Role permission setting method and device
A technology of roles and permissions, applied in the computer field, can solve problems such as no permissions and difficulty in changing, and achieve the effect of flexible setting methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
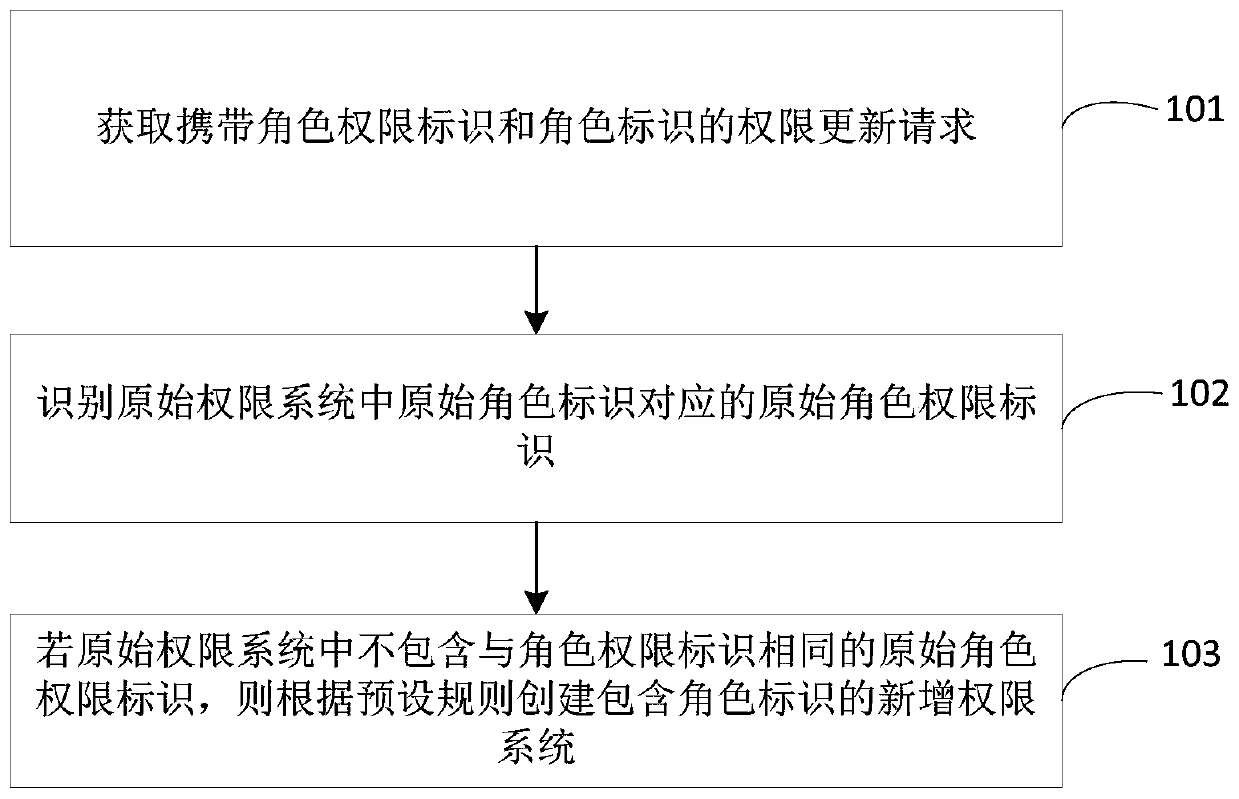
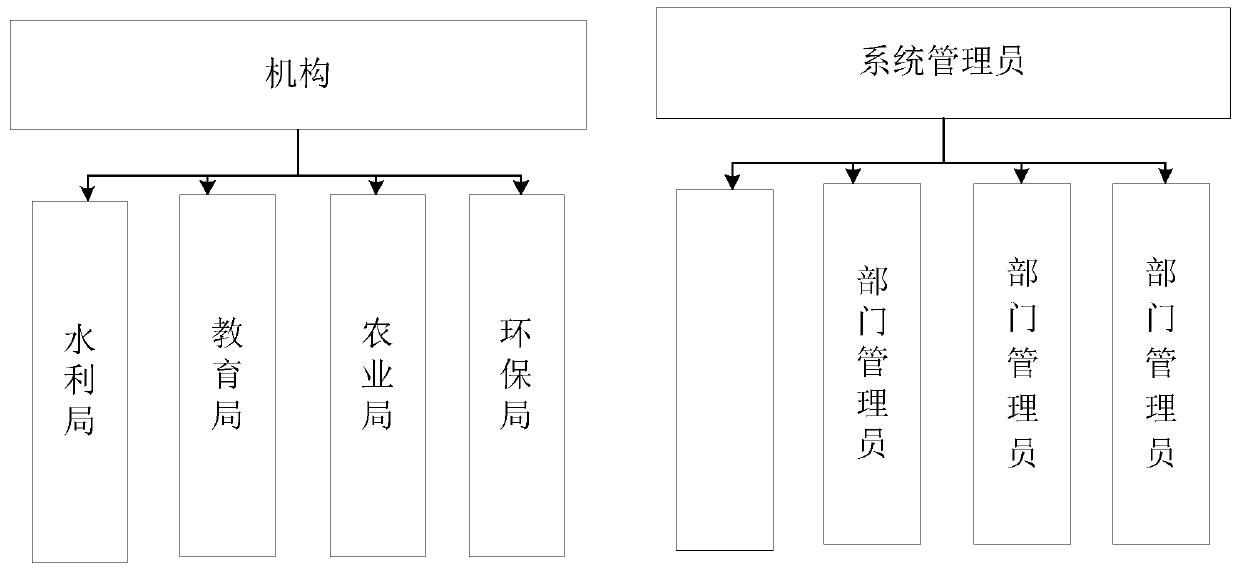
[0042] In this example, create a new administrator account, set the setting permissions corresponding to the new administrator account, and send a permission update request to the new administrator account, so that the new administrator account will be created with the corresponding role ID. Add a permission system, that is, add a new administrator account to perform the configuration of the new management system.
[0043] In this embodiment, it is also possible for the administrator to gradually delegate role authority setting, and the corresponding role authority is set by the upper-level role identifier corresponding to each role identifier, for example, the administrator sets the role authority of the department administrator, The administrator assigns department administrators to set the role permissions of project administrators, etc.
example 2
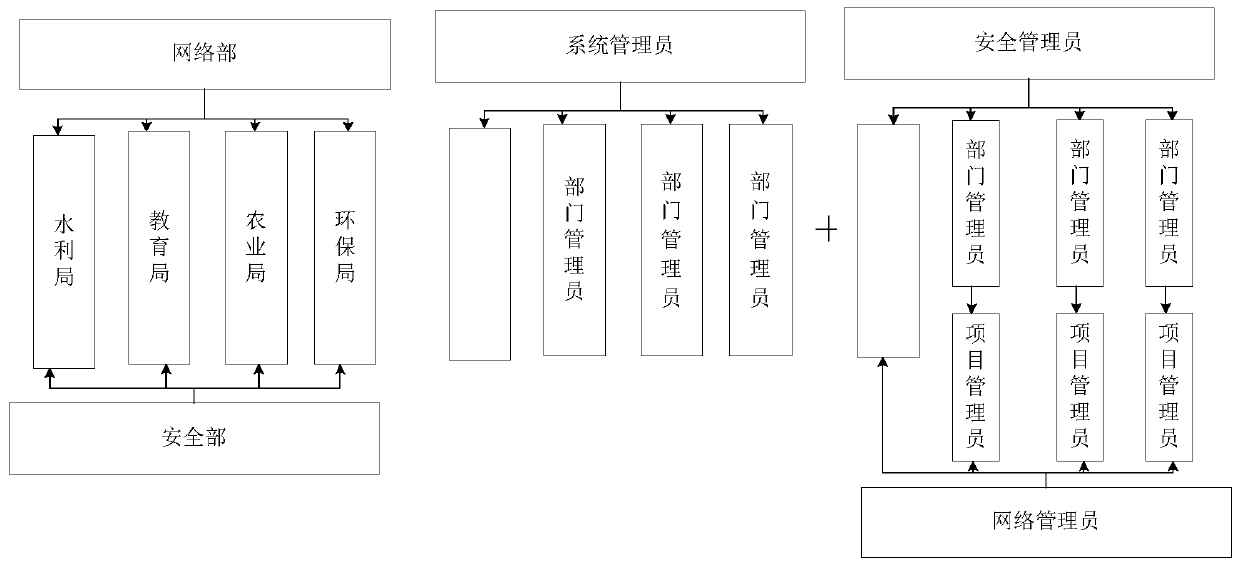
[0045] In this example, considering that in practical applications, role permissions have both functional and hierarchical relationships. For example, department management role permissions are associated with corresponding project management role permissions, and department management role permissions must be hierarchical. It is higher than the project management role permissions, and the lower-level role permissions depend on the higher-level role permissions. Therefore, it is necessary to supplement the high-level role permissions to create a corresponding new permission system.
[0046] Specifically, determine the priority of the role permission identifier carried in the permission update request, which can be obtained by querying the corresponding relationship in advance according to the service level, and then determine that the priority is higher than the role permission associated with the role permission identifier business ID, create a role ID corresponding to the rol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com