Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35results about How to "Achieve data isolation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
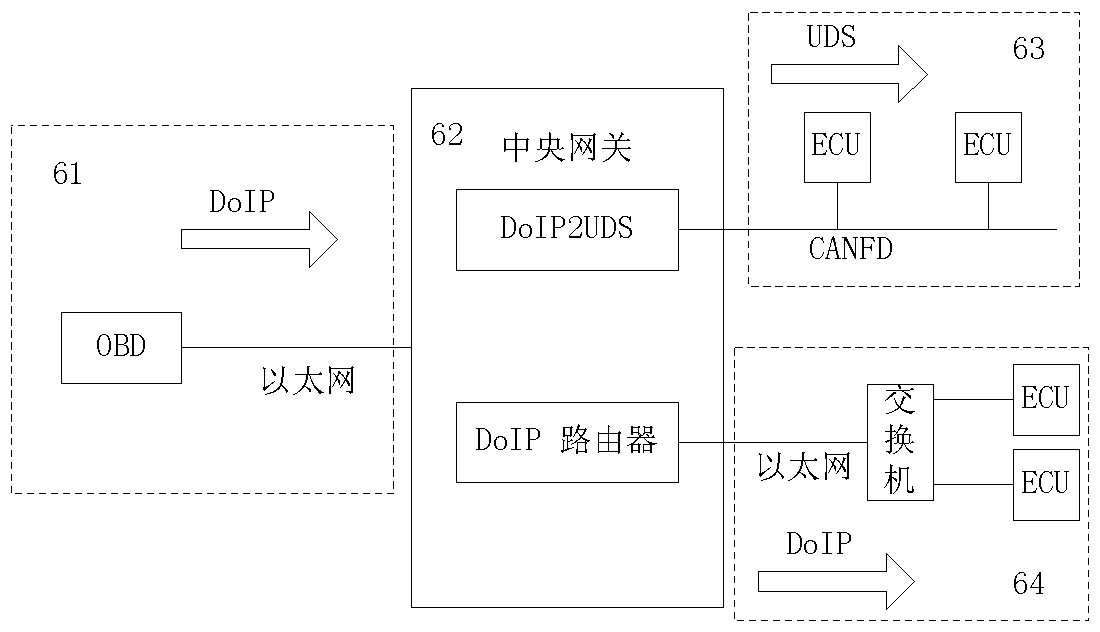
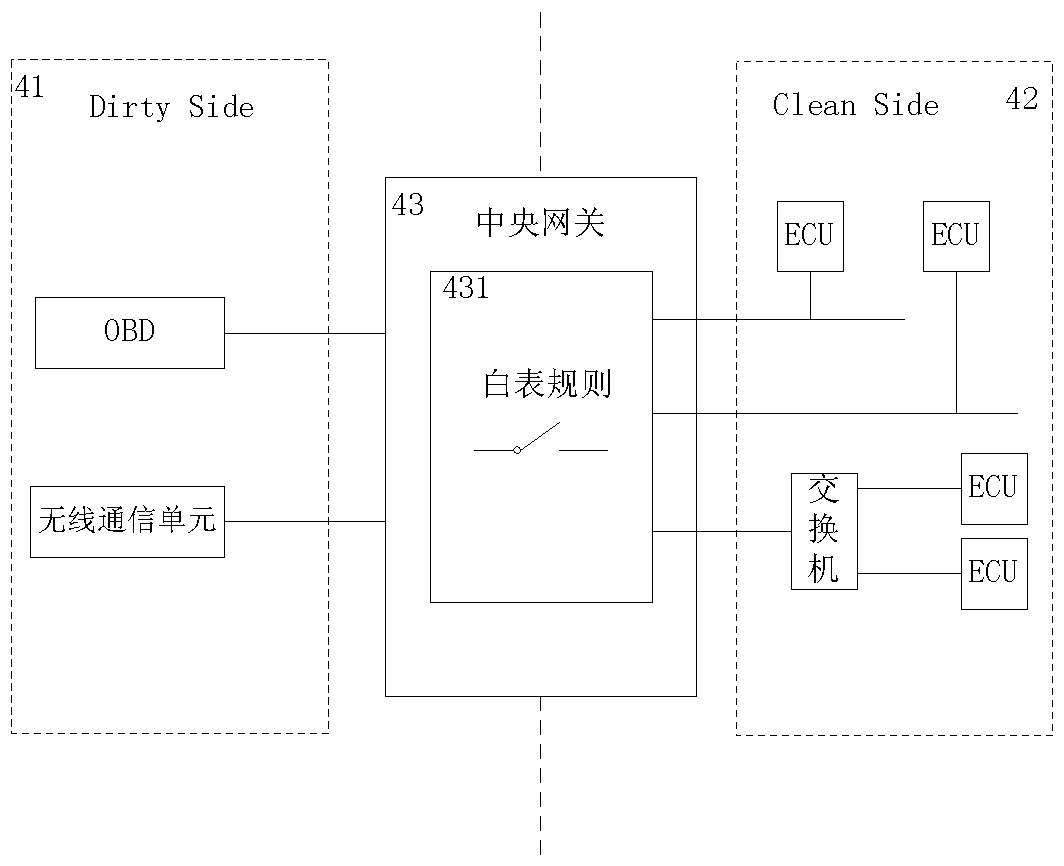
Vehicle communication system
InactiveCN108696424AImprove reliabilitySimple structureNetwork connectionsBus networksEmbedded systemElectronic control unit
The invention relates to a vehicle communication system comprising: a diagnosis port for providing diagnosis for functional units in a vehicle; at least one Ethernet node used for realizing Ethernetcommunication between the functional units in the vehicle; at least one electronic control unit usedfor controlling the functional units in the vehicle; a wireless communication unit used for realizing wireless communication between the vehicle communication system and an external system; a switch respectively connected with the Ethernet nodes and used for realizing information interaction among the Ethernet nodes; and a central gateway used for forming communication coupling with the diagnosis port, the at least one Ethernet node, at least one electronic control unit, the wireless communication unit and the switch for implementing the protocol conversion between the Ethernet communication and the CAN / CAN FD protocol communication in the vehicle. A vehicle-mounted gateway with a simple structure, a low implementation cost and a high integration level can be provided, and then the vehicle communication system with high reliability and a better application prospect can be provided.
Owner:SAIC GENERAL MOTORS +1
Alliance chain master-slave multi-chain consensus method based on tree structure
ActiveCN110245951AImplement classificationAchieve data isolationDigital data protectionPayment protocolsByzantine fault toleranceConsistency problem
The invention discloses an alliance chain master-slave multi-chain consensus method based on a tree structure. An alliance chain consensus group is divided; an upper-layer channel and a lower-layer channel are obtained; channels are mutually isolated, classification and data isolation of different digital assets are realized; privacy requirements of data isolation are met; concurrent processing ofmultiple channels is carried out, the transaction performance is improved, the problems that an existing block chain is low in throughput and too high in transaction delay are solved. The invention provides a master-slave multi-chain architecture of a tree structure and the occupancy fault-tolerant consensus algorithm based on the threshold signature under the master-slave multi-chain architecture to solve the problem of consistency caused by diversified digital asset classification concurrent processing; the method has the advantages of low communication complexity and signature verification complexity, the master-slave multi-chain structure breaks through the function and performance constraint of a single chain and has good high-concurrency transaction performance, meanwhile, isolation protection of privacy data is considered, and diversified business requirements of enterprises are met.
Owner:芽米科技(广州)有限公司
Multi-tenant data query method and system, and sharing platform server
ActiveCN106202309AAchieve data isolationWeb data indexingSpecial data processing applicationsComputer terminalData query
Owner:上海火炬电子科技集团有限公司 +1
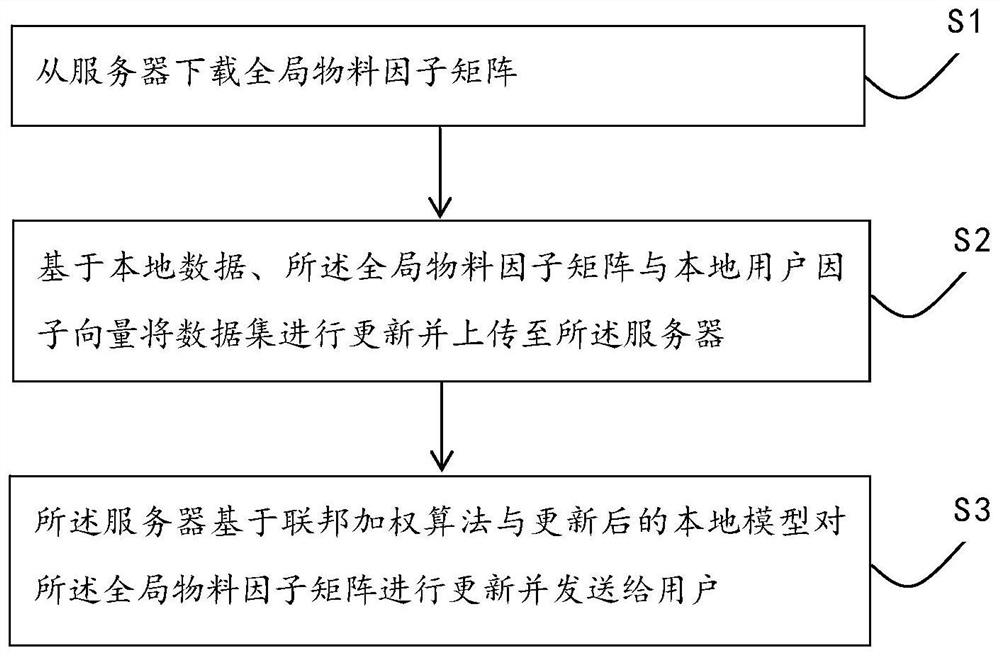
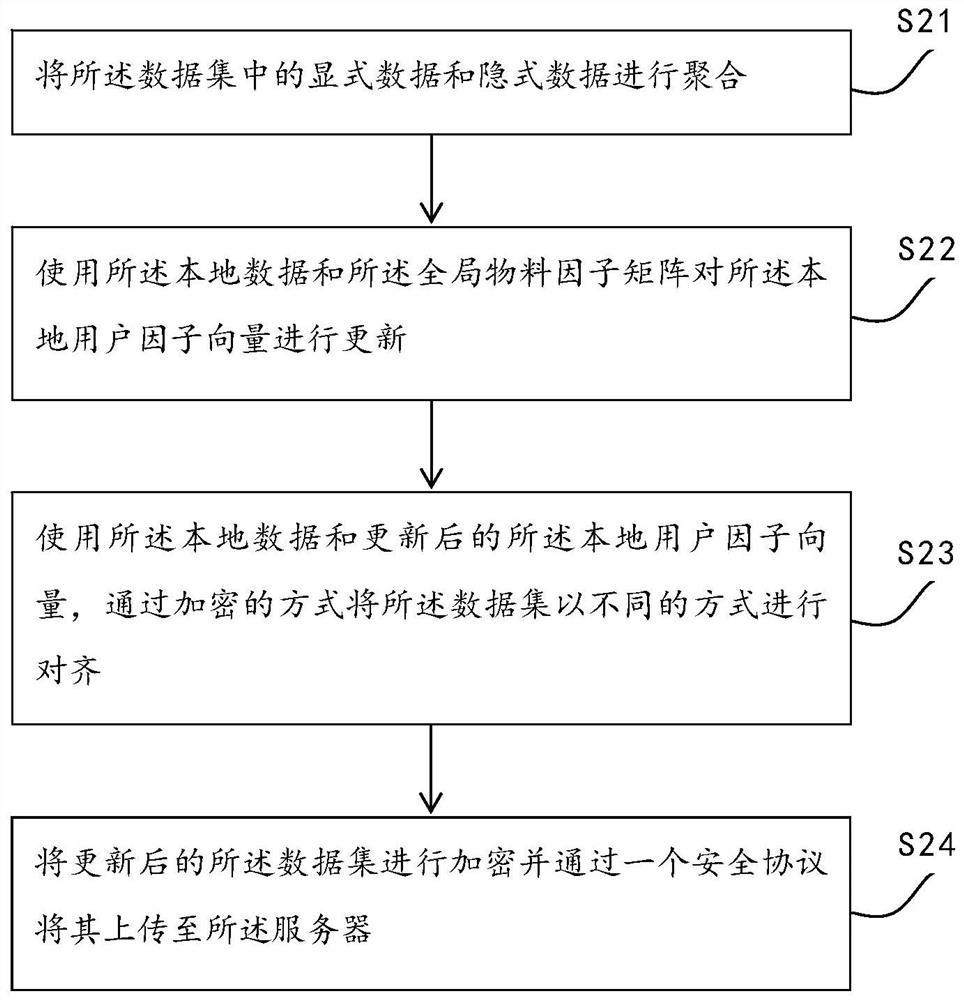
Federal learning model training method and system, electronic equipment and readable storage medium
PendingCN112487456AAchieve data isolationPromote fair cooperationDigital data information retrievalDigital data protectionData privacy protectionData set
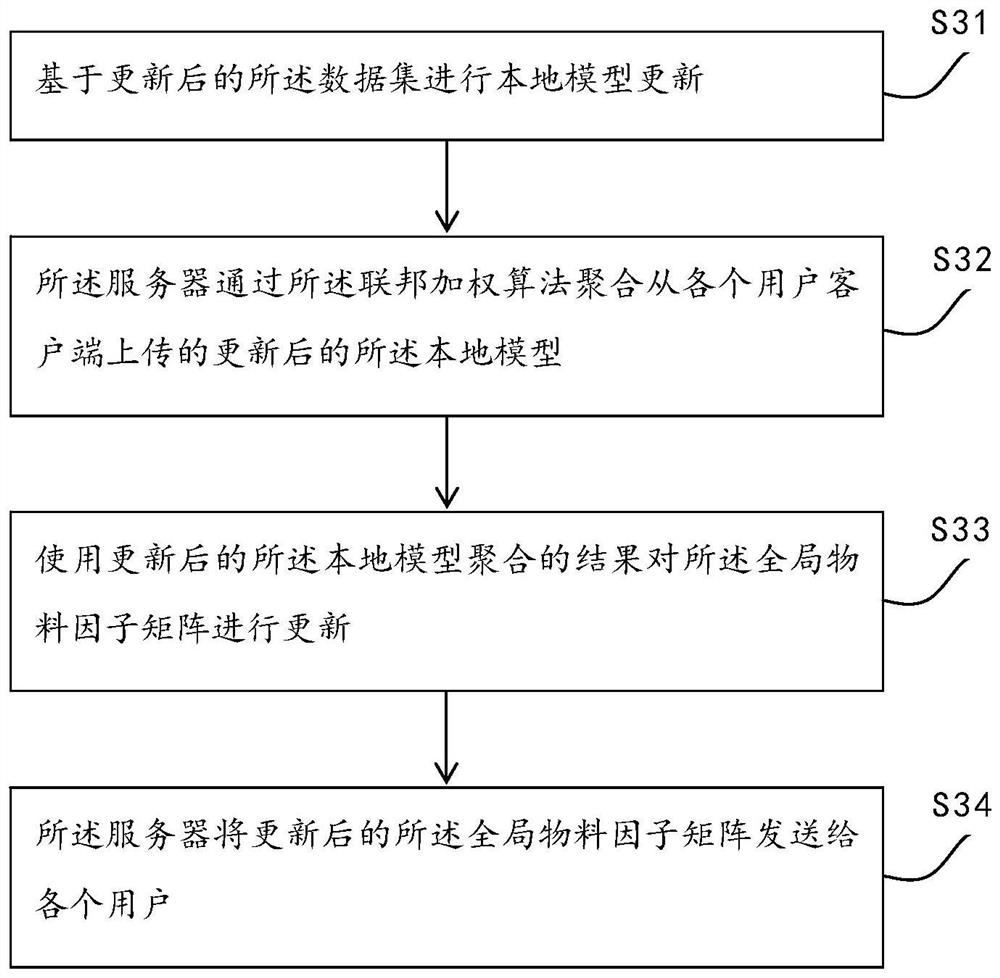
The invention discloses a federated learning model training method and system, electronic equipment and a readable storage medium. The method comprises the steps that a global material factor matrix is downloaded from a server; the data set is updated based on the local data, the global material factor matrix and the local user factor vector and uploaded to the server; and the server updates the global material factor matrix based on a federated weighting algorithm and the updated local model and sends the updated global material factor matrix to the user. In the whole modeling process, data sharing and data privacy protection are effectively achieved, and encryption exchange of information is carried out under the condition that it is guaranteed that two participating parties are kept independent.
Owner:BEIJING XUEZHITU NETWORK TECH
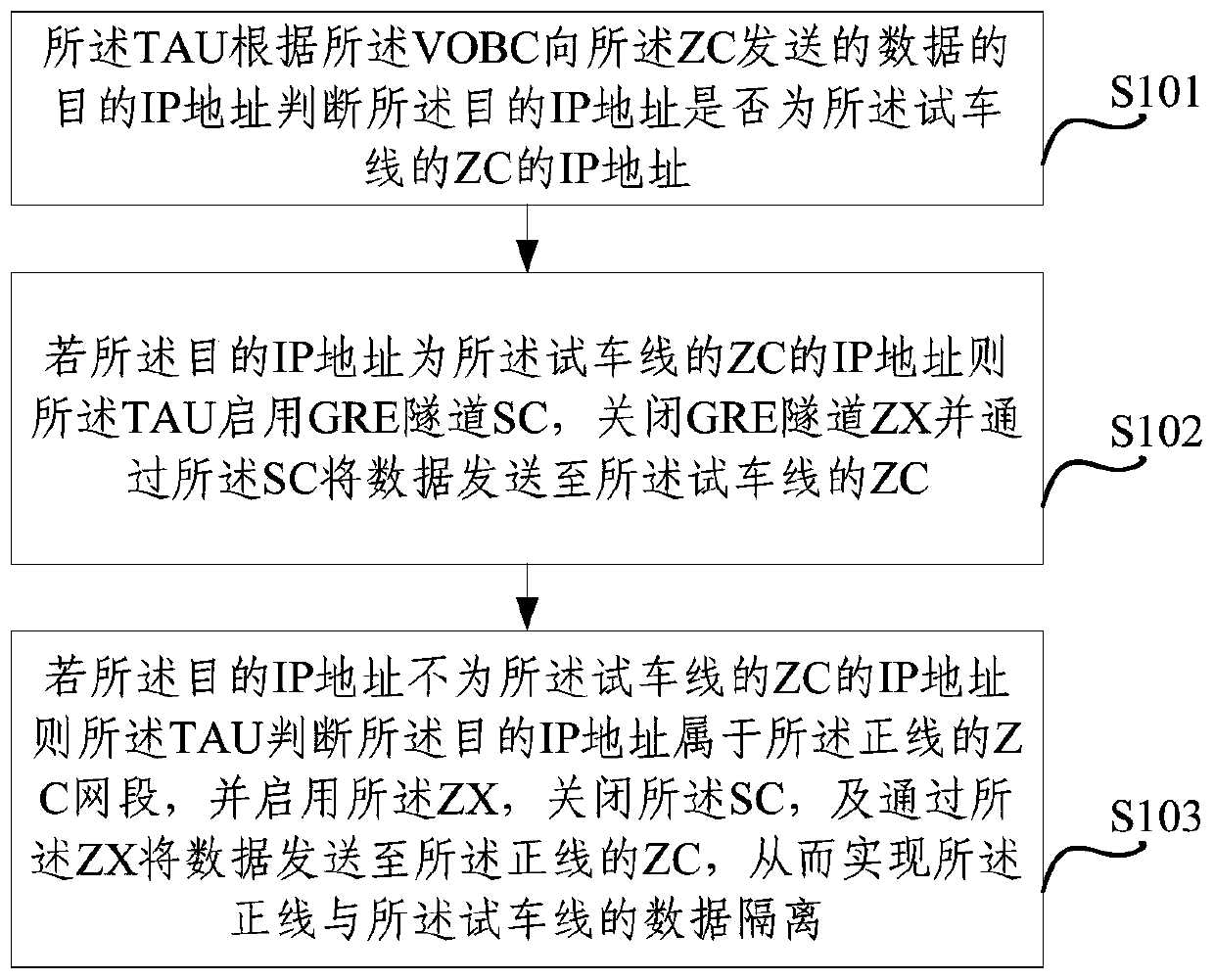
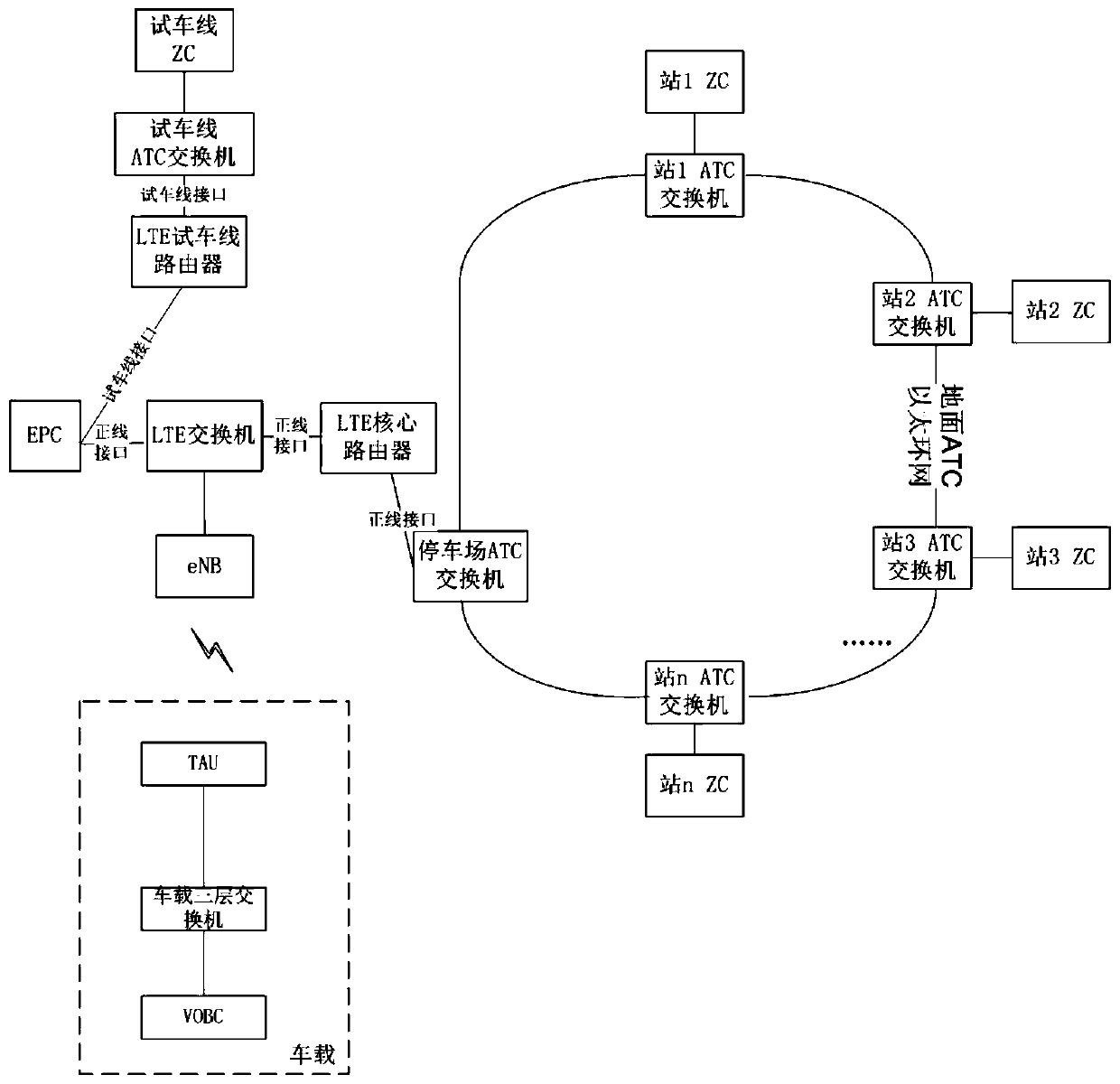
Data isolation method for main line and testing line, and communication device applied to the method
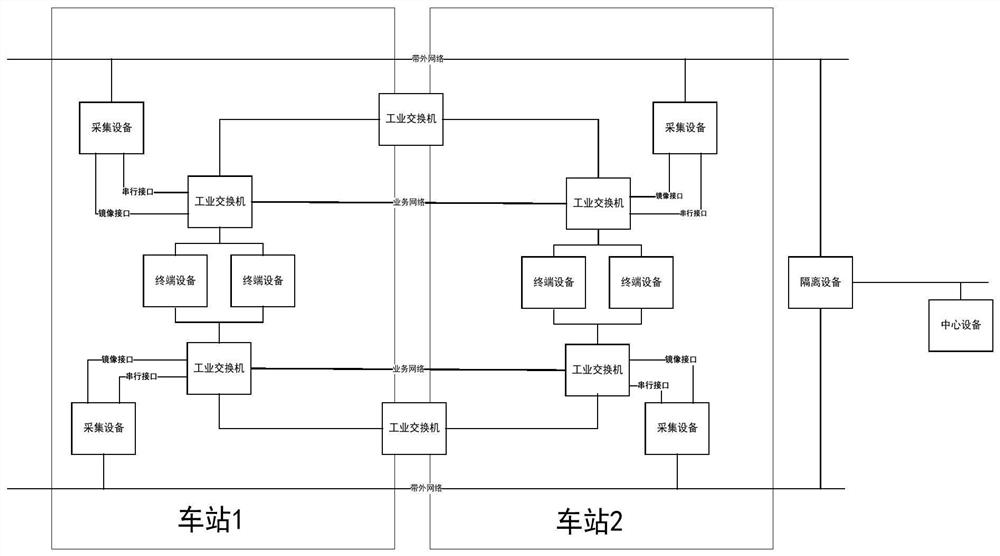
The invention provides a data isolation method for a main line and a testing line in an urban mass transit line, and a communication device applied to the method, and relates to the technical field of communication. The method comprises the following steps: a TAU judges whether a destination IP address is the IP address of the testing line according to the destination IP address of data sent by a VOBC to a ZC; if the destination IP address is the IP address of the testing line, the TAU starts a GRE tunnel SC, closes a GRE tunnel ZX, and sends data to the ZC of the testing line through the SC; if the destination IP address is not the IP address of the ZC of the testing line, the TAU judges that the destination IP address belongs to a ZC network segment of the main line, starts the ZX, closes the SC, and sends the data to the ZC of the main line through the ZX so as to realize the data isolation of the main line and the testing line, wherein the urban mass transit line comprises a vehicle-mounted controller VOBC, a zone controller ZC and a communication device TAU. By adoption of the data isolation method provided by the invention, undesirable influence of the device operation of the testing line to the operation of a TAC network device of the main line can be avoided.
Owner:TIANJIN TRAFFIC CONTROL TECH CO LTD
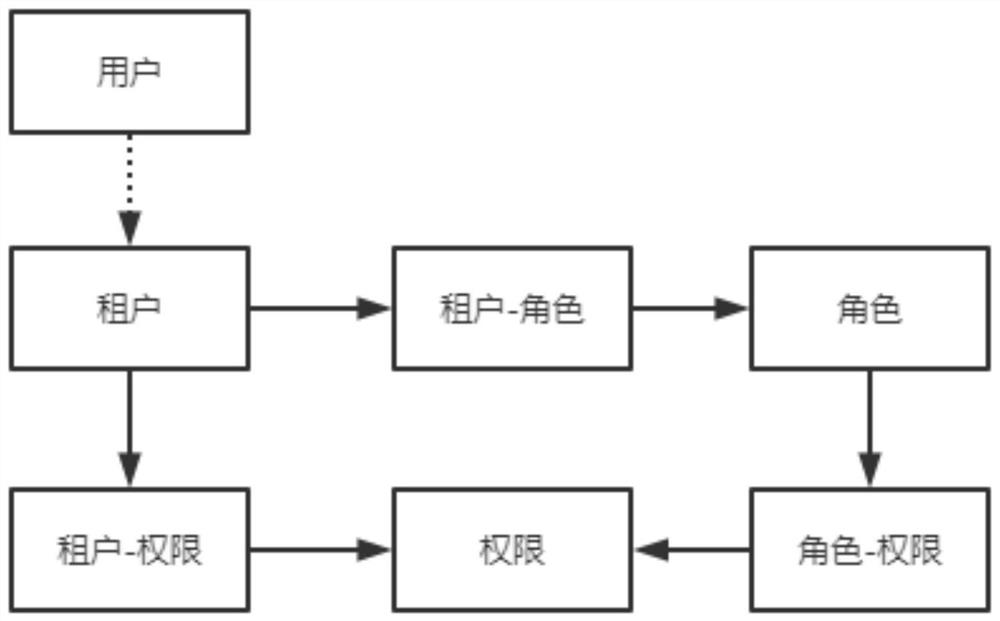
Multi-tenant permission system based on BRAC model
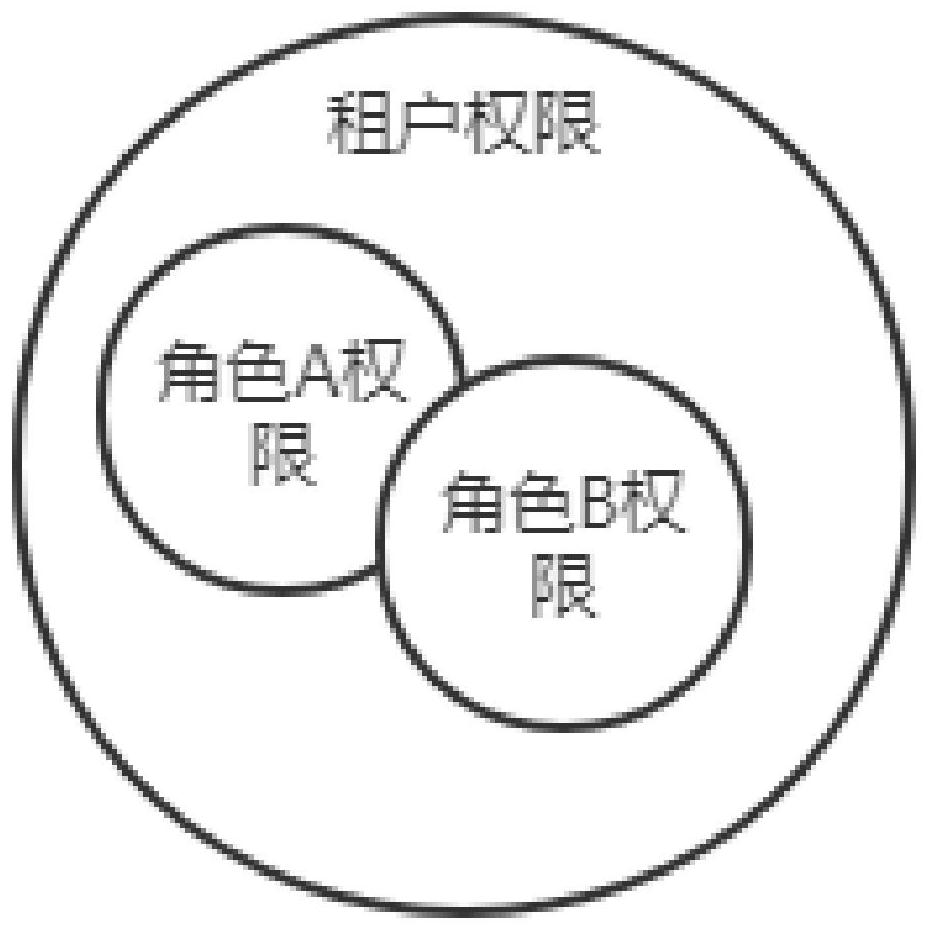
The invention discloses a multi-tenant permission system based on a BRAC model, which associates tenants with permissions, and can set the maximum permissions owned by all users under the tenants by default in batches by directly allocating permissions to the tenants. The tenants are associated with the roles, and the permissions are allocated to the roles of the tenants, so that the permissions can be allocated to all users under the tenants in a personalized and batched manner. The data is related to the tenants, so that the data accessed by the user is the data under the tenants, the data under other tenant spaces cannot be accessed, and the data isolation effect is achieved.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
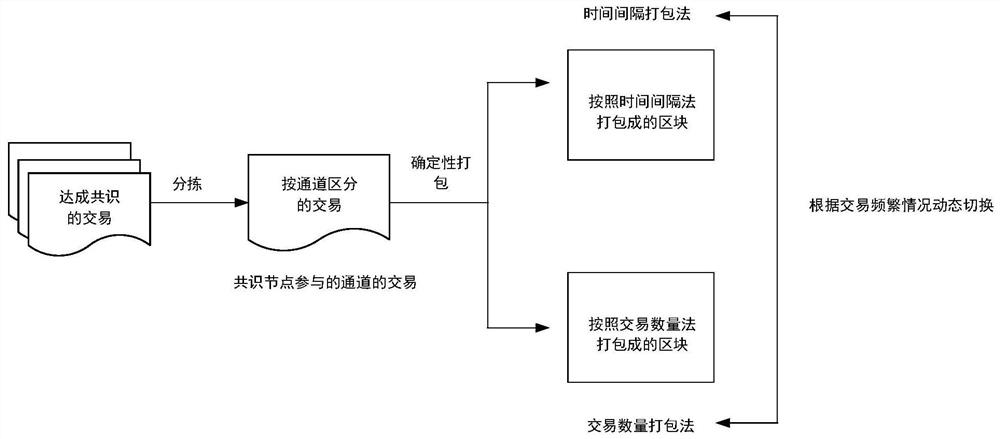
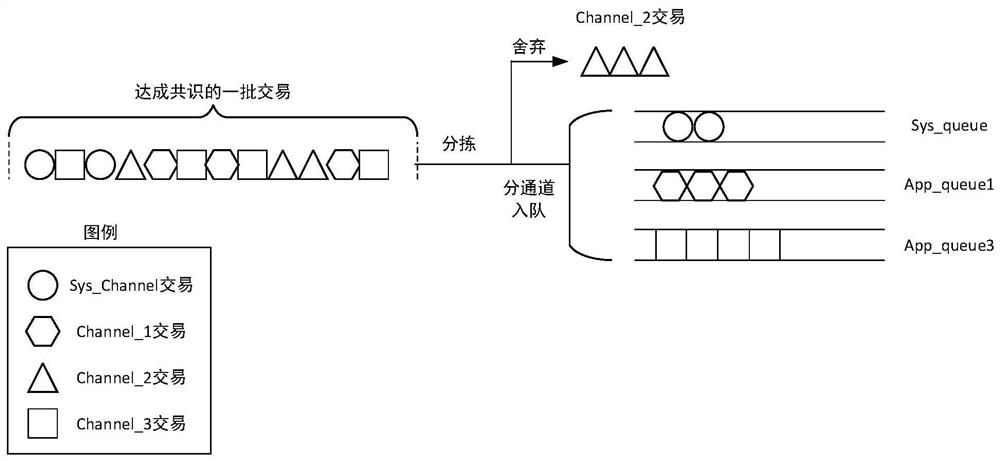
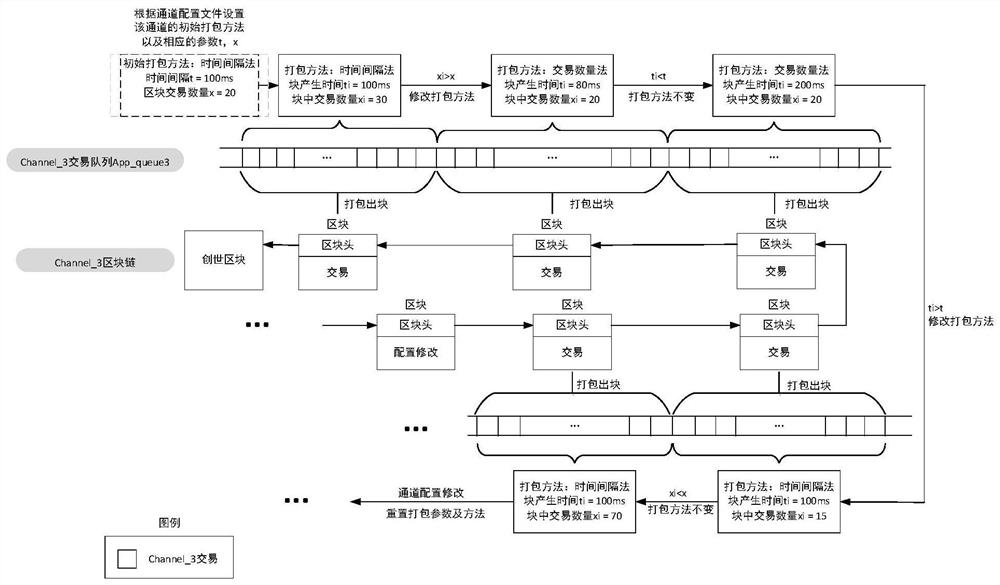
Block packaging method and device for multiple channels of blockchain, and storage medium
ActiveCN112804233AGuaranteed timelinessAchieve data isolationEnergy efficient computingSecuring communicationComputer networkFinancial transaction
The invention relates to a block packaging method and device for multiple channels of a blockchain, and a storage medium. The method comprises the following steps: S1, sorting and storing transactions reaching a consensus according to channels by each consensus node, and forming a system channel queue and an application channel queue corresponding to each consensus node, wherein the system channel queue stores system channel transactions, the application channel queue stores application channel transactions in application channels participated by the consensus node, and each application channel participated by the consensus node corresponds to one application channel queue; S2, for a system channel queue, when system channel transactions exist in the queue, immediately packaging the system channel transactions to generate blocks; and S3, for the application channel queue, dynamically adjusting a block packaging method according to the transaction frequency condition of the corresponding application channel, and packaging the application channel transaction based on the determined packaging method to generate a block. Compared with the prior art, data isolation based on channels is achieved, and safety and packaging efficiency are improved.
Owner:欧冶云商股份有限公司
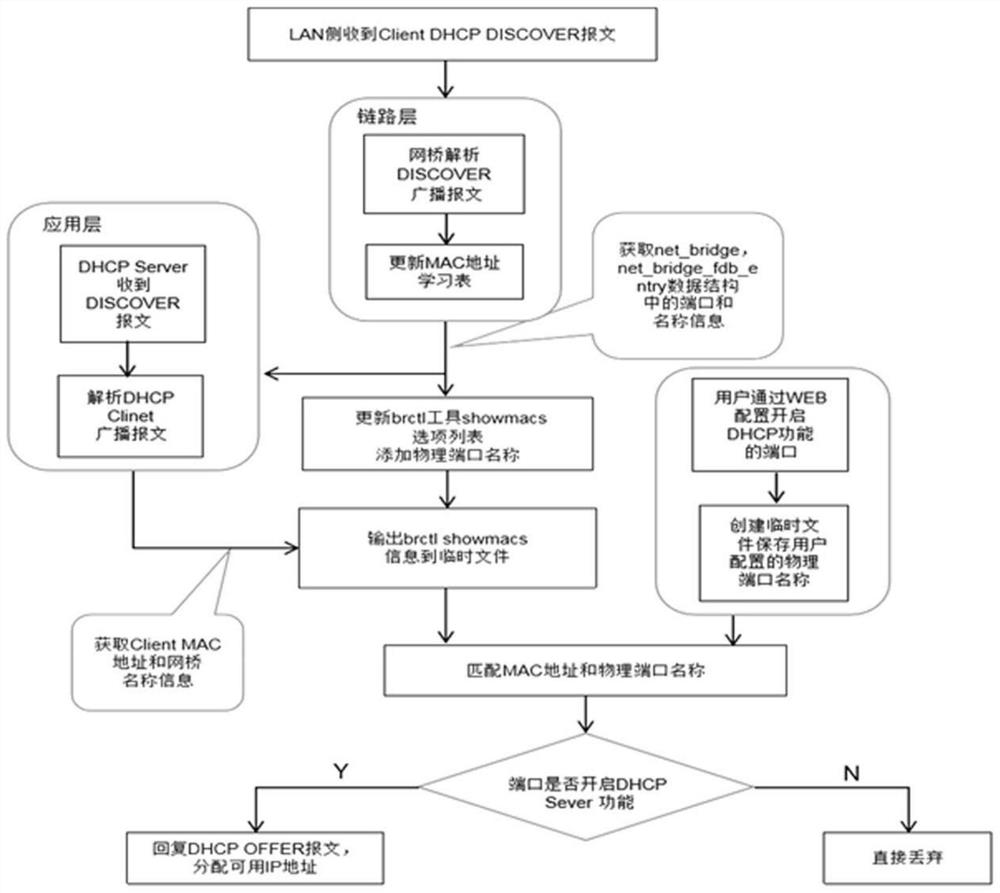
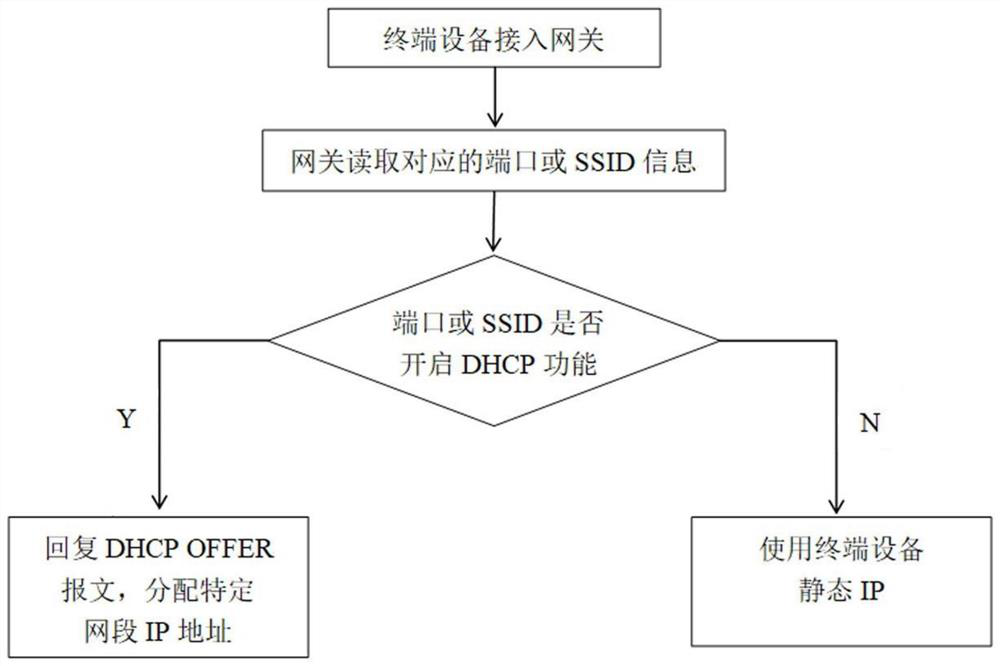
Method for realizing intelligent network access of LAN side terminal
InactiveCN112003771AMeet the needs of building a mixed network environmentAchieve data isolationWide area networksIntelligent NetworkIp address
The invention discloses a method for realizing intelligent network access of an LAN side terminal. The method comprises the following steps: receiving a Client DHCP DISCOVER message by an LAN side; enabling the network bridge to analyze the DISCOVER message and update the MAC address learning table; after the DHCP Server receives the DISCOVER message, acquiring a Client MAC address and network bridge name information, querying user configuration information, and matching the MAC address with the physical port name, inquiring whether the physical port starts a DHCP Server function, if so, replying a DHCP OFFER message by the DHCP Server, allocating an available IP address, and otherwise, losing the message to realize a function of forbidding automatic IP address allocation. Therefore, the equipment accessed to different ports on the same LAN side can select to automatically obtain the address or configure the static IP address through the DHCP.
Owner:SICHUAN JIUZHOU ELECTRONICS TECH
Logic network establishing method based on functional blocks
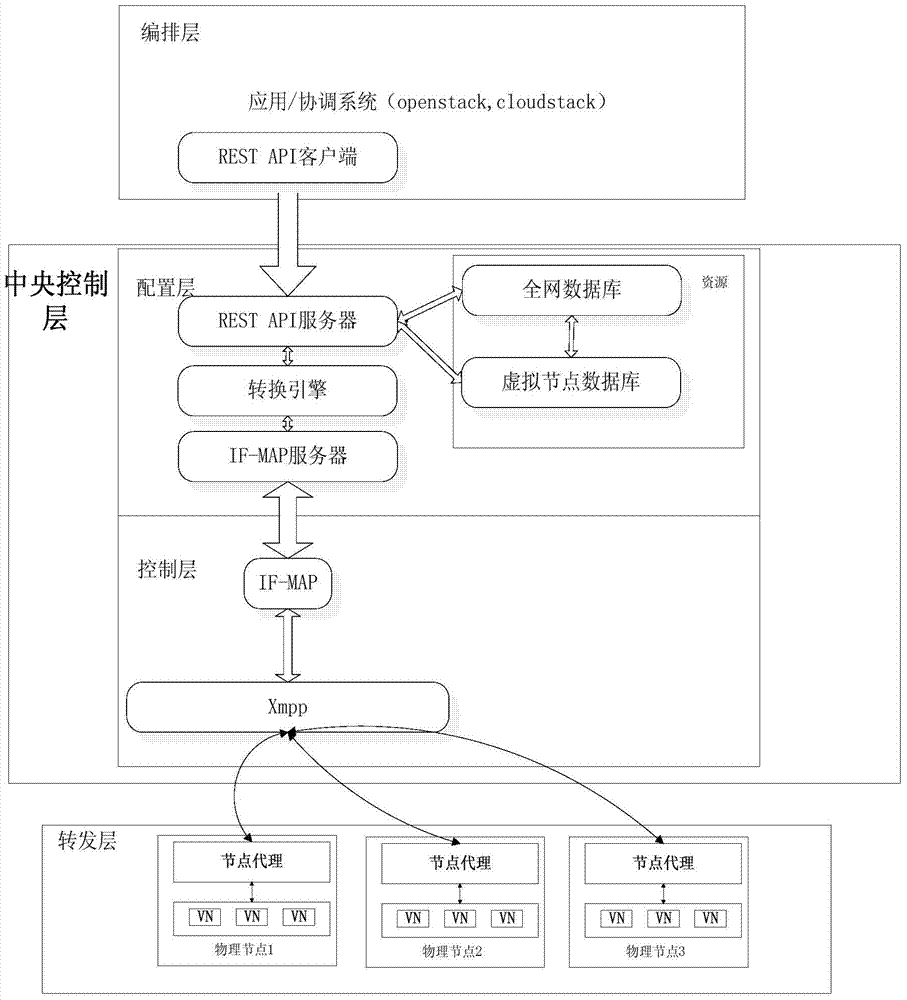
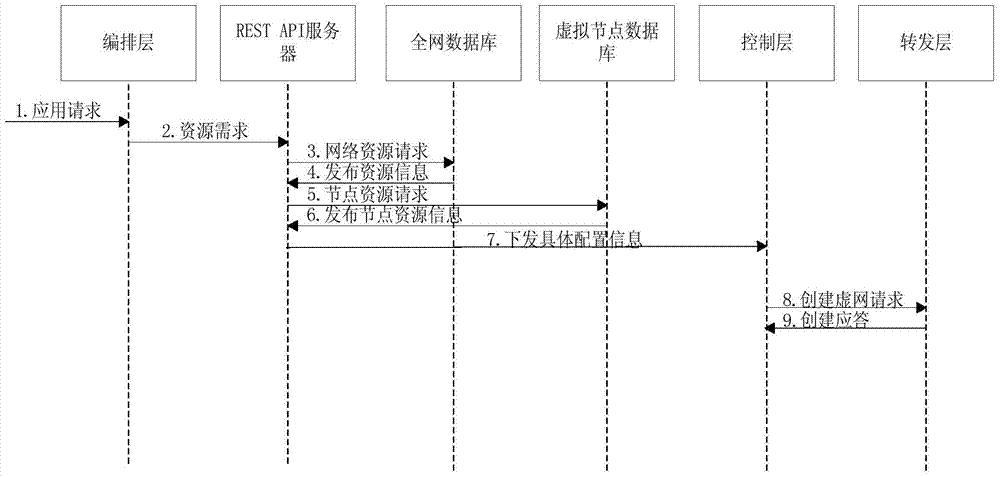
ActiveCN104283949ALoad balancingAchieve data isolationData switching networksSpecial data processing applicationsNODALControl layer
The invention discloses a logic network establishing method based on functional blocks. The method includes the steps that an arrangement layer, a center control layer and a forwarding layer are defined for a logic network, the specific functional blocks are defined at each layer, and therefore logic network establishment from upper layer applications to bottom layer data forwarding is achieved; resource demands are sent through the specific arrangement layer to an RESTAPI server located in the center control layer; the RESTAPI server sends virtual node resource information to a conversion engine assembly located in a configuration layer, and logic network configuration information is calculated by the conversion engine assembly and sent to the control layer through an IF-MAP protocol; according to the logic network configuration information, the control layer finds physical nodes corresponding to the logic network configuration information and sends a virtual node creating notice to each physical node. By the adoption of the method, according to different upper layer applications, a bottom layer forwarding plane can establish a special logic network used by the upper layer applications all the time, and data isolation in a virtual network is achieved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
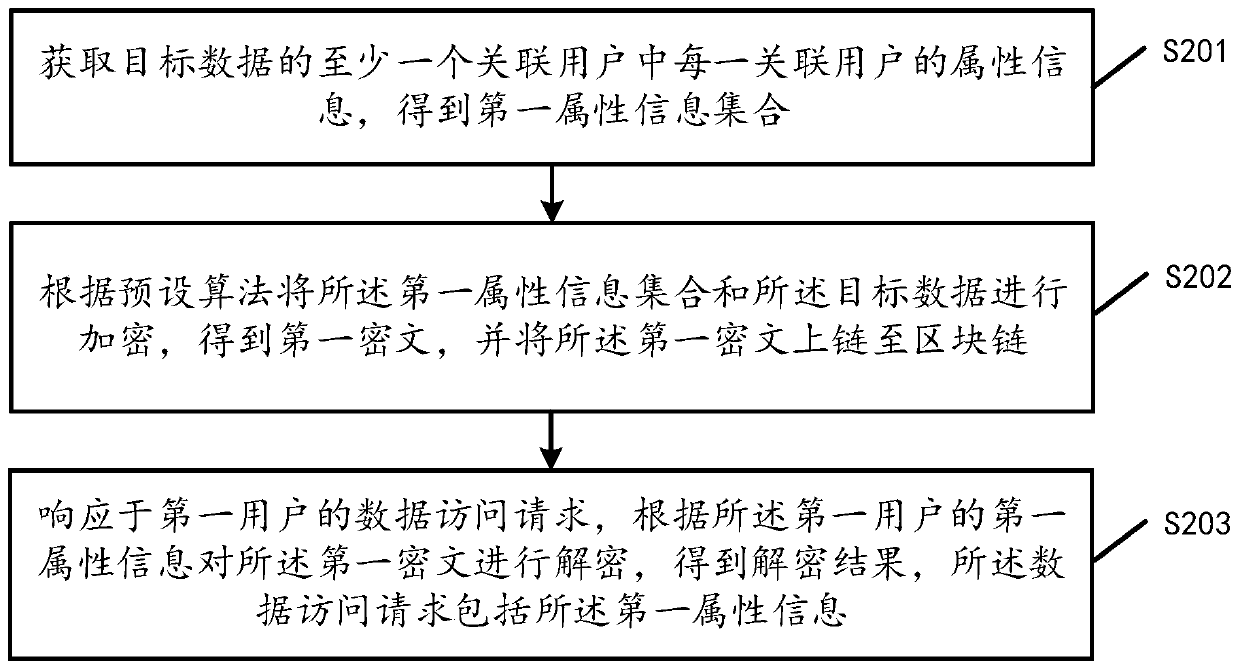
Data processing method and device, computer equipment and storage medium
PendingCN111553686AAchieve data isolationPayment protocolsPayments involving neutral partyCiphertextData access
The embodiment of the invention discloses a data processing method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining a first attribute information setthrough obtaining the attribute information of each associated user in at least one associated user of target data; encrypting a first attribute information set and the target data according to a preset algorithm to obtain a first ciphertext, and uploading the first ciphertext to a block chain; furthermore, when the first user needs to access the target data, in response to a data access request of the first user, the first ciphertext is decrypted according to the first attribute information of the first user to obtain a decryption result, and the data access request comprises the first attribute information, so that data isolation can be realized by associating the attribute information of the user.
Owner:TENCENT TECH (SHENZHEN) CO LTD
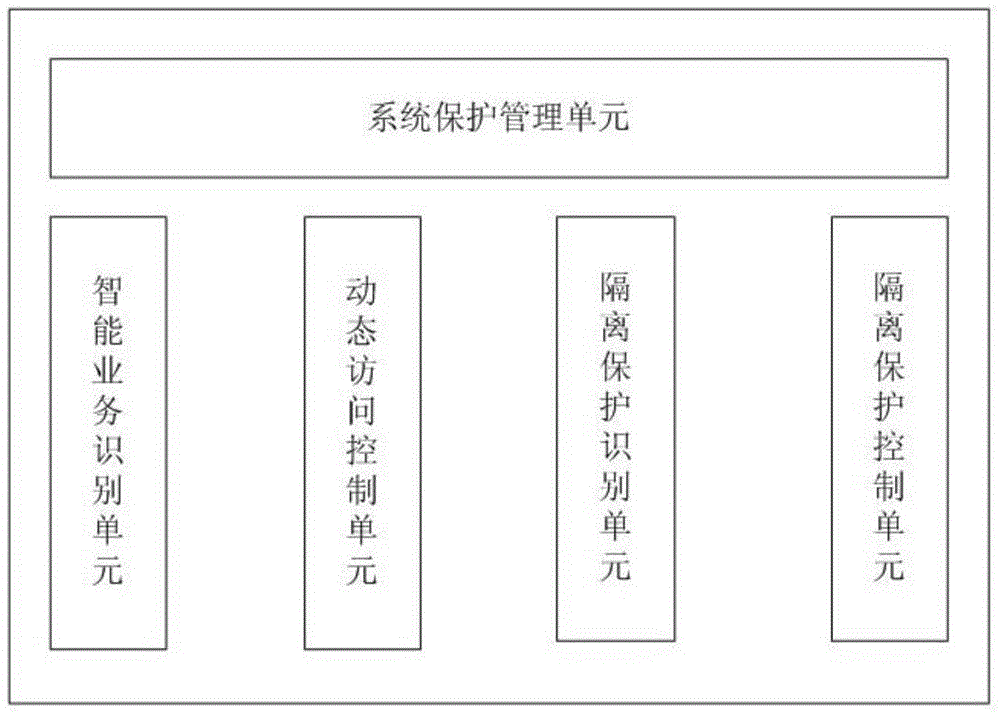
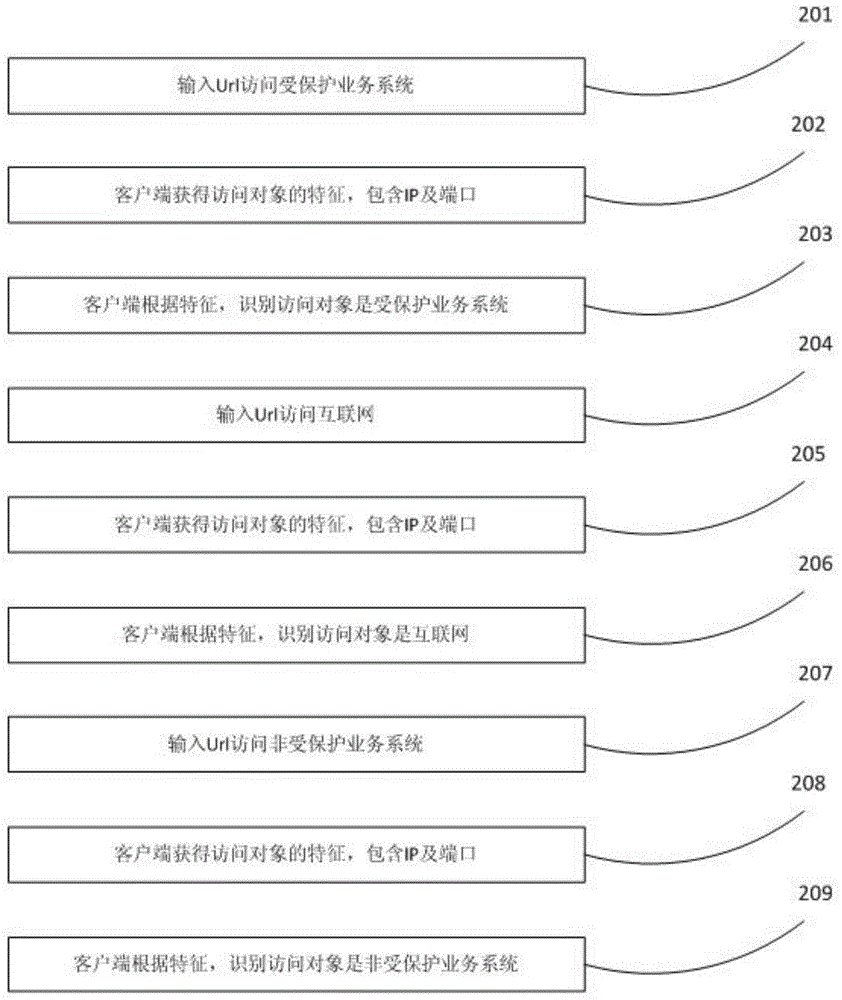
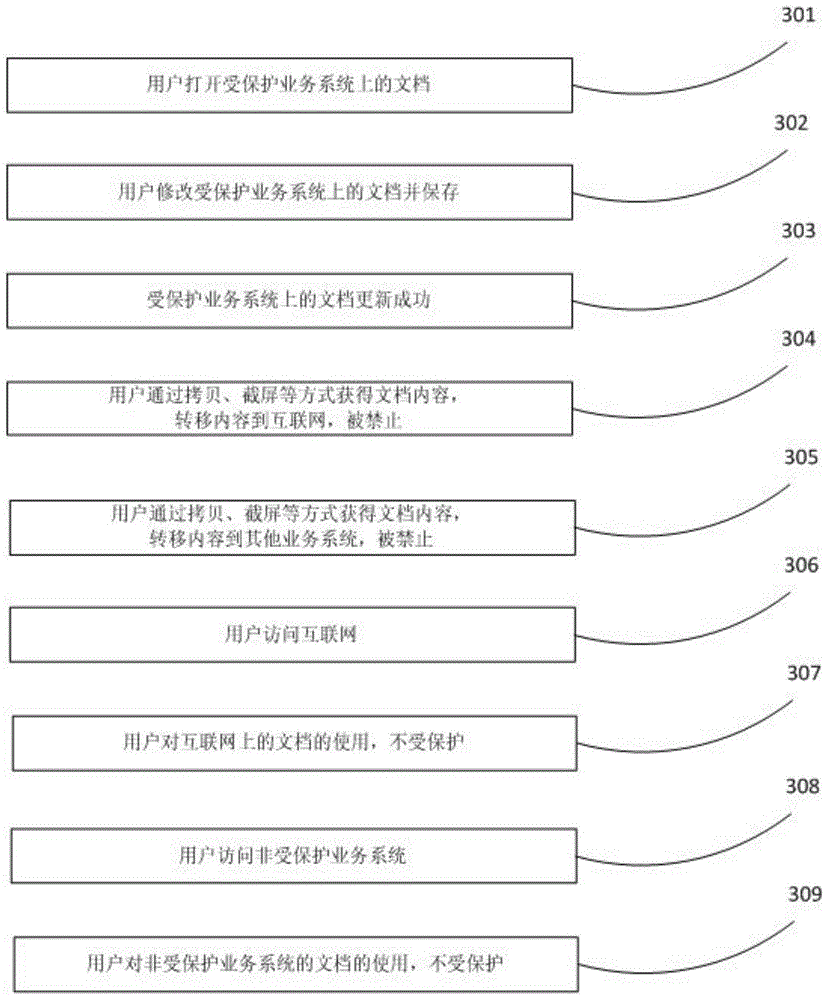
Service system dynamic isolation protecting method and system based on browser
The invention relates to a service system dynamic isolation protecting method and system based on a browser. According to the service system dynamic isolation protecting method and system based on the browser, intelligent recognition of a service system is taken as the core, a protected service system is dynamically recognized in real time, documents of the protected service system, users of the protected service system and users accessing the protected service system currently are bound, the protected service system is made to be isolated from the other service systems and external networks, and the documents of the current users are isolated from the other users. When the users access the protected service system through the browser, the accessing objects do not need to be recognized actively, manual switching is not needed, the assistance of a dedicated safe browser or other hardware equipment is not needed either, and the service system can be used directly. The users can continue to use the external networks or other service systems when using the protected service system. Meanwhile, isolation protection is carried out on the data of the protected service system, and thus the risks of exposure of data of enterprises are eliminated.
Owner:CHINA NAT SOFTWARE & SERVICE
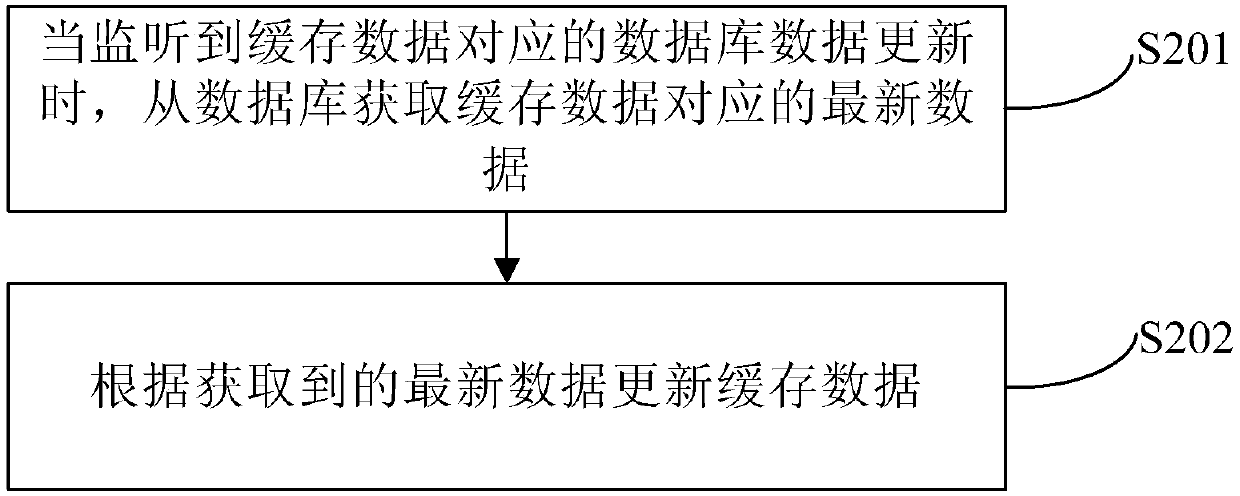
Data synchronous updating method and device
PendingCN110309157AReduce network overhead and time consumptionReduce the risk of read timeoutsDatabase updatingDatabase distribution/replicationService systemSystem stability
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
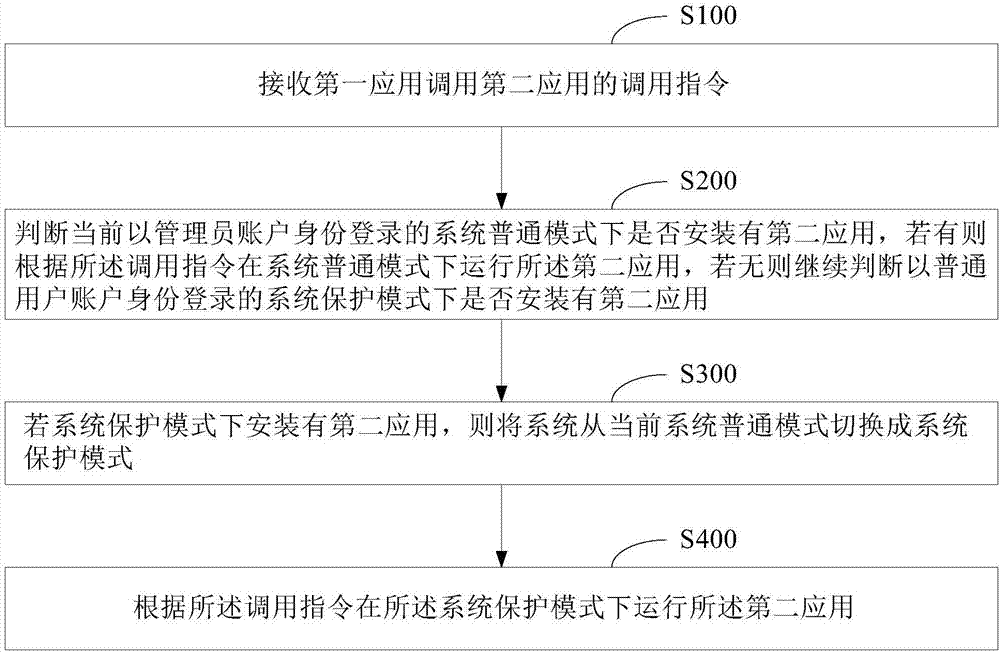
Method and device for invoking application range and mobile terminal
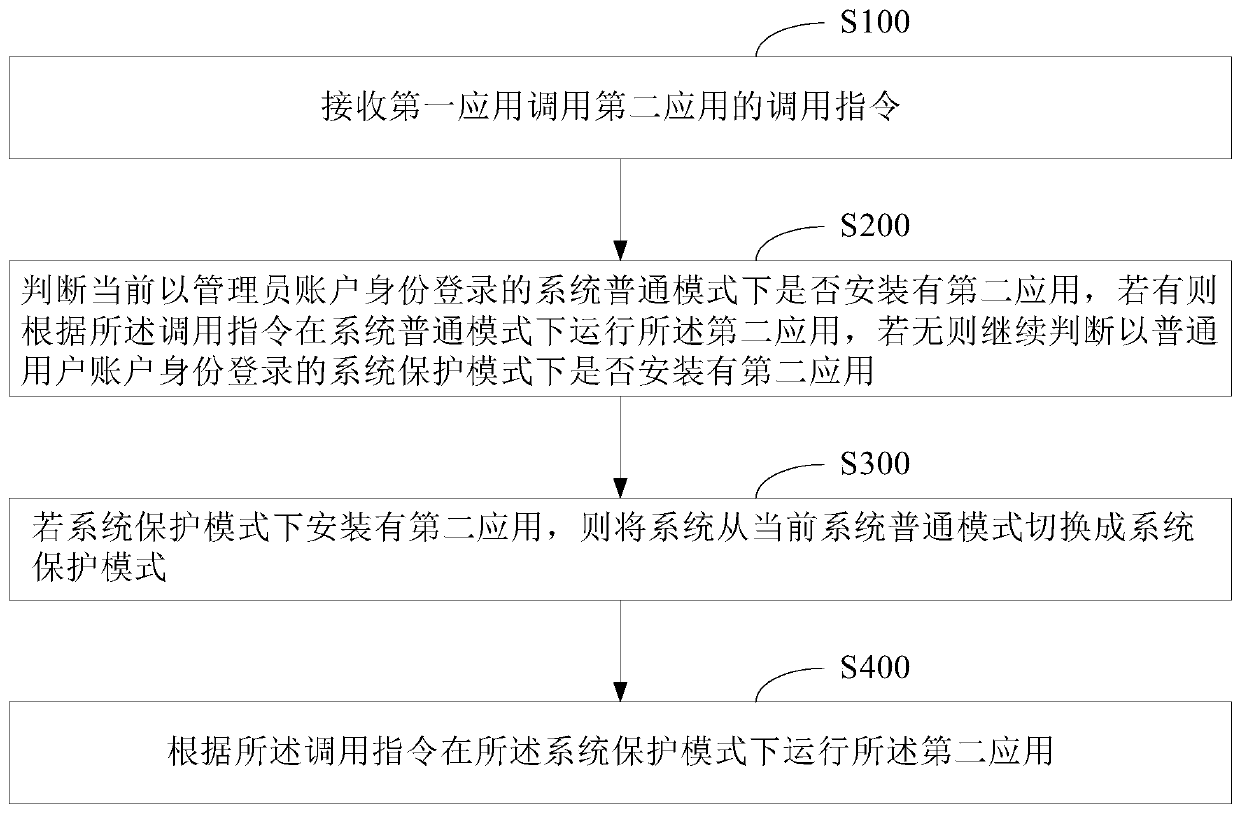
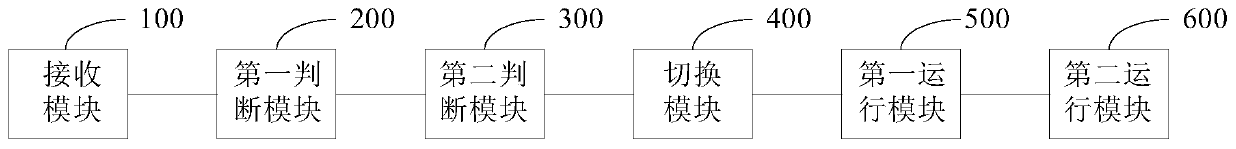
ActiveCN106874746AImprove experienceSave spaceInternal/peripheral component protectionNormal modeComputer terminal
The invention provides a method and device for invoking an application program. The method comprises: receiving an invoking instruction to invoke a second application by a first application; determining whether the second application is installed in a current system normal mode with an administrator logged in; if yes, running the second application in the system normal mode according to the invoking instruction; if no, continuing to determine whether the second application is installed in a system protection mode with a normal user logged in; switching the system from the current system normal mode to the system protection mode when the second application is installed in the system protection mode; and running the second application in the system protection mode according to the invoking instruction, wherein a safe space providing a running resource for running of a predetermined application is configured in the system protection mode, and the safe space is unavailable in the system normal mode. The above method and device avoid repeated installation of an application in multiple modes, thereby saving the system space and enhancing the user experience. Besides, a mobile terminal is also provided.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
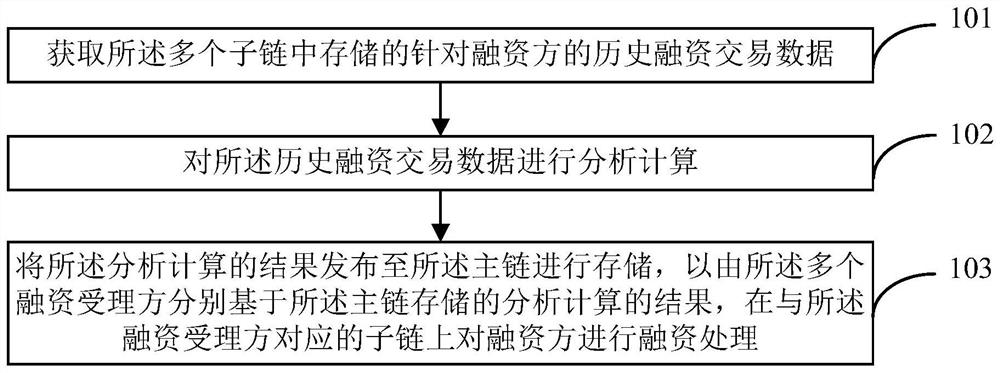
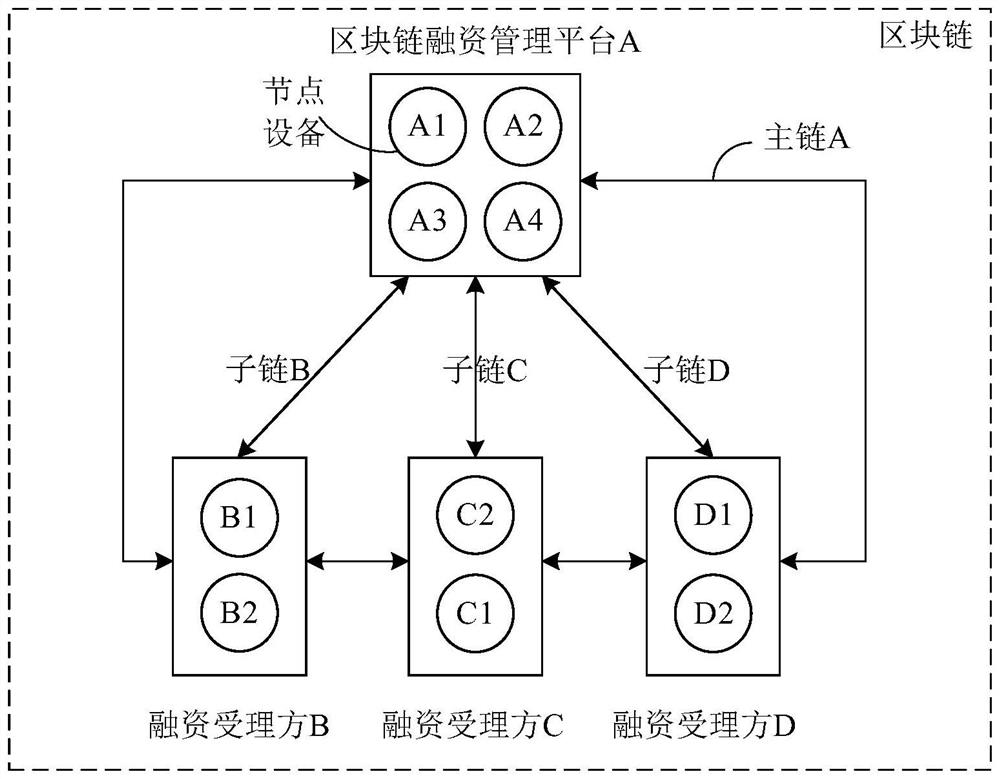
Financing method and device based on block chain, electronic equipment and storage medium
PendingCN114444120AEasy to carry outPrevent leakageFinanceDigital data protectionPrivacy protectionTransaction data
The invention provides a financing method based on a block chain, and the method is applied to a block chain financing management platform, and comprises the steps: obtaining historical financing transaction data which is stored in a plurality of sub-chains and aims at a financing party; analyzing and calculating the historical financing transaction data; and issuing an analysis and calculation result to a main chain for storage, so that a plurality of financing acceptance parties carry out financing processing on the financing parties on sub-chains corresponding to the financing acceptance parties based on the analysis and calculation result stored in the main chain. According to the technical scheme, on one hand, the platform can provide a plurality of financing acceptance parties for a financing party, each financing acceptance party provides a financing service on the corresponding sub-chain, and data isolation and privacy protection are achieved; and on the other hand, the platform can obtain historical financing transaction data through each sub-chain for analysis and calculation, and through giving an analysis and calculation result, leakage of the historical financing transaction data is avoided, and at the same time, a financing acceptor can make a more accurate decision, and financing business can be further developed.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD +1
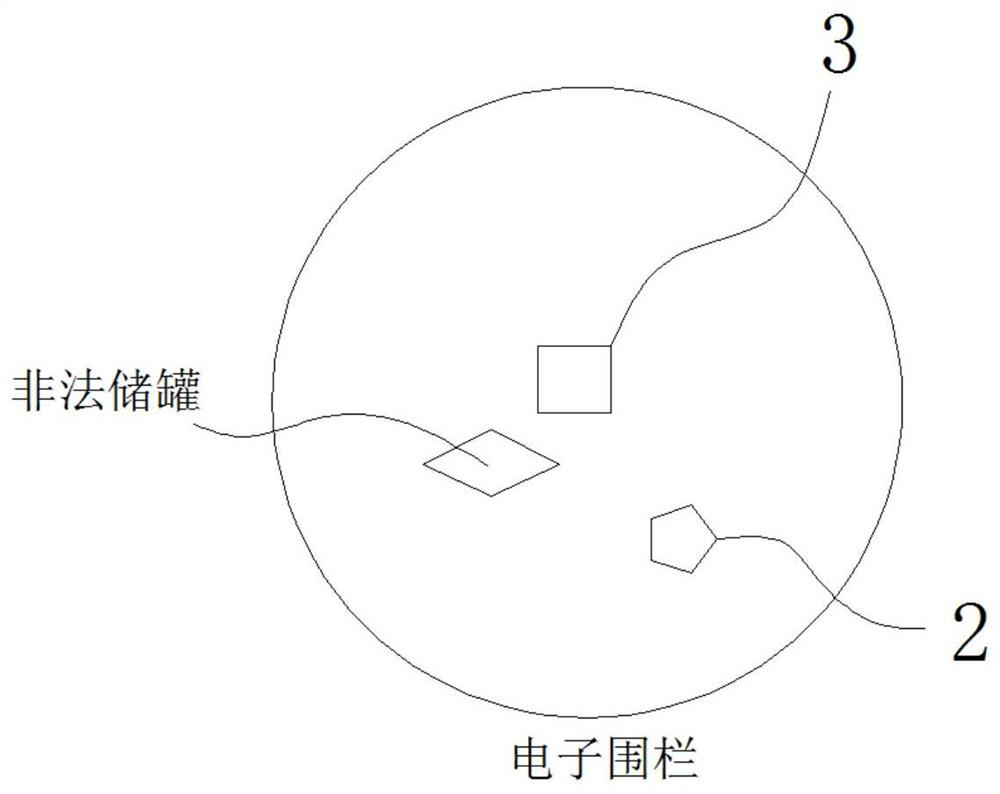
Hazardous chemical substance transportation liquid unloading comprehensive monitoring management system and monitoring management method
ActiveCN113110248AAvoid liquid fillingReduce energy consumptionProgramme controlComputer controlIntegrated monitoringTank truck
The invention relates to a hazardous chemical substance transportation liquid unloading comprehensive monitoring management system and a monitoring management method, and the system comprises: a monitoring platform which is used for managing and transmitting waybill information and waybill electronic tag information, and constructing a pump tank car digital twin; a tank car with a pump is driven to a specified fixed storage tank for unloading liquid, collecting and sending tank car information and position information, establishing near field communication with the storage tank, receiving a secret key sent by the storage tank, comparing the secret key with the storage tank, generating a storage tank control instruction, and judging whether liquid unloading is allowed or not; a fixed storage tank which is used for replying the secret key, unlocking the electronic lock according to the tank control instruction, comparing the electronic tag and sending a comparison result to the tank car with the pump; and an MQTT protocol proxy server which is used for subscribing and distributing data among the monitoring platform, the tank car with the pump and the fixed storage tank, and configuring data subscription permissions of different monitoring platforms. The condition that a legal tank truck with a pump fills liquid into an illegal storage tank can be completely eradicated, repeated construction of a supervision platform in the industry is reduced, and energy consumption and flow consumption of a terminal are reduced.
Owner:杭州数成金象科技有限公司
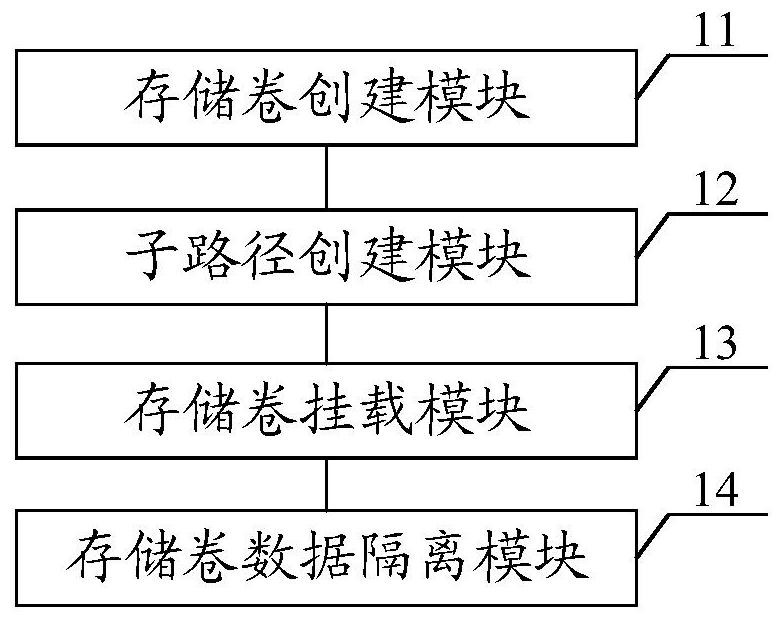
Sub-path-based data storage method and device, equipment and storage medium
PendingCN113835625AImprove multi-service application performance and storage resource utilizationAchieve data isolationInput/output to record carriersEnergy efficient computingPathPingSystems engineering
The invention discloses a sub-path-based data storage method and device, equipment and a storage medium. The method comprises the following steps: creating a storage volume for storing to-be-stored data of a plurality of business applications according to a first instruction; creating a plurality of sub-paths, corresponding to the plurality of business applications, of the storage volume according to a second instruction; wherein a unique corresponding relationship exists between each business application and the corresponding sub-paths; and mounting the plurality of sub-paths of the storage volume according to a third instruction, and storing the to-be-stored data of the corresponding business application by using the mounted sub-paths respectively. It can be seen that the storage volume and the multiple sub-paths, corresponding to the multiple business applications, of the storage volume are created according to the corresponding instructions, and then the to-be-stored data is stored by mounting the sub-paths, so that data isolation of different business systems is achieved, and the multi-business application performance and the storage resources utilization rate are improved.
Owner:GUANGDONG INSPUR BIG DATA RES CO LTD
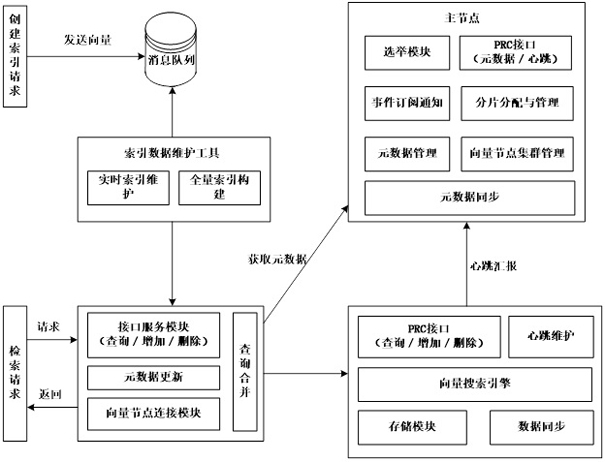
Distributed vector retrieval system and method
ActiveCN113254511AEnsure consistent updatesAchieve data isolationDatabase updatingSpecial data processing applicationsData synchronizationMessage queue
The embodiment of the invention discloses a distributed vector retrieval system, which comprises a main node group, which comprises a plurality of main nodes, one is a leader node, the leader node distributes an index table fragment to a specified vector node group, and the leader node synchronizes data of the index table to other main nodes; a plurality of vector node groups, each vector node group comprising a plurality of vector nodes, each vector node storing vector data and index table fragments, each vector node responding to a request from the routing node and retrieving data or synchronizing data; a routing node group which comprises a plurality of routing nodes, wherein each routing node sends the request to the corresponding vector node group and merges and returns retrieval results; and an index data maintenance tool which writes the index vector data into the index message queue according to the request and calls the routing node according to the message type. The embodiment of the invention further discloses a distributed vector retrieval method. Under the condition of high concurrent access, consistent updating of the offline index data and the online index data can be ensured.
Owner:北京华品博睿网络技术有限公司
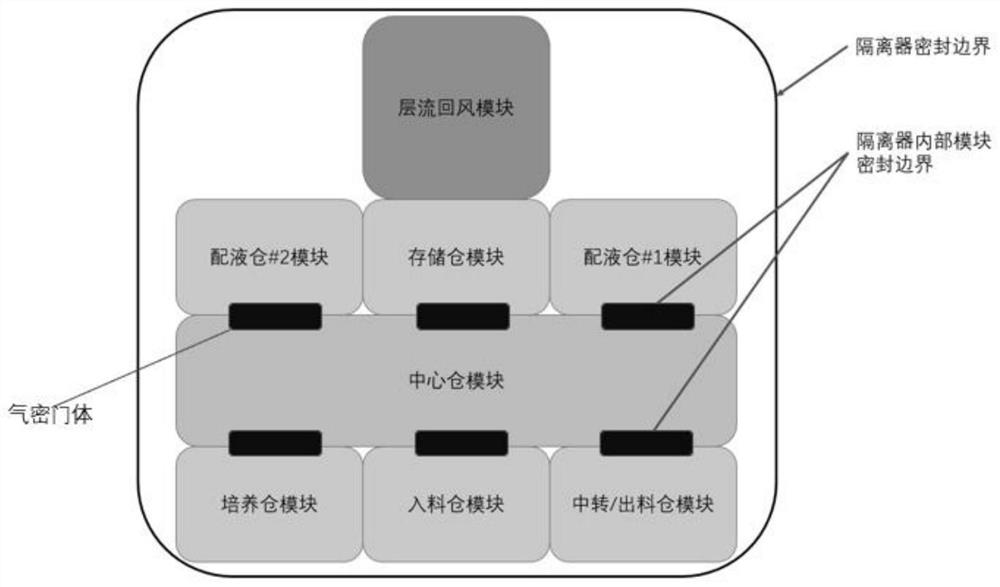
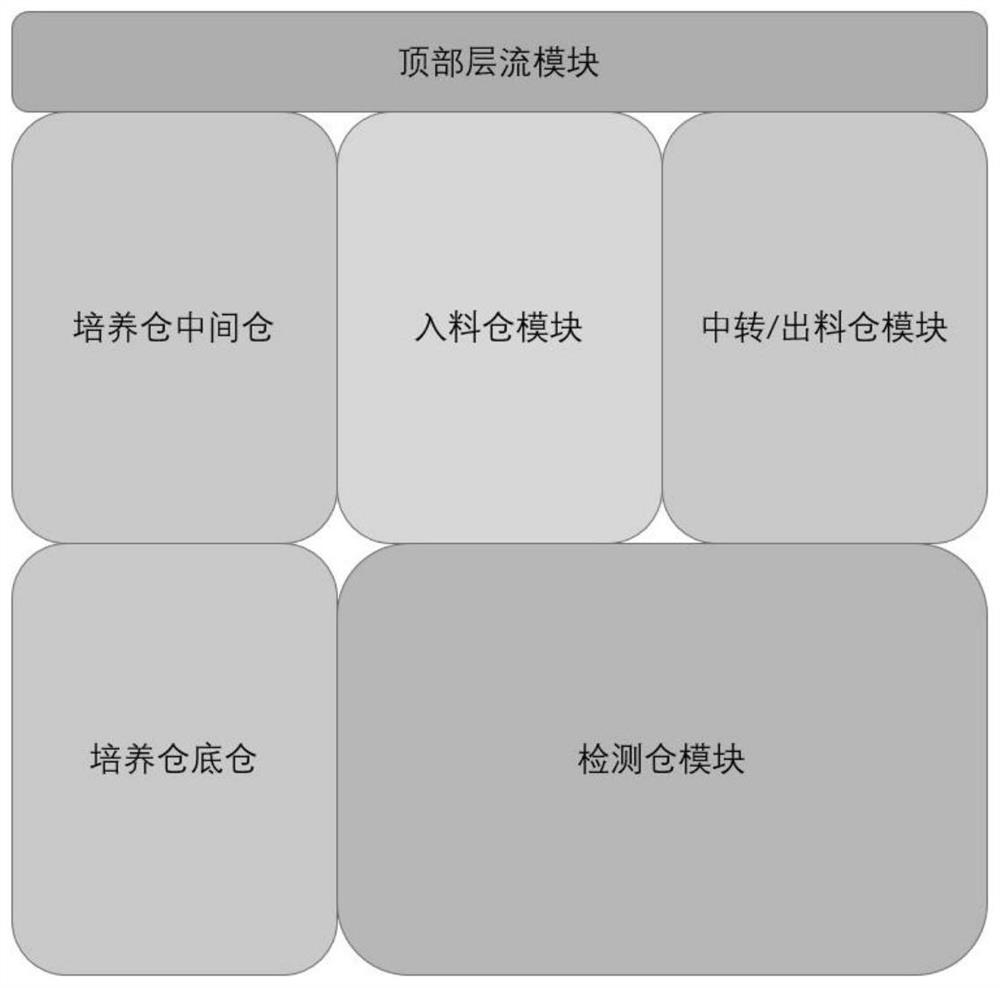
GMP compliance high-throughput intelligent biological medicine production system
PendingCN113549553ARealize complete traceabilityQuick researchBioreactor/fermenter combinationsBiological substance pretreatmentsProcess engineeringBiopharmaceutical
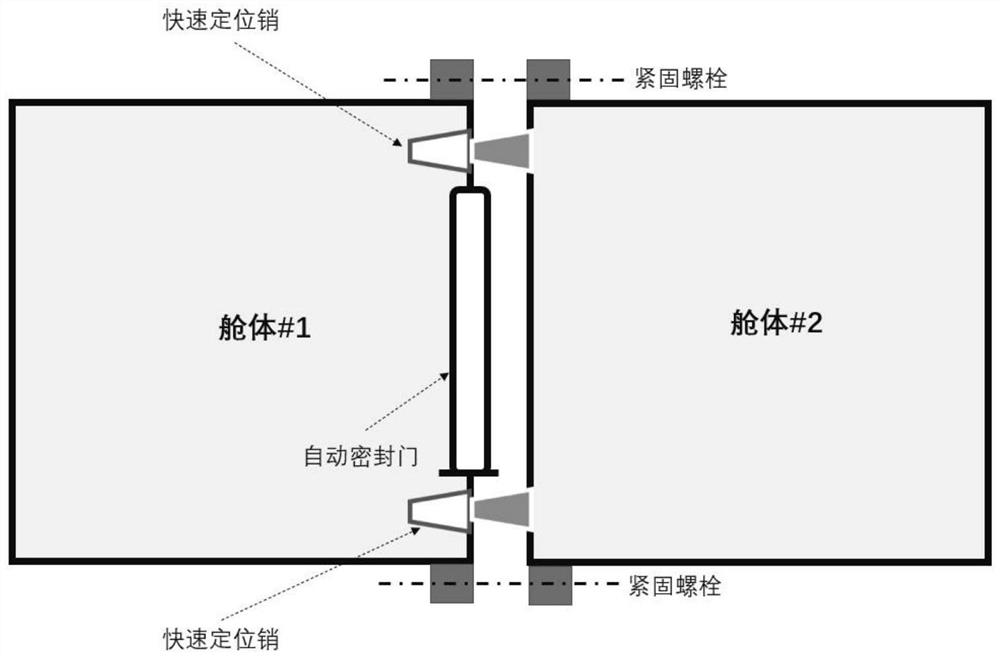
The invention relates to the technical field of biological medicine production, in particular to a GMP compliance high-throughput intelligent biological medicine production system. The GMP compliance high-throughput intelligent biological medicine production system comprises a detection cabin, a transfer discharging cabin, a feeding cabin, a culture cabin, a central cabin, a first liquid preparation cabin, a storage cabin, a second liquid preparation cabin, a laminar flow air return pipeline and a laminar flow air return cabin. The transfer discharging cabin is arranged on the right side of the end part of the detection cabin, the culture cabin is arranged on the left side of the feeding cabin, the central cabin is arranged on the rear side of the culture cabin, the second liquid preparation cabin is arranged on the rear side of the central cabin, the storage cabin is arranged on the right side of the second liquid preparation cabin, and the first liquid preparation cabin is arranged on the right side of the storage cabin; according to the GMP compliance high-throughput intelligent biological medicine production system, different operation areas are reasonably arranged and isolated, different technological operations such as important material transfer, liquid operation, culture and the like are executed in a completely closed and airtight cabin body, and full-automatic research, development and production of biological medicines are realized in combination with an intelligent dispatching system, an intelligent operation system and an intelligent data acquisition system.
Owner:INNOVEL INTELLIGENT TECH CO LTD
Data processing method and device, equipment and storage medium
PendingCN113935046AAchieve data isolationConsider data storage costsDigital data protectionData accessEngineering
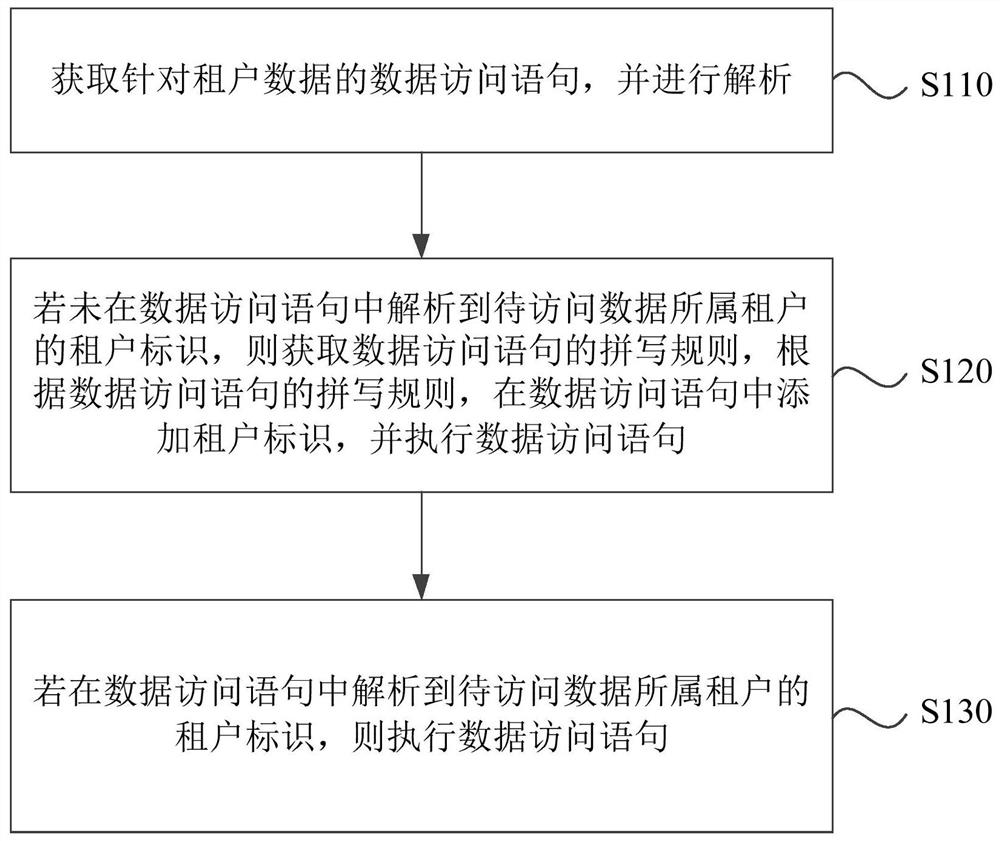
The invention discloses a data processing method and device, equipment and a storage medium. The method is applied to a software-as-a-service (SaaS) system, the SaaS system supports software services of at least two tenants and stores tenant data supporting the software services, and the method comprises the steps: acquiring and analyzing a data access statement for the tenant data; if a tenant identifier of the tenant to which the to-be-accessed data belongs is not analyzed in the data access statement, obtaining a spelling rule of the data access statement, adding the tenant identifier to the data access statement according to the spelling rule of the data access statement, and executing the data access statement; and if the tenant identifier of the tenant to which the to-be-accessed data belongs is analyzed in the data access statement, executing the data access statement. Through the technical scheme, data isolation can be achieved, and the data storage cost and the data isolation safety are both considered.
Owner:浙江大搜车软件技术有限公司
A network isolation device and method
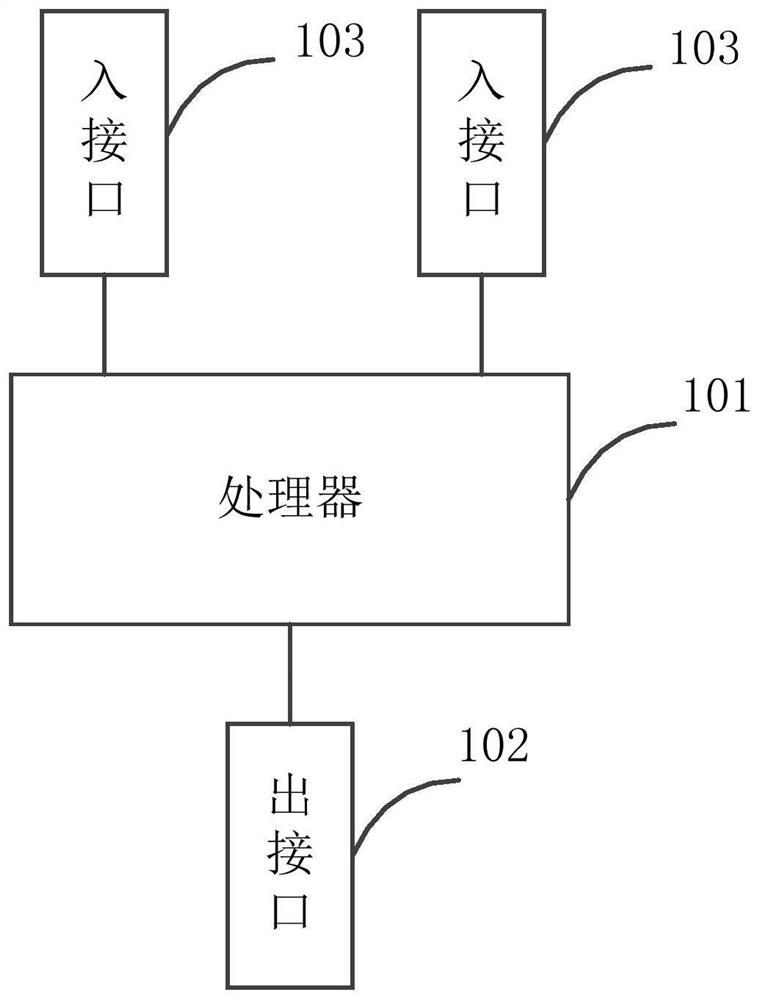
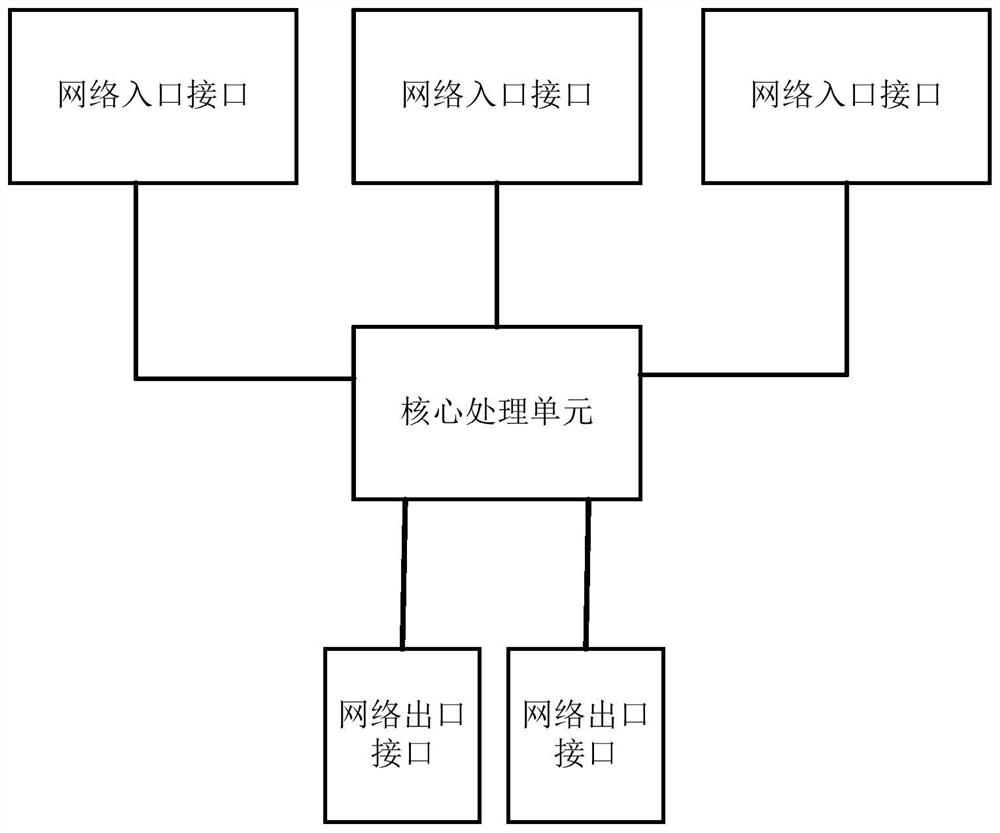
InactiveCN110708305BImprove securityAchieve physical isolationSecuring communicationData packDual network
The embodiment of the present invention provides a network isolation device and method, including a processor, an output interface, and multiple input interfaces; the network isolation device is connected to the collection device through the input interface, and the network isolation device is connected to the central device through the output interface; multiple The incoming interfaces are isolated from each other; the first incoming interface among the multiple incoming interfaces is used to receive data packets and send the data packets to the processor; the processor is used to detect whether the data packets match the preset filtering rules; if , the data packet is discarded; if not, the data packet is sent to the outbound interface; the outbound interface is used to send the data packet to the central device. It can be seen that the embodiment of the present invention realizes the data isolation of the redundant dual network at the physical level and the logical level, and improves network security.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
Power grid process switch and configuration method
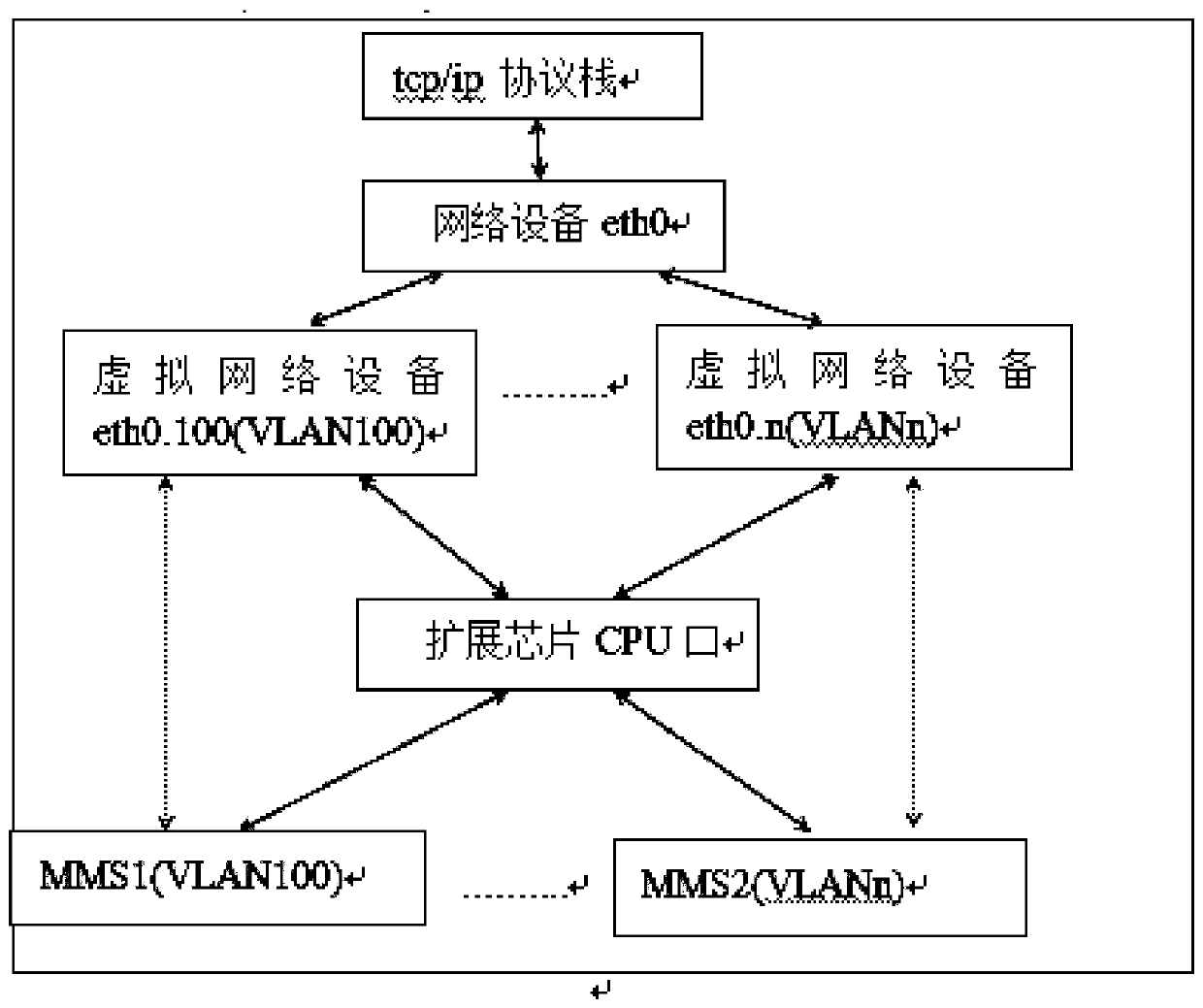
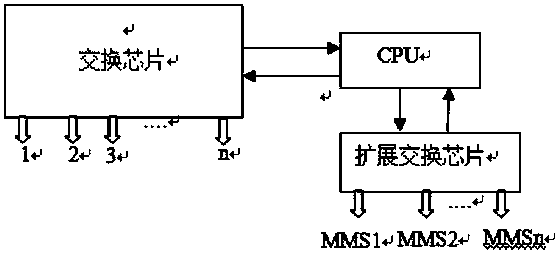
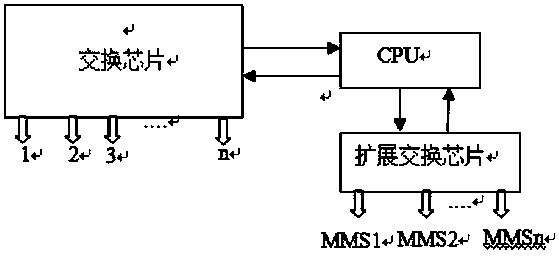
InactiveCN111131092AAchieve data isolationAchieving data network securityData switching networksPower gridEmbedded system
The invention provides a power grid process switch and a configuration method. The power grid process layer switch comprises a CPU, a switch chip and an extended switch chip, wherein the CPU is respectively connected with the switch chip and the extended switch chip, the switch chip is provided with a plurality of service ports, the extended switch chip is provided with a plurality of MMS ports, and the plurality of MMS ports achieve mutual isolation of data through a VLAN method. The beneficial effects are that the power grid switch needs a plurality of MMS ports, the isolation between the MMS ports and common service port of the switch is physically isolated, the plurality of MMS ports can be realized through the extended switch chip, and the data isolation between the MMS ports is realized by utilizing the VLAN technology, so that the power grid data network security is realized.
Owner:深圳市源拓光电技术有限公司
Data encryption method and device and data decryption method and device
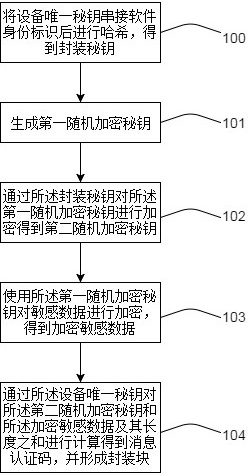
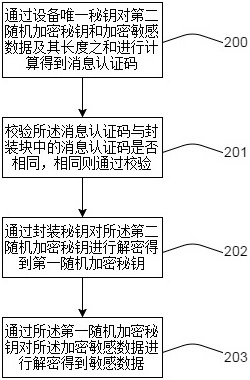
InactiveCN112214785AAchieve data isolationDoes not affect business processingDigital data protectionSoftware engineeringSecure state
The invention discloses a data encryption method and device, and a data decryption method and device, relates to the technical field of data security, and solves the technical problem that sensitive data between chips or software entities cannot be completely isolated.According to the technical scheme, a packaging key is obtained by combining an equipment unique key with a software identity; The equipment unique secret key is a unique identifier for identifying the equipment, and software entities with different software identities are identified by the software identities, so that data isolation among different chips, different CPUs, different security states on the same CPU, different privilege levels, different supported virtual machines and different processes can be achieved, and normal service processing is not influenced.
Owner:NANJING SEMIDRIVE TECH CO LTD
Data processing method, device and system, electronic equipment and storage medium
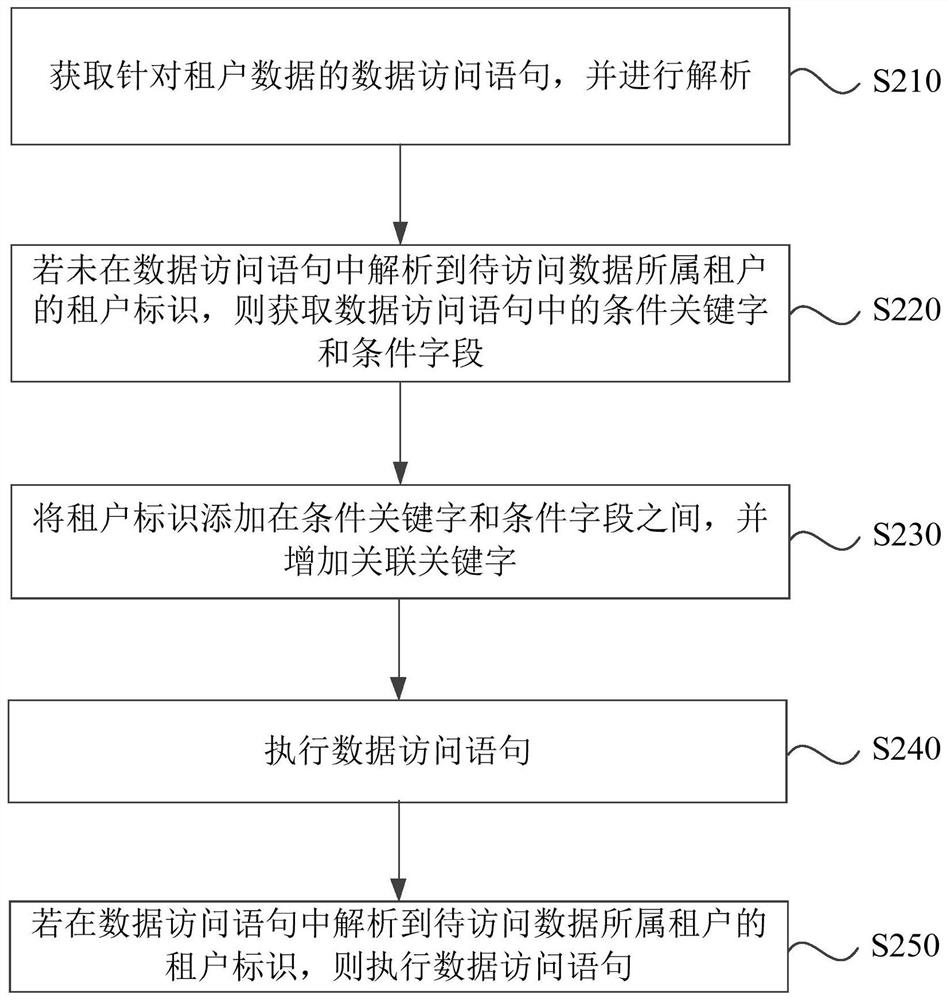
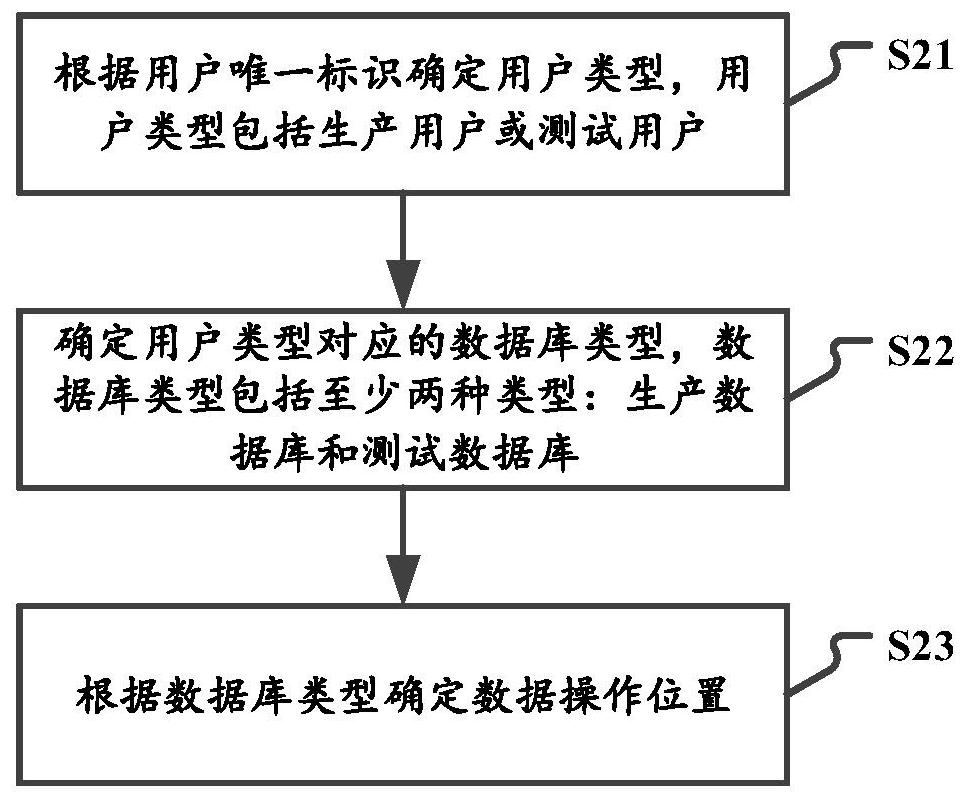
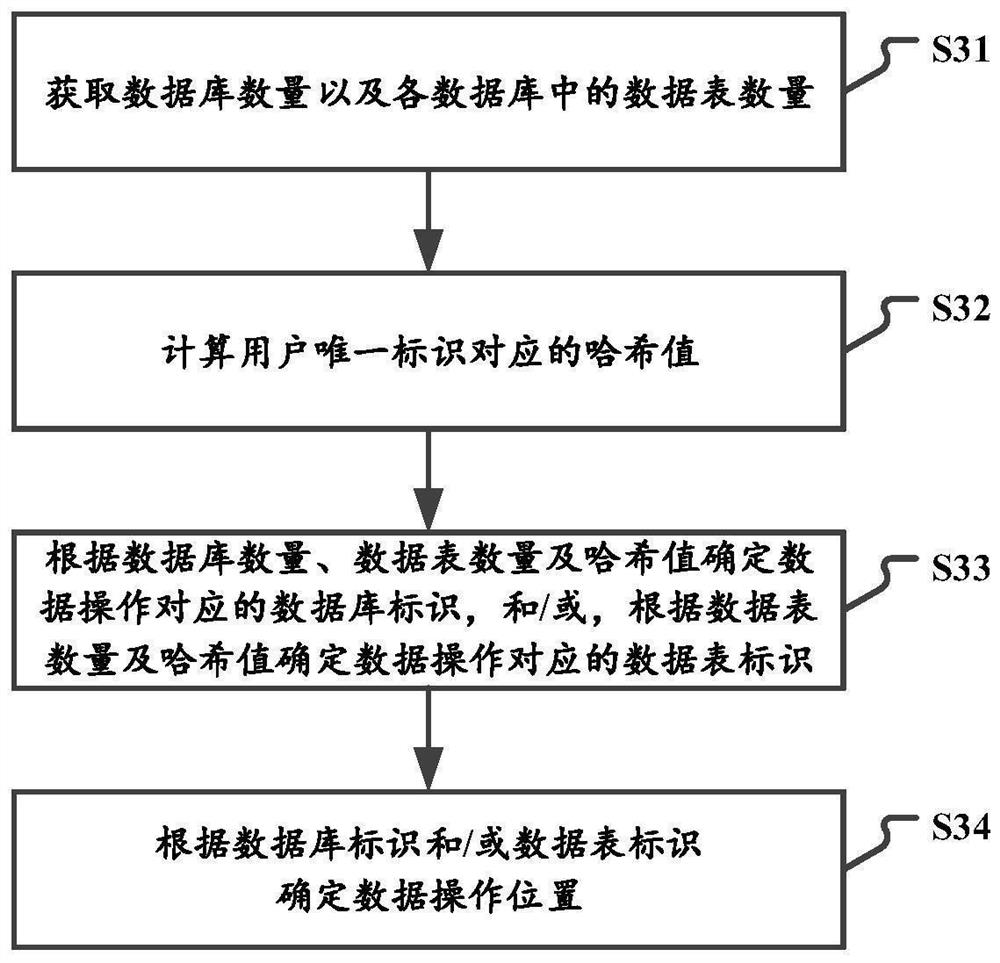
PendingCN114253964AAvoid mixingAvoid mixing together and interfering with each otherDatabase updatingSpecial data processing applicationsData operationsUnique identifier
The invention relates to a data processing method, device and system, electronic equipment and a storage medium. The method comprises the following steps: receiving a data operation request comprising a unique identifier of a user; determining a data operation position according to the user unique identifier; and executing a data operation corresponding to the data operation request at the data operation position. According to the technical scheme, the data operation requests of different users are routed to different database tables for data operation based on the user unique identifier, so that different users respectively perform data operation on different database tables, data isolation is realized, different types of data are prevented from being mixed together to influence each other, and the user experience is improved. Particularly, production data and test data are prevented from being mixed together, and the accuracy and integrity of various types of data are guaranteed.
Owner:JINGDONG TECH HLDG CO LTD
Data isolation method for main line and test run line and communication equipment used in the method
The invention provides a data isolation method for a main line and a test line in an urban rail transit line and a communication device used for the method, and relates to the technical field of communication. Wherein, the method includes: the TAU judges whether the destination IP address is the IP address of the ZC of the test line according to the destination IP address of the data sent by the VOBC to the ZC; If the IP address of the ZC of the test line, the TAU enables the GRE tunnel SC, closes the GRE tunnel ZX, and sends data to the ZC of the test line through the SC; if the destination IP address is not the ZC of the test line IP address, the TAU judges that the destination IP address belongs to the ZC network segment of the main line, and enables the ZX, closes the SC, and sends data to the ZC of the main line through the ZX , thereby realizing data isolation between the main line and the test line, wherein the urban rail transit line includes an on-board controller VOBC, a zone controller ZC, and a communication device TAU. Through the present invention, it is possible to prevent the operation of the equipment on the test line from adversely affecting the operation of the ATC network equipment on the main line.
Owner:TIANJIN TRAFFIC CONTROL TECH CO LTD
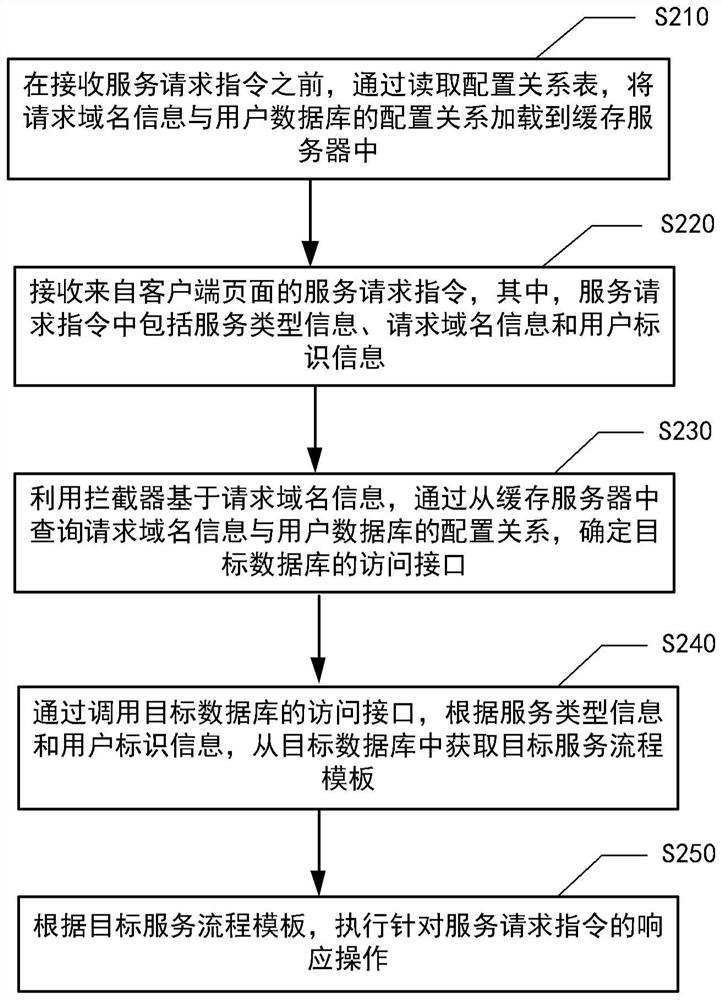
Service request response method and device, equipment and medium
ActiveCN114844950AQuick response to service requestsQuick responseDatabase management systemsDigital data protectionDomain nameCache server
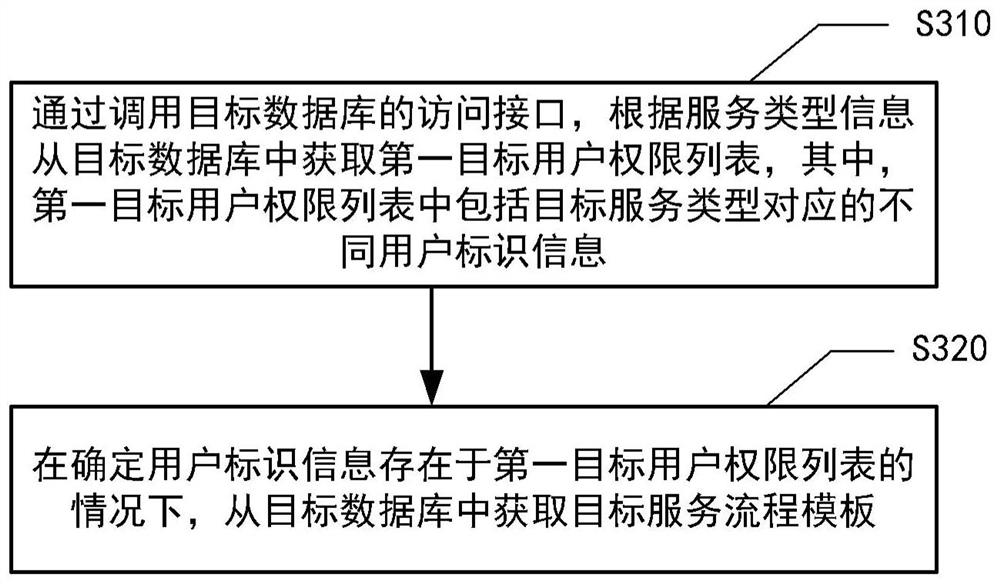
The invention provides a service request response method and device, equipment and a medium, and can be applied to the technical field of computers and the technical field of finance. The service request response method comprises the following steps: before receiving a service request instruction, loading a configuration relation between request domain name information and a user database into a cache server by reading a configuration relation table; a service request instruction from the client page is received, and the service request instruction comprises service type information, request domain name information and user identification information; determining an access interface of a target database by querying a configuration relationship between request domain name information and a user database from the cache server based on the request domain name information by using an interceptor; obtaining a target service process template from the target database according to the service type information and the user identification information by calling an access interface of the target database; and executing a response operation for the service request instruction according to the target service process template.
Owner:CCB FINTECH CO LTD
A multi-tenant data query method, system and shared platform server
ActiveCN106202309BAchieve data isolationWeb data indexingStructured data retrievalComputer terminalData query
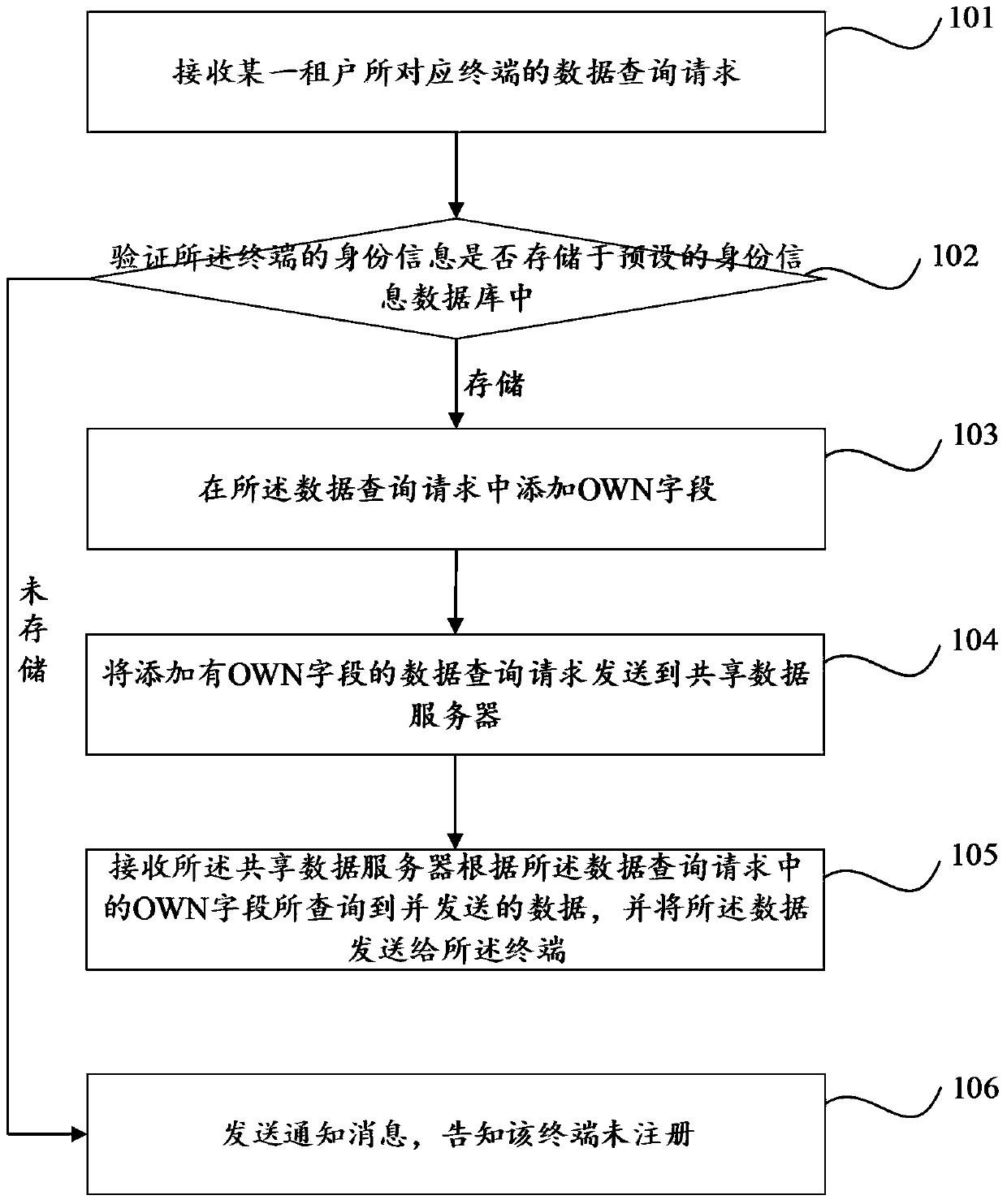
The invention discloses a multi-tenant data query method comprising the following steps of receiving a data query request of a terminal corresponding to a certain tenant, wherein the data query request carries identity information of the terminal; verifying whether the identity information of the terminal is stored in a preset identity information database; when that the identity information of the terminal is stored in the identity information database is verified, adding an OWN field to the data query request, wherein identity information of the terminal is marked in the OWN field; sending the data query request added with the OWN field to the sharing data server; and receiving data that is queried by the sharing data server according to the OWN field in the data query request and sent by the same, and sending the data to the terminal. According to the method provided by the invention, data isolation of different registered enterprises can be achieved without modifying an original system program.
Owner:上海火炬电子科技集团有限公司 +1
File access control method, file encryption method and computing device
ActiveCN113051598BControl accessAchieve data isolationDigital data protectionDirectoryAccess control
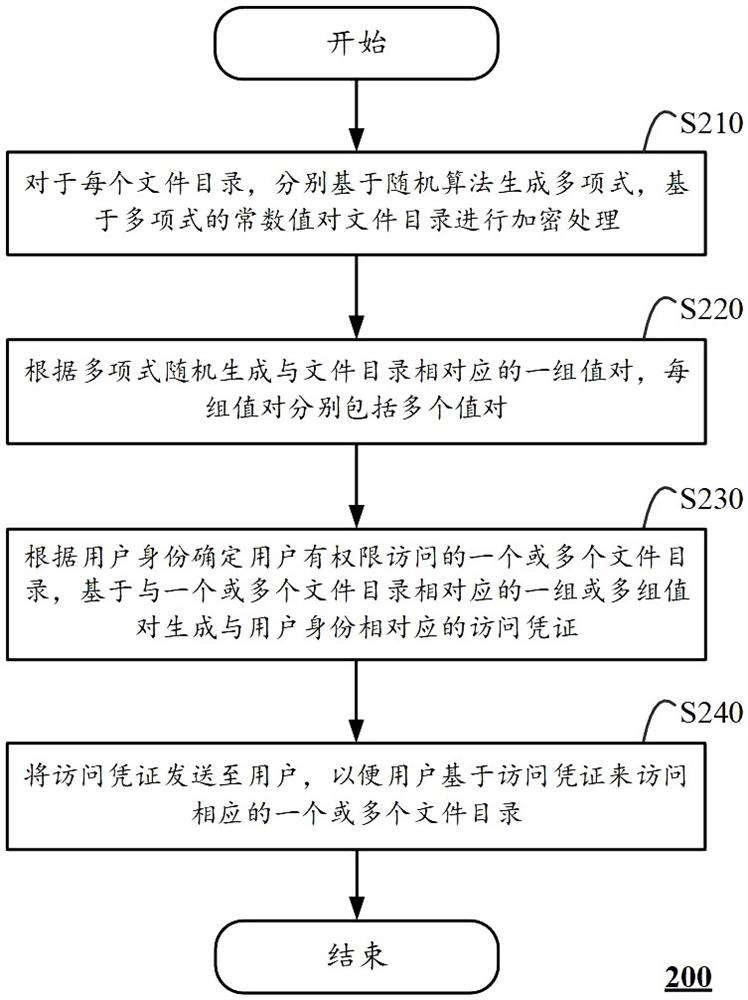
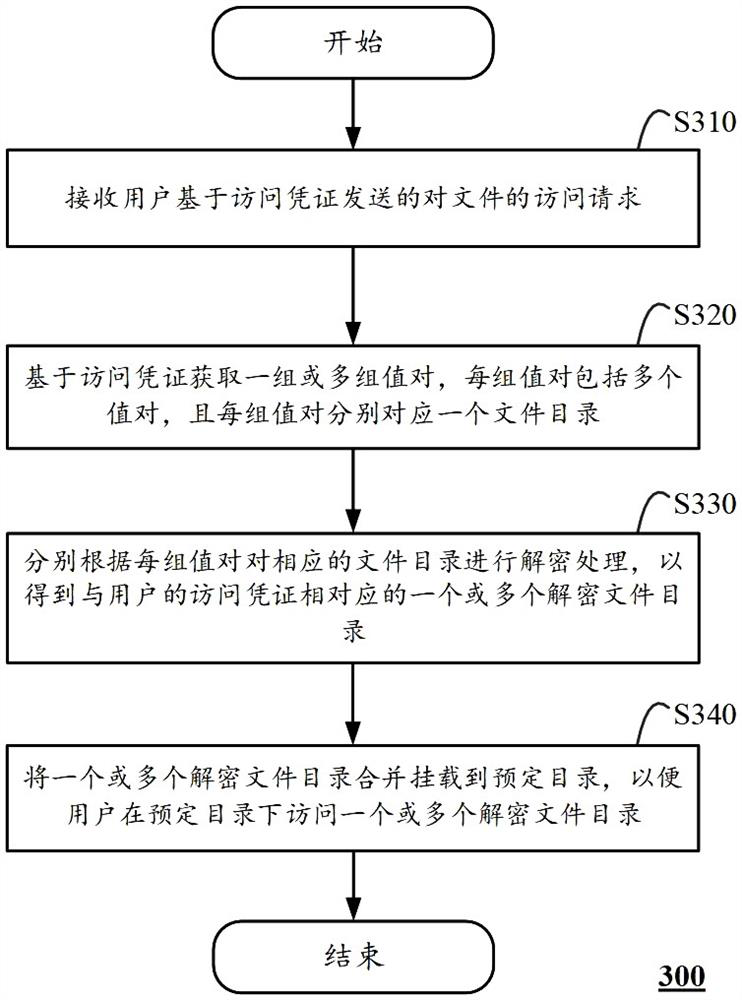
The invention discloses a file access control method, which is executed in a computing device, comprising the steps of: receiving a file access request sent by a user based on an access credential; obtaining one or more sets of value pairs based on the access credential, each set of value The pair includes multiple value pairs, and each set of value pairs corresponds to a file directory; respectively, according to each set of value pairs, the corresponding file directory is decrypted to obtain one or more decrypted file directories corresponding to the user's access credentials ; and merging and mounting the one or more decrypted file directories to a predetermined directory, so that the user can access the one or more decrypted file directories under the predetermined directory. The invention also discloses a corresponding file encryption method and computing equipment. According to the solution of the present invention, it is possible to control the access rights of users with different identities to the file directory, and the user experience is better.
Owner:UNIONTECH SOFTWARE TECH CO LTD
USB data isolation safety equipment
InactiveCN111355094AEnsure data securityAchieve data isolationCoupling device detailsInternal/peripheral component protectionData transmissionUSB
The invention discloses USB data isolation safety equipment, and relates to the technical field of data transmission equipment. An output port is installed in a front end of an equipment body; an input port is formed in a rear end of the equipment body; a first base plate is arranged on an inner bottom surface of the output port; a first output electrode and a second output electrode are mounted on the first base plate; a second base plate is arranged on an inner bottom surface of the input port; a first input electrode and a second input electrode are mounted on the second base plate; and theinput port is connected with a USB interface of a data line. According to the equipment, the output port is connected with a USB interface of the power supply equipment, the input port is connected with the USB interface of the data line, power supply pins are arranged in the output port and the input port for charging, data pins are cut such that data isolation is realized, and the data securityof a mobile phone of a user is ensured.
Owner:北京华安普特网络科技有限公司
Application calling method, device and mobile terminal
ActiveCN106874746BImprove experienceSave spaceInternal/peripheral component protectionSoftware engineeringApplication procedure
The invention provides a method and device for invoking an application program. The method comprises: receiving an invoking instruction to invoke a second application by a first application; determining whether the second application is installed in a current system normal mode with an administrator logged in; if yes, running the second application in the system normal mode according to the invoking instruction; if no, continuing to determine whether the second application is installed in a system protection mode with a normal user logged in; switching the system from the current system normal mode to the system protection mode when the second application is installed in the system protection mode; and running the second application in the system protection mode according to the invoking instruction, wherein a safe space providing a running resource for running of a predetermined application is configured in the system protection mode, and the safe space is unavailable in the system normal mode. The above method and device avoid repeated installation of an application in multiple modes, thereby saving the system space and enhancing the user experience. Besides, a mobile terminal is also provided.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
A browser-based business system dynamic isolation protection method and system
The present invention relates to a browser-based business system dynamic isolation protection method and system. The present invention takes business system intelligent identification as the core, real-time and dynamic identification of protected business systems, and documents of protected business systems and protected business systems And the binding of users currently accessing the protected business system, so that the protected business system is isolated from other business systems and the external network, and the current user's documents are isolated from other users. When users access the protected business system through a browser, they do not need to actively identify the access object, do not need to manually switch, and do not need to resort to a special secure browser or other hardware devices, and can directly use the business system. While using the protected business system, users can continue to use the extranet and other business systems. At the same time, the data of the protected business system is isolated and protected to eliminate the risk of enterprise data leakage.
Owner:CHINA NAT SOFTWARE & SERVICE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com