Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
363results about How to "Improve protection efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Porcine pseudorabies virus virulent strain, and gene deletion vaccine strain thereof and applications thereof
ActiveCN102994458AEffective preventionEffective therapeuticMicroorganism based processesAntiviralsRabiesMicrobacterium
The invention discloses a porcine pseudorabies virus virulent strain, and a gene deletion vaccine strain thereof and applications thereof. The porcine pseudorabies virus virulent strain is named as HeN1, the microbial preservation number of the porcine pseudorabies virus virulent strain is CGMCC NO.6656, the deleted gE gene obtaines the gene deletion vaccine strain rPRV-gE-EGFP+ on the basis of the virulent strain HeN1, and the microbial preservation number is CGMCC NO.6657. The virulent strain can be prepared into inactivated vaccine (single vaccine or combined vaccine), the gene deletion vaccine strain rPRV-gE-EGFP+ can be prepared into activated vaccine or inactivated vaccine (single vaccine or combined vaccine) and the like, so that porcine pseudorabies can be effectively prevented or cured, or the gene deletion vaccine strain rPRV-gE-EGFP+ can be prepared into a diagnosis reagent for diagnosing the porcine pseudorabies. The gene deletion vaccine strain rPRV-gE-EGFP+ has the advantages of being good in safety, high in protection efficiency, beneficial to differential diagnosis.
Owner:HARBIN VETERINARY RES INST CHINESE ACADEMY OF AGRI SCI
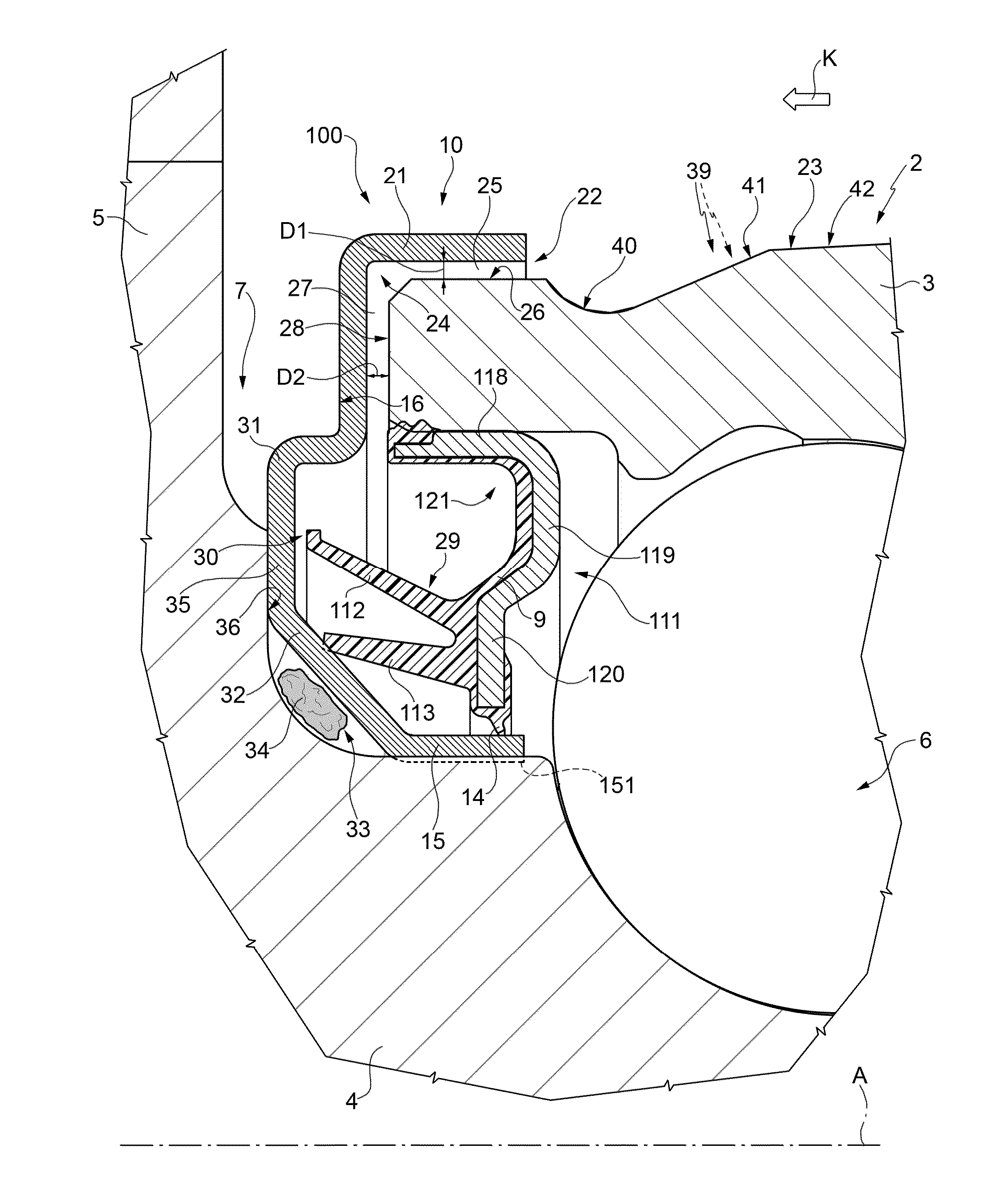
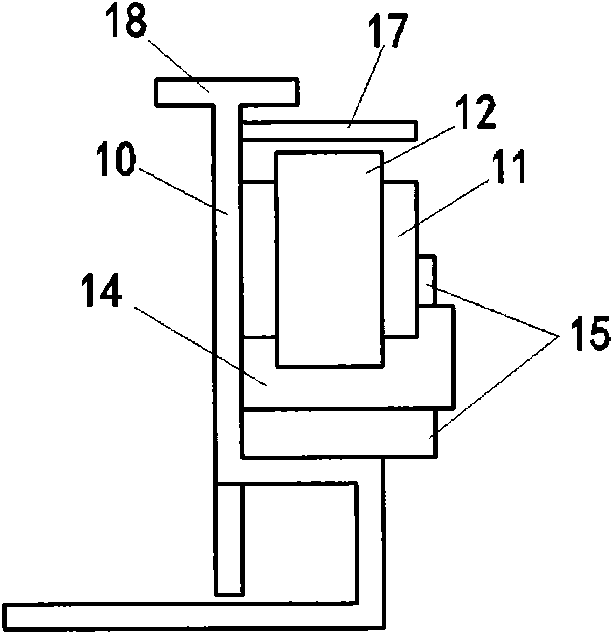
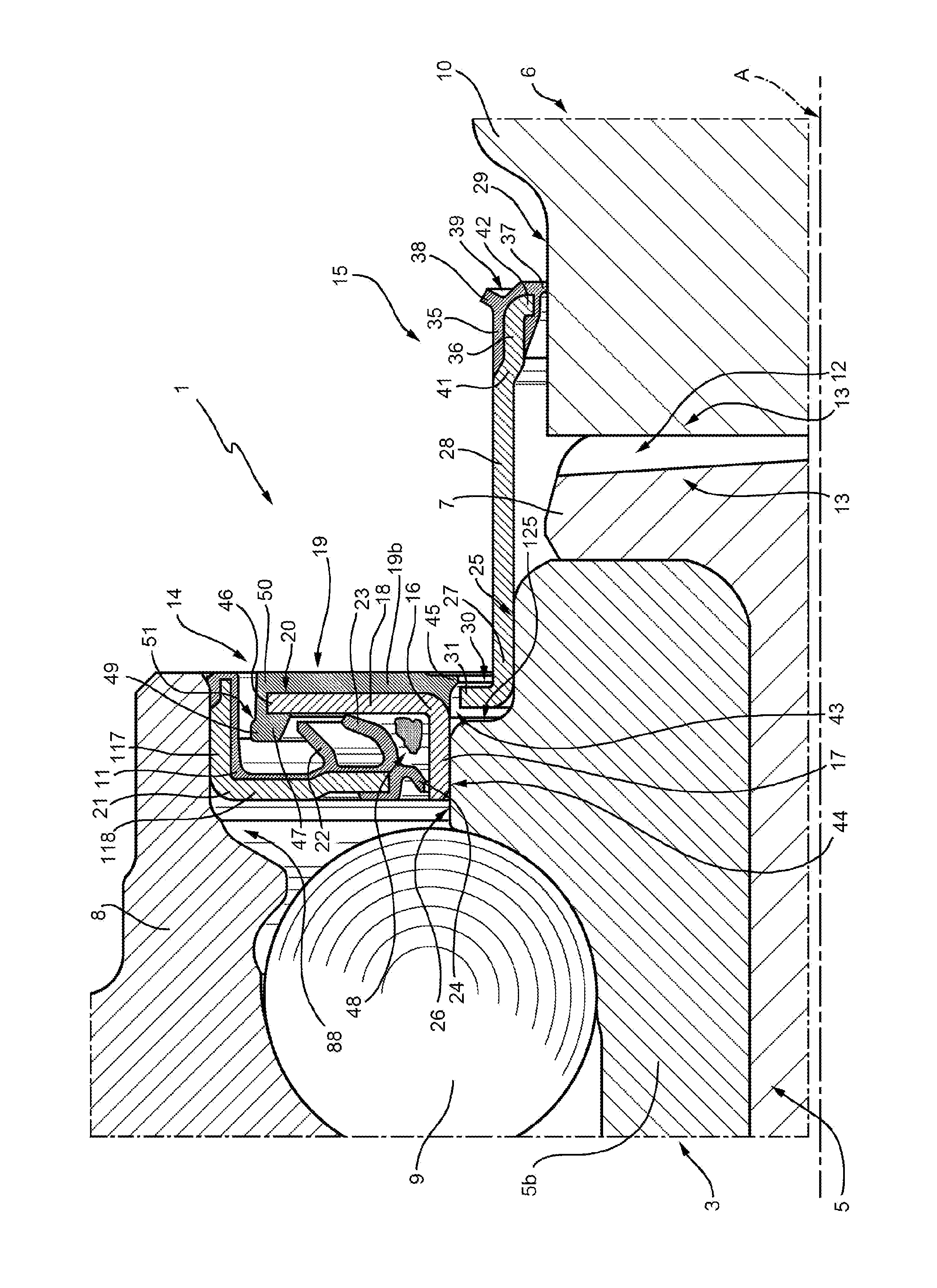
Hub bearing unit equipped with a low friction sealing assembly
ActiveUS20150003766A1Improve protection efficiencyEasy and affordable to embodyHubsBall bearingsFlangeLow friction
An assembly providing a first annular shield including a sleeve portion integral with a rotating member and with a flange portion, which radially extends to protrude from the first sleeve portion; a second annular shield having a sleeve portion integral with a stationary member and with a flange portion that radially extends to protrude on the opposite side of the sleeve portion of the first shield and facing the flange portion; and an annular seal, which the flange portion of the first shield ends with an L-shaped annular portion that protrudingly radially and axially extends out of an annular gap delimited between the rotating and stationary members to define an L-shaped channel in radial section having constant width and forming a first labyrinth seal; the channel leads into an annular recess, delimited between the second shield and a first lip of the annular seal without contacting the first shield.
Owner:AB SKF
Translational energy-absorbing seat for protecting neck during rear-end collision
The invention discloses a translational energy-absorbing seat for protecting the neck during rear-end collision and belongs to the technical field of automotive passive safety. A seat translational energy-absorbing mechanism is arranged on a slideway of a conventional automobile seat; and the mechanism is arranged under a seat cushion and symmetrically arranged on two sides of the seat. During rear-end collision, the provided translational energy-absorbing mechanism can make the seat and the passenger translate a certain distance backward under the action of a certain constraint force, and reduce relative motion of the trunk and the head of the passenger. Therefore, the neck injury to the automobile passenger during rear-end collision is effectively reduced. Meanwhile, the translational energy-absorbing seat overcomes the defect that the conventional passenger neck protecting seat during rear-end collision has heavy weight, high cost, narrow rear-end collision speed range, and the like, and has better application prospects.
Owner:TSINGHUA UNIV
DNA5-methylcytosine and 5-hydroxymethylcytosine genome sequencing method
ActiveCN105648537AHigh selectivityImprove efficiencyMicrobiological testing/measurementLibrary creationSolid phases5-Methylcytosine
The invention provides a DNA5-methylcytosine and 5-hydroxymethylcytosine genome sequencing method, comprising the following steps: (1), purifying and fragmentation pretreating DNA: extracting targeted DNA, breaking it into fragments having an average length of 50 nucleotides to 10000 nucleotides; (2), repairing trace DNA and connecting linker-adaptors: repairing and connecting pretreated DNA fragments to sequencing linker-adaptors required for next-generation sequencing; (3), covalently labeling 5-methylcytosine and 5-hydroxymethylcytosine; (4), enriching in solid phase DNA fragments of labeled 5-position modified cytosine, and in the solid phase, amplifying with PCR (polymerase chain reaction) amplimers of the corresponding linker-adaptors; purifying obtained PCR products to obtain a distribution map of genome 5-position modified cytosine required for next-generation sequencing. The invention greatly enhances bonding selectivity and efficiency of solid phase surface with DNA modified bases.
Owner:SHANGHAI YIBIEN GENE TECH CO LTD +1
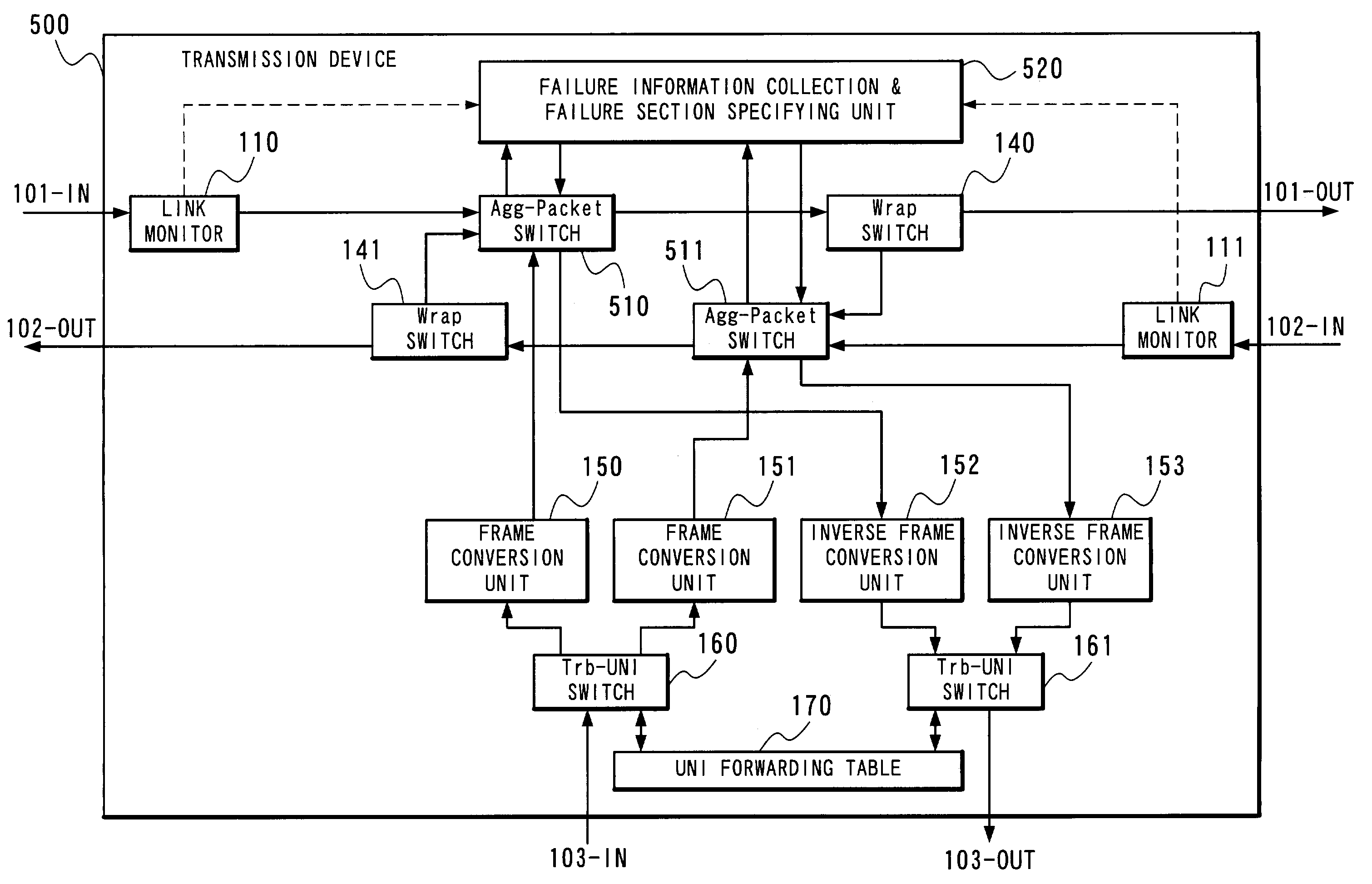
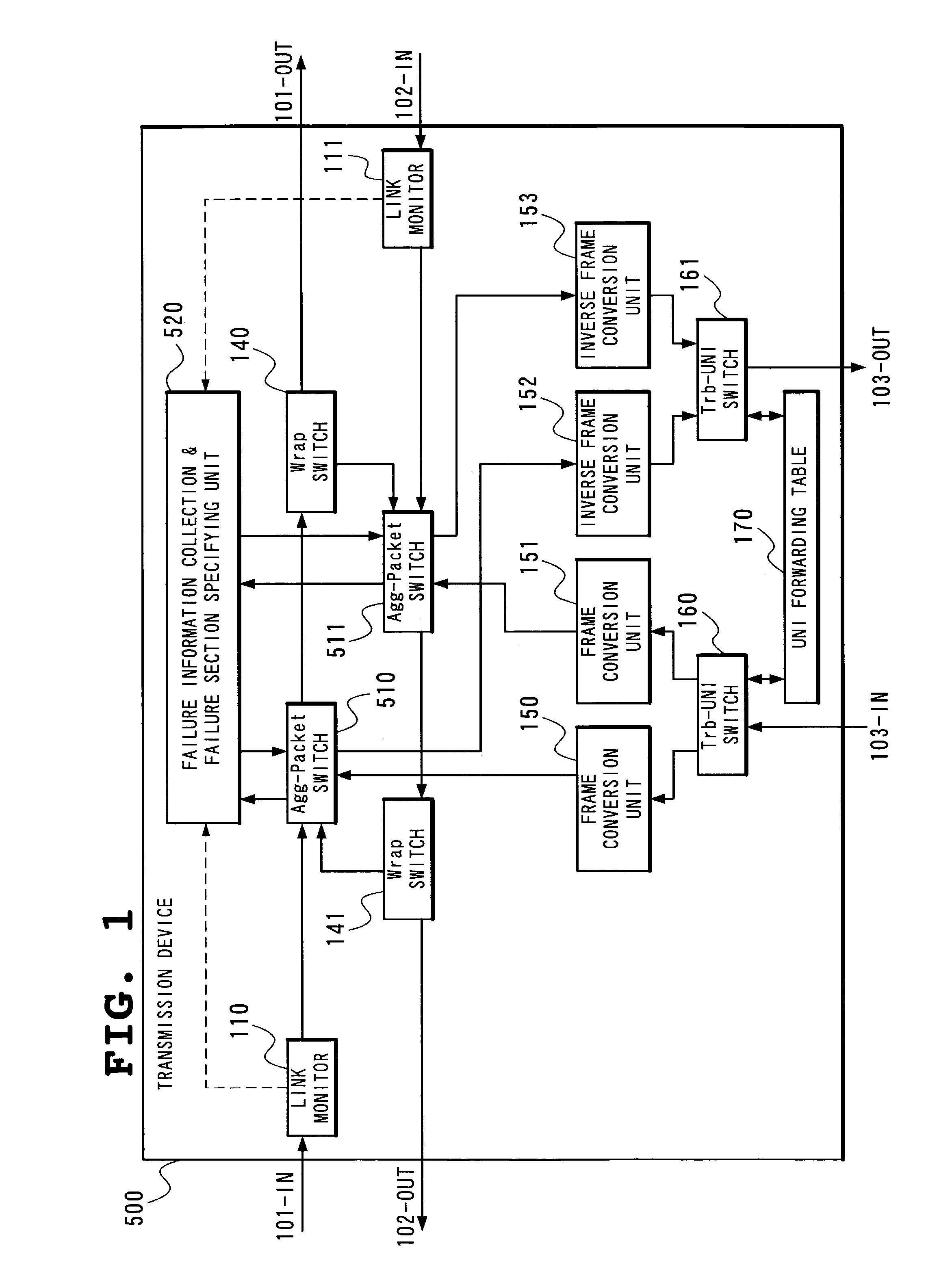
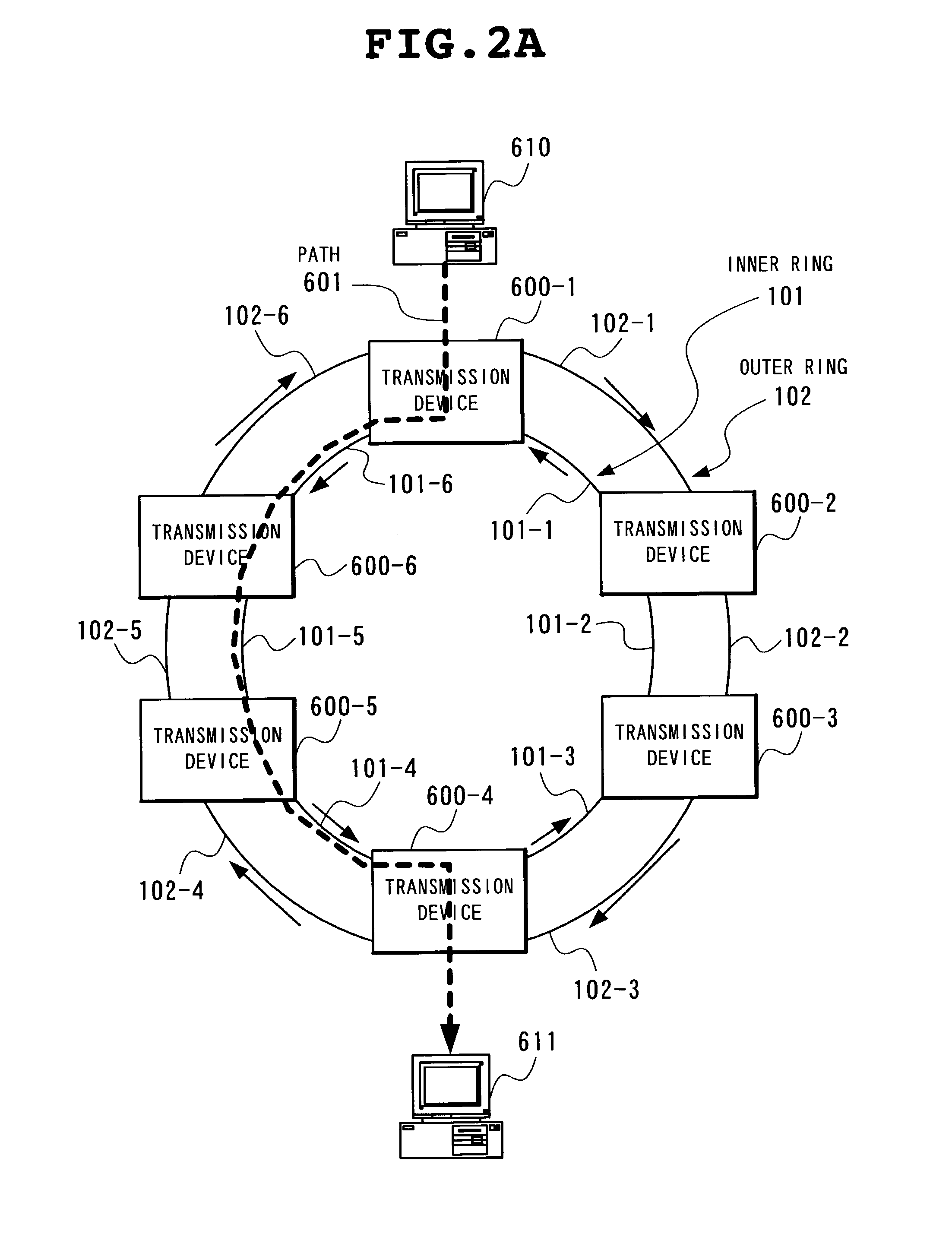
Packet protection method and transmission device in ring network, and program therefor
InactiveUS7385918B2Easy to useFailure recovery rateError preventionTransmission systemsRing networkTransmission equipment
Two transmission devices connected to a link in which a failure occurs turn back a ring. Other transmission device changes a transmission ring of an NNI packet which is a UNI packet whose transmission source is its own transmission device and which had been transmitted through the link before the failure occurs to have a reverse direction. In addition, each transmission device, upon receiving an NNI packet whose transmission destination NNI address is one or any one of a plurality of NNI addresses applied to its own transmission device, outputs the packet to a self-owned tributary port irrespectively of whether it is sent through an inner ring or an outer ring.
Owner:NEC CORP
Person and property protection system and method
InactiveUS20150087259A1Improve portabilitySimplified user interfaceEmergency connection handlingTelephonic communicationCommunication unitComputer module
A person and property protection system has a portable handheld transmitter, a control center comprising a receiving unit for receiving the emergency call signal from the handheld transmitter with a localization unit designed to determine a location of the handheld transmitter and a communication unit which is designed to inform an emergency service. A signal transmitted to the emergency service comprises details of the handheld transmitter and its location. The control center is provided with a person protection module and a property protection module. The communication unit is connected at least to the person protection module. The property protection module features an uplink interface which is designed to transmit blocking signals to financial institutions and further a downlink interface which is designed to send protection signals to a home base of the handheld transmitter.
Owner:ULTRAVEX TRADING
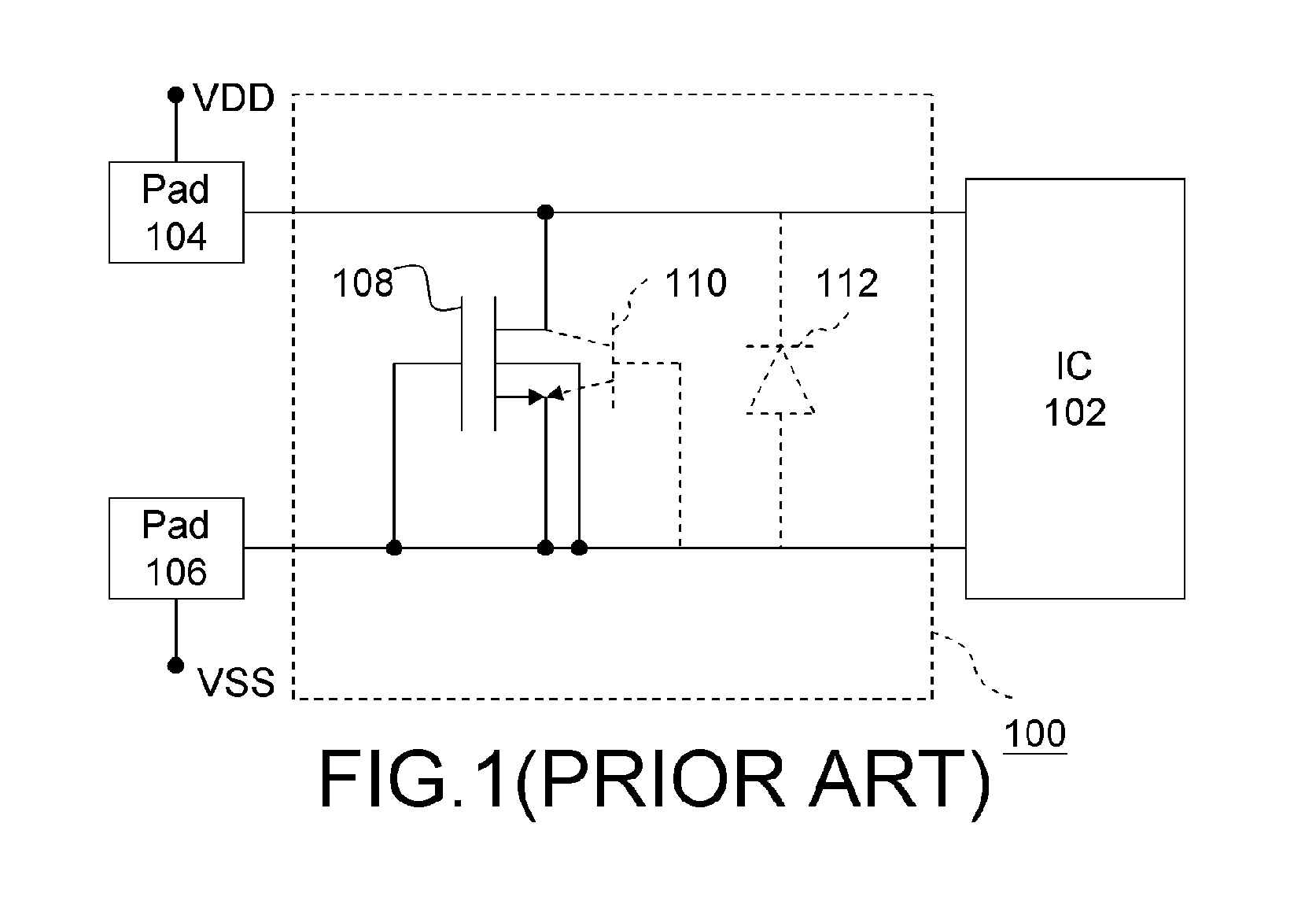
Electrostatic discharge protection circuit
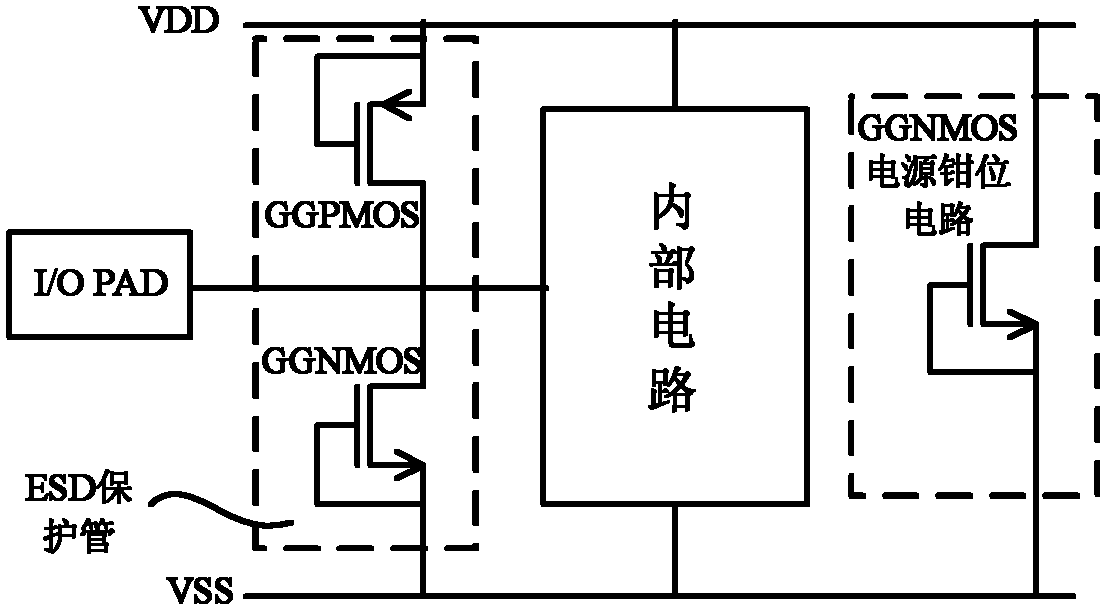
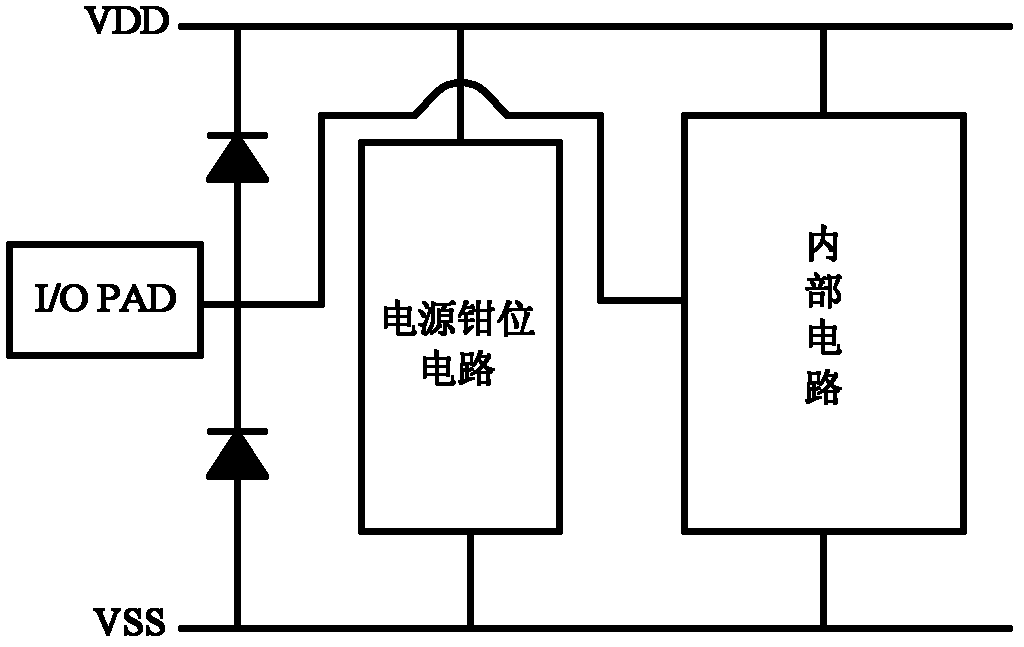
InactiveUS20060050451A1Reduce conductive resistanceLower voltage surgeEmergency protective arrangements for limiting excess voltage/currentElectrostatic discharge protectionElectrical and Electronics engineering
An ESD protection circuit includes a detection circuit for detecting an ESD current and a bypass circuit for bypassing the ESD. The detection circuit and bypass circuit are connected to a first pad and a second pad. The bypass circuit is connected to an output terminal of the detection circuit. The bypass circuit comprises a MOS transistor, a first bipolar transistor and a second bipolar transistor. The drain of the MOS transistor, the collectors of the first bipolar transistor and the collector of the second bipolar transistor are connected to the first pad. The source and the substrate of the MOS transistor and the emitter of the second bipolar transistor are connected to the second pad. The base of the first bipolar transistor is connected to the gate of the MOS transistor and the emitter of the first bipolar transistor is connected to the base of the second bipolar transistor.
Owner:WINBOND ELECTRONICS CORP
Turf protection utilization method
ActiveCN106416652AImprove targetingHigh feasibilityAgriculture tools and machinesHops/wine cultivationRoad engineeringEngineering
A turf protection utilization method is provided for turf protection utilization programming and planning, and comprises the following steps: delimiting a turf protection level according to nature vegetation types and coverage; delimiting a vegetation retrieval level according to rainfall, temperature and soil factors; carrying out field investigation to check two said levels; superposing and delimiting a plurality of ecology control sections; determining the turf excavating technology according to the vegetation types and coverage in each ecology control section; selecting three protection technologies according to road engineering construction progress and turf utilization time intervals, wherein the three technologies include piled stacking, layered stacking, and skeleton layered temporary planting; determining three planting modes according to wind erosion and water erosion characteristics and propagation coefficients, wherein the three planting modes include a chessboard type, a tic-tac-toe mode and a bar stripped mode. The method can scientifically unify turf protection and utilization planning, storage and utilization, thus providing best ecology benefits; the turf protection utilization method is practical in applications.
Owner:CHINA ACAD OF TRANSPORTATION SCI
Graphene/deimpurity polyaniline-containing anticorrosive coating and preparation method thereof
ActiveCN105400373AEfficient electron transfer capabilityExcellent electron transfer abilityAnti-corrosive paintsEpoxy resin coatingsEpoxyIn situ polymerization
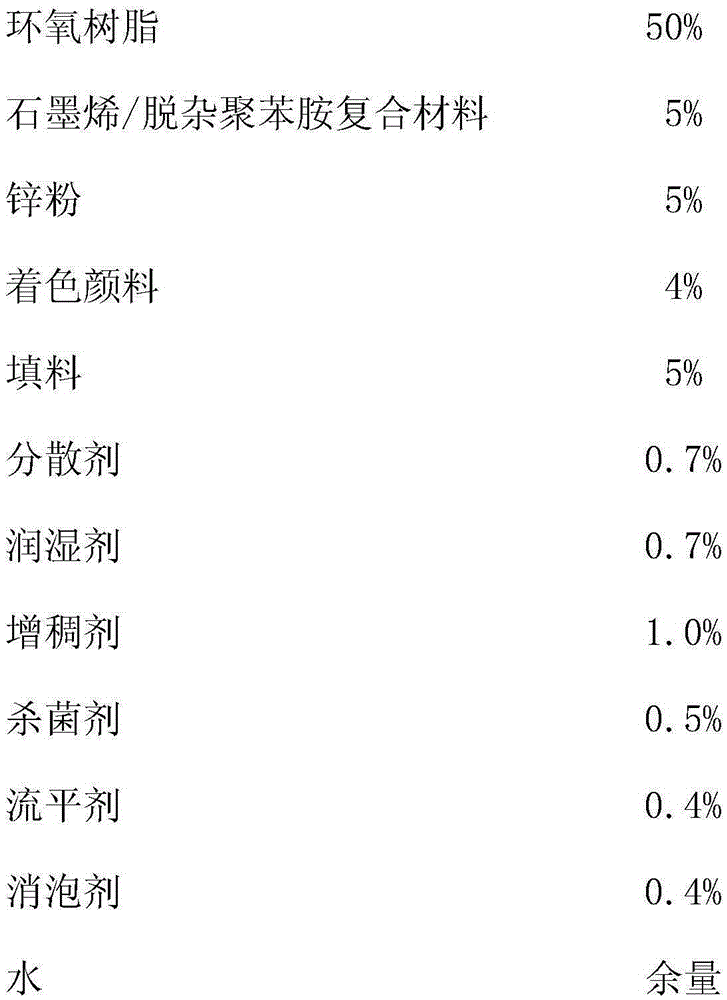
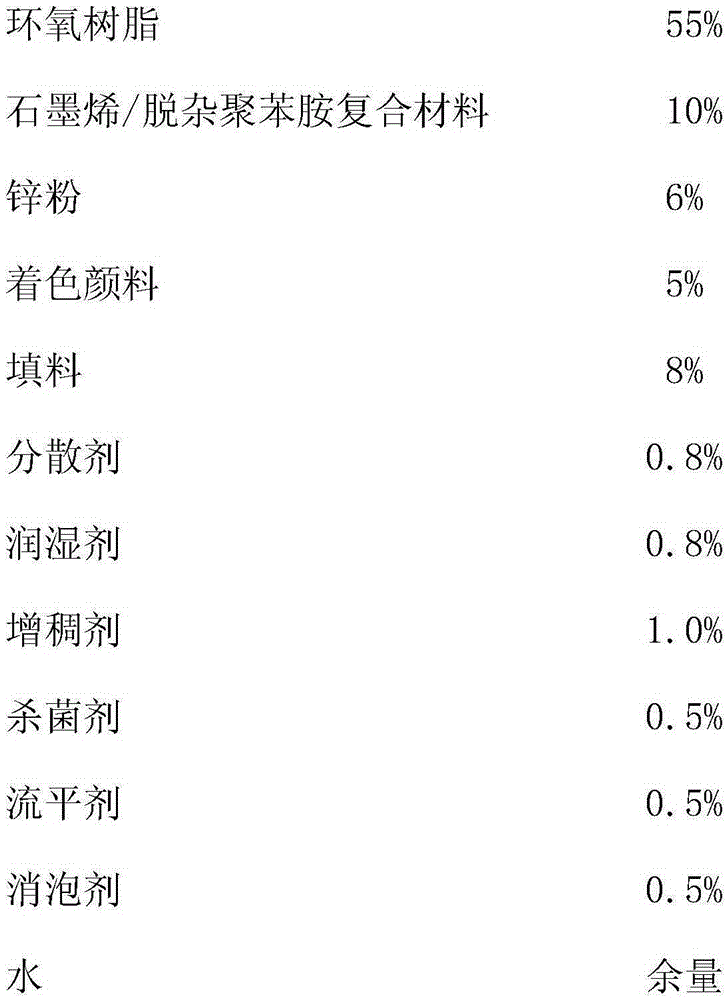
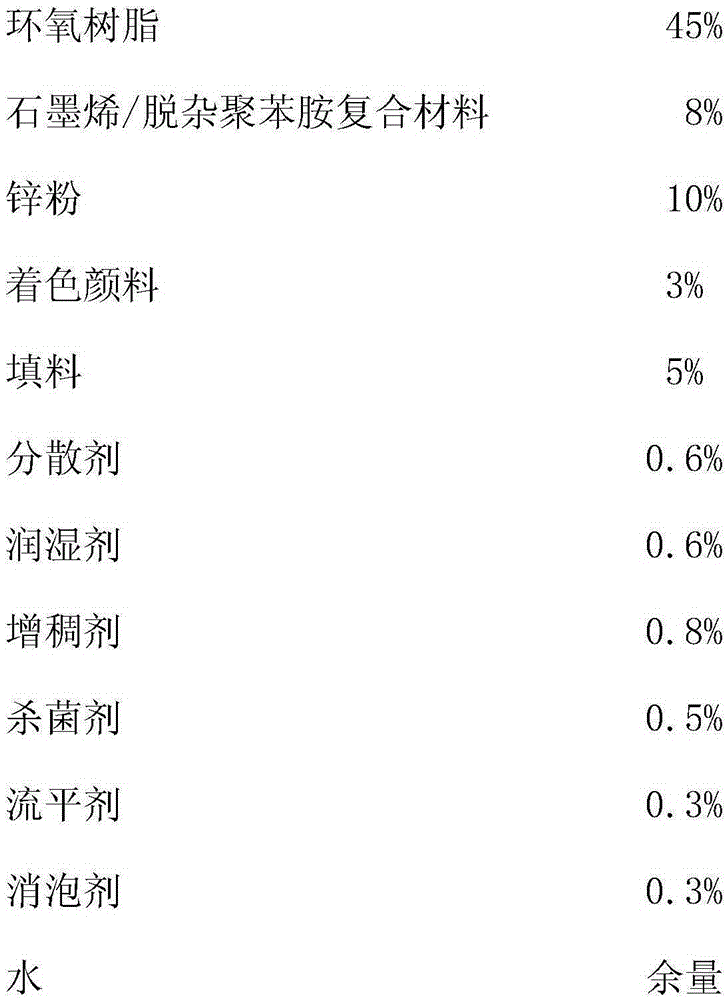
The invention belongs to the field of anticorrosive coating, and in particular, relates to a graphene / deimpurity polyaniline-containing anticorrosive coating. The anticorrosive coating is composed of the following raw materials in parts by weight: 20-80% of epoxy resin, 5-15% of a graphene / deimpurity polyanilin composite material, 5-10% of a zinc powder, 5-10% of a filler, 1-10% of a coloring pigment, 0.1-3% of a dispersion agent, 0.1-3% of a wetting agent, 0.1-3% of a thickening agent, 0.1-1% of a levelling agent, 0.1-1% of a defoaming agent, 0.1-1% of a bactericide, and 1-35% of water. In the preparation process of the anticorrosive coating, polyaniline is loaded on graphene by an in-situ polymerization method, so that the dispersion of polyaniline is improved, polyaniline agglomeration is avoided, and the graphene / deimpurity polyaniline-containing anticorrosive coating is prepared.
Owner:常州纳欧新材料科技有限公司
Security architecture system for realizing software definition security and security controller
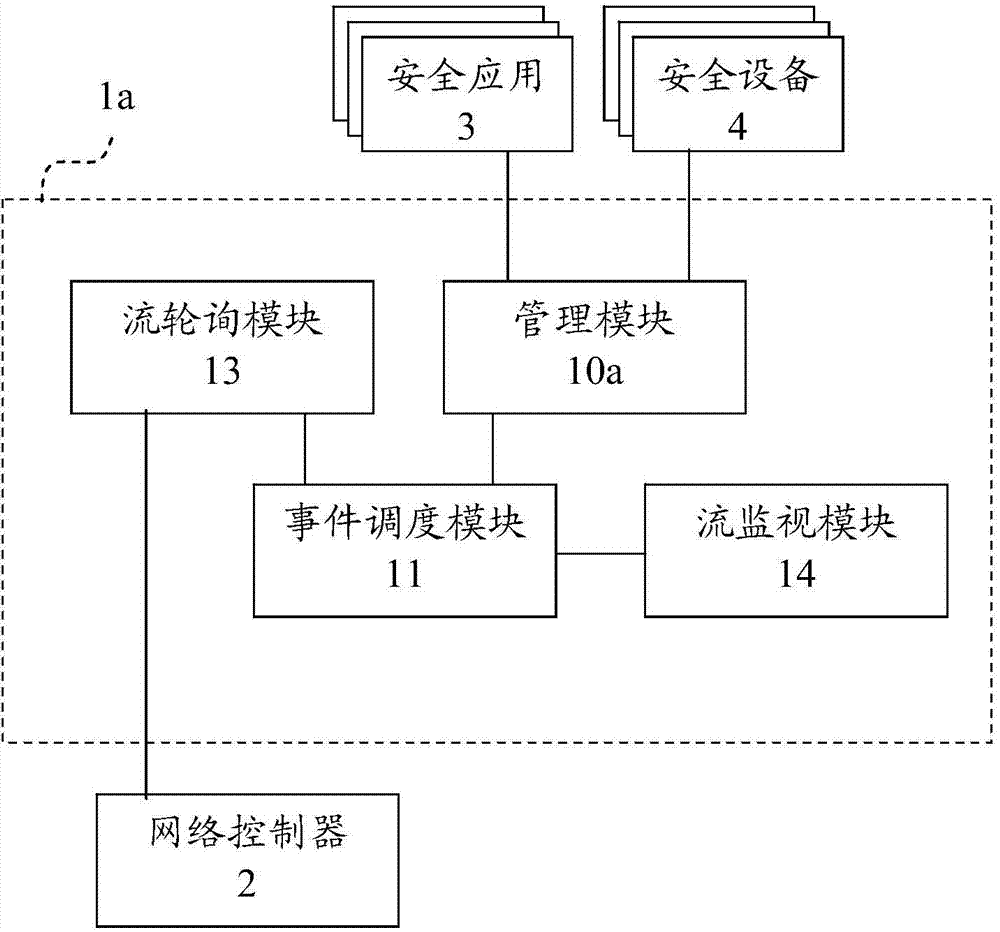
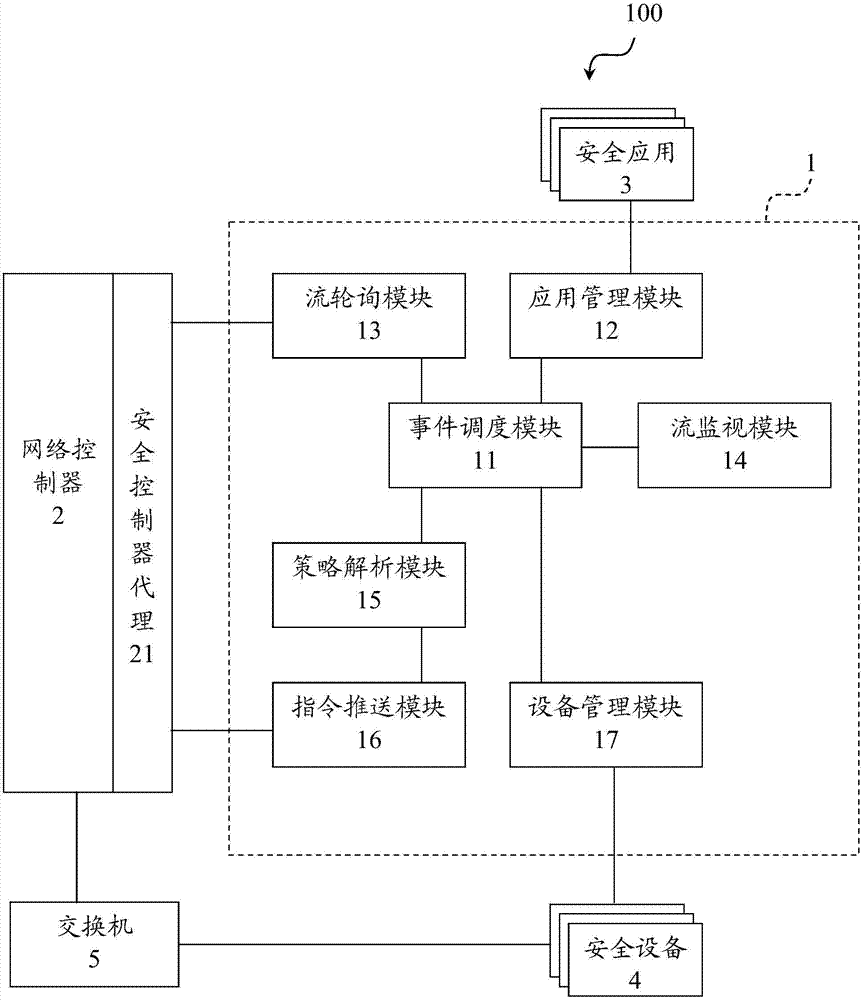
ActiveCN104125214AReduce loadImprove protection efficiencyTransmissionComputer moduleEvent scheduling
The invention discloses a security architecture system for realizing software definition security and a security controller. The security controller comprises a management module, an event scheduling module, a polling module and a flow monitoring module, wherein the management module is used for providing at least one piece of security equipment or at least one security application for registration; the polling module is used for polling a network controller to acquire data flow; the flow monitoring module is used for detecting the data flow according to a triggering condition; the event scheduling module is used for generating an execution strategy event according to the detection result of the triggering condition.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Method and device for networked protection of microgrid
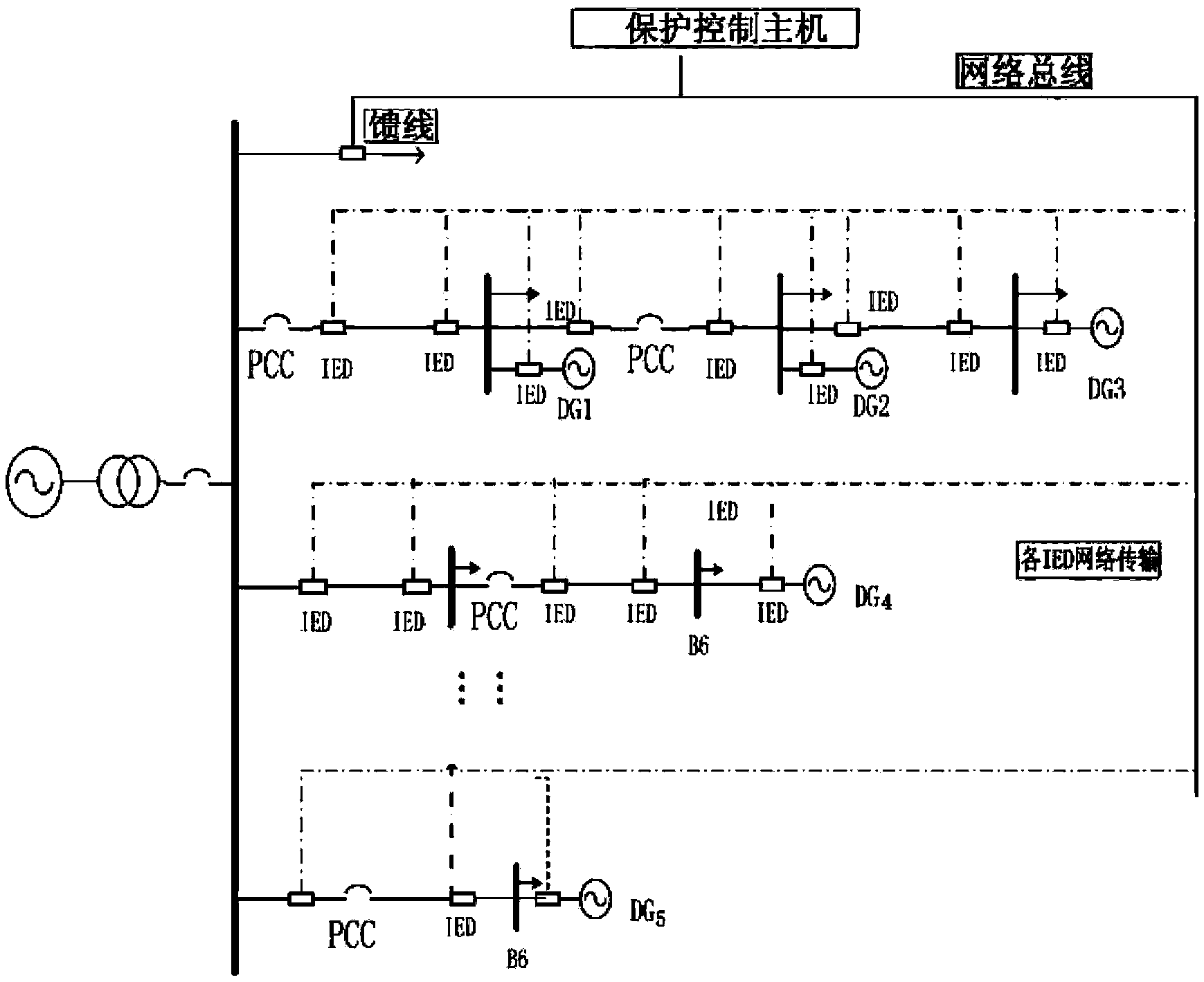
ActiveCN103354355ARelieve pressureImprove protection efficiencyEmergency protective circuit arrangementsInformation technology support systemMicrogridTransformer
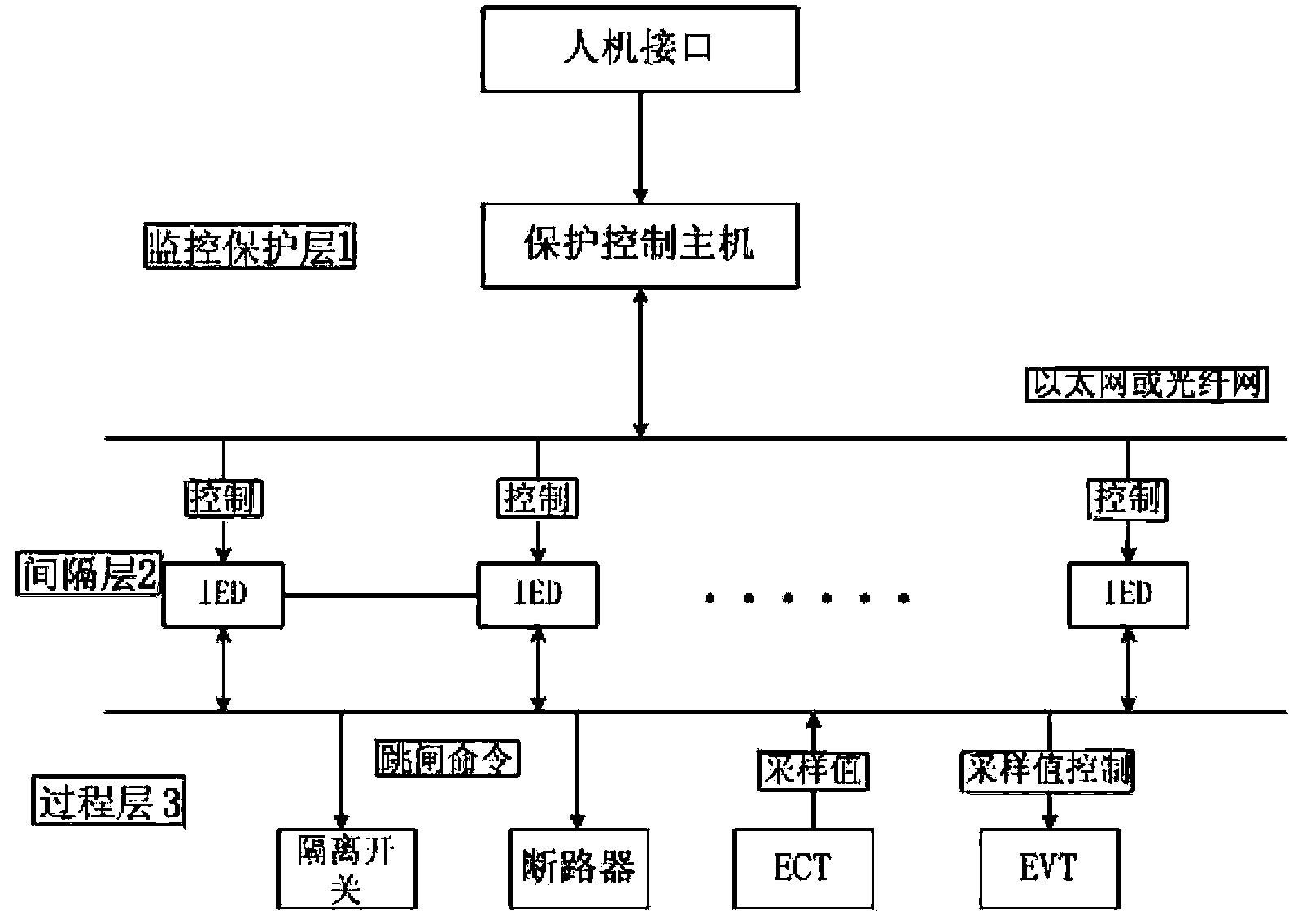
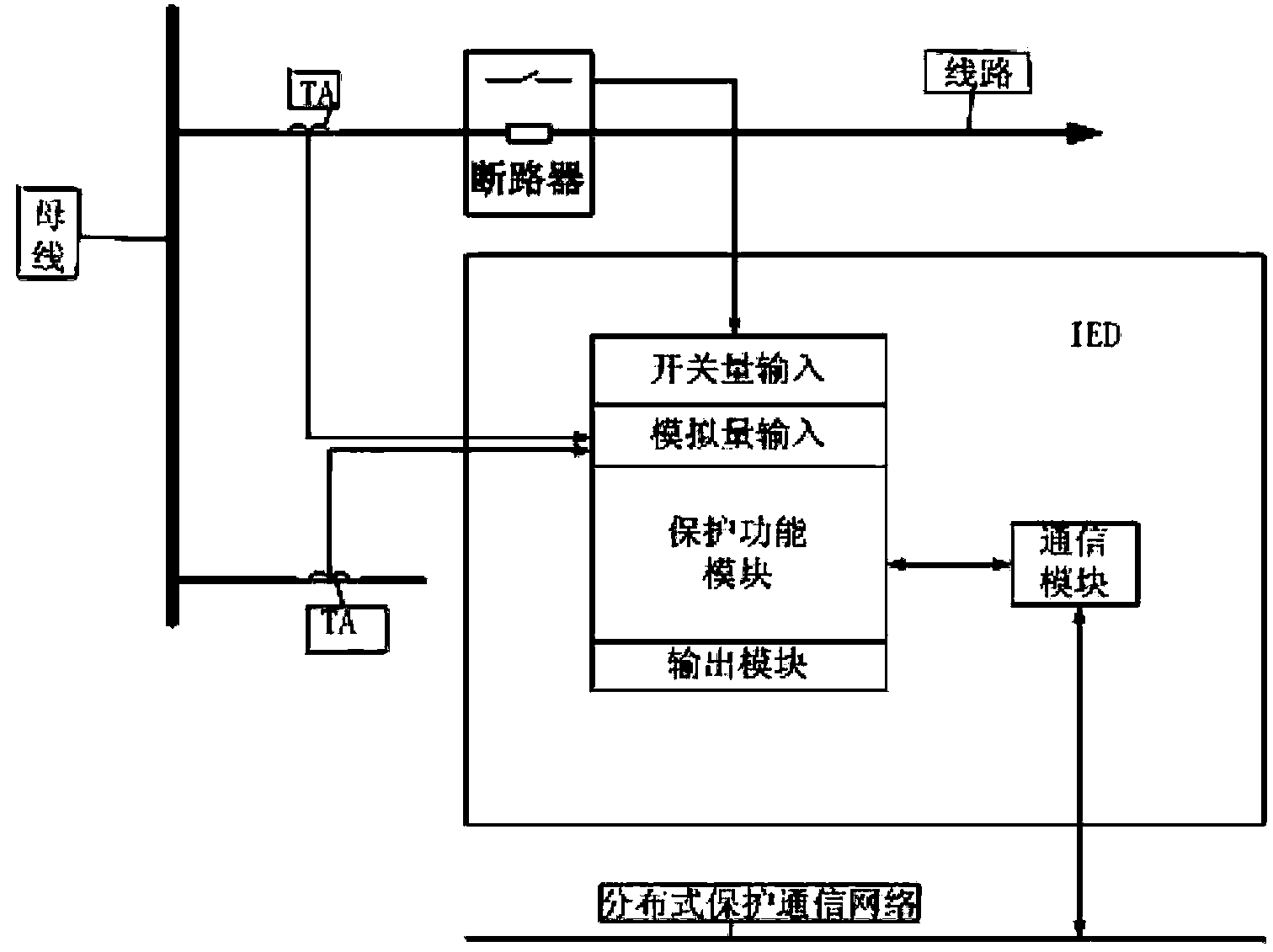
The invention discloses a method and a device for networked protection of a microgrid. Voltage and current information of a line is collected through intelligent electronic devices (IEDs) dispersedly installed on a main transformer, a bus and two sides of a power grid line; a main power grid is judged to break down or not according to a set fault detection method; operating states of the main power grid and the microgrid are monitored continuously when the main power grid is judged to operate normally, a networked monitoring system is put into operation when the main power grid is judged to break down, the intelligent electronic devices (IEDs) first judge a line on which a fault occurs according to fault direction information, and then send fault judgment information to a protection control host. According to the invention, real-time monitoring is carried out on the microgrid by adopting a networked protection system, thereby enabling the microgrid protection to become an organic unity, coordinating with each other, realizing protection for the selectivity, the rapidity, the sensitivity and the reliability of the microgrid, ensuring safe and stable operation of the microgrid system, and improving the utilization rate and the reliability of distributed generation (DG).
Owner:CHINA ENERGY ENG GRP GUANGDONG ELECTRIC POWER DESIGN INST CO LTD +1
Method and device for achieving data protection
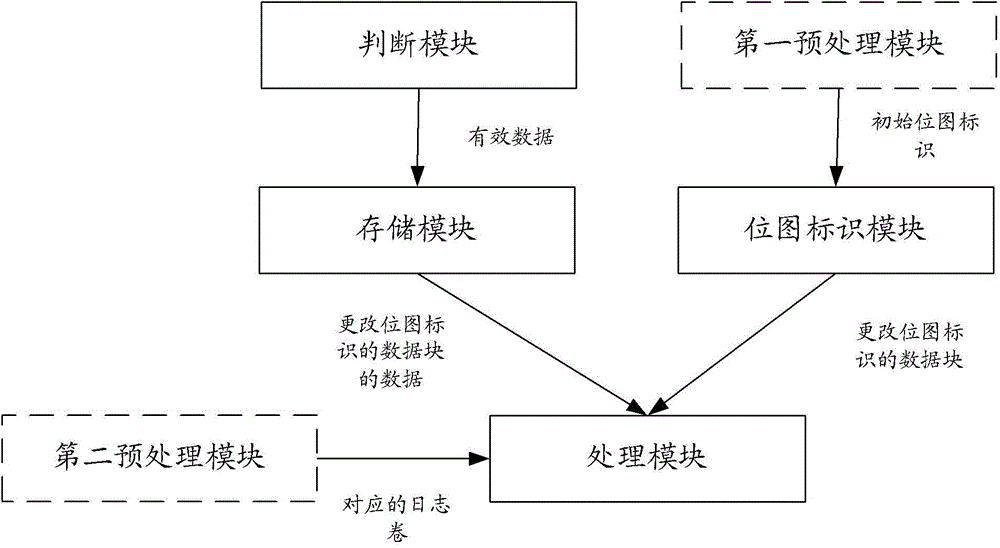
ActiveCN104615504AImprove protection efficiencyInput/output to record carriersRedundant operation error correctionData transmissionBitmap
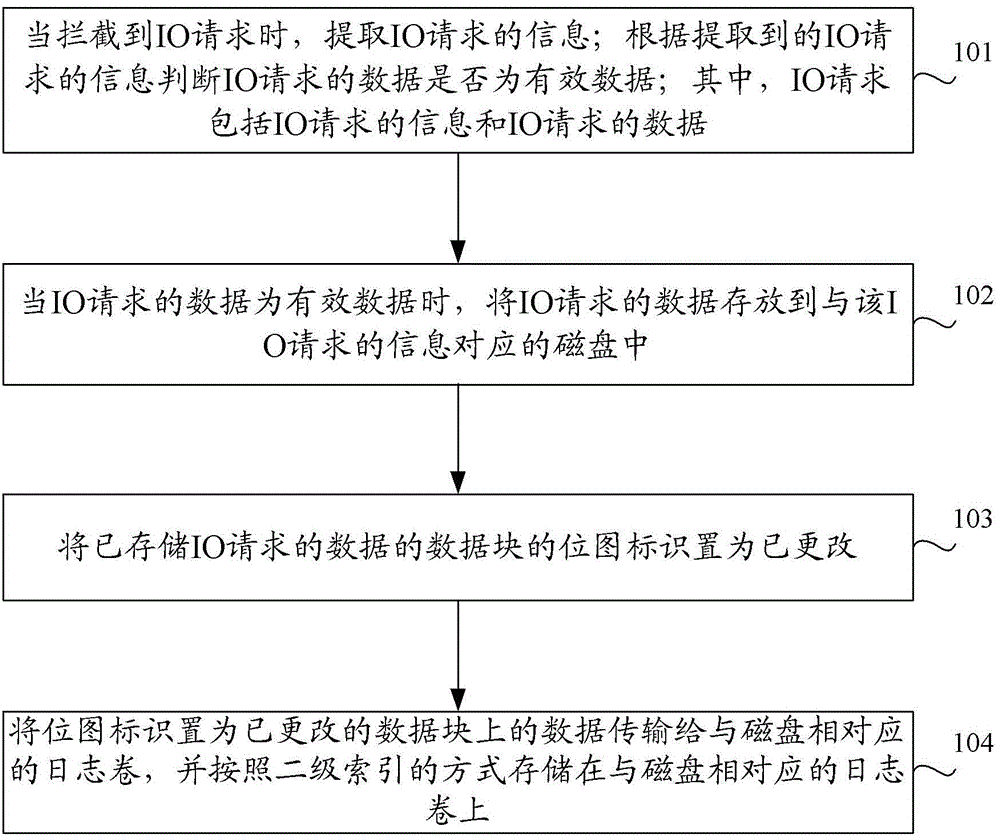
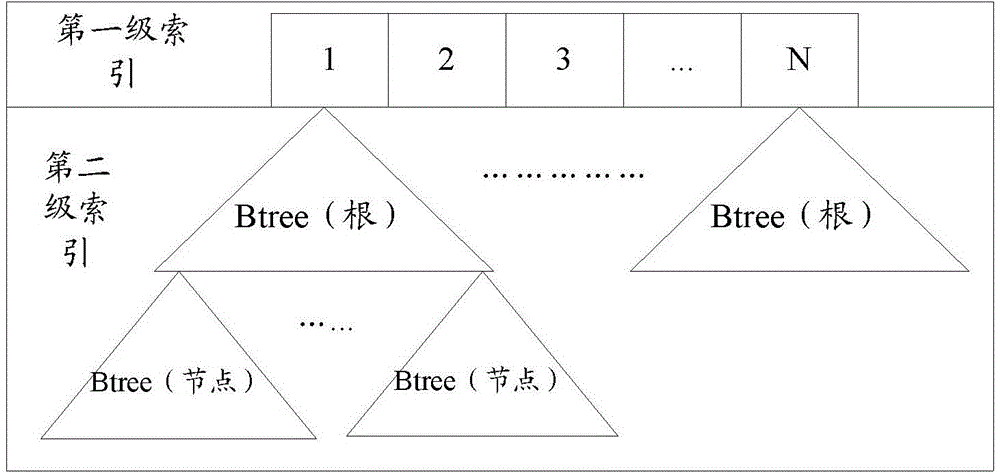
The invention discloses a method and device for achieving data protection. The method includes the following steps that when an IO request is intercepted, information of the IO request is extracted, and whether data of the IO request are valid or not is judged according to the extracted information of the IO request, wherein the IO request includes the information of the IO request and the data of the IO request; when the data of the IO request are valid, the data of the IO request are stored in a disk corresponding to the information of the IO request; a bitmap identification of a data block where the data of the IO request are stored is set to have been changed; data on the data block with the changed bitmap identification is transmitted to a log volume corresponding to the disk and stored on the log volume corresponding to the disk in a secondary index mode. The problem of repeated copying of data is solved by monitoring changes of each IO and changes of the bitmap identification, and therefore data protection efficiency is improved.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
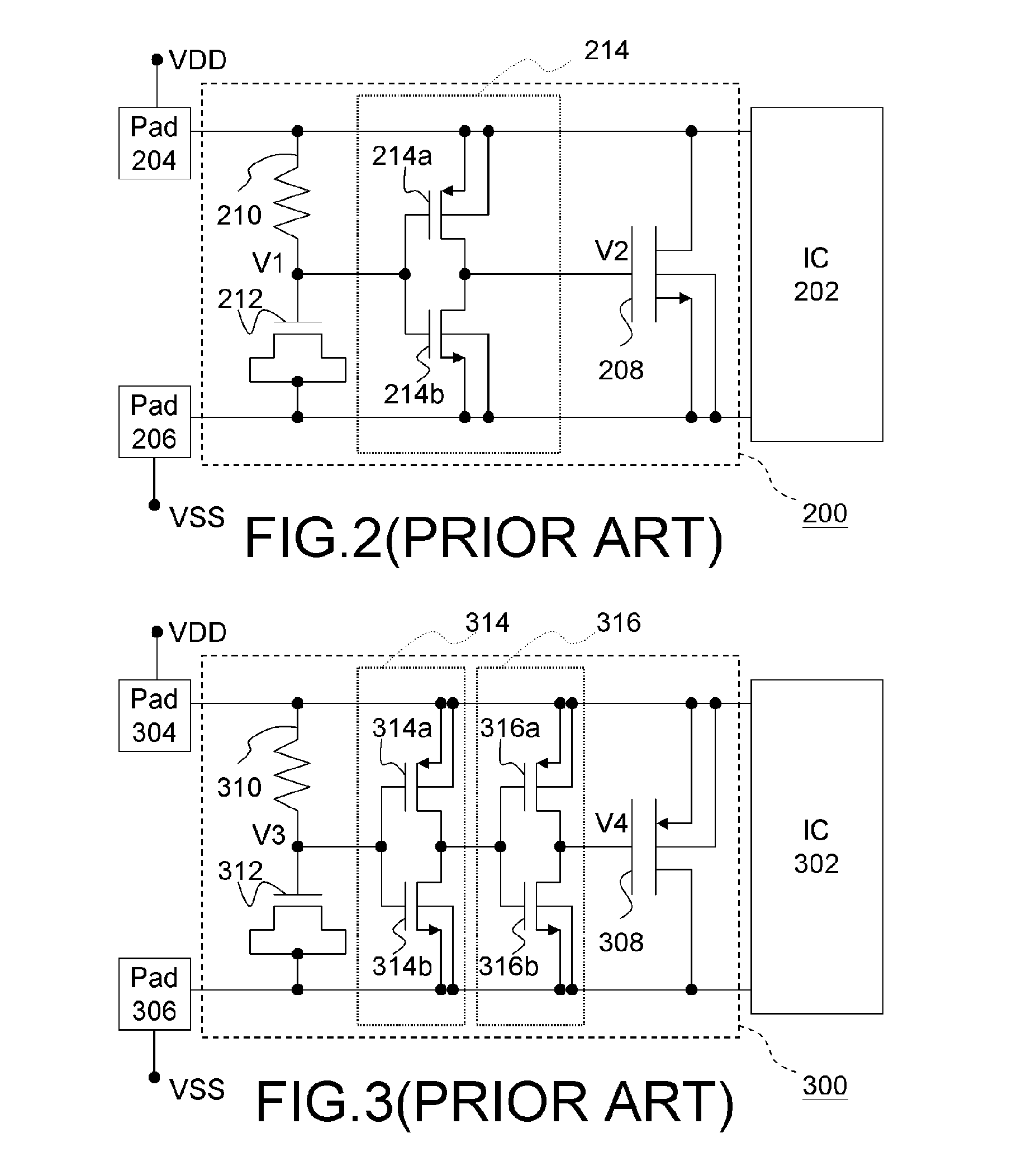
SCR (Silicon Controlled Rectifier) structure for providing ESD ( Electro-Static discharge) protection for I/O (Input/Output) port of integrated circuit under all modes
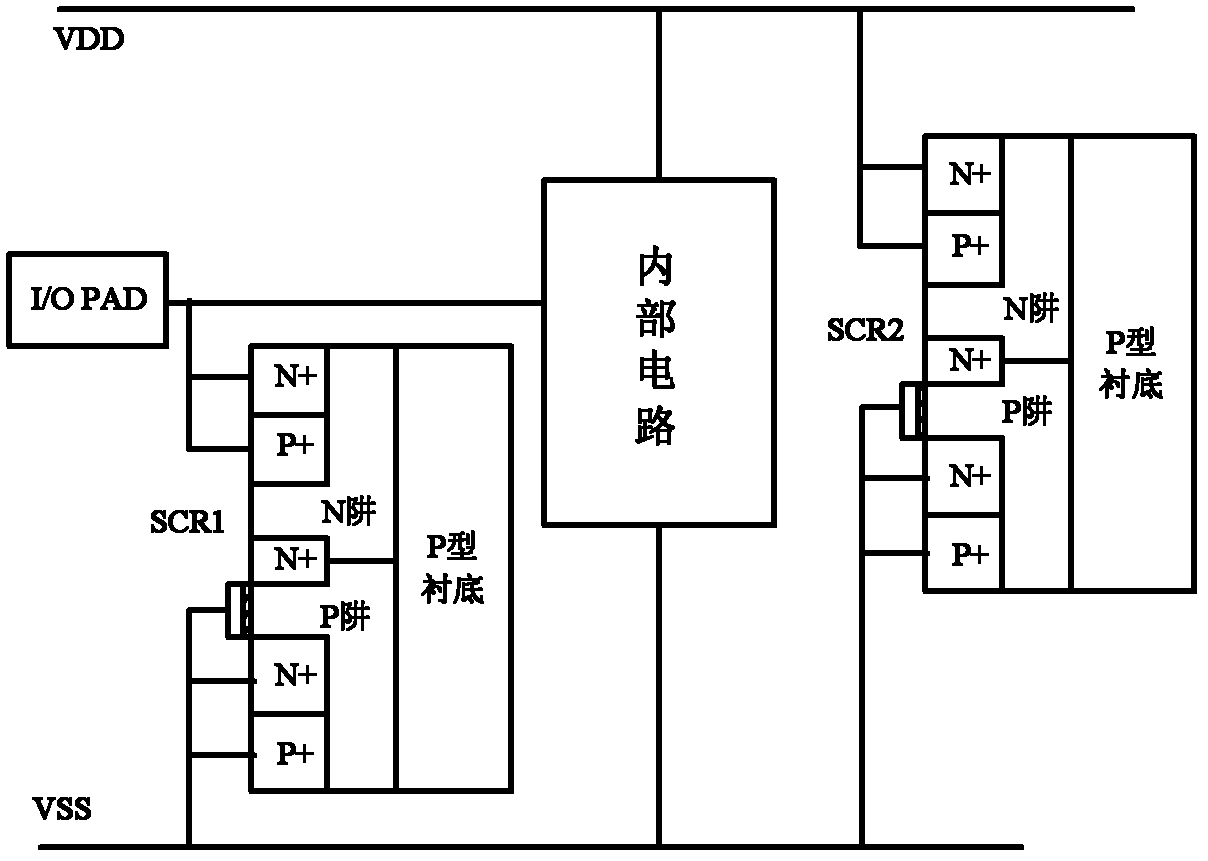
InactiveCN102544001AImprove efficiencyReduce areaSolid-state devicesEmergency protective arrangements for limiting excess voltage/currentIntegrated circuitInput/output
The invention provides an SCR (Silicon Controlled Rectifier) structure for providing ESD (Electro-Static discharge) protection for an I / O (Input / Output) port of an integrated circuit under all modes, belonging to the technical field of electronics. The SCR structure comprises a P well region on the surface of a substrate, two N well regions, three P+ regions and five N+ regions. The P well region is sandwiched between the two N well regions; the first N+ region and the first P+ region are located in the first N well region and are connected with the I / O port of an external chip; the second N+ region and the second P+ region are located in the second N well region and are connected with a VDD (Voltage Drain Drain) track of a power source of the external chip; the third N+ region and the third P+ region are located in the P well region and are connected with a VSS (Voltage Series Series) track of the power source of the external chip; the fourth N+ region is located at the joint area of the first N well region and the top of the P well region; the fifth N+ region is located at the joint area of the P well region and the top of the second N well region; and a first and a second polysilicon regions are located on the surface of the P well region and are connected with the VSS track of the power source of the external chip. According to the invention, one single device is utilized to provide ESD protection for the I / O port under all modes, the occupying area of the protected device in the chip is effectively reduced and the parasitic capacitance is effectively reduced.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
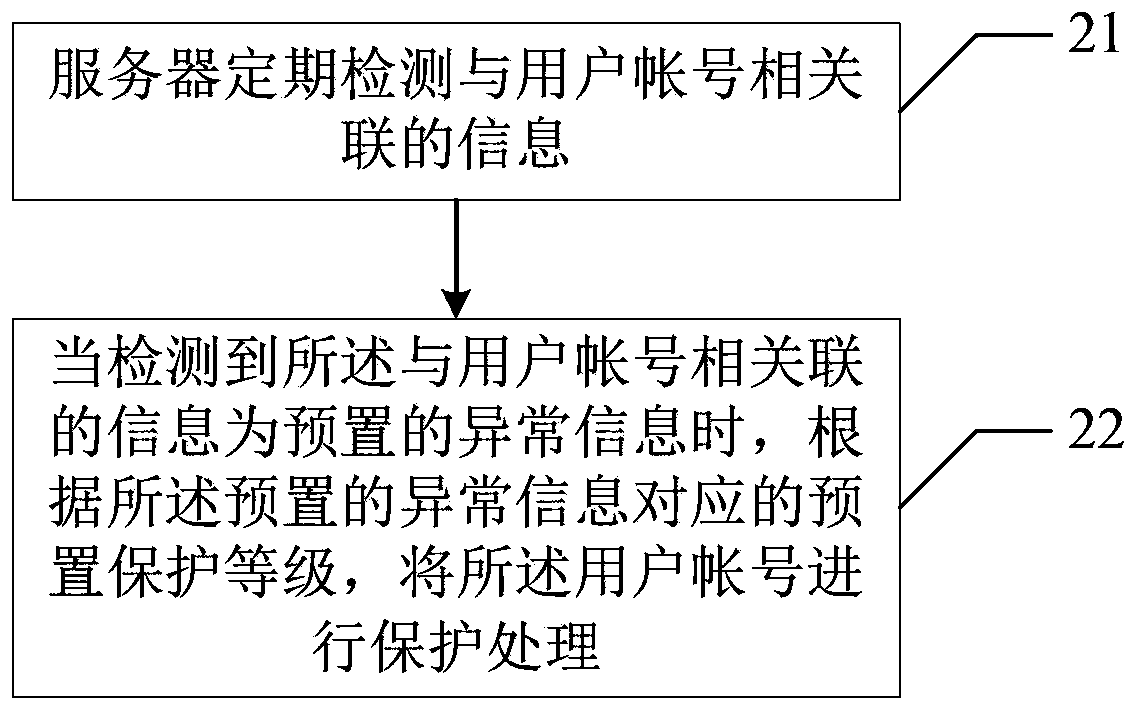
User account protection method and user account protection device
The invention provides a user account protection method which comprises the following steps: detecting information related to a user account regularly by use of a server; and when detecting that the information related to the user account is preset abnormal information, performing protective treatment on the user account according to the preset protection grade corresponding too the preset abnormal information. Furthermore, the invention also provides a user account protection device. The user account protection method and the user account protection device can be used for improving the user account protection efficiency.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
A swine pseudorabies virus variant XF-1 strain, a preparing method thereof and applications of the strain
ActiveCN106497890AUnique stabilityNo side effectsViral antigen ingredientsMicroorganism based processesVaccine researchImmunogenicity
The invention relates to the technical field of swine pseudorabies viruses, and relates to a swine pseudorabies virus variant XF-1 strain, a preparing method thereof and applications of the strain. The accession number of the variant is CCTCC NO V201654. The swine pseudorabies virus variant (the XF-1 strain) is adopted to prepare an inactivated vaccine, and safety and immunoprotective experiments are performed. Results prove that the swine pseudorabies virus variant (the XF-1 strain) inactivated vaccine has good safety, and that the immunoprotection efficiency of the inactivated vaccine is obviously higher than that of other immune groups, and therefore the virus strain is proved to have good immunogenicity, can be used for vaccine research and development for the swine pseudorabies, and has a food vaccine development prospect.
Owner:WUHAN KEQIAN BIOLOGY CO LTD
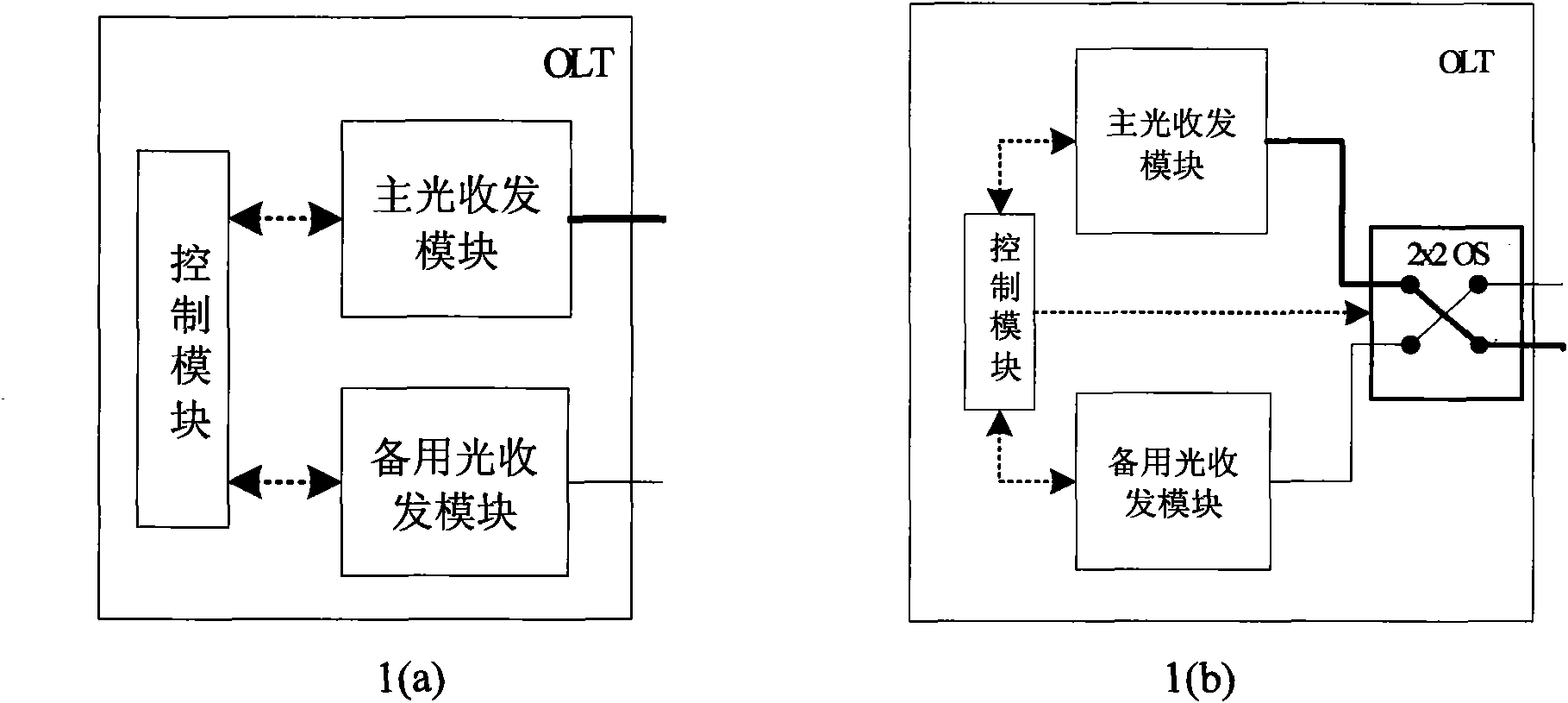
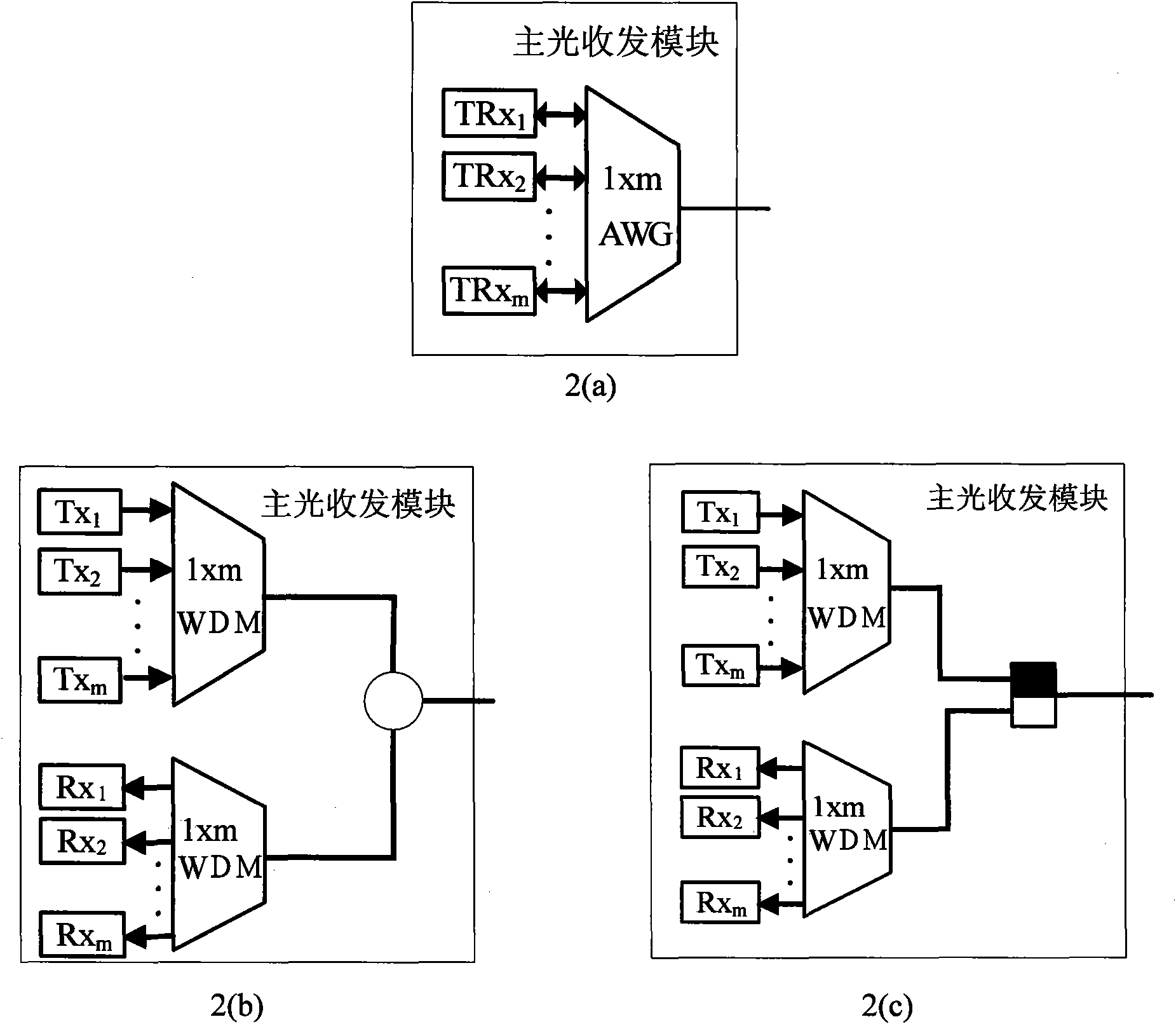
Wavelength division multiplexing passive optical network optical line terminal having shared protection function
ActiveCN101841746ALower internal assemblyImprove protection efficiencyMultiplex system selection arrangementsElectromagnetic transceiversFiberTransceiver
The invention discloses a wavelength division multiplexing passive optical network optical line terminal having a shared protection function. The outside of the optical line terminal is provided with two ports, namely a primary port and a backup port; the inside of the optical line terminal comprises a primary optical transceiver module, a backup optical transceiver module and a control module as well as a 2*2 optical path switching module for optical path selection and switching; wherein the control module is connected to the primary optical transceiver module and the backup optical transceiver module, the number of the optical transceiver units of the backup optical transceiver module is not more than that of the optical transceiver unit needed to be protected by the primary optical transceiver module, at least light sources of part of optical transceiver units are wavelength-adjustable light sources; the primary optical transceiver module and the backup optical transceiver module are respectively connected with the primary port and the backup port through the 2*2 optical path, and the control module is also connected to a control end of the 2*2 optical path connected with the backup port; the control module is connected with the primary optical transceiver module and the backup optical transceiver module; and a light source of at least part of optical transceiver units of the backup optical transceiver module adopts a wavelength dimmablelight source. The optical line terminal provided by the invention can realize the protection to all wavelength optical transceivers in the wavelength division multiplexing passive optical network optical line terminal at the low cost of a redundant device, can realize the fault protection switching to a feeder line fiber and the local recovery to local faults of a distribution fiber, and even canrealize the recovery of a plurality of concurrent faults in a network when used in the network having double-fiber backups.
Owner:南京曦光信息科技研究院有限公司
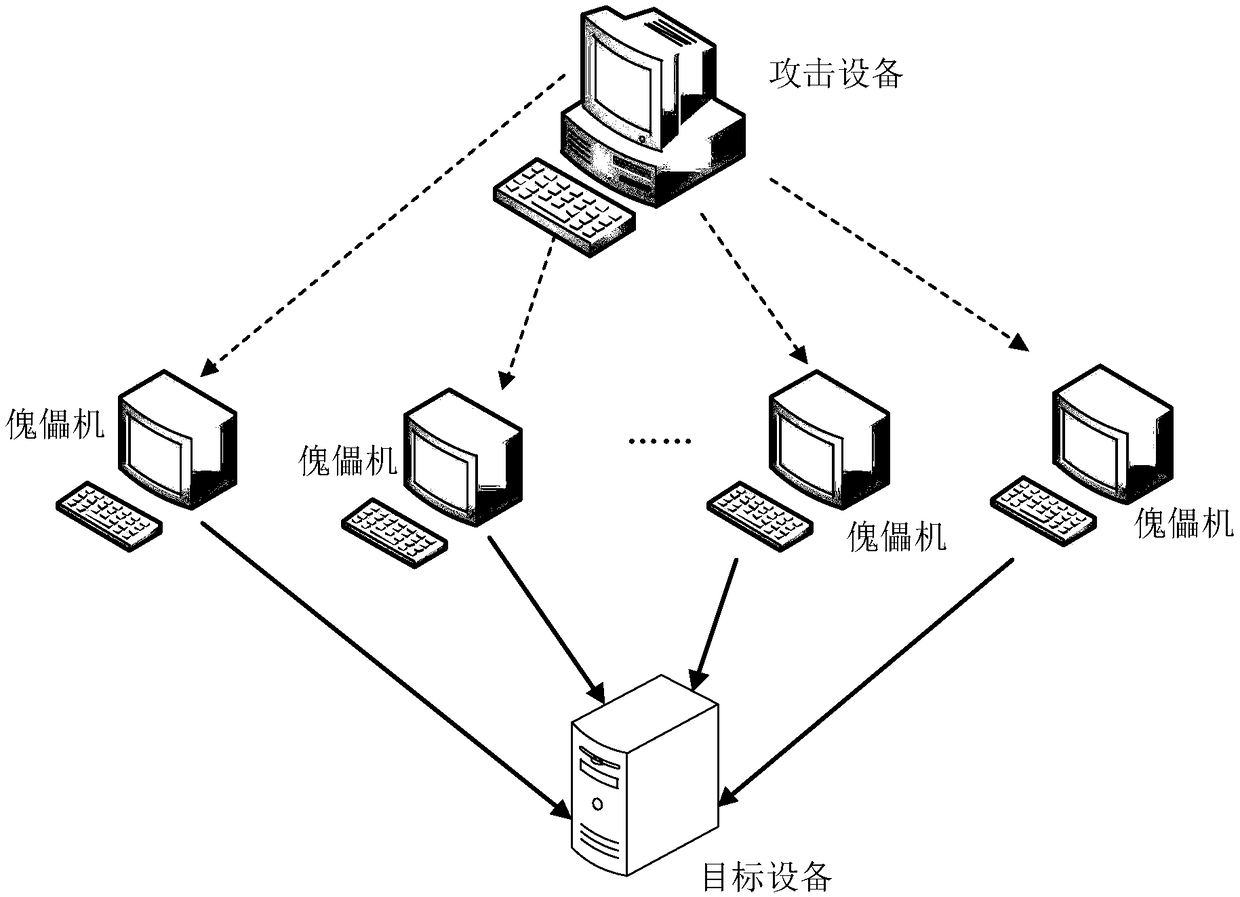
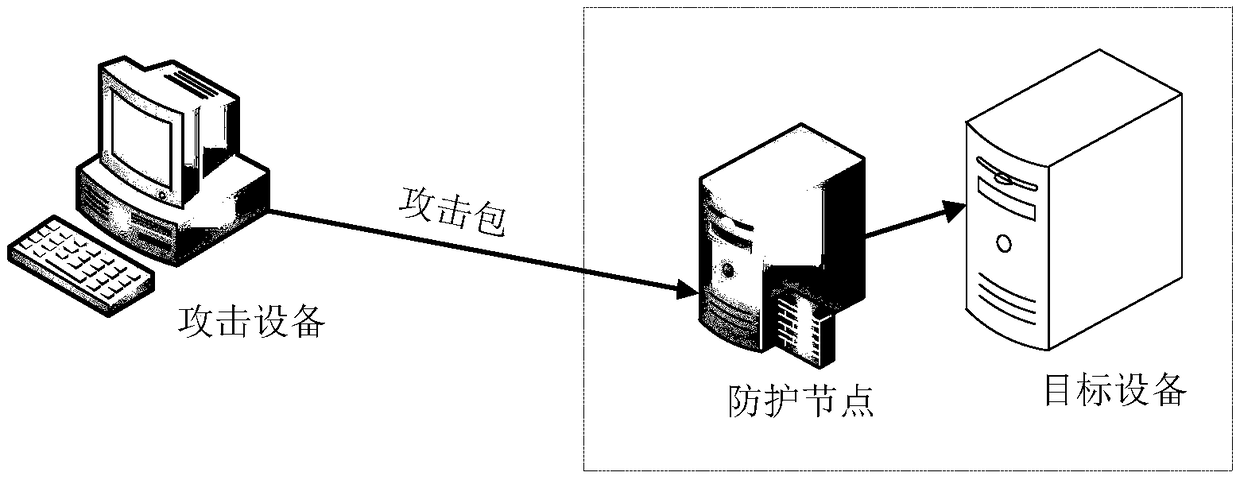
Method and device for denial-of-service simulation attack and computing device
ActiveCN109194684AEliminate negative effectsImprove accuracyData switching networksComputer security
The present invention discloses a method and a device for denial-of-service simulation attack and a computing device, belonging to the technical field of computers. The method comprises the steps of:determining an intercepted attack packet in the last round of denial-of-service simulation attack process; employing the intercepted attack packet to perform training of a protection prediction modelto obtain a trained protection prediction model, wherein the protection prediction model is configured to predict a protection policy employed by a protection node; and performing the next round of denial-of-service simulation attack through the trained protection prediction model. Through adoption of a mode of employing the intercepted attack packet at the last round to perform training and learning of the protection prediction model and employing the trained protection prediction model to perform the next round of the denial-of-service simulation attack, the accuracy of the protection policyprediction is improved through a machine self-learning mode so as to improve the effectiveness of the simulation attack and the simulation attack efficiency.
Owner:TENCENT TECH (SHENZHEN) CO LTD
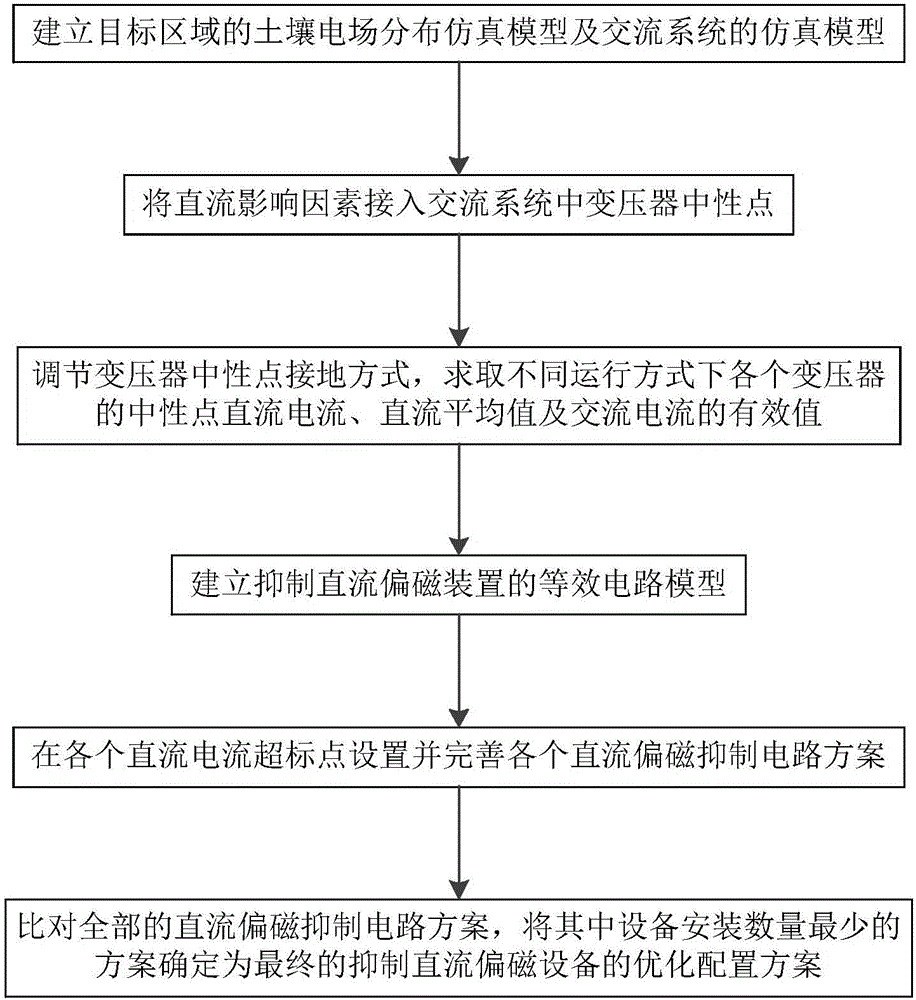
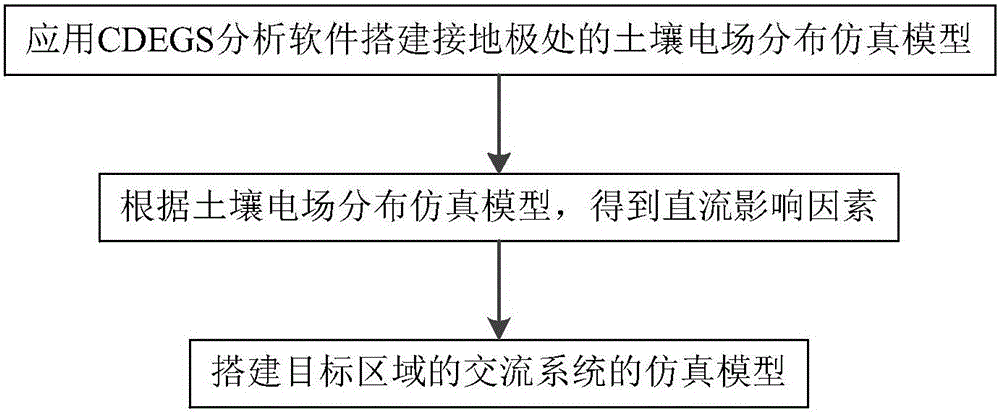
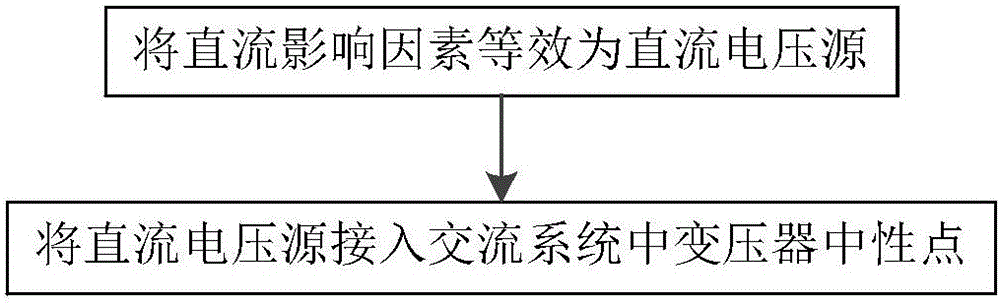
Optimal configuration method for direct current magnetic bias suppressing device in direct current power transmission system
InactiveCN105914770AImprove running stabilityImprove accuracyElectric power transfer ac networkTransformerOperation mode
The invention provides an optimal configuration method for a direct current magnetic bias suppressing device in a direct current power transmission system. A soil electric field distribution and alternating current system simulation model is built, direct current influence factors access a voltage transformer neutral point, a voltage transformer neutral point grounding mode is adjusted and evaluated, an equivalent circuit model of the direct current magnetic bias suppressing device is built, all direct current magnetic bias suppressing circuit solutions are set and improved, and a final solution with a minimum number of installed devices is determined. The method brought forward in the invention can effectively and reliably realize overall optimal configuration of the direct current magnetic bias suppressing device in the direct current power transmission system; while no extra cost is caused and not extra workload is produced, an optimal device configuration solution can be put forward for a plurality of operation modes, an overall and effective basis is provided for configuration of the direct current magnetic bias suppressing device in the direct current power transmission system, configuration accuracy and protection efficiency of the direct current magnetic bias suppressing device in the direct current power transmission system can be effectively improved, and operation stability of the direct current power transmission system can be enhanced.
Owner:STATE GRID CORP OF CHINA +2
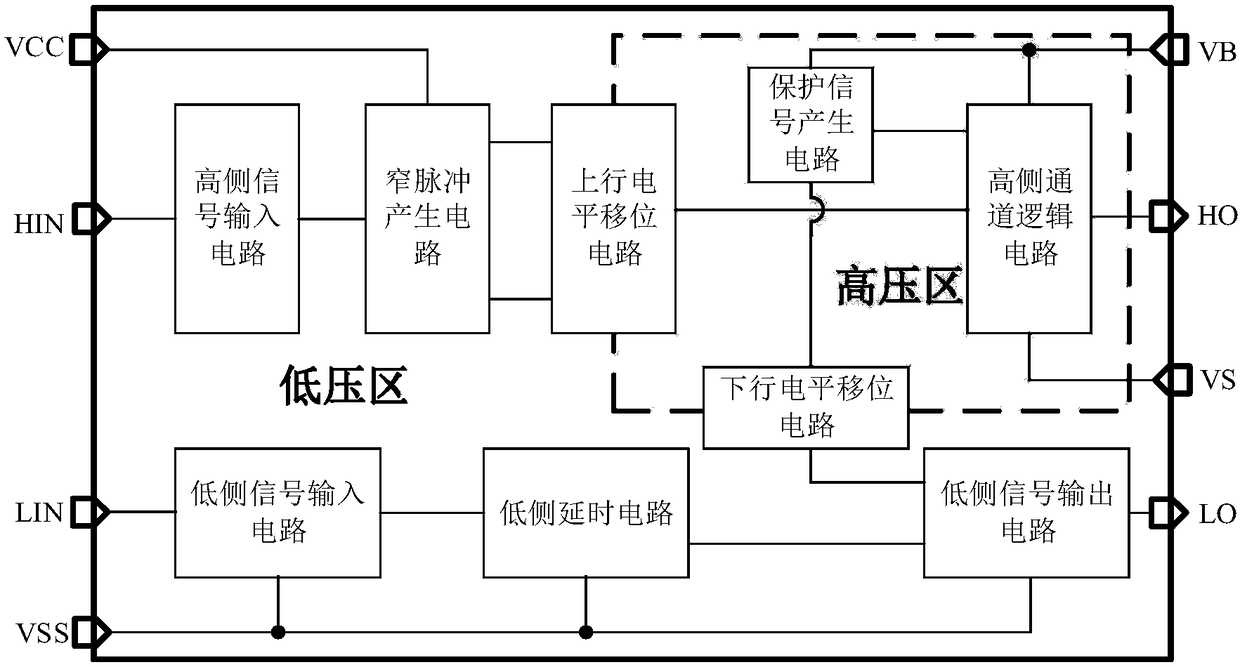
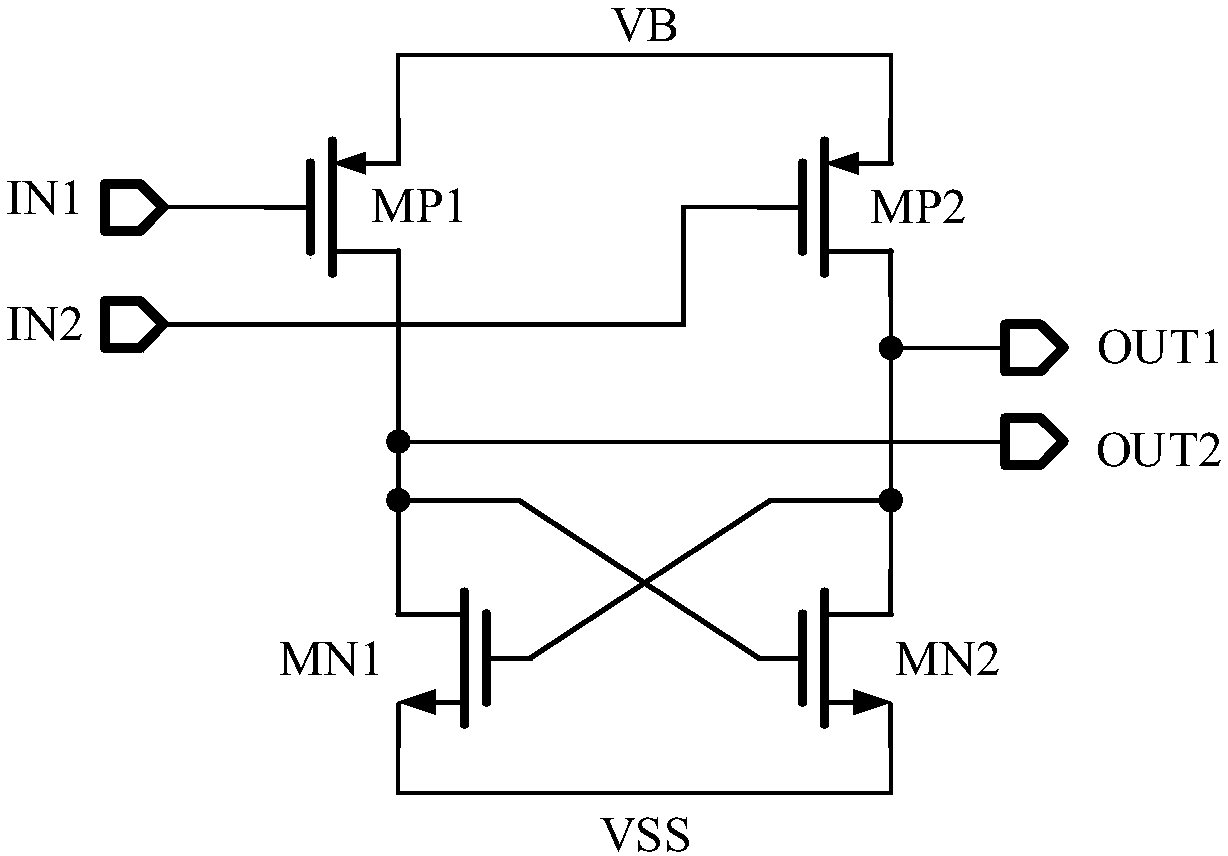
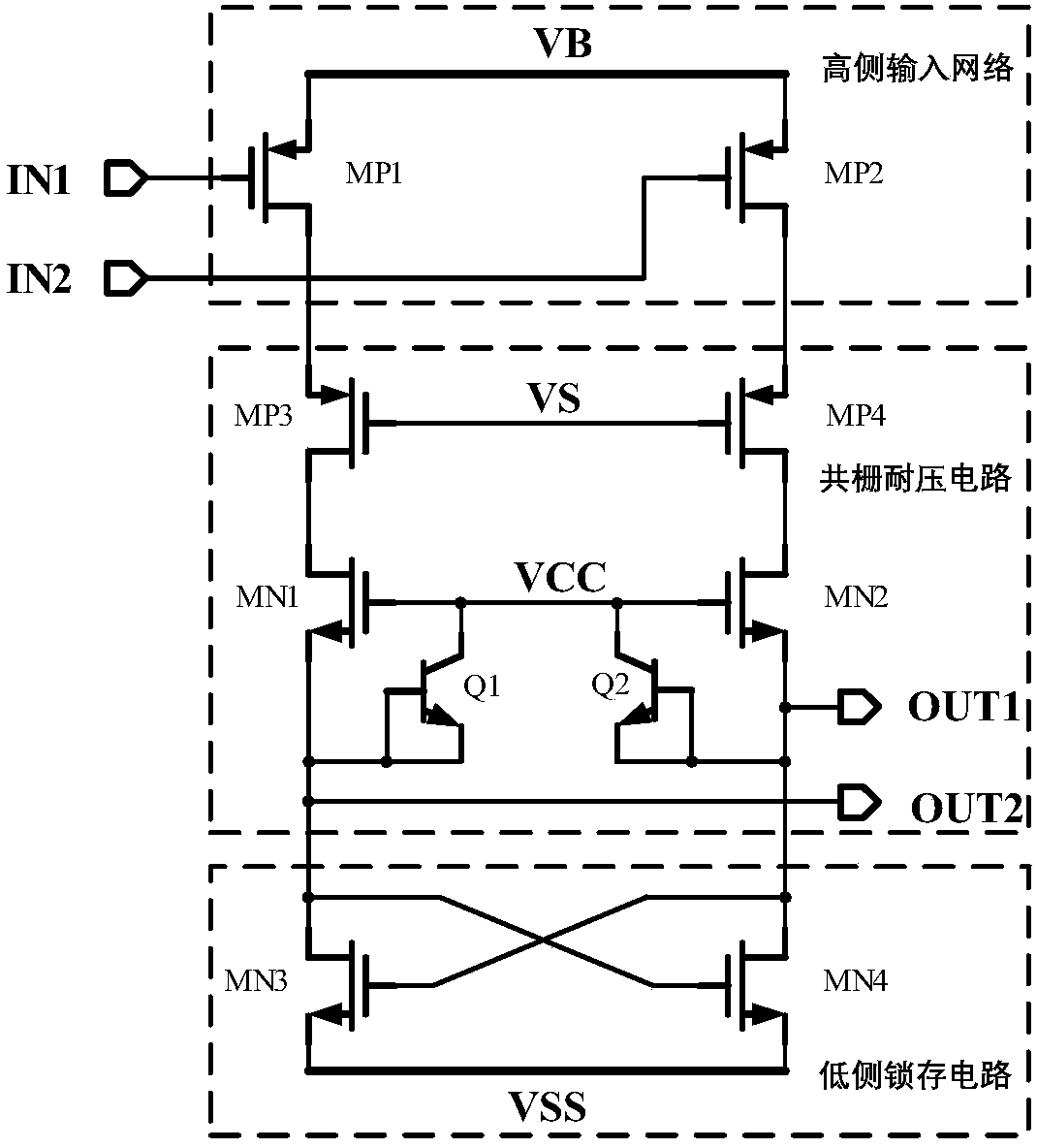
Downlink level shifting circuit with low operating voltage
PendingCN108616269AIncrease grid voltageNormal openLogic circuit interface arrangementsLevel shiftingLow voltage
A downlink level shifting circuit includes a high side input network, a common gate voltage-withstanding structure and a low side latch circuit; the high side input network consists of two parallel PMOS devices of a common source structure, and transmits an input signal to the common gate voltage-withstanding structure; the common gate voltage-withstanding circuit includes a pair of common gate PMOS transistors, a pair of common gate NMOS transistors and two clamp diodes; and the low side latch circuit includes two pairs of NMOS transistors used as linear resistors and a latch structure formedby a pair of cross-coupled NMOS devices, and enables a high-side signal to be transmitted to a low-voltage region when a high-side voltage difference is very small.
Owner:无锡安趋电子有限公司
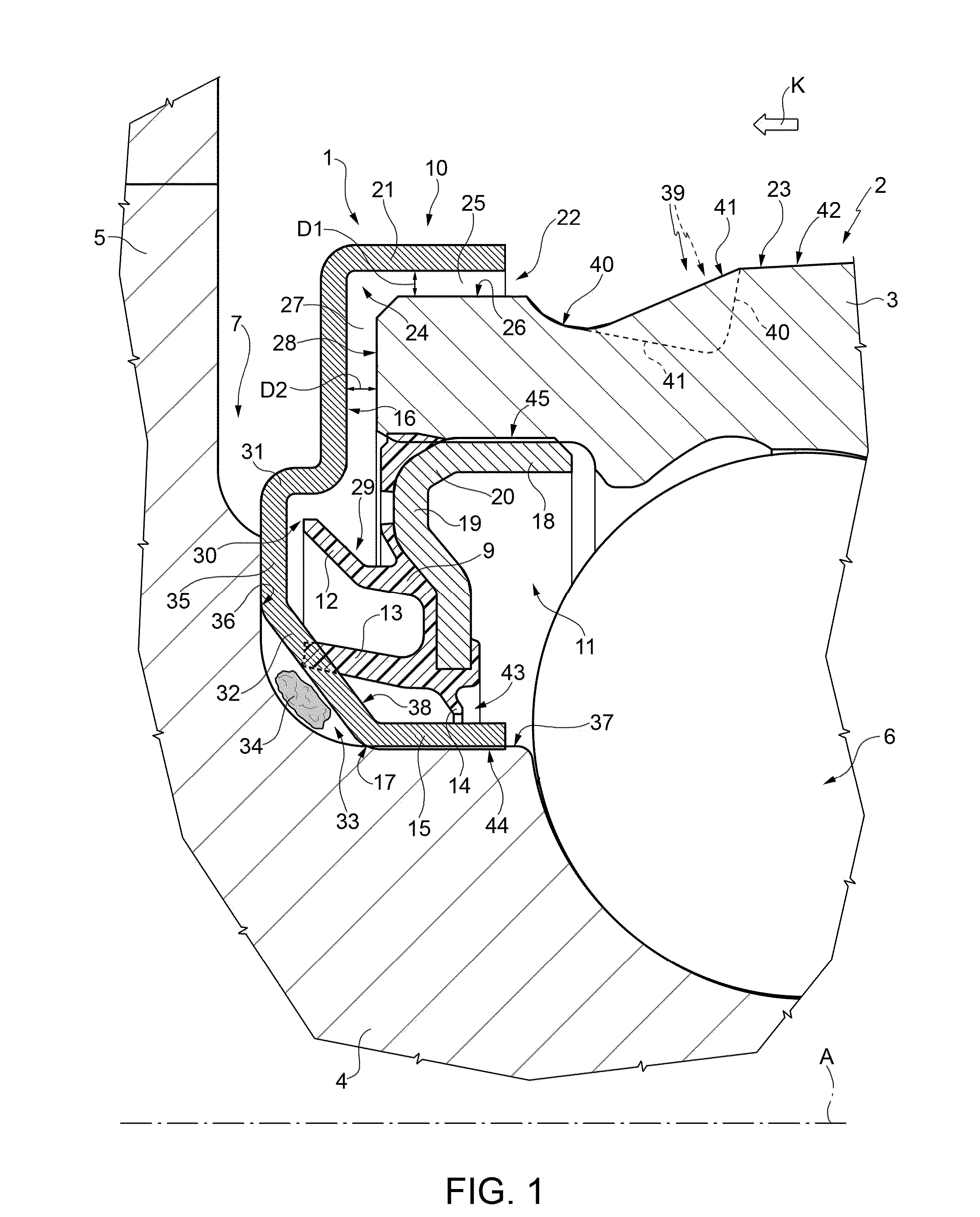
Arrangement of a wheel hub connected to a constant velocity joint provided with a low friction seal device
An arrangement including a first and second sealing assembly disposed between an inner ring and an outer ring of the wheel hub and straddling the wheel hub and an outer ring of a constant velocity joint, and an annular step formed on the side of the constant velocity joint on a radially outer lateral surface of the inner ring, in a position adjacent to a sleeve portion of a first shield of the first sealing assembly from a flange portion radially extends so as to protrude towards the outer ring, the flange portion being provided towards the constant velocity joint with a signal generating element (19) consisting of an annular insert; an end of a tubular core of the second sealing assembly is fitted angularly onto the step and is radially externally provided with an L-shaped edge arranged within the step and radially under the annular insert.
Owner:AB SKF
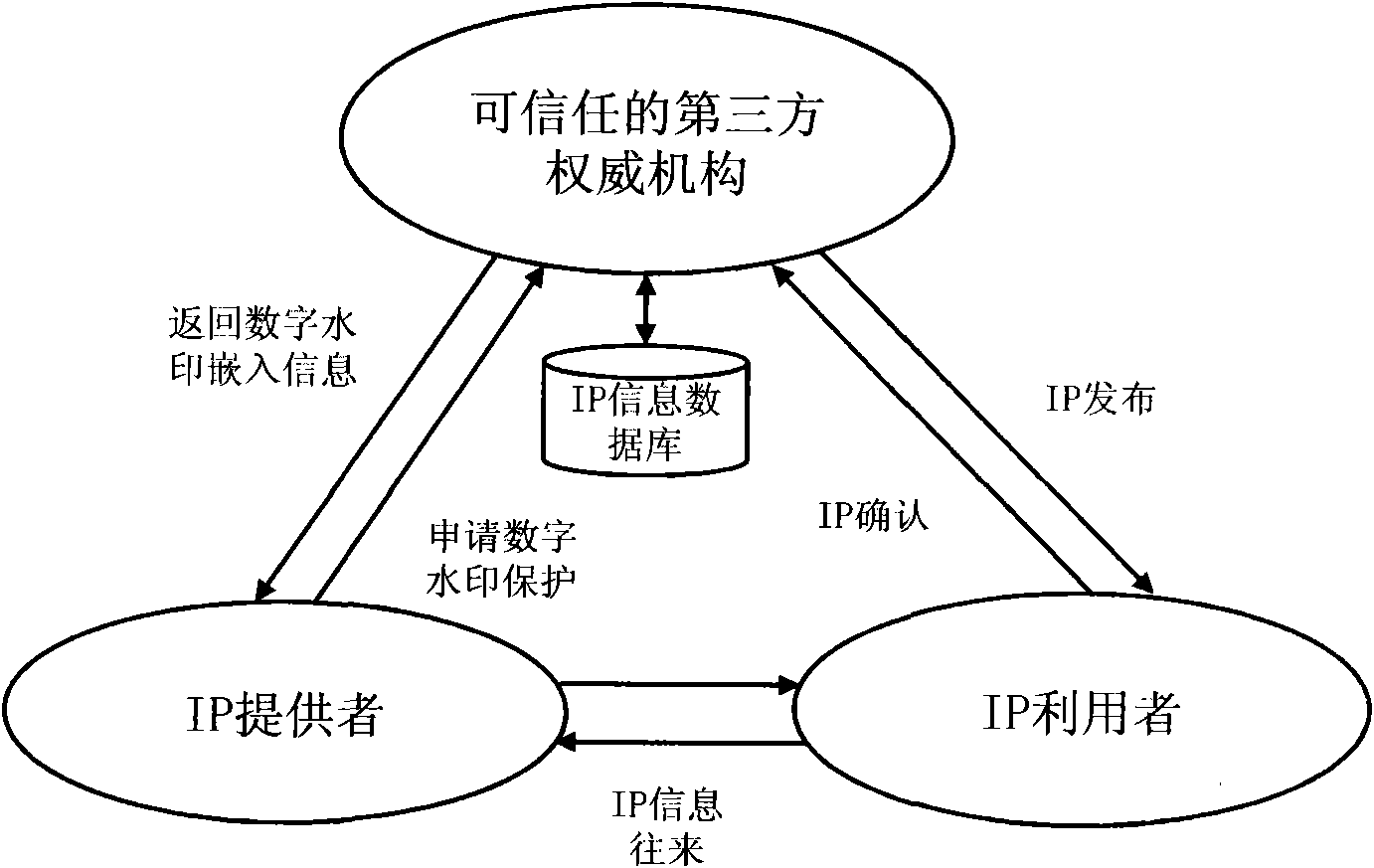
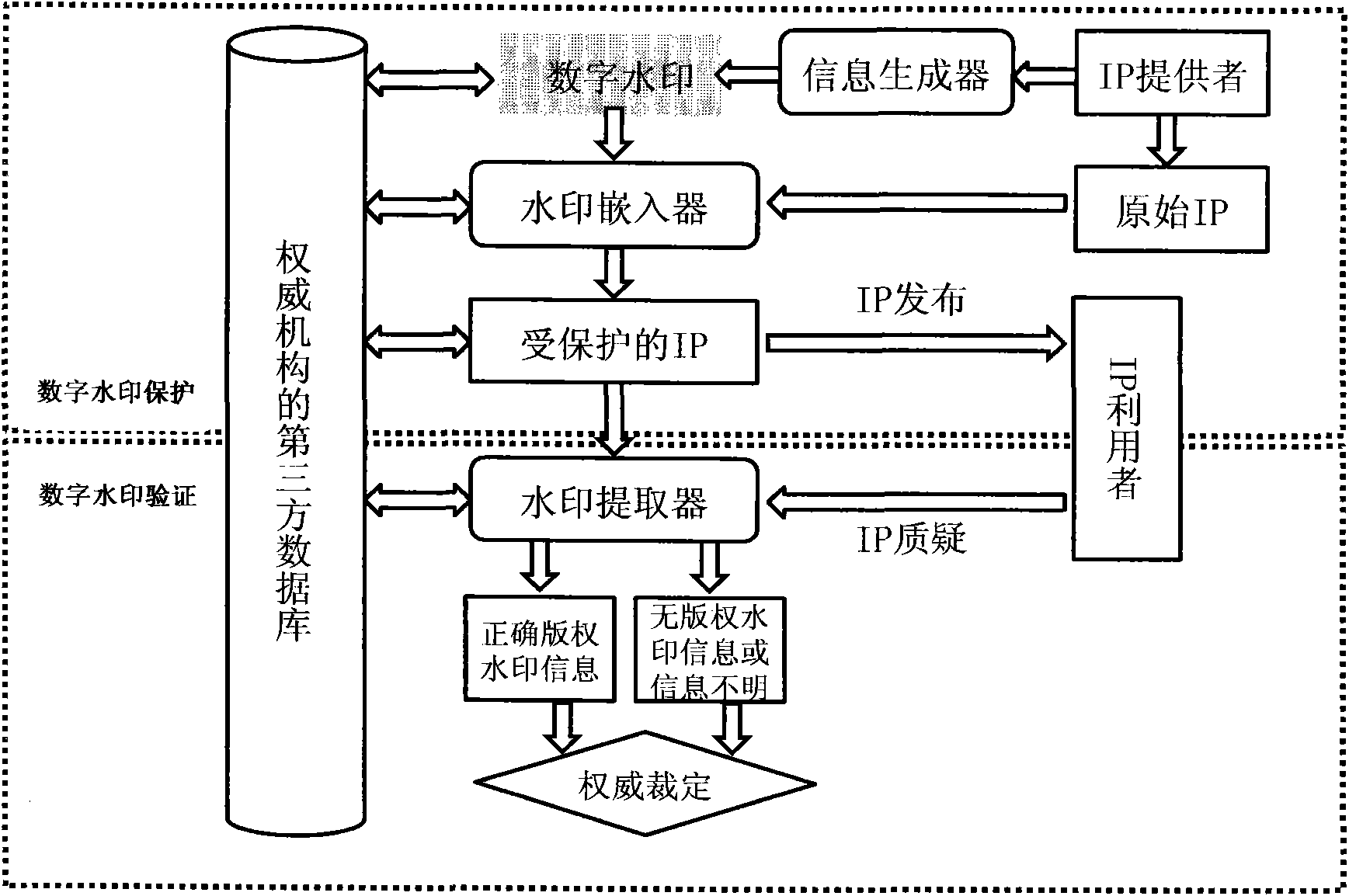
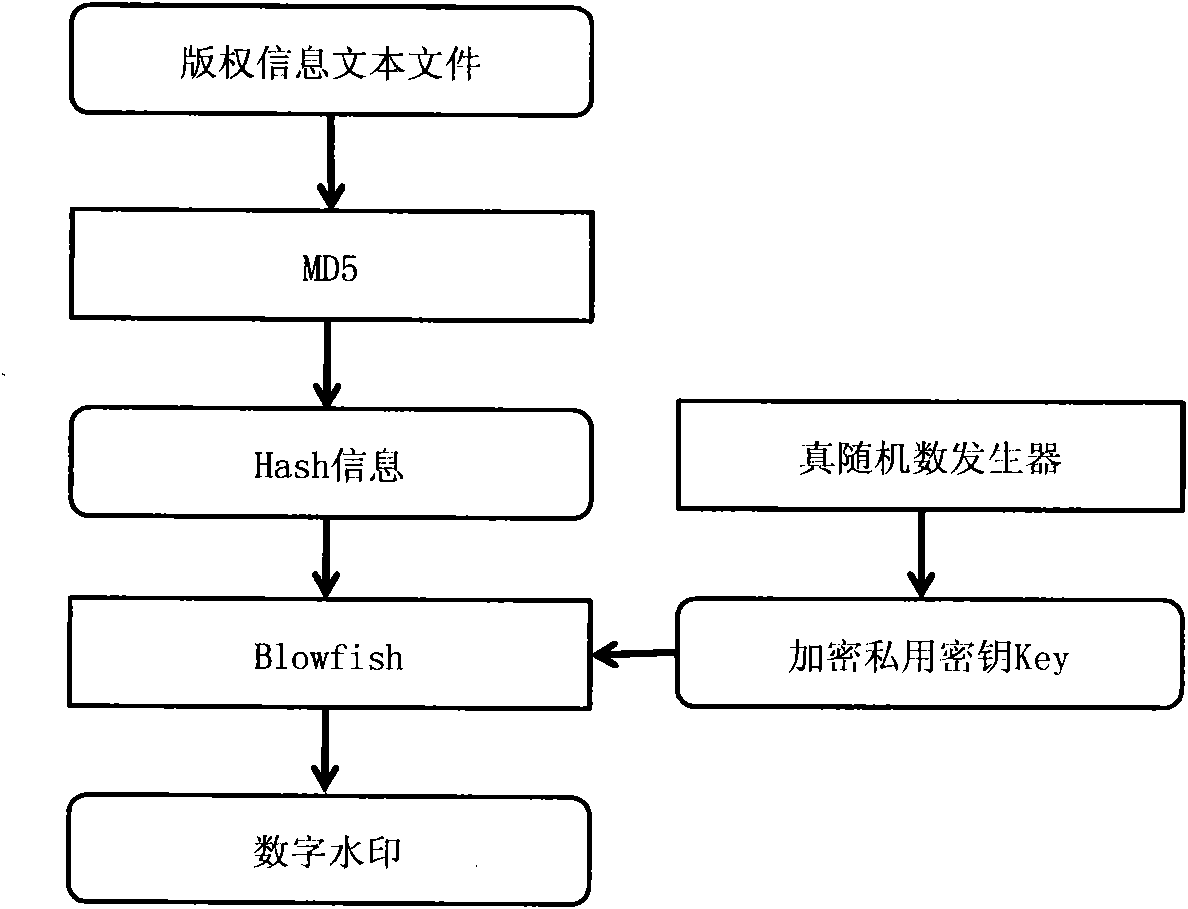
Digital watermarking method
InactiveCN101882297AWith transparencyImprove universalityImage data processing detailsSpecial data processing applicationsRelevant informationData file
The invention provides a digital watermarking method, which protects and checks an IP copyright by means of a digital watermarking technology and has the characteristics of high efficiency, low design cost, low overhead and high feasibility, etc. The technical scheme comprises a watermarking embedding part and a watermarking checking part. The watermarking embedding part comprises the following steps of: encrypting copyright information to generate digital watermarking; selecting a wire net which accords with a carrier for adding a digital watermarking condition in an IP domain territory; changing partial wiring trend of the wire net according to a set constraint condition; passively generating digital watermarking piece information according to the change of the topological structure of a constitutional diagram of the wire net and ambient nodes; normally embedding the piece information into the IP and generating a watermarking secret key after mapping the piece information on the digital watermarking; and outputting a domain territory data file with the digital watermarking information after all digital watermarking information are embedded into the IP. The watermarking checking part comprises the following steps of: extracting correlative information of the IP from a digital watermarking system database; watermarking the secret key and the original IP domain territory data; extracting the wire net from the original IP domain territory data according to the watermarking secret key information; watermarking the wire net with the same method of watermarking embedding; extracting the digital watermarking piece information if structure of the wire net is as the same as that of corresponding wire net in the IP to be checked; synthesizing all digital watermarking piece information to extract the whole digital watermarking information; comparing with the original digital watermarking stored in the database to check the IP and generate an IP copyright checking report.
Owner:QINGDAO TECHNOLOGICAL UNIVERSITY
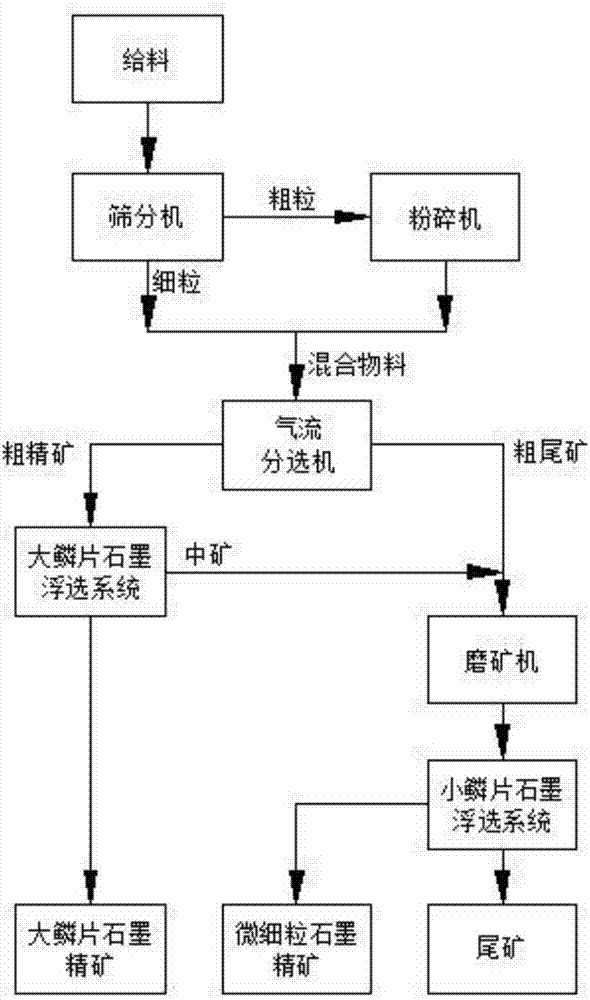
Separation method for flake graphite based on air flow separation and flotation
InactiveCN107321472AImprove protection efficiencyLess investmentSievingScreeningEconomic benefitsMixed materials
The invention relates to a separation method for a flake graphite ore and belongs to the technical field of mineral processing. The separation method is conducted according to the following steps that graphite ore materials are fed into a sieving machine to be graded, and oversize coarse-grained products and undersize fine-grained products are separated; the oversize coarse-grained products are fed into a crusher to be crushed to obtain crushed materials; the crushed materials are mixed with the undersize fine-grained products to obtain mixed materials; the mixed materials are fed into an air flow separator to be separated, and coarse concentrate and coarse tailings are obtained; the coarse concentrate is fed into a large flake graphite flotation system to be finely separated, and large flake graphite concentrate and middling products are separated; the middling products and the coarse tailings are mixed and fed into an ore grinding machine to be subjected grinding-up treatment, and ground coarse tailing products are obtained; and the crushed coarse tailing products are fed into a small flake graphite flotation system to separate fine-grained graphite concentrate and tailings. Compared with the prior art, the separation method for the flake graphite ore based on the air flow separator and a flotation machine has the characteristics of being high in protection efficiency of graphite piece diameters, little in investment, little in environmental pollution, remarkable in economic benefit and the like.
Owner:CHINA UNIV OF MINING & TECH (BEIJING)
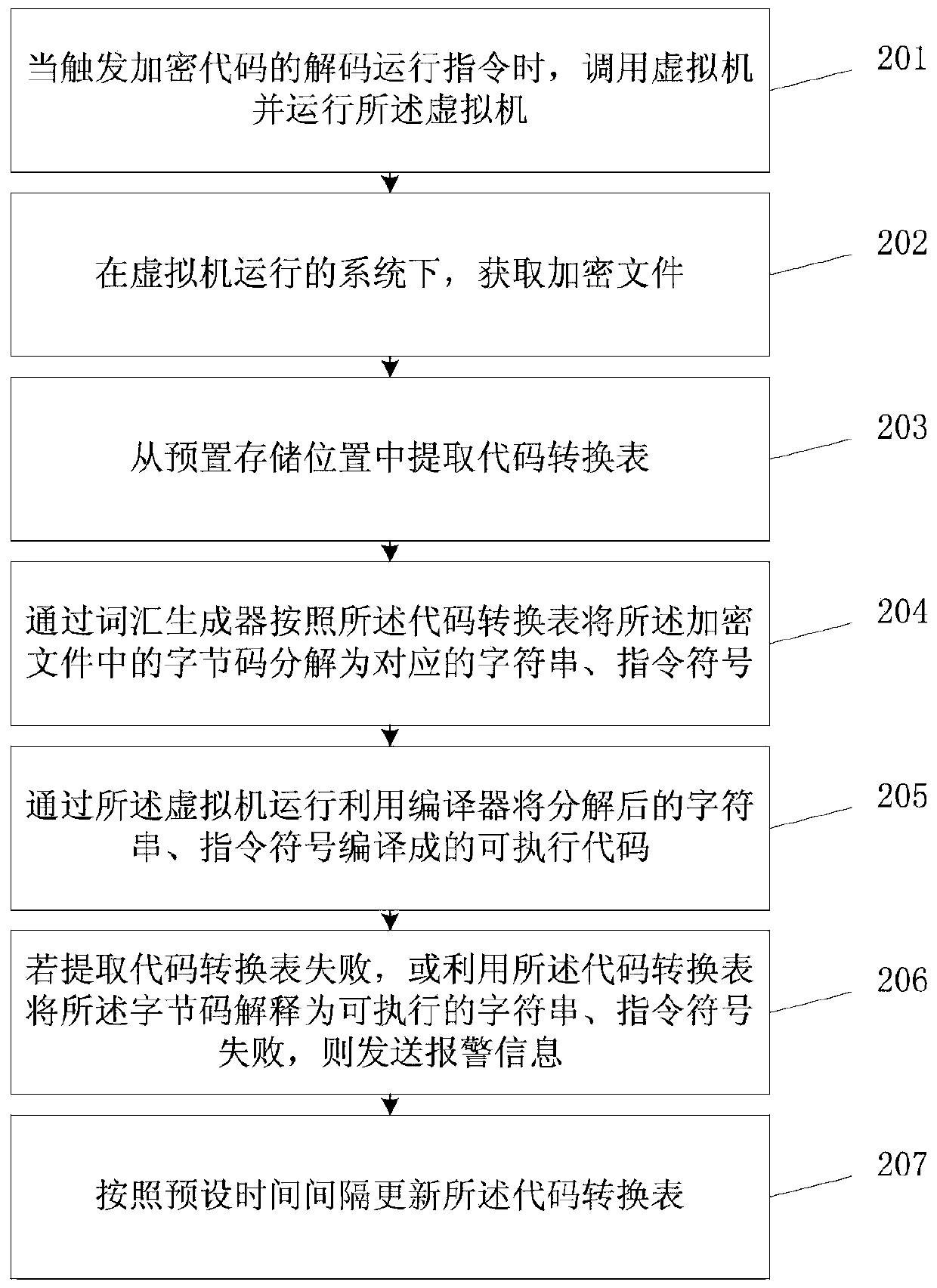
Encrypted code operation method and device, storage medium and terminal
InactiveCN109711119AAchieve normal operationReduce the probability of reverse analysisDigital data protectionProgram/content distribution protectionVirtual machineCode conversion
The invention discloses an encrypted code operation method and device, a storage medium and a terminal, relates to the technical field of information security, and mainly aims to solve the problem that core codes needing to be protected cannot be strictly protected due to the fact that decrypted codes can be obtained through reverse analysis in existing code protection. The method mainly comprisesthe steps that a code conversion table is extracted, the byte codes are interpreted into executable character strings and instruction symbols through the code conversion table, codes corresponding tothe character strings and the instruction symbols are compiled and run through a virtual machine, and the byte codes corresponding to the different character strings and the instruction symbols are stored in the code conversion table. The invention is used for running for encrypted code.
Owner:QI AN XIN SECURITY TECH ZHUHAI CO LTD +1
Construction method for delaying attenuation and increasing expression exogenous antigen salmonella suipestifer carrier through regulation and control of gene
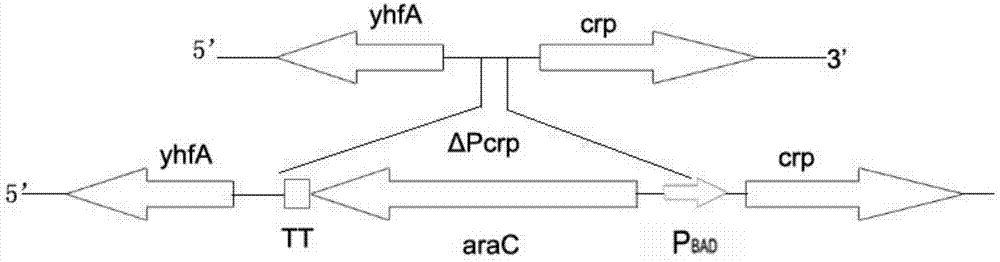
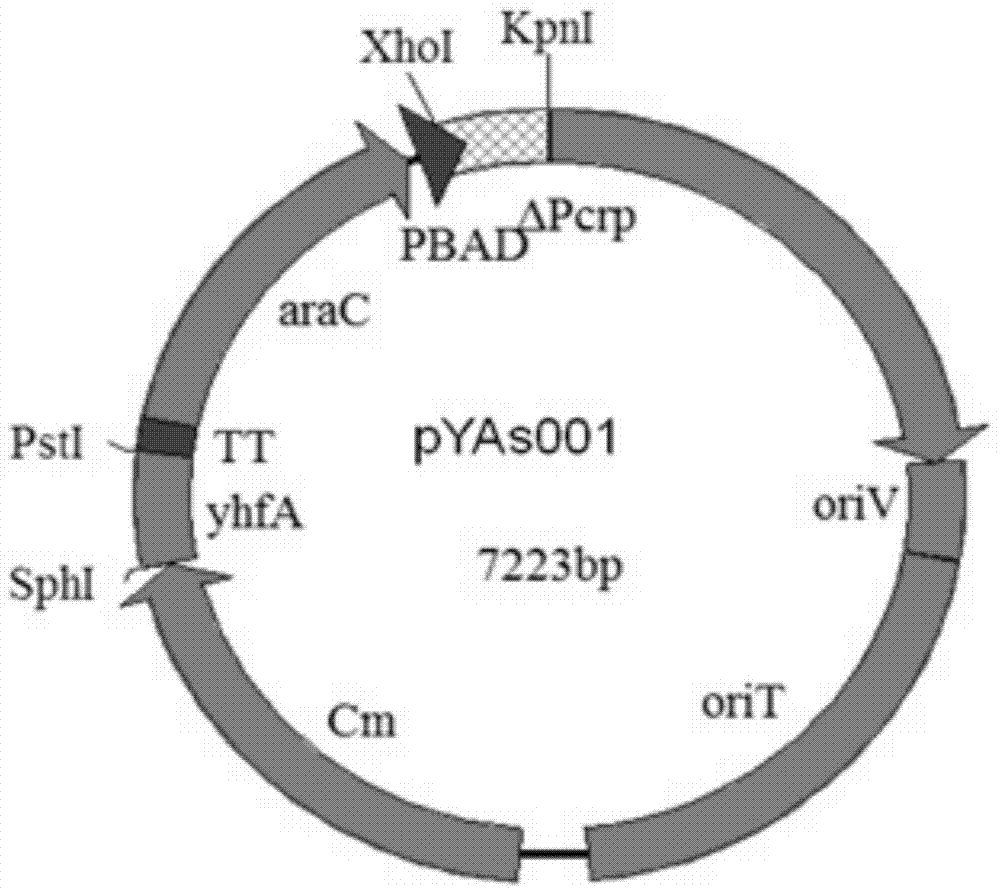
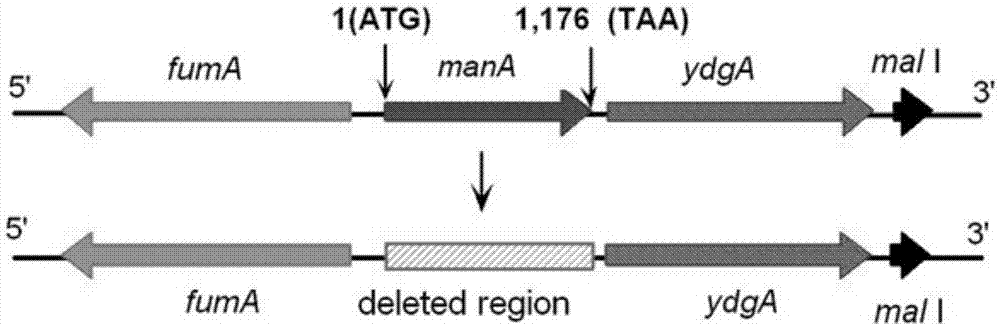
ActiveCN104498418ALarge market applicabilityImmunogenicBacteriaMicroorganism based processesBacteroidesEscherichia coli
The invention provides a construction method for delaying attenuation and increasing an expression exogenous antigen salmonella suipestifer carrier through regulation and control of gene, which is characterized in that receptor bacterium C78-3 is combined with manA, crp, relA and asd -containing deleted suicide carrier escherichia coli donor bacterium, mutants delta manA, delta Pcrp: : TT ara C PBAD crp, delta relA: : araC PBAD lacI TT and delta asd A are introduced in wild-type salmonella suipestifer C78-3, the introduced salmonella suipestifer after mutation can be called x0011; and four types of mutation enable phenotype identification. The method of the invention makes salmonella suipestifer to become safe and effective vaccine carrier of many exogenous antigens; and provides the delaying attenuation and increasing expression exogenous antigen salmonella suipestifer carrier through regulation and control of gene for various pig diseases, especially many bacteria diseases of pig, and has great market applicability.
Owner:YANGZHOU UNIV
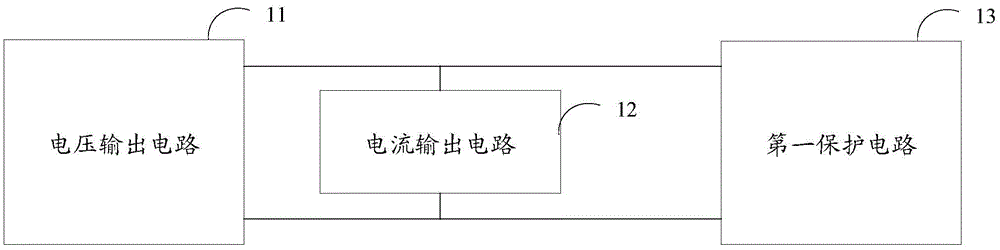
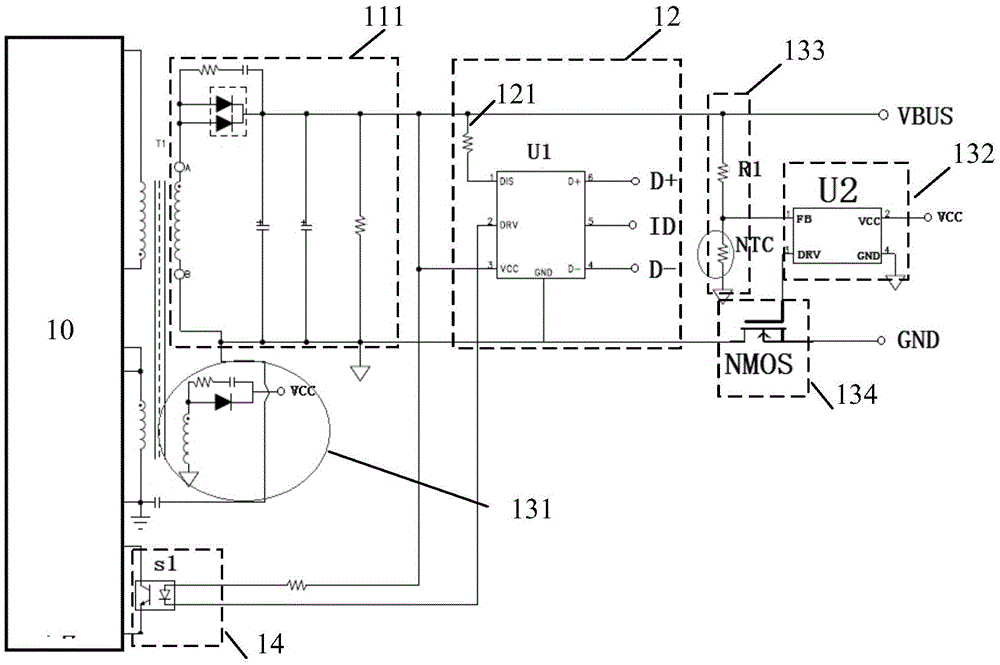
Charging circuit, charger with USB port and charging system
ActiveCN105634092AAvoid burnsShort response timeElectric powerEmergency protective arrangements for automatic disconnectionControl signalTerminal equipment
The invention relates to a charging circuit, a charger with a USB port and a charging system, wherein the charging circuit comprises a voltage output circuit, a current output circuit and a first protective circuit, wherein the voltage output circuit receives an AC input by an AC power supply, carries out voltage transformation and rectifying treatment and outputs a DC to the current output circuit; the current output circuit receives the DC output by the voltage output circuit, carries out filtering treatment on the DC and then outputs the DC to terminal equipment; the first protective circuit is used for detecting whether a voltage on a live wire is greater than or equal to a preset voltage or not and / or a temperature on the liver wire is greater than or equal to a preset temperature or not, and outputting a first control signal to control the voltage output circuit to stop outputting of the DC when the voltage on the live wire is greater than or equal to the preset voltage and / or the temperature on the liver wire is greater than or equal to the preset temperature. Through the technical scheme, burn-out of a charger connector or a terminal mainboard and the like can be avoided; the response time of the cycle can be shortened; and the protection efficiency is improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Colon bacillus outer membrane protein monoclonal antibody and preparation method and application thereof
ActiveCN102584992AStrong specificityIncreased sensitivityAntibacterial agentsImmunoglobulins against bacteriaESCHERICHIA COLI ANTIGENBALB/c
The invention belongs to the technical field of veterinary biology, and particularly relates to a colon bacillus outer membrane protein monoclonal antibody and a preparation method and an application thereof. The antibody is prepared by taking cloned, expressed and purified taking avian pathogenic escherichia coli 78 (APECO78) outer membrane protein as an antigen immune BALB / c mouse with a hybrid tumor technology. The antibody has high specificity and high sensitivity, and an experimental basis is laid for future rapid and specific detection of colon bacillus infection with an immunology method. Meanwhile, as proved by an experiment, the monoclonal antibody disclosed by the invention has high neutralizing activity and protecting efficiency on colon bacillus infection of the same type, and can be used for preventing colibacillosis.
Owner:兆丰华生物科技(南京)有限公司 +1
Anti-shrimp white spot syndrome virus recombined bacterium typhosum strain, preparation and uses thereof
InactiveCN101293931AImprove protection efficiencyImprove immunityBacteriaBacteria material medical ingredientsCompetent cellTyphimurium strain
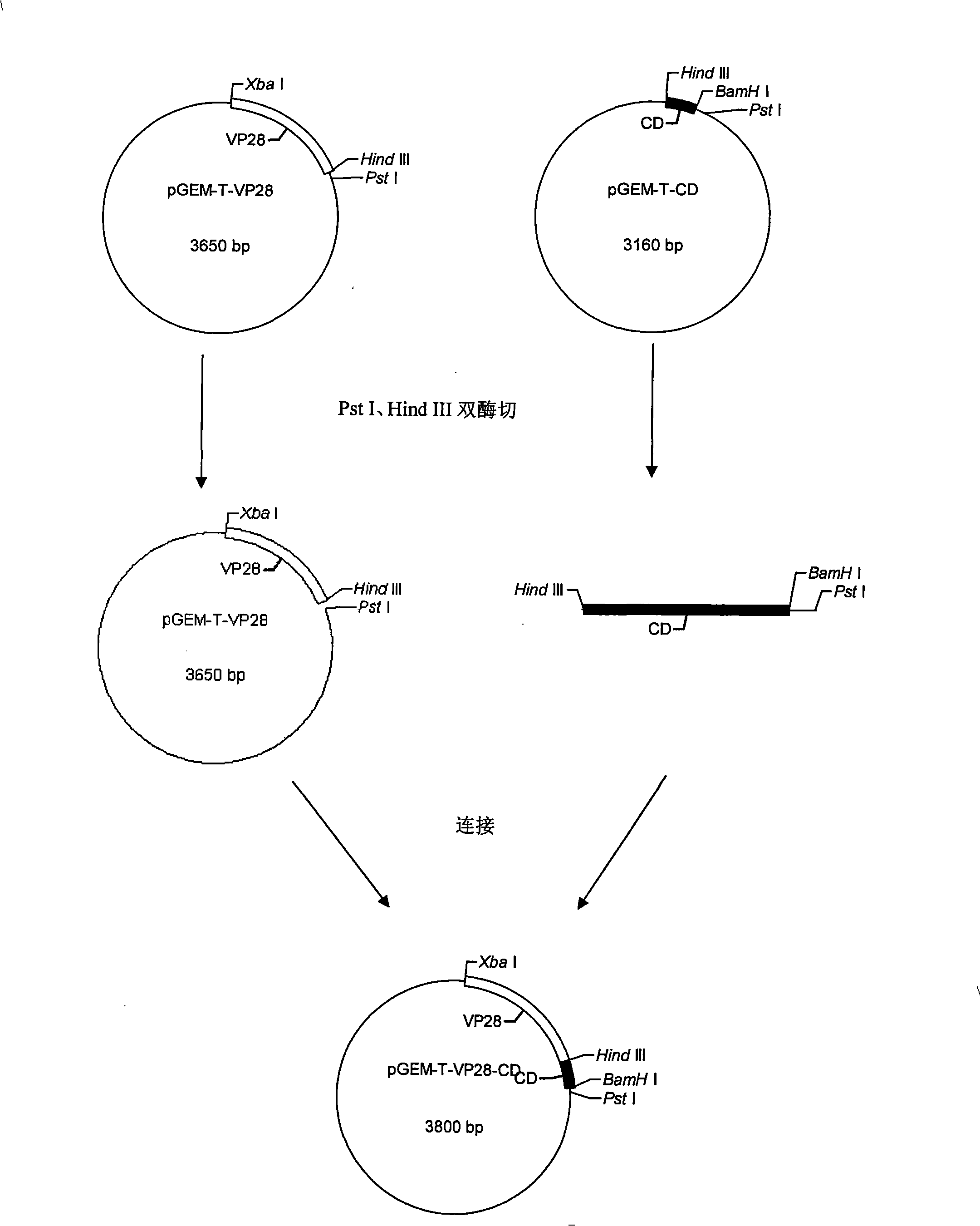
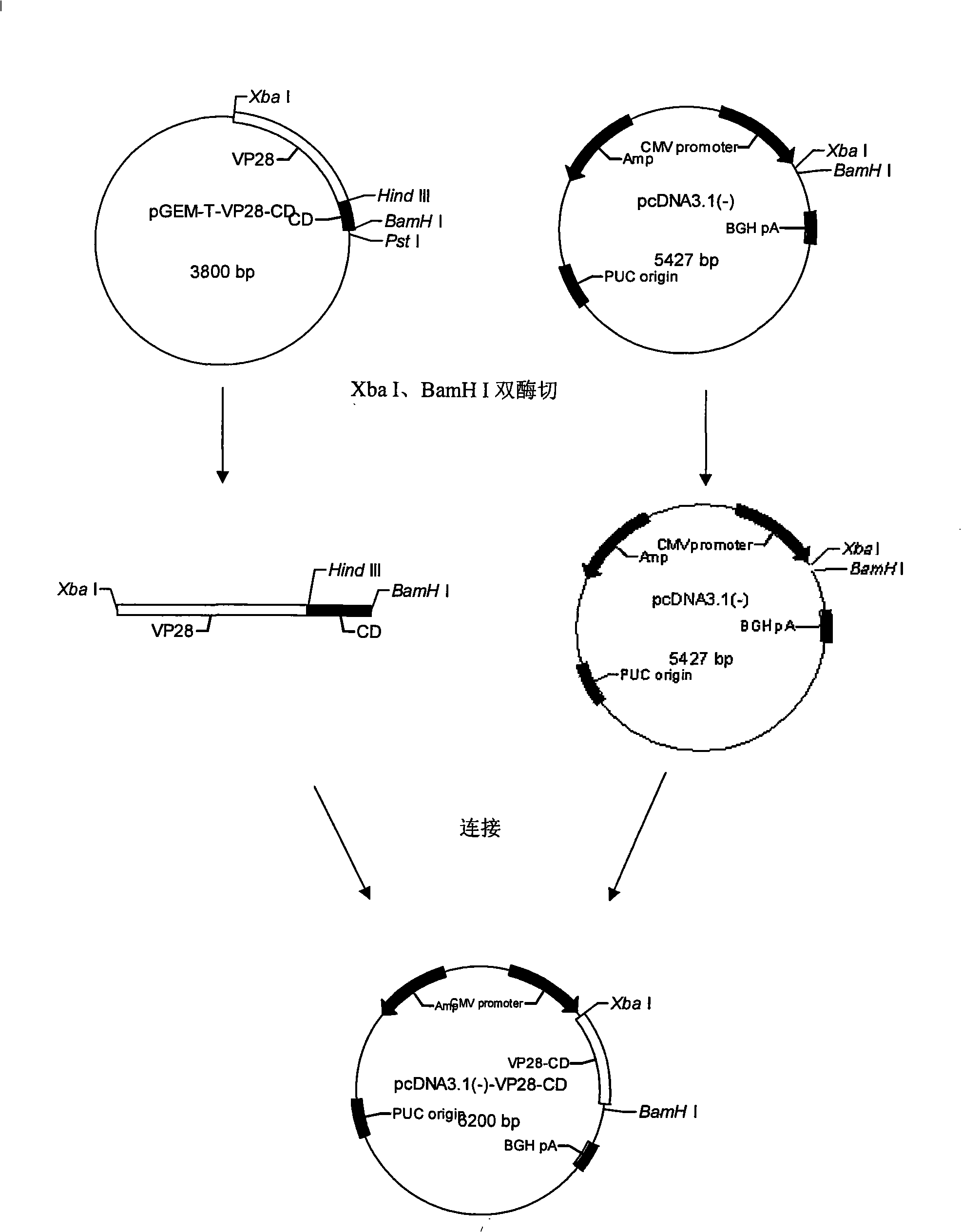
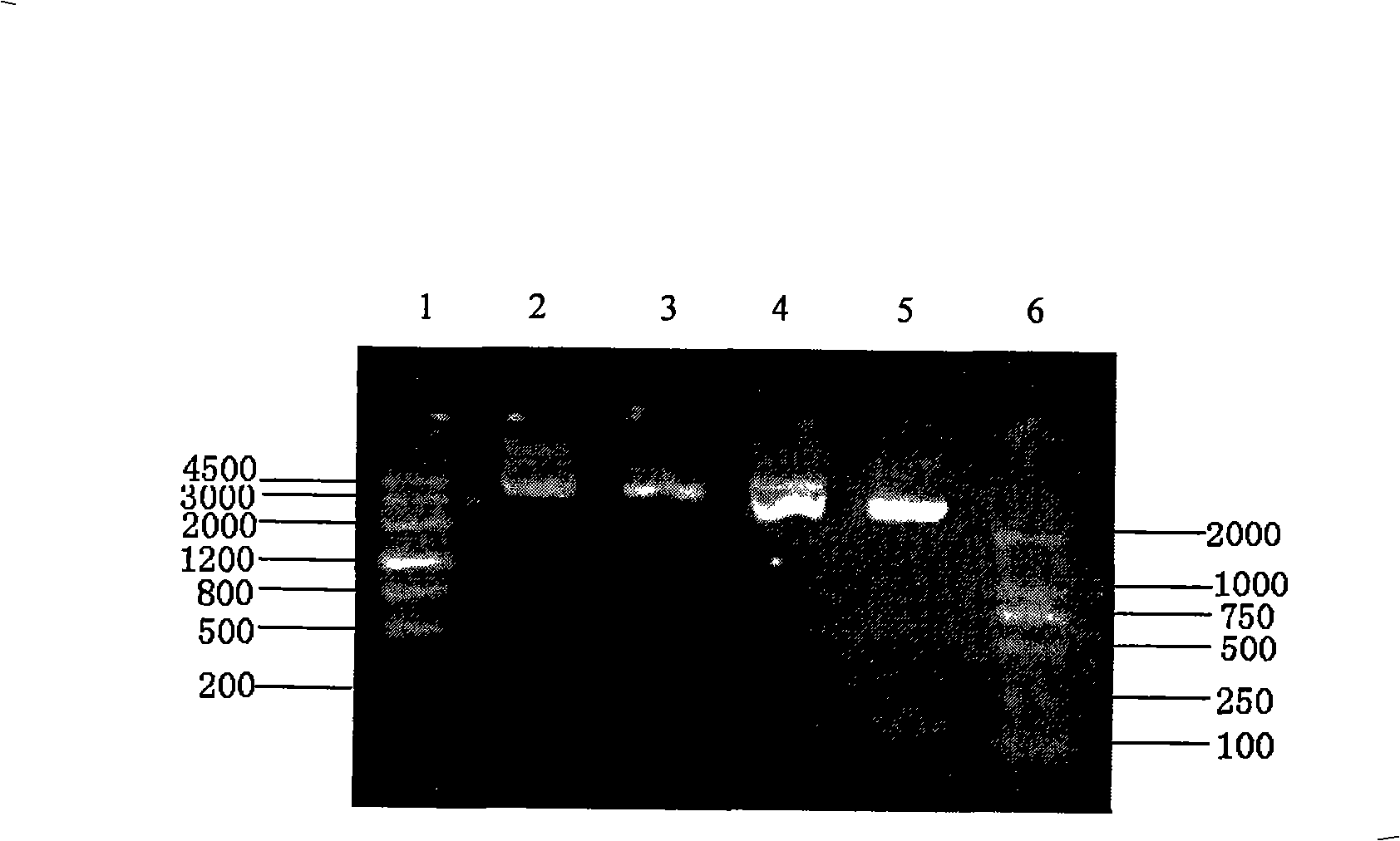
The invention discloses an anti-prawn white spot syndrome virus (WSSV) recombinant Salmonella typhimurium strain, and a preparation method and an application thereof. The preparation method comprises the steps of: extracting WSSV genomic DNA from an infected prawn, and obtaining WSSV envelope protein VP28 genes by a PCR method; extracting total RNA from a silkworm fat body, and obtaining silkworm antimicrobial peptide CD genes by a reverse transcription PCR method; constructing an eukaryotic expression plasmid pcDNA3.1(-)-VP28-CD containing the WSSV envelope protein VP28 genes and the silkworm antimicrobial peptide CD genes; and transforming into attenuated Salmonella typhimurium W0420 strain competent cells. The WSSV recombinant Salmonella typhimurium strain can be used for preparing a vaccine, which can be directly orally fed prawns. Compared with the current commonly used protein vaccines and injectable DNA vaccines, the inventive vaccine has double functions of inhibiting WSSV infection and enhancing prawn immunity.
Owner:施成华
Brucellosis nucleic acid vaccine
InactiveCN101020064AImprove protection efficiencyRaise the level of responseAntibacterial agentsBacterial antigen ingredientsNucleotideActive component
The present invention discloses one kind of Brucellosis nucleic acid vaccine. The active component of the vaccine is one of the following mixture: 1. the mixture of at least two of the recombinant containing BCSP31 gene, the recombinant containing sodC gene and the recombinant containing L7 / L12 gene obtained through cloning BCSP31, sodC and L7 / L12 gene separately into eukarotic cell expression vector; and 2. the mixture of at least two of recombinant expression vectors obtained through fusing BCSP31, sodC and L7 / L12 gene separately with other nucleic acid sequence or deleting partial sequence or mutating partial nucleotides to obtain nucleotide sequence coding protein with the same activity as that of BCSP31, sodC and L7 / L12 gene and cloning separately to the eukarotic cell expression vector. The vaccine of the present invention may be used in preventing brucellosis of human body and animal.
Owner:PEKING UNIV
Tree protection device and real-time monitoring system
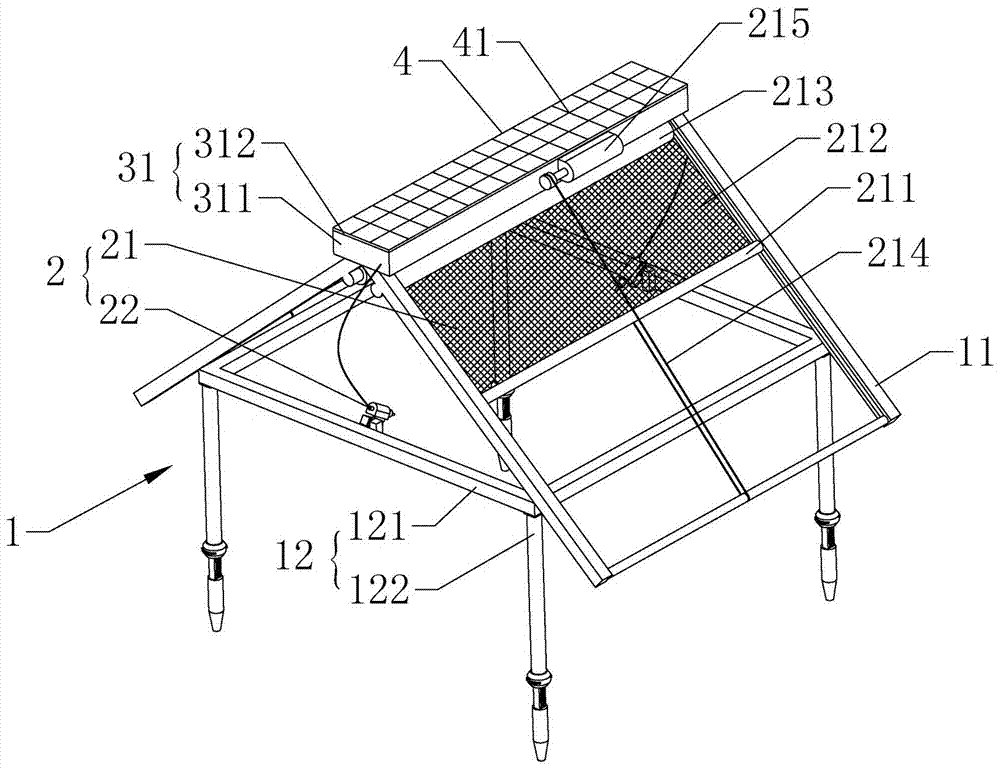
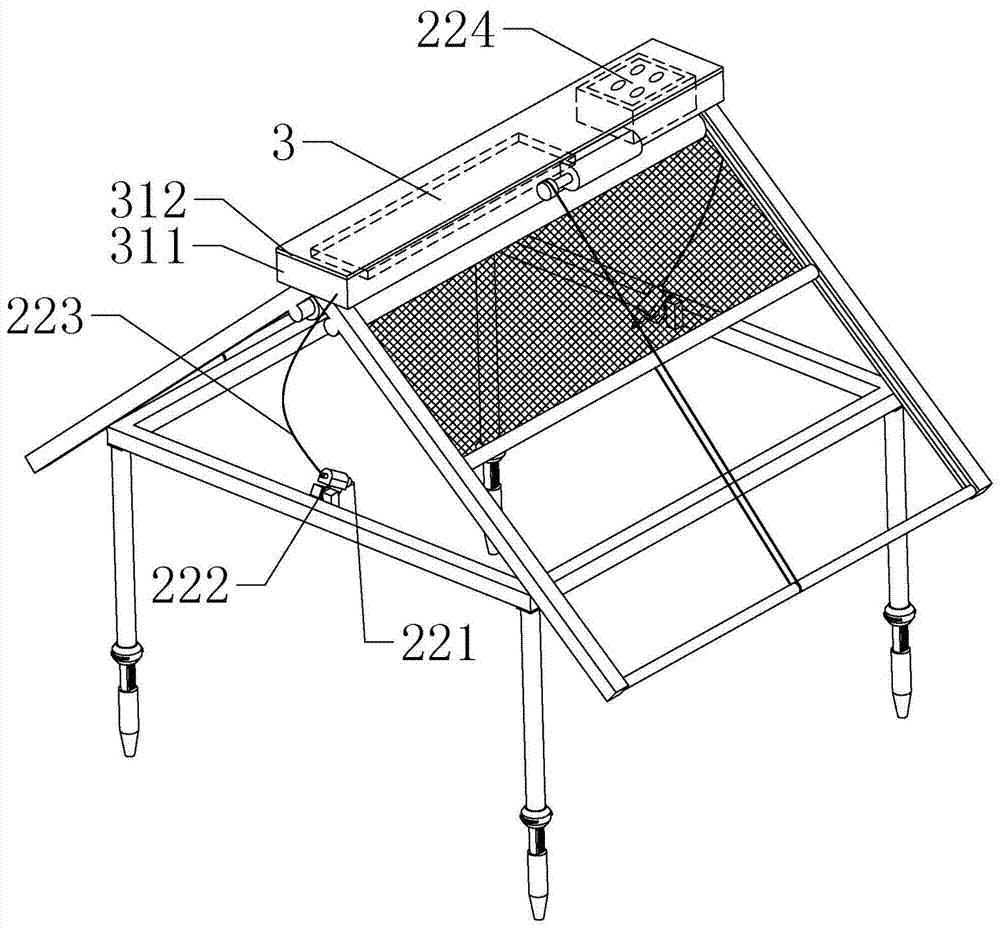
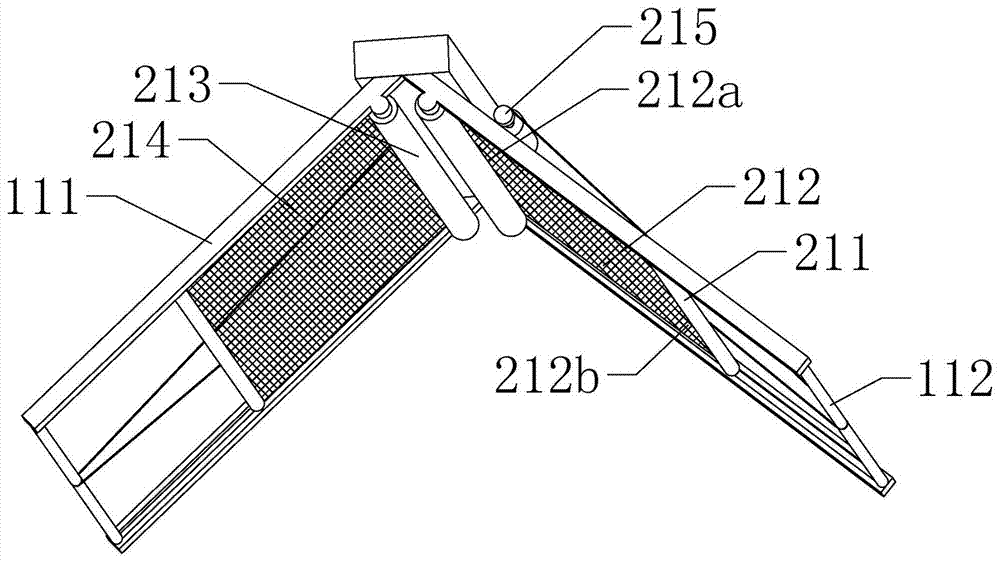
The invention relates to the field of plant protection, in particular to a tree protection device and a real-time monitoring system. The tree protection device includes a protection bracket, an execution part, a regulation and control part and a power supply part; the protection bracket includes a overhead guard and a supporting frame; the execution part includes a sun shading mechanism and a watering mechanism; the regulation and control part includes a regulation and control box, a controller, a sensor module and a communication module, wherein the controller, the sensor module and the communication module are installed in the regulation and control box; the sensor module includes a temperature sensing module, a humidity sensing module, a smoke sensing module, an infrared sensing module and a tilt module, and each module of the sensor module are correspondingly connected with a temperature sensor, a humidity sensor, a smoke sensor, an infrared sensor and a horizontal gyroscope respectively. The real-time monitoring system includes the tree protection device, a data center and a maintenance unit.
Owner:HUZHOU WUXING EXPERIMENTAL MIDDLE SCHOOL
A message processing method of an anti-rejection cloud protection system
InactiveCN109088878AImprove protection efficiencyImprove the protective effectTransmissionTraffic capacityMessage processing
The invention relates to the technical field of network cloud security protection, in particular to a message processing method of an anti-rejection cloud protection system, comprising the steps of: acloud protection device accepts a client message processing; an end device accepts a message processing of the cloud protection device; an end device accepts a server message processing; and the cloud protection device accepts a message processing of the end device. The invention has the advantages of: Cleaned traffic is forwarded from the cloud to the server, before reaching the server, after the end equipment is processed and then sent to the server, the message returned by the server is first processed by the end device and sent to the cloud, after cleaning from the cloud, it is sent to the customer to realize the joint defense between the cloud protection equipment and the end equipment. The user server can realize the smooth over defense without any modification. It supports IPv4 / IPv6 protocol suite and all TCP / IP protocol protection.
Owner:ANHUI ZHONGXIN SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com