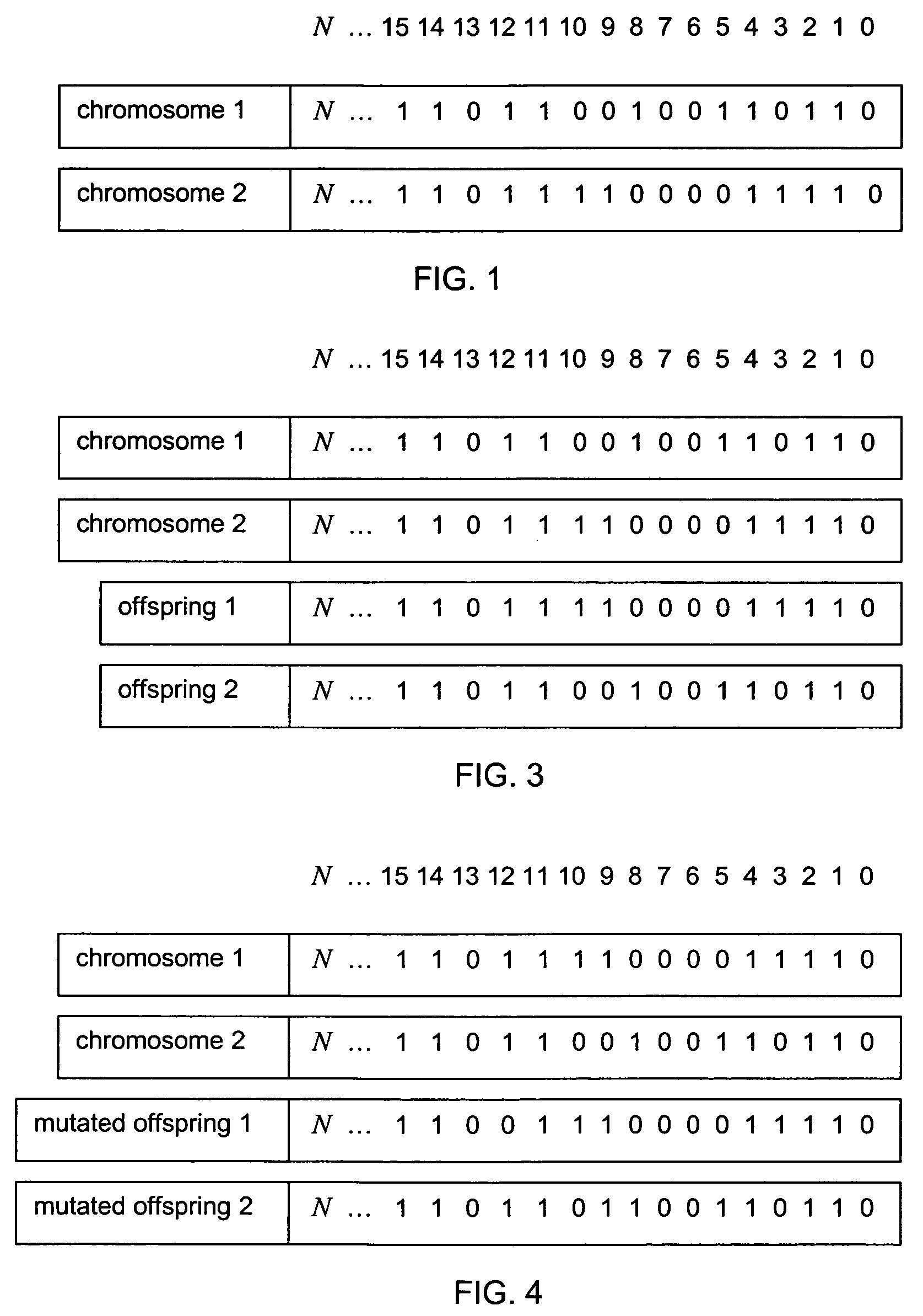
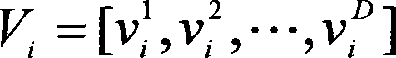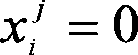Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
274 results about "Binary strings" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
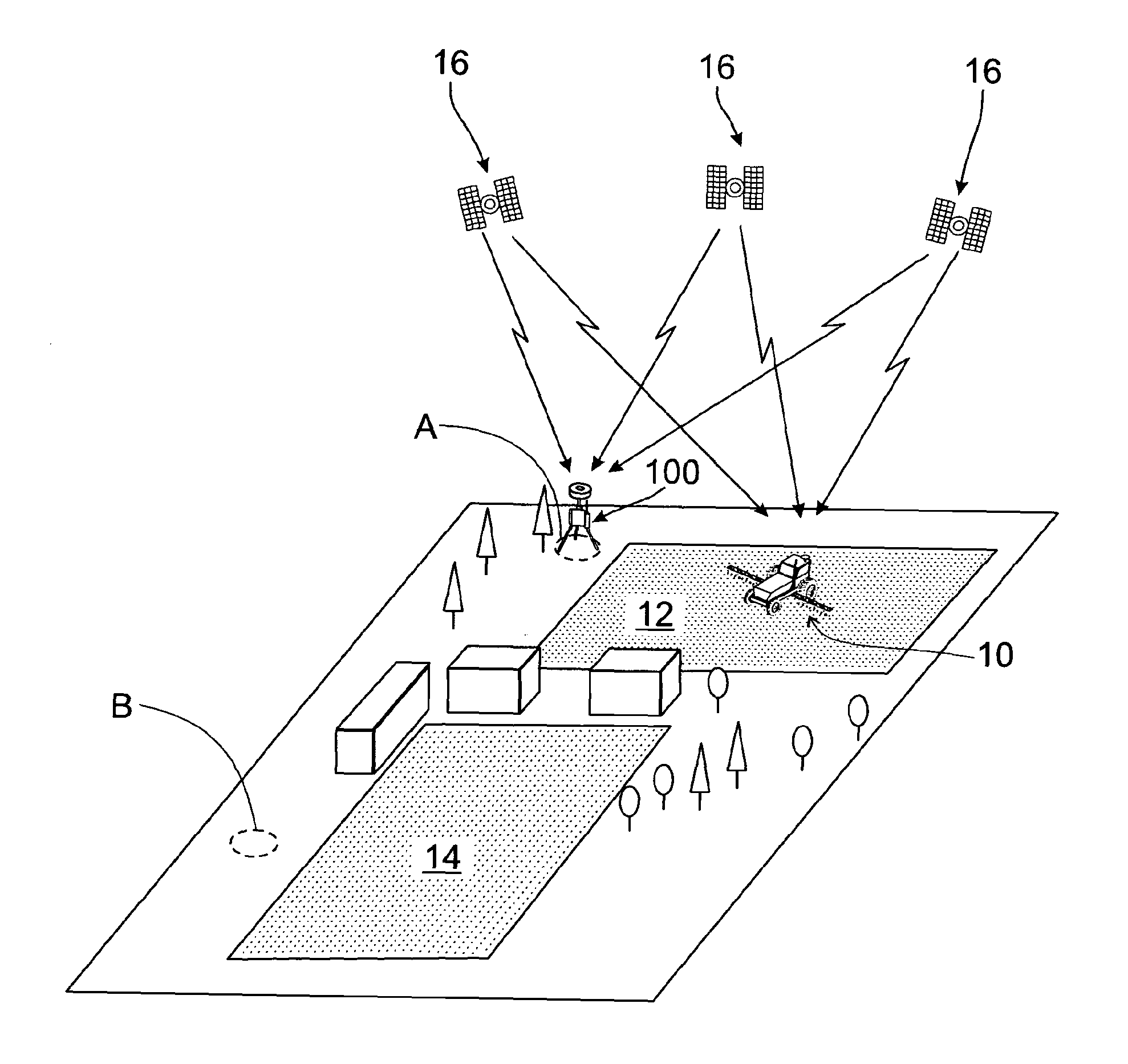
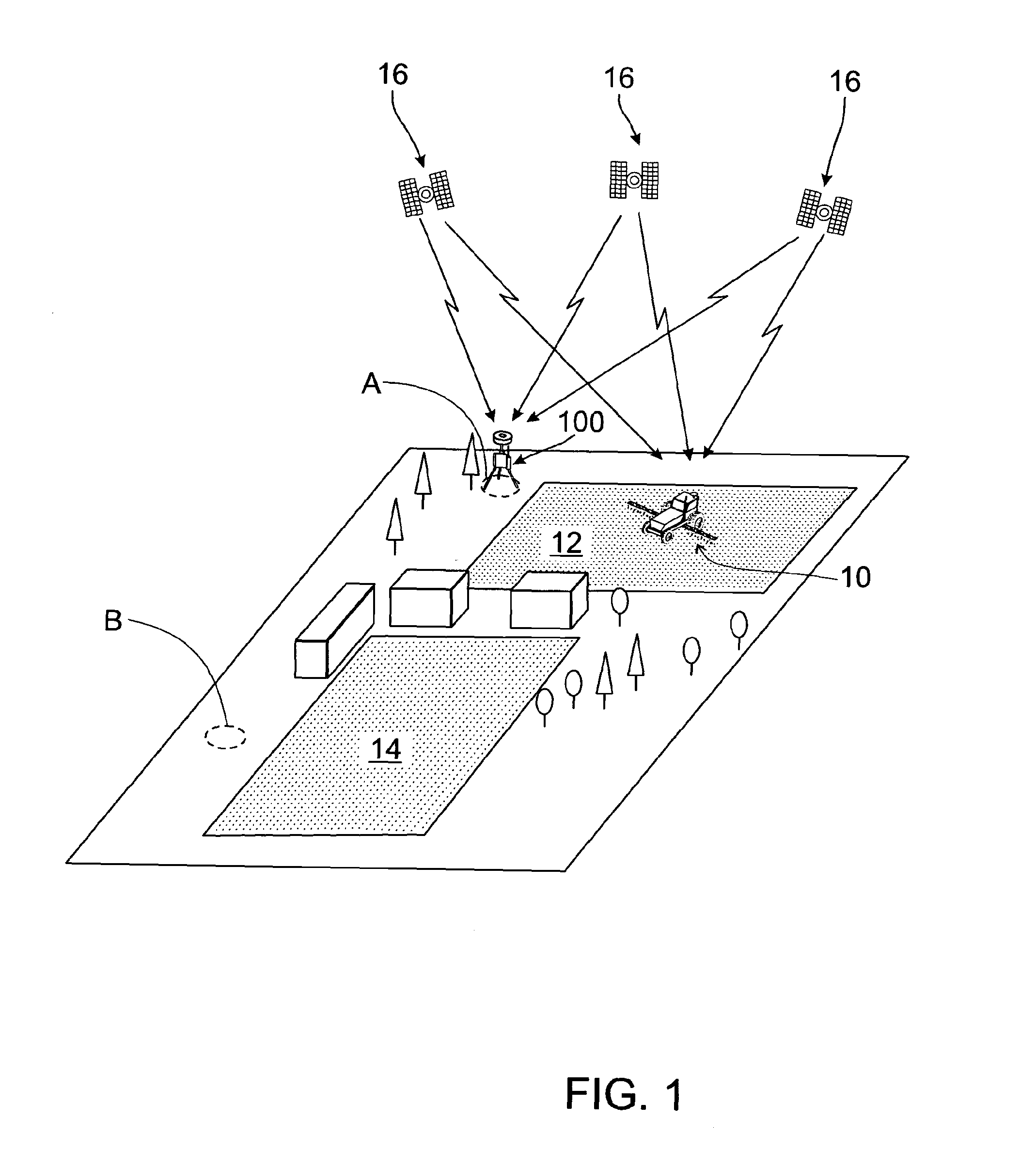
Binary strings. A binary string is a sequence of bytes. Unlike character strings, which usually contain text data, binary strings are used to hold non-traditional data such as pictures, voice, or mixed media. Character strings of the FOR BIT DATA subtype may be used for similar purposes. Binary strings are not associated with a code page.
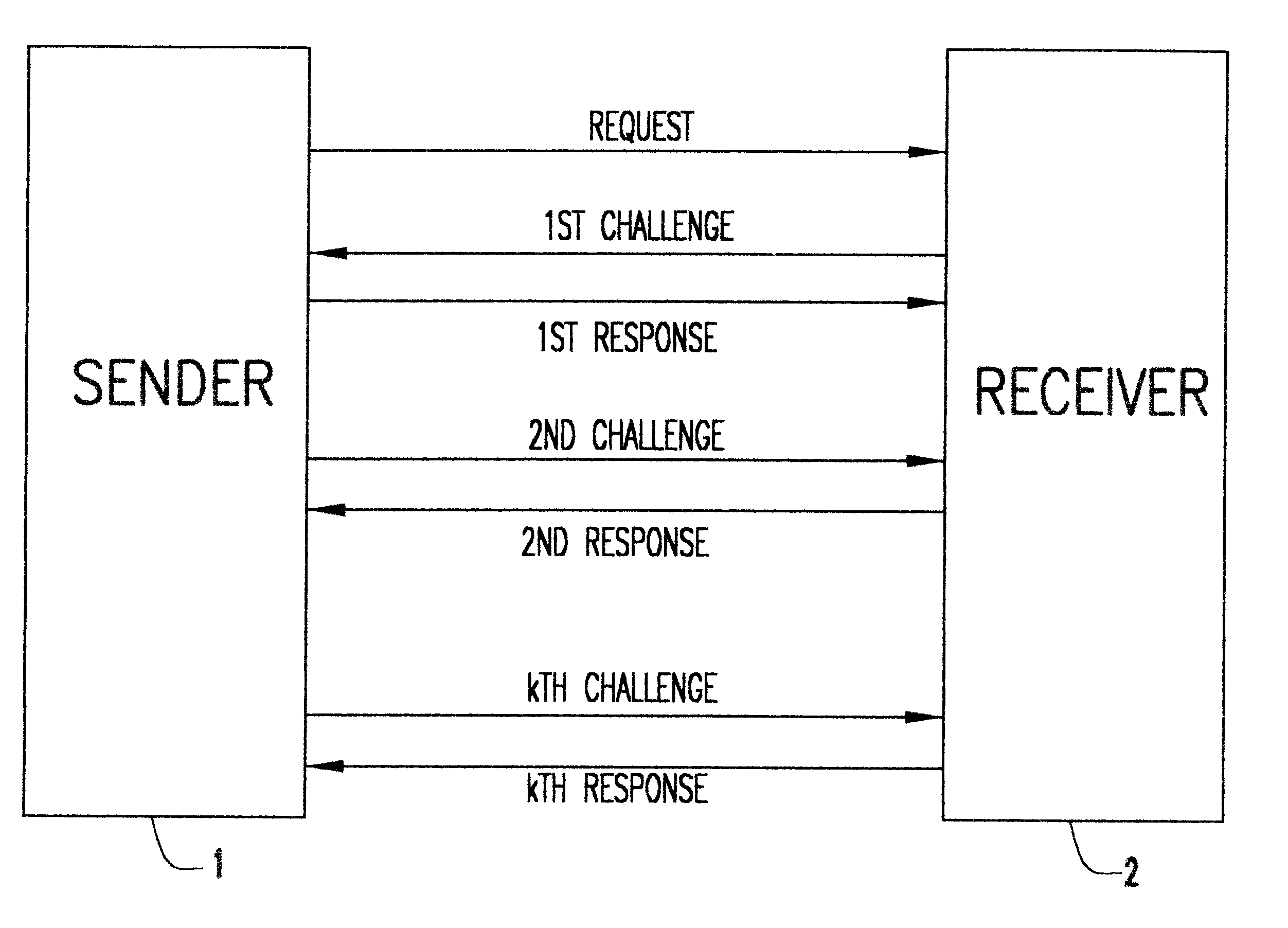
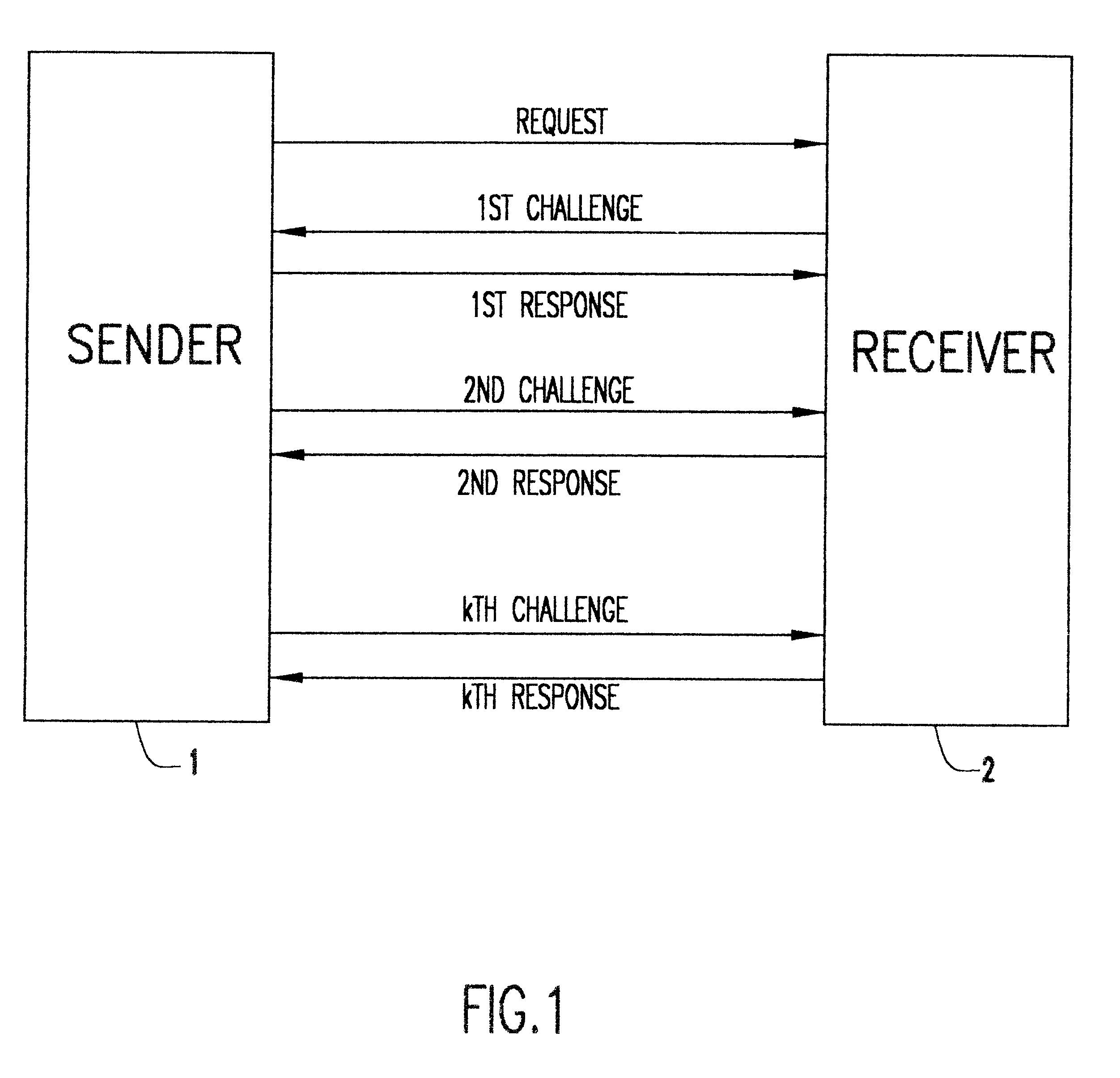
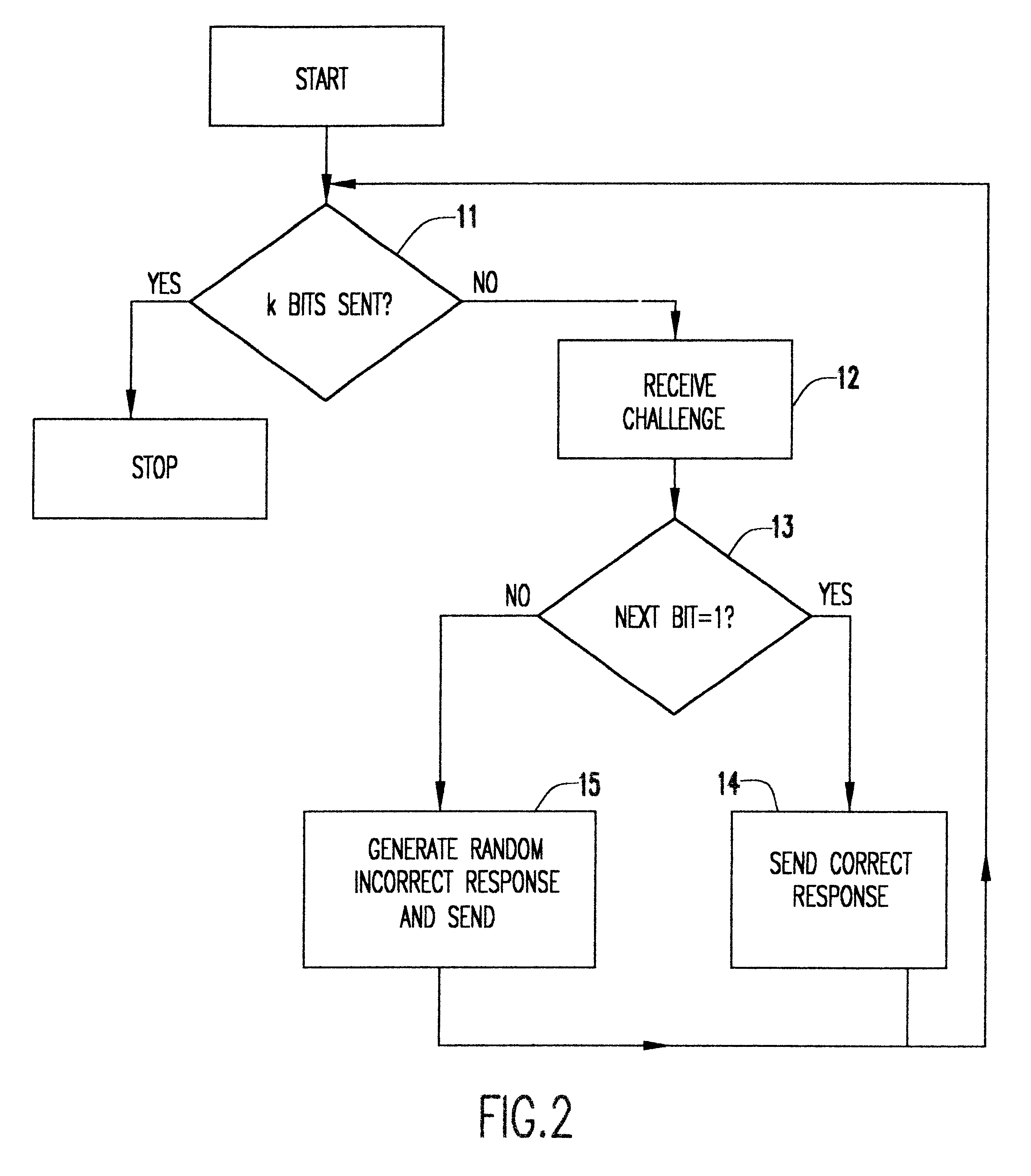
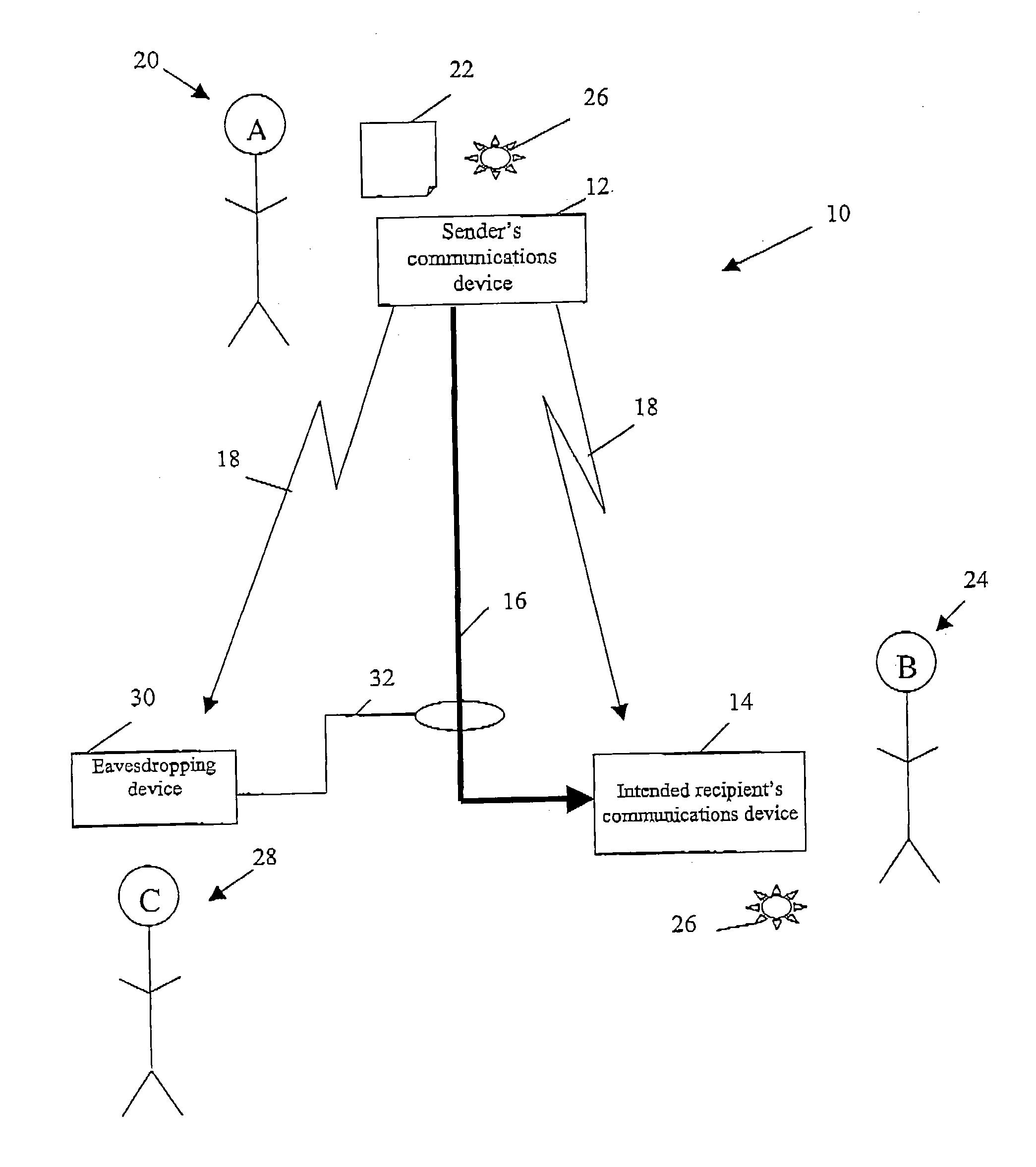
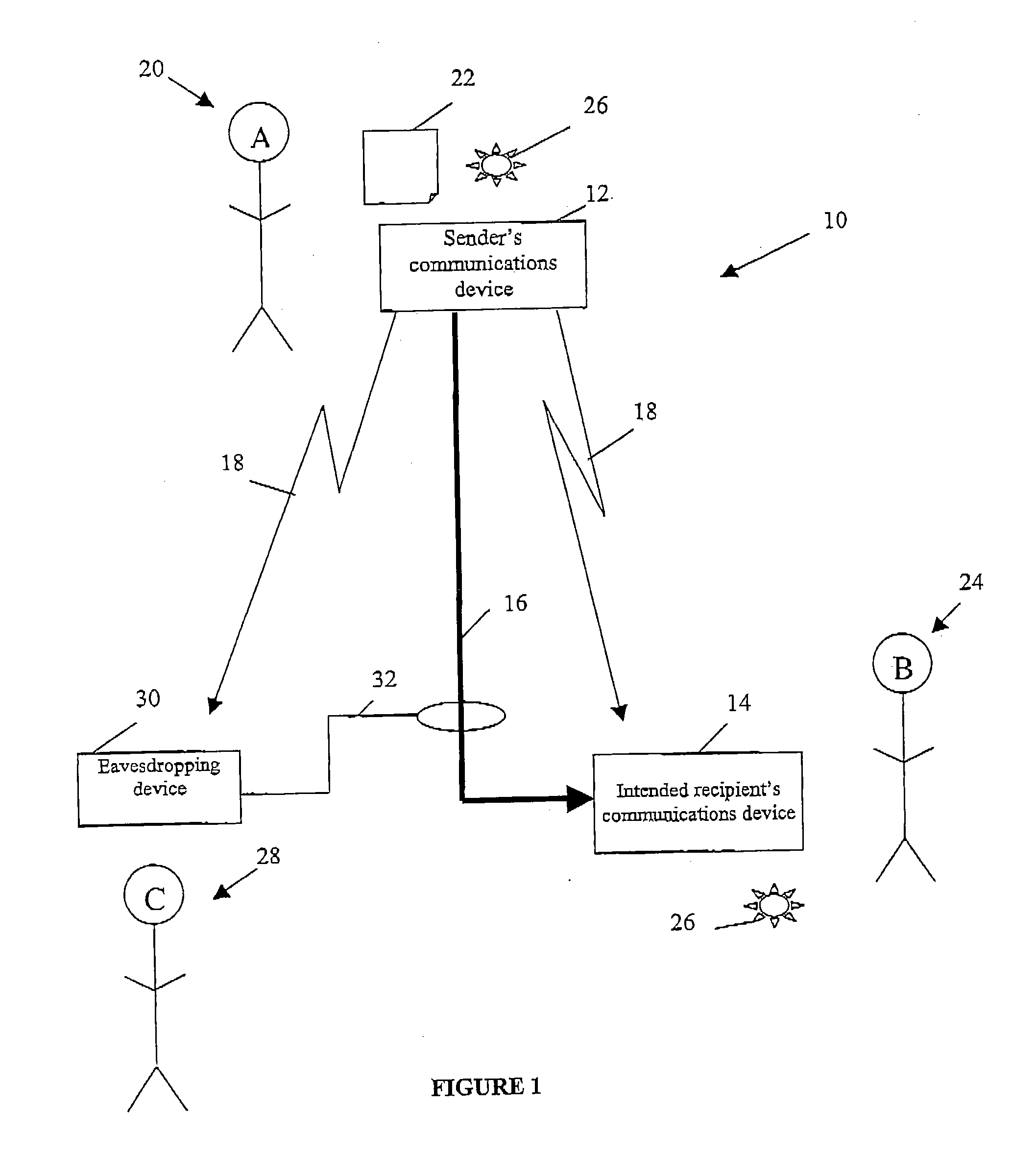
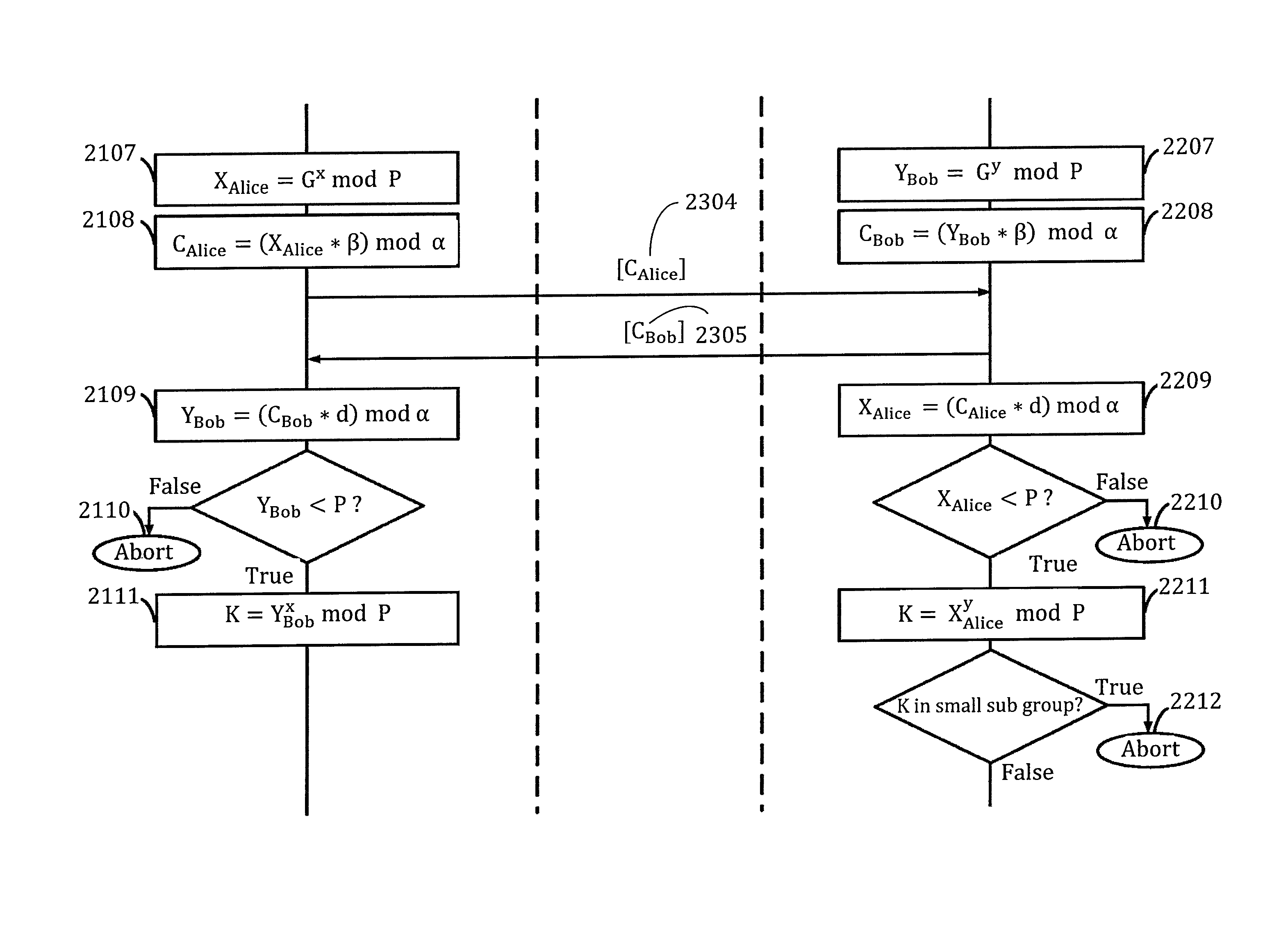
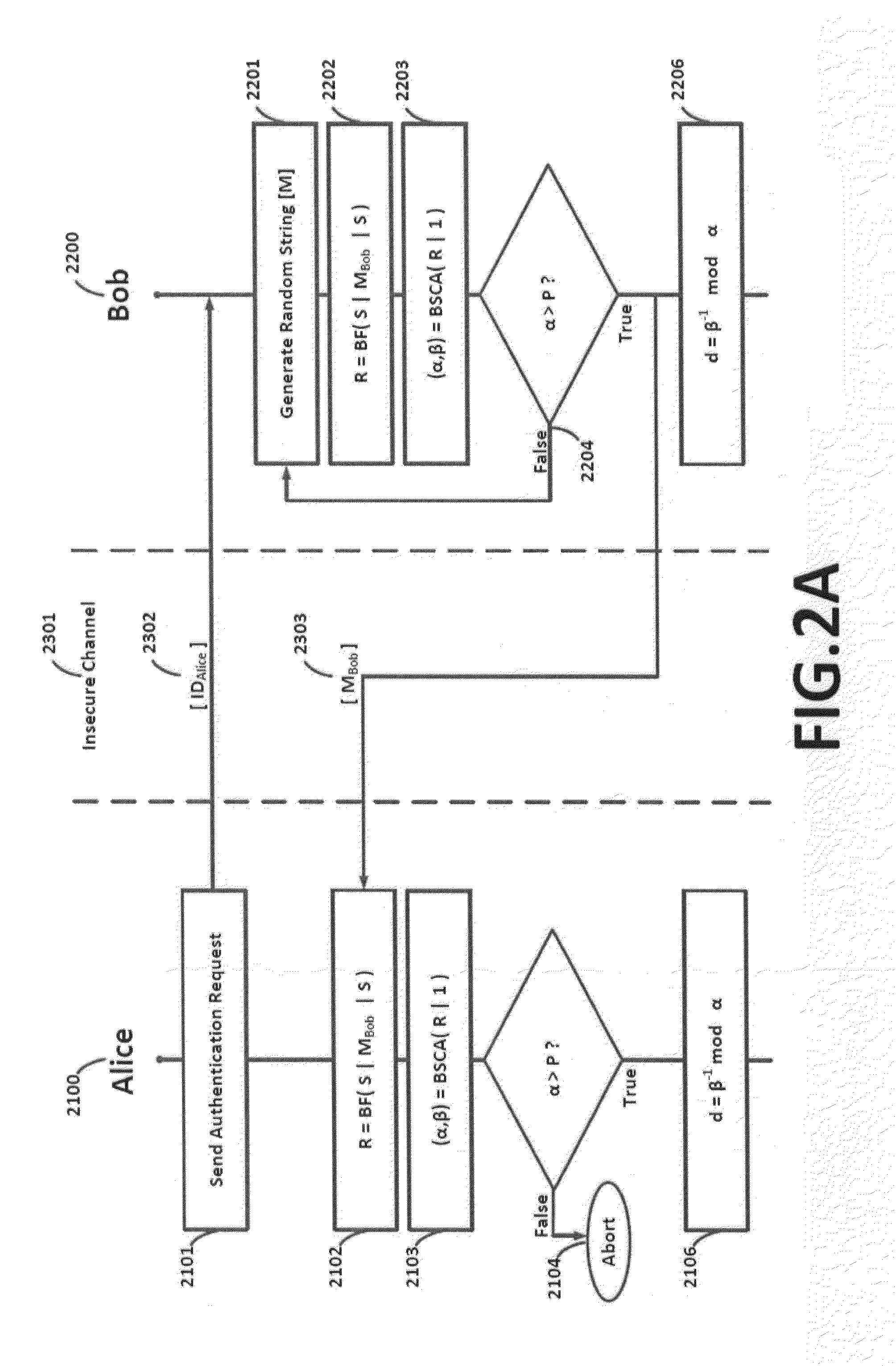
Keyless encryption of messages using challenge response
InactiveUS6535980B1Key distribution for secure communicationUser identity/authority verificationComputer hardwareSecure transmission
A method of keyless encryption of messages allows secure transmission of data where data security is not available for some technical or legal reason. The method of data transfer uses a challenge response in which a correct response to a challenge is used to transmit the value "1", while a deliberately false response is made to transmit the value "0". Any message can be transmitted as a binary string using successive applications of this method.
Owner:IBM CORP
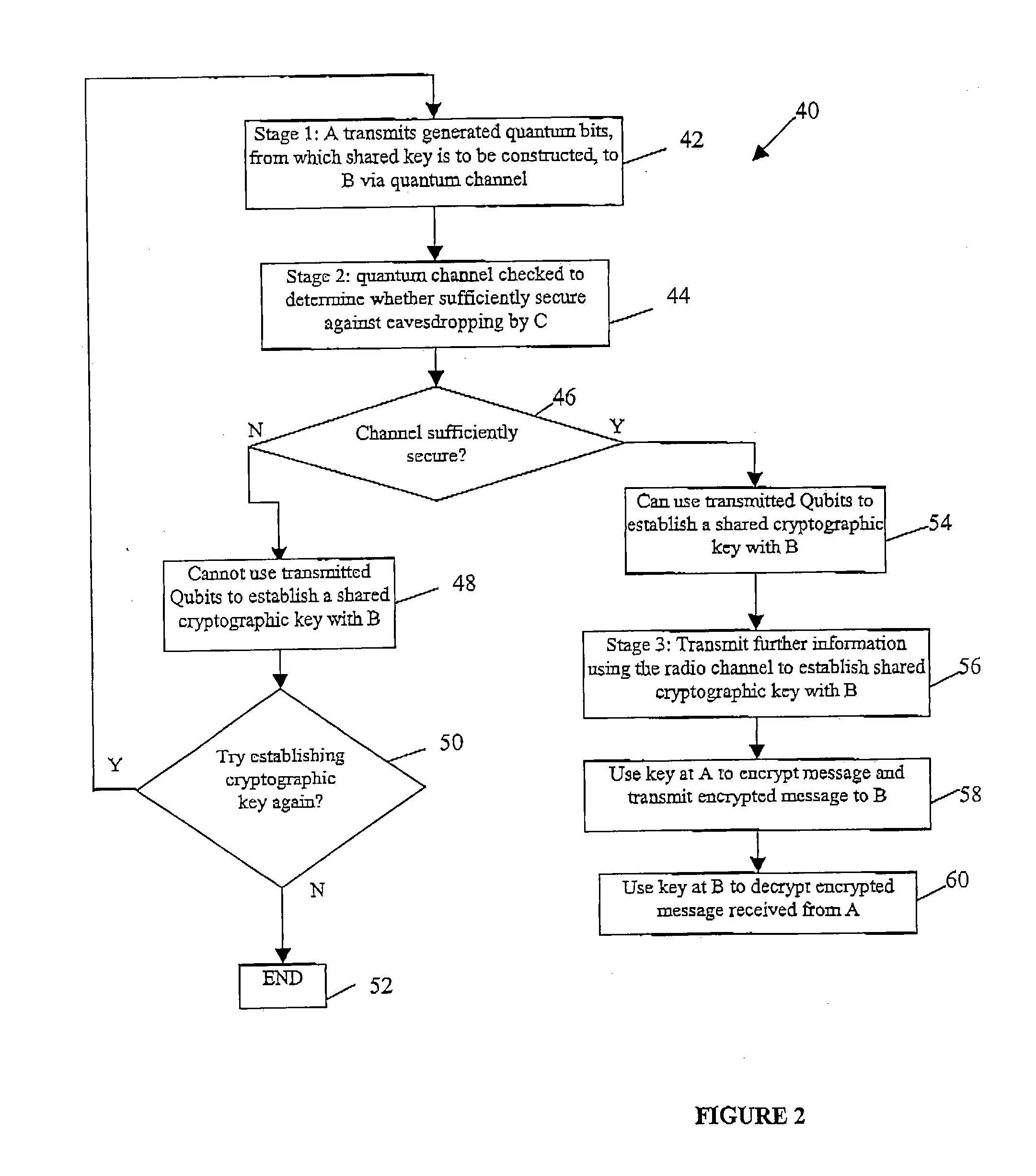
Quantum cryptography
ActiveUS20050036624A1Reduce bitrateIncrease bitrateKey distribution for secure communicationQuantum channelHilbert space
A method of establishing a shared secret random cryptographic key between a sender and a recipient using a quantum communications channel is described. The method comprises: generating a plurality of random quantum states of a quantum entity, each random state being defined by a randomly selected one of a first plurality of bases in Hilbert space, transmitting the plurality of random quantum states of the quantum entity via the quantum channel to a recipient, measuring the quantum state of each of the received quantum states of the quantum entity with respect to a randomly selected one of a second plurality of bases in Hilbert space, transmitting to the recipient composition information describing a subset of the plurality of random quantum states, analysing the received composition information and the measured quantum states corresponding to the subset to derive a first statistical distribution describing the subset of transmitted quantum states and a second statistical distribution describing the corresponding measured quantum states, establishing the level of confidence in the validity of the plurality of transmitted random quantum states by verifying that the first and second statistical distributions are sufficiently similar, deriving a first binary sting and a second binary string, correlated to the first binary string, respectively from the transmitted and received plurality of quantum states not in the subset, and carrying out a reconciliation of the second binary string to the first binary string by using error correction techniques to establish the shared secret random cryptographic key from the first and second binary strings.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
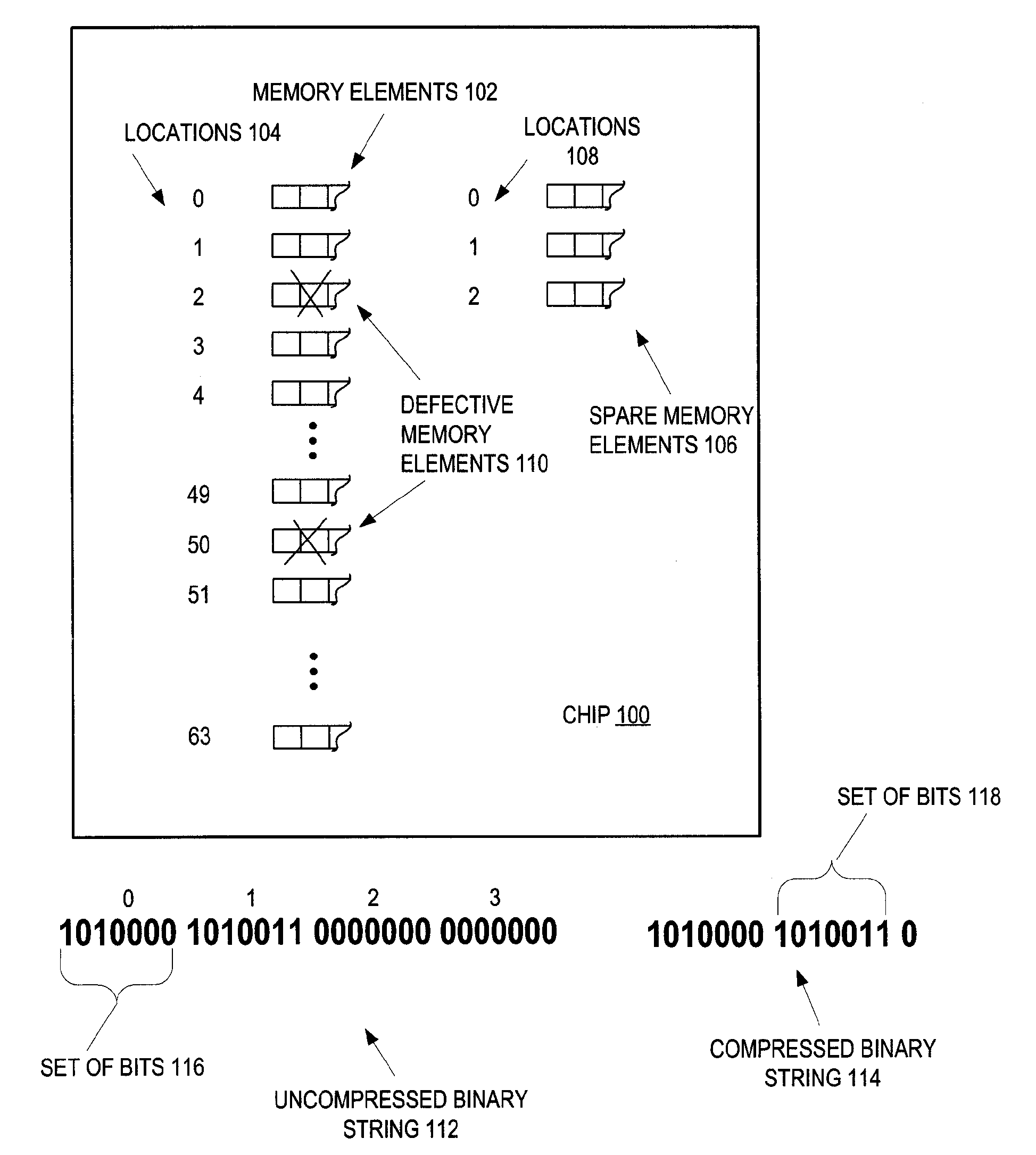
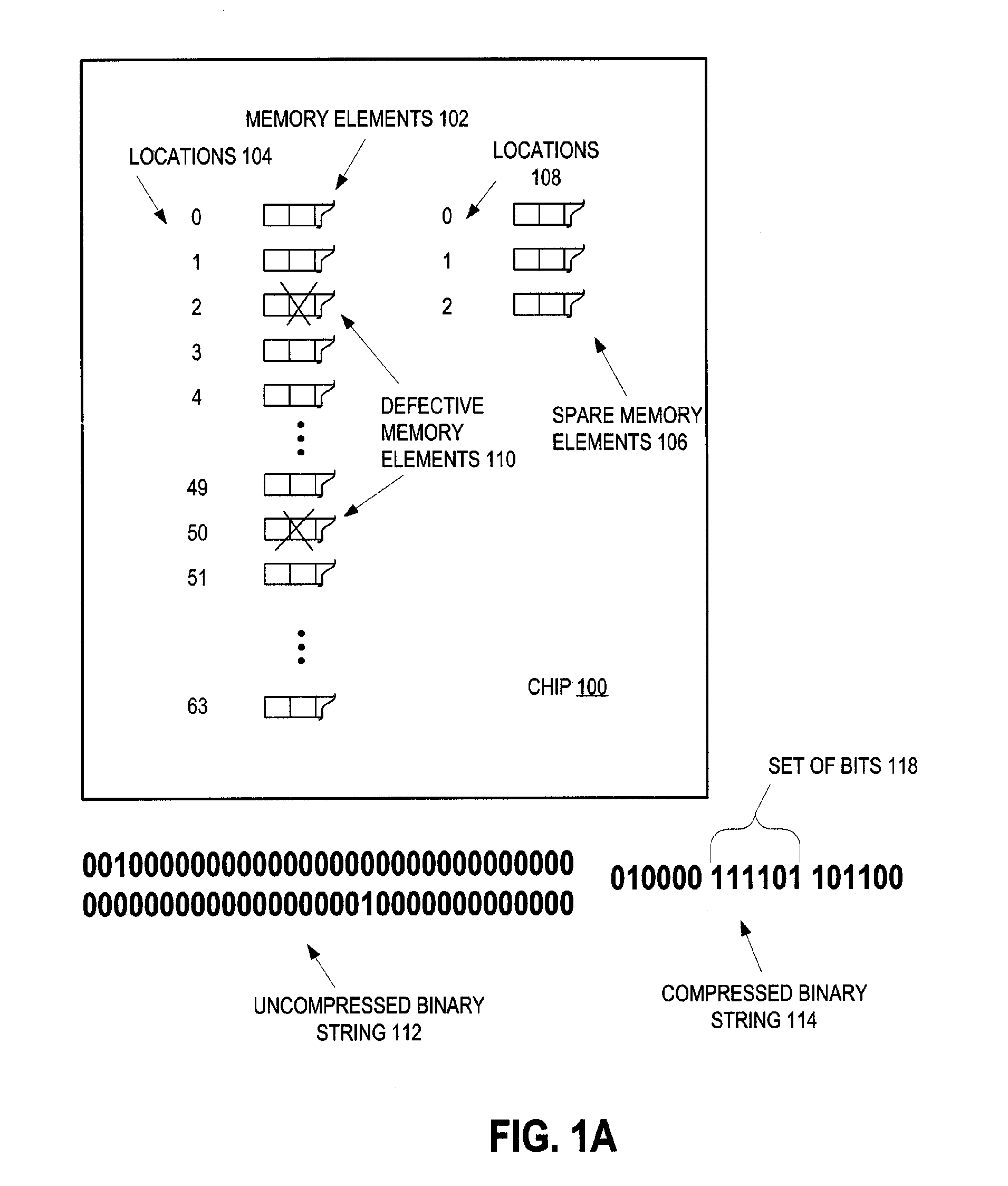
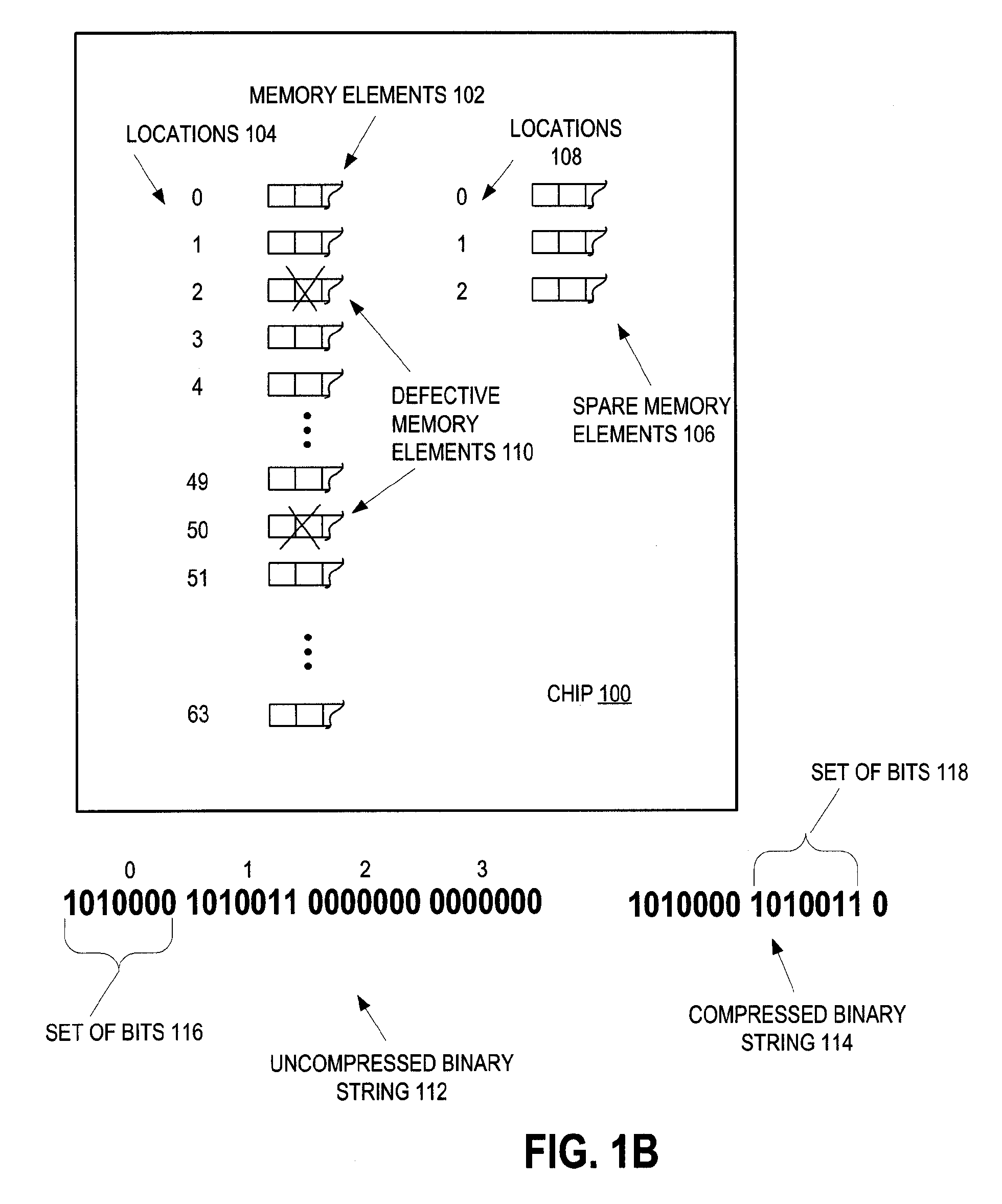
Method and apparatus for increasing fuse programming yield through preferred use of duplicate data
Integrated circuit memory is tested to discover defective memory elements. To replace the defective memory elements, spare memory elements are selected and a string is generated to indicate which ones of the spares replace which ones of the defective memory elements. The number of bits of the string depend upon how many of the memory elements are defective. Although a certain number of the memory elements are defective, which determines the number of the string bits, nevertheless, a number of fuses to program on the integrated circuit is determined responsive to how many fuses are available for programming relative to the number of the binary string bits. That is, if more fuses are available than a certain threshold number relative to the number of string bits (as is preferred), then more than the threshold number are programmed. If not, then only that certain threshold number of fuses are programmed.
Owner:MARVELL ASIA PTE LTD
Self-Adaptive Prefix Encoding for Stable Node Identifiers
InactiveUS20060004858A1Improve efficiencyEasy to exportDigital data processing detailsSemi-structured data retrievalConcurrency controlTheoretical computer science
A variable-length binary string is utilized to encode node identifiers in a tree for an XML document object model. A general prefix encoding scheme is followed; a node identifier is generated by the concatenation of encodings at each level of a tree along a path from a root node to another particular node. Arbitrary insertions are supported without change to existing node identifier encodings. In addition, the method provides for document order when unsigned binary string comparison is used to compare encoded node identifiers. In support of sub-document concurrency control, prefix encoding provides a way to derive ancestor-descendant relationships among nodes in a tree. Lastly, the encoding method provides a natural pre-order clustering sequence, also known as depth-first clustering. If a prefix is applied to an encoding with a level number, starting with zero at the root, width-first clustering will result. A mixed clustering can also be supported.
Owner:IBM CORP
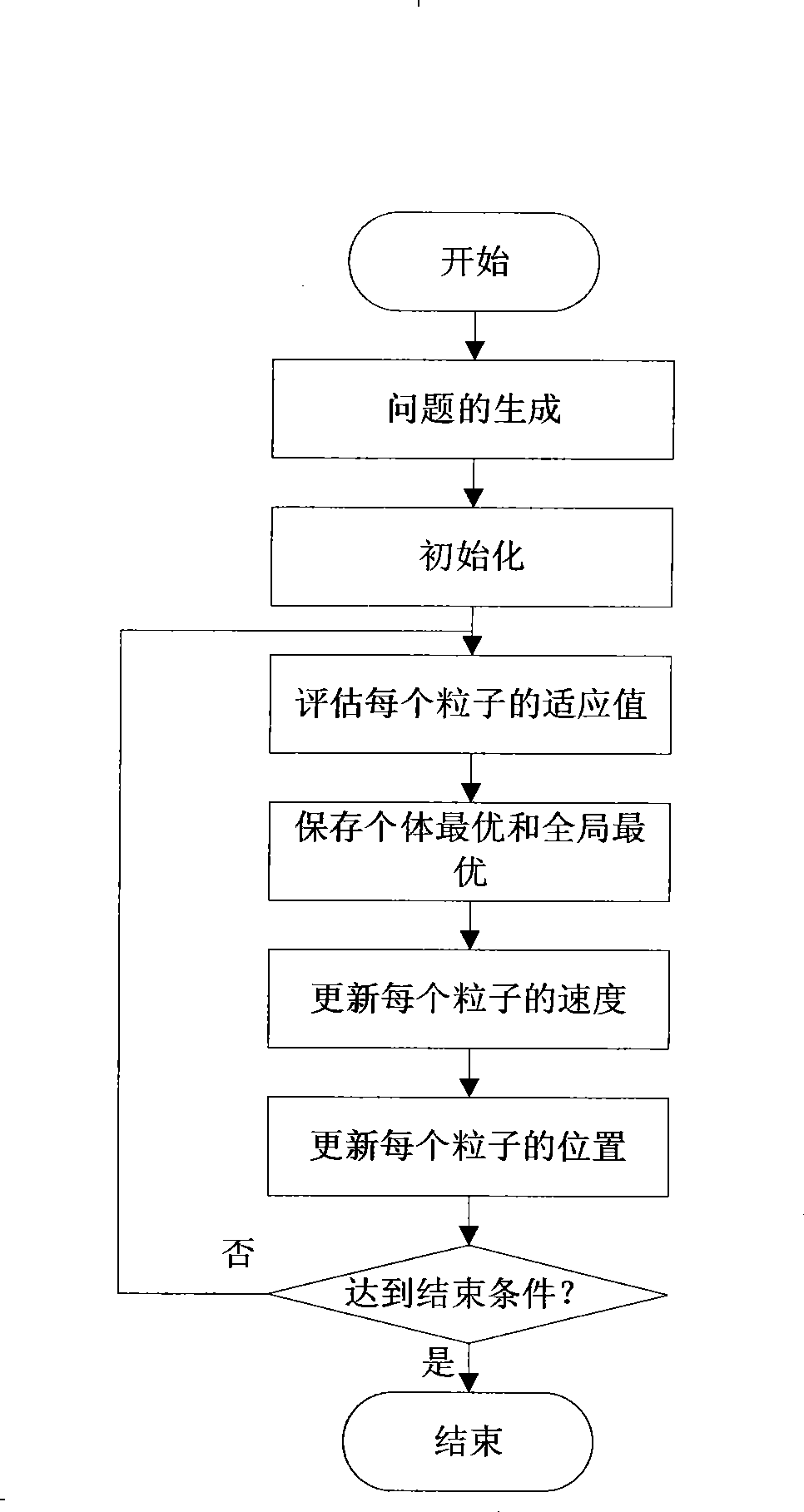
Wireless sensor network node coverage optimization method based on particle swarm algorithm
InactiveCN101448267AIncrease flexibilityIncrease coverageNetwork topologiesNetwork planningCoverage ratioWireless sensor networking
A particle swarm algorithm is applied to an optimum coverage problem of wireless sensor network nodes, and the invention provides a coverage mechanism of the particle swarm optimization algorithm based on a discrete binary edition, and the mechanism is used for performing optimal solution on the wireless sensor network node coverage problem. The method comprises the following steps: defining the wireless sensor network node coverage problem as a 0 / 1 planning problem, encoding individuals of a binary particle swarm algorithm as a 0 / 1 binary string and then performing optimization by an evolutionism of the particle swarm algorithm. In the method, two important indexes are defined to evaluate the solution results, one index is 'coverage' of a region, and the other index is 'consumption rate' of the sensor. Validity and high efficiency of the algorithm are verified by a simulation experiment.
Owner:SUN YAT SEN UNIV
Cellphone-based dynamic two-dimension code access control system
InactiveCN103955975APrevent malicious openingEasy to useIndividual entry/exit registersApplication moduleBinary strings
The invention discloses a cellphone based dynamic two-dimension code access control system. The cellphone based dynamic two-dimension code access control system comprises a cellphone and an access control device with a two-dimension code identification module, a two-dimension code application module is arranged in the cellphone, a binary string code is generated through twice encryption calculation of a preset secret key, a time parameter and the IMEI (International Mobile Equipment Identity) code of the cellphone, and a two-dimension code image generated by the binary string code is used as a key for opening the door; the two-dimension code image is obtained through scanning of the two-dimension code identification module, and the IMEI code for opening the door and the key generation time are obtained through identification and decoding, the door is opened after verification, and the key which is used for opening the door this time is abolished. The cellphone-based dynamic two-dimension code access control system has the characteristics that one key only can open the door once and can not be copied, the security is high, and the cellphone is used as the carrier of the key to achieve carrying convenience.
Owner:广州闪购软件服务有限公司
Cryptographic method and system for secure authentication and key exchange
InactiveUS20150319149A1Key distribution for secure communicationUser identity/authority verificationKey exchangeComputer hardware
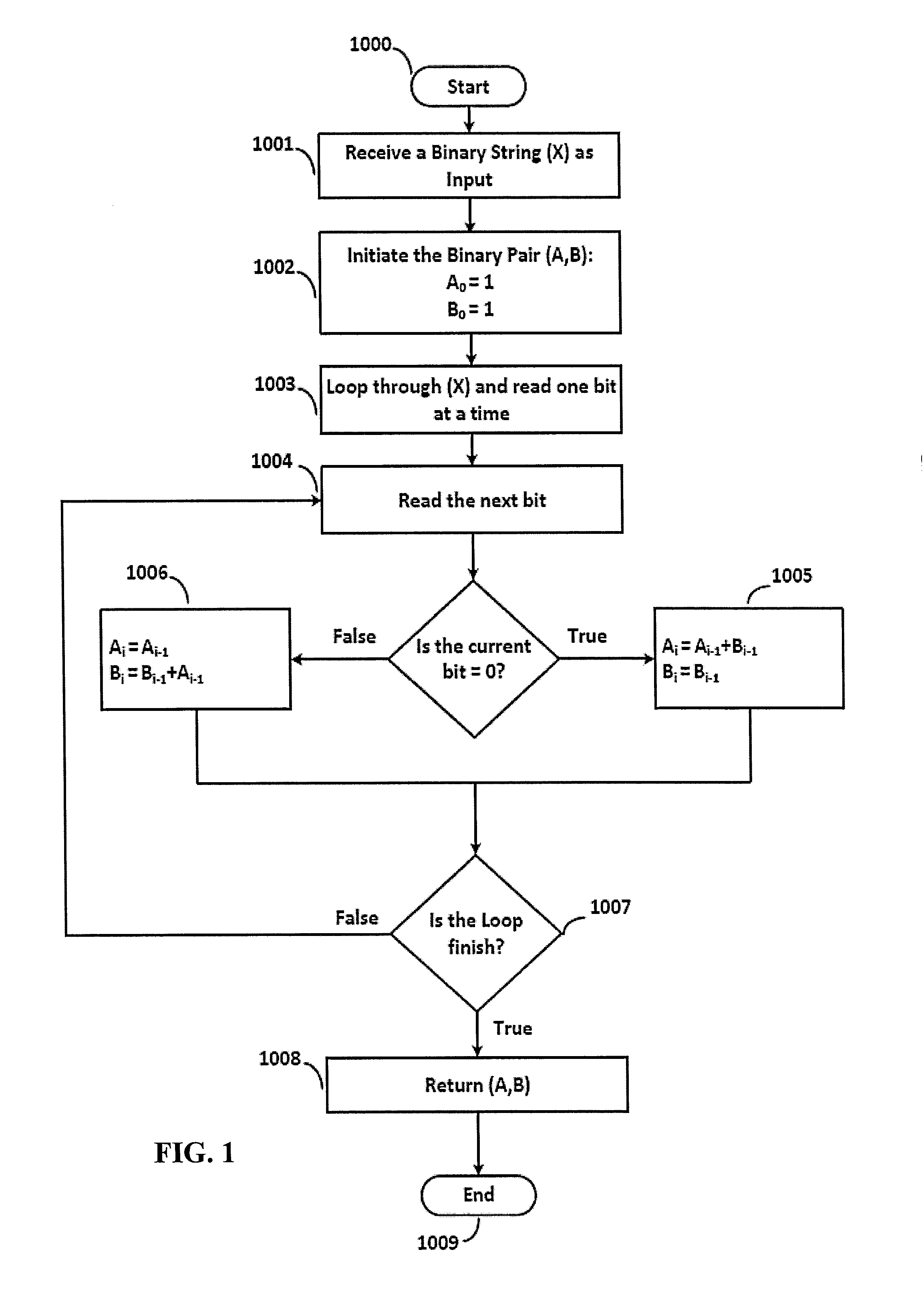
A method and algorithm of authentication between parties includes receiving a randomly generated binary string. A shared secret of the parties is combined with the randomly generated binary string to form a new binary string. A binary pair (A, B) is initiated; a first bit of the new binary string is read. A current value of B is added to A when the read bit is zero, and a current value of A is added to B when the read bit is one. A next bit of the new binary string is read. The steps of adding the current values and reading a next bit are repeated until all bits have been read. A resulting binary pair (A, B) is returned after all of the bits have been read. Ephemeral Diffie-Hellman public keys are securely exchanged between the parties. Challenge responses are exchanged and a session key is agreed upon.
Owner:ALSHAMMARI THAMIR
Method and apparatus for compressing three-dimensional point cloud data
InactiveUS20130297574A1Ease storageFacilitate transmissionDigital data information retrievalDigital data processing detailsComputational scienceVoxel
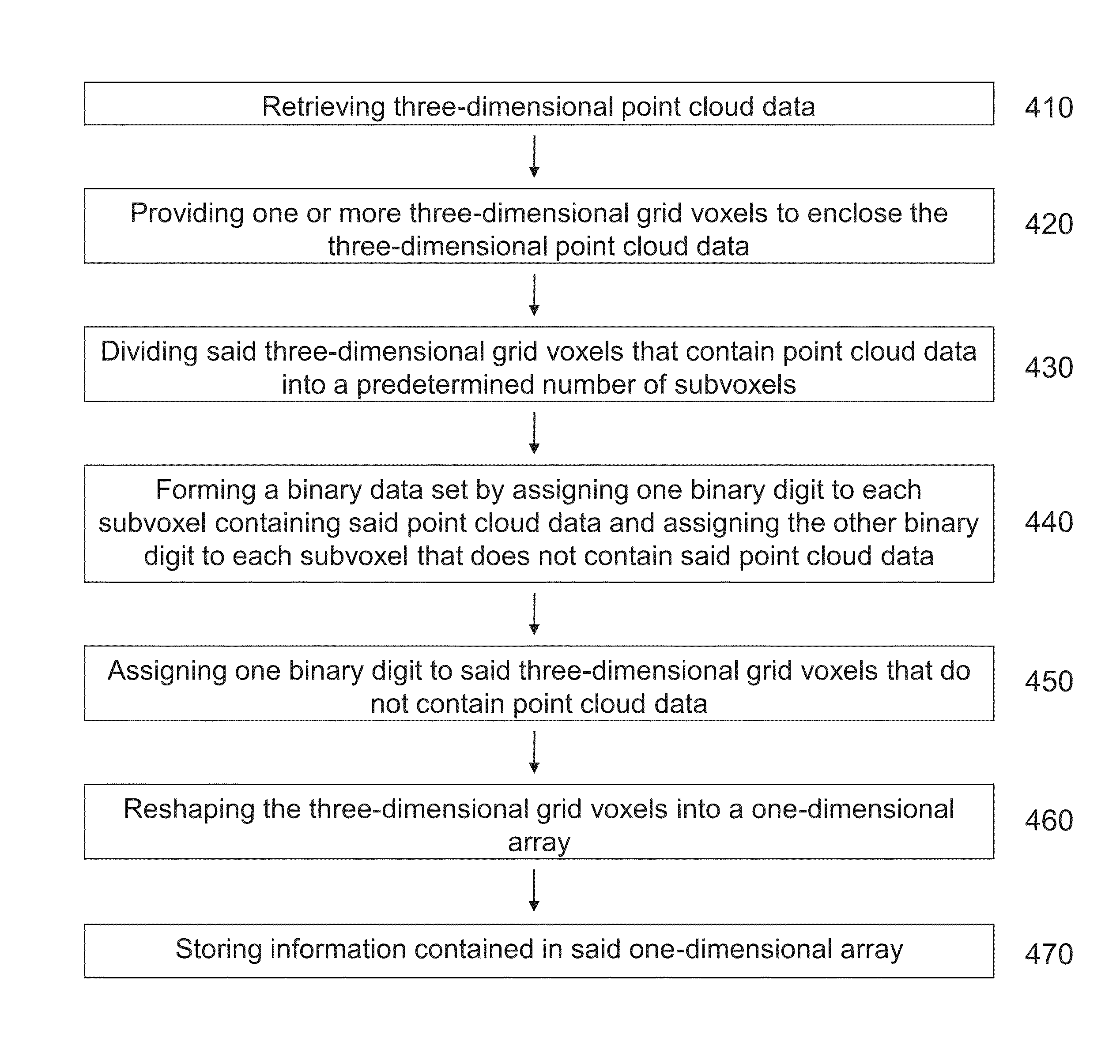
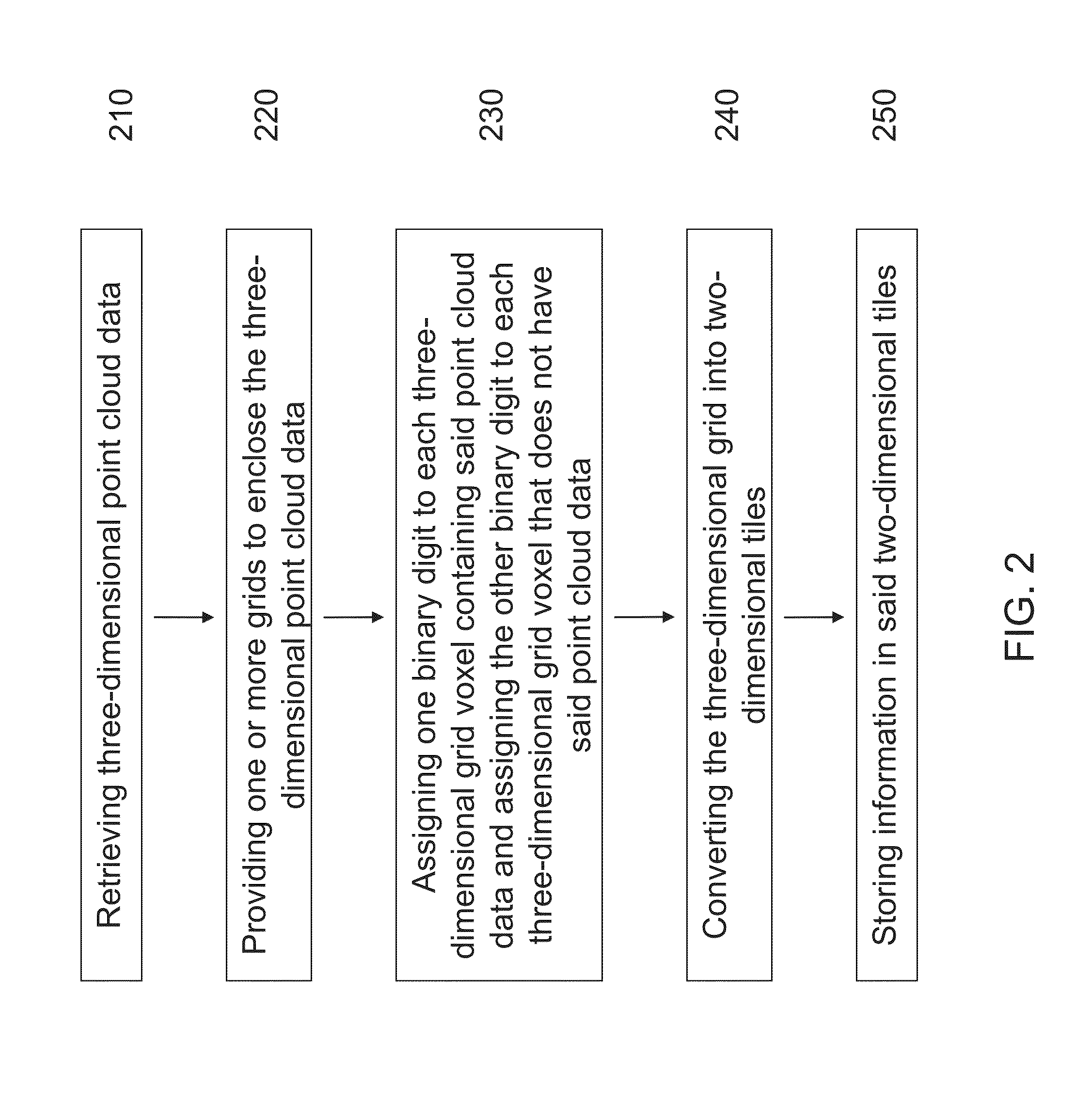
A method and apparatus for compressing three-dimensional point cloud data is disclosed. In one aspect, a method for compressing three dimensional point cloud includes steps of retrieving three-dimensional point cloud data; providing one or more grids to the three-dimensional point cloud data; assigning one binary digit to each three-dimensional grid voxel containing said point cloud data and assigning the other binary digit to each three-dimensional grid voxel that does not have said point cloud data; converting the three-dimensional grid into two-dimensional tiles; and storing information of a plurality of binary strings in said two-dimensional tiles. In one embodiment, the step of storing information of a plurality of binary strings in said two-dimensional tiles includes a step of storing the number of repeating times of each binary digit in the binary strings. The method can significantly reduce memory space, as well as preserving small details of the point cloud.
Owner:LEVEL SET SYST
Method for designing dna codes used as information carrier
InactiveUS20070042372A1Improve stabilityEasy to detectFungiSugar derivativesDna geneticsInformation transmission
The present invention provides a method for designing DNA code consisting of a set of information codes as an information carrier to write optional information into an optional noncoding region not including any DNA genetic information which can avoid an error occurring when the designed DNA is used. A set S1 of the base sequences corresponding to a signal unit for information transmission is obtained as follows: 1) selecting a template such that its Hamming distance of templates, against its block shift, and against the ligated sequences are equal to or above the predetermined value, when DNA sequence of predetermined length is specified by the binary string of 0 and 1 (template), meaning that the position of G or C ([GC]), or A or T ([AT]) are fixed, 2) further selecting a template having a subword constraint of length m from the set of the selected templates, and 3) combining thus selected template and codewords of the predetermined error-correcting codes having a subword constraint of length m.
Owner:NAT INST OF ADVANCED IND SCI & TECH
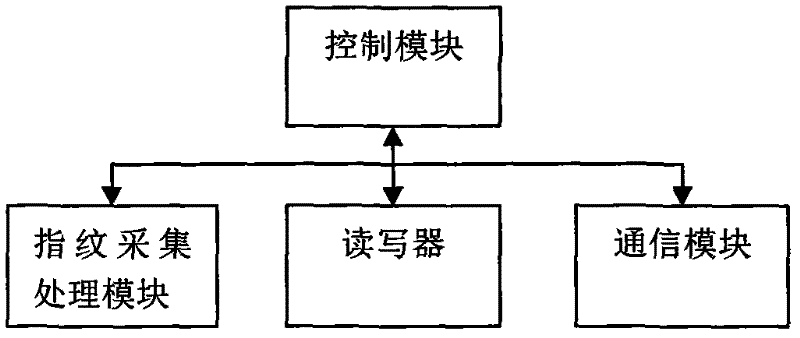
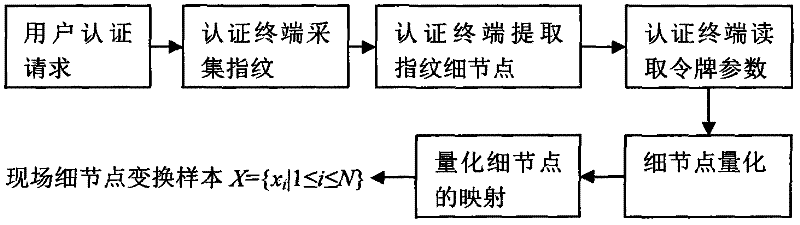
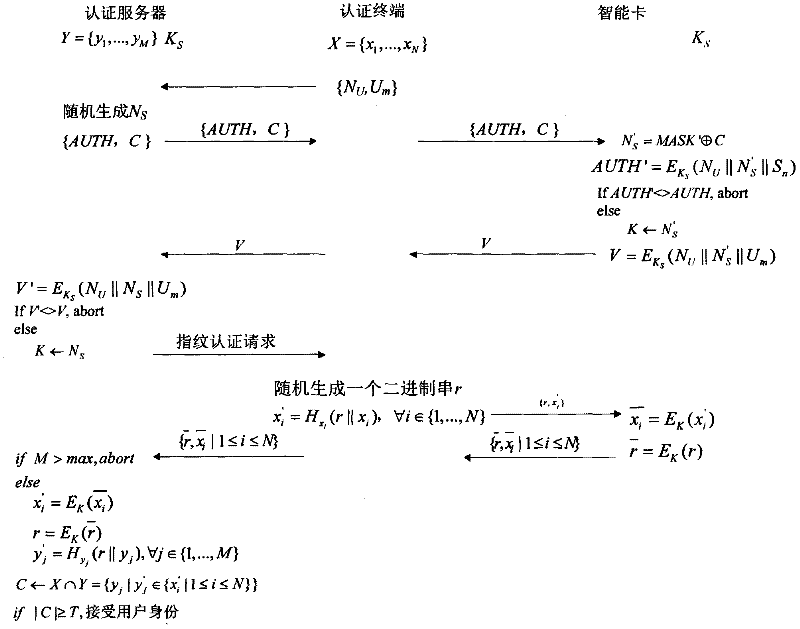
Privacy-protection fingerprint authentication method and system based on token
InactiveCN102394896AImprove securityPrivacy protectionUser identity/authority verificationPrivacy protectionAuthentication server
The invention provides an identity authentication method and system using fingerprints in an open network. The identity authentication system comprises an authentication terminal, an authentication server, a token and an authentication information issuance server. The identity authentication method comprises the following steps: the authentication terminal or the token calculates a hash value in the event that transformation detailed points and a random binary string are cascaded with each other, the token encrypts the hash value, the authentication terminal transfers the encryption result of the token to the authentication server, and the authentication server cascades the encrypted binary string with each stored template set value and calculates a cascaded hash value; and the authentication server judges whether identity of a user is accepted according to the number of the transformation detailed points matched with the hash value. By adopting the identity authentication method and system, private fingerprint data of the user and the authentication server is not leaked to each other during the fingerprint identity authentication process in an open network environment, which protects data privacy of the user and the authentication server.
Owner:GANSU AGRI UNIV
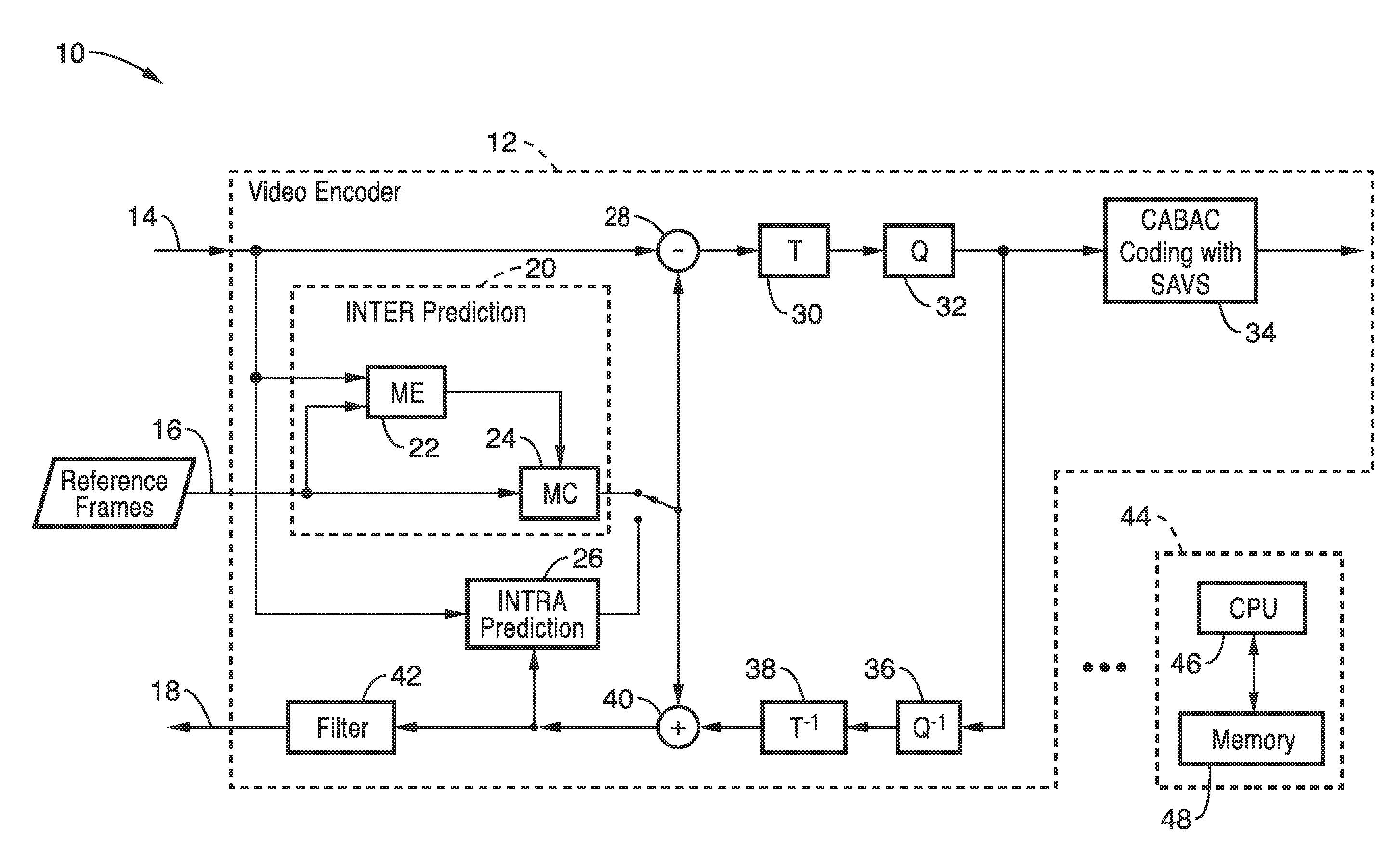
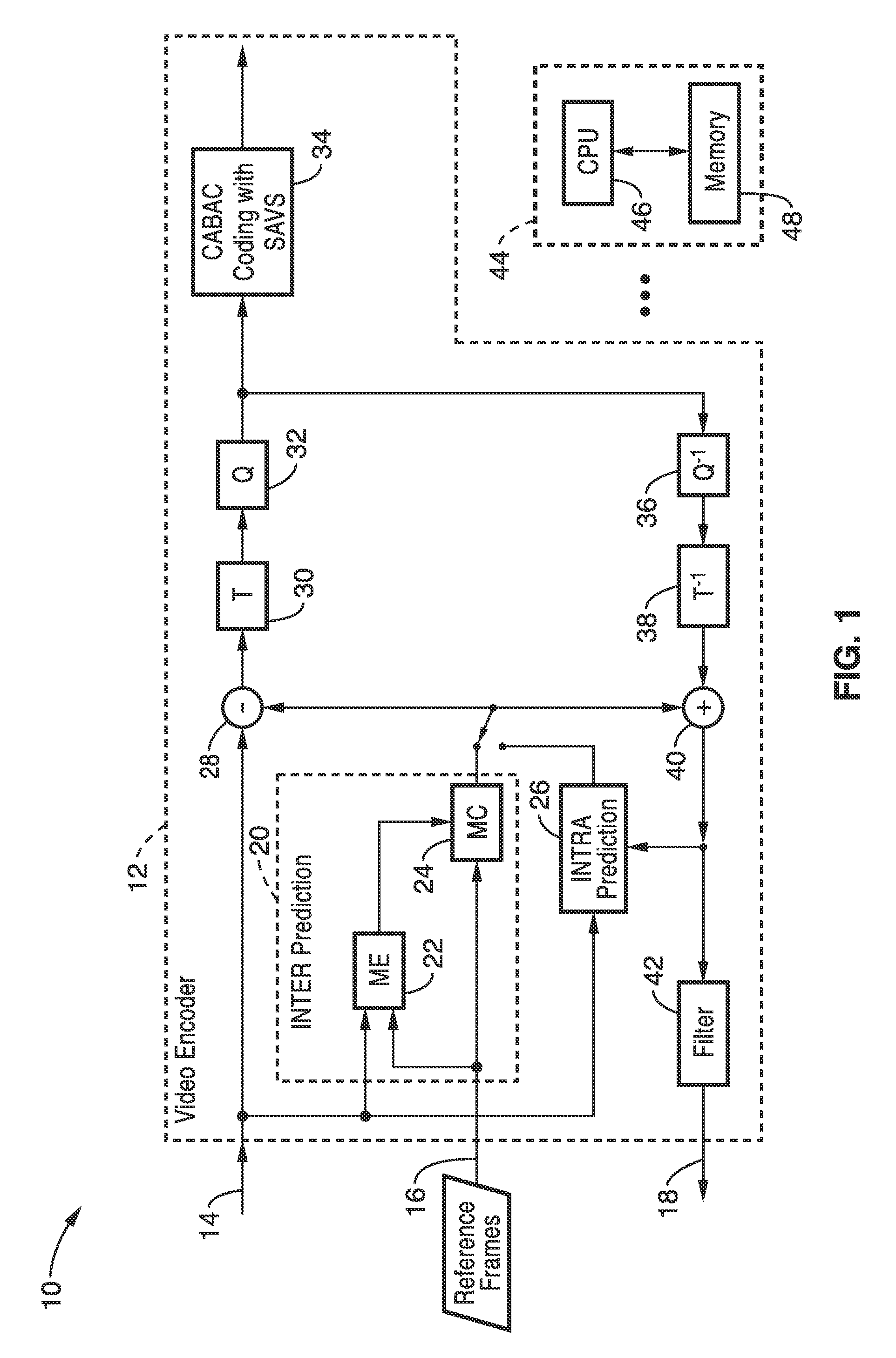
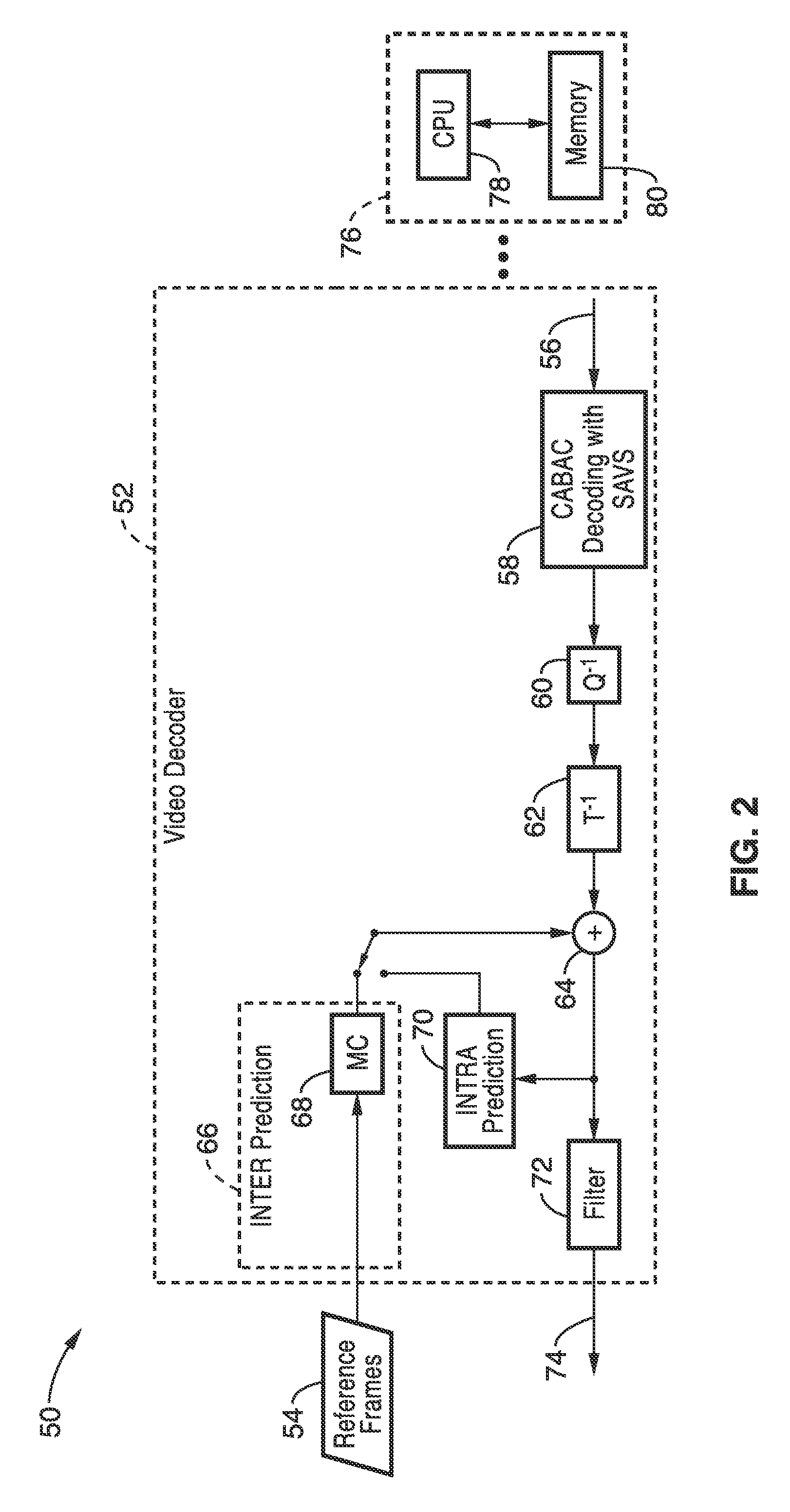
Binarization of dqp using separate absolute value and sign (SAVS) in cabac
ActiveUS20120320971A1Color television with pulse code modulationColor television with bandwidth reductionUnary codingContext based
Video coding systems or apparatus utilizing context-based adaptive binary arithmetic coding (CABAC) during encoding and / or decoding, are configured according to the invention with an enhanced binarization of non-zero Delta-QP (dQP). During binarization the value of dQP and the sign are separately encoded using unary coding and then combined into a binary string which also contains the dQP non-zero flag. This invention capitalizes on the statistical symmetry of positive and negative values of dQP and results in saving bits and thus a higher coding efficiency.
Owner:SONY CORP
Industrial Internet intrusion detection method based on flow feature map and perception hash
InactiveCN107070943AMeet the robustnessGood intrusion detection performanceData switching networksSingular value decompositionData set
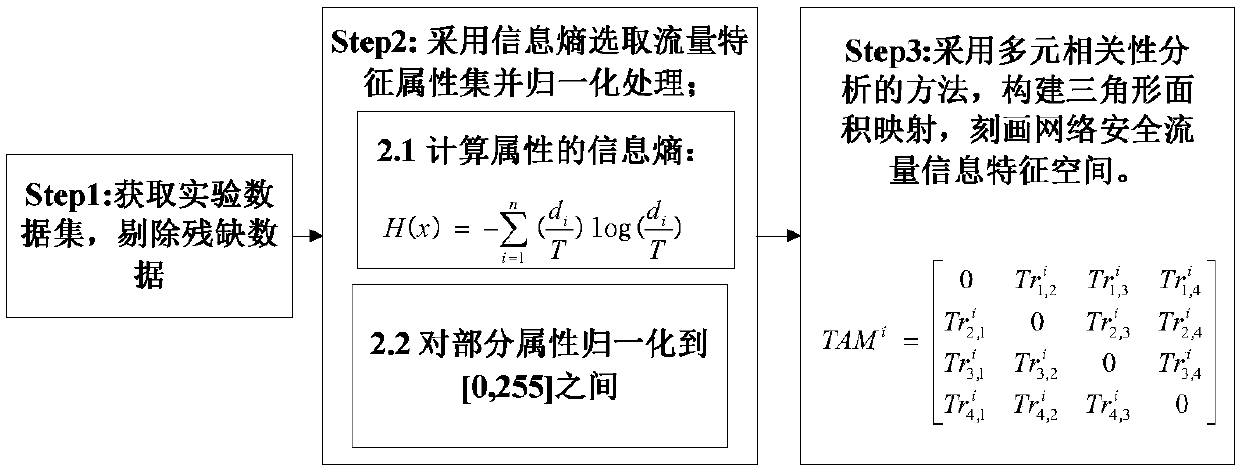
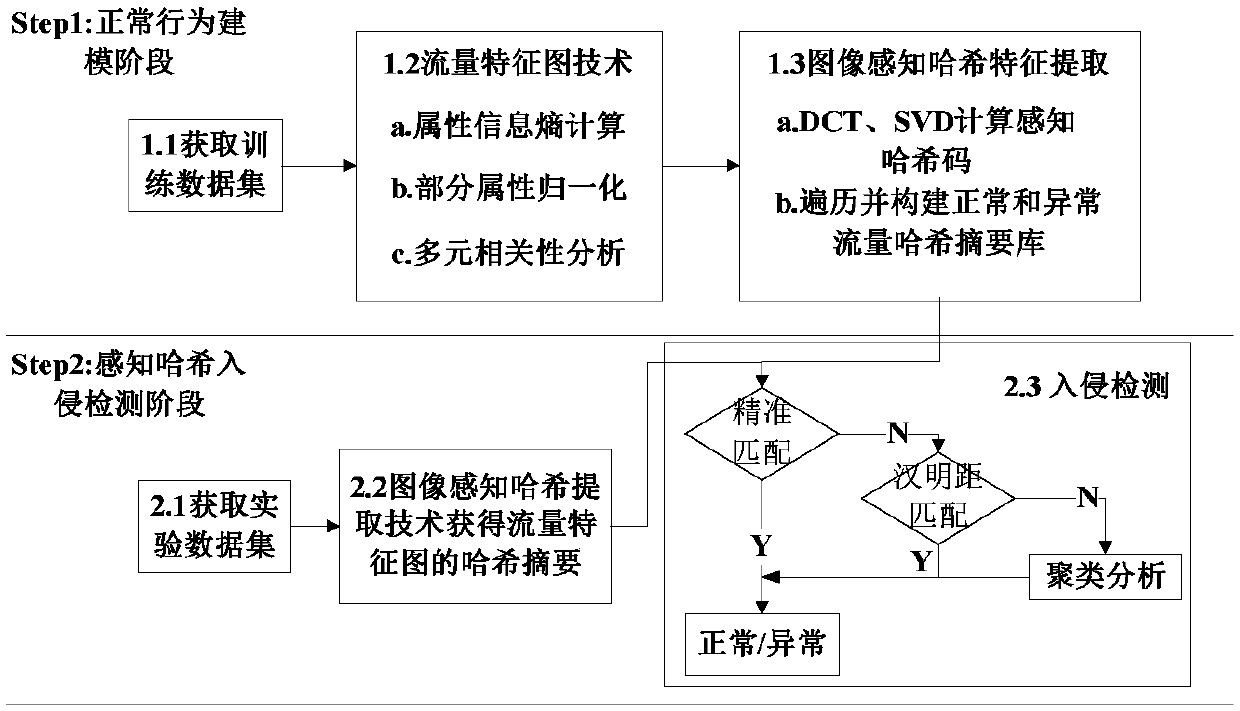
The invention provides an industrial Internet intrusion detection method based on a flow feature map and perception hash for mainly solving the problems of low detection performance and poor adaptability of the existing industrial Internet intrusion detection method. The industrial Internet intrusion detection method draws lessons from an image processing method and comprises the following steps: firstly obtaining a standard test bed experimental data set, performing feature selection by using an information entropy method to construct a flow feature vector, and performing a normalization operation on a part of attributes; then, converting the flow feature vector into a triangle area mapping matrix by using a multivariate correlation analysis method to construct the flow feature map; and finally, obtaining a hash abstract of the flow feature map by using an image perception hash algorithm based on discrete cosine transform SVD and singular value decomposition SVD, and generating an intrusion detection rule set in the form of a binary character string. Moreover, hash matching is performed by using an accurate matching method based on character strings, a similarity measurement method based on a normalized Hamming distance and a clustering analysis method based on a Euclidean distance so as to detect abnormal flow and malicious intrusion in the industrial Internet.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
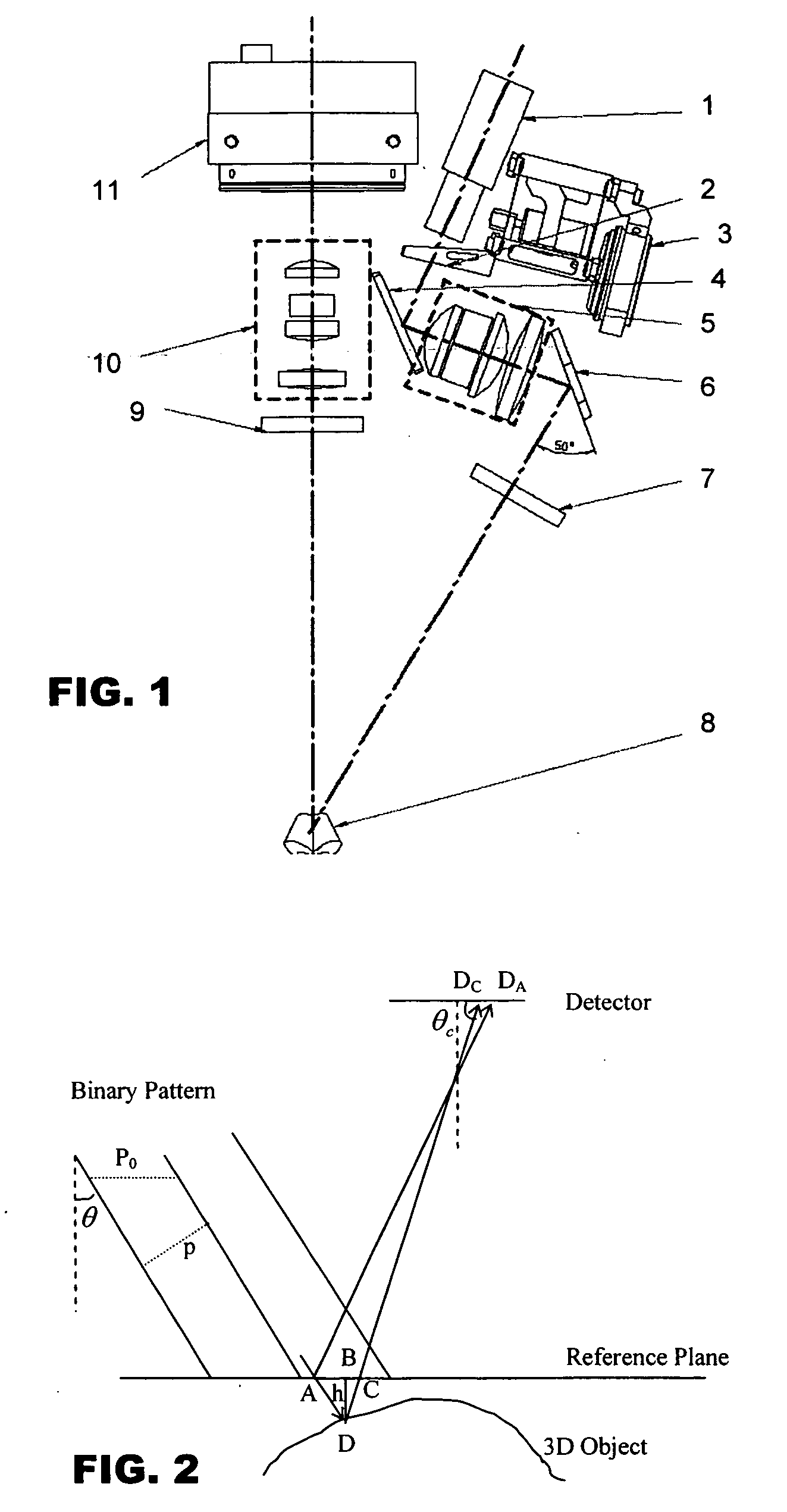
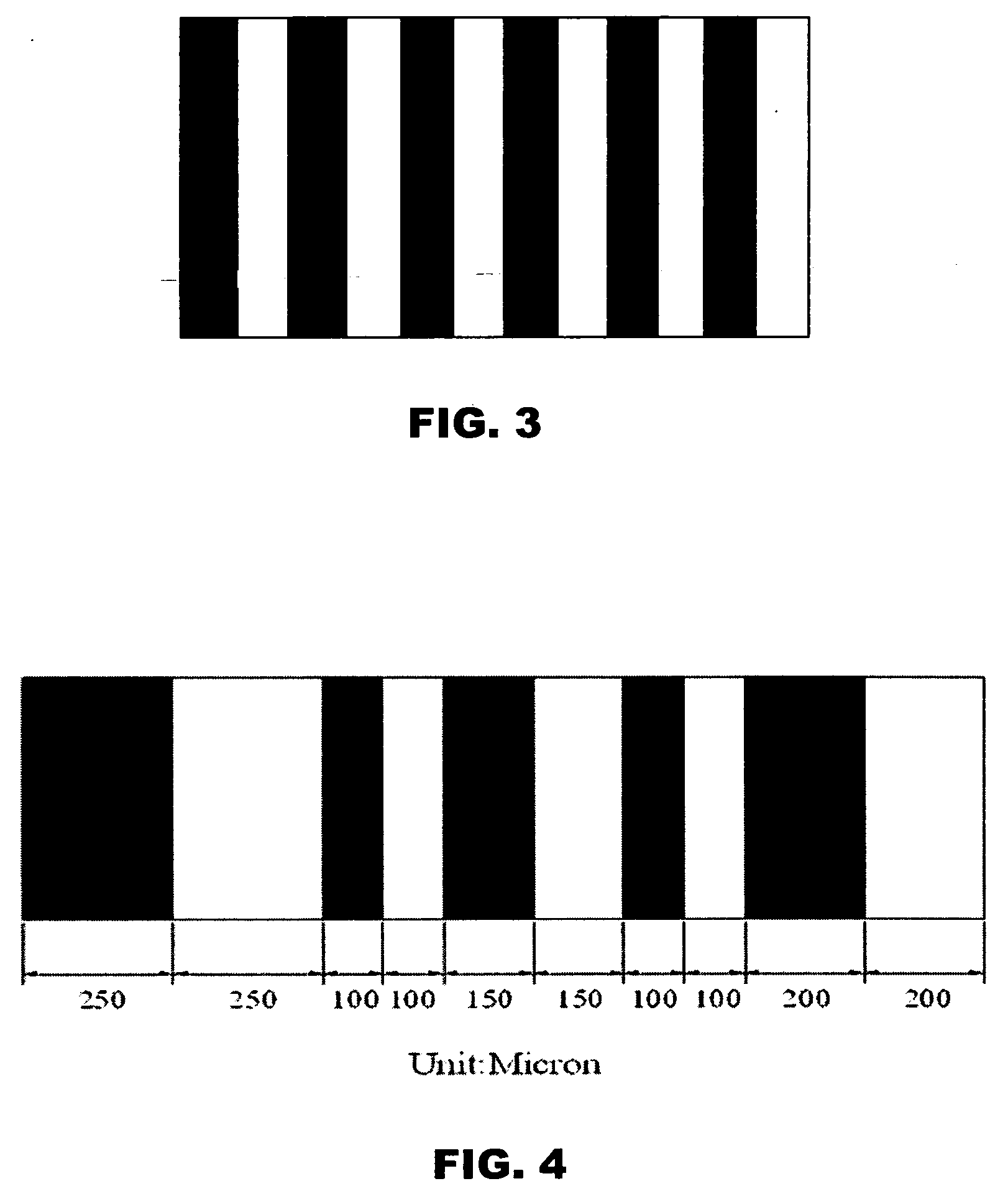
Imaging system for three-dimensional reconstruction of surface profiles
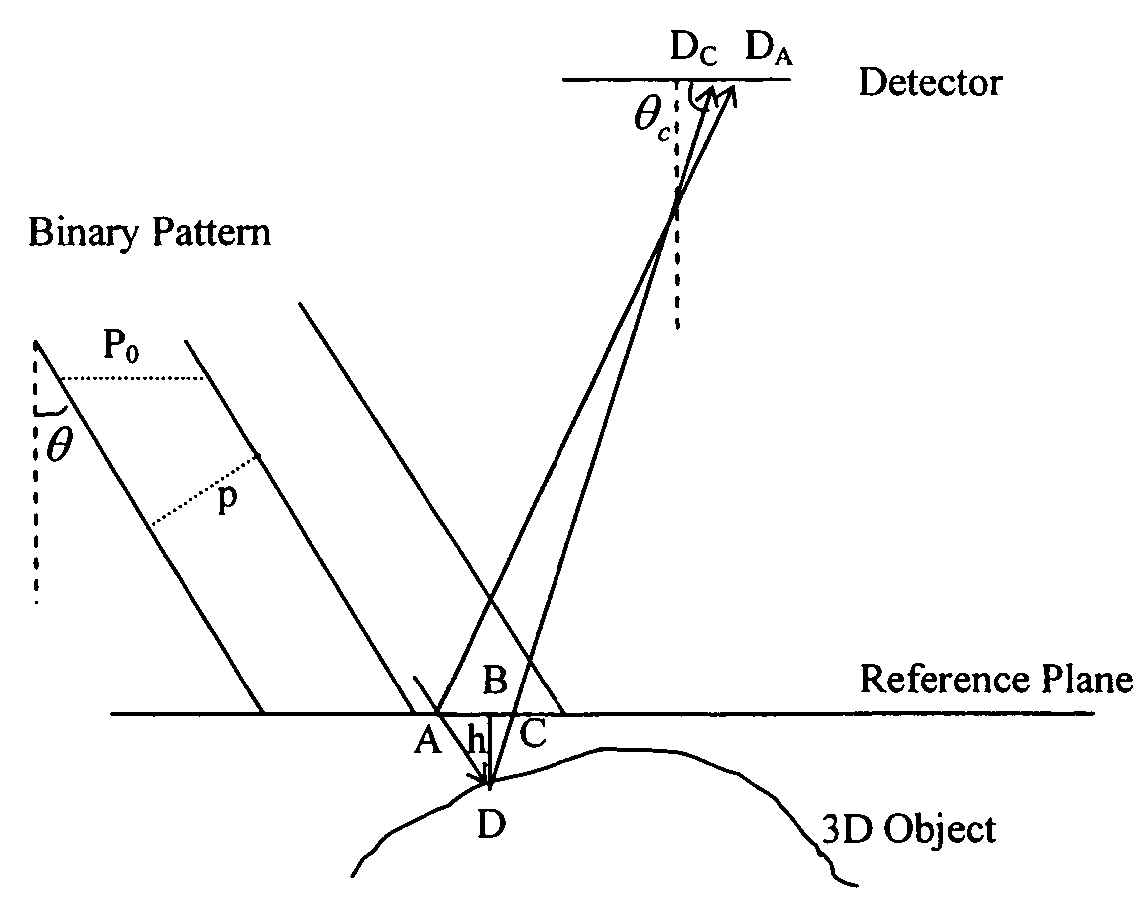
ActiveUS20060132802A1Avoid disadvantagesCharacter and pattern recognitionUsing optical meansBinary stringsSurface contour
A system for three-dimensional reconstruction of a surface profile of a surface of an object is provided that utilizes a binary pattern projected onto the surface of the object. A binary string consisting of a series of “1”s and “0”s is first created, and a binary pattern of light that is constructed in accordance with the binary string such that bright and dark bands of light of equal widths correspond to “1”s and “0”s from the binary string respectively is projected onto the surface. The binary pattern is shifted with respect to the surface multiple times, during which an image of the binary pattern illuminating the surface is obtained at each position of the binary pattern. Thereafter, a height of each predetermined point on the surface is calculated relative to a reference plane based upon the images cumulatively obtained at said predetermined point.
Owner:ASM ASSEMBLY AUTOMATION LTD
Encoding method, decoding method, encoding device and decoding device
Embodiments of the invention provide an encoding method, a decoding method, an encoding device and a decoding device. The encoding method comprises the following steps: acquiring to-be-encoded data, wherein the to-be-encoded data is a binary character string; and encoding the to-be-encoded data according to base-64 encoding rules to get encoding data corresponding to the to-be-encoded data, wherein the encoding data is a base-64 encoding character string, and the 64 encoding rules employ the following 64 characters: 0-9, @, A to Z, _, and a to z. On the basis of shortening the length of the to-be-encoded data and saving the storage space, the encoding method in the embodiment of the invention is of higher compatibility because all the characters in the character set employed by the encoding method can be used as a file name under the Linux operating system and the Windows operating system, and the characters '@' and '_' can be used directly in shell and regular expressions and are compatible with code statements in the common language C / C++ / Java.
Owner:HUAWEI TECH CO LTD +1
Vector dot product accumulating network supporting reconfigurable fixed floating point and configurable vector length
InactiveCN102520906ASimplify complexityHigh densityComputation using non-contact making devicesParallel computingFloating point
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
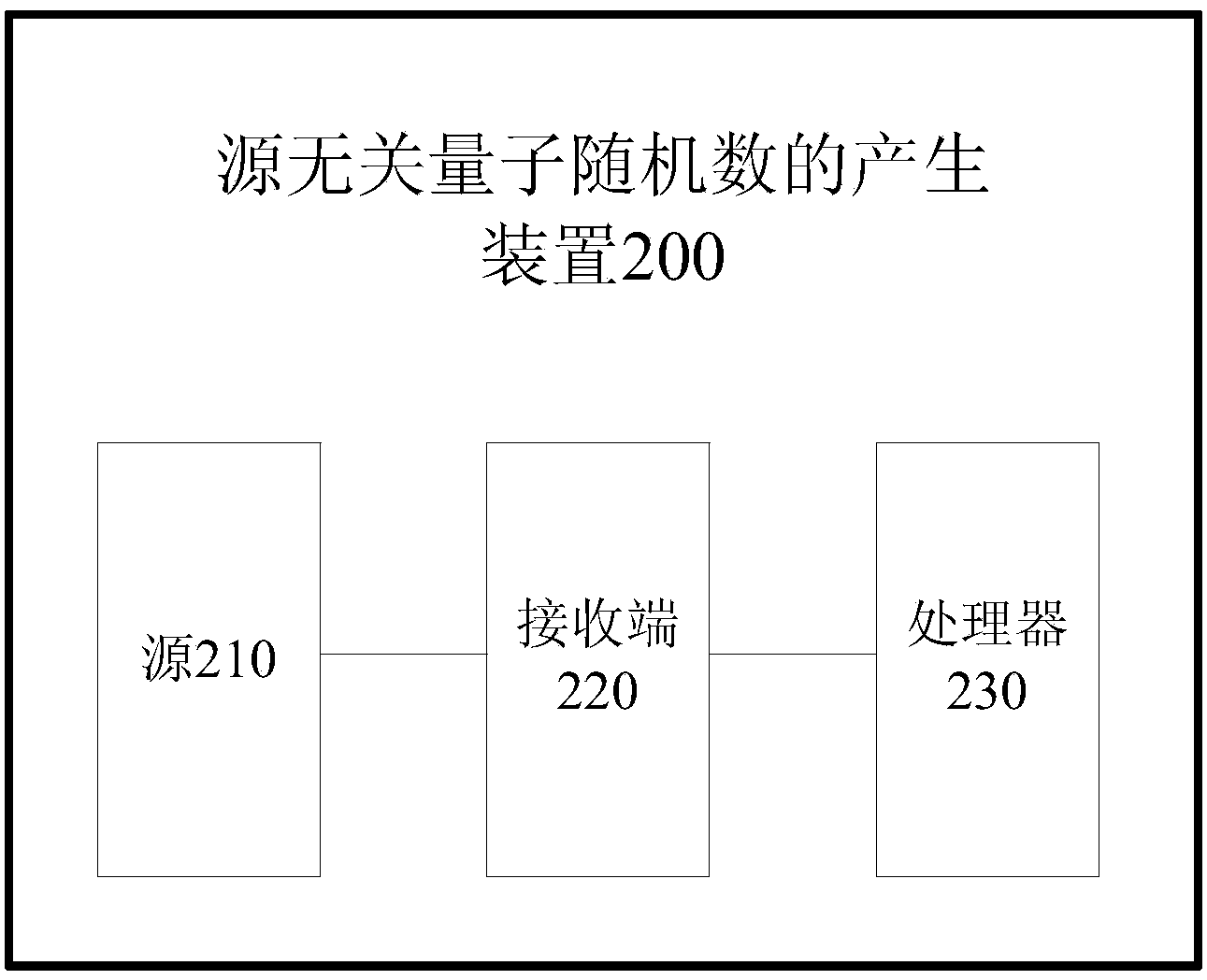
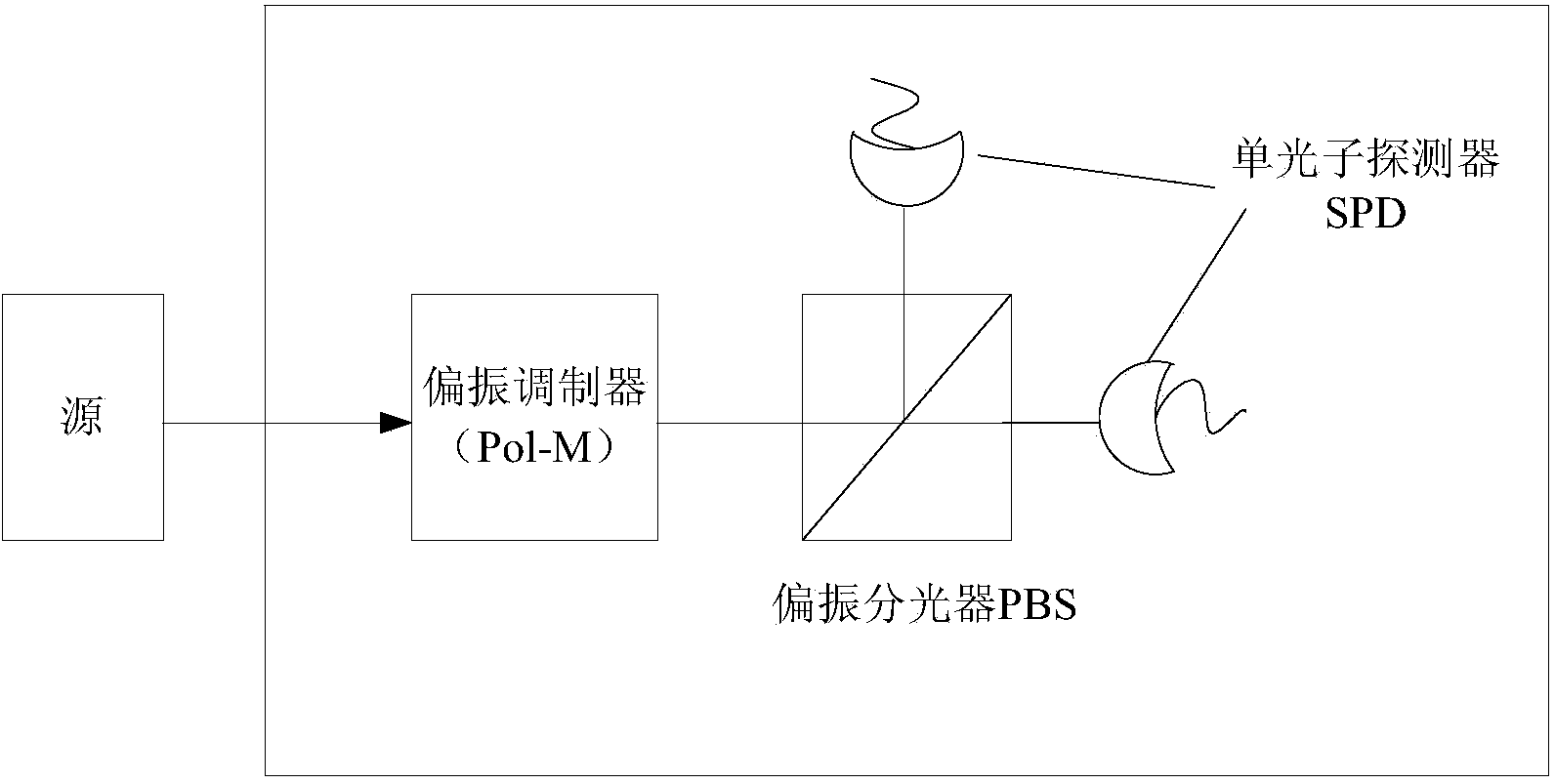
Source irrelevant quantum random number generation method and device
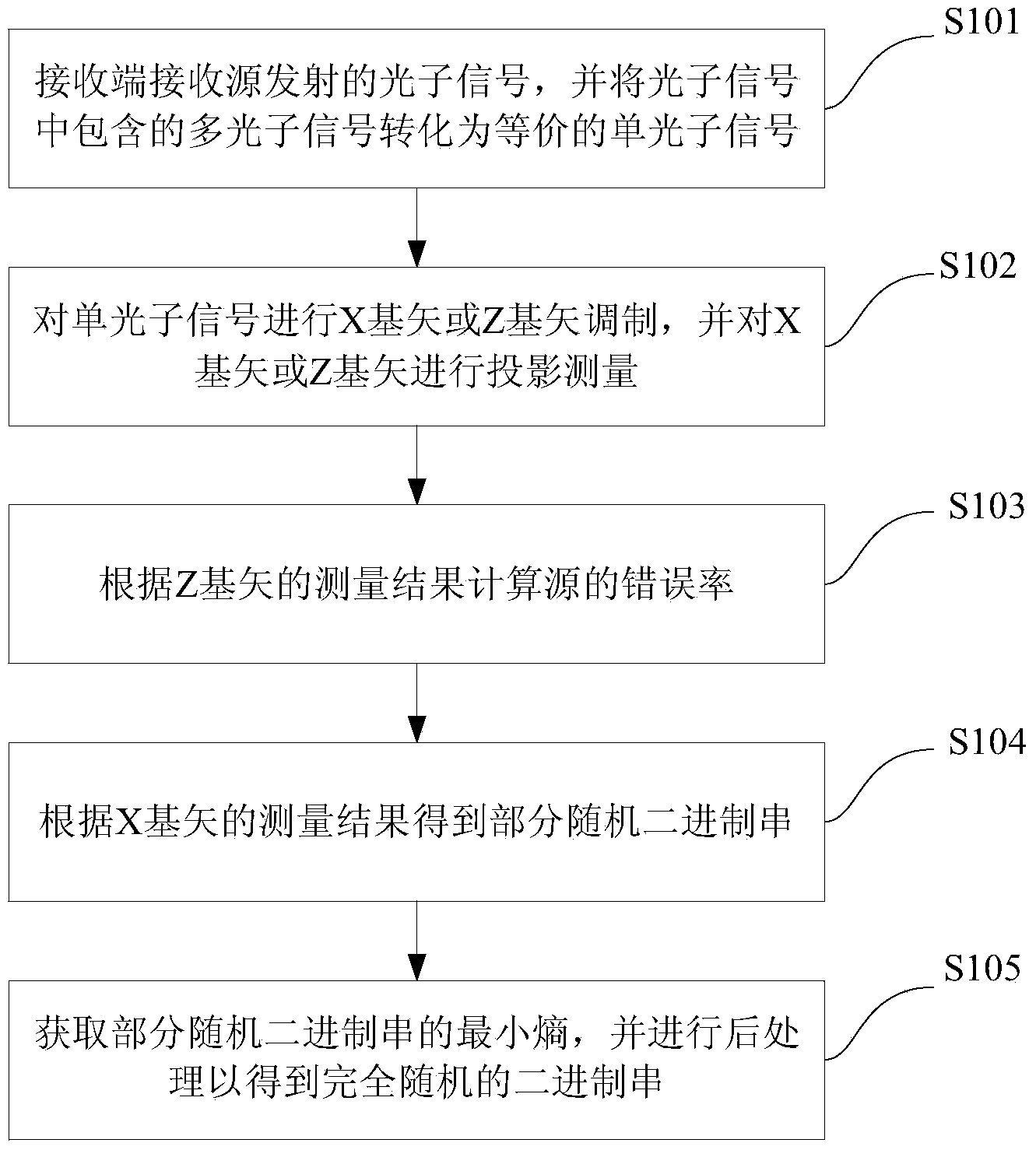
ActiveCN104238996AGuaranteed correctnessChannel loss toleranceRandom number generatorsMinimum entropyBinary strings
The invention provides a source irrelevant quantum random number generation method, which comprises the following steps: receiving a photon signal emitted via a source by a receiving end, and converting a multiphoton signal contained in the photon signal into an equivalent single-photon signal; carrying out X basis vector or Z basis vector modulation on the single-photon signal, and carrying out projection measurement on an X basis vector or Z basis vector; according to the measurement result of the Z basis vector, calculating an error rate; according to the measurement result of the X basis vector, obtaining parts of random binary string; obtaining the minimum entropy of the parts of random binary string, and carrying out aftertreatment to obtain a completely random binary string. The method disclosed by the invention does not need to depend on source hypothesis, a true random number guaranteed by quantum mechanics can be generated, and the method can tolerate high channel loss, and has high practical value. The invention also provides a source irrelevant quantum random number generation device.
Owner:TSINGHUA UNIV
Authority control method and system under micro-service architecture, and access token
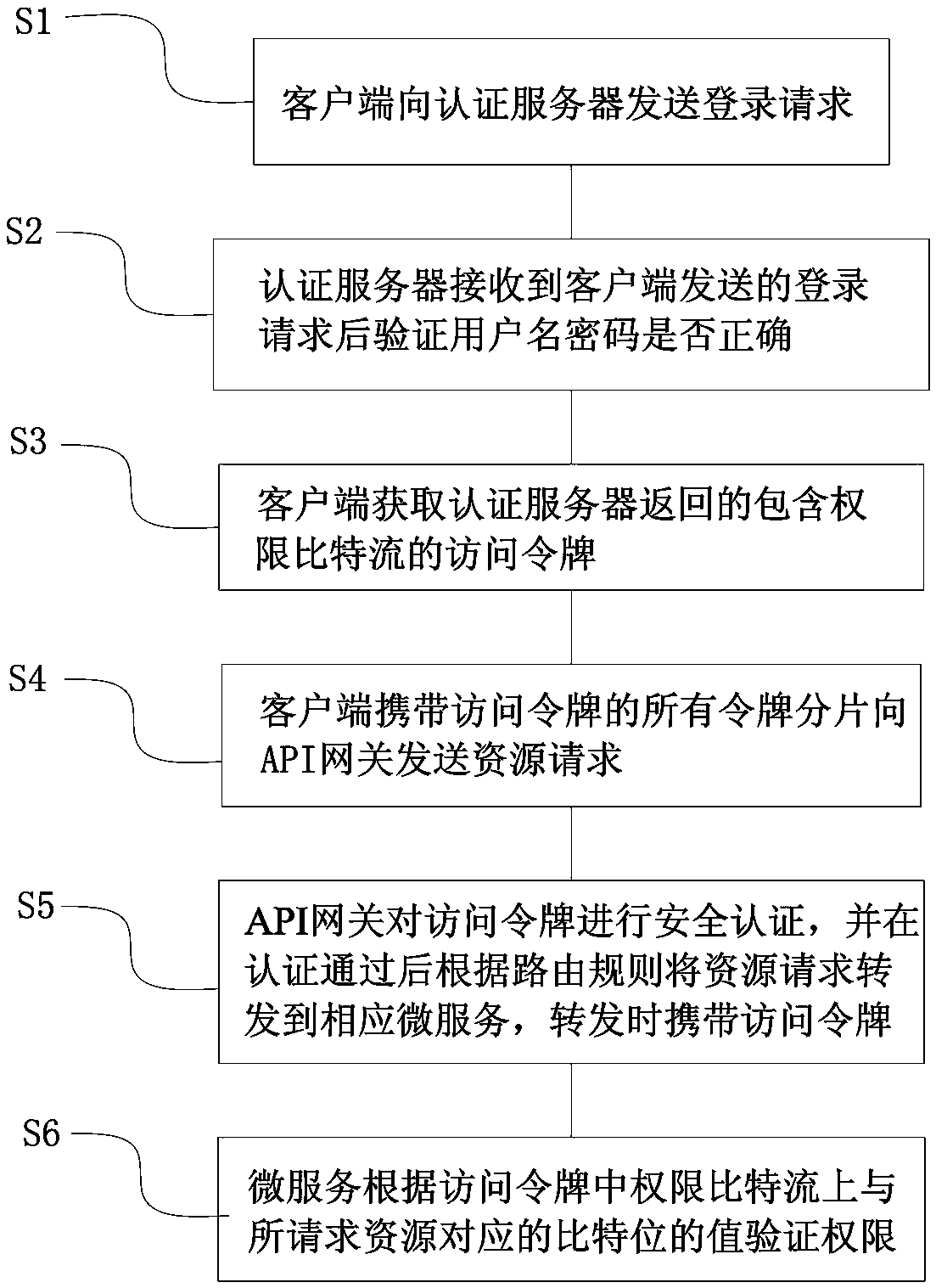
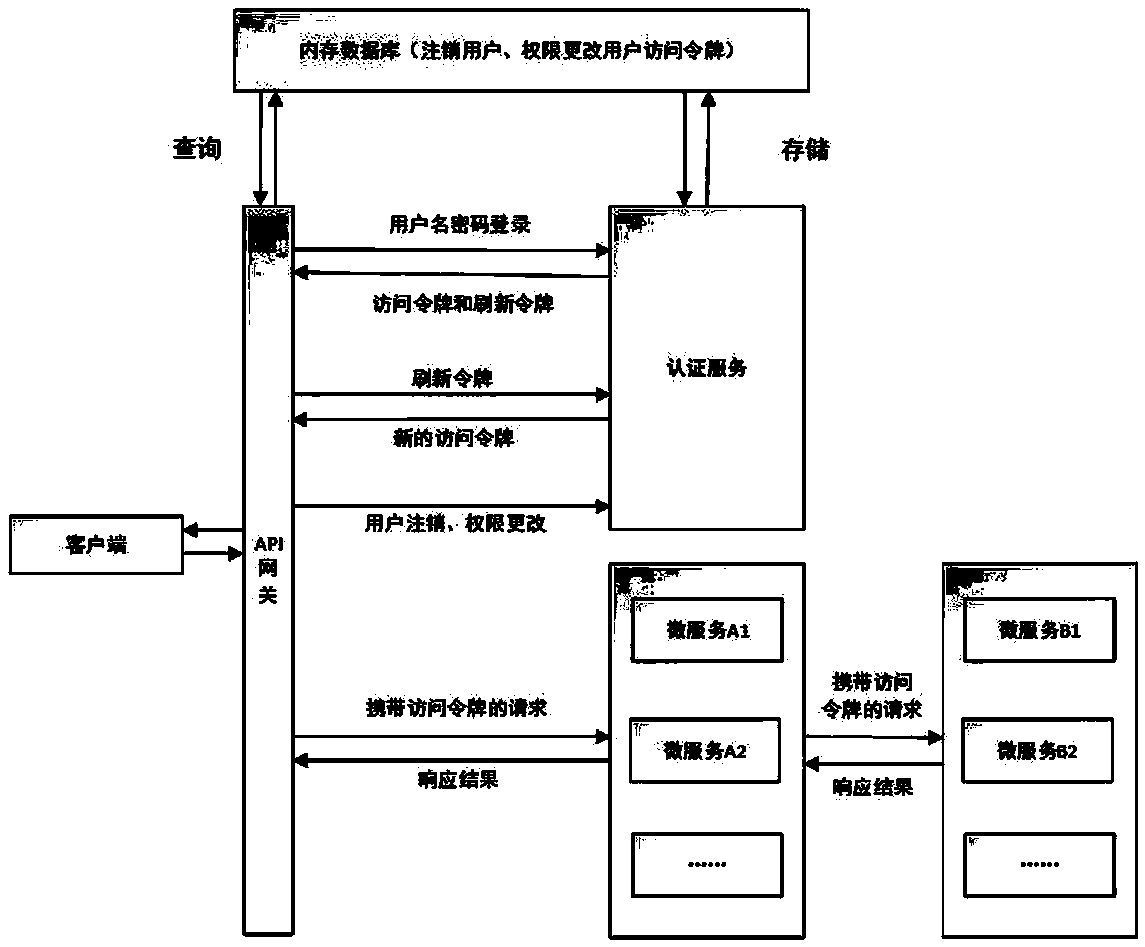
ActiveCN111030828ASimplify the calling linkSave time and costUser identity/authority verificationEngineeringAuthentication server
The invention relates to a permission control method and system under a micro-service architecture, and an access token, and aims to solve the problem of low efficiency caused by frequent request of authentication service by each resource service and frequent query of a database by the authentication service to obtain current user permission information in the micro-service architecture. Accordingto the technical scheme, the method comprises the steps that a client obtains an access token which is returned by an authentication server and contains an authority bit stream, wherein the authoritybit stream is a binary string with a fixed bit number, the bit number of the binary string is determined according to the number of system authorities, each bit in the binary string is in one-to-onecorrespondence with the authority in the system, and the value of each bit represents the state of the corresponding authority; a client carries the access token to send a resource request to the APIgateway; an API gateway carries out security authentication on the access token and forwards the resource request to the corresponding micro-service after the authentication is passed, and the accesstoken is carried during forwarding; and a micro-service verifies the permission according to the value of the bit corresponding to the requested resource on the permission bit stream in the access token.
Owner:POWERCHINA HUADONG ENG COPORATION LTD +1
Data compression system based on tree models
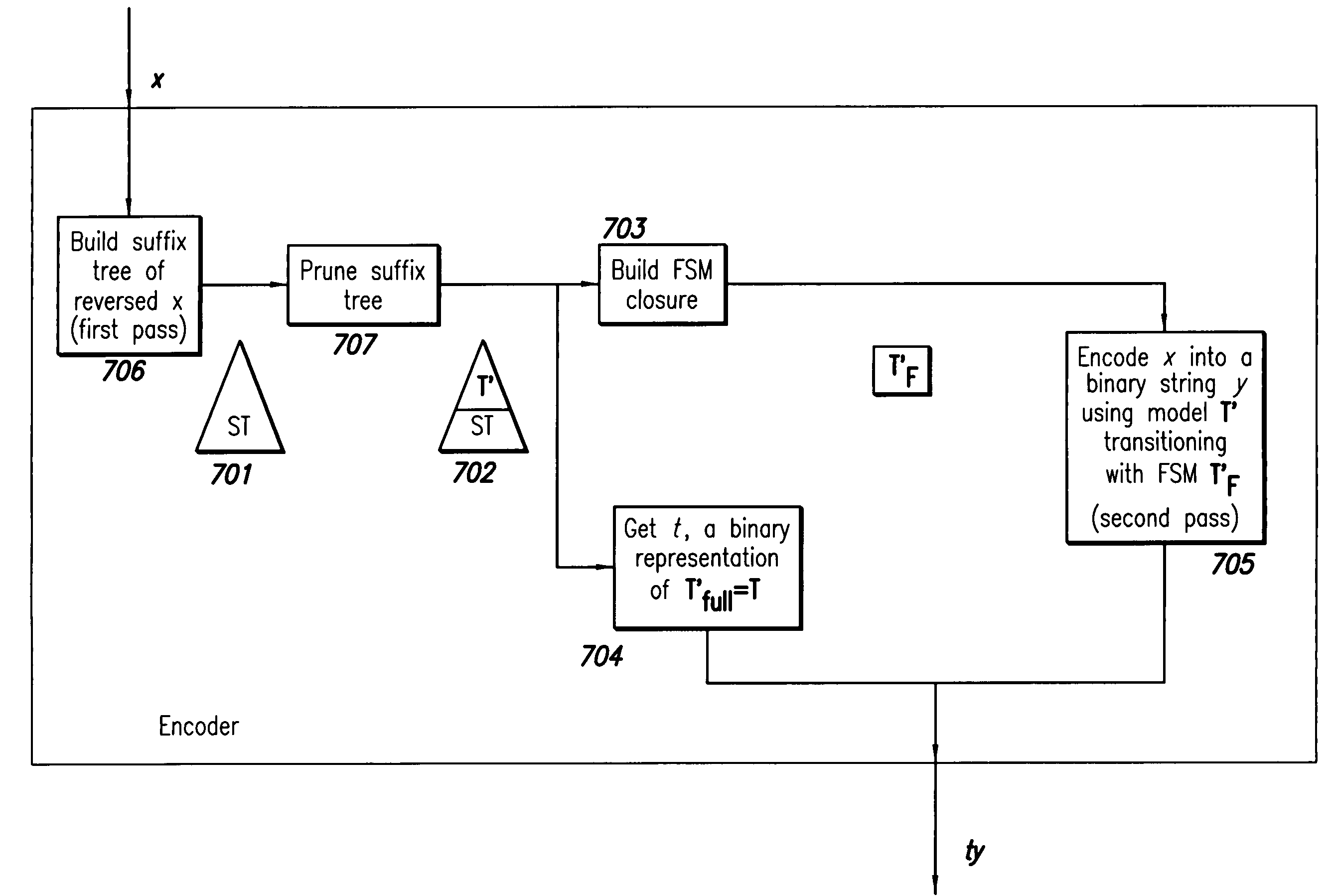
A method for encoding and decoding a sequence is provided. The method comprises searching a set of candidate trees varying in size for a tree T having a plurality of states. Tree T provides a structure that relatively minimizes code length of the sequence from among all the candidate trees. The method further comprises encoding data conditioned on the tree T, which may be a generalized context tree (GCT), using a sequential probability assignment conditioned on the states of the tree T. This encoding may use finite state machine (FSM) closure of the tree. Also provided are methods for decoding an encoded binary string when the encoded string includes a full tree or generalized context tree, as well as decoding an encoded string using incomplete FSM closure, incremental FSM, and suffix tree construction concepts.
Owner:HEWLETT PACKARD DEV CO LP
Method for error control in multilevel cells with configurable number of stored bits
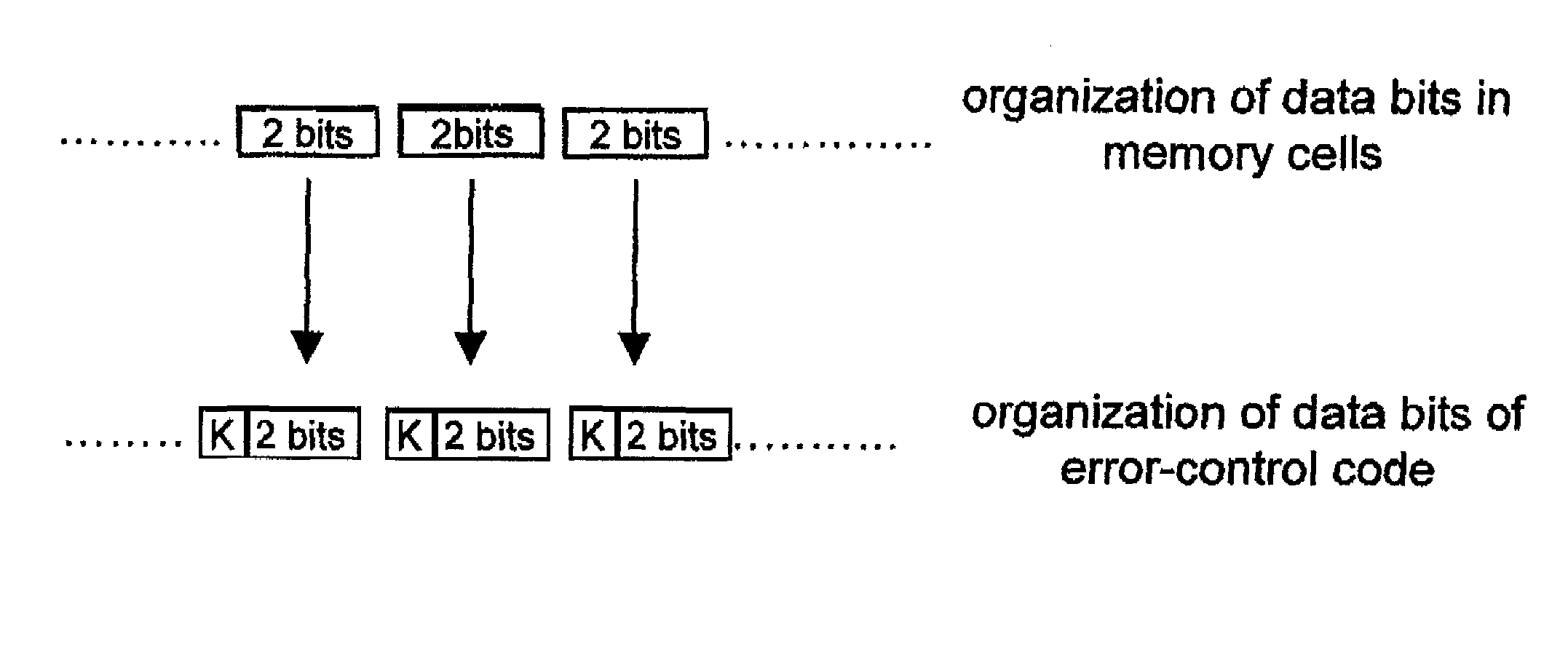
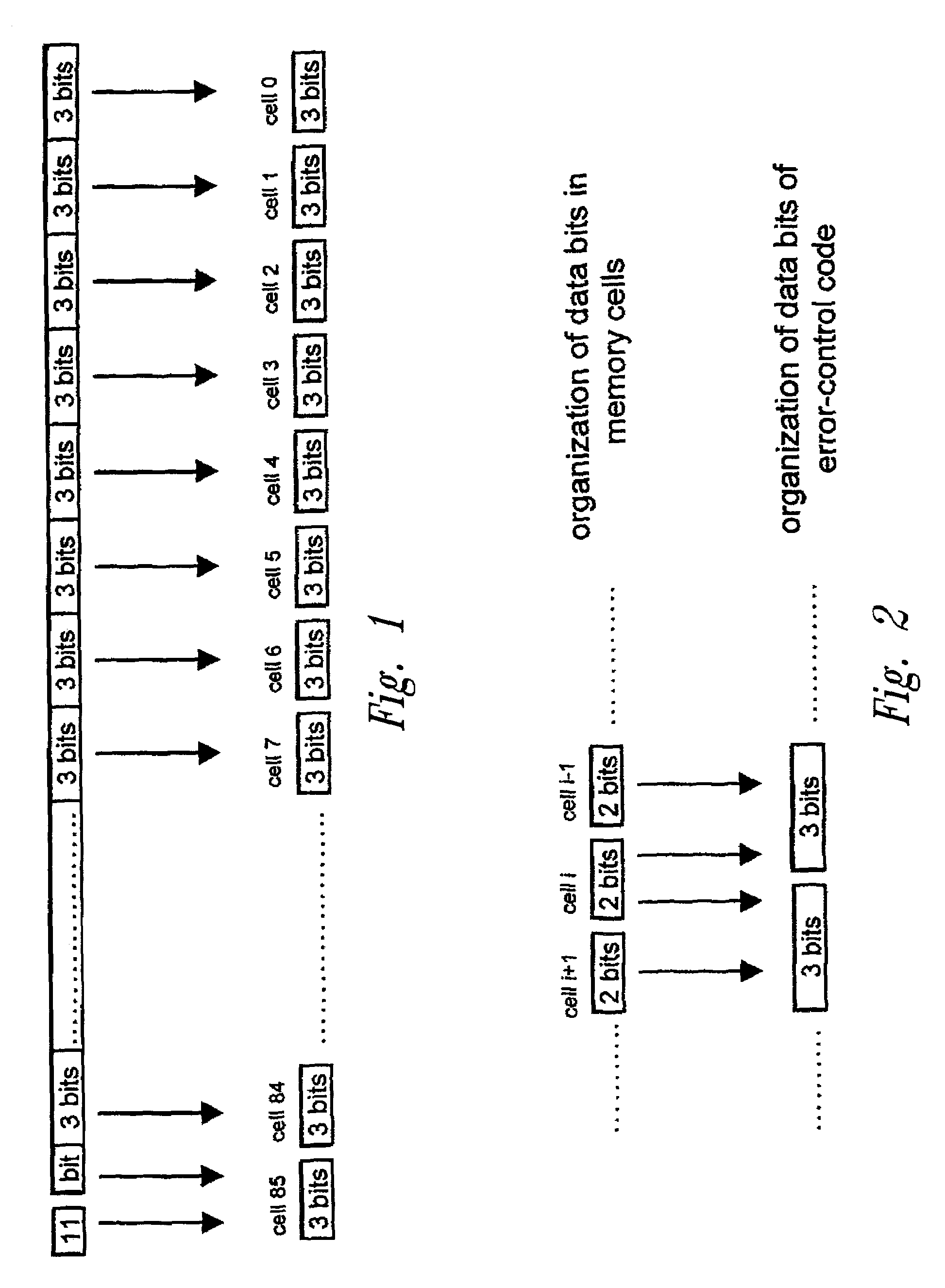
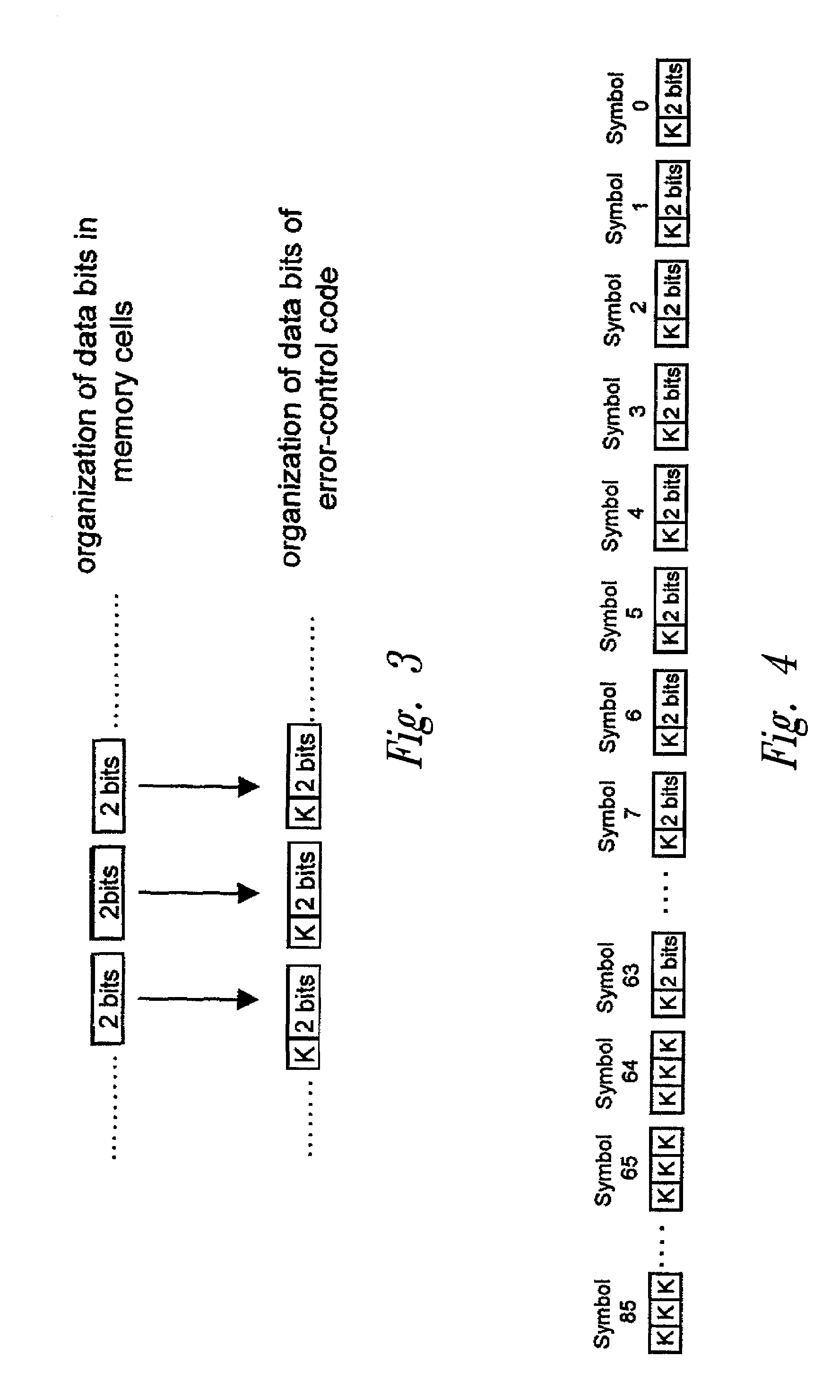
A method for error control in multilevel memory cells storing a configurable number of bits. The error control is performed using an error-control code which operates, in the encoding phase, on b-bit binary strings made up of k symbols of r-bit data. When the memory cells store a number r of bits, a data symbol is formed only with the data bits stored in a memory cell. When the memory cells store a number s of bits smaller than r, a data symbol is formed with the data bits stored in a memory cell and with r-s bits having a pre-determined logic value, in which the data bits stored in the memory cell are arranged in the least significant part of the data symbol, and the r-s bits having a pre-determined logic value are arranged in the most significant part of the data symbol.
Owner:MICRON TECH INC
Use and construction of time series interactions in a predictive model
InactiveUS20080154808A1Digital computer detailsElectric digital data processingData setTemporal logic
A gene is disclosed for use in a predictive genetic algorithm that performs time series interactions between dataset variables. The temporal logic that performs the interaction is encoded as a binary string.
Owner:EGAN MANAGED CAPITAL II
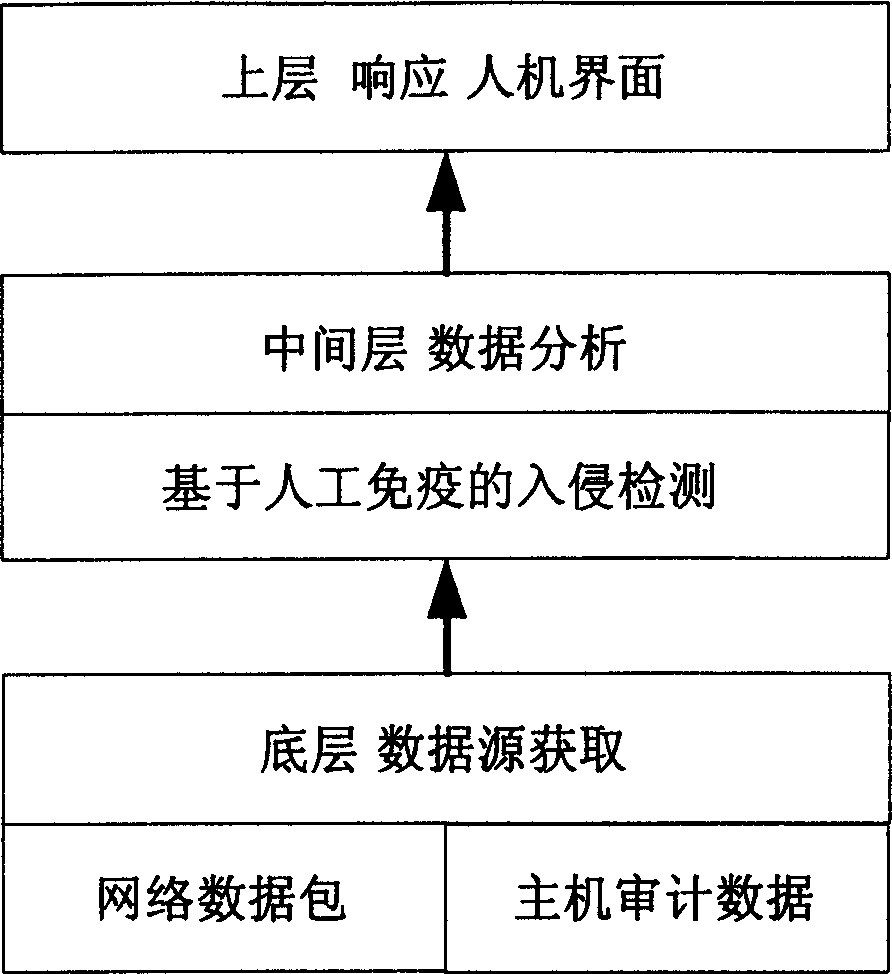
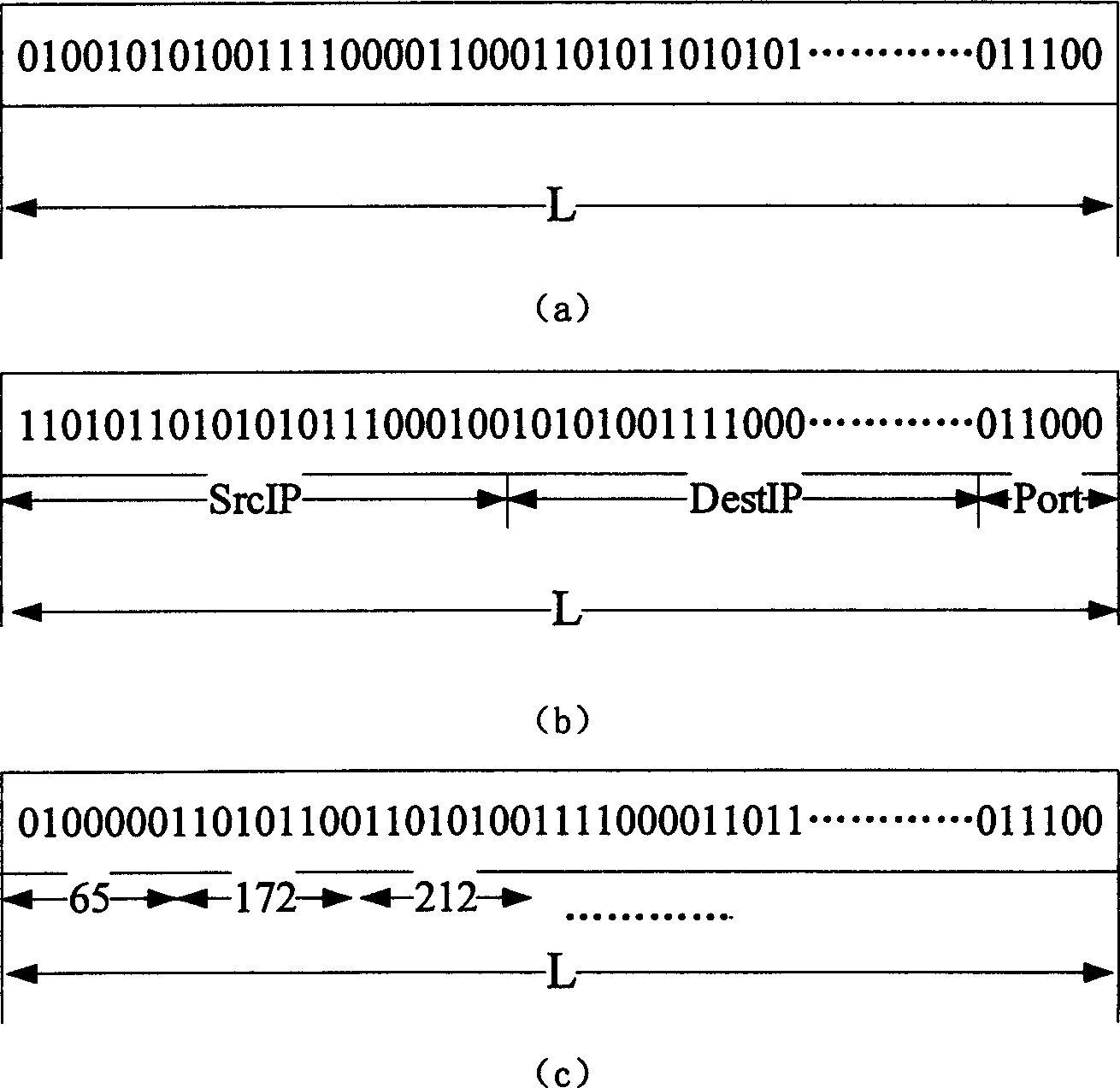
Analogue biological immunological mechanism invasion detecting method
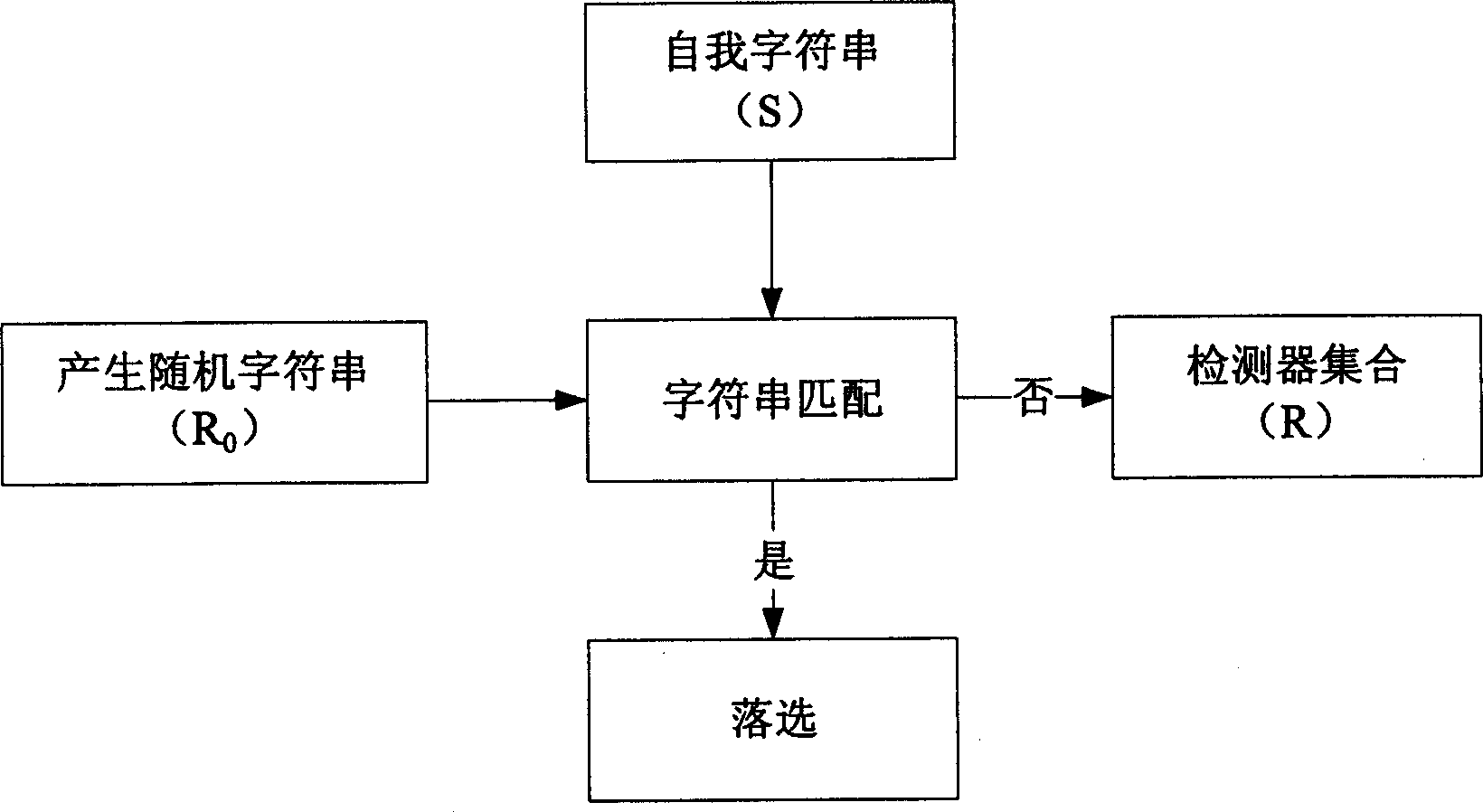
InactiveCN1777119AImprove featuresReduce time complexityData switching networksData acquisitionNetwork conditions
The invention is in use for intelligentized analyzing data source collected in intrusion detection system. The invention includes methods of anomaly detection under host condition and network condition. The method includes following steps: first obtaining data source to be detected including host audit data and data of network data packet, characters of which are formatted as binary element string character string in length L; then, based on data source under normal condition, set of tester is generated; finally, using the set of tester carries out anomaly detection for real data. Based on host audit data and data of network data packet, the invention implements overall process: data acquisition, feature extraction and intrusion detection. Features are: system in distributed, lightweight level, and having fine characteristics of biological immune system: self-organization, diversity and self-adapting.
Owner:NANJING UNIV OF POSTS & TELECOMM
Encrypted domain H.264/AVC video data hiding method based on CABAC binary string mapping
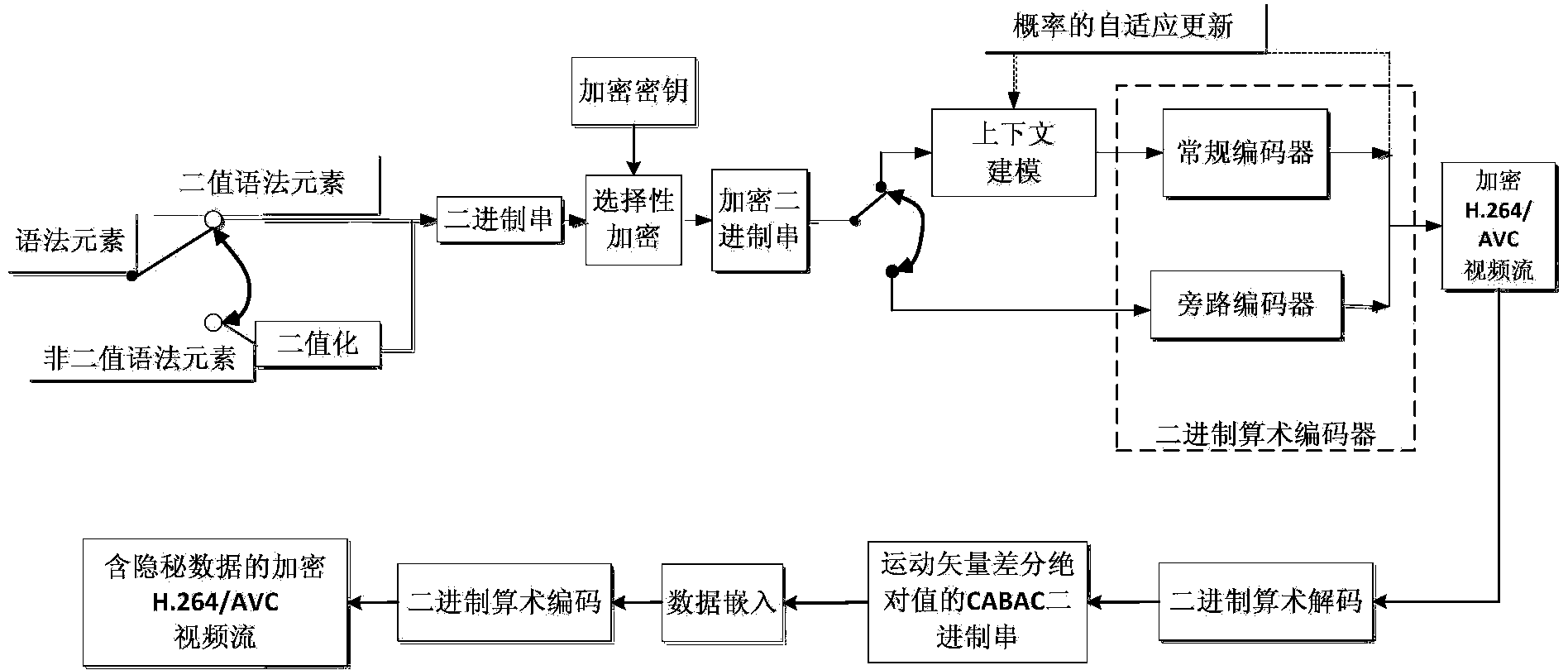
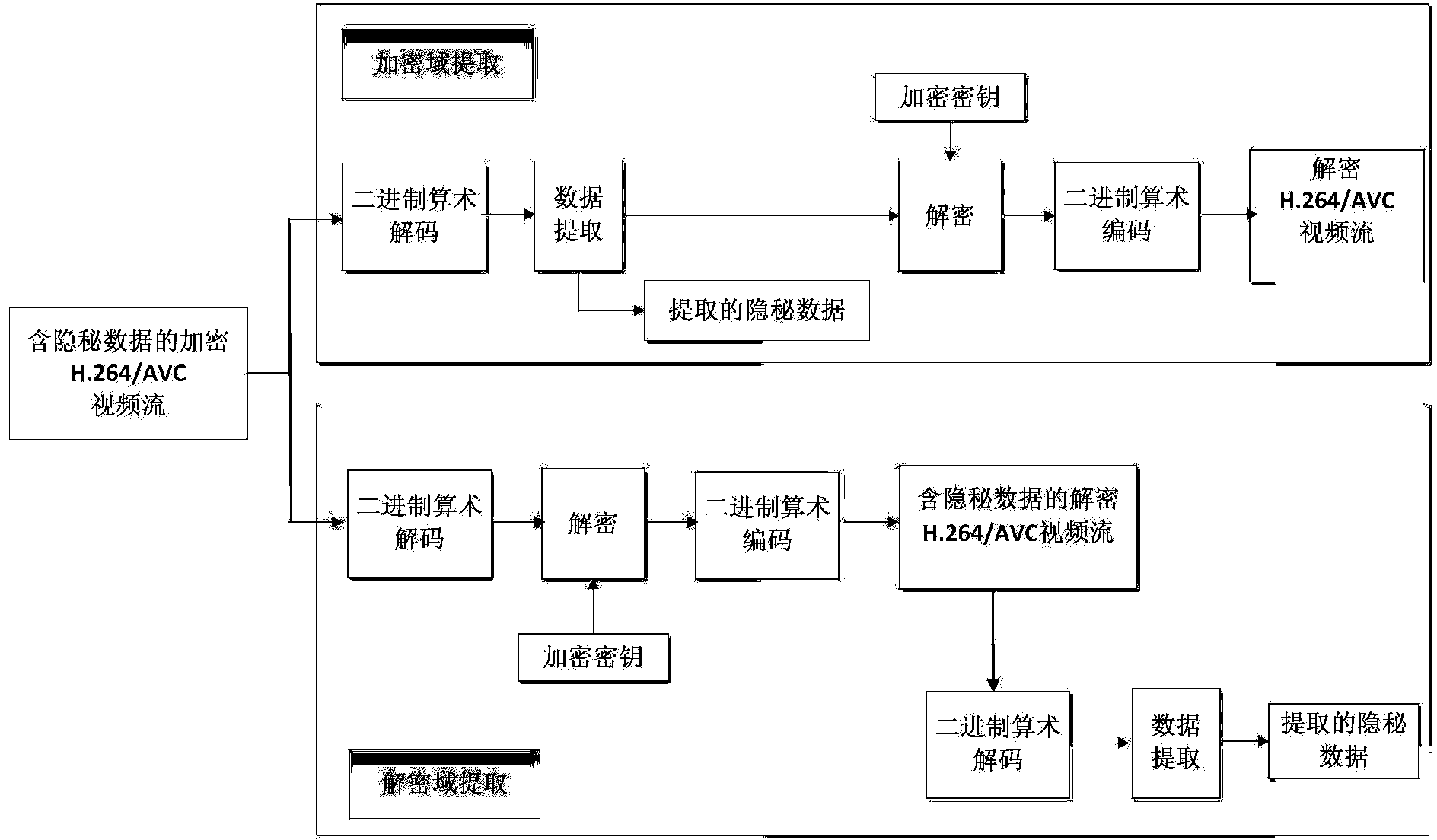
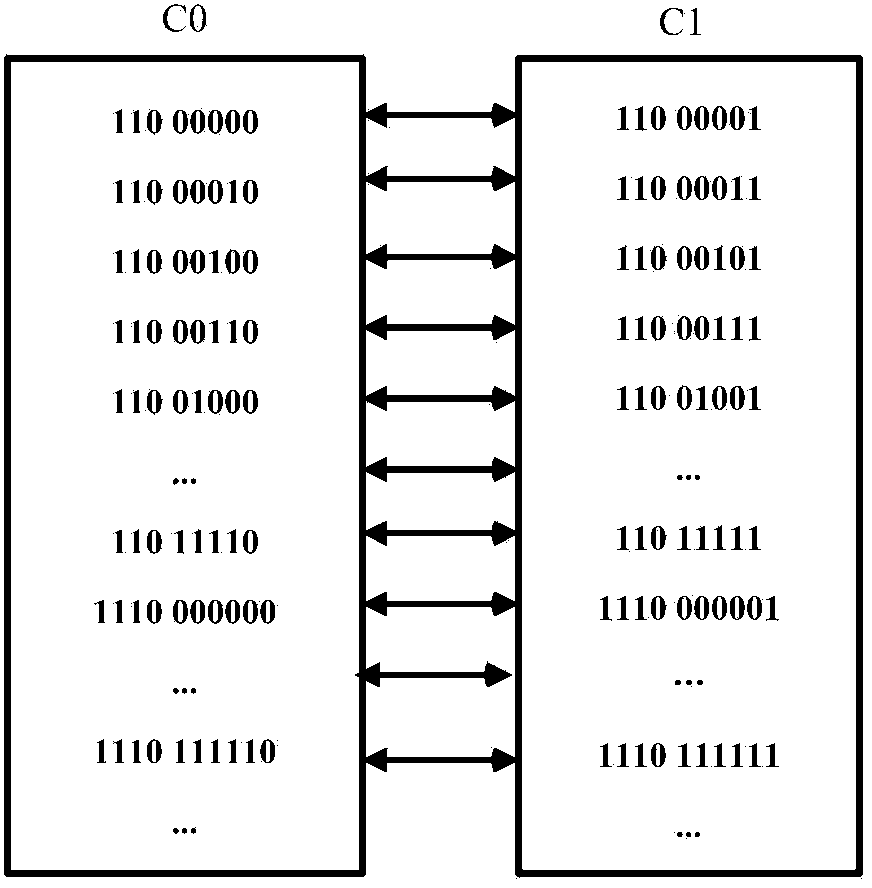
ActiveCN104038761ASolve the problem of data expansionFix security issuesDigital video signal modificationComputer hardwareMotion vector
The invention discloses an encrypted domain H.264 / AVC video data hiding method based on CABAC binary string mapping. The encrypted domain H.264 / AVC video data hiding method based on the CABAC binary string mapping includes H.264 / AVC video encryption, encrypted domain H.264 / AVC video data hiding and hidden data extracting, to be specific, using syntax elements of a bypass coding mode in a CABAC to carry out equal-length binary string substitution to encrypt a video, hiding data through a CABAC binary string mapping method for an absolute value of a motion vector difference, wherein both the encryption and data hiding do not change the code rate of a H.264 / AVC video streaming. Both the encryption and the data hiding are finished under CABAC entropy coding and are completely compatible with the CABAC entropy coding, and the encrypted video streaming with hidden data can be decoded through a standard H.264 / AVC video decoder; a person who hides the data can directly embed secrete information in the H.264 / AVC video, even if the person who hides the data does not know the original video content, the person can effectively guarantee the video content safety and avoid the privacy disclosure problem; and in addition, the encrypted domain H.264 / AVC video data hiding method based on the CABAC binary string mapping can effectively extract the hidden data from the encrypted domain and decryption domain.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
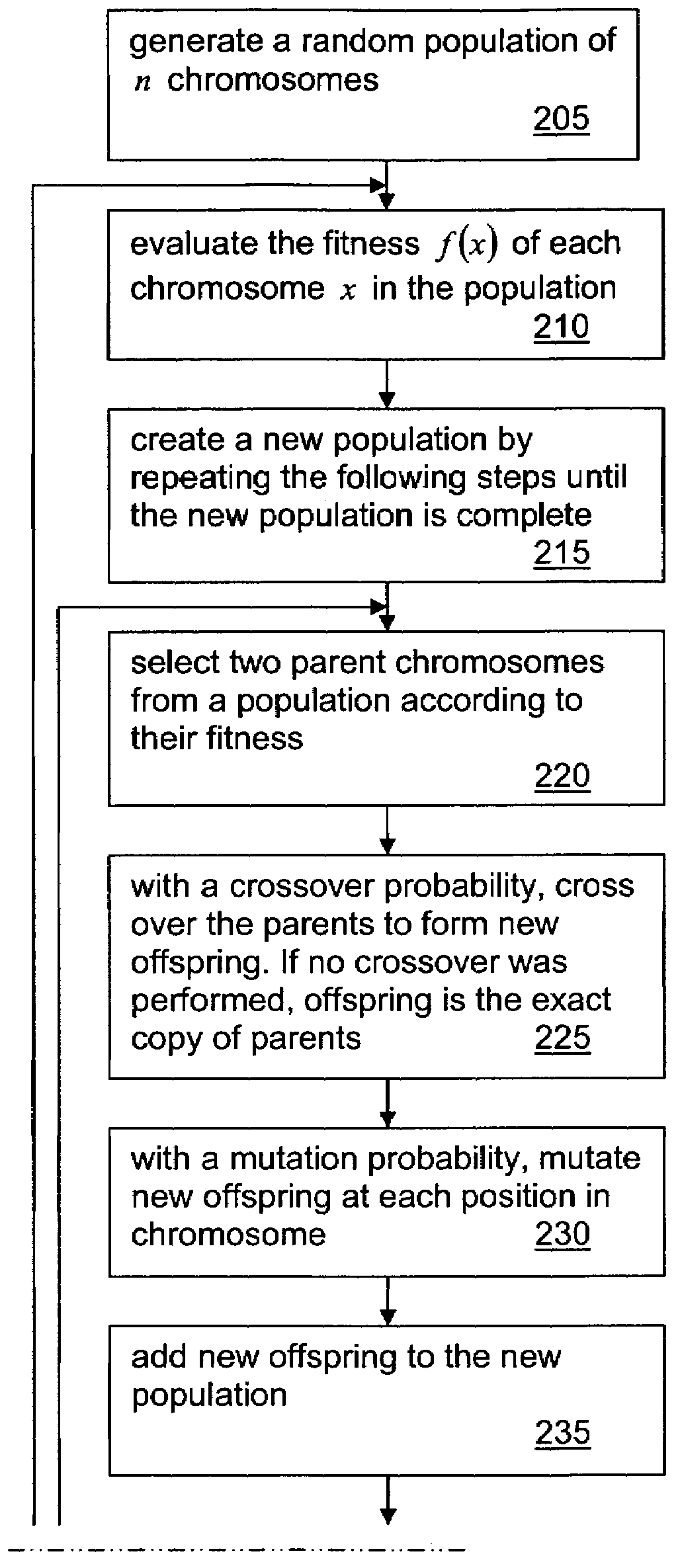
Genetic algorithm-based classification algorithm parameter optimization method
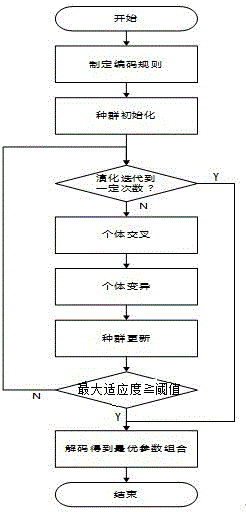
InactiveCN104572993AEfficient combinationSpecial data processing applicationsGenetic algorithmsGenetic algorithmDiscretization
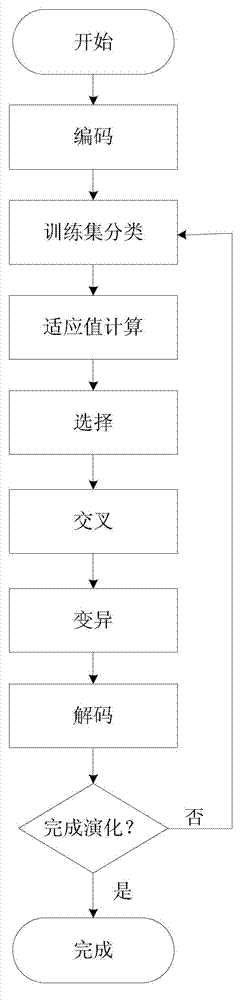
The invention discloses a genetic algorithm-based classification algorithm parameter optimization method, and belongs to the field of algorithm parameter optimization. The method comprises the following specific steps: (1) making a coding and decoding rule; (2) performing population initialization; (3) performing cyclical iteration; (4) decoding to obtain an optimal parameter. Aiming at the parameter optimization problem of a classification algorithm, all parameters are discretized according to numerical values and sequentially connected into a binary coding sequence, each individual corresponds to a binary string, each performance indicator value weight of the classification algorithm is used as fitness, the fitness is used as a standard for judging the quality of the individual to maintain a group, and the finally obtained group is coded to obtain a corresponding parameter value and further obtain an optimal parameter combination; the method is suitable for various classification algorithms for parameter constraint of the parameter sensitivity.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Secret key generation method based on multi-modal biological characteristics
InactiveCN104168112AMeet the needs of obtaining encrypted dataKey distribution for secure communicationUser identity/authority verificationFeature vectorBiometric data
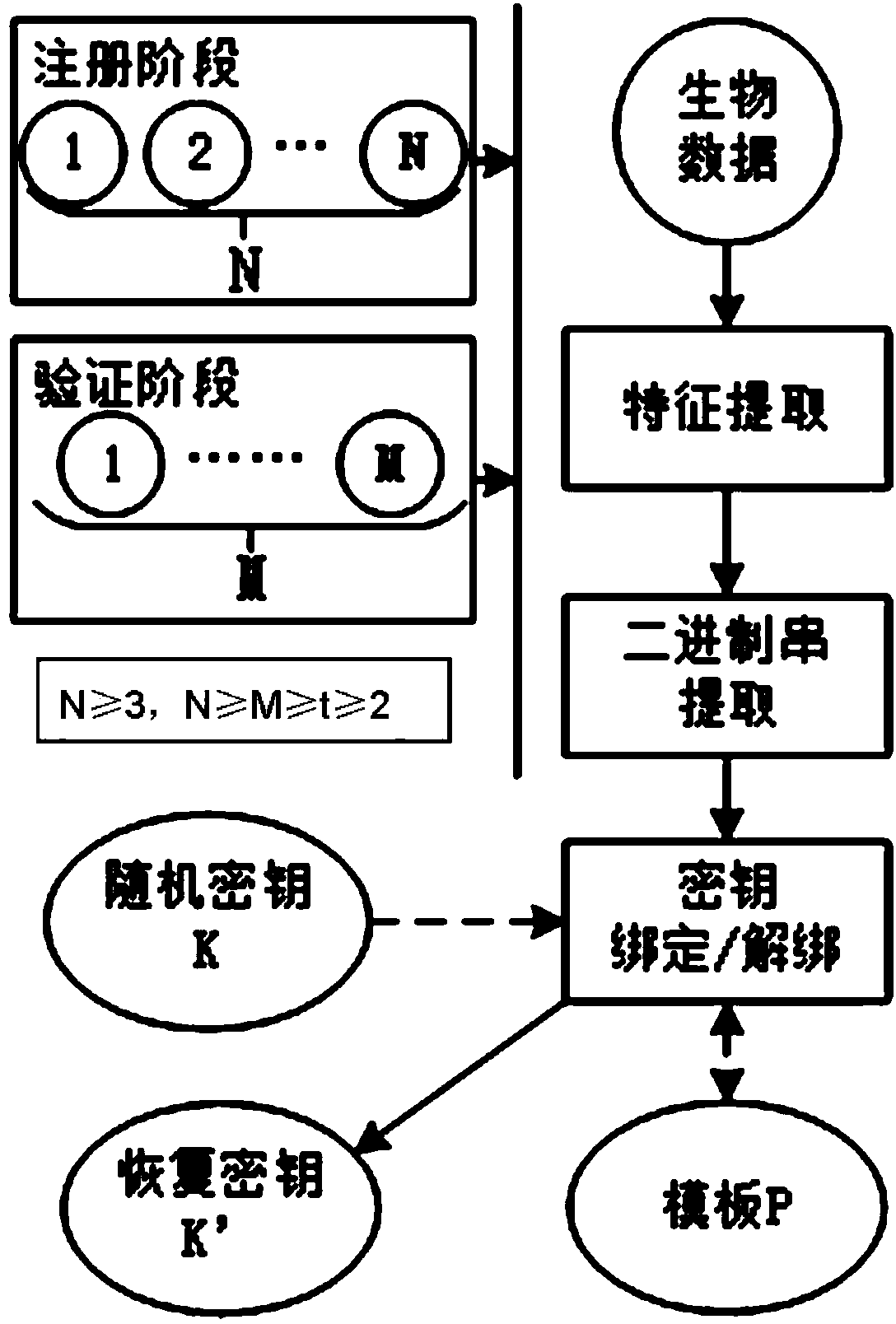
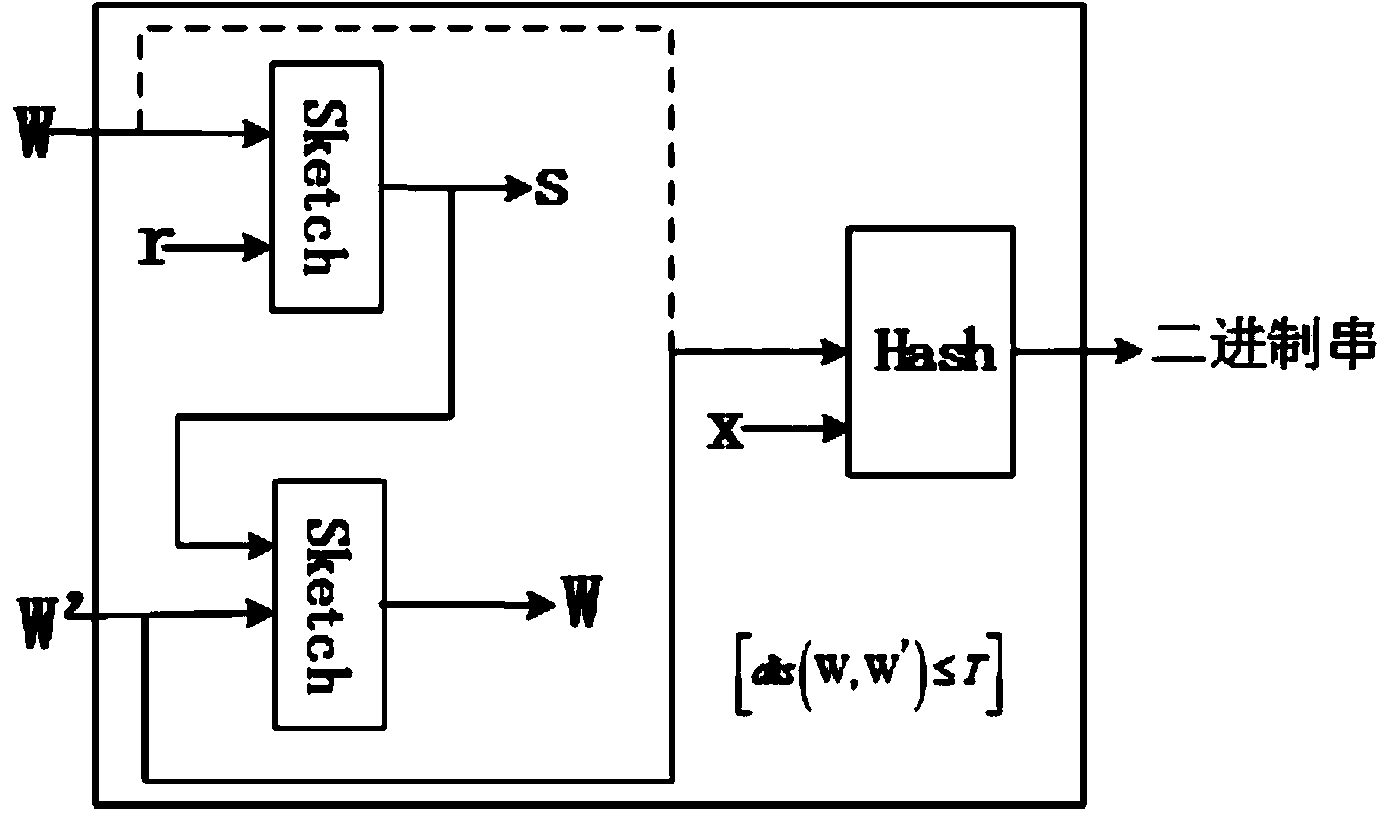
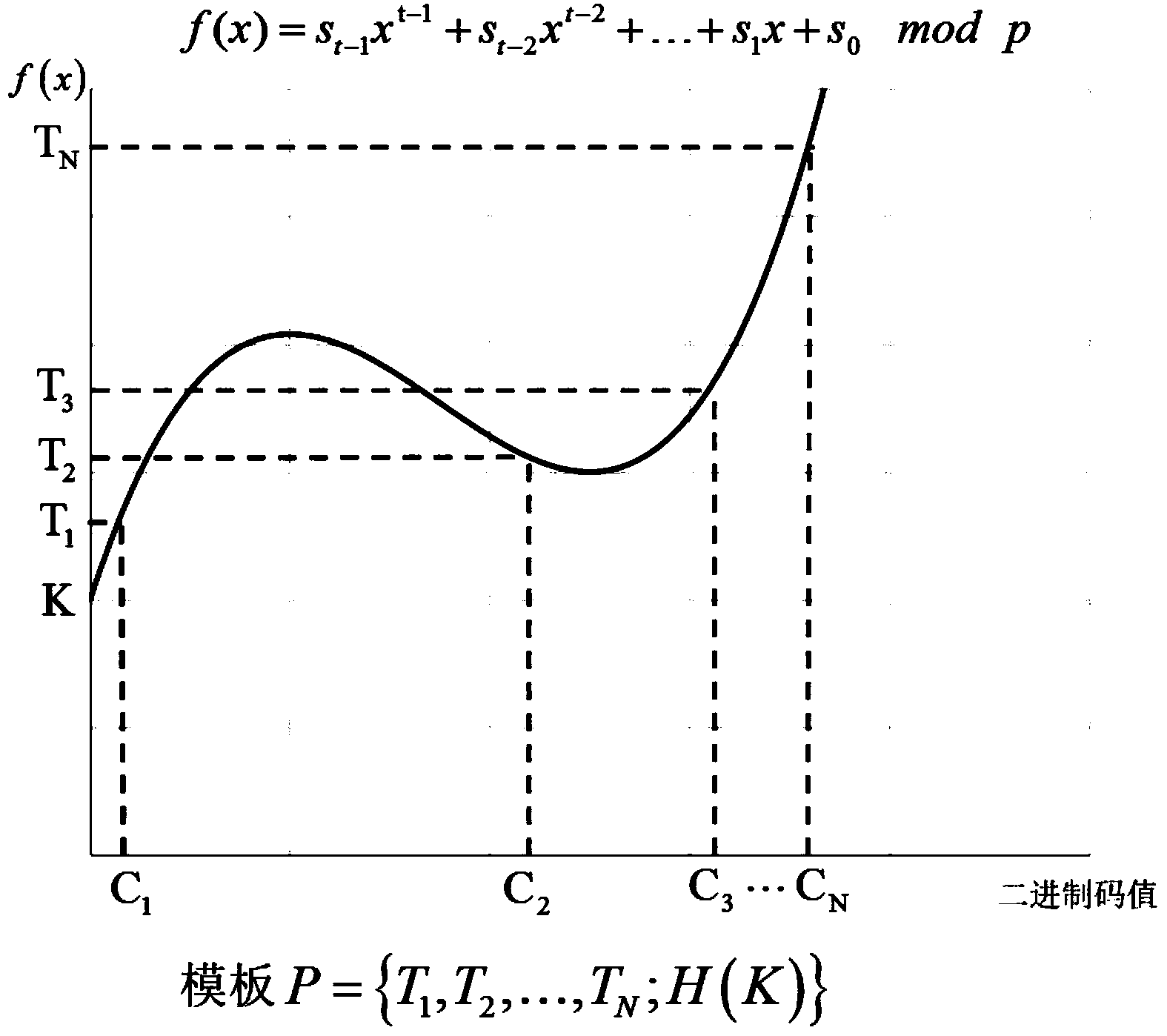
The invention discloses a secret key generation method based on multi-modal biological characteristics, comprising (1) collecting characteristic images of N species of biology, extracting and quantifying the biological characteristic data as characteristic vector, (2) processing the characteristic vector and extracting the binary string to present the characteristic of the creature, (3) generating a random secret key, binding and outputting a public template P by utilizing a Shamir secret sharing method with the binary string collection, (4) sampling M creature characteristics and obtaining a binary string collection, wherein n>-M>=t>=2, and the t is a threshold value of the Shamir method, 5) inputting the binary string collection and the template P into the Shamir secret sharing method to recovery a secret key K', (6)and comparing the K and K'. The invention can improve the recognition rate and reduce the false rejection rate, can produce secret key with higher entropy, and can finish the user authentification while recovering the secret key by binding the user identity and the secret key.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
System and method of reference position determination
A method of reference position determination for a DGNSS base station. The base station comprises a memory, a logic controller and a GNSS receiver. Stored reference positions are stored in the memory as coordinate sets comprising components. The GNSS receiver determines a current estimate position of the base station as a coordinate set comprising components. The logic controller retrieves a stored reference position, converts the components of the stored reference position and the current estimate position to binary string format. The current estimate position is matched to the stored reference position by matching the binary string format components of the current estimate position with the binary string format components of the stored reference position. If the stored reference position is matched to the current estimate position, the base station is assigned the stored reference position as its reference position.
Owner:LEICA GEOSYSTEMS AG
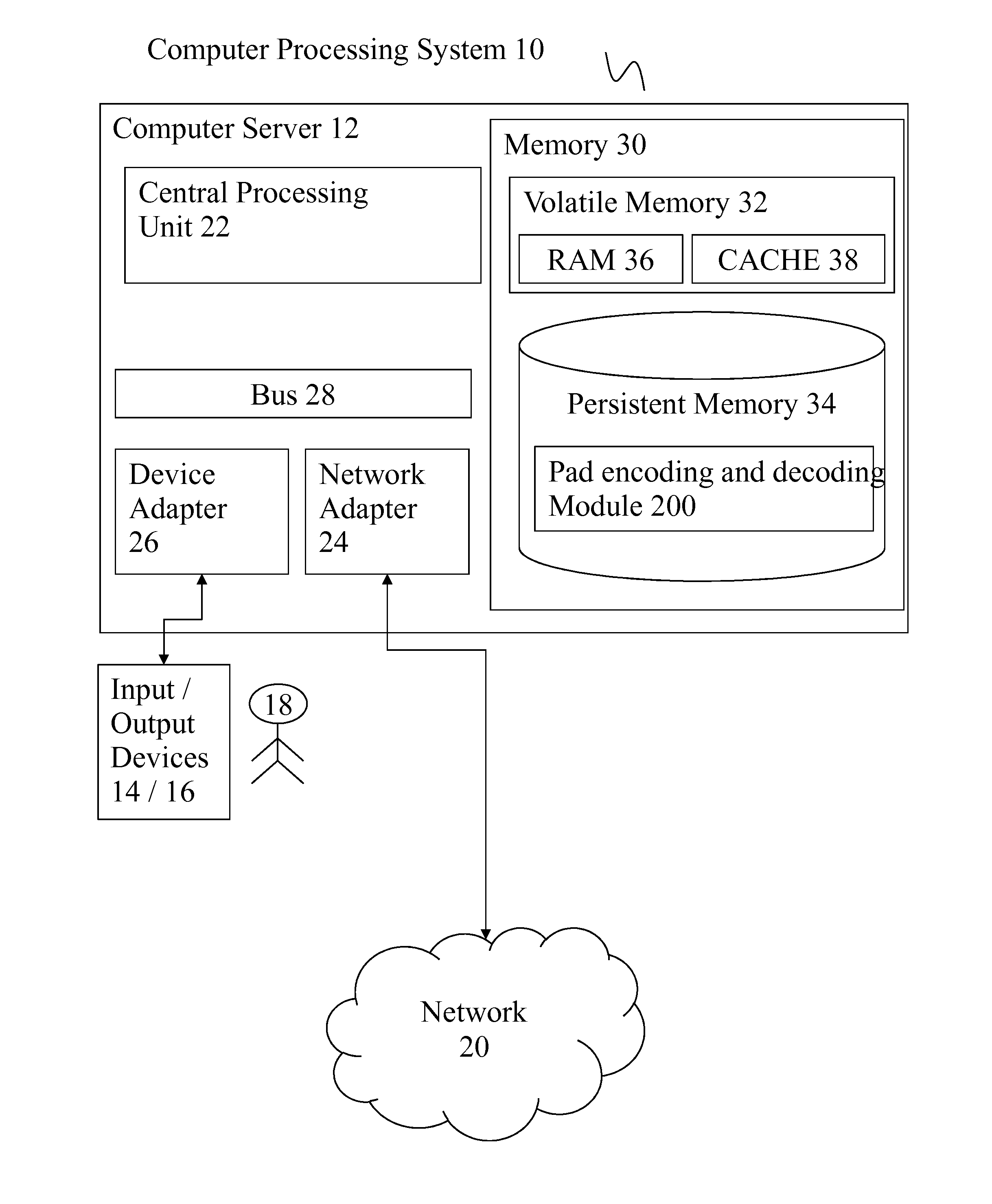
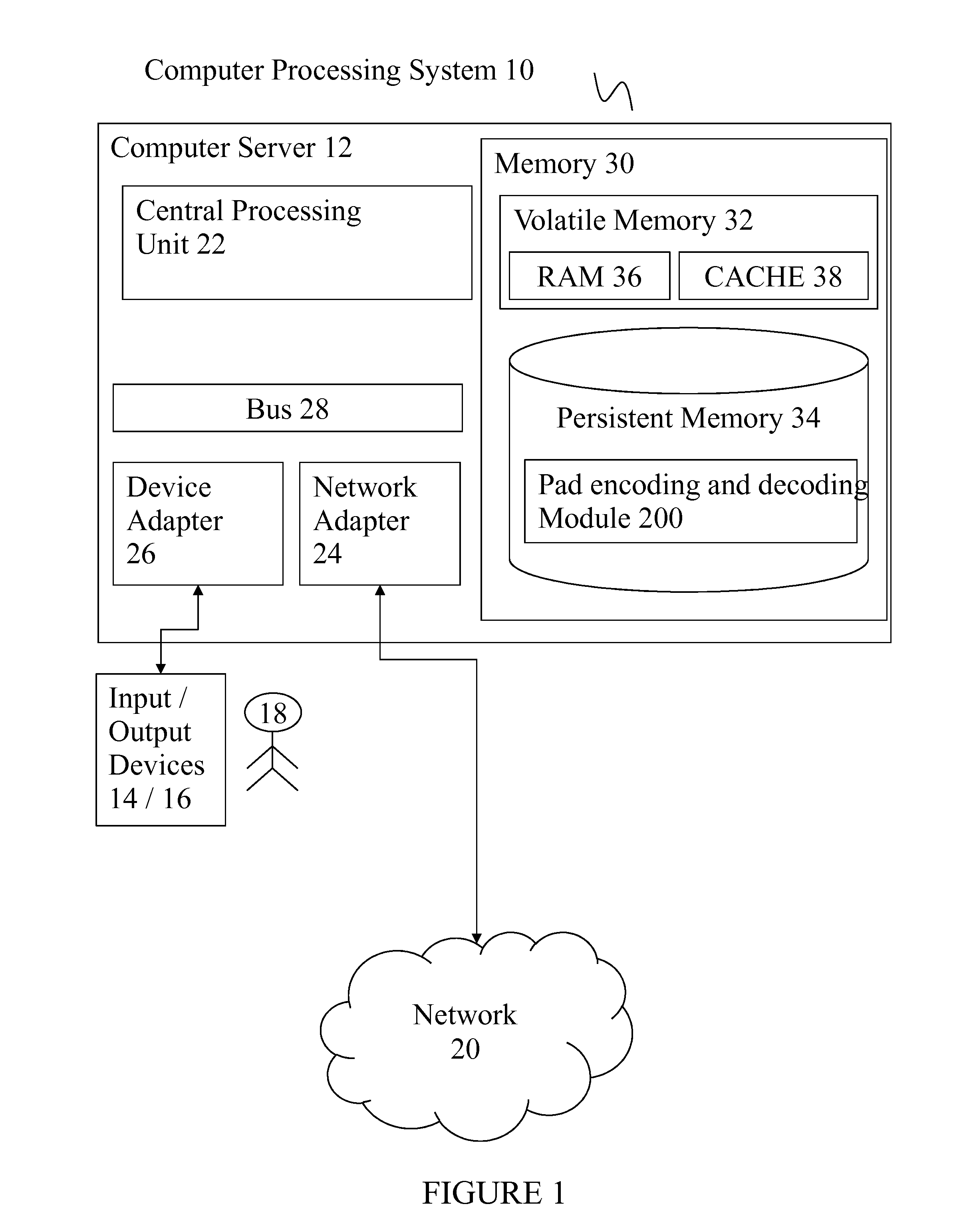
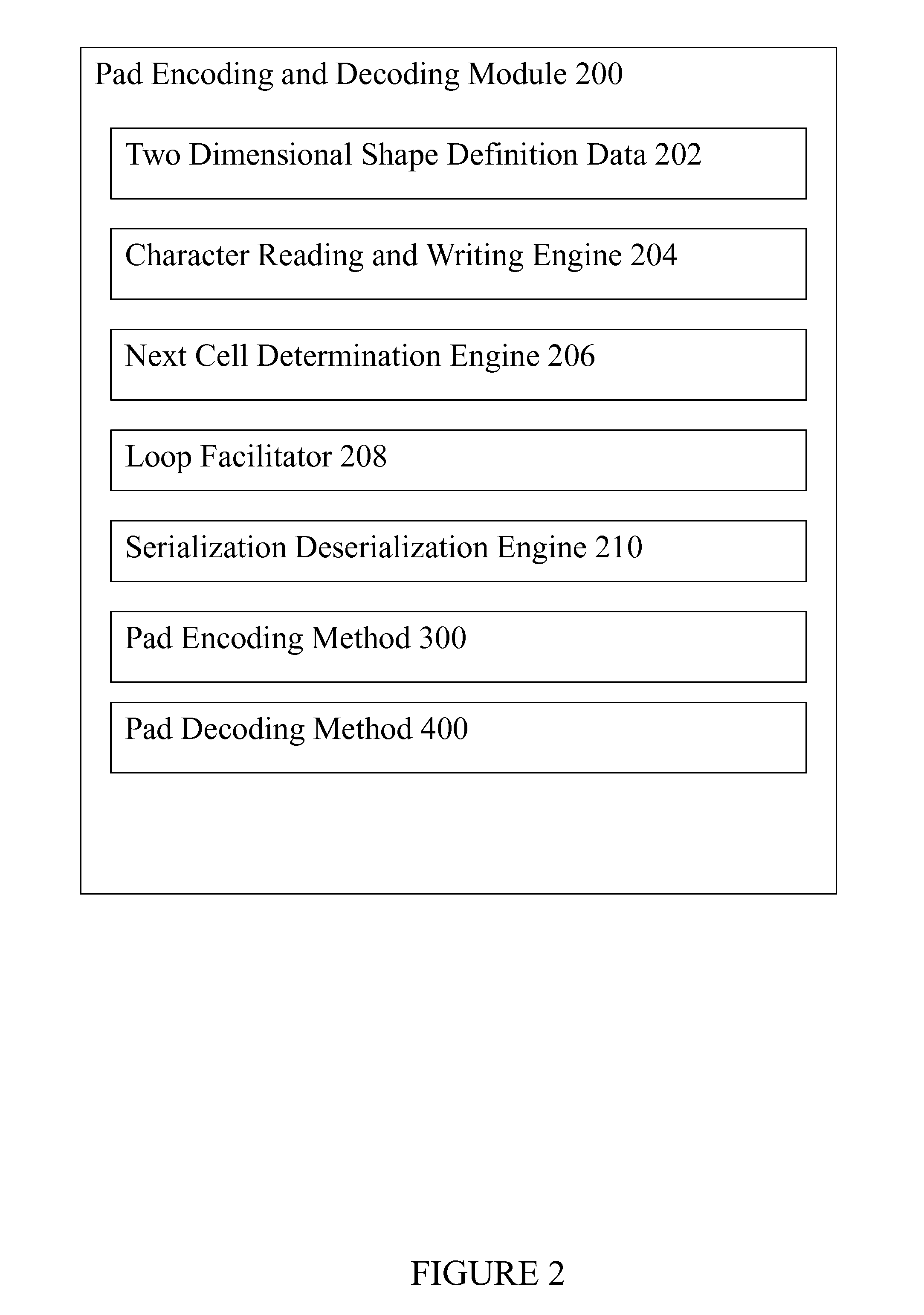
Pad encoding and decoding
ActiveUS9350382B1Key distribution for secure communicationMultiple keys/algorithms usageTheoretical computer scienceSerialization
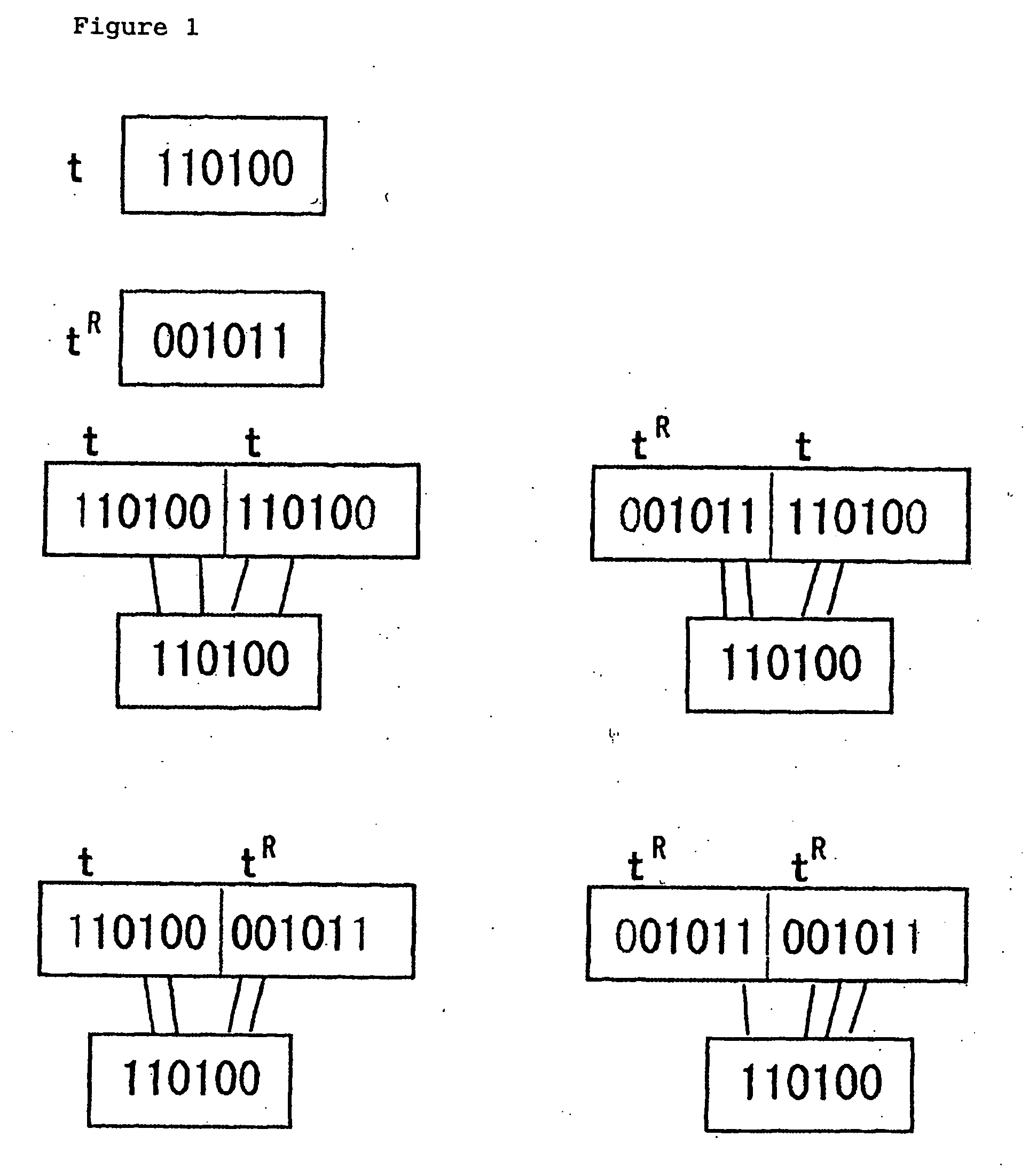
A system, method and computer program product for encoding an input string of binary characters representing alphanumeric characters. A system includes: a register for storing a two dimensional cellular shape definition including a starting empty cell; a character writing engine for writing a binary character to an empty cell with a predefined initial position; a next cell determination engine for determining a next empty cell by methodically traversing neighboring cells in the two dimensional shape until an empty cell is located; a loop facilitator for looping back to the character writing engine and the next cell determining engine until there are no more data characters or a next empty cell is not determined; and a serialization engine for methodically serializing the two dimensional cells into a one dimensional binary string of characters representing an encoded string of alphanumeric characters.
Owner:IBM CORP
Parallel evolution super-network DNA micro array gene data sorting system and method based on GPU
ActiveCN103258147AImprove diagnostic accuracyClassification result stabilitySpecial data processing applicationsInformation processingDNA microarray
The invention provides a parallel evolution super-network DNA micro array gene data sorting system and method based on a GPU and relates to the technical field of intelligent information processing. After preprocessing on DNA micro array data is carried out, a processed binary string is used as input information of a super-network, the super-network is initialized on a CUP of a host computer, the initialized super-network is transferred to the GPU, a hyperedge bank is divided into a plurality of sets of hyperedges, evolution studies based on a genetic algorithm are executed in parallel on the GPU respectively to acquire priori knowledge, the best hyperedge with decision-making ability is searched, and the super-network after evolution carries out classification on input samples by utilizing the hyperedges together. According to the parallel evolution super-network DNA micro array gene data sorting system and method based on the GPU, super-network parallel evolution studies based on the genetic algorithm are achieved on the GPU, study time and recognition time are short, and system execution efficiency is high. The super-network can classify the samples by utilizing a plurality of singles with the decision-making ability together, and therefore system recognition rates and generalization ability are high.
Owner:博拉网络股份有限公司
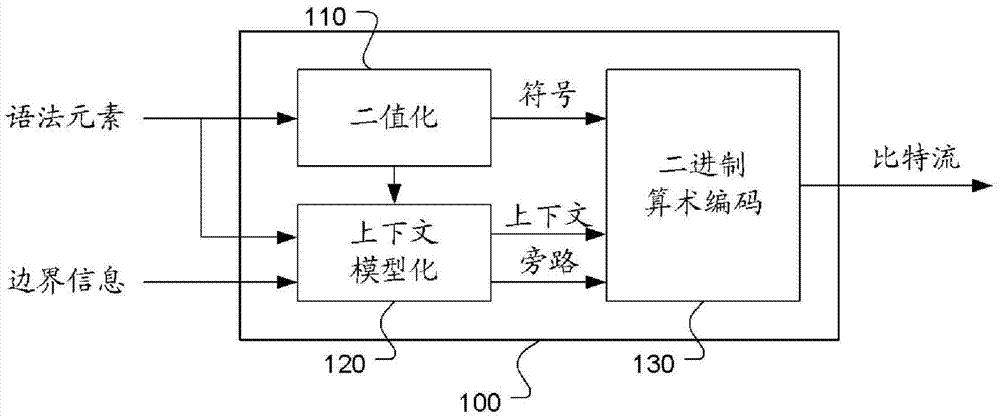
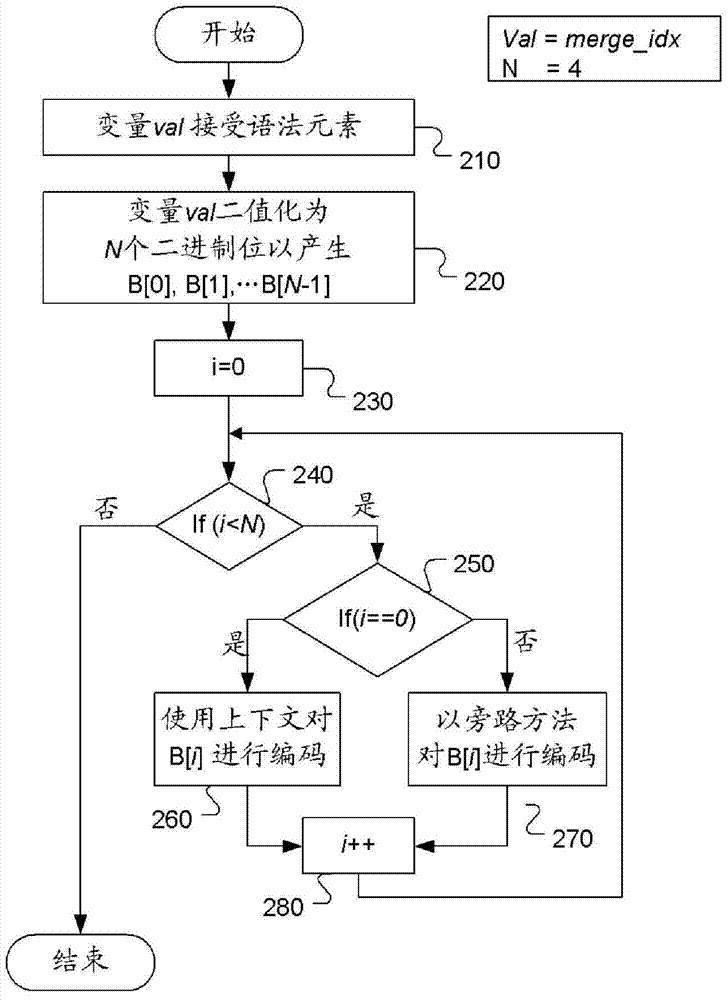
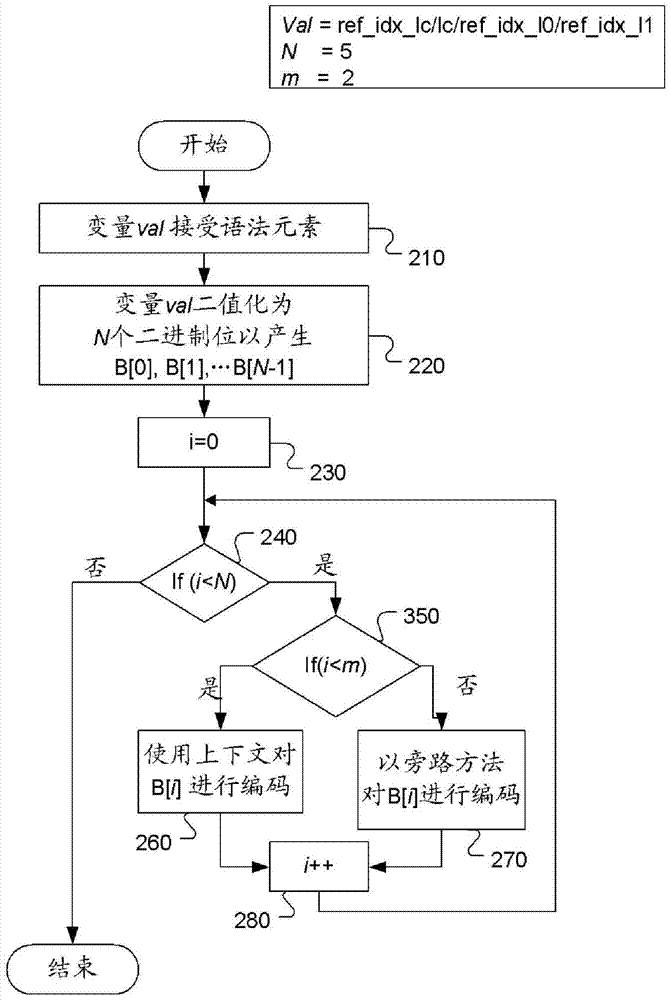
Method and apparatus for context-adaptive binary arithmetic coding of syntax elements
ActiveCN103931188AReduce the number of contextsDigital video signal modificationProgramming languageArithmetic coding
A method and apparatus for context-adaptive arithmetic coding (CABAC) of a syntax element are disclosed. The bin string corresponding to a syntax element is processed by context- adaptive arithmetic coding with a reduced number of contexts using the bin-level bypass mode, bin-level context sharing, or both. The syntax element belongs to a group comprising merge_idx, ref_idx_lc / ref_idx_10 / ref_idx_l1, pred_type, and cu_qp_delta. In one embodiment, the syntax element corresponds to merge_idx and three bins of the bin string with bin indices corresponding to 1, 2 and 3 are coded in the bin bypass mode. In another embodiment, the syntax element corresponds to ref_idx_lc / ref_idx_10 / ref_idx_l1 and one or more bins of the bin string with bin indices larger than 1 or larger than 2 are coded in the bin bypass mode.
Owner:HFI INNOVATION INC
Global optimization and construction method and system of TRIE double-array
InactiveCN101788990AAvoid wastingNarrow down the search spaceSpecial data processing applicationsArray data structureTheoretical computer science
The invention provides a global optimization and construction method of a TRIE double-array, comprising the following steps of: 1. representing each node in a TRIE structure by using binary strings, wherein each bit in each binary string from left to right is in one-to-one correspondence with each subnode in each node, 1 represents that the subnodes are contained, and 0 represents that the subnodes are not contained, then rightwards shifting each binary string until the 0 bit is 1, and respectively recording the shifted binary representations and the shifted digits; 2. mapping all nodes in the TRIE to the corresponding class according to the binary representations of the nodes; 3. determining the stored sequence of each nodes of the TRIE in the double-array and recording the shifted basic value of each node in the double-array; and 4. setting a check and a base arrays according to the shifted basic value stored in each node, the parent-child relationships among the nodes in the TRIE and the shifted step length corresponding to each subnode.
Owner:北京金远见电脑技术有限公司
Modified SHA-1 hash algorithm
InactiveCN101872338AImprove efficiencyImprove securityTransmissionComplex mathematical operationsMessage processingMessage passing
The invention relates to a modified SHA-1 hash algorithm. The existing SHA-1 harsh algorithm has low security. The invention firstly adds a 1, a plurality of 0 and a 64-bit binary string after the information to be processed, then enlarges and groups the information, so the original 512-bit group is changed into a 1024-bit group and a register value is initialized; then a main cycle is utilized to sequentially process each group, the main cycle totally has four operations, and each operation contains logical function and compression function processing; and finally, after the processing of all the groups is completed, 160-bit message digest is output, and when the message digest is transferred, the message to be transferred is added with a safety hashed value. Through the algorithm of the invention, the original SHA-1 algorithm has more safety on message processing, and through modifying the logical function expression and the compression function logical structure of the algorithm, the efficiency of the SHA-1 algorithm is improved.
Owner:HANGZHOU DIANZI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com