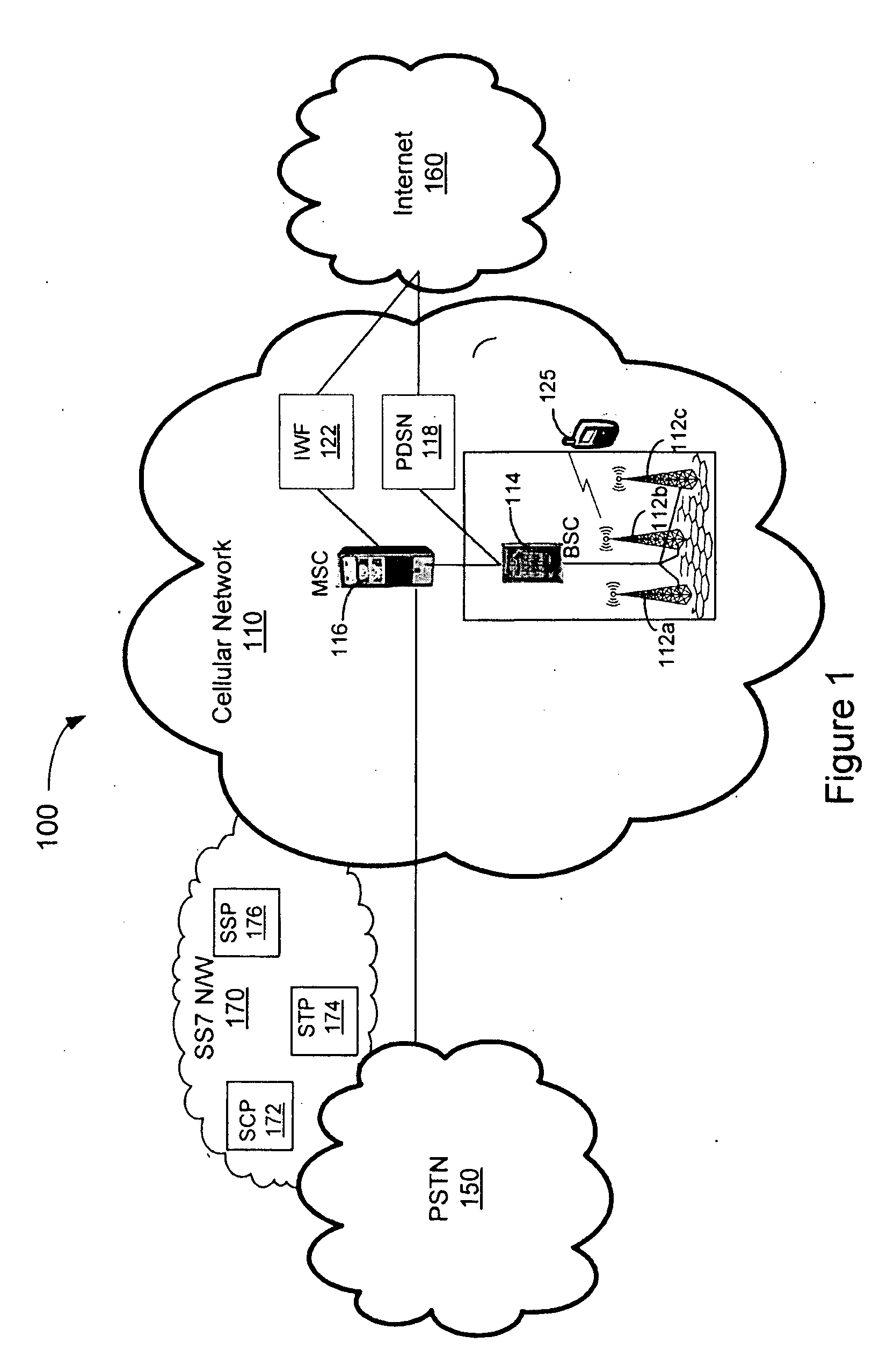
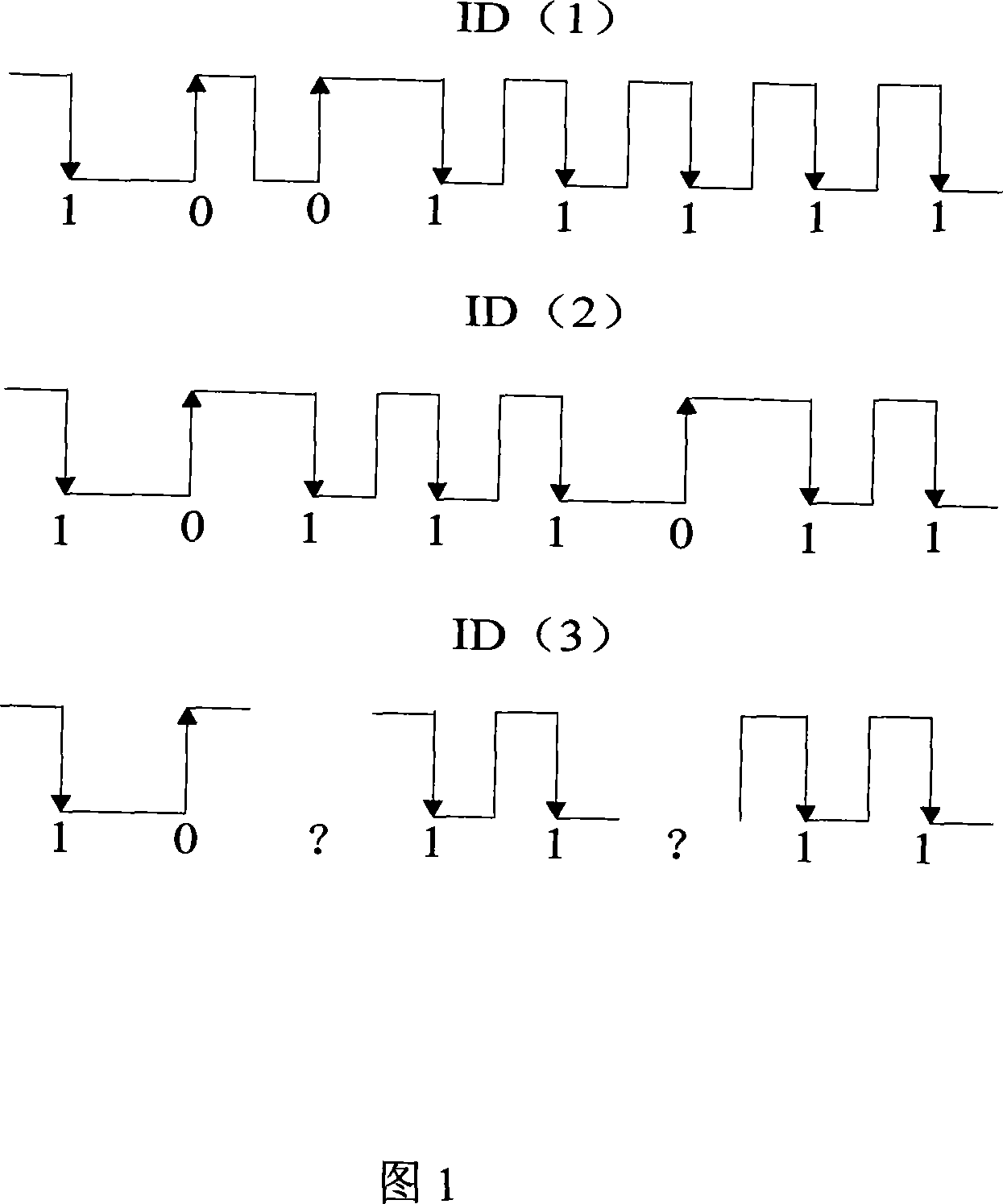Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
106 results about "Electronic serial number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic serial numbers (ESNs) were created by the U.S. Federal Communications Commission (FCC) to uniquely identify mobile devices, from the days of AMPS in the United States starting in the early 1980s. The administrative role was taken over by the Telecommunications Industry Association in 1997 and is still maintained by them. ESNs are currently mainly used with CDMA phones (and were previously used by AMPS and TDMA phones), compared to International Mobile Equipment Identity (IMEI) numbers used by all GSM phones.
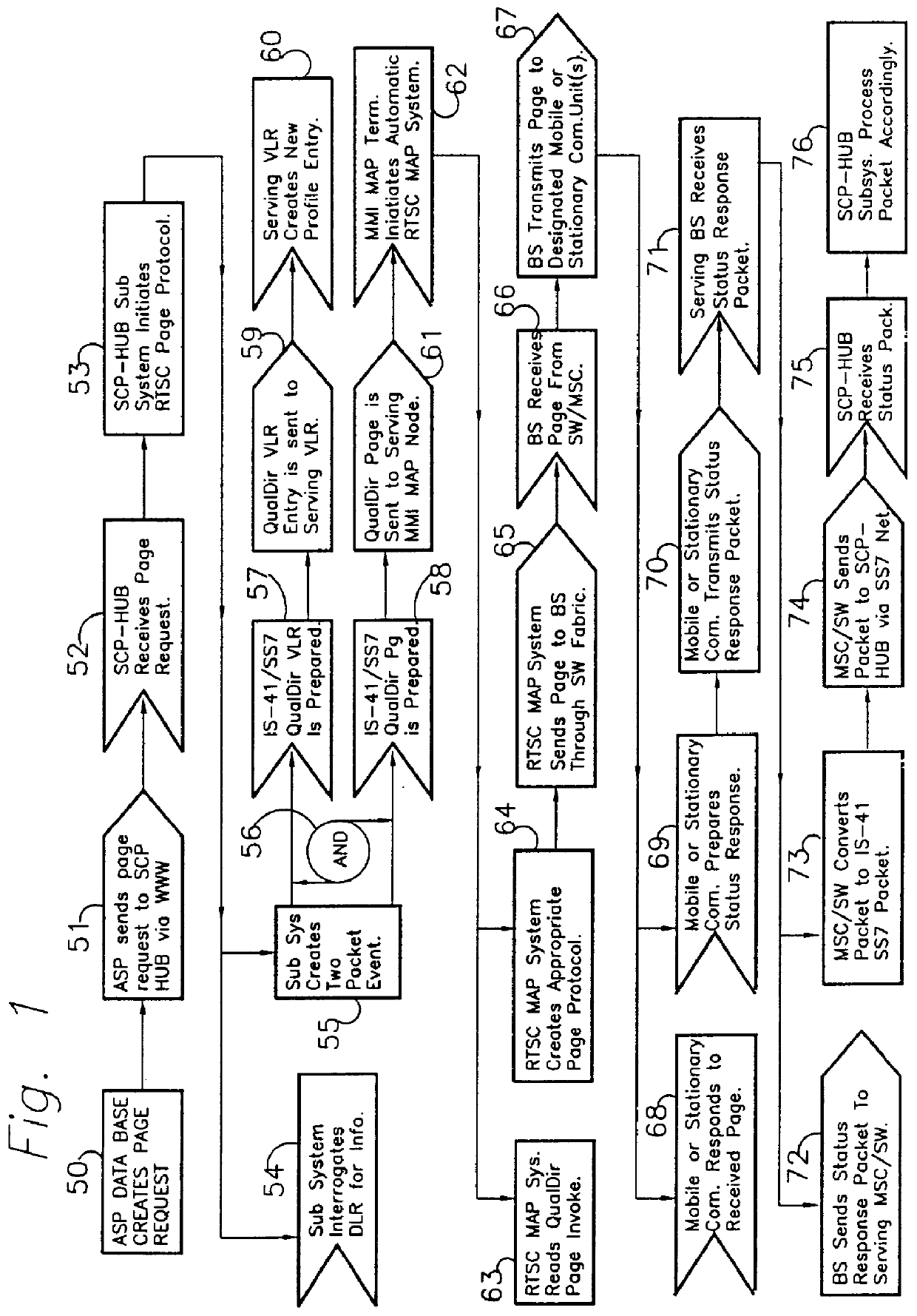
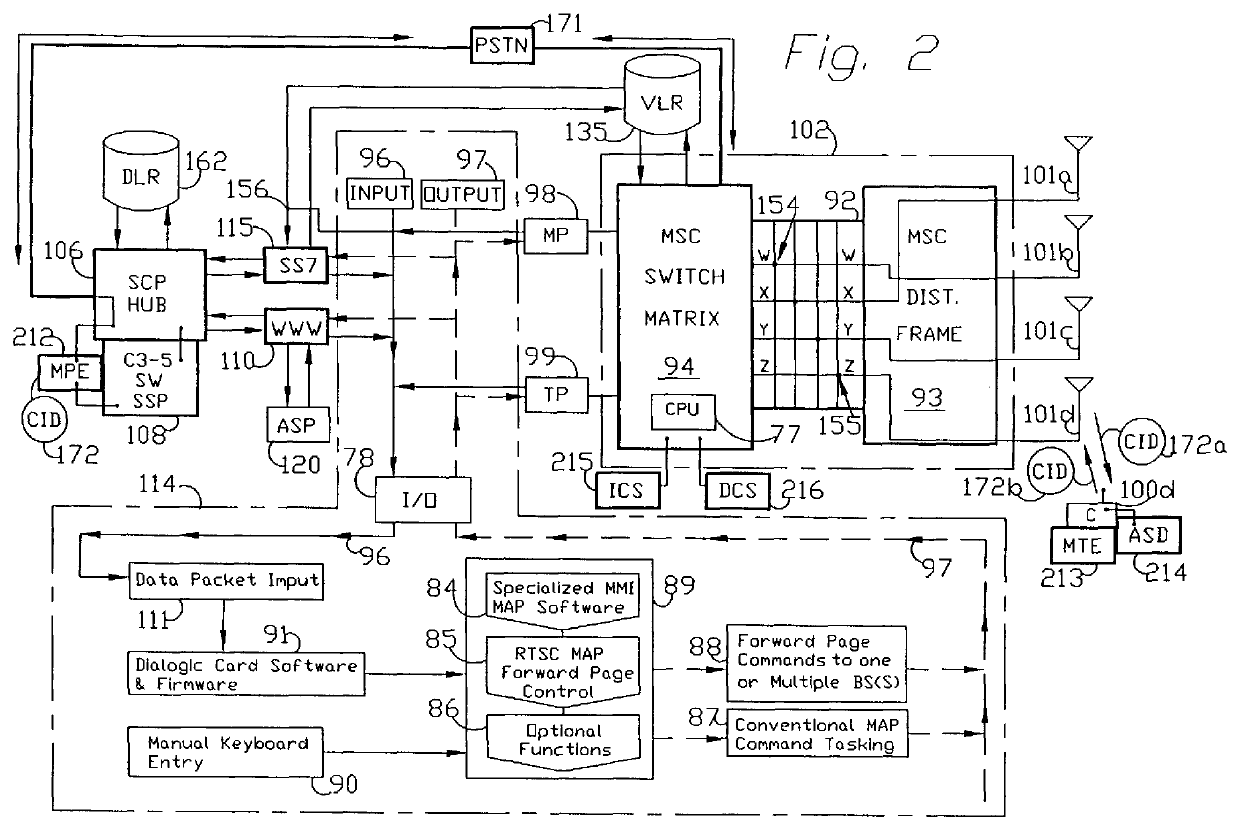
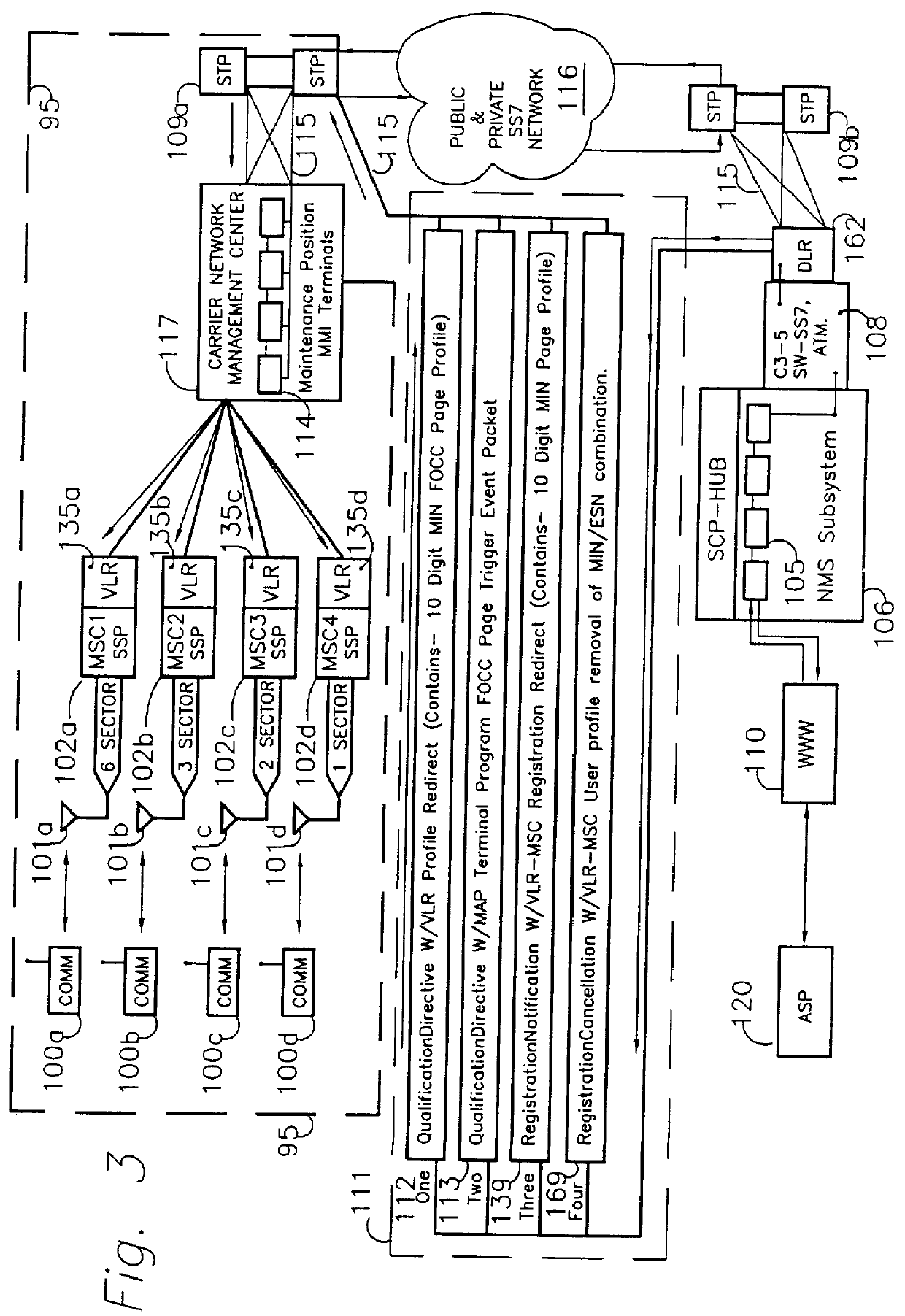
Method and apparatus for remote telephony switch control
InactiveUS6070070AEnabling message/page call delivery (MPCDMultiplex system selection arrangementsTelemetry/telecontrol selection arrangementsMobile identification numberElectronic serial number
A command, such as an application specific command, is communicated from a central host to a remote station via a cellular mobile radio network. The station may be a fixed or roaming device. The central host sends the command a network switch, such as an SS7 SSP, wherein the command comprises a mobile identification number (MIN) and an electronic serial number (ESN). The network switch queries an associated HLR database to locate the remote station, the query specifying the MIN and the ESN. If the HLR does not recognize the MIN / ESN combination, it so informs the network switch, as well as the VLR associated with the MSC serving a remote station identified by the ESN. In response to the notification from the HLR, the VLR removes any entry in its database relating to the ESN and updates its database with the new MIN / ESN combination transmitted by the HLR to the VLR. The VLR confirms with the HLR that it has taken these steps and then sends the command to the remote station by calling the station using the new MIN / ESN.
Owner:AERIS COMM
Method for providing differing service levels in a wireless telecommunications network
ActiveUS7206593B1Radio/inductive link selection arrangementsRadio transmissionMobile identification numberTelecommunications network
A mobile station in a wireless network can be assigned a priority level. The wireless network may support two or more different priority levels. A mobile station's priority level may be stored in a database containing other identifiers, such as the mobile station's electronic serial number and mobile identification number. The priority level can be stored as a part of a profile in the home location register or in a visitor location register. When the mobile station attempt to access the wireless network, the access request can be serviced based on the priority of the mobile station. The access request may also be serviced based on a current usage status of the wireless telecommunications network. Mobile stations with higher priorities may receive a preference for access to the wireless network's resources. Mobile stations with lower priorities may be disconnected from the wireless network to accommodate a higher priority mobile station.
Owner:SPRINT SPECTRUM LLC
Collection of enhanced caller ID information
ActiveUS20050232247A1Enhanced identification informationTelevision system detailsError preventionComputer networkEmail address
Network entities such as an access device and a gateway analyze messages exchanged during a communication session to identify information items of interest such as, for example, email addresses, universal resource locators, file paths, and attachments. References to and / or the contents of the identified information items may be stored in a database that associates the identified information items with the participants of the communication session. The participants in the communication session may be identified by conventional caller ID information, or by an Internet protocol address, an electronic serial number, or a variety of other identifiers. Information received at the beginning of a later communication session that identifies participant(s) in that communication session may then be used to select from the database, information items from previous communication session, that are associated with the identified participant in the current communication session. Information about the selected information items may be delivered as enhanced caller ID information to parties of the communication session, allowing them to have easy access to the previously exchanged information.
Owner:AVAGO TECH INT SALES PTE LTD
Method and apparatus for securely activating a credit card for a limited period of time
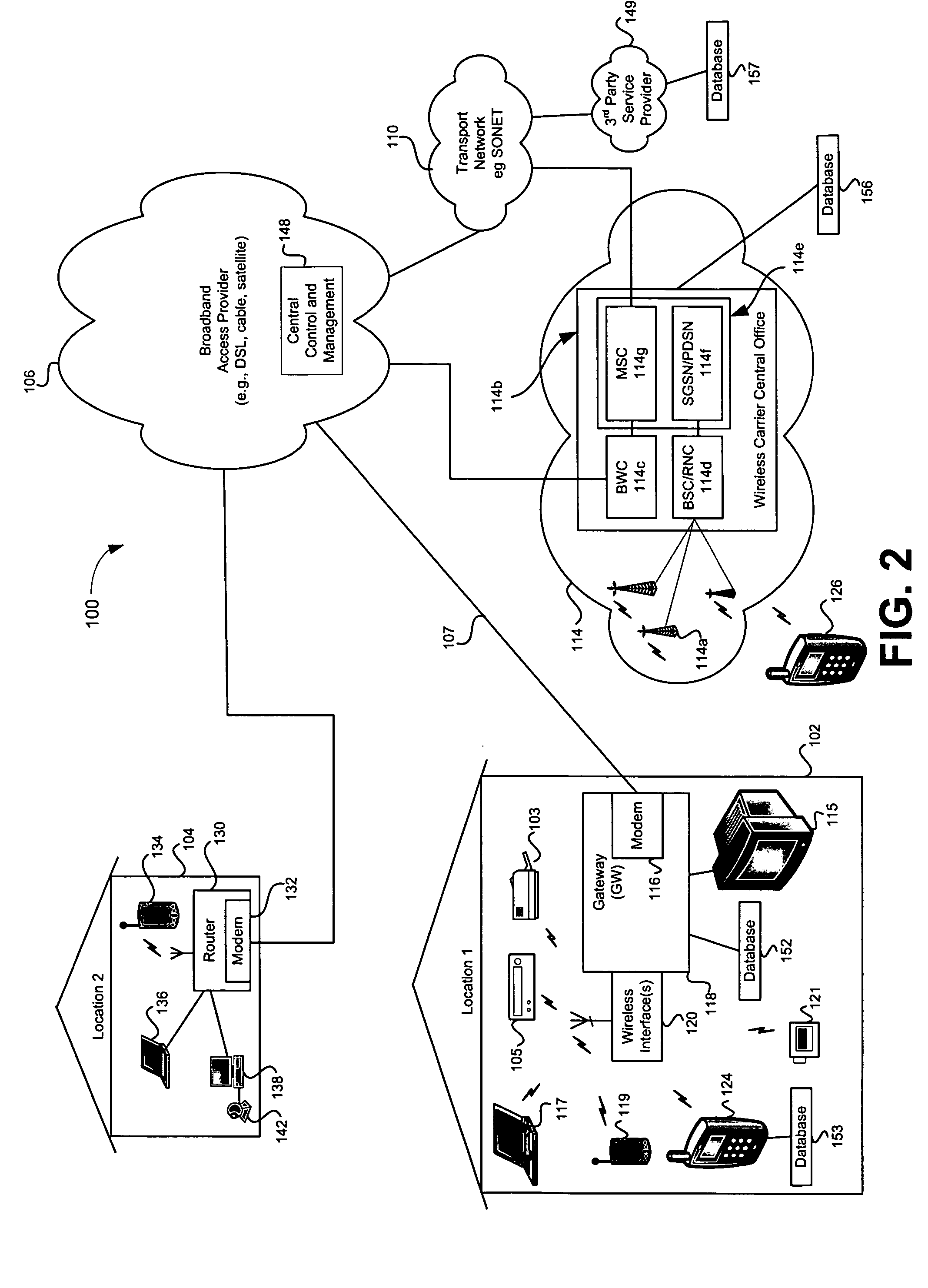
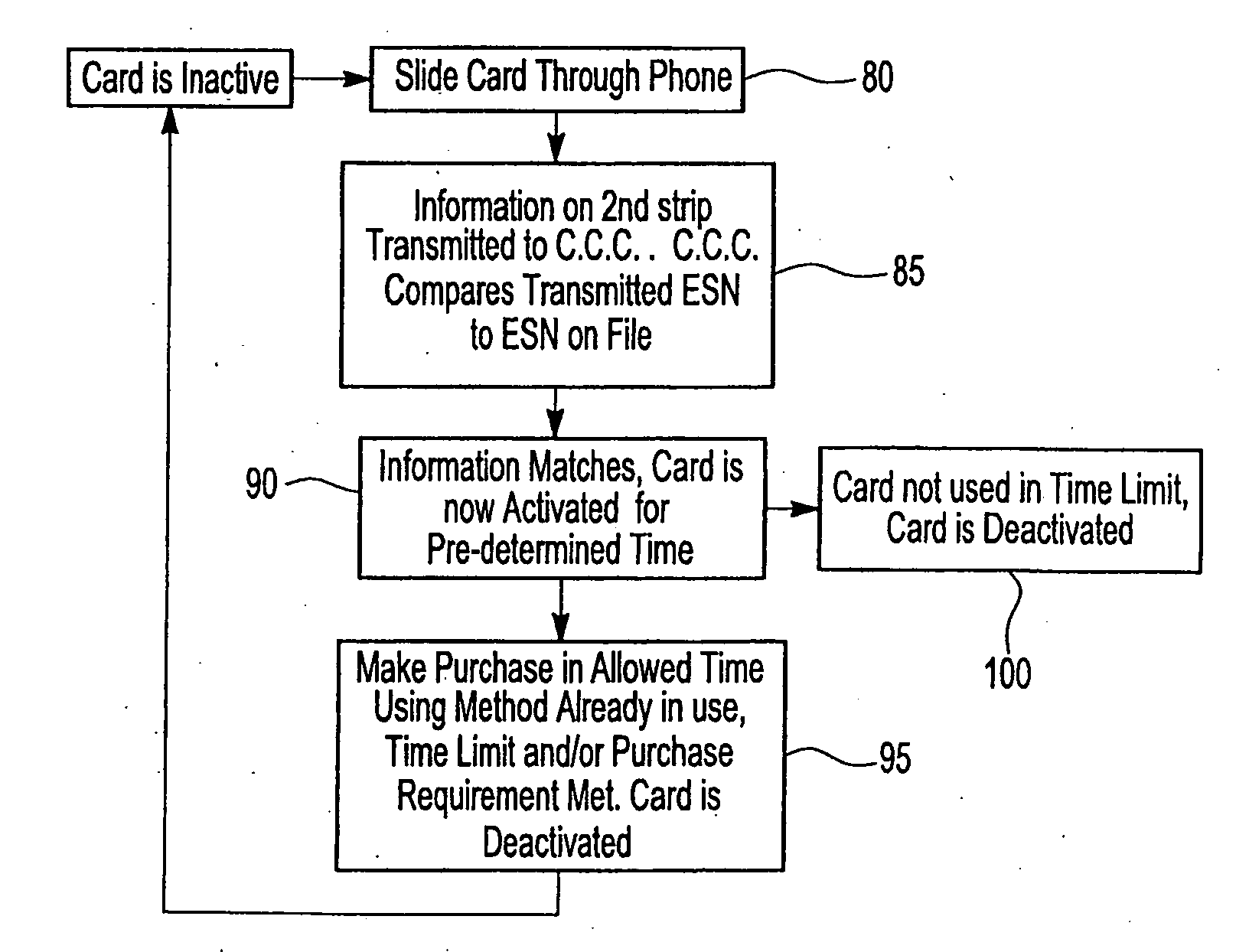
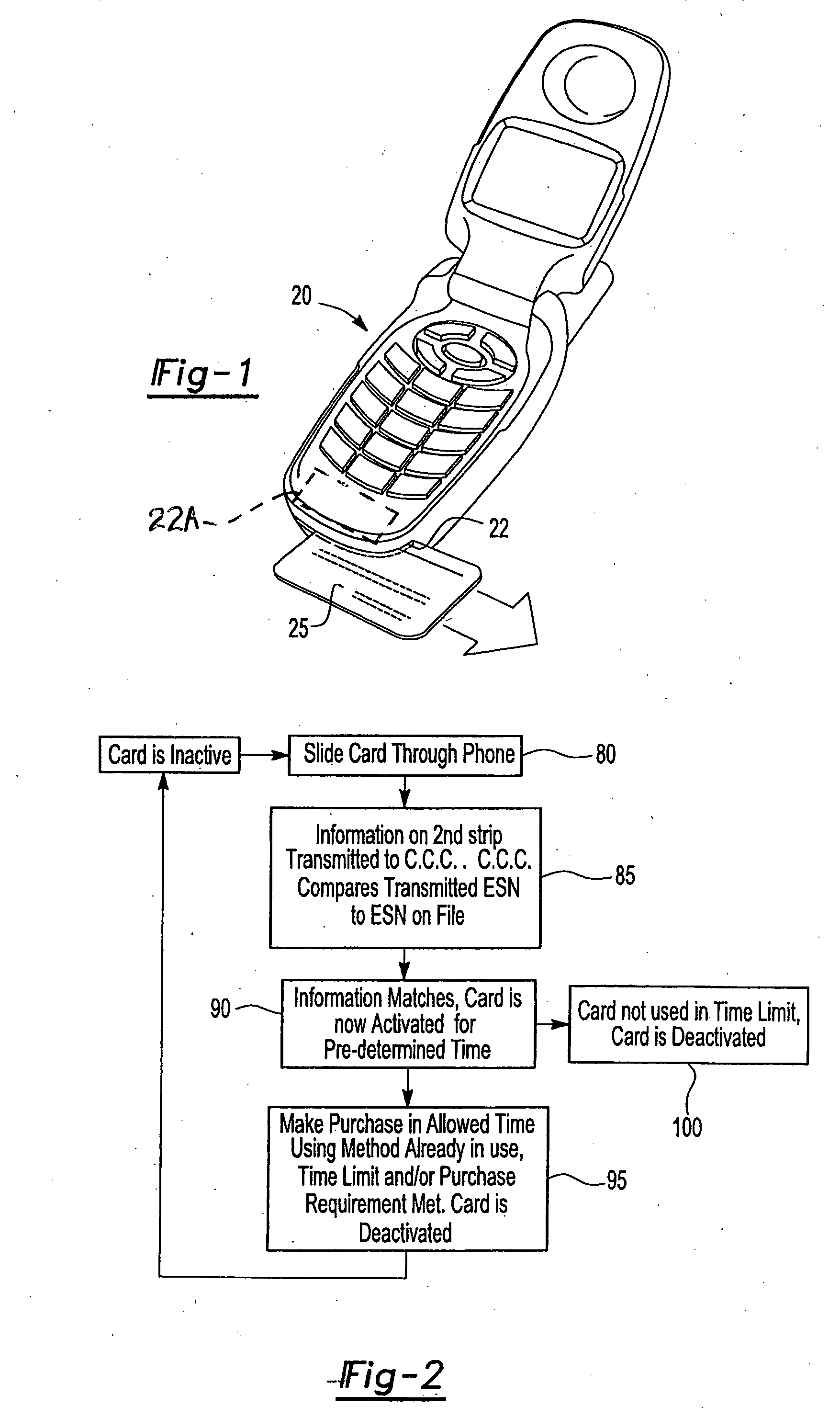
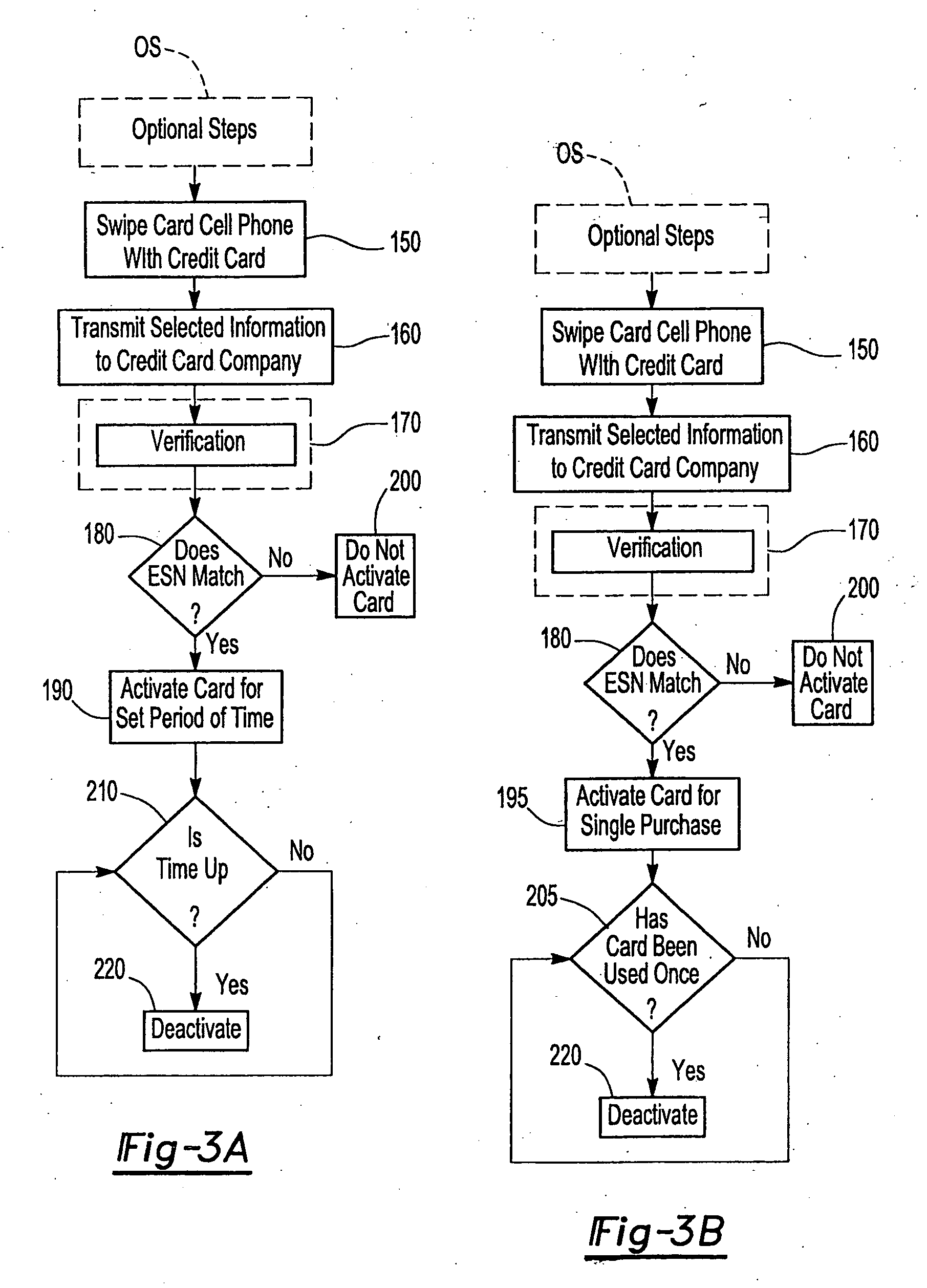
An apparatus and methods securely activate a credit or debit card for a single purchase, a predetermined amount of time, or a predetermined amount of purchases in a predetermined amount of time, while utilizing a portable phone, especially a cell phone, having a card reader. Only transactions using the electronic telephone number and electronic serial number of the cell phone being used, along with preselected information identifying the owner of a swiped card will be authorized to perform credit and debit card transactions, thus providing secured transactions. Current card magnetic strips and possibly magnetic or other type of strips that are smaller in size and closer to the edge of the credit or debit card are serviced.
Owner:WORONEC JOHN S
System and method for using a temporary electronic serial number for over-the-air activation of a mobile device
InactiveUS20080171532A1Accurate procedureUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile identification numberElectronic serial number
A system and method for activating a subscriber identification module (SIM) based mobile device in a PCS / ANSI type wireless network. The method comprises pre-programming the SIM card of the mobile device with temporary activation identifiers, such as an international mobile station identity (IMSI) and / or a mobile identification number (MIN), and a temporary electronic serial number. The temporary electronic serial number, rather than the mobile device actual electronic serial number, is used to identify the mobile device during registration and activation. The network identifies the temporary electronic serial number associated with the SIM vendor and invokes an over-the-air activation procedure especially for the SIM card mobile devices. A SIM-over-the-air-activation processor is notified to perform the activation for that mobile device on the PCS wireless network. Authentication of the mobile device may be bypassed and the mobile device is instructed to transmit its actual electronic serial number for future registrations. Once the activation process is completed, the temporary activation identifiers are overwritten.
Owner:AT&T WIRELESS SERVICES
Wireless module security system and method
ActiveUS7460853B2Television system detailsUnauthorised/fraudulent call preventionComputer hardwareWireless transmission
A wireless module security system and method is provided which includes, in one embodiment providing security data to a wireless module. The security data including a security code provided to the wireless module after the wireless module has been activated. The method for providing the security code includes encrypting the security code after establishing a wireless module account, issuing the security code through wireless transmission to the wireless module, and decrypting and storing the security code inside the wireless module. The security system and method also utilizes user authorized associated peripheral devices which may be connected to the wireless module to provide further combinations of security data. In one embodiment, the wireless module is provided with an electronic serial number and that electronic serial number is stored to the peripheral device for a security measure. In another embodiment, the peripheral device is provided with peripheral device data and that peripheral device data is stored inside the wireless module for a further security measure. The wireless module is removably connected to any number of user authorized peripheral devices, and thus the wireless module security system and method is provided upon wireless module and peripheral device initialization.
Owner:SONY CORP +1
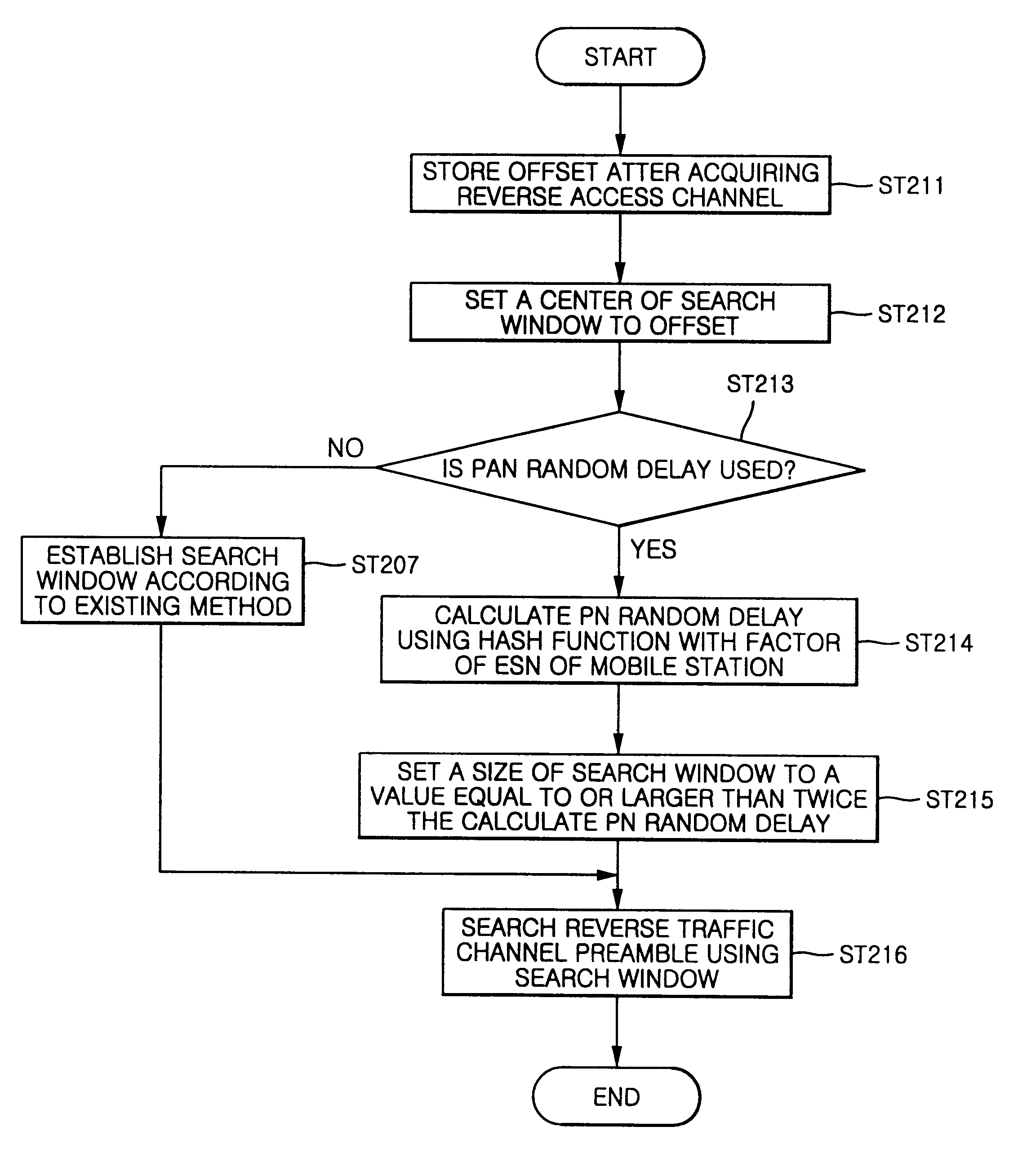
Method of searching reverse traffic channels in a CDMA mobile radio communication system
A method of searching reverse traffic channels in a code division multiple access (CDMA) mobile radio communication system for allowing for acquisition of reverse traffic channels without increase or decrease of size of a search window for traffic channels, the method comprising the steps of: storing an offset by a propagation delay after acquiring a reverse access channel; determining whether or not a pseudonoise (PN) random delay is employed for the reverse access channel and, when the PN random delay is used, calculating the PN random delay using a hash function with a factor of an electronic serial number (ESN) transmitted from a mobile station; computing the stored offset and the PN random delay and setting a new offset to a result of the computing; setting a center of a search window for searching the reverse traffic channel to the new offset and establishing the search window; and searching a reverse traffic channel preamble with the established search window.
Owner:TRANSPACIFIC SONIC
System for identifying mobile terminal device automatically and value added service access
InactiveUS7715824B2Earn incomeWide range of servicesDigital data processing detailsUser identity/authority verificationEmail addressNetwork communication
An automatic identification system of mobile terminal equipment, which consists of the mobile terminal equipment, mobile network communication platform and mobile terminal equipment service center. The mobile terminal equipment is provided with subscriber information handling means for transmitting terminal subscribers information to mobile terminal service center through communication channels of the mobile network communication platform. The mobile terminal equipment service center compares the terminal subscriber information with that in its database and then identifies and processes said terminal subscribers information. The terminal subscriber information includes the electronic serial number, terminal subscriber ID identification, terminal software version number and any one or any combination of two or more of the followings: network ID identification, base station number, short message center number Email address, LP internet protocol address and the information of registration place in subscriber identification card.
Owner:HANGZHOU EASYCOMM TECH
Methods for authentication using near-field
ActiveUS20110238995A1Random number generatorsEncryption apparatus with shift registers/memoriesElectronic serial numberAuthentication
Authentication methods are used to authenticate, a device1 having an ESN1 (electronic serial number), a device2 having an ESN2, and / or a user of the devices. In one implementation, device1 receives the ESN2 in a near-field signal; derives an authentication result as a function of the ESN1 and ESN2; and sends the authentication result to an authenticator device to use in completing authentication. Authentication is confirmed when the device1 authentication result matches an authentication result independently generated by the authenticator device, which is provisioned with the ESN1 and ESN2. In a second implementation, device1 generates a RAND1 (random number) and sends the RAND1 to device2 over a near-filed link. An authenticator device confirms authentication upon receiving the same RAND1 from both device1 and device2.
Owner:MOTOROLA SOLUTIONS INC
Self-identifying electrical connector
ActiveUS20090149037A1Easy to operateRotary current collectorElectric discharge tubesElectricityEngineering
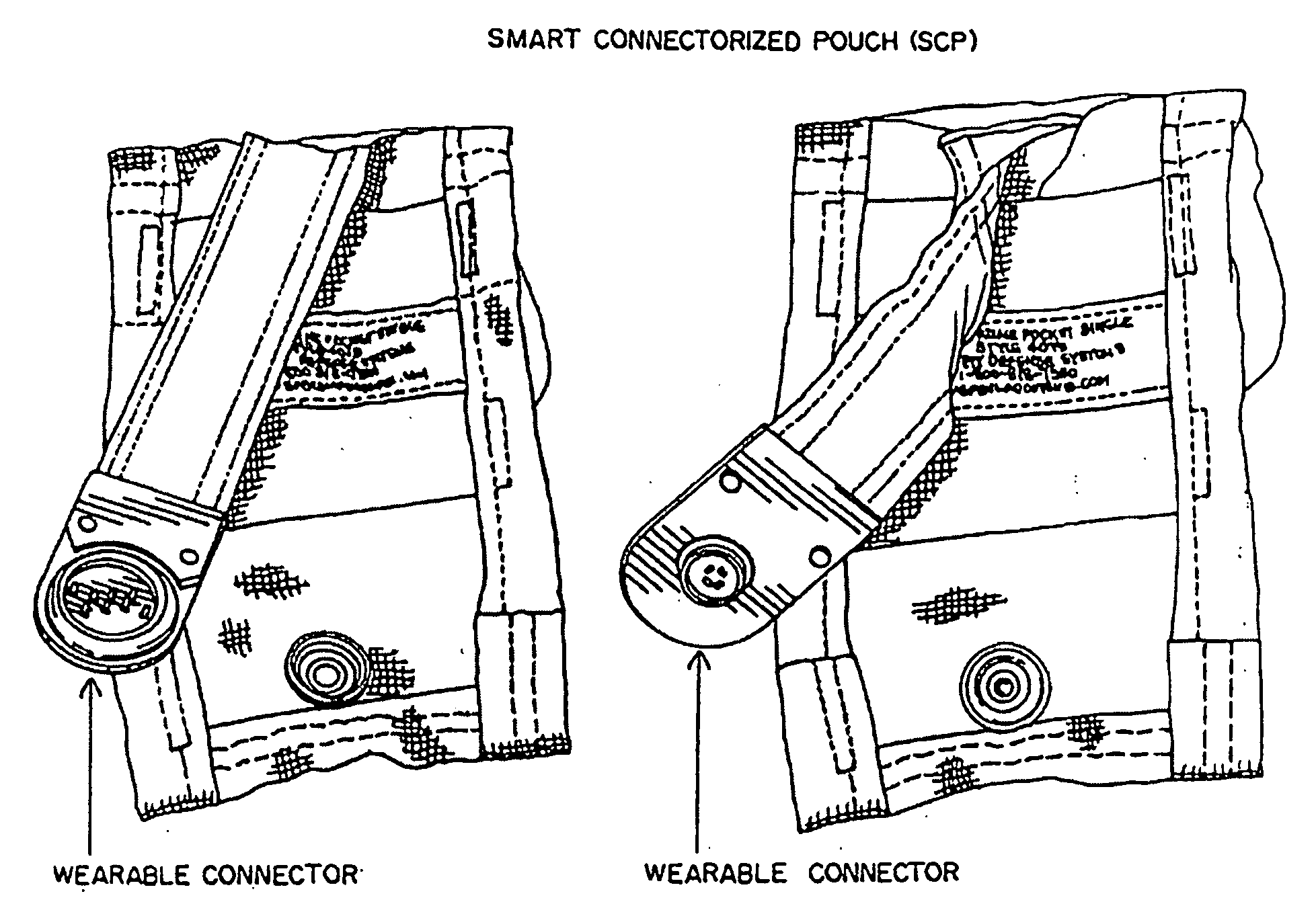
An entirely wearable electrical connector for power / data connectivity. The principal element of a modular network is the wearable electrical connector, which is integrated into a personal area network with USB compatibility. Several wearable connector embodiments are disclosed. An enhancement to the wearable connector includes OSI Layer 2 (and potentially Layer 3) functionality. Data Link layer functionality is supported by including electronic serial numbers at wearable snap-connector points.
Owner:INTELLISENSE SYST INC
Two-tiered authorization and authentication for a cable data delivery system
InactiveUS6324267B1Prevent illegal useLoss of revenueBroadband local area networksCode conversionModem deviceDelivery system
Apparatus for a cable television subscriber to log onto a computer network with a modem over an upstream path using a USERID and password. The network validates the subscriber USERID and subscriber password with a stored database of valid USERIDs and associated passwords. After the USERID and password are validated, the modem then provides its electronic serial number to the network for validation against a stored database of authorized serial numbers. Upon additional validation of the modem's serial number, the subscriber is authorized to use the network.
Owner:CISCO TECH INC
Overlay calling plan for wireless telephone
InactiveUS20050113091A1Accounting/billing servicesTelephonic communicationMobile identification numberRoaming
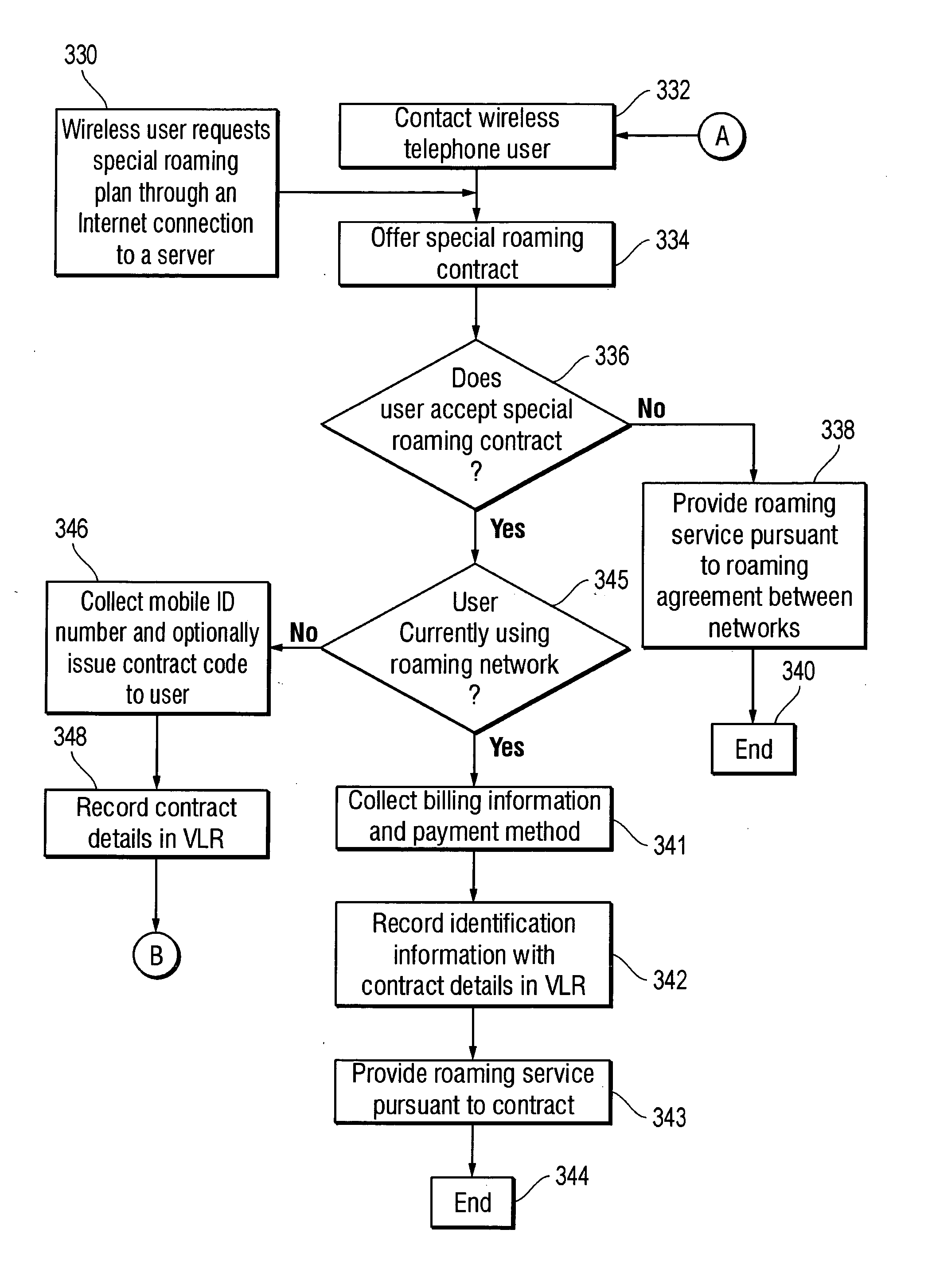
Methods, systems and computer program products for providing roaming services to a wireless telephone roaming outside of its home service area by receiving a request for roaming service from a wireless telephone that is within a roaming network and offering a special roaming contract to the user of the wireless telephone. The request for services comprises an identify of the wireless telephone wherein the identity comprises the mobile identification number and the electronic serial number. Using the identity of the wireless telephone received in the request, the roaming network determines that the wireless telephone identity is not recorded as a record within the roaming network and is therefore roaming. The method provides offering a special roaming contract to the user and then executing the special roaming contract if the user decides to accept the offer for a special roaming contract.
Owner:IBM CORP
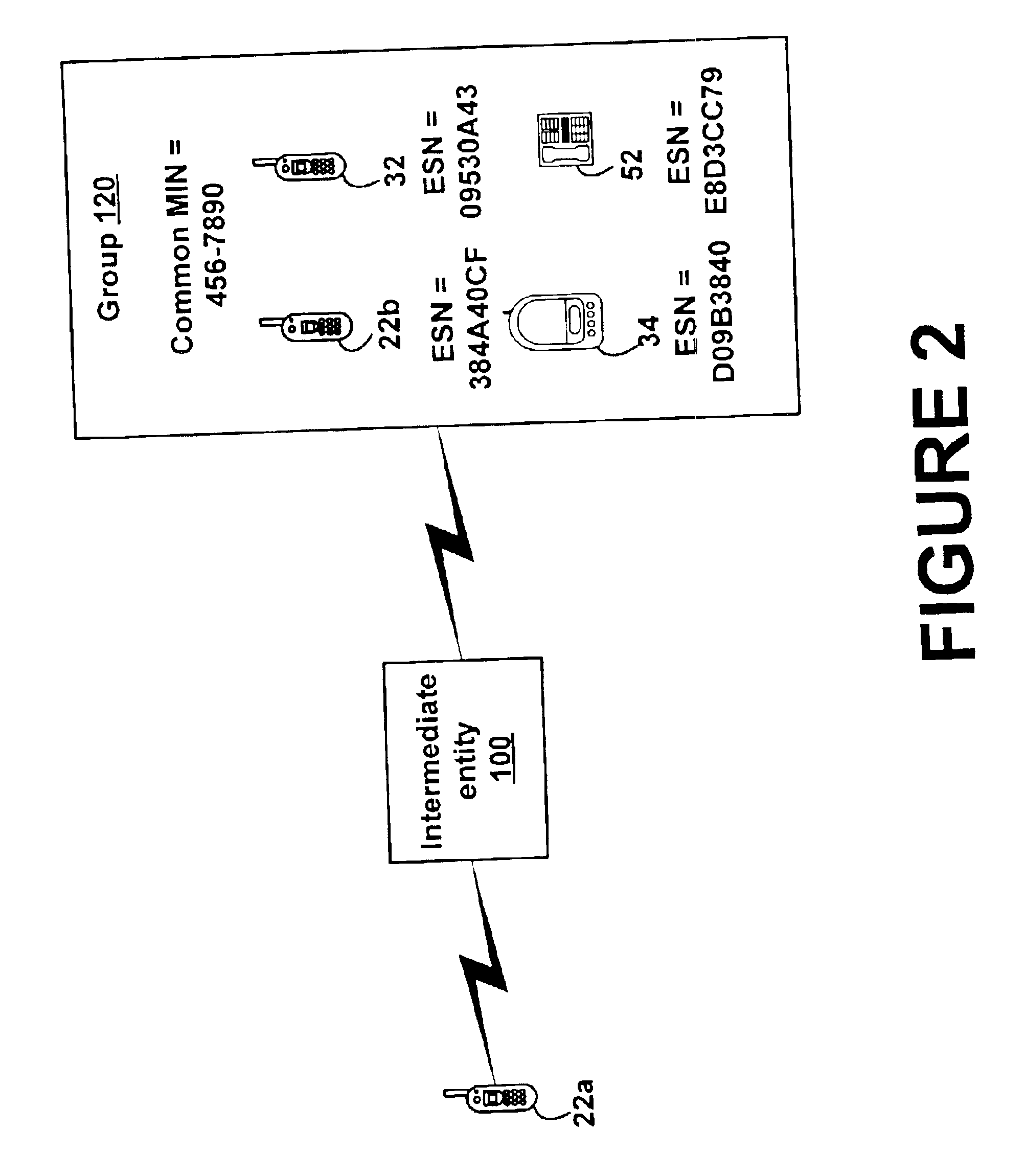
Method and system for serving multiple subscriber stations under a common subscriber ID
InactiveUS7155226B1Saving in quantityAvoiding termination conflicts among the mobile stationsSubstation equipmentRadio/inductive link selection arrangementsMobile identification numberComputer network
A method for serving multiple mobile stations under a common mobile identification number (MIN). A service provider assigns the common MIN to multiple mobile stations and maintains a subscriber profile that associates the MIN with the electronic serial numbers (ESNs) of the mobile stations. However, the service provider allows the MIN to be associated with at most one mobile station that is arranged to respond to a MIN-based termination message. As a result, when the service provider seeks to terminate a call through signaling keyed to the MIN, only one of the mobile stations will respond (e.g., begin to ring). At the same time, all of the mobile stations having the common MIN can originate calls through signaling keyed to their MIN and ESN (since the MIN / ESN pair should uniquely identify the originating station).
Owner:SPRINT SPECTRUM LLC
Apparatus and method for fine art authentication
InactiveUS20070247317A1Increase valueProgramme controlElectric signal transmission systemsElectronic serial numberAuthentication system
The present invention incorporates a fine art authentication system to authenticate artwork that are certified to be originals from an accounted-for limited edition. Each reproduction has a non-reproducible RFID (Radio Frequency Identification Device) tag attached to the back of the canvas or paper, using a specially developed inert compound that will not react with the canvas or inks. The bonding is secure, acid-free and will not hurt or degrade the image. The embedded RFID tag is covered with a Lexan disk identifying the art as an authentic original reproduction. The RFID tag contains an electronic serial number that can be read by an inexpensive RFID scanner at participating galleries. This number is unique to the artist, the image and the edition number and cannot be duplicated. The device cannot be removed without damaging artwork and rendering the RFID tag inoperative. The electronically encrypted data may include the serial number, date of purchase, name of artist and number of reprints in the limited edition. The process allows certification that the artwork is authentic and that it is a specific number from the limited edition.
Owner:FARRELL RICK
System, method, and computer-readable medium for user equipment acquisition of an ip-femtocell system
A system, method, and computer readable medium for acquisition of an IP-based femtocell system by a user equipment are provided. A manual femtocell acquisition procedure may be invoked at a user equipment for acquiring access to a femtocell system or network of femtocell systems. The femtocell acquisition routine may be invoked by supply of a command to a femto application hosted by the user equipment. Invocation of the femtocell acquisition routine results in the user equipment seeking the femtocell system allocated a prioritized preferred routing list entry. In the event that a femtocell system is located, the femtocell system may perform electronic serial number screening to prevent unintended attachment and registration on a femtocell system with which the user equipment does not have authorized access
Owner:INT BUSINESS MASCH CORP
Method and device for testing mobile device
InactiveCN101022637ALimit illegal useRadio/inductive link selection arrangementsTransmissionComputer hardwareProcessor register
A method for checking mobile device includes receiving request of checking mobile device identification sent from MSC and HLR as well as AC or VLR by EIR, using mobile device number MEID as mobile device identification required to be checked by MSC and HLR or AC and using electronic serial number ESN as mobile device identification required to be checked by VLR, executing said check by EIR and returning information of said mobile device back. The device used for realizing said method is also disclosed.
Owner:HUAWEI TECH CO LTD
Method and system for measuring market information for wireless telecommunication devices
ActiveUS7761088B1Reduce data collection errorEliminate needSpecial service for subscribersMarketingElectronic serial numberModel Number
A method of measuring wireless telecommunication market information for wireless devices. The method includes selecting a panel of numbers, generating signaling messages for the selected panel, sending the generated signaling messages, receiving a response from plurality of databases and processing the received response to determine market information. In one embodiment, the response is an electronic serial number (ESN) of a wireless device. Processing the ESN may determine the manufacturer of the wireless device, the model of the wireless device and its corresponding serial number. As such; the market-share of manufacturer of the device, its corresponding market-share for a given model, and the number of unsold wireless devices may be determined. Tracking the selected panel of numbers may determine the lifespan of a device and the relationship between providers and replacing or acquiring devices. It is appreciated that identifiers other than ESN may be used (e.g., IMEI in GSM technology).
Owner:THE NIELSEN CO (US) LLC
System, method, and computer-readable medium for mobile-to-mobile calls within femtocell network
ActiveUS20090131016A1Interconnection arrangementsUnauthorised/fraudulent call preventionTelecommunications networkCommunications system
A system, method, and computer readable medium for terminating calls in a network system is provided. The communication system features an IP-based femtocell system for provisioning communication services to a user equipment. The femtocell system is provisioned with a list of electronic serial numbers of user equipments that are authorized to access the femtocell system. When a call is received by the femtocell system, the femtocell system determines a directory number of a user equipment to which the call is directed. If the destination user equipment is authorized to access the femtocell system and is currently within the service area of the femtocell system, the call setup may be completed by the femtocell system without any call setup signaling being transmitted to a core telecommunication network.
Owner:OPEN INVENTION NEWTORK LLC
Method of modifying the home location register (HLR) system database for digital wireless communication whenever the database contents of main memory are altered
The present invention provides a method for modifying the Home Location Register (HLR) system database for digital wireless mobile communication. The method modifies or revises the database of the HLR system that is used to manage mobile subscribers by maintaining all the wireless communication system subscribers' information such as electronic serial number, directory number, international mobile station identification, user profile and current location, etc. The method includes extracting subscriber information from the database which resides in a main memory device and is being used at the present time; migrating the extracted information to a new database; and saving the migrated information onto a disk. In addition, the present method automatically generates the structure and contents of the database to be modified, regardless of each database version and structure, and without requiring the modification and testing of the source code by an operator.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for using a temporary electronic serial number for over-the-air activation of a mobile device
InactiveUS7539514B2Accurate procedureUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile identification numberBiological activation
A system and method for activating a subscriber identification module (SIM) based mobile device in a PCS / ANSI type wireless network. The method comprises pre-programming the SIM card of the mobile device with temporary activation identifiers, such as an international mobile station identity (IMSI) and / or a mobile identification number (MIN), and a temporary electronic serial number. The temporary electronic serial number, rather than the mobile device actual electronic serial number, is used to identify the mobile device during registration and activation. The network identifies the temporary electronic serial number associated with the SIM vendor and invokes an over-the-air activation procedure especially for the SIM card mobile devices. A SIM-over-the-air-activation processor is notified to perform the activation for that mobile device on the PCS wireless network. Authentication of the mobile device may be bypassed and the mobile device is instructed to transmit its actual electronic serial number for future registrations. Once the activation process is completed, the temporary activation identifiers are overwritten.
Owner:AT&T WIRELESS SERVICES
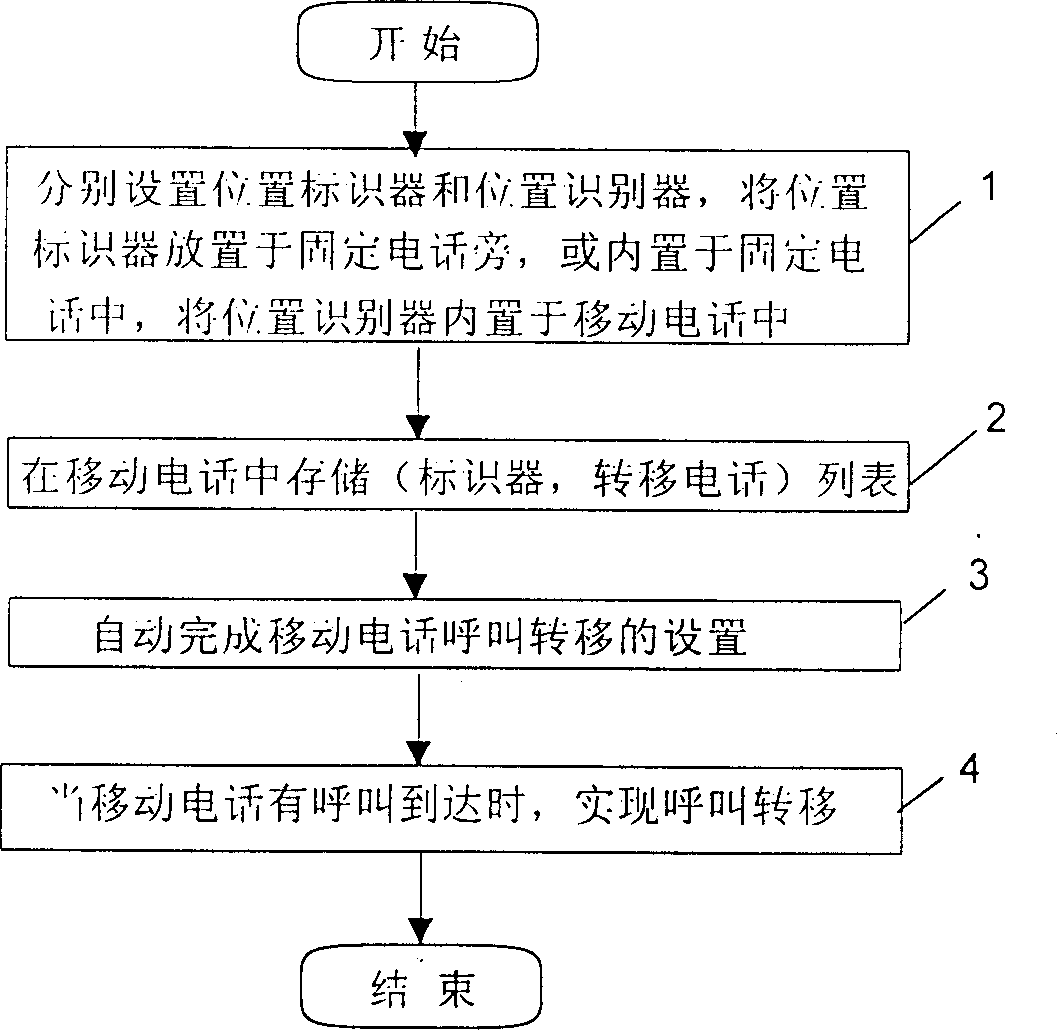
Method for realizing calling intelligent transfer of mobile telephone
InactiveCN1386001ALow costEasy to useSpecial service for subscribersCall forwardingElectronic serial number
This invention discloses a method of realizing mobile phone calling intelligent transfer including setting a position marker used for identifying fixed phones, a position distinguished in the mobile phone for identifying the position marker, calling transfer listing including the position marker set by stored clients. Thus if the mobile phone searches for the position marker and gets its electronic sequence number(ESN) it will transfer listing combined with stored calling of mobile phone to send an order of calling transfer to mobile network of finish the calling transfer as deciding the fixed phones suitable for the transfer calling. When calling orives at the mobile phone, the mobile network transfers the said calling to the set fixed phones.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
Multi-label collision-proof method
InactiveCN101071471ASpeed upComplete quickly and efficientlySensing record carriersElectronic serial numberInstruction sequence
The invention discloses a multi-tag anti-collision method. The reader is set to a section of memory stack, stack from the above instructions in the pop-up REQUEST parameters for the whole or a part of the initial signal sequence; if sent 1 is the initial signal, all electronic tags to its own serial number given to RF cards; If sent to the partial sequence of RF cards, their sequence and the sequence of received, the sequence of its own if the former Several REQUEST instruction sequences, with the parameters being equal, this label to send their electronic serial number to the rest of the readers, not the same if we do not respond to the recycling process until all the labels have been disposed of. The invention overcomes the multi-tag identification process in the complex for steps, such as lack of long transmission time, quickly and effectively narrow the scope of the identification tags, shortened the time for, effective and expeditious completion of its readers between all labels communication.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Overlay calling plan for wireless telephone
InactiveUS7103358B2Accounting/billing servicesTelephonic communicationMobile identification numberRoaming
Methods, systems and computer program products for providing roaming services to a wireless telephone roaming outside of its home service area by receiving a request for roaming service from a wireless telephone that is within a roaming network and offering a special roaming contract to the user of the wireless telephone. The request for services comprises an identify of the wireless telephone wherein the identity comprises the mobile identification number and the electronic serial number. Using the identity of the wireless telephone received in the request, the roaming network determines that the wireless telephone identity is not recorded as a record within the roaming network and is therefore roaming. The method provides offering a special roaming contract to the user and then executing the special roaming contract if the user decides to accept the offer for a special roaming contract.
Owner:INT BUSINESS MASCH CORP
Method and system for use of shared data to gain wireless packet data connectivity
ActiveUS7620008B1Easily gain wireless packet-data connectivityEnhanced interactionPrintersProjectorsMobile identification numberData connection
A method and system to allow wireless devices, such as wirelessly-equipped digital cameras, to gain wireless packet-data connectivity and to interact with a media management server, such as a photo server. A wireless carrier distributes multiple devices all having the same set of radio access data (e.g., mobile identification number and electronic serial number), and all having shared or unique pre-registration data. Any such device can then readily use the shared radio access data to acquire radio connectivity and can then use the pre-registration data to gain access to the media management server. The first time such a device connects with the media management server using the pre-registration data, the server will engage in a online account registration session with the device and provision the device with post-registration data that the device can thereafter use to access the online account.
Owner:SPRINT SPECTRUM LLC
Methods for authentication using near-field
ActiveUS8850196B2Random number generatorsUser identity/authority verificationElectronic serial numberAuthentication
Owner:MOTOROLA SOLUTIONS INC
Method of preventing the unauthorized use of a user identification module
InactiveUS7496381B2Prevent illegal useUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCard holderElectronic serial number
A method of preventing unauthorized use of a user Identification module (UIM) is provided. The method comprises attaching a UIM previously used with a first communication terminal to a second communication terminal, wherein the UIM is configured to have first and second card holder verification (CHV) states; authenticating the second communication terminal and the UIM regardless of whether the UIM is in the first or the second verification states. The authenticating step may comprise determining an electronic serial number (ESN) of the second communication terminal; and comparing the ESN of the second communication terminal with an ESN of the first communication terminal.
Owner:LG ELECTRONICS INC
Method and system for vocoder bypass using electronic serial numbers
InactiveUS6865391B1Avoid performanceSpeech analysisSubstation equipmentMobile identification numberTerminal equipment
A system and method are provided for using electronic serial numbers (ESNS) to determine whether to perform vocoder bypass. In an exemplary embodiment, a terminal device may share a common mobile identification number (MIN) with other terminal devices. The terminal device may answer a page and provide its ESN to an intermediate entity. The intermediate entity may query a database to determine whether the answering terminal device is a mobile station. The intermediate entity may perform vocoding if the answering terminal device is a non-mobile station, or vocoder bypass if the answering terminal device is a mobile station.
Owner:SPRINT SPECTRUM LLC
Methods, apparatus and computer program products for controlling a reverse link traffic channel code responsive to detection of a duplicate terminal identity
InactiveUS7254124B2Time-division multiplexRadio transmission for post communicationCommunications systemElectronic serial number
According to some embodiments of the present invention, a reverse link traffic channel code used by a terminal accessing a CDMA wireless communications system is controlled responsive to determining whether the terminal has a duplicate Electronic Serial Number (ESN). In some embodiments, for example, an alternative ESN may be sent to the terminal having the duplicate ESN for use in generating the reverse link traffic channel code. In other embodiments, a time shift may be applied in generating the reverse traffic channel code, such as by time-shifting the reverse link traffic channel code or a long code used to generate the reverse link traffic channel code. In still other embodiments, an alternative long code mask, such as a private long code mask used for a voice privacy feature, may be used responsive to detection of a duplicate ESN. The present invention may be embodied as methods of operating wireless communications systems and / or terminals, wireless communications apparatus such as network components and terminals, and computer program products including program code configured to execute in a wireless communications apparatus.
Owner:SONY ERICSSON MOBILE COMM AB
Method and System for Remote Call Forwarding of Telephone Calls from an IP Connection
InactiveUS20070037571A1Telephone data network interconnectionsIntelligent networksMobile identification numberService control
Owner:AT&T MOBILITY II LLC
Intelligent trajectory matching correlation analysis algorithm model based on big data mining
ActiveCN109634946AImprove accuracyImprove complicatedDigital data information retrievalSpecial data processing applicationsLongitudeCorrelation analysis
The invention provides an intelligent trajectory matching correlation analysis algorithm model based on big data mining, and belongs to the technical field of big data mining. The method comprises: carrying out duplicate removal, missing value record deletion and other cleaning treatments on vehicle and electronic serial number source data; performing co-station matching on the detection code acquisition equipment and the vehicle snapshot bayonet by adopting equipment latitude and longitude, and judging whether the vehicle and the electronic serial number track direction are consistent or not;multi-dimensional features are extracted from the data to serve as samples, and outliers and abnormal points in the samples are removed; and finally, establishing a model of the processed vehicle andelectronic serial number data by using a Logistic Regression algorithm, and optimizing the model. According to the invention, correlation analysis is carried out on the vehicle and the electronic serial number detection code, vehicle personnel and vehicle characteristics can be mastered in all directions, the accuracy of personnel-vehicle correlation is improved, a good support effect on analysisof traffic big data is achieved, and important technologies such as personnel search and the like are provided for traffic case investigation of a certain department so as to fight against crimes.
Owner:南京森根科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com