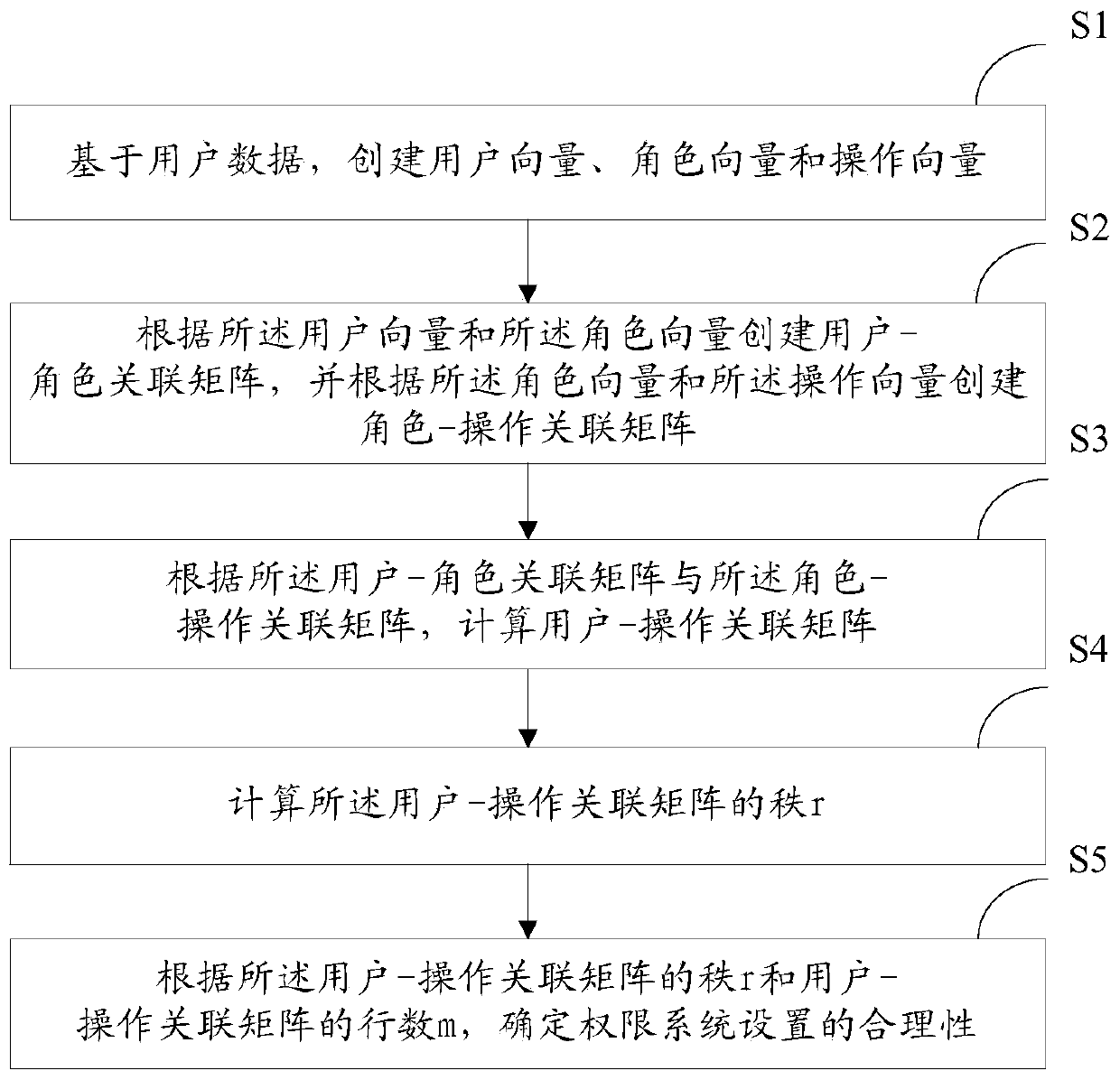
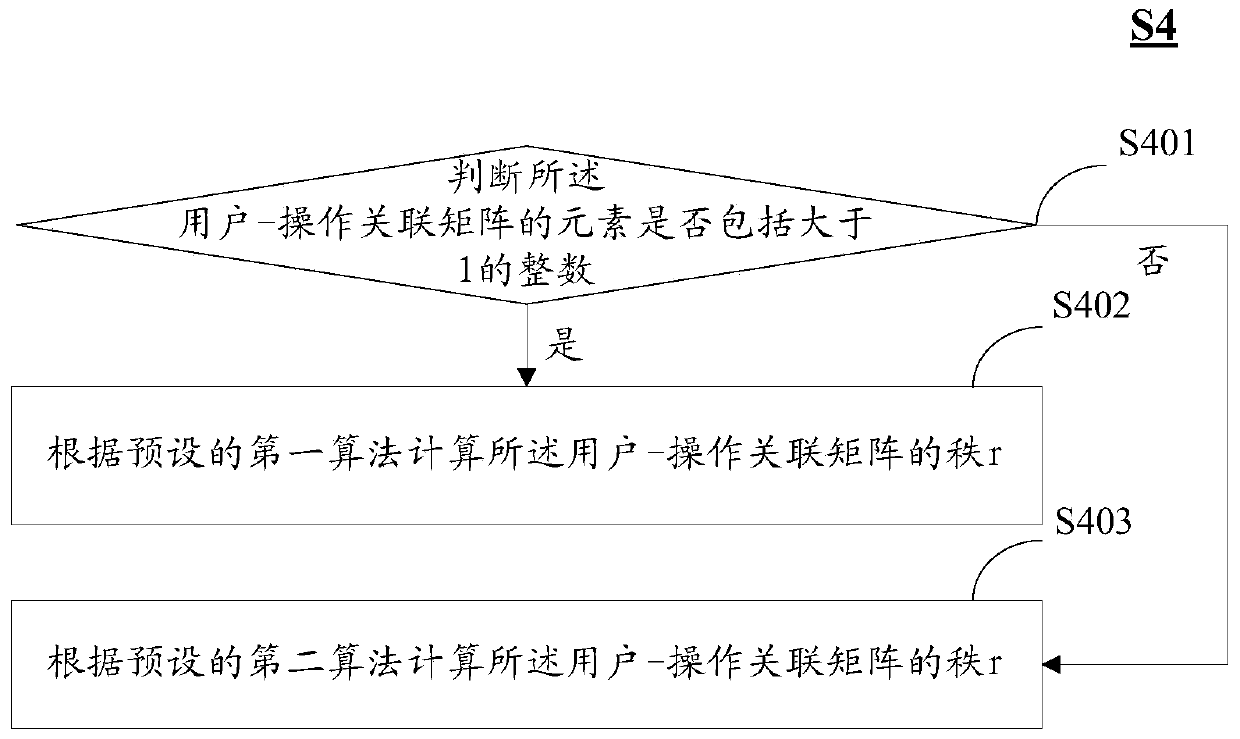
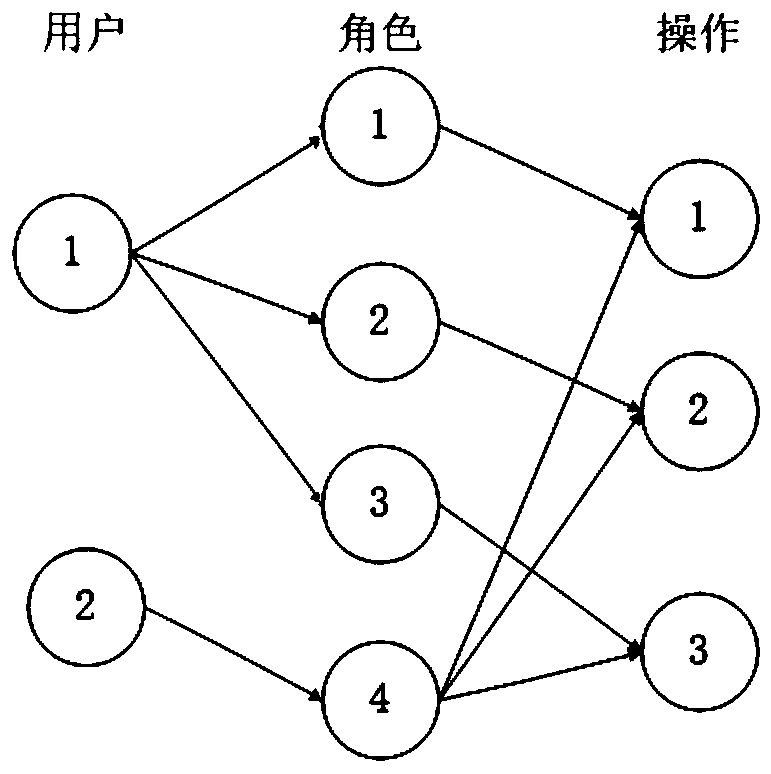
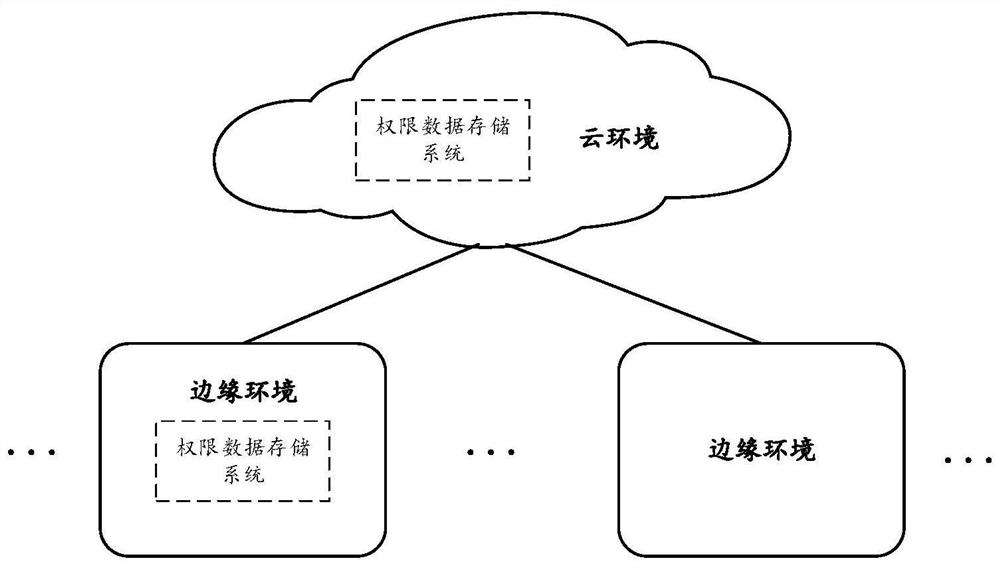
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
76 results about "Permission system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The permission system is the legislated methods of regulating activities that require permission or accreditation under Australian and Queensland government acts, regulations and the Zoning Plan. The Permission System Policy outlines the approach to managing the permission system within the Marine Parks.
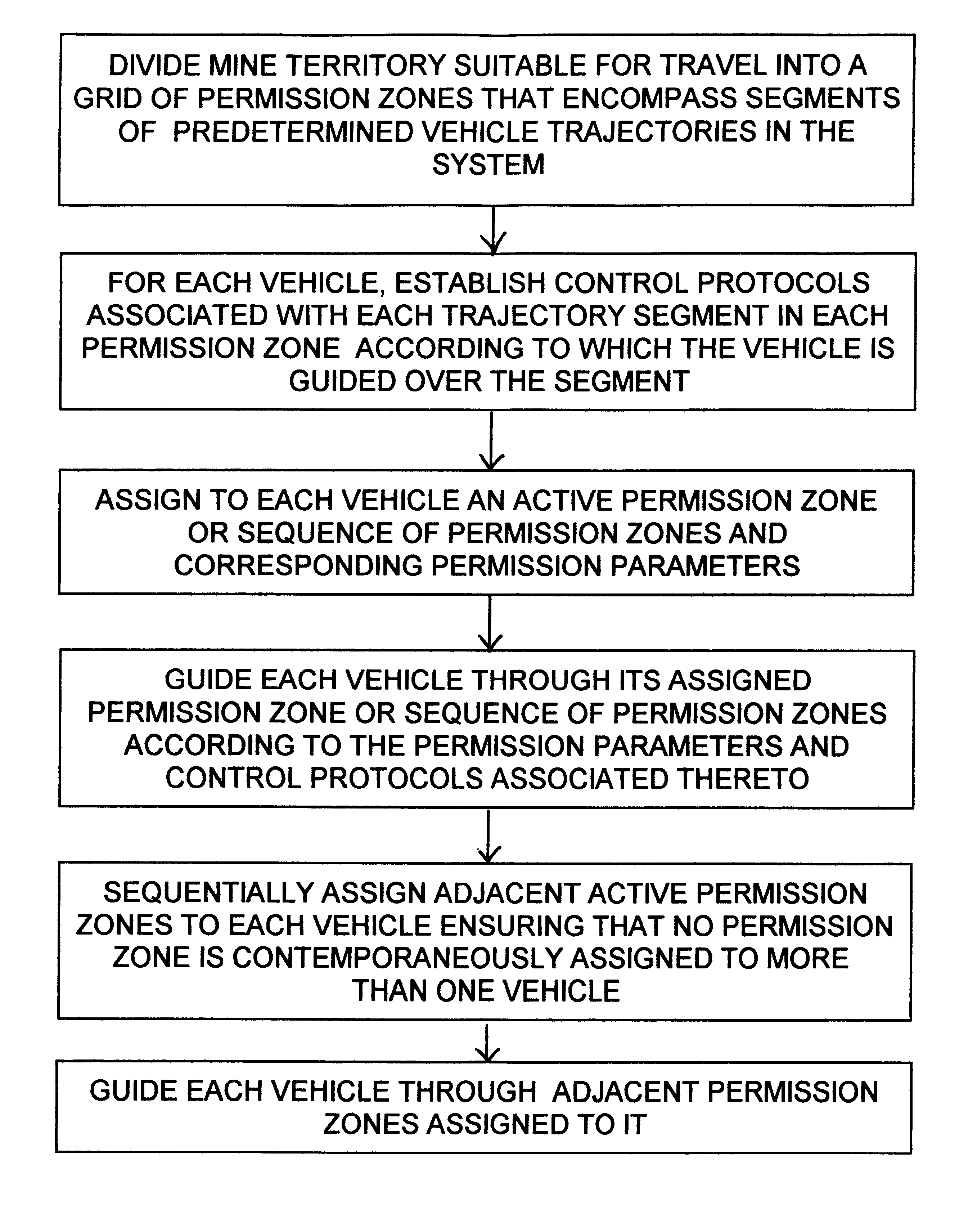
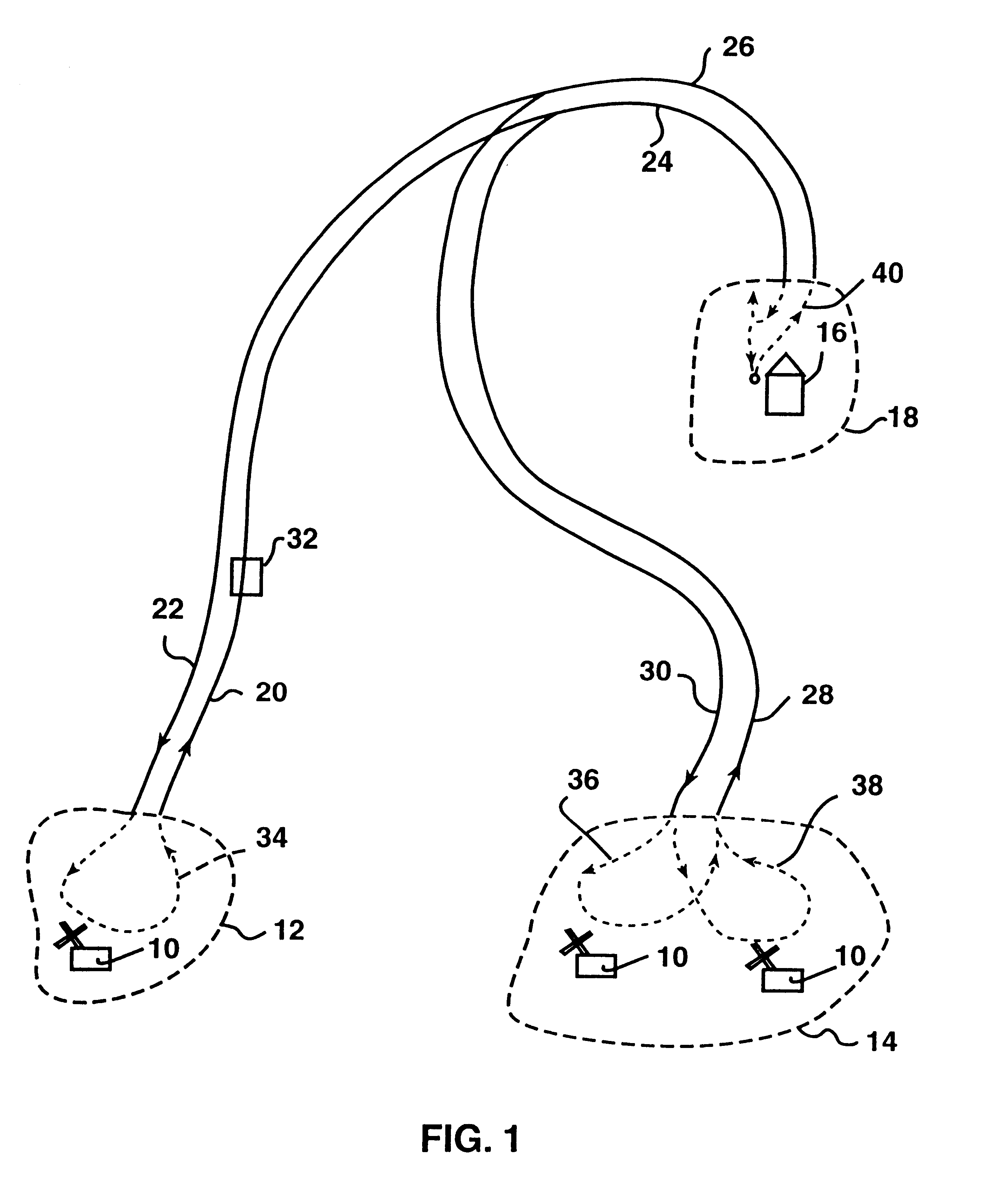
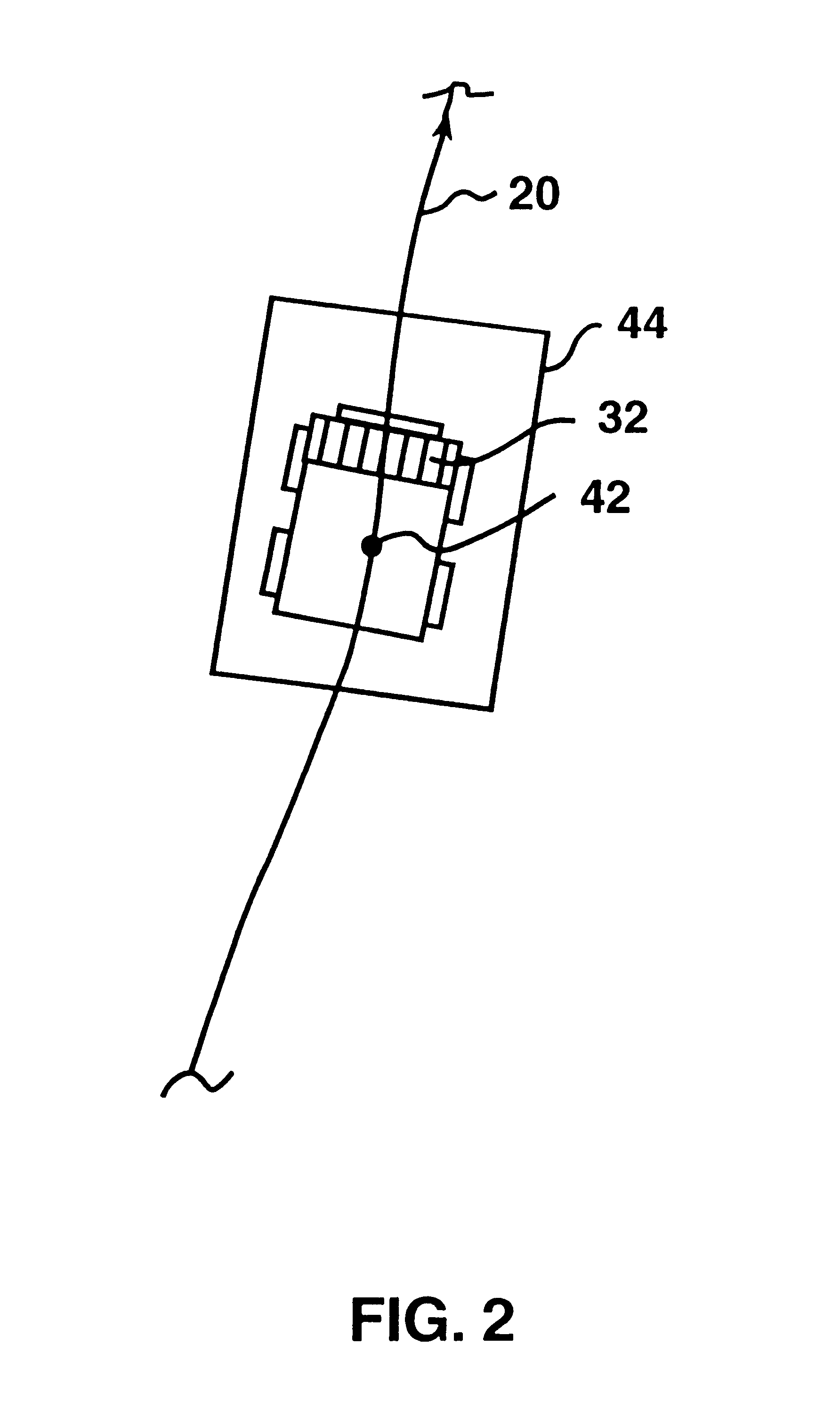
Permission system for controlling interaction between autonomous vehicles in mining operation
InactiveUS6799100B2Analogue computers for vehiclesAnalogue computers for trafficGuidance systemControl system
A supervisory safety-control system is implemented by dividing a mine's territory into zones of free operation ("permission zones") wherein a vehicle is allowed to move according to predetermined permission parameters but unhindered by other system constraints. Traffic of autonomous vehicles in each permission zone is controlled by the supervisory system in conjunction with and in addition to conventional safety constraints associated with the guidance system that effects the vehicle's tracking of predetermined trajectories. Permission zones are assigned and activated using criteria that ensure the vehicle will remain entirely within active zones so long as the vehicle acts within such predetermined permission parameters. Each permission zone is also associated with a maximum velocity profile that overrides guidance-system safety controls, if necessary, and ensures stoppage of the vehicle at the end of the permission zone.
Owner:MODULAR MINING SYSTEMS
Security in virtualized computer programs
ActiveUS20130086299A1Binary to binaryMemory architecture accessing/allocationOperational systemPermission system
In an embodiment, a data processing method comprises implementing a memory event interface to a hypercall interface of a hypervisor or virtual machine operating system to intercept page faults associated with writing pages of memory that contain a computer program; receiving a page fault resulting from a guest domain attempting to write a memory page that is marked as not executable in a memory page permissions system; determining a first set of memory page permissions for the memory page that are maintained by the hypervisor or virtual machine operating system; determining a second set of memory page permissions for the memory page that are maintained independent of the hypervisor or virtual machine operating system; determining a particular memory page permission for the memory page based on the first set and the second set; processing the page fault based on the particular memory page permission, including performing at least one security function associated with regulating access of the guest domain to the memory page.
Owner:CISCO TECH INC
Multi-hierarchy user permission management method
InactiveCN106713340ASimplify the authorization processReduce complexityTransmissionPermission systemData operations
The invention discloses a multi-hierarchy user permission management method. All hierarchical relationships are centralized on organizations, superior-subordinate relationships of users, characters and permissions are transferred by the organizations to which the users, the characters and the permissions belong, and complexity brought to permission system design by multiple superior-subordinate relationships is greatly reduced. In the multi-hierarchy user permission management method disclosed by the invention, a data range is only associated with the organizations; after the users are authorized by "organizations-characters", when operation permissions are limited by the "characters", data operation ranges of the users are also limited by the "organizations", so that service logics of checking legalities of the data ranges are greatly simplified. Accounts, the organizations, the characters and the permissions have many-to-many relationships, and in an actual service, very high operation flexibility can be brought in. The multi-hierarchy user permission management method disclosed by the invention is designed on the basis of universality, and can be completely reused by modular design for various management systems of multi-hierarchy organizations, such as the education industry, government departments, group companies and the like. Based on the points above, the multi-hierarchy user permission management method disclosed by the invention can bring the effects of greatly simplifying the permission system service logic of the multi-hierarchy organizations and greatly reducing range checking logics, so that product quality can be improved, and development and maintenance cost is greatly reduced.
Owner:深圳开维信息技术股份有限公司
Permissions configuration management system
InactiveCN102393889ASimple configurationAchieve maintenanceDigital data authenticationSpecial data processing applicationsExtensibilityPermission system
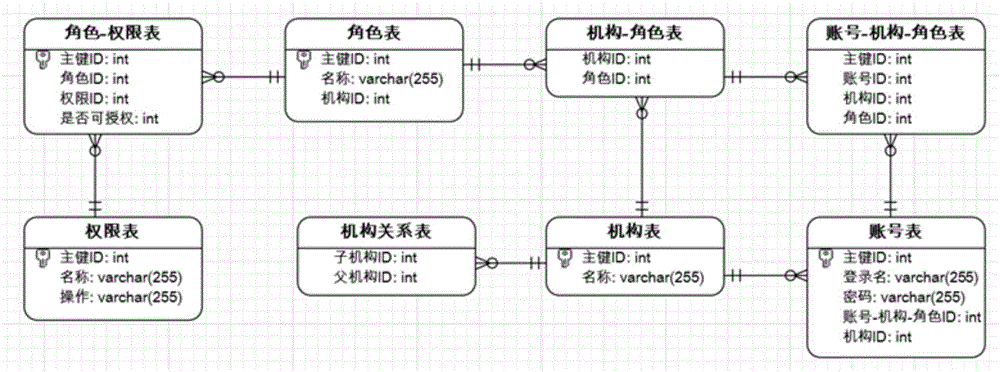
The invention relates to a permissions configuration management system, which belongs to the technical field of internet information technology. The system comprises a permissions definition module, a role definition module, a user definition module, a role and permissions relation maintaining module, a user and role relation maintaining module and an external interface module; the permissions definition module and the role definition module are connected through the role and permissions relation module; the data in the permissions definition module is stored in XML files; the data in the role definition module is stored in database; the data in the role and the permissions relation module is stored in the database; the role definition module and the user definition module are connected through the user and the role relation module; the data in the user definition module and the user and the role relation module are all stored in the database; and the external interface of the permissions system is connected with the database for transferring data of the database. The permissions configuration management system has a function of dynamically configuring permissions and is featured with simple configuration, strong extensibility and strong transferability.
Owner:BEIJING ITOWNET DIGITAL TECH
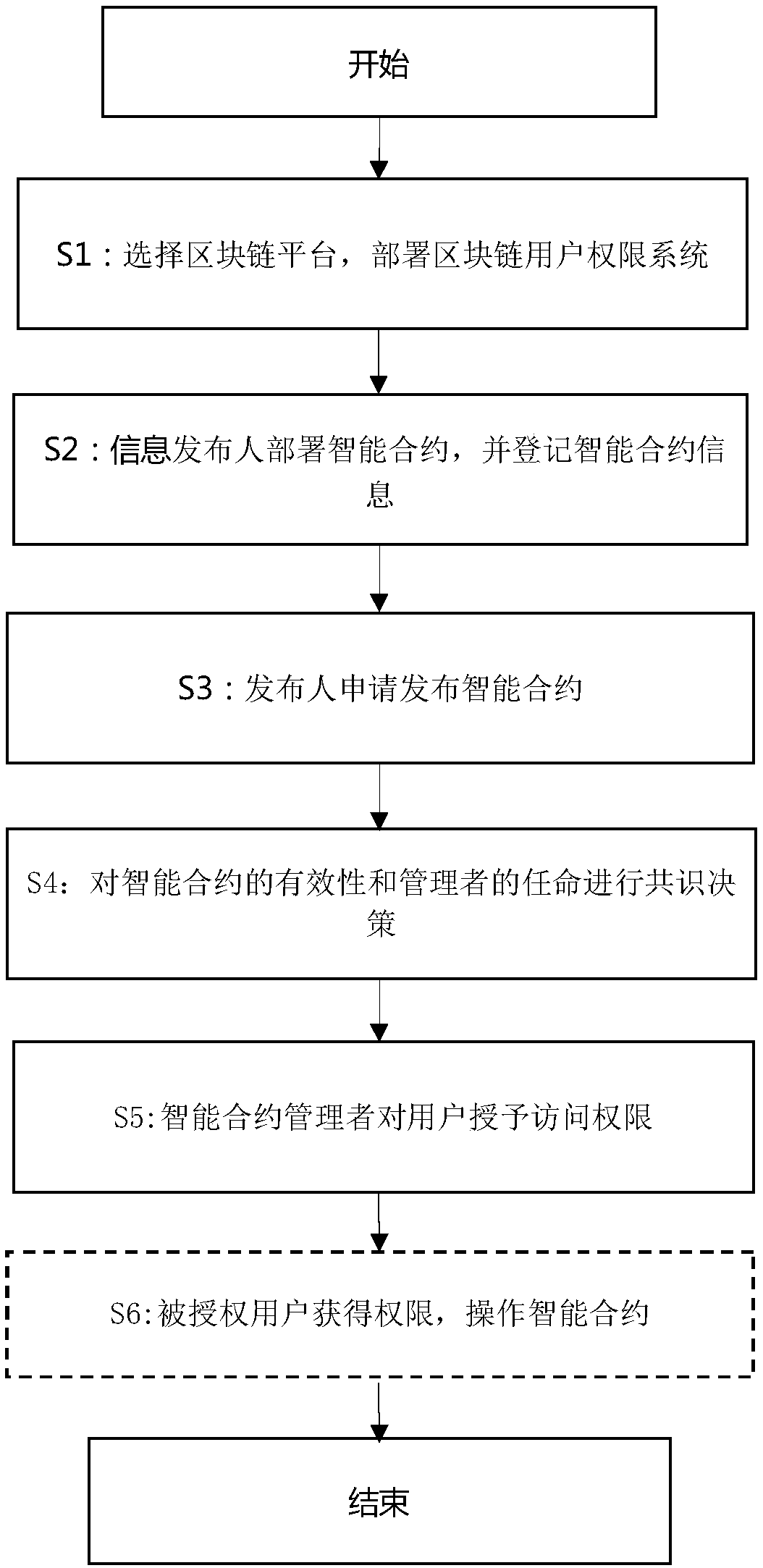
Blockchain user permission system and implementation method
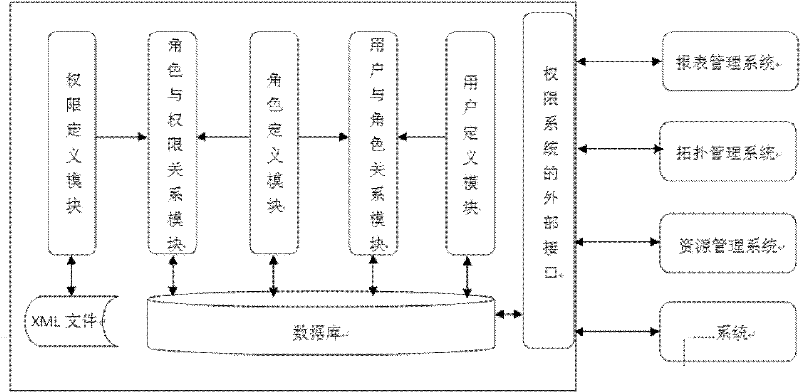
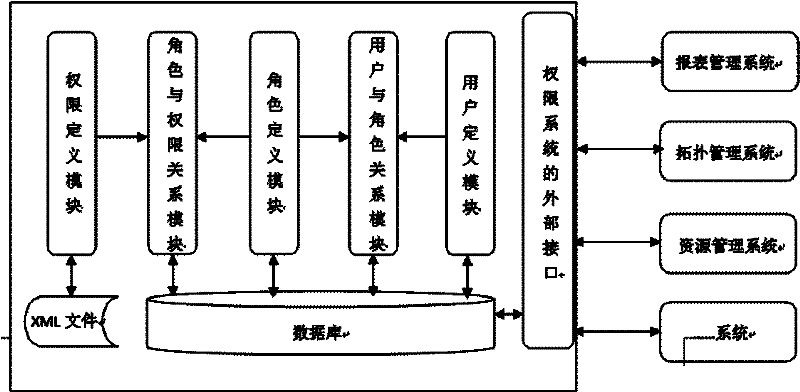
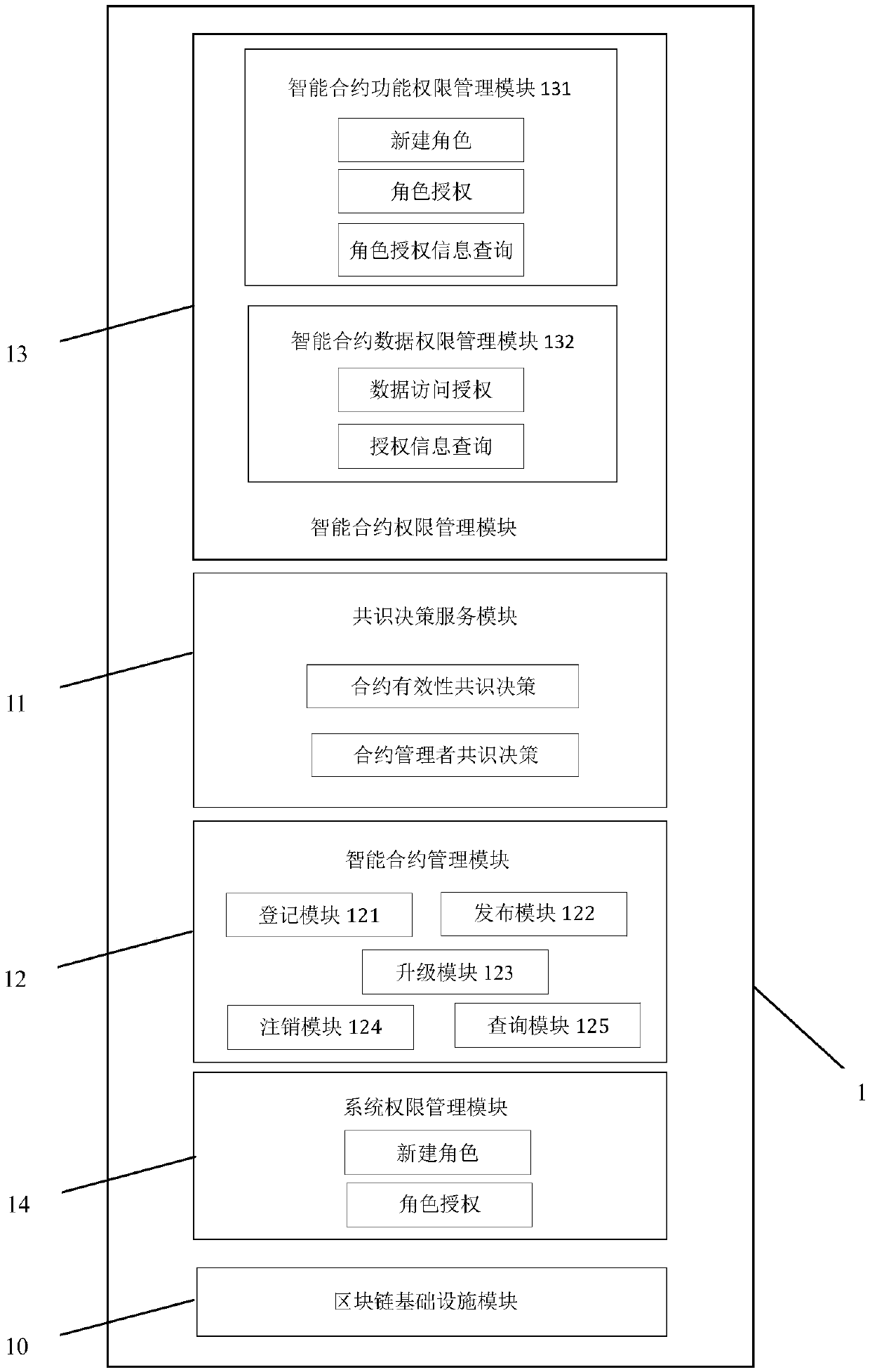
In order to solve the problem that in the prior art, in enterprise-level application based on a block chain technology, how to build blockchain user access authority management meeting industry rulesand standard data of enterprise-level application requirements, the invention provides a blockchain user permission system based on different blockchain platforms and a permission implementation method in the system. The authority system is composed of a block chain infrastructure module, a consensus decision service module, an intelligent contract management module, an intelligent contract authority management module and a system authority management module. The system built by the modules determines the validity of the smart contract by using a consensus mechanism, selects a new smart contract manager, manages the access permission of the smart contract by judging the validity of the contract and the validity of the contract manager at the same time, and finally achieves the purposes ofdecentralization and high security of the access permission management of the blockchain user.
Owner:北京轻信科技有限公司
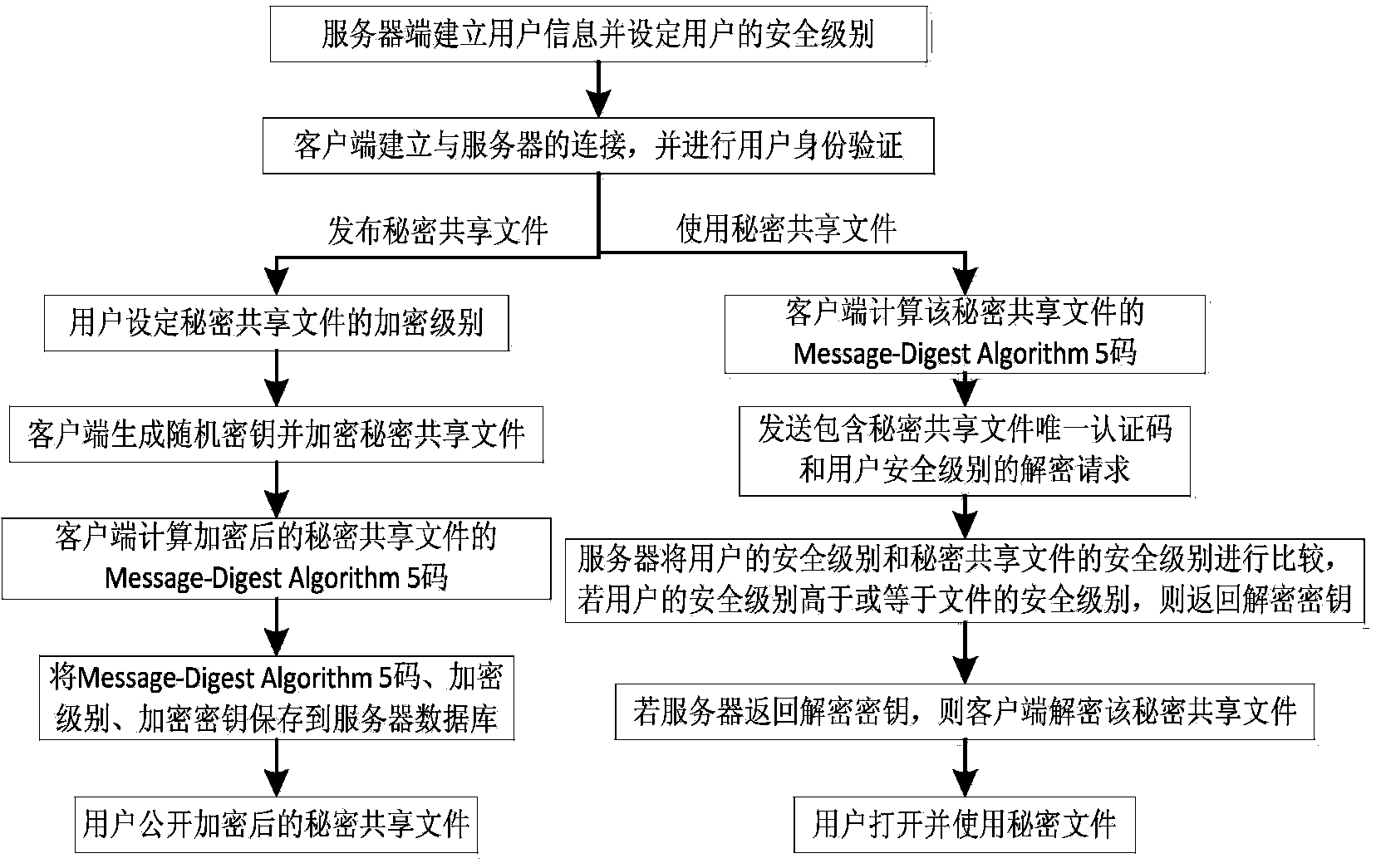
File sharing method based on encryption and permission system
InactiveCN103929434AEasy maintenanceImplement permission controlTransmissionComputer hardwareSecret share
The invention discloses a file sharing method based on an encryption and permission system. The file sharing method comprises the implementation steps that (1) a server establishes user information and sets the security level of a user; (2) the user logs in and carries out authentication; (3) the user sets the security level of a secret shared file, carries out encryption through a random secret key, stores the unique authentication code, the security level and the encryption secret key of the encrypted secret shared file on the server, and sends the encrypted secret shared file to a network; (4) when the secret shared file is used, a client sends a decryption request including the unique authentication code of the secret shared file and the security level of the user, if the security level of the user is higher than or the same as the security level of the secret shared file, the client can receive a decryption secret key fed back by the server, the client decrypts the secret shared file through the decryption secret key, and opens the secret shared file, and if the security level of the user is lower than the security level of the secret shared file, rejection information is fed back. The file sharing method based on the encryption and permission system has the advantages of being high in safety, convenient to use and capable of being used for sharing of secret files inside a unit.
Owner:XIDIAN UNIV
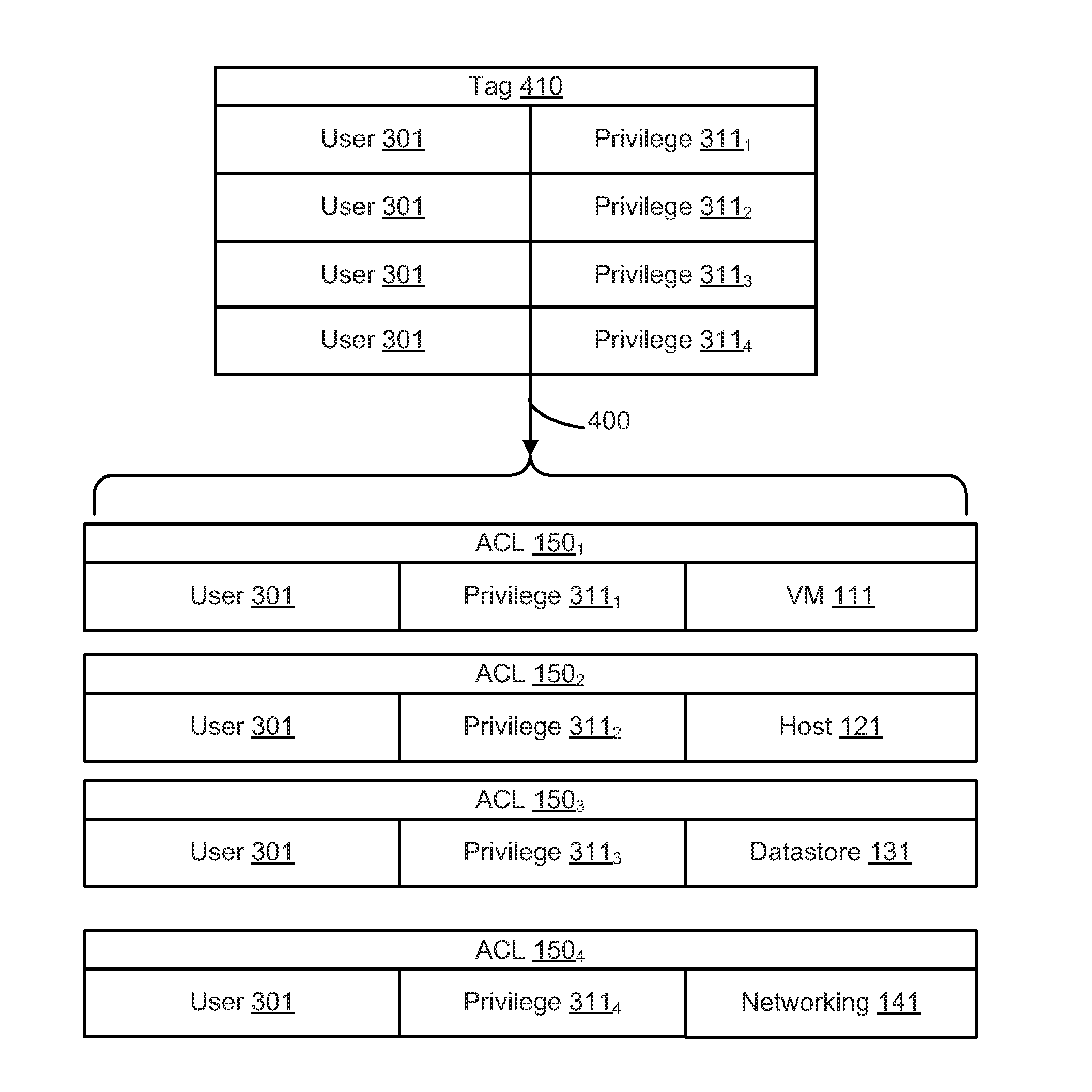
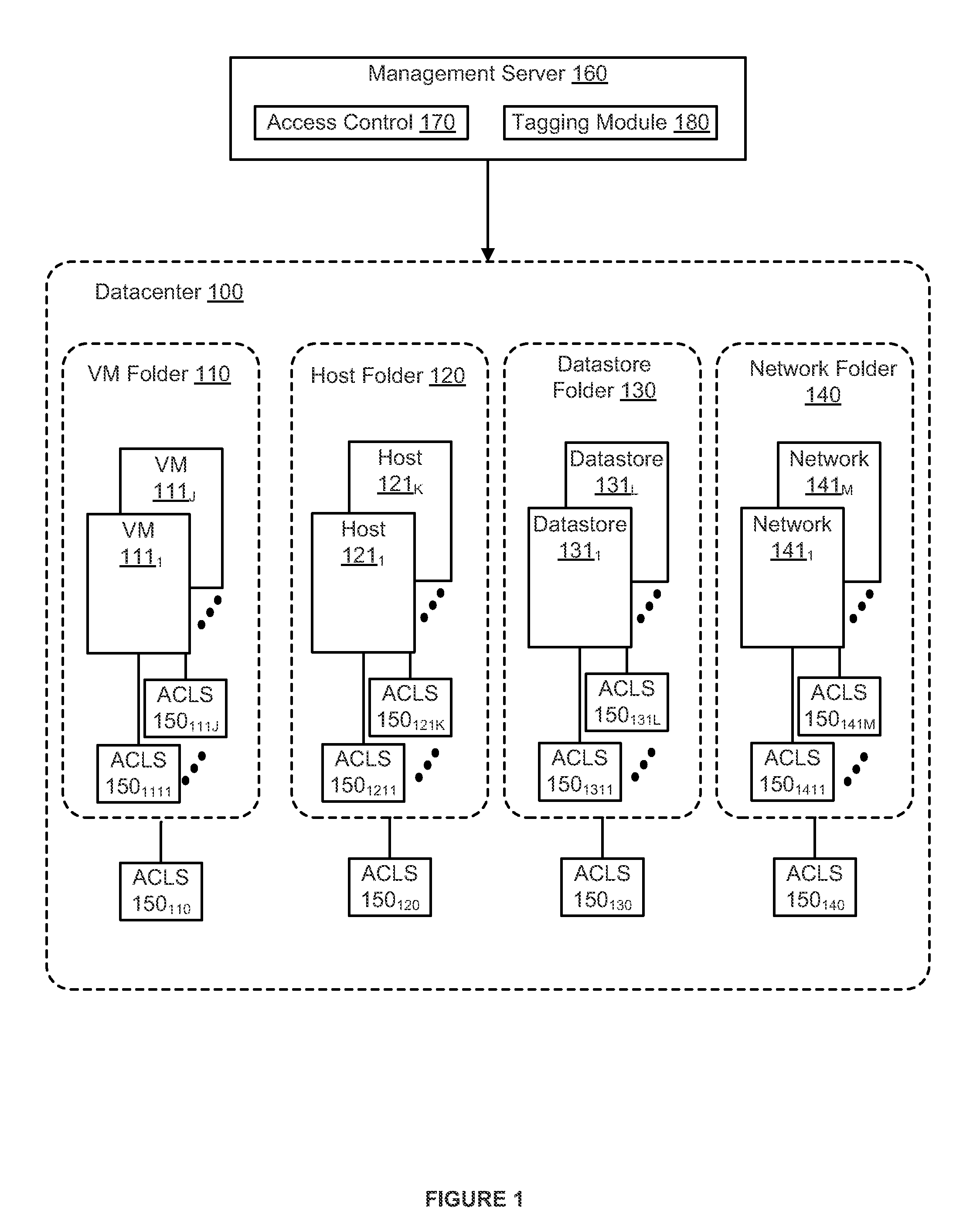
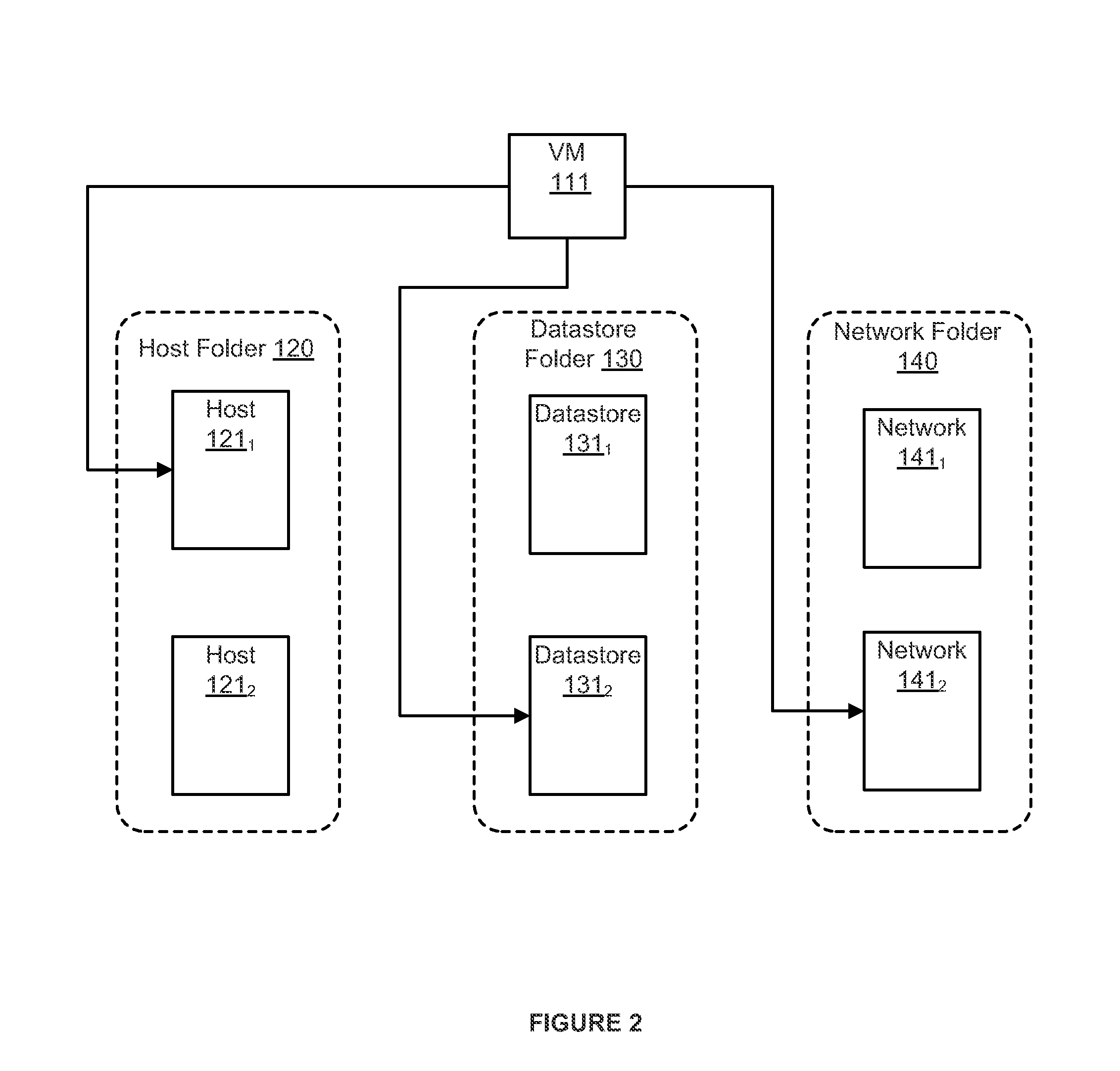
Tag based permission system and method for virtualized environments
ActiveUS20150101042A1Special service provision for substationDigital data processing detailsVirtualizationPermission system
A virtualized computing system includes a plurality of inventory objects and an access control subsystem that manages permissions to perform actions on the inventory objects using corresponding access control labels of the inventory objects. Permissions are managed by detecting a change in an association of a tag with an inventory object, where the tag defines one or more users and one or more privileges. In response to the detecting, an access control label of the inventory object is updated based on the users and privileges that are defined by the tag.
Owner:VMWARE INC
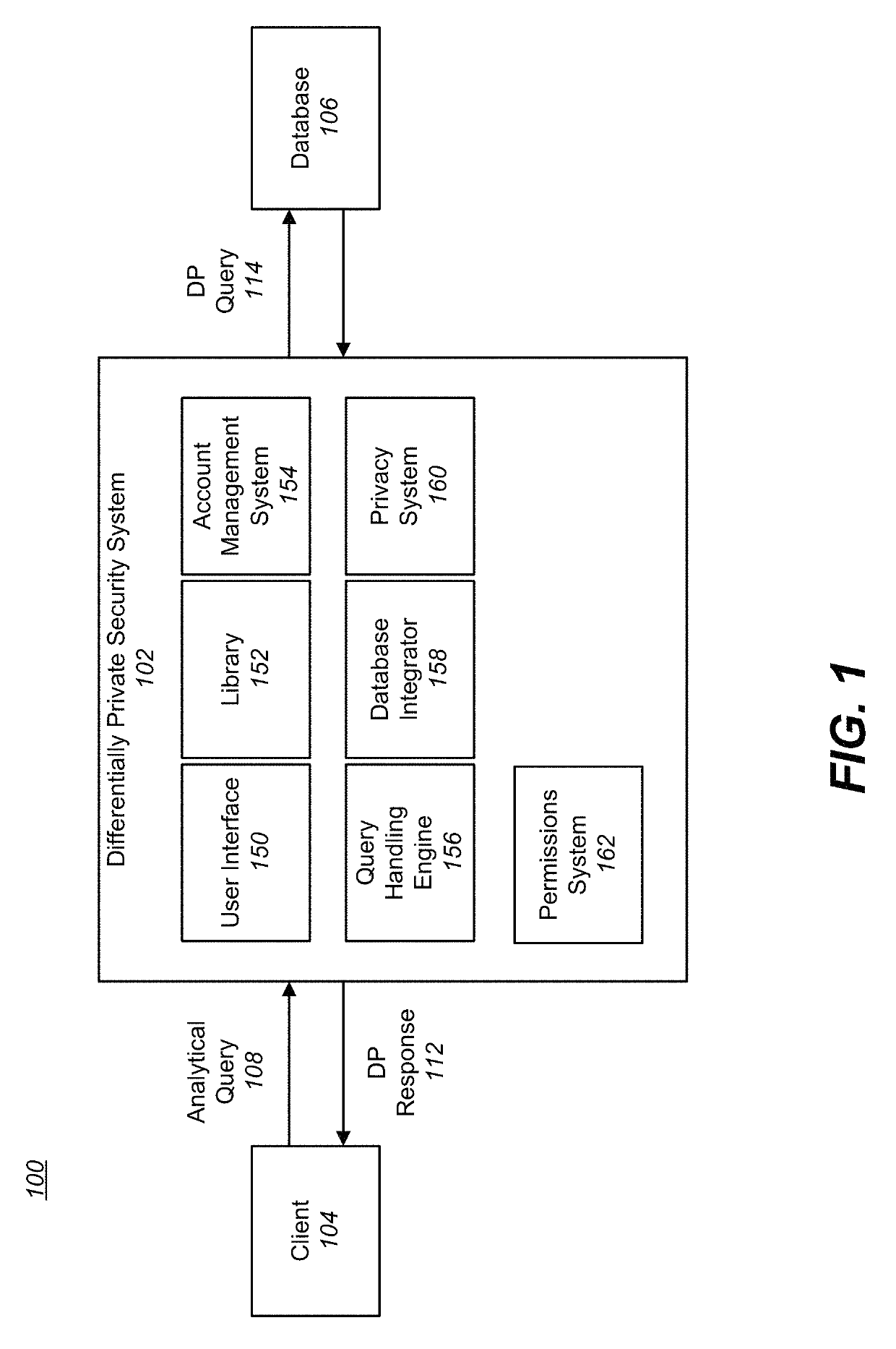
Differentially private database permissions system
ActiveUS10430605B1Digital data information retrievalDigital data protectionProgramming languageData set
A differentially private system receives a request from a client to perform a query on data stored in a database. The differentially private system establishes a set of permissions of the client with respect to the data in the database. The differentially private system deconstructs the query into query components. The query components include at least one relation that identifies a dataset in the database and at least one expressions specifying an operation to be performed in the identified dataset. The differentially private system identifies permissions necessary to perform the specified operation on the identified dataset. The differentially private system determines whether the established permissions grants of the client include the identified permissions necessary to perform the specified operation on the identified dataset. The differentially private system selectively executes the query responsive to the determination.
Owner:SNOWFLAKE INC
Method for performing permission configuration on permission resources, permission system and storage medium
ActiveCN110363012ARealize unified configurationRealize managementDigital data protectionPermission systemDatabase
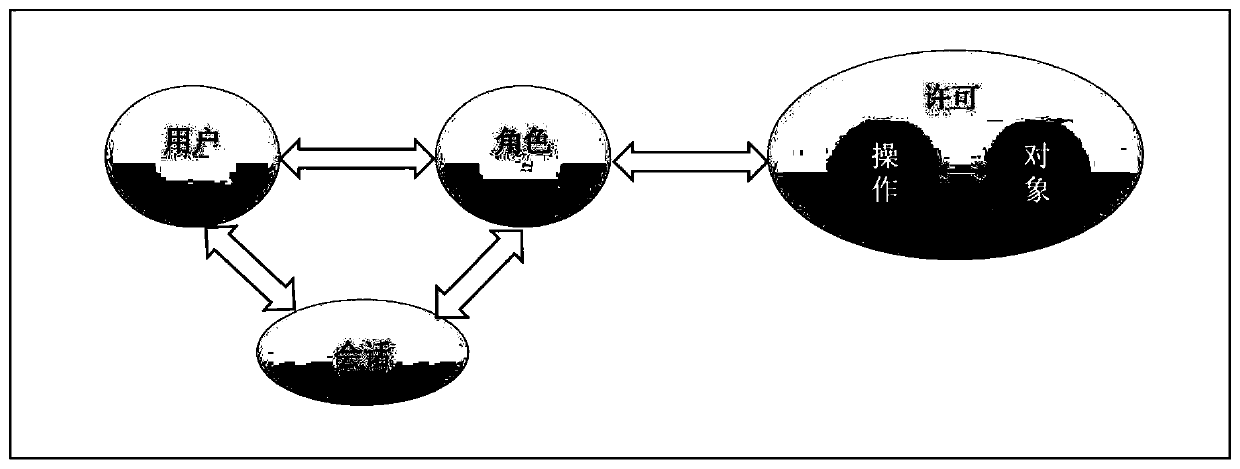
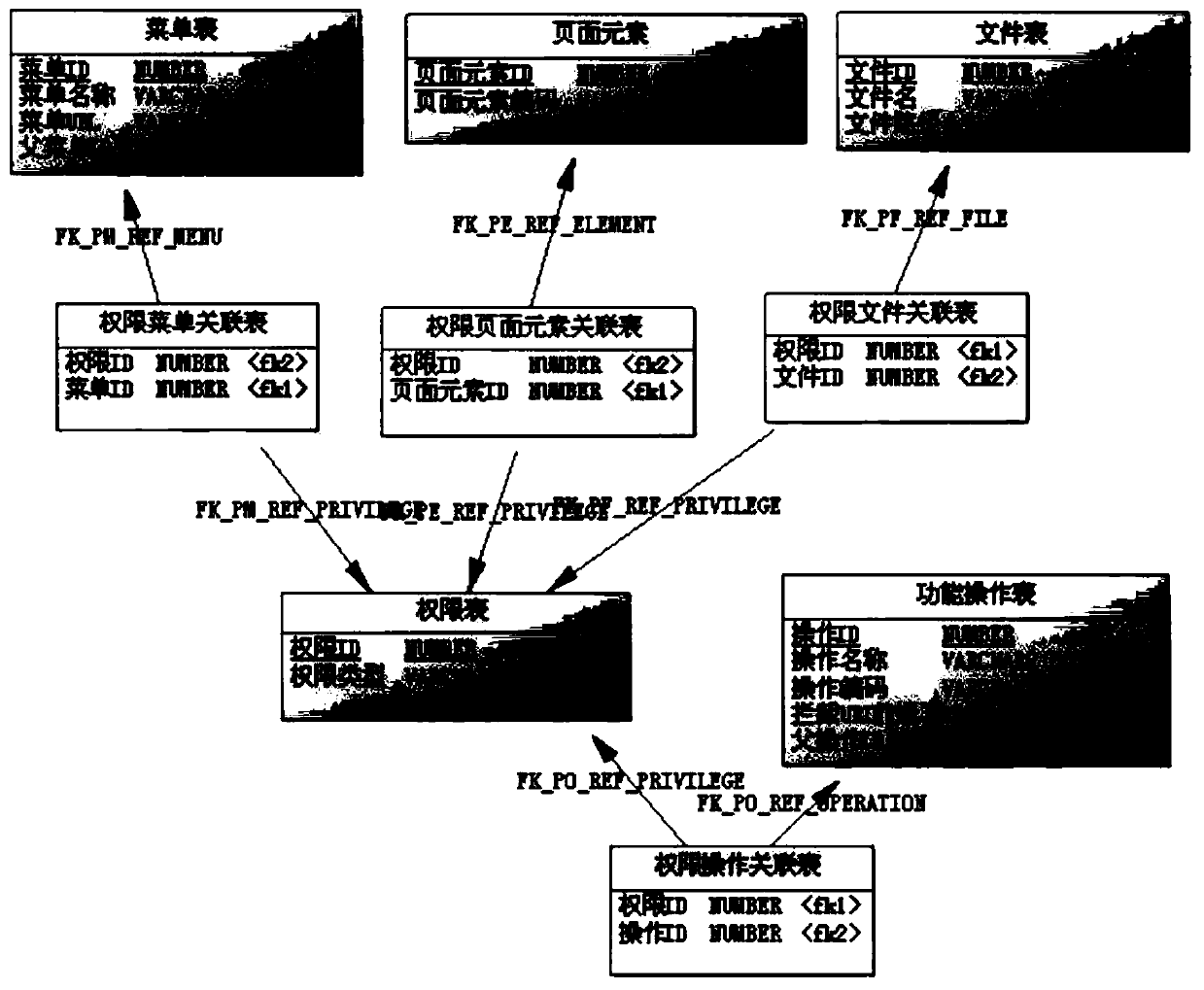
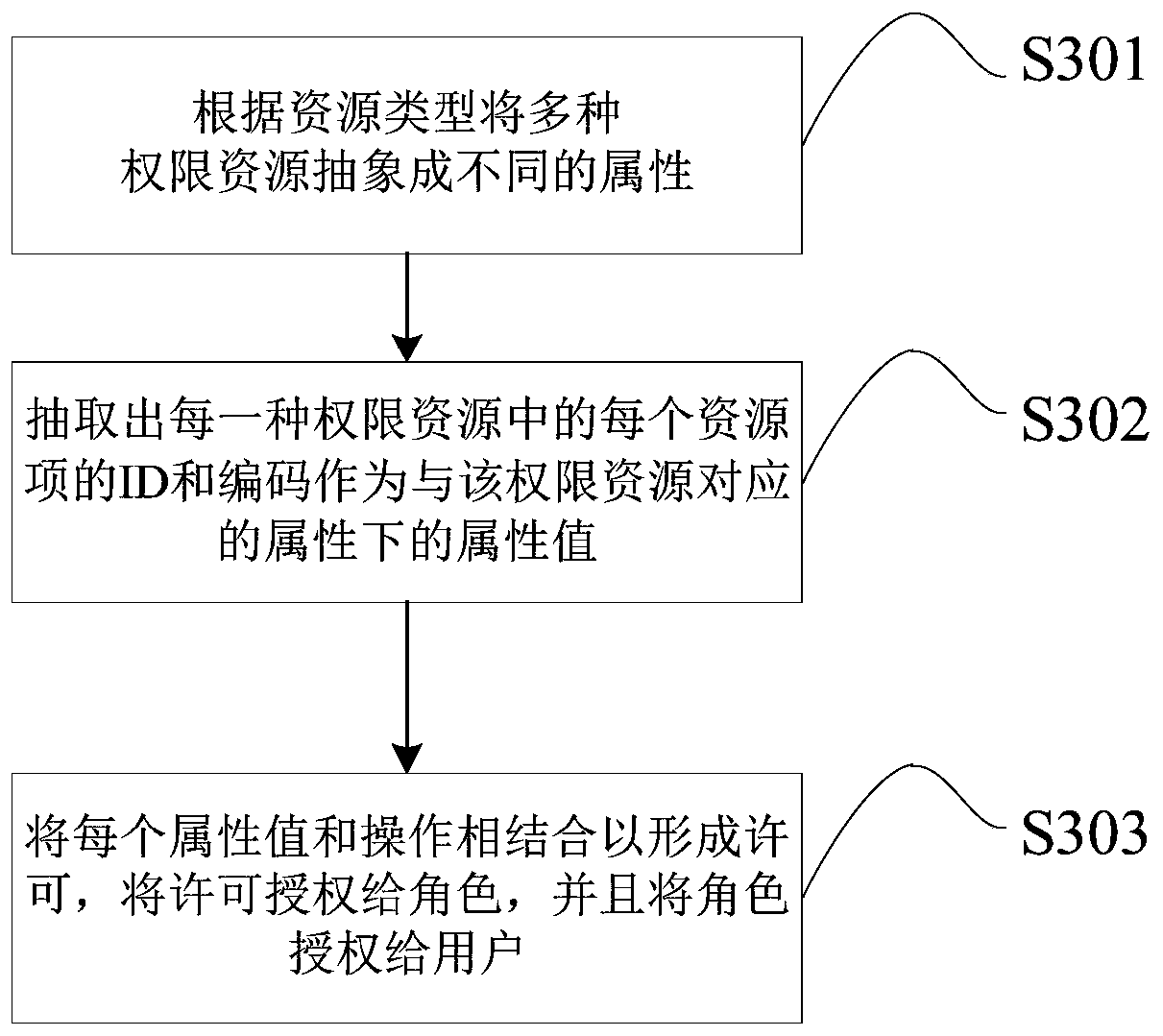
The invention relates to a method for performing permission configuration on permission resources, a permission system and a storage medium. The method comprises the following steps: abstracting various permission resources into different attributes according to resource types; extracting the ID and the code of each resource item in each permission resource as an attribute value under the attribute corresponding to the permission resource; and combining each attribute value with the operation to form permission, authorizing the permission to the role, and authorizing the role to the user. Forpermission resources of different resource types, the extracted ID and code of each resource item are used as the attribute value under the attribute to which the resource item belongs, so that unified configuration of the permission resources of different types is realized, the maintenance is convenient, the use is flexible, and the convenience and the expansibility are better.
Owner:石化盈科信息技术有限责任公司
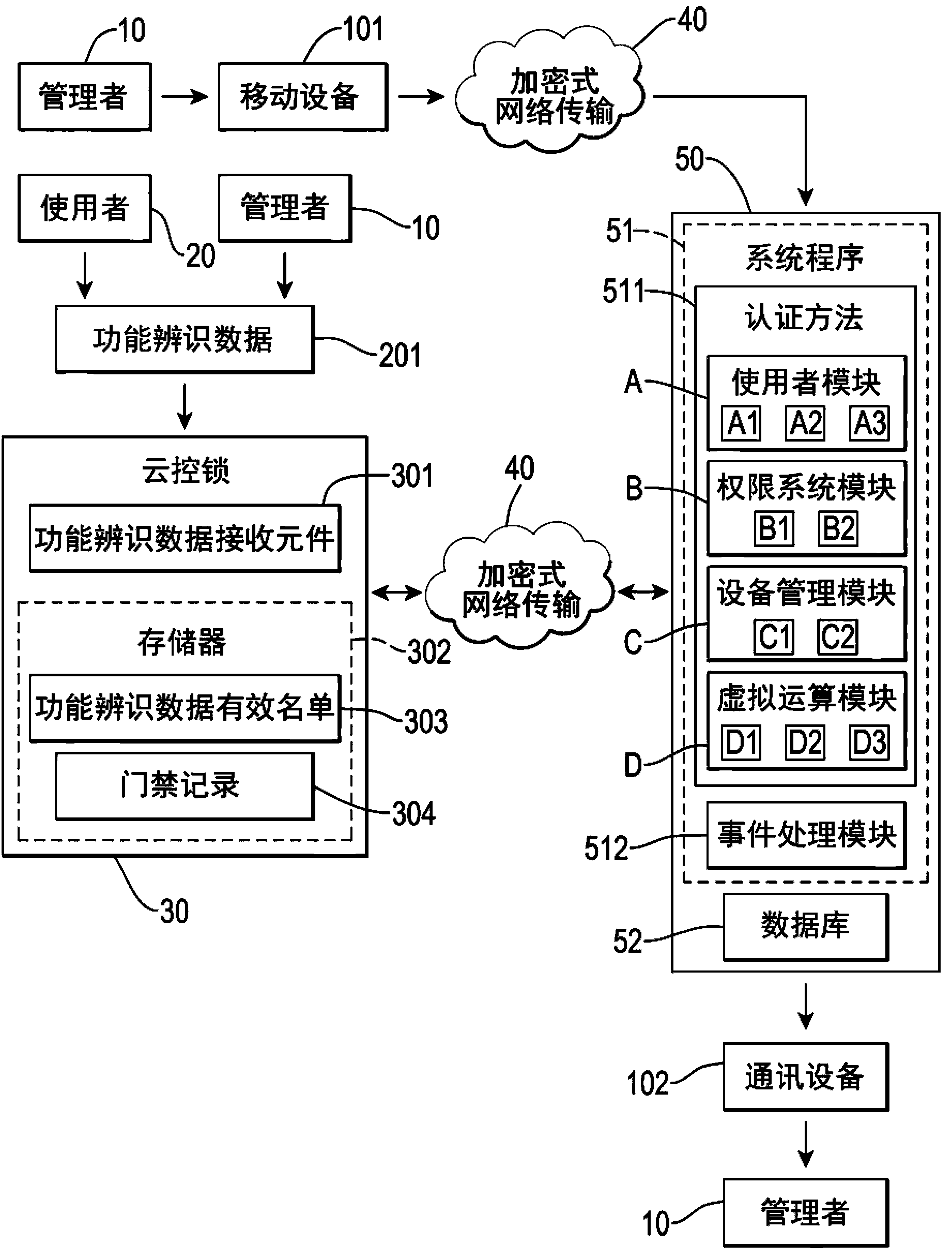
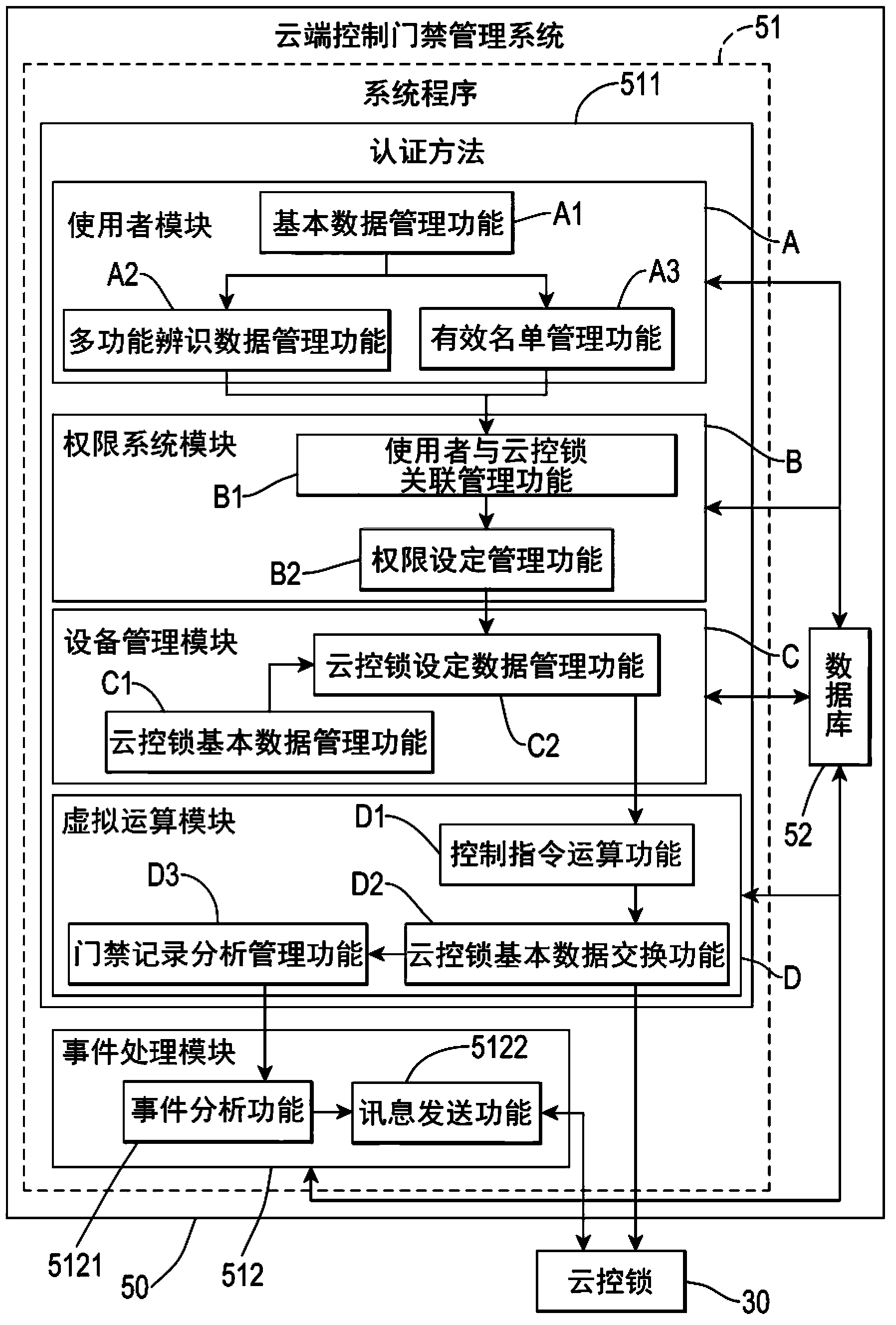
Cloud control the access control management system and the authentication method
InactiveCN103544749AInsufficient improvementAvoid breakingIndividual entry/exit registersFunctional identificationManagement information systems
A cloud control the access control management system and the authentication method used with one or a plurality of C-Lock connection management, the system includes at least: a system program and provide the management interface for programming operations, which contain five functional modules: a user module, a permission system module, a device management module, a virtual computing module and an event processing module combination; a database for storing the management information and function of identification information. Certification Department of the present invention is the use of multi-functional identification of cloud control lock mechanism through the encryption of network traffic and Cloud control the access control management system connection; it is close and remote two ways to achieve the purpose of certification.
Owner:EGE TECH
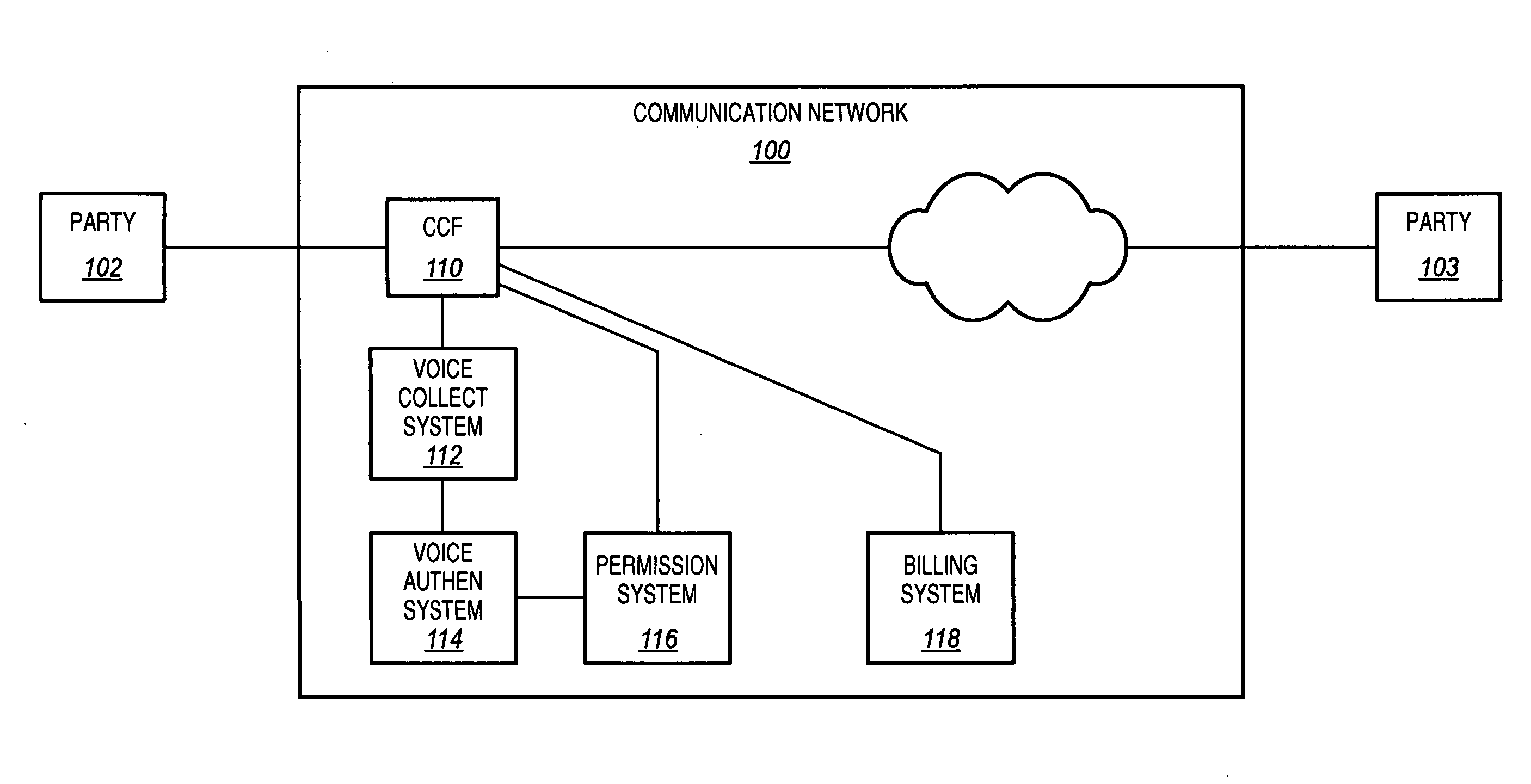
Voice authentication for call control
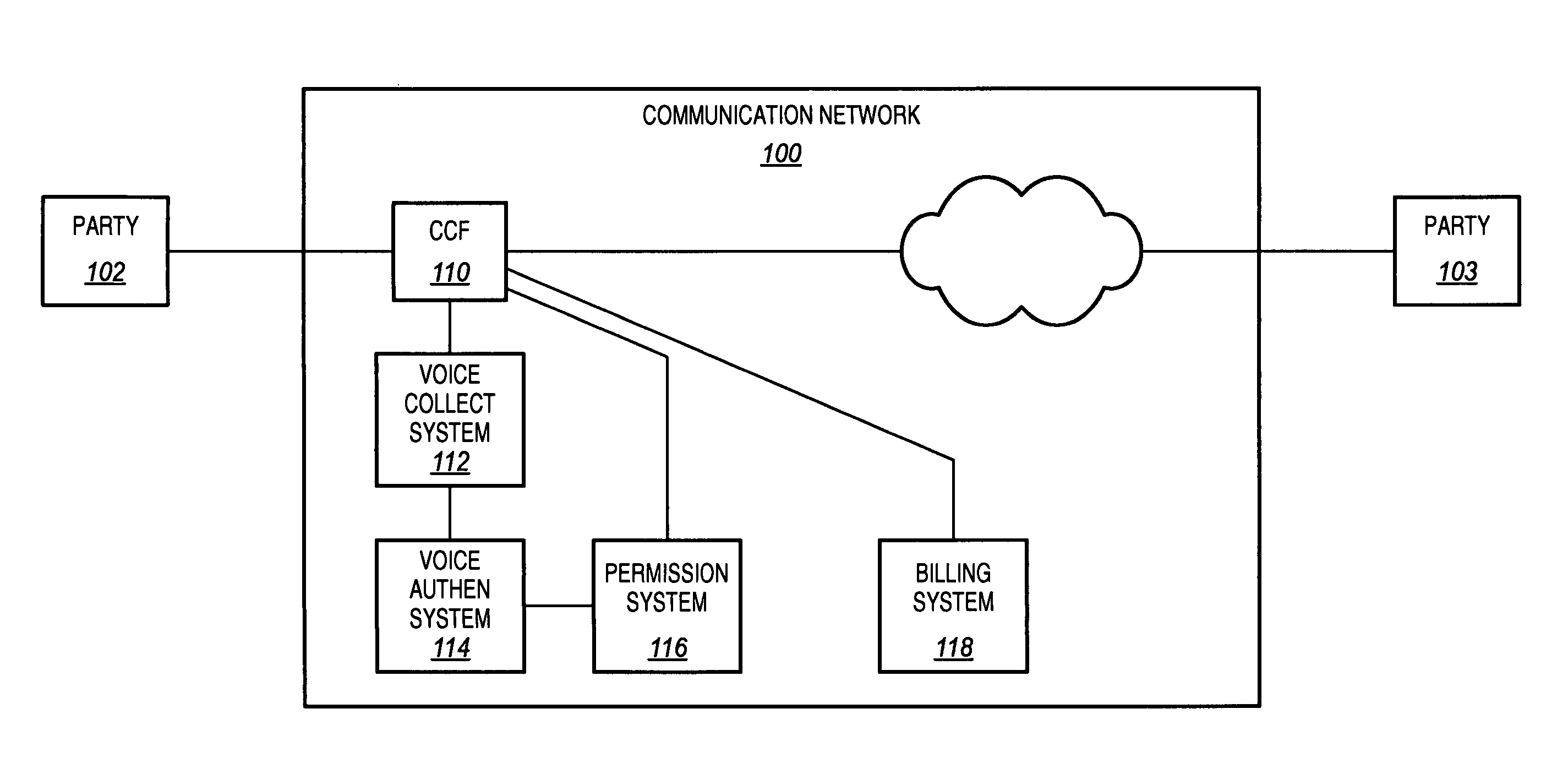
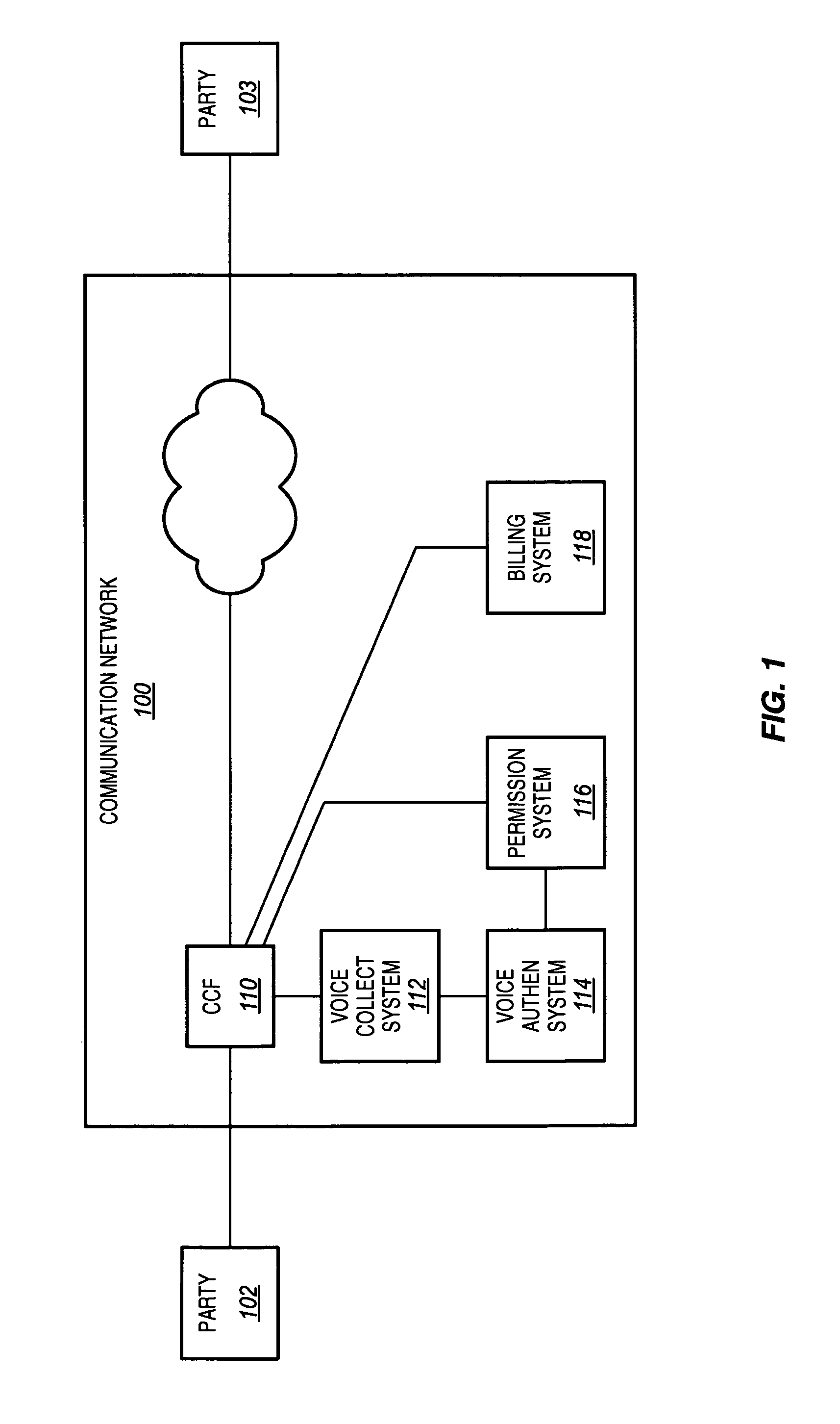
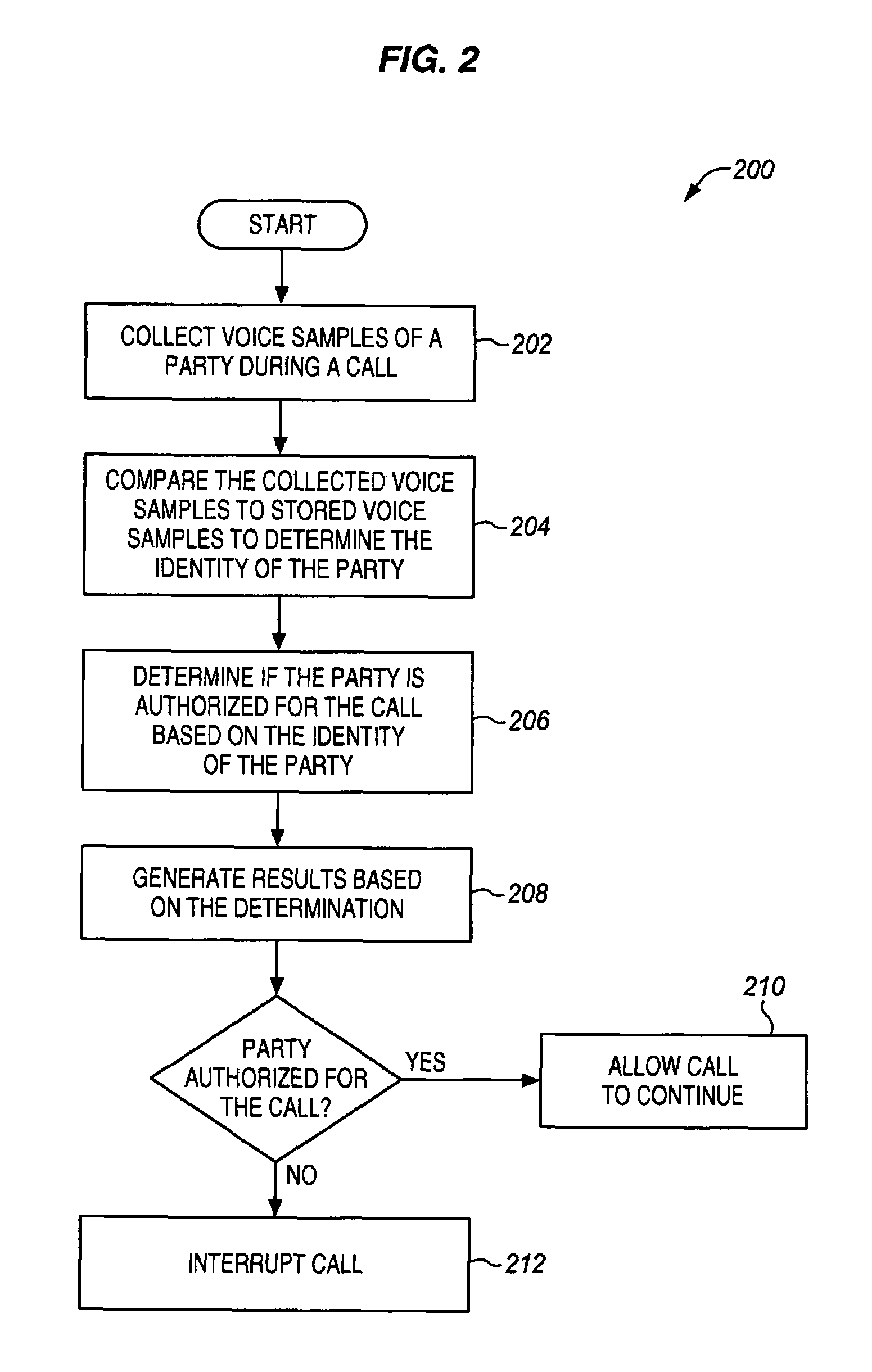
InactiveUS20060262908A1Efficient implementationImprove securityAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesPermission systemCollection system
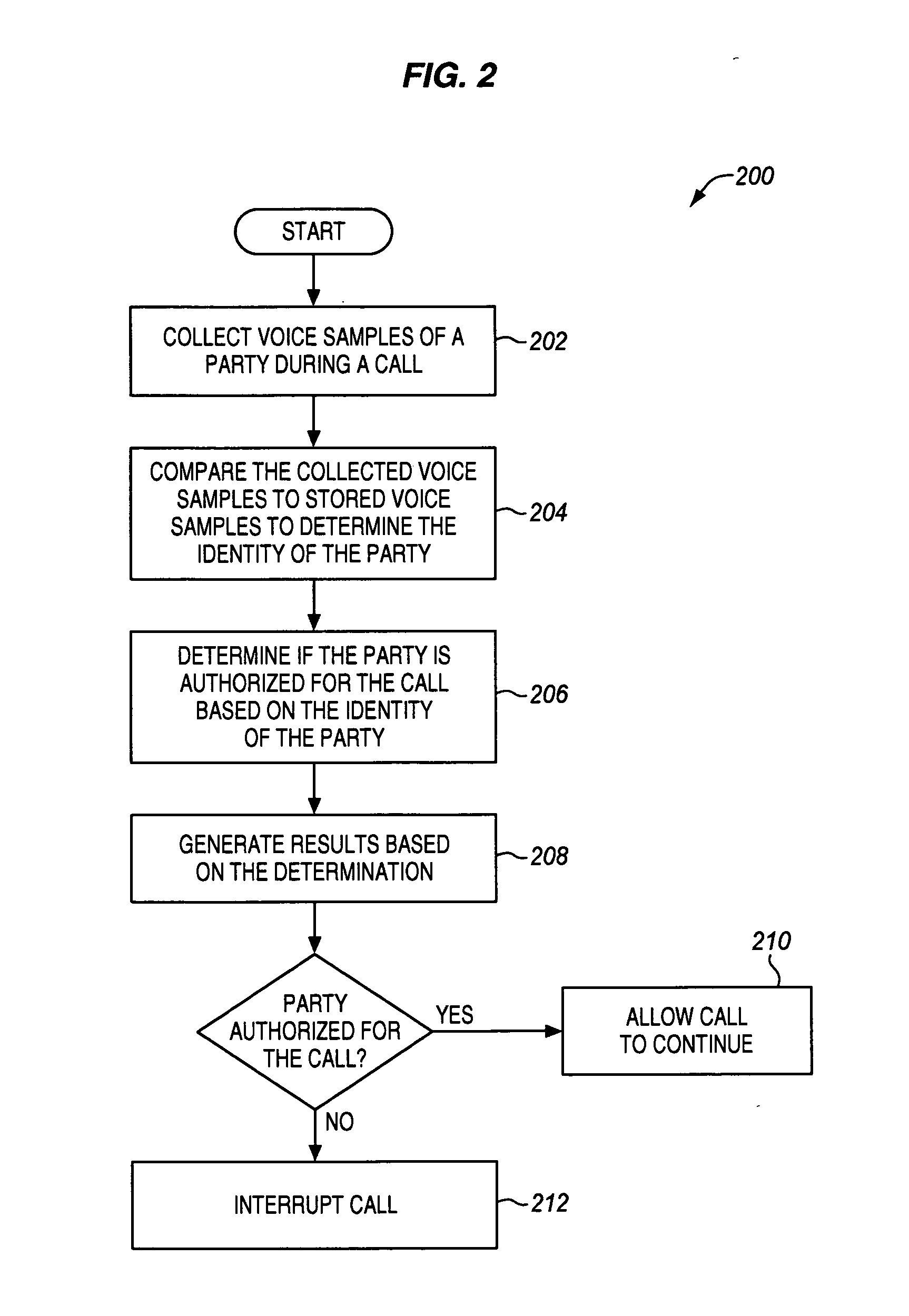
A communication network is disclosed that uses voice authentication to provide call control. The communication network includes a call control function, a voice collection system, a voice authentication system, and a permission system. The voice collection system collects voice samples of a first party during the call to a second party, and transmits the collected voice samples to the voice authentication system. The voice authentication system compares the collected voice samples to stored voice samples to determine the identity of the first party. The permission system determines whether the first party is authorized for the call based on the identity of the first party. The permission system generates results based on the determination and transmits the results to the call control function. The call control function then processes the results, and interrupts the call if the first party is not authorized.
Owner:ALCATEL-LUCENT USA INC
Method for cutting and combing computer network pages with permission system
InactiveCN101719163ARealize personalized customizationShorten the timeTransmissionSpecial data processing applicationsPermission systemCombined method
The invention discloses a method for cutting and combing computer network pages with a permission system, relating to the cutting and displaying of the computer network web system pages. The method comprises the steps of system and data table establishment, permission penetration, page cutting, cutting content combination and cutting content displaying. The invention combines the permission penetration technology with the page cutting and combining technology, firstly realizes permission penetration for service subsystems by the single sign-on technology, and then recombines the contents and functions required by the pages of a plurality of service subsystems to form an integrated page based on the affiliated permission via the page cutting and combining technology. The method has the advantages of integrating and displaying contents which are scattered in a plurality of service subsystems with permission originally via technical means, and maintaining real-time synchronization of the displayed information and the original service subsystems.
Owner:湖北电力信息通信中心 +1
Alliance block chain wallet node communication permission system and method
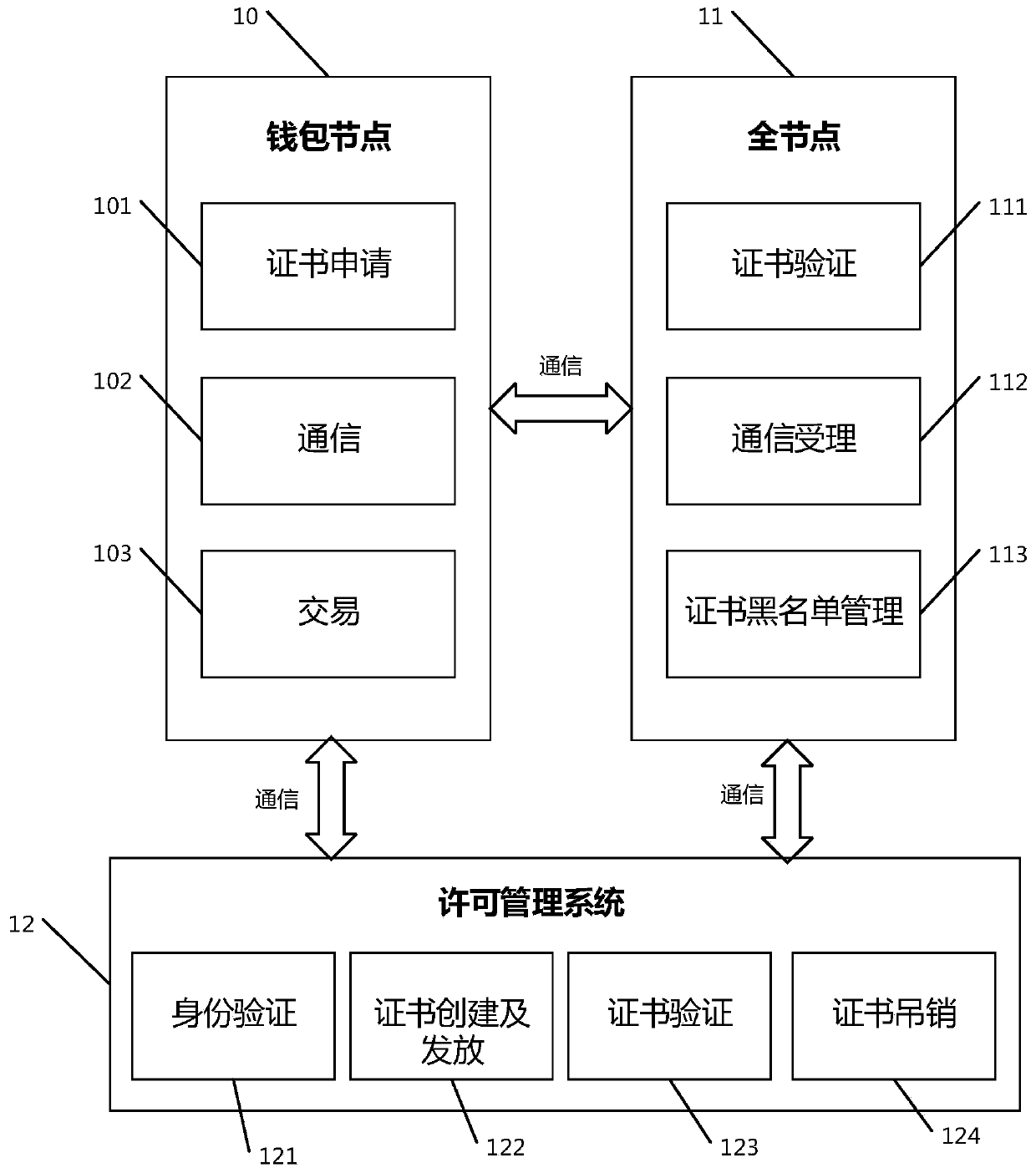
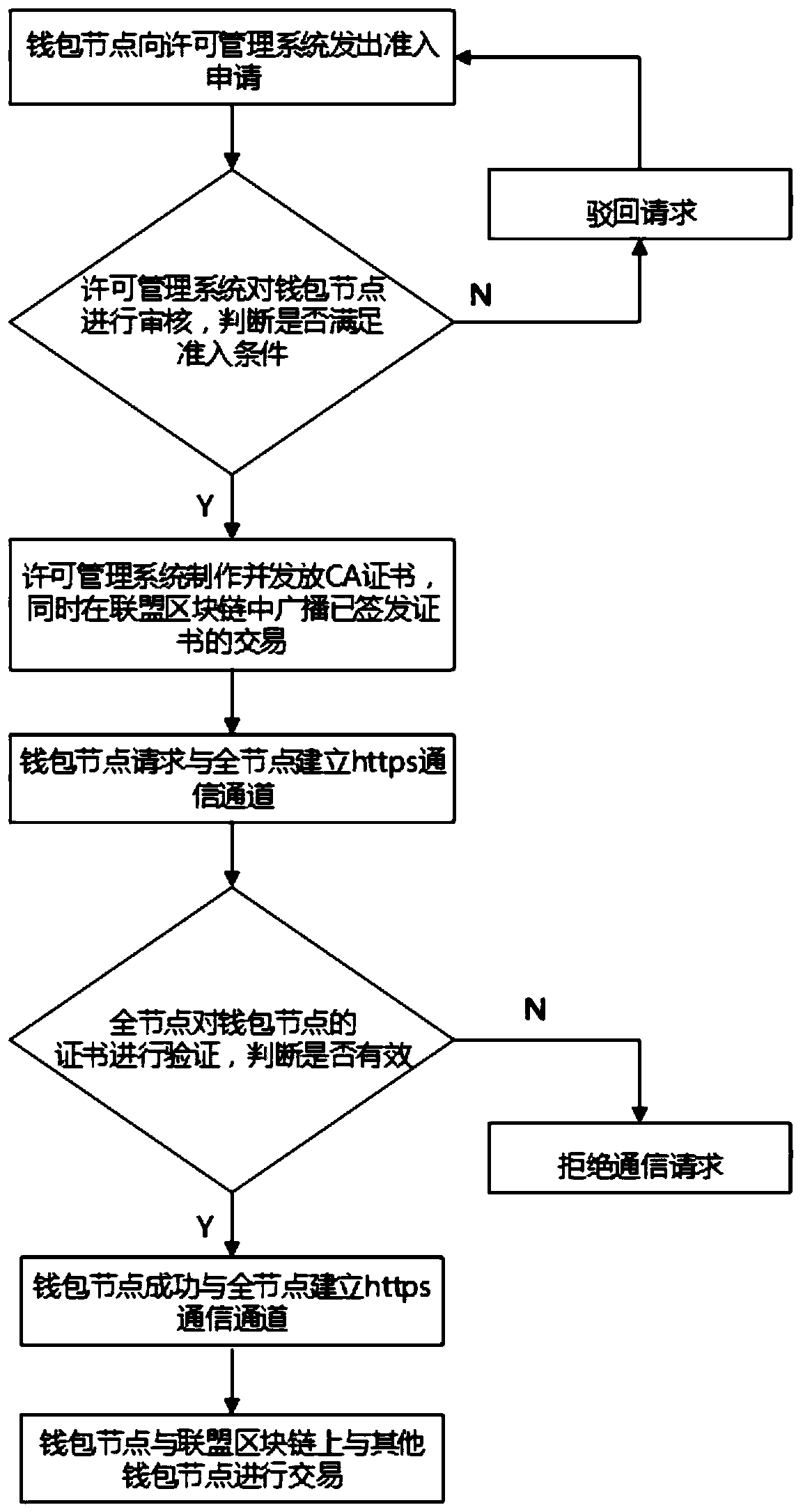
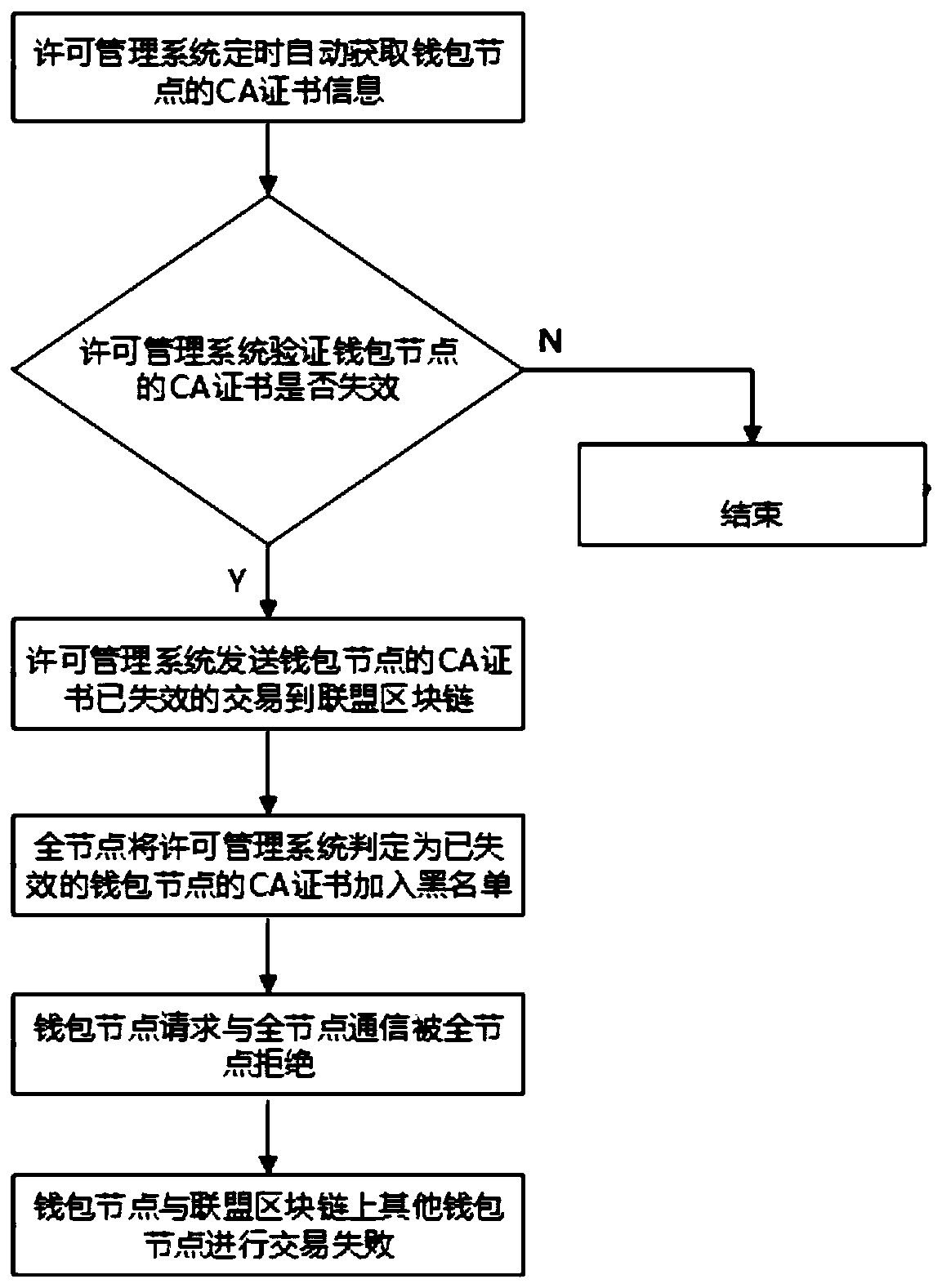
ActiveCN110099067AAvoid dependencyAvoid Information LeakageTransmissionPermission systemManagement system
The invention discloses an alliance block chain wallet node communication permission system and method. The system comprises a wallet node, a full node and a permission management system; the wallet node is configured and deployed at a personal client and is a block chain access entrance, so that the personal client can conveniently access the block chain to carry out transaction, and the wallet nodeprovides certificate application, communication request and acceptance, and transaction initiation and acceptance services for the user; the full node is configured to be deployed on a server and provided with a node of a complete block chain account book, synchronize all block chain data, independently verify all transactions on a block chain and update the data in real time, is responsible for broadcasting and verifying the transactions of the block chain, and is responsible for providing certificate verification, communication acceptance or certificate blacklist management service; and the permission management system is configured to be deployed on the alliance block chain, is responsible for auditing all wallet nodes on the alliance block chain, and is responsible for providing identity verification, certificate creation and issuing, certificate verification or certificate revocation services.
Owner:DAREWAY SOFTWARE
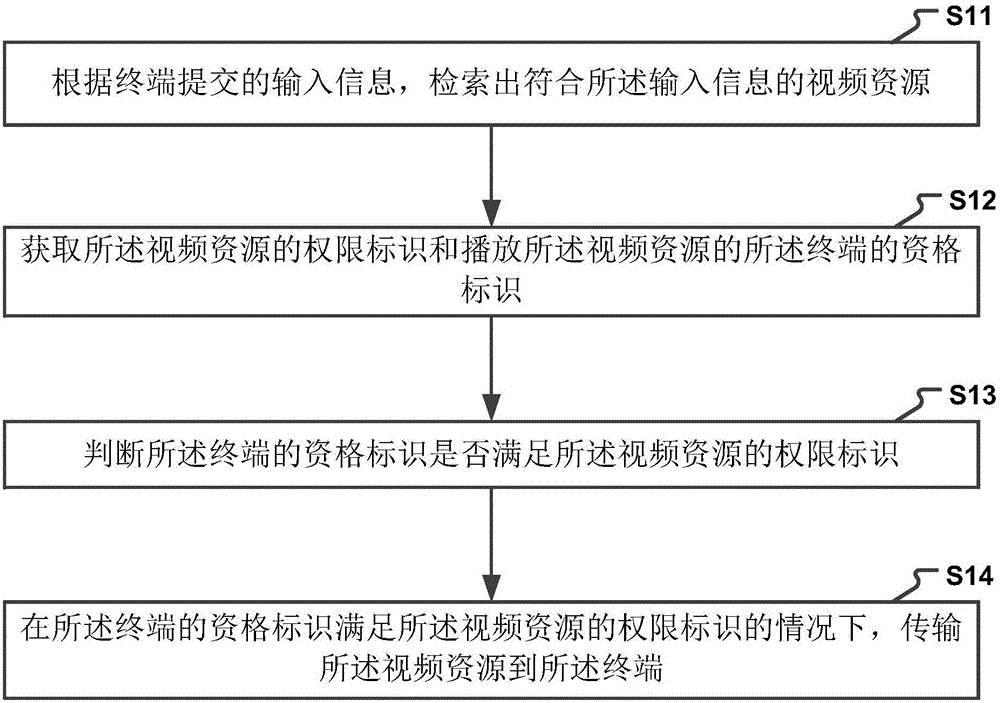
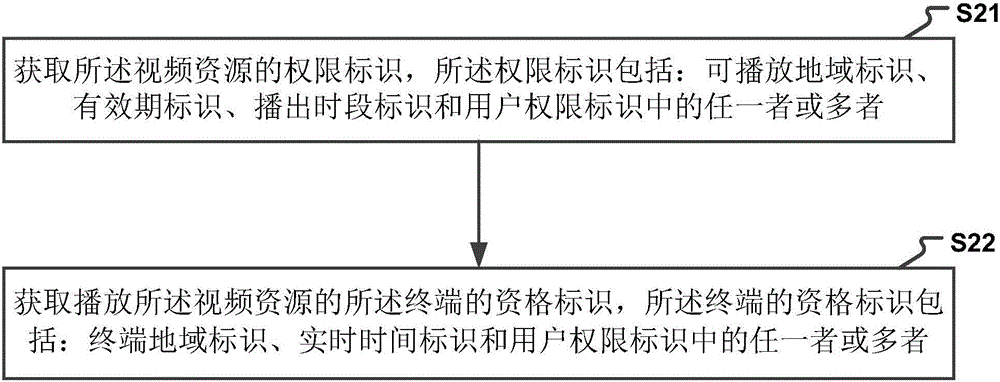
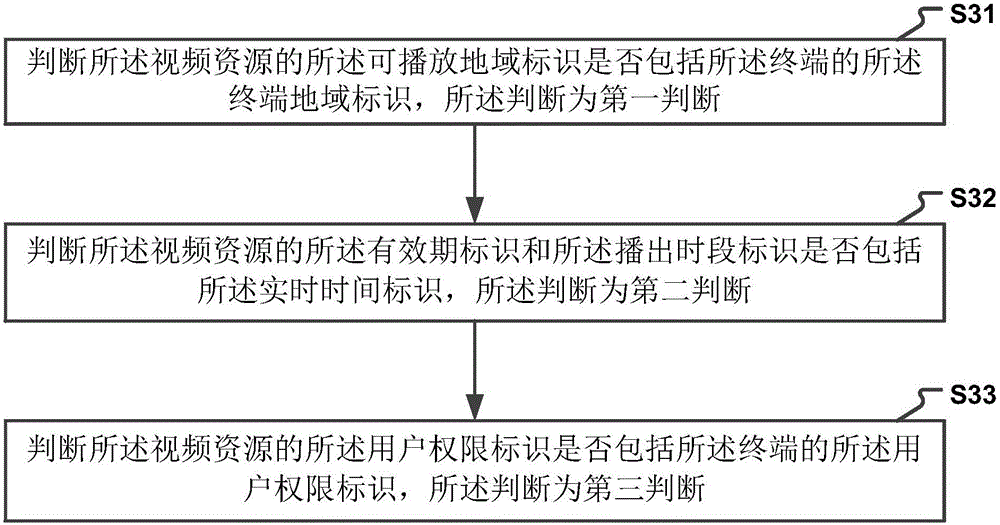
Method and device for managing playing permission
The invention discloses a method and a device for managing playing authority. The method for managing playback rights includes: according to the input information submitted by the terminal, retrieving video resources that conform to the input information; obtaining the permission identifier of the video resource and the qualification identifier of the terminal that plays the video resource; Judging whether the qualification identifier of the terminal satisfies the authority identifier of the video resource; if the qualification identifier of the terminal meets the authority identifier of the video resource, transmit the video resource to the terminal. The present invention can automatically judge whether the terminal has the authority to play the video resource according to the above-mentioned permission identifier and qualification identifier after obtaining the authority identifier of a certain video resource and the qualification identifier of the terminal playing the video resource, and realizes the identification through the identification To manage the playback rights of video resources, thereby improving the operating efficiency of the video resource playback rights system.
Owner:TVMINING BEIJING MEDIA TECH
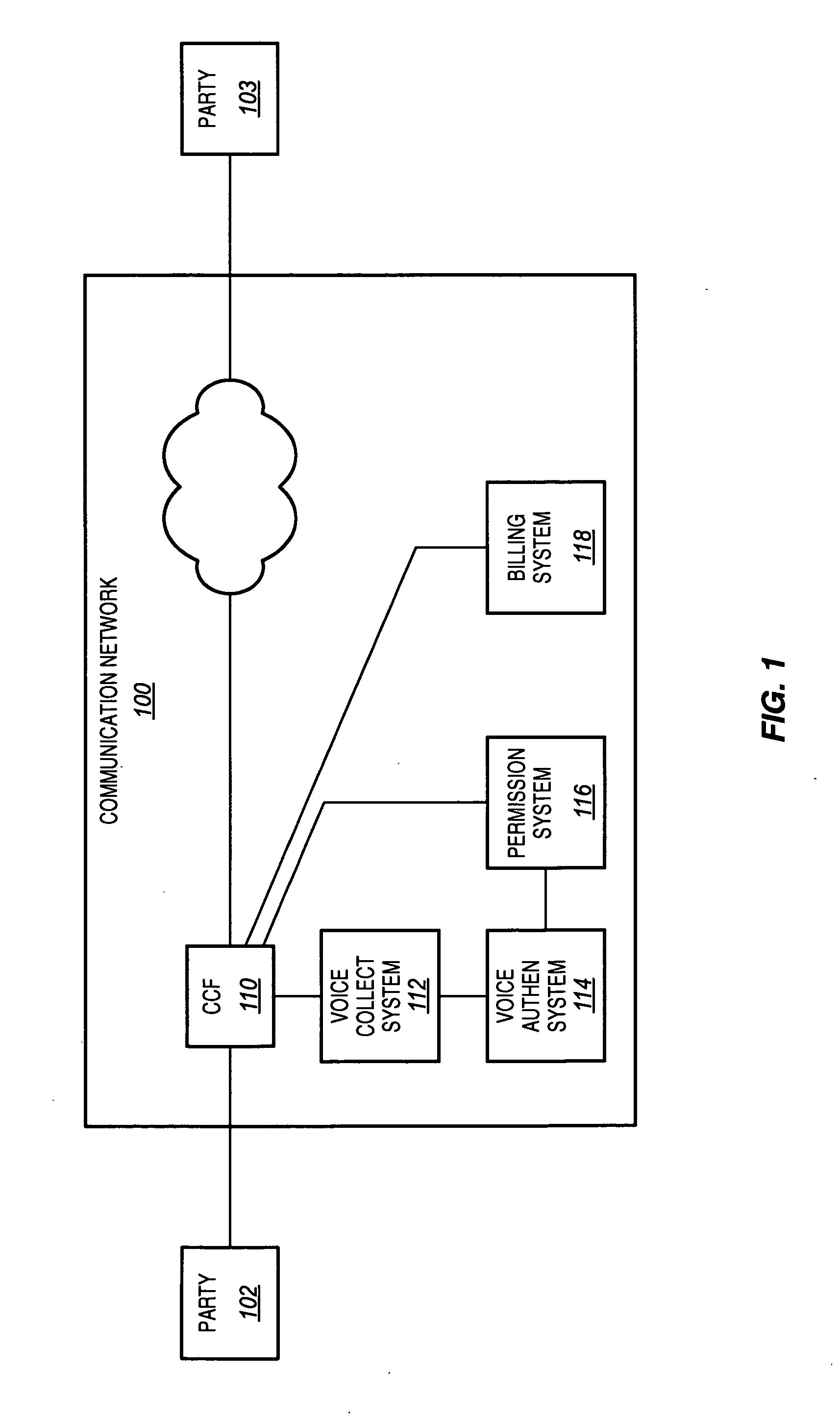
Voice authentication for call control
InactiveUS7636425B2Efficient implementationReduce processingAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesPermission systemCollection system
A communication network is disclosed that uses voice authentication to provide call control. The communication network includes a call control function, a voice collection system, a voice authentication system, and a permission system. The voice collection system collects voice samples of a first party during the call to a second party, and transmits the collected voice samples to the voice authentication system. The voice authentication system compares the collected voice samples to stored voice samples to determine the identity of the first party. The permission system determines whether the first party is authorized for the call based on the identity of the first party. The permission system generates results based on the determination and transmits the results to the call control function. The call control function then processes the results, and interrupts the call if the first party is not authorized.
Owner:ALCATEL-LUCENT USA INC
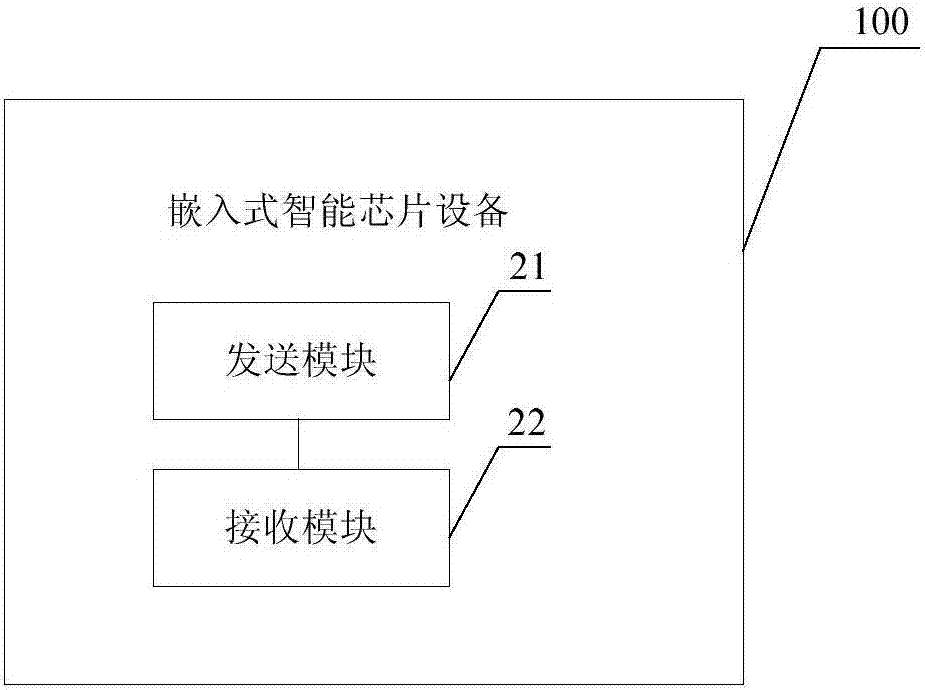
Embedded intelligent chip device and background application system
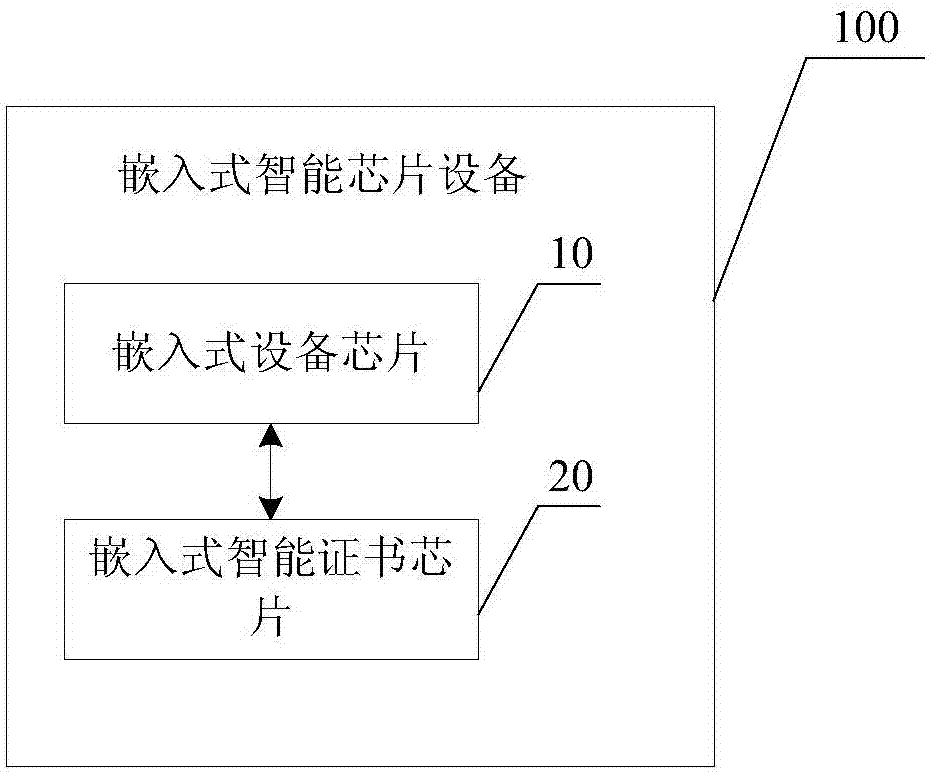
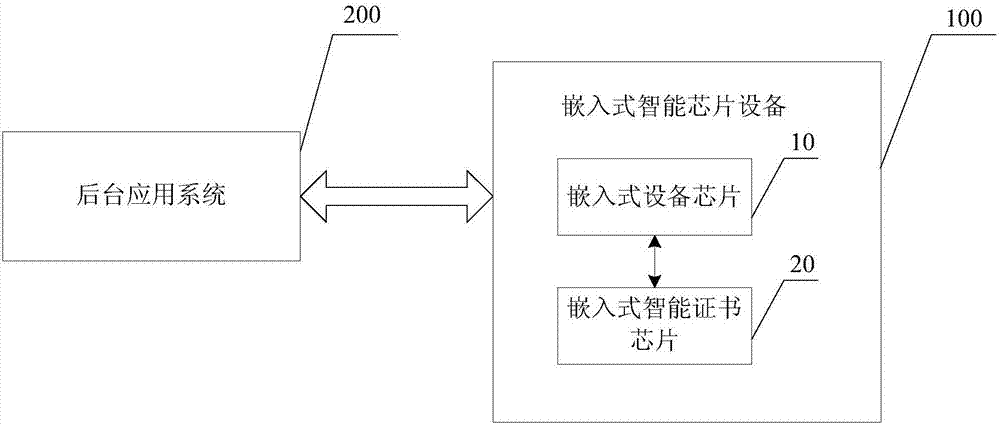
ActiveCN106855924AEasy to identifyPrevent intrusionUser identity/authority verificationDigital data authenticationPermission systemTransfer procedure
The invention discloses an embedded intelligent chip device and a background application system. The embedded intelligent chip device comprises an embedded device chip and an embedded intelligent certificate chip, wherein the embedded device chip is used for sending a control instruction to the embedded intelligent certificate chip, the embedded intelligent certificate chip is used for receiving the control instruction sent by the embedded device chip and conducting identity authentication on the embedded intelligent chip device and the background application system through the control instruction and encrypting and sending updated configuration data to the background application system through the embedded device chip after identity authentication is qualified, and meanwhile the embedded device chip begins to execute the functions of the embedded intelligent chip device after the authentication succeeds. By adopting the embedded intelligent chip device and the background application system, viruses or illegal permission systems are effectively prevented from invading the embedded intelligent chip device, and the data safety in the transmission process is ensured.
Owner:南方城墙信息安全科技有限公司
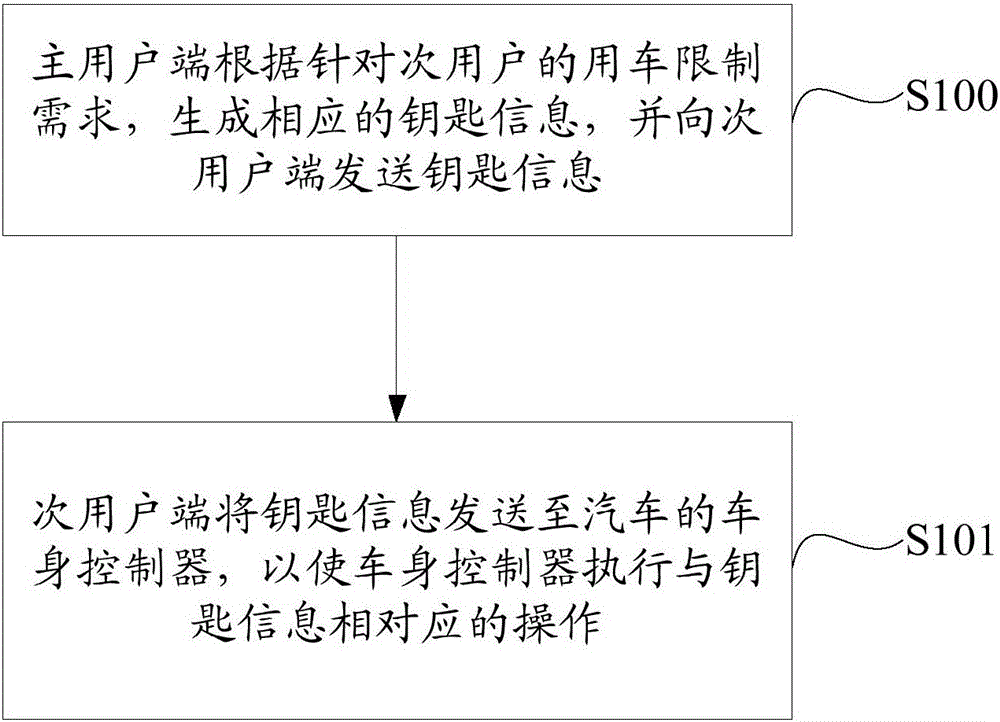
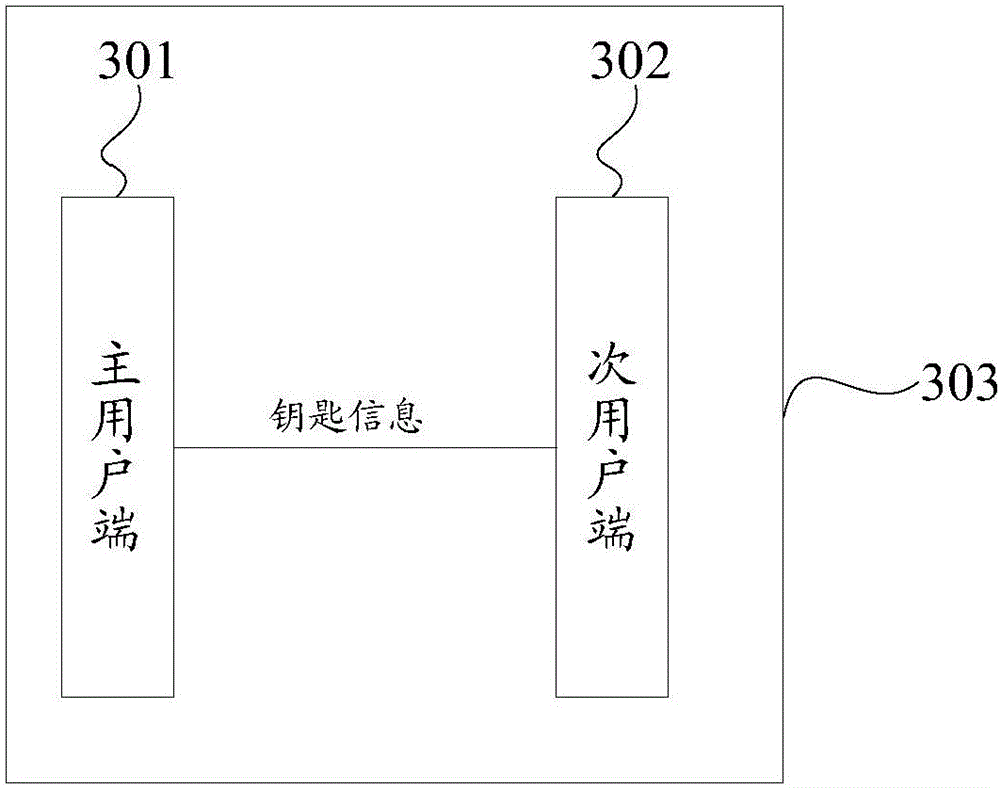
Access control permission management method and access control permission system for automobiles
InactiveCN105976472AEasy to manageFlexible managementIndividual entry/exit registersTransmissionEffective datePermission system
The invention discloses an access control permission management method and an access control permission system for automobiles. The method comprises the following steps that: a main user terminal generates corresponding key information according to vehicle utilization limit requirements of a secondary user and sends the key information to a secondary user terminal, wherein the key information include access right contents, valid number of times and effective date; and the secondary user terminal sends the key information to a vehicle body controller of an automobile to drive the vehicle body controller to carry out operations corresponding to the key information. According to the access control permission management method of the technical scheme, the purposes of conveniently, rapidly and flexibly managing the access control permission of the automobile when the main user shares the access control permission of the automobile with the secondary user can be achieved.
Owner:KOSTAL SHANGHAI MANAGEMENT +1
System and computer program for providing high delivery performance in a value chain
ActiveUS20210065118A1Improve delivery capabilitiesDatabase updatingData switching by path configurationData storeNetwork module
A system, computer program product and method for providing high delivery performance in a value chain network utilizing a finite capacity planning and scheduling model. The system includes a plurality of remote computers in communication with a respective plurality of remote users, a service provider computer having a computer program stored in non-transient memory and one or more microprocessors, a network interface in communication with the central server and the plurality of remote computers over a shared network, a shared database, having a master data repository and an execution data repository, in communication with the service provider computer, a multi-party module configured to onboard the plurality of remote users onto the shared network via the network interface, a real-time module configured to manage in real-time a shared data model common to at least a portion of the plurality of remote users, a permissibility network module having a permission system, a control system and software tools that manages access permissions to the shared network, the master data repository and to the execution data repository, and a planner module having an initial overall planning module and re-planning module. The re-planning module is configured to re-plan upon a change in condition in the value chain network and to limit planning to only those portions of the value chain network affected by the change in condition. Each of the plurality of remote users represents one of a plurality of entities in a value chain. Each of the plurality of remote users has at least one of a plurality of roles. The network interface is configured to receive one or more transactions via the shared network. The value chain network has shared access to a shared database on the service provider computer over the shared network. The shared data model is in communication with the master data repository and the execution data repository. The permission system is configured to provide access permissions to the plurality of remote users using predefined configuration settings. The control system includes rules that vary for each of the plurality of entities and by the respective role of the plurality of remote users. The rules define the read, write, edit and delete permissions and access rights to specific portions of the shared data model. The service provider computer is configured to: (i) provide access to the shared network to the plurality of remote computers based on the respective access permission of the one of the plurality of remote users provided by the permissibility network module, (ii) provide access to the master data repository and to the execution data repository based on the respective access permission of the one of the plurality of remote users provided by the permissibility network module, and (iii) manage access and updates to specific portions of the shared data model for all relevant remote users of the plurality of remote users.
Owner:ONE NETWORK ENTERPRISES
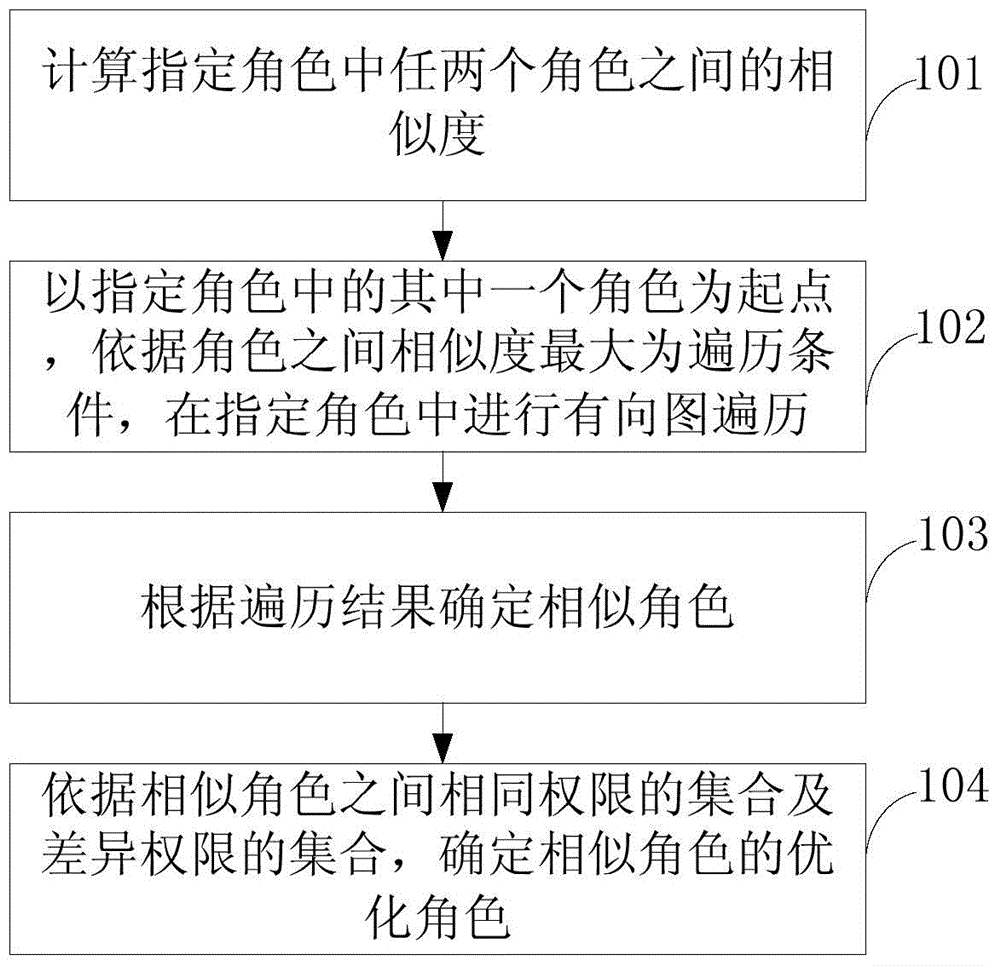
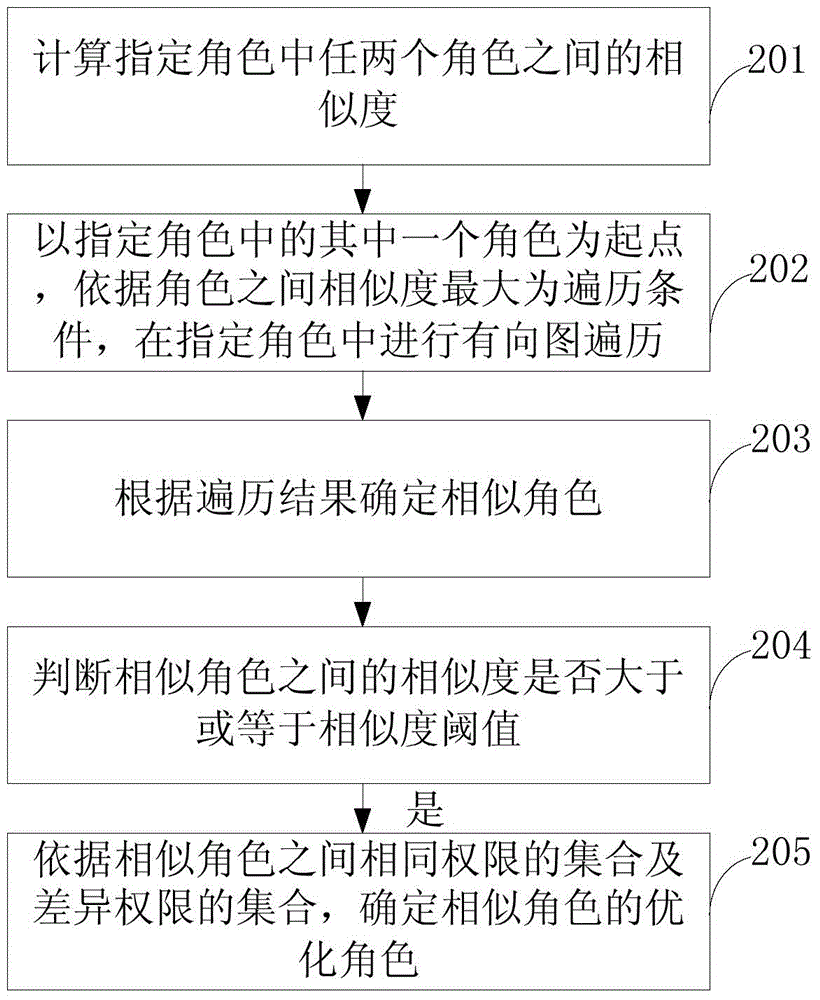
Role optimization method and apparatus in RBAC permission system
ActiveCN105989276AReduced permissions are the sameReduce the situationDigital data authenticationDirected graphPermission system
The embodiment of the present application provides a role optimization method and device in the RBAC authority system. The method includes: calculating the similarity between any two roles in the specified roles; taking one of the specified roles as a starting point, and according to the traversal condition that the similarity between the roles is the largest, in the specified role. traversing the graph; determining similar roles according to the traversal results; determining an optimized role for the similar roles according to a set of identical permissions and a set of different permissions among the similar roles. The embodiment of the present application makes the set of permissions among the roles as completely independent as possible, and together represent a business meaning, thereby reducing the occurrence of the same or overlapping permissions in different roles, and further reducing the unreasonable assignment of roles to users. System security risks.
Owner:ADVANCED NEW TECH CO LTD
Dual-system code/file management platform architecture
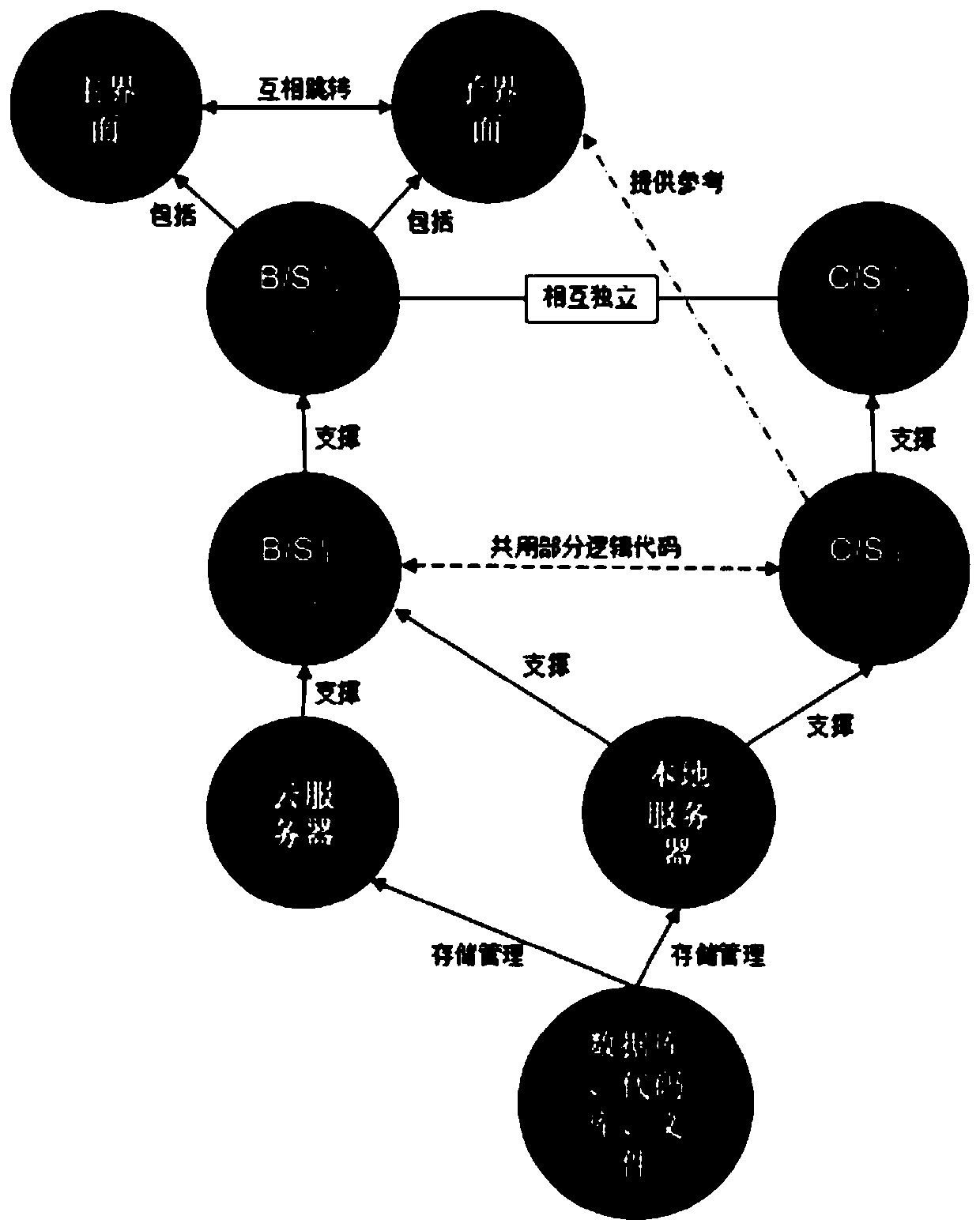
ActiveCN109739541AQuick buildQuick searchVersion controlDigital data protectionSystems designEnd system
The invention provides a dual-system code / file management platform architecture. The dual-system code / file management platform architecture comprises a function collection layer, a server layer, two permission system layers, an algorithm and logic layer, a database layer, two dual-front-end interface layers and two dual-rear-end system layers. According to the invention, two sets of system designsrespectively based on C / S architecture and B / S architecture are applied; Functions of code / file management, visualization, algorithm interface calling, algorithm search query recommendation, algorithm establishment, online and offline calculation and the like are realized by sharing part of database data, code files and the like, two sets of authority systems and authority price overflow systems,and a cloud server and a local server which are reasonably arranged, so that functional extension of conventional code / file management systems are carried out, the use difficulty is reduced, the working efficiency and the collaborative development efficiency are improved, a large amount of repeated work is avoided, the use experience is improved, research and development server resources can be ensured not to be additionally occupied, and the data transmission speed, the data transmission safety and the like can be ensured.
Owner:CETC BIGDATA RES INST CO LTD
A heterogeneous asset application mode containing safety guarantee measures
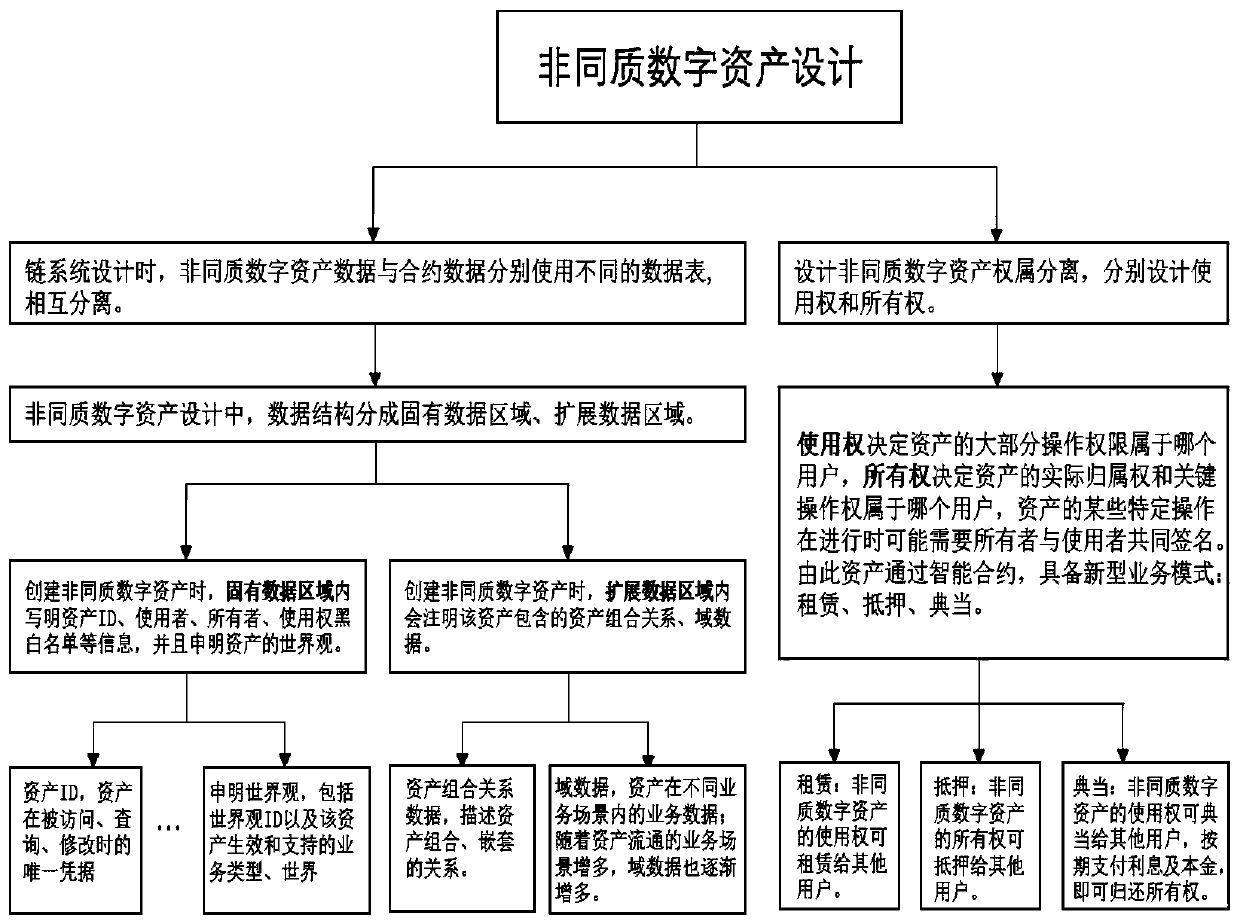
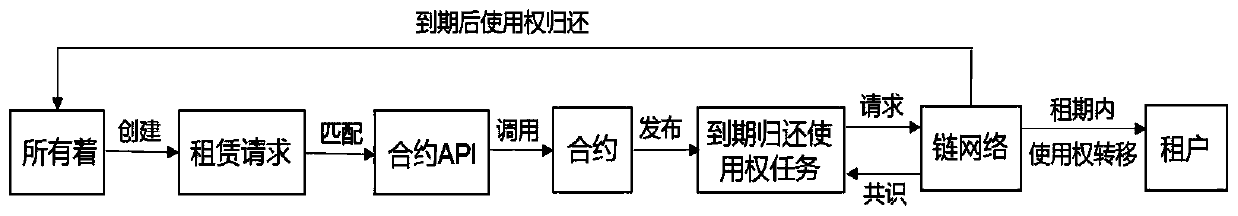
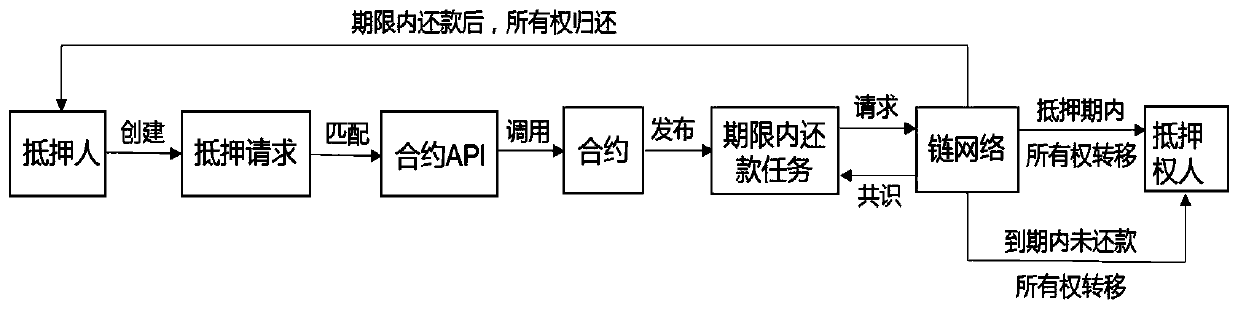
InactiveCN109934581AWith atomic operation characteristicsOptimize data structureFinancePayment protocolsPermission systemWorld Wide Web
The invention relates to a blockchain, and particularly relates to a heterogeneous asset application mode containing safety guarantee measures. The system comprises heterogeneous digital assets. the ownership of the heterogeneous digital asset design assets is separated; wherein the asset ownership separation comprises steps of determining whether the user has the use right of most of the operation authorities of the assets and determining whether the user has the ownership of the asset actual ownership and the key operation right or not; wherein the data structure of the heterogeneous digitalassets decides whether the heterogeneous digital assets can use the asset use right blacklist and the asset use right blacklist of the assets in a specific occasion, the ownership and the disposal right of the heterogeneous digital assets only belong to all the users, and the destruction operation of the heterogeneous digital assets can only be authorized and processed by the users; The technicalscheme provided by the invention can effectively overcome the defects that the heterogeneous digital assets lack an asset permission system and the heterogeneous digital assets lack a safety guarantee mechanism in the prior art.
Owner:有看(广东)信息科技有限公司
Permission control method and device
ActiveCN108920914AShorten the timeHas accessDigital data authenticationPermission systemConfiguration item
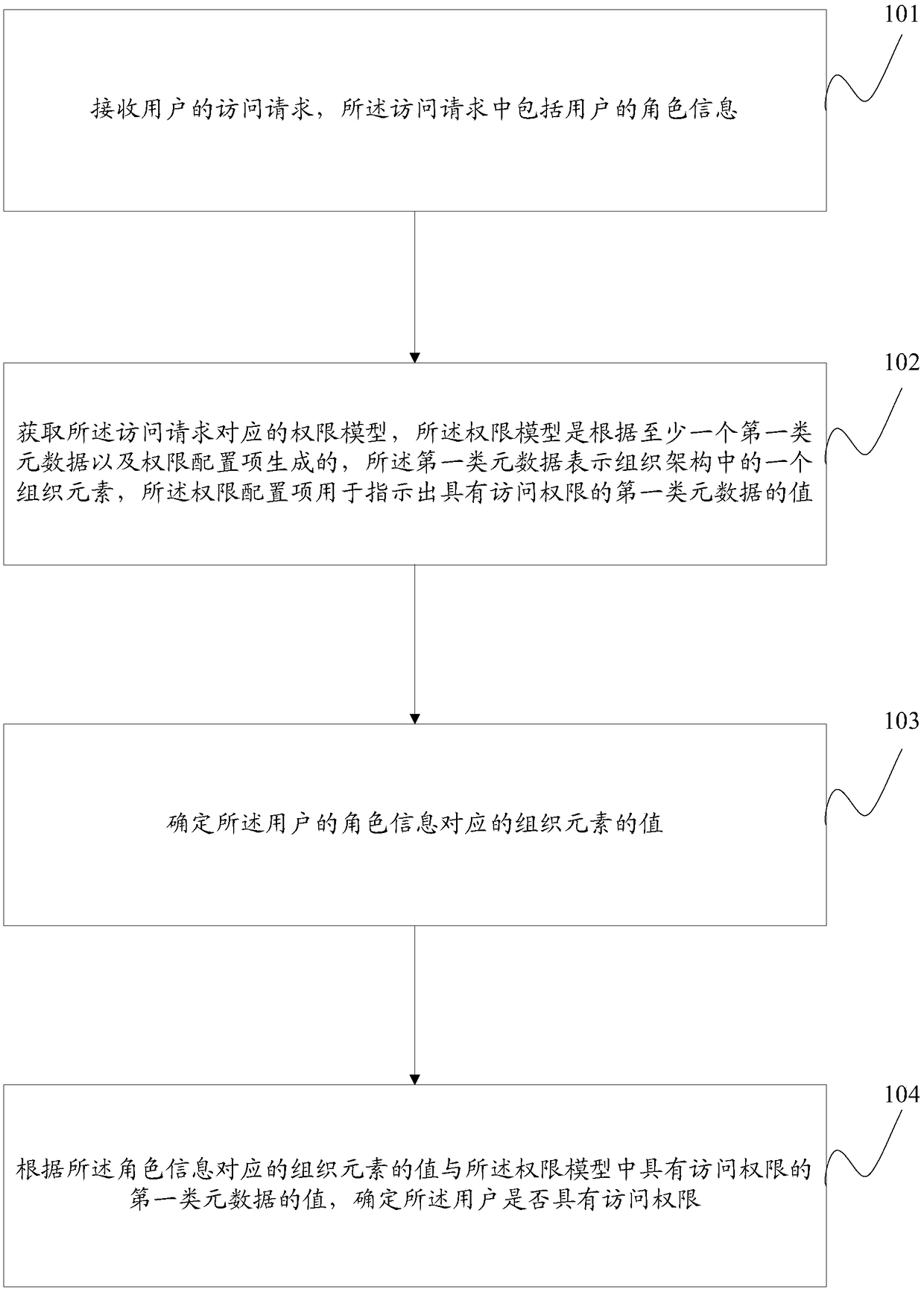
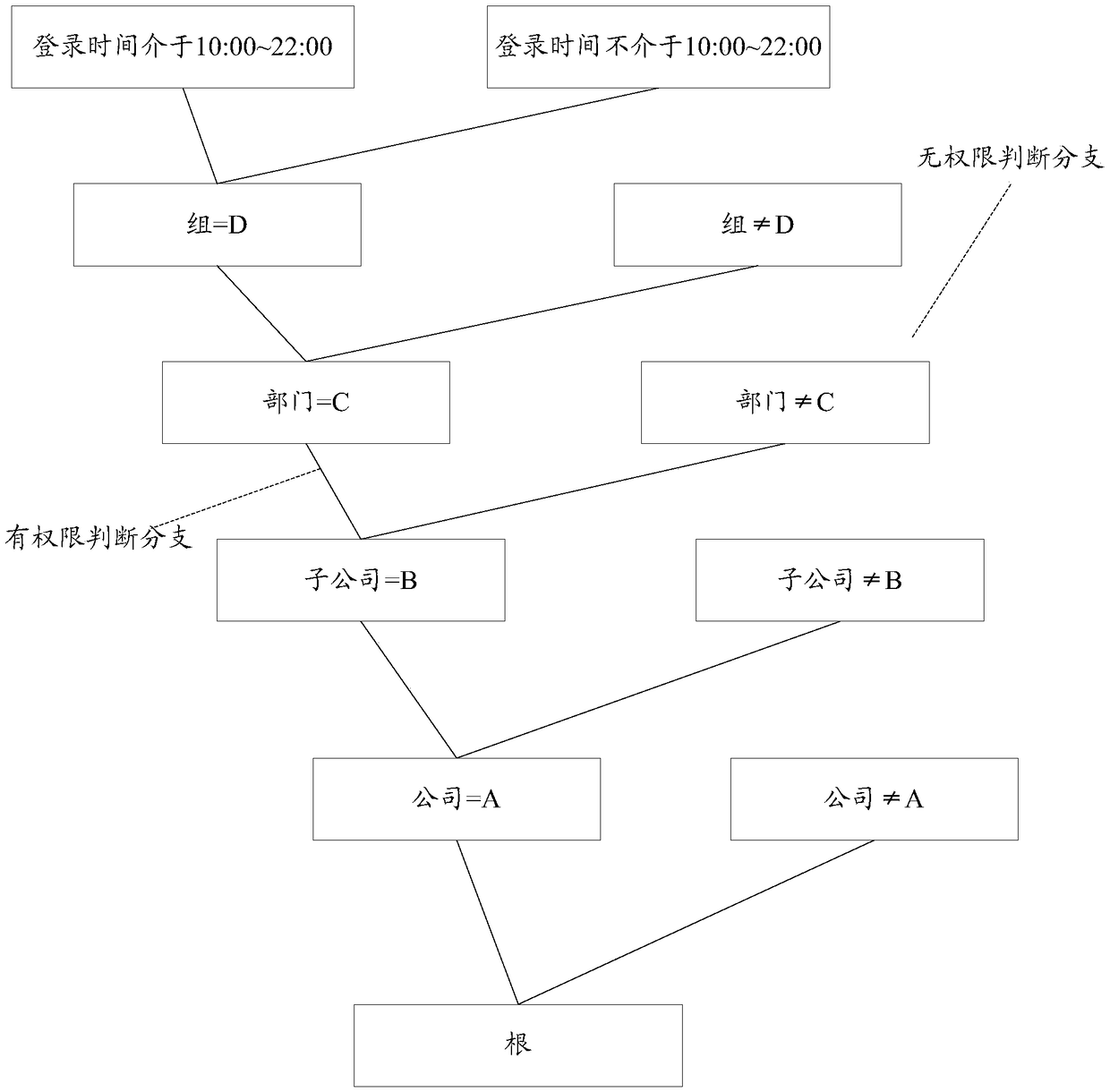
The invention provides a permission control method and device and relates to the technical field of permission management. The method includes: receiving a user's access request, wherein the access request contains role information of a user; acquiring a permission model corresponding to the access request, wherein the permission model is generated according to at least one first-type metadata andpermission configuration items, the first-type metadata represents an organizational element in the organizational architecture, and the permission configuration items are used for indicating the value of the first-type metadata with access permission; determining the value of the organizational element corresponding to the role information of the user; determining whether the user has the accesspermission or not according to the value of the organizational element corresponding to the role information and the value of the first-type metadata in the permission model that has the access permission. The permission model is determined according to the organizational architecture element corresponding to the user, modification of the permission system is not needed when the organizational architecture is changed, the permission model is continuously used to perform permission judgment, and autoadaptation after one-step configuration of the permission model is achieved.
Owner:CHINA UNIONPAY
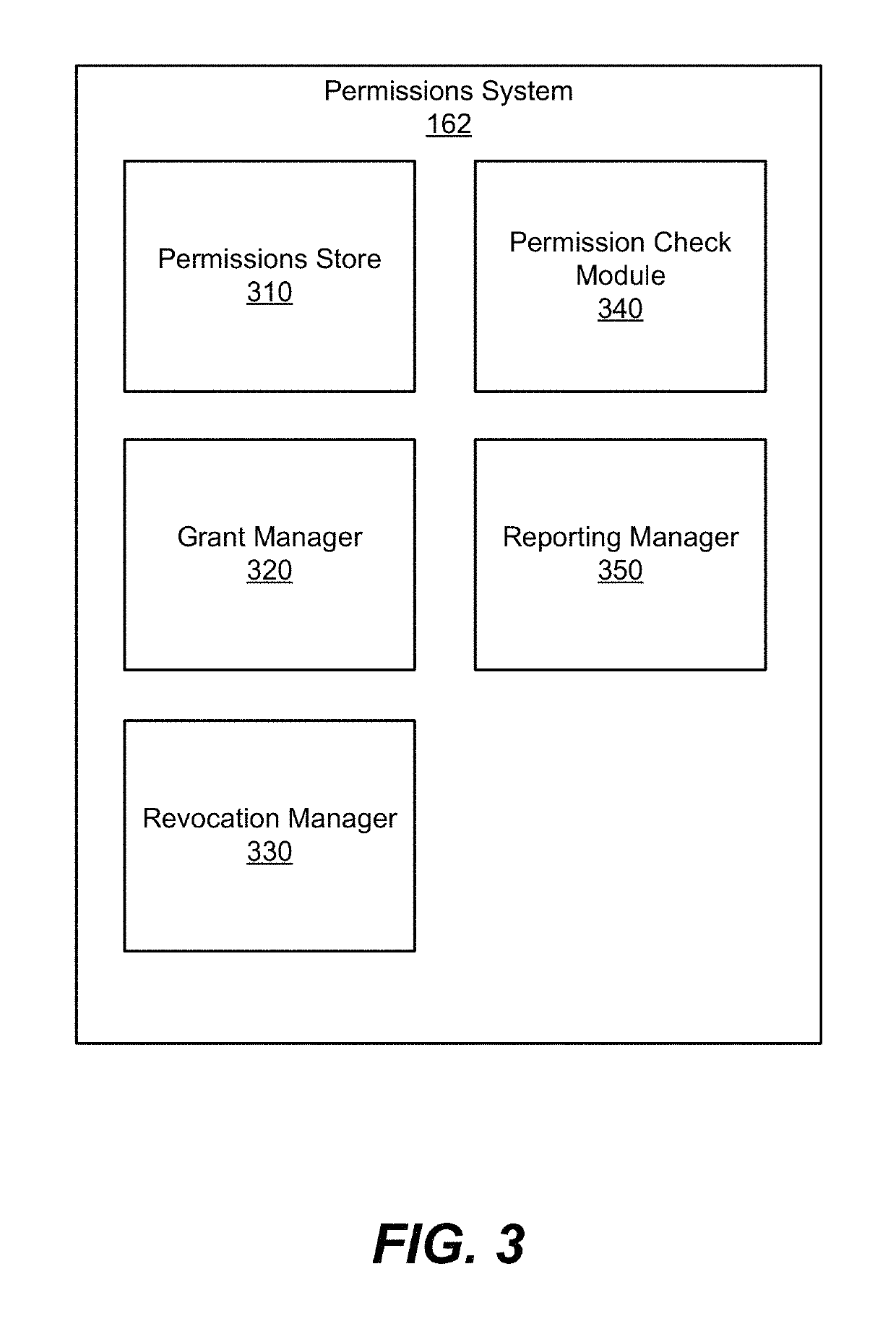
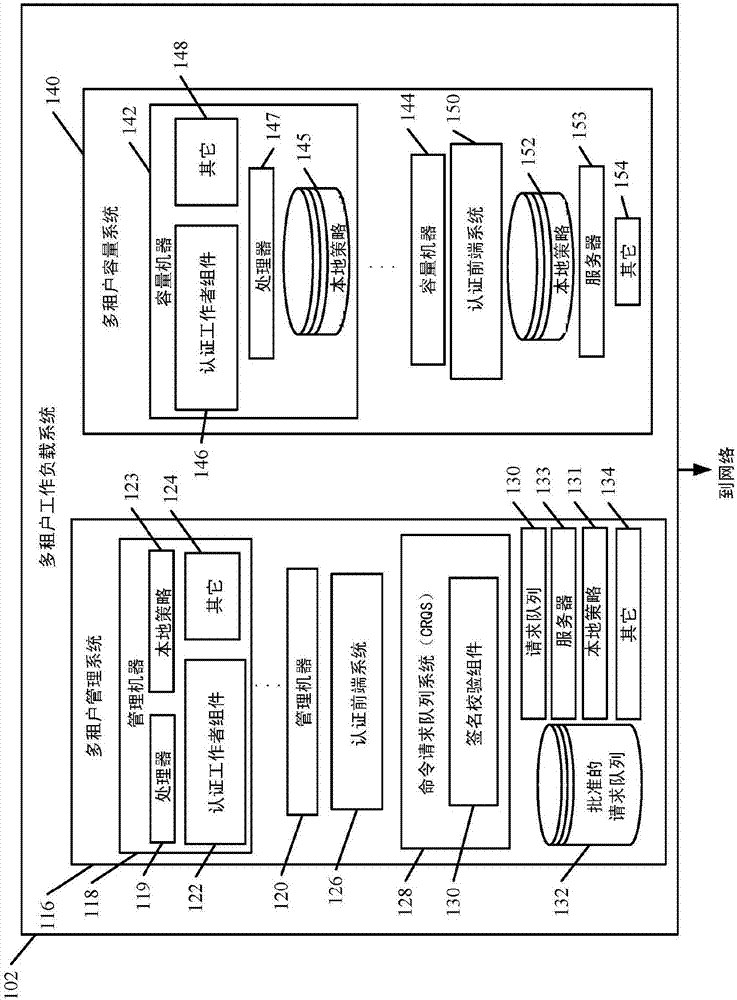
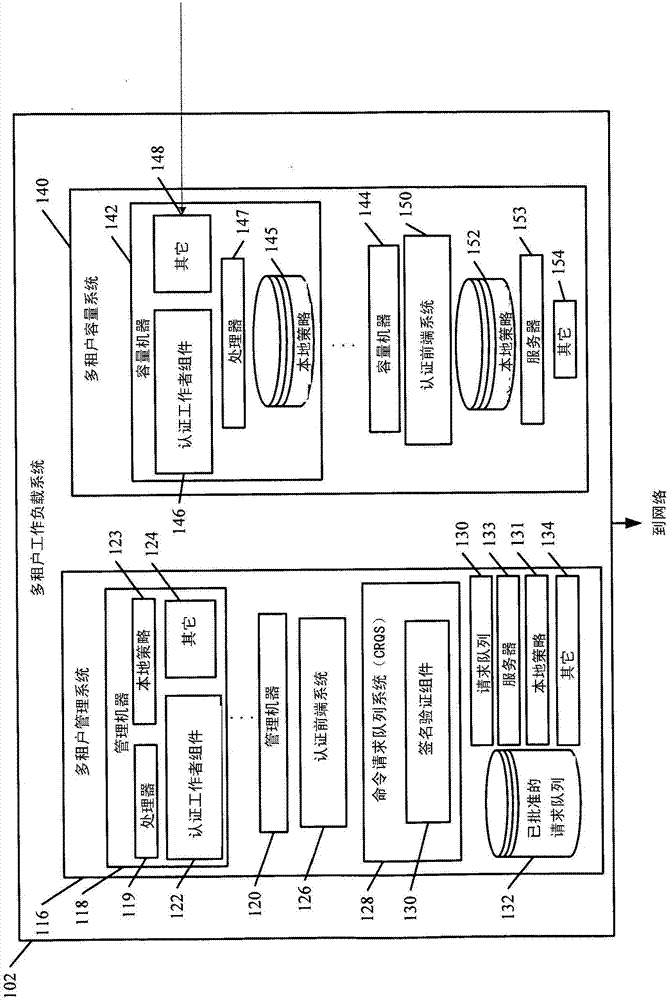
Security and permission architecture in a multi-tenant computing system
When a user inputs an action request, such as a requested command, to be performed on a target machine, a management system receives the request and verifies it with a separate authentication and permission system. The verified command request is sent to the target machine. An authentication worker on the target machine accesses a set of policies, local to the target machine, to identify a least privileged execution environment in which the requested command can be performed. The authentication worker on the target machine launches the requested command within the identified least privileged execution environment on the target machine.
Owner:MICROSOFT TECH LICENSING LLC
Routing method and device for database cluster
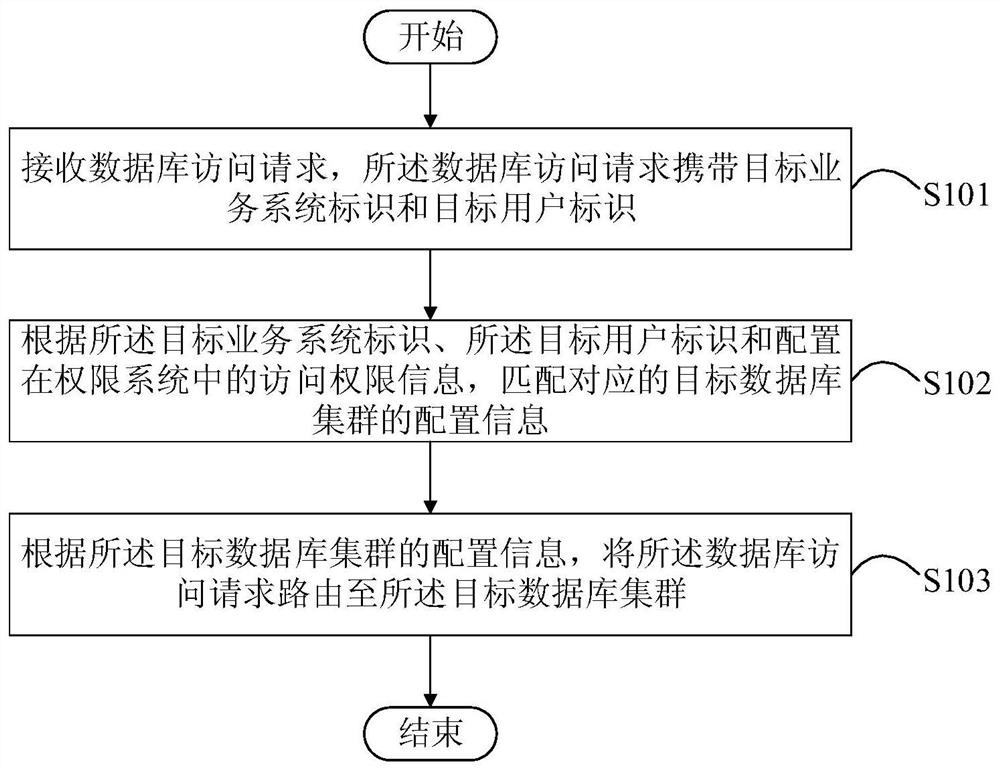
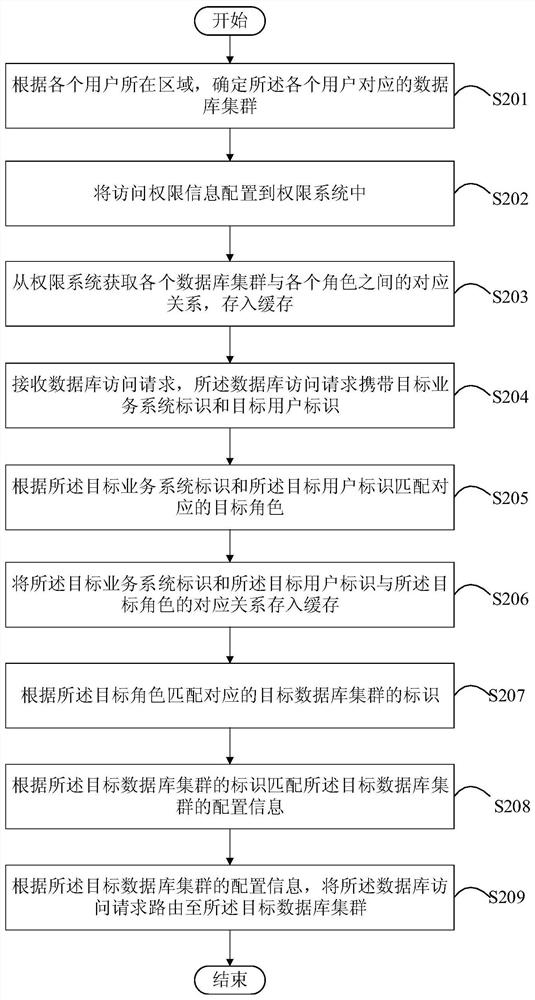
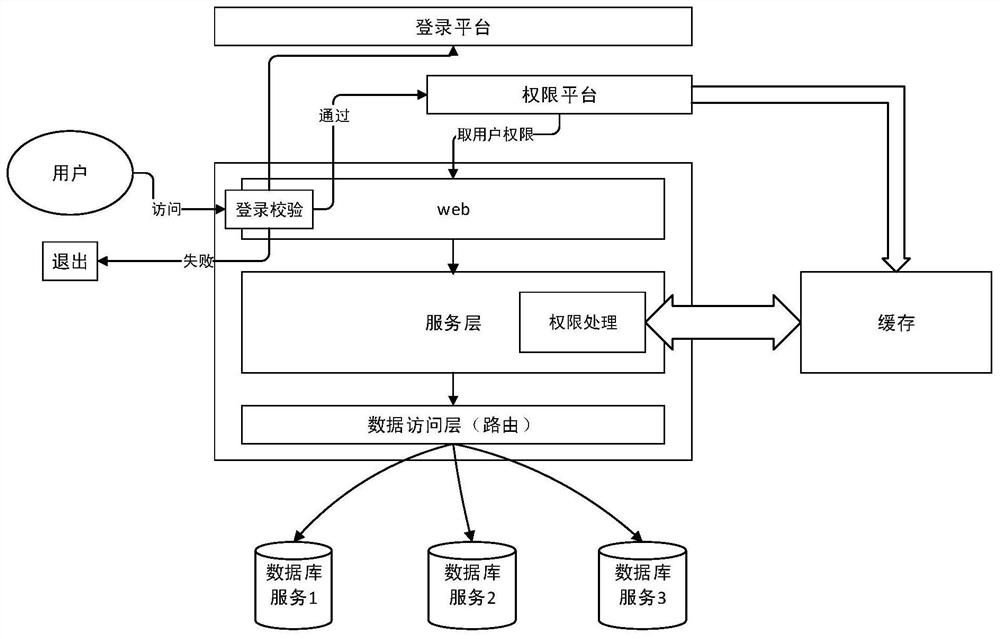
PendingCN113495921AOvercome resourcesOvercome costsDatabase distribution/replicationDigital data protectionPermission systemEngineering
The invention discloses a routing method and device for a database cluster, and relates to the technical field of computers. A specific embodiment of the method comprises the following steps: receiving a database access request, wherein the database access request carries a target business system identifier and a target user identifier; matching configuration information of a corresponding target database cluster according to the target service system identifier, the target user identifier and access permission information configured in a permission system; and routing the database access request to the target database cluster according to the configuration information of the target database cluster. According to the embodiment, the technical problems that server resources are wasted, the maintenance cost is high or the service operation invasiveness is large can be solved.
Owner:BEIJING JINGDONG ZHENSHI INFORMATION TECH CO LTD
Method and device for determining setting rationality of permission system
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
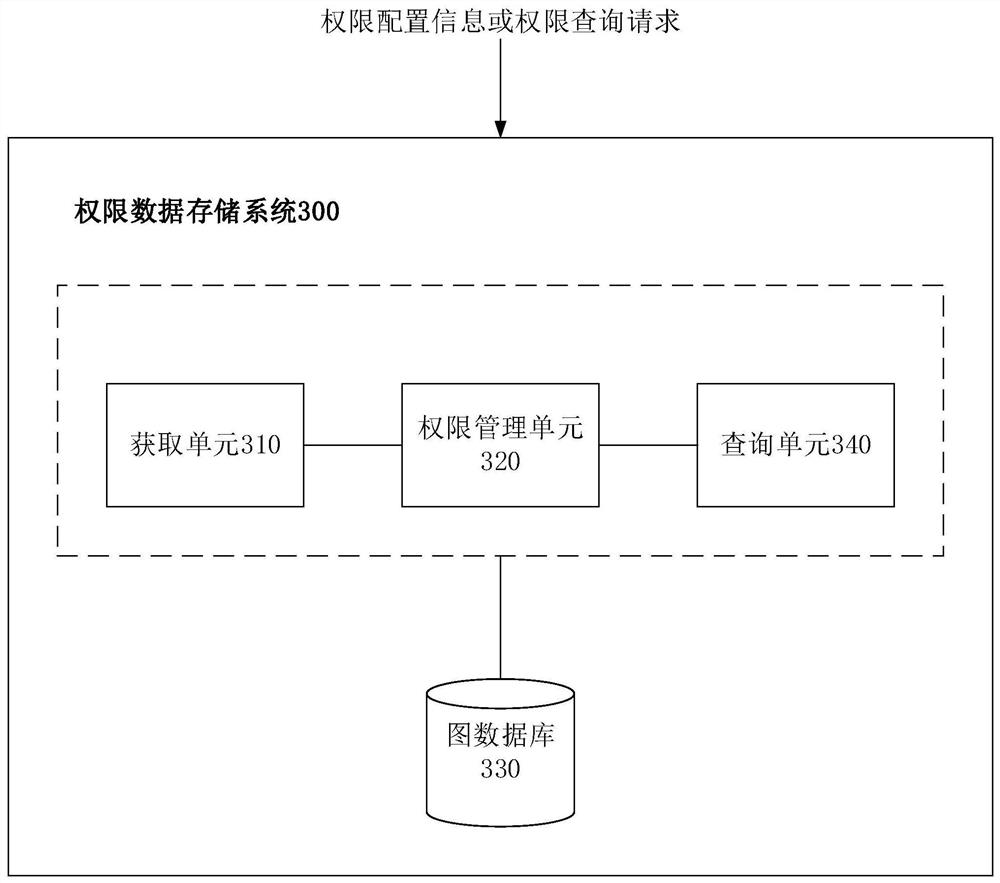
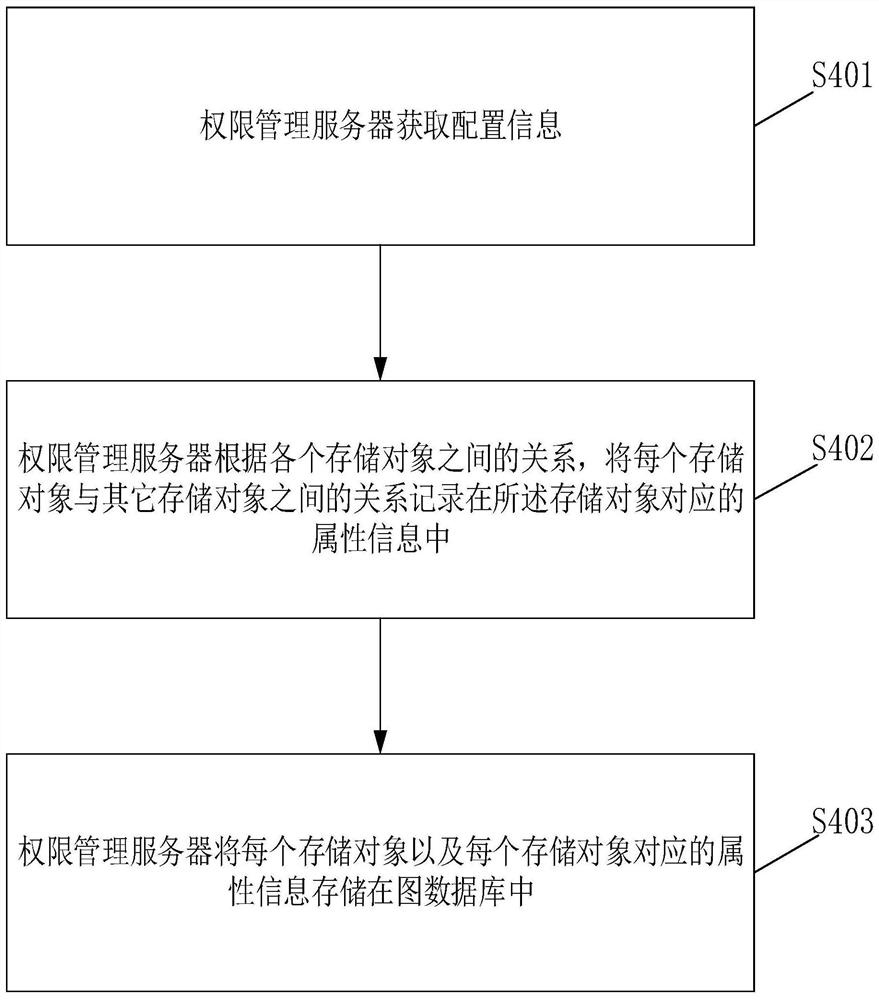
Permission system data storage method and related equipment
PendingCN113127848ADigital data protectionDigital data authenticationInformation resourceResource information
The invention provides a permission system data storage method and related equipment. The method comprises the steps that an authority management server obtains authority configuration information, and the authority configuration information comprises directional relations between storage objects; the method also includes recording the relationship between each storage object and other storage objects in attribute information corresponding to the storage object; storing each storage object and the attribute information corresponding to the storage object in a graph database, wherein the storage object comprises resource information, permission information and role information of the permission system, the resource information comprises permission system data, the permission information comprises operation executed on the resource information, and the role information comprises roles with permissions corresponding to the permission information. The method can improve the authority query efficiency and shorten the authority query time.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Security and permission architecture in a multi-tenant computing system
When a user inputs an action request, such as a requested command, to be performed on a target machine, a management system receives the request and verifies it with a separate authentication and permission system. The authentication and permission system verifies signatures on the request and signs it and generates an approved workflow package. The approved workflow package is sent to the target machine.
Owner:MICROSOFT TECH LICENSING LLC
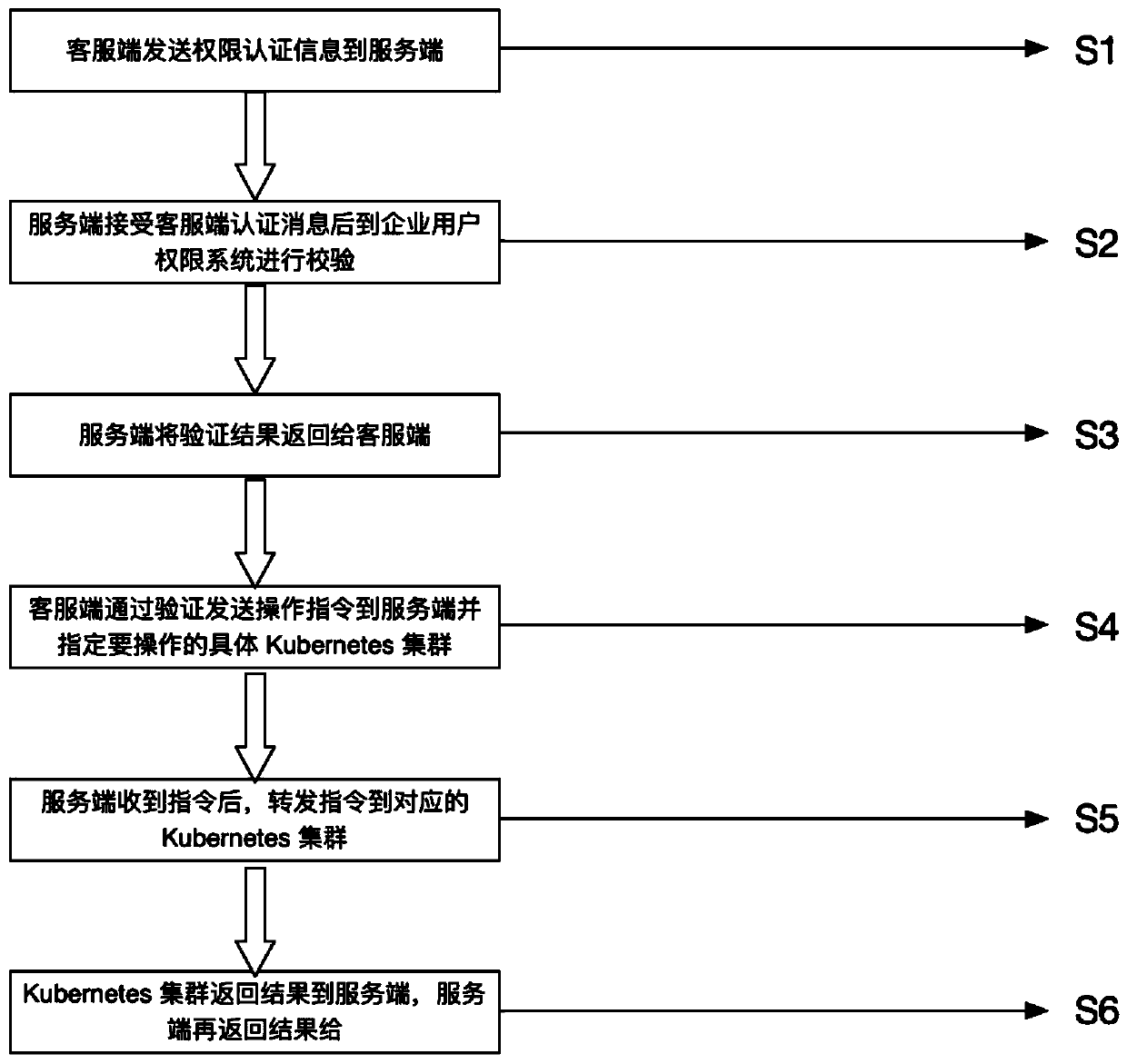
System for managing multi-Kubernetes cluster based on multiple users of enterprise
The invention discloses a system for managing a multi-kubernetes cluster based on multiple users of an enterprise. A client where a user is located sends authority authentication information to a server where a system is located; after the server where the system is located receives the authority authentication information sent by the client, the verification is performed through an enterprise user permission system; the enterprise user permission system of the server completes verification and allows the client to send an instruction to the server, and specifies a specific kubernetes clusterto be operated; the system forwards the operation instruction to the corresponding kubernetes cluster after receiving the operation instruction, and the kubernetes cluster processes the instruction, feeds back a result to the server side and feeds back the result to the client side where the user is located. Under the condition of the technical scheme, an enterprise can be helped to easily and quickly manage a plurality of kubernetes clusters and operating cloud service containers thereof in a production environment, and existing third-party public container cloud services can also be accessed, so that the enterprise can quickly expand the capacity during great promotion, and the operation cost is saved.
Owner:重庆天蓬网络有限公司
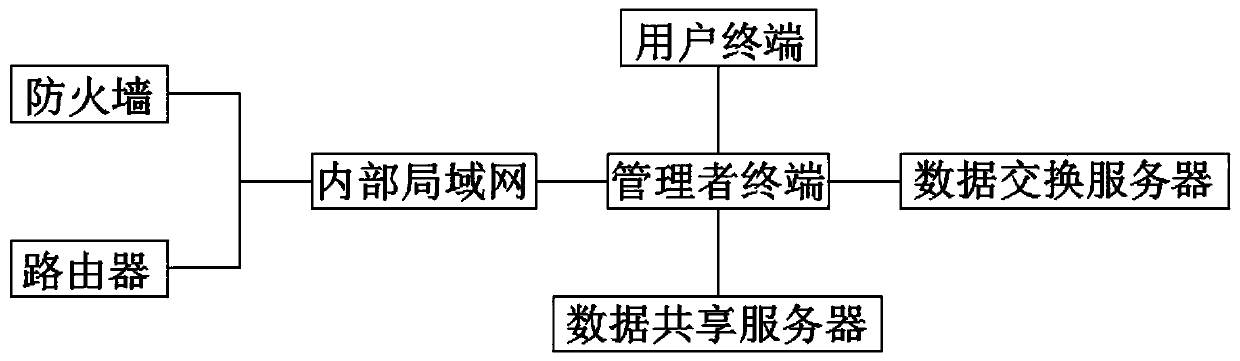
Authority system login access control method
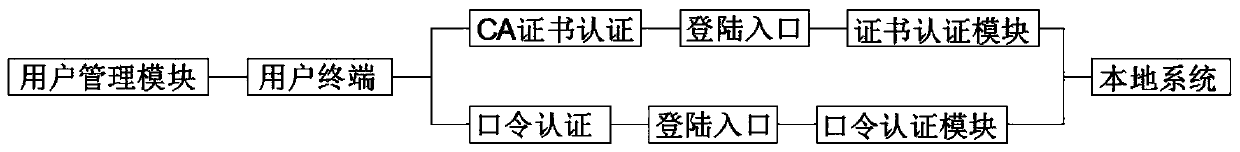
InactiveCN110598388AEasy loginEasy to operateDigital data authenticationThird partyPermission system
The invention discloses an authority system login access control method. The method comprises a manager terminal and a user management module. The manager terminal is connected with an internal localarea network. The internal local area network is respectively connected with the firewall and the router. The manager terminal is further connected with the user terminal, the data sharing server andthe data exchange server. The user management module is connected with a user terminal. The user terminal enters the login entrance through CA certificate authentication. The login entrance logs in the body system through the certificate authentication module. The user terminal can enter the login entrance through password authentication. The login entrance logs in the body system through the password authentication module. According to the invention, CA certificate authentication and password authentication are utilized to facilitate login of a user permission system; the security of the system is improved, the operation efficiency of the system is improved through setting of a third party, an illegal user, a common user and an administrator user in the user management module, and the control method is simple, convenient to operate and capable of facilitating rapid login of the user and control of access permission.
Owner:达疆网络科技(上海)有限公司
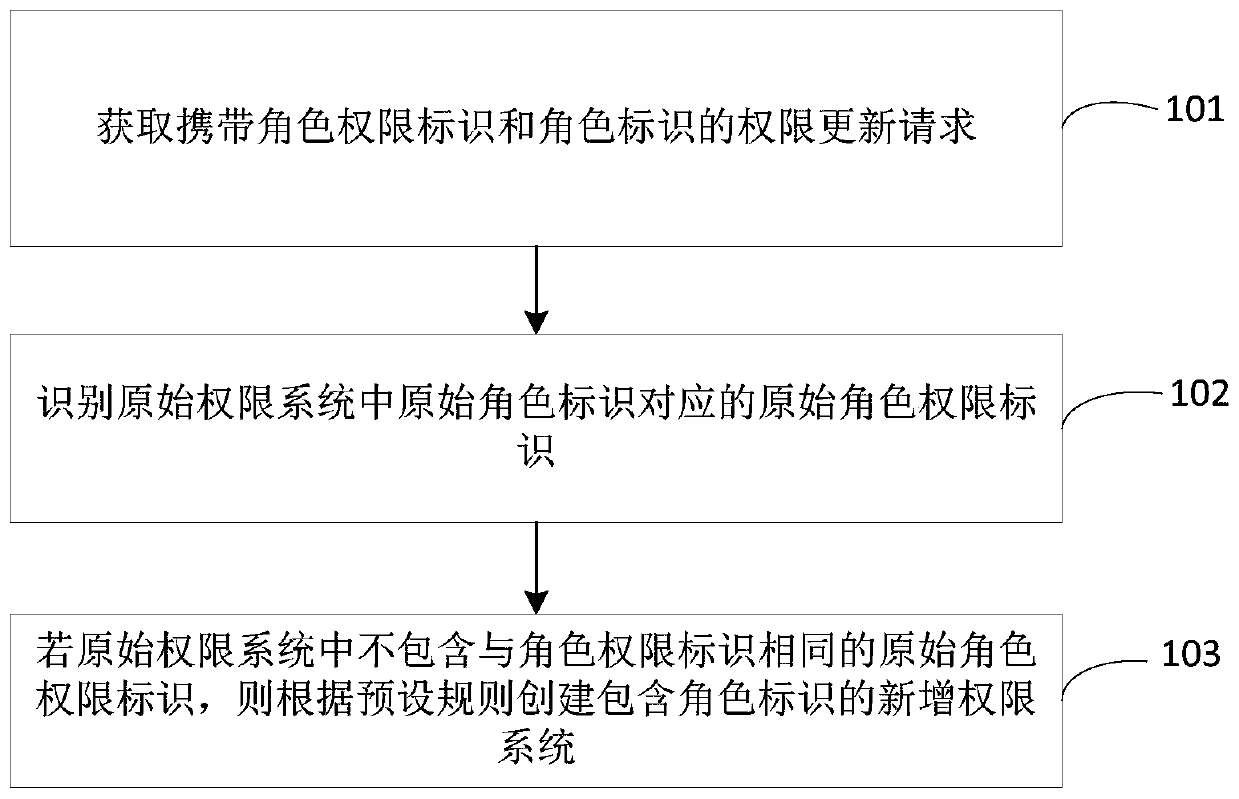
Role permission setting method and device
The invention provides a role permission setting method and device, and belongs to the technical field of computers, and the method comprises the steps: obtaining a permission updating request carrying a role permission identifier and a role identifier; identifying an original role permission identifier corresponding to the original role identifier in the original permission system; and when the original permission system does not contain the original role permission identifier which is completely the same as the role permission identifier, creating a newly-added permission system containing the role identifier according to a preset rule, wherein the role identifier in the newly-added permission system has a role permission corresponding to the role permission identifier. Therefore, a flexible role permission setting method is provided, and when the role permission changes, the original role permission is not covered, and a new role permission service can be provided.
Owner:HANGZHOU DT DREAM TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com