Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
90 results about "Dual access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
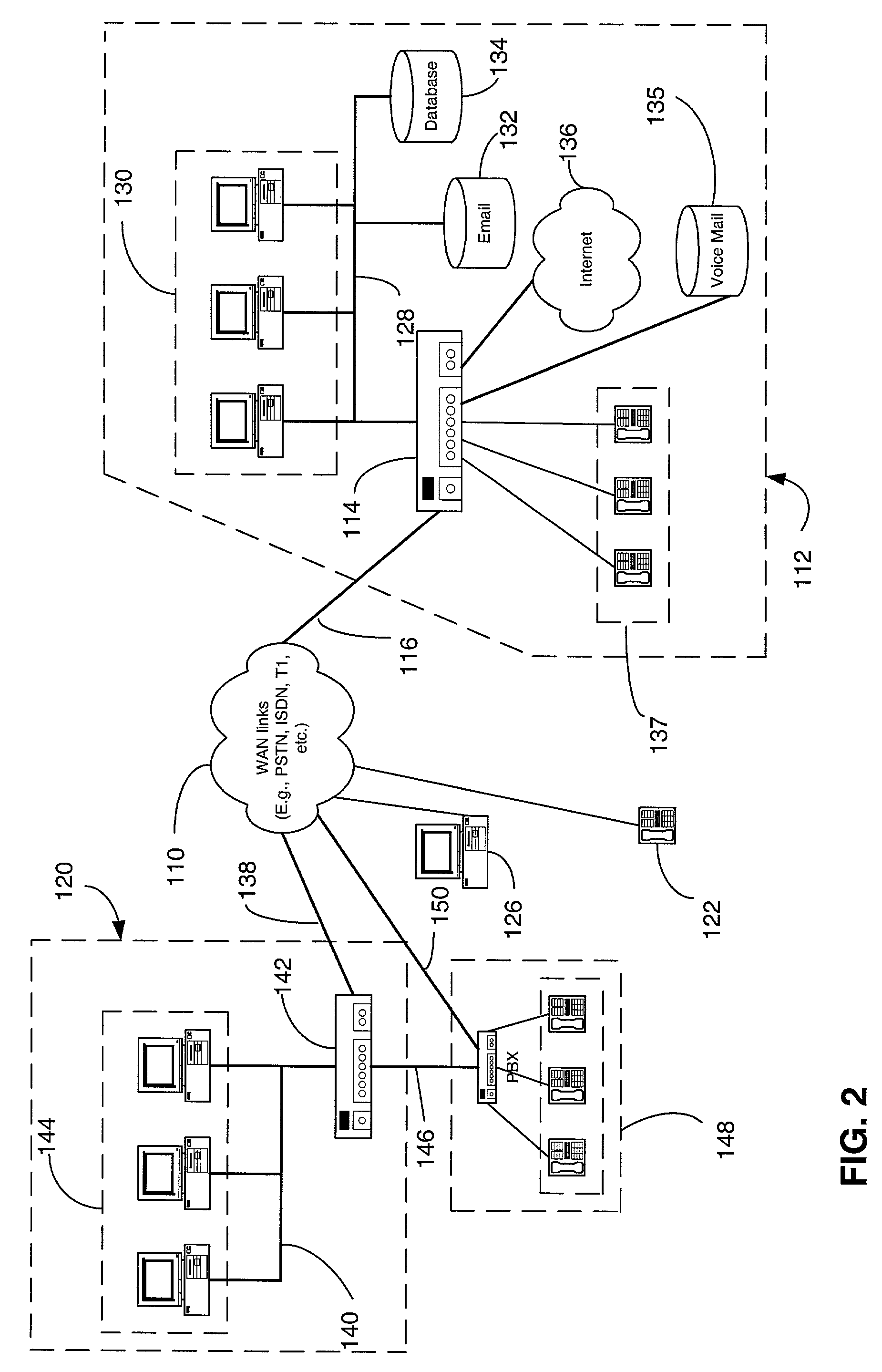
In telecommunication, the term dual access has the following meanings: The connection of a user to two switching centers by separate access lines using a single message routing indicator or telephone number. In satellite communications, the transmission of two carriers simultaneously through a single communication satellite repeater. Also, network hardware company D-Link has named technology which allows two simultaneous connections over one cable, for example 1) Internet and 2) provider's local FTP or game servers or IPTV data flow.
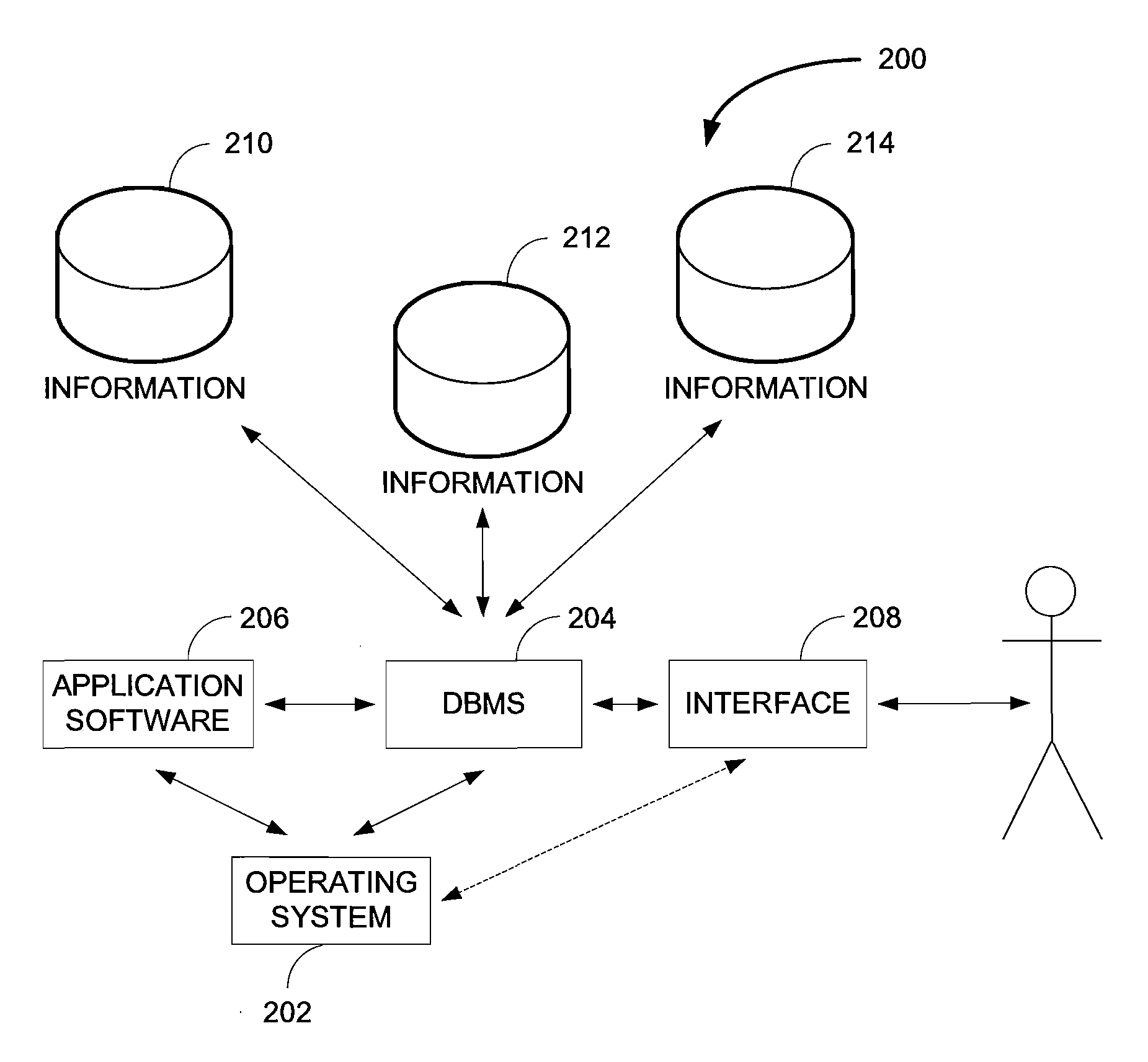
Dual access to concurrent data in a database management system
ActiveUS20090070330A1Digital data information retrievalDigital data processing detailsConcurrency controlRelational database management system
Various embodiments include one or more of systems, methods, software, and data structures that allow dual access to concurrent data in a database management system including uncommitted updated data. Some embodiments include a dual snapshot of data in a multi-version concurrency control style database, but the embodiments described herein are equally applicable to virtually any other type of database and database management system.
Owner:SAP AG
Voice print access to computer resources
InactiveUS7054819B1Automatic call-answering/message-recording/conversation-recordingSpeech analysisComputer resourcesVocal response
A dual-access communications server system is disclosed for enabling communication between server resources and a wide spectrum of end-terminals to enable users access to the resources of both converged and non-converged networks via voice and / or electronically generated commands. Server resources are provided through a converged computer / telephony system interface such that the data and resources are readily accessed by either voice or data calls. A set of applications provide dual interfaces for rendering services and data based upon the manner in which a user accesses the data. A user is authenticated by receiving vocal responses by a user to one or more requests variably selected and issued by a speaker recognition-based authentication facility. Thereafter, an application proxy is created. The application proxy acts on behalf of the authenticated authorized user in accessing applications via the dual-access communications interface.
Owner:MICROSOFT TECH LICENSING LLC
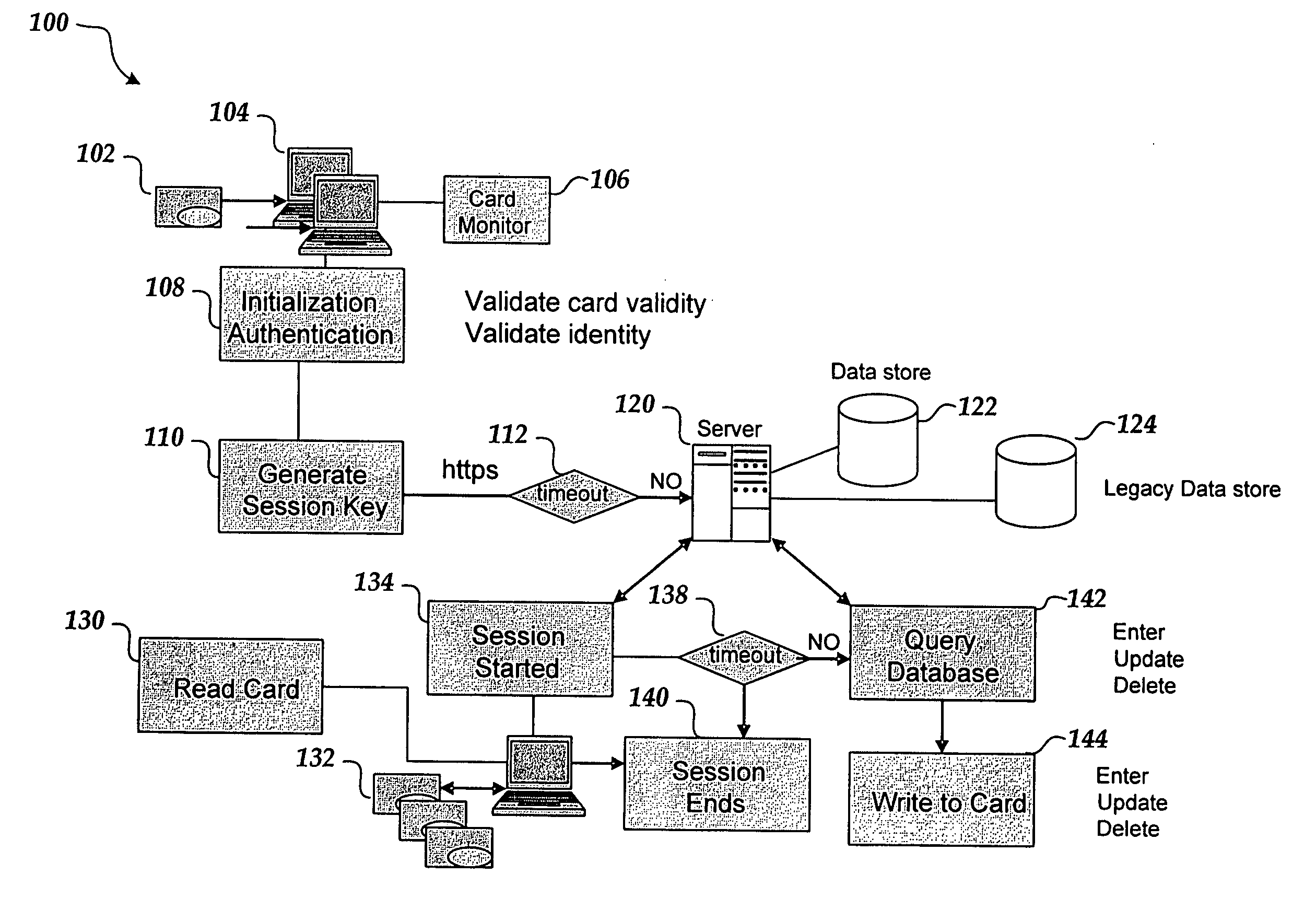
Dual-access security system for medical records
InactiveUS20080071577A1Reduce medical errorsConvenient careDigital data processing detailsUser identity/authority verificationMedical recordPassword
A secure system for accessing records uses a provider media device and a consumer media device to access records associated with the consumer. Both the consumer and provider media devices are normally authenticated before access to the consumer records is granted. Records can be centrally stored in a central location and downloaded, in full or in part, to the consumer media device. Passwords can be used to grant local access to consumer media device, for example, in the absence of network connectivity.
Owner:CHI SQUARE TECH
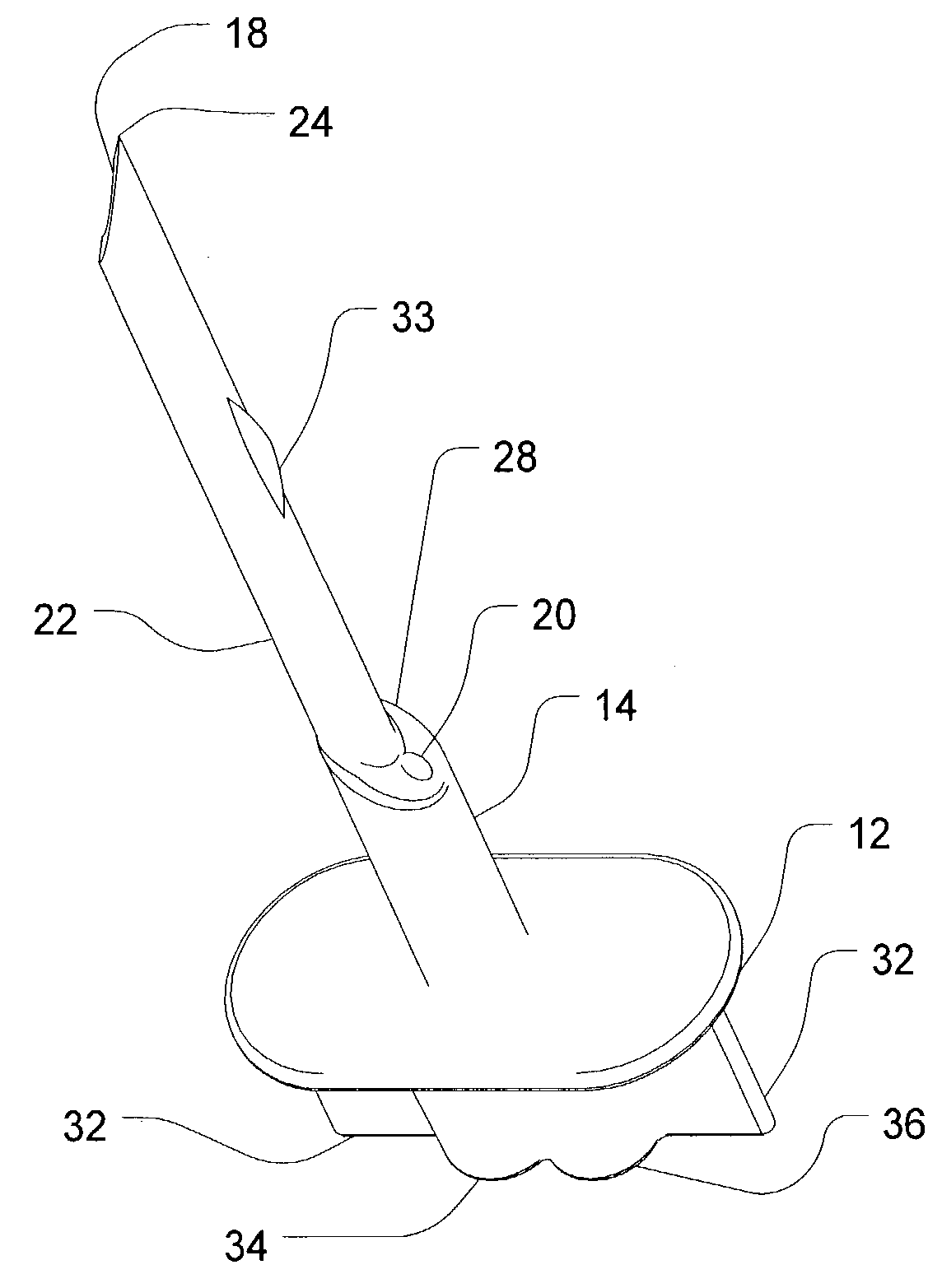
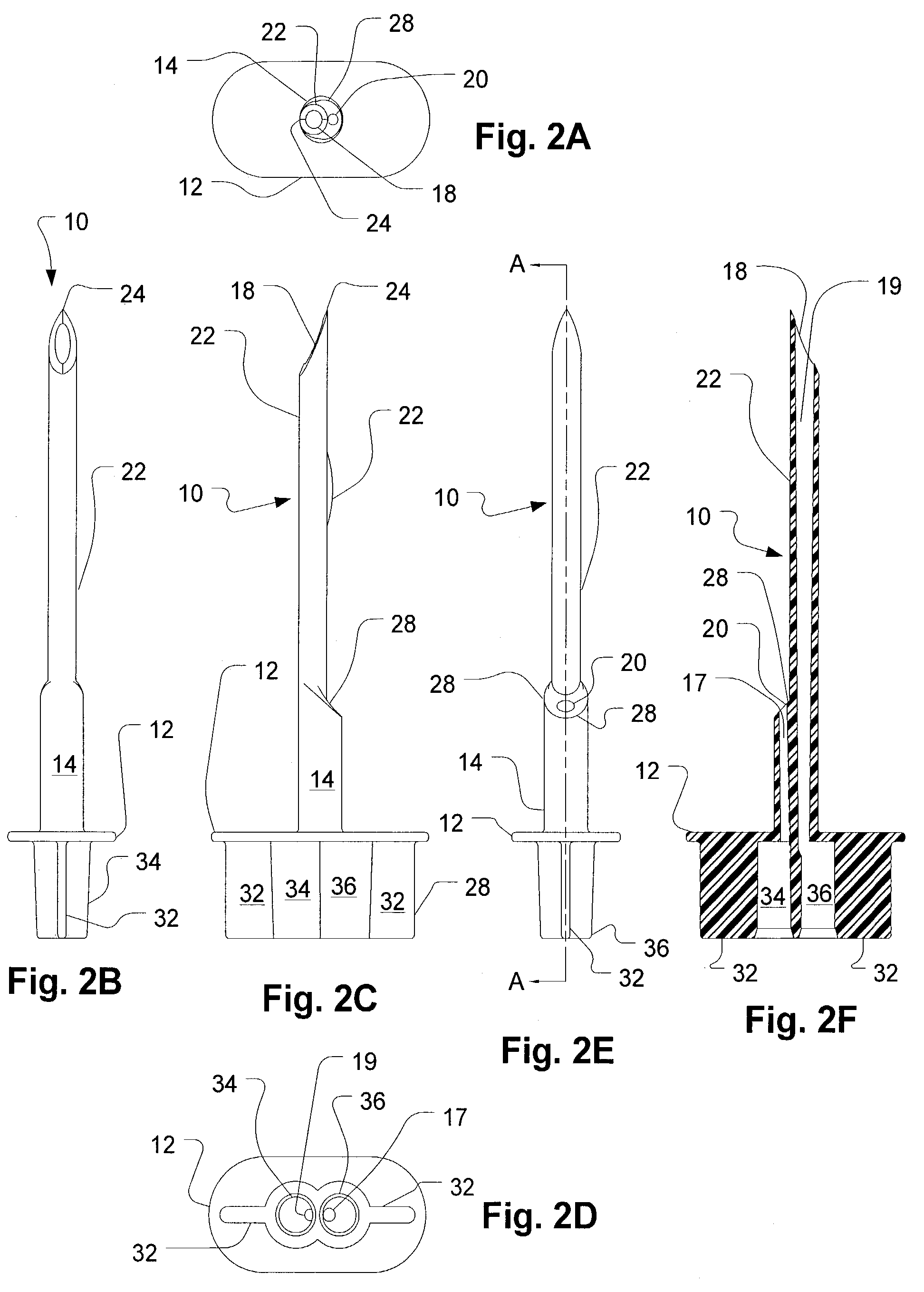
Dual access spike for infusate bags
ActiveUS7470265B2Reduce perforationEasy to insertDiagnosticsSurgeryDual accessMechanical engineering
Owner:NXSTAGE MEDICAL INC
System and method for transmitting high throughput data between multiple devices
A system for transmitting data directly between a plurality of client network devices in a network is disclosed. The system may include a first client network device having a first client (“STA”) module and a second client network device of the plurality of client network devices where the second client network device includes a Dual Access Point and Station enabled device (“DAS-enabled device”).
Owner:AVAGO TECH INT SALES PTE LTD
Dual access to concurrent data in a database management system
ActiveUS7930274B2Digital data information retrievalDigital data processing detailsConcurrency controlDual access
Various embodiments include one or more of systems, methods, software, and data structures that allow dual access to concurrent data in a database management system including uncommitted updated data. Some embodiments include a dual snapshot of data in a multi-version concurrency control style database, but the embodiments described herein are equally applicable to virtually any other type of database and database management system.
Owner:SAP AG
Dual Access Level Security System and Method
A dual or progressive access level security system and method is disclosed. The system receives or acquires one or more initial access identifiers of the user via an identity reader. In examples, the identity reader is a biometric scanner such as a fingerprint scanner that reads a fingerprint, or an antenna such as a Near Field Communication (NFC) antenna that reads an initial access identifier from a tag within a user device such as a fob or mobile phone or a Bluetooth identifier from the user's mobile computing device. In response to validation of the initial access identifier, the system presents virtual keys for the user to enter an access code. In embodiments, the virtual keys are included within a touchscreen and within a virtual projected keyboard presented by the security system. The security system grants access to the user in response to validation of the access code.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
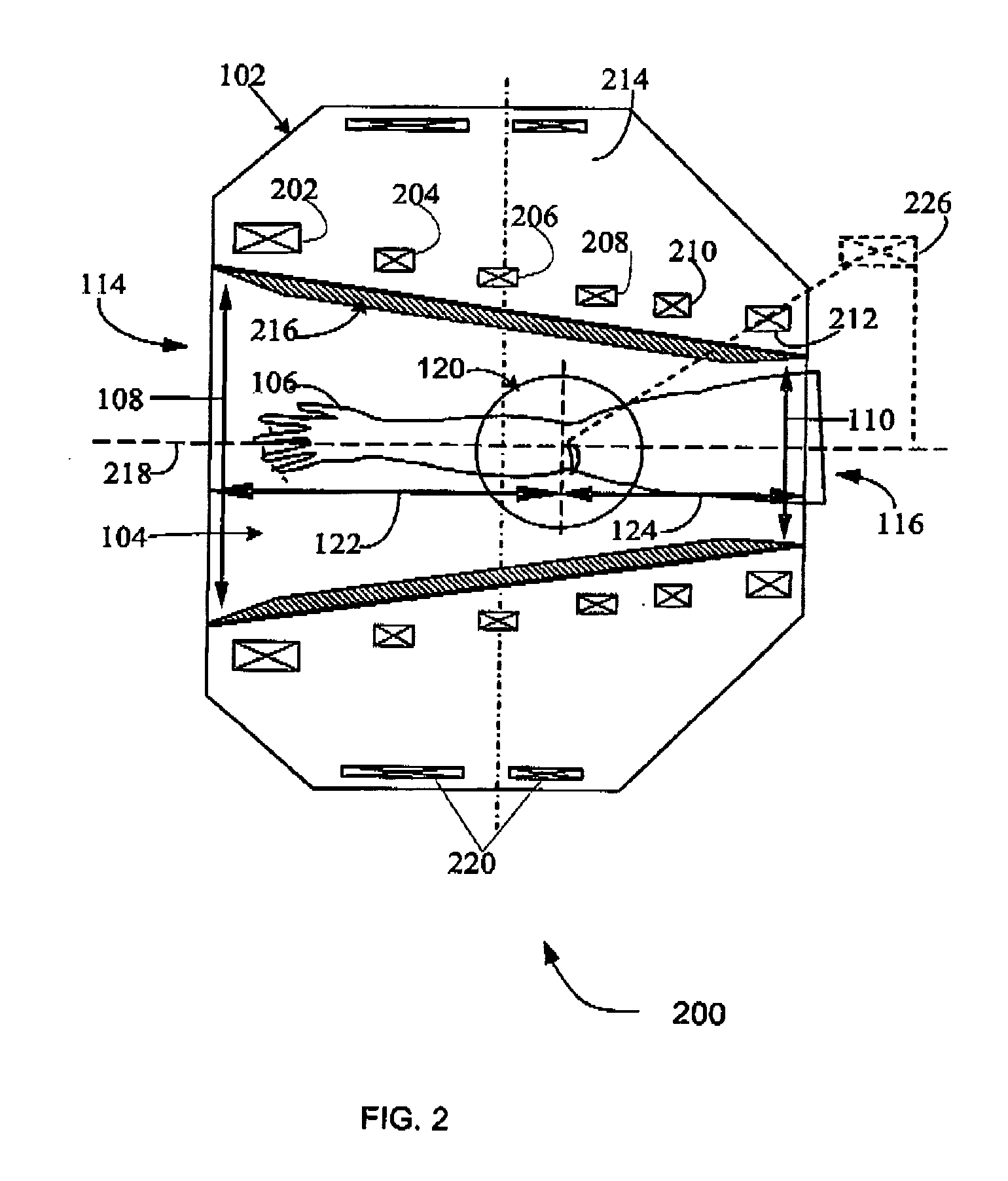
Systems, methods and apparatus for specialized magnetic resonance imaging with dual-access conical bore
An apparatus for magnetic resonance imaging is described having a casing with an inner bore which in some embodiments is substantially frustoconical shape for receiving a subject. The apparatus contains devices disposed in the casing to create a uniform field within an inner bore. The apparatus employs dual access since the inner bore has a first and second end at the outer edge of the casing for which the part of the subject's body would travel so as to be imaged. Further, in some embodiments, the apparatus provides one or more recesses for inserting at least one gradient coils into position about an inner bore. The MRI system induces resonance in selected dipoles in an examination region created along an inner bore of a casing housing in a magnetic resonance imaging system such that the selected dipoles generate magnetic resonance signals to create an image representation of the part of the subject's body.
Owner:GENERAL ELECTRIC CO
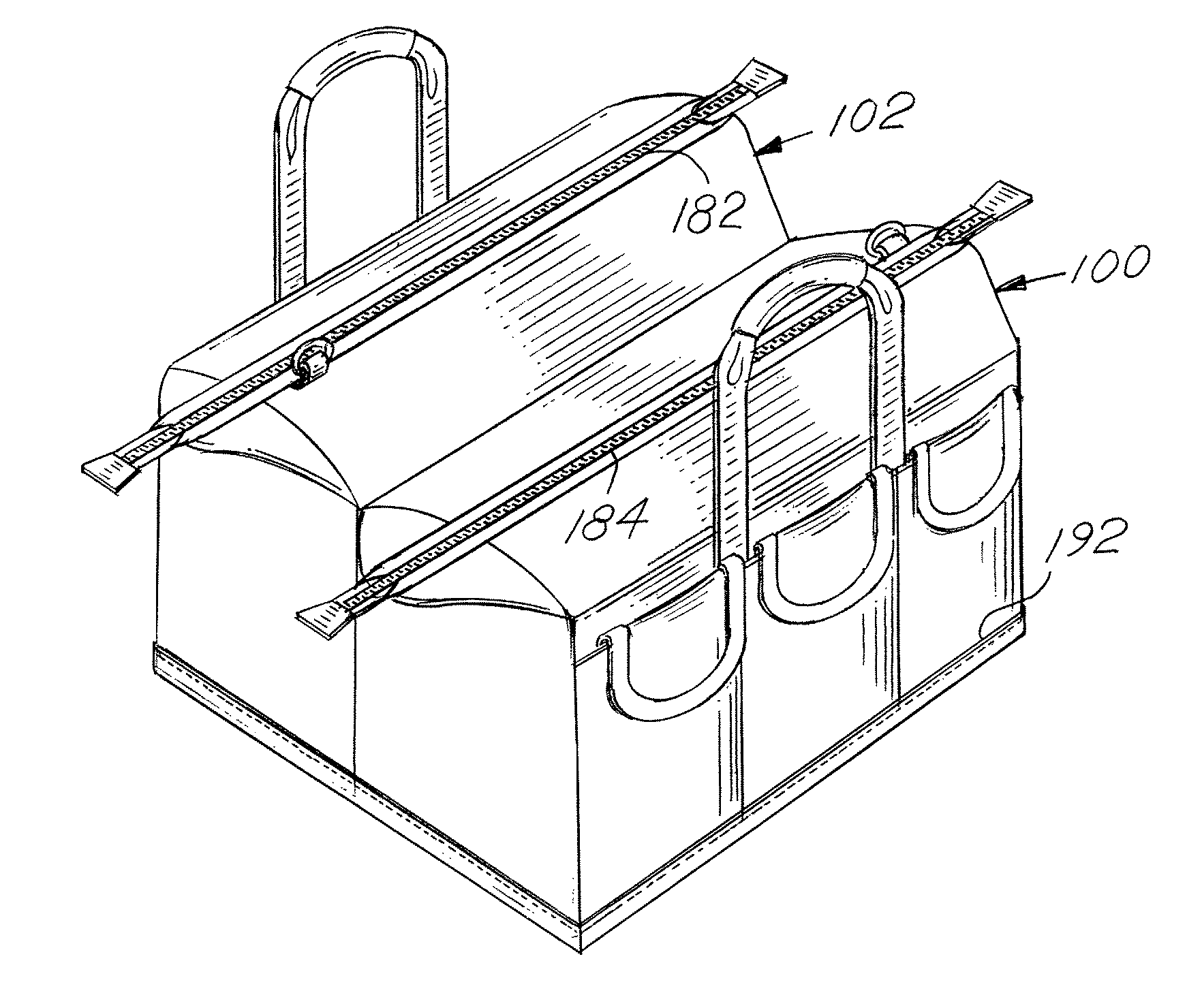
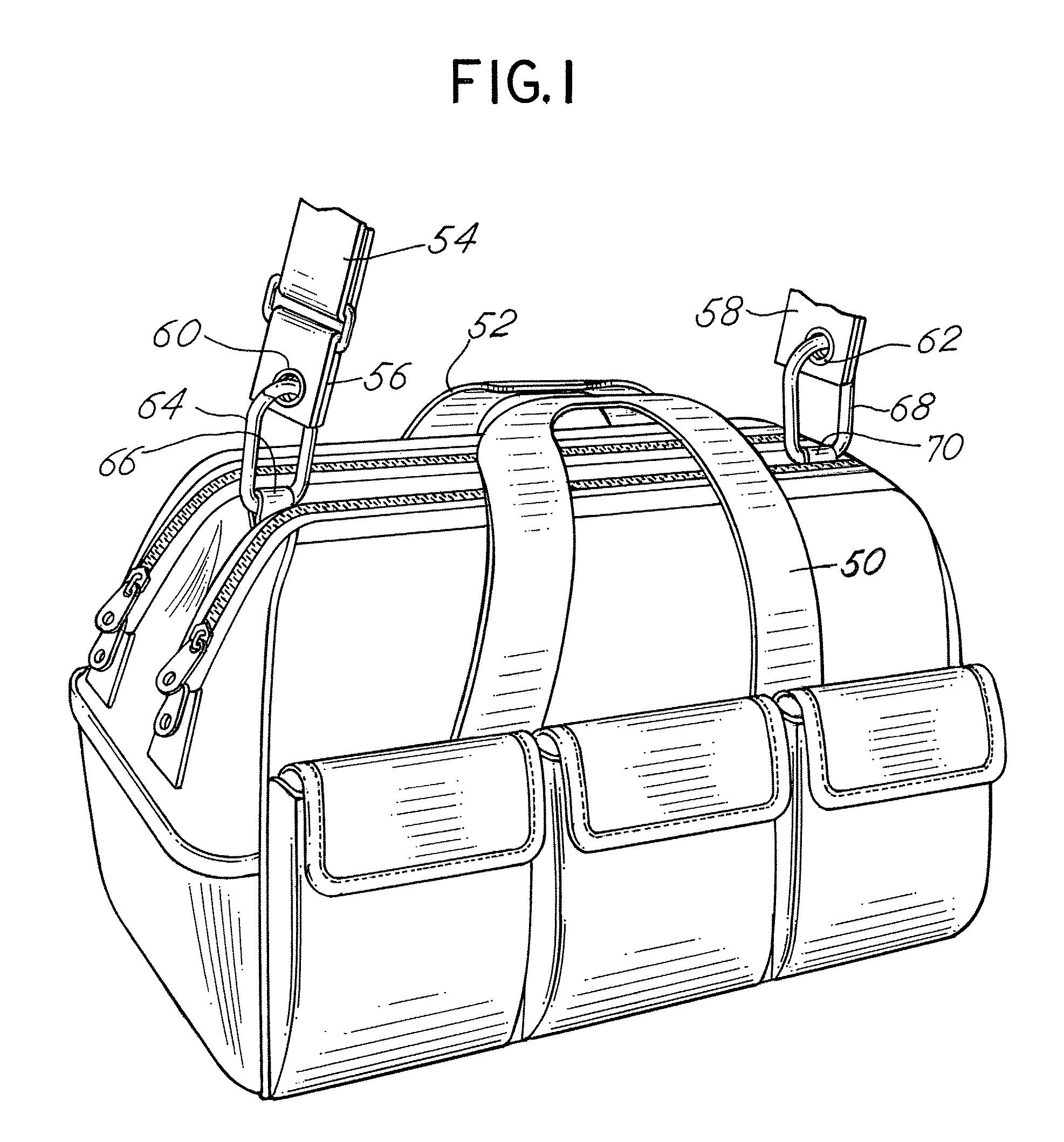
Dual compartment tool bag
A dual compartment, dual open mouth tool bag is fabricated from flexible material forming the side and top panels of the bag and the dual access openings. Each of the separate open mouth openings provides separate access to an individual compartment within the bag. The compartments may, in an alternative embodiment, be connected one to the other.
Owner:TRAVEL CADDY
Optoelectronic transceiver having dual access to onboard diagnostics
InactiveUS7149430B2Electromagnetic transmittersElectromagnetic transceiversDiagnostic dataTransceiver
The optoelectronic transceiver includes first and second controller ICs. Each controller IC includes logic, a memory, an interface, and at least one input port. Each memory is configured to store digital diagnostic data and has a unique serial device address to allow a host access to each of these controller ICs separately and independently. At least some of the digital diagnostic data is common to both the first controller IC and the second controller IC. The inclusion of two controller ICs allows the same diagnostic data to be stored in completely different memory mapped locations. This allows hosts that are preconfigured differently to read different memory mapped locations on the different controller ICs to obtain the same diagnostic data.
Owner:II VI DELAWARE INC
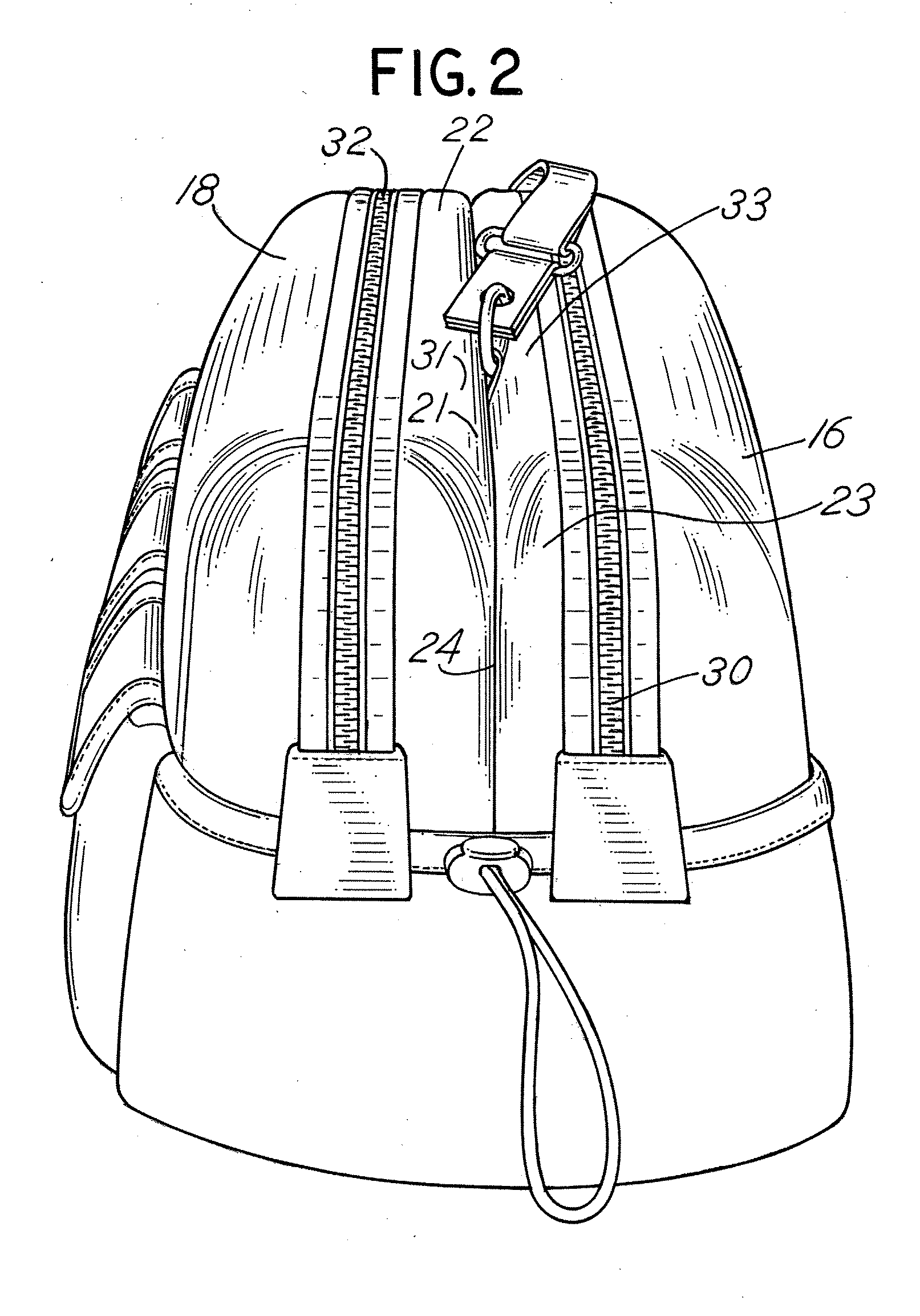
Dual access cargo system for outerwear
A convertible garment, such as from a garment to a fanny pack, having a first material portion affixed to the outside surface of the garment over an opening formed in the garment defining a first chamber for holding an object therein, including a first zipper providing access through the first material portion. A second zipper is located in the opening in the garment that is under the first material portion. A second material portion having a third zipper therein is affixed to the inside surface of the garment defining a second chamber for holding an object therein. When the second zipper is open, the first and second chambers are in communication with each other, so that an object placed in the first chamber when worn as a garment can be accessed after the garment has been converted to a fanny pack by opening the second zipper.
Owner:GREEN III JARVIS
Phase Change Memory Cells with Dual Access Devices
A self aligning memory device, with a memory element switchable between electrical property states by the application of energy, includes a substrate and word lines, at least the sides of the word lines covered with a dielectric material which defines gaps. An access device within a substrate has a first terminal under a second gap and second terminals under first and third gaps. First and second source lines are in the first and third gaps and are electrically connected to the second terminals. A first electrode in the second gap is electrically connected to the first terminal. A memory element in the second gap is positioned over and electrically connected to the first electrode. A second electrode is positioned over and contacts the memory element. The first contact, the first electrode, the memory element and the second electrode are self aligning. A portion of the memory element may have a sub lithographically dimensioned width.
Owner:MACRONIX INT CO LTD
Dual access luminaire junction box
The present invention relates to a junction box for a use with a recessed luminaire fixture frame wherein the junction box may be accessed from two opposed sides, eliminating the need to move the fixture to access and inspect the junction box.
Owner:SIGNIFY HLDG BV
Dual Compartment Tool Bag
A dual compartment, dual open mouth tool bag is fabricated from flexible material forming the side and top panels of the bag and the dual access openings. Each of the separate open mouth openings provides separate access to an individual compartment within the bag. The compartments may, in an alternative embodiment, be connected one to the other or may be separated by an intermediate open top storage compartment.
Owner:TRAVEL CADDY
Dual compartment tool bag
A dual compartment, dual open mouth tool bag is fabricated from flexible material forming the side and top panels of the bag and the dual access openings. Each of the separate open mouth openings provides separate access to an individual compartment within the bag. The compartments may, in an alternative embodiment, be connected one to the other or may be separated by an intermediate open top storage compartment.
Owner:TRAVEL CADDY
Dual access luminaire junction box
ActiveUS20100224404A1Installation of lighting conductorsLighting support devicesEngineeringDual access
A recessed fixture having a junction box positioned adjacent at least one ceiling support structure comprises a recessed luminaire fixture, the junction box mounted to the recessed luminaire frame, the junction box being horizontally oriented, the junction box having a first facing junction box door and a second junction box door, the first junction box door and the second junction box door being oppositely positioned and pivotally connected to a junction box housing, the first and second junction doors being in a substantially horizontal orientation in a closed position, one of the first junction box door and the second junction box door facing substantially upwardly and the other of the first junction box door and the second junction box door facing substantially downwardly, wherein the horizontal orientation allows the junction box doors to be positioned adjacent a ceiling structure without limiting opening of the junction box doors.
Owner:SIGNIFY HLDG BV
Insulated cabinet for installation in a home exterior wall
InactiveUS6484531B1Lighting and heating apparatusDomestic refrigeratorsDual accessBiomedical engineering
The present invention provides a convenient means for delivery personnel to deliver refrigerated goods to a building without having to wait until the building owner is home. The invention provides a dual-access insulated cabinet installable into the exterior wall of a home, with outside and inside doors. Both outside and inside doors contain lockable mechanisms for securing the doors. The insulated cabinet includes a main compartment for storing items to be frozen, an interior compartment for inserting into the wall of a building, and a cooling apparatus connected to the main compartment for selectively cooling the insulated cabinet to a selected temperature. An optional indicator light is inside whereby the light turns on when a delivery of refrigerated goods is made through the outside door of the invention. The indicator light then resets to the off state when the resident of the building opens the inside door of the present invention.
Owner:HAMBLETON JOHN D +1
Dual access vehicle storage assembly
A vehicle storage assembly can cover a vehicle storage area such as an interior console or a cargo box. The storage assembly can include a base and a lid. The lid can be opened from two sides to allow easy access for a driver and passengers to an interior storage compartment. The base includes at least two rods, which can act as axles for the lid to pivot about. The lid includes at least one rotation member or guide which can be released from the rod only when the lid is in a desired position, for example, a closed position. The lid can include a latch for each rod. The lid can have a lock to secure one or both of the latches with the lid in a closed position.
Owner:LUND MOTION PRODS
Dual access vehicle storage assembly
A vehicle storage assembly can cover a vehicle storage area such as an interior console or a cargo box. The storage assembly can include a base and a lid. The lid can be opened from two sides to allow easy access for a driver and passengers to an interior storage compartment. The base includes at least two rods, which can act as axles for the lid to pivot about. The lid includes at least one rotation member or guide which can be released from the rod only when the lid is in a desired position, for example, a closed position. The lid can include a latch for each rod. The lid can have a lock to secure one or both of the latches with the lid in a closed position.
Owner:LUND MOTION PRODS
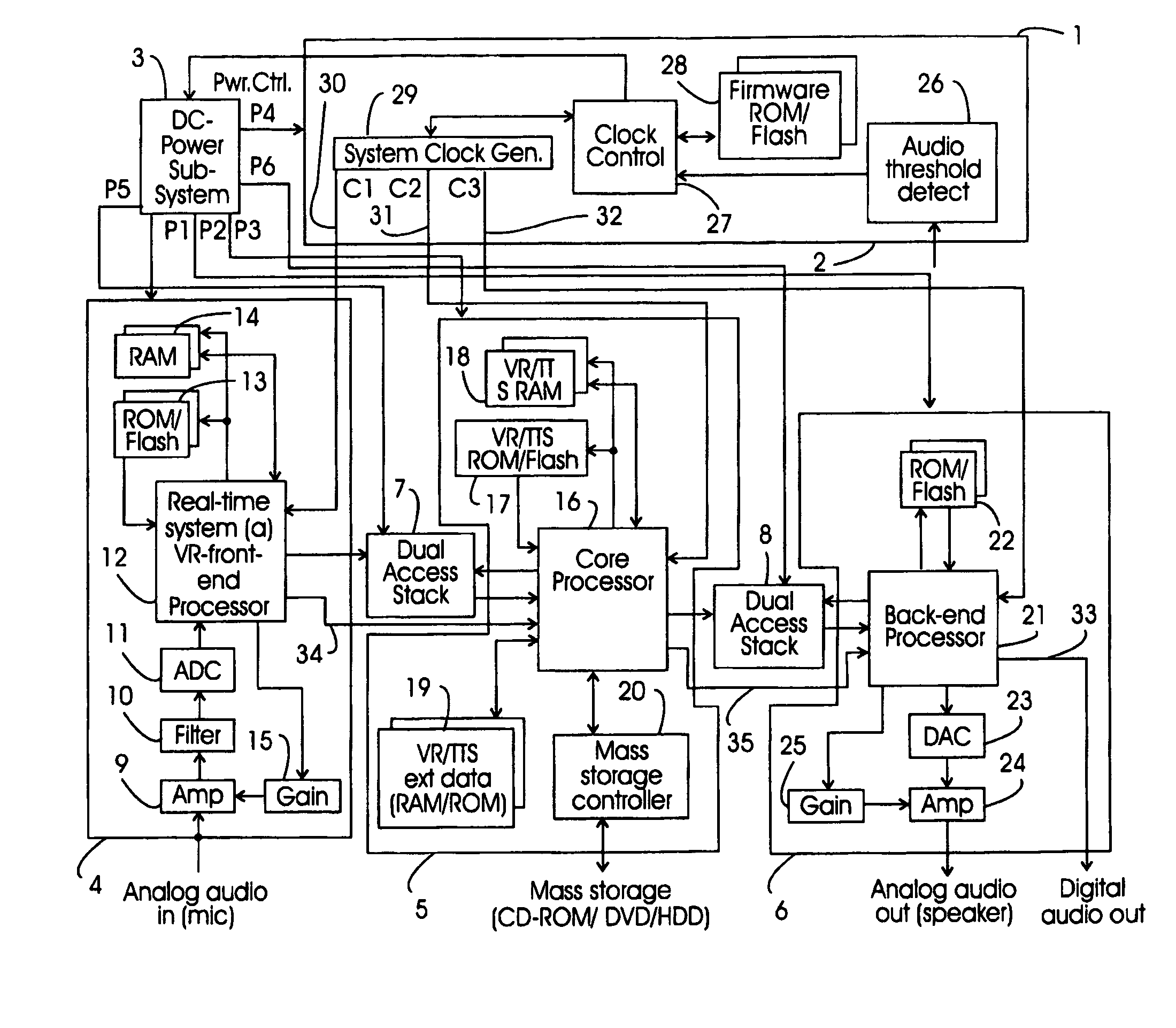
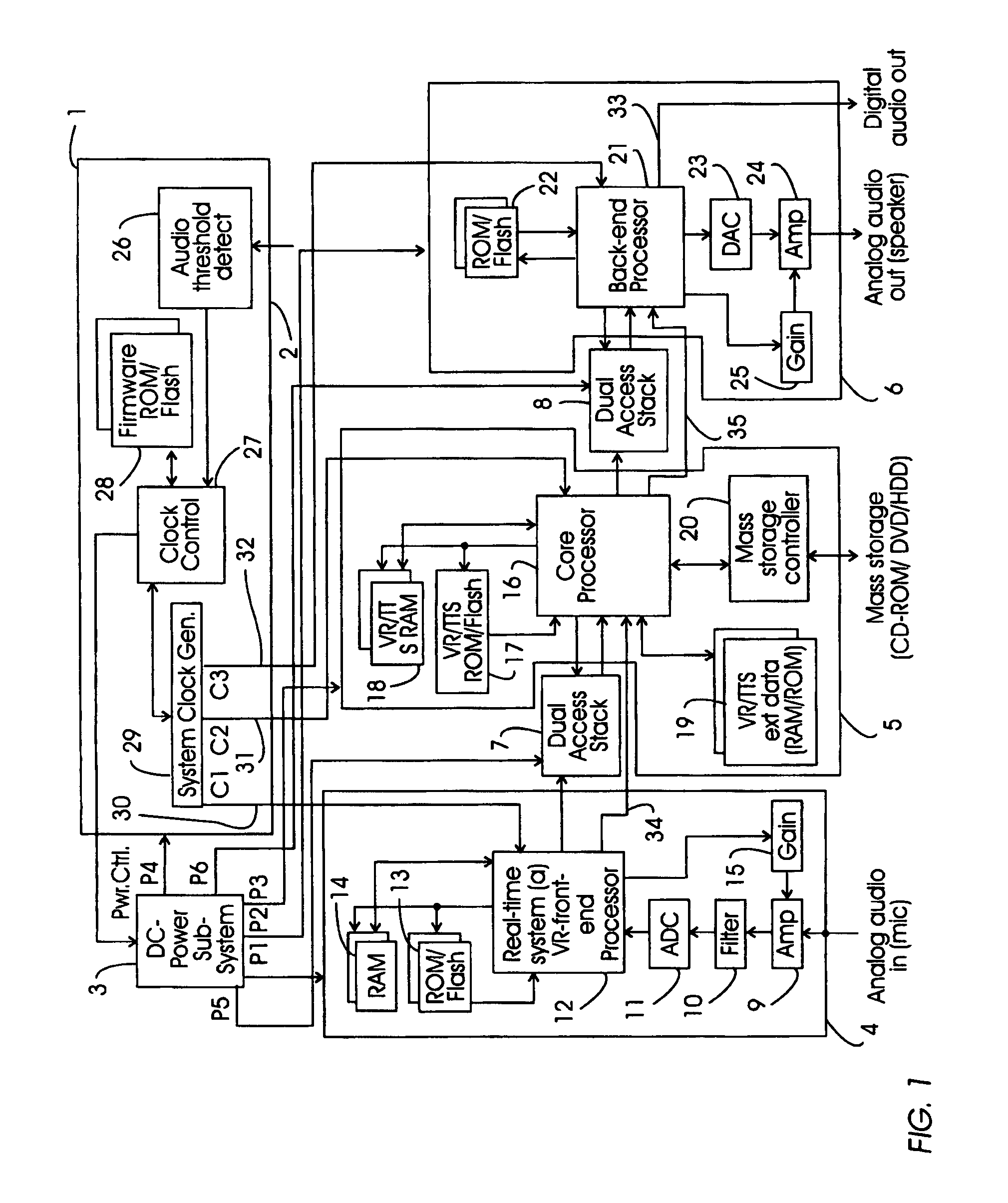
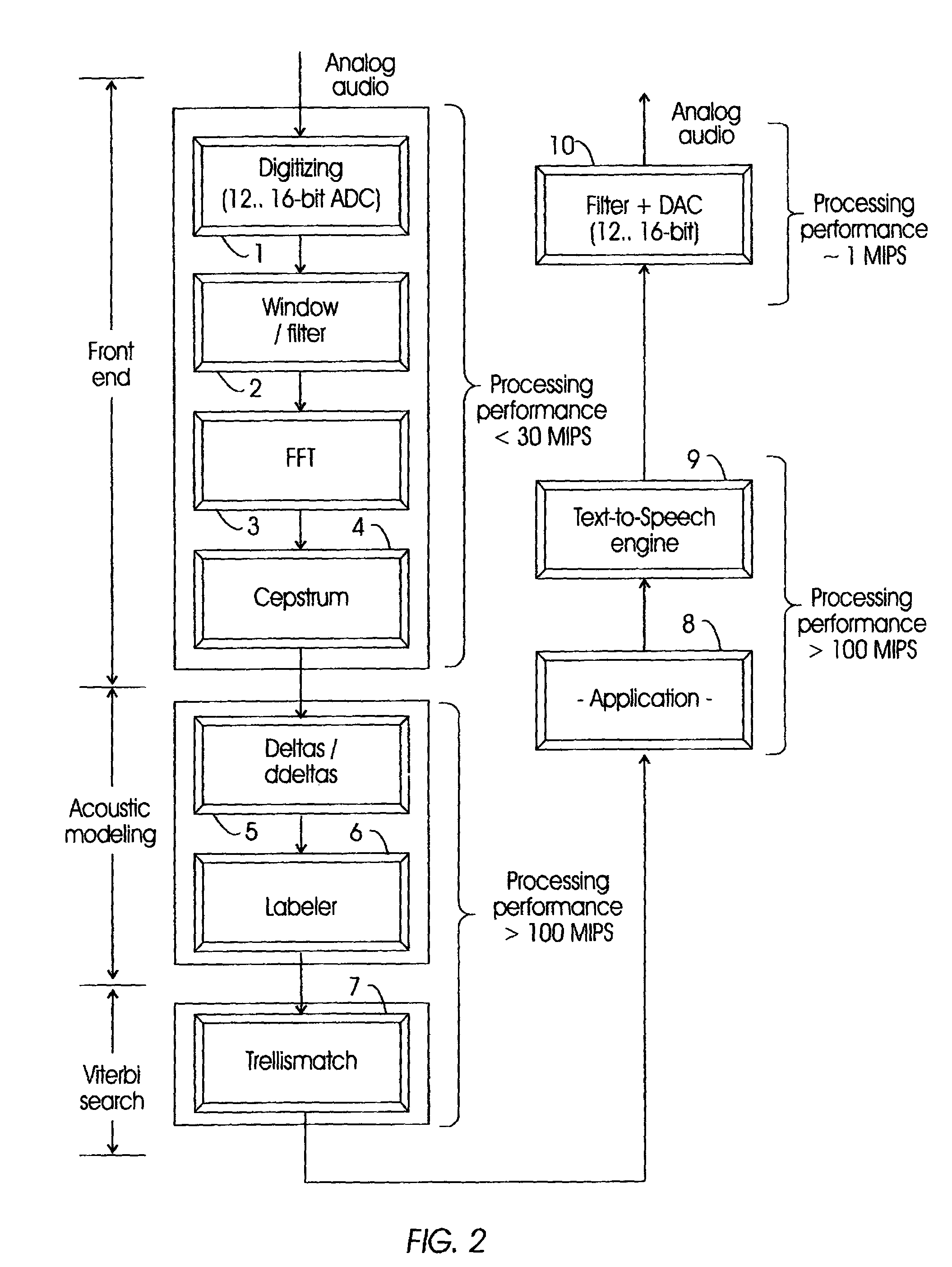
Minimizing resource consumption for speech recognition processing with dual access buffering
ActiveUS7349844B2Improve speech recognition performanceAvoiding processing demandSpeech recognitionMemory systemsResource consumptionSpeech identification
In a processor system for audio processing, such as voice recognition and text-to-speech, a dedicated front-end processor, a core processor and a dedicated back-end processor are provided which are coupled by dual access stack. When an analog audio signal is inputted core processor is invoked only when a certain amount of data is present in the dual access stack. Likewise the back-end processor is invoked only when a certain amount of data is present in the dual access stack. This way the overall processing power required by the processing task is minimized as well as the power consumption of the processor system.
Owner:NUANCE COMM INC
Dual access serial peripheral interface
A dual access peripheral interface uses a shared data bus (16) for communication with dual master units (30,32) coupled to a common peripheral device (34). Each master control unit provides a shared subset of control bits to a logic configuration block (48), which combines the control bits in a logic operation to present to the slave peripheral unit (34). The logic configuration block (48) is configured by configuration bits accessible by only one of the master units (30). In this way, both of the master units can access the peripheral at the same time with the logic of the logic configuration block determining the ultimate control of the peripheral.
Owner:GOOGLE TECH HLDG LLC
Systems, methods and apparatus for specialized magnetic resonance imaging with dual-access conical bore
An apparatus for magnetic resonance imaging is described having a casing with an inner bore which in some embodiments is substantially frustoconical shape for receiving a subject. The apparatus contains devices disposed in the casing to create a uniform field within an inner bore. The apparatus employs dual access since the inner bore has a first and second end at the outer edge of the casing for which the part of the subject's body would travel so as to be imaged. Further, in some embodiments, the apparatus provides one or more recesses for inserting at least one gradient coils into position about an inner bore. The MRI system induces resonance in selected dipoles in an examination region created along an inner bore of a casing housing in a magnetic resonance imaging system such that the selected dipoles generate magnetic resonance signals to create an image representation of the part of the subject's body.
Owner:GENERAL ELECTRIC CO
Terminal dual sim-dual access handling
ActiveCN106465134AAvoid interferenceNetwork traffic/resource managementAssess restrictionDual accessMulti access
The disclosure pertains to the field of dual access handling. More particularly the disclosure relates to methods of handling more than one connection, each connection corresponding to a respective subscriber identity and connecting a wireless device to a respective wireless network, as well as to a corresponding wireless device and to a computer program. This object is obtained by a method, performed in a wireless device 1, of handling multi access of more than one connection, each connection corresponding to a respective subscriber identity and connecting the wireless device to a respective wireless network. The method comprises detecting S1, for a first connection corresponding to a first subscriber identity, a change in connection properties, and determining S2, for at least one of the other subscriber identities, a set of updated network capabilities, based on the changed connection properties of the first connection.
Owner:TELEFON AB LM ERICSSON (PUBL)
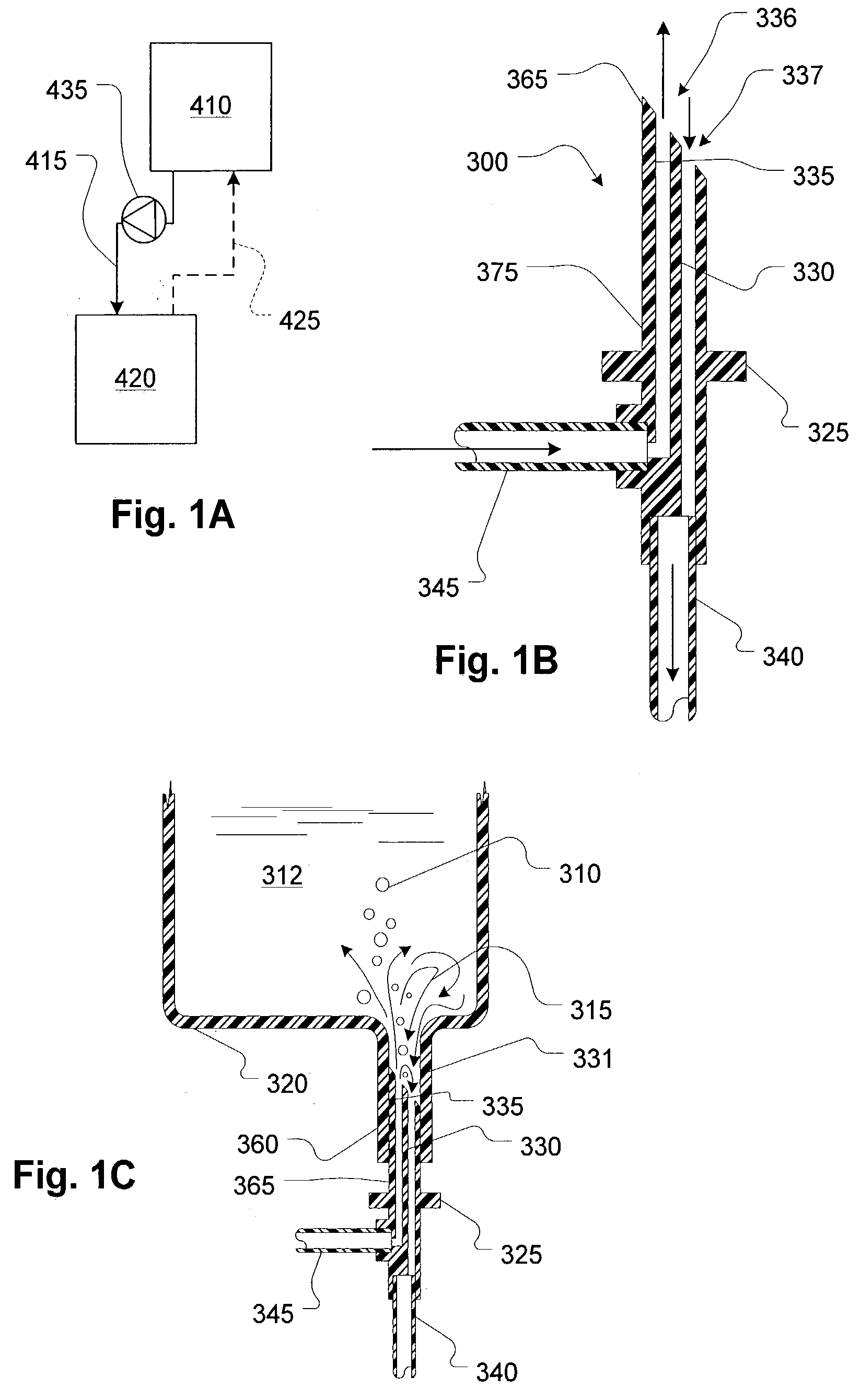
Dual access pathways to serially-connected mass data storage units
ActiveUS7594134B1Elevated level of redundancyReduce circumstanceError detection/correctionSequential dataDual access
A group of data storage units are serially connected in a sequential data communication path to communicate read and write operations to first and second interfaces of each data storage unit in the group. A data management computer device (“filer”) manages read and write operations of the data storage units of the group through an adapter of the filer. Main and redundant primary communication pathway connectors extend from the filer to the interfaces of the data storage unit, thereby establishing redundancy through multiple pathways to communicate the read and write operations to the data storage units of the group. Main and redundant secondary communication pathway connectors extend from partner filers to the groups of data storage units associated with each partner filer, thereby further enhancing redundancy.
Owner:NETWORK APPLIANCE INC
Optoelectronic Transceiver Having Dual Access to Onboard Diagnostics
InactiveUS20060263092A1Electromagnetic transmittersElectromagnetic transceiversDiagnostic dataTransceiver
An optoelectronic transceiver includes first and second controller ICs. Each controller IC includes logic, a memory, an interface, and at least one input port. Each memory is configured to store digital diagnostic data and has a unique serial device address to allow a host access to each of these controller ICs separately and independently. At least some of the digital diagnostic data is common to both the first controller IC and the second controller IC. The inclusion of two controller ICs allows the same diagnostic data to be stored in completely different memory mapped locations. This allows hosts that are preconfigured differently to read different memory mapped locations on the different controller ICs to obtain the same diagnostic data.
Owner:II VI DELAWARE INC
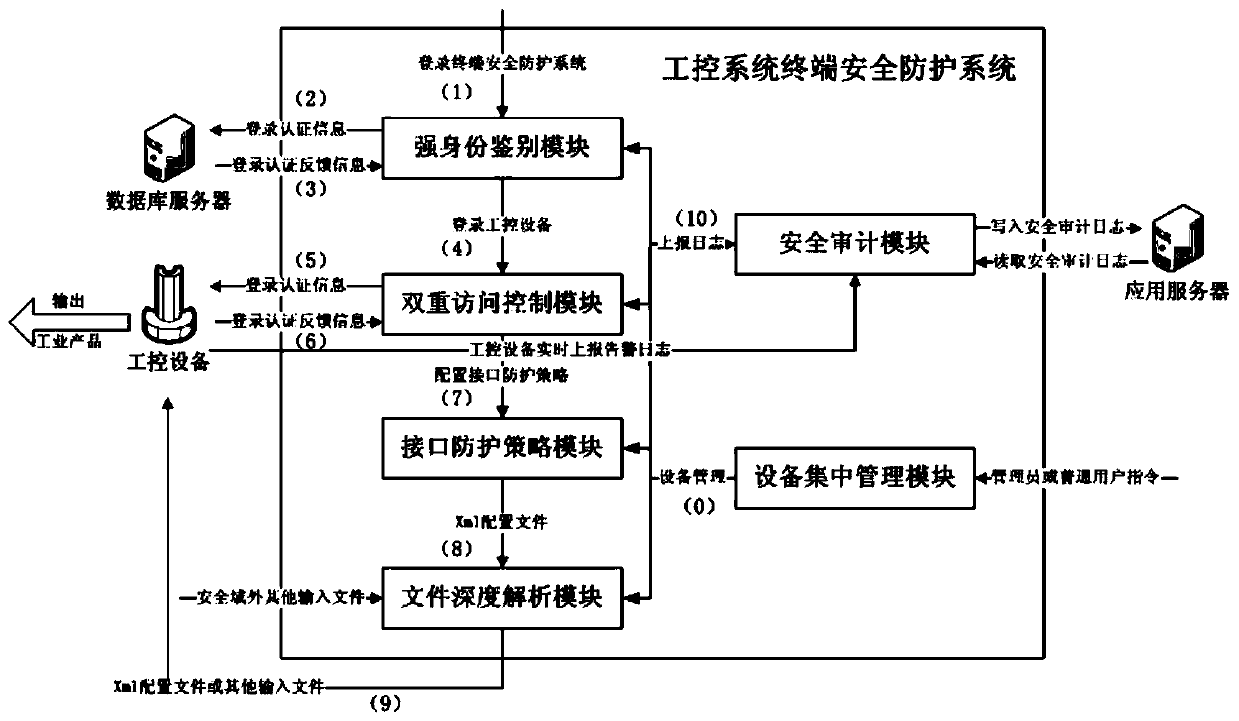
Industrial control system terminal safety protection method
ActiveCN109995796AImprove the protective effectImprove the level ofEncryption apparatus with shift registers/memoriesComputer compatibilityEngineering
The invention belongs to the technical field of industrial control system terminal safety protection, and particularly relates to an industrial control system terminal safety protection method. The method is implemented based on an industrial control system terminal safety protection system, and the system comprises terminal safety protection equipment and a terminal safety centralized managementsystem. According to the scheme, a series of technical means of strong identity authentication, dual access control, an interface protection strategy, file deep analysis, security audit and equipmentcentralized management are comprehensively applied; malicious behaviors such as network attack and illegal access in operation of industrial control system equipment are effectively blocked, and centralized configuration and management of security protection strategies of a plurality of industrial control system equipment terminals of the same type or different types are realized at the same time.The scheme has the advantages that the safety protection level of the industrial control equipment terminal is high, centralized and unified management of multiple pieces of equipment is supported, and the centralized management platform is suitable for multiple application environments and multiple industrial protocols, good in compatibility, flexible in protection strategy configuration, efficient in alarm reporting and equipment management and the like.
Owner:北京京航计算通讯研究所
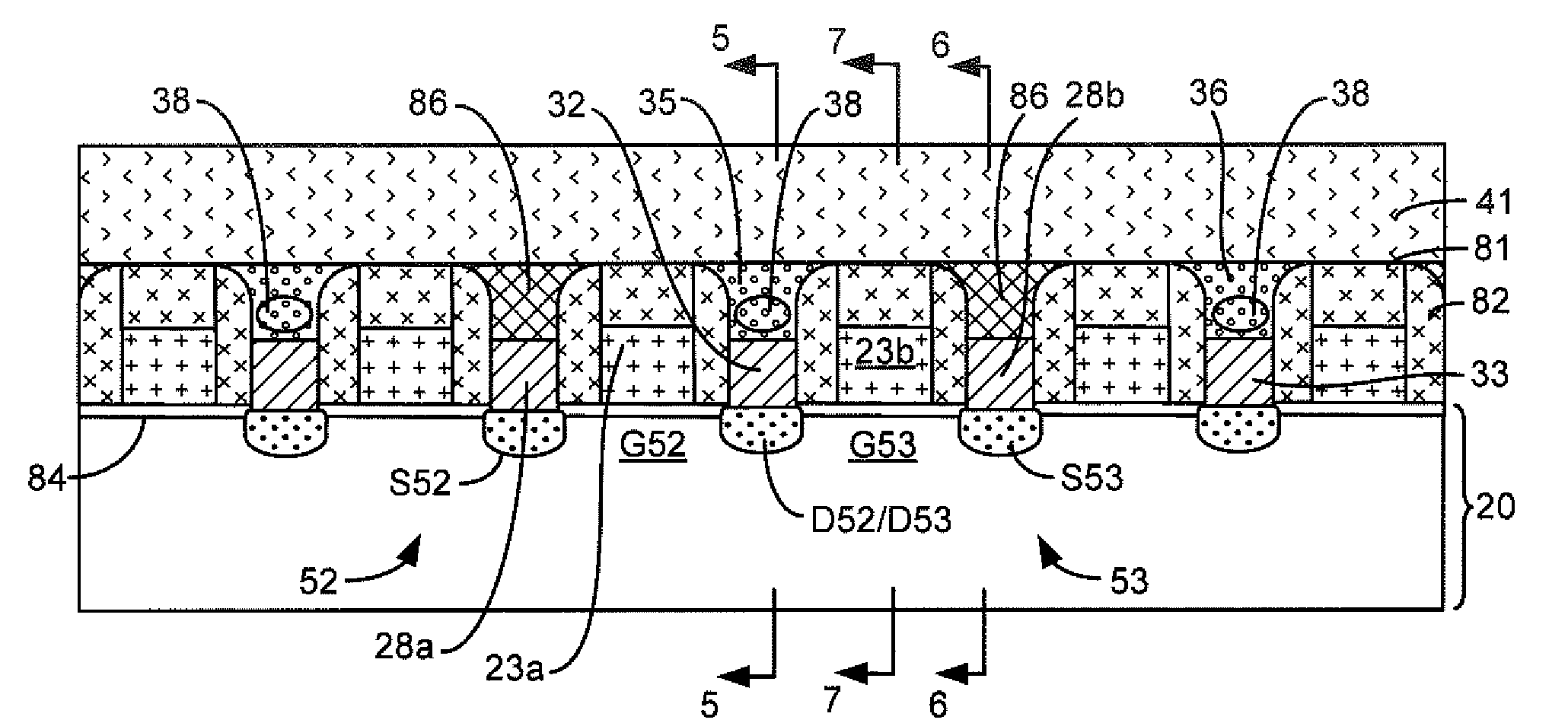
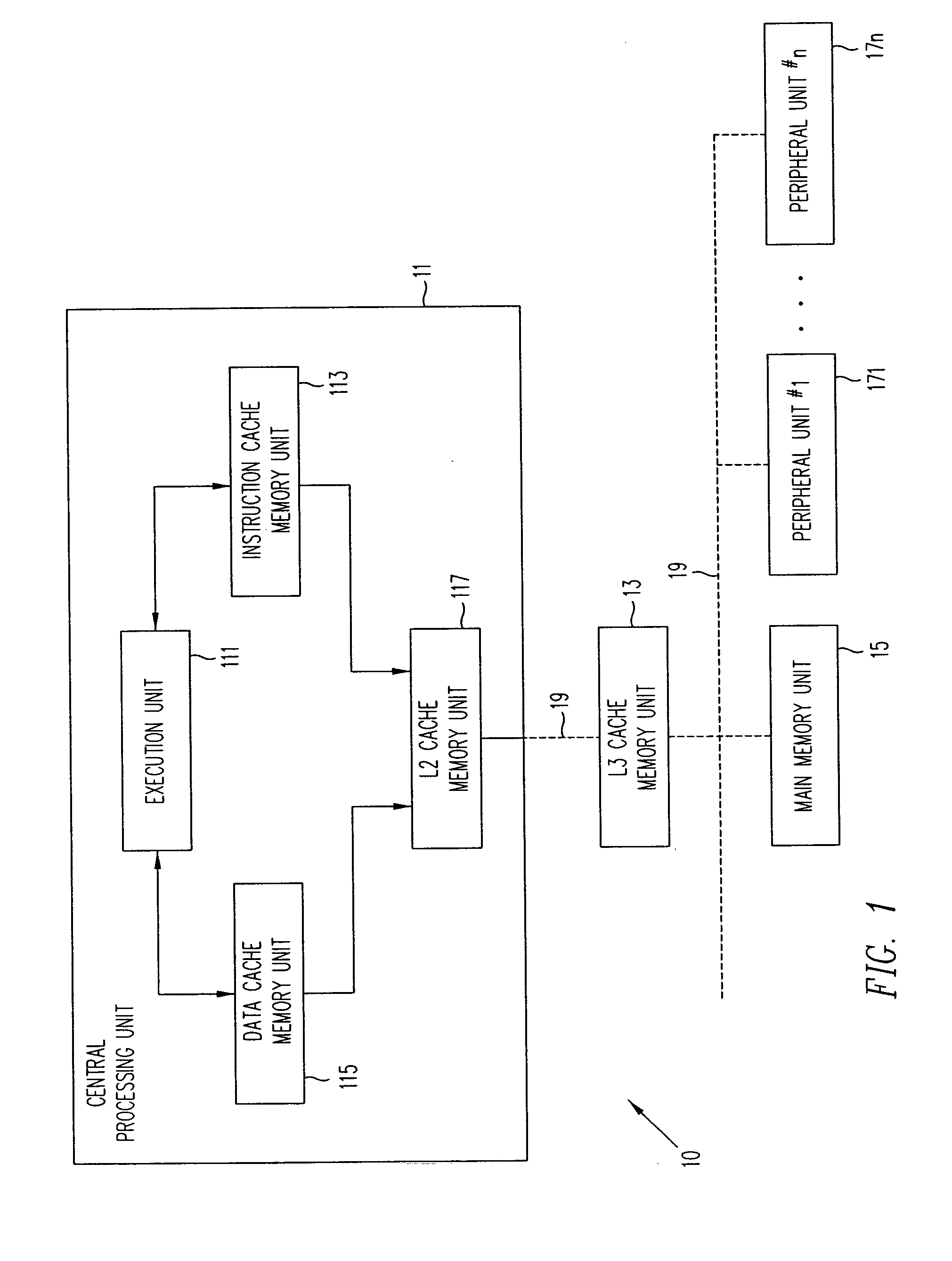
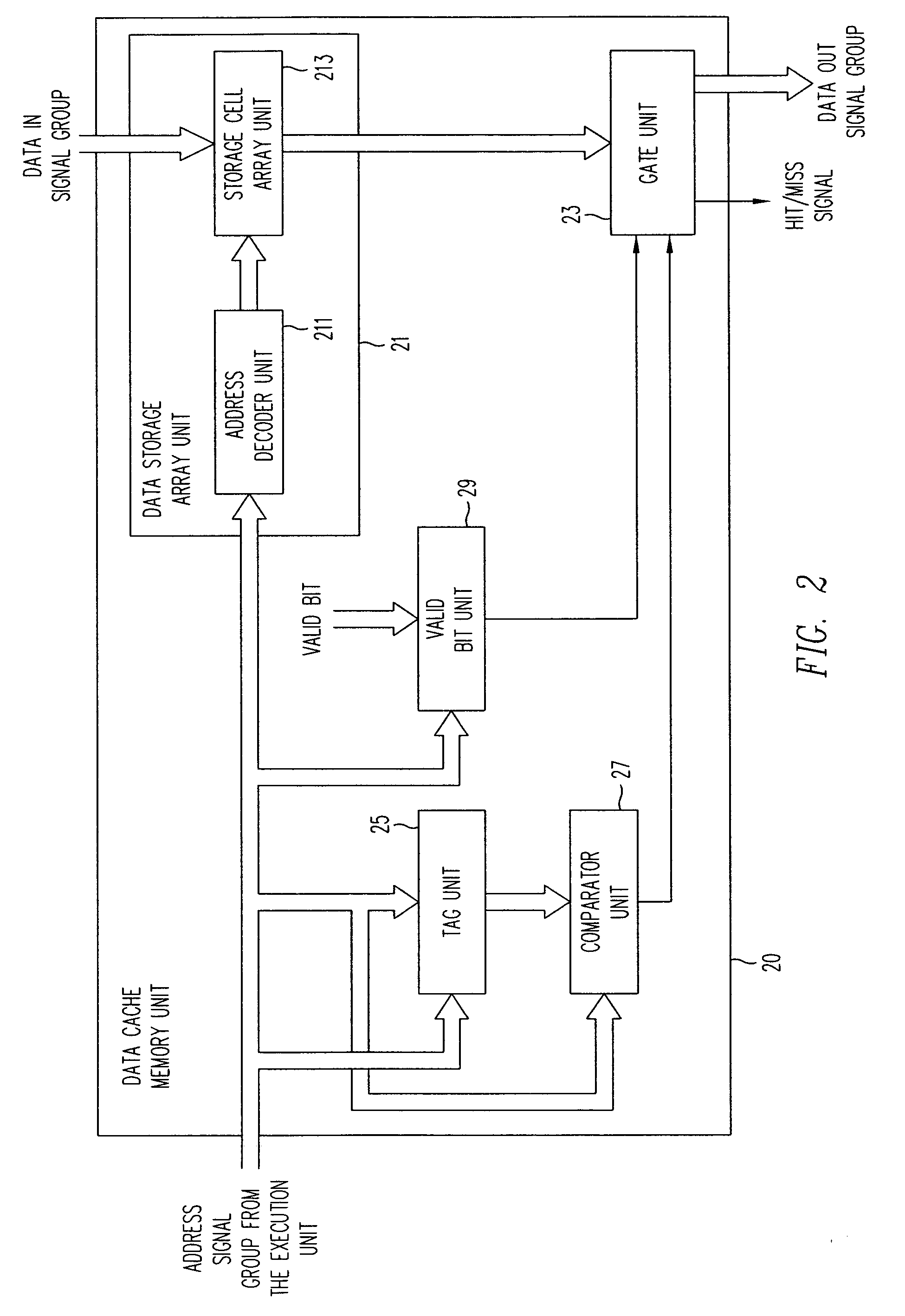
Apparatus and method for snoop access in a dual access, banked and pipelined data cache memory unit
ActiveUS20040158683A1Memory adressing/allocation/relocationGenerating/distributing signalsThree stageControl signal
In a data cache unit that exchanges data signal groups with at least two execution units, the operation of the data cache unit is implemented as a three-stage pipeline in order to access data at the speed of the system clock. The data cache unit has a plurality of storage cell banks. Each storage cell bank has valid bit array unit and a tag unit for each execution unit incorporated therein. Each valid bit array unit has a valid / invalid storage cell associated with each data group stored in the storage cell bank. The valid bit array units have a read / write address port and snoop address port. During a read operation, the associated valid / invalid signal is retrieved to determine whether the data signal group should be processed by the associated execution unit. In a write operation, a valid bit is set in the valid / invalid bit location(s) associated with the storage of a data signal group (or groups) during memory access. The valid bit array unit responds to a snoop address and a control signal from the tag unit to set an invalid bit in a valid / invalid bit address location associated with the snoop address. The tag unit can be divided into a plurality of tag subunits to expedite processing.
Owner:ORACLE INT CORP
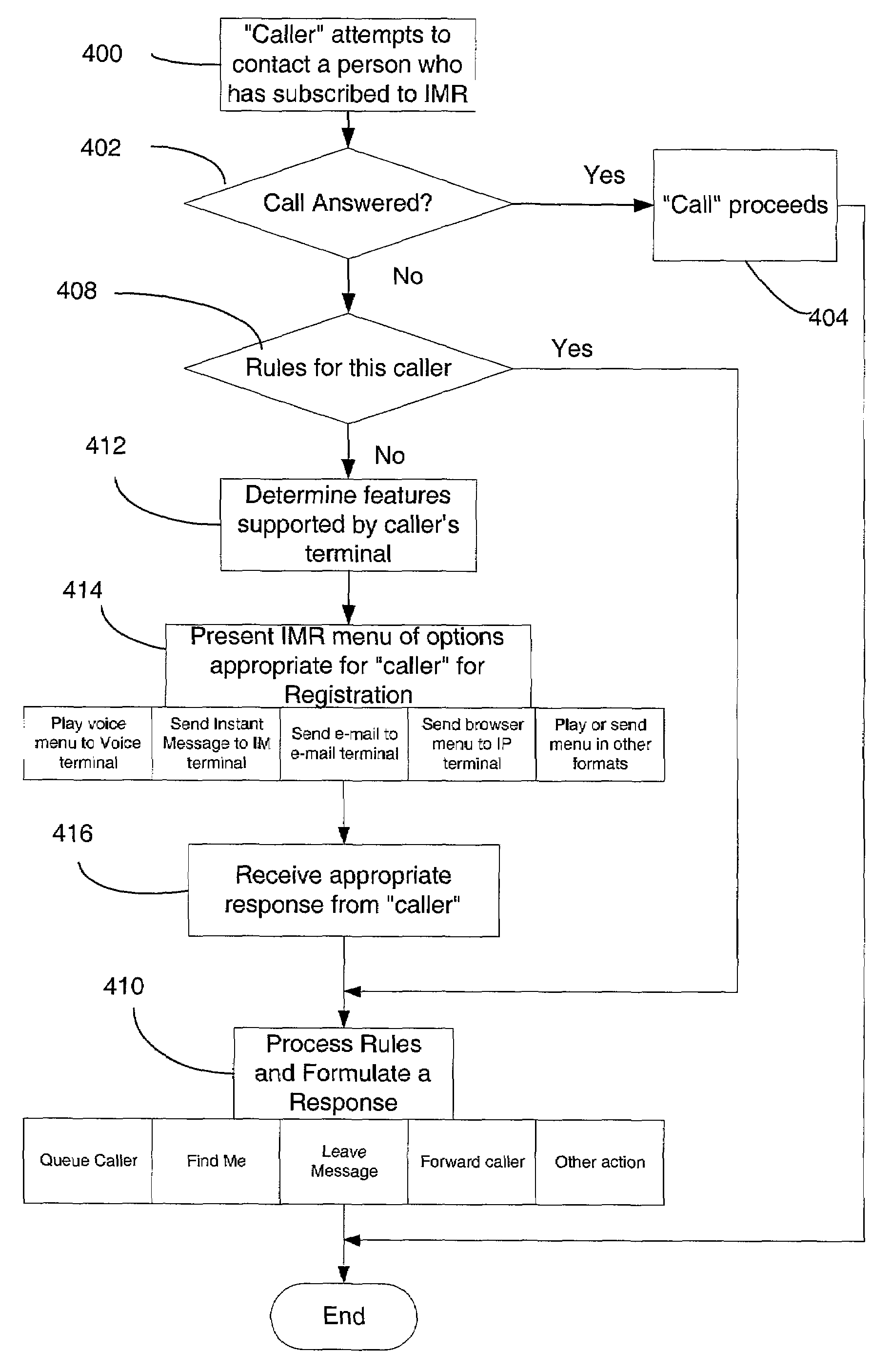
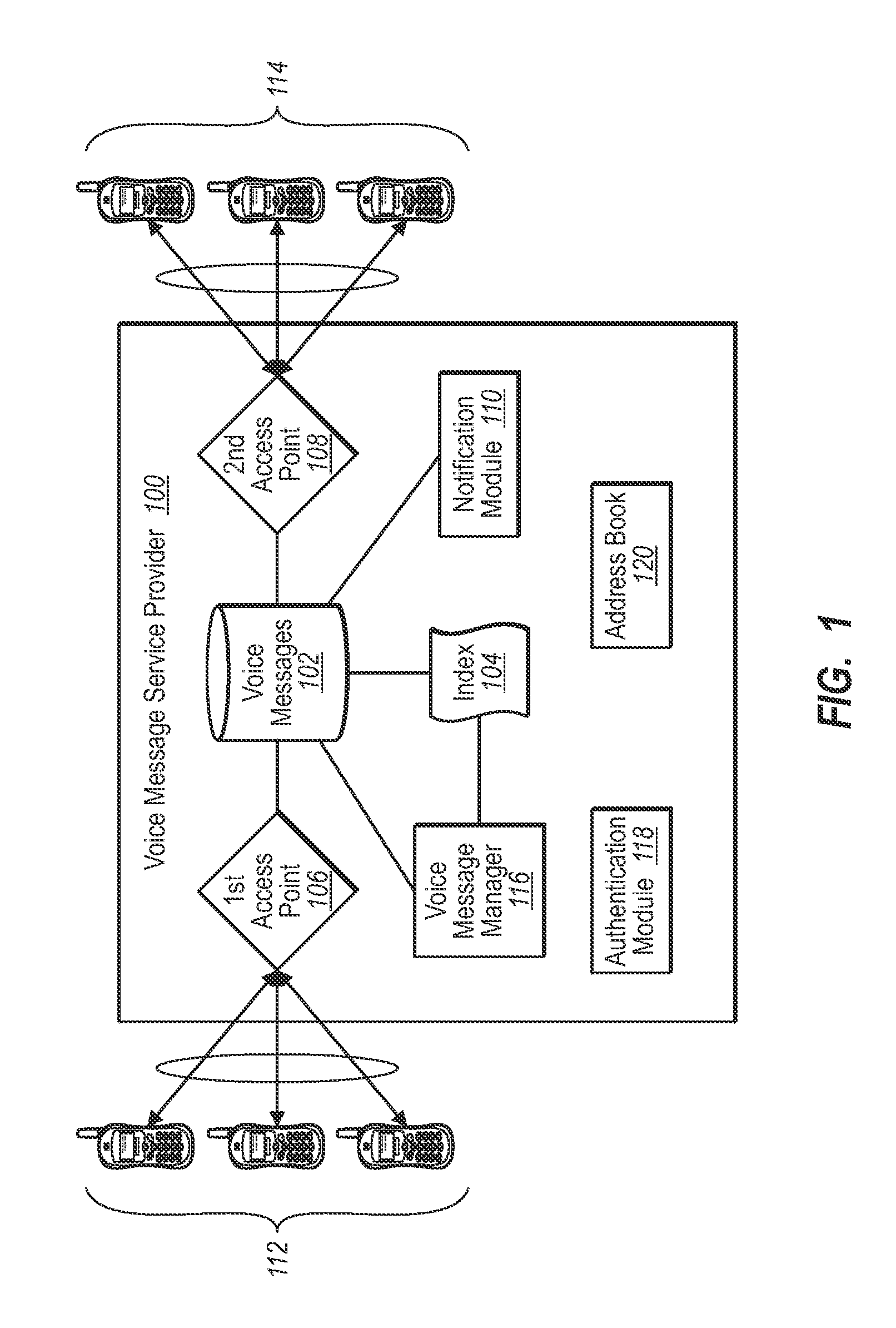
Providing voice messages through dual access points
ActiveUS20080043939A1Automatic call-answering/message-recording/conversation-recordingAutomatic exchangesService provisionDual access
A voice message service provider enables users to access voice messages through a first access point for creating voice messages and a second access point for retrieving the created voice messages. In one implementation, a user calls the first access point to create a message, and the voice message provider indexes the created voice message with a message retrieval telephone number and one or more recipient identifiers. A notification message containing the message retrieval telephone number is sent to the intended recipient to provide notification of the voice message. The intended recipient may retrieve the voice message by calling the message retrieval number contained within the notification message and providing the recipient identifier. The voice message service provider identifies the voice message associated with the message retrieval number and recipient identifier and returns the voice message to the intended recipient.
Owner:PINGER INC
Super resolution contextual close-up visualization of volumetric data
ActiveUS20080055310A1Fast super resolution close-up visualizationRadiation diagnostics3D-image renderingData setVolumetric data
The present invention relates to a method and system for processing a volumetric dataset for providing close-up visualization of a subset therefrom. A volumetric dataset is processed based on a dual access gradient quantization data structure. The data structure is generated in a fast pre-processing stage and provides substantially immediate access to a quantized gradient using either an index or an arbitrary normalized vector. The method provides a clear, enlarged high-resolution image of a user selected region of interest at interactive rates and allows the user to freely move and visualize the region of interest within the volumetric dataset and with any orientation.
Owner:CALGARY SCIENTIFIC INC
Warning device for monitoring a health status of a bearing having a close range wireless interface
A warning device having a close range wireless interface is provided. The warning device includes a body portion, top portion, a base portion, a microcontroller for controlling the device, a battery, at least one sensor for sensing at least one of a velocity, an enveloped acceleration and a temperature reading of the bearing, and at least one LED for displaying the health status of the bearing.The close range wireless interface includes an RFID tag having an integrated circuit, and a radio, an antenna for receiving and transmitting modulated and demodulated signals, and a digital bus connecting the microcontroller to the RFID tag. The microcontroller stores at least one of the sensed velocity, enveloped acceleration and the temperature values into a memory disposed within the RFID tag. The memory is a dual access memory that enables data transfer via the RFID radio or via the digital bus.
Owner:AB SKF
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com