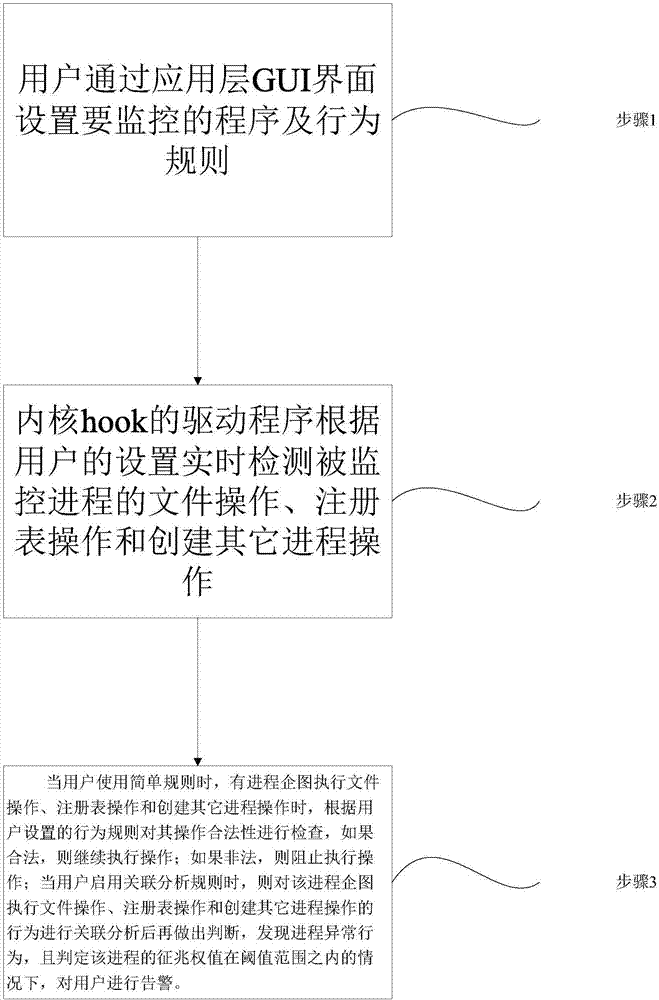
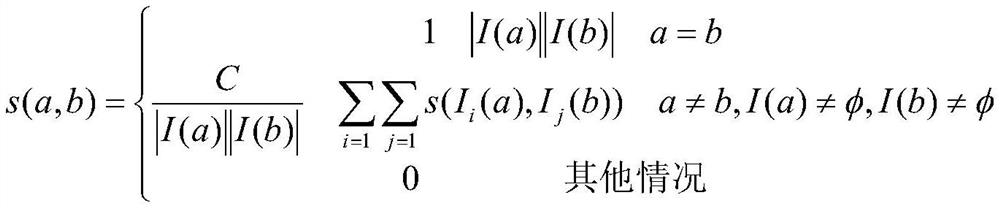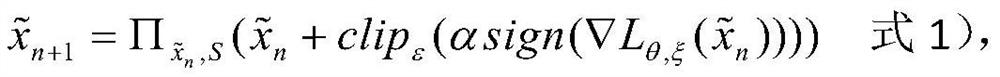Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
98results about How to "Achieve defense" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
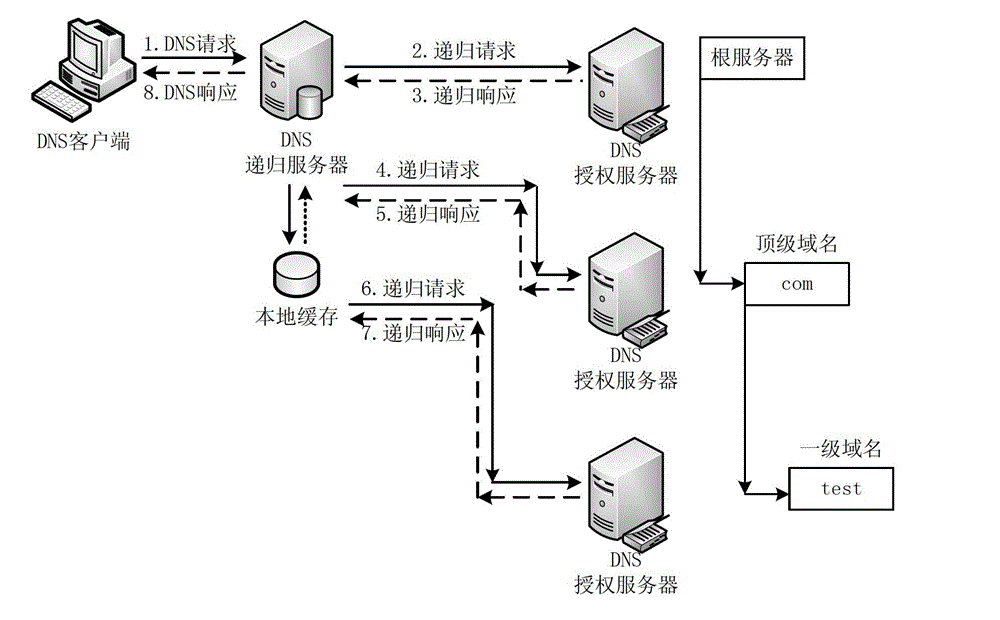
Defense method, device and system for DNS (Domain Name System) services
The invention provides a defense method, a defense device and a defense system for DNS (Domain Name System) services. The method comprises: monitoring a DNS data query request message flux of a DNS recursive server network gateway within unit time; judging whether the DNS data query request message flux exceeds a predetermined safety access flux threshold value or not; obtaining a proportional value between the quantity of DNS data query request messages containing top-level domain addresses and the DNS data query request message flux; in the case of judging the proportional value to exceed the predetermined value, recording the top-level domain addresses as attacked addresses; transmitting the DNS data query request messages of which the domain addresses are not the attacked addresses; judging whether second-level domain addresses of the DNS data query request messages corresponding to the attacked addresses exist in a normal domain name list or not; and performing defense processing on the DNS data query request messages of which the second-level domain name addresses do not exist in the normal domain name list. The transmission of attack messages can be effectively decreased, so that the defense of a DNS server is realized; and meanwhile, the normal DNS data query request is not affected.
Owner:BEIJING LEADSEC TECH
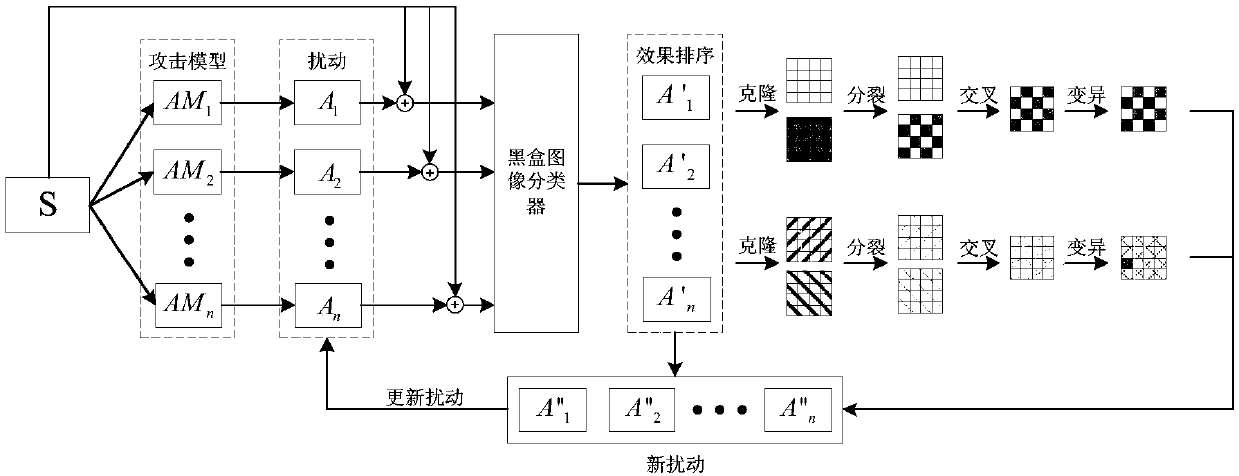
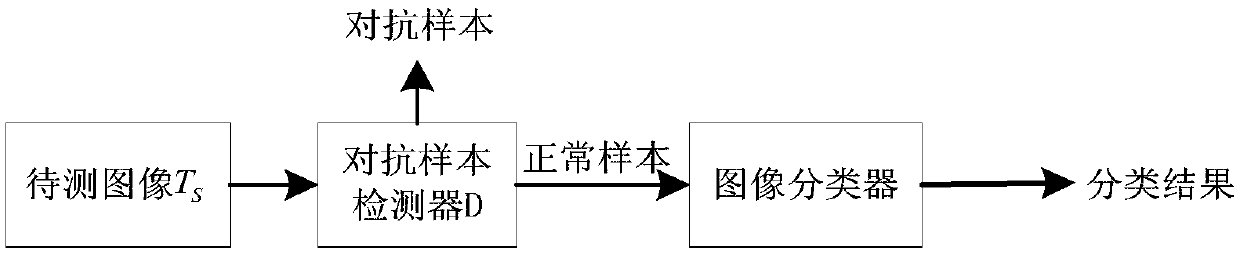
Image classifier adversarial attack defense method based on disturbance evolution
ActiveCN108615048AIncrease diversityEfficient detectionCharacter and pattern recognitionGenetic algorithmsAttack modelBox model
The invention discloses an image classifier adversarial attack defense method based on disturbance evolution. The method comprises the following steps that 1) the sample is attacked by different attack models so as to obtain different types of disturbance; 2) a block box model is attached by the adversarial sample corresponding to the disturbance and the attack effect is ordered; 3) cloning, crossing, variation and other operation are performed on the disturbance of great attack effect so as to obtain the new disturbance; 4) the disturbance is updated by using the parent-child hybrid selectionmode so as to achieve the objective of disturbance evolution; 5) an adversarial sample detector is trained by the adversarial sample corresponding to the evolved disturbance and the normal sample; and 6) when the detection sample is detected, detection is performed by using the adversarial sample detector firstly and then the normal sample is inputted to the black box model and the class is returned so as to achieve the adversarial attack defense effect.
Owner:ZHEJIANG UNIV OF TECH
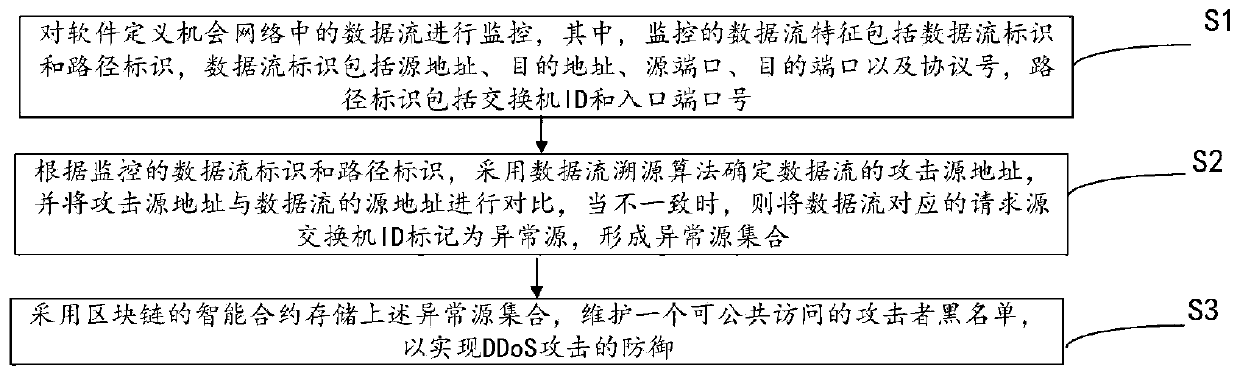
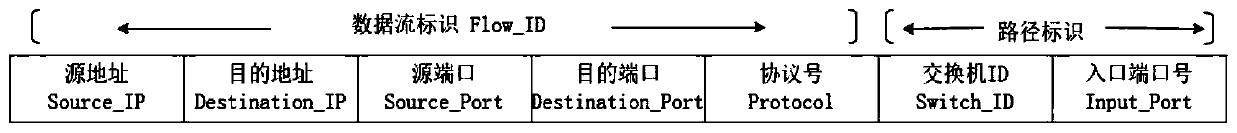
Software defined opportunity network DDoS defense method based on block chain
ActiveCN110113328AGuaranteed reliabilityPrevent tamperingTransmissionTraffic characteristicControl layer
The invention discloses a software defined opportunity network DDoS defense method based on a block chain. Firstly, the characteristic that the SDN can perform logic centralized management and controlon a control layer is utilized; the network state is dynamically monitored in real time; then, the possibility of existence of a DDoS amplification attack is analyzed by analyzing the traffic characteristics obtained by monitoring, an attacker address is determined according to a traceability algorithm, and finally, a public accessible attacker blacklist is maintained by using a block chain architecture to assist an application layer in malicious traffic filtering so as to realize defense of the DDoS attack. According to the method, the attack source tracking accuracy is improved, the storage of the attack source blacklist address is realized in combination with the block chain architecture, and the attack source storage architecture based on the distributed account book technology can effectively prevent the data from being tampered or damaged while maintaining the data reliability. The whole network can perform filtering in a data packet receiving stage by inquiring a blacklist address, so that the DDoS attack is prevented from the source.
Owner:WUHAN UNIV OF TECH
Method and system for defending address analysis protocol message aggression
InactiveCN101415012AEffective interceptionEffective attackData switching networksAddress Resolution ProtocolAddress resolution
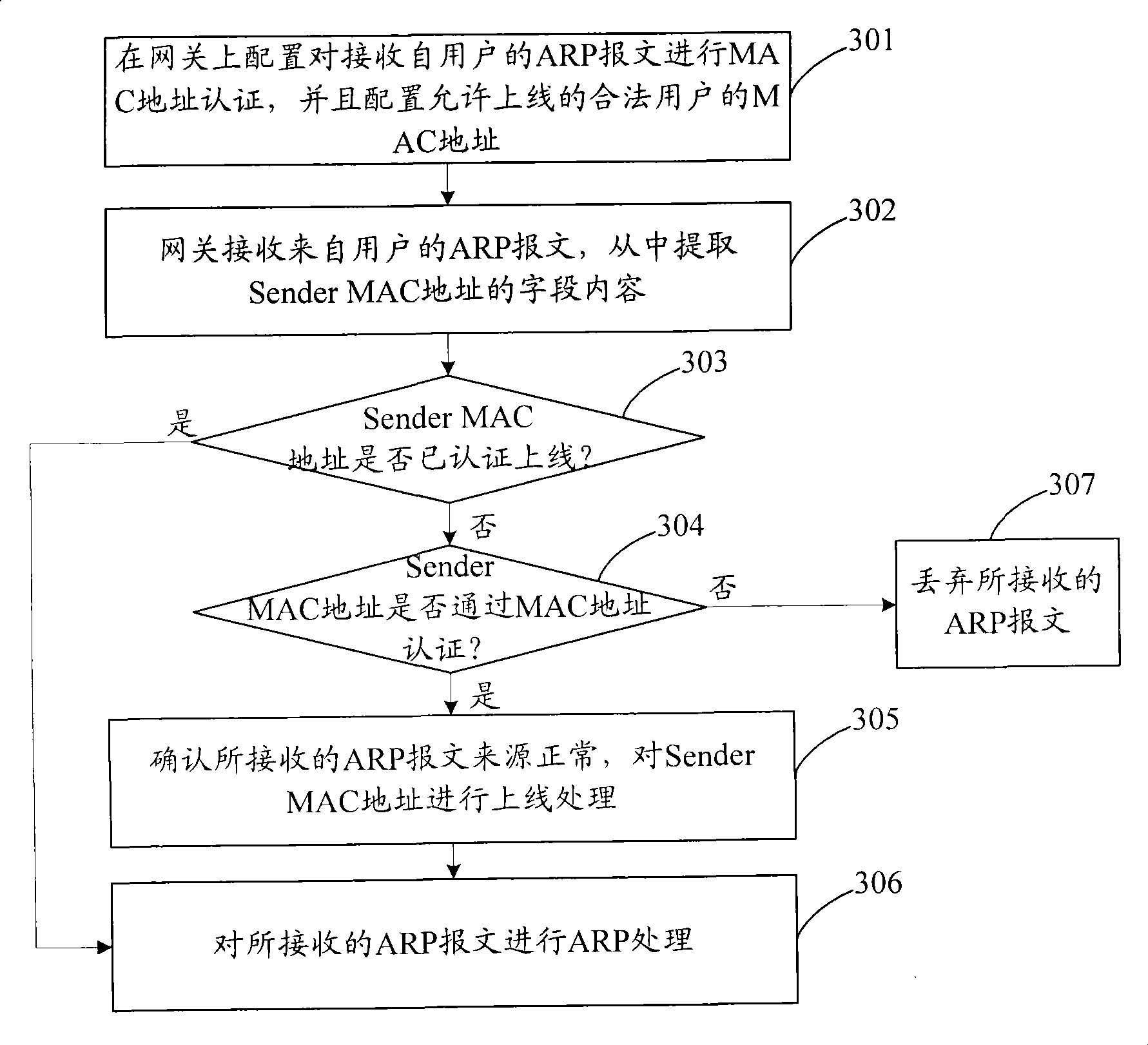
The invention discloses a method used for defending address resolution protocol message attack, comprising the steps as follows: media access control MAC address of legal user is configured in advance; network equipment receives the address resolution protocol ARP message coming from the user; the field content of the MAC address of the sender is extracted out of the received ARP message; whether the extracted MAC address of the sender is the MAC address of the legal user configured in advance or not is judged; if not, the received ARP message is abandoned. The invention also discloses a system which can defend the address resolution protocol message attack. The method and the system are suitable for the users which adopt all types and do not need to modify the network equipment greatly.
Owner:NEW H3C TECH CO LTD
Mid-long-term unit commitment optimizing method
ActiveCN102097866AImprove driving abilityIncrease resourcesCircuit arrangementsMinimum deviationCommitment scheme
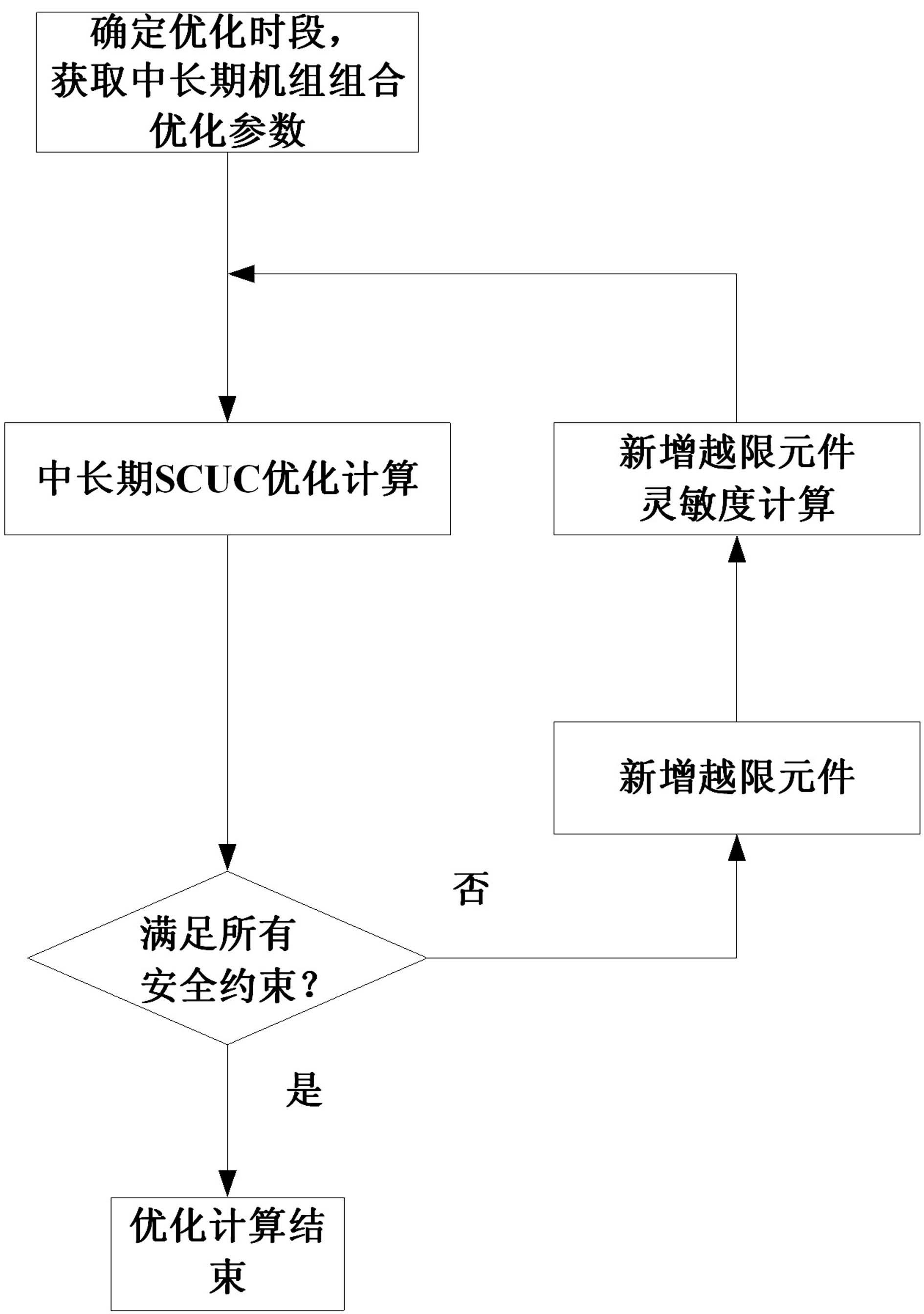
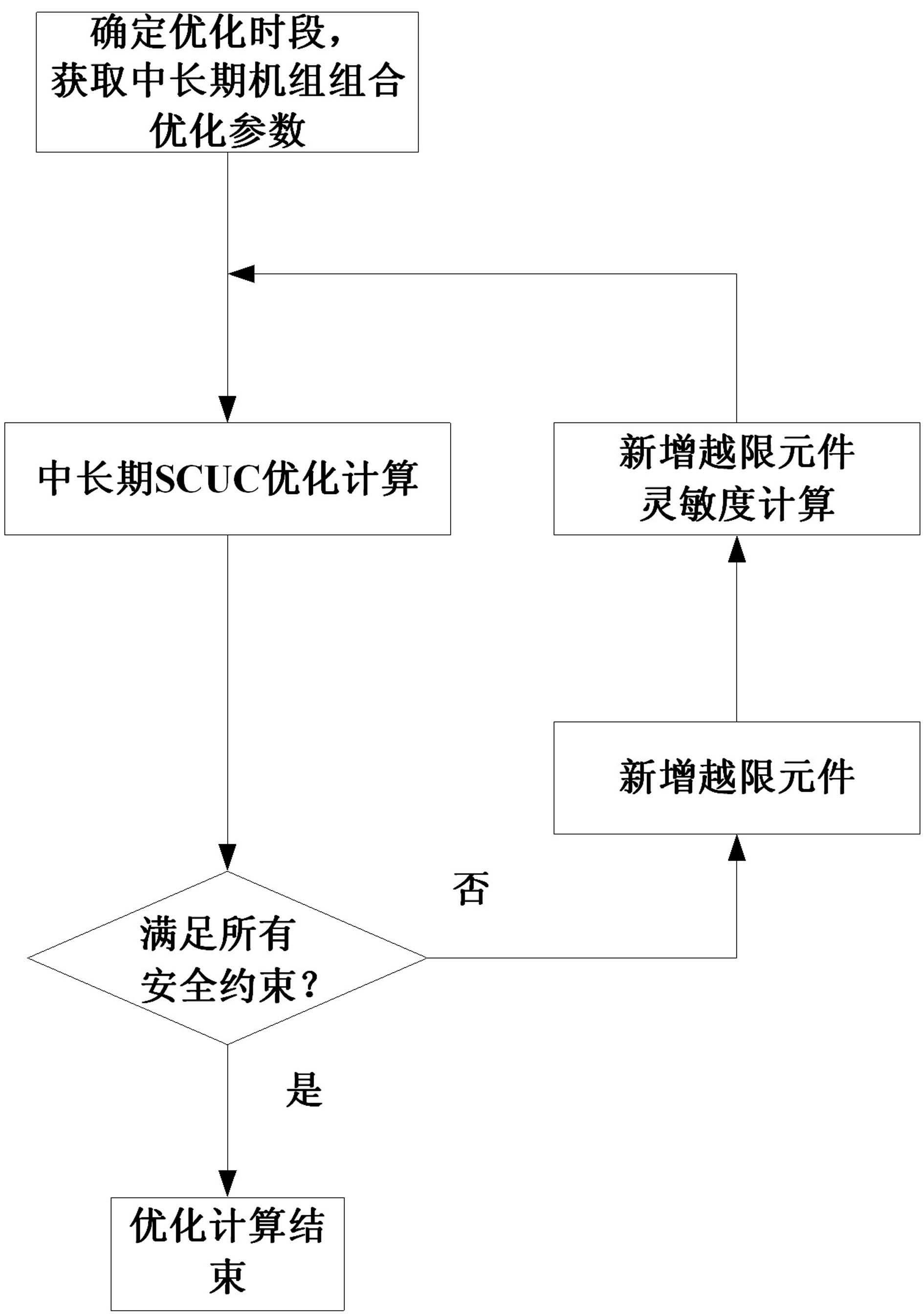
The invention discloses a mid-long-term unit commitment optimizing method. The method comprises the following steps: acquiring various optimized data to determine the optimal space of mid-long-term unit commitment; then establishing a mid-long-term security constrained unit commitment model with minimum deviation between the generated energy of the unit and the expected electric quantity as the target according to the practical power grid model; adopting the mixed integer programming approach to compute the starting / stopping state, load factor and active power output in the peak load period of the unit in each day in the dispatching period; considering all the network monitoring components and adopting the daily maximum load point to carry out security check according to the starting / stopping state and power output in the peak load period of the unit which are obtained through optimization; and finally acquiring the mid-long-term unit commitment scheme satisfying the power grid security through the optimization technology and iteration of security check. The large power grid steering capability and the power resource optimal allocation capability are greatly improved by adopting the method.
Owner:NARI TECH CO LTD +1
Annual power generation plan rolled decomposition optimization method taking balance between plan finishing rate and load rate into consideration
ActiveCN104616069AImplement trackingRealize regulationForecastingInformation technology support systemLinear programming algorithmDecomposition
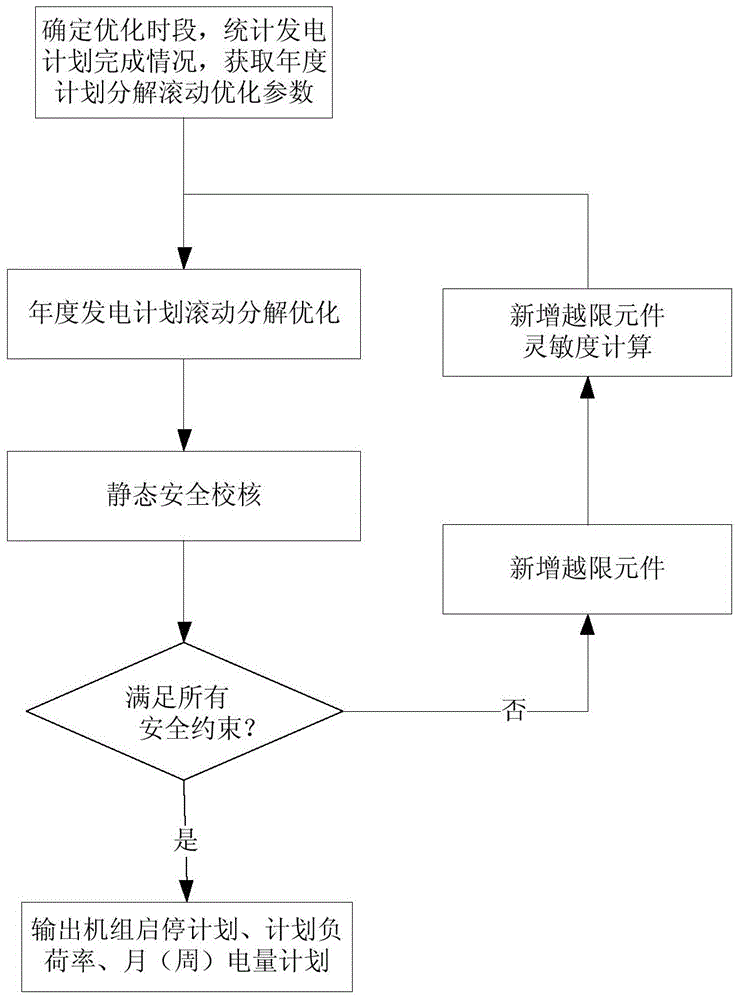
The invention discloses an annual power generation plan rolled decomposition optimization method taking balance between plan finishing rate and load rate into consideration; the method comprises the following steps: (1) determining a plan period and a plan parameter requiring the annual power generation plan rolled decomposition optimization; (2) establishing a security constraint machine set combined optimization model applicable to the annual power generation plan rolled decomposition; (3) using a mixed integer linear planning algorithm to calculate start and stop states, the plan load rate and the peak and valley active outputs of the machine set at each plan period; (4) implementing the security check, judging if all security constraints are satisfied; if all the security constraints are satisfied, going to step (5); if not all the security constraints are satisfied, adding a new out-of-limit element, and calculating sensitivity information of the newly added out-of-limit element, going to step (2). The disclosed method circularly optimizes and drafts the machine set start and stop plan as well as the machine set average plan load rate, drafts monthly, weekly and daily power generation amount plans of the power plant; the disclosed method ensures the execution of the annual power generation amount plant, and achieves the purpose of saving energy and reducing emission.
Owner:NARI TECH CO LTD +2
Intelligent substation network intrusion detection system and detection method based on deep learning
PendingCN110086776AAchieve defenseAchieve unificationTransmissionNeural learning methodsSmart substationFeature extraction
The invention belongs to the technical field of transformer substation network intrusion detection, and particularly relates to an intelligent transformer substation network intrusion detection systemand method based on deep learning. The system is used for intrusion detection aiming at network attacks of an IEC61850 communication protocol of an intelligent substation. The system comprises a datacollection module, a feature extraction module, a behavior analysis module and a defense behavior trigger module which are sequentially connected, wherein the data collection module is connected to an intelligent substation network to collect data, the defense behavior trigger module is connected to the intelligent substation network, the network information flow based on the IEC61850 protocol inthe intelligent substation is collected and analyzed in real time, and abnormal communication behaviors are detected and alarmed in real time.
Owner:ECONOMIC TECH RES INST OF STATE GRID HENAN ELECTRIC POWER
Machine learning training data poisoning attack defense method
ActiveCN111914256AAchieve defenseWork around limitationsPlatform integrity maintainanceMachine learningData setAttack
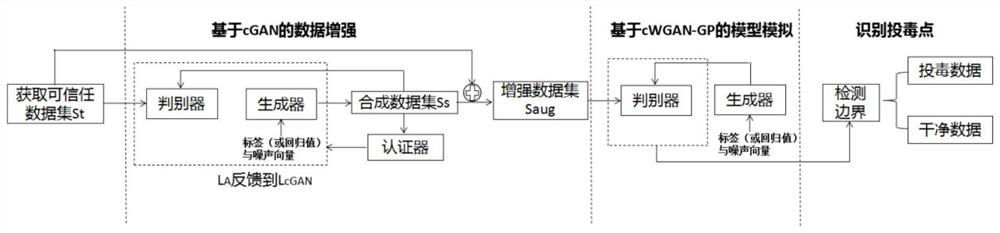
The invention belongs to the field of information security, and particularly relates to a machine learning training data poisoning attack defense method, which is used for intelligent security and protection, training data are collected in security and protection video data, and the method comprises the following steps: obtaining prediction value distribution of a clean training data set corresponding to a training data set to be identified; inputting each piece of to-be-identified training data into the trained prediction model to obtain a prediction value; determining and identifying poisoning data based on the predicted value and the predicted value distribution so as to realize defense; generating synthetic data based on the trusted training data of the same type as the training data to be identified; training by adopting an enhanced data set consisting of the synthetic data and the trustworthy training data to obtain a prediction model; wherein the distribution of the enhanced data set is the same as that of the clean training data set, and the prediction model takes the distribution of prediction values output by the enhanced data set as the prediction value distribution. Effective protection can be provided without defining a machine learning algorithm or an attack type, and the problem of limitation on specific attacks in an existing defense method is solved.
Owner:HUAZHONG UNIV OF SCI & TECH
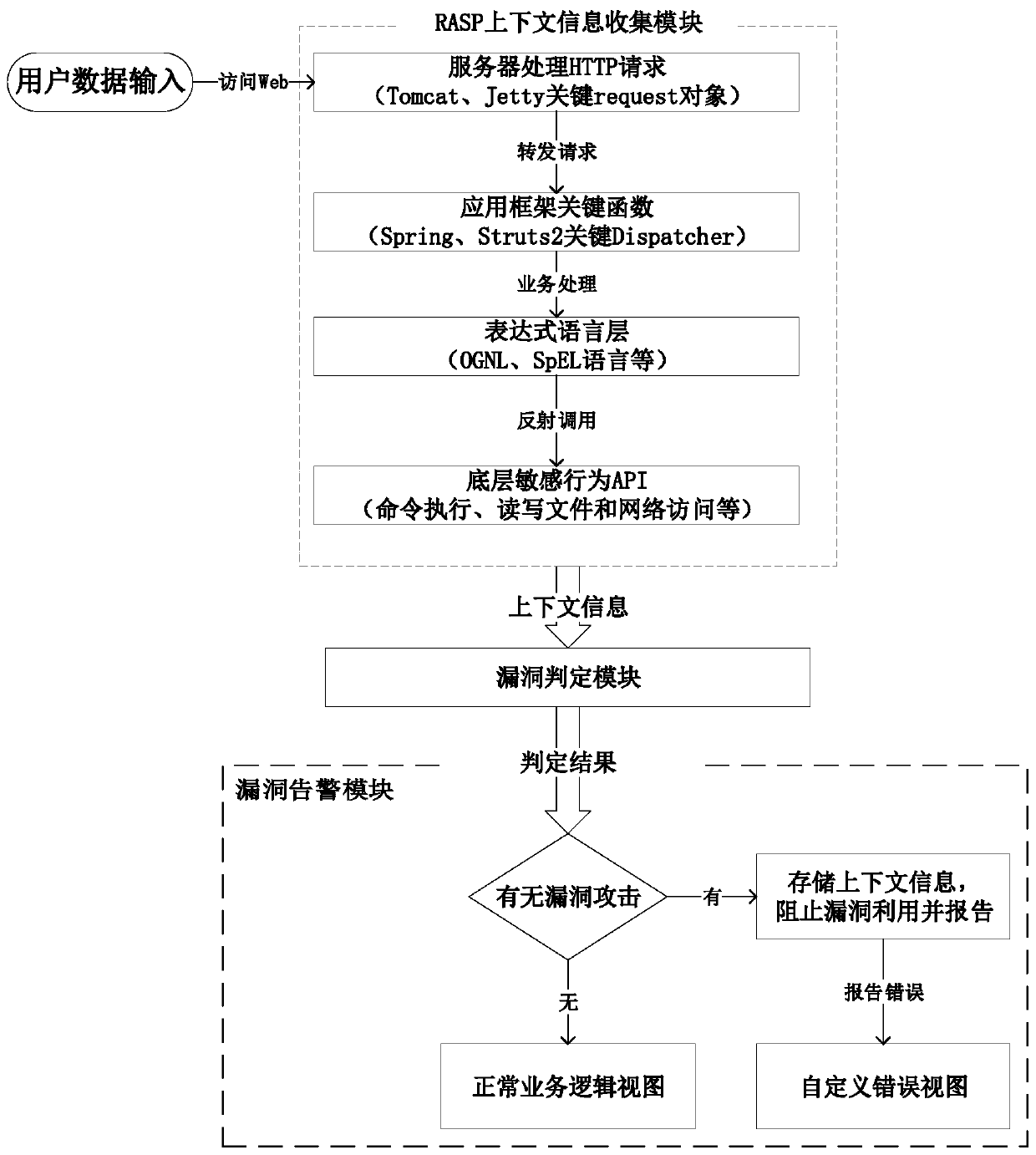
Java Web framework vulnerability attack general detection and positioning method and system
The invention discloses a Java Web framework vulnerability attack general detection and positioning method and system, and the system comprises: a context information collection module which is used for deploying a probe code of an RASP at each key level of an application program, and obtaining key context data such as parameter information of a related sensitive function; a vulnerability judgment module which is used for constructing an attack detection rule matching algorithm according to the established vulnerability utilization rule set, namely the representation characteristics of different vulnerability attack types in each level of the Web program; and a vulnerability alarm module which is used for receiving a judgment result of the vulnerability judgment module and outputting feedback information which comprises a judgment result of vulnerability attacks suffered by the program. The collected context information application rules in the program can be directly matched, meanwhile, the detection rule set can be expanded along with expansion of vulnerability attack types analyzed in the early stage, the operation state in the program can be monitored in real time, unknown vulnerability defense is achieved, and effectiveness and practicability are achieved.
Owner:WUHAN UNIV
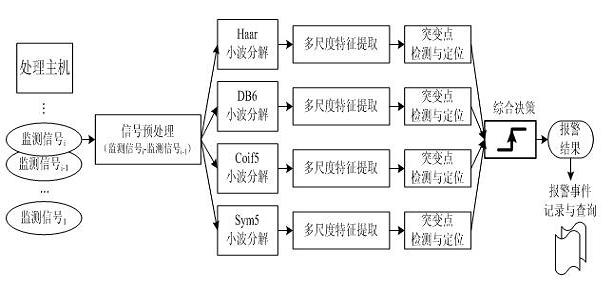
Intrusion detection and location method of distributed fiber optic fence based on φ-otdr
The invention discloses a distributed optical fiber fence intrusion detection and location method based on a phi-OTDR (Optical Time Domain Reflectometer), and the method comprises the following steps of: firstly, subtracting an acquired ith signal by an acquired (i-1)th signal to obtain a preprocessing monitoring signal; secondly, carrying out at least four-layer wavelet decomposition on the preprocessing monitoring signal by adopting a plurality of wavelet functions; thirdly, judging whether actual intrusion exists according to the consistency of distribution positions of maximum-wavelet mode maximums in all scale signals; fourthly, judging that the actual intrusion exists if the distribution positions of the maximum-wavelet mode maximums in at least three scale signals are consistent; fifthly, corresponding multiplying the scale signals in which the intrusion exists and the distribution positions of the maximum-wavelet mode maximums are consistent to obtain a composite signal of which pseudo maximums are inhibited and mode maximums at a catastrophe point are enhanced, using a position corresponding to the maximum-mode maximum in the composite signal as a position of the determined intrusion point, determining the intrusion generation and the intrusion position by combining various composite signal judgment results of wavelet multi-scale analysis according to the majority voting criterion.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
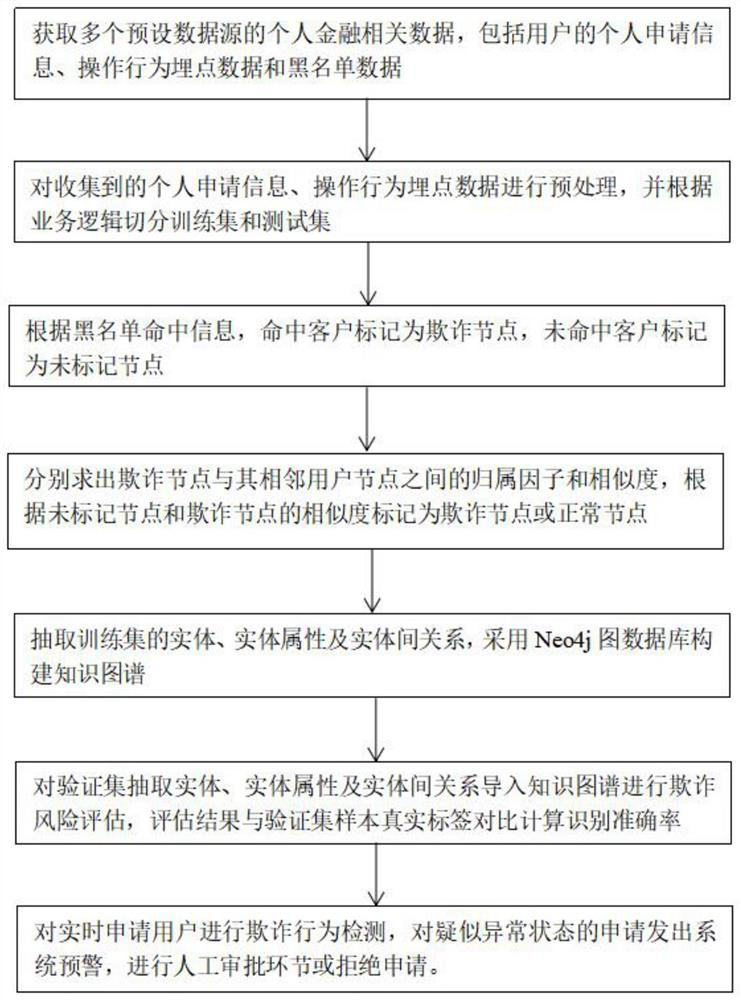
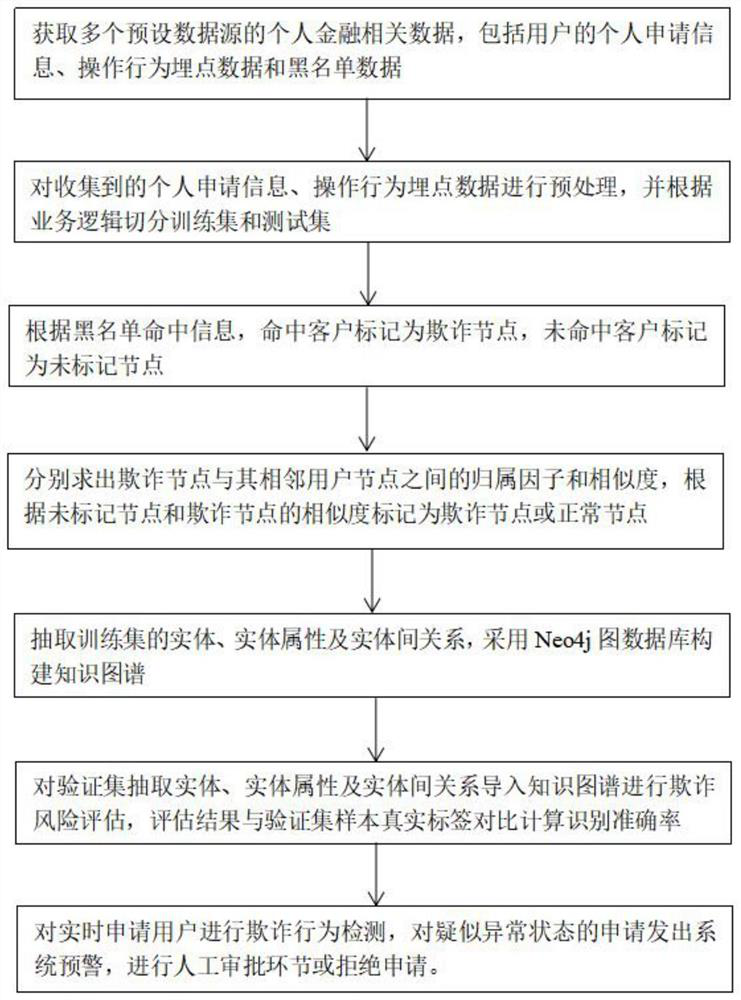
Internet financial gang fraud behavior detection method based on knowledge graph
InactiveCN112053221AAchieve defenseIdentifying gang fraudFinanceNatural language data processingTheoretical computer scienceThe Internet
The invention discloses an Internet financial gang fraud behavior detection method based on a knowledge graph. The method comprises the following steps: obtaining personal application information, operation behavior burying point data and blacklist data of users of a plurality of preset data sources; preprocessing application information and operation behavior buried point data, segmenting a training set and a test set, marking clients as fraudulent nodes and unmarked nodes according to blacklist hit conditions, solving similarity and affiliation factors between the fraudulent nodes and adjacent user nodes, and performing fraudulent risk assessment on the unmarked nodes to obtain a fraudulent risk assessment result; adopting a Neo4j graph database to construct a knowledge graph, testing averification set fraud risk assessment result, and detecting and processing real-time application user fraud behaviors. According to gang fraud behavior detection of the knowledge graph, an anti-fraudengine is constructed, suspicious group fraud risks are rapidly and efficiently recognized, financial risk control capacity is improved, and credit risks are reduced.
Owner:百维金科(上海)信息科技有限公司
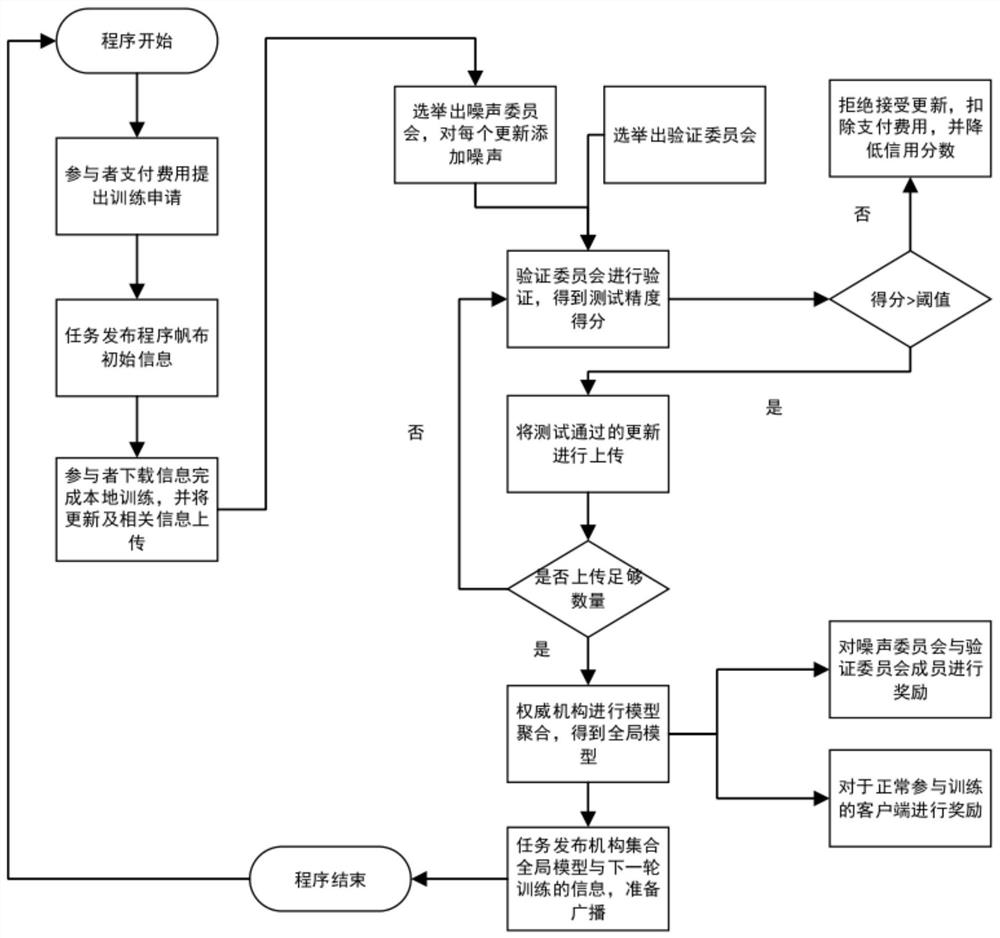
Federated learning defense method based on block chain
PendingCN112434280AProtect privacy and securityAchieve defenseFinanceDigital data protectionData setEngineering
The invention discloses a federated learning defense method based on a block chain. The method comprises the following steps: a participant establishing an intelligent contract with an authority; obtaining the model from the block chain by the participant in the book, carrying out local training, uploading the trained local model and the corresponding training time to the corresponding block node,and broadcasting the local model and the corresponding training time to the block chain; constructing a noise committee of a noise committee for each on-book participant, and adding noise to the local model of the corresponding on-book participant by using the noise committee to update the local model to obtain an updated model; constructing a verification committee for all in-book participants,verifying the prediction reliability and authenticity of each update model by using the verification committee according to the data set and the training time, and recording the update model passing the verification in a new block node; and the authority obtaining all the updated models passing the verification from the block nodes and aggregating the updated models to obtain an aggregated model,and broadcasting the aggregated model to the block chain for the next round of in-book participants to download local training.
Owner:ZHEJIANG UNIV OF TECH
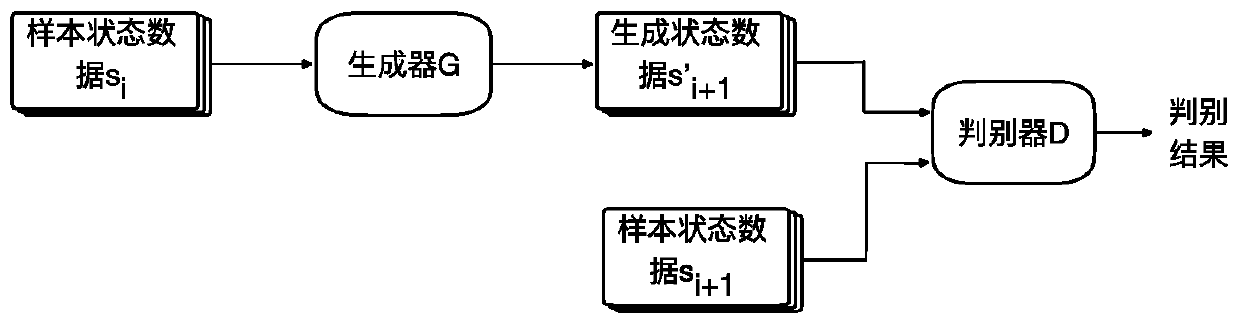
Reinforcement learning-oriented data exception detection defense method
PendingCN111310915ATimely replacementAchieve defenseCharacter and pattern recognitionNeural architecturesGenerative adversarial networkEngineering
The invention discloses an abnormal data detection defense method for reinforcement learning, and the method comprises the steps: (1) building a car automatic driving environment, carrying out the reinforcement learning through employing a deep deterministic strategy gradient algorithm based on the state data provided according to the car automatic driving environment, and generating driving statedata as a training sample; (2) training a generative adversarial network composed of a generator and a discriminator by using the training sample; (3) according to the collected driving state data, generating predicted driving state data at the next moment according to the driving state data at the current moment by utilizing a trained generator; and (4) judging whether the real driving state data and the predicted driving state data at the next moment are normal or not by utilizing the trained discriminator, and when the real driving state data at the next moment are abnormal, judging that the predicted driving state data are normal, and replacing the real driving state data by utilizing the predicted driving state data.
Owner:ZHEJIANG UNIV OF TECH
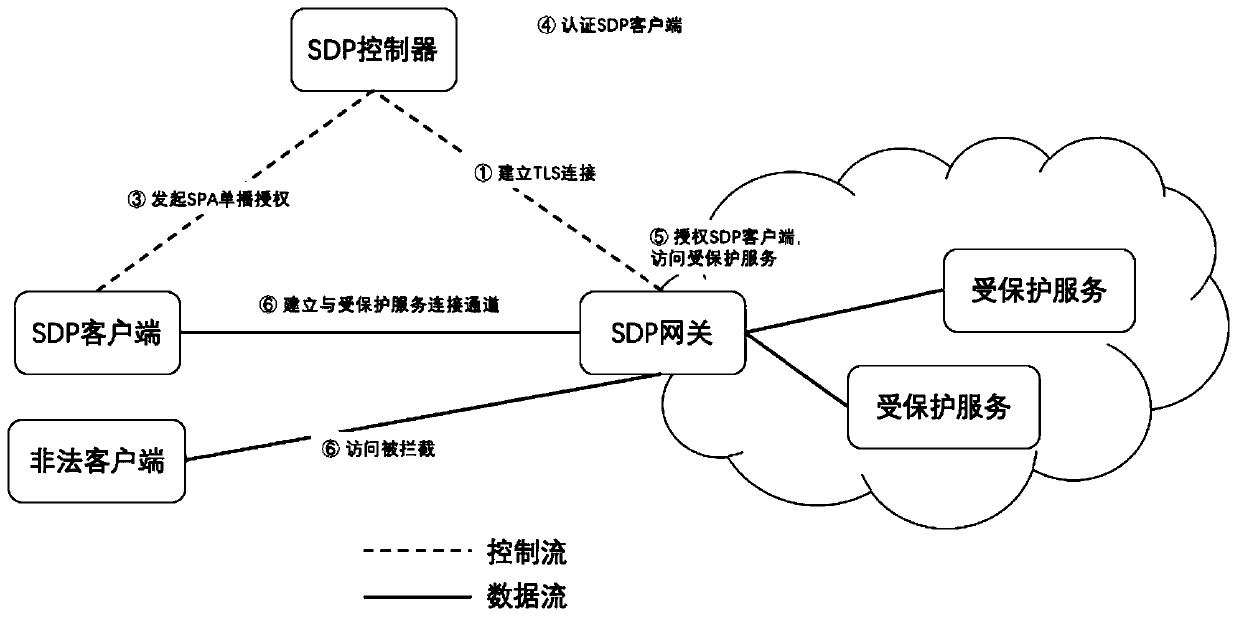
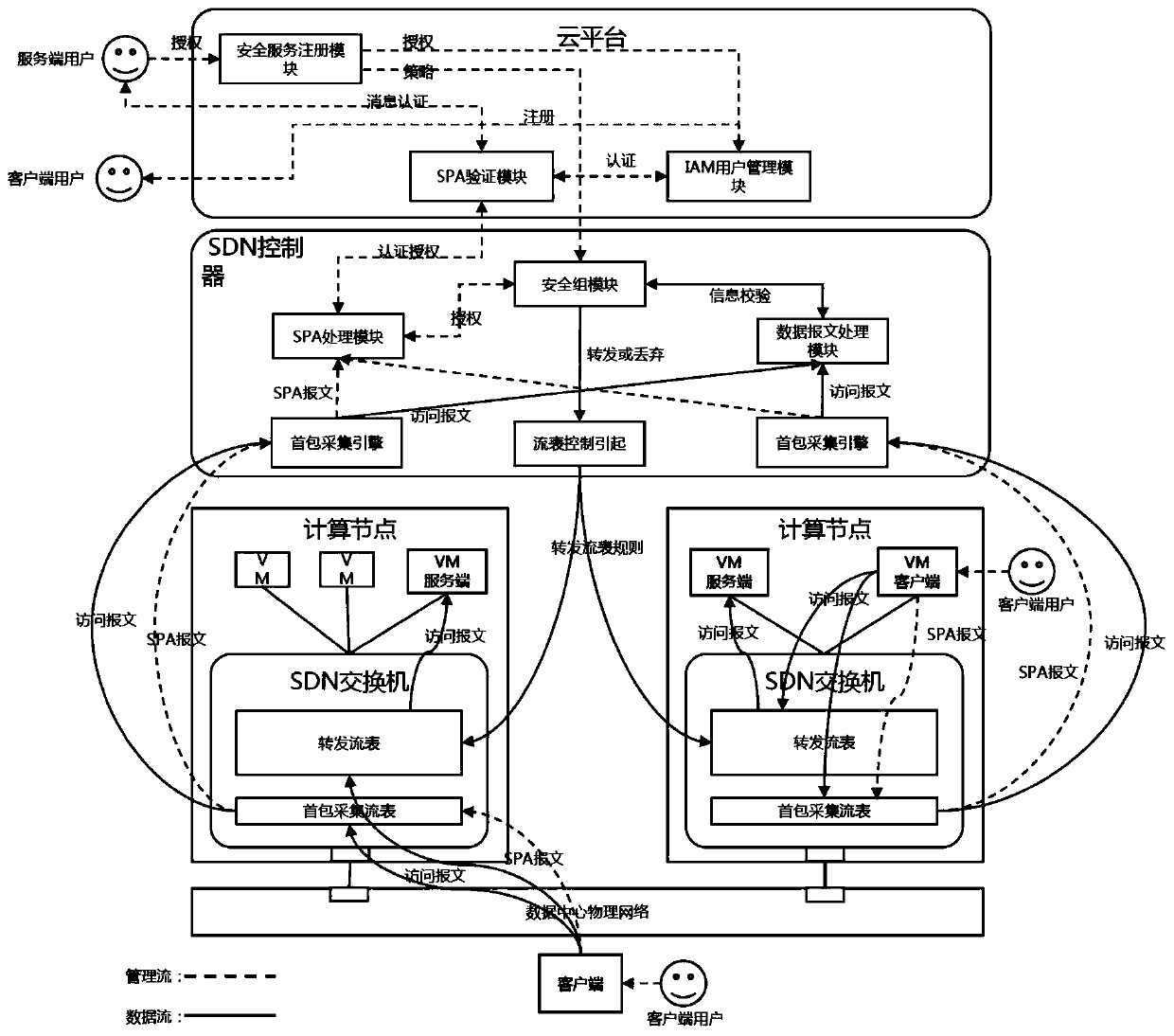
SDN-based SDP security group implementation method and security system
The invention discloses an SDN-based SDP security group implementation method and a security system, and the method achieves SPA single-packet authorization service logic through adoption of a flow table method of an SDN network, and carries out the planning and identity authentication of access authorities of different users through combining with the IAM user management of a cloud platform. According to the invention, the security of the cloud platform security group function is enhanced; accurate control of the security group on external authorization is realized; in combination with the identity authentication technology of the cloud platform and the SDN cloud network, the additional cost of the SDP gateway and the SDP controller is reduced, the SDP technology and the cloud computing security technology are fused, meanwhile, attacks from an internal network can be effectively defended, and comprehensive defense of flow in all directions of the cloud platform can be achieved.
Owner:GUANGZHOU BINGO SOFTWARE
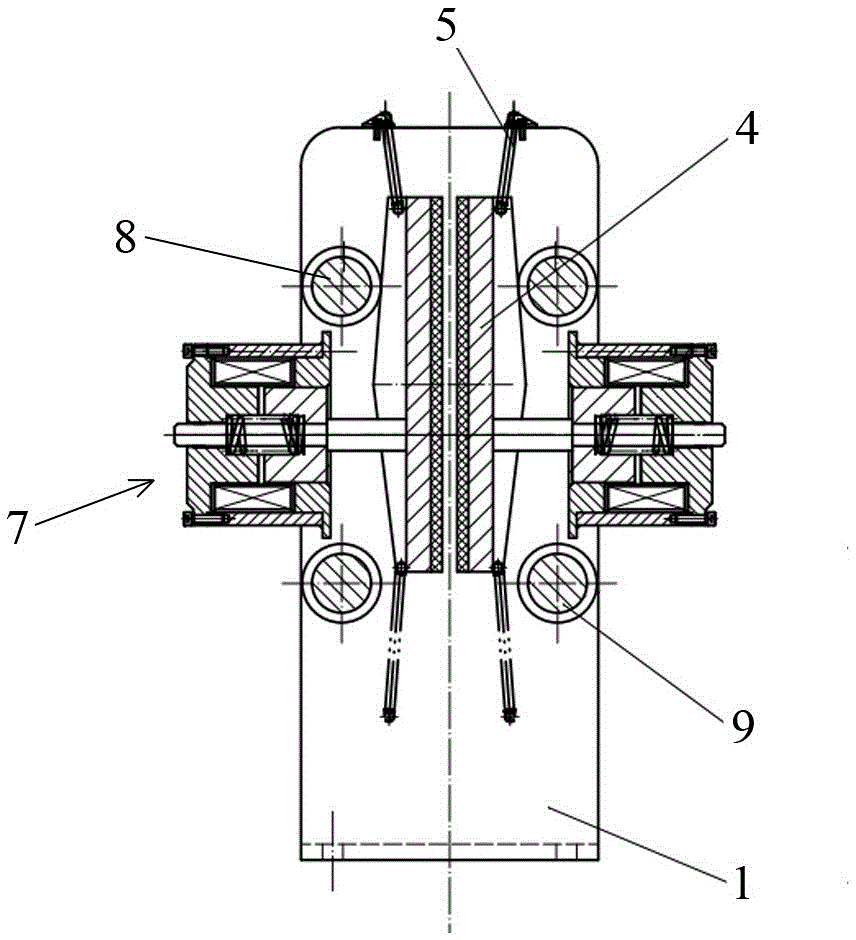
Rope gripper
The invention relates to a rope gripper. The rope gripper is structurally characterized in that two brake clamping blocks of which clamping surfaces are opposite to each other are arranged in a rack; at least one of the two brake clamping blocks is a movable clamping block; the back of each movable clamping block comprises an upper inclined plane and a lower inclined plane, so that the movable clamping block forms a compound wedge-shaped block formed by connecting an upper wedge-shaped body and a lower edge-shaped body; an elastic draw-off mechanism for drawing off the movable clamping blocks is arranged on the rack; upper transverse shafts and lower transverse shafts are arranged on the rack; an axial plane of each upper transverse shaft is opposite to an upper inclined plane of the back of the corresponding movable clamping block; an axial plane of each lower transverse shaft is opposite to a lower inclined plane of the back of the corresponding movable clamping block; and according to the setting positions of the upper transverse shafts and the lower transverse shafts, the movable clamping blocks can generate translation towards the direction of the clamping surface in the upward or downward moving process, so that a rope passing through a rope channel is clamped and stopped. The rope gripper disclosed by the invention serves as a safety brake; and a car or a hoisted heavy object can be immediately gripped by the rope gripper no matter upward heading or downward rolling, thereby preventing malignant consequence caused by unforeseen circumstances.
Owner:SHIJIAZHUANG WULON BRAKE
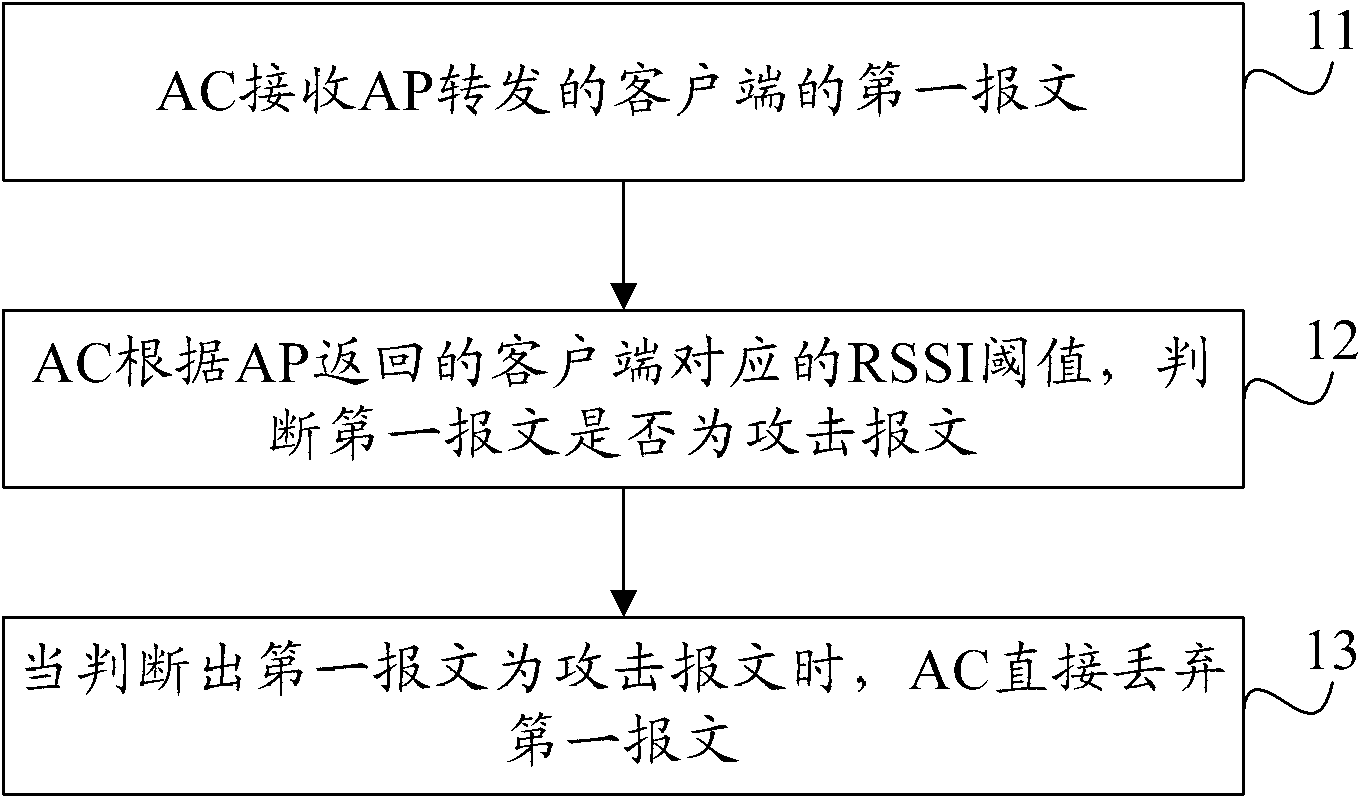
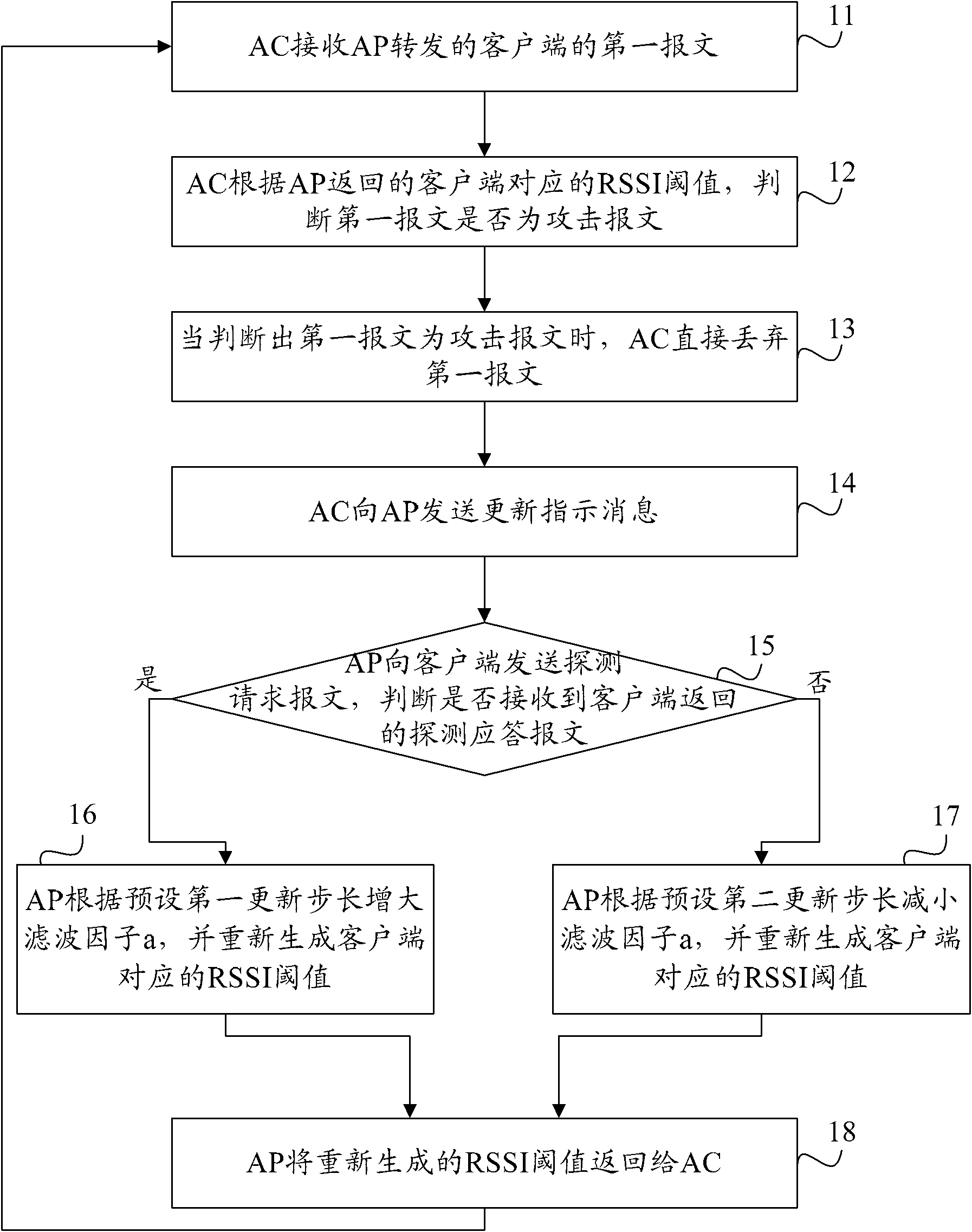
Method and system for defending denial of service attack, wireless access point and wireless controller
ActiveCN102036248AAchieve defenseImprove service qualitySecurity arrangementQuality of serviceReceived signal strength indication
The invention provides a method and a system for defending denial of service attack, a wireless access point and a wireless controller. The method comprises the following steps that: the wireless controller receives a first message of a client forwarded by the wireless access point; the wireless controller judges whether the first message is an attack message or not according to a receiving signal intensity indication threshold which corresponds to the client and is returned by the wireless access point; and the wireless controller directly discards the first message when determining that thefirst message is the attack message. By the method and the system for defending the denial of service attack, the wireless access point and the wireless controller which are provided by the invention, defense against a denial of service (DOS) attack can be realized, the client cannot be off-line or a wireless access service cannot be interrupted due to the DOS attack to the message, and the service quality of the wireless access of the client is improved.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
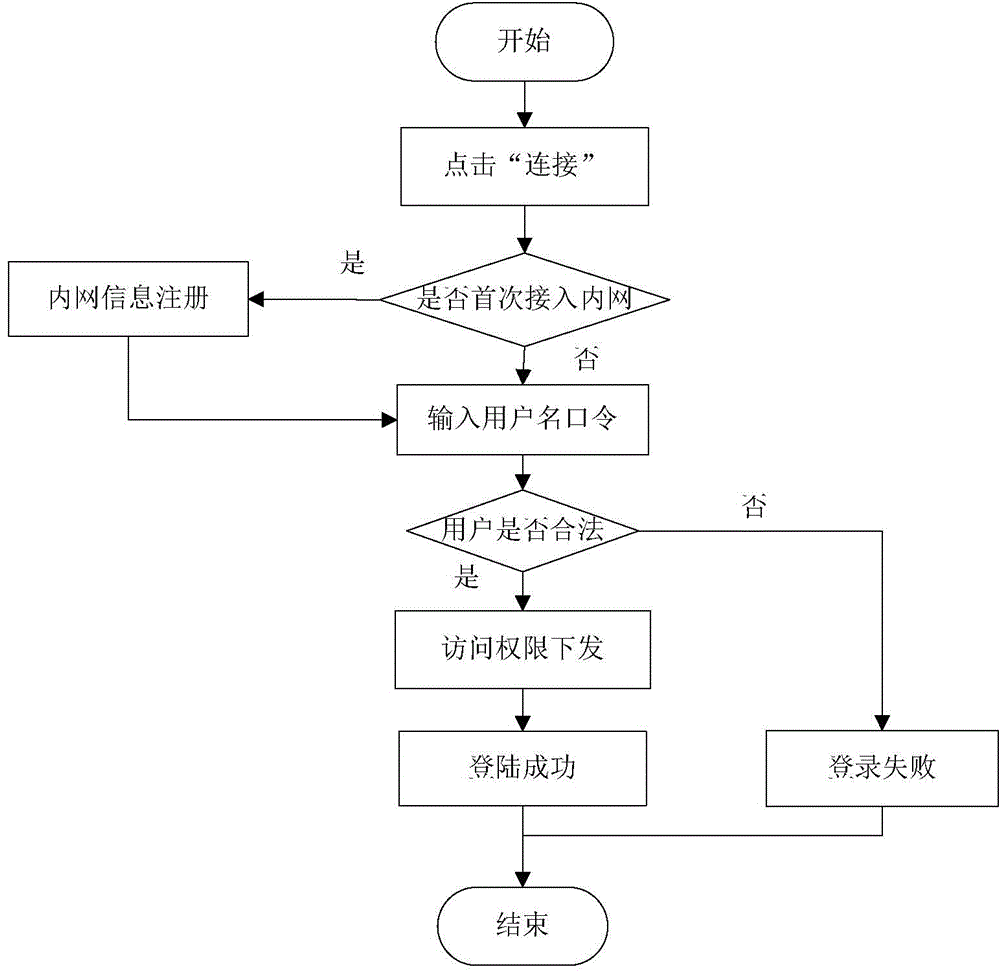
System and method for authenticating terminal trusted access
ActiveCN104869111ASolve the problem of uncertain identityAchieve defenseTransmissionPoint-to-Point ProtocolDigital signature
The invention discloses a system and a method for authenticating terminal trusted access. According to the invention, a public key and identification information of a user are bound and stored in an electronic certificate through a CA, and identity authentication of the user is realized; and the confidentiality, the integrity and the non-repudiation of user information are ensured by being combined with data encryption and digital signature technologies. The system disclosed by the invention is low in requirement for the overall performance of equipment, can effectively reduce the networking cost, supports multicast services, is compatible with a PPP (point-to-point protocol), good in expansibility and adaptability, designed with a controllable port and an uncontrollable port, and realizes separation of services and authentication. The system does not need to carry out packaging processing on a data packet after passing authentication, is high in efficiency, can map different user levels to different VLANs (virtual local area networks), realizes management for user domains with different authorities, and has the advantages of simple implementation mode, high authentication efficiency, safety, reliability and easy operation.
Owner:CHANGAN UNIV
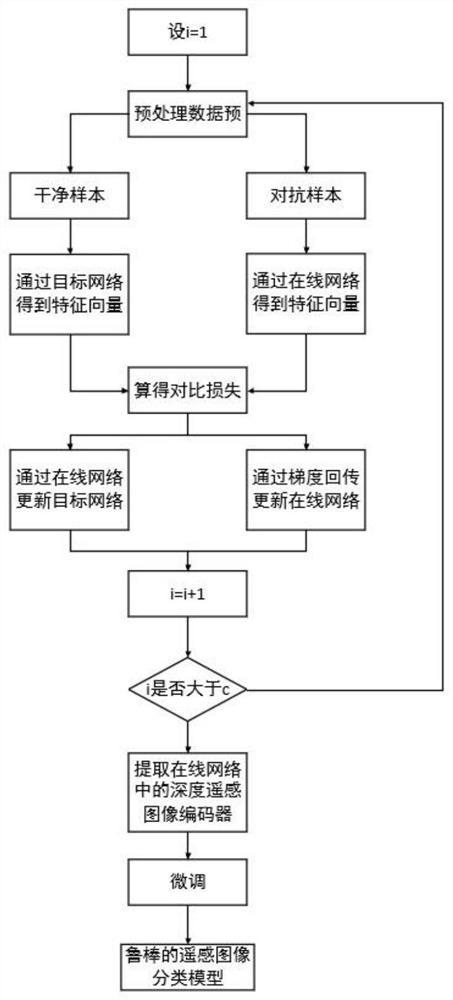
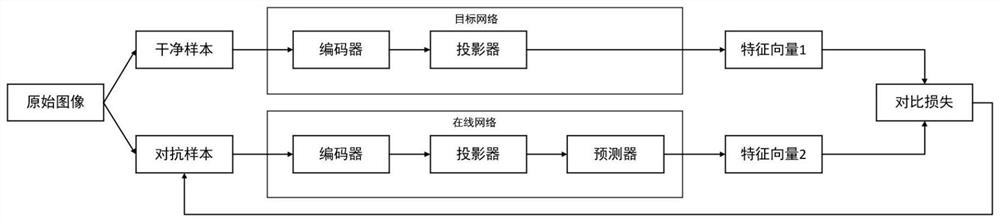
Remote sensing image classification network robustness improvement method based on self-supervised learning
ActiveCN114067177AImprove robustnessDoes not affect the classification effectCharacter and pattern recognitionFeature vectorFeature extraction
The invention provides a remote sensing image classification network robustness improvement method based on self-supervised learning, which not only utilizes labeled data, but also fully utilizes a large amount of non-labeled data existing in the remote sensing field, and effectively improves the robustness of a model by mining the information of images through a twin network. Feature extraction is conducted on the clean sample and the adversarial sample simultaneously by using a twin network to obtain feature vectors, and model training is completed by comparing and learning the feature vectors approaching the clean sample and the adversarial sample, so that the image has stable expression in a deep remote sensing image encoder network in an online network in the twin network, and therefore, the robustness is improved. According to the method, the robustness of the model to adversarial sample noise and natural noise is effectively enhanced, meanwhile, the classification effect of a clean data set is hardly influenced, and application is facilitated.
Owner:NAT UNIV OF DEFENSE TECH
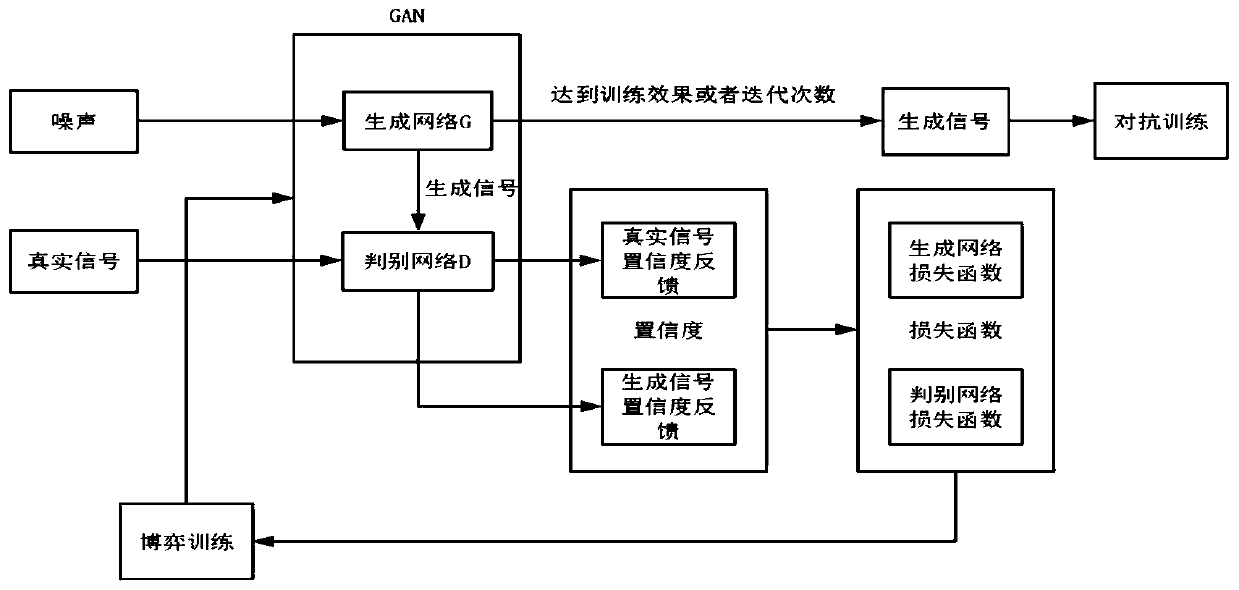
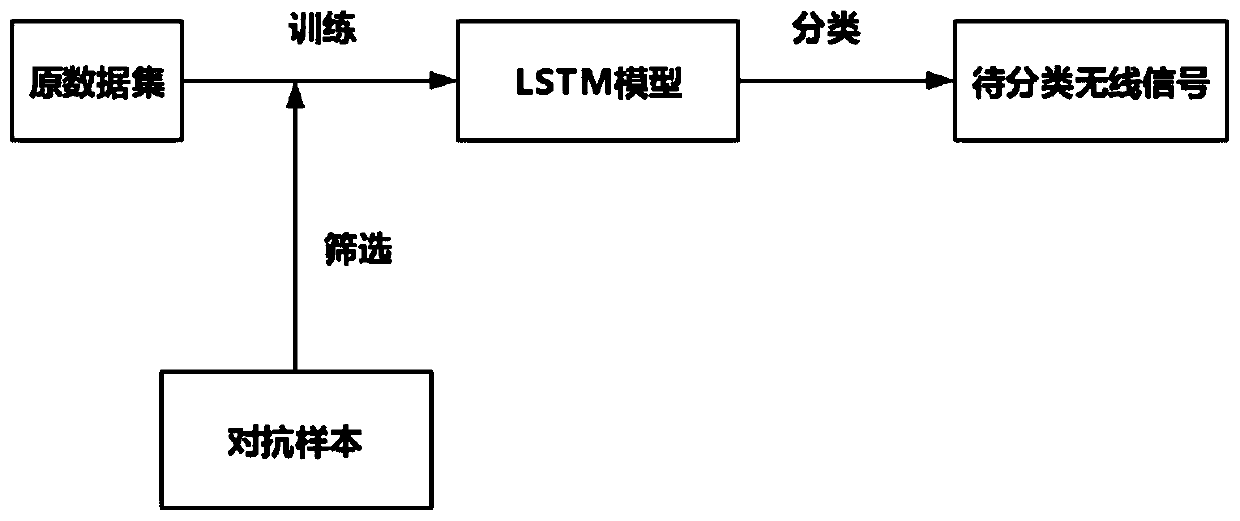
Signal identification attack defense method based on generative adversarial network
ActiveCN111163472AAchieve defenseComprehensive Adversarial ExamplesNeural architecturesSecurity arrangementGenerative adversarial networkAlgorithm
A defense method based on generative adversarial network attacks comprises the following steps: 1) establishing an appropriate generative adversarial network structure GAN by using a long short term memory (LSTM) network; 2) pre-training a discrimination model in the structure; 3) according to the loss function of the generator G, training the generator G by taking the number of iterations as a limit and the convergence loss function as a purpose; 4) according to the loss function of the generator D, training the generator D by taking the number of iterations as a limit and the convergence loss function as a purpose; (5) repeating the steps (3) to (4), optimizing a generator and a discriminator in the generative adversarial network in turn, obtaining a better network structure by taking the number of iterations as an upper limit, and completing the generation of an optimal adversarial sample; 6) observing indexes of the adversarial samples and generating a large number of adversarial samples of different types of signals, and 7) adding some screened adversarial samples into a model training stage to achieve a defense effect on signal boundary exploration attacks.
Owner:ZHEJIANG UNIV OF TECH
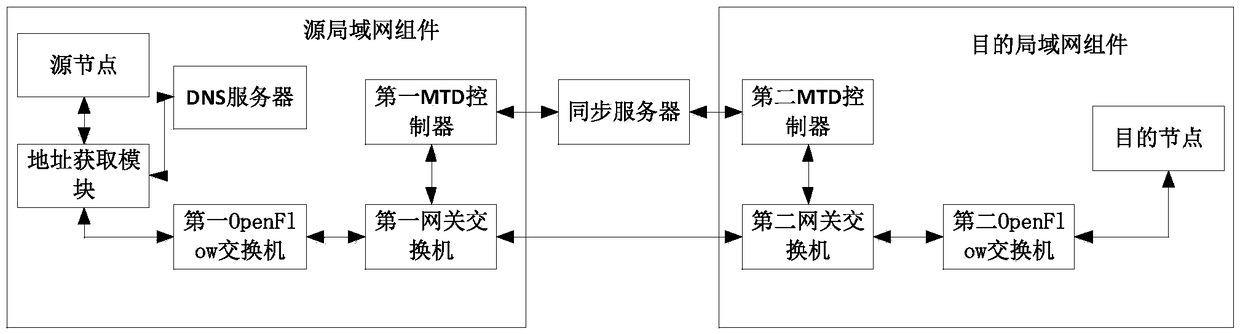
Network layer mobile target defense method and system based on OpenFlow
The invention provides a network layer mobile target defense method and system based on OpenFlow. The method comprises steps of address acquisition, construction of initial data packet header information, first IP jump, first port jump, second port jump, second IP jump and destination node communication. The method is advantaged in that upper-layer opacity protection can be achieved without third-party software, that is, modifying an upper-layer application is not needed, and the information sent from a node is always in the movement and change state, and thereby attack of an attacker is effectively avoided.
Owner:ZHEJIANG JIESHANG ARTIFICIAL INTELLIGENCE RES & DEV CO LTD
A LDoS attack detection method in SDN environment
The invention relates to an LDoS attack detection method under an SDN environment, comprising the following steps: positioning an exchange suspected to be attacked according to a difference Del between an incoming data packet and an outgoing data packet in a unit time of each exchange in an SDN network; Aiming at the switch suspected to be attacked, locating the incoming port of the attack trafficthrough the traffic statistics of each port, For each stream flowing into the port, counting the traffic information separately, and locating the source Mac and destination Mac information of the attack stream, so as to find the attack stream.
Owner:TIANJIN UNIV
Internet financial gang fraud behavior detection method based on knowledge graph
InactiveCN112053222ASolve data silosSolve data inequalitiesFinanceNatural language data processingTheoretical computer scienceThe Internet
The invention discloses an internet financial gang fraud behavior detection method based on a knowledge graph. The method comprises the following steps: obtaining personal application information, operation behavior burying point data and blacklist data of users of a plurality of preset data sources; preprocessing application information and operation behavior buried point data, segmenting a training set and a test set, marking clients as fraudulent nodes and unmarked nodes according to blacklist hit conditions, solving similarity and affiliation factors between the fraudulent nodes and adjacent user nodes, and performing fraudulent risk assessment on the unmarked nodes to obtain a fraudulent risk assessment result; adopting a Neo4j graph database to construct a knowledge graph, testing averification set fraud risk assessment result, and detecting and processing real-time application user fraud behaviors. According to gang fraud behavior detection of the knowledge graph, the anti-fraud engine is constructed, suspicious group fraud risks are rapidly and efficiently recognized, financial risk control capacity is improved, and credit risks are reduced.
Owner:百维金科(上海)信息科技有限公司
Defense method based on signal boundary exploration attack
ActiveCN110768959AAchieve defenseCharacter and pattern recognitionTransmissionDecision boundaryAlgorithm
The invention discloses a defense method based on signal boundary exploration attack, which comprises the following steps: S101, screening a to-be-attacked signal A, and carrying out initialization disturbance addition to obtain an adversarial signal A '; S102, according to confidence coefficient changes of the to-be-attacked signal A and the countermeasure signal A ', judging a decision boundarydistribution condition around the to-be-attacked signal A; S103, performing disturbance modification on the countermeasure signal A' according to the decision boundary distribution condition around the to-be-attacked signal A; S104, randomly generating deviation disturbance, so that the adversarial signal A' explores the boundary; S105, optimizing disturbance to enable the countermeasure signal A'not to deviate from an expected track; S106, realizing disturbance optimization until an iteration upper limit is reached or a good confrontation signal A' is obtained; S107, screening adversarial signals, adding the adversarial signals into the training set, and training the signal classification model; and S108, classifying the to-be-classified signals by utilizing the trained signal classification model so as to defend attacks.
Owner:ZHEJIANG UNIV OF TECH
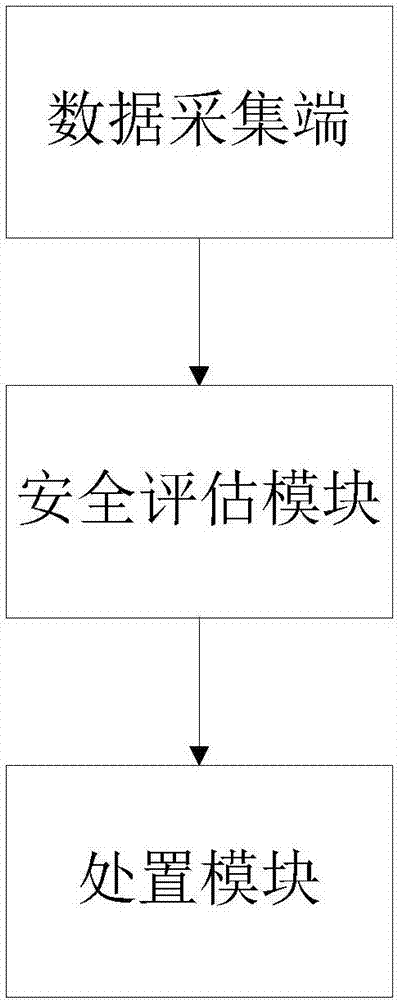
Network security defense disposing system
InactiveCN106973045AOvercoming the problems with major hidden dangers in safetyAchieve defenseTransmissionOriginal dataData acquisition
The invention discloses a network security defense disposing system. The system comprises a data acquisition end, a safety evaluation module and a disposing module, wherein the data acquisition end is used for acquiring a network event, system running data and equipment operation data so as to obtain original data; the security evaluation module is configured to connected with the data acquisition end so as to normalize multivariate data of the network event, the system running data and the equipment operation data, and performing security evaluation to obtain an evaluation weight and an evaluation level; the disposing module is configured to connect with the security evaluation module so as to perform the security disposing according to the evaluation level. The network security defense disposing system overcomes a problem that the network security has great hidden danger in the prior art, and the defense and the disposing of the network threat are realized.
Owner:北京金钻芯科技有限公司
Anti-chopping shield with W-shaped shield body
ActiveCN106895746AEffective interceptionEnsure safetyShieldsElectrical and Electronics engineeringElbow locking
The invention discloses an anti-chopping shield with a W-shaped shield body. The anti-chopping shield comprises the shield body, handheld handles, a protective pad, and elbow locking and fixing devices, wherein the shield body comprises a shield body front surface and a shield body back surface; the protective pad is connected with the shield body back surface; each handheld handle and the corresponding elbow locking and fixing device penetrate through the protective pad and are connected with the shield body; the shield body front surface comprises shield ridges, shield front surfaces, shield lateral surfaces and a shield bottom; the shield ridges transversely extend to the shield bottom to form the shield front surfaces, and height gradually decreases when the shield ridges transversely extend; the shield ridges extend along the direction of the shield body back surface to form the shield lateral surfaces; the shield ridges, the shield front surfaces and the shield lateral surfaces are in symmetrical arrangement along the axis of the shield bottom, and are integrated into the W-shaped shield body front surface; and an anti-chopping bar is arranged on the surface of each shield ridge. The shield can be used for defending against the attack of liquid, thrown objects, cutters and the like, and has offending and defending functions.
Owner:BENGBU ZHIDA TECH CONSULTING CO LTD
Data processing method and device, server and user terminal
InactiveCN108282452AAffect the sense of experienceAchieve defenseTransmissionClient-sideComputers technology
The invention provides a data processing method and device, a server and a user terminal, and belongs to the field of computer technology. The data processing method comprises the following steps that: a server generates response data according to a data request sent by a client; the server generates check information according to the data request, the response data and a key; and the server sendsthe response data and the check information to the client, so that the client judges whether the response data are hijacked or not according to the check information in order to prevent the hijackedresponse data from affecting the user experience.
Owner:ALIBABA (CHINA) CO LTD
Federal learning data poisoning attack-oriented defense method and device
ActiveCN113965359AAchieve defenseEliminate hazardsMachine learningSecuring communicationAttackLearning data
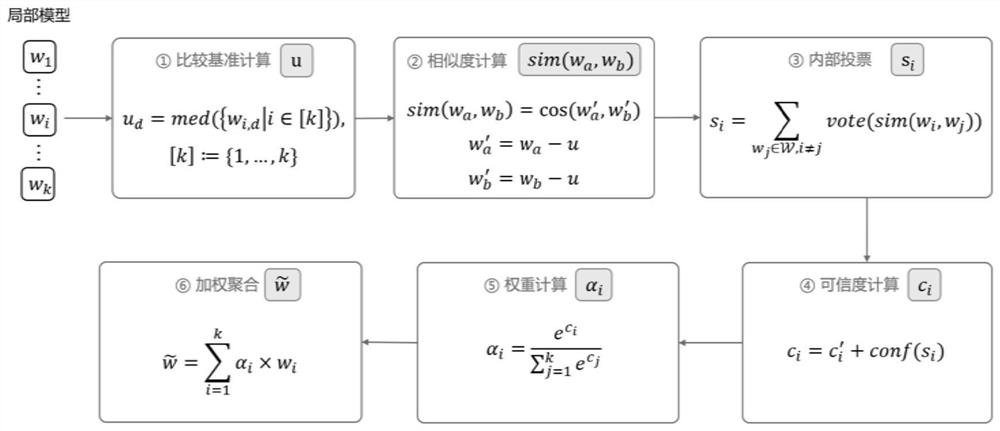
The invention discloses a federal learning data poisoning attack-oriented defense method and device. The method comprises the steps that each client uses local data to train model parameters; each client uploads local model parameters to the server, and the server receives all the model parameters; the server calculates a reference basis u for comparison, and for any two local models wa and wb, the similarity of the two local models wa and wb relative to the reference basis u is calculated; whether a local model is malicious or not is judged by adopting an internal voting method; the credibility of each local model is calculated according to the votes obtained by each local model; and model weighted aggregation is carried out based on credibility to obtain a final global model, and defense of data poisoning attack is achieved based on the final global model. According to the method, the model of the malicious client can be endowed with a lower weight, and the influence of the malicious client on the global model is weakened during weighted aggregation, so that defense against data poisoning attacks is realized.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
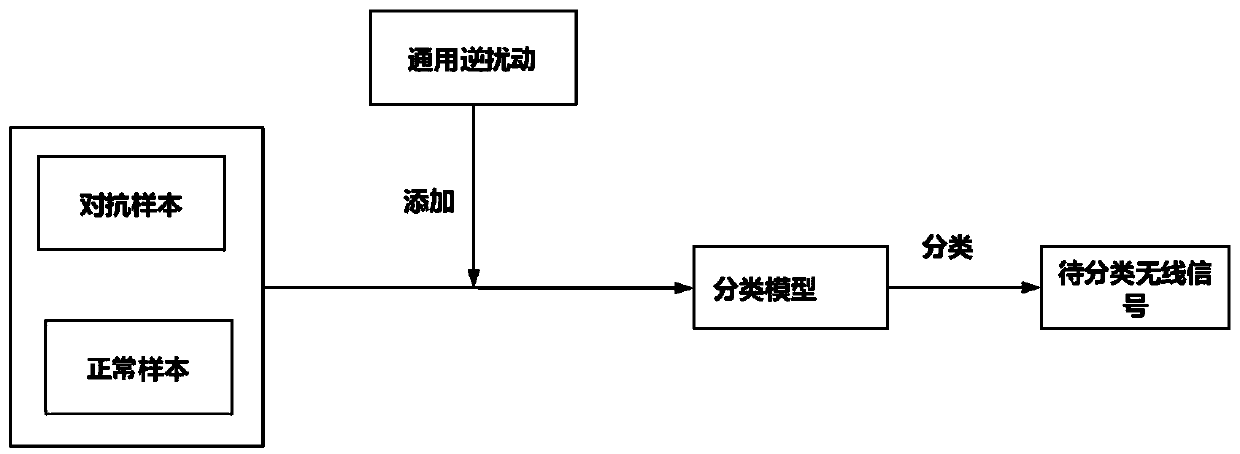
Defense method for generating general inverse disturbance based on generative adversarial
InactiveCN110969242AAchieve defenseDefense of defenseNeural architecturesNeural learning methodsFeature extractionAlgorithm
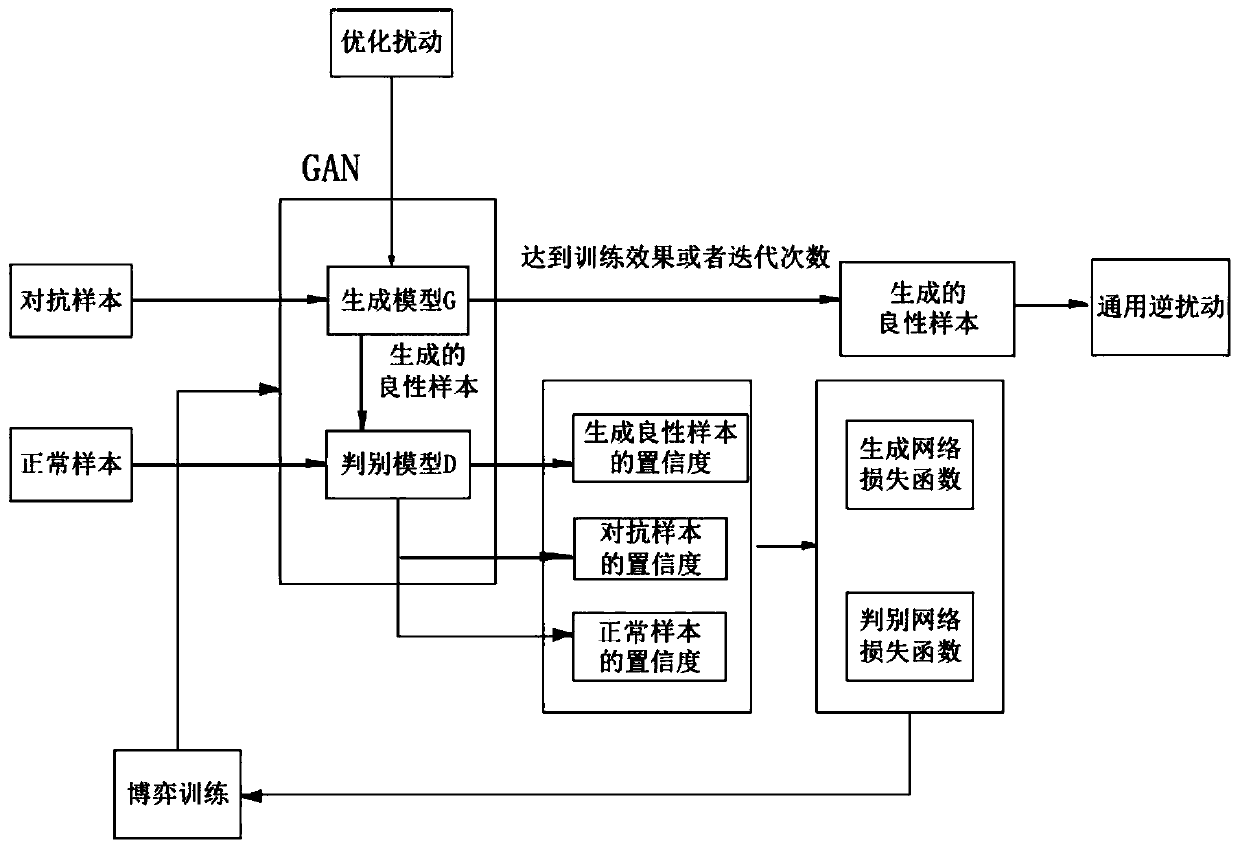
The invention discloses a defense method for generating general inverse disturbance based on generative adversarial, and the method comprises the steps: (1) building a generative adversarial network which comprises a generation model and a discrimination model; (2) obtaining a relatively comprehensive adversarial sample by utilizing various attack methods; (3) pre-training the generation model andthe discrimination model in the generative adversarial network by adopting normal samples; (4) establishing a loss function of the generation model, and training the generation model; (5) establishing a loss function of the discrimination model, and training the discrimination model; (6) repeating the steps (4) and (5) until the number of iterations reaches a preset upper limit value or the lossfunctions of the two models reach a preset threshold value; and (7) performing performance index detection and application on the trained generation model. According to the method, a proper generativeadversarial network is built, feature extraction of general disturbance distribution is completed, and proper general inverse disturbance is generated, so that the robustness of the model is improved.
Owner:ZHEJIANG UNIV OF TECH
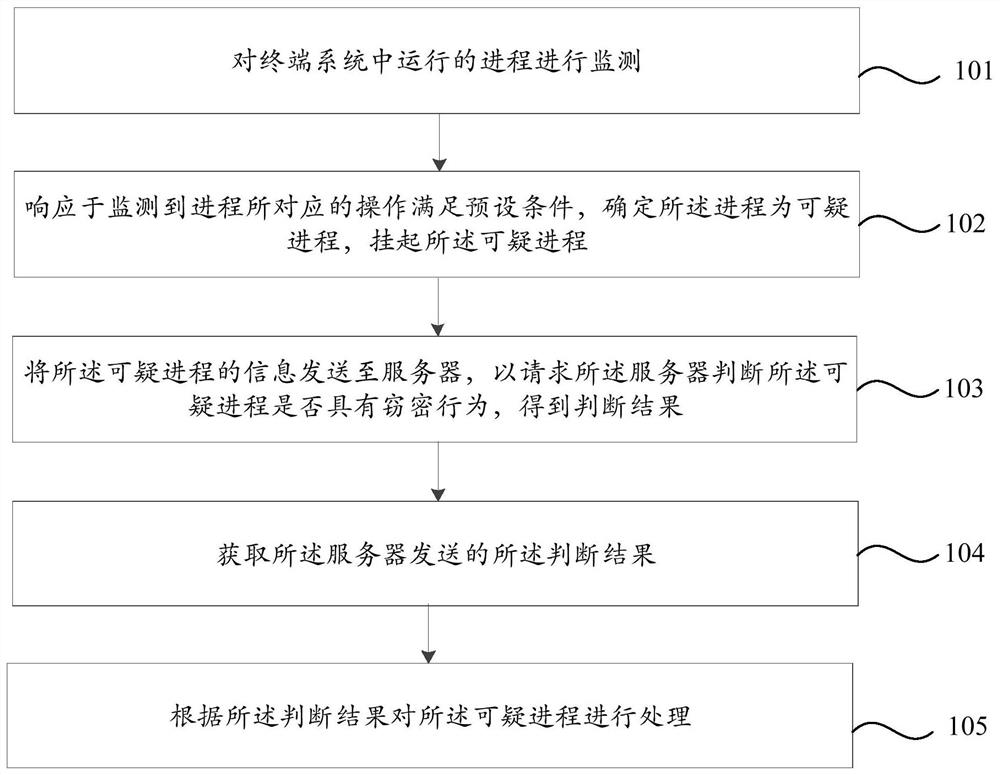
Suspicious process processing method and device, storage medium and electronic equipment
PendingCN113961920AEasy to detectAchieve defensePlatform integrity maintainanceRansomwareData security
The invention provides a suspicious process processing method and device, a storage medium and electronic equipment, relates to the technical field of data security, and aims to effectively detect attack behaviors of ransomware. The suspicious process processing method comprises the following steps: monitoring processes running in a terminal system; in response to monitoring that the operation corresponding to the process meets the preset condition, determining that the process is a suspicious process, and suspending the suspicious process; sending the information of the suspicious process to a server to request the server to judge whether the suspicious process has a secret stealing behavior or not, and obtaining a judgment result; obtaining the judgment result sent by the server; and processing the suspicious process according to the judgment result. The method provided by the embodiment of the invention are suitable for detecting the attack behavior of the ransomware.
Owner:HARBIN ANTIY TECH
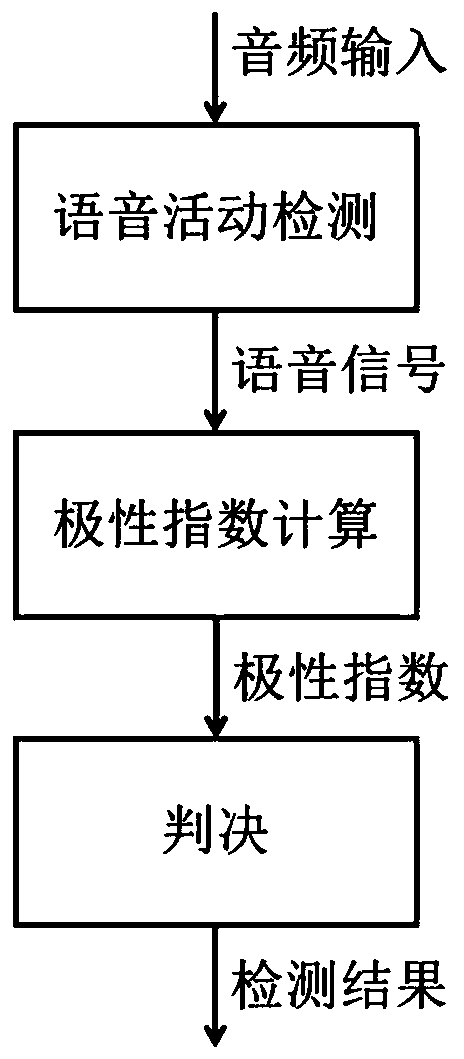
Replay attack detection method of voice certification system
The invention discloses a replay attack detection method of a voice certification system based on time domain polarity of a voice signal. The voice signal is collected and recorded through the voice certification system; a positive polarity signal and a negative polarity signal of the voice signal are extracted; and the proportional relationship of the positive polarity signal and the negative polarity signal is compared to judge that the voice signal belongs to replay attack or live voice, specifically, if the positive and negative polarity part proportion difference is large and the positivepolarity signal proportion is higher than the negative polarity signal proportion, the replay attack is considered, and if the positive and negative polarity part proportion difference is large and the positive polarity signal proportion is not higher than the negative polarity signal proportion, the live voice is considered. The replay attack in the voice certification system can be accurately and effectively detected.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com