Java Web framework vulnerability attack general detection and positioning method and system
A general-purpose detection and vulnerability detection technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems of difficulty in vulnerability attack detection and detailed positioning, inability to identify unknown vulnerabilities, and high detection false positive rate, achieving high efficiency and accuracy. Vulnerability detection and detail localization, good practicability and scalability, and the effect of improving detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
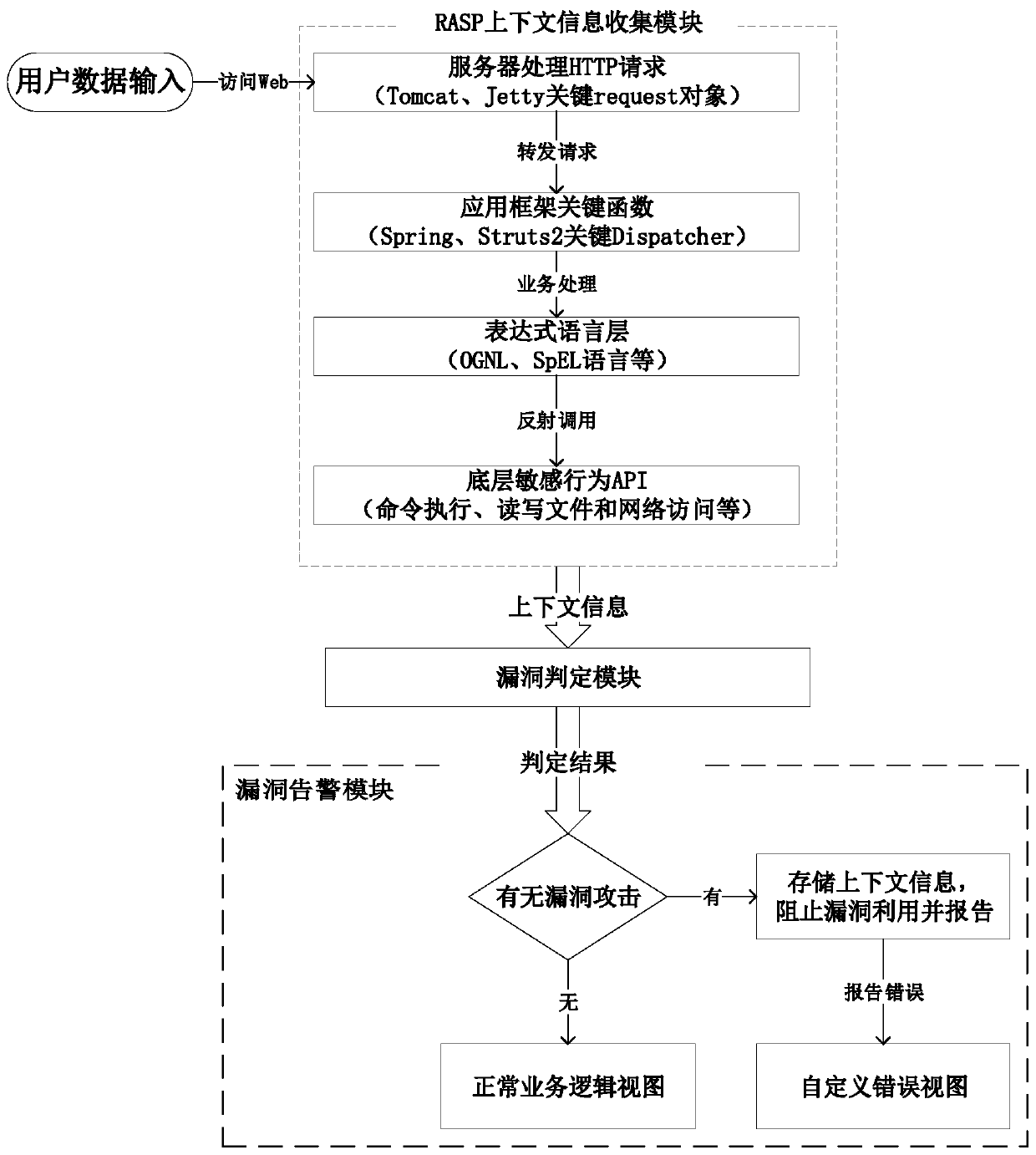
[0051] figure 1 Shown is the system framework diagram of the method provided by the present invention. The specific implementation of the present invention is as follows:
[0052] 1. According to the typical vulnerabilities of the Java Web framework, analyze the key steps and principles in the vulnerability attack, summarize the common points in the attack process, and establish a set of general vulnerability exploitation rules.
[0053] 2. According to the set of vulnerability exploitation rules established in step 1, the "context information collection module" deploys RASP probe codes at each key level of the application to obtain key context data such as parameter information of related sensitive functions. The specific operations are as follows:
[0054] 21) Extract the key function points from the set of exploit rules. Along the path between the entry point that the vulnerability attack must pass through to the sink point where the attack effect is finally realized, the "context...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com