Data encryption method and device and data decryption method and device
A data encryption and data decryption technology, applied in the field of data security, can solve problems such as non-sharing, and achieve the effect of data isolation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The technical solution of the present disclosure will be described in detail below in conjunction with the accompanying drawings. In the description of the present disclosure, it should be understood that the terms "first", "second", and "third" are used for descriptive purposes only, and cannot be interpreted as indicating or implying relative importance or implicitly indicating the indicated The number of technical characteristics is only used to distinguish different components.
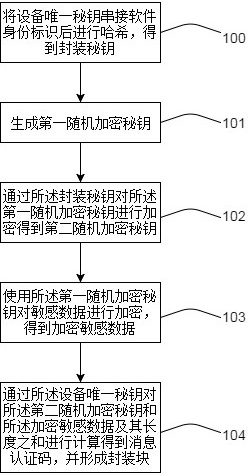
[0038] figure 1 It is a flow chart of the disclosed encryption method, such as figure 1 As shown, 100: The device unique key is concatenated with the software identity and then hashed to obtain the encapsulation key. The encapsulation key is the hash value obtained by concatenating the unique key of the device and the software identity and hashing it, which is not less than 256 bits.
[0039] The device unique key is used to uniquely identify the device. For example, each chip has its ow...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com