Short message reading method and apparatus
A technology for reading short messages and short messages, which is applied in the field of information security to avoid leakage and achieve the effect of permission control.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
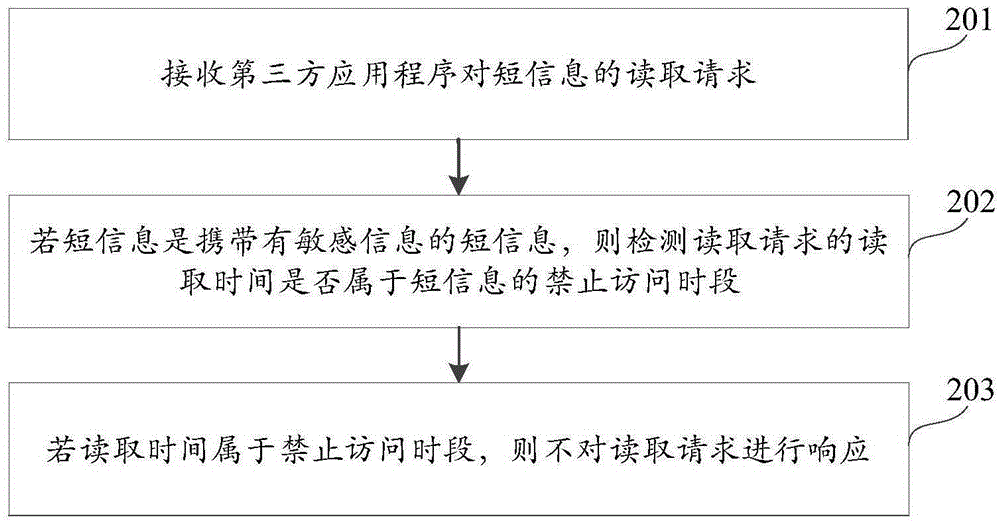
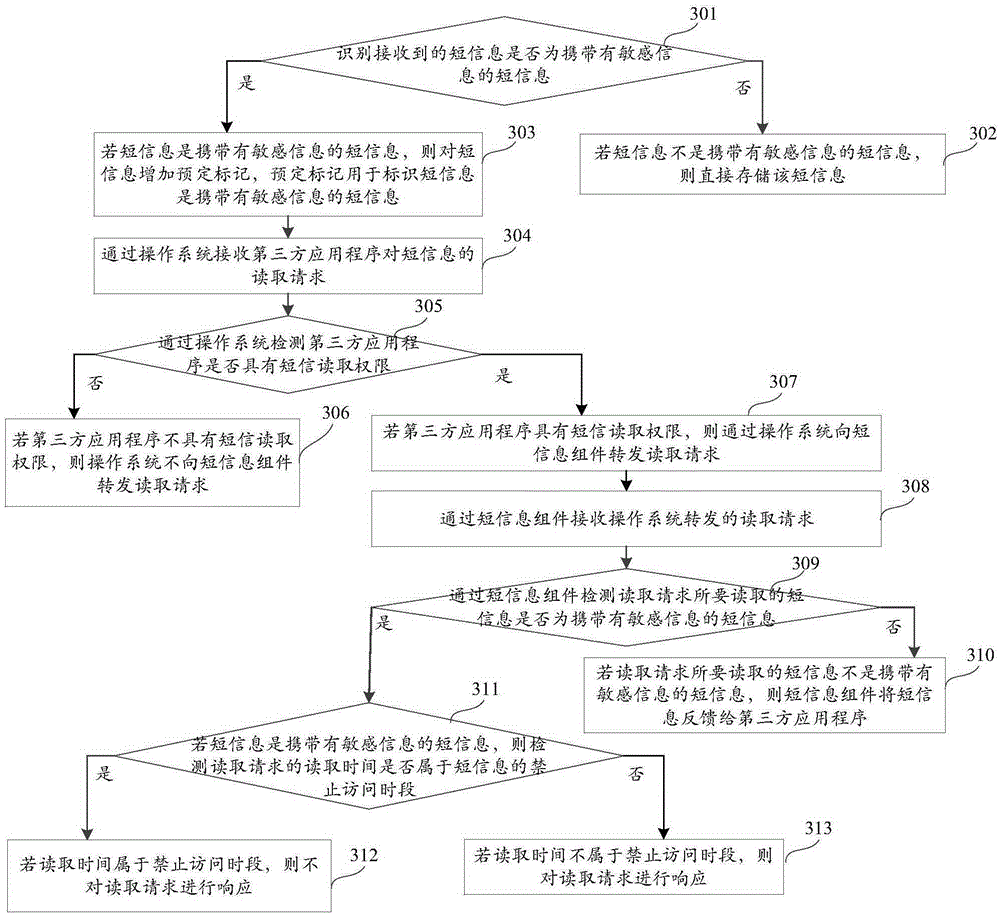
[0095] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0096] First, several nouns involved in this disclosure are briefly introduced:
[0097] Android operating system: a free and open-source operating system based on Linux produced by Google, the United States, mainly used in mobile terminals. The mobile terminal can be a mobile phone, a tablet computer, an electronic book reader, an MP3 player (MovingPictureExpertsGroupAudioLayerIII, moving picture experts compress standard audio layer 3), MP4 (MovingPictureExpertsGroupAudioLayerIV, moving picture experts compress standard audio layer 4) player and a laptop Laptops and more.
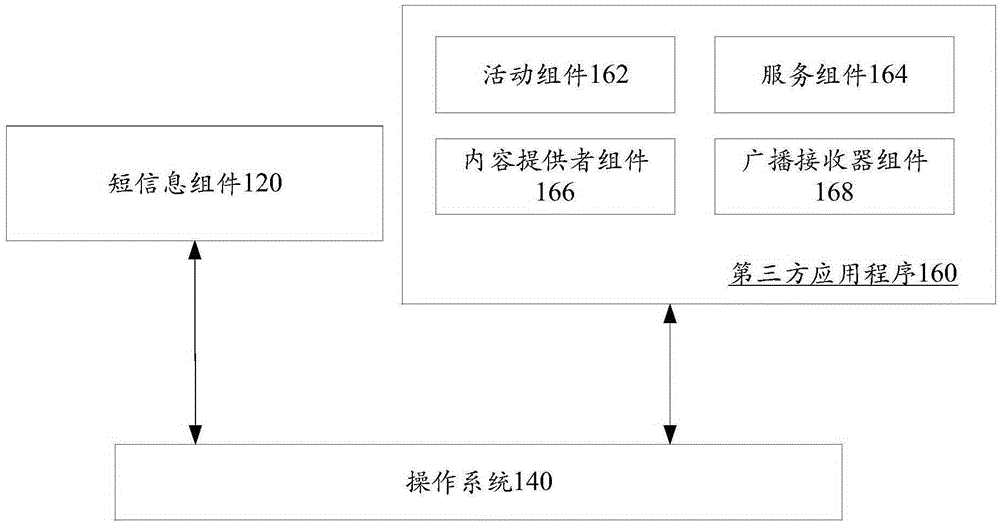
[0098] Application program: In the Android operating system, an application program usually includes at least one program component. Program components are divi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com