Setting method for identifying device
A marker and identification technology, applied in security devices, communication between multiple stations, special services for subscribers, etc., can solve the problems of increased volume, cost, unfavorable expansion of new functions, unfavorable use by non-professionals, etc. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
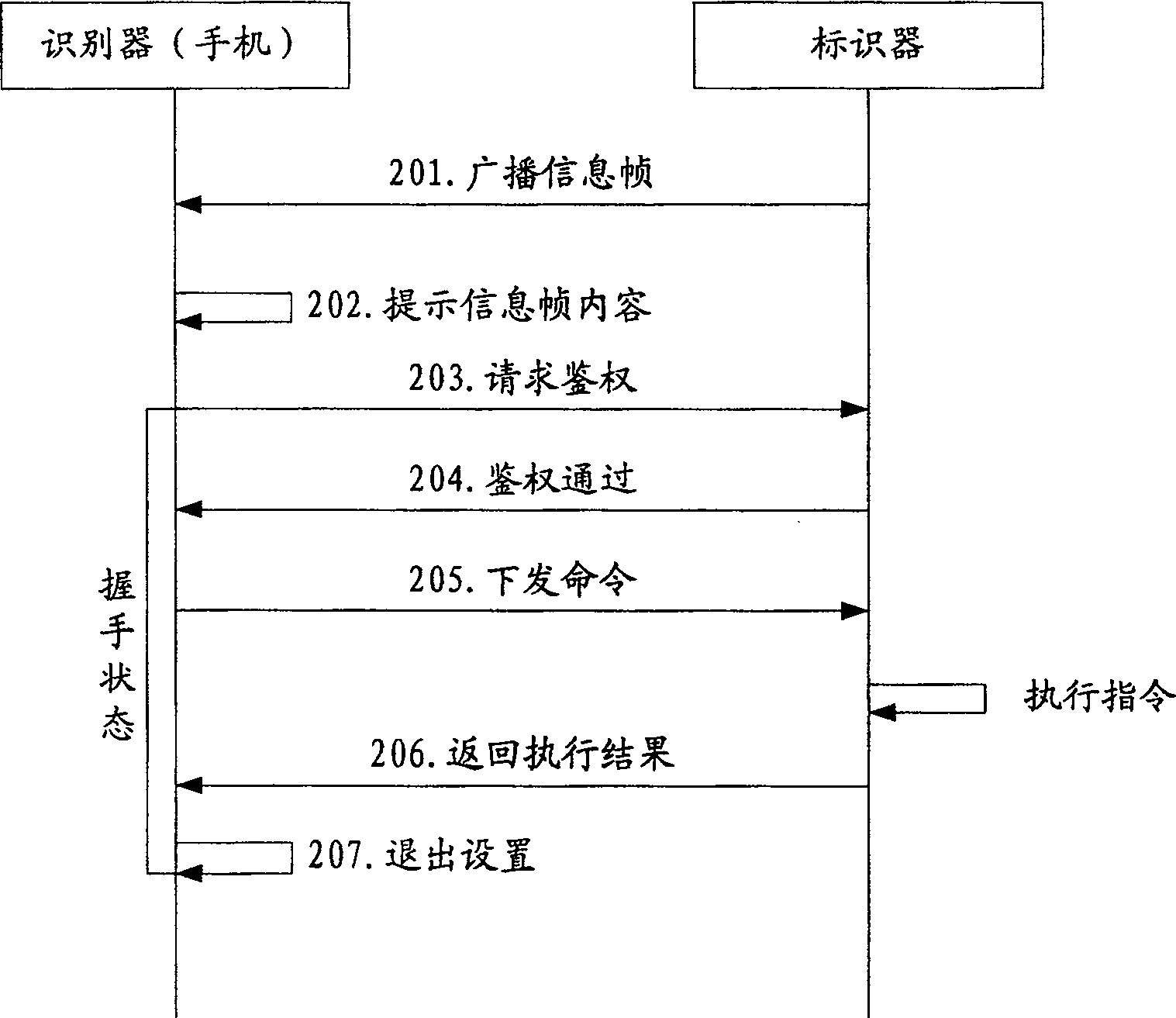
[0025] In the present invention, an input device other than the marker itself is used to configure the marker, such as various wireless terminals. The following uses a mobile phone as an input device for illustration.
[0026] In this example, the identifier is implanted in the mobile phone in advance, so that the mobile phone has the function of the identifier. Using the wireless technology, the mobile phone searches for the marker, interacts with the marker through the information frame, and sets the marker.
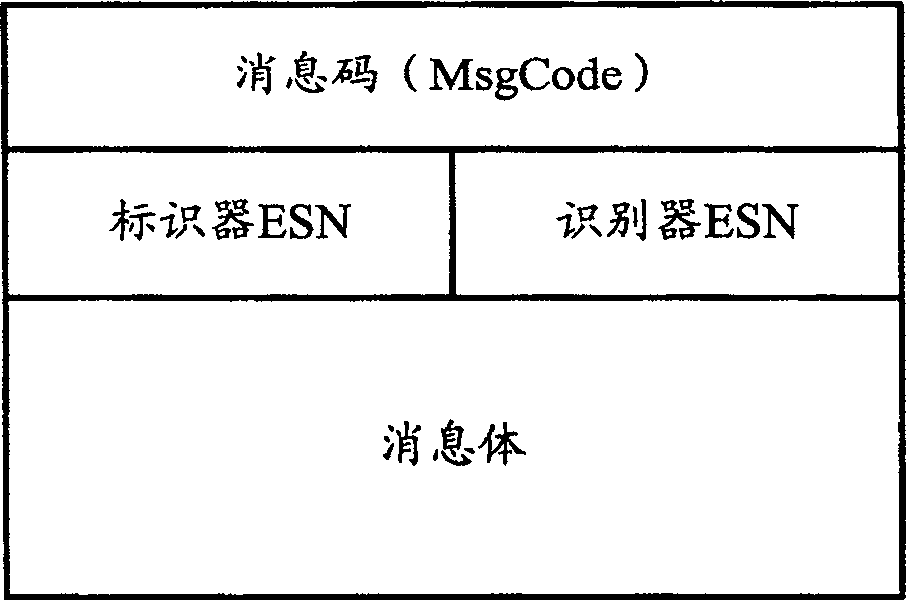
[0027] figure 1 It is the information frame structure diagram used in the interaction process between the mobile phone and the marker. Such as figure 1 , The information frame is mainly composed of a message code (MsgCode), an identifier electronic serial number (ESN), an identifier ESN, and a message body. ESN is the serial number solidified into the device when the device leaves the factory, and is used to identify different devices. Here, the identifier ESN is us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com