of freedom
The invention discloses a universal type automatic-butt-joint charging apparatus applicable to an indoor mobile robot, and belongs to the technical field of a robot. The universal type automatic-butt-joint charging apparatus comprises a fixed charging station and an automatic charging accessory mounted on the mobile robot, wherein the fixed charging station comprises a charging butt-joint system, a control system, a wireless communication module A, a butt-joint state detection system and a power supply system; and the automatic charging accessory comprises a battery electric quantity monitoring module, a wireless communication module B and a charging base. After the automatic charging accessory is connected with the control system and a charging battery system of the mobile robot, automatic-butt-joint charging is realized by executing the respective programs at the mobile robot end and the fixed charging station end; the charging butt-joint system can realize butt jointing / separating actions with the charging base through an electric push rod in movement of single degree of freedom; and the butt-joint state detection system judges the state of the butt-joint system through voltage detection.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
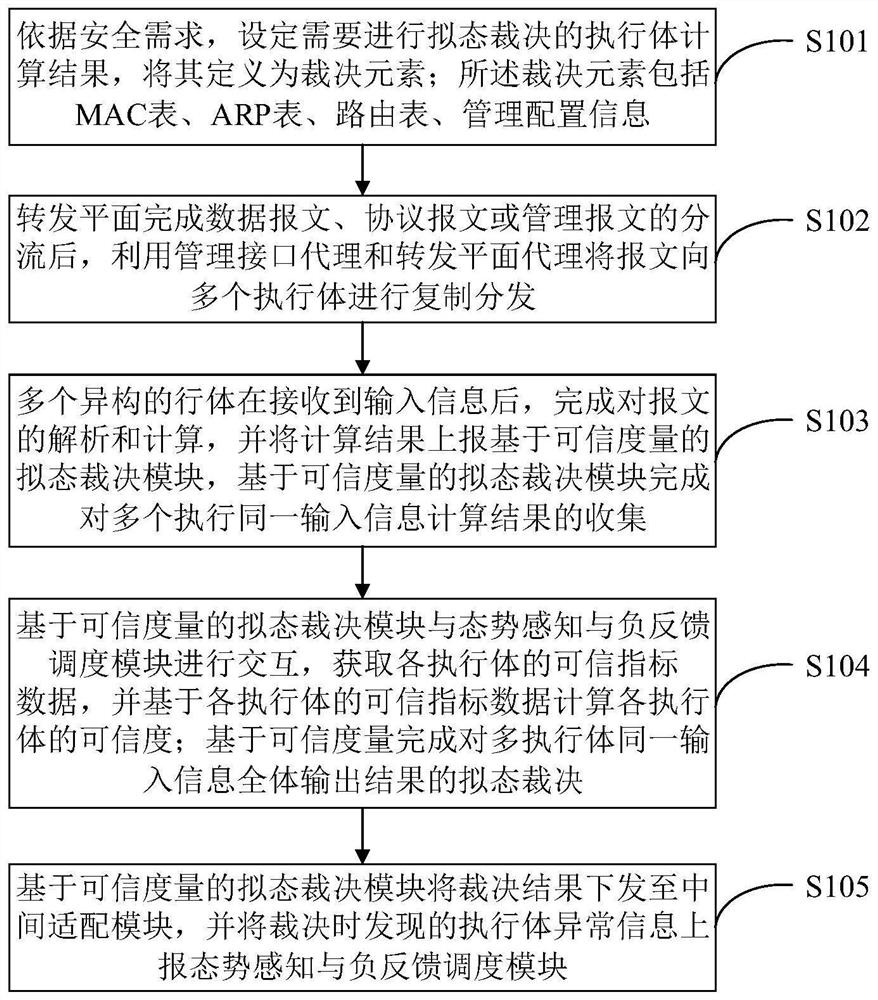
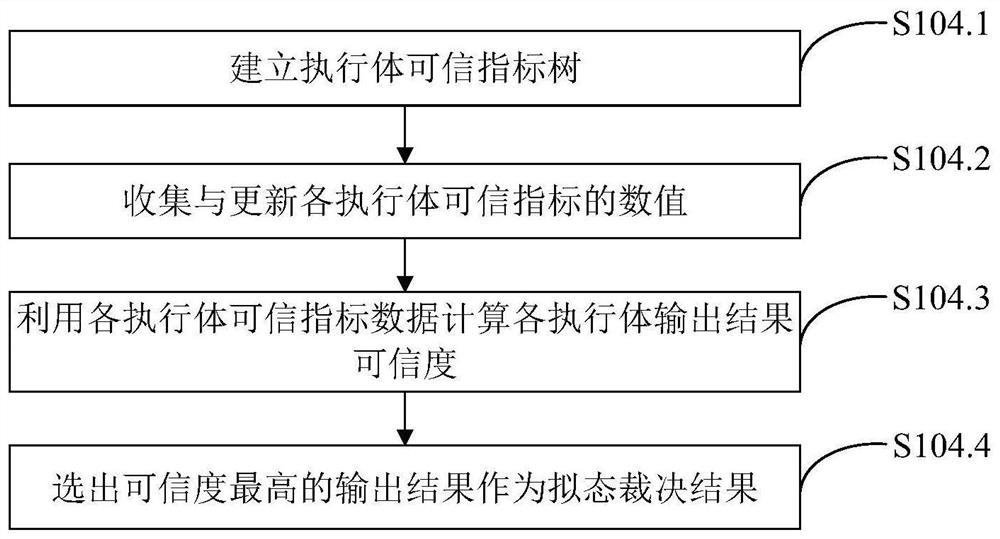
Mimicry switch judgment system and method based on trusted measurement
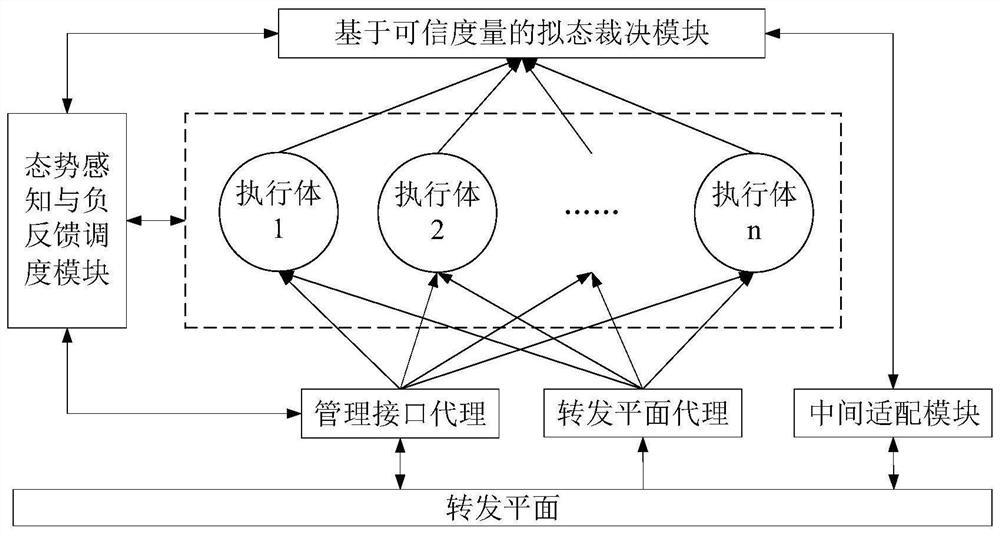
ActiveCN111884996AReduce security threatsImprove the level of security protectionData switching networksComplex mathematical operationsDecision systemInformation Harvesting
The invention belongs to the technical field of network security, and discloses a mimicry switch decision system based on trusted measurement, and the system comprises a forwarding plane, a managementinterface agent, an intermediate adaptation module, a forwarding plane agent, a plurality of heterogeneous actuators, a trusted measurement-based mimicry decision module and a situation awareness andnegative feedback scheduling module. The invention further discloses a mimicry switch judgment method based on trusted measurement. The mimicry switch judgment method comprises the steps: setting mimicry switch judgment elements; distributing input information; collecting output information; carrying out mimicry decision based on credibility measurement; issuing a judgment result, sensing the threat situation of the switch, and scheduling an executor; the mimicry decision based on credibility measurement comprises the following steps: establishing an executive credible index tree; collectingand updating the credible index data of the executive body; calculating the credible weight of the output result of each executive body; and calculating the credibility of each output result. The method can effectively reduce the influence of unknown loopholes and potential backdoors, and improves the safety protection level of a local area network.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
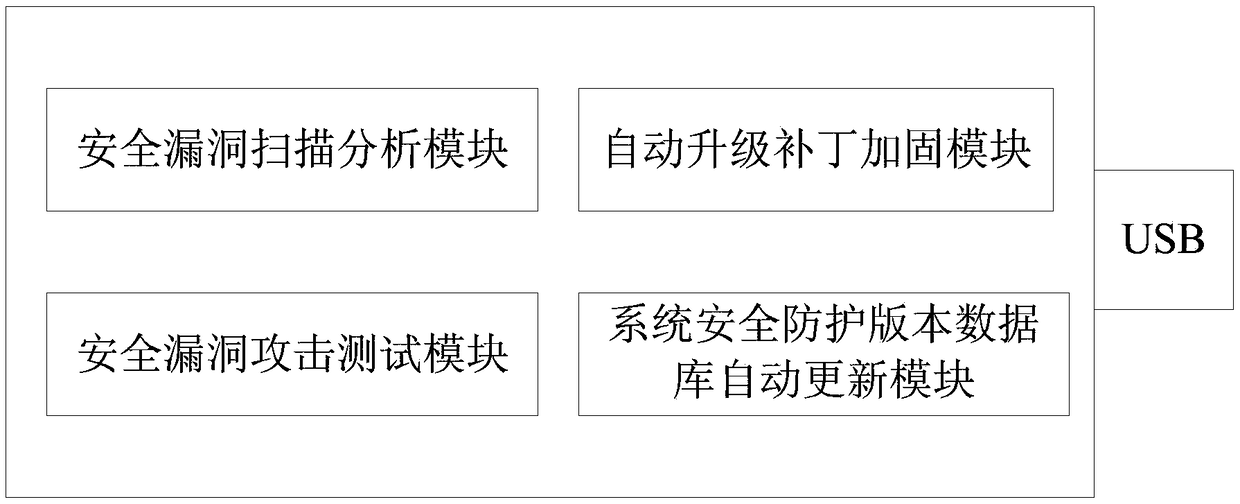
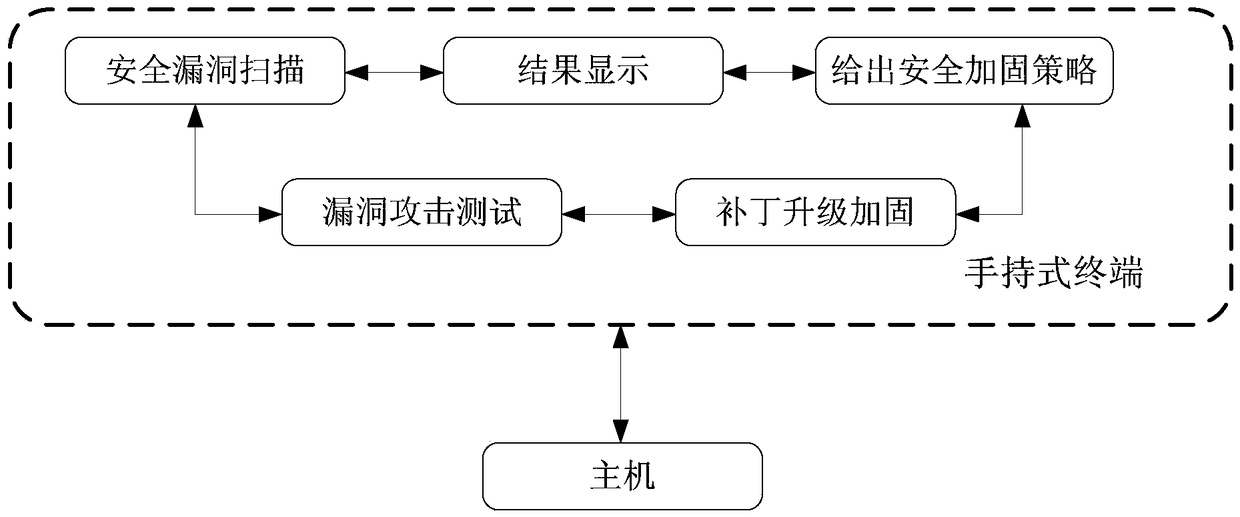
Handheld terminal of realizing computer information security protection, vulnerability scanning and protection reinforcement and protection method
ActiveCN108830084AImprove work efficiencyImprove the level of security protectionPlatform integrity maintainanceTransmissionMaterial resourcesComputer terminal
The invention provides a handheld terminal of realizing computer information security protection, vulnerability scanning and protection reinforcement. The terminal includes a USB interface, a securityvulnerability scanning and analysis module, an automatic upgrading patch reinforcement module, a security vulnerability attack test module and a system security protection version database automatic-updating module. The handheld terminal is plugged onto a host, which needs to be detected, through the USB interface, and realizes security protection, vulnerability scanning and protection reinforcement on the host through the security vulnerability scanning and analysis module, the automatic upgrading patch reinforcement module, the security vulnerability attack test module and the system security protection version database automatic-updating module. The terminal improves working efficiency of computer security protection reinforcement, and saves manpower and material resource costs.
Owner:JIANGSU ELECTRIC POWER CO
Full-face intelligent fire fighting helmet
InactiveCN104970477AWith communication functionHas a wide-angle visual field of viewHelmetsHelmet coversEyepieceDisplay device
A full-face intelligent fire fighting helmet comprises a helmet main body and transparent goggles positioned in the middle of the front face of the helmet main body; a thermal imaging camera and a low-light-level night vision camera are disposed over the goggles side by side, the thermal imaging camera and the low-light-level night vision camera are embedded into the helmet main body, a row of laser light-compensating lamps are disposed over the thermal imaging camera and the low-light-level night vision camera, and the laser light-compensating lamps are also embedded into the helmet main body; an upper portion of the inside of the goggles is provided with a display used when fire scene ambient conditions cannot be seen clearly in the view, temperature T degree distribution of the fire scene can be displayed, and display information can be transmitted to a background command vehicle system timely; and a lower portion of the inside of the goggles is provided with a respirator, the respirator is connected with an external breathe supply system, and a hands-free communication system for ensuring clear communication between fire fighters and between the fire fighter and a superior is disposed below the respirator side in the goggles. The helmet is high in safety protection degree and maximum service temperature, long in service lifetime, small in size, light in weight and easy to handle, and can continuously work for a long time.
Owner:SHANGHAI KEQIN ELECTRICAL MACHINE
Keyboard safe protecting device and method of payment terminal
ActiveCN103617908AImprove the level of security protectionImplement cross-interlock protection mechanismElectric switchesComputer hardwareEmbedded system
The invention provides a keyboard safe protecting method of a payment terminal. Two sets of independent safe network detection signals are output through a safe processor of the payment terminal in a driving mode, the signals pass through two sets of safe network detection contacts on the periphery of a keyboard PCB, two sets of the same corresponding safe network detection contacts on a dome FPC protecting film and two layers of corresponding network cables, and constitute an access through extrusion of a limiting column in a matched mode, the two sets of safe network detection contacts on the periphery of the keyboard PCB are arranged in a crossed mode, and the two sets of the same corresponding safe network detection contacts on the dome FPC protecting film are arranged in a crossed mode, the detection signals are fed back to a safe detection input circuit of the safe processor, and therefore safety of a keyboard is guaranteed through cross interlocking of the safe detection signals. The invention further provides a keyboard safe protecting device of the payment terminal, a safe protection mechanism of cross interlocking can be achieved, equipment is safer by means of safe network detection and safe switch detection, and the keyboard safe protection grade of the payment terminal is improved.
Owner:FUJIAN XINO COMM TECH
Wireless local area network non-perception control method and system and readable storage medium
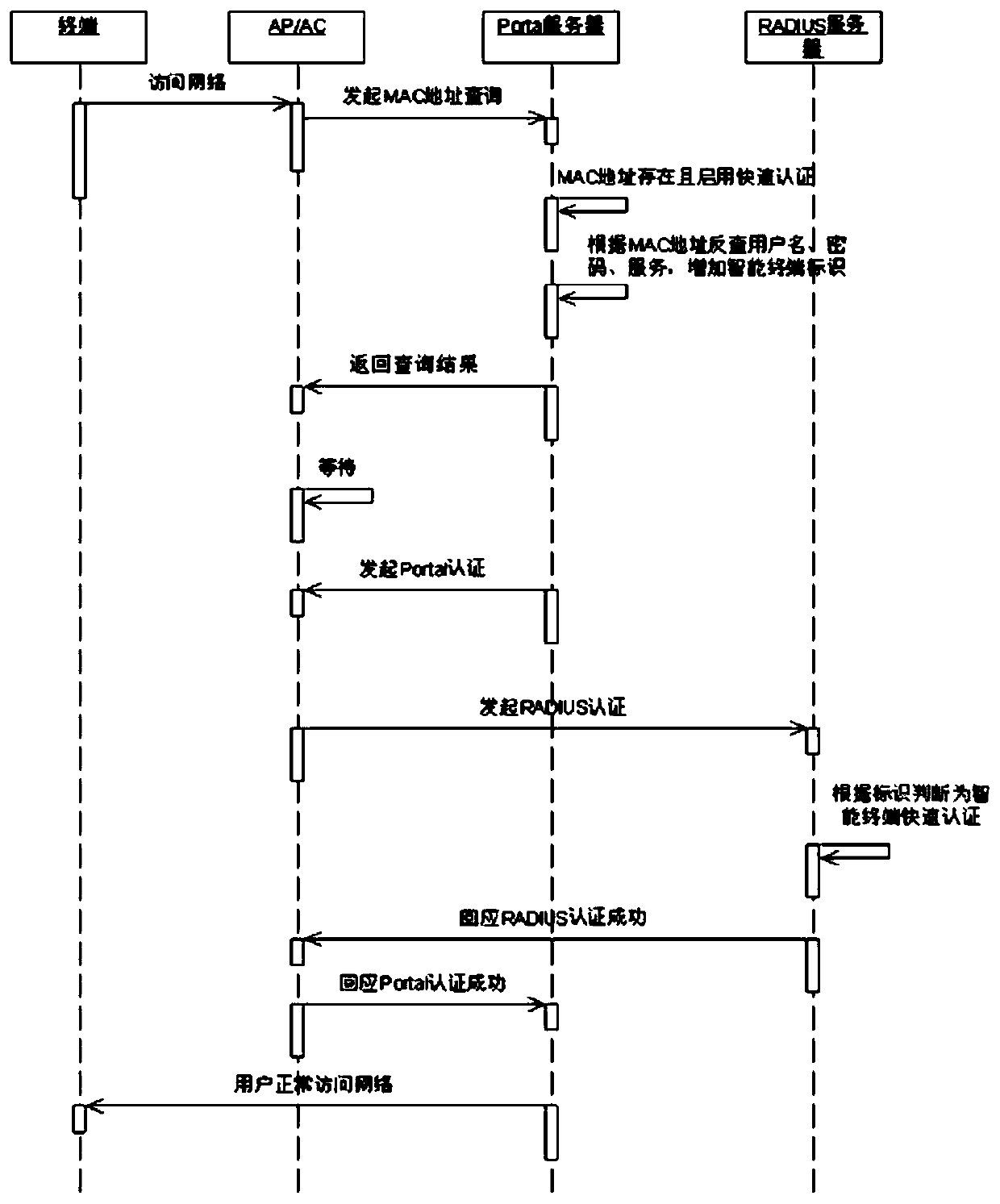
InactiveCN109862565ASimplify the certification processImprove and enhance the user experienceNetwork topologiesSecurity arrangementPattern perceptionWireless gateway
The invention relates to a wireless local area network non-perception control method and system and a readable storage medium. The method comprises the steps that a wireless gateway receives access request information; the wireless gateway generates MAC address query information according to the access request information; the MAC address query information is sent to a Portal server; the Portal server queries whether the MAC address information is recorded or not; and if the MAC address information is recorded, authentication success information is returned to the wireless gateway, and a wireless link of an access address is established. According to the invention, the authentication information is automatically authenticated in the secondary login process of the user; on one hand, the management level and the information security protection level of the wireless local area network are enhanced; on the other hand, the problem of non-perception authentication is solved through binding of AD domain accounts, so that the authentication process of the user is simplified, the use experience of the user is improved, a better wireless local area network service is provided for the user, and the user can use the wireless local area network service more conveniently, quickly and freely.
Owner:GUANGDONG URBAN & RURAL PLANNING & DESIGN INST
IC (Integrate Circuit) card access terminal adopting commercial cipher and operation method thereof
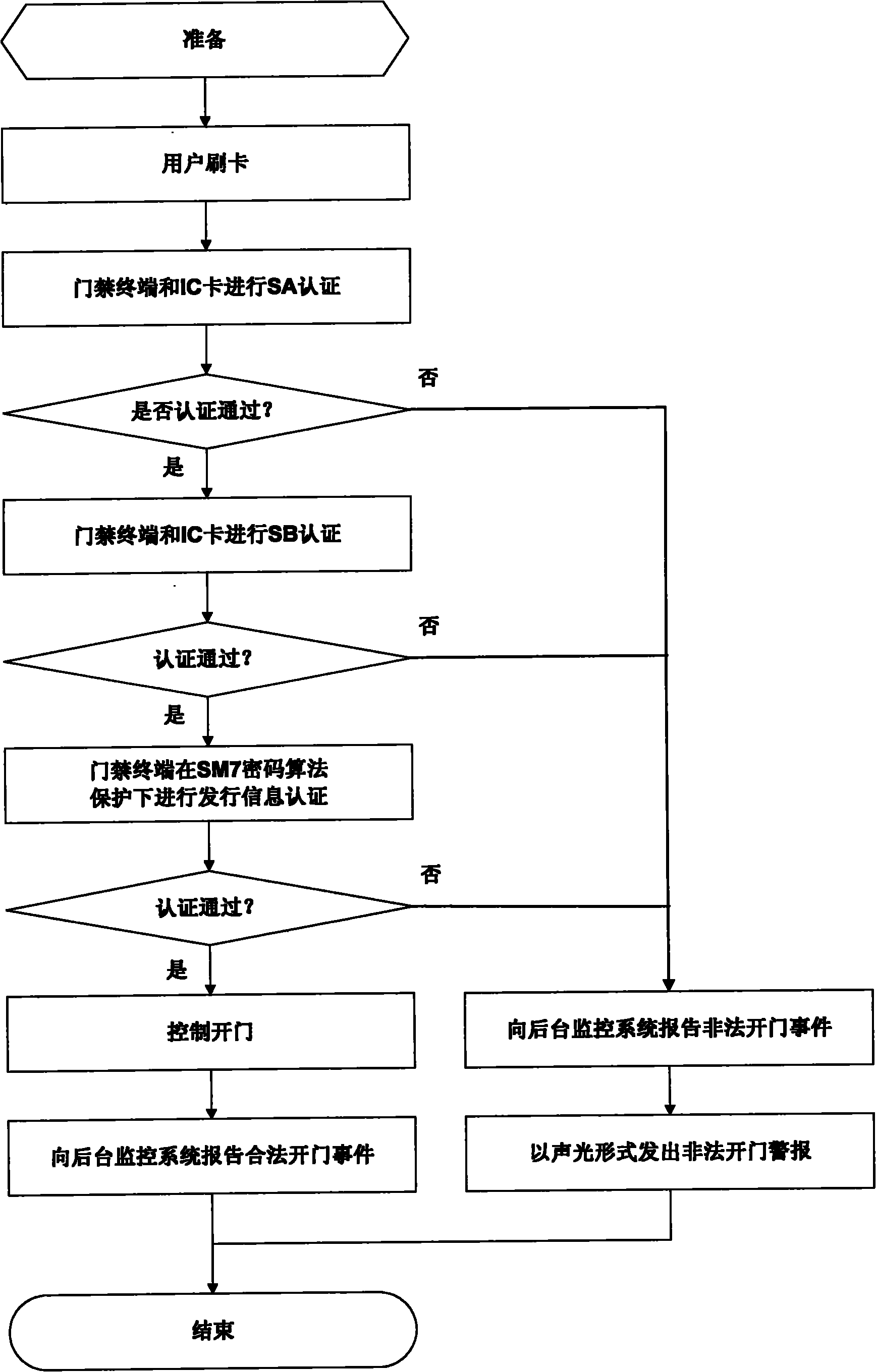
ActiveCN101840592AEnsure safetyEliminate security threatsIndividual entry/exit registersMatched controlComputer module
The invention relates to an IC (Integrate Circuit) card access terminal which adopts a commercial cipher and is provided with a commercial SM (Smart Media)7 / SM1 cipher module. The IC card access terminal comprises an antenna, an RF (Radio-Frequency) interface, an MCU (Microprogrammed Control Unit), a cipher module with a commercial cipher algorithm, an access executing mechanism and a data interface connected with a background monitoring system, wherein the MCU is respectively connected with the RF interface, the cipher module, the access executing mechanism and the data interface for data interaction, and the RF interface is connected with the antenna and is in charge for RF communication between the MCU and the IC card. An operation method of the invention comprises the following steps of: (1) swiping a card on the induction antenna of the access terminal by a user; (2) carrying out SA (Social Accountability) authentification on the access terminal and the IC card under the matched control of the MCU and the SM7 / SM1 cipher module; (3) carrying out SB authentification; (4) authenticating user release information; (5) controlling access; and (6) reporting a legal access accident to the background monitoring system. The invention has a commercial cipher secured authentification mechanism and effectively ensures the security of important access.
Owner:上海微通电子设备有限公司
Encrypted data storage system based on key other-place storage and method
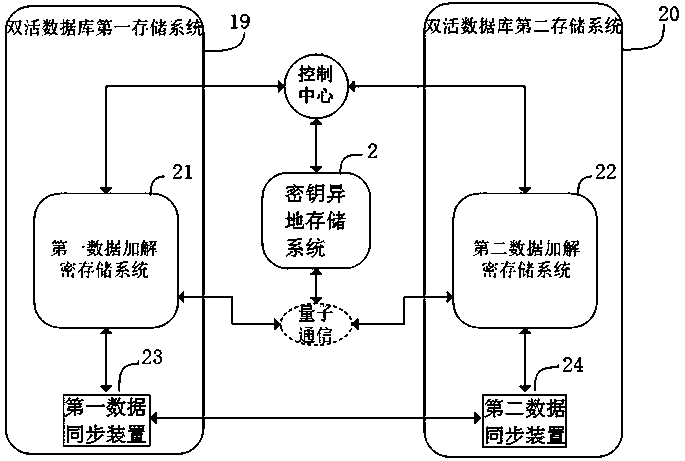
ActiveCN109561047AAvoid easy theftImprove data storage securityKey distribution for secure communicationError detection/correctionComputer hardwareKey storage
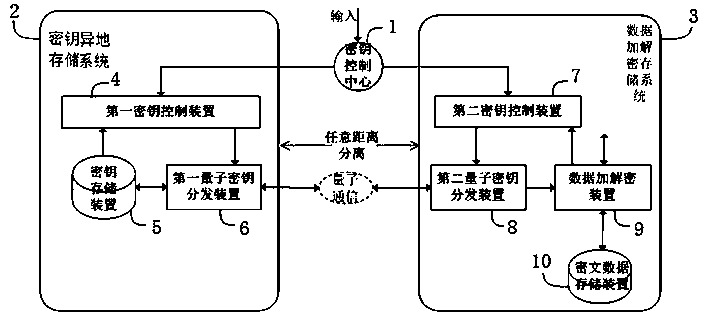
The invention discloses an encrypted data storage system based on key other-place storage and method. The encrypted data storage system based on key other-place storage comprises a key control center,a key other-place storage system and a data encryption and decryption storage system, wherein the key other-place storage system comprises a first key control device, a key storage device and a firstquantum key distribution device; the data encryption and decryption storage system comprises a second key control device, a data encryption and decryption storage device and a second quantum key distribution device; the first quantum key distribution device and the second quantum key distribution device are in quantum communication connection; the first key control device is in communication connection with the key storage device and the first quantum key distribution device respectively; and the second key control device is in communication connection with the data encryption and decryptionstorage device and the second quantum key distribution device respectively. The key other-place storage system and the data encryption and decryption storage system can be separated at any distance safely and reliably, and other-place separate and safe storage between encryption and decryption keys and data can be realized.
Owner:ANHUI QASKY QUANTUM SCI & TECH CO LTD
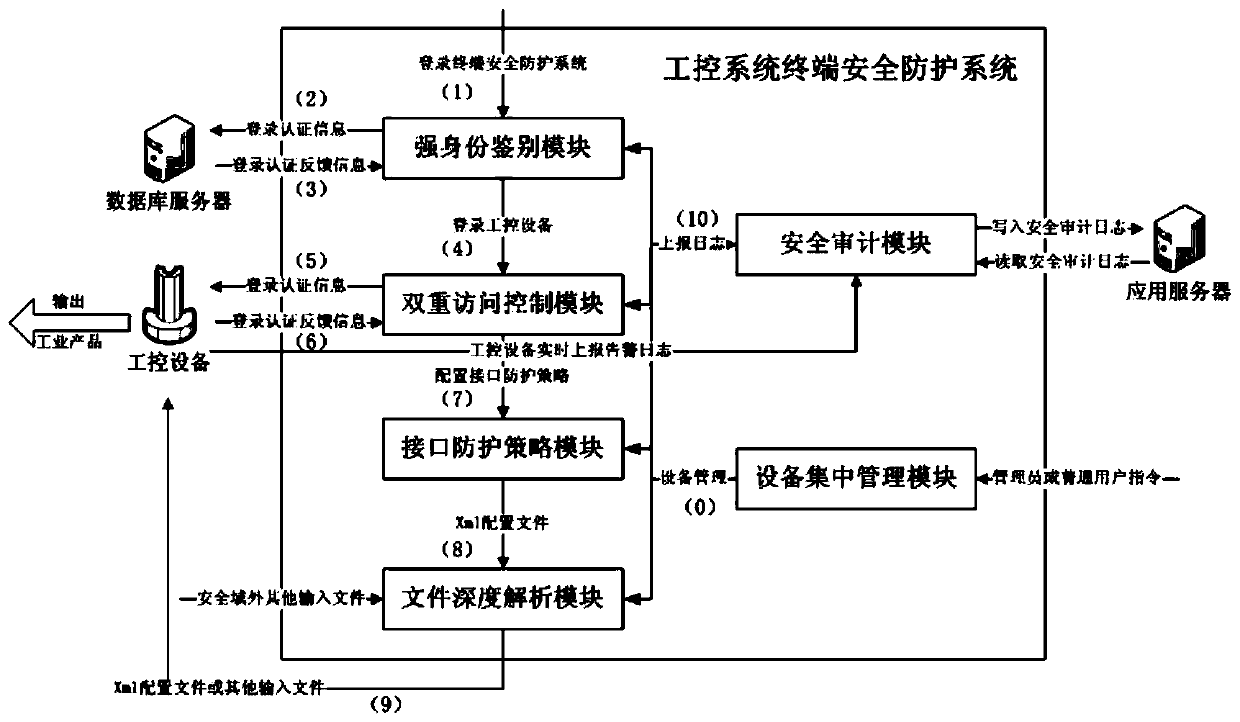
Industrial control system terminal safety protection system
ActiveCN109976239AImprove the protective effectImprove the level ofProgramme controlComputer controlEngineeringCentralized management
The invention belongs to the technical field of safety protection of industrial control system terminals and particularly relates to an industrial control system terminal safety protection system. Theindustrial control system terminal safety protection system comprises a terminal safety protection device and a terminal safety centralized management system. According to the scheme, a series of technological means of strong identity authentication, double access control, an interface protection strategy, file depth analysis, safety audit and equipment centralized management are comprehensivelyapplied, so that malicious behaviors such as network attack, illegal access and the like during operation of the industrial control system equipment are effectively blocked, and meanwhile, centralizedconfiguration and management on safety protection strategies of a plurality of industrial control system equipment terminals of the same type or different types can be realized. The scheme has the advantages that the safety protection level of the industrial control equipment terminal is high, the centralized and unified management of multiple equipment is supported, the centralized management platform is suitable for various application environments and multiple industrial protocols, the compatibility is good, adding and deleting of the equipment is simple, configuration of the protection strategies is flexible, alarm reporting and equipment management are efficient, and the like.
Owner:北京京航计算通讯研究所
Real-time flow monitoring and abnormity early warning system and method for wireless internet of things
InactiveCN108076053ARealize online real-time collectionRealize transmissionTransmissionSecurity arrangementEarly warning systemReal time analysis
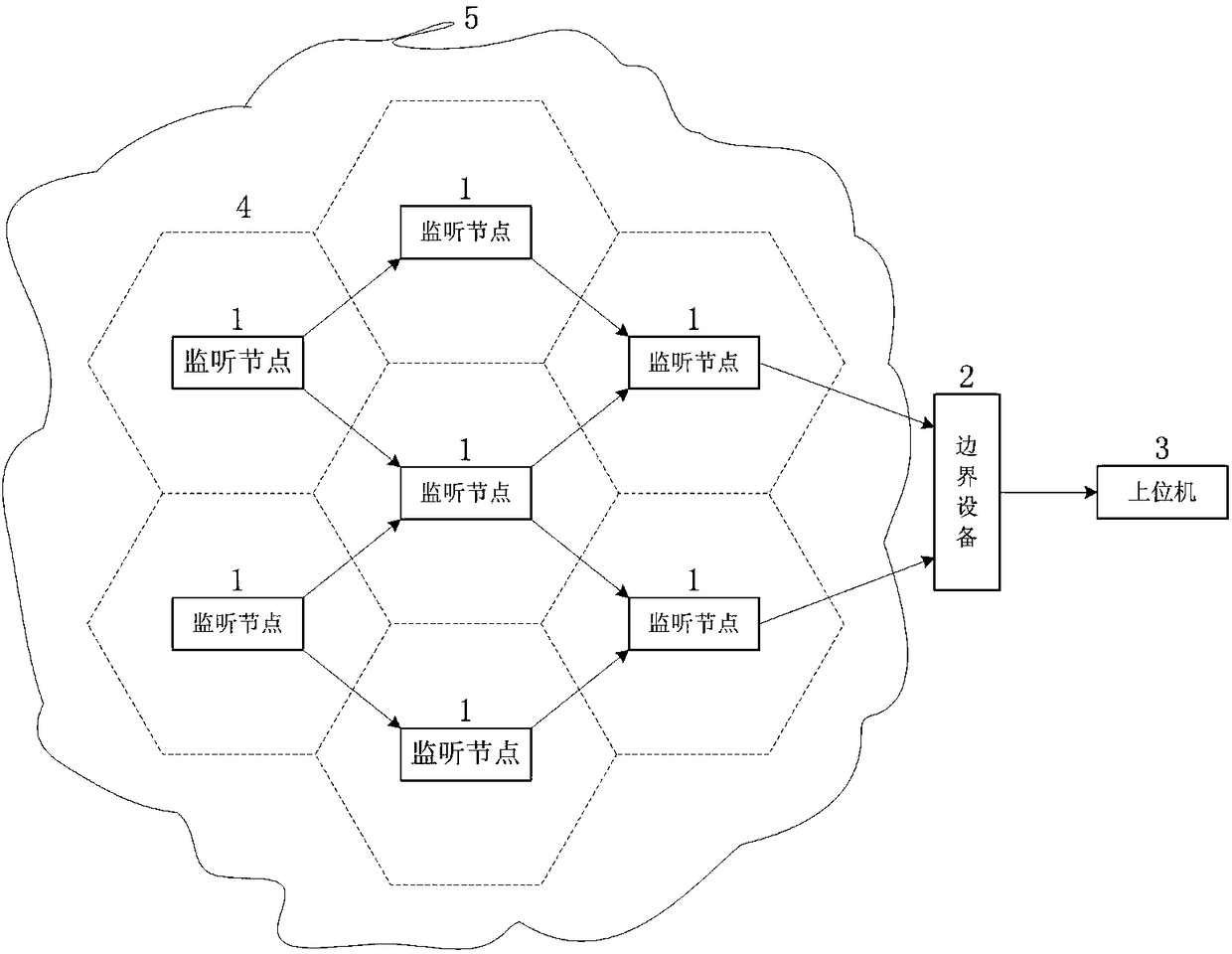
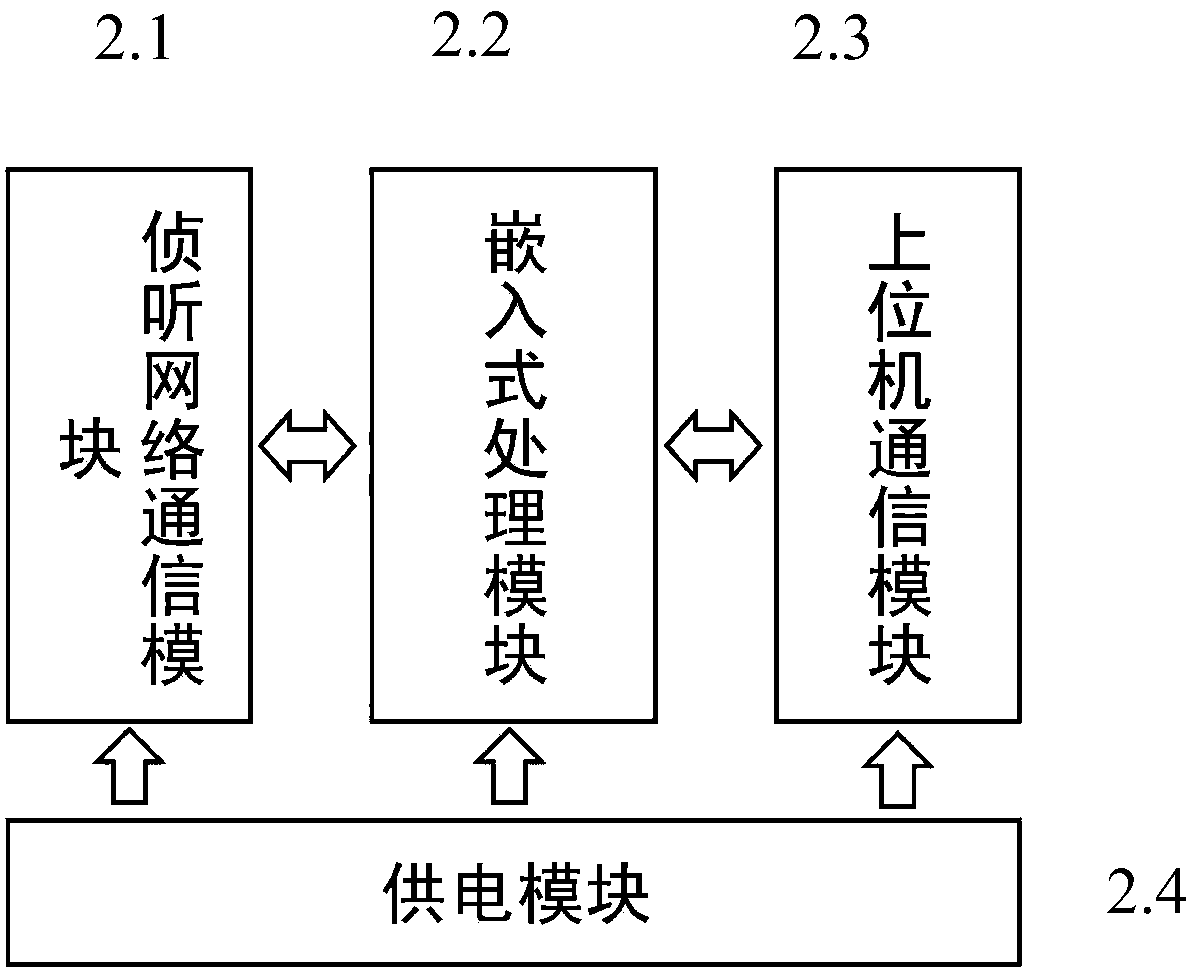
The invention relates to a real-time flow monitoring and abnormity early warning system and method for wireless internet of things; the system is technically characterized by comprising a plurality ofmonitoring nodes, boundary equipment and an upper computer, wherein the output ends of the monitoring nodes are sequentially connected and are used for monitoring and collecting the data traffic of the wireless internet of things in real time; the output ends of the monitoring nodes are respectively connected with the boundary equipment and are used for outputting the data traffic of the wirelessinternet of things detected by the monitoring nodes to the boundary equipment in real time; the output end of the boundary equipment is connected with the upper computer and is used for outputting the data flow of the wireless internet of things to the upper computer through the boundary equipment and for performing real-time on-line analysis and processing on the data traffic of the monitored wireless internet of things. According to the system and method, online real-time analysis processing of the network traffic of the wireless internet of things can be realized, network abnormity and malicious intrusion events of the wireless internet of things can be found in real time, and the system and the method have important significance for guaranteeing the system integrity and the information safety of the wireless internet of things.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +3
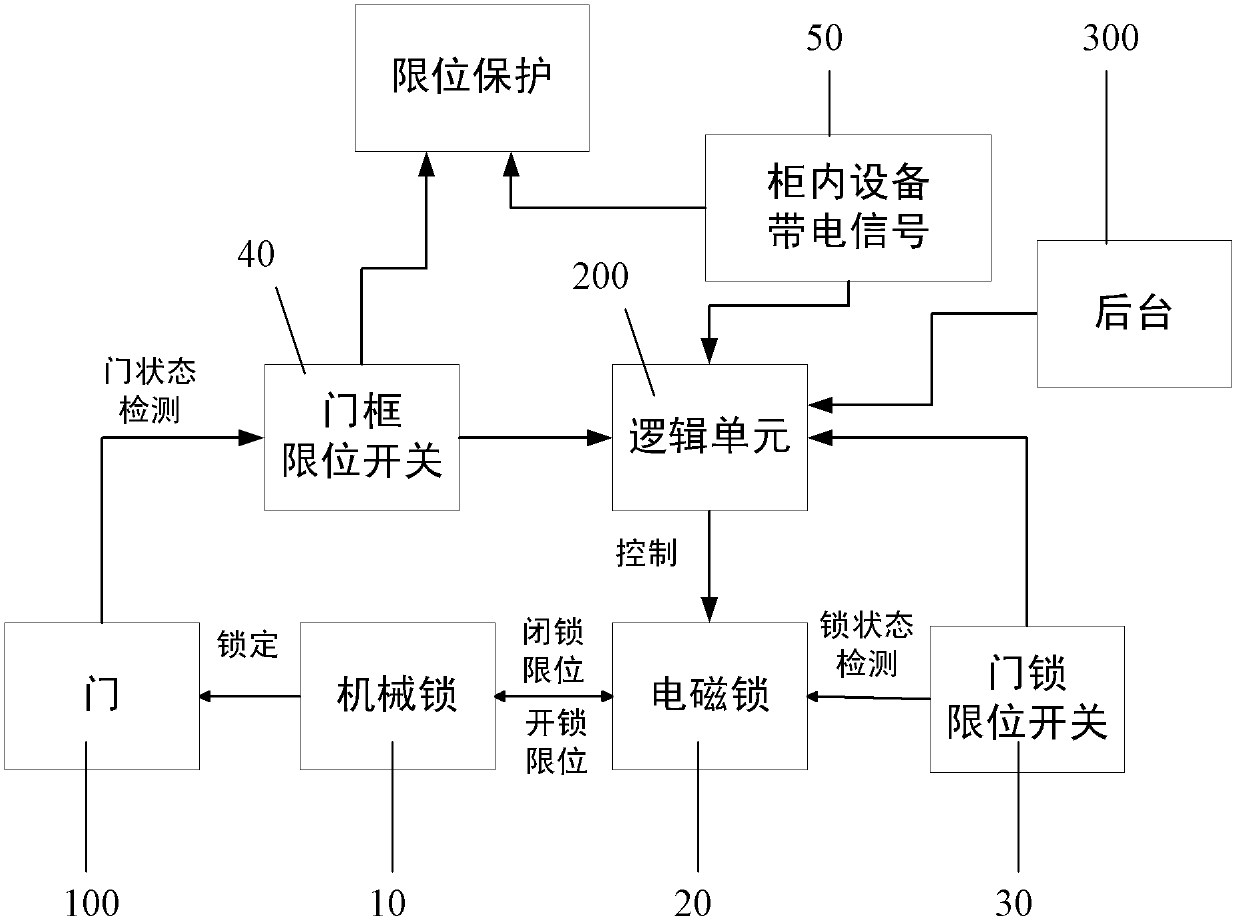
Cabinet type device door lock system and control method thereof
ActiveCN102606008AEnsure safetyGuaranteed power-down stateNon-mechanical controlsElectricityElectromagnetic lock
The invention discloses a cabinet type device door lock system and a control method of the cabinet type device door lock system. The system comprises a logic unit, and a connecting rod type mechanical door lock, an electromagnetic lock and a sensor A, which are arranged on a cabinet type device door, wherein the electromagnetic lock, the sensor and voltage signals of a device in a cabinet are respectively in signal connection with the logic unit; a lock piece of the electromagnetic lock is matched with a fixing piece of a locking structure on a lock rod of the mechanical door lock, and the locking piece and the locking structure are matched to realize the locking to the mechanical door lock due to the electromagnetic lock at the position where the mechanical lock locks the cabinet type device door; the method is realized based on the cabinet type device door lock system, and the logic unit receives locking signals of the mechanical lock of the sensor A, sends electrifying signals to the device in the cabinet after receiving all door-closing signals and controls the locking of the electromagnetic lock; and when the device in the cabinet is in power down, the voltage signals of the device in the cabinet are transmitted to the logic unit, and the logic unit controls the unlocking of the electromagnetic lock. According to the invention, the power down of the device in the cabinet after the cabinet door is unlocked is ensured, and the safety of the maintenance personnel can be ensured.
Owner:SHENZHEN HOPEWIND ELECTRIC CO LTD
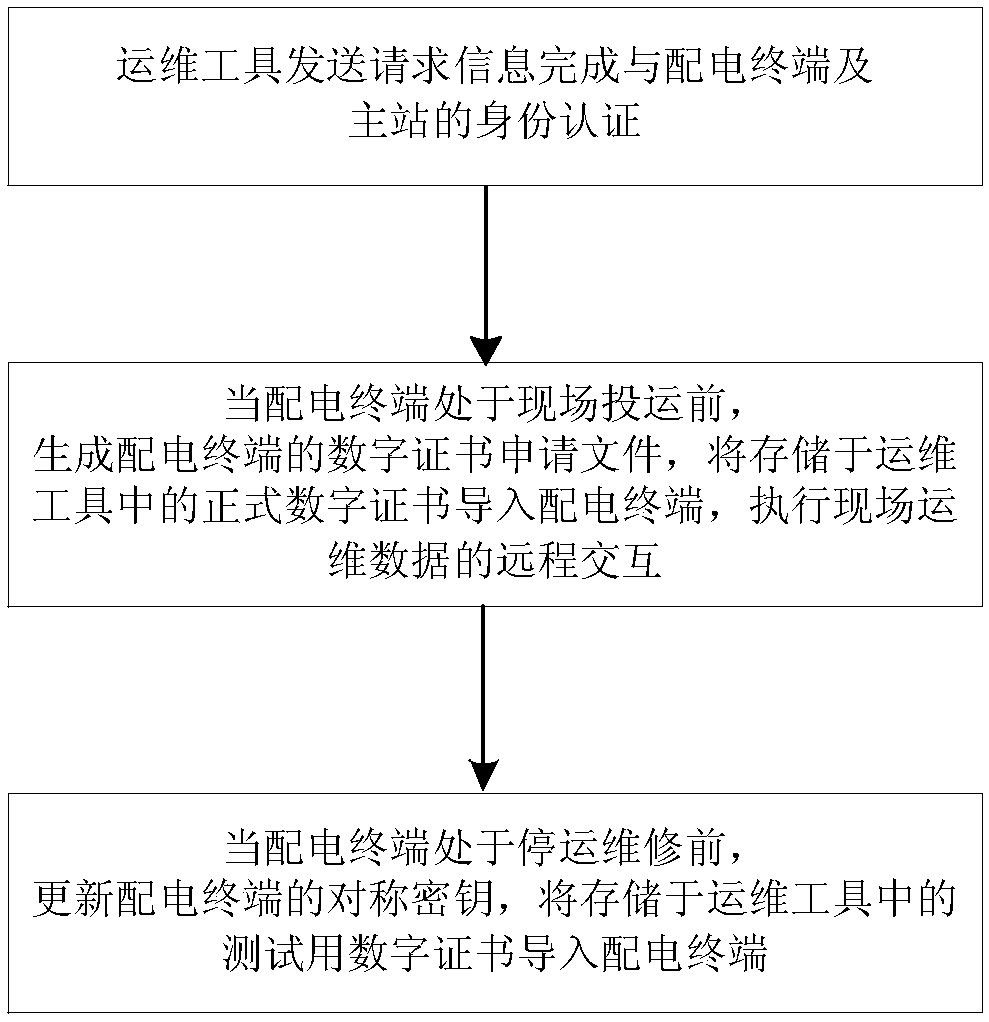
Method and a device for safely interacting on-site operation and maintenance data
ActiveCN109257328APrevent imitationAvoid destructionKey distribution for secure communicationCircuit arrangementsMaster stationComputer terminal
The invention relates to a method and a device for safely interacting on-site operation and maintenance data, comprising the following steps: an operation and maintenance tool sends request information to complete identity authentication with a power distribution terminal and a master station; generating a digital certificate application file of the distribution terminal before the distribution terminal is put into operation on site, importing a formal digital certificate stored in an operation and maintenance tool into the distribution terminal, and performing remote interaction of the fieldoperation and maintenance data; when the distribution terminal is out of service, the symmetric key of the distribution terminal is updated, and the test digital certificate stored in the operation and maintenance tool is imported into the distribution terminal. This scheme improves the management flow of digital certificate and symmetric key, and makes up for the security loopholes in the operation and maintenance process of distribution terminals, so as to improve the security protection level of field application and operation and maintenance of distribution terminals.
Owner:CHINA ELECTRIC POWER RES INST +1
Computer system safety protection setting method and its device
InactiveCN101071459AImprove the level of security protectionDigital data authenticationData setComputer users
A computer system's security protection method and setup equipment belongs to computer systems technology involved in supporting the implementation of the data protection features of the computer. Have a choice to stay preventing the competence of the user runs the specific methods and procedures for equipment, and methods include: user mode implementation of the provision of data protection steps; 'whether to implement the show bit' set up operations. The state is set to executable steps on the user access authentication, to confirm whether the user has the rights to the steps if there is the competence of users, will be 'whether to implement the show bit' Setup is changed to the status of the executable steps. According to the invention, the data set in the implementation of the function of the computer system, on the other users on the network bank or personal safety information related to the operation of the certification process, so as not to impede a legitimate authority of computer users use other procedures, greatly enhance the system's security.
Owner:LEJIN ELECTRONICS KUNSHAN COMPUTER CO LTD
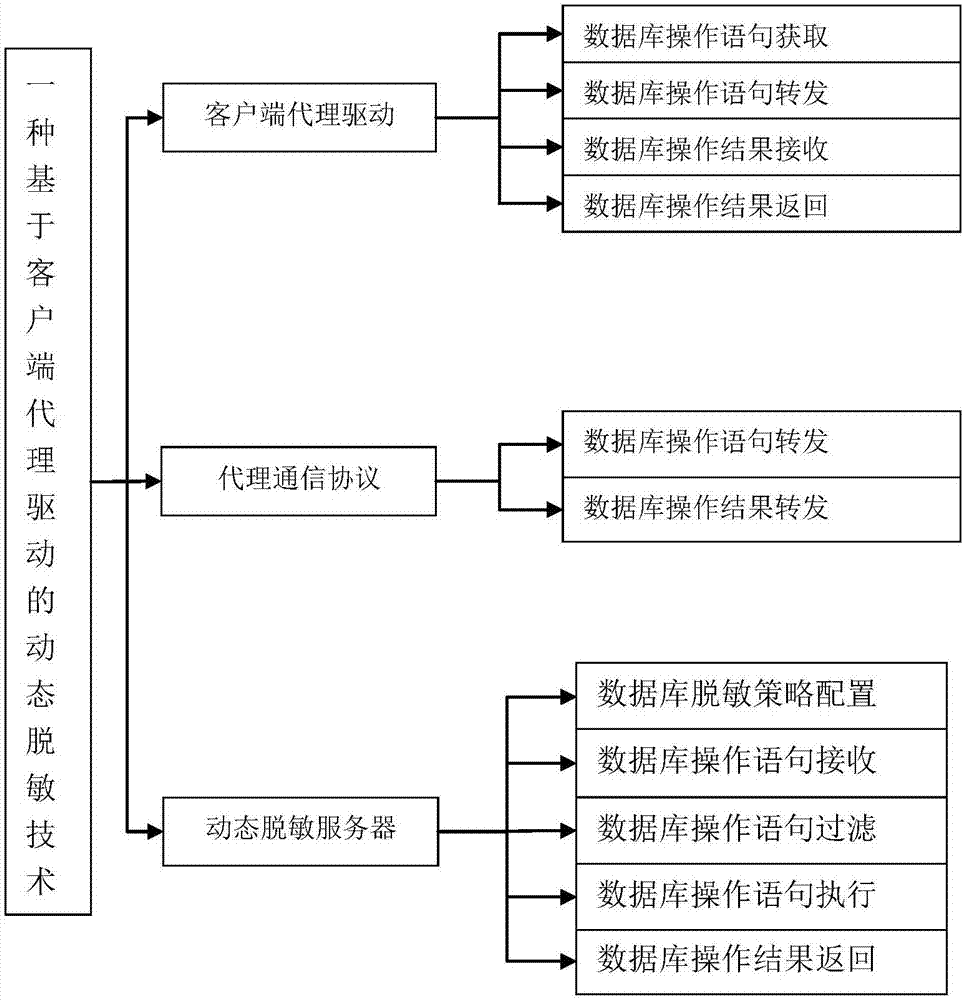
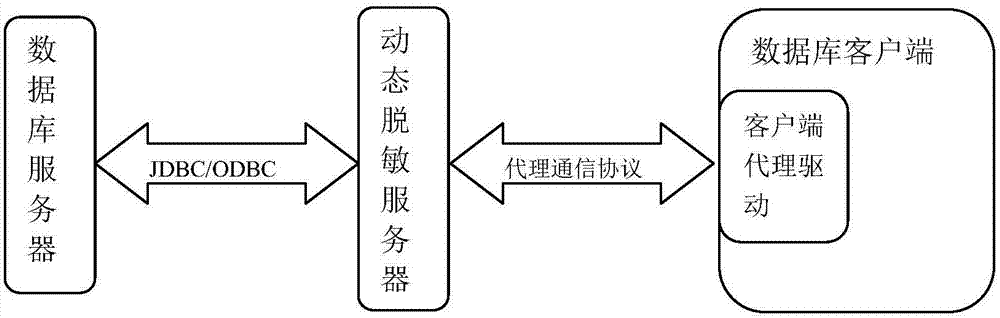
Dynamic database desensitization method and equipment
InactiveCN107194276AReduce risk of leakageElevate the authority control levelDigital data protectionSpecial data processing applicationsUplevelData access
The purpose of the invention is to provide a dynamic database desensitization method and equipment. The method comprises the steps: a client proxy driver acquires a database operation statement of an upper-layer application through a standard client driver interface; and the client proxy driver returns a desensitized execution result to the upper-layer application through the standard client driver interface. The client proxy driver can be compatible to a mainstream database manufacturer and a big data analysis platform easily; in addition, the overall filtering and permission control can be carried out on the operation statement and / or the returned result, thus the permission control grade of database access is improved, the safety protection grade of data access is enhanced and the data leakage risk is reduced.
Owner:SUNINFO INFORMATION TECH
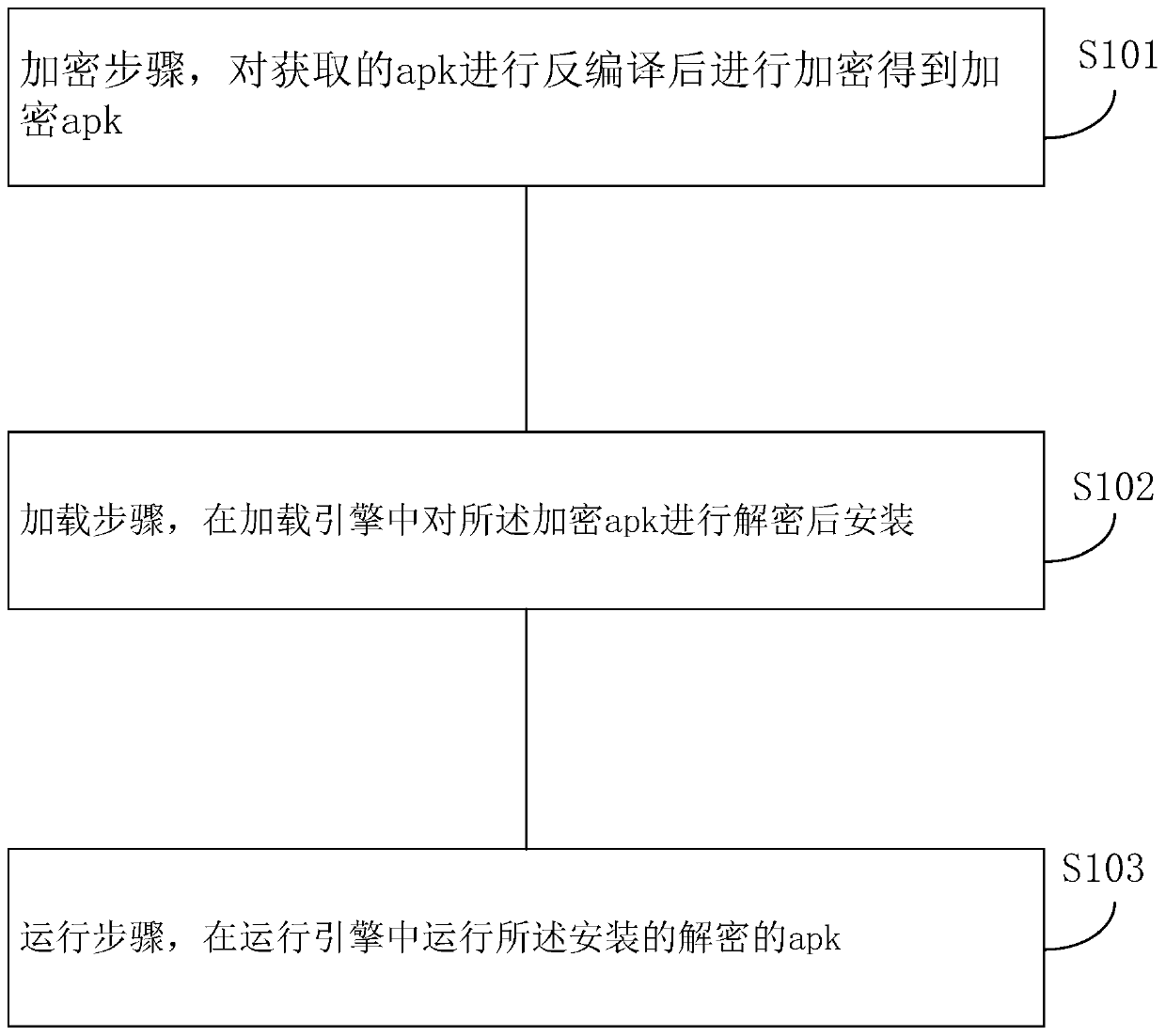
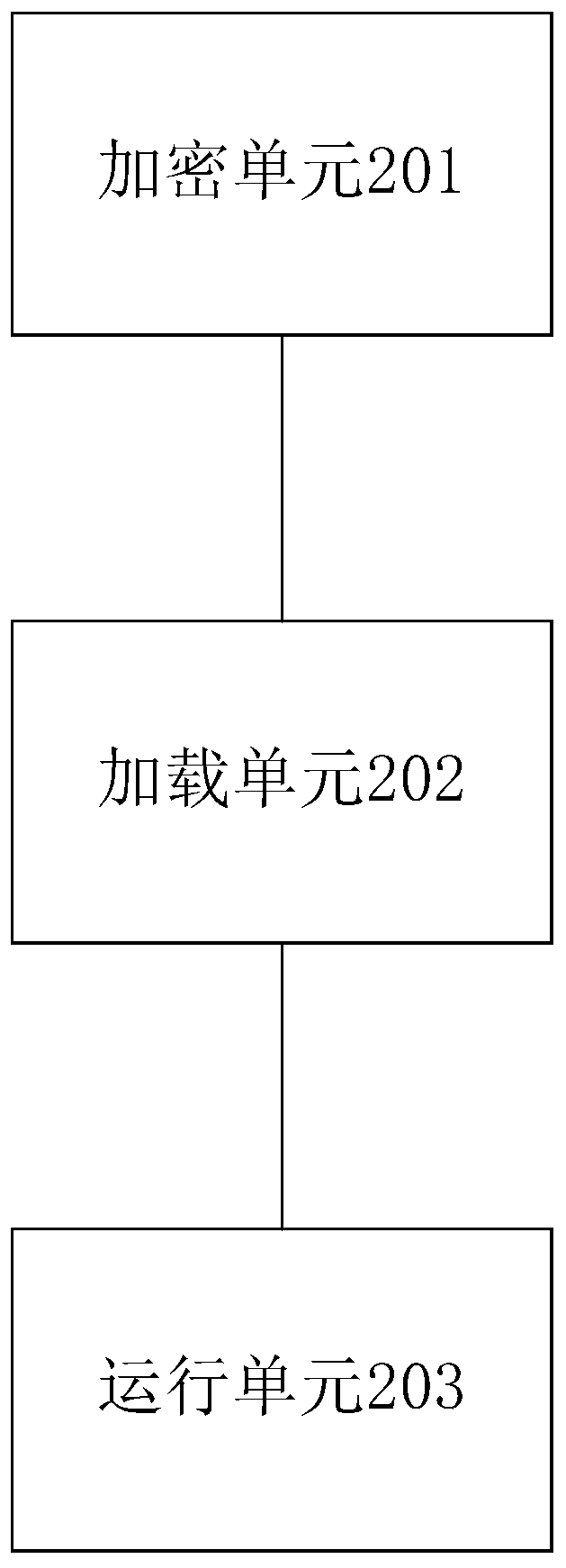
Security protection method and device for Android platform application and storage medium
InactiveCN109858203AImprove securityImprove the level of security protectionProgram/content distribution protectionComputer hardwareEncryption
The invention provides a security protection method and device for an Android platform application and a storage medium. The method comprises the following steps: an encryption step: decompiling an obtained apk, and encrypting the obtained apk to obtain an encrypted apk; a loading step: decrypting the encrypted apk in a customized system loading engine and then installing the encrypted apk; and arunning step: running the installed decrypted apk in a customized system running engine. According to the invention, resources are confused; encrypting the dex files respectively; so file, the resource file and the like are repackaged to obtain an encrypted apk; Safety is higher, the safety protection level of the application is improved. The released application does not contain a decryption code. The decryption code is written in a customized Android system. A cracker wants to crack the source program and must perform reverse analysis on the encrypted application and the customized Android system at the same time, so that the cracking difficulty is greatly increased, and meanwhile, as the program is decrypted by the customized Android system instead of self-decryption of the program, theoperation efficiency of the application is improved.
Owner:XIAMEN MEIYA PICO INFORMATION
Network protocol safety test method and device, electronic equipment and storage medium
ActiveCN110752966AImprove the level of security protectionImprove the protective effectData switching networksNetworking protocolEngineering
The invention provides a network protocol safety test method and device, electronic equipment and a storage medium. The method comprises the following steps: establishing a plurality of protocol models of a plurality of protocol layers of a protocol set based on an original message of the network protocol set; generating a plurality of variation messages according to the plurality of protocol models and variation strategies; sending the variation message and the background flow message to the equipment to be tested; and monitoring a transmission process of the to-be-tested device in receivingthe variation message and the background flow message so as to judge whether the to-be-tested device is safe or not.
Owner:NR ELECTRIC CO LTD +1
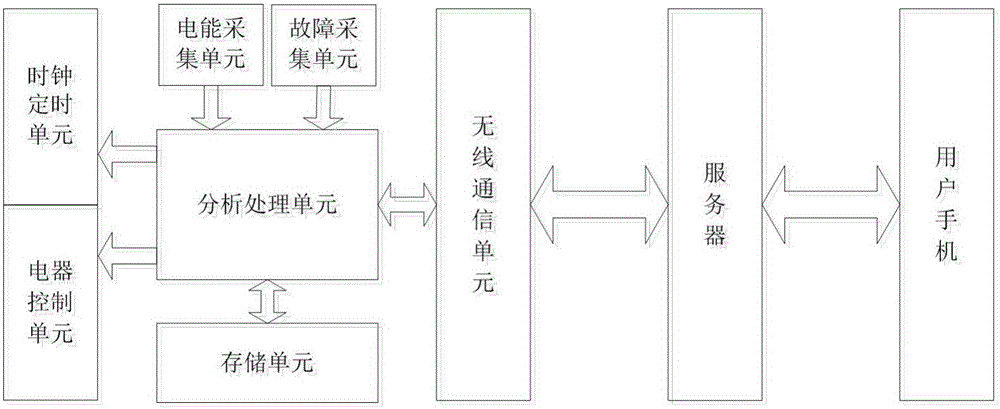
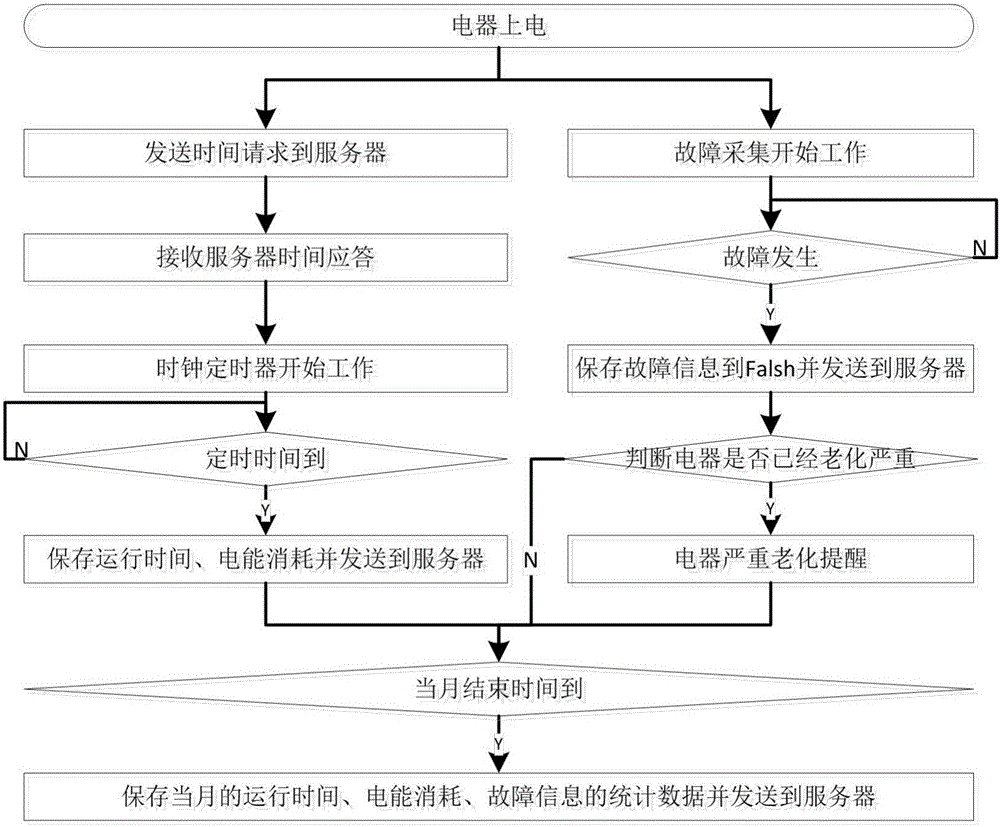
Continuous electric appliance aging degree detection system and detection method based on Internet
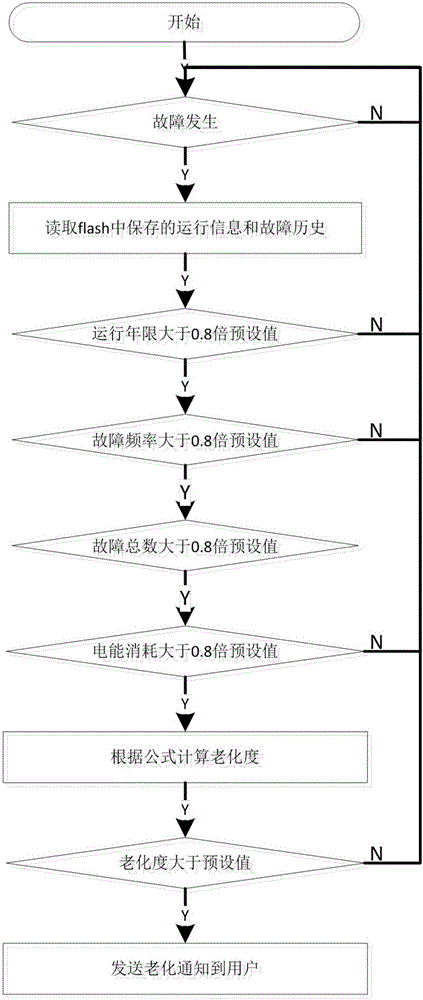
ActiveCN106199261AContinuous detection of agingReduce wasteElectrical testingTransmissionThe InternetEmbedded system
The invention discloses a continuous electric appliance aging degree detection system and detection method based on the Internet. The detection system comprises a clock timing unit, an electric energy collecting unit, a fault collecting unit, an analysis processing unit and a storing unit. According to the detection system and detection method, by combining an electric appliance with the Internet, the aging degree of the electric appliance is continuously detected, reminding is made, the safety protection level of people is increased, therefore, social resource waste is reduced, and electric appliance disasters are reduced or avoided.
Owner:CHIPSEA TECH SHENZHEN CO LTD
Comprehensive pipe gallery intelligent tour inspection system
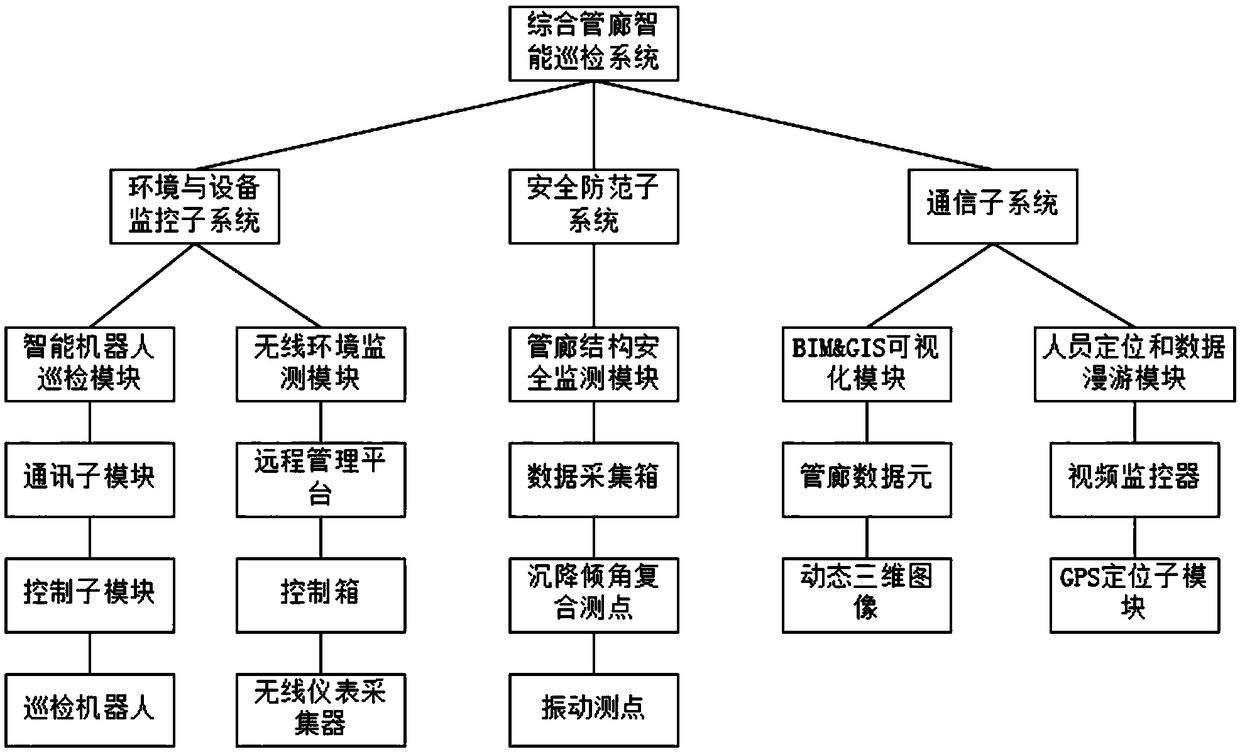
InactiveCN109238359AImprove the level of security protectionIntelligent information service comprehensive platformData processing applicationsMeasurement devicesInformatizationSecurity monitoring
The invention belongs to the field of pipeline gallery tour inspection, and specifically relates to a comprehensive pipe gallery intelligent tour inspection system. The system comprises an environmentand equipment monitoring sub-system, a security protection sub-system, and a communication subsystem, the environment and equipment monitoring subsystem comprises an intelligent robot tour inspectionmodule and a wireless environment monitoring module, the security protection subsystem comprises a pipeline gallery structure security monitoring module, and the communication subsystem comprises a BIM & GIS visualization module and a personnel positioning and data roaming module. According to the comprehensive pipe gallery intelligent tour inspection system, comprehensive informatization management of underground comprehensive pipeline galleries is realized, an intelligent, high-efficiency and stable information service comprehensive platform is provided for detection and emergency command of the comprehensive pipeline galleries, and the security protection level of the comprehensive pipe galleries is improved.
Owner:合肥市信同信息科技有限公司
Electromagnetic soft contact continuous casting crystallizer
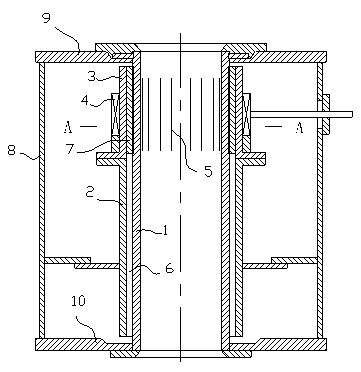
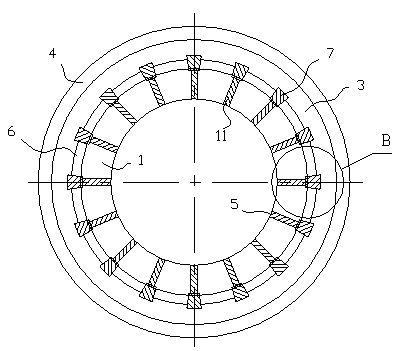
ActiveCN102371348AGuaranteed electromagnetic permeabilityGuaranteed service lifeEngineering plasticEngineering
The invention relates to a kerf-valving external water-cooled type electromagnetic soft contact continuous casing crystallizer, comprising a kerf copper pipe (1), an upper-section inner water jacket (3), a lower-section inner water jacket (2), an electromagnetic induction coil (4), a shell (8), an upper flange (9) and a lower flange (10), wherein the shell (8), the upper flange (9) and the lower flange (10) constitute a crystallizer assembly structure; the upper-section inner water jacket is made of engineering plastics and is sleeved in the electromagnetic induction coil; a groove (12) is machined on the outer wall of the outer wall surface of the kerf copper pipe along each kerf (5); a high-temperature resisting insulation sheet (11) is inserted into each kerf; bonding glue (120) is coated and filled in the groove; the edge of the inserted tail end of the insulation sheet slightly protrudes out of the bottom plane of the groove; and the high-temperature resisting insulation sheets and the serf copper pipe are fixed by the binding glue. A top rib sealing bar (8) which aims at each kerf is arranged between the outer wall of the kerf copper pipe and the upper-section inner water jacket. The invention has the advantages of strong electromagnetic permeability and safe and reliable cooling water path.
Owner:BAOSHAN IRON & STEEL CO LTD
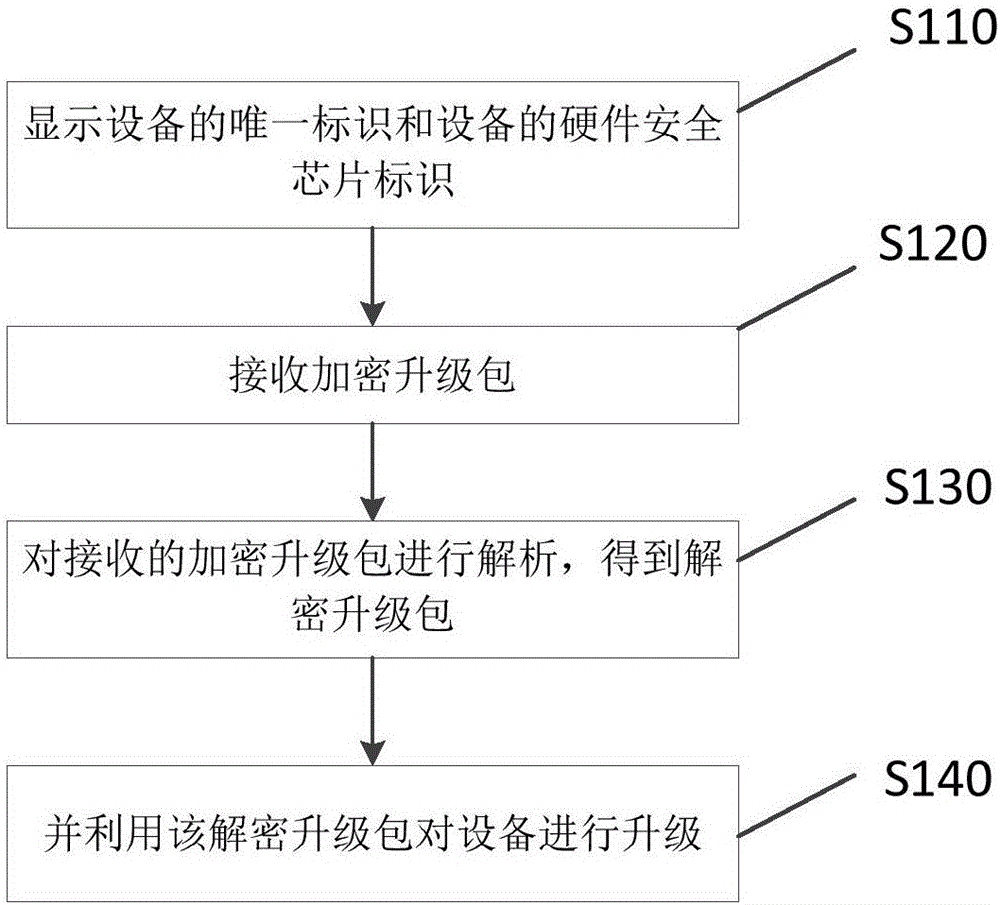
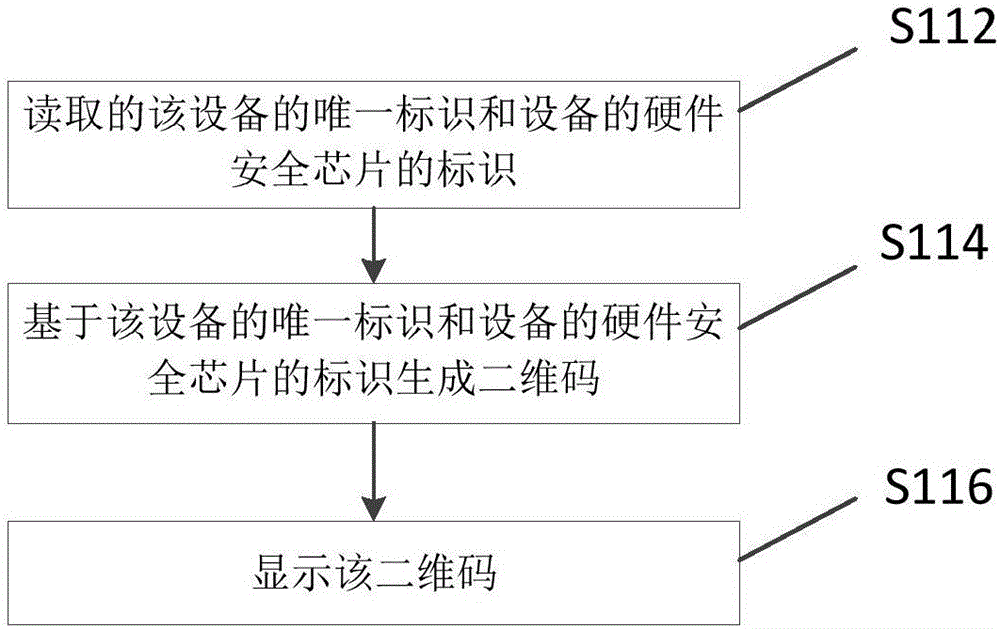
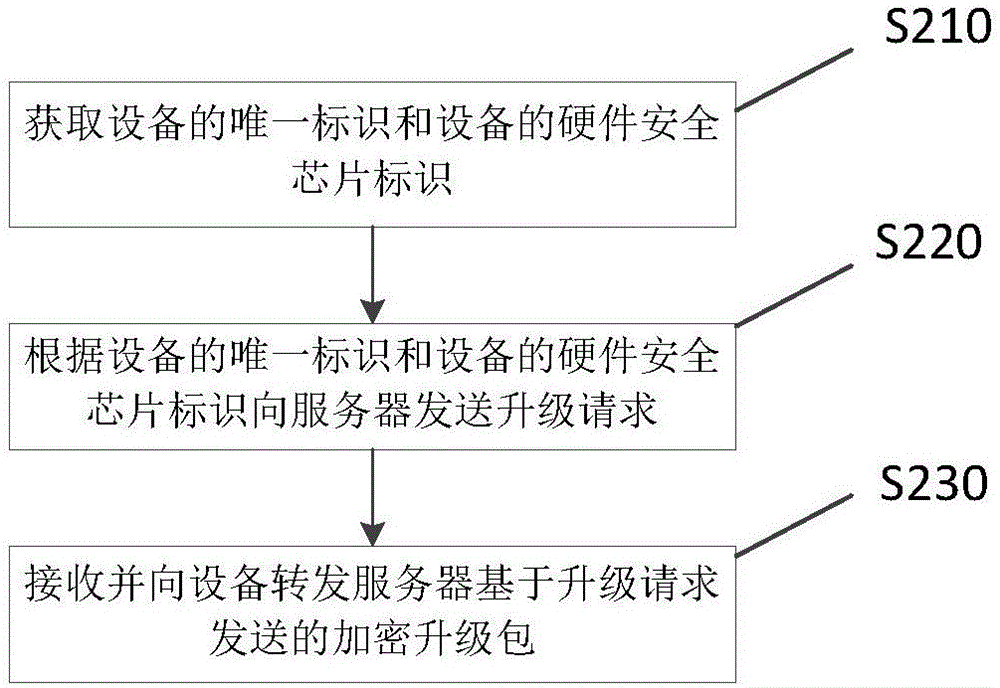
Method and device for upgrading equipment
PendingCN106778285AImprove the level of security protectionInternal/peripheral component protectionPlatform integrity maintainanceUnique identifierUpgrade
The invention relates to the technical field of Internet of Things and discloses a method and device for upgrading equipment, which are used for an equipment end. The method comprises the following steps: displaying a unique identifier of the equipment and a hardware safety chip identifier of the equipment; receiving an encrypted upgrade package; analyzing the received encrypted upgrade package to obtain a decrypted upgrade package; upgrading the equipment by utilizing the decrypted upgrade package; and upgrading the equipment accessed into a network so as to improve the safety protection grade of the equipment.
Owner:MIDEA SMART TECH CO LTD +1
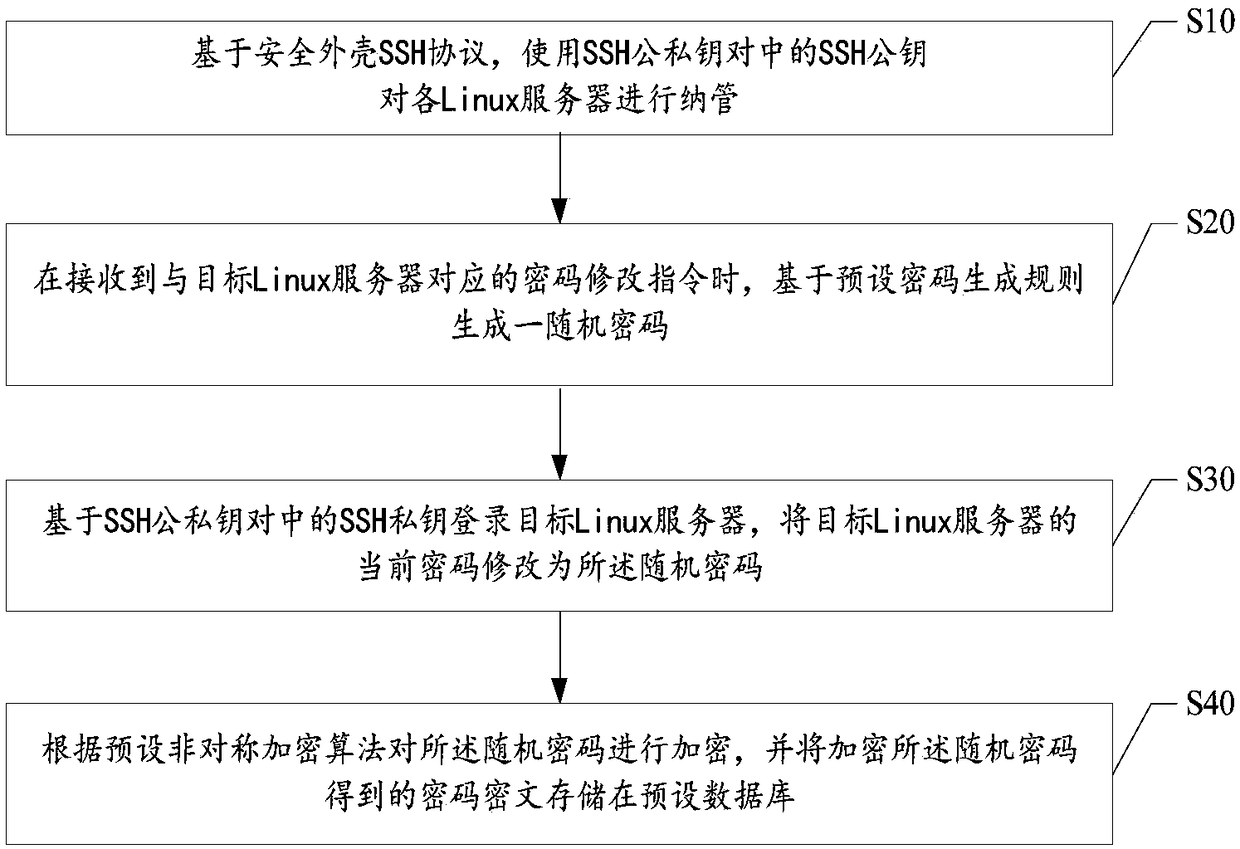
Linux password management method, central control computer, and readable storage medium
InactiveCN109472130AImprove the level of security protectionAvoid the risk of direct exposureDigital data authenticationCiphertextGNU/Linux
The invention provides a Linux password management method, which is applied to a central control computer. The method comprises the following steps: based on a secure shell SSH protocol, the SSH public key of an SSH public-private key pair is used for managing each Linux server; the SSH public key of the SSH public-private key pair is used for managing the Linux server. When receiving the passwordmodification instruction corresponding to the target Linux server, a random password is generated based on the preset password generation rule. Logging on the target Linux server based on the SSH private key in the SSH public-private key pair, and modifying the current password of the target Linux server to the random password; The random cipher is encrypted according to a preset asymmetric encryption algorithm, and the cipher cipher text obtained by encrypting the random cipher is stored in a preset database. The invention also provides a central control computer and a readable storage medium. The invention solves the technical problems that the password inquiry or modification is easy to make mistakes and the password security is poor in the prior Linux password management mode based onthe unified record file.
Owner:试金石信用服务有限公司
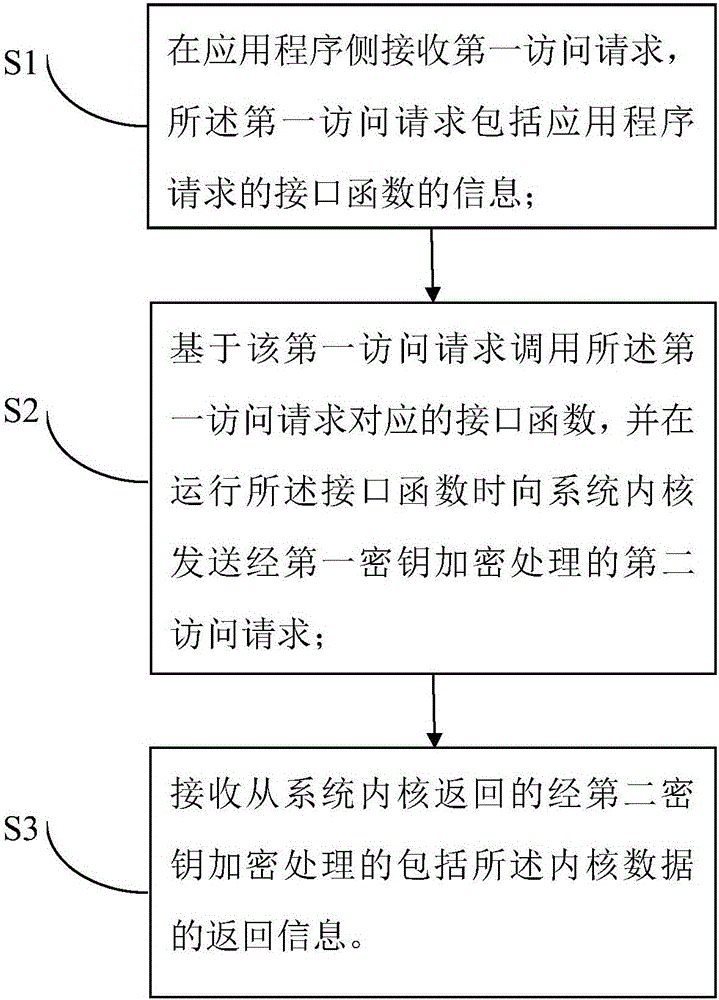
Application programming interface (API) protection method and device
ActiveCN106372497AImprove the level of security protectionPlatform integrity maintainanceApplication programming interfaceData needs
The invention provides an application programming interface (API) protection method and device. The method comprises the following steps: S1, receiving a first access request on an application program side, wherein the first access request includes information of an interface function of the application program request; S2, calling the interface function corresponding to the first access request based on the first access request, and sending a second access request encrypted by a first key to a system kernel during running of the interface function, wherein the second access request includes kernel data needed for executing the interface function; S3, receiving return information which is encrypted by a second key, includes the kernel data and is returned from the system kernel. By adopting the API protection method and device, higher anti-decoding performance and higher safety are achieved.
Owner:BEIJING SENSESHIELD TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com