Defense method, device and system for DNS (Domain Name System) services
A technology of DNS service and recursive server, which is applied in the field of DNS service, can solve problems such as crashes, consume large resources, and cannot be effectively defended, and achieve the effect of reducing forwarding and realizing defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] In order to make the above objects, features and advantages of the present invention more comprehensible, specific implementations of the present invention will be described in detail below in conjunction with the accompanying drawings.
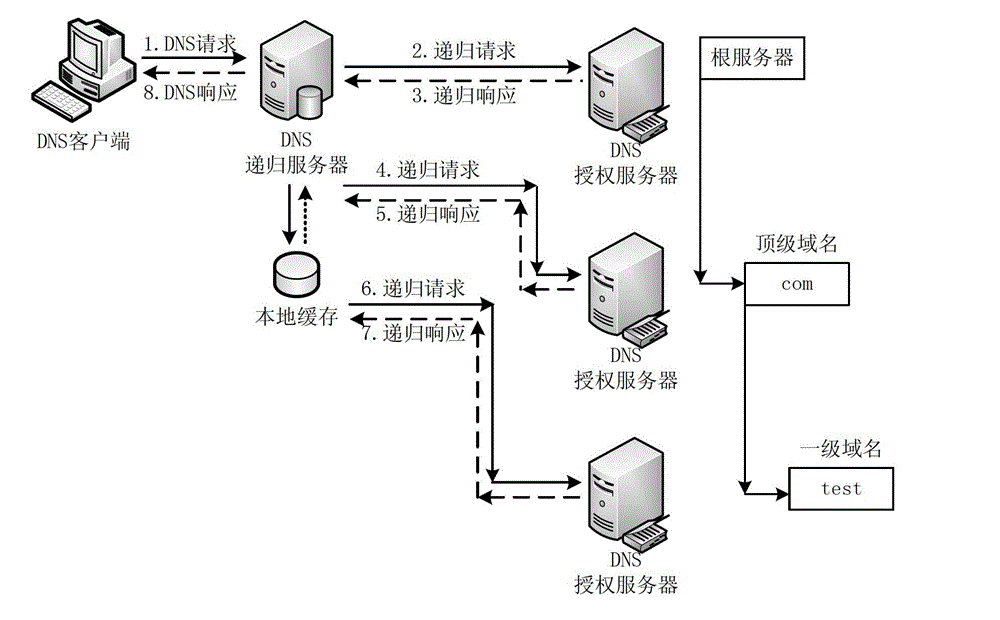
[0075] refer to image 3 , which is a flow chart of Embodiment 1 of a DNS service defense method provided by the present invention.
[0076] S301: Forward the DNS data query request message normally.
[0077] S302: Monitor the flow of DNS data query request packets at the egress of the DNS recursive server network per unit time.
[0078] For example, it is detected that there are 100 DNS data query request message flows at the network egress of the current DNS recursive server per unit time.
[0079] S303: Determine whether the traffic of the DNS data query request message exceeds a predetermined security access traffic threshold. If yes, execute S303; if no, execute S301 for all the monitored DNS data query request messages.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com