Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31results about How to "Guaranteed transactional" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
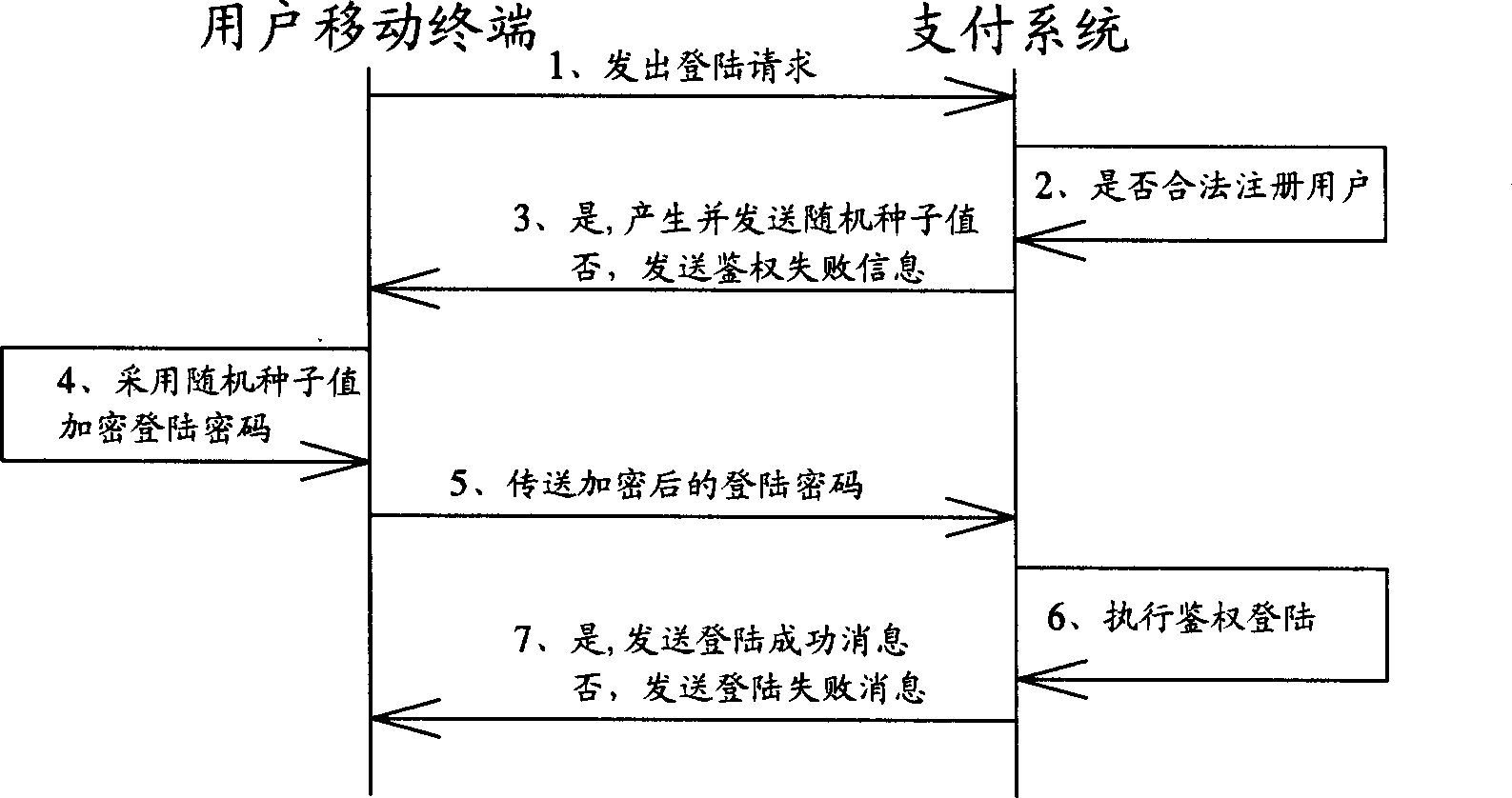
Mobile-terminal-based general transaction method and its system
InactiveCN1776732APrevent theftEnsure safetyFinancePayment architectureEmbedded systemPayment system
Purpose of the invention is to disclose secure general transaction system, which is capable of connecting to multiple bank system and diversified mobile terminals. Thus, mobile terminal possesses payment function and function of collection of payment. Main technique is to setup payment system between mobile terminal and bank system. Through payment system, mobile terminal can connect to multiple bank system to implement transaction. Through the payment system, security of transaction is guaranteed.
Owner:肖勇 +1
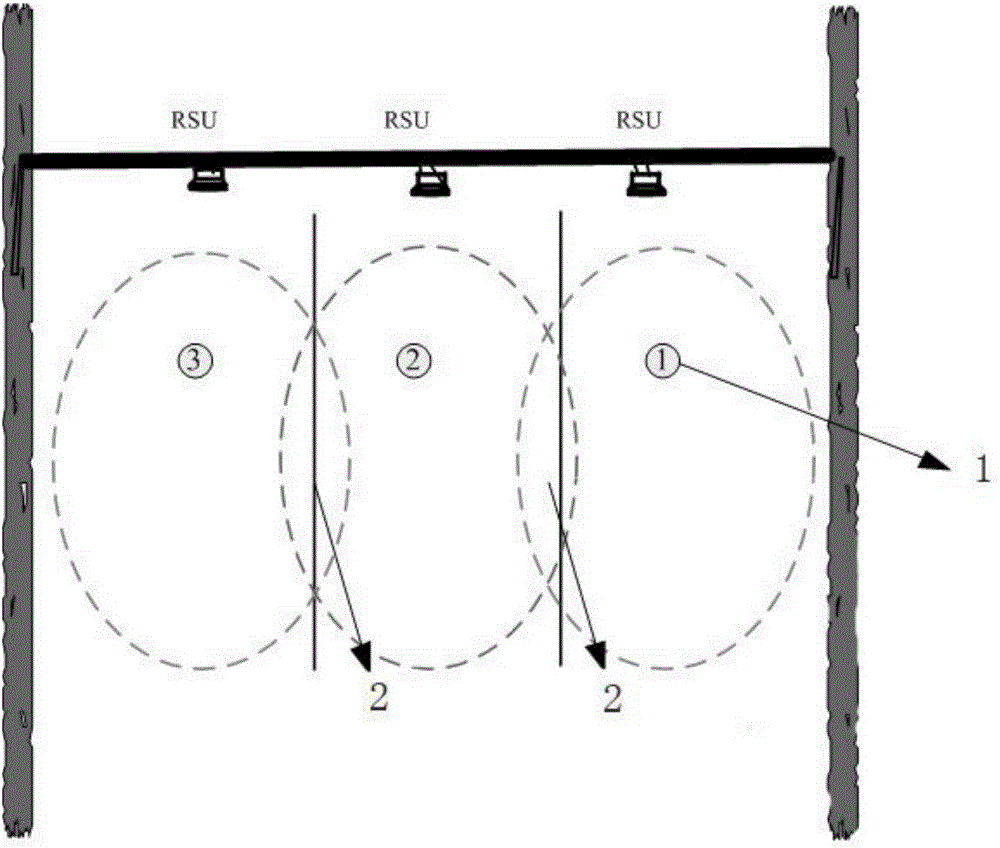
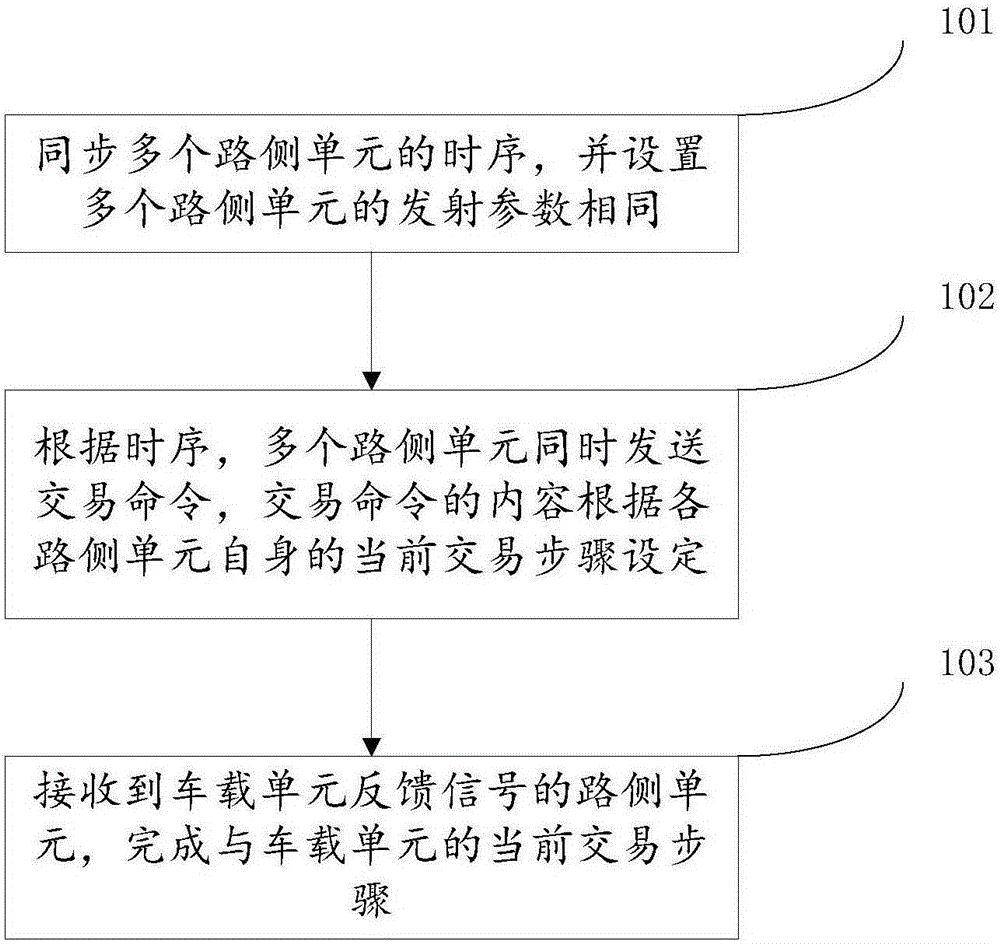
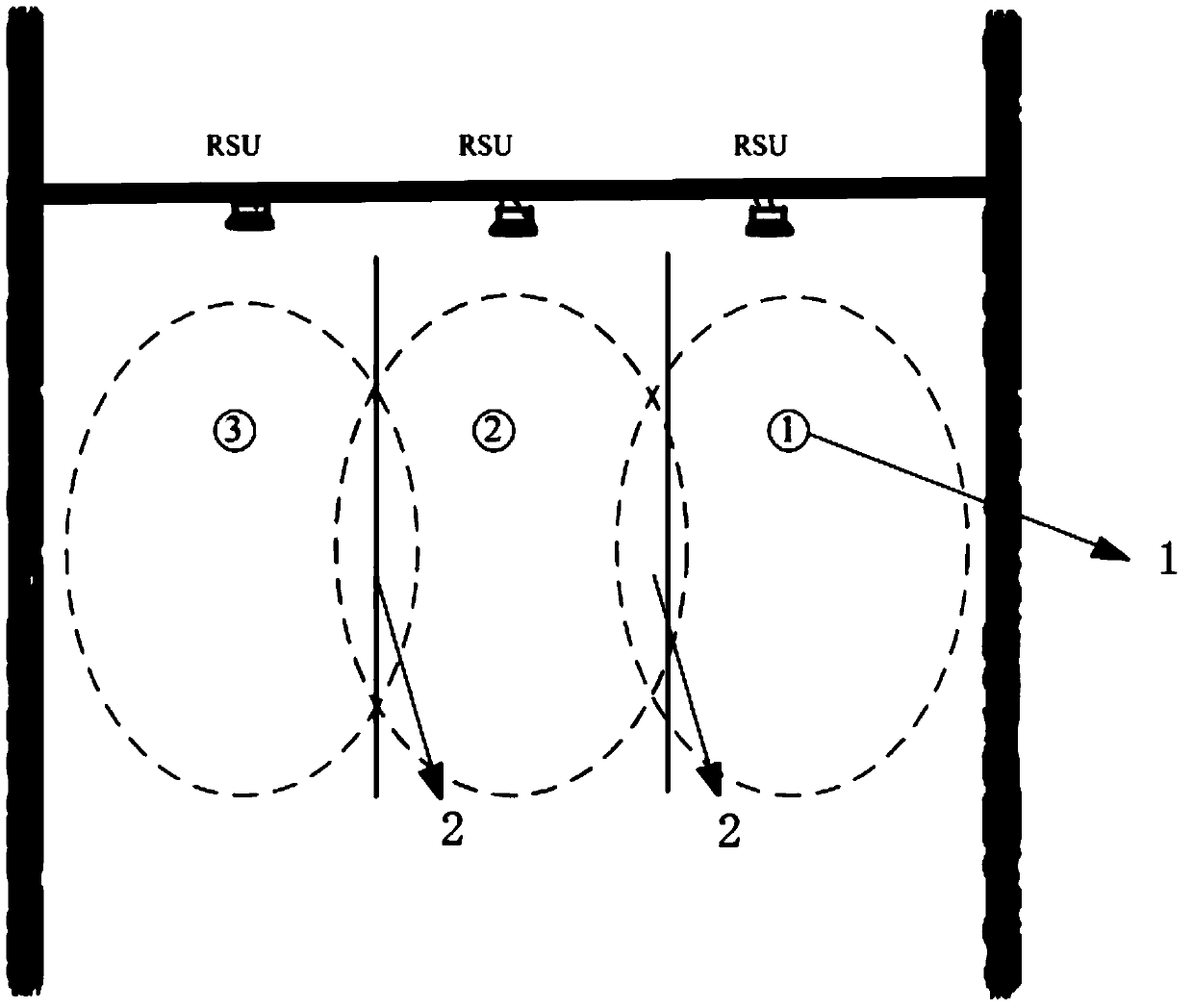
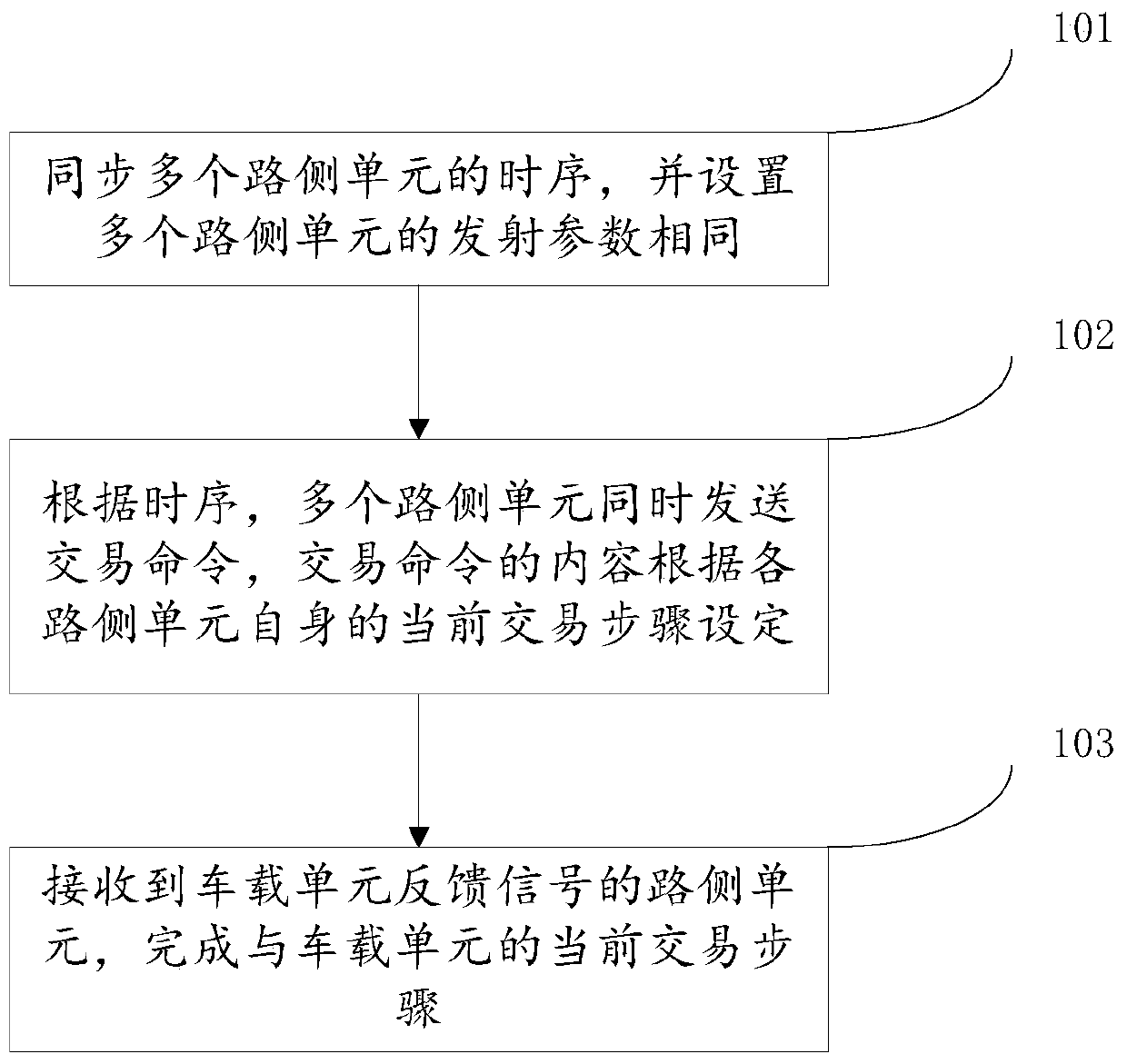
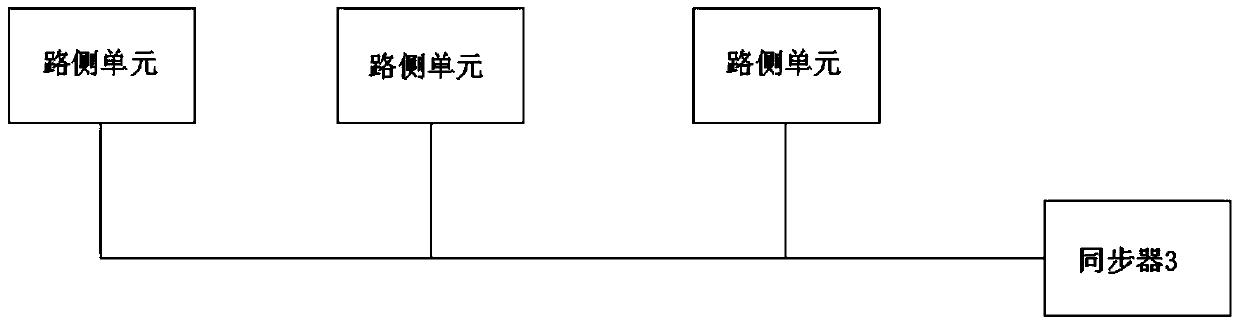
Transaction method, road-side unit and equidirectional multiple lane system of eliminating adjacent lane interference
ActiveCN105184878AGuaranteed transactionalEliminate adjacent road interferenceTicket-issuing apparatusOn boardTime sequence
The invention discloses a transaction method of eliminating adjacent lane interference, applied to an equidirectional multiple lane system. Each lane is correspondingly provided with a road-side unit (RSU) used for wireless communication with an on board unit (OBU); the coverage areas of a plurality of RSUs share overlapped parts. The method comprises: synchronizing the time sequence of the plurality of RSUs, and configuring the emission parameters of the plurality of RSUs to be same; according to the time sequence, the plurality of RSUs simultaneously issuing transaction commands, the contents of transaction commands being set according to the current transaction step of each RSU; and the RSU receiving the feedback signal of the OBU completing the current transaction step with the OBU. According to the invention, the OBU can not transact in the overlapped parts of the RSUs, so that the RSU of a lane can not transact with the OBU of a nearby lane, thereby completely eliminating lane interference.
Owner:SHENZHEN GENVICT TECH
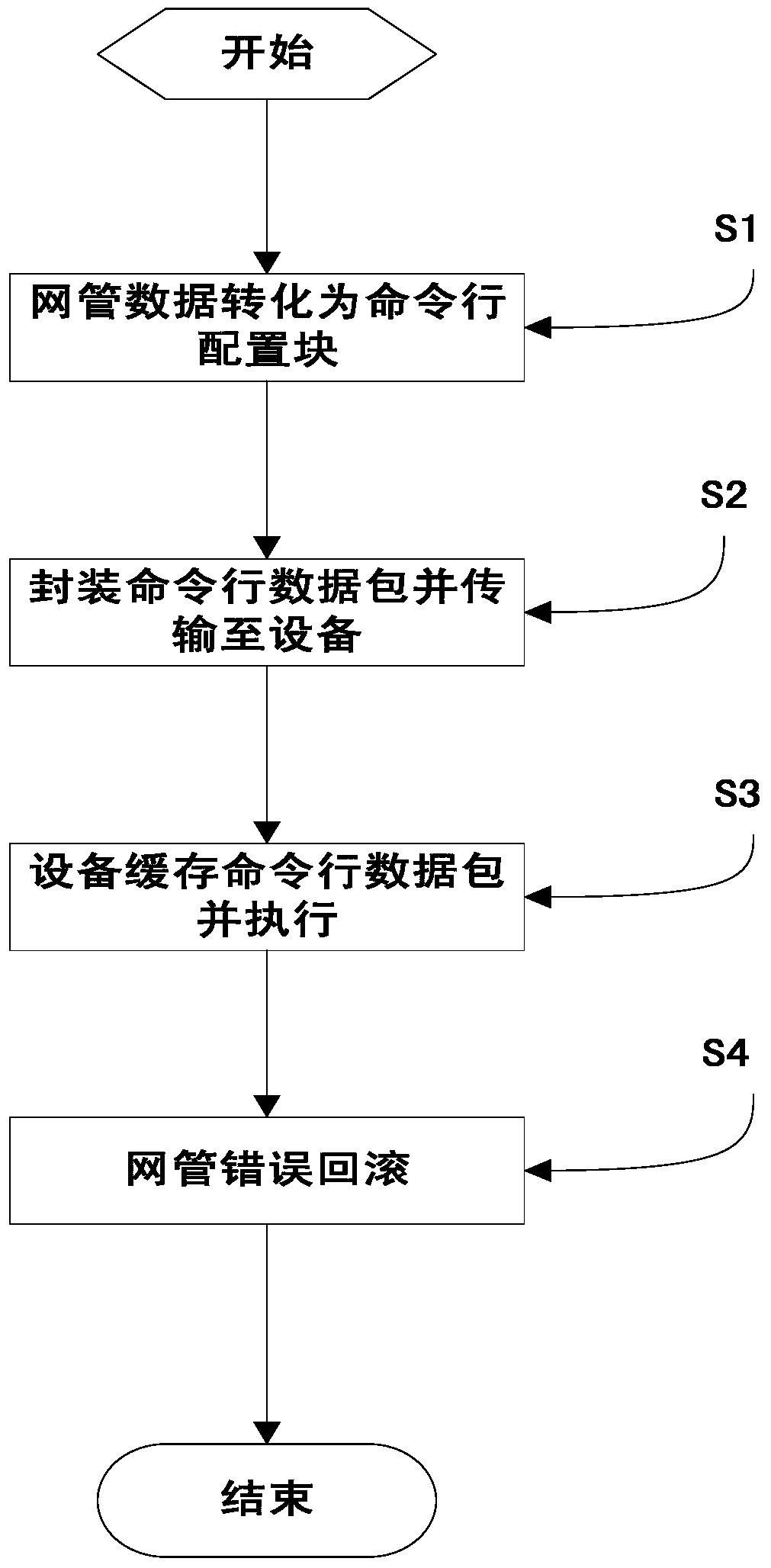
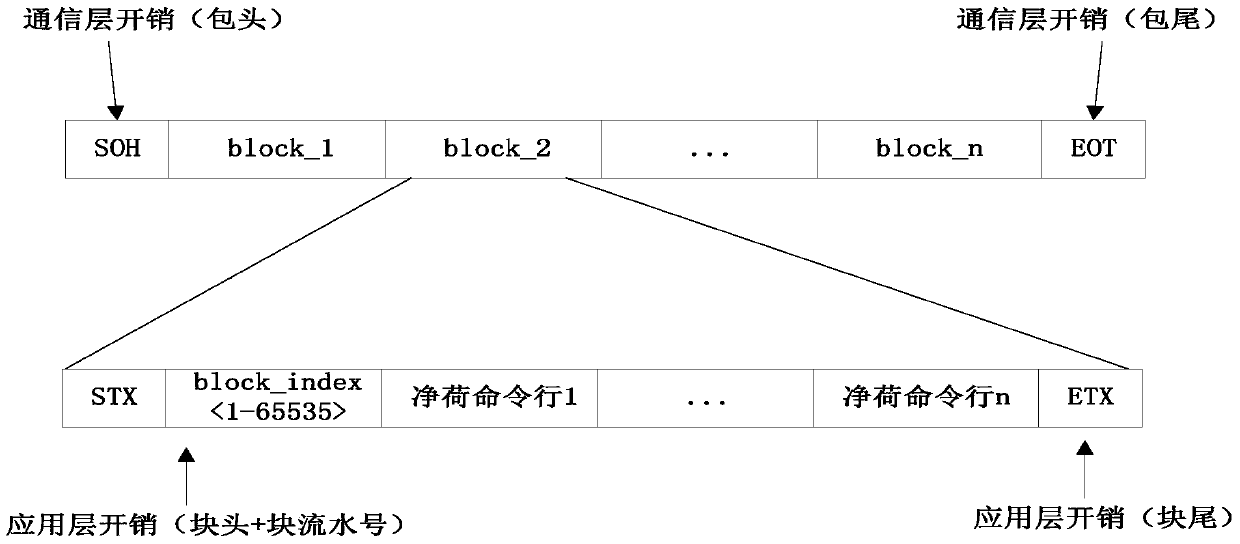
Interactive method based on command line data of network management system
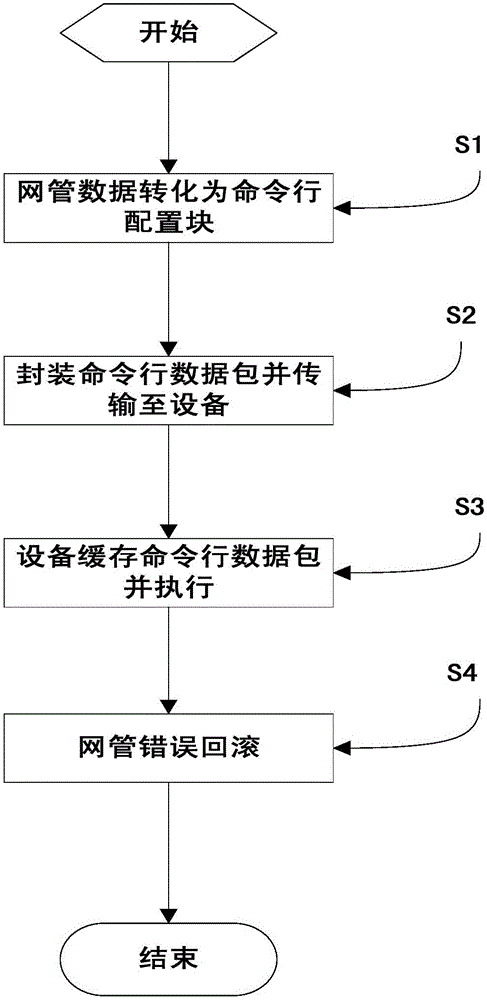
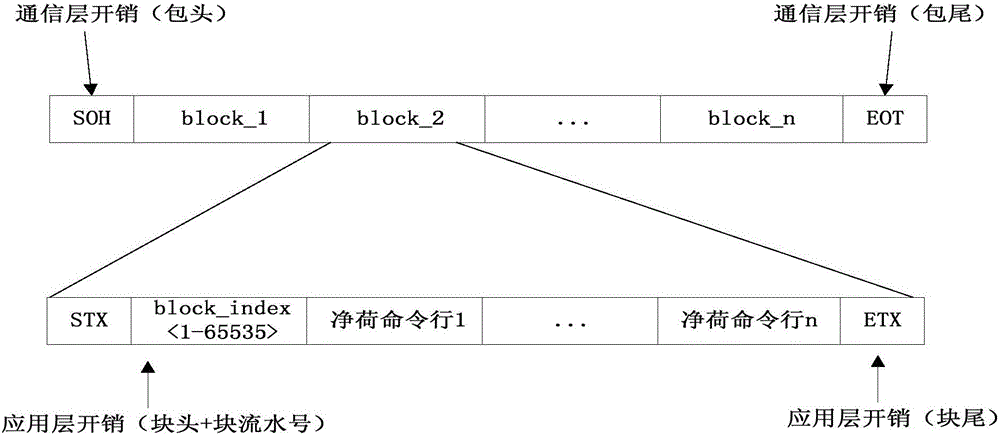
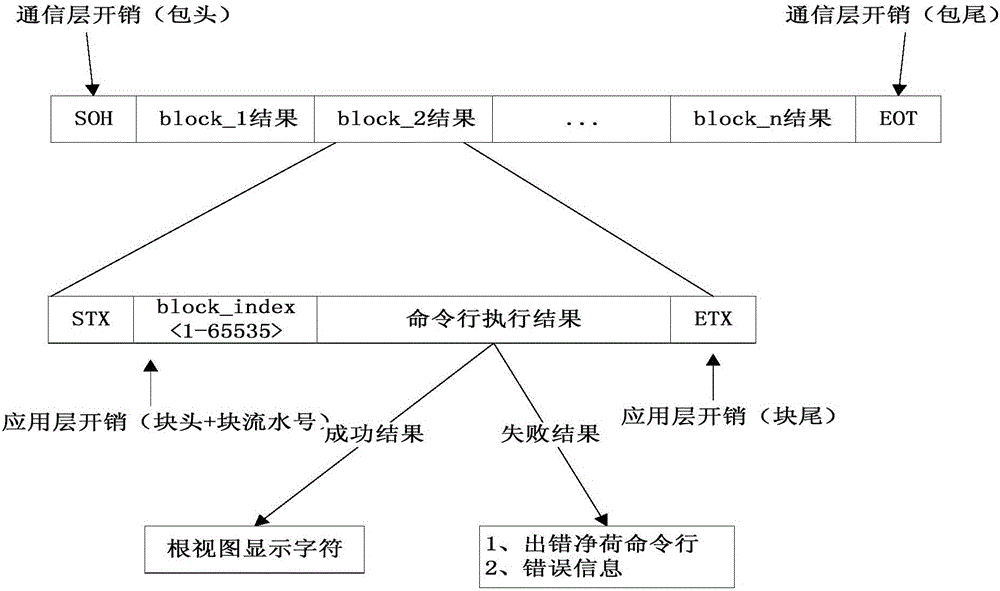
ActiveCN105847041AReduce the number of interactionsReduce the difficulty of download status maintenanceData switching networksInteraction timeNetwork management
The invention discloses an interactive method based on command line data of a network management system. The method comprises the following steps: converting a network management data model into a command line configuration block; packaging the command line data, and transmitting the command line data to a network device; caching and executing the command line data in batches by the network device; and carrying out rollback on a network management error. According to the invention, the data of the network management system is converted into the command line configuration blocks in batches, and an error rollback mode is supported, in this way, the interaction times of the network management system and the network device are decreased, meanwhile the downloading state maintenance difficulty of the network management data model is reduced, and the network management system is supported to simultaneously release multiple items of data command line configuration blocks; the network management system adds an error rollback mark in the command line to ensure the execution transaction of the data command line configuration blocks, once an execution failure occurs, the original operation on the network device is cancelled by an effective reverse operation; and the network management system optimizes the Telnet echo character, reduces the redundant data and simplifies the data returned to the network management system.
Owner:FENGHUO COMM SCI & TECH CO LTD
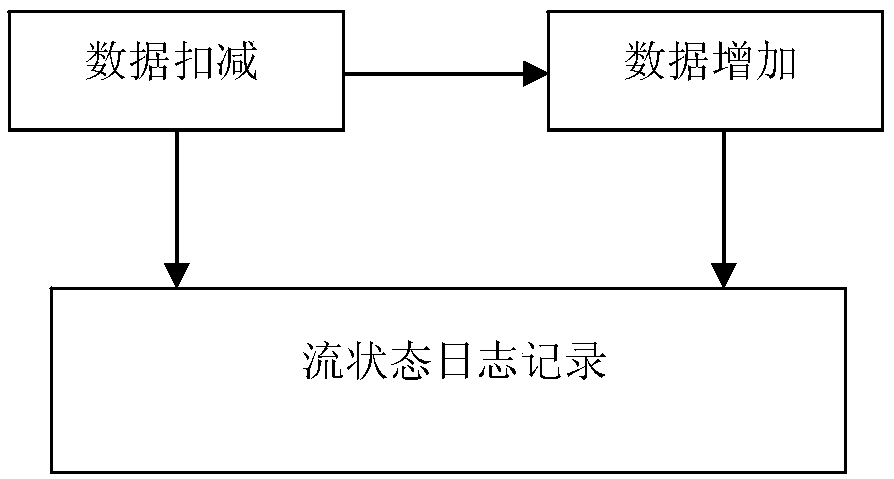
Distributed transaction management method based on state flow
InactiveCN109165084AGuaranteed transactionalFinanceDistributed object oriented systemsTransaction managementData operations
The invention relates to the technical field of data transaction management between computer technology and micro-service multi-modules, and discloses a distributed transaction management method basedon state flow, which solves the problem of data transaction management between multi-services across databases and ensures the atomicity of business transactions. The method comprises the following steps: a, the final state of each data operation in the business process is stored in a preset position; the details of the corresponding data operation is saved while saving the state; b if that datain the intermediate step is problematic, reverse restore operation is carried out accord to the status of each step and the data exchange situation at the beginning of recording; c, the status flow table of the completed transaction is scanned through the timer, the order with abnormal status but not yet processed is queried , and then e compensation operation is performed.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
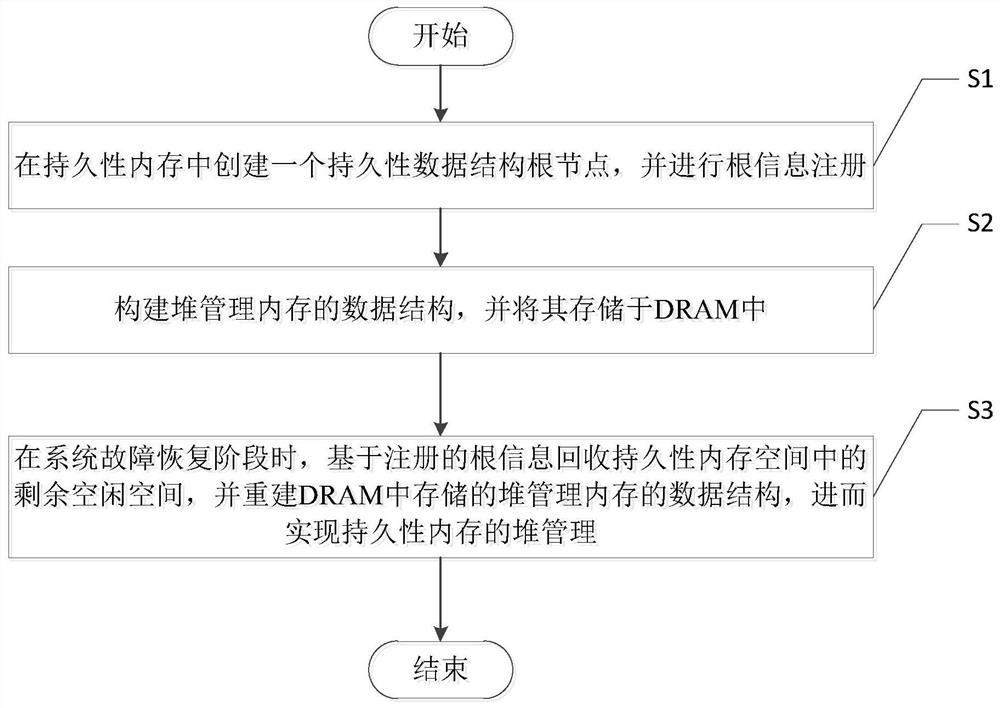
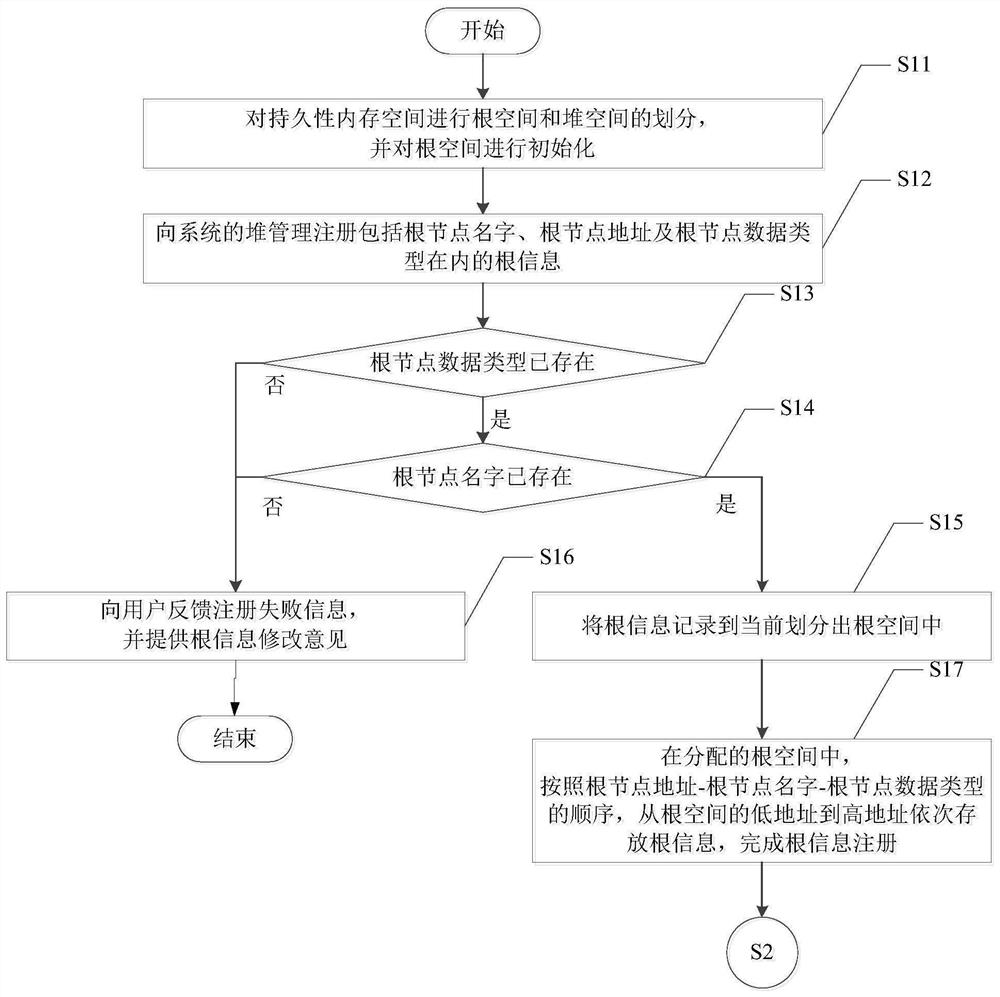
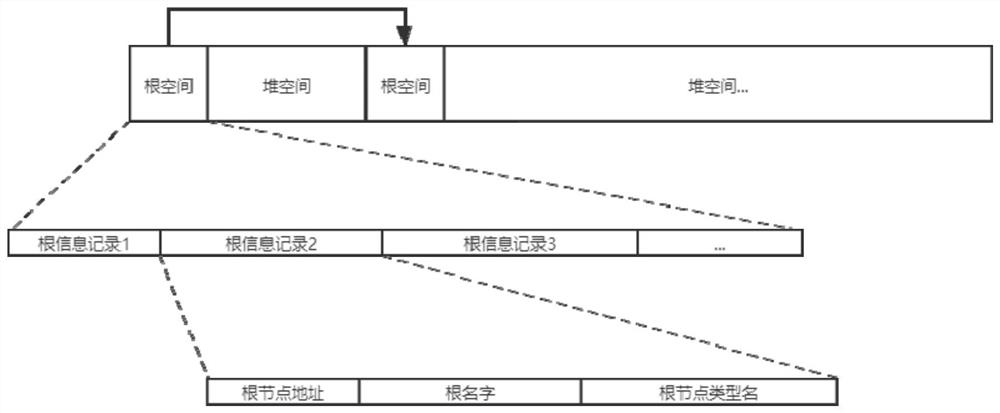
Write-optimized persistent memory heap management method
ActiveCN112084032AReduce write operationsExtend your lifeResource allocationEnergy efficient computingHeap (data structure)Parallel computing
The invention discloses a write-optimized persistent memory management method. The method comprises the steps of S1, performing root information registration in a persistent memory; s2, constructing adata structure of a heap management memory, and storing the data structure in a DRAM; and S3, in a system fault recovery stage, recovering residual free space in the persistent memory space based onthe registered root information, and reconstructing a data structure of the heap management memory stored in the DRAM to achieve heap management of the persistent memory. According to the method, allmetadata structures allocated to the management memory can be stored in the DRAM, and extra write operation on the persistent memory cannot be caused by allocation or release operation of any persistent memory space; in addition, in the fault recovery process, the reference count of the object can be accurately restored through the number of times of searching the same object while the allocated space is searched, so that the reference count of the object can be stored in the DRAM without worrying about the reference count error or loss caused by the fault.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
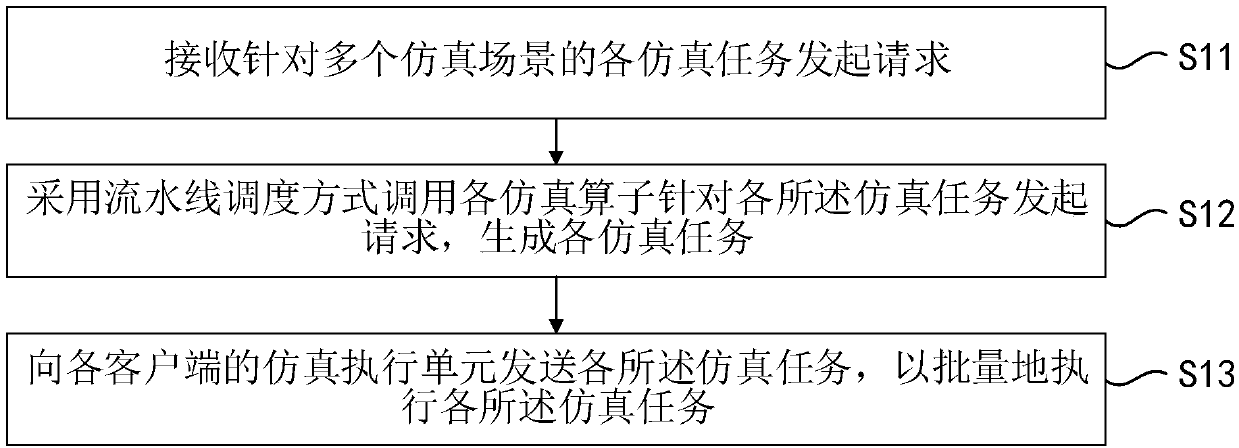
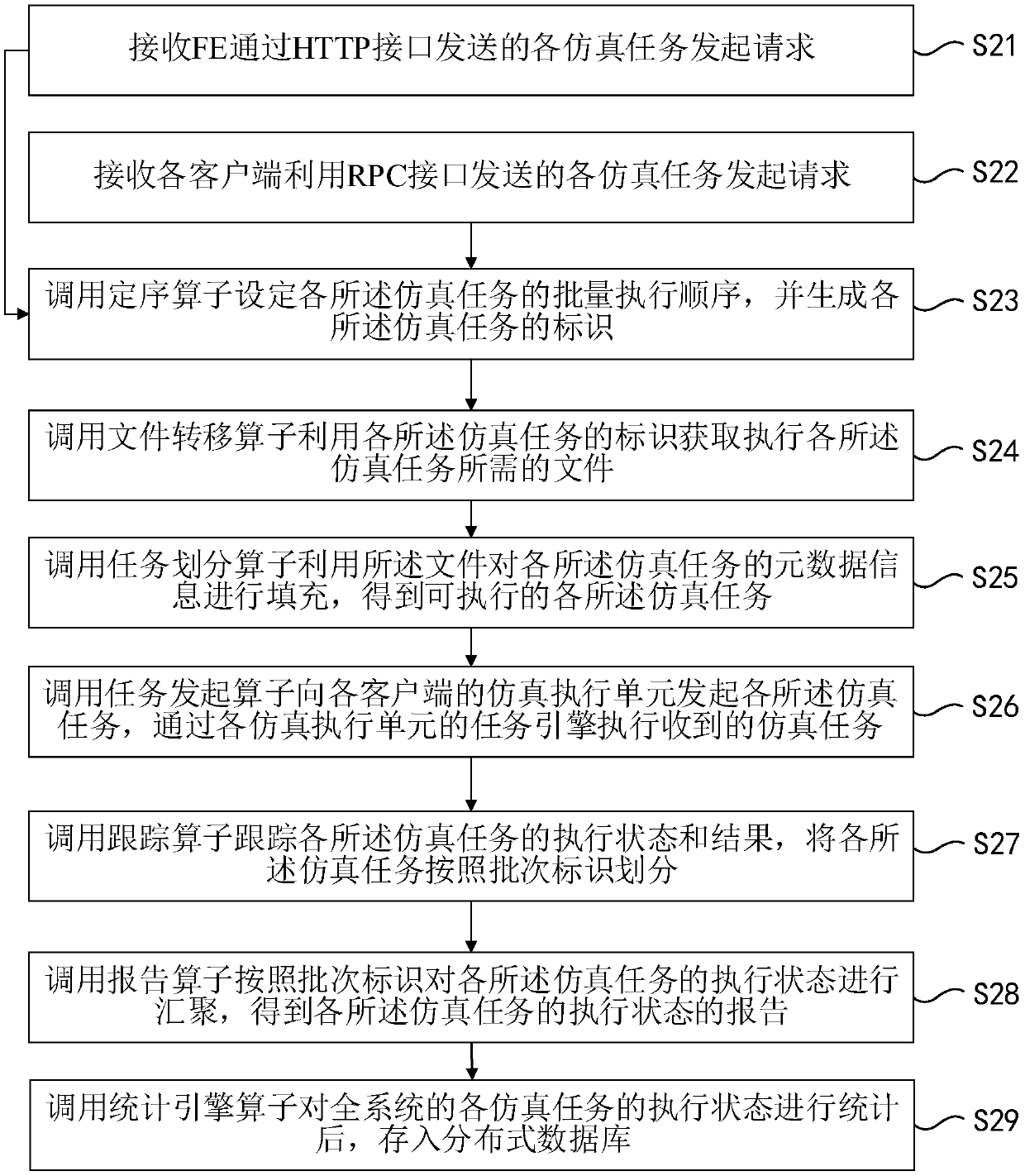
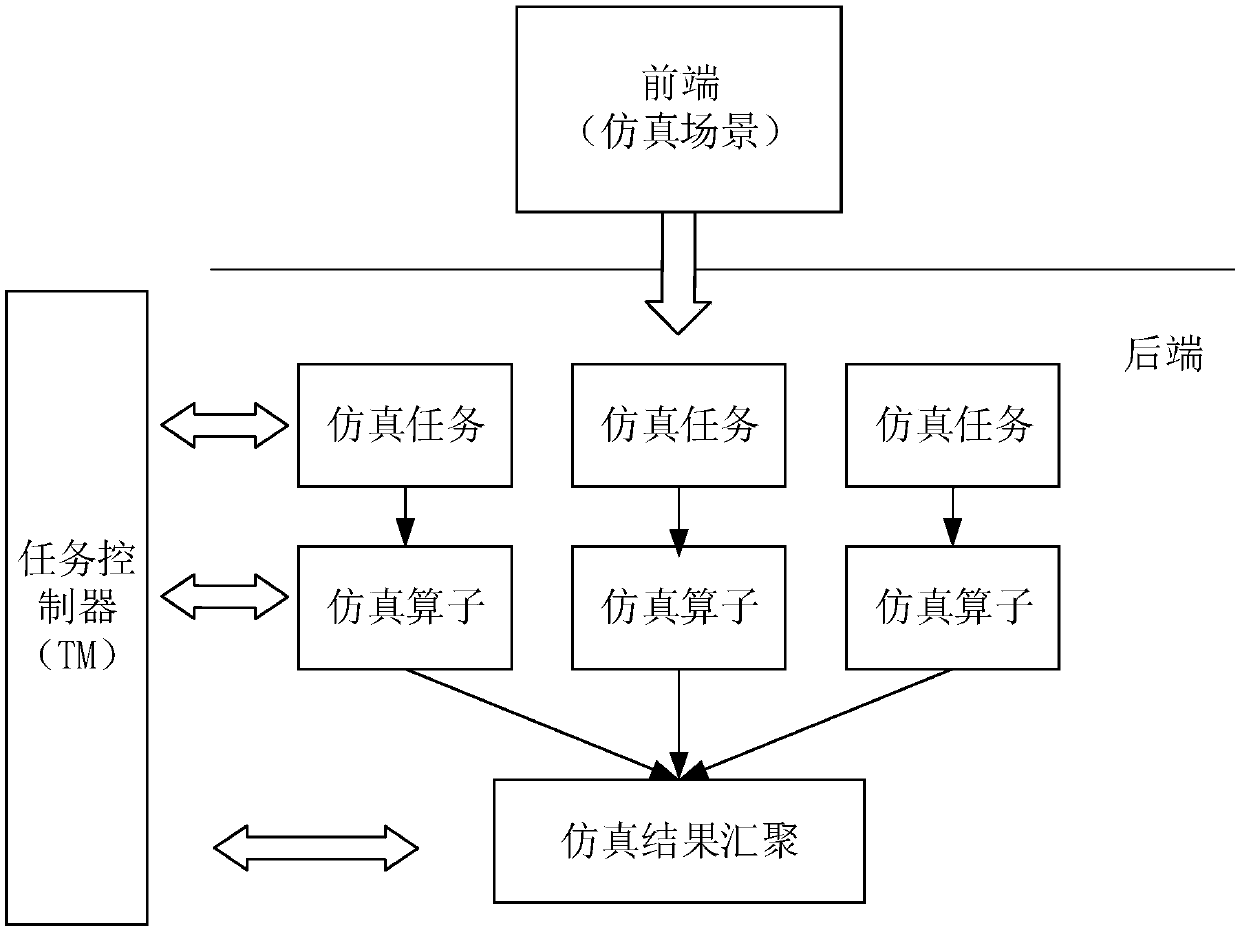
Simulation task scheduling method and device
PendingCN111199079AGuaranteed transactionalEfficient executionDesign optimisation/simulationTransmissionParallel computingEngineering
The embodiment of the invention provides a simulation task scheduling method and device. The method comprises the following steps: receiving a request initiated for each simulation task of a pluralityof simulation scenes; calling each simulation operator to initiate a request for each simulation task by adopting an assembly line scheduling mode, and generating each simulation task; and sending each simulation task to a simulation execution unit of each client so as to execute each simulation task in batches. According to the embodiment of the invention, the simulation tasks are generated in an assembly line scheduling mode, and the generation and execution of the plurality of simulation tasks of the plurality of simulation scenes are controlled, so that the method is suitable for large-batch simulation scene operation requirements, the simulation tasks can be efficiently executed on a distributed system, and the transactional property of a calculation result can be ensured.
Owner:APOLLO INTELLIGENT DRIVING (BEIJING) TECHNOLOGY CO LTD
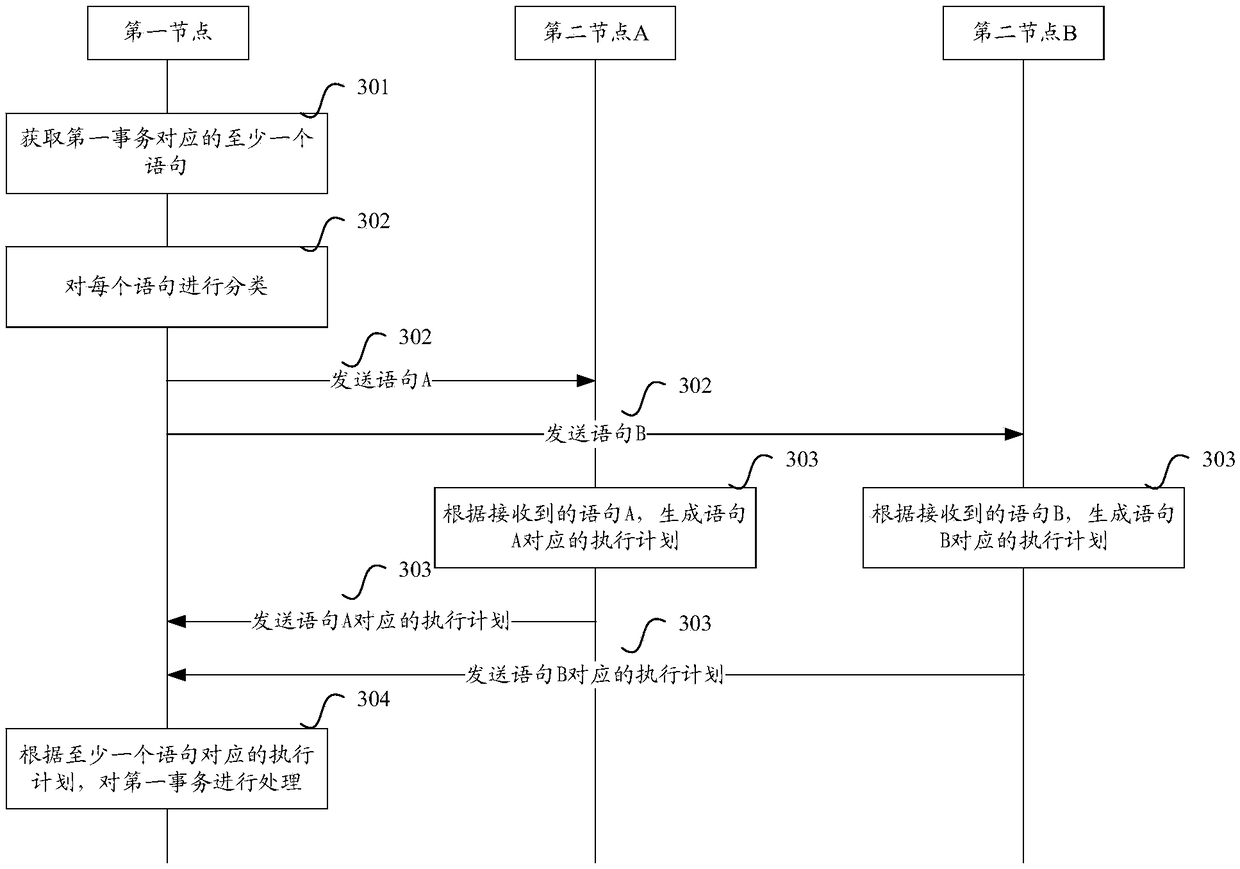
Transaction processing method, server and transaction processing system
ActiveCN108551478AReduce Design ComplexityReduce operating burdenMulti-dimensional databasesTransmissionExecution planTransaction processing system
The invention discloses a transaction processing method, a server and a transaction processing system. The method comprises the steps as follows: after acquiring at least one statement corresponding to a first transaction, a first node can classify each statement, and separately send the at least one statement to at least one second node according to the type of each statement, and thus the at least one second node generates an execution plan corresponding to the statement according to the received statement; and then the first node can process the first transaction according to the received execution plan corresponding to the at least one statement corresponding to the first transaction sent by the at least one second node. Therefore, according to the method, server and system provided bythe embodiment of the invention, the multiple types of statements can be synchronously processed, the system processing efficiency is effectively improved, the running load of the system is reduced,and the transactional performance of the system is effectively ensured.
Owner:CHINA UNIONPAY
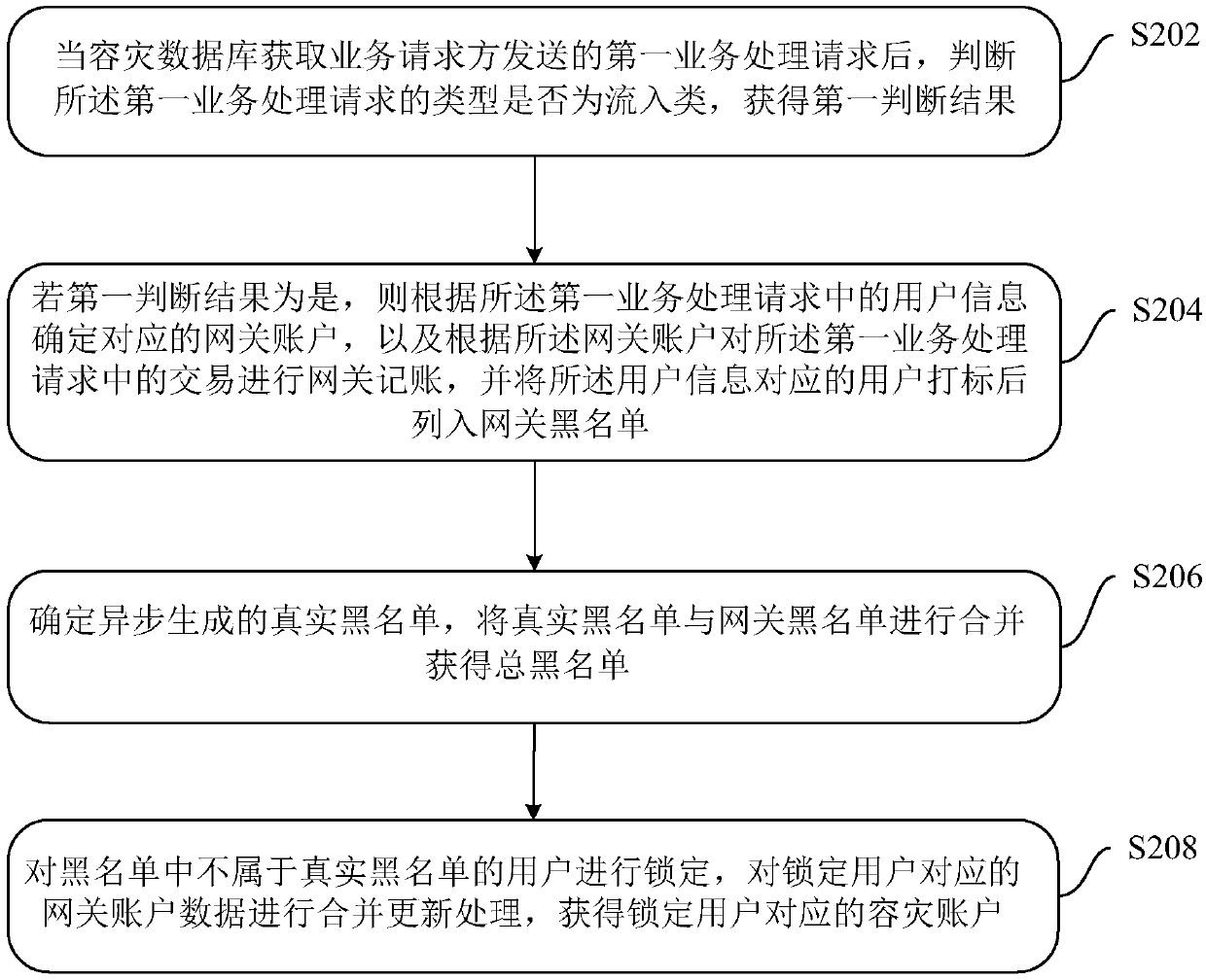
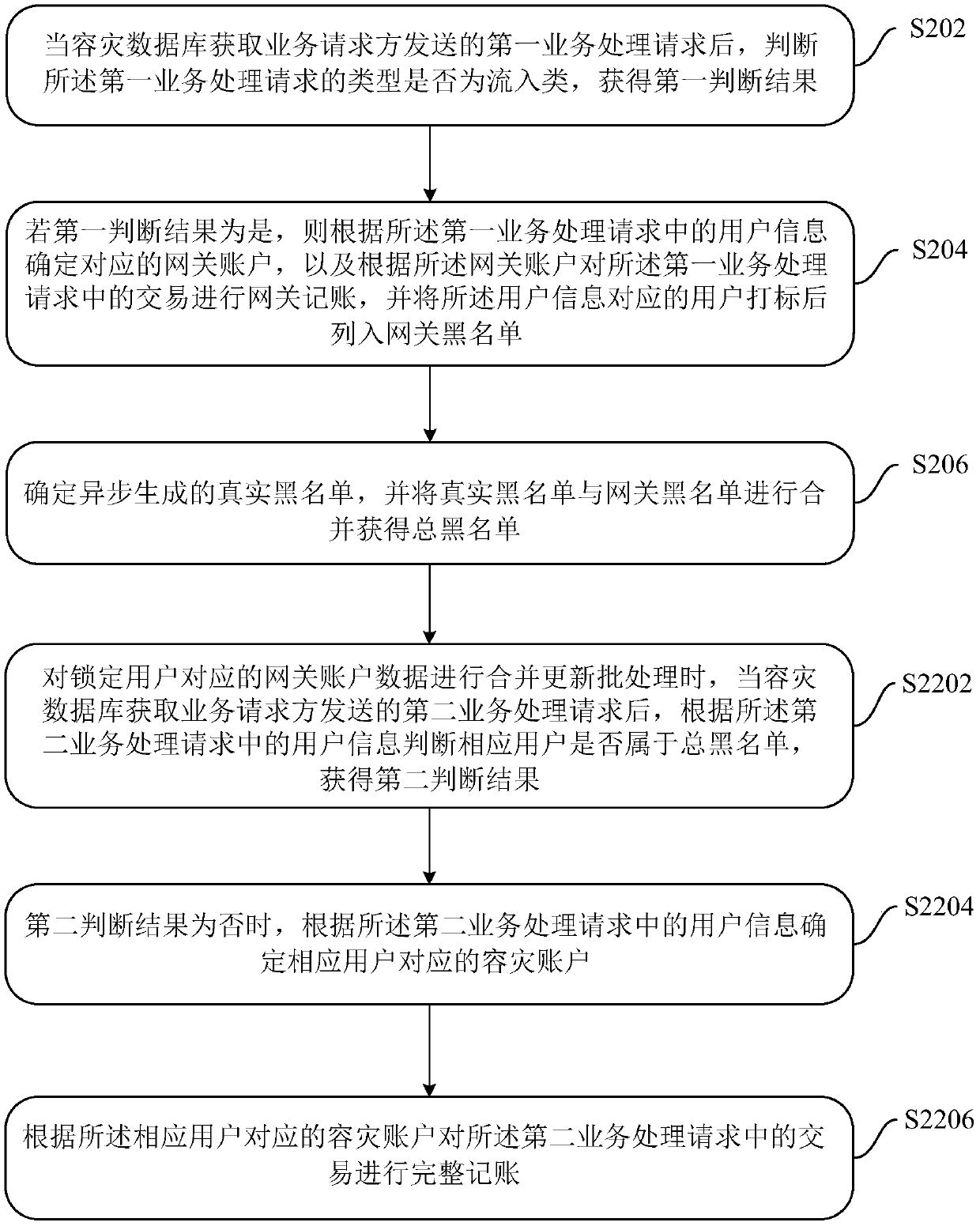
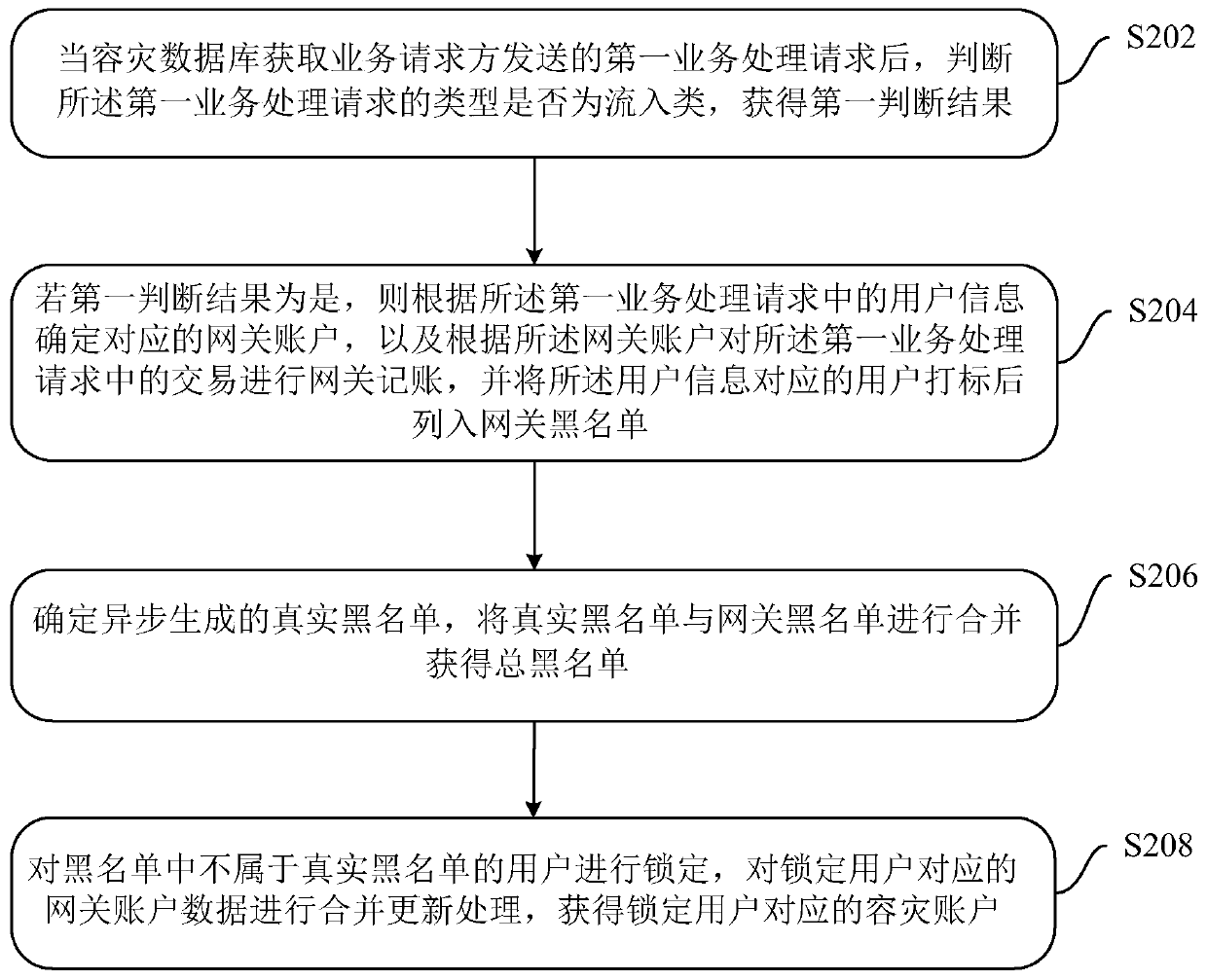
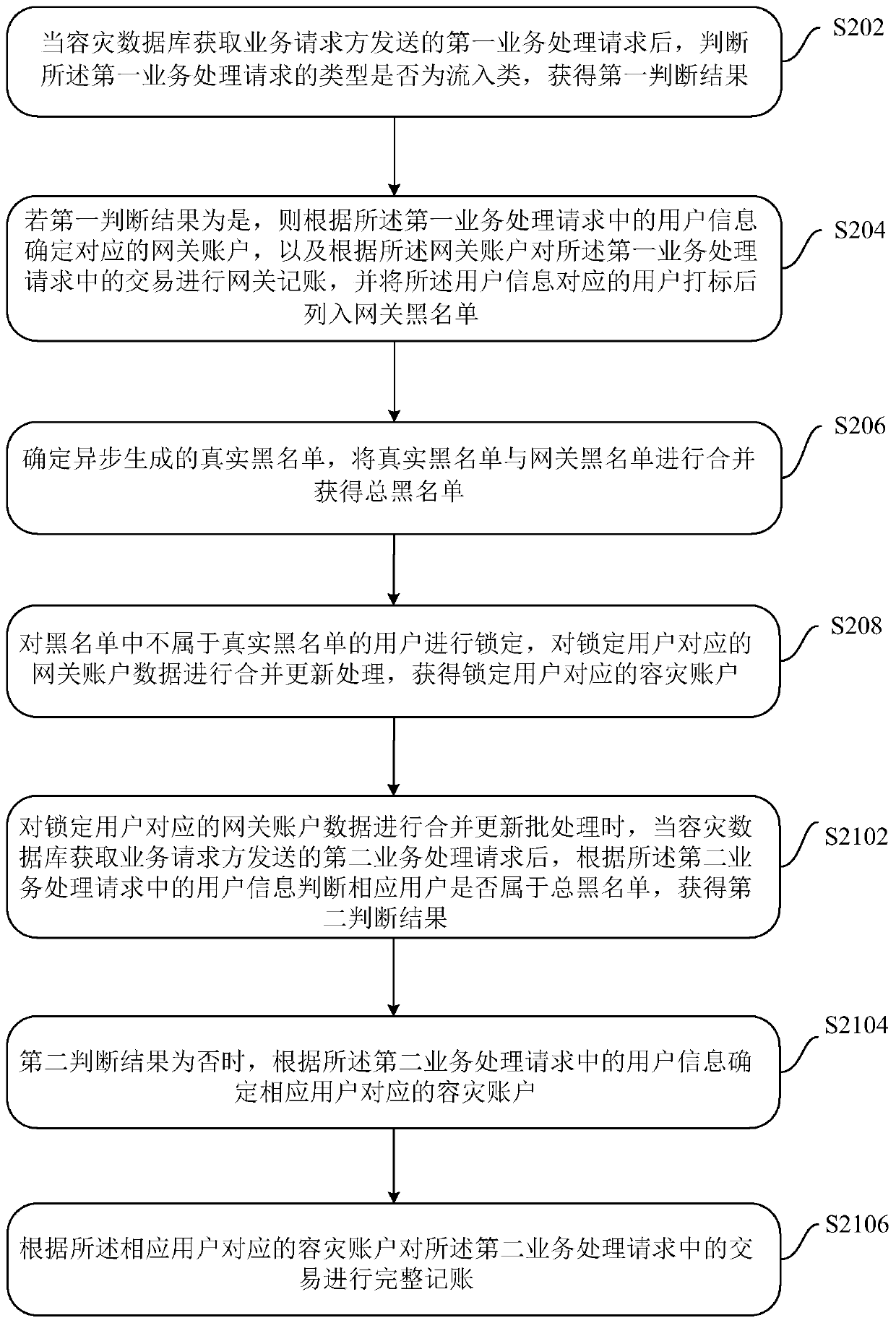
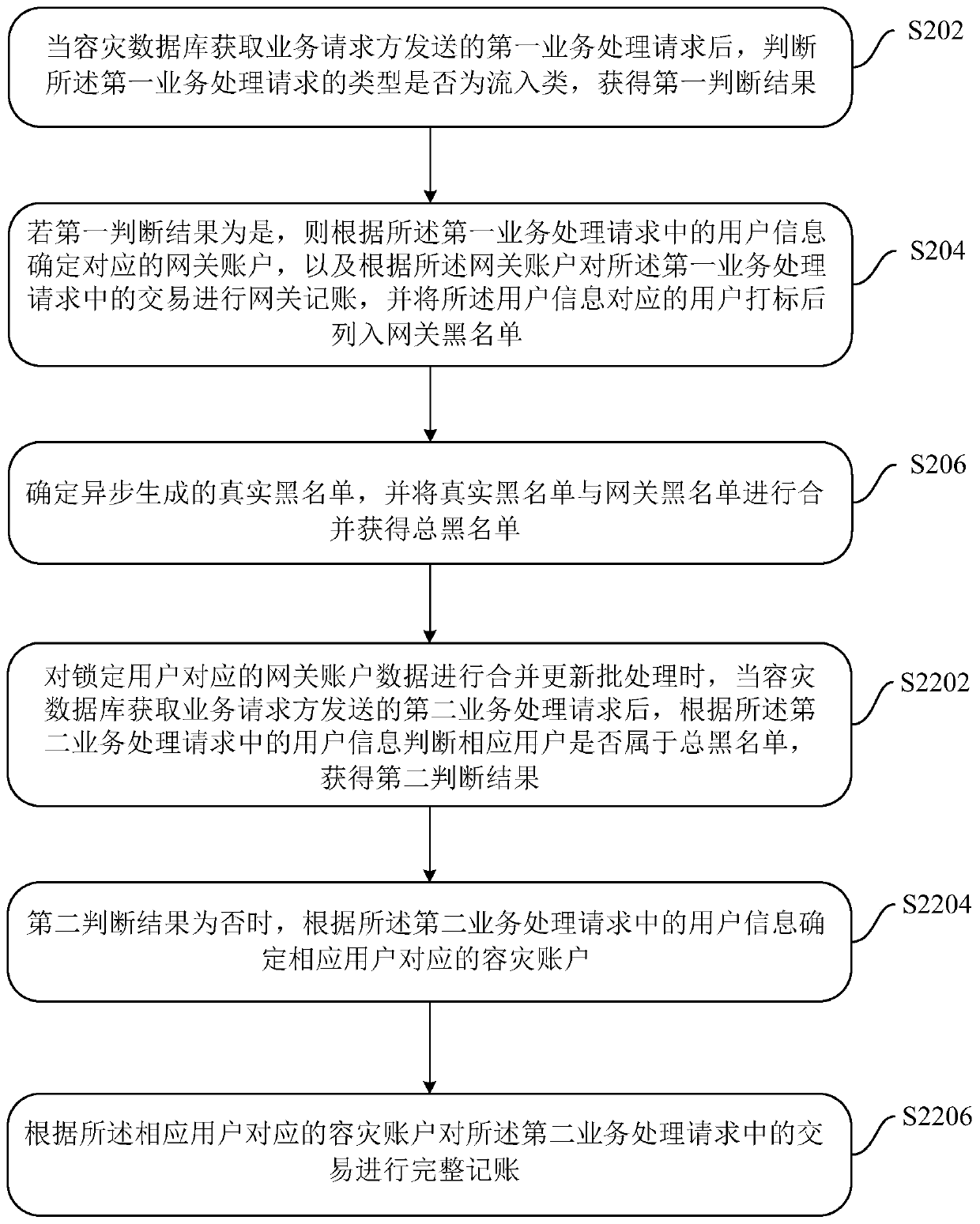
Disaster recovery data processing method, device and system
ActiveCN109614263ATransaction preventionGuaranteed transactionalDatabase updatingDatabase distribution/replicationBlack listDisaster recovery
The embodiment of the invention discloses a disaster recovery data processing method, device and system, and the method comprises the steps: after a disaster recovery database obtains a first serviceprocessing request sent by a service requester, judging whether the type of the first service processing request is an inflow type, and obtaining a first judgment result; if the first judgment resultis yes, determining a corresponding gateway account according to the user information in the first service processing request, performing gateway accounting on the transaction in the first service processing request according to the gateway account, and listing the corresponding user into a gateway blacklist; determining a real blacklist generated asynchronously, and combining the real blacklist with the gateway blacklist to obtain a total blacklist; and locking the users who do not belong to the real blacklist in the total blacklist, and carrying out merging and updating processing on the gateway account data corresponding to the locked users. By means of the embodiments of the present specification, normal transactions can be performed on the user accounts except the real blacklist in the disaster recovery period.
Owner:ADVANCED NEW TECH CO LTD
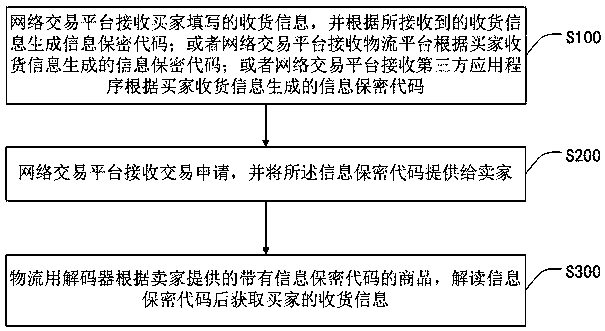
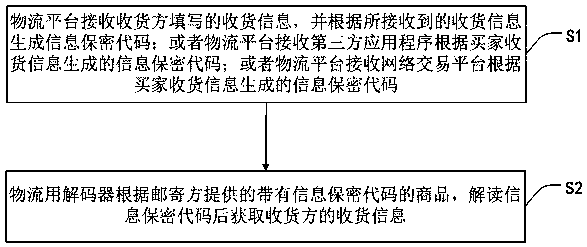
Buyer receiving information confidentiality method and system, storage medium and confidentiality processing method
PendingCN109559118AGuaranteed transactionalNormal life is not affectedBuying/selling/leasing transactionsAnonymous user systemsThird partyLogistics management
The invention discloses a buyer receiving information confidentiality method and system, a storage medium and a confidentiality processing method, and the method comprises the steps that a network transaction platform receives receiving information written by a buyer, and generates an information confidentiality code according to the received receiving information; or the network transaction platform receives an information confidential code generated by the logistics platform according to the receiving information of the buyer; or the network transaction platform receives an information confidential code generated by the third-party application program according to the receiving information of the buyer; the network transaction platform receives the transaction application and provides the information confidential code for the seller; and the logistics decoder interprets the information confidential code according to the commodity with the information confidential code provided by theseller and then obtains the receiving information of the buyer. Based on this, according to the buyer receiving information confidentiality method provided by the invention, the seller can not obtainthe receiving information of the buyer, and the logistics company can decrypt the receiving information through the logistics decoder to obtain the receiving information, so that the normal network transaction is ensured.
Owner:深圳海普瑞丽科技有限公司
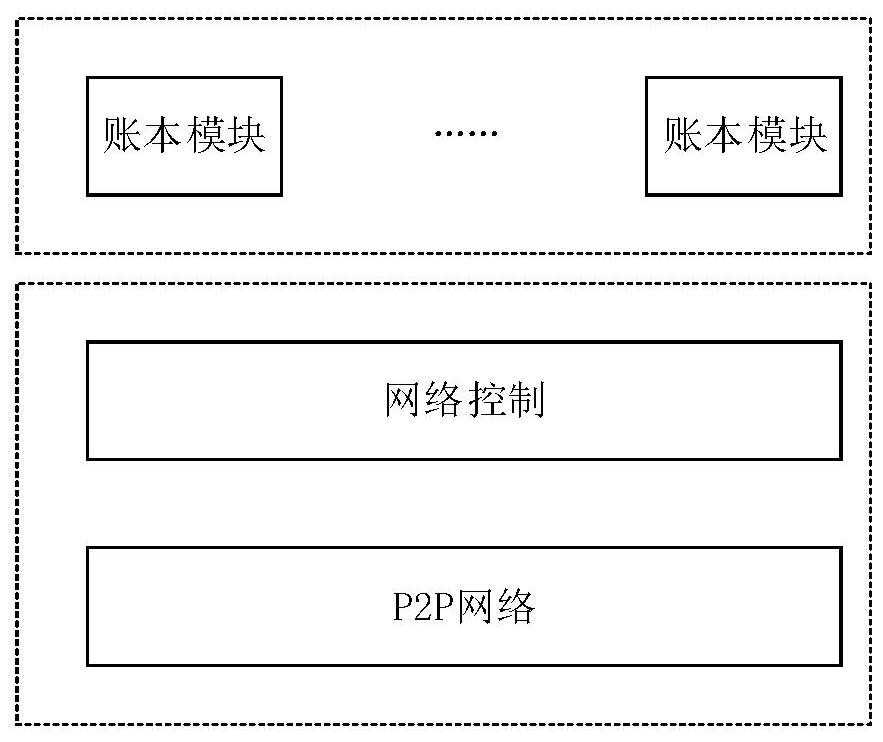
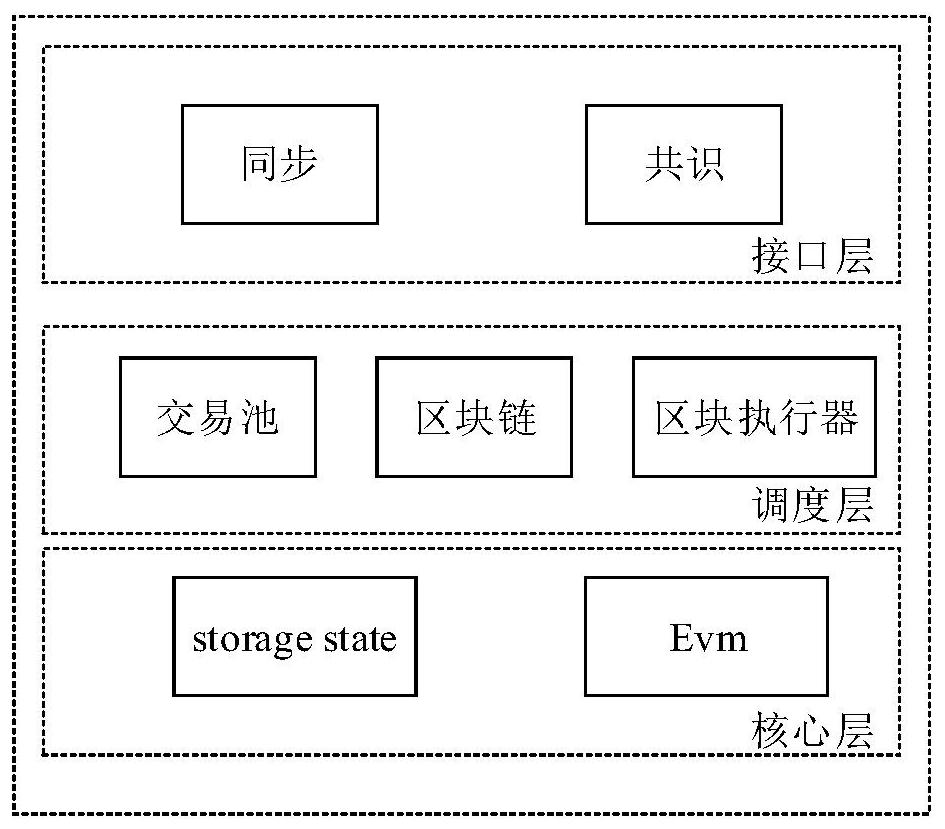
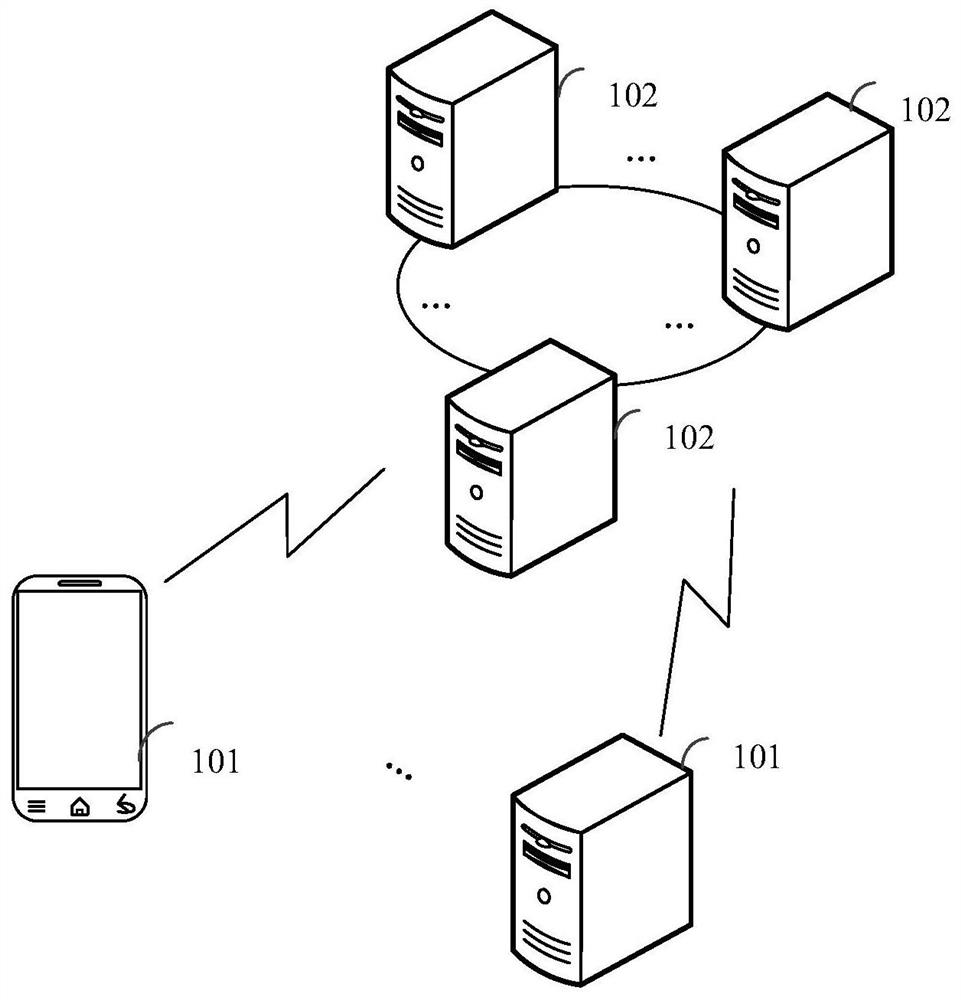
Ethereum-compatible distributed account book method, device and equipment and medium
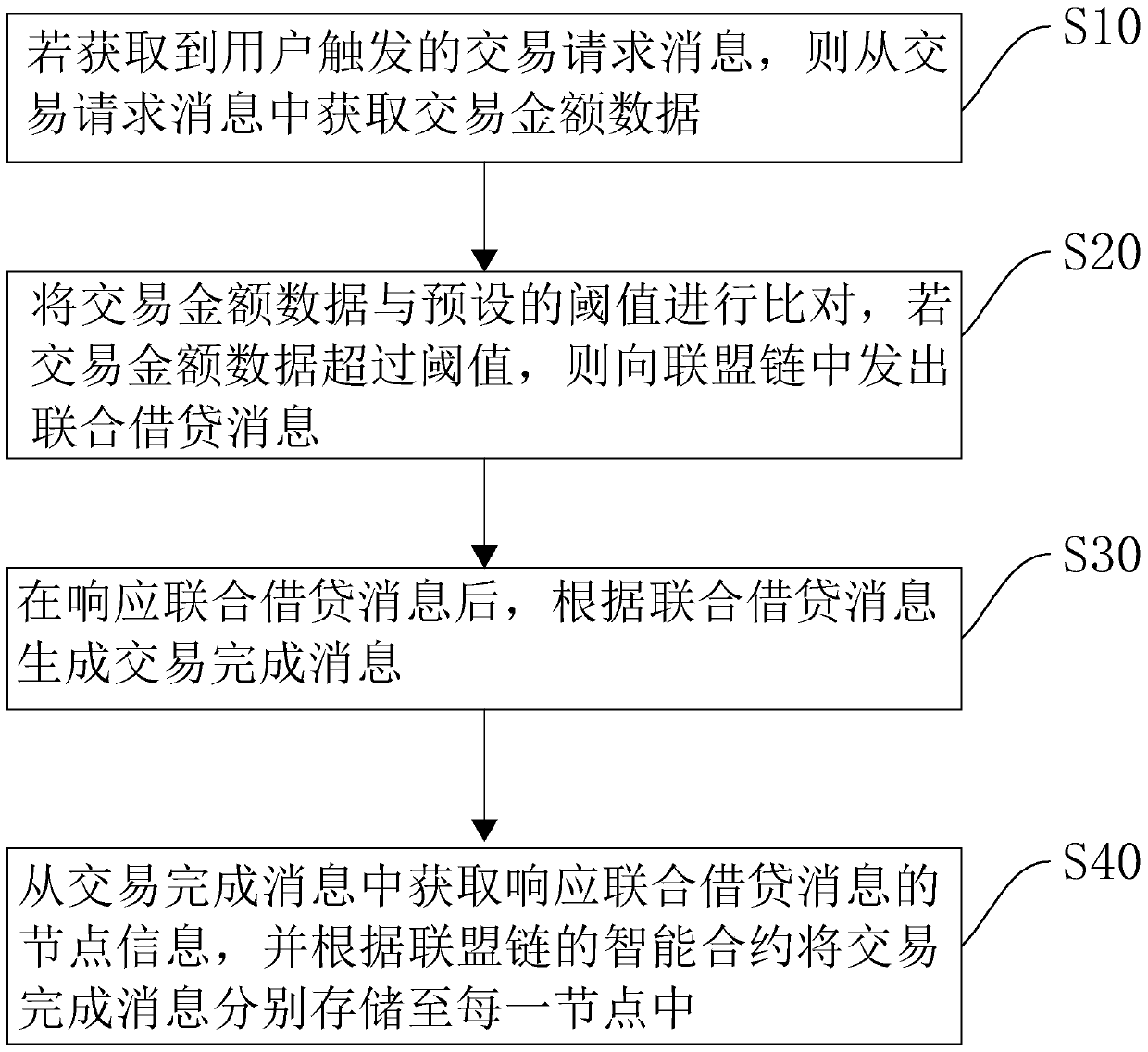
InactiveCN110046895AEnsure safetyGuaranteed transactionalPayment protocolsTransmissionComputers technologyReal-time computing
The invention relates to the technical field of computer technology, in particular to an Ethereum-compatible distributed account book method, device and equipment and a medium, and the method comprises the steps of S10, if a transaction request message triggered by a user is obtained, obtaining the transaction amount data from the transaction request message; s20, comparing the transaction amountdata with a preset threshold value, and if the transaction amount data exceeds the threshold value, sending a joint lending message to an alliance chain; s30, generating a transaction completion message according to the joint lending message after the joint lending message is responded; and S40, obtaining the node information responding to the joint lending message from the transaction completionmessage, and respectively storing the transaction completion message into each node according to the smart contract of the alliance chain. The method has the effect of optimizing the throughput capacity of the block chain.
Owner:浙江泰链科技有限公司
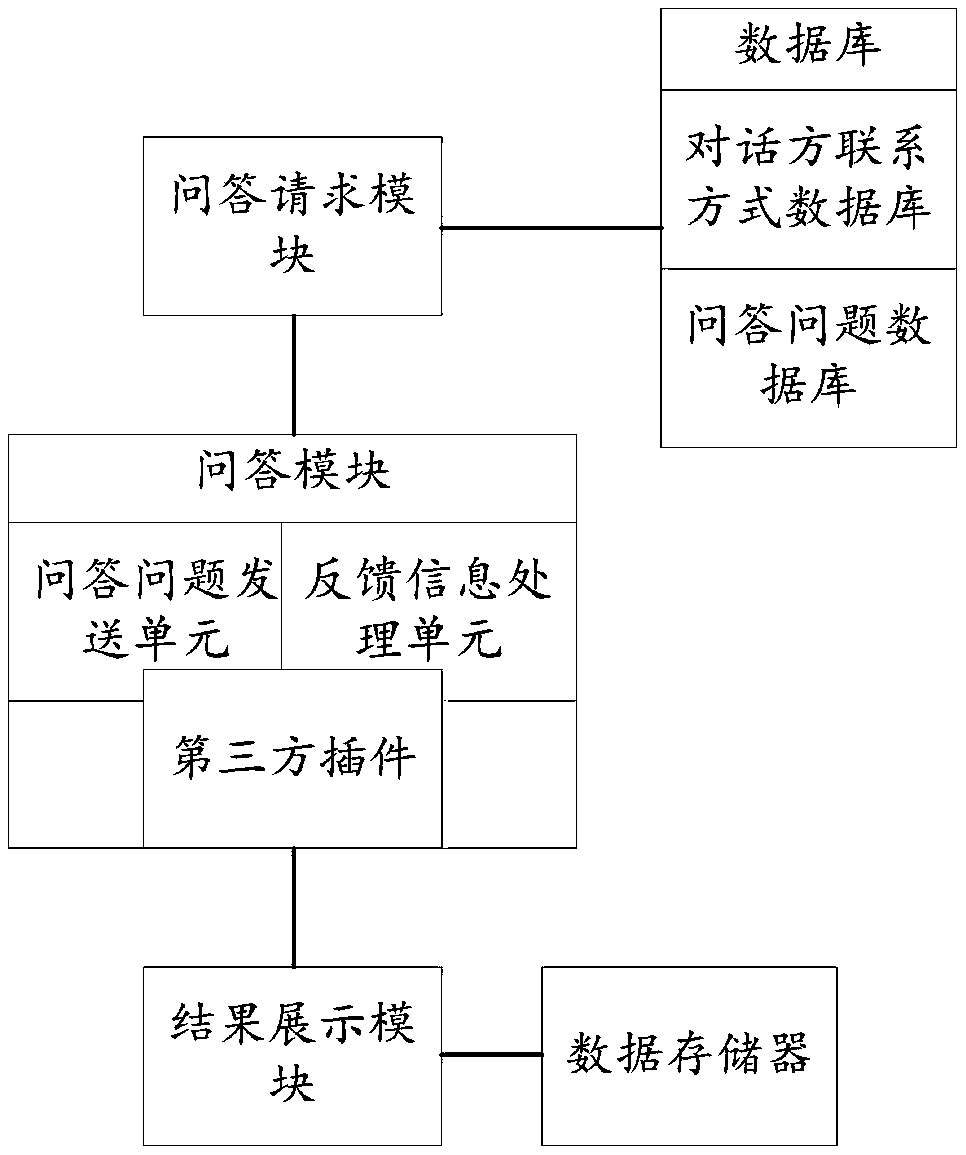
Automatic question and answer method and system
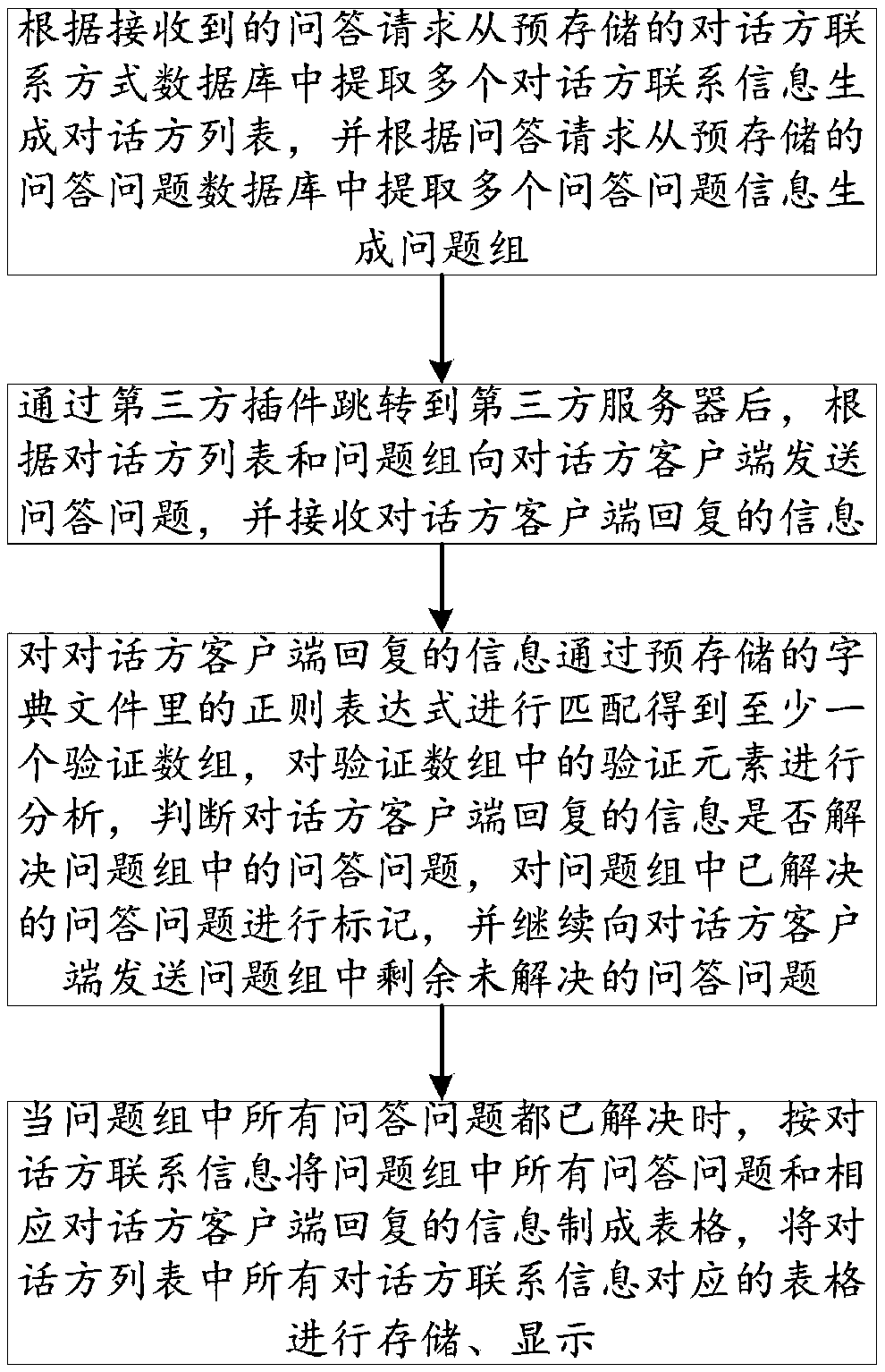
InactiveCN107609031AEasy to chooseImplement Smart ReplySpecial data processing applicationsThird partyInformation processing
The invention relates to an automatic question and answer method and system. The automatic question and answer system comprises a question and answer request module, a question and answer module, databases, a result display module and a data memory, wherein the question and answer module comprises a question sending unit, a feedback information processing unit and a third-party plug-in; and the databases include a dialogue party contact information database and a question database. A dialogue party list and a question group are generated according to a question and answer request sent by a client, the dialogue party contact information database and the question database; by analyzing information replied by dialogue party clients, whether questions in the question group are solved or not isjudged; the solved questions are tagged; and when all the questions are solved, a form formed by the questions corresponding to contact information of all dialogue parties in the dialogue party listand corresponding information replied by the dialogue parties is displayed, so that a user can select the most proper dialogue party according to the form conveniently.
Owner:武汉蜕变人工智能科技有限公司
Implementation method of a fault-tolerant distributed security event data transmission protocol
The invention aims to provide an implementation method of a fault-tolerant distributed security event data transmission protocol. Security events are handled through a distributed cluster, and event nodes in the cluster are determined through a periodical election mechanism in order to ensure the transaction of message data. A message queue mechanism is adopted for the nodes in the cluster in order to ensure the concurrency and expandability of security event handling. Thus, a fault-tolerant security event transmission mechanism is implemented. The method comprises the following steps that: A, security events in a whole network are handled through an event handling distributed cluster; B, the event handling cluster periodically elects event nodes Transactional; C, scoring factors of event nodes Transactional election are determined; D, one Performer node can process security event transmission requests of a plurality of Performer nodes concurrently; and E, the Performer node processes messages.
Owner:中国南方电网有限责任公司信息中心 +1
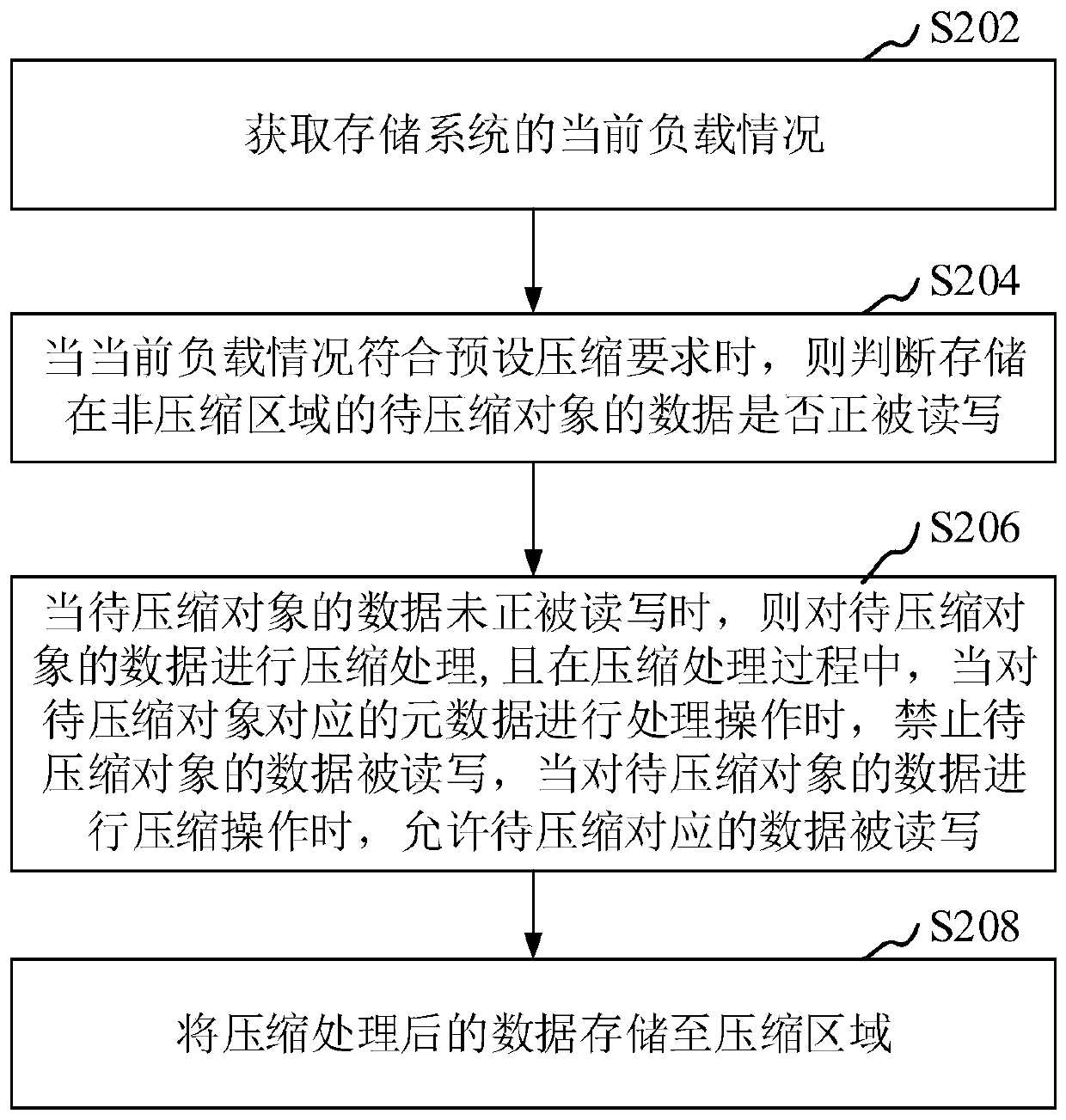
Data compression method and device, computer equipment and storage medium
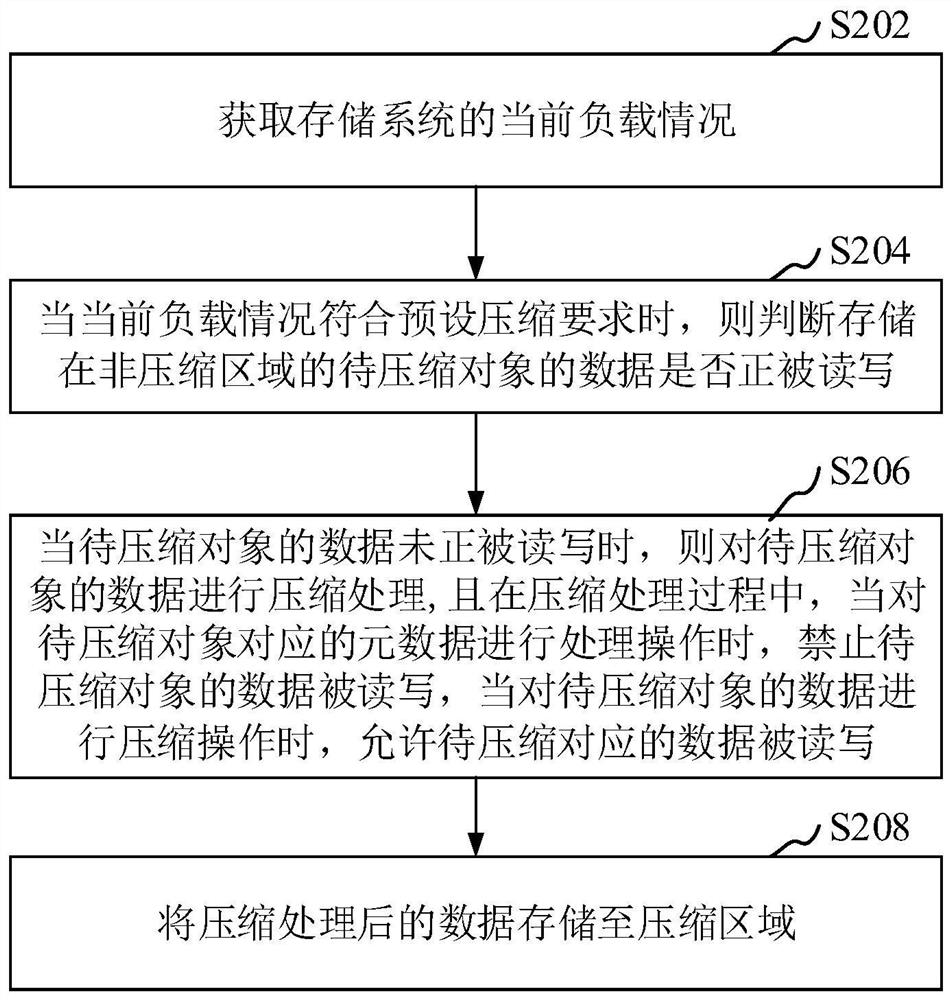
ActiveCN111459404AGuaranteed transactionalAvoid the long tail effectInput/output to record carriersObject storeComputer equipment
The invention relates to the field of data storage, in particular to a data compression method and device, computer equipment and a storage medium. The method comprises the steps of obtaining a current load condition of a storage system; when the current load condition meets a preset compression requirement, judging whether the data of the to-be-compressed object stored in the non-compression areais being read and written or not; when the data of the to-be-compressed object is not read and written, compressing the to-be-compressed object; forbidding the data of the to-be-compressed object from being read and written when the metadata corresponding to the to-be-compressed object is processed in the compressing process, and allowing the data corresponding to the to-be-compressed object to be read and written when the data of the to-be-compressed object is compressed; and storing the compressed data to a compression area. By adopting the method, data compression and read-write operationcan be both considered.
Owner:PING AN TECH (SHENZHEN) CO LTD
Fund data processing method and device
PendingCN113393310AImprove the efficiency of liquidation processingGuaranteed transactionalFinanceAlgorithmBusiness enterprise
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
User security level identification method and device based on multi-stage time sequence and multiple tasks
ActiveCN114742645AData SecuritySafety of tradementDigital data information retrievalFinanceModel sampleEngineering
The invention relates to a user security level identification method and device based on multiple stages of time sequences and multiple tasks. The method comprises the following steps: generating a plurality of stage sets according to total users and user stages corresponding to the total users; sequentially arranging the plurality of stage sets according to a time sequence; performing multi-task training on the (n + 1) th group of initial models according to the (n + 1) th stage set and the nth group of model parameter vectors to generate the (n + 1) th group of model parameter vectors, n being a positive integer; generating a plurality of groups of stage scoring models based on a plurality of groups of model parameter vectors until the plurality of stage sets are trained; and performing security level identification on the current user through the multiple groups of stage scoring models. According to the method, the multi-task machine learning method can be integrally improved from the aspects of actual problems and application scenes, model samples and model parameters, so that user data security and transaction security of an application system are ensured.
Owner:北京淇瑀信息科技有限公司
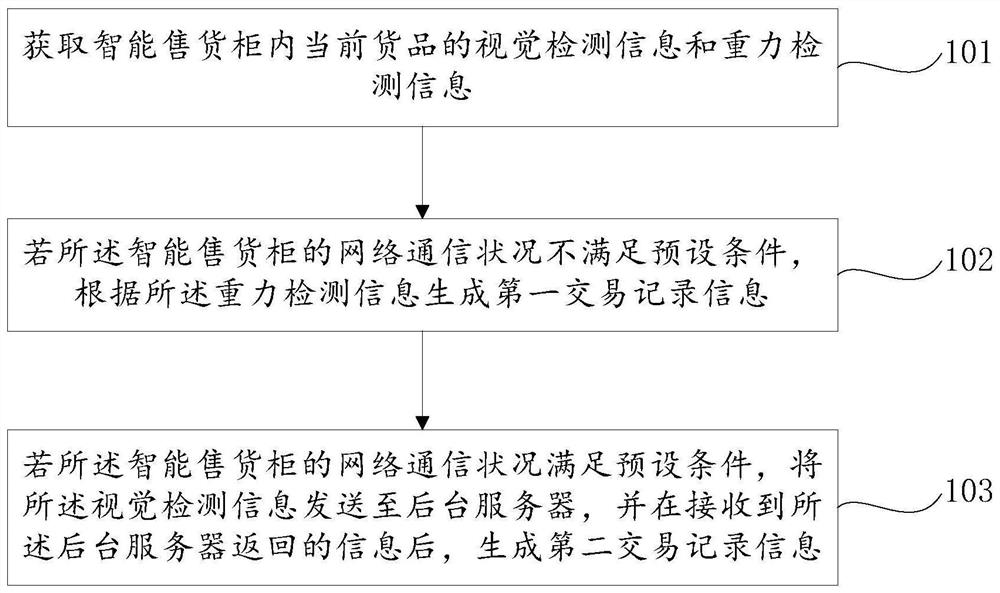
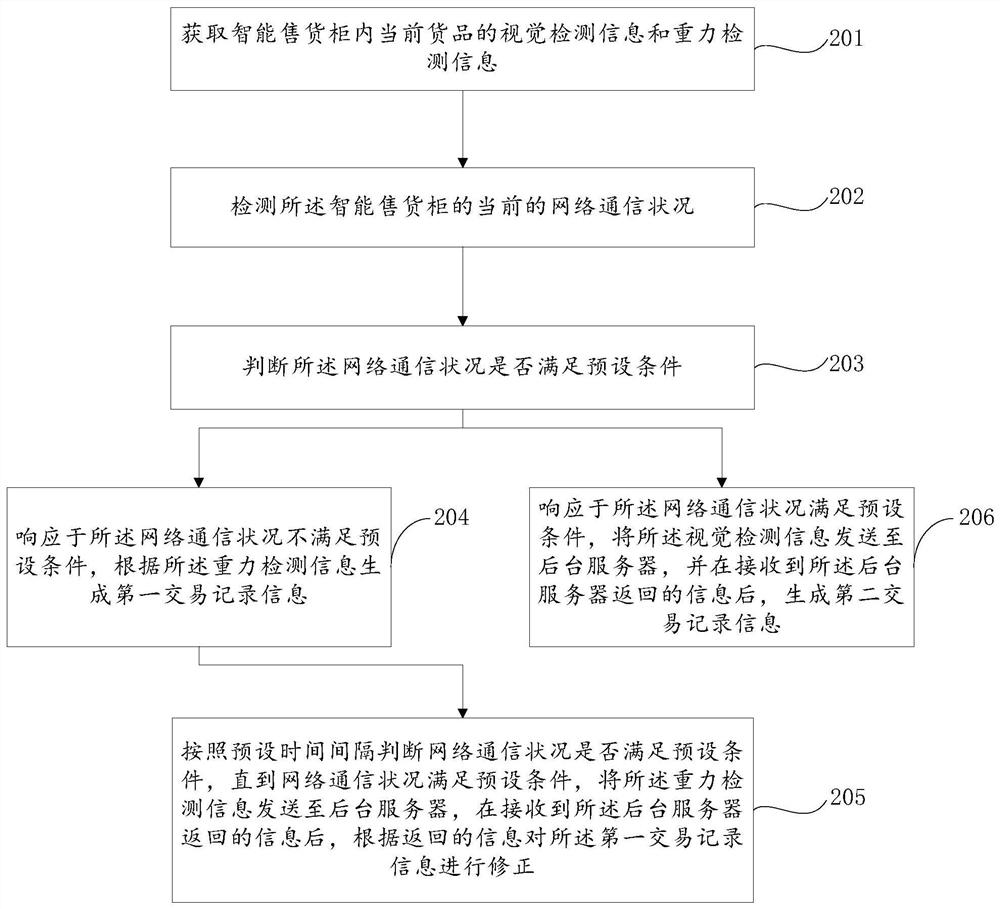
Commodity verification method and device based on vision and gravity detection
PendingCN112734446AGuaranteed transactionalImprove experienceCoin-freed apparatus detailsCommerceNetwork communicationFinancial transaction
The invention provides a commodity verification method and device based on vision and gravity detection. The method comprises the steps: acquiring vision detection information and gravity detection information of current commodities in an intelligent vending cabinet; if the network communication condition of the intelligent vending cabinet does not meet the preset condition, generating first transaction record information according to the gravity detection information; and if the network communication condition of the intelligent vending cabinet meets a preset condition, sending the visual detection information to a background server, and generating second transaction record information after receiving information returned by the background server. In this way, when a network communication fault occurs, the commodity verification scheme based on vision and gravity detection can quickly generate a transaction order, ensure normal transaction of commodities and improve the user experience of consumers.
Owner:BEIJING MISSFRESH ECOMMERCE CO LTD
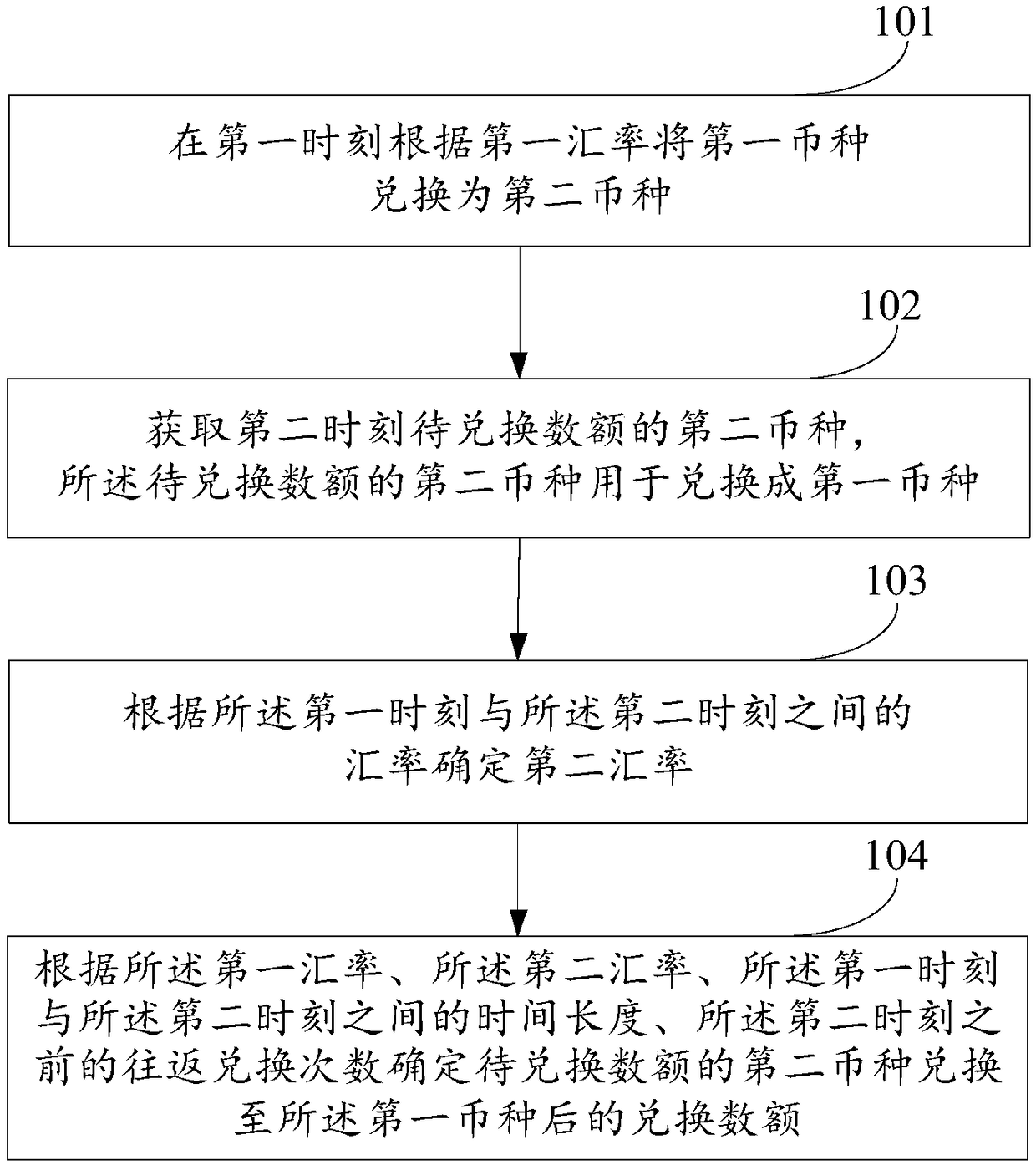
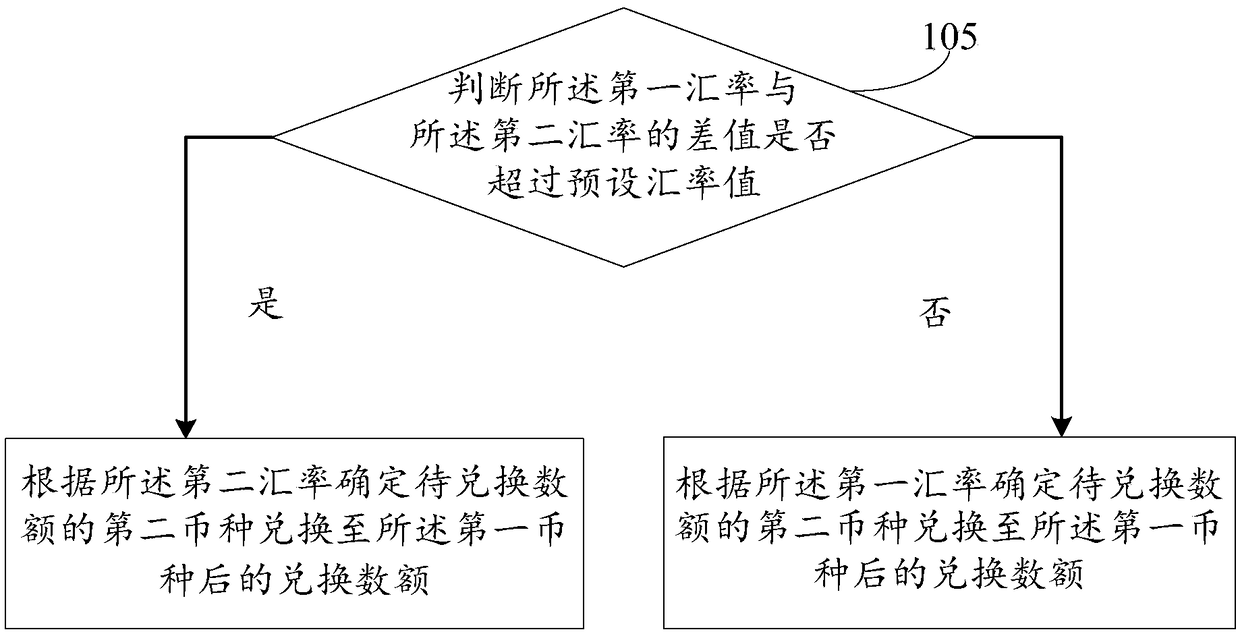
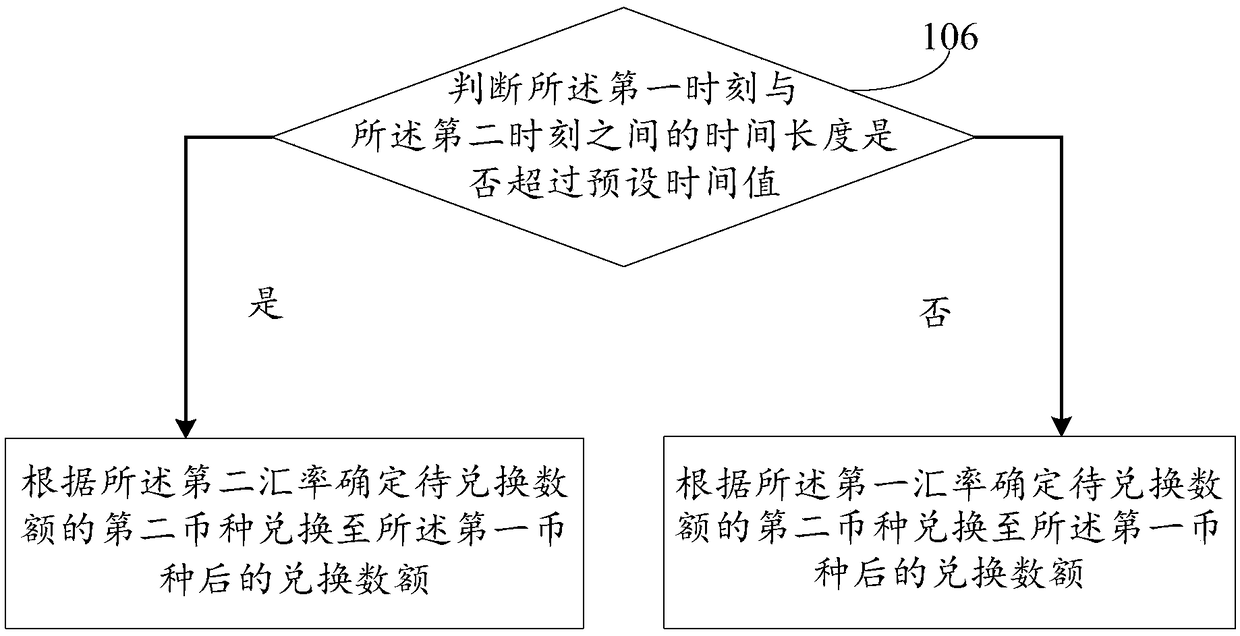
Method and device for exchanging currency
InactiveCN108898486AGuaranteed transactionalAvoid problems with changing account balancesFinanceDistributed computingTime duration
The invention discloses a method and a device for exchanging currency, to alleviate a problem in the prior art of poor user experience caused by a change of balance when a user performs forward and backward conversion. The method includes: exchanging a first currency to a second currency at a first time according to a first exchange rate; acquiring a second currency in amount to be exchanged at asecond time, and exchanging the second currency in the amount to be exchanged into the first currency; determining a second exchange rate according to the exchange rate between the first time and thesecond time; based on the first exchange rate, the second exchange rate, time duration between the first time and the second time, and the number of exchanging prior to the second time, determining the exchanged amount of the second currency in the amount to be exchanged to the first currency. The scheme can make the account balance consistent with that before exchanging in a short period of time,ensure the exchange rate to be stable in a period of time, and prevent a problem of poor user experience caused by the changes of account balance after exchanging due to changes of the exchange rate.
Owner:QILIN HESHENG NETWORK TECH INC
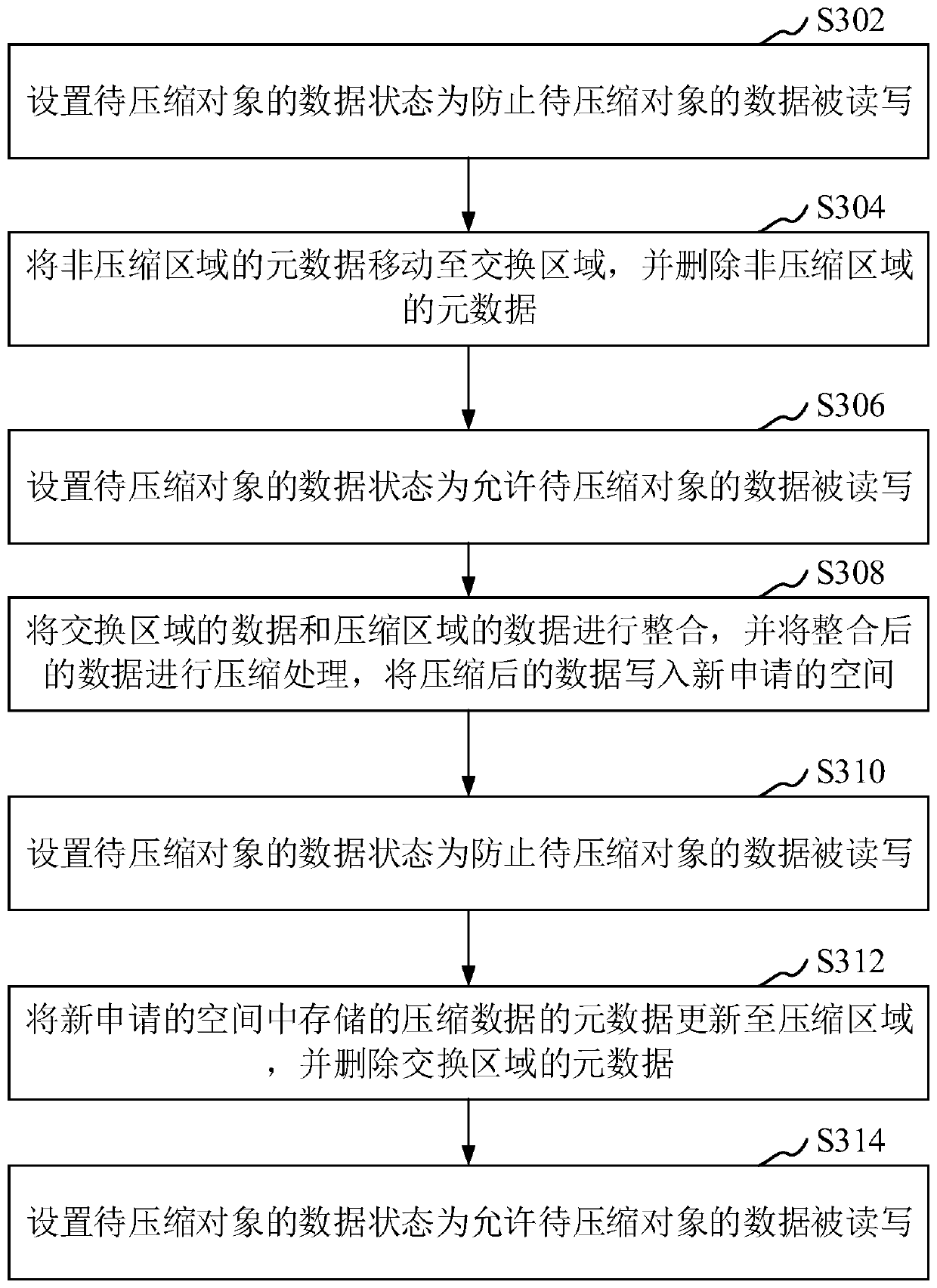
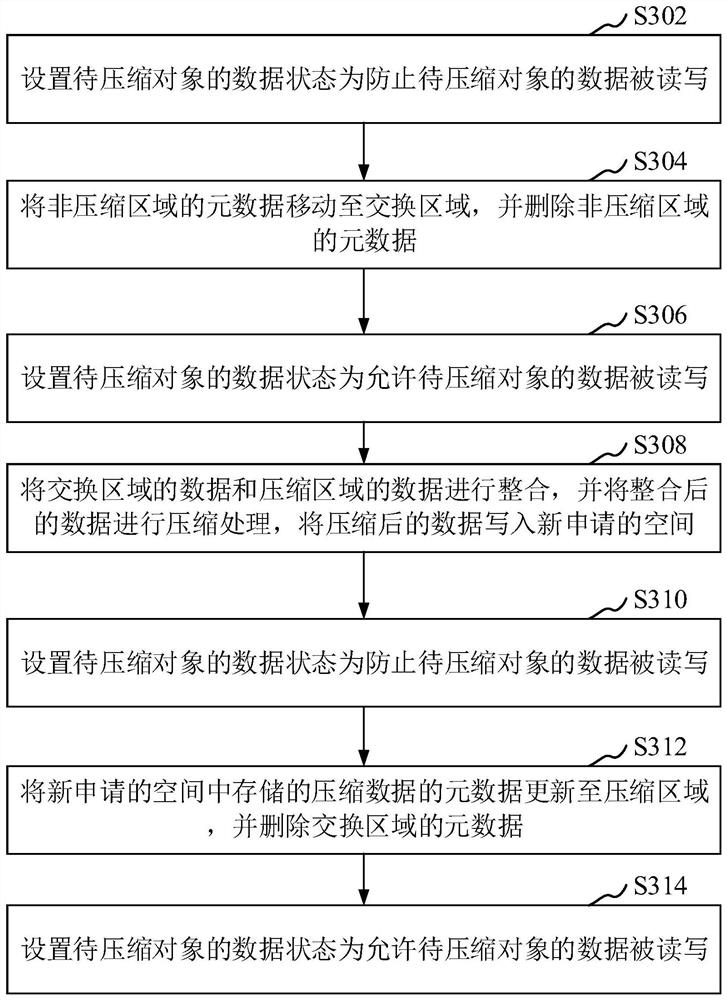
Data compression method, device, computer equipment and storage medium
ActiveCN111459404BImprove experienceGuaranteed transactionalInput/output to record carriersComputer hardwareData compression
The present application relates to the field of data storage, in particular to a data compression method, device, computer equipment and storage medium. The method includes: obtaining the current load condition of the storage system; when the current load condition meets the preset compression requirements, judging whether the data of the object to be compressed stored in the non-compressed area is being read or written; when the to-be-compressed When the data of the object is not being read and written, the data of the object to be compressed is compressed, and during the compression process, when the metadata corresponding to the object to be compressed is processed, the data of the object to be compressed is prohibited from being Read and write, when the data of the object to be compressed is compressed, the corresponding data to be compressed is allowed to be read and written; the compressed data is stored in the compressed area. Adopting this method can take into account both data compression and read and write operations.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method and system for generating electronic receipts and electronic signatures based on Ftp
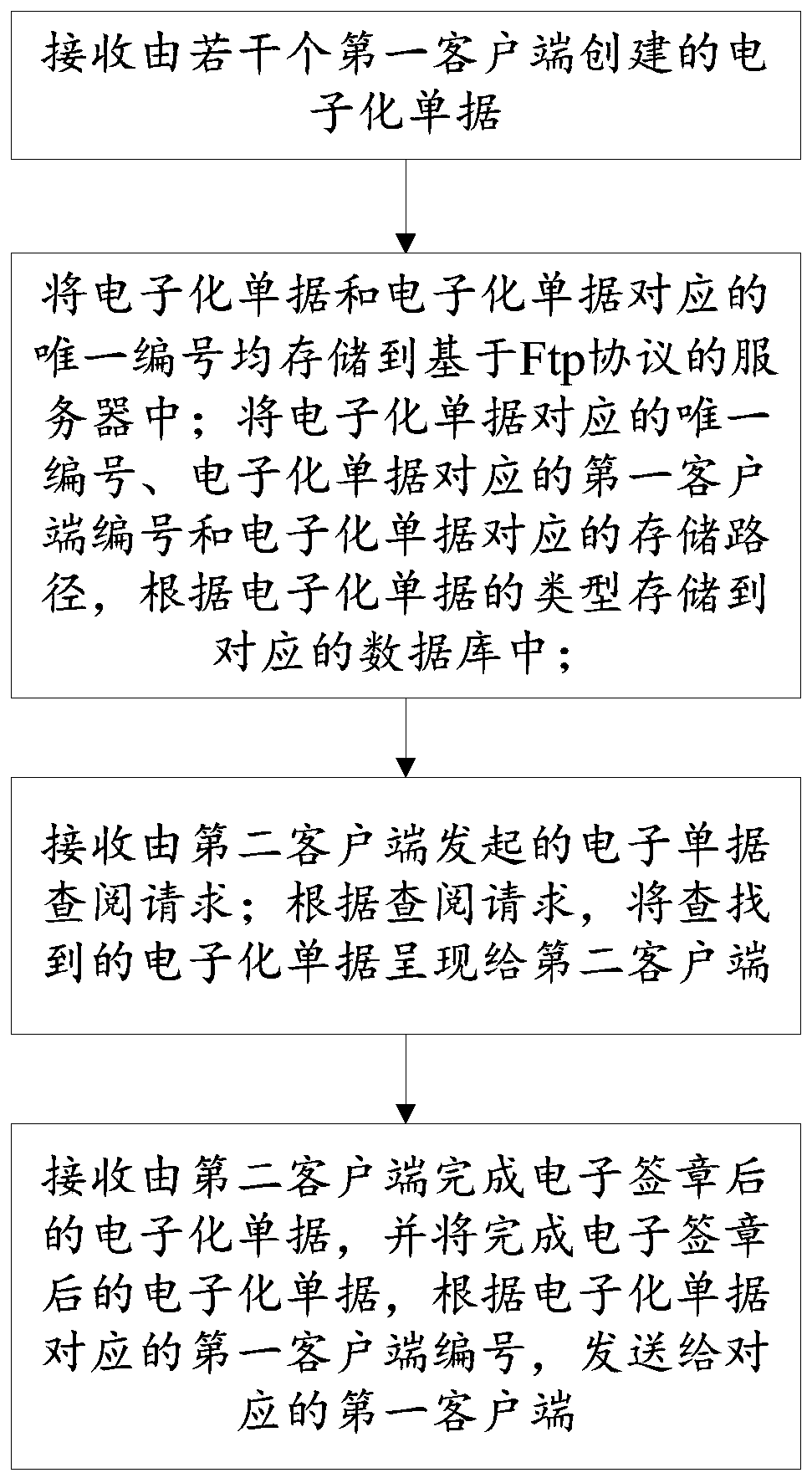
PendingCN110942284AAvoid \"multiple tasks\"Avoid problems such as \"one order with multiple signatures\"Digital data information retrievalUser identity/authority verificationElectronic documentDatabase
The invention discloses an Ftp-based electronic receipt and electronic signature generation method and system. The method comprises the steps of receiving electronic receipts created by a plurality offirst clients; storing the electronized document and the unique number corresponding to the electronized document into a server based on an Ftp protocol; storing the unique number corresponding to the electronized document, the first client number corresponding to the electronized document and the storage path corresponding to the electronized document into a corresponding database according to the type of the electronized document; realizing association between the database and the server based on the Ftp protocol through the unique number corresponding to the electronic document; receivingan electronic receipt consulting request initiated by a second client; presenting the searched electronic receipt to a second client according to the consulting request; and receiving the electronic receipt after the electronic signature is completed by the second client, and sending the electronic receipt after the electronic signature is completed to the corresponding first client according to the first client number corresponding to the electronic receipt.
Owner:SHANDONG LUNENG SOFTWARE TECH +1
Control method and device for non-relational database
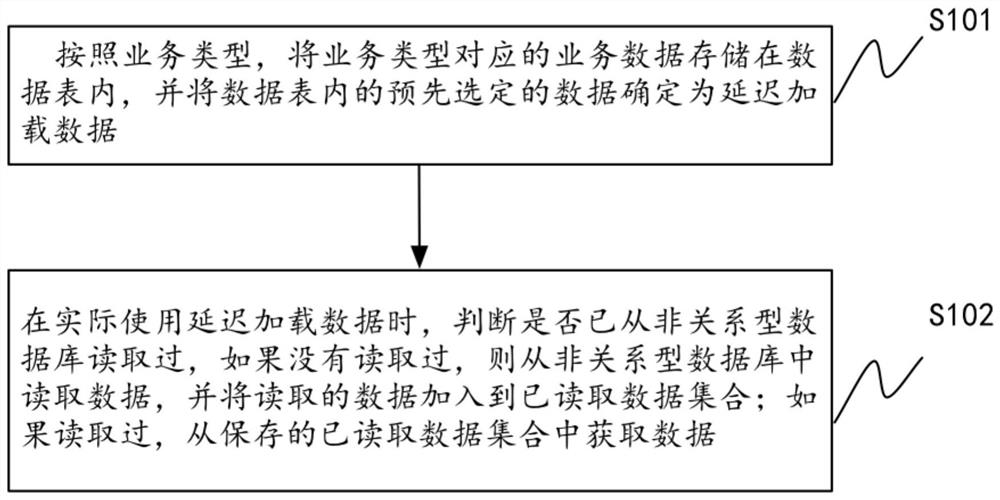
ActiveCN107122435BReduce loadReduce resource overheadSpecial data processing applicationsDatabase indexingTable (database)Datasheet
The present invention provides a control method and device for a non-relational database, wherein the method includes: storing business data in a data table corresponding to the business type according to the business type, and pre-selecting the data in the data table The data is determined as lazy loading data; when the lazy loading data is actually used, it is judged whether the lazy loading data has been read from the non-relational database; if not, it is read from the non-relational database The data is read from the database, and the read data is added to the read data set; if it has been read, the delayed loading data is obtained from the saved read data set. The invention can reduce the resource overhead of the client and the overhead of network transmission, and reduce unnecessary loading of data.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Trading method to eliminate interference from adjacent roads, roadside units and multi-lane systems in the same direction
ActiveCN105184878BGuaranteed transactionalEliminate adjacent road interferenceTicket-issuing apparatusAdjacent-channel interferenceCommunication unit
The invention discloses a transaction method for eliminating the interference of adjacent lanes, which is applied to a multi-lane system in the same direction, wherein each lane is correspondingly provided with a roadside unit for wireless communication with a vehicle-mounted unit, and multiple roadside units cover There is an overlapping area in the range, and the method includes synchronizing the timing of multiple roadside units, and setting the transmission parameters of multiple roadside units to be the same; according to the timing, multiple roadside units send transactions at the same time command, the content of the transaction command is set according to the current transaction steps of each roadside unit itself; the roadside unit that receives the feedback signal from the vehicle-mounted unit completes the current transaction steps with the vehicle-mounted unit. Adopting the present invention can ensure that the vehicle-mounted unit cannot be traded in the overlapping area of the roadside unit, and further ensures that the roadside unit of the current lane cannot trade with the vehicle-mounted unit of the adjacent lane, thereby completely eliminating the interference of the adjacent road.
Owner:SHENZHEN GENVICT TECH
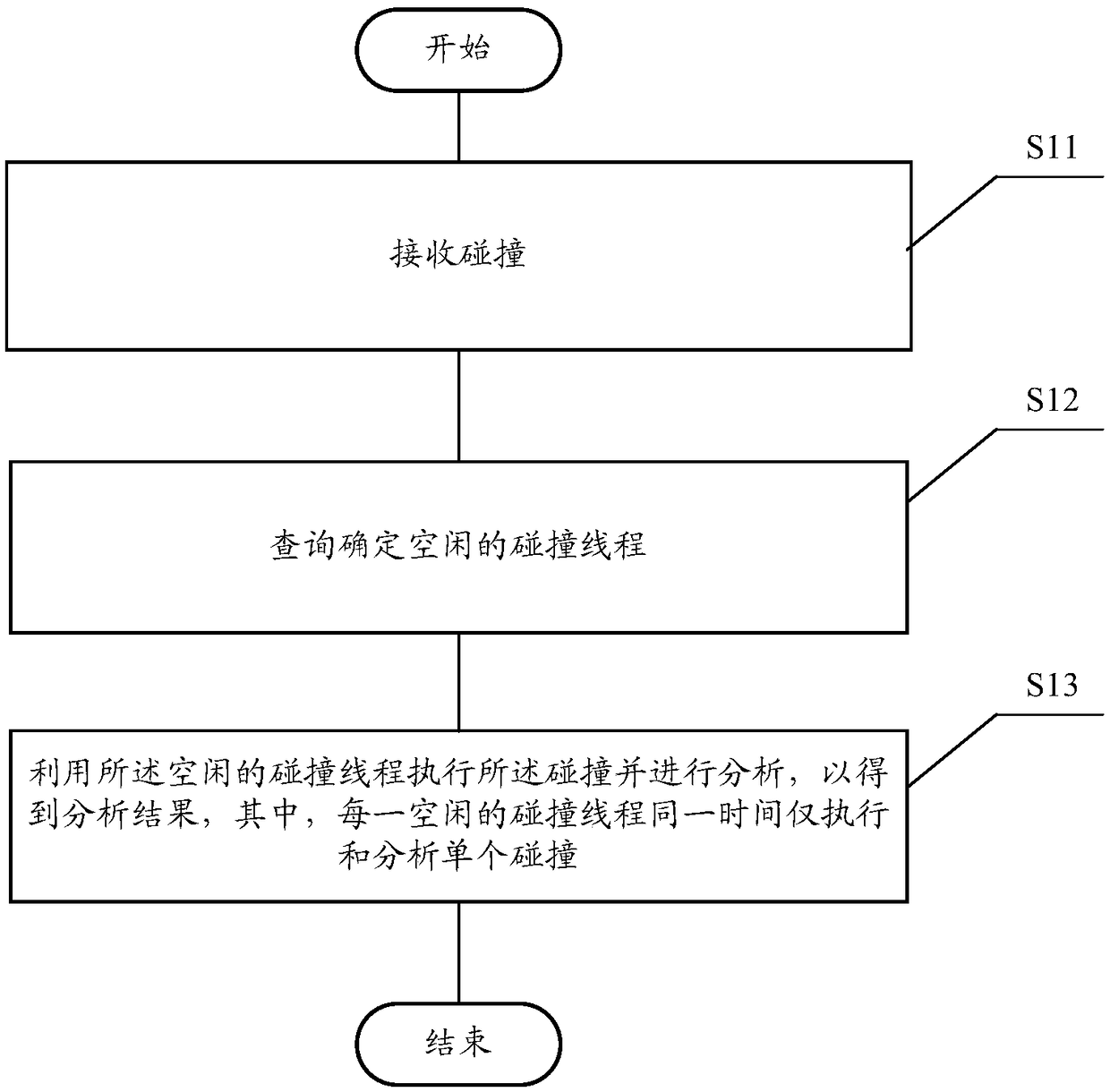
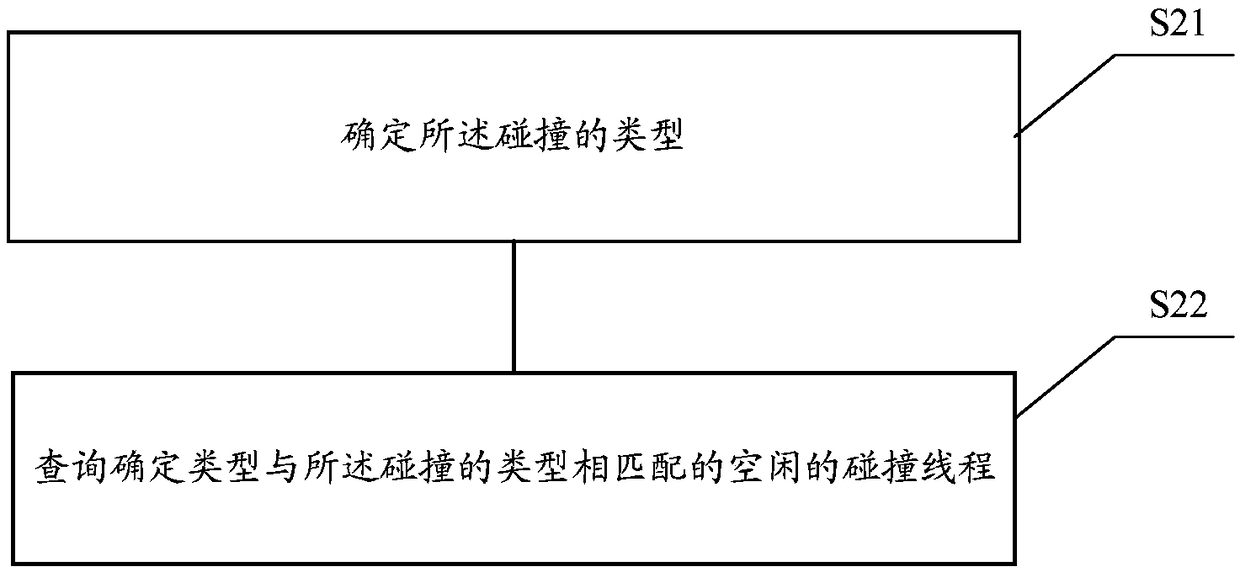
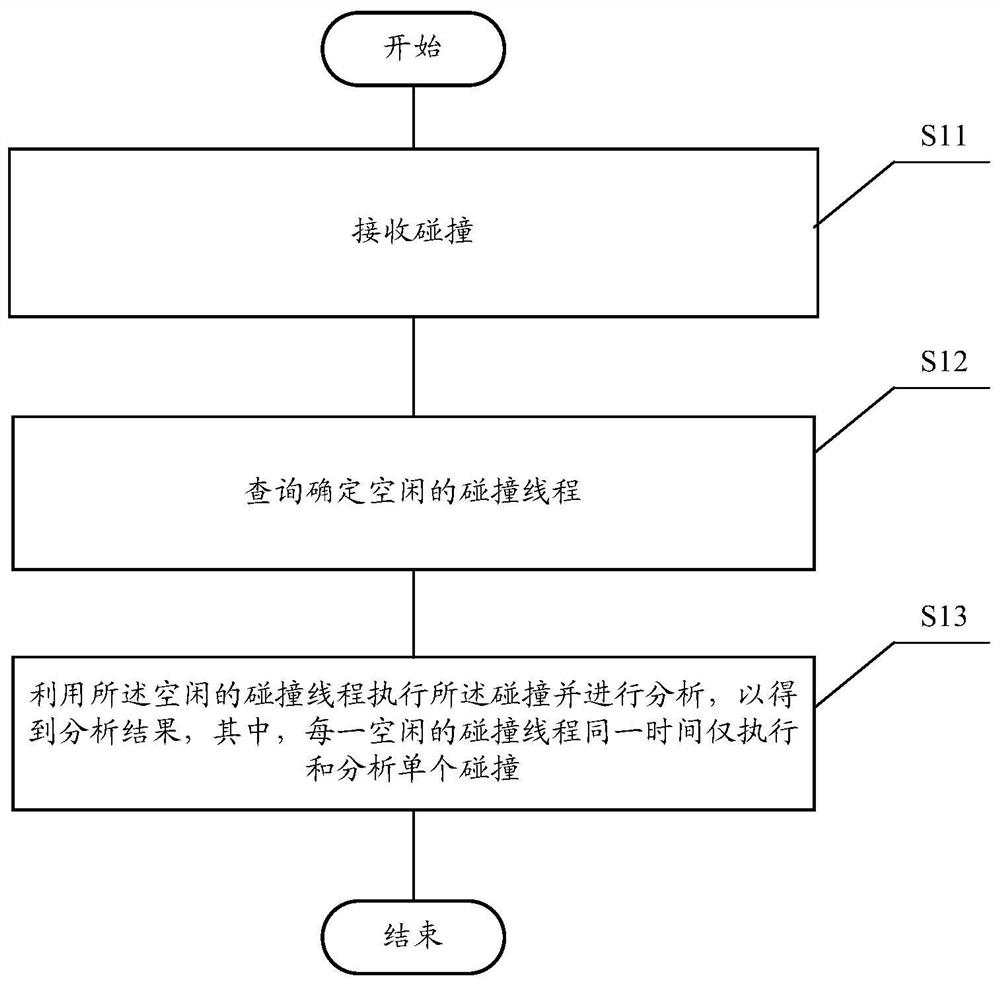
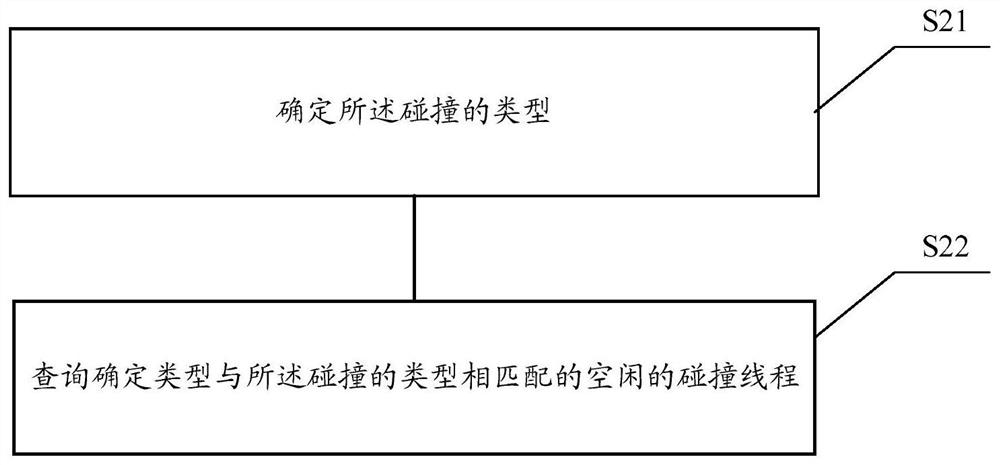
Data collision flow analysis method and device, storage medium, and terminal
ActiveCN108984285AImprove accuracyAvoid lossProgram initiation/switchingParallel computingAnalysis method
The invention relates to a data collision flow analysis method and device, a storage medium and a terminal. The data collision flow analysis method comprises the following steps: receiving collision;carrying out query to determine idle colliding threads; performing and analyzing the collision using the idle collision thread to obtain an analysis result, wherein each idle collision thread performsand analyzes only a single collision at the same time. The technical scheme of the invention can effectively avoid the loss of the circulation data and improve the accuracy of the data analysis.
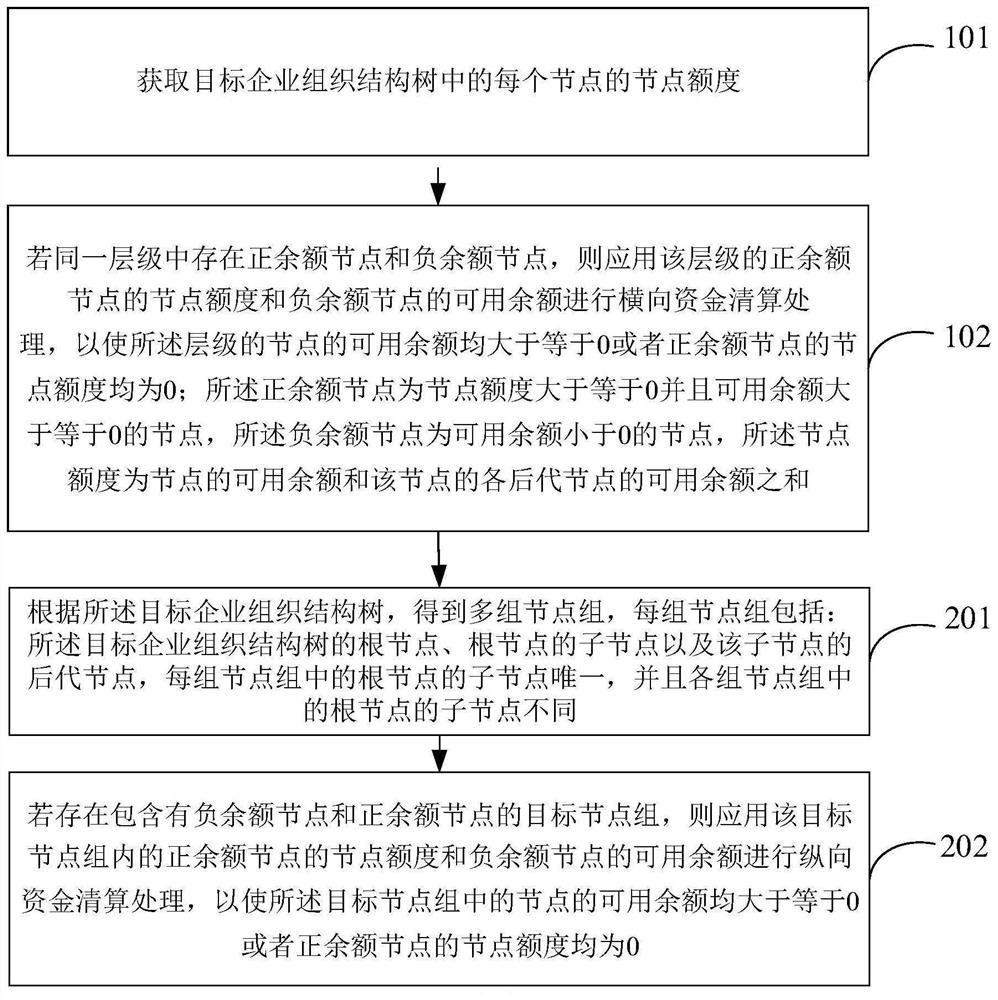
Owner:上海数据发展科技有限责任公司
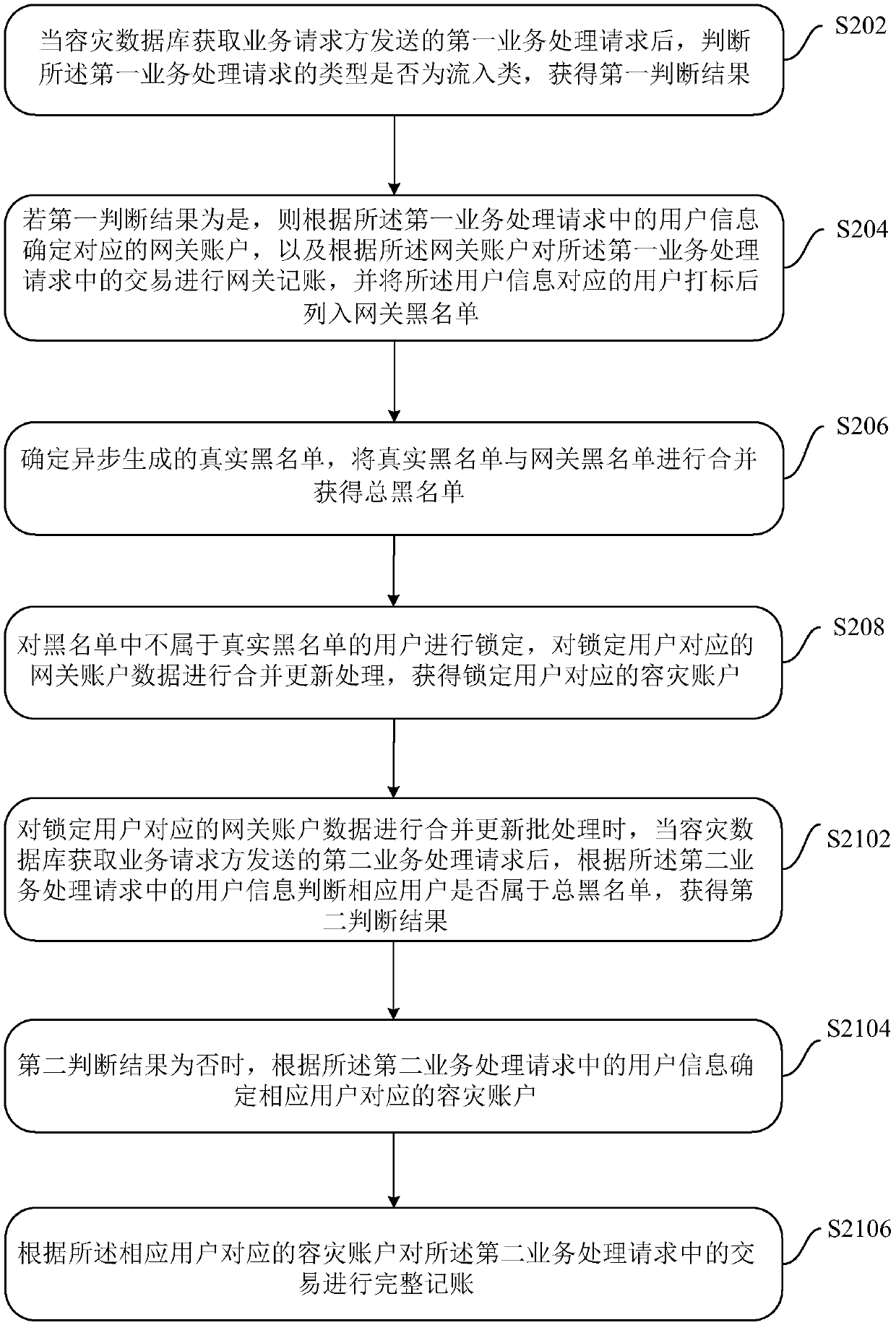
Disaster recovery data processing method, device and system
ActiveCN109614263BTransaction preventionGuaranteed transactionalDatabase updatingDatabase distribution/replicationEngineeringFinancial transaction
Disclosed in the embodiments of the present description are a failover data processing method, apparatus, and system, the method comprising: after a failover database acquires a first service processing request sent by a service requesting party, determining whether the type of the first service processing request is an inflow type and acquiring a first determining result; if the first determining result is affirmative, then determining a corresponding gateway account on the basis of the user information in the first service processing request, performing gateway accounting on a transaction in the first service processing request on the basis of the gateway account, and adding the corresponding user to a gateway blacklist; determining an asynchronously generated real blacklist, and merging the real blacklist with the gateway blacklist to acquire a total blacklist; locking the users in the total blacklist that do not belong to the real blacklist, and merging and updating the gateway account data corresponding to the locked users. Using the embodiments in the present description enables normal transactions of user accounts other than the real blacklist during a failover period.
Owner:ADVANCED NEW TECH CO LTD
A data collision flow analysis method and device, storage medium and terminal
The present invention relates to a data collision flow analysis method and device, a storage medium, and a terminal. The data collision flow analysis method includes the following steps: receiving a collision; querying and determining an idle collision thread; using the idle collision thread to execute the collision And analysis is performed to obtain analysis results, wherein each idle collision thread only executes and analyzes a single collision at the same time. The technical scheme of the invention can effectively avoid the loss of circulation data and improve the accuracy of data analysis.
Owner:上海数据发展科技有限责任公司
Implementation method of fault-tolerant distributed security event data transmission protocol
The invention aims to provide an implementation method of a fault-tolerant distributed security event data transmission protocol. Security events are handled through a distributed cluster, and event nodes in the cluster are determined through a periodical election mechanism in order to ensure the transaction of message data. A message queue mechanism is adopted for the nodes in the cluster in order to ensure the concurrency and expandability of security event handling. Thus, a fault-tolerant security event transmission mechanism is implemented. The method comprises the following steps that: A, security events in a whole network are handled through an event handling distributed cluster; B, the event handling cluster periodically elects event nodes Transactional; C, scoring factors of event nodes Transactional election are determined; D, one Performer node can process security event transmission requests of a plurality of Performer nodes concurrently; and E, the Performer node processes messages.
Owner:中国南方电网有限责任公司信息中心 +1
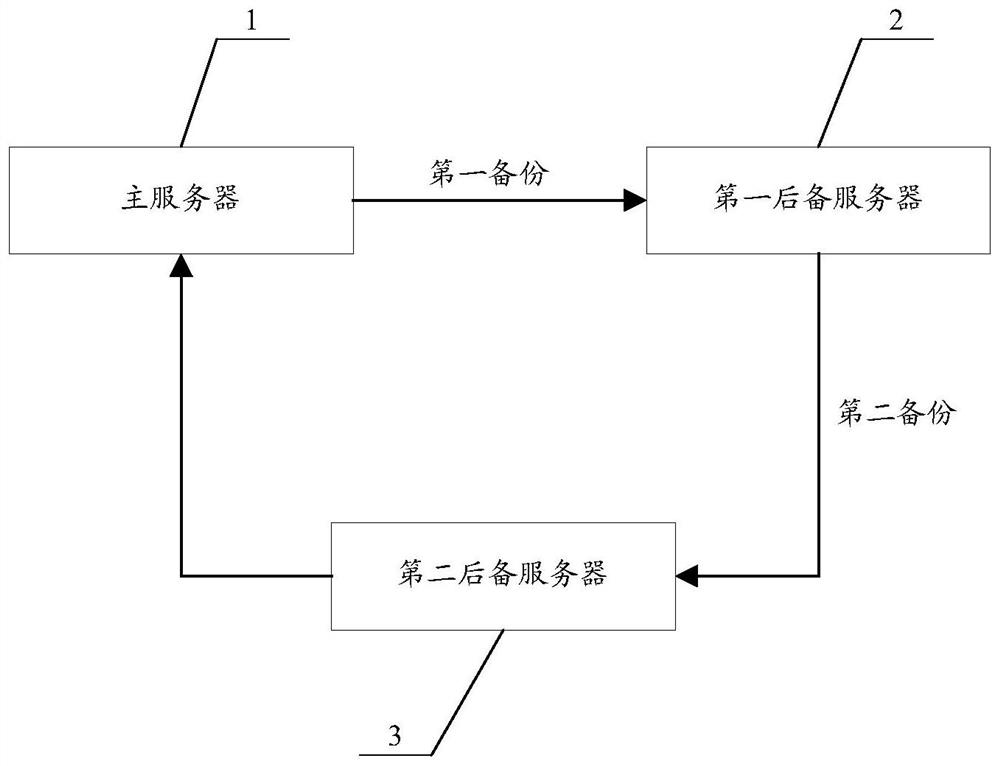
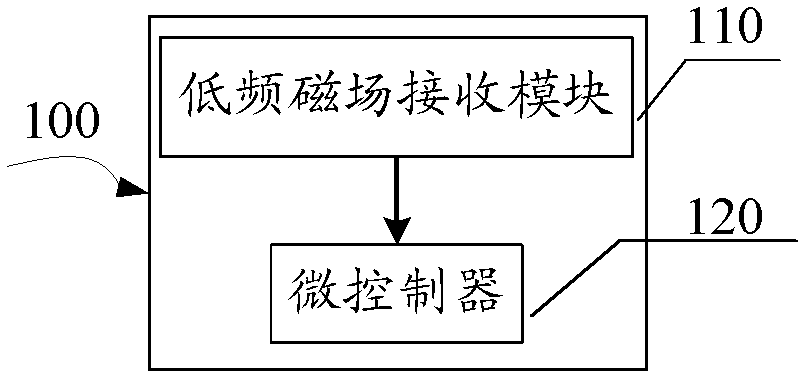
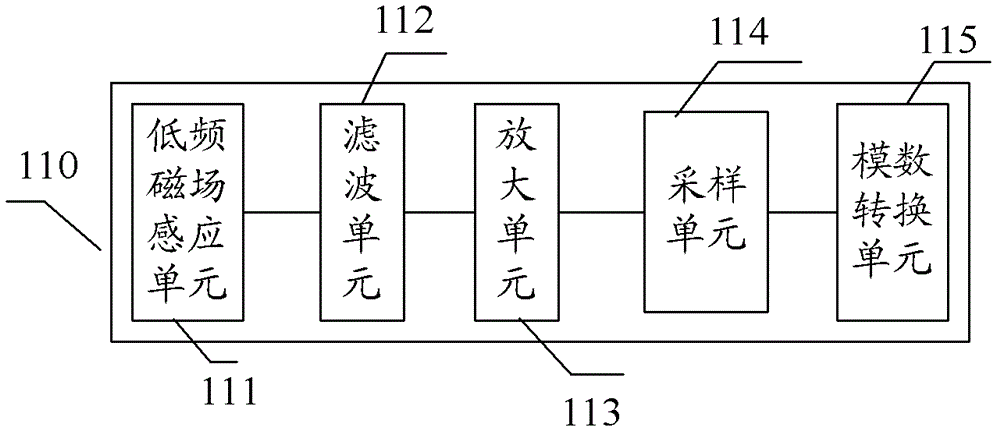
Device, method, and card reader for low-frequency magnetic field signal detection
ActiveCN102799843BGuaranteed transactionalGuaranteed correctnessNear-field transmissionSensing record carriersMicrocontrollerComputer module
The invention discloses a detection device and a method thereof of low-frequency magnetic field signals and a card reader, wherein the detection device comprises a low-frequency magnetic field receiving module used for receiving low-frequency magnetic field signals emitted from a low-frequency magnetic field emission source, and a microcontroller used for determining whether the low-frequency magnetic field emission source fault occurs according to the receiving result of the low-frequency magnetic field signals by the low-frequency magnetic field receiving module. The detection device can be used for determining whether the work of the current low-frequency magnetic field emission source is normal or not, and informing the low-frequency magnetic field emission source of adjusting corresponding low-frequency emission parameters when detecting that the work of the emission source is abnormal, so that the normal work of the low-frequency magnetic field emission source is ensured.
Owner:NATIONZ TECH INC
A transaction-based method for reading and writing large-capacity data
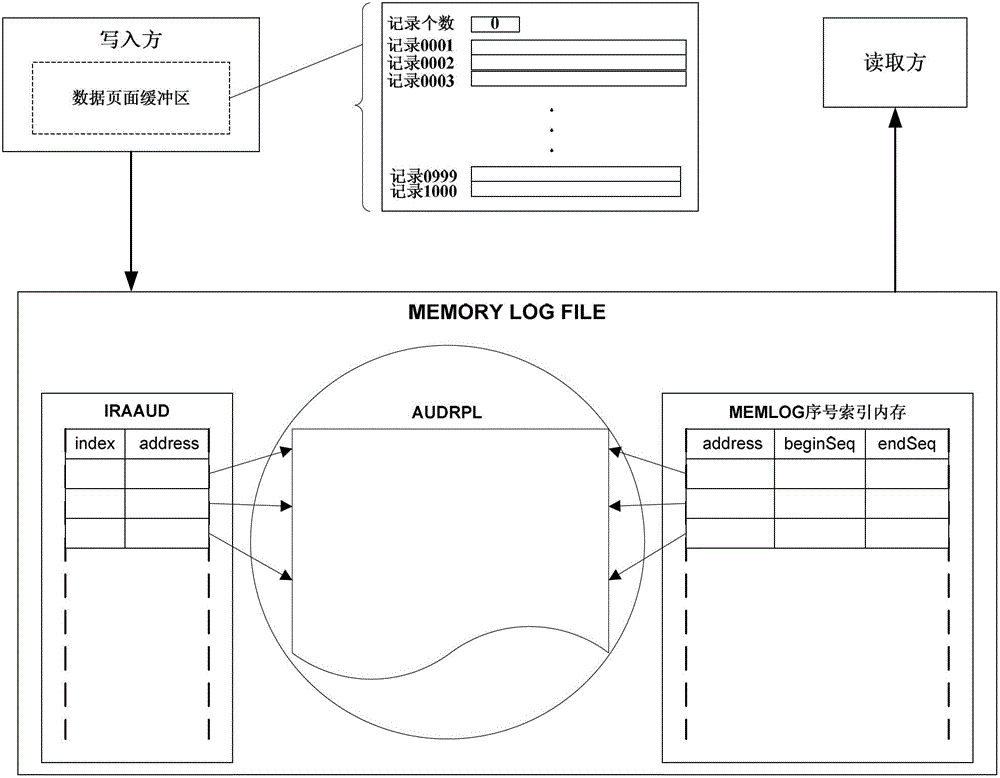
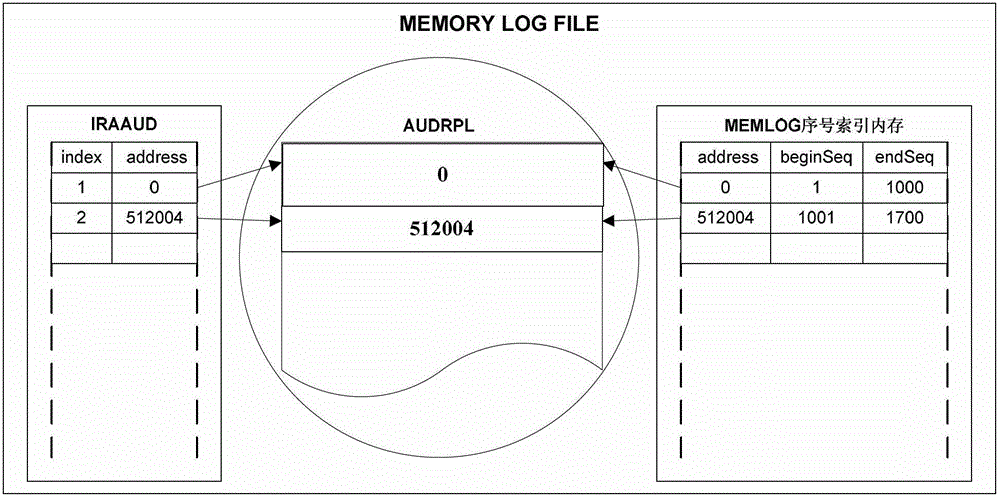
ActiveCN102929935BImprove speed performanceGood choiceInput/output to record carriersSpecial data processing applicationsBatch processingTime delays
The invention relates to the technical field of electronic information and electronic information data operation, and particularly relates to transaction-based large-volume data read and write methods. According to the write method, data records are organized by virtue of data pages and then are subjected to batch processing, and simultaneously, a great deal of transactional write operation is converted into non-transactional write operation, so that the data volume of transactional read and write is reduced effectively; and by virtue of transaction characteristics of index files, the integrity and the transaction of data are ensured, and the efficient read-write of the mass data is achieved. According to the reading method, a data page index is established by a shared memory, and the quick positioning of the data records is realized by using a bisection method. In an occasion that the mass data need to be subjected to the transactional read-write, the transaction-based large-volume data read and write methods can be used for achieving the aims of reducing the IO (input / output) operation, improving the handing capacity and shortening the time delay.
Owner:上交所技术有限责任公司
An interactive method based on command line data of network management system
ActiveCN105847041BReduce the number of interactionsReduce the difficulty of download status maintenanceData switching networksNetwork managementRollback
Owner:FENGHUO COMM SCI & TECH CO LTD
Transaction method and device, electronic equipment and computer readable storage medium
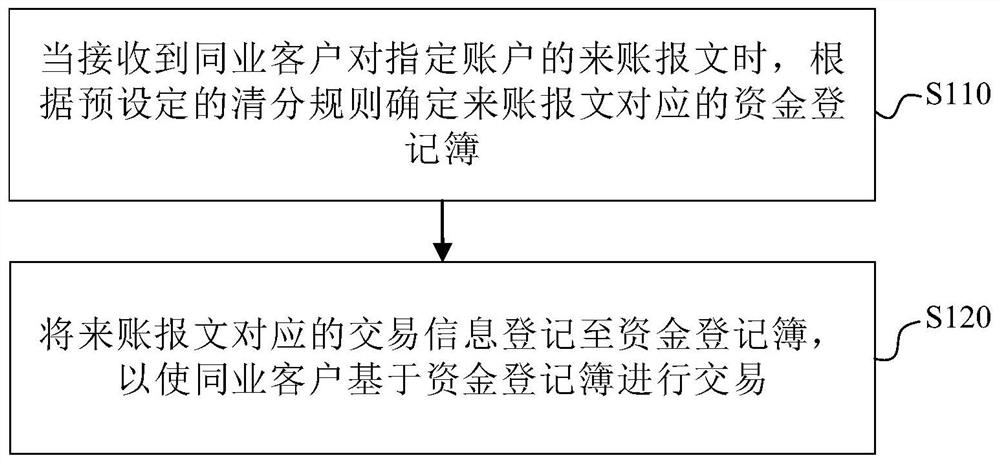
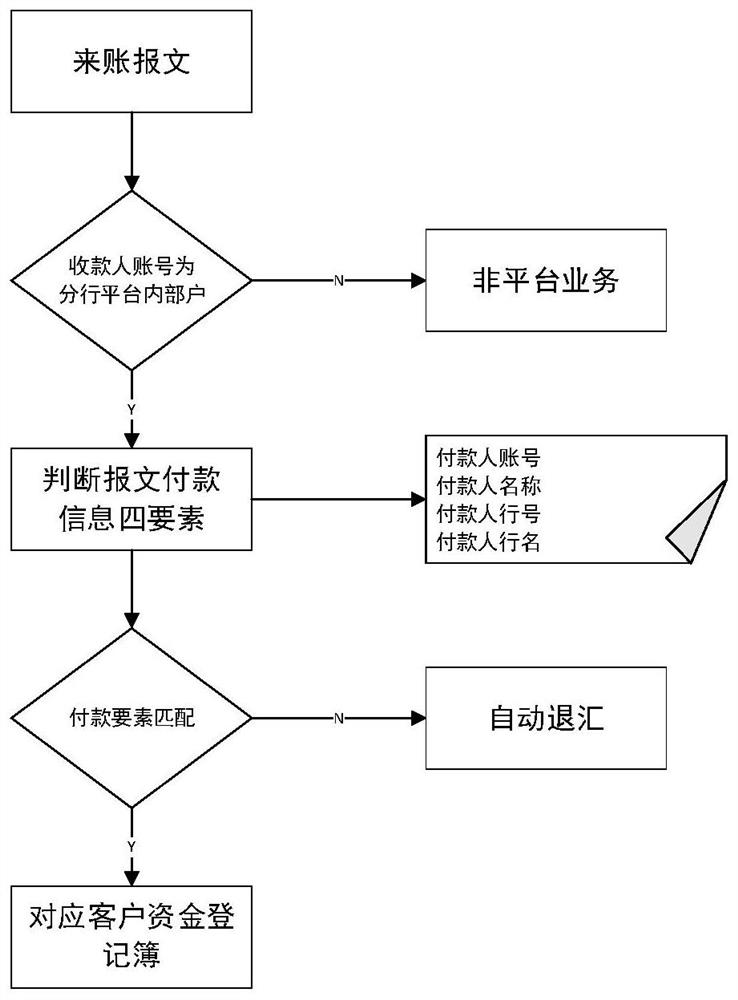
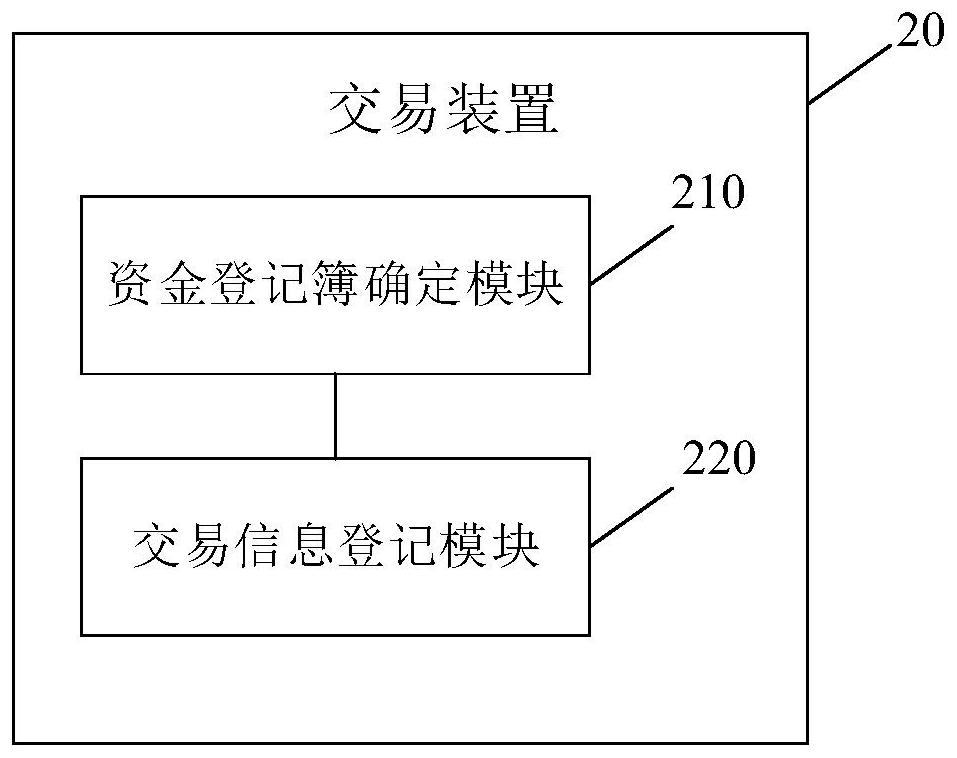
PendingCN112348683AMeet the needs of fast and easy transactionGuaranteed transactionalFinanceOffice automationEngineering managementSystems engineering
The embodiment of the invention provides a transaction method and device, electronic equipment and a computer readable storage medium. The method comprises the steps of determining a fund registrationbook corresponding to an incoming account message according to a preset clearing rule when the incoming account message of a client in the same industry for a specified account is received; and registering the transaction information corresponding to the incoming account message in the fund registration book, so that the client in the same industry can perform transaction based on the fund registration book. Based on the scheme, the enrollment of the same-industry clients can be registered through the fund registration book, and the same-industry clients can perform transaction based on the fund registration book, so that tedious procedures during account opening are avoided, the requirement of the same-industry clients for rapid and convenient transaction can be met, and the normal transaction of the same-industry clients is ensured.
Owner:CHINA CITIC BANK
Block chain data processing method, node equipment and system
PendingCN112487101AAvoid occupyingGuaranteed Normal ConsensusFinanceDatabase distribution/replicationData packEngineering
The embodiment of the invention provides a block chain data processing method, node equipment and a system. The method comprises the following steps of receiving a plurality of message data sent by other consensus nodes, wherein the message data comprises a block chain group identifier, screening the plurality of message data according to a first data volume of the plurality of message data and anode maximum communication flow of a consensus node to obtain primary message data, and screening the primary message data according to a group maximum communication flow of each block chain group toobtain secondary message data, and processing the secondary message data. According to the method and the device, the message data is screened twice according to the maximum communication flow of theconsensus node and the maximum communication flow of the group respectively, so that the screening of a node level and a group level is realized, and the resource preemption is avoided when a plurality of block chain groups are operated on the same consensus node, and thus, the block chain group can perform normal consensus and transaction.
Owner:WEBANK (CHINA)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com