Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
94results about How to "Implement permission control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
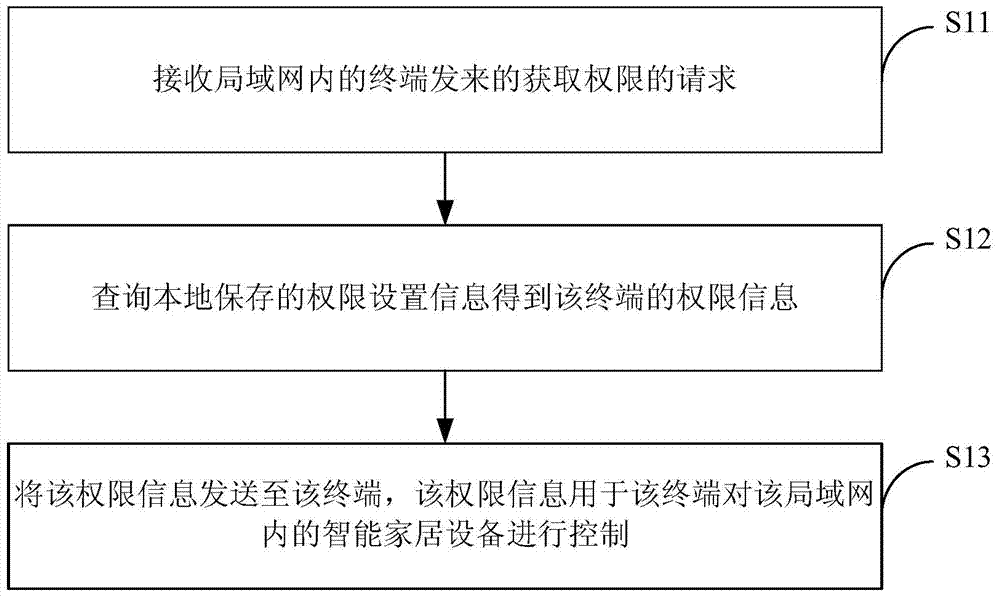
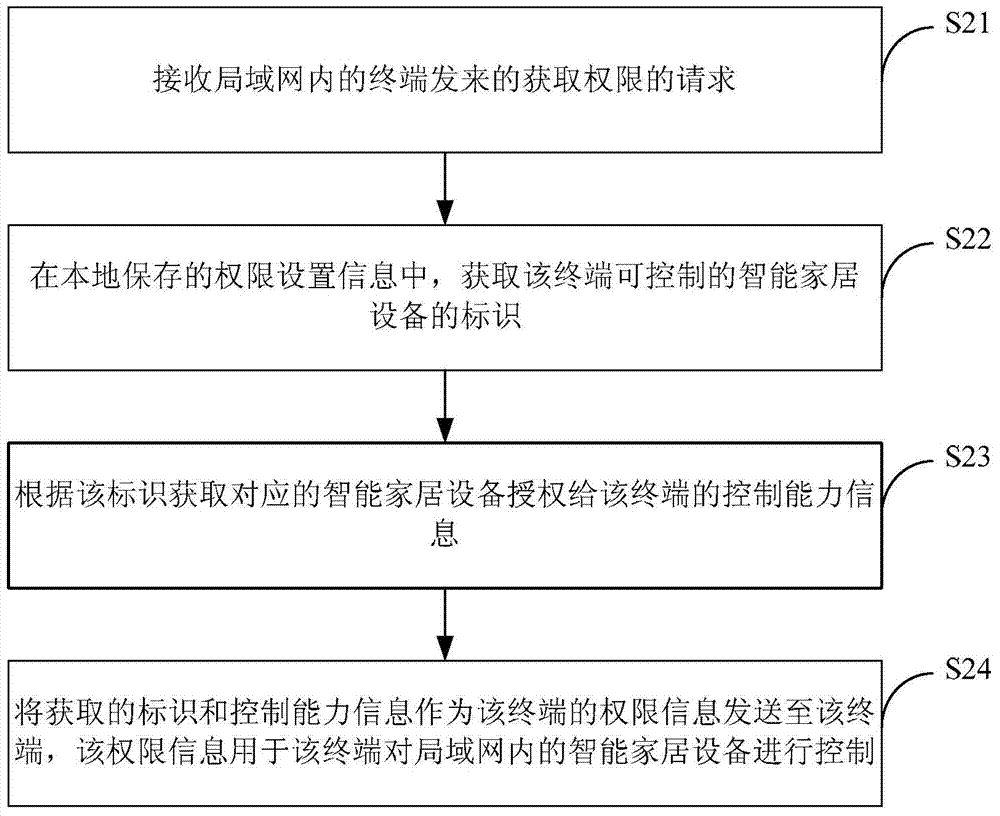
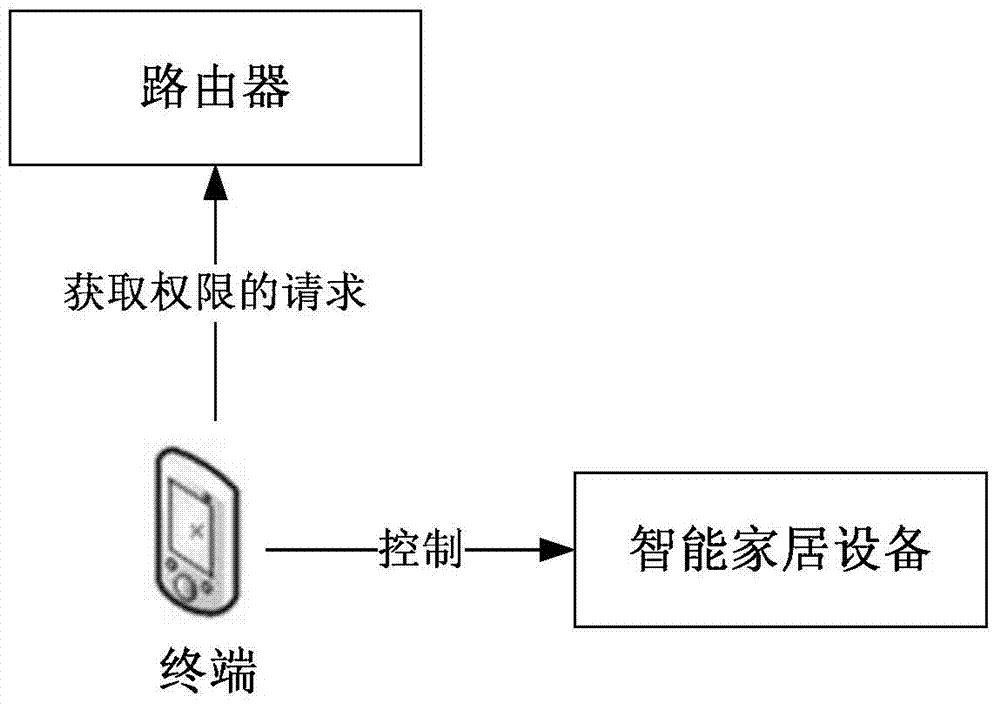
Method, device and system for controlling intelligent household equipment
InactiveCN104283745AImplement permission controlImprove intelligenceData switching by path configurationProgramme total factory controlComputer terminalComputer science
The invention relates to a method, device and system for controlling intelligent household equipment, and belongs to the field of controlling of the intelligent household equipment. The method includes the steps of receiving a request for obtaining a right sent from a terminal in a local area network, inquiring right setting information stored locally to obtain right information of the terminal and sending the right information to the terminal, wherein the right information is used for the terminal to control the intelligent household equipment in the local area network. The device comprises a receiving module, an inquiry module and a sending module. The system comprises a router and the terminal. By means of the method, device and system for controlling the intelligent household equipment, right control over the intelligent household equipment is achieved, and controlling intelligentization of the intelligent household equipment is greatly improved.
Owner:XIAOMI INC
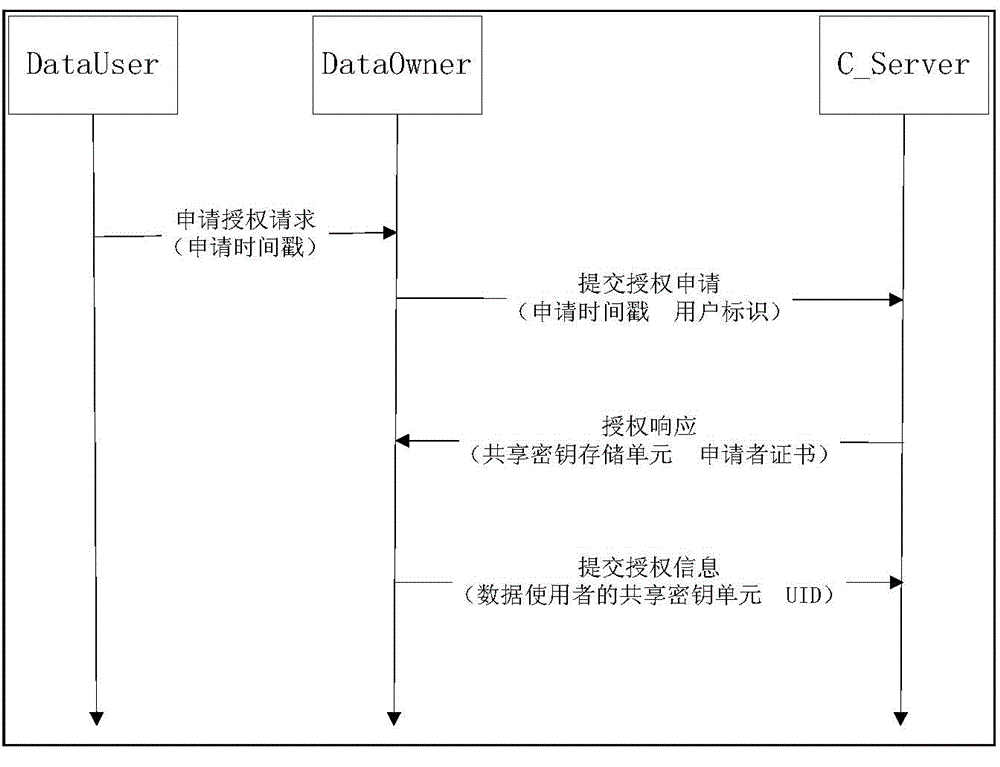
Data access control method and system in cloud storage environment
ActiveCN104980477AGuaranteed confidentialityIntegrity guaranteedTransmissionSpecial data processing applicationsConfidentialityData access control
Embodiments of the invention provide a data access control method and system in a cloud storage environment. The method mainly comprises the steps that a user registers personal information to a cloud server through a client side; when a data owner determines that the data to be transmitted to the cloud server is shared data, the client side of the data owner uses a symmetric key to encrypt the data, and sends the encrypted data, the symmetrical key, a hash operation result of the data and a shared attribute of the data to the cloud server; when the data is not the shared data, the client side of the data owner uses its own public key to encrypt the data, and sends the encrypted data, the hash operation result of the data and the shared attribute of the data to the cloud server. Through adoption of the method and system, confidentiality and integrity of the user data are guaranteed, and confidentiality of the user files is classified, so that authority control under data sharing is better realized, and security improvement of data access control under cloud storage is effectively provided.
Owner:黑龙江航天信息有限公司
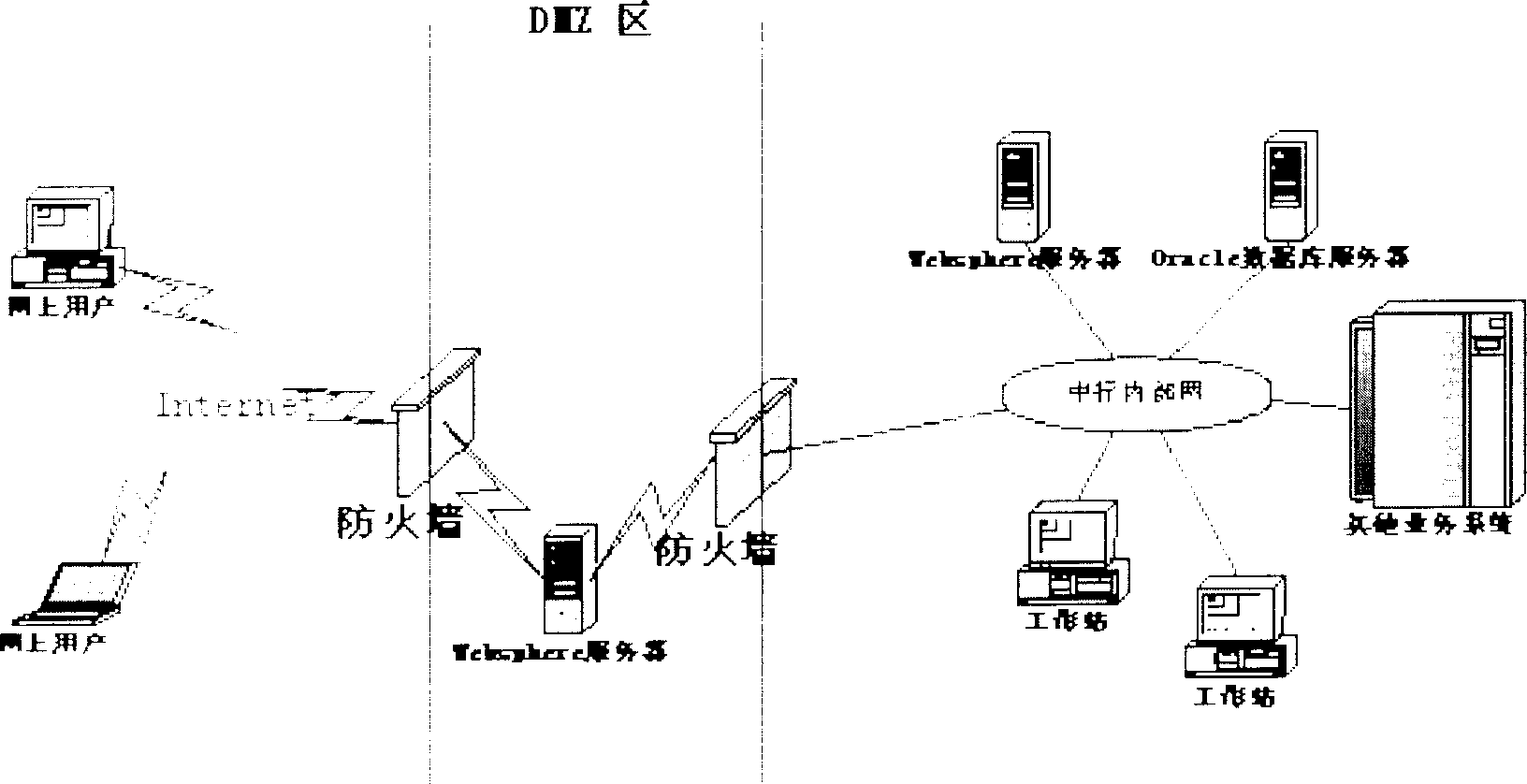
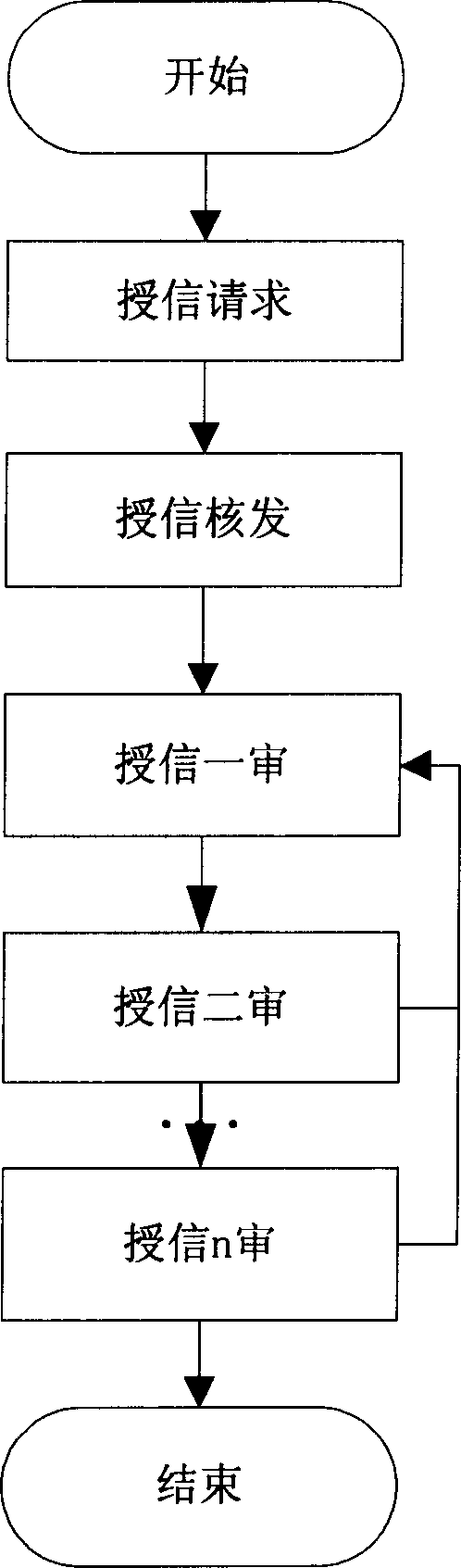
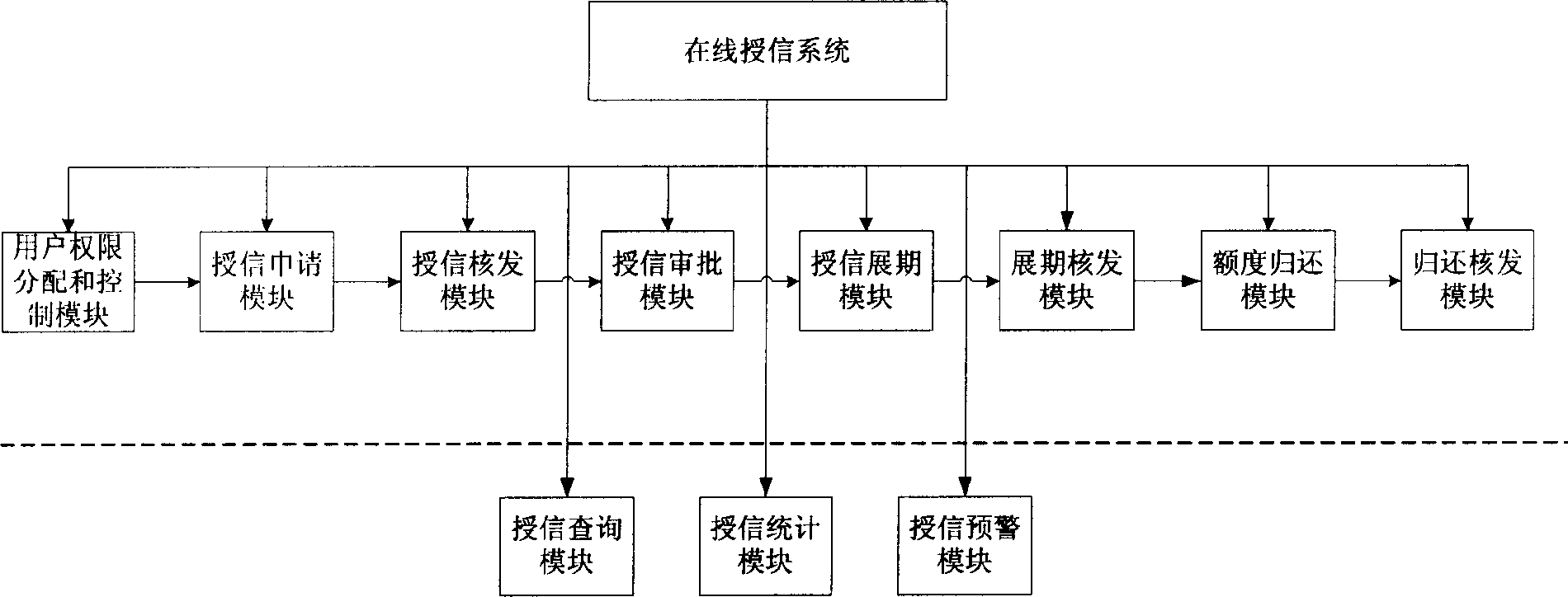
System and method for online user authorization for banks
A system of granting credit to the client on line by financial enterprise comprises user power distribution and control module, credit application module, credit checking and issuing module, credit approval module, credit extending module, extension period approval module, ceiling return module, return back checking and issuing module, credit inquiry module, credit statistic analysing module and credit prewarning module. The system can be used as control system of credit approval operation within financial enterprises.
Owner:BANK OF CHINA
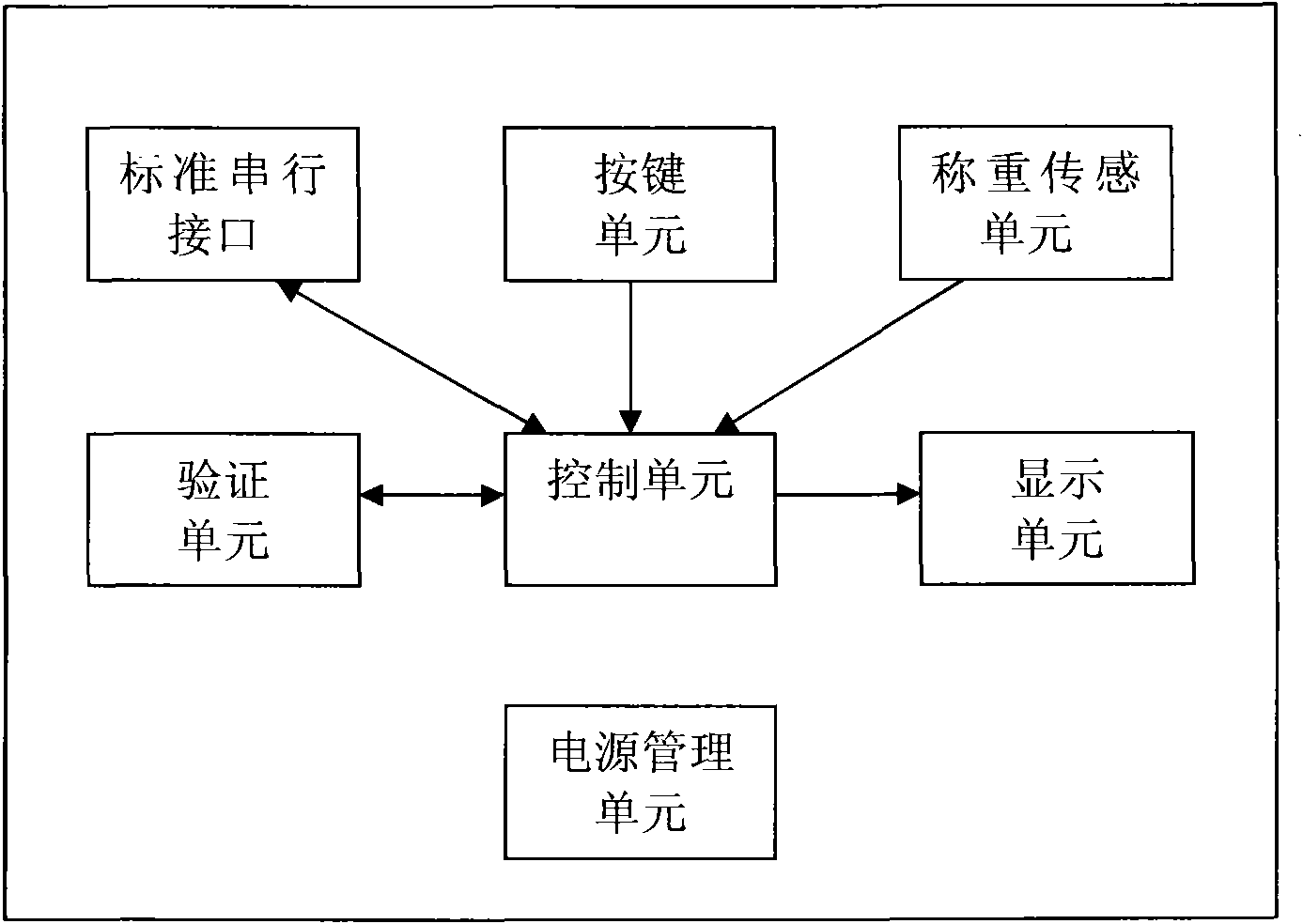
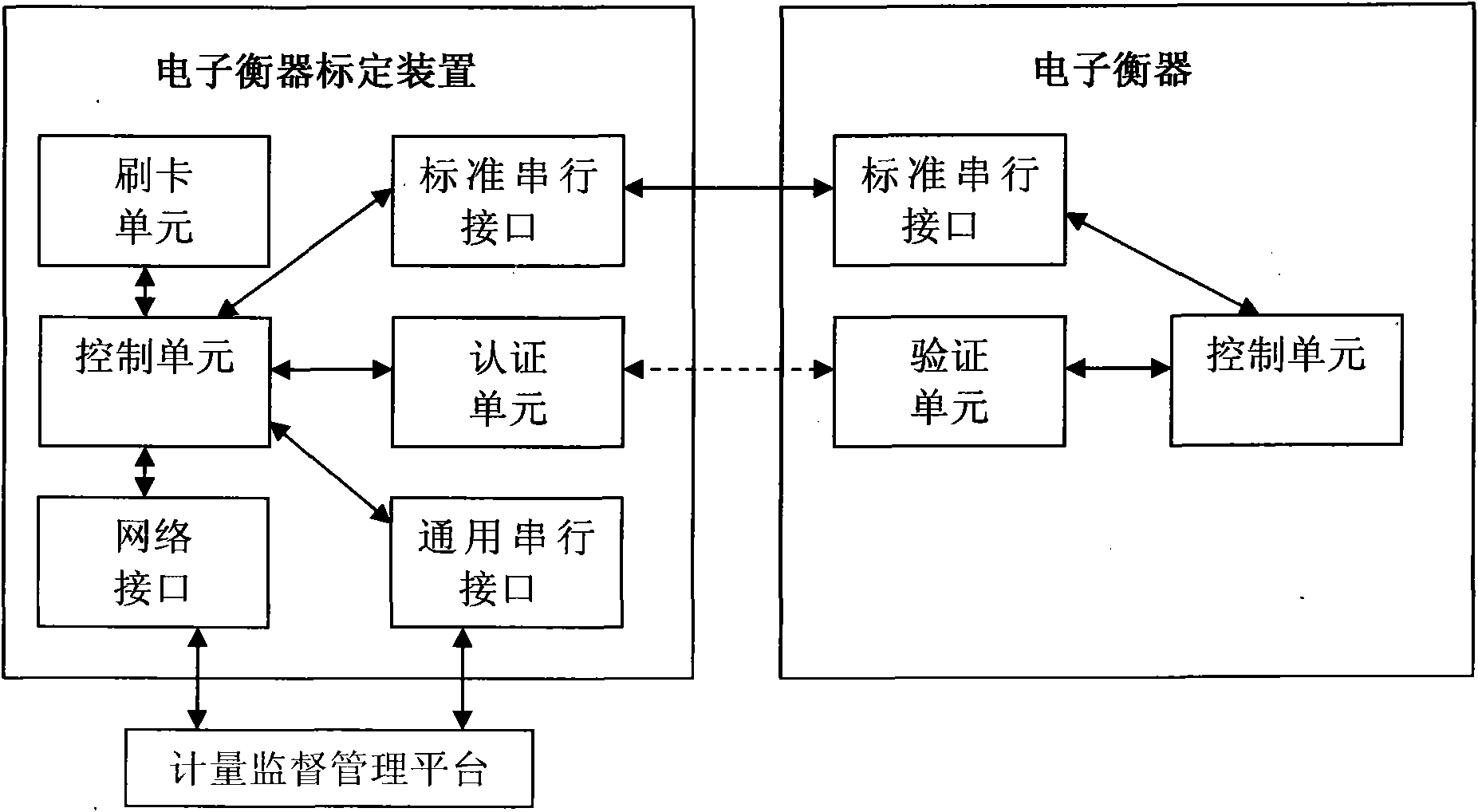
Cheating prevention electronic weighing apparatus calibrating system and method
ActiveCN101806613APrevent illegal calibrationImprove safety and reliabilityWeighing apparatus testing/calibrationSensing record carriersEngineeringCheating prevention
The invention relates to cheating prevention electronic weighing apparatus calibrating system and method. The calibrating system comprises an electronic weighing apparatus, an electronic weighing apparatus calibrating device and a metering supervisory management platform, wherein the metering supervisory management platform comprises an electronic weighing apparatus, a calibrating device, databases comprising various identity information and operating information of a calibrating staff and a computer or a server for carrying the databases, and establishes direct or indirect data communication link by a network and the calibrating device. The system is provided with a card swiping unit and an authenticating unit, a calibrating mode of the traditional electronic weighing apparatus can be changed, the calibrating operation is transmitted to the calibrating device to be carried out so as to ensure the electronic weighing apparatus can not independently finish the calibrating program, which enhances the safety and reliability of calibration and effectively prevents illegal calibration, thereby effectively preventing a behavior for cheating on the electronic weighing apparatus by the illegal calibration on the electronic weighing apparatus.
Owner:CHENGDU JIUZHOU ELECTRONIC INFORMATION SYSTEM CO LTD
Workflow frame based user-defined permission flow method and system
ActiveCN105046446AMeet permission control requirementsAvoid secondary developmentResourcesFrame basedWork flow
The present invention discloses a workflow frame based user-defined permission flow method and a system. The method comprises the steps of: receiving a request initiating a review flow from a client, parsing out at least one user-defined permission data from the request initiating the review flow, calling a workflow frame to initiate a review task flow, acquiring a task identifier of the review task flow returned by the workflow frame, and storing the task identifier and all the user-defined permission data associated with the request initiating the review flow as correlations; and receiving a query task request from the client, enabling the user-defined permission data in the correlations to meet user-defined roles, taking the task identifier for a corresponding task to flow to a user workflow frame role in the workflow frame as a to-be-queried task identifier, and returning the to-be-queried task identifier to the client. By adopting the workflow frame based user-defined permission flow method, while work flow control of the existing workflow frame is used, user-defined permission control is realized, and complex and changeable permission control requirements can be met.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
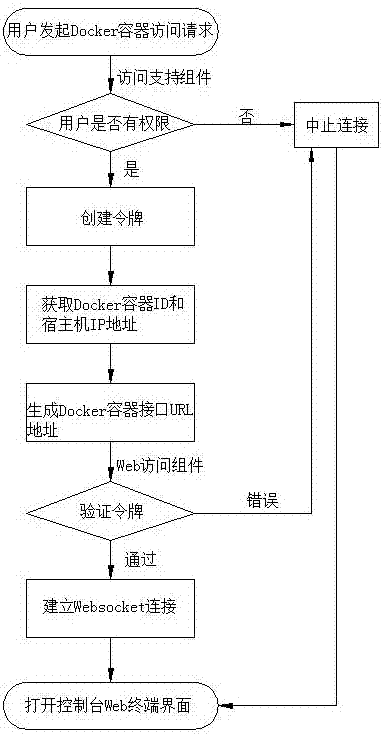
Method and system of Web for accessing Docker container
ActiveCN107493344AImplement permission controlConvenient and flexible accessTransmissionUser PrivilegeWebSocket
The invention discloses a method and a system of a Web for accessing a Docker container, and belongs to the technical field of cloud computing. The technical problems needing to be solved are that an independent SSH service for remote login and access still needs to be built for the Web to access the Docker container remotely, configuration of parameters such as a user name and a password is needed, and the remote access process is tedious. By adoption of the technical scheme, the method comprises the steps of finding a to-be-accessed Docker container at a Web page and initiating an access request by a user; judging user authority by an access support assembly; if the user has the authority, building a token for Docker container access and returning the token to the user; by the access support assembly, obtaining the ID of the Docker container and the IP address of a host machine where the Docker container is, and generating an URL address of the Docker container interface; verifying the token by a Web access assembly, and building Websocket connection through the URL address of the Docker container interface if the token passes the verification; and opening the Web page containing a console terminal of the Docker container through the Web access assembly. The method and the system of the Web for accessing the Docker container can still realize authority control on Docker container access without enabling an sshd course.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Method for customizing role authorization in management information system
InactiveCN102402663AEasy to controlGuaranteed reliabilityDigital data authenticationManagement information baseRights management
The invention provides a method for customizing role authorization in a management information system. By the method, the control of fine grit authorization is realized at the level of specific certain operation or even a certain event, the problem about the customization of role authorization in the management information system is solved; when the method is used in the management information system, the customization of role authorization can be conveniently realized and the management of customized authorization is realized, and the method can be effectively applied in both coarse grit authorization and the fine grit authorization aspects, so the universality and the high reliability of an authorization management range are ensured and customized role authorization is conveniently and effectively controlled.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Home network multimedia content sharing access control method and device
InactiveCN104683320AImplement permission controlSelective content distributionData switching networksContent sharingClient-side
Disclosed is an access control method for sharing multimedia content in a home network. The method comprises the following steps: receiving an access request sent by a client device; judging whether the client device has access permission, and if the client device has the access permission, displaying to the client device a catalogue and content that corresponds to the permission, and permitting the client device to access the catalogue and content. Also disclosed is an access control device for sharing multimedia content in a home network. The present invention effectively solves the permission control problem when a DLNA device conducts sharing, including the authentication of the device access permission, and the access permission control of whether the public and non-public catalogues / contents of shared content is visible to different users.
Owner:ZTE CORP
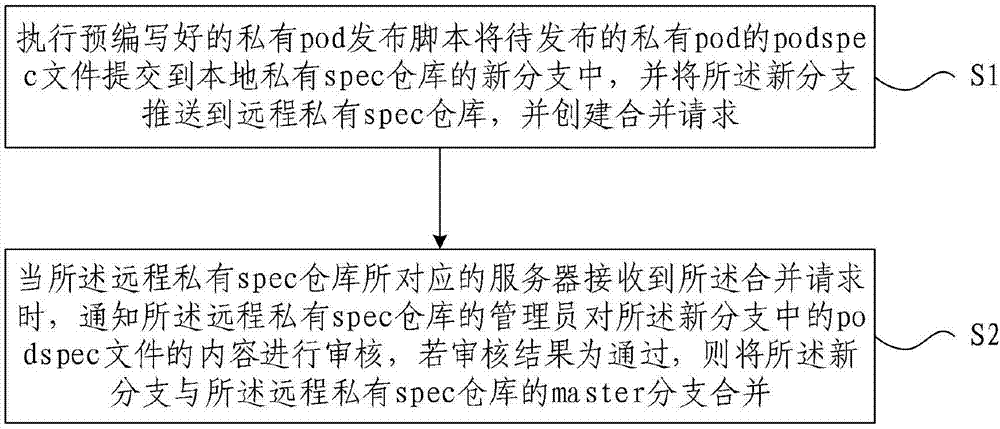
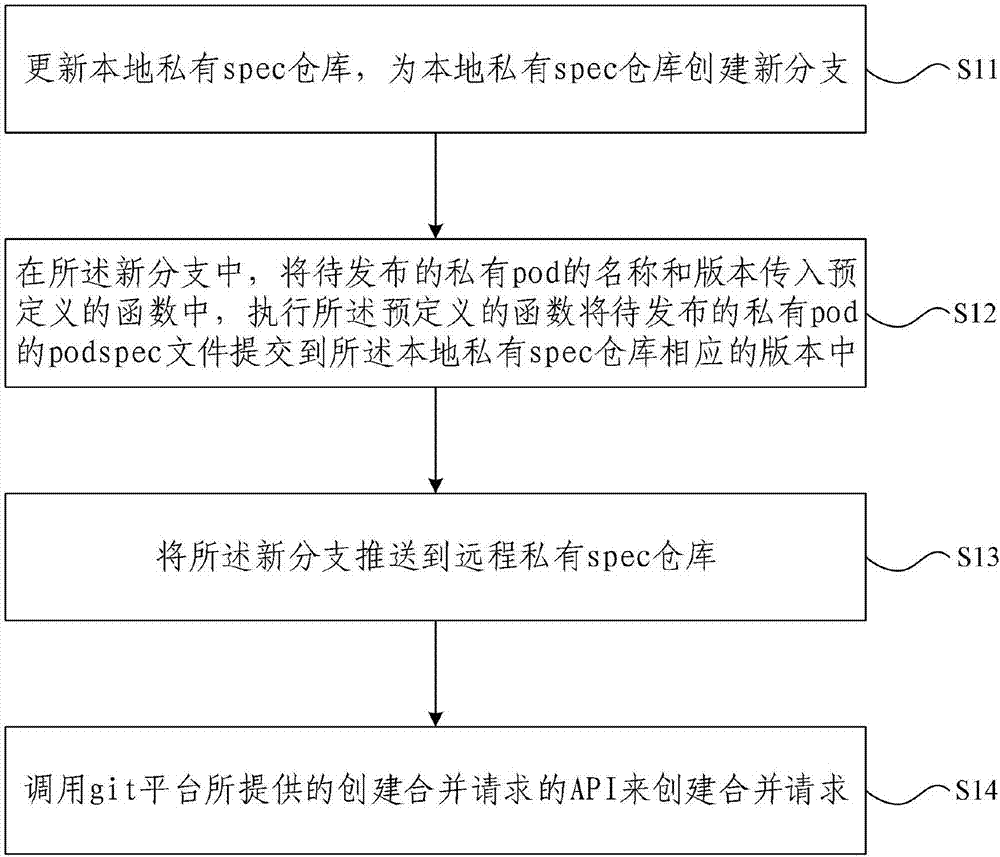
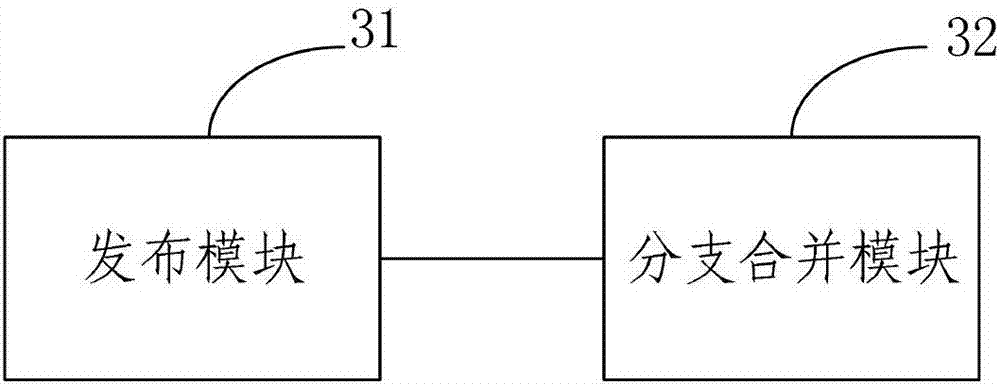
Private pod release permission control implementation method and device
ActiveCN107391968AImplement permission controlReduce communication costsSoftware designProgram/content distribution protectionOperating system
The invention provides a private pod release permission control implementation method and device. The method includes: S1, executing a pre-written private pod release script to submit a podspec file of a to-be-released private pod into a new branch of a local private spec repository, pushing the new branch to a remote private spec repository, and creating a merging request; S2, when a server corresponding to the remote private spec repository receives the merging request, informing a manager of the remote private spec repository of checking of podspec file content in the new branch; if the checking is passed, merging the new branch with a master branch of the remote private spec repository. The private pod release permission control implementation method and device have the advantage that permission control of a private pod release process can be realized conveniently without increasing cost of communication between the manager of the spec repository and developers.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Identity identification method and device
InactiveCN106339624AImplement permission controlDigital data authenticationPattern recognitionComputer terminal
The embodiment of the invention discloses an identity identification method and an identity identification device, and relates to the technical field of electronic equipment application. The method comprises the steps: acquiring fingerprint information which is input into a fingerprint identification region of a terminal by a user; identifying the fingerprint input area according to the fingerprint information; and identifying the type of the user who inputs the fingerprint according to the fingerprint input area. According to the embodiment of the invention, the terminal can identify the type of the user, so that right control can be realized according to the type of the user.
Owner:LETV HLDG BEIJING CO LTD +1
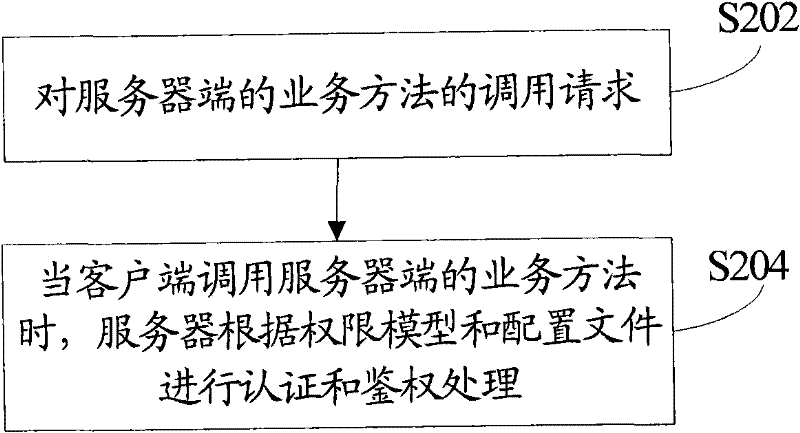
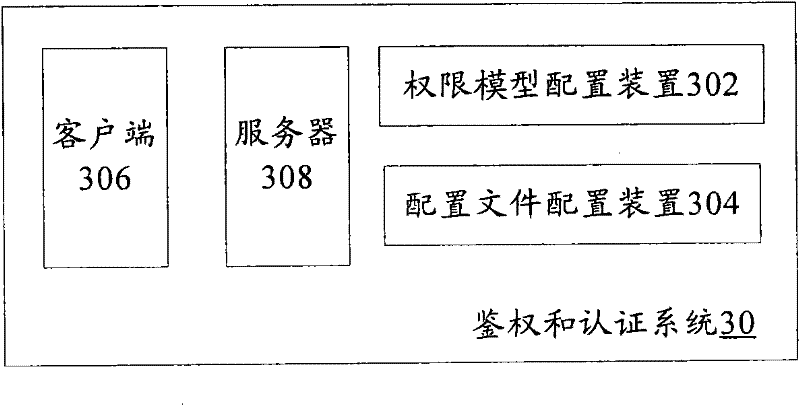
Authentication and certification method and system
The invention discloses an authentication and certification method and system. The authentication and certification method comprises the following steps that: an authority model and configuration files are configured in advance, wherein the authority model is used for defining authority data storage; and when a client end calls the service method of a server end, the server performs certification and authentication according to the authority model and the configuration files. The technical scheme of the invention can support fine grain authority control, and simultaneously can realize pluggable authority control in an aspect oriented programming (AOP) mode at the server end.
Owner:DATANG MOBILE COMM EQUIP CO LTD +1
Account system setting method and system, computer device and storage medium
ActiveCN109325359AAvoid excessiveGuaranteed relevanceFinanceDigital data protectionRoot certificatePassword
The invention relates to the field of account management, in particular to an account system setting method and system, a computer device and a storage medium. The method comprises: setting up a distributed fabric network structure, invoking the password original cryptogen utility, generating the certificate and key, generating a primary user after the super administrator certificate is bound to the first user, wherein the primary user has the new service permission, the query service permission and the permission to create the secondary user; calling the root certificate to issue the user certificate, and binding the user certificate with the user to generate the secondary user, wherein the secondary user has the new service permission and the query service permission. The Fabric networkstructure of the invention provides policy services such as identity service, access control, authorization management and the like for the block chain network, wherein the secondary users can be registered and registered by the primary users, which ensures the relevance between the users. The secondary users can further refine the functions to avoid the excessive exposure of the primary users, realize the control of the account authority, and ensure the security of the account.
Owner:PING AN TECH (SHENZHEN) CO LTD
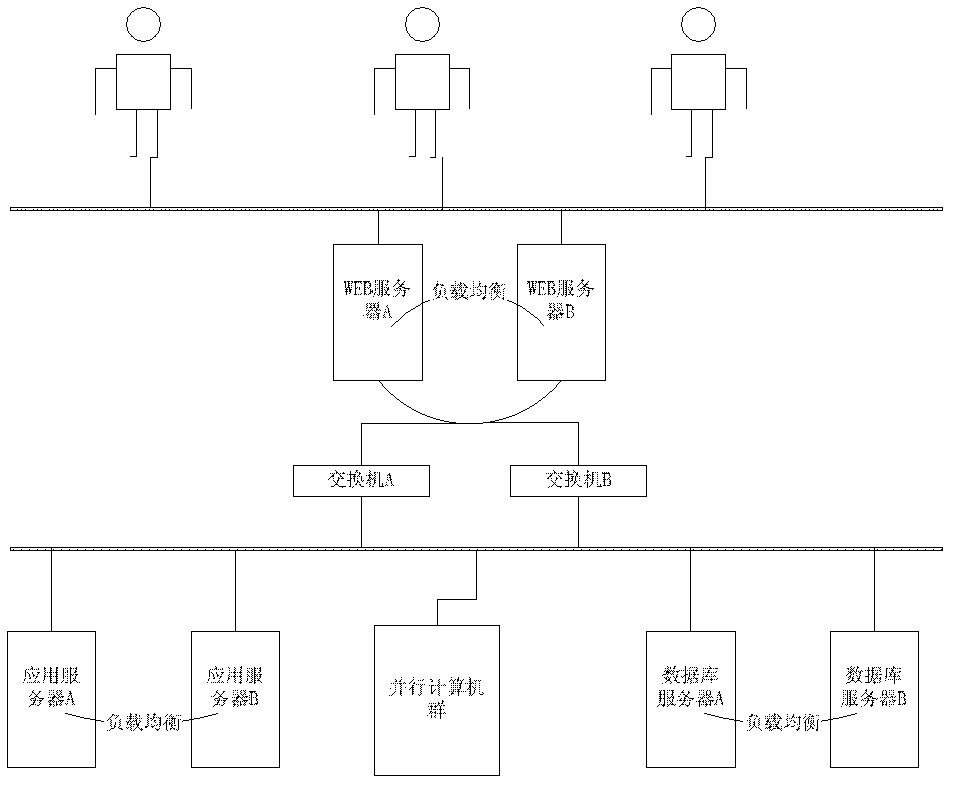
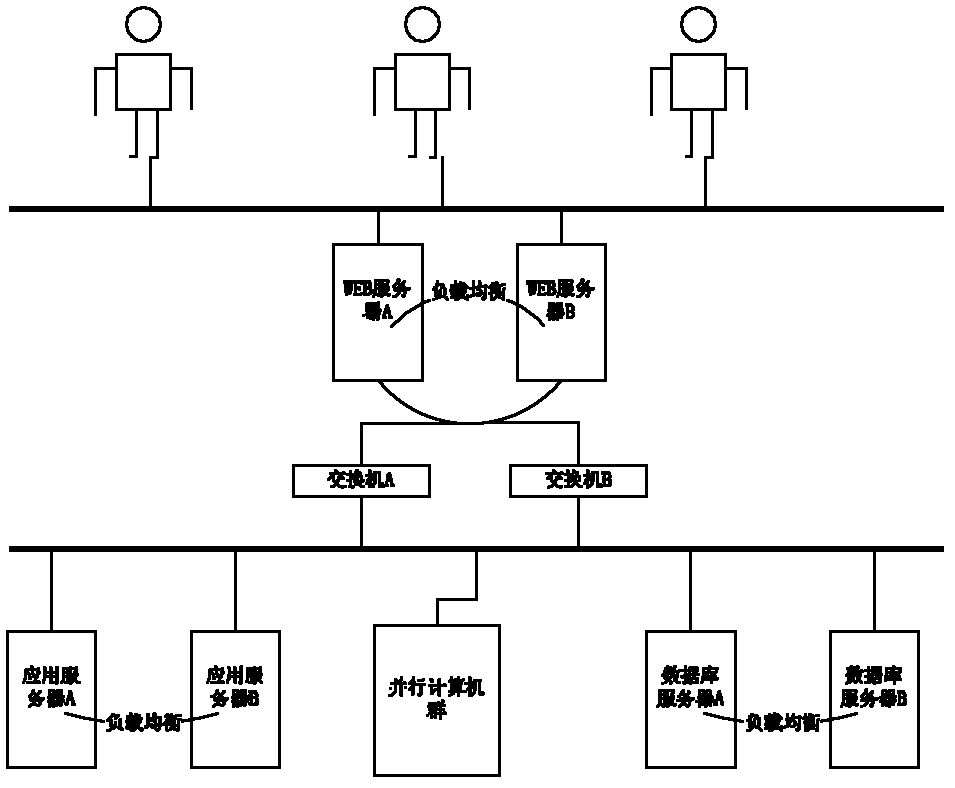
Multi-user remote parallel computation system
ActiveCN102646223ASolve the conflict problem of concurrent operationImplement permission controlResourcesTransmissionWeb servicePower system scheduling
The invention belongs to the field of power systems, and particularly relates to a multi-user remote parallel computation system. The multi-user remote parallel computation system comprises a WEB server, an application server, a database server, a parallel computer group and network connection switching equipment, wherein the WEB server, the application server, the database server and the parallel computer group are respectively connected with the network connection switching equipment. According to the technical scheme provided by the invention, the design scheme that the software system adopts 'concentrated storage, data sharing, remote maintenance, cooperation and component integration' as the predominant idea while meeting the requirements of 'practicability, modularization, integrity and expandability' is determined, and the requirements of the mode calculation of the power system on functions and performances of a computer software system and the need for relatively flexible updating and maintenance of the system are comprehensively considered. According to the multi-user remote parallel computation system provided by the utility model, the reliability and the mode calculation working efficiency of power grid data are comprehensively improved.
Owner:CHINA ELECTRIC POWER RES INST +1
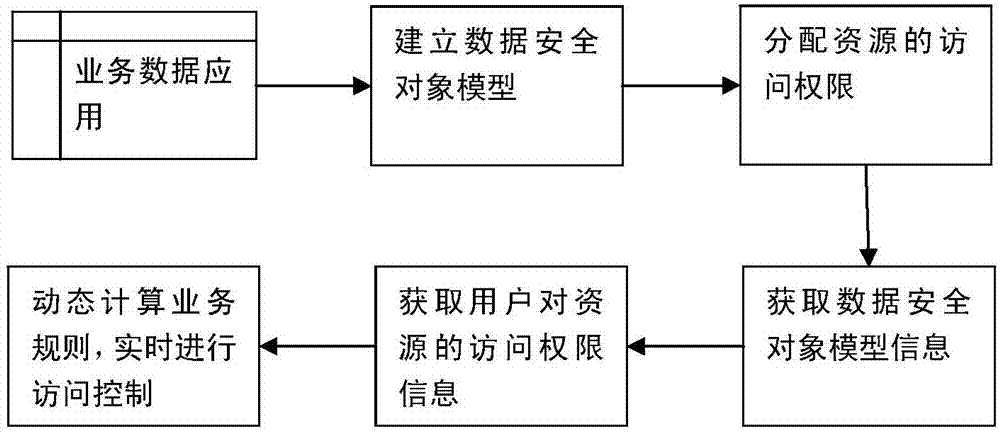
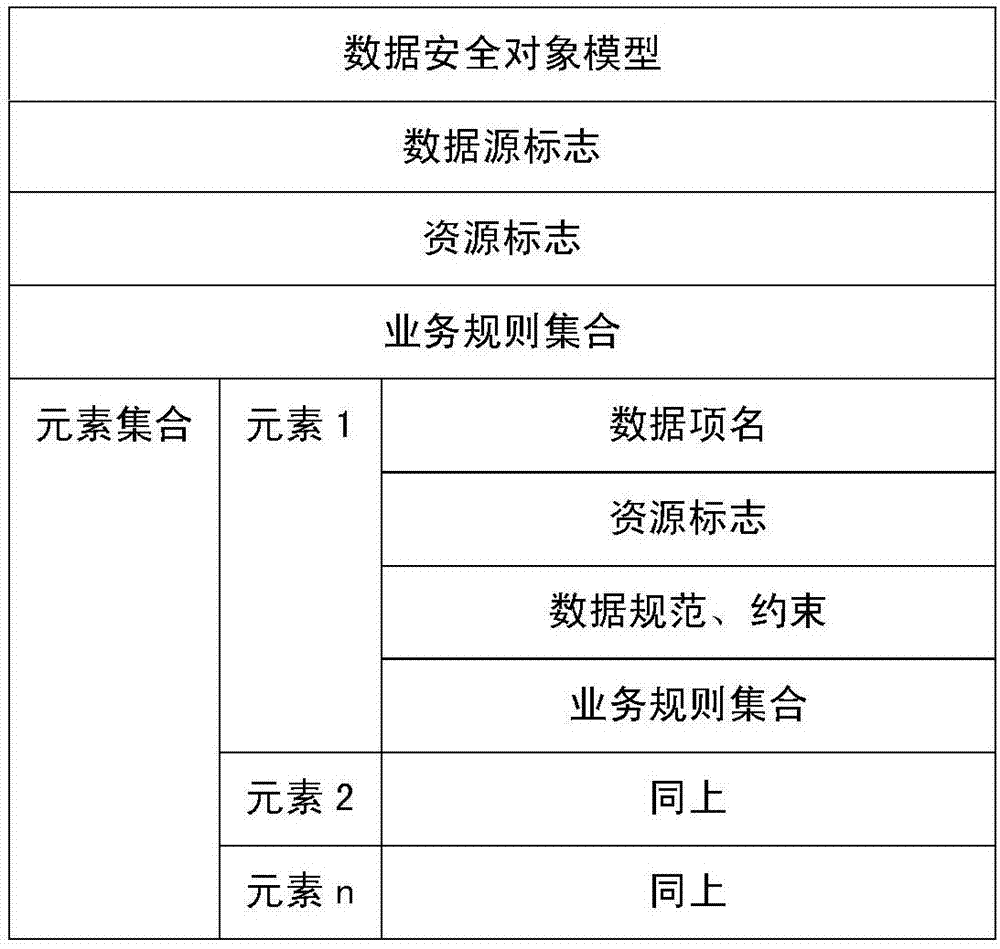
Fine-grained data permissiondynamic control system and method
ActiveCN107025411AImplement permission controlDigital data protectionTransmissionControl systemBusiness data
The invention discloses a fine-grained data permissiondynamic control system and method and relates to the field of computer data security. The method comprises steps as follows: analyzing and acquiringbusiness data application information, and establishing a data security object model on the basis of the business data application information; allocating resource access permissions for login users according to thebusiness data application information; acquiring permission information of target business data application information in the data security object model before the target business data application information requested by the login users is loaded; loading the target business data application information in real time according to the permission information. The system comprises a database unit, a model establishing unit, a user management unit and a permission control module. On the basis of the business data application information, the data security object model is established, and refined and dynamically changingpermission control for the business data is realized through authorization for elements or attributes in the model.
Owner:KARAMAY HONGYOU SOFTWARE
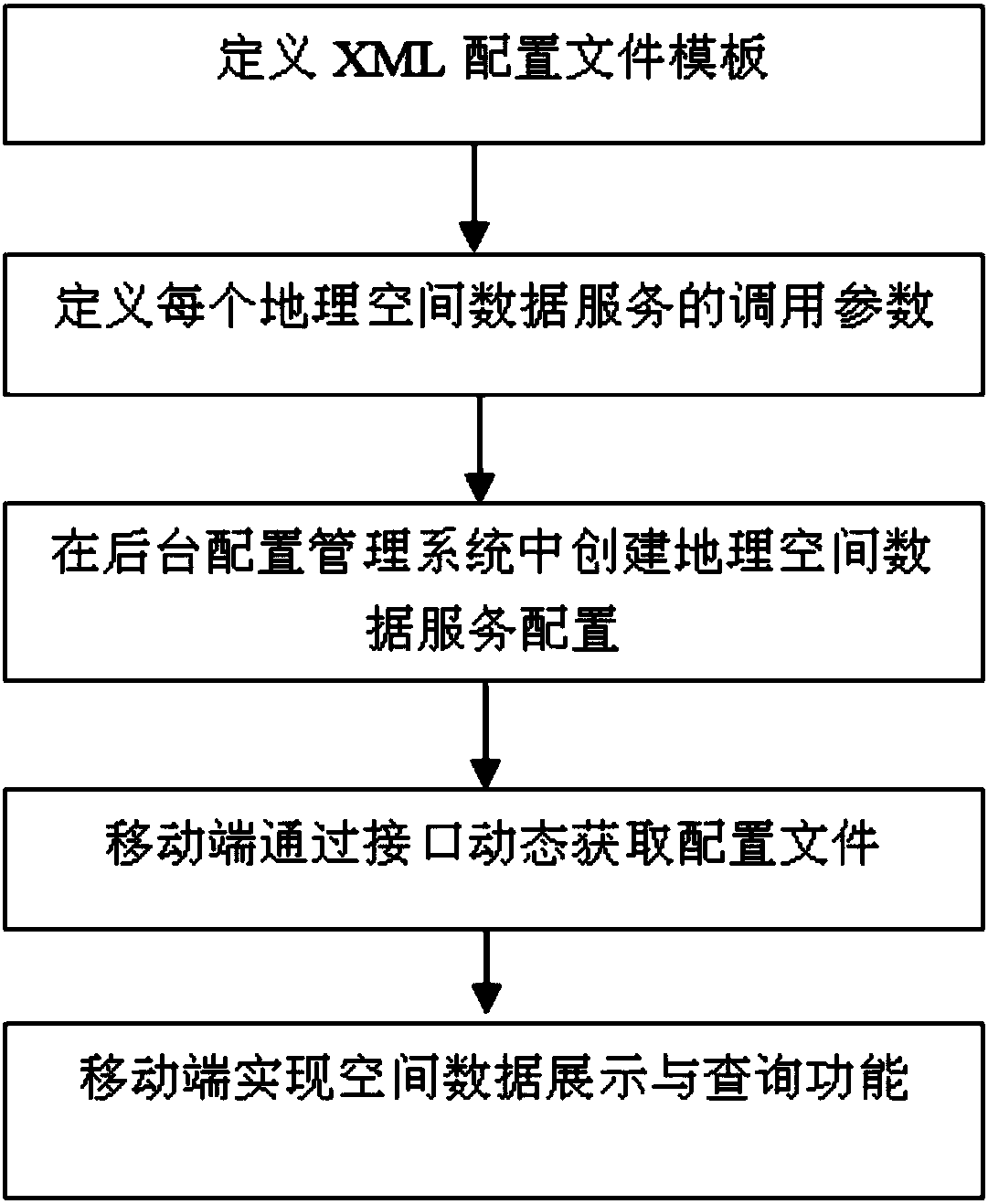
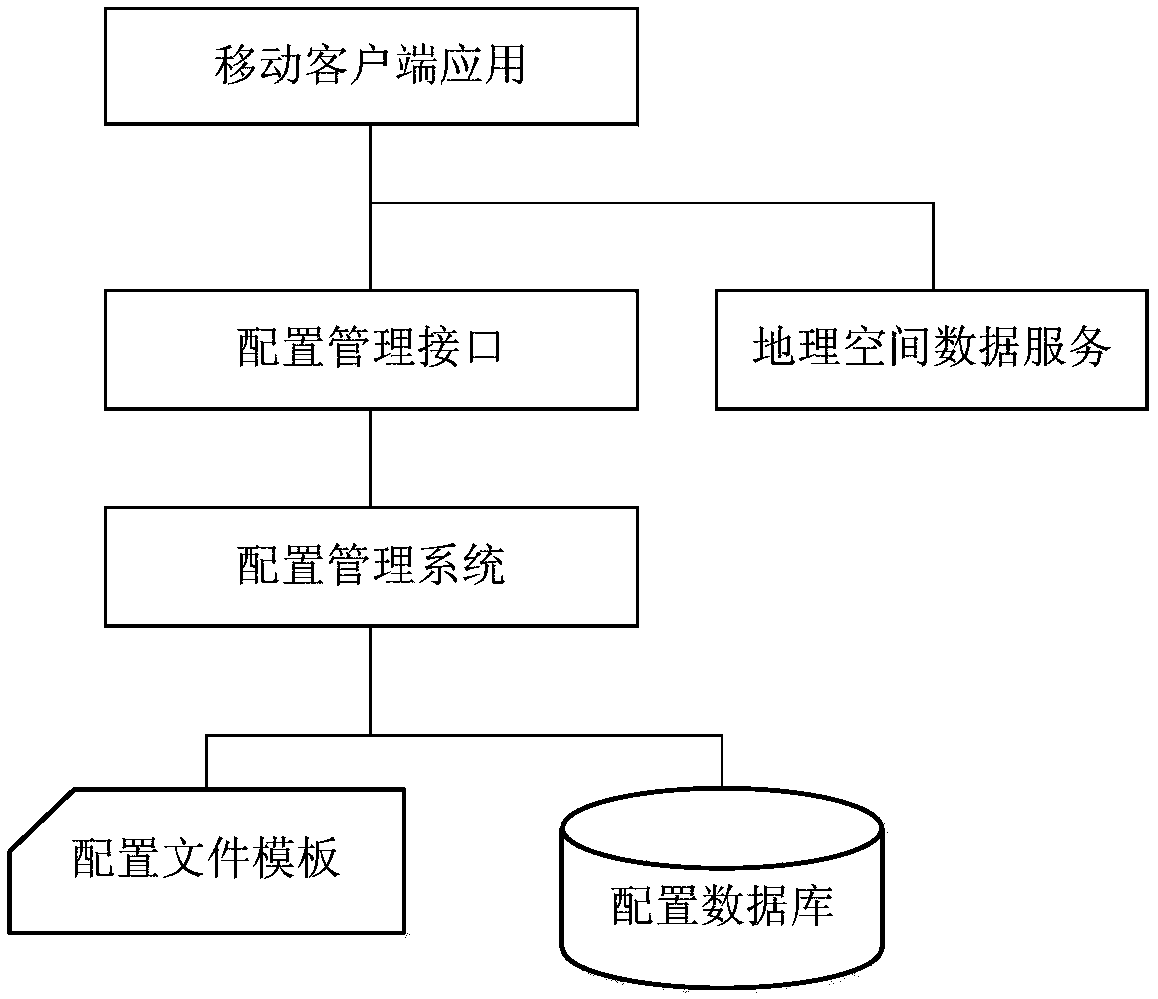
Geographic space data service integrating method of dynamic configuration oriented to mobile client side
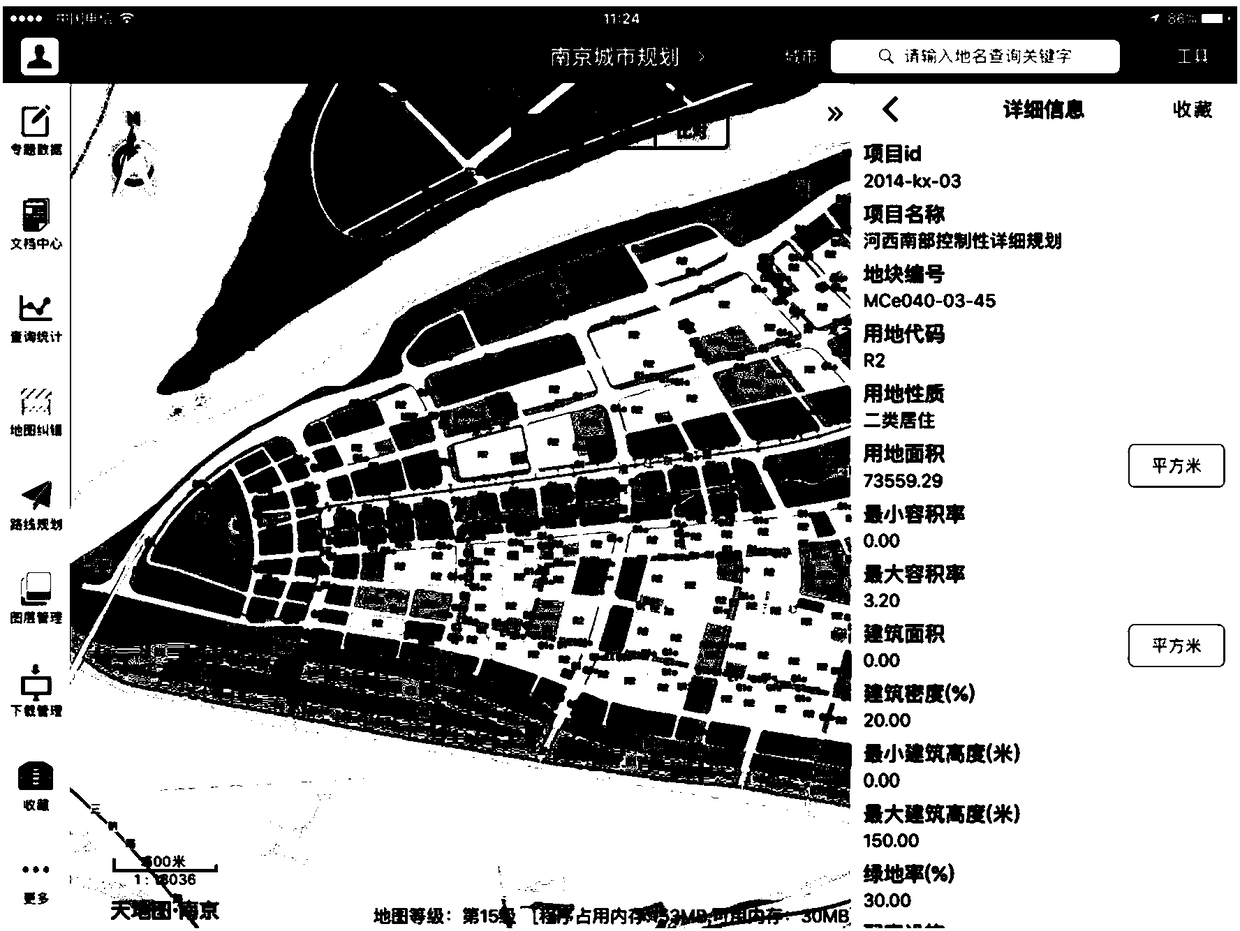
InactiveCN108133024AFast Statistical Analysis CapabilitiesBreak through limitationsVersion controlGeographical information databasesStructure of Management InformationClient-side
The invention discloses a geographic space data service integrating method of dynamic configuration oriented to a mobile client side. The method includes the following steps of firstly, defining an XML configuration file template to regulate the structural and universal parameters of a dynamic configuration file; secondly, analyzing and collecting the types of existing geographic space data service, and defining calling parameters of all geographic space data service; thirdly, establishing geographic space data service configuration in a background configuration management system; fourthly, dynamically obtaining a configuration file by a mobile side through a service interface; fifthly, achieving a space data displaying and inquiring function by the mobile side. By means of the method, thedynamic configuration of all geographic space data integrated in the mobile client side can be realized, the application requirements for rapid displaying and inquiring on the mobile client side aremet, and the user experience of geographic space data application under the mobile side environment is greatly improved.
Owner:南京市城市规划编制研究中心
IO processing method of RAID system and related device
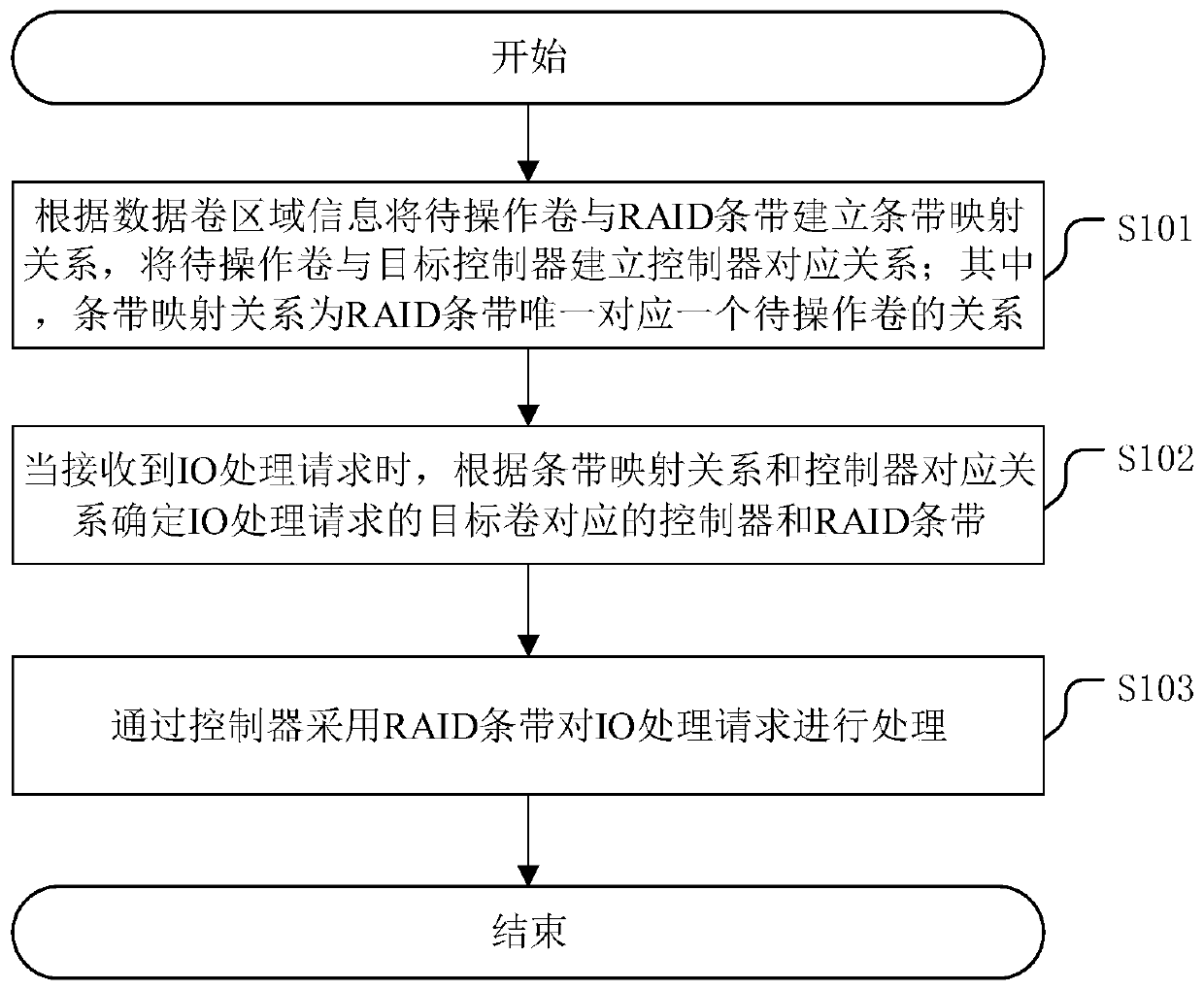
InactiveCN111290711AImplement permission controlAvoid performance lossInput/output to record carriersRAIDTarget control
The invention discloses an IO processing method for an RAID system, and the method comprises the steps: building a stripe mapping relation between a to-be-operated volume and an RAID stripe accordingto the region information of a data volume, and building a controller corresponding relation between the to-be-operated volume and a target controller; when an IO processing request is received, determining a controller and an RAID stripe corresponding to a target volume of the IO processing request according to the stripe mapping relationship and the controller corresponding relationship; and processing the IO processing request by adopting the RAID strip through the controller. The controller and the RAID stripe during IO processing each time are determined through the established stripe mapping relation and the established controller corresponding relation instead of being called by other IOs, so that control can be performed without adopting a stripe lock, performance loss is avoided,and the processing speed is increased. The invention further discloses an IO processing device of the RAID system, a storage server and a computer readable storage medium, which have the above beneficial effects.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
User permission control and transfer method and system in edge cloud scene
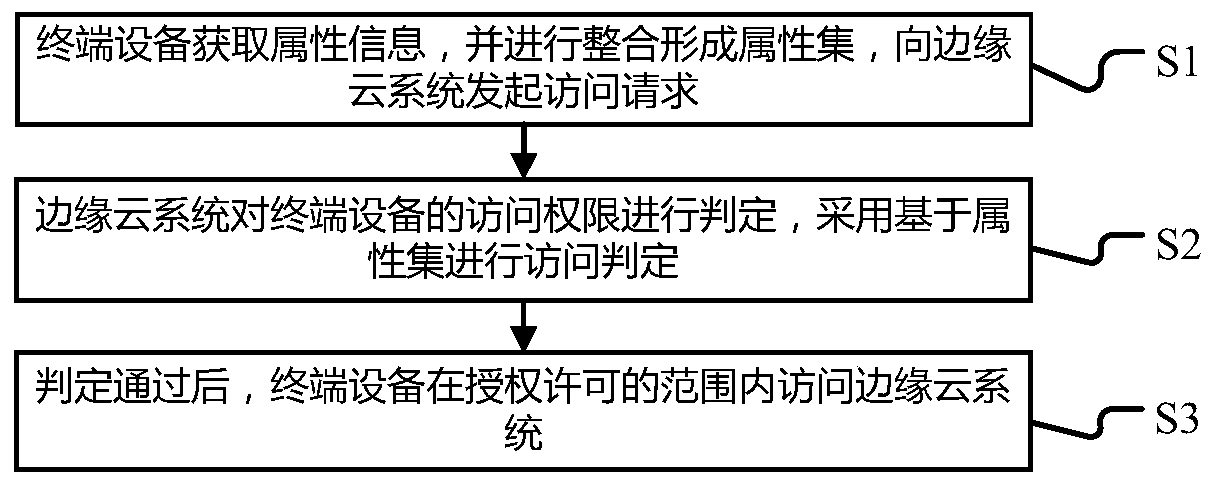
ActiveCN110300104APrevent leakageImplement permission controlDigital data authenticationTransmissionUser PrivilegeCloud user
The invention provides a user permission control and transfer method in an edge cloud scene, and the method comprises the steps: obtaining attribute information by terminal equipment, carrying out theintegration of the attribute information to form an attribute set, and initiating an access request to an edge cloud system; the edge cloud system judging the access permission of the terminal equipment, and carrying out access judgment based on the attribute set; and after the judgment is passed, the terminal equipment accessing the edge cloud system within an authorization permission range. Information leakage is prevented, and the problem of complicated authority control caused by high user mobility between edge clouds is avoided. Fine-grained access control of authority is realized, and the cloud system and the service are ensured to be correctly and safely used. In addition, an authority control layer is introduced to meet the requirements of small edge cloud authority control granularity, user authority transfer and the like, and edge cloud user authority control and transfer are achieved.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
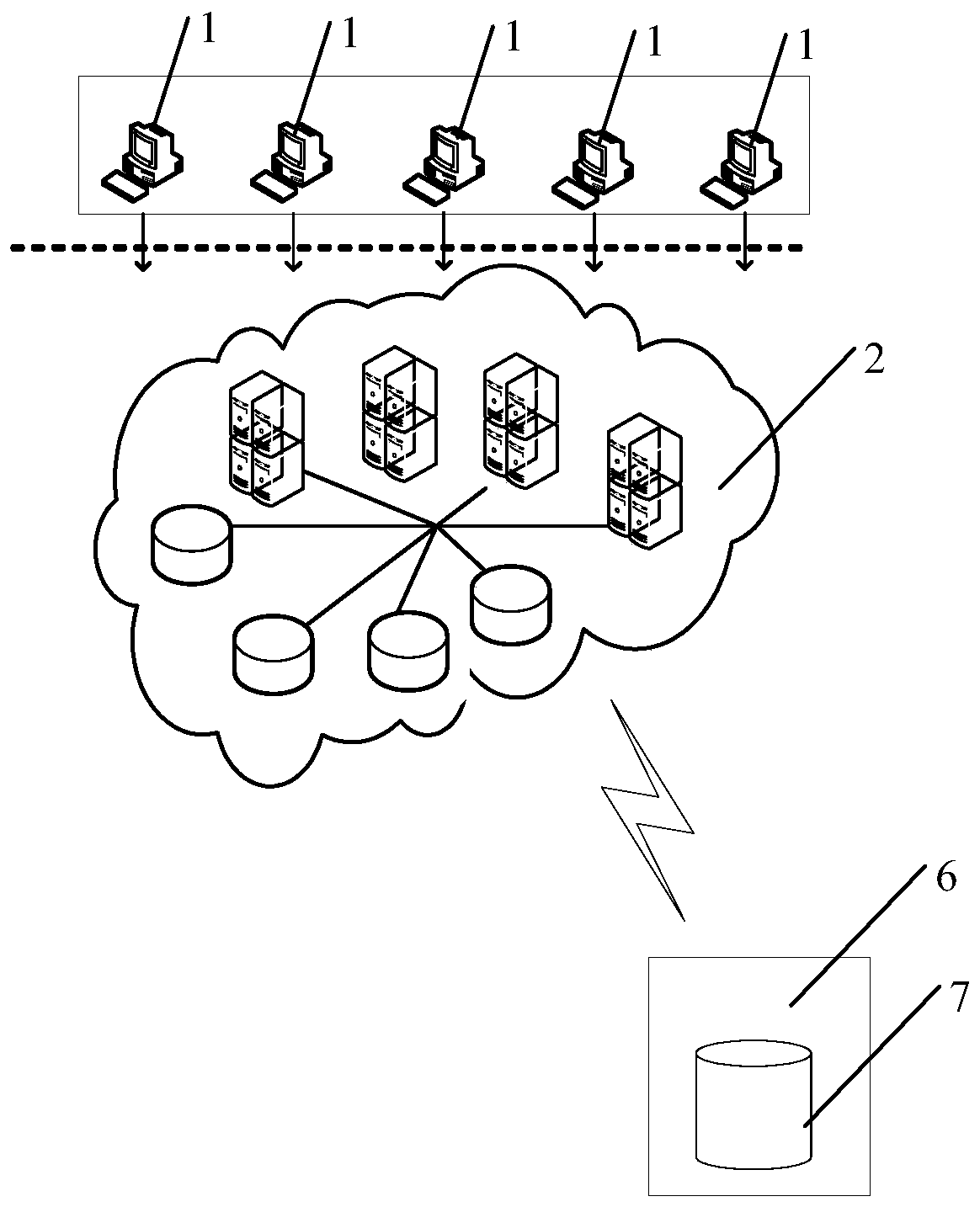
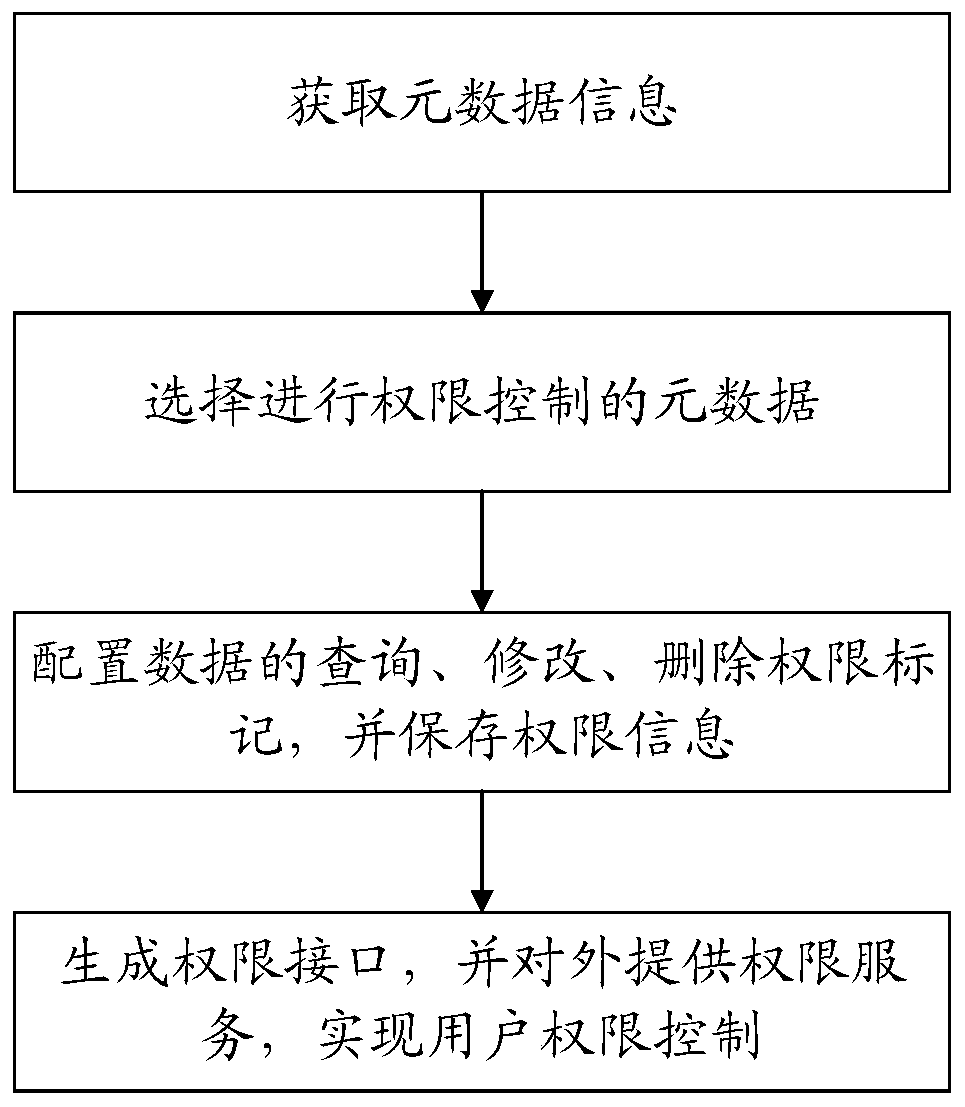
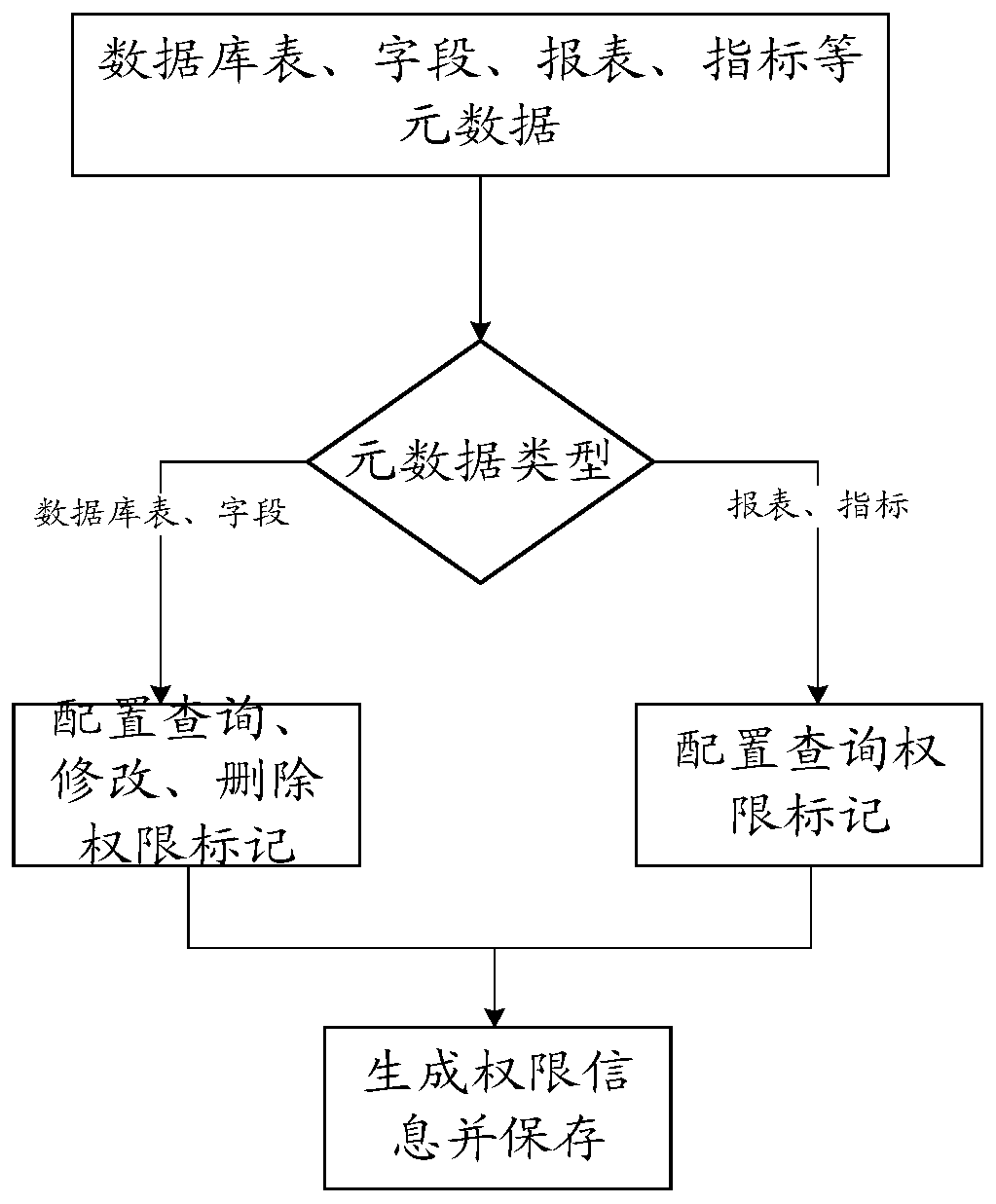
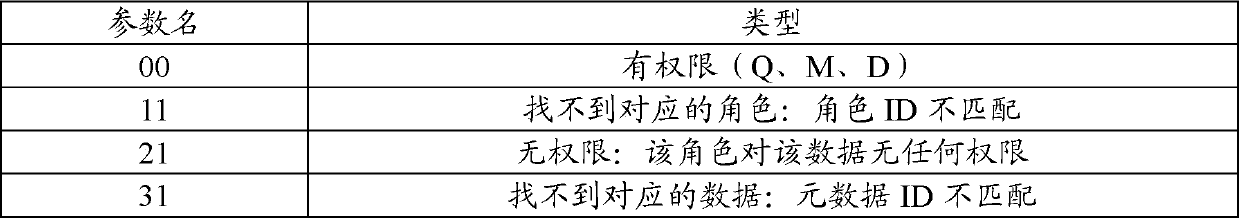
System and method for realizing data authority control based on metadata in big data environment
ActiveCN110929280AImplement permission controlReduce coding timeDigital data protectionMetadata managementData acquisition
The invention relates to a system for realizing data authority control based on metadata in a big data environment. The system comprises: a metadata management module used for acquiring metadata information in the big data environment from different databases through a built-in adapter; a authority configuration module which is used for configuring authority marks of metadata for different roles;and an authority service module which is used for generating an authority service interface according to the stored authority information and providing authority authentication service to the outside.The invention further relates to a method for realizing metadata-based data permission control in the big data environment. The system and the method for realizing data authority control based on metadata in the big data environment are adopted; the problem of data permission control of different types of databases is solved, meanwhile, a large amount of encoding time for data acquisition is saved, the complexity of data permission control is reduced, the problems that cross-system data permission control cannot be performed and the permission control process cannot be effectively monitored at present are solved, and unified control of data permission is realized.
Owner:PRIMETON INFORMATION TECH
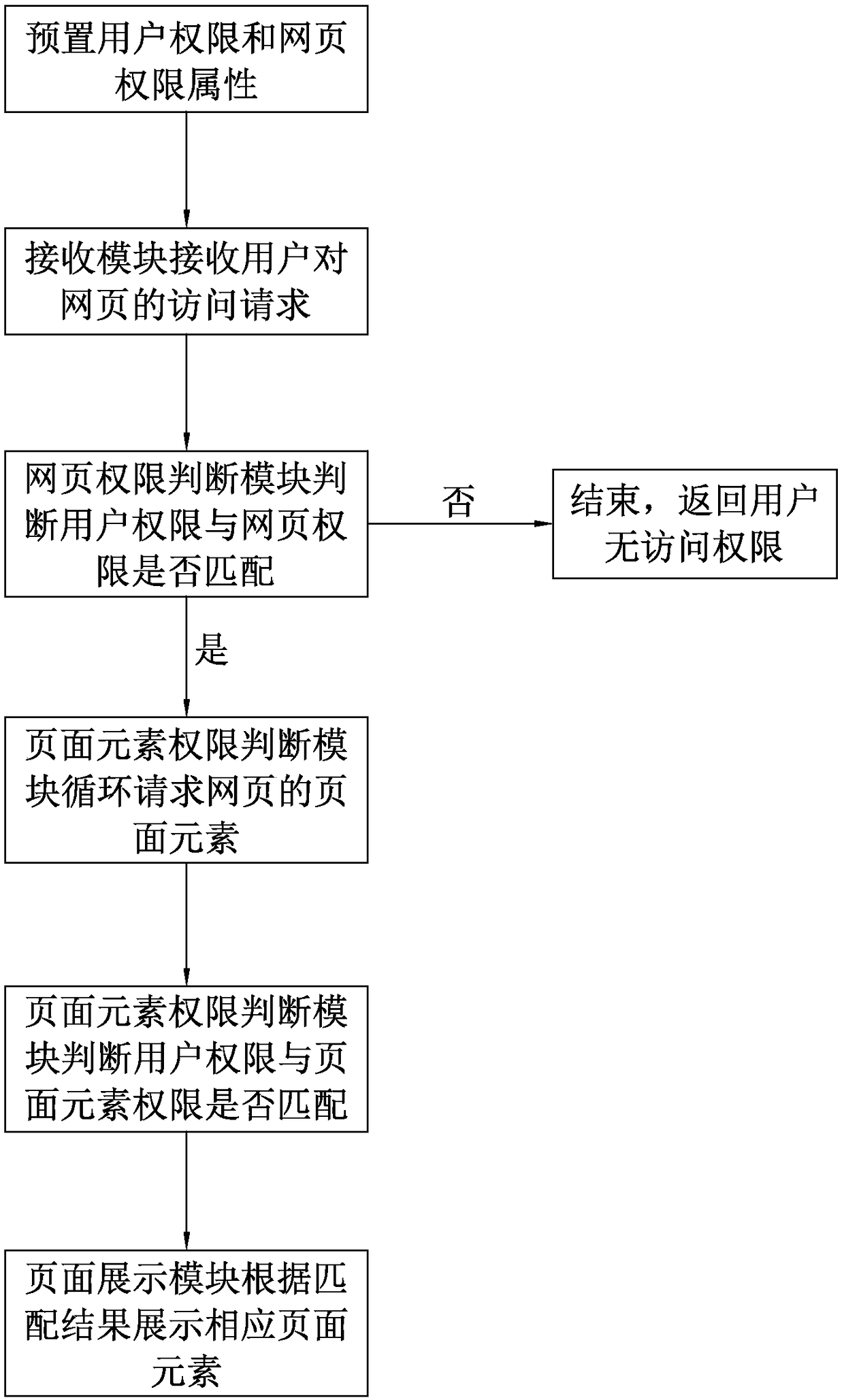
A system and method for realizing page refinement authority control
InactiveCN109409048AImplement permission controlReduce maintenance costsDigital data authenticationWebsite content managementAuthority controlAuthorization
The invention discloses a system and a method for realizing page refinement authority control. The system includes a receiving module, Web page authority judging module, a page element authority judgment module and a page display module, the receiving module receives an access request of a user to a web page. The page authority judging module judges whether the user authority matches the page authority, and the page element authority judging module circularly requests the page element of the page, and judges whether the user authority matches the page element authority, and determines the display or hiding of the corresponding page element, and the page display module displays the corresponding page element according to the matching result. On the basis of presetting page element authorization attributes and user authorization information, By implementing Struts 2 user-defined tag, the display and hiding of page elements are realized according to the return result of user-defined tag,and the permissions of elements in the page are controlled, which achieves the purpose of fine control of page element permissions and reduces the maintenance cost.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Urban brain intelligent big data system
InactiveCN112527791AMonitor running status in real timeRealize managementDatabase management systemsRelational databasesBusiness enterpriseEngineering
The embodiment of the invention provides an urban brain intelligent big data system. The urban brain intelligent big data system comprises a big data analysis module, an AI algorithm model module, a big data visualization module and a big data management module. According to the invention, the data standard of each business unit of city management is unified, and standardized storage and real-timeinteraction of the data of each business unit are facilitated; according to the method, an X-SQL algorithm is introduced, and SQL statements required in a new business scene are automatically generated according to historical SQL statements, so the labor cost is greatly reduced, and the intelligence of an urban brain is improved; data of each business unit is automatically sorted, mined and analyzed, an analysis report is generated, leaders are assisted to make decisions according to the analysis report, interconnection and information interaction between departments and enterprises of a cityare achieved, automatic sorting, analysis and display of big data are achieved, and the intelligent level of city management is improved.
Owner:BEIJING ZHONGHAIJIYUAN DIGITAL TECH DEV CO LTD
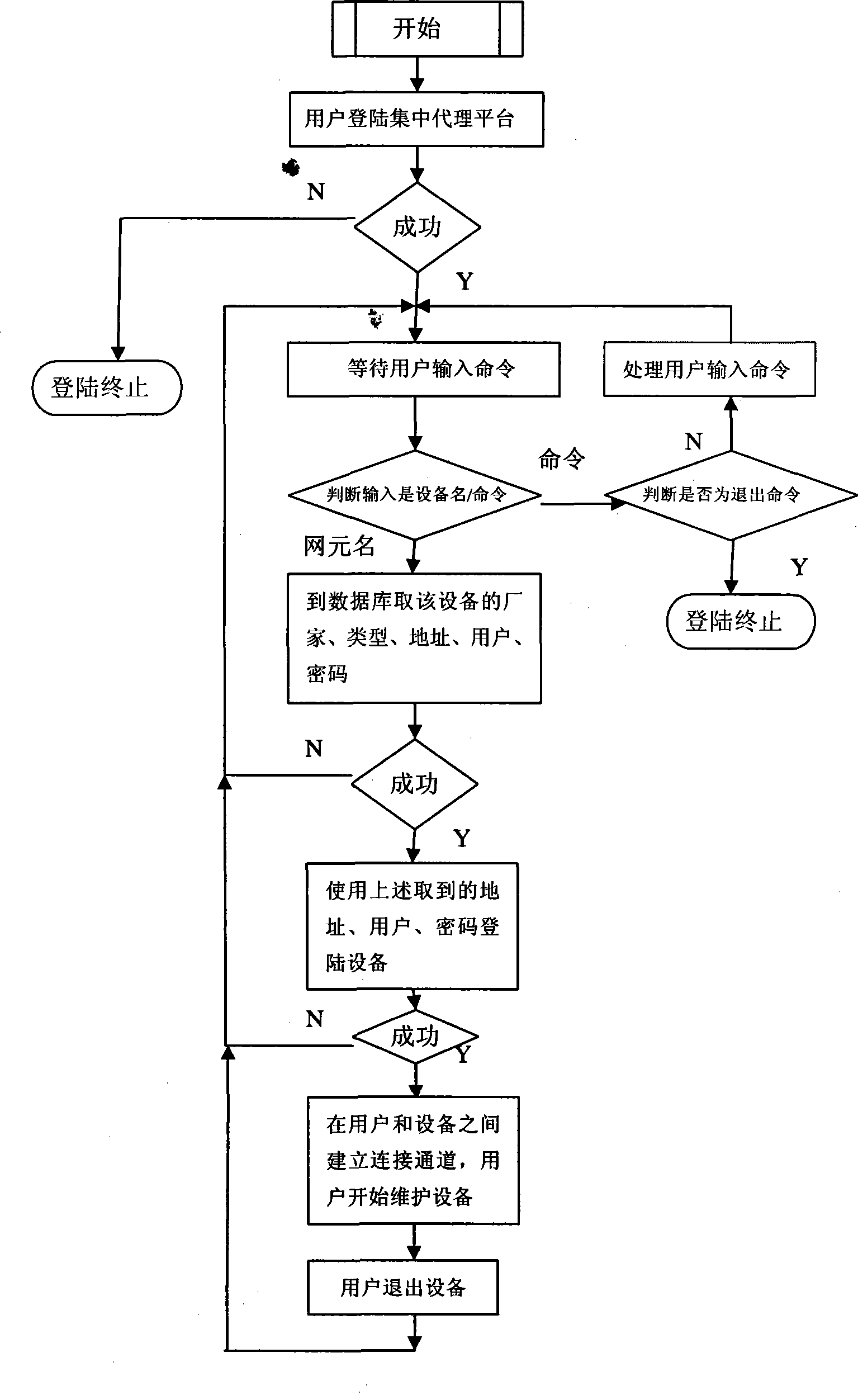
System for telecommunication equipment centralized login and implementing method thereof
InactiveCN101459543AImplement permission controlImprove work efficiencySupervisory/monitoring/testing arrangementsData switching networksDevice typeEngineering
The invention relates to the maintaining and managing field of telecommunication apparatuses, in particular to a system in which telecommunication apparatuses collectively log on and an implementation method thereof. The system in which telecommunication apparatuses collectively log on and an implementation method thereof replace a plurality of landing procedures allocated by oem equipment by a single agent program, enable an operating and maintaining staff to finish the landing, operating and maintaining work of all telecommunication apparatuses through only one operational interface after logging on the system, and can freely switch in each device. The system in which telecommunication apparatuses collectively log on and an implementation method thereof solve the problems of more client landing procedures, inconvenient use and difficult management caused by a plurality of equipment types and a plurality of manufactures, which improve the efficiency and the security of operating and maintaining work of telecommunication apparatuses.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
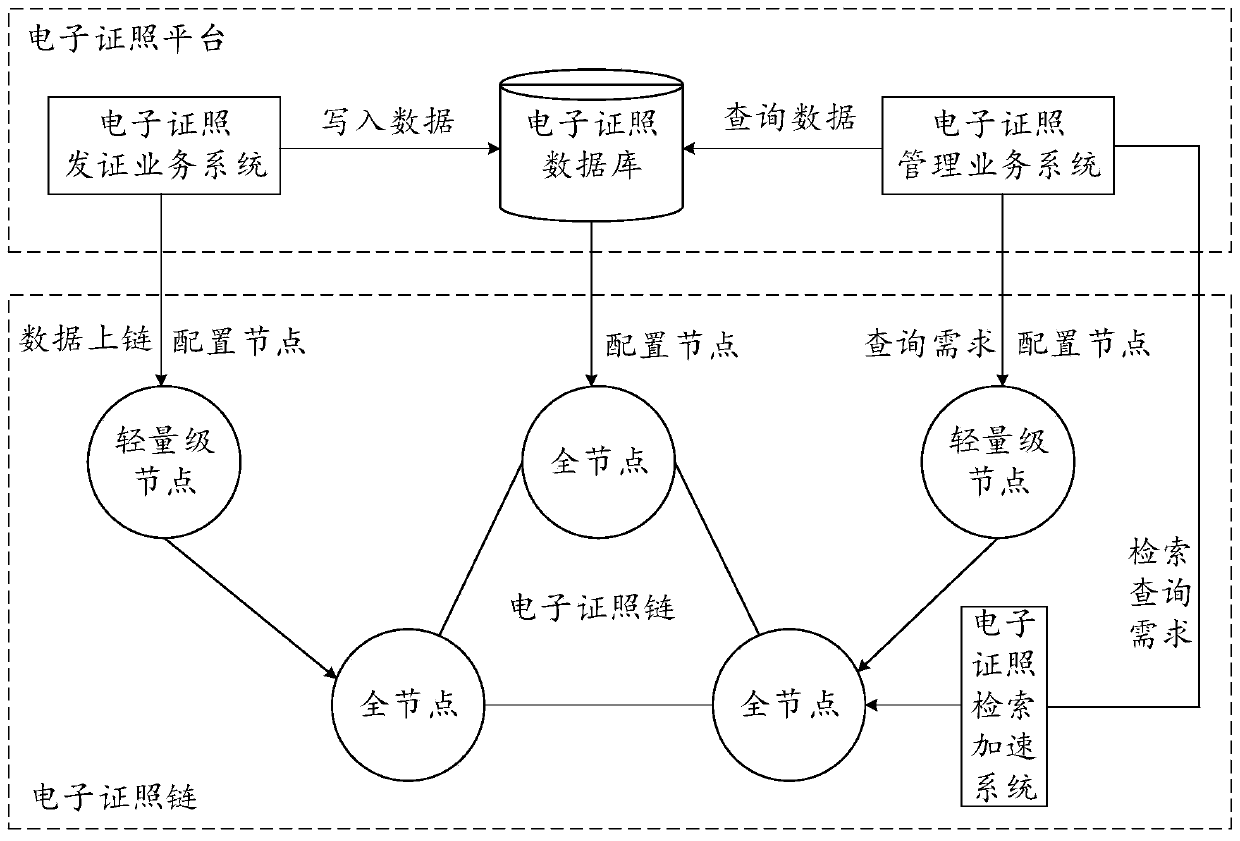
Electronic certificate processing method, device, equipment, platform and medium
ActiveCN110765137AEasy to storeSafe storageDatabase distribution/replicationNatural language data processingTransaction dataEngineering
The embodiment of the invention discloses an electronic certificate processing method and device, equipment, a platform and a medium, and relates to the technical field of block chains, and the methodcomprises the steps: obtaining an electronic certificate processing transaction request, wherein the electronic certificate content in the electronic certificate processing transaction request is generated based on a preset certificate content template deployed in a block chain system; and executing the electronic certificate processing transaction request to generate electronic certificate processing transaction data, and adding the electronic certificate processing transaction data to the block, the processing operation information corresponding to the electronic certificate processing transaction request being added to a life cycle record field in a preset certificate content template. According to the embodiment of the invention, effective supervision processing of the electronic certificate data can be realized, so that data storage and interaction are more convenient and reliable.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
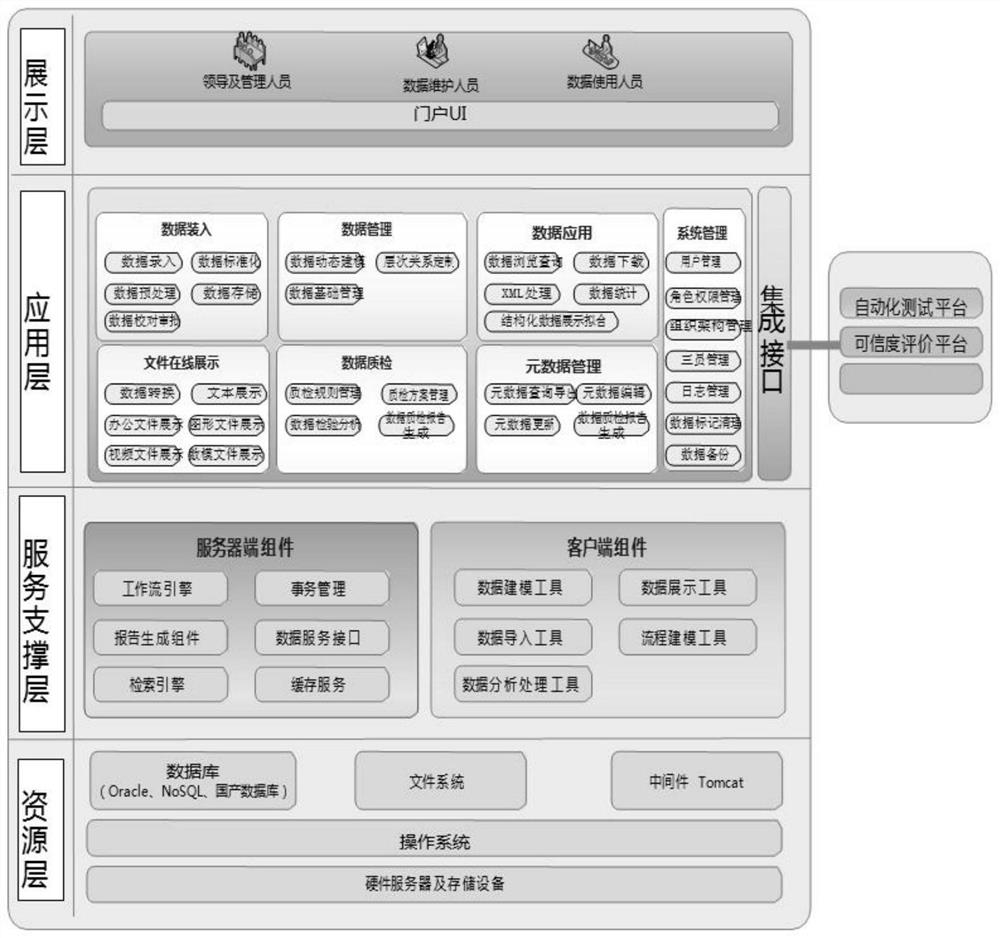
CFD software verification and confirmation database platform
ActiveCN112559351AFull potentialImplement permission controlDatabase management systemsSoftware testing/debuggingData displayData modeling
The invention discloses a CFD software verification and confirmation database platform which comprises a display layer, an application layer, a service support layer and a resource layer. The displaylayer displays information to different users and provides quick entrances of various service functions; the application layer provides various specific functions for the database platform and achieves data transmission with an external system through an integrated interface; the service support layer mainly provides basic functional components or tools and is divided into a server-side componentand a client-side plug-in; the server-side component provides platform transaction processing, a data interface, a data cache, a workflow engine and a report generation and retrieval engine; the client assembly mainly comprises a data modeling tool, a data display tool, a data import tool, a process modeling tool and a data processing analysis tool; and the resource layer provides a software and hardware platform for supporting the database platform to operate. The database platform provides a special database for CFD software verification and confirmation.
Owner:中船奥蓝托无锡软件技术有限公司 +1
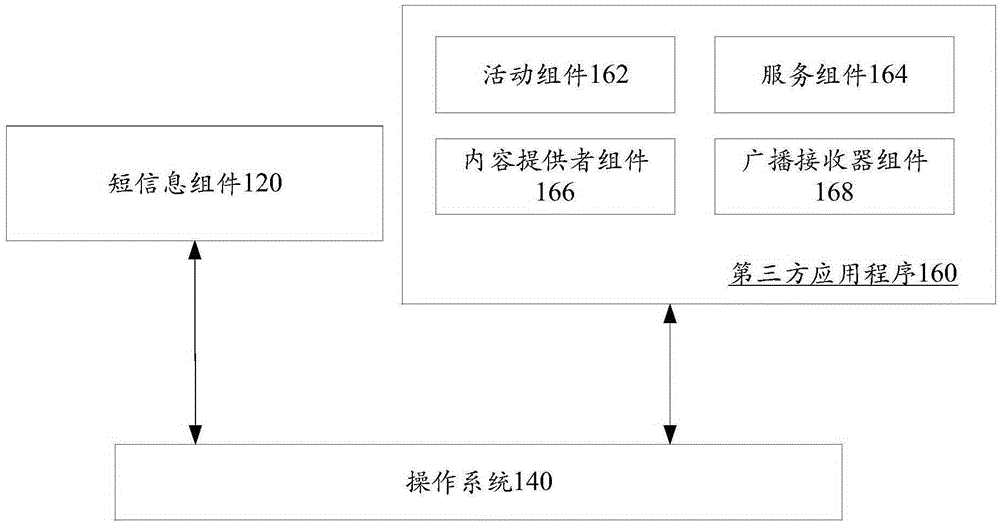
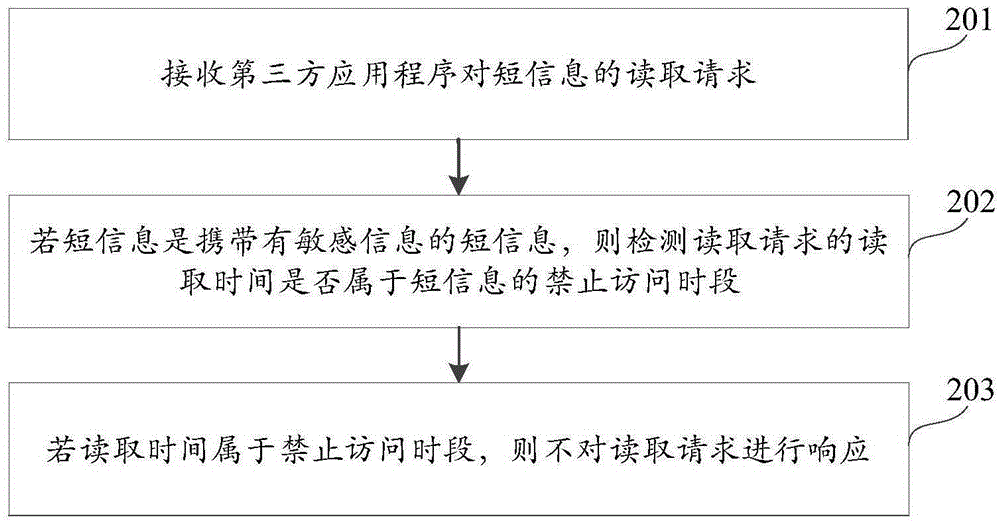
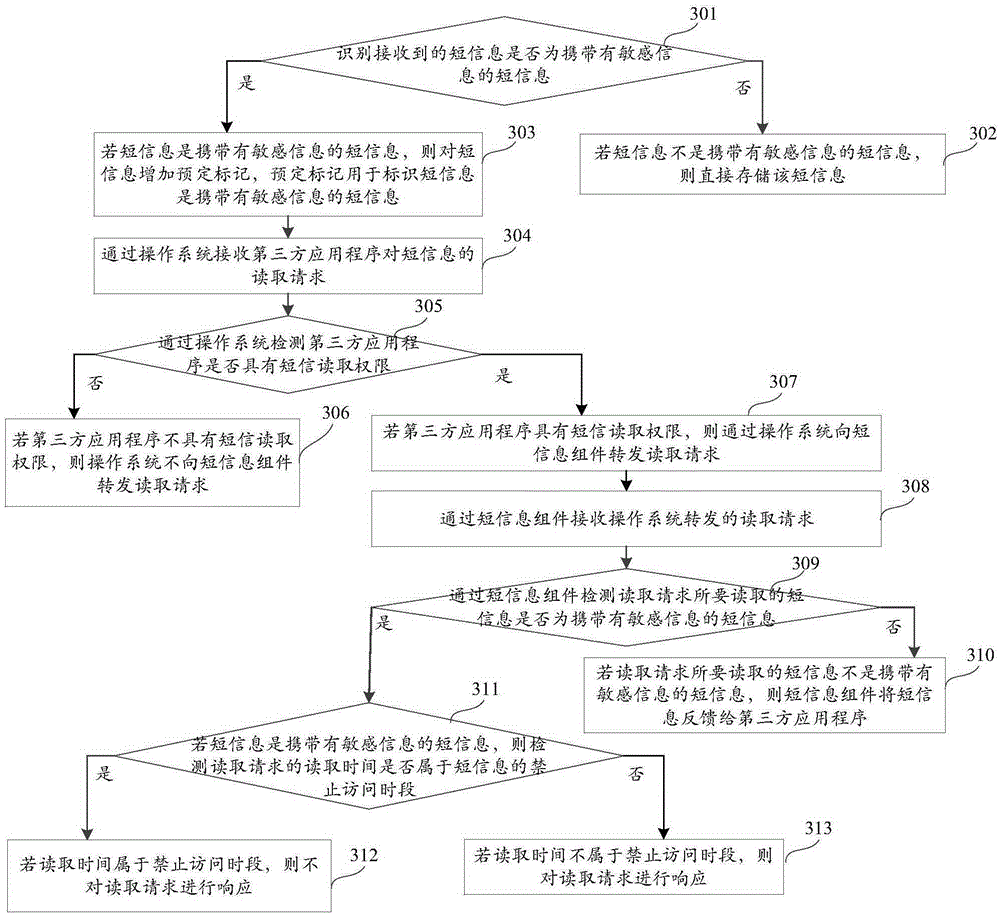
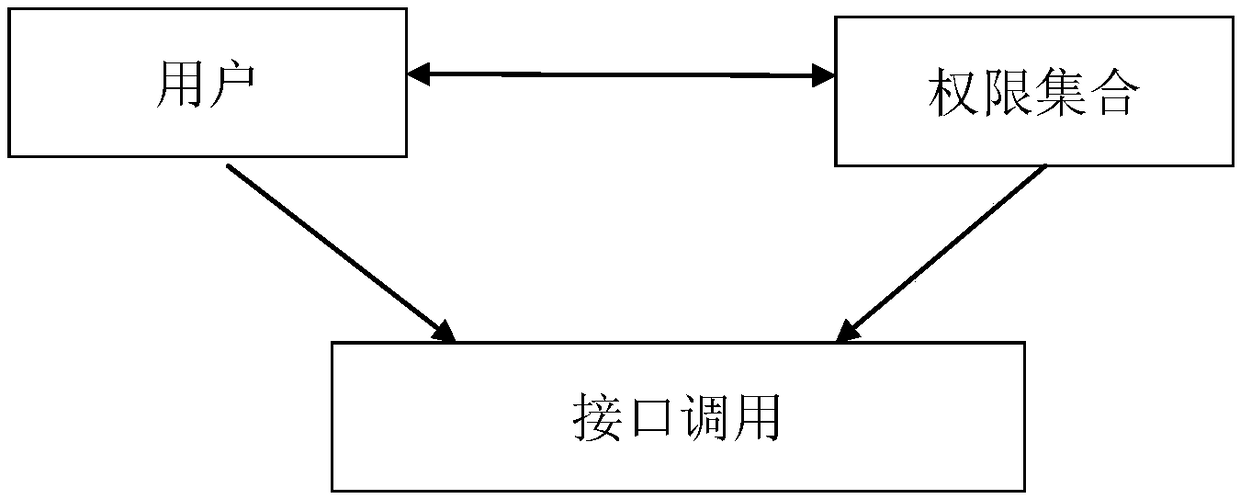
Short message reading method and apparatus
ActiveCN105303120APrevent leakageImplement permission controlDigital data protectionPayment architectureApplication softwareThird party
The invention discloses a short message reading method and apparatus and belongs to the field of information security. The short message reading method comprises the following steps of receiving a short message reading request by a third party application program, detecting whether reading time for reading the request is within a short message forbidding visit period when the short message carries sensitive information, and making no respond to the reading request when the reading time belongs to the forbidding visit period. A problem can be solved that malignant application program acquires a permission for executing sensitive operations via reading verification codes in the short message when a third party application program can read short message content in a short message assembly when only owning a short message reading permission from the perspective of operation system. By the use of the method, the third party application program cannot read short message content in the forbidding visit period in light of short message carrying sensitive information, so sensitive information in the short message can be prevented from being leaked in the forbidding visiting period; and single short message granularity permission can be controlled.
Owner:XIAOMI INC
A configurable interface access control method
ActiveCN109165486ALess invasiveImprove reusabilityDigital data authenticationAuthority controlDatabase
The invention discloses a configurable interface access authority control method, comprising the following steps: S1, an interface database is created, including all interface authority identifiers; S2, a user table is created to store the user's information and the user's role; S3, an association table accessed by roles and interfaces is created; S4, a right identification is added to each external interface, wherein the right identification corresponds to the right in the interface database one by one; S5, the user logs in, and the interface database acquires the interface access authority set owned by the user, and caches the corresponding data; S6, the user accesses the interface for the first time, and calls the interface access authority set cached in step S5 once, and compares the authority owned by the user with the authority identification of the interface at this time, and permits access if the user has the corresponding authority, and does not have the corresponding authority if the user has the corresponding authority; Access is blocked; S7, the user accesses the external interface again, does not need to call the interface access permission set, and directly compares the permission owned by the user with the permission identification of the interface.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
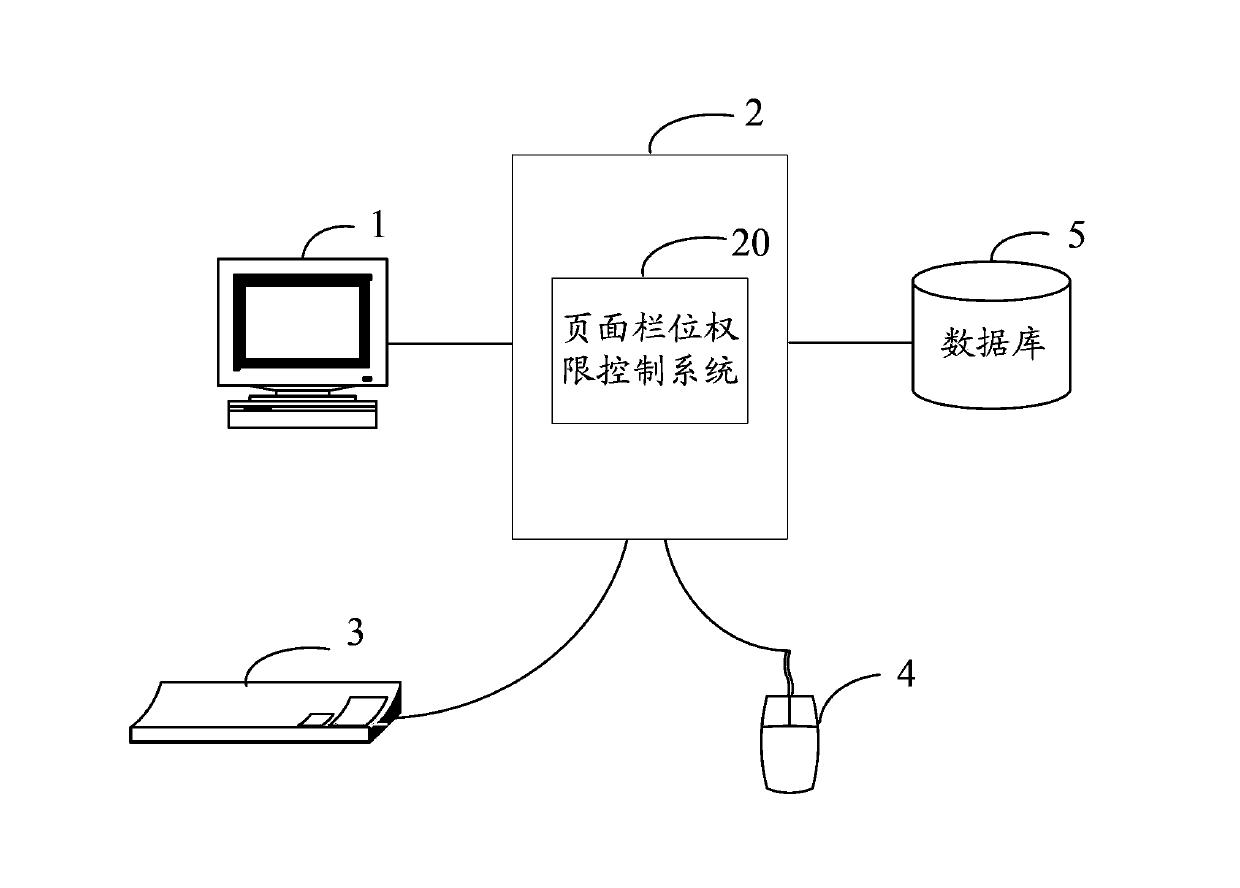
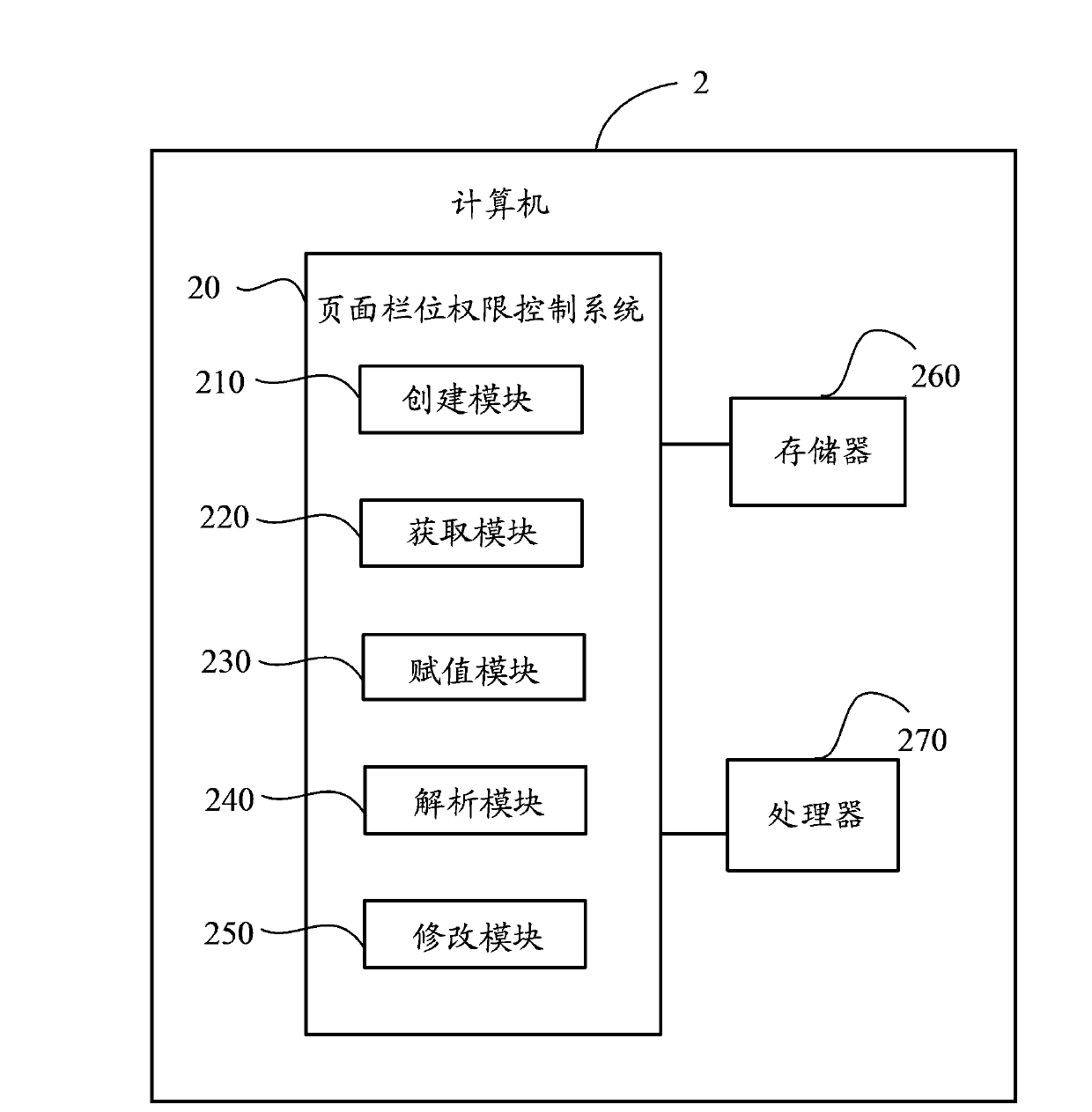
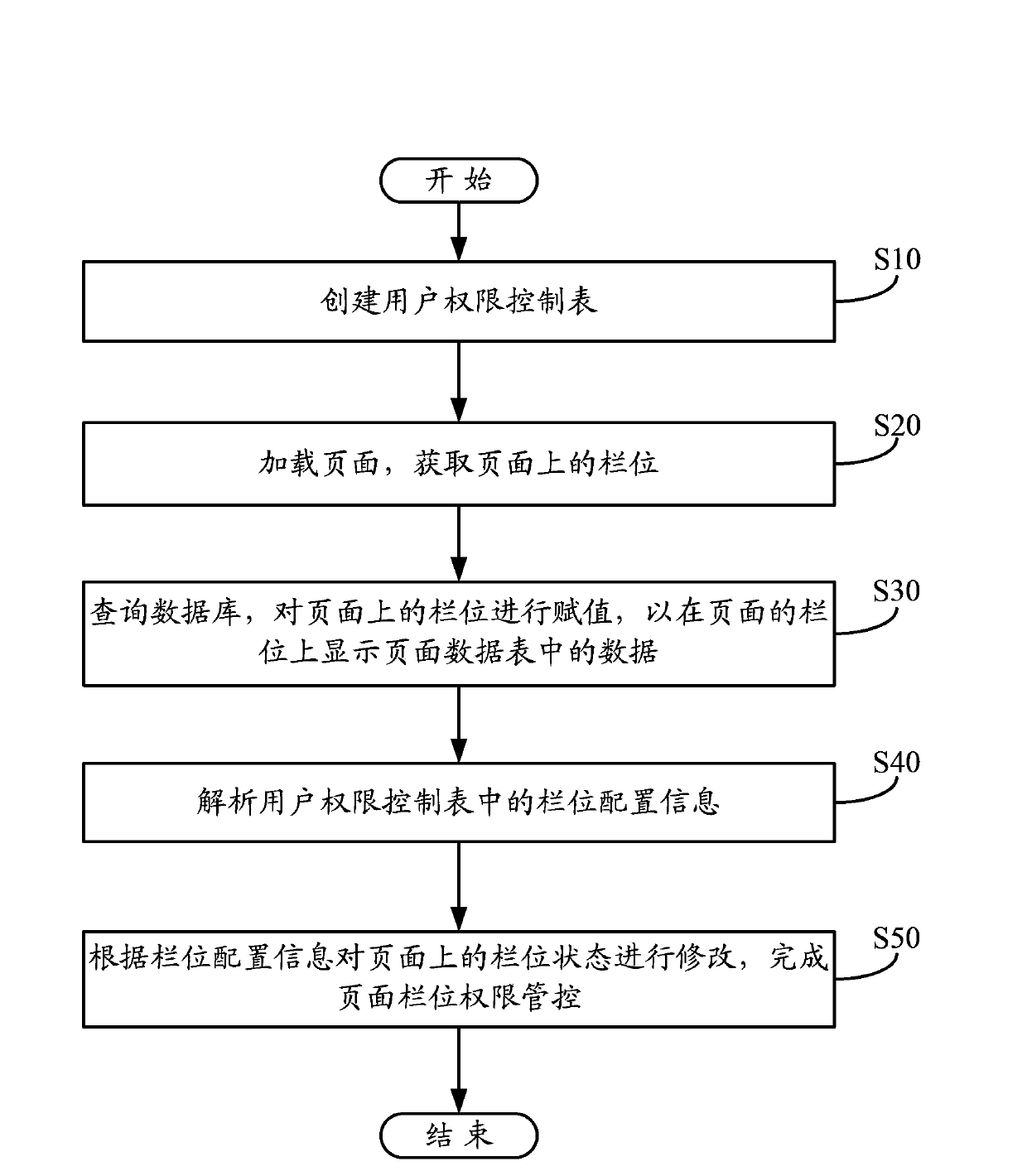
Page field access control system and method
InactiveCN103971036AImplement permission controlSave resourcesDigital data authenticationSpecial data processing applicationsUser PrivilegeControl system
The invention relates to a page field access control method which comprises the following steps of: creating a user access control list; loading a page from a database and obtaining a field on the page; inquiring a page data list in the database and assigning the field on the page according to a corresponding relation between the page data list and the page to display data in the page data list on the field of the page; analyzing field configuration information in the user access control list; modifying a field status on the page according to the field configuration information and finishing the page field access management and control. The invention also provides a page field access control system. With the adoption of the page field access control method and the page field access control system, the access control of the field on the page can be conveniently realized, all pages can be controlled in a same way, the coding implementation needs not be independently performed aiming at different pages and different roles, and a large quantity of resources is saved.
Owner:广东学无国界科技有限公司
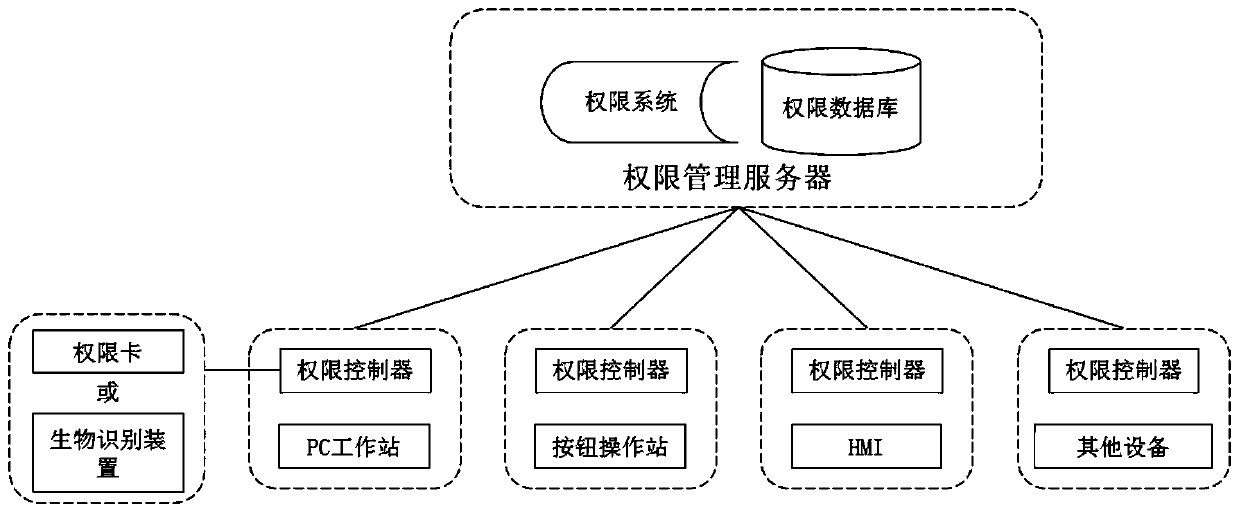
An authority unified management platform applied to an intelligent factory
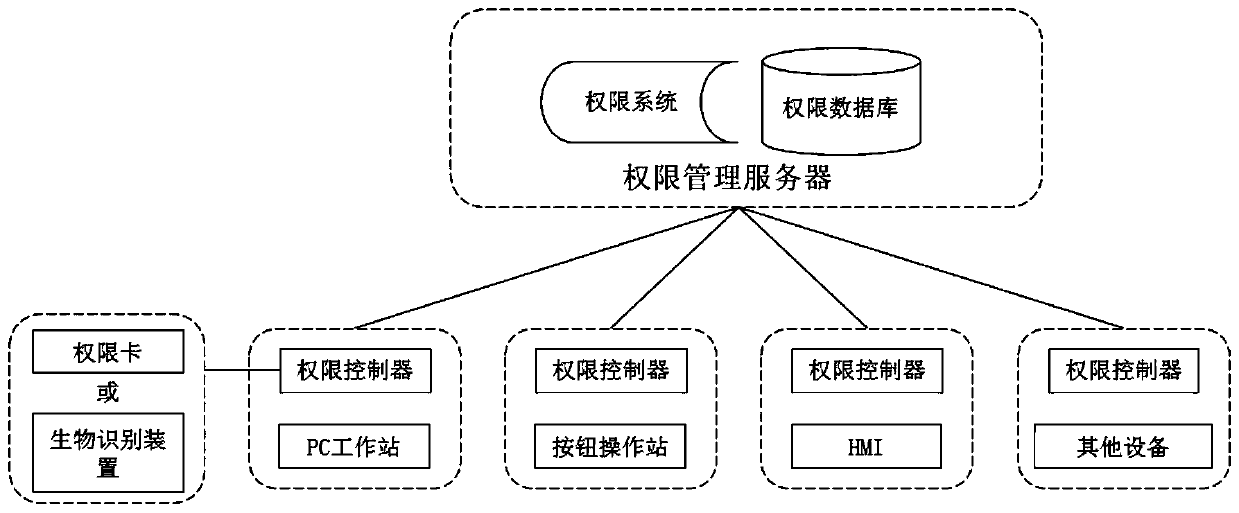
InactiveCN109711128AUnified authority managementImplement permission controlDigital data authenticationManagement systemLibrary science
The invention discloses an authority unified management platform applied to an intelligent factory. The system comprises an authority management system, and the authority management system comprises an authority management server, an authority database installed in the authority management server through software, an authority system, an authority controller which is connected with managed equipment and can run online or offline, and authority recognition equipment which is used in cooperation with the authority controller to achieve authority recognition. The authority management server is incommunication connection with each authority controller; wherein the authority management server is communicated with managed equipment, and the managed equipment is in communication connection withthe authority card reader. According to the invention, authority management and distribution are performed on the managed equipment through the unified authority management system, and the authority management server controls login of the equipment according to the read authority information, so that unified authority management of equipment login is realized.
Owner:AUTOMOTIVE ENG CORP +1
Permission control method and device
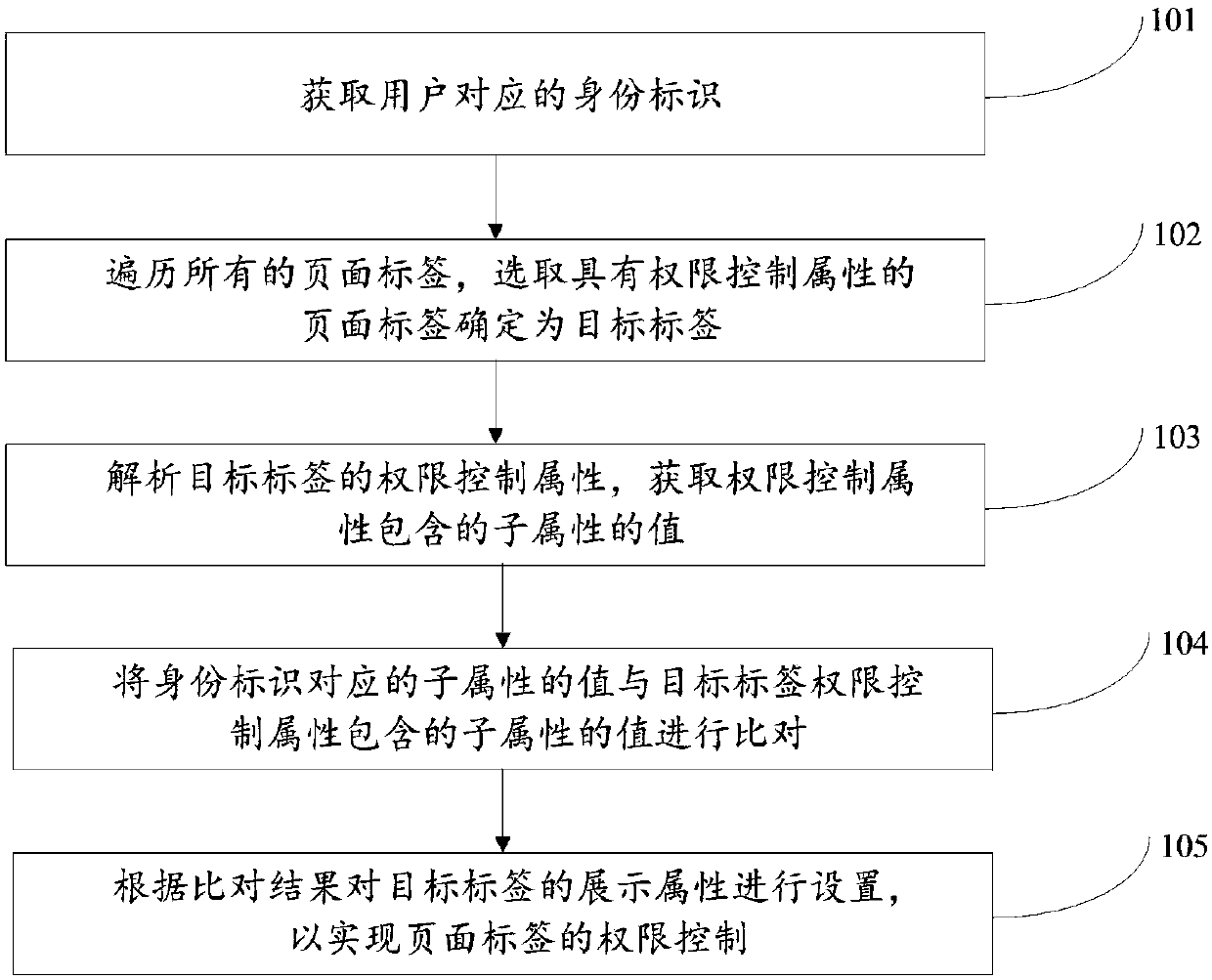
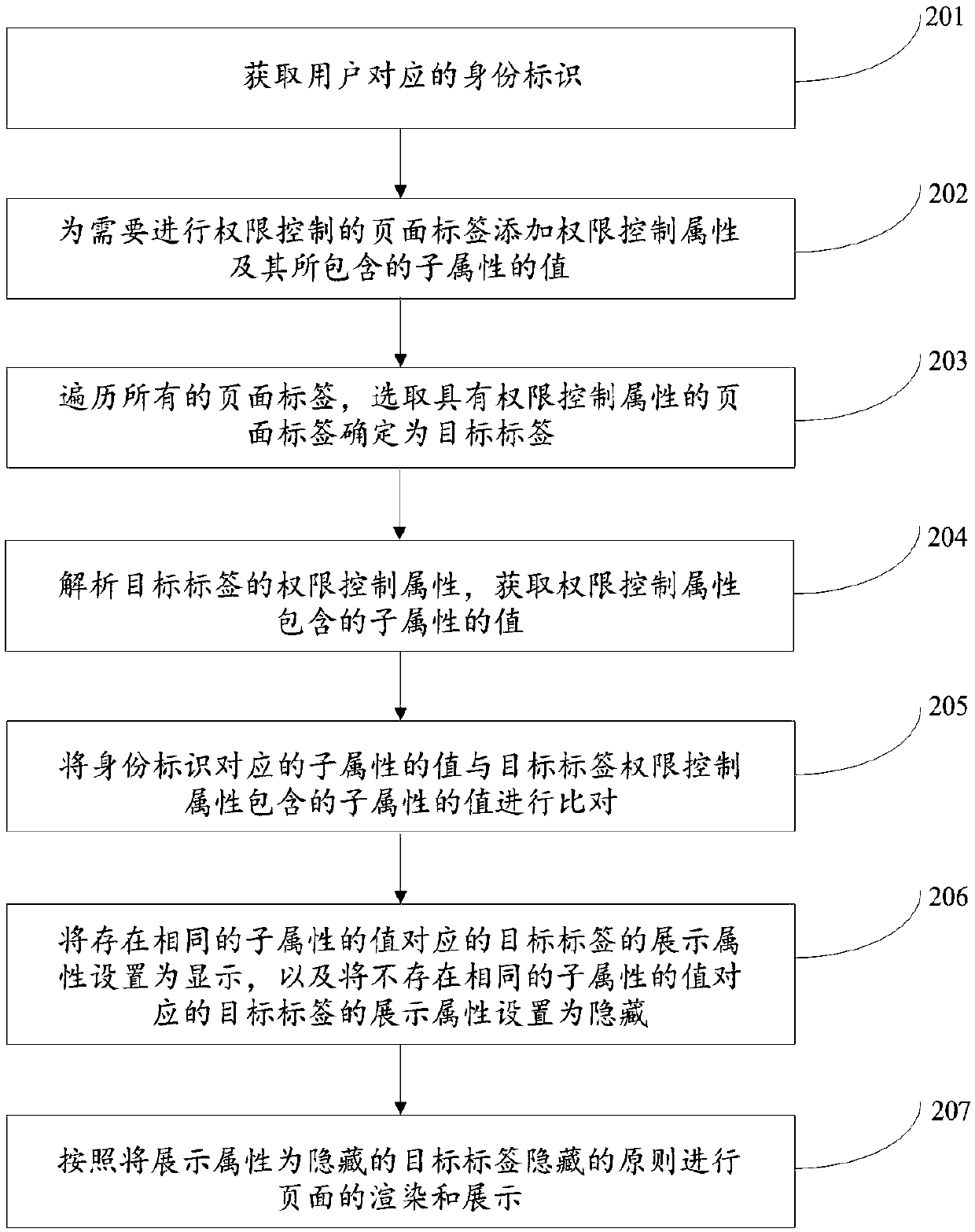
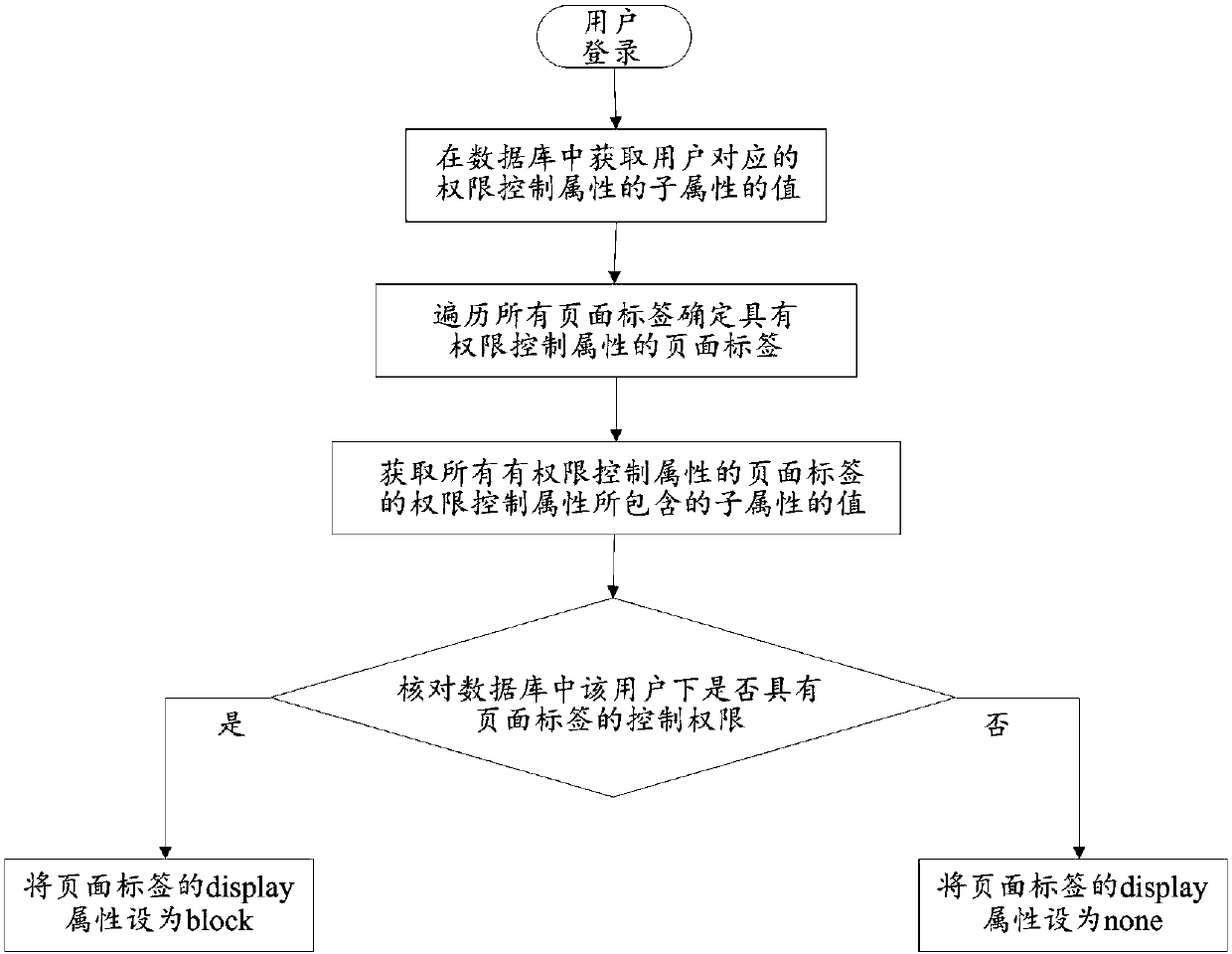
PendingCN109657427AImplement permission controlImprove scalabilityDigital data protectionDigital data authenticationExtensibilityAction Code
The invention discloses a permission control method and device, relates to the technical field of web system role management, and aims at solving the problems that an existing permission control modeis poor in role expandability and not fine enough in control granularity. The method comprises the following steps: after a user logs in a web system, obtaining an identity identifier corresponding tothe user; Traversing all the page tags, and selecting the page tag with the authority control attribute to determine as a target tag; Analyzing the authority control attribute of the target tag, andobtaining the value of a sub-attribute contained in the authority control attribute, the sub-attribute at least containing the product identifier, the resource code and the action code corresponding to the page tag; Comparing the value of the sub-attribute corresponding to the identity label with the value of the sub-attribute contained in the target label authority control attribute; And settingthe display attribute of the target tag according to the comparison result so as to realize authority control of the page tag. The method and the device are suitable for being applied to the web front-end authority control process.
Owner:BEIJING GRIDSUM TECH CO LTD
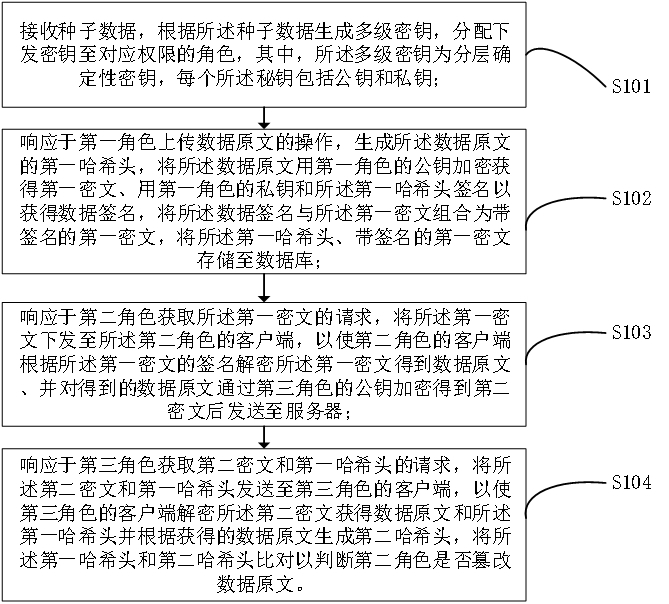
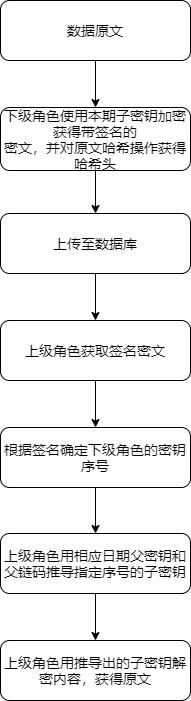
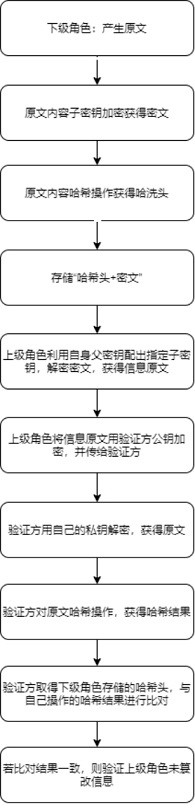
Multi-level role permission control method and device based on cryptography
ActiveCN112422287AReduce development and maintenance costsStrong stability and securityKey distribution for secure communicationUser identity/authority verificationData inputKey (cryptography)
The invention provides a multi-level role permission control method and device based on cryptography, electronic equipment and a storable medium. The method comprises the following steps: dividing a role superior-subordinate relationship according to a service permission demand; controlling the access permission in the spatial dimension through the key encryption and decryption permission; whereina part of roles have verification permission, single original text information needing to be verified is sent to a verification party by a verified party (data input party) or a management party (highest permission party), the verification party performs hash operation on the original text information to obtain a hash head, the hash head is compared with the hash head of the encrypted informationobtained by the verification party, and if the two hash heads are consistent, the verification content is not tampered. The method is suitable for various access permission and verification permission requirements in the space dimension and the time dimension, extremely complex service requirements in real life can also be flexibly realized through simple configuration, and the development cost and the maintenance cost of a permission system are greatly reduced. Based on the cryptography technology, the permission is determined through the secret key, and high safety and stability are achieved.
Owner:杭州城市大数据运营有限公司 +2
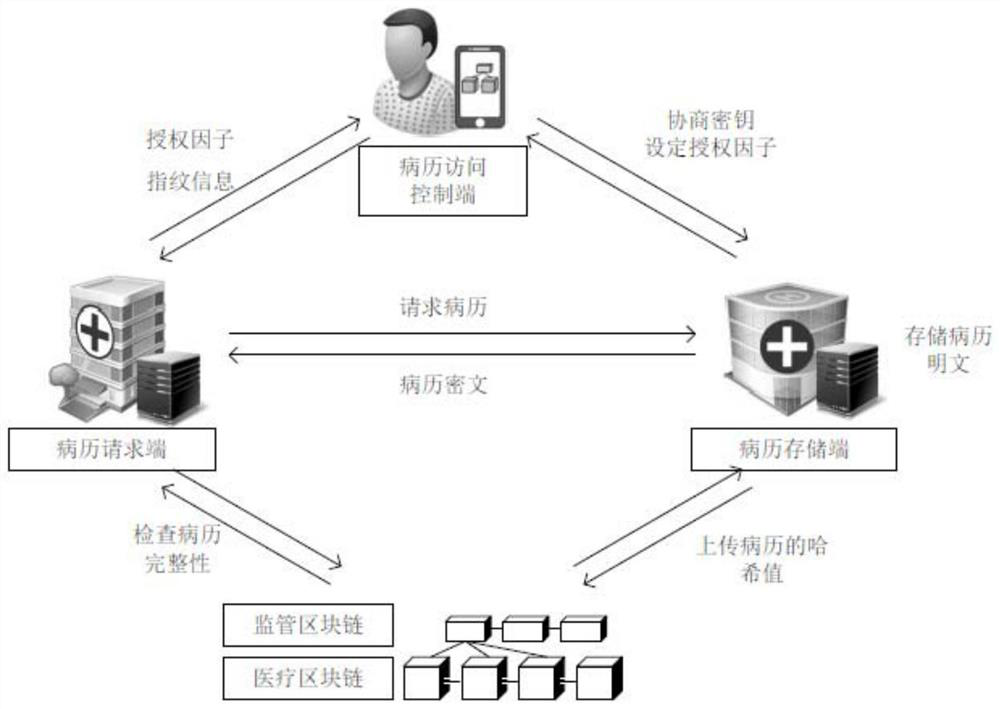
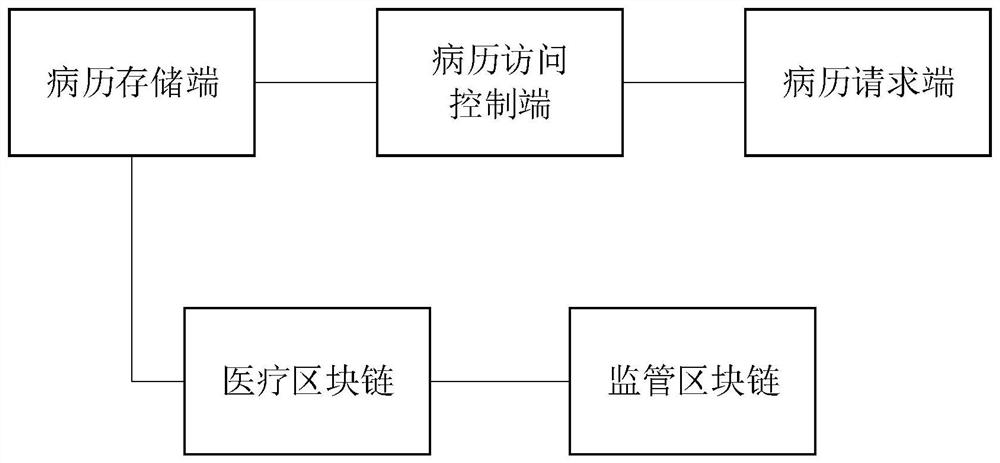
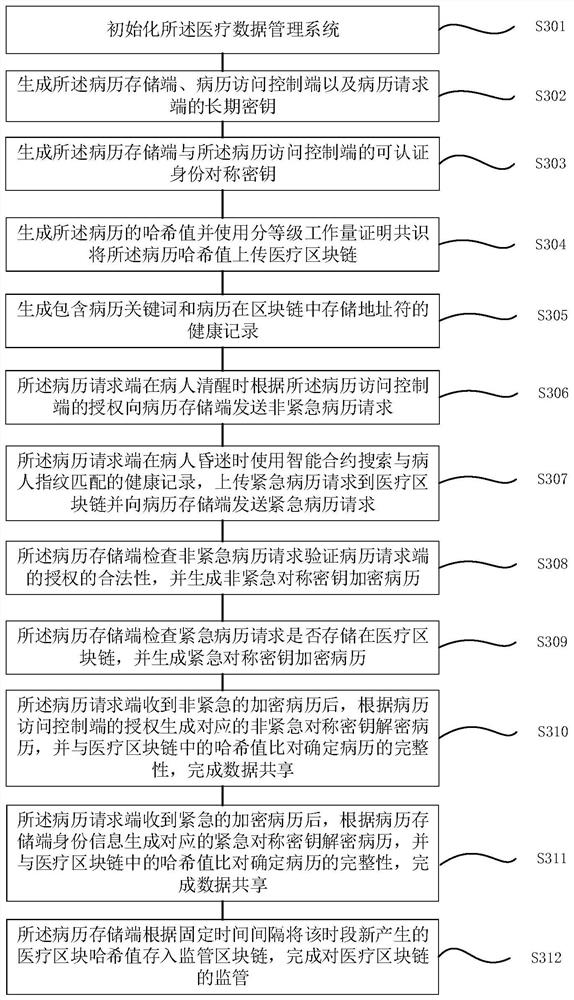
Medical data management system based on double block chains and patient authorized medical record sharing method
PendingCN113764060ADefend against attackAvoid the risk of medical disputesDatabase distribution/replicationDigital data protectionMedical emergencyIn patient
The invention discloses a medical data management system based on double block chains and a patient authorized medical record sharing method, and relates to the technical field of authenticated key negotiation algorithms. The medical data management system comprises a medical block chain, a supervision block chain, a medical record storage end, a medical record access control endfor sending medical record access authorization to a medical record request end and calling an intelligent contract to store health records containing medical record keywords, and a medical record request end which is used for acquiring active authorization and requesting data from the medical record storage end when the patient is awake and calling the intelligent contract to search the health record matched with the fingerprint of the patient when the patient is coma so as to request data from the medical record storage end. According to the system and the method, a graded workload proof consensus mechanism is adopted, the speed of generating the new block is changed according to the emergency degree of the transaction, a double-chain structure is used for supervising the data on the chain, and privately mining attacks are effectively resisted.
Owner:ANHUI NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com