Service system dynamic isolation protecting method and system based on browser
A business system, isolation and protection technology, applied in the field of information security, can solve problems such as cross-leaking of business systems, inability to use basic functions of browsers such as the Internet, and inability to isolate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] The browser-based business system dynamic isolation protection and its working method of the present invention will be further elaborated below in conjunction with the accompanying drawings.
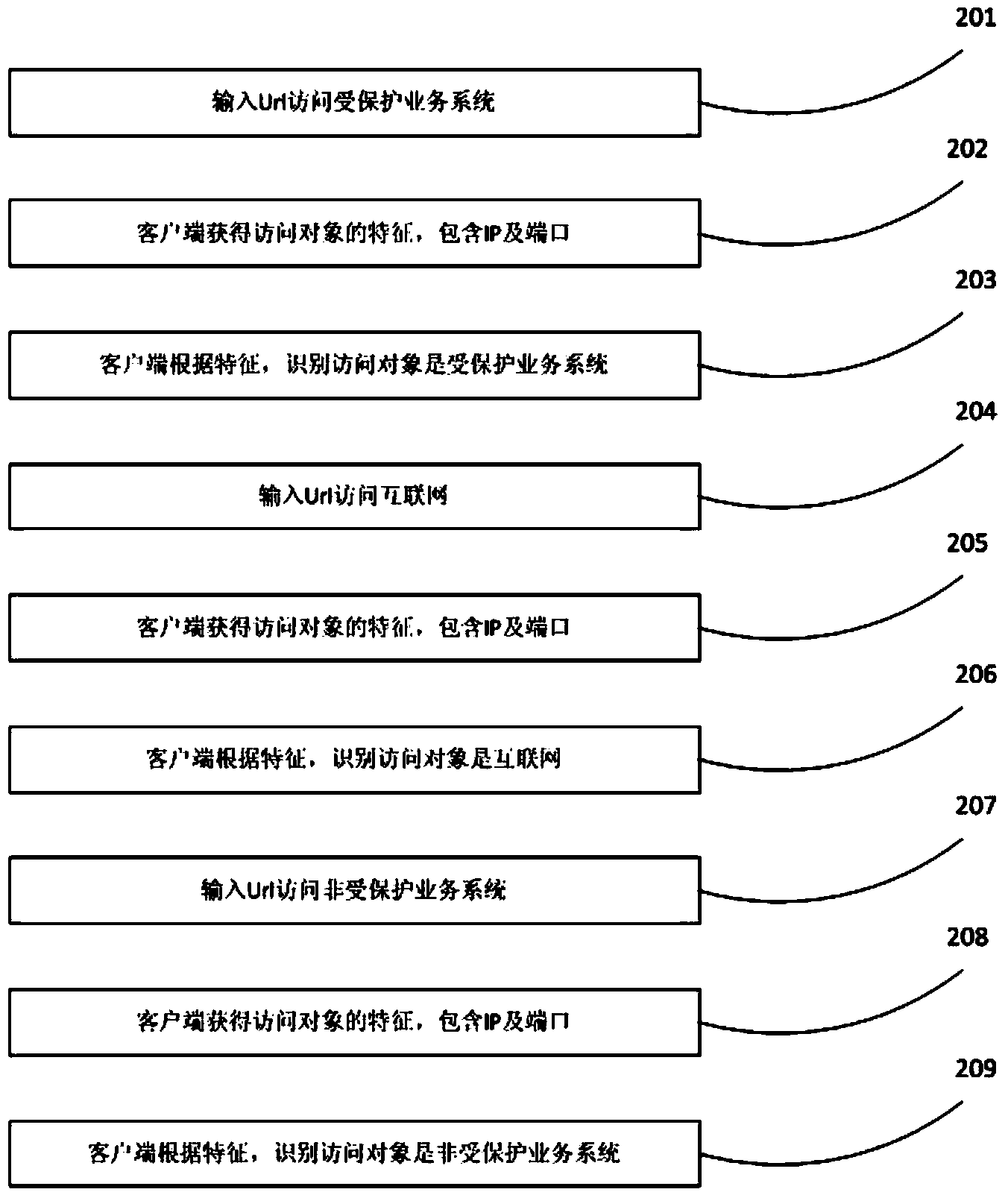
[0067] In the present invention, users can freely use the business system without resorting to a special way such as a dedicated security browser, manually switching the security desktop, or hardware gateway equipment, and without any modification of the business system itself. The identification and isolation of protected business systems are done automatically without user participation. The present invention realizes the isolation and protection of the service system, does not affect the use of other functions by the user, does not change the user's usage habit, and satisfies the enterprise's requirements for data protection while taking into account the user's use experience.
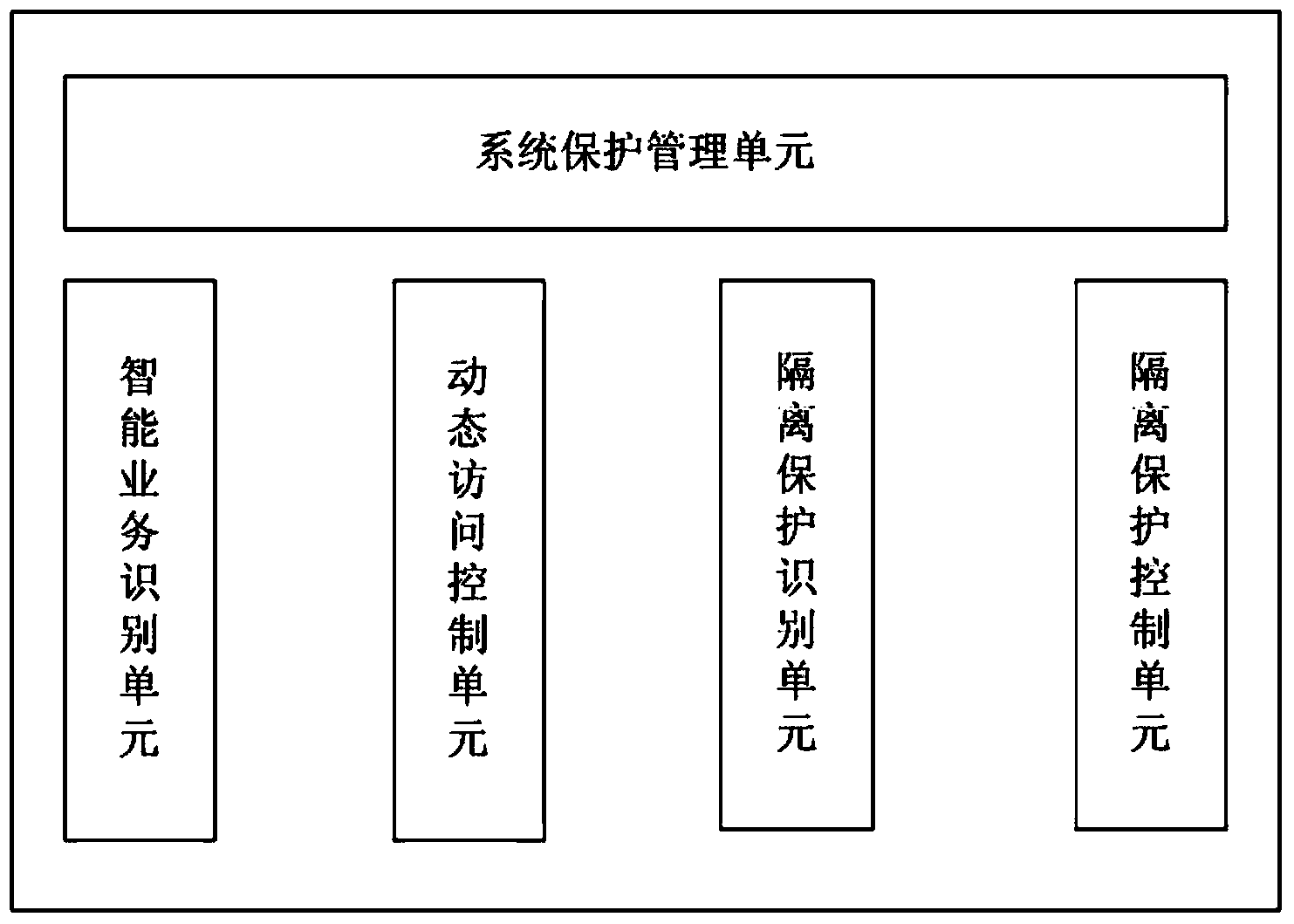
[0068] figure 1 It is a schematic diagram of components in a browser-based business system dynamic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com