User account protection method and user account protection device
A technology for user accounts and users, applied in the field of computer communication, can solve the problems of inability to change passwords, cumbersome operations to change passwords, leakage, etc., and achieve the effect of improving protection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
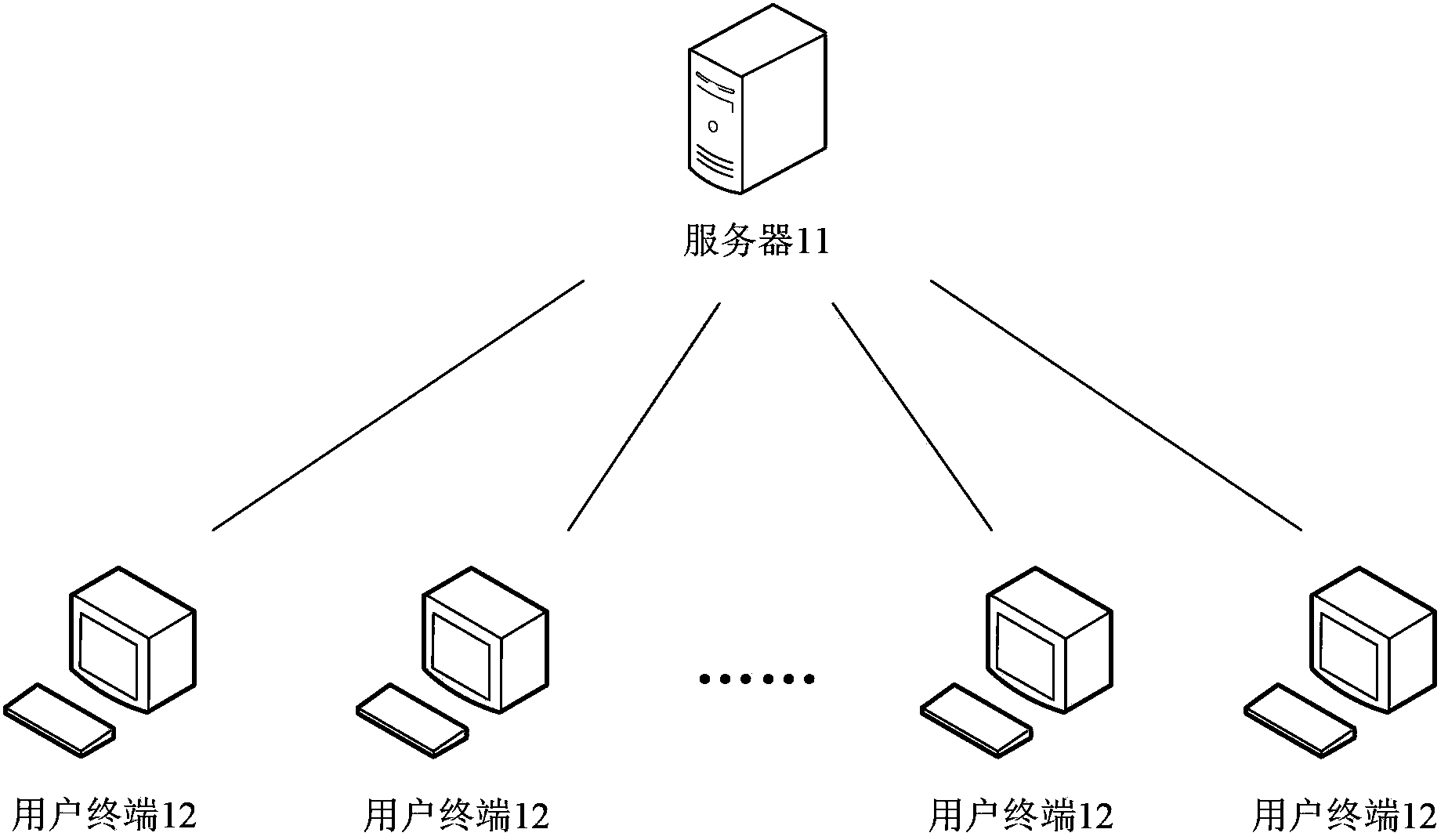
[0021] see figure 1 , shows an application environment diagram of the method for protecting a user account provided by the first embodiment of the present invention. Such as figure 1 As shown, the server 11 and the user terminal 12 are located in a wireless or wired network, and the server 11 and the user terminal 12 communicate with each other through the wireless or wired network.
[0022] User terminal 12 can include smart phone, tablet computer, e-book reader, MP3 player (Moving Picture Experts Group Audio Layer III, moving picture expert compression standard audio level 3), MP4 (Moving Picture Experts Group Audio Layer IV, moving picture Expert Compression Standard Audio Level 4) Players, Laptops and Desktops, etc.
[0023] see figure 2 , shows a flow chart of the method for protecting a user account provided by the first embodiment of the present invention. combine figure 1 The method for protecting a user account provided by this embodiment includes the following ...
no. 2 example
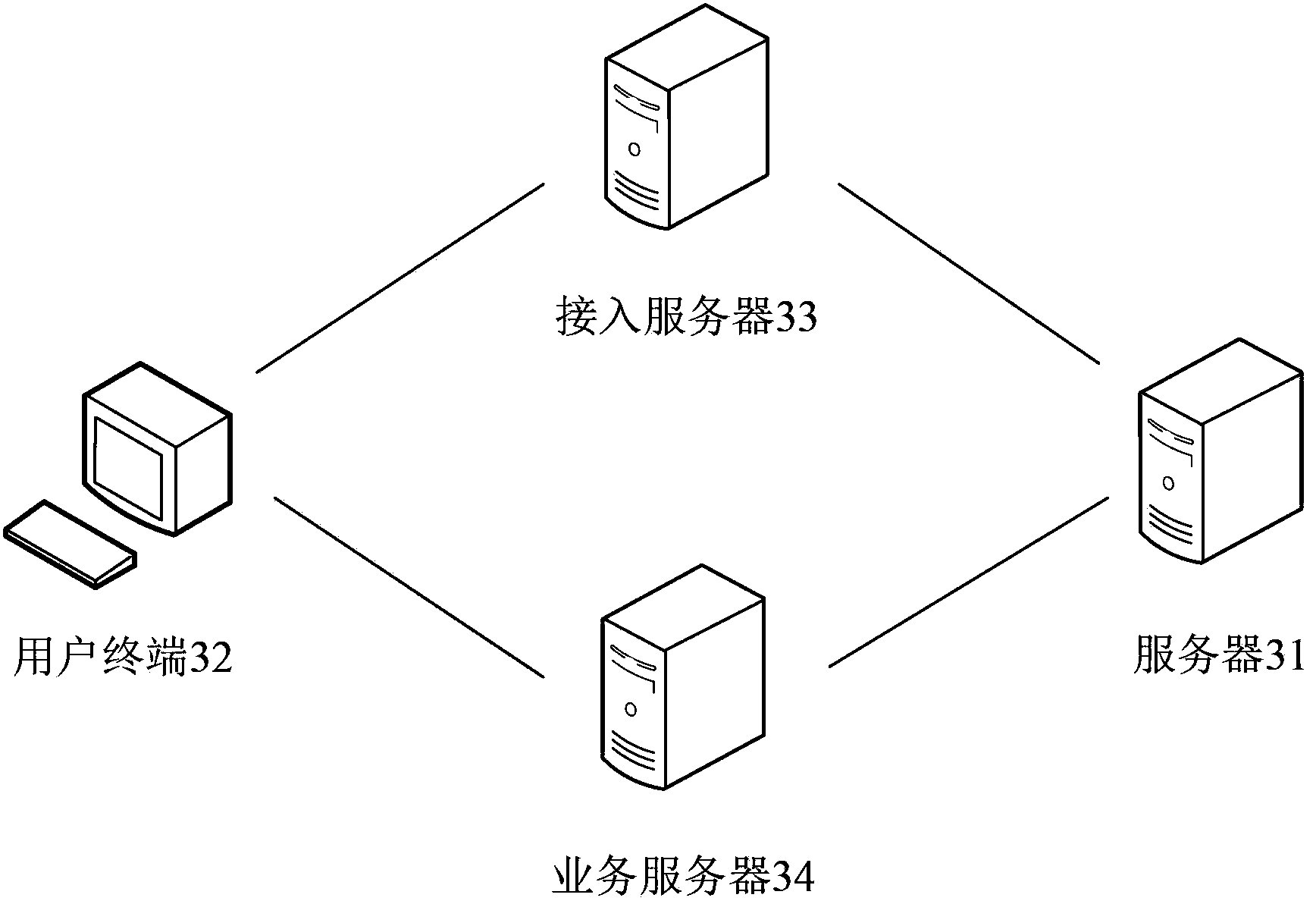
[0032] see image 3 , shows an application environment diagram of the method for protecting a user account provided by the second embodiment of the present invention. Such as image 3 As shown, the server 31, the user terminal 32, the access server 33, and the service server 34 are located in a wireless or wired network, and through the wireless or wired network, the above-mentioned server 31, user terminal 32, access server 33, and service server 34 communicate with each other.
[0033] It can be understood that the above-mentioned server 31, access server 33, and service server 34 may be a single server, or may be a server cluster composed of multiple servers.
[0034] see Figure 4 , shows a flow chart of the method for protecting a user account provided by the second embodiment of the present invention. combine image 3 The method for protecting a user account provided by this embodiment includes the following steps:
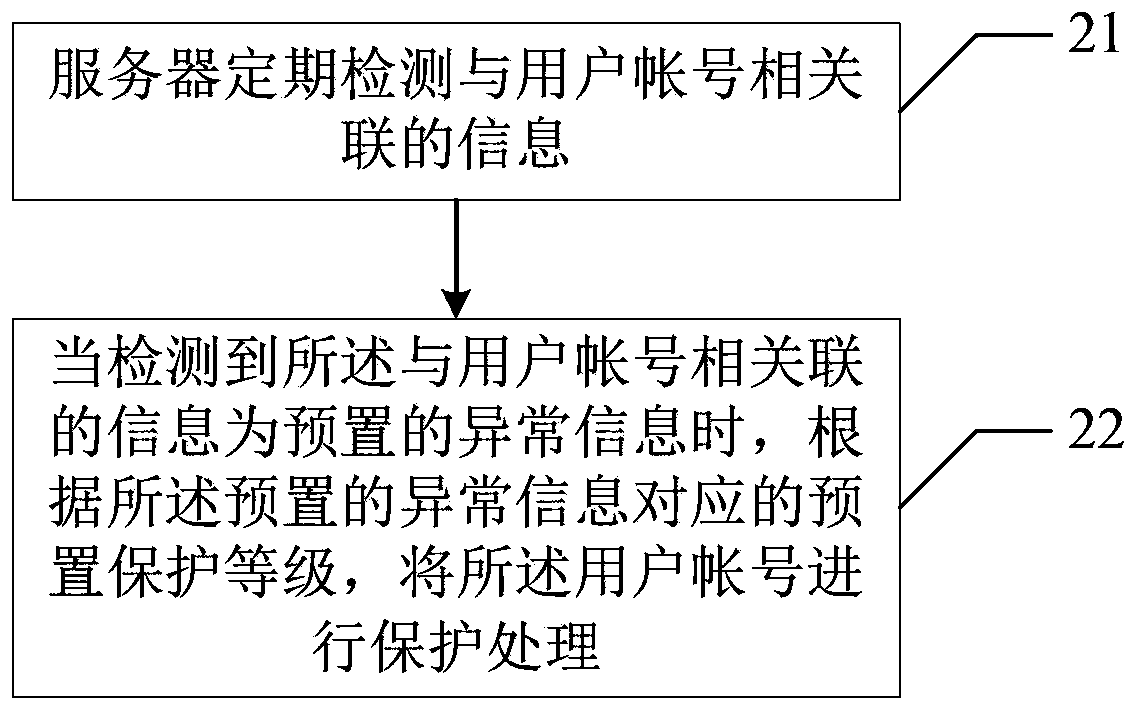
[0035] Step 41, the server periodically detects ...
no. 3 example
[0047] see Figure 5 , shows a flow chart of the method for protecting a user account provided by the third embodiment of the present invention. This embodiment can also be applied to figure 2 shown in the application environment, combined with figure 2 ,Such as Figure 5 As shown, the user account protection method provided in this embodiment includes the following steps:
[0048] Step 51, the server periodically detects the information associated with the user account.
[0049] The information associated with the user account includes security information of the user account and the corresponding password, that is, leakage information of the user account and the corresponding password. Specifically, the server 31 regularly detects whether the user account database is attacked by hackers and whether the data information in the user account database is stolen by others, so as to detect whether the user account and the corresponding password are leaked. It can be underst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com