Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31 results about "Blocks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Blocks are a non-standard extension added by Apple Inc. to Clang's implementations of the C, C++, and Objective-C programming languages that uses a lambda expression-like syntax to create closures within these languages. Blocks are supported for programs developed for Mac OS X 10.6+ and iOS 4.0+, although third-party runtimes allow use on Mac OS X 10.5 and iOS 2.2+ and non-Apple systems.
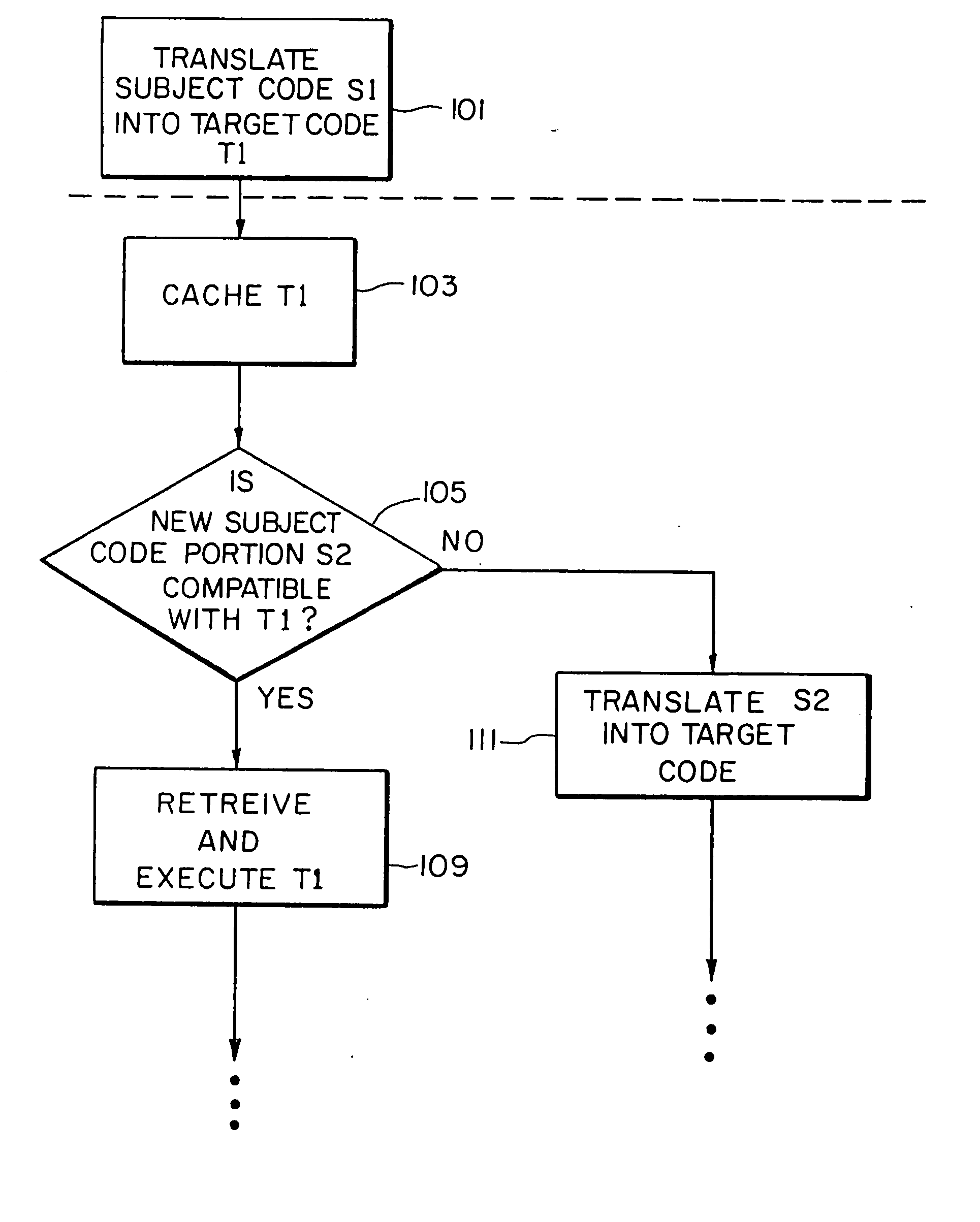
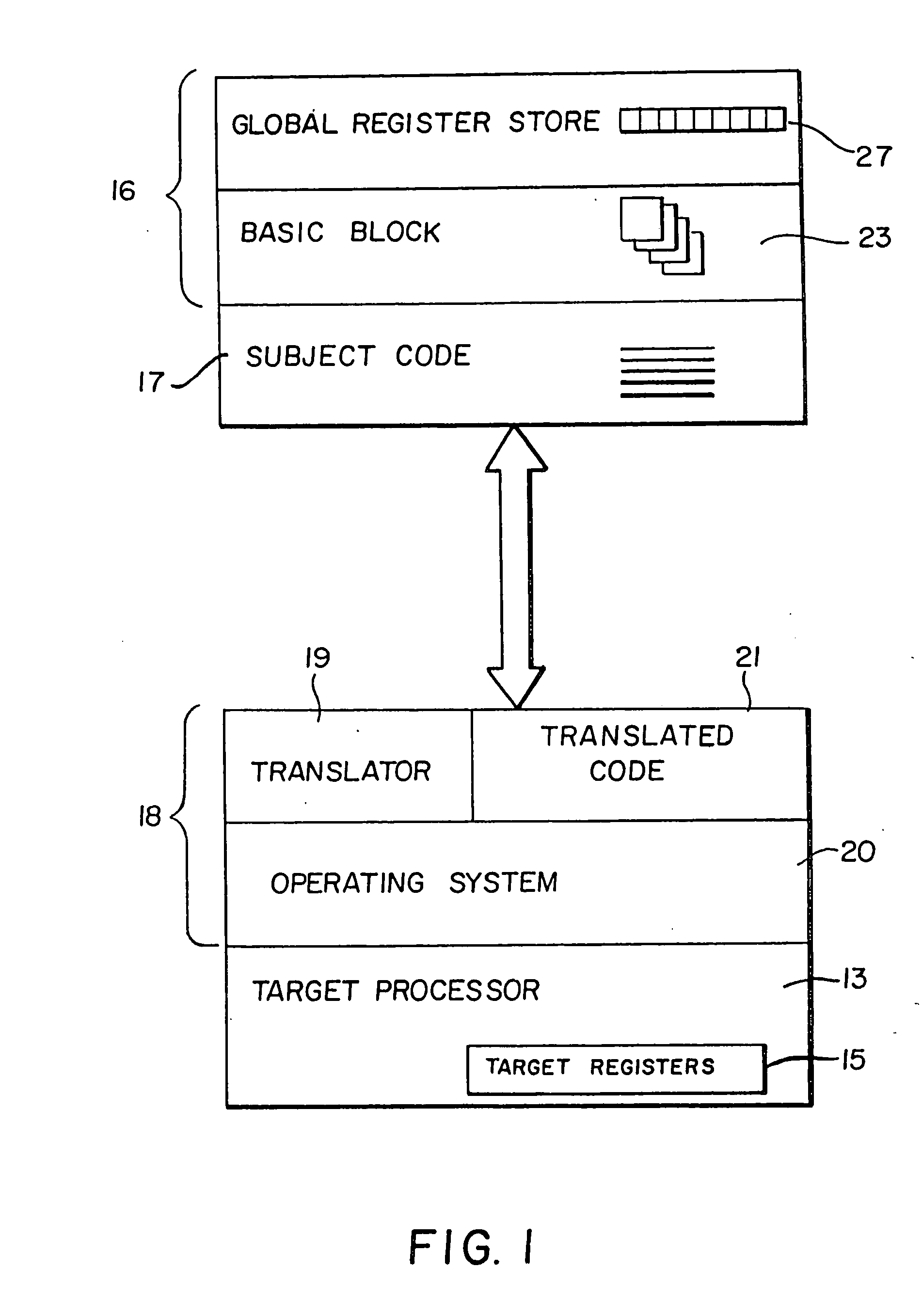
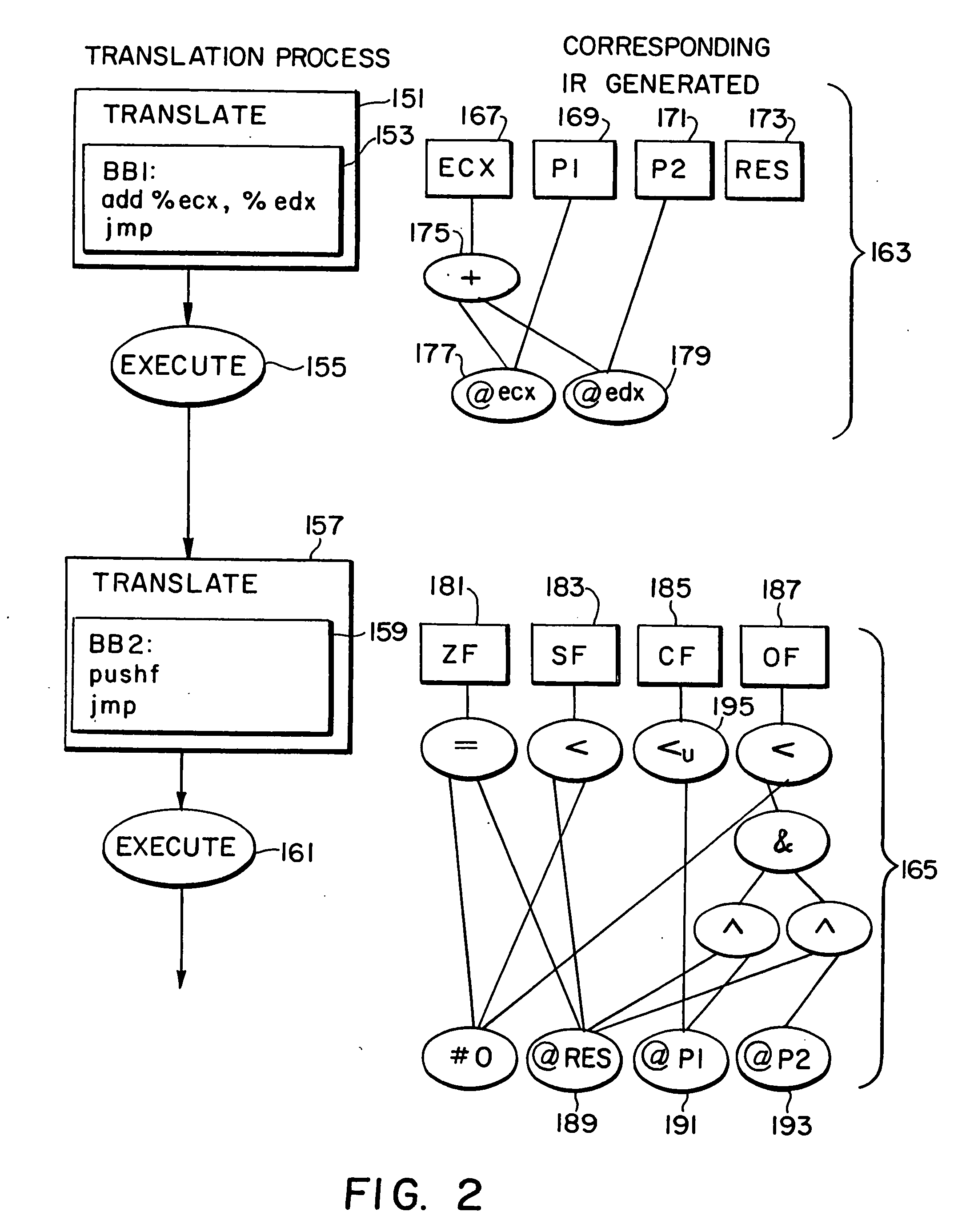
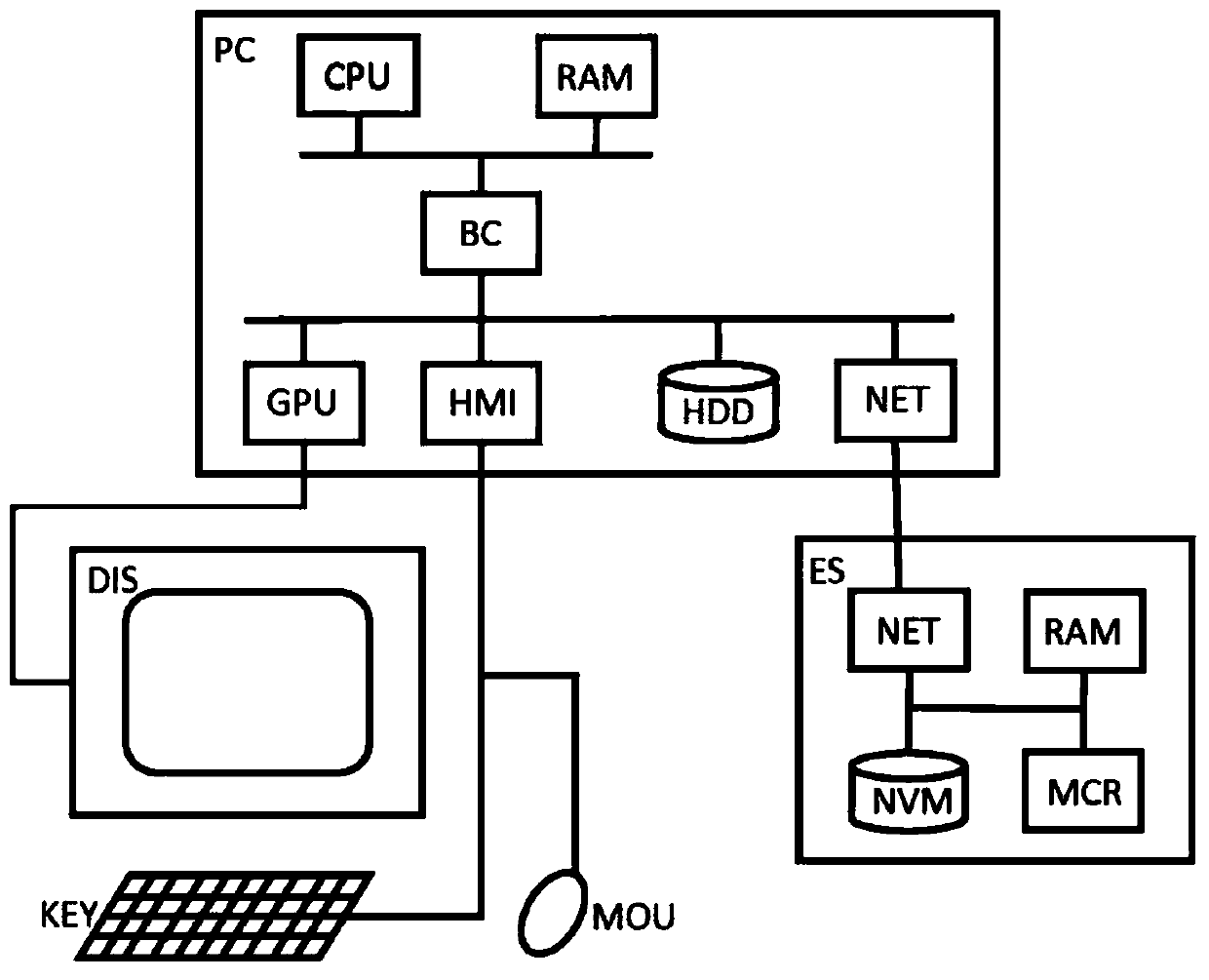
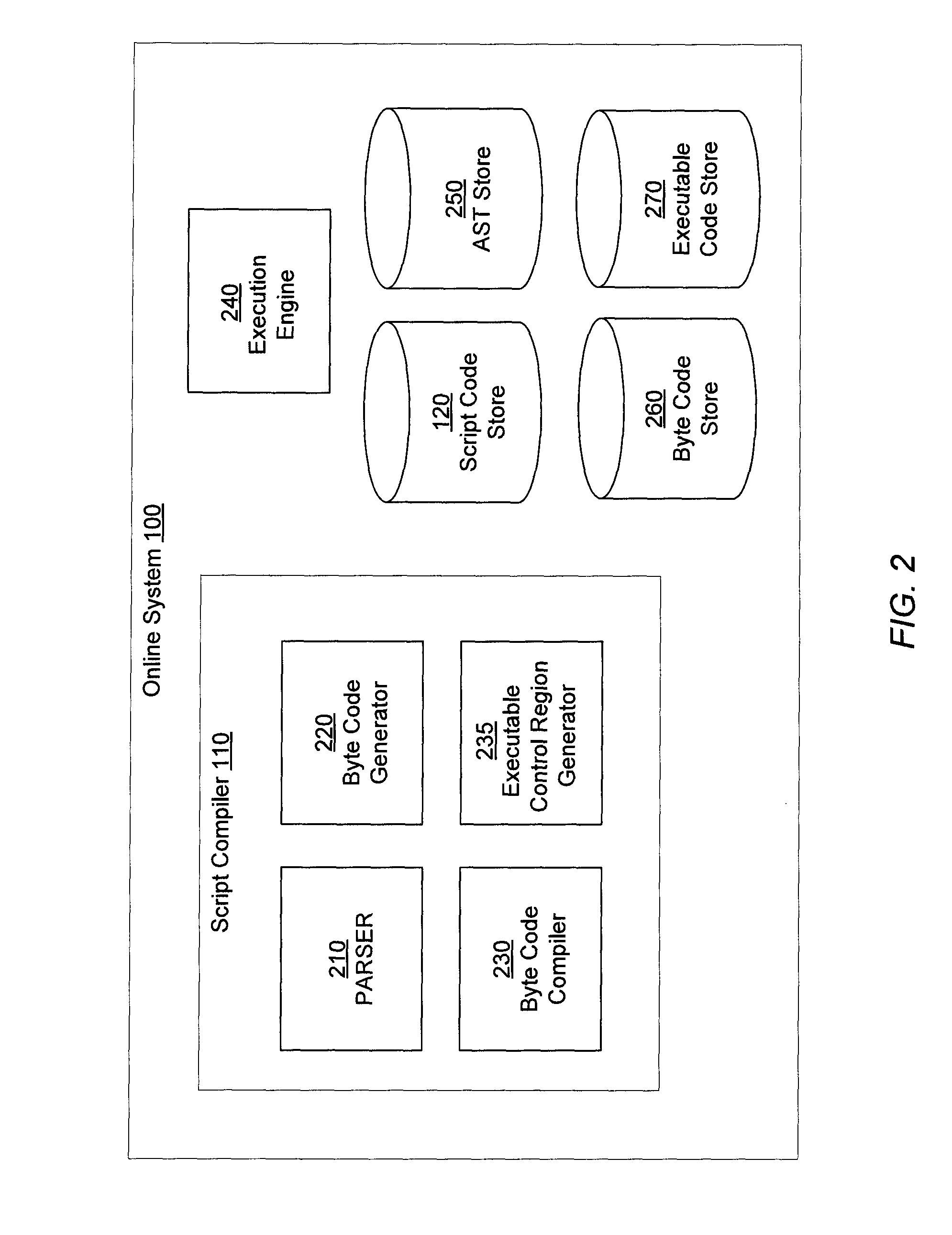
Shared code caching method and apparatus for program code conversion
ActiveUS20050015758A1General purpose stored program computerProgram loading/initiatingCode TranslationProgram code
Subject program code is translated to target code in basic block units at run-time in a process wherein translation of basic blocks is interleaved with execution of those translations. A shared code cache mechanism is added to persistently store subject code translations, such that a translator may reuse translations that were generated and / or optimized by earlier translator instances.
Owner:IBM CORP
Method for detecting error of program control flow
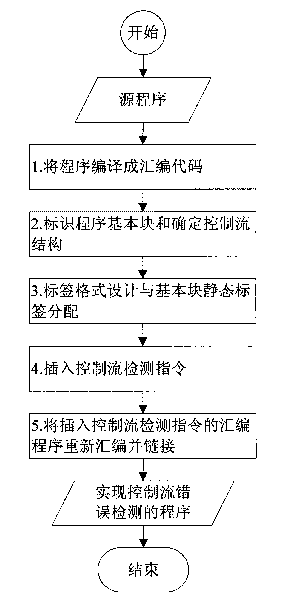
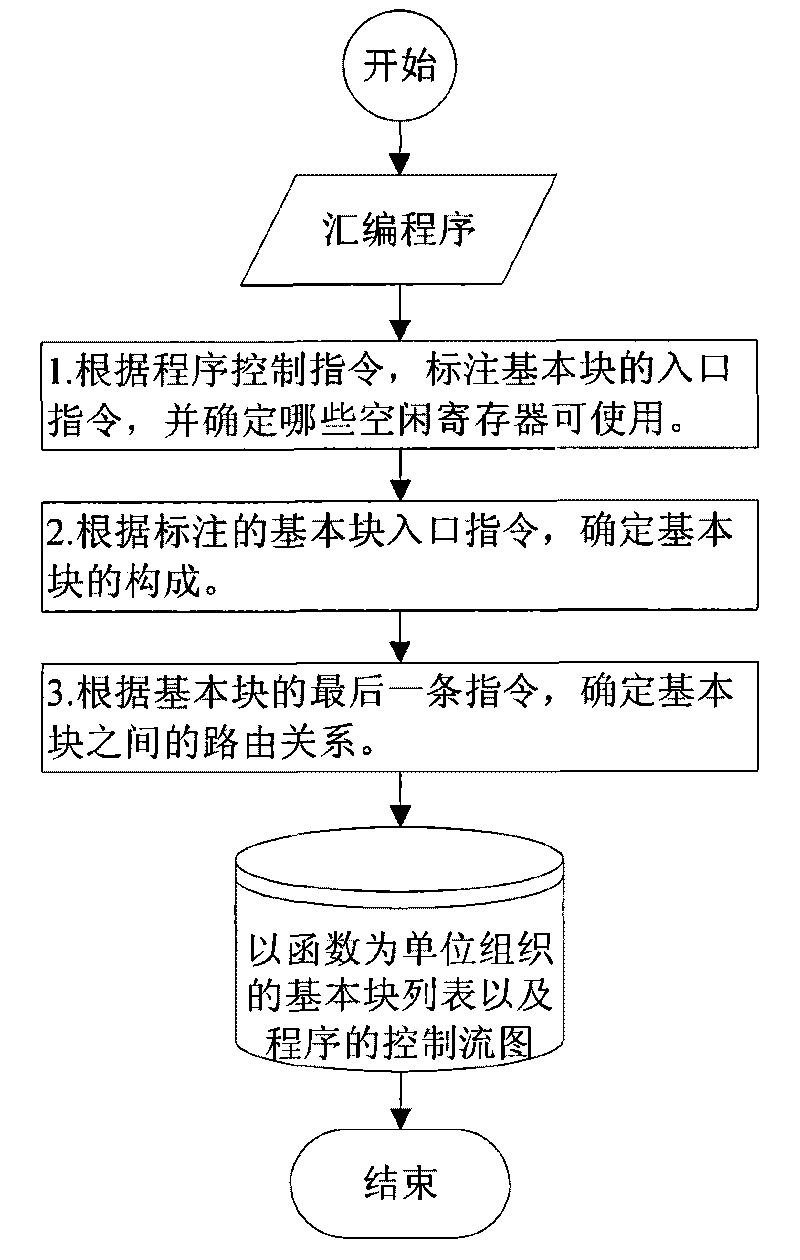
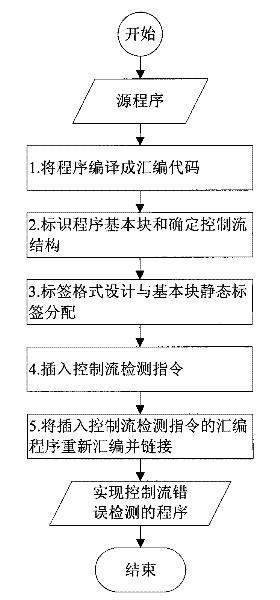
InactiveCN101763291ADoes not require multithreading supportImprove detection rateError detection/correctionProgram controlBasic blockSoftware engineering
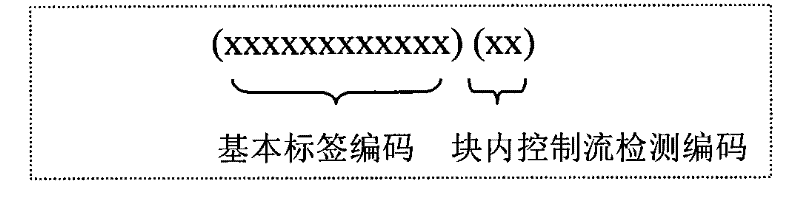
The invention discloses a method for detecting the error of a program control flow and intends to overcome the difficulties in increasing the detection rate of the errors of the control flow by the conventional method and solve the difficult problem with the detection of the control flow inside basic blocks and among processes. The method comprises the following steps according to the technical scheme of the invention: firstly, identifying basic blocks and confirming the routing relation among the basic blocks; then, confirming the maximum required number of detection commands of the internal control flow of each basic block according to the requirements of the internal control flow and the constitutive characteristics of the basic blocks; designing the labels for the basic blocks on that basis, and distributing the unique static label to each basic block; then, inserting the detection commands into the head part, inner part and tail part of each basic block in the program respectively, re-assembling and re-linking the assembler of the inserted detection commands of the control flow, and generating an executable program for achieving the detection of the error of the control flow.
Owner:NAT UNIV OF DEFENSE TECH
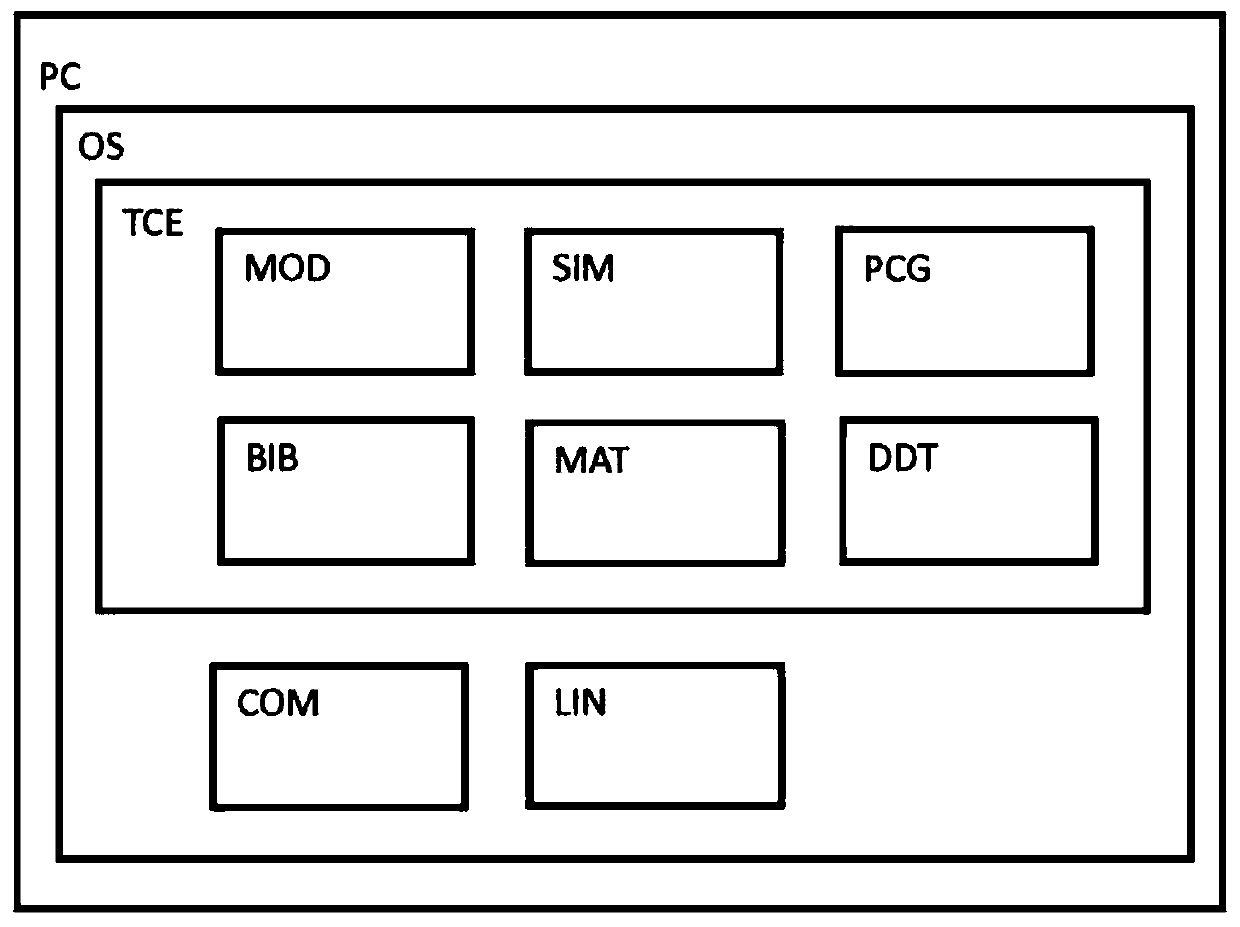
Method and system for generating program code
ActiveUS20200201608A1Easy and flexible possibilityEasy to set upVisual/graphical programmingModel driven codeAlgorithmTheoretical computer science
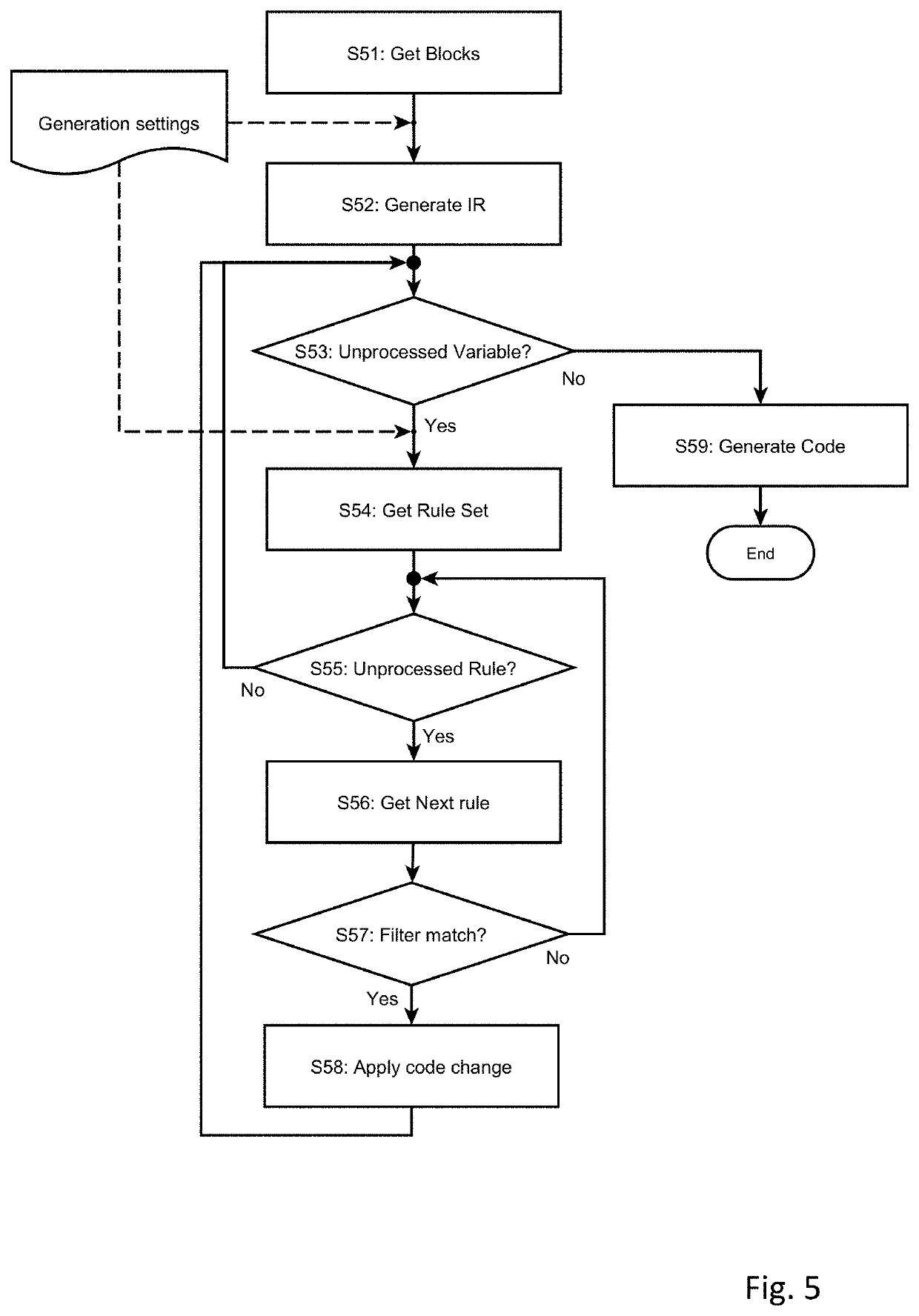
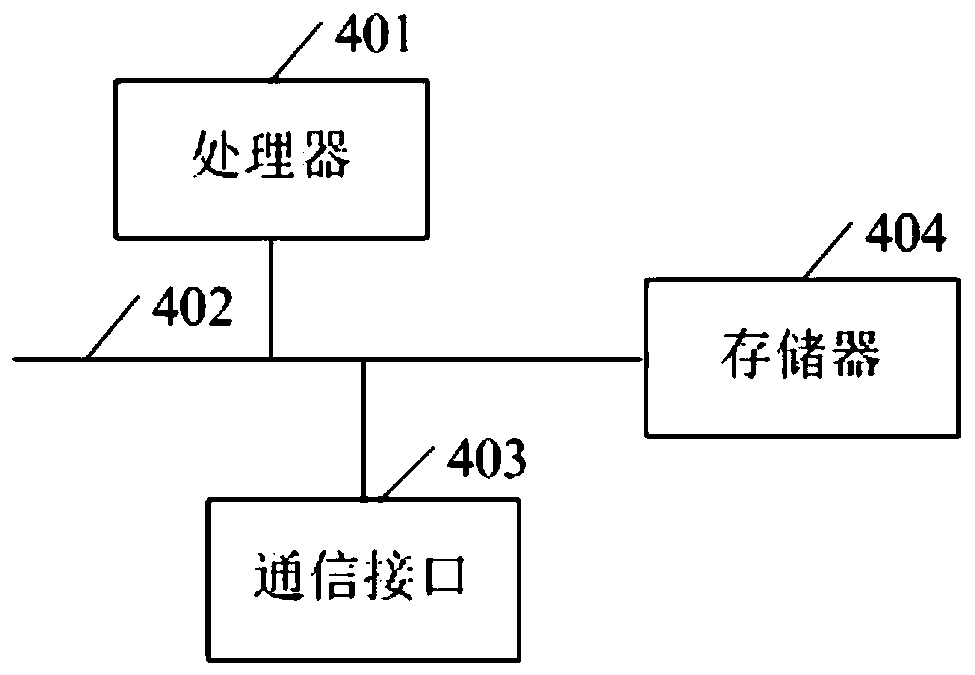
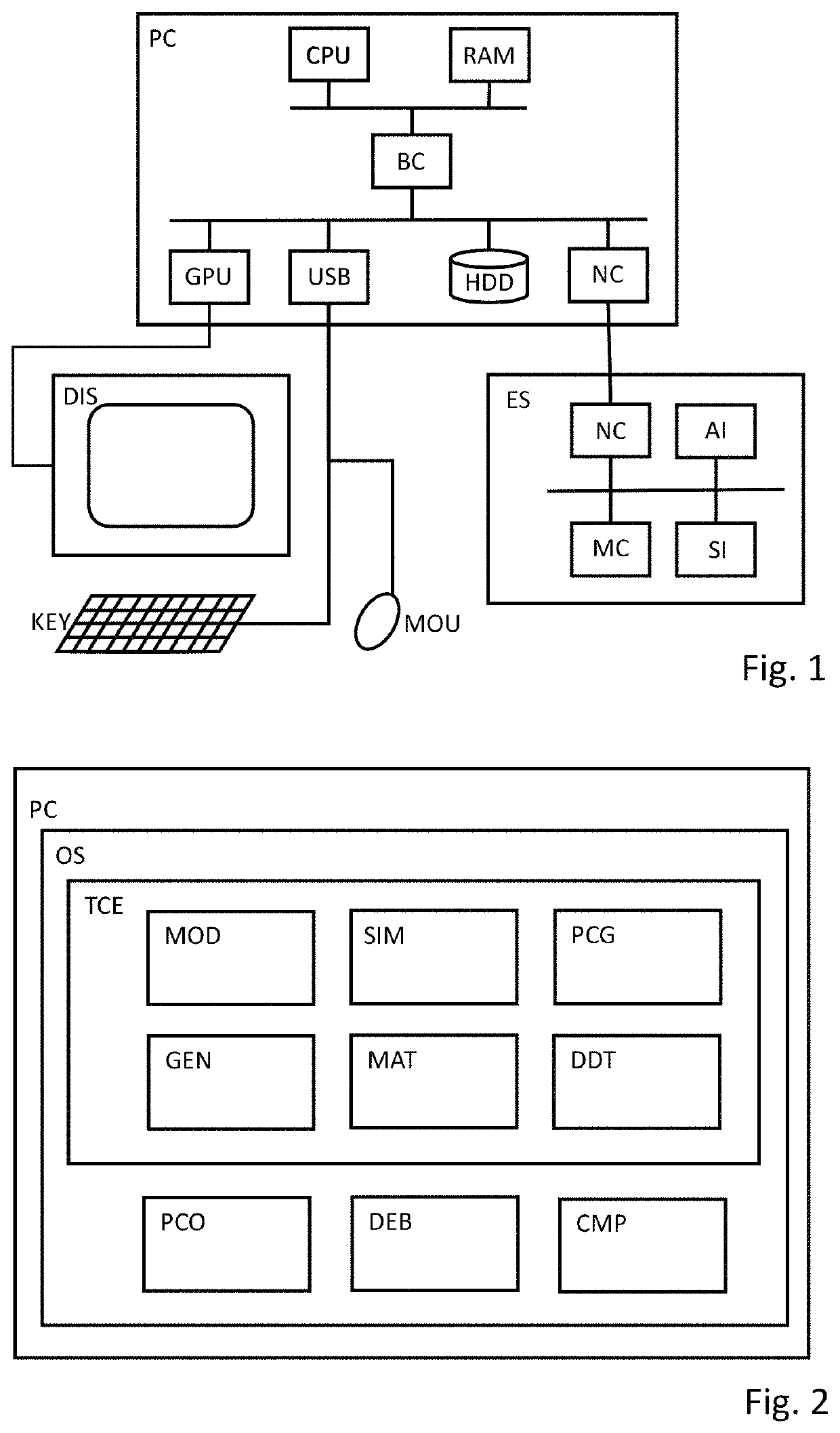
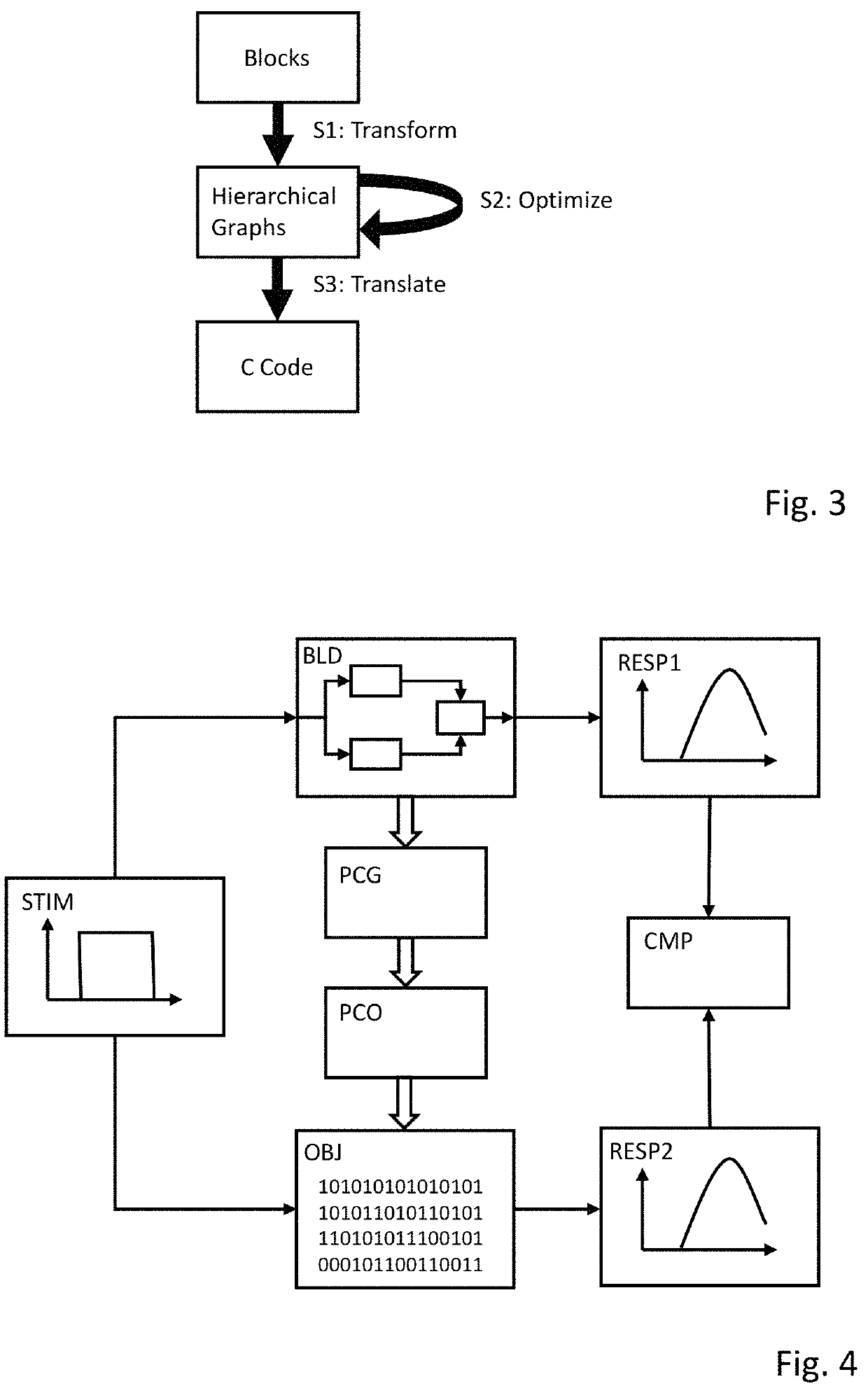
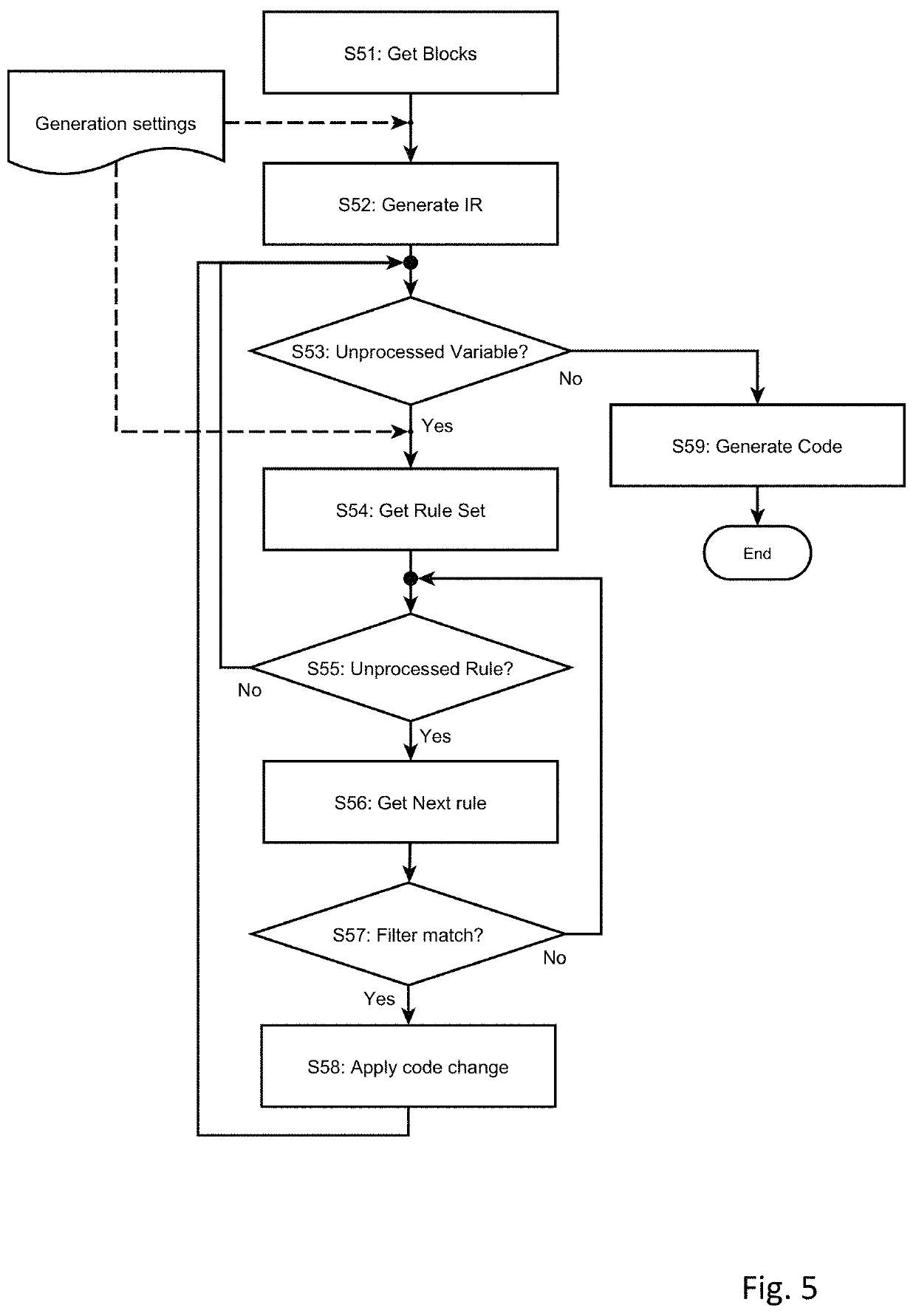
A computer-implemented method for generating program code based on one or more blocks of a block diagram, at least one block including a block variable. The method comprises opening the block diagram in a model editor, retrieving generation settings for the block variable from a data definition tool, the generation settings comprising a scope of the variable, determining that a modification rule is referenced in the generation settings, and retrieving the referenced modification rule from the data definition tool, wherein a modification rule comprises a filter condition and one or more code changes. A processor generates program code based on the block diagram and the generation settings and applies the referenced modification rule to the block variable in the generated code, which includes verifying that the filter condition is fulfilled for the block variable and applying the code changes to each occurrence of the variable in the code.
Owner:DSPACE DIGITAL SIGNAL PROCESSING & CONTROL ENG
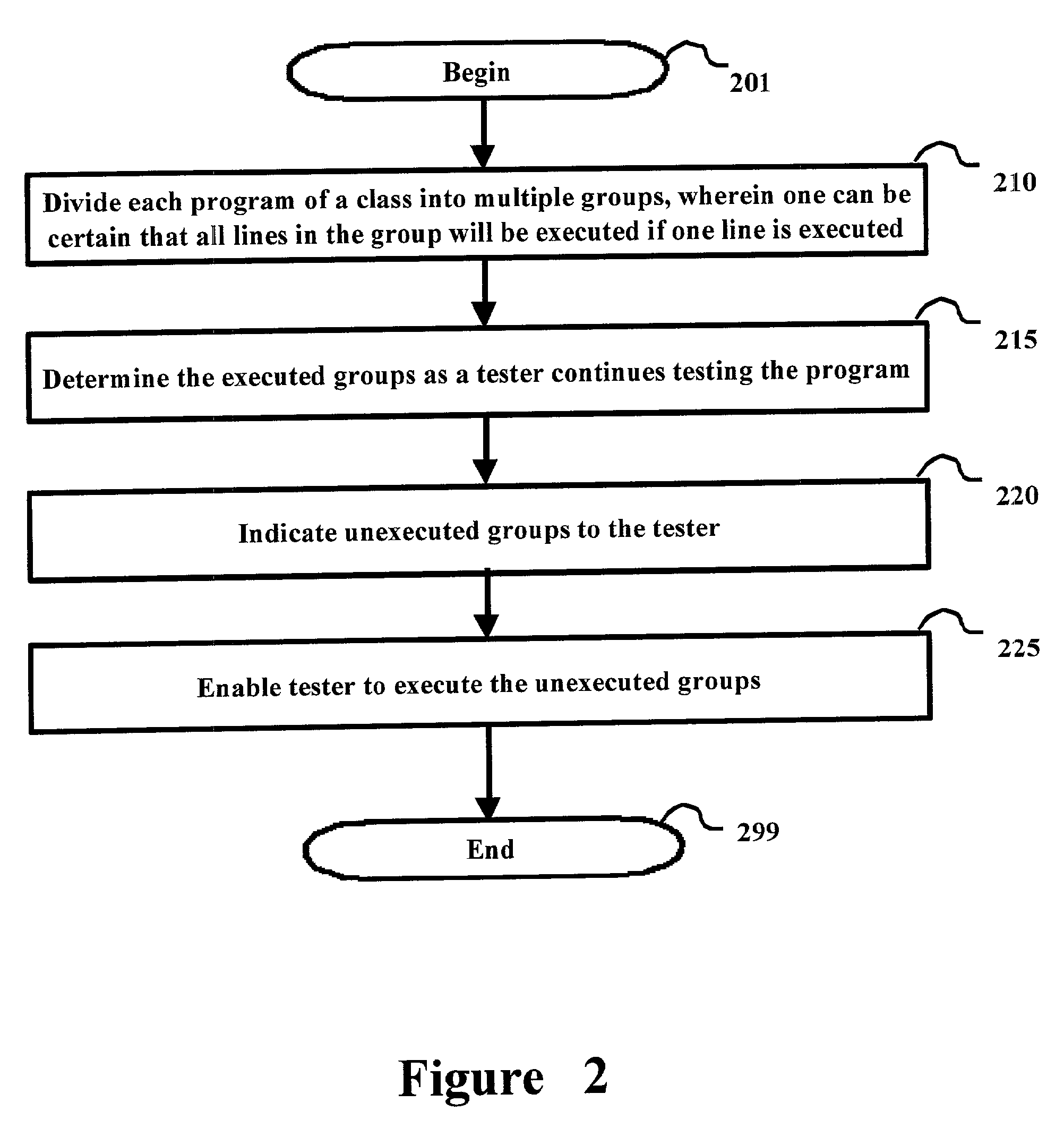
Software testing by groups
InactiveUS20080046867A1Easier for a tester to quickly appreciateSoftware testing/debuggingSpecific program execution arrangementsTest proceduresSingle group
A testing tool allowing convenient testing of programs and also classes in general. The tool automatically divides each program into many groups such that if one line (or statement) is executed it may reasonably be assumed that all the lines in the group are also executed. A tester is provided the ability to provide desired arguments (including class instances) and cause all groups to be executed such that all lines of code in the programs of a class are executed at least once. The groups are conveniently further logically combined into hierarchical blocks, with each block at a higher level corresponding to a logical structure such as if structure, for structure, while structure, etc. The blocks at the lowest level may contain a single group. Due to such hierarchy, a tester may visually easily identify the unexecuted blocks / groups. The tester may further define and execute small pieces of code (macros) in the middle of testing.
Owner:KYNDRYL INC
Method for producing source code
The invention relates to a method for generating source code from one or more blocks of a block diagram comprising a model of a dynamic system having at least one directional connection between two blocks, wherein the block diagram can be designed to simulate the dynamic system, and wherein at least one region in which one or more blocks are located is defined in the block diagram. The block diagram comprises a first block and a second block, wherein the first block has a first block variable and the second block has a second block variable, each block variable of the block diagram having a descriptor. The descriptor of the first block variable is compared with the descriptor of the second block variable, and a check is performed to determine whether the first block and the second block are located in the same region. The first block variable and the second block variable are implemented in the source code as a single variable if the descriptors are concordant and the blocks are located in one region. If the descriptors are different and / or the blocks are not located in the same region, the first block variable and the second block variable are implemented in the source code as twoseparate variables. Moreover, the invention relates to a method for configuring a controller, to a computer program product and to a computer system.
Owner:디스페이스게엠베하
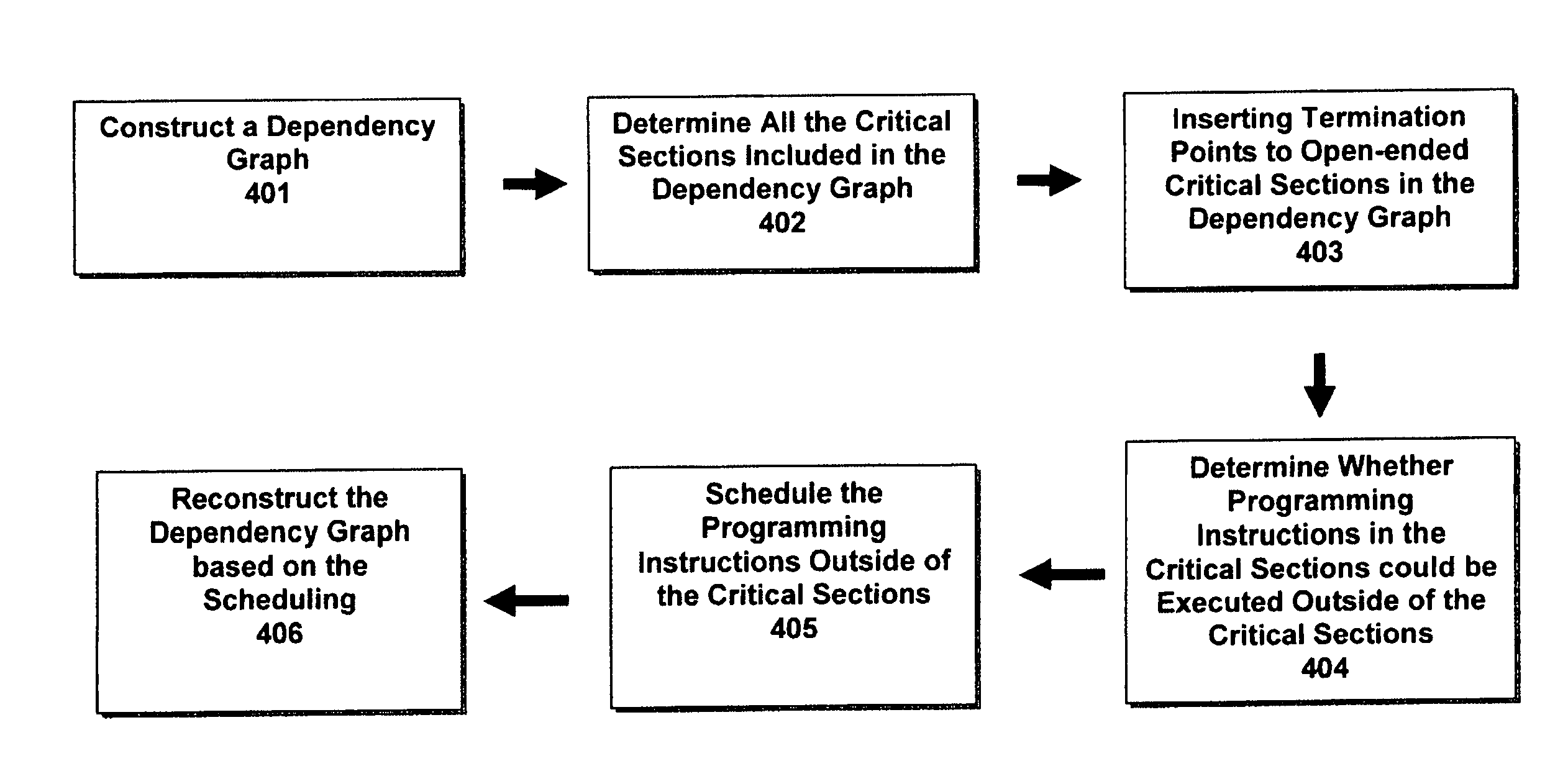
Scheduling multithreaded programming instructions based on dependency graph
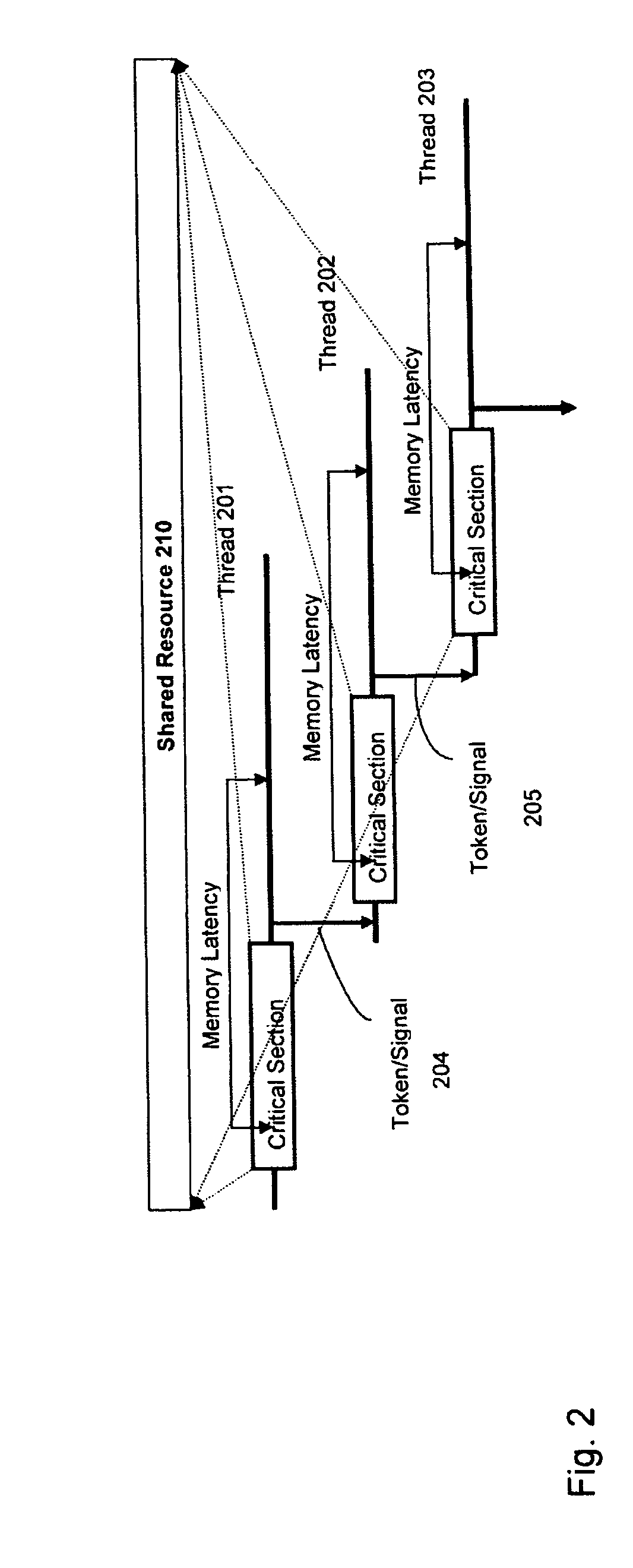
InactiveUS8612957B2Optimize network performanceImprove network performanceSoftware engineeringDigital computer detailsDependency graphCritical section
A computer implemented method for scheduling multithreaded programming instructions based on the dependency graph wherein the dependency graph organizes the programming instruction logically based on blocks, nodes, and super blocks and wherein the programming instructions could be executed outside of a critical section may be executed outside of the critical section by inserting dependency relationship in the dependency graph.
Owner:IS2BE
Incremental compilation of a script code in a distributed environment
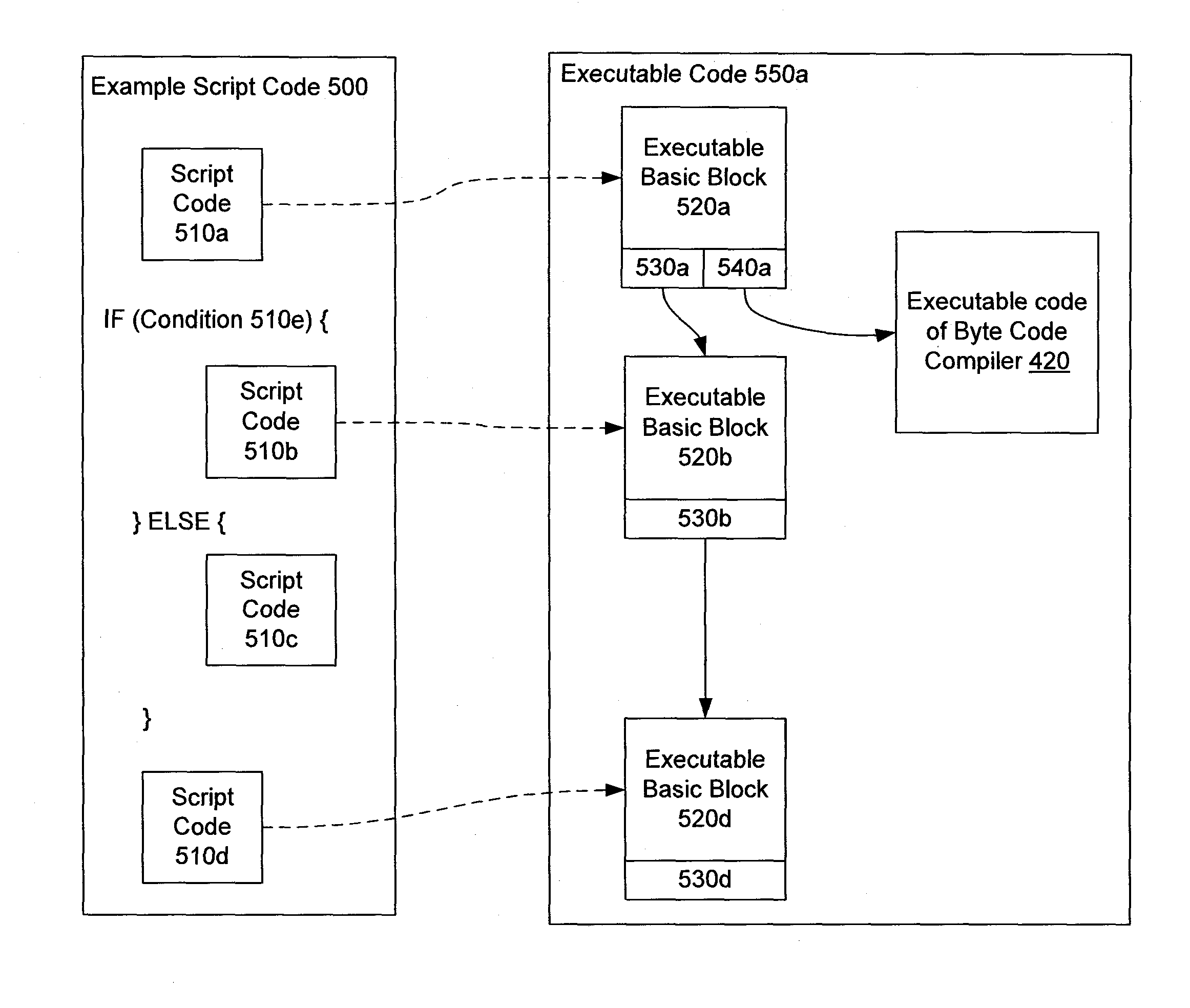
ActiveUS8984492B2Software simulation/interpretation/emulationMemory systemsExecution controlBasic block
Disclosed here are methods, systems, paradigms and structures for incrementally compiling scripts at runtime to generate executable code. In a first phase, an executable block for a basic block of the script is generated for a set of types of variables of the basic block. In a second phase, a set of executable blocks whose profiling information, such as frequency of (a) execution, (b) transition between executable blocks, or (c) execution of a path, satisfies an optimization criterion is identified, and an executable control region is generated. In a third phase, profiling information from a number of systems in a distributed environment is aggregated, and an executable control region corresponding to the aggregated profile is generated. The executable code generated in each of the phases is more optimal than the code generated in a previous phase, and is used for execution until replaced by the code of a subsequent phase.
Owner:META PLATFORMS INC
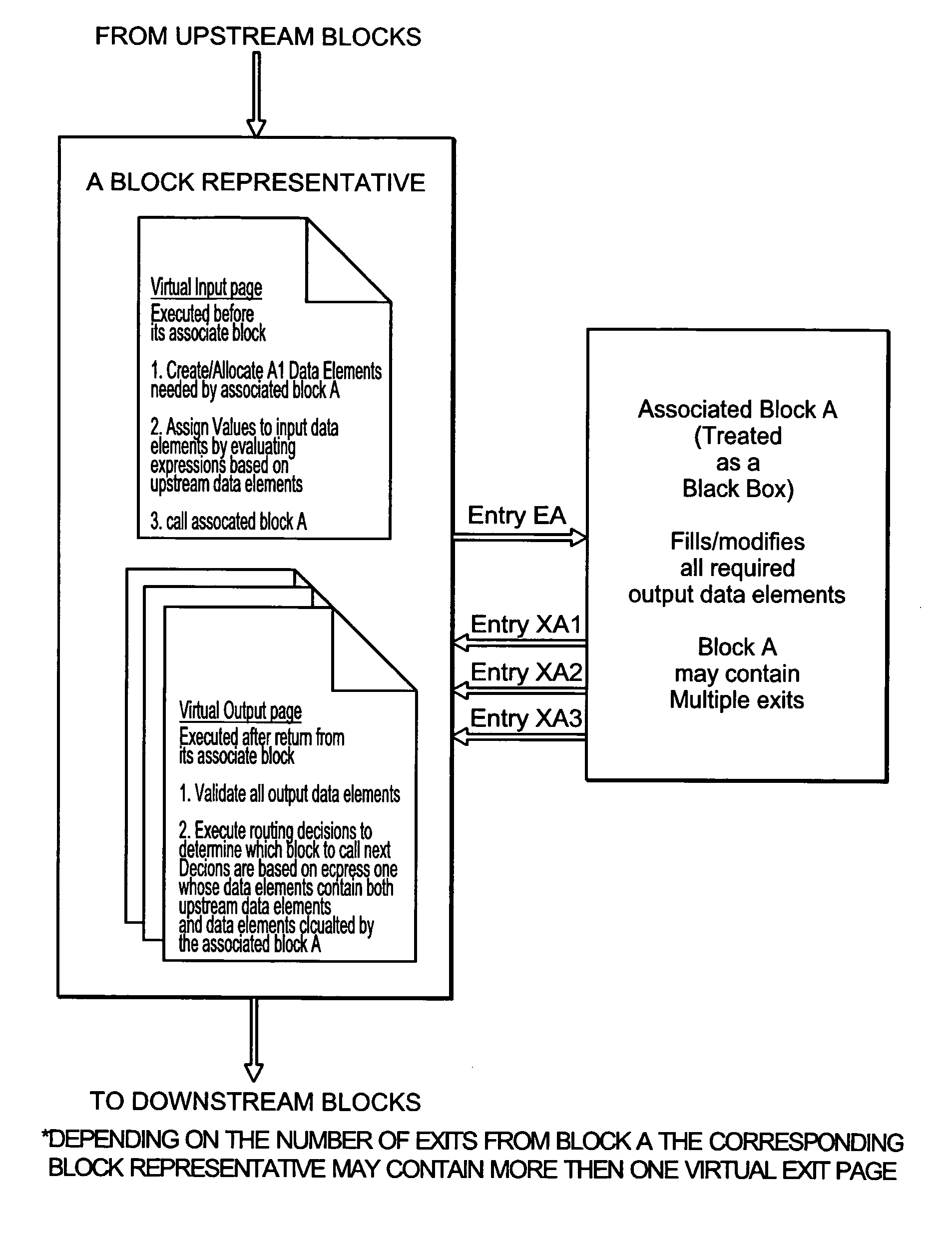
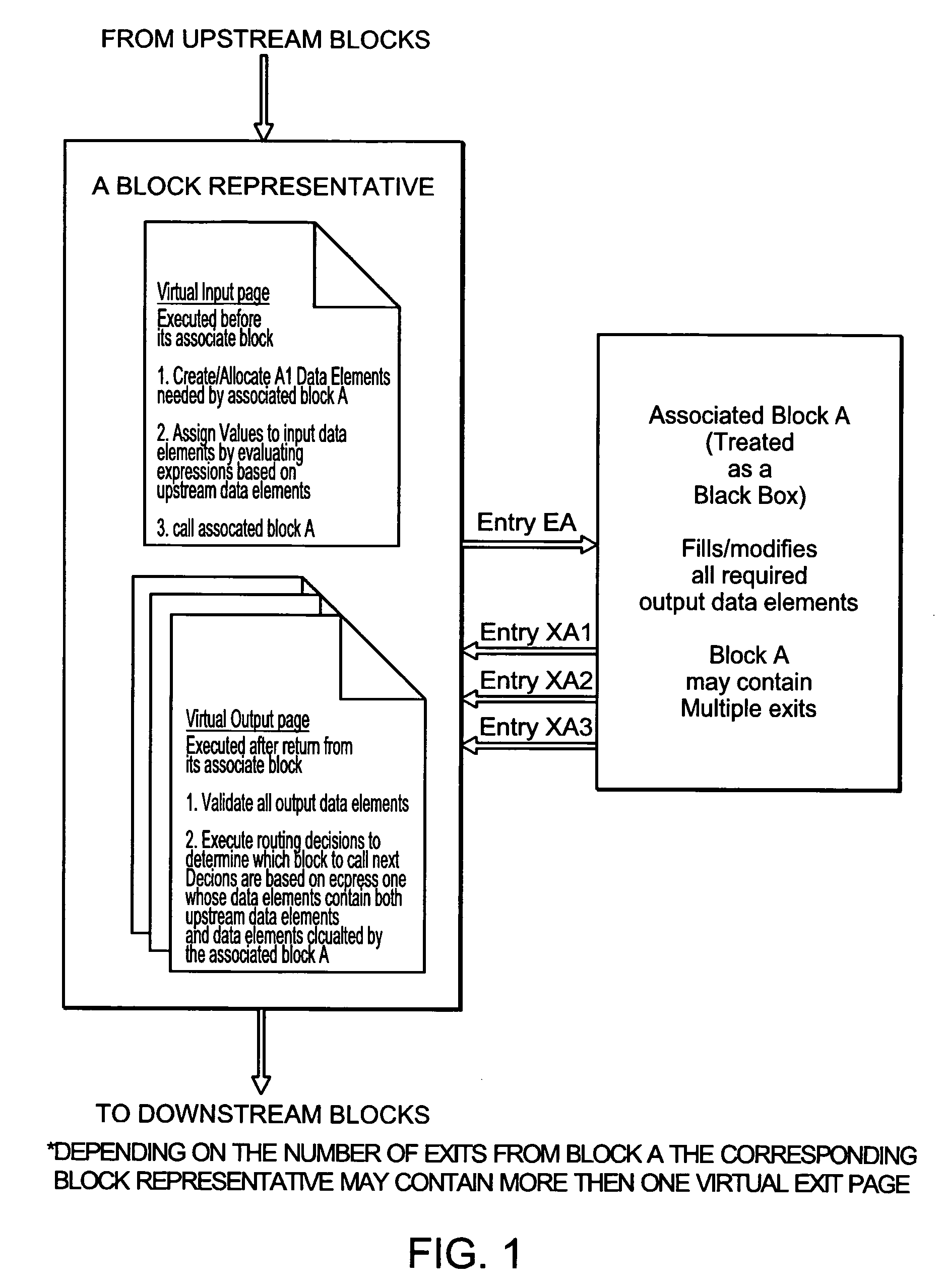
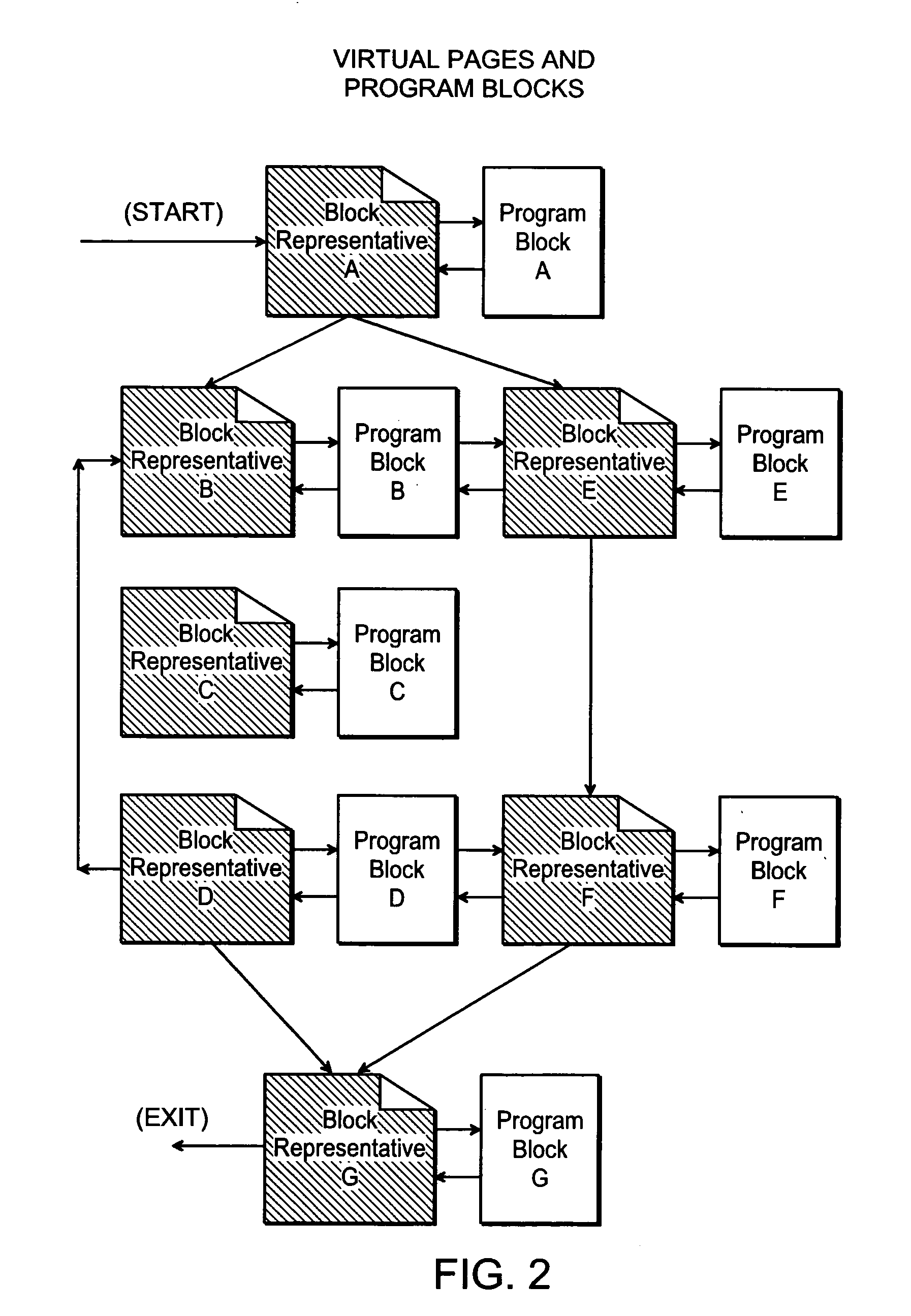
Automatic consistency checking of computer programs
InactiveUS20050028150A1Maintain consistencyResource allocationSoftware testing/debuggingProgram segmentParallel computing
A method, for use with a computer having memory, for structuring a program segment, is described. A series of program blocks in the segment are identified. Each block is a functional piece of code in the segment and has at least one point corresponding to at least one of entry and exit, in such a manner that the entire segment is divided into blocks with each block being situated in an execution path along which the segment executes in a downstream direction. With respect to each block, a block representative is associated. The block representative allocates computer memory for data elements that are needed for the associated block to execute. The block representative also assigns a value to any data element required by the associated block to have a value. Additionally, the block representative calls the associated block for execution, receives return of control after execution of the block, and passes control based on available data.
Owner:HALPERN MORDECHAI
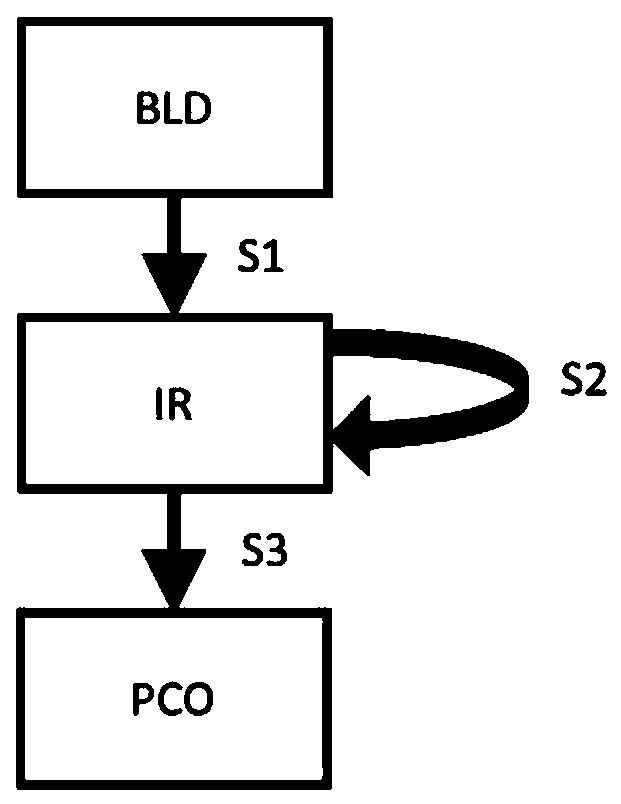
Method to secure a software code
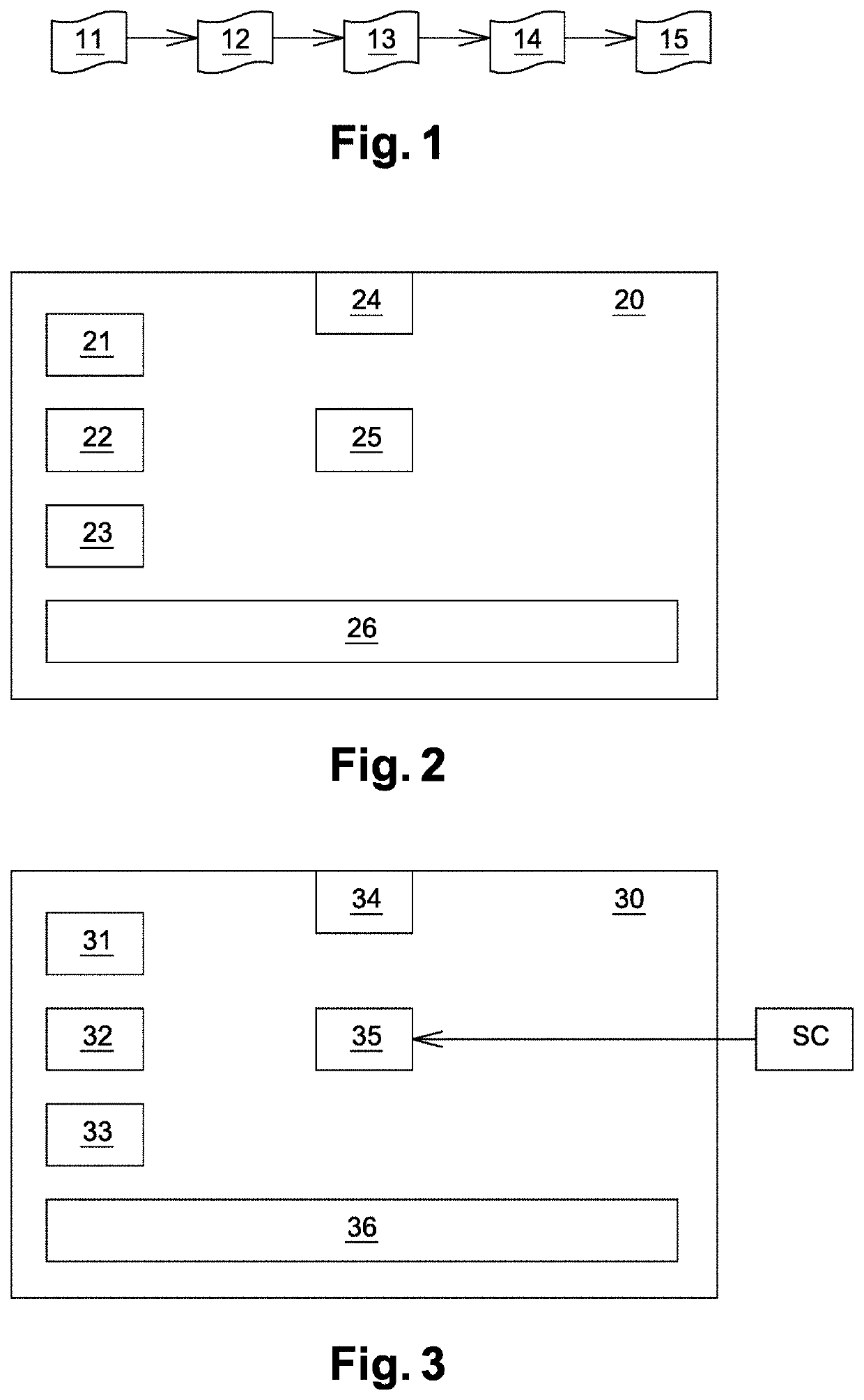
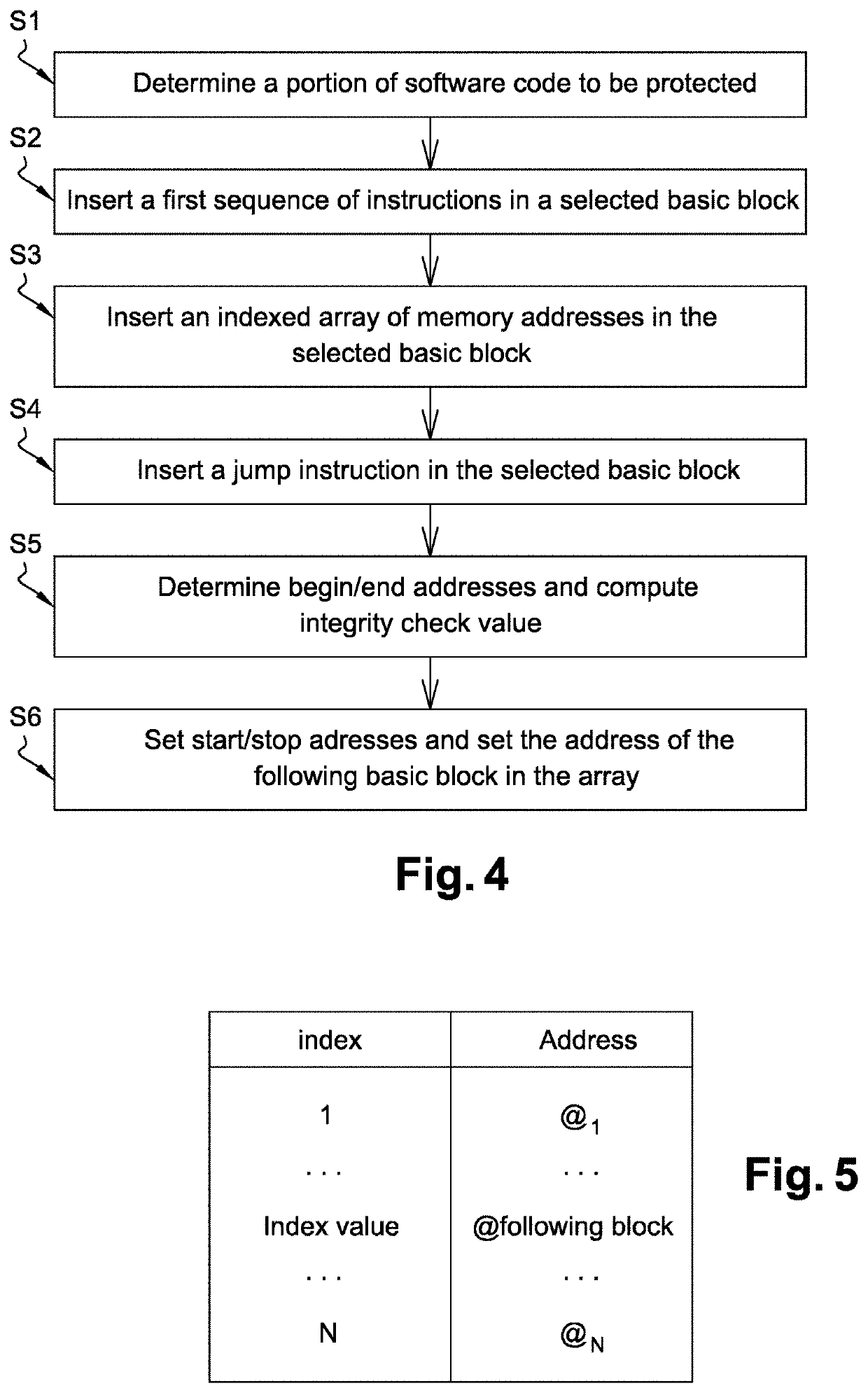
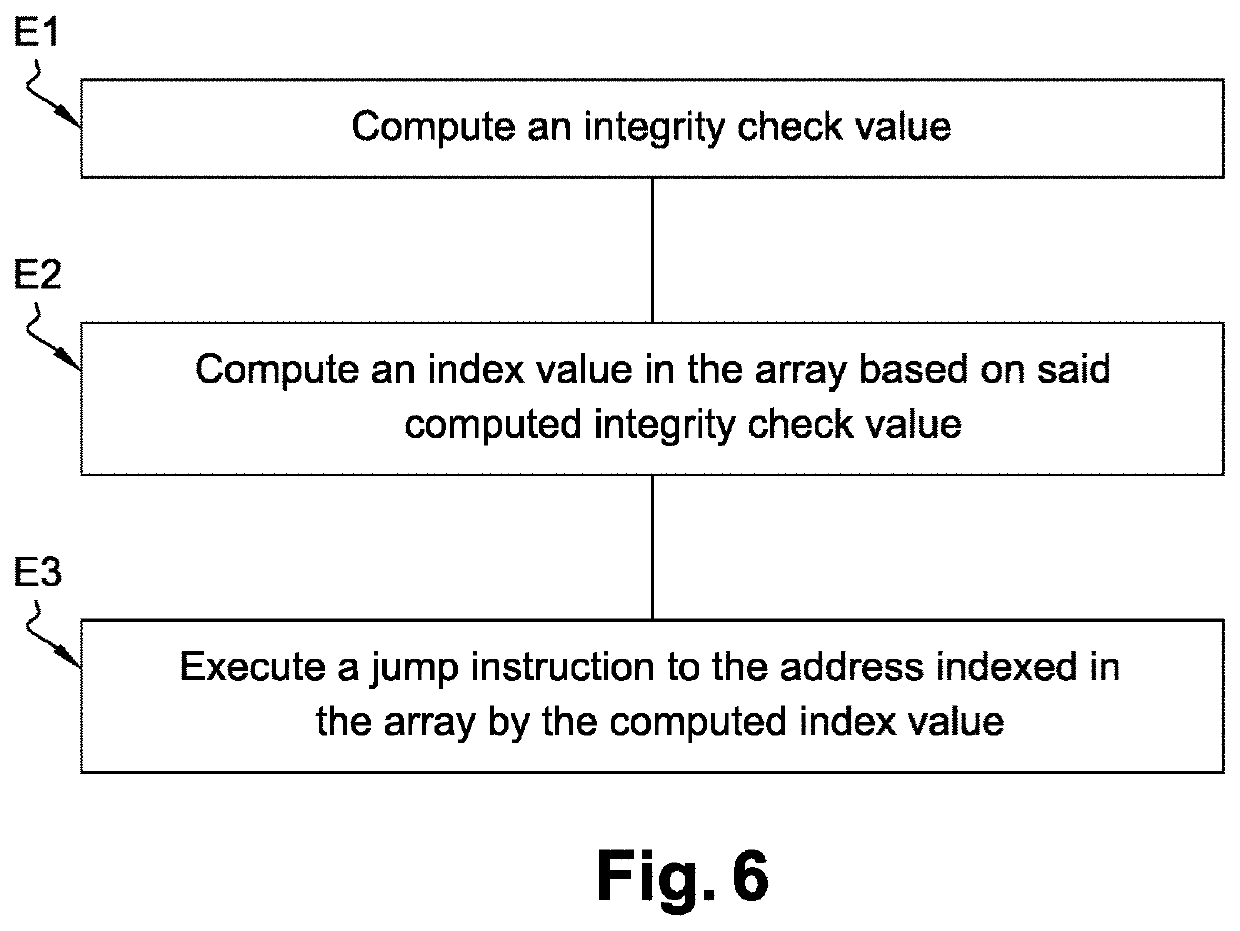
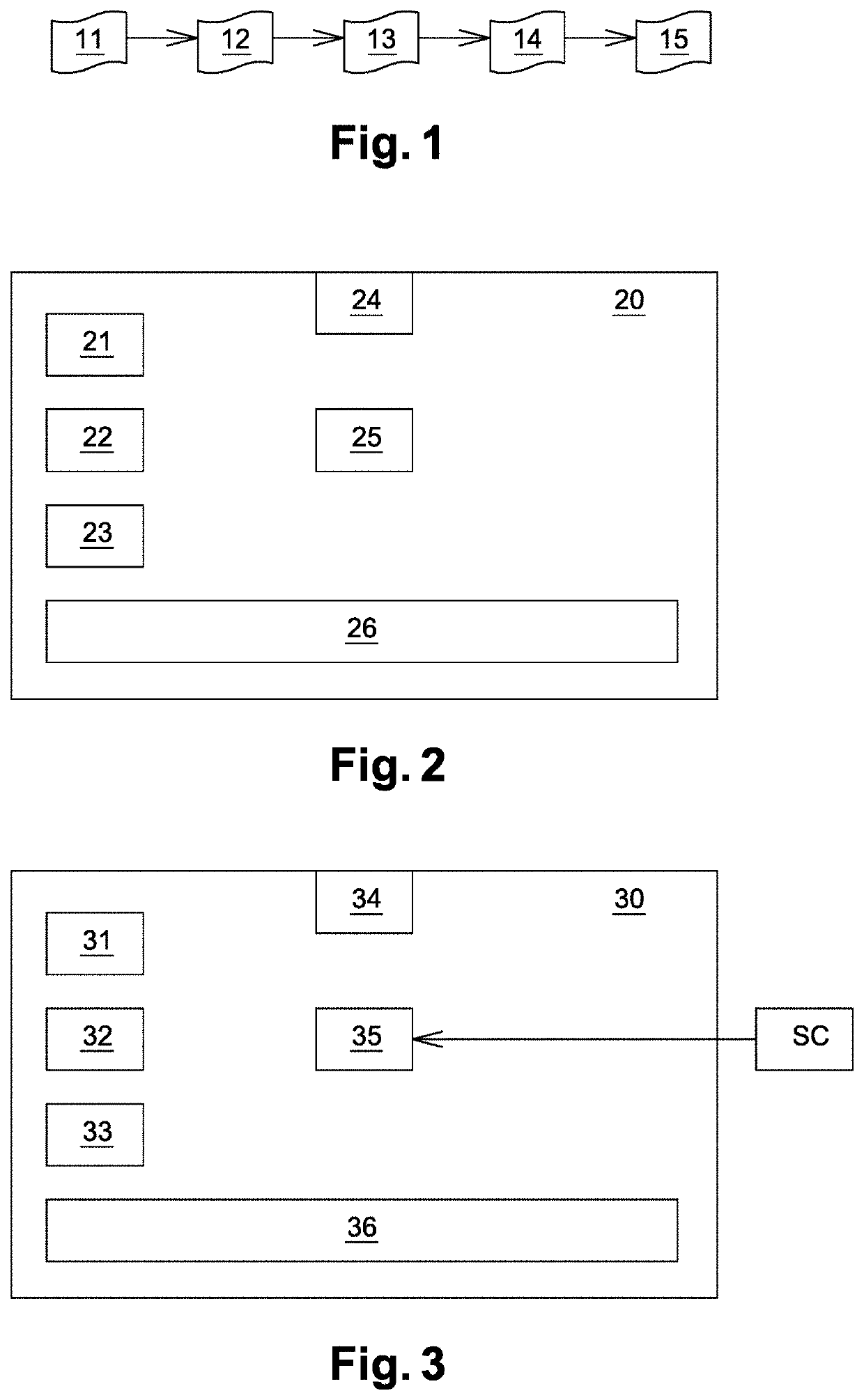
ActiveUS20200004934A1Breakage pointDifficult to understandProgram/content distribution protectionMemory addressSecurity software
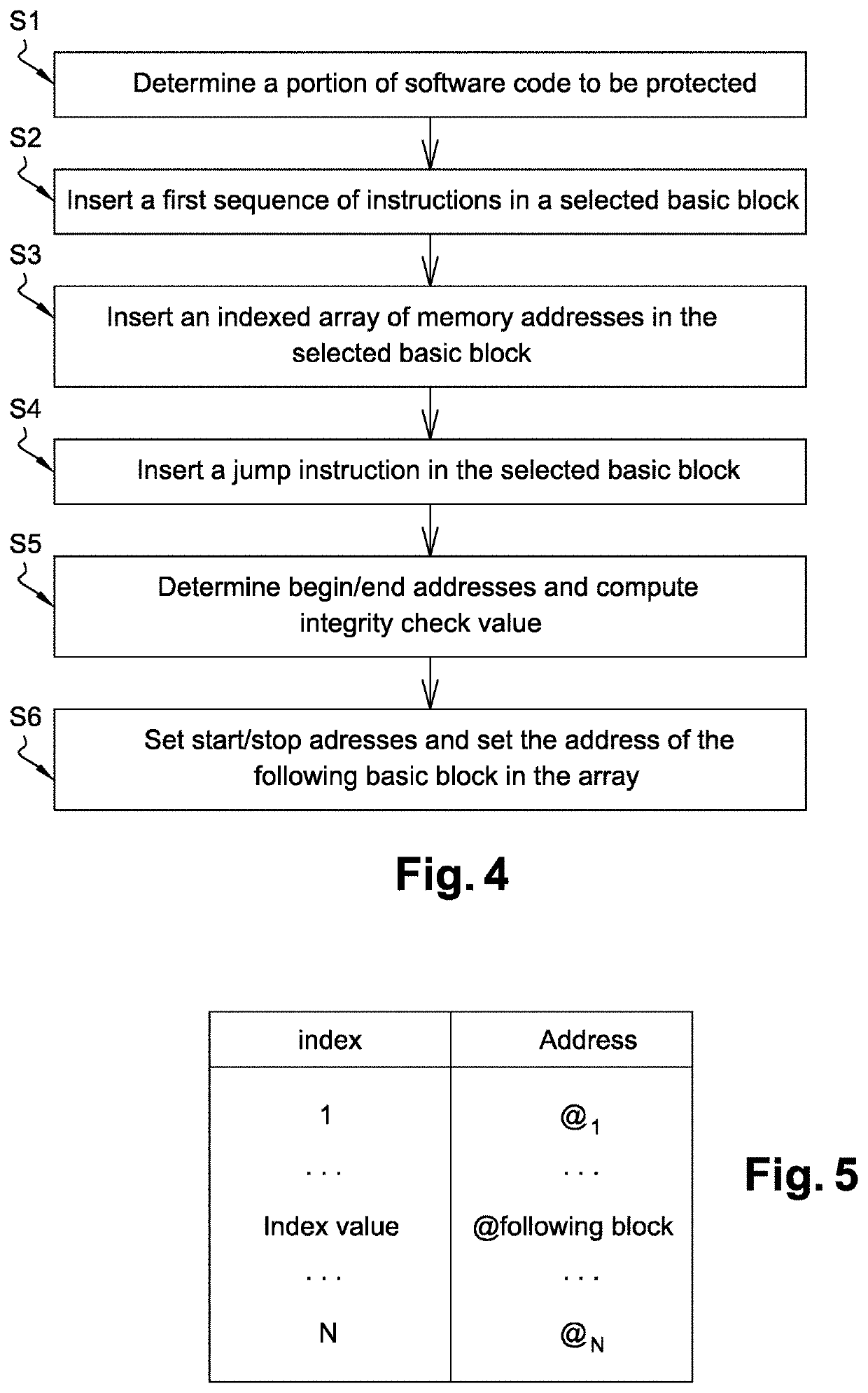
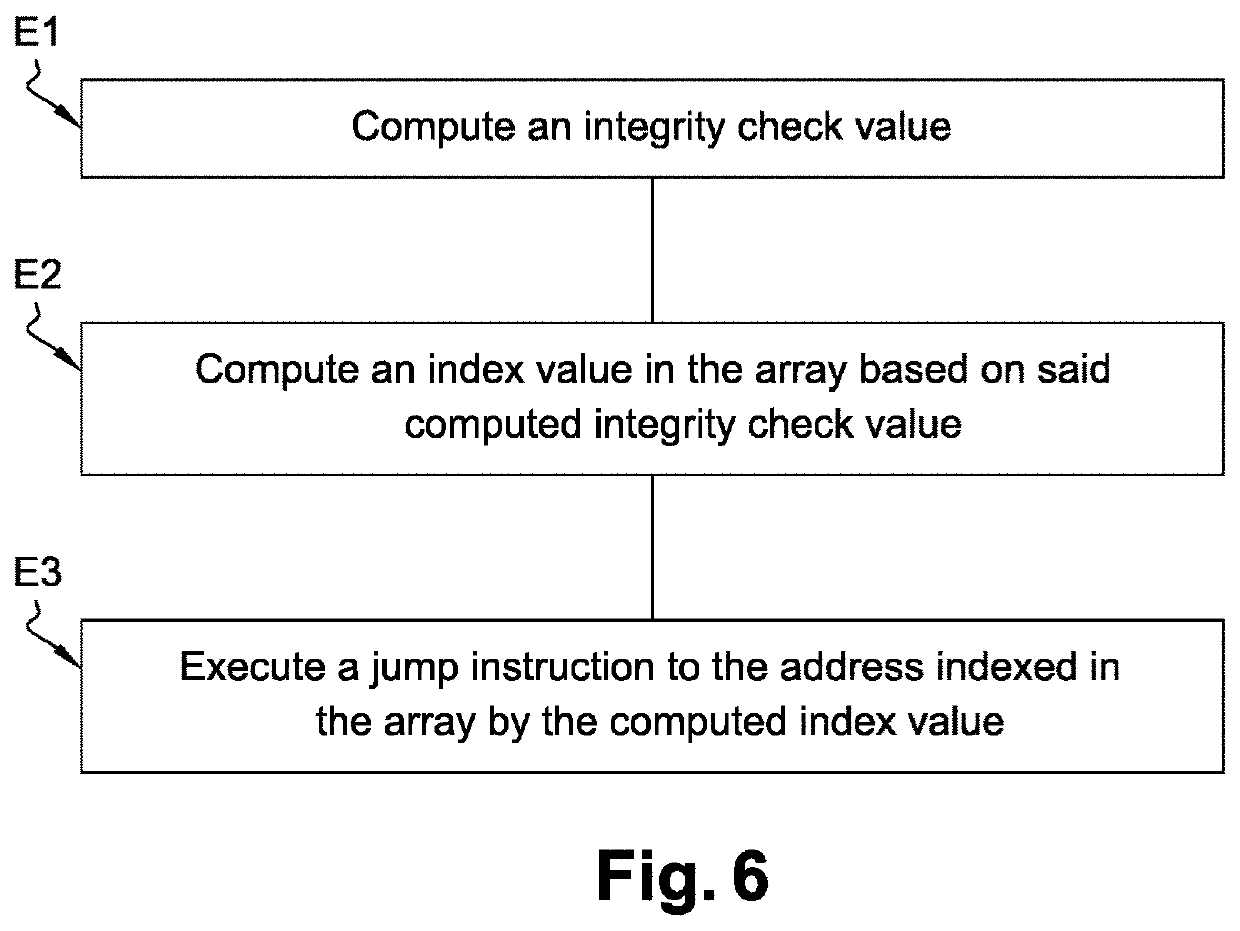
The present invention relates to a method of securing a compiled software code (SC) comprising computer code instructions organized in a plurality of basic blocks, said method generating a secure software code (SSC) and comprising the steps of: •determining (S1) by a processor a portion of the software code to be protected, •inserting (S2) by the processor in a selected basic block of the software code a first sequence of instructions which when executed at runtime: computes an integrity check value on said portion of the software code to be protected and computes an index value based on said computed integrity check value, •inserting (S3) by the processor in the selected basic block of the software code an indexed array of memory addresses in which the address, when executing the secure software code, of a following basic block to be executed after the selected basic block is indexed by said index value, •inserting (S4) by the processor at the end of the selected basic block of the software code a jump instruction to the address indexed in the array by said index value computed at runtime.
Owner:SFNT GERMANY +1
Method to secure a software code
ActiveUS11250110B2Breakage pointDifficult to understandProgram/content distribution protectionMemory addressSecurity software
The present invention relates to a method of securing a compiled software code (SC) comprising computer code instructions organized in a plurality of basic blocks, said method generating a secure software code (SSC) and comprising the steps of: •determining (S1) by a processor a portion of the software code to be protected, •inserting (S2) by the processor in a selected basic block of the software code a first sequence of instructions which when executed at runtime: computes an integrity check value on said portion of the software code to be protected and computes an index value based on said computed integrity check value, •inserting (S3) by the processor in the selected basic block of the software code an indexed array of memory addresses in which the address, when executing the secure software code, of a following basic block to be executed after the selected basic block is indexed by said index value, •inserting (S4) by the processor at the end of the selected basic block of the software code a jump instruction to the address indexed in the array by said index value computed at runtime.
Owner:THALES DIS CPL DEUTSCHLAND GMBH +1
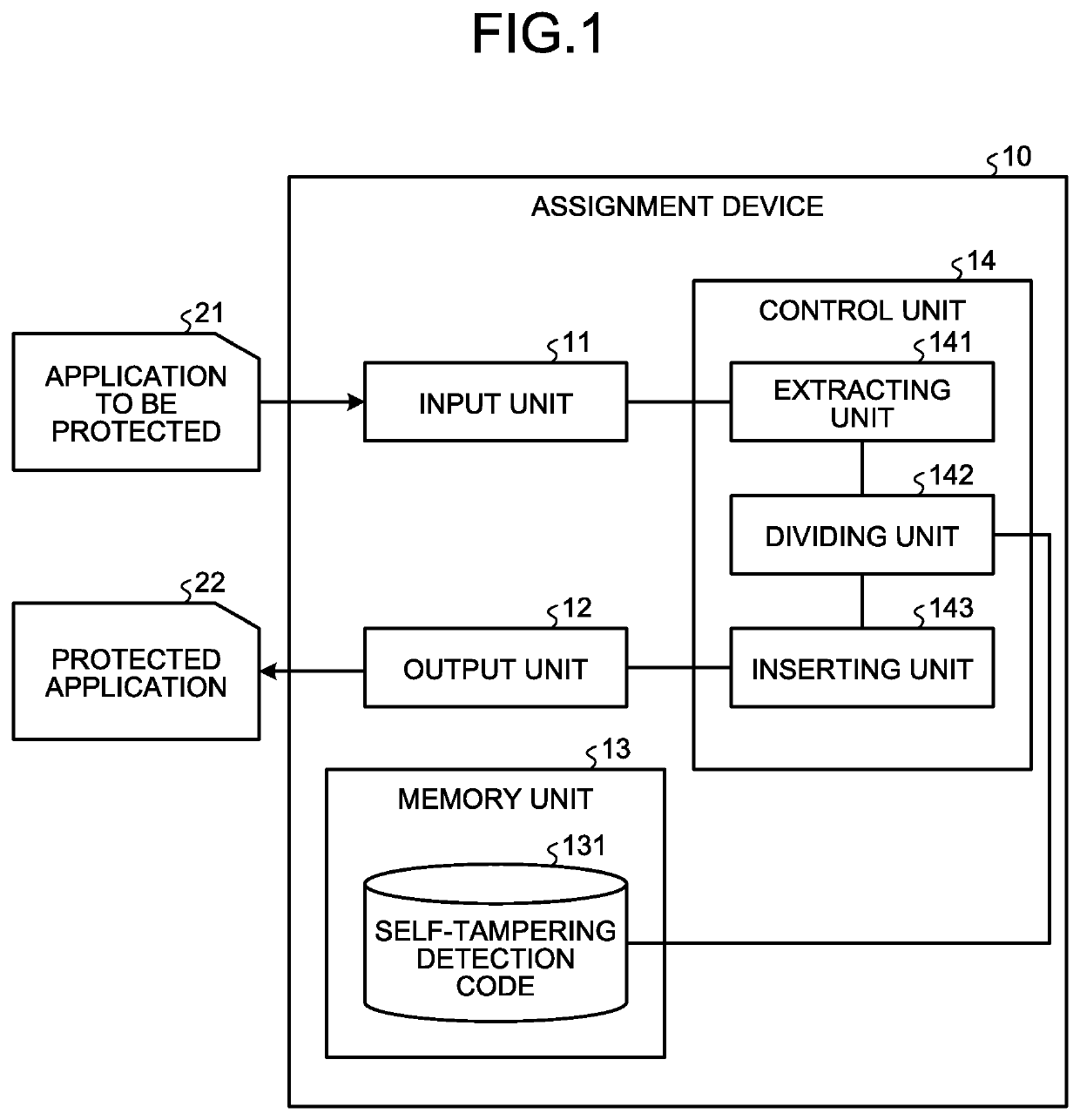
Assignment device, assignment method, and assignment program
ActiveUS20200042695A1Easy to findDigital data protectionPlatform integrity maintainanceParallel computingEngineering
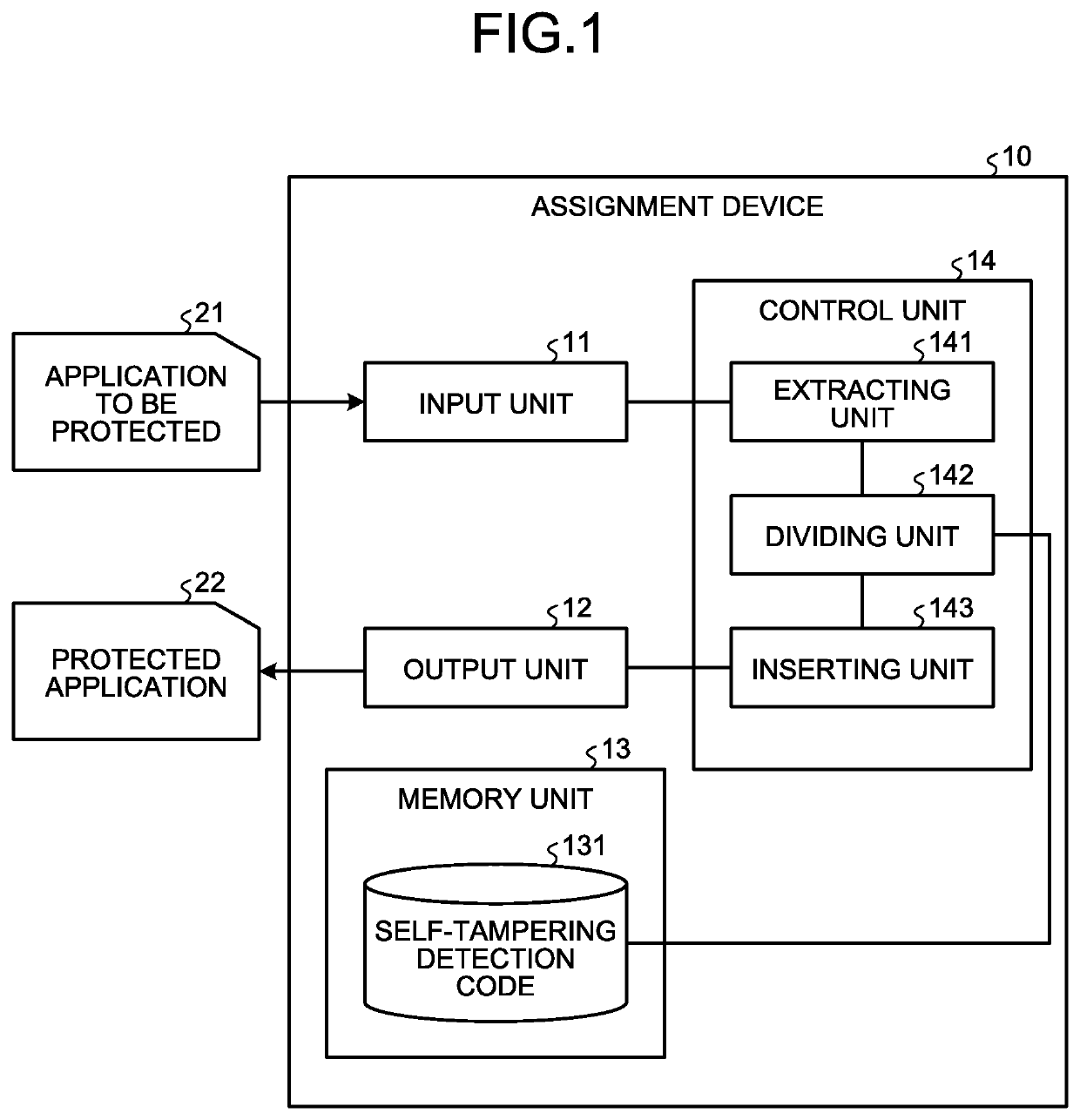
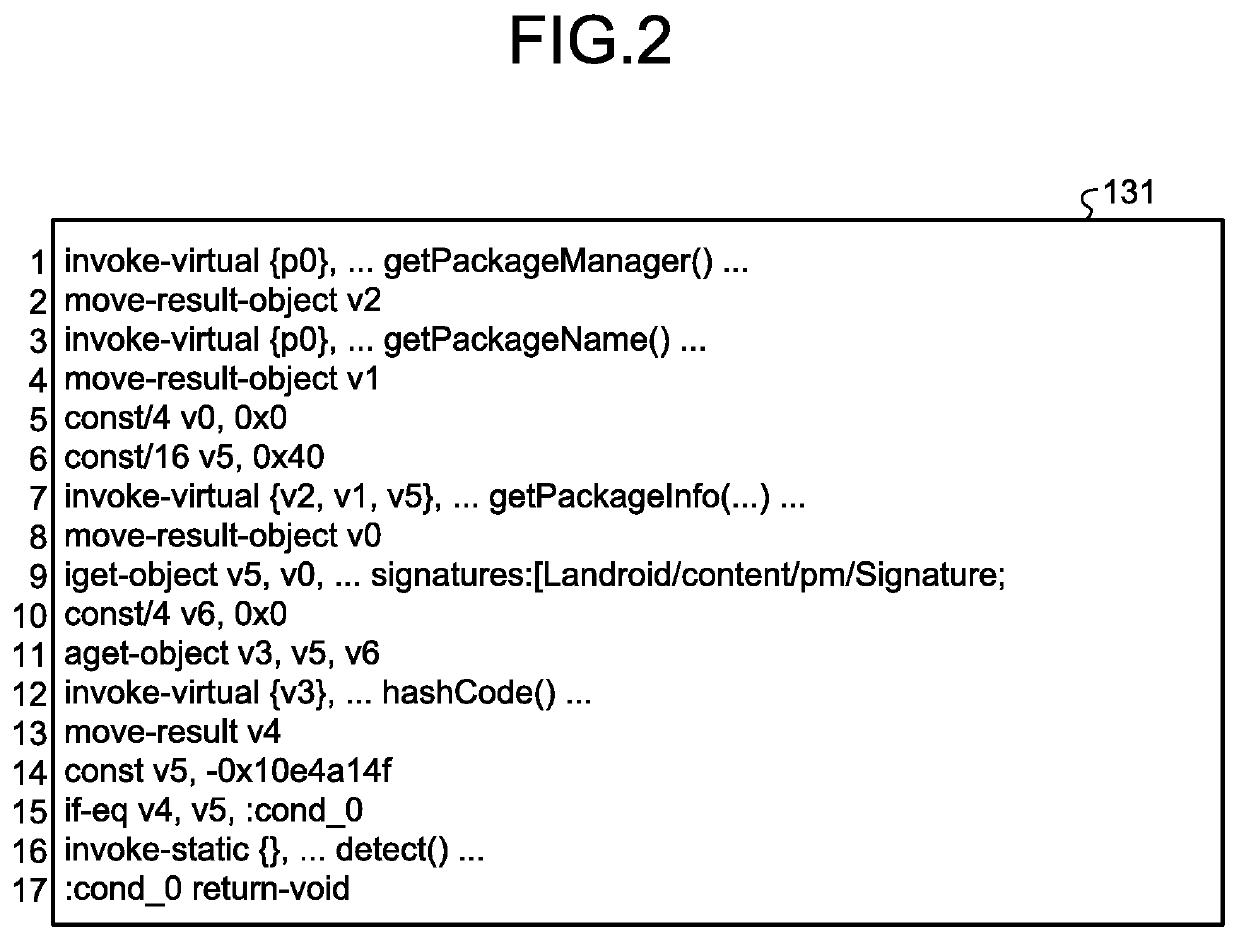
An extracting unit randomly extracts a block from among the blocks of instruction strings constituting the byte code of a first program and, at the time of execution of the first program, extracts the blocks which are invariably executed before the randomly-extracted block. A dividing unit randomly divides, into a plurality of blocks, the instruction strings constituting the byte code of a second program which enables detection of tampering of the first program. An inserting unit inserts the plurality of blocks, which are obtained by division by the dividing unit, at different positions in the block extracted by the extracting unit, while maintaining the execution sequence written in the second program.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Conditional branch instruction fusion method, device and computer storage medium
ActiveCN111930428BImplement parallel executionAvoid wastingInstruction analysisConcurrent instruction executionProgramming languageCoding block
The embodiment of the invention discloses a conditional branch instruction fusion method and device and a computer storage medium. The method comprises the following steps: in a compiling stage, respectively generating corresponding code blocks from branch statements in a conditional branch statement sequence in response to detecting that the conditional branch statement sequence appears in a program; fusing the code blocks according to a set instruction fusion strategy to obtain a fusion instruction, and storing the fusion instruction in an instruction memory, wherein the branch statement corresponds to a judgment result corresponding to a conditional judgment statement in the conditional branch statement sequence; in an execution stage, decoding a fusion instruction read from the instruction memory to obtain a code block contained in the fusion instruction; scheduling code blocks obtained by decoding to corresponding execution units in parallel according to an execution result obtained by executing the conditional judgment statement; and executing the scheduled code block through the execution unit.
Owner:西安芯云半导体技术有限公司
A Low-Power Register Allocation Compilation Optimization Method
ActiveCN112445481BReduce development costsLow power potentialEnergy efficient computingCode compilationRegister allocationScheduling instructions
Owner:JIANGNAN INST OF COMPUTING TECH
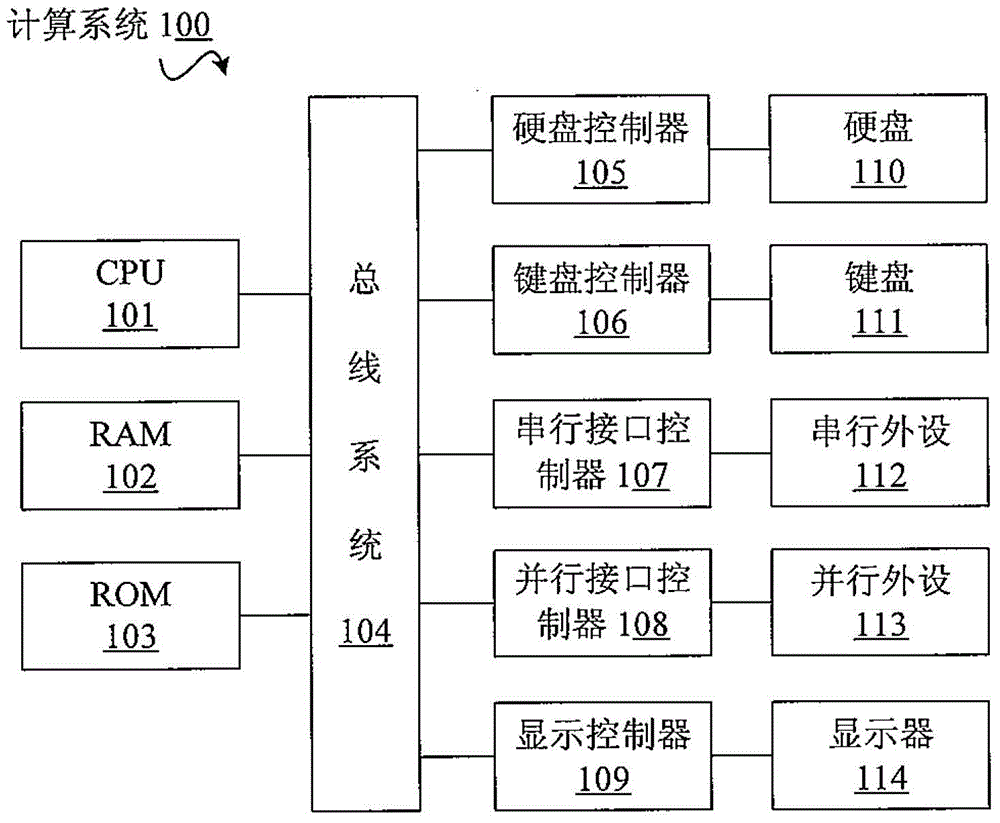
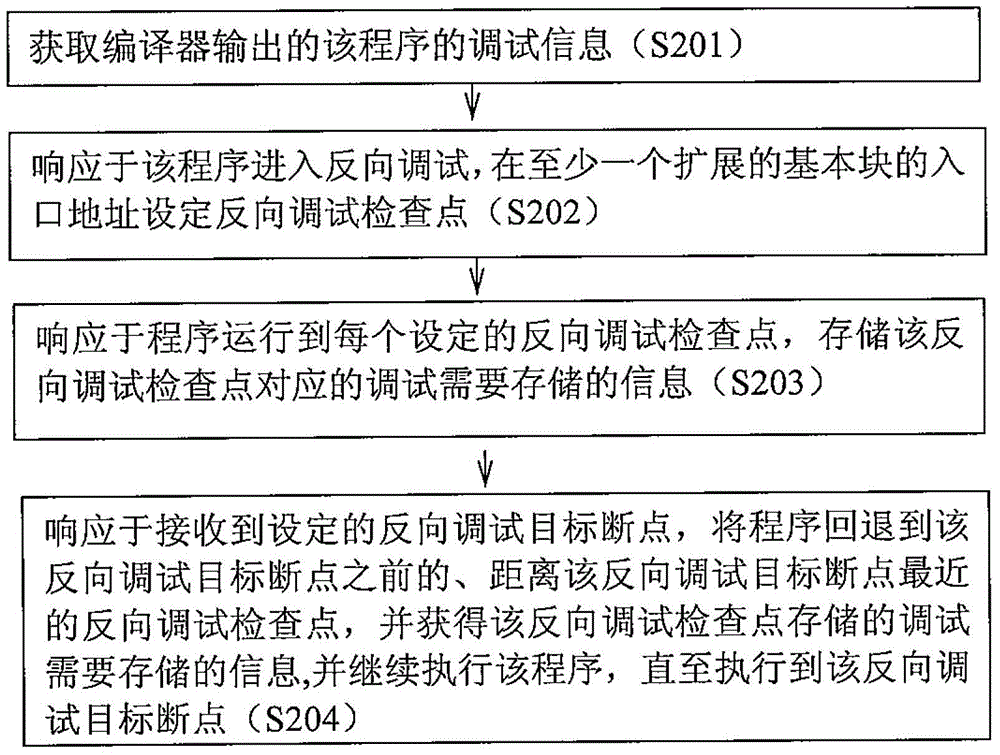
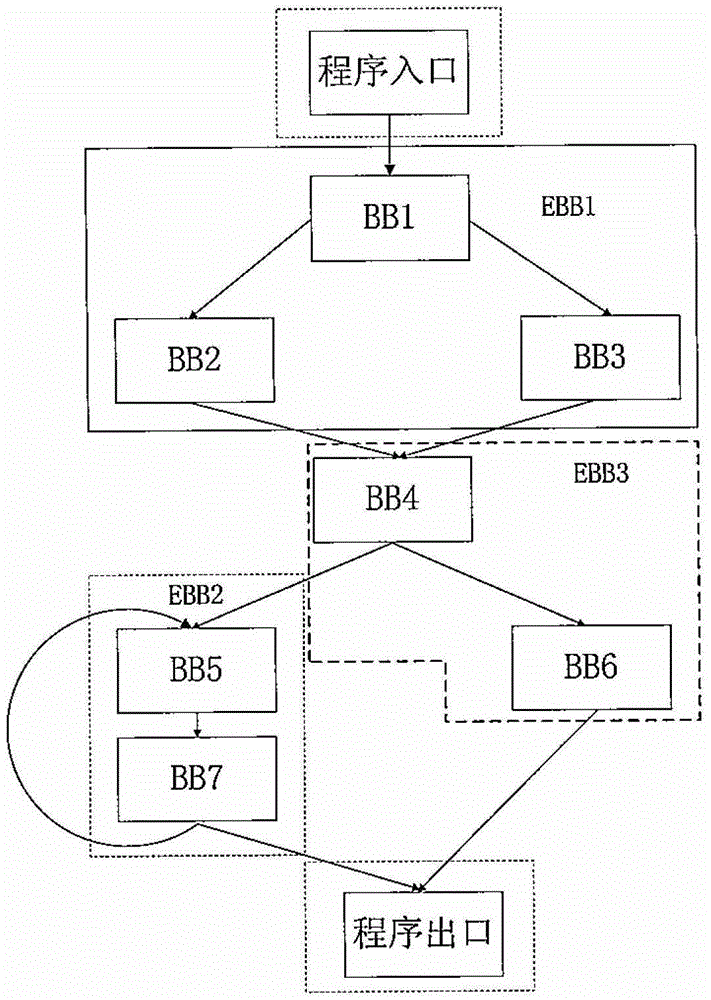
Reverse Debugger and Reverse Debugging Methods
The present invention relates to a method for reverse debugging a program and a reverse debugger, wherein the method includes: obtaining debugging information of the program output by a compiler, the debugging information including information related to the extended basic block of the program; responding When the program enters reverse debugging, a reverse debugging checkpoint is set at the entry address of at least one extended basic block; in response to the program running to the set reverse debugging checkpoint, the debugging corresponding to the reverse debugging checkpoint is stored. Information that needs to be stored; in response to receiving a set reverse debugging target breakpoint, rolling back the program to the reverse debugging checkpoint that is closest to the reverse debugging target breakpoint before the reverse debugging target breakpoint, And obtain the information that needs to be stored for debugging stored in the reverse debugging checkpoint, and continue to execute the program until it reaches the reverse debugging target breakpoint. The invention can reduce the information to be stored for reverse debugging and improve the debugging efficiency.
Owner:INT BUSINESS MASCH CORP
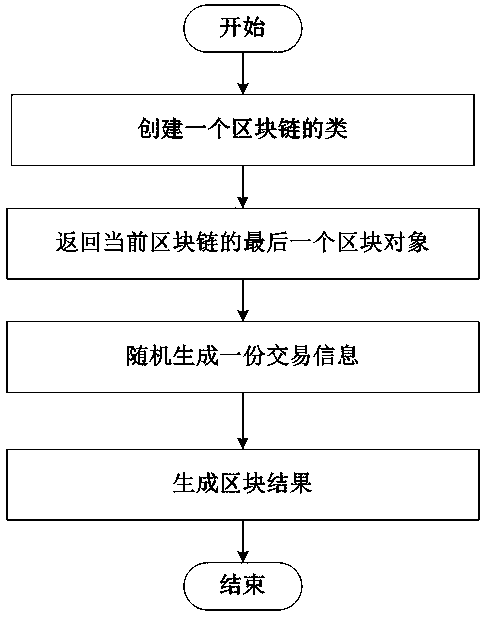
Implementation method of blockchains
InactiveCN110888631ASolve the problem of generating new blocks that are not uniqueFinanceCreation/generation of source codeSoftware engineeringFinancial transaction
Owner:ZHUHAI HENGQIN SHENGDA ZHAOYE TECH INVESTMENT CO LTD
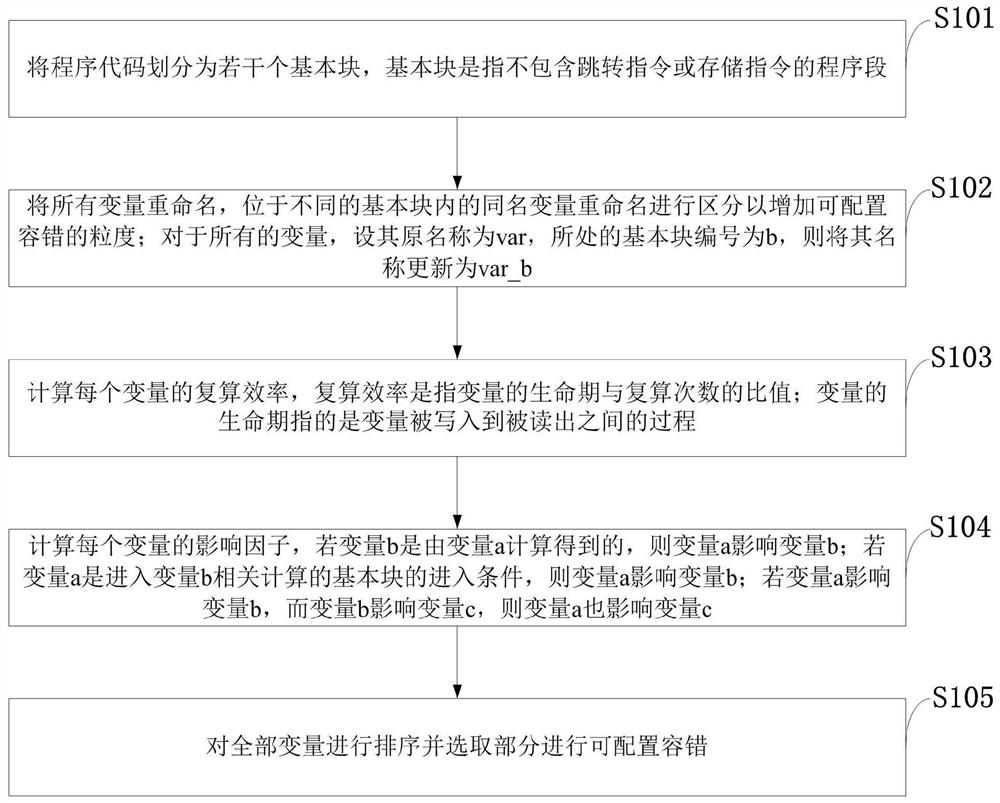
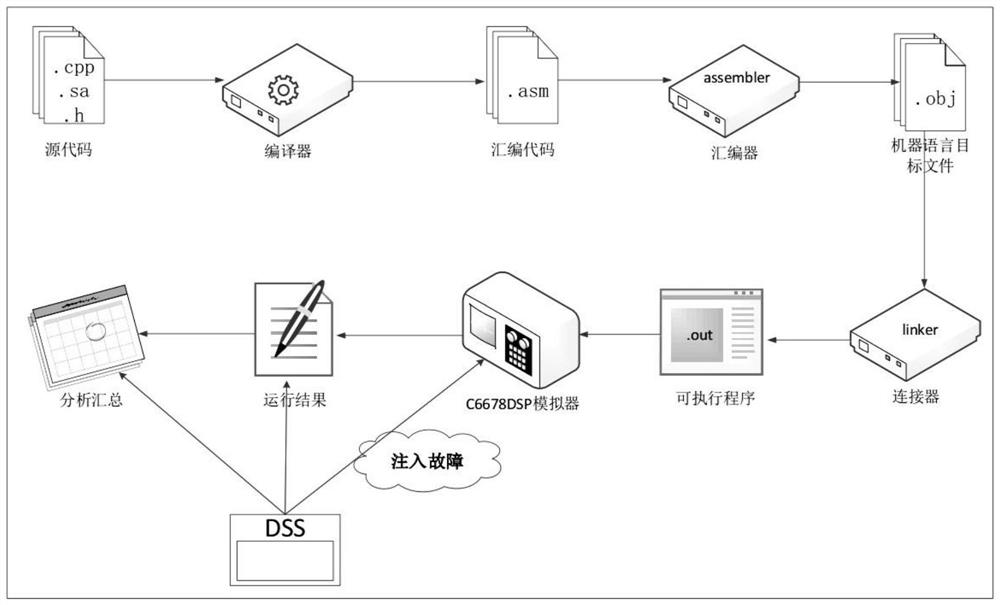
A configurable fault-tolerant method at linear assembly level, computer, computer program
InactiveCN108171016BFully configurable hardening methodsGood value for moneyProgram/content distribution protectionRedundant operation error correctionFault toleranceRename
Owner:NAT UNIV OF DEFENSE TECH
Assignment device, assignment method, and assignment program
ActiveUS11403388B2Easy to findMemory loss protectionError detection/correctionParallel computingByte
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Symbolic execution scheduling method and system for vulnerability path priorities
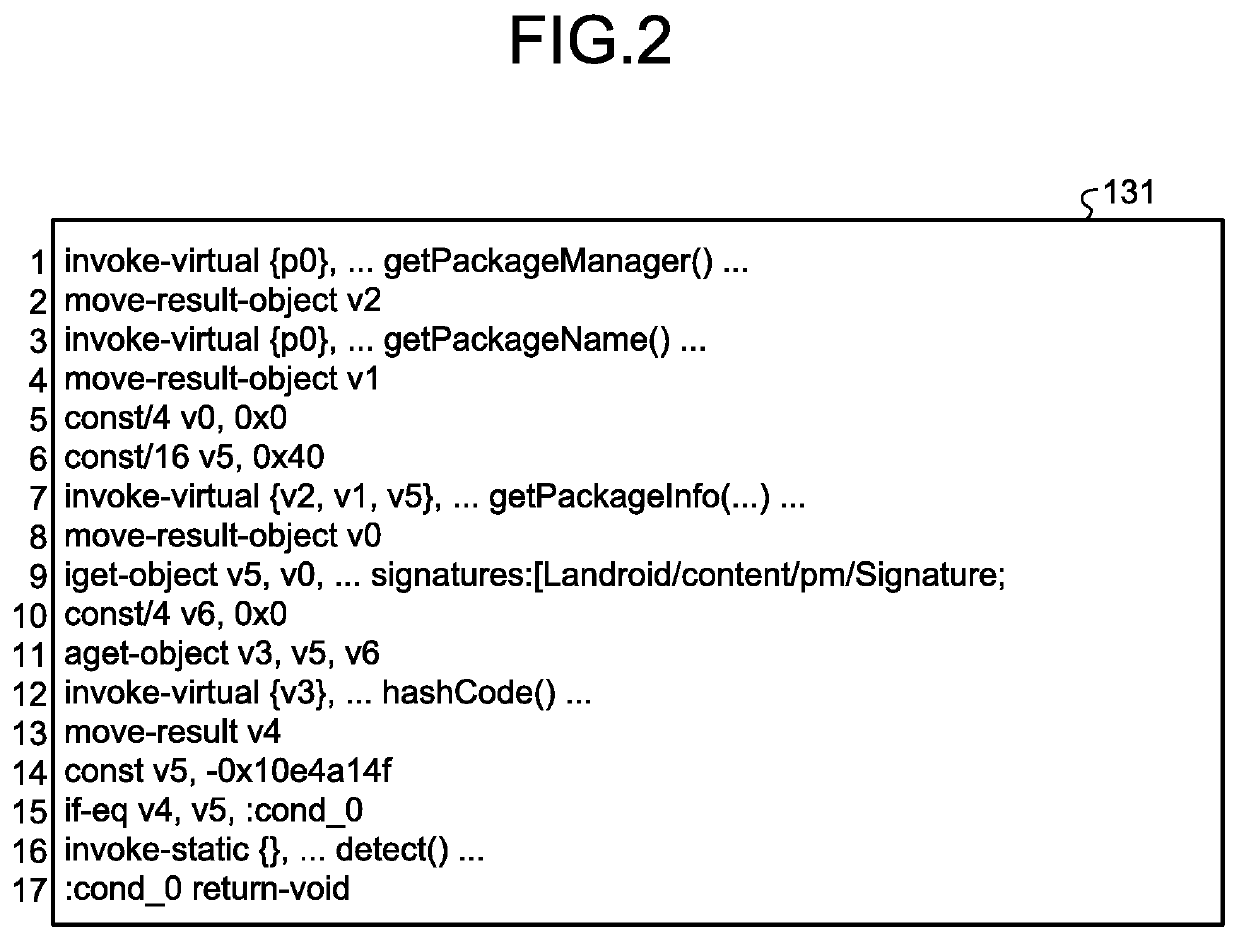
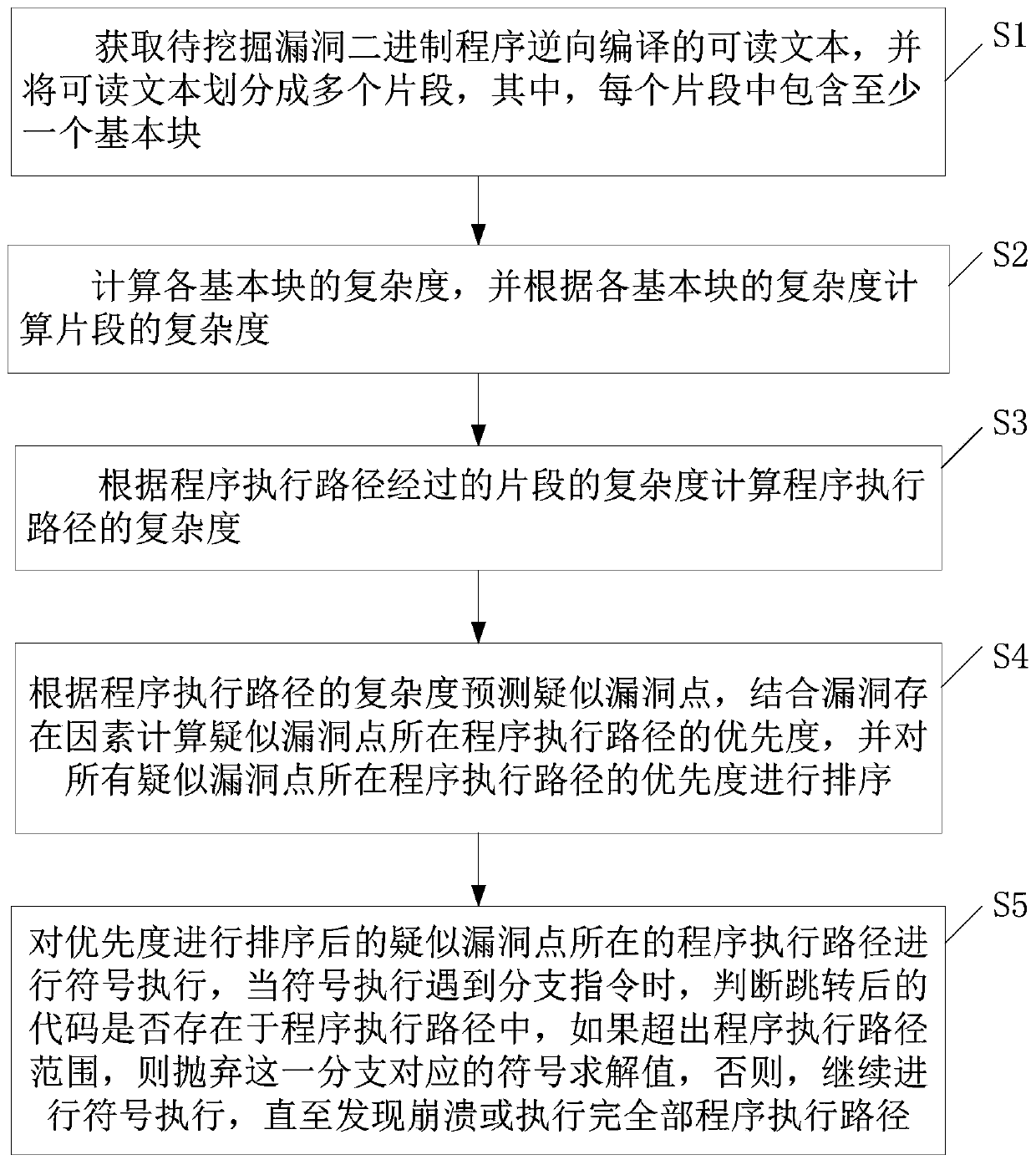
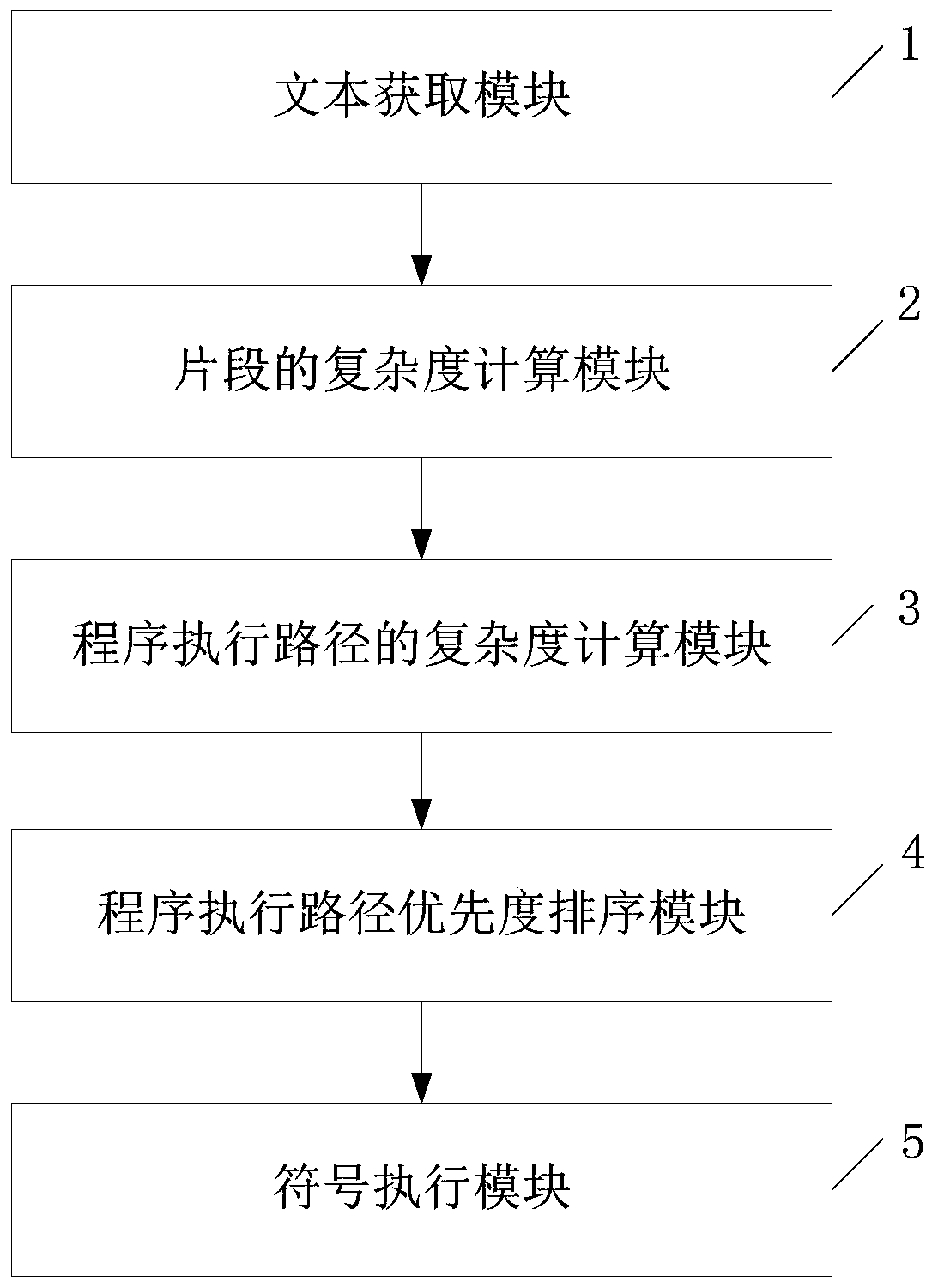
ActiveCN111581099AQuick discoveryEfficient discoveryReverse engineeringSoftware testing/debuggingPathPingRound complexity
The invention discloses a symbolic execution scheduling method and system for bug path priorities, and the method comprises the steps: enabling a to-be-mined bug binary program to be reversely compiled into a readable text, dividing the readable text into a plurality of segments, and enabling each segment to comprise at least one basic block; analyzing the complexity of the basic blocks with highvulnerability potentiality; combining the complexity of fragments and the complexity of program execution paths with vulnerability existence factors to calculate the priorities of the program execution paths where suspected vulnerability points are located, sorting the priorities, scheduling symbolic execution testing according to the priorities of the program execution paths, so that path guidance is provided for efficient symbolic execution, and vulnerability paths can be found quickly and efficiently.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
Method and system for generating program code modified by rule sets
ActiveUS11074049B2Easy and flexible possibilityEasy to set upVisual/graphical programmingModel driven codeAlgorithmTheoretical computer science
A computer-implemented method for generating program code based on one or more blocks of a block diagram, at least one block including a block variable. The method comprises opening the block diagram in a model editor, retrieving generation settings for the block variable from a data definition tool, the generation settings comprising a scope of the variable, determining that a modification rule is referenced in the generation settings, and retrieving the referenced modification rule from the data definition tool, wherein a modification rule comprises a filter condition and one or more code changes. A processor generates program code based on the block diagram and the generation settings and applies the referenced modification rule to the block variable in the generated code, which includes verifying that the filter condition is fulfilled for the block variable and applying the code changes to each occurrence of the variable in the code.
Owner:DSPACE DIGITAL SIGNAL PROCESSING & CONTROL ENG
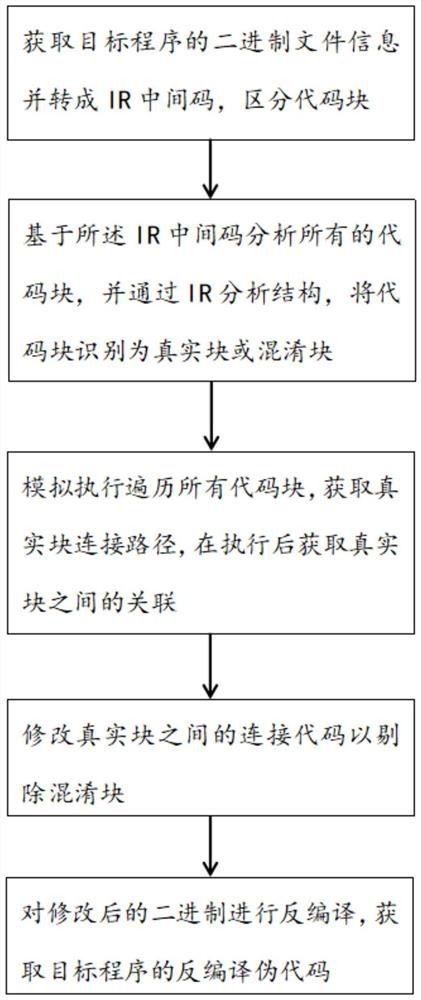
Anti-confusion method, system and application
PendingCN114817918AAchieve cullingAddresses issues with poor de-aliasingDecompilation/disassemblyPlatform integrity maintainanceCoding blockPathPing
The invention provides an anti-obfuscation method, system and application, and the method comprises the steps: converting a target program, distinguishing a real block from an obfuscation block, traversing all code blocks to obtain the connection paths of the real block and the correlation between the connection paths, and modifying the time connection codes of the real block to completely reject the obfuscation block. The problem of poor anti-confusion effect caused by omission during traversal of the existing anti-confusion scheme is solved.
Owner:厦门蝉羽网络科技有限公司
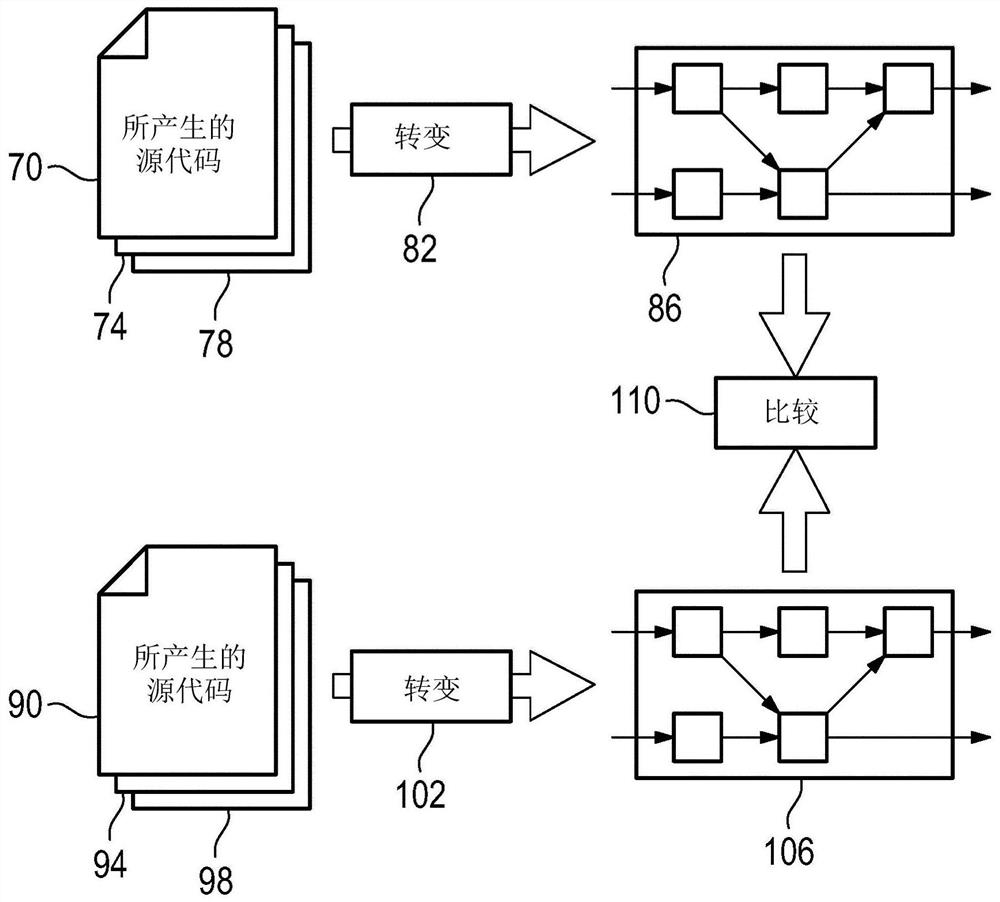
Methods for checking code equivalence
ActiveCN107567618BFully rebuiltAvoid reliabilityPower plant safety arrangementSafety arrangmentsData streamAlgorithm
A method for checking the functional equivalence of two pieces of software of a control system, in particular a programmable logic controller based control system designed from a function block diagram (120, 196) having a plurality of interconnected function blocks, the The method comprises the steps of: a) generating a first instance of compilable source code from a first plurality of functional block diagrams (70, 74, 78) by means of a first code generator following a first set of serialization rules; b ) parses the first instance of said source code and identifies groups of all function block I / O ports and nodes (nodes) and all connections between all function block I / O ports and nodes (arcs) of the data flow c) using the information from step b) to reconstruct in the upstream direction a first dataflow graph (86) of a first instance of said source code; d) by means of the first code following the first set of serialization rules generator or a second code generator following a second set of serialization rules to generate a second instance of compilable source code from a second plurality of function block diagrams (90, 94, 98); e) parsing said source code The second instance and identifies the set of all functional block I / O ports and nodes (nodes) and the set of all connections between all functional block I / O ports and nodes (arcs) of the data stream; f) use the set from step e) information to reconstruct in the upstream direction a second dataflow graph (106) of a second instance of said source code; g) combining said first identified dataflow graph (86) with said second identified The dataflow graphs (106) are compared with each other node by node, thereby checking whether the transitive closure up to the input of a node is the same in the second instance of the source code as in the first instance of the source code.
Owner:FRAMATOME ANP
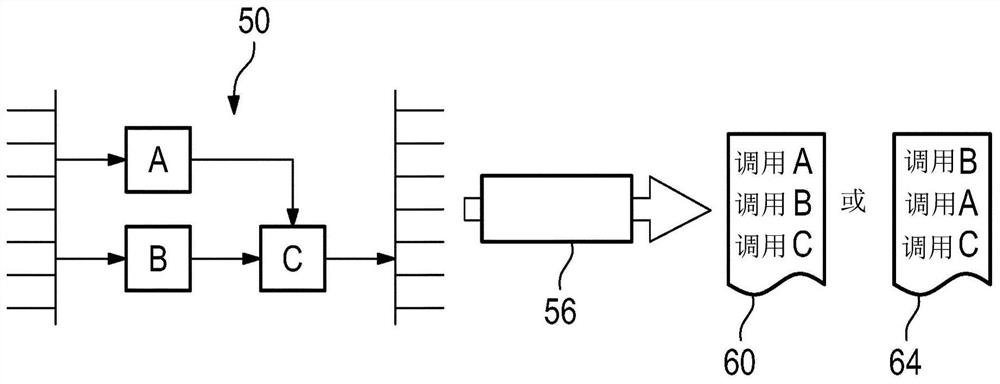
Operating program writing system
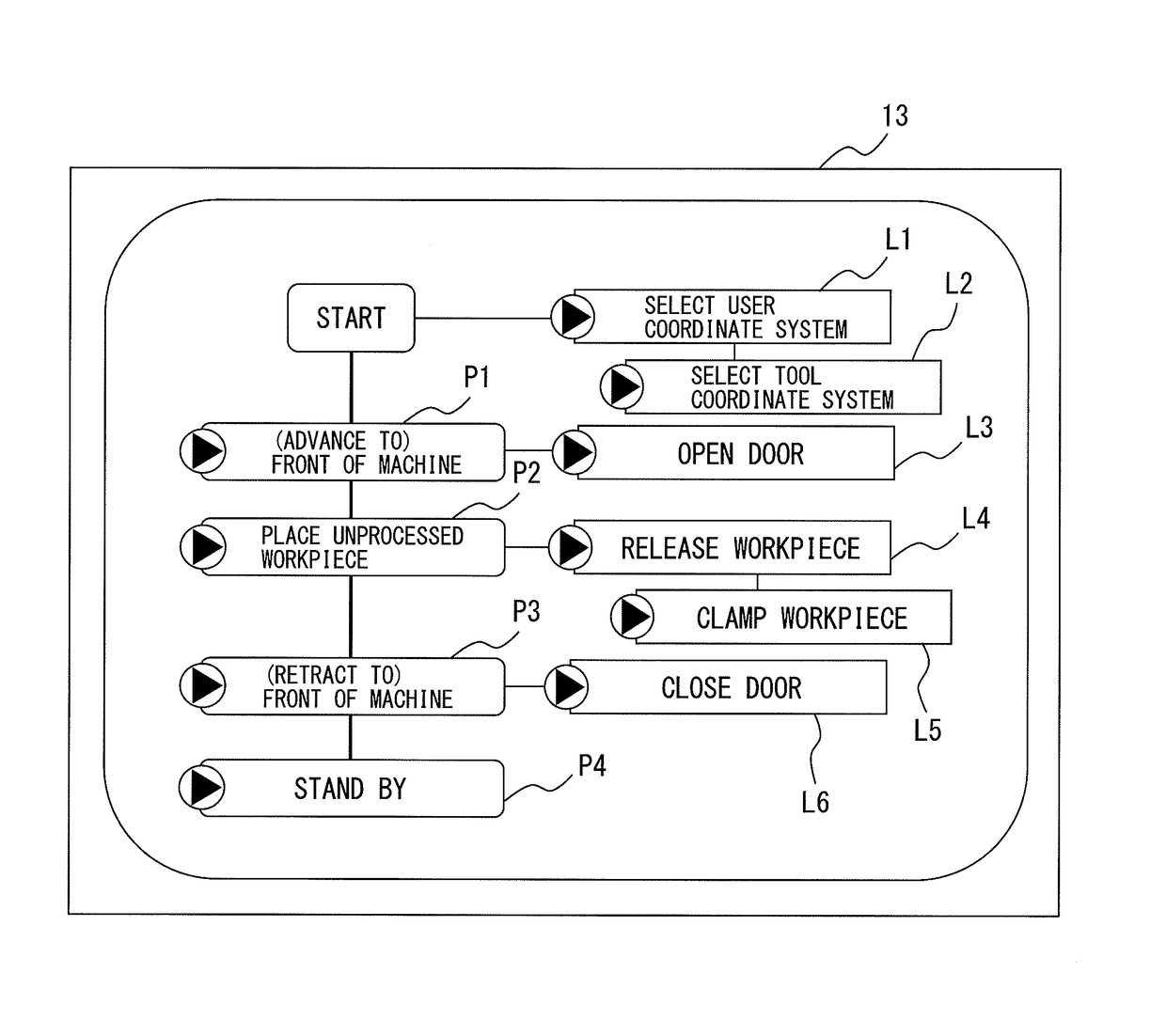
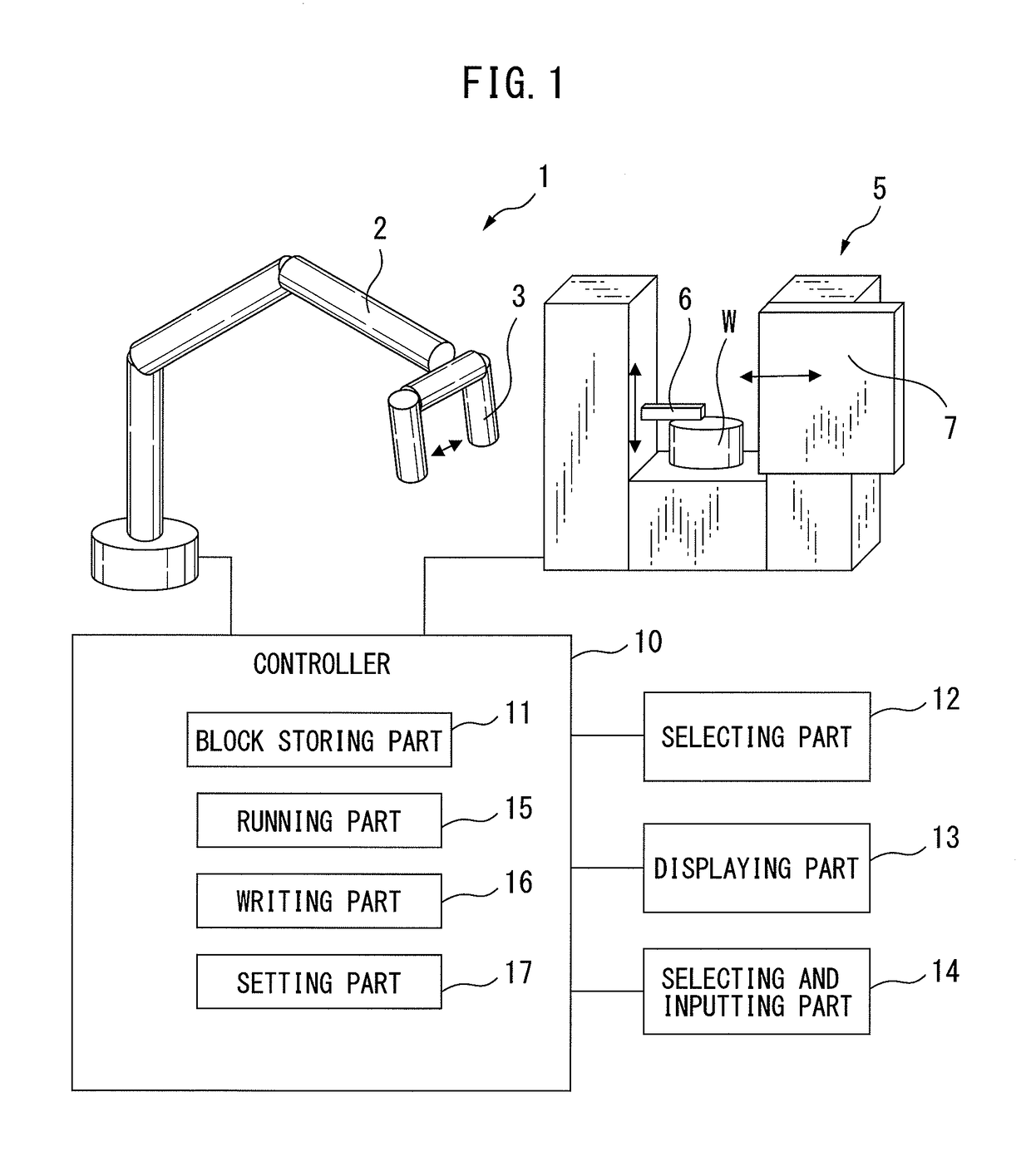
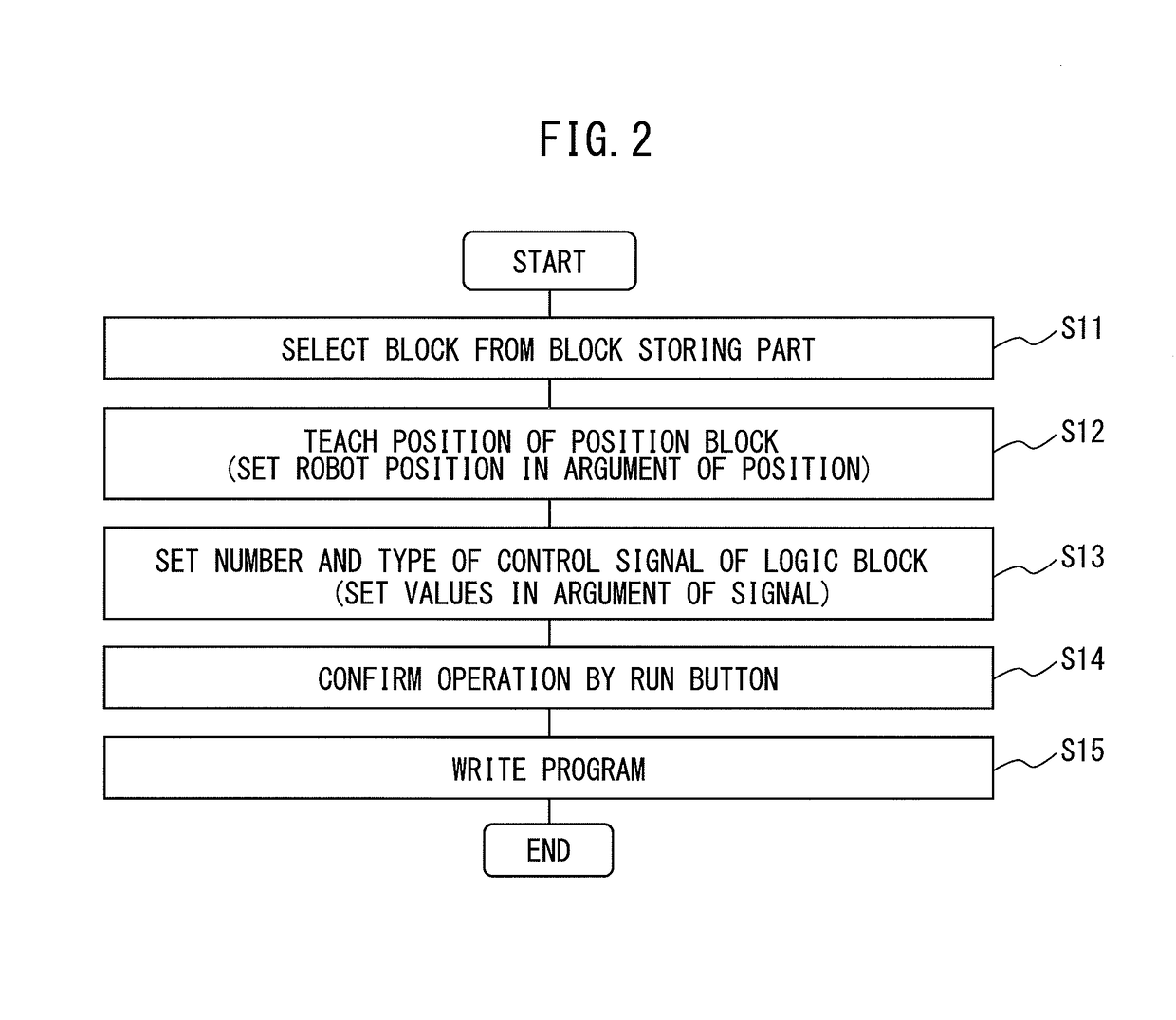
An operating program writing system includes a block storing part which stores a plurality of blocks constituting work units of an operating program, a selecting part which selects any number of blocks from the plurality of blocks, a displaying part which displays a path diagram including the any number of blocks and arguments which are contained in the blocks, a selecting and inputting part which selects at least one block among the any number of blocks and inputs the arguments of the at least one block, a running part which arranges run buttons for the respective any number of blocks and runs blocks which correspond to the run buttons, and a writing part which uses the any number of blocks and the input argument of the at least one block as the basis to write an operating program.
Owner:FANUC LTD
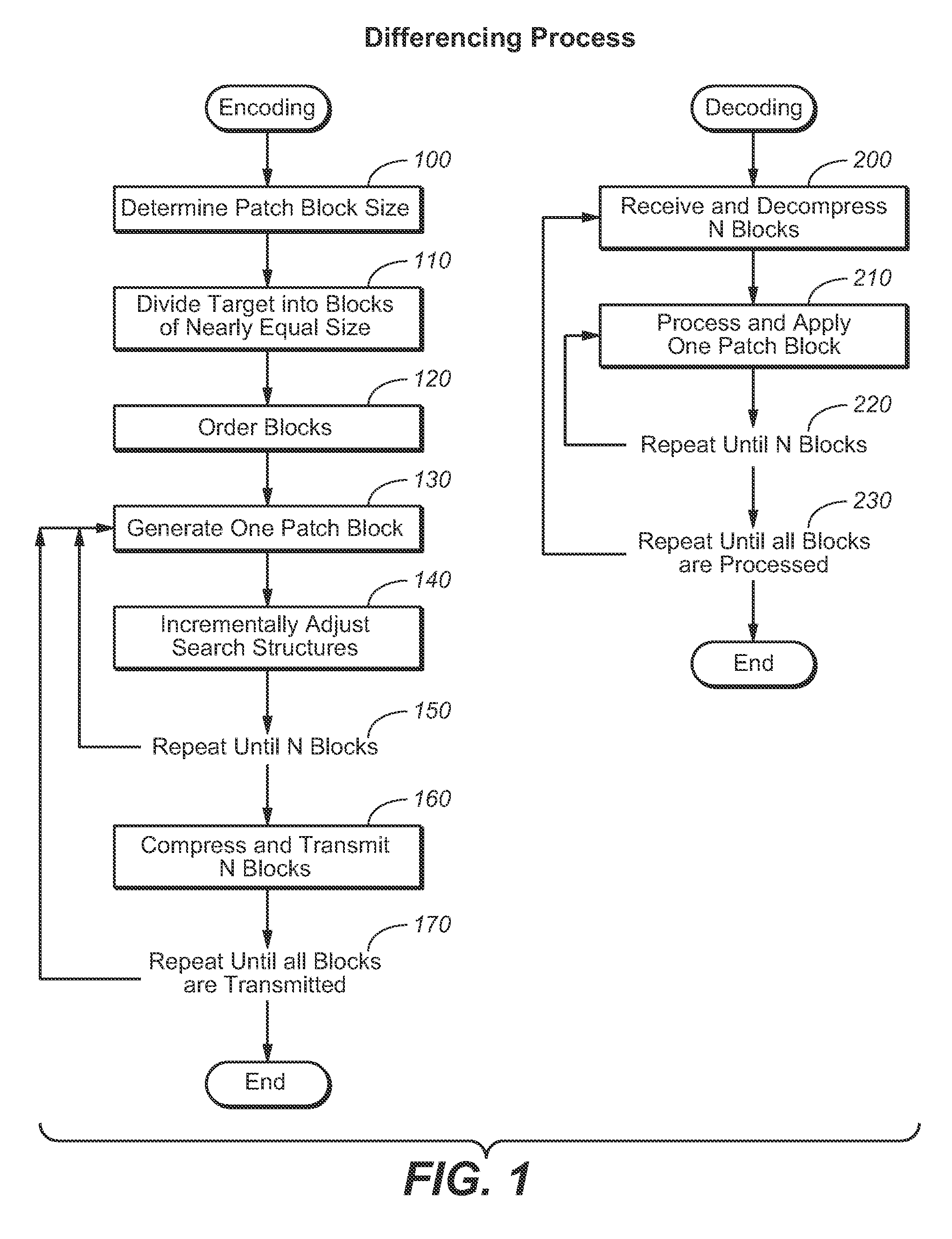
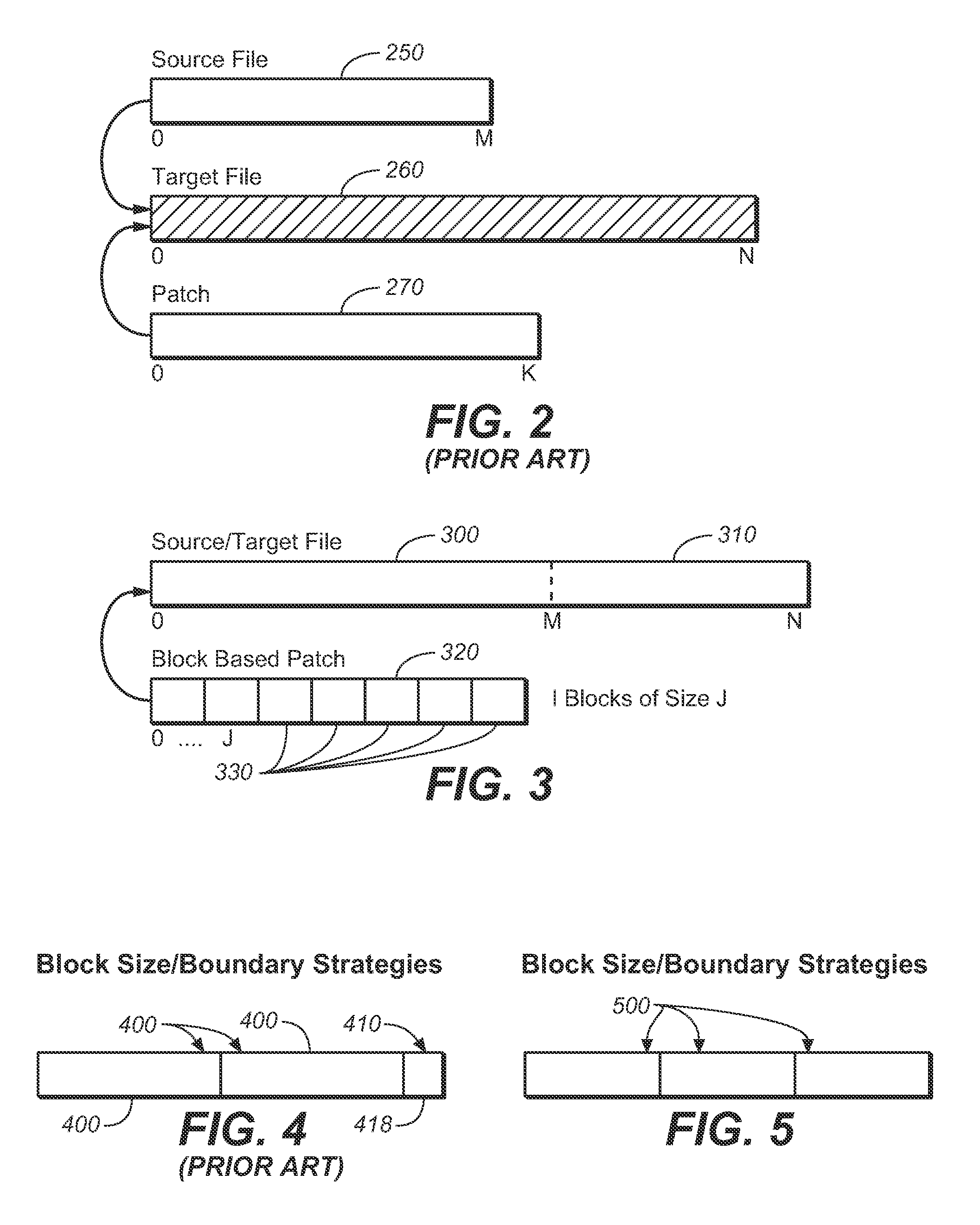
Block-based differencing algorithm
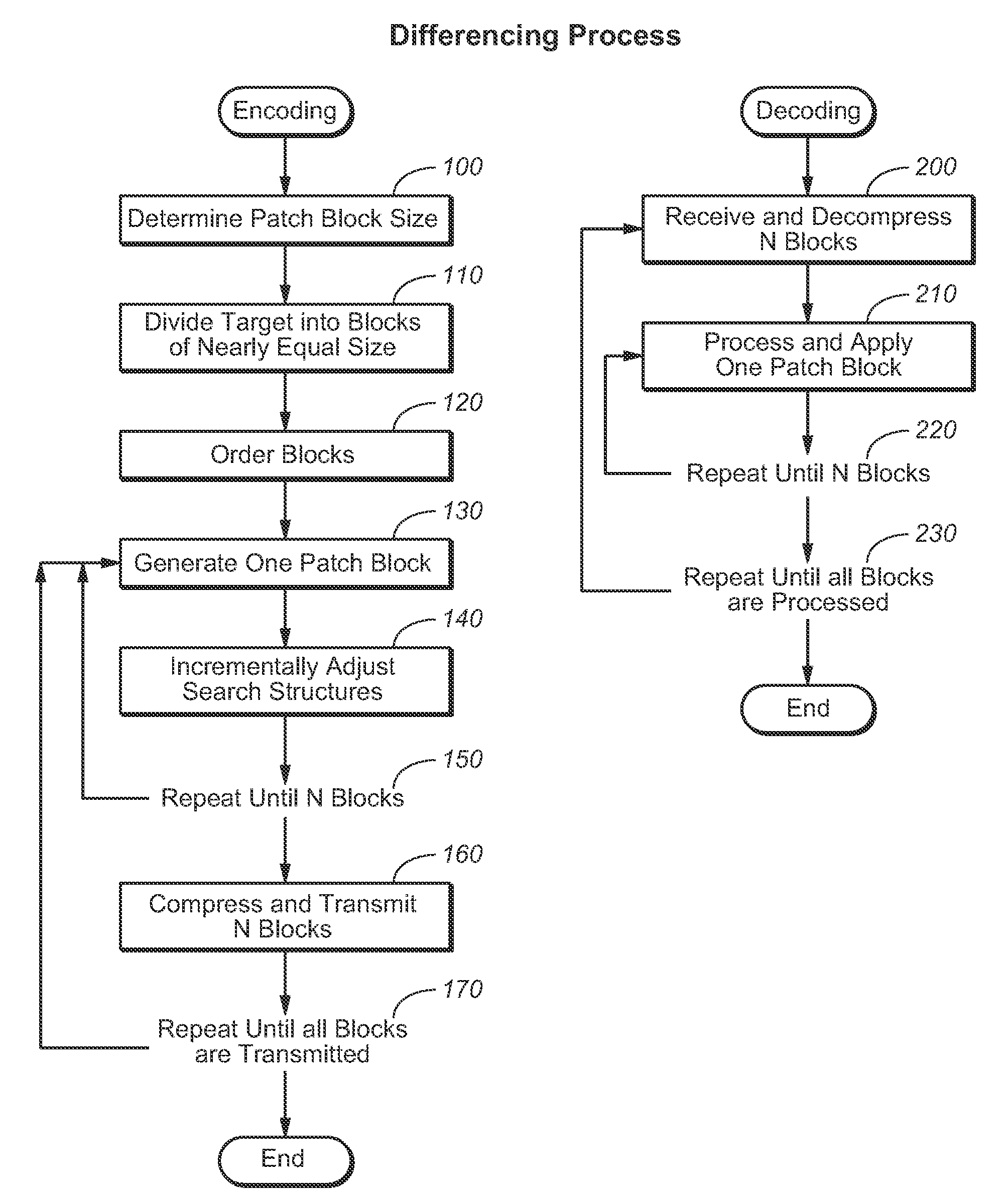
ActiveUS20110202503A1Avoid performanceImprove performanceSoftware engineeringDigital data processing detailsDifferential algorithmFile size
A system and method for a block based differencing algorithm which includes the ability to limit memory requirements regardless of source file sizes by splitting the source file into optimally sized blocks. The invention allows the blocks to be processed in any order allowing in-place operation. Further, the present invention allows a second stage compressor to match the compressor blocks to those used by the differencing algorithm to optimize compressor and decompressor performance.
Owner:SMITH MICRO SOFTWARE INC
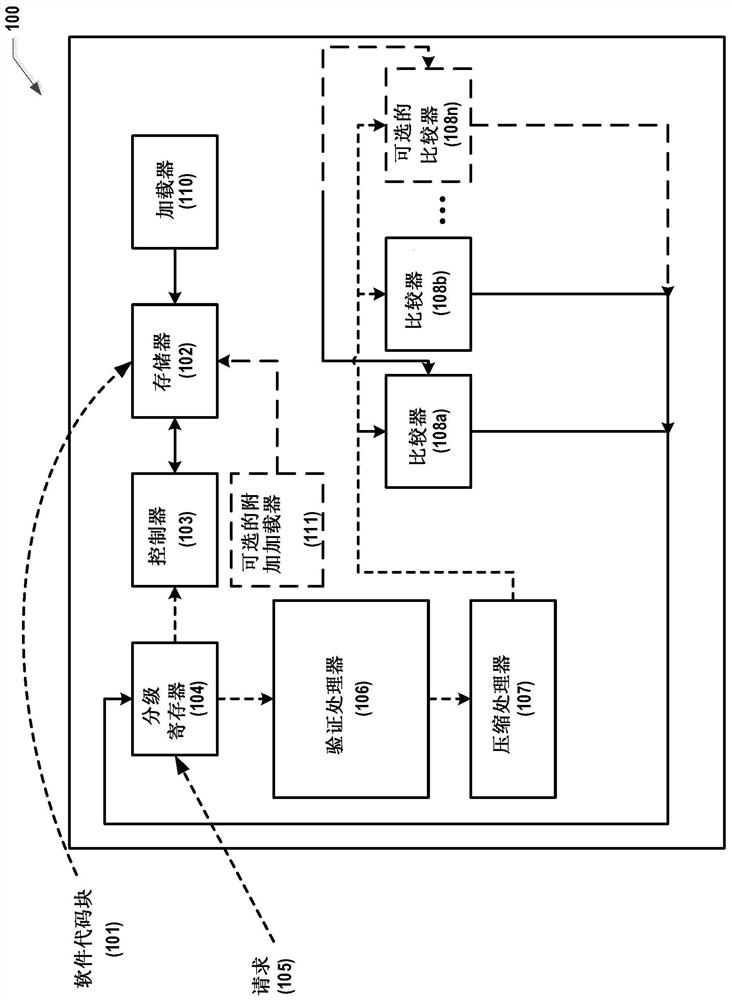
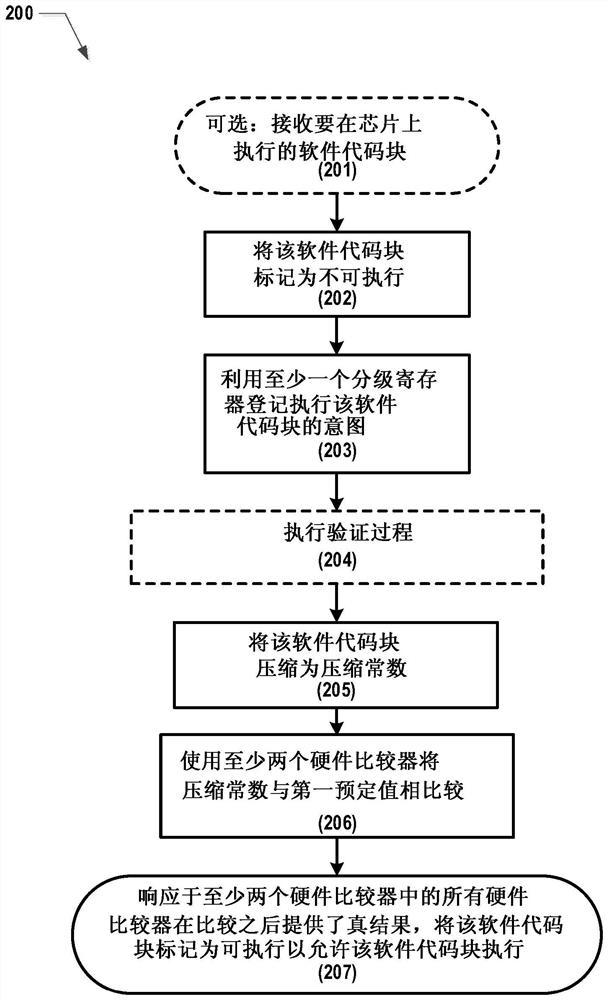
Safe Code Jumps and Execution Strobes
ActiveCN108537066BInternal/peripheral component protectionSecuring communicationCoding blockSafety property
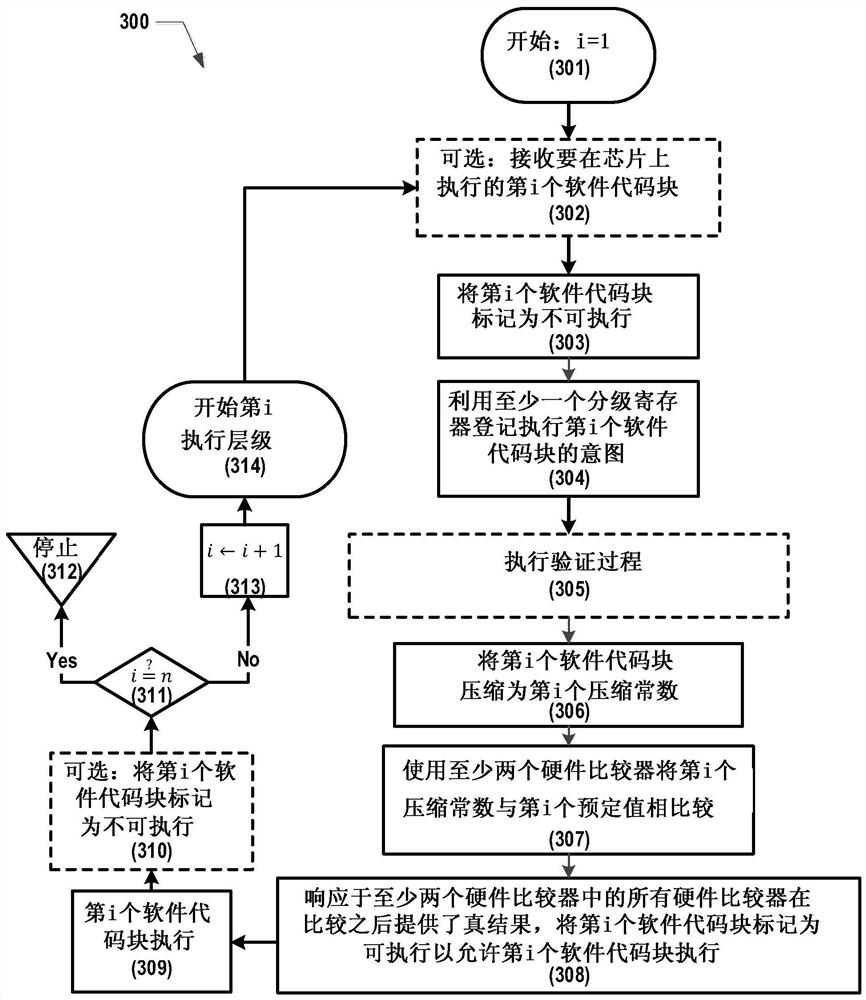
This application relates to secure code jumps and execution gating. Systems, apparatus, and methods are disclosed for improving the security of silicon-based systems by creating a glitch-resistant process for executing blocks of software code on the silicon-based systems. An example method may begin by marking a block of software code as non-executable. Second, the intent to execute the block of software code is registered using a staging register. Third, the software code blocks are compressed into compressed constants. Fourth, the compression constant is compared to a first predetermined value using two comparators. Fifth, the block of software code is marked executable to allow execution of the software code in response to the comparator providing a true result after the comparison. In another aspect, the example method may be repeated for n>1 iterations, and in each iteration i, the ith block of software code is compressed to the ith compression constant compared to the ith predetermined value.
Owner:GOOGLE LLC
Anti-vulnerability mining method and device based on code injection
ActiveCN112163218ALow efficiencyAchieve protectionDecompilation/disassemblyPlatform integrity maintainancePathPingIntermediate language
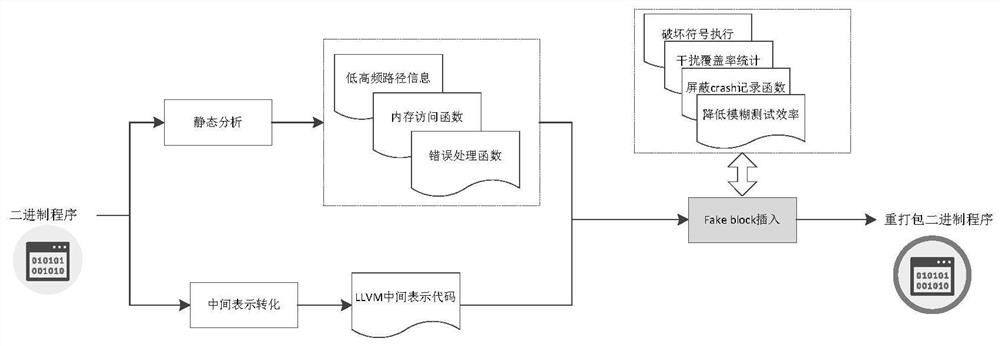
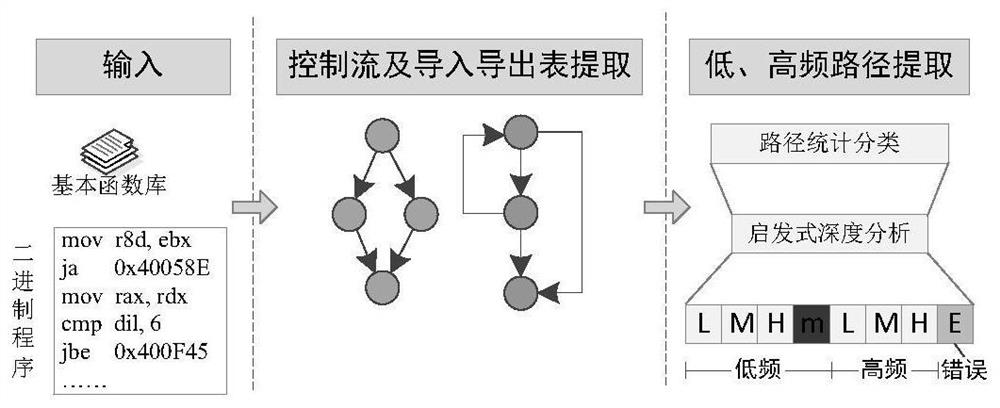
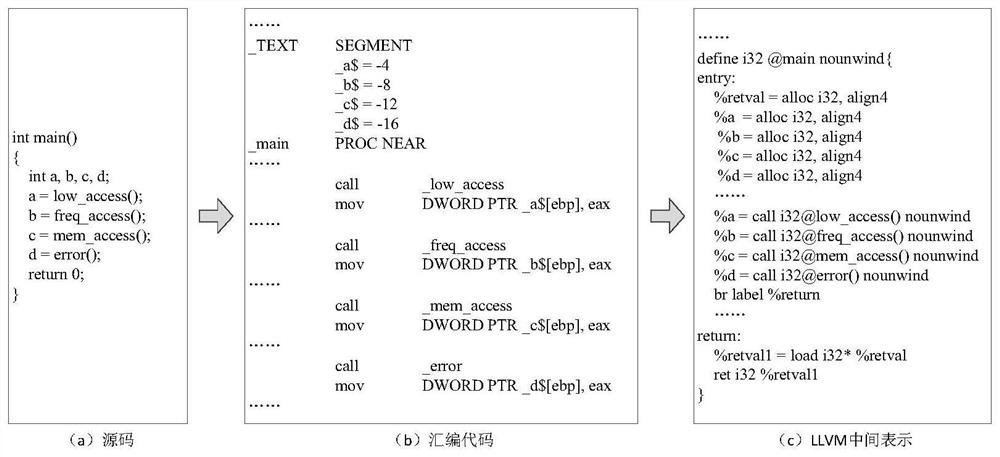
The invention belongs to the technical field of software security protection, and discloses an anti-vulnerability mining method and device based on code injection. The method comprises the steps: recognizing an import and export table, a low-frequency path and a high-frequency path of a target program for a known binary program through static analysis, and determining a call relation; converting the target program into a unified intermediate representation, and respectively inserting pseudo code blocks in the low frequency and the high frequency to reduce the efficiency of the fuzzy tester; and finally, packaging and publishing the modified binary program again. According to the method, the binary program can be effectively protected from being influenced by fuzzy test mining vulnerabilities, and calling of a third-party dll library is supported.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Function execution method, building block function rewriting method and related equipment
ActiveCN114840198AVisual/graphical programmingEnergy efficient computingProgramming languageUser-defined function
The invention provides a function execution method, a building block function rewriting method and related equipment which are applied to a programming platform, a plurality of basic building blocks are provided in the programming platform, and each basic building block corresponds to a built-in function. The function execution method comprises the steps that when an execution instruction is received, a function corresponding to a building block indicated by the execution instruction is executed; wherein the building blocks indicated by the execution instruction comprise target building blocks corresponding to the custom function; the self-defined function is a function for realizing a set function after being assembled according to a built-in function provided by the programming platform. Thus, when the target building block is executed in the programming platform, the user-defined function can be executed, other functions except the basic function provided by the programming platform are achieved, and therefore the flexibility and creativity of languages in the programming platform are improved. Furthermore, the custom function can be associated with the basic building blocks, so that the function of the building blocks is rewritten, and the flexibility and creativity are further improved.
Owner:北京聪明核桃教育科技有限公司
A binary software protection method using dynamic fine-grained code hiding and obfuscation technology
ActiveCN106650340BImprove securityImprove protection strengthProgram/content distribution protectionTheoretical computer scienceLogisim
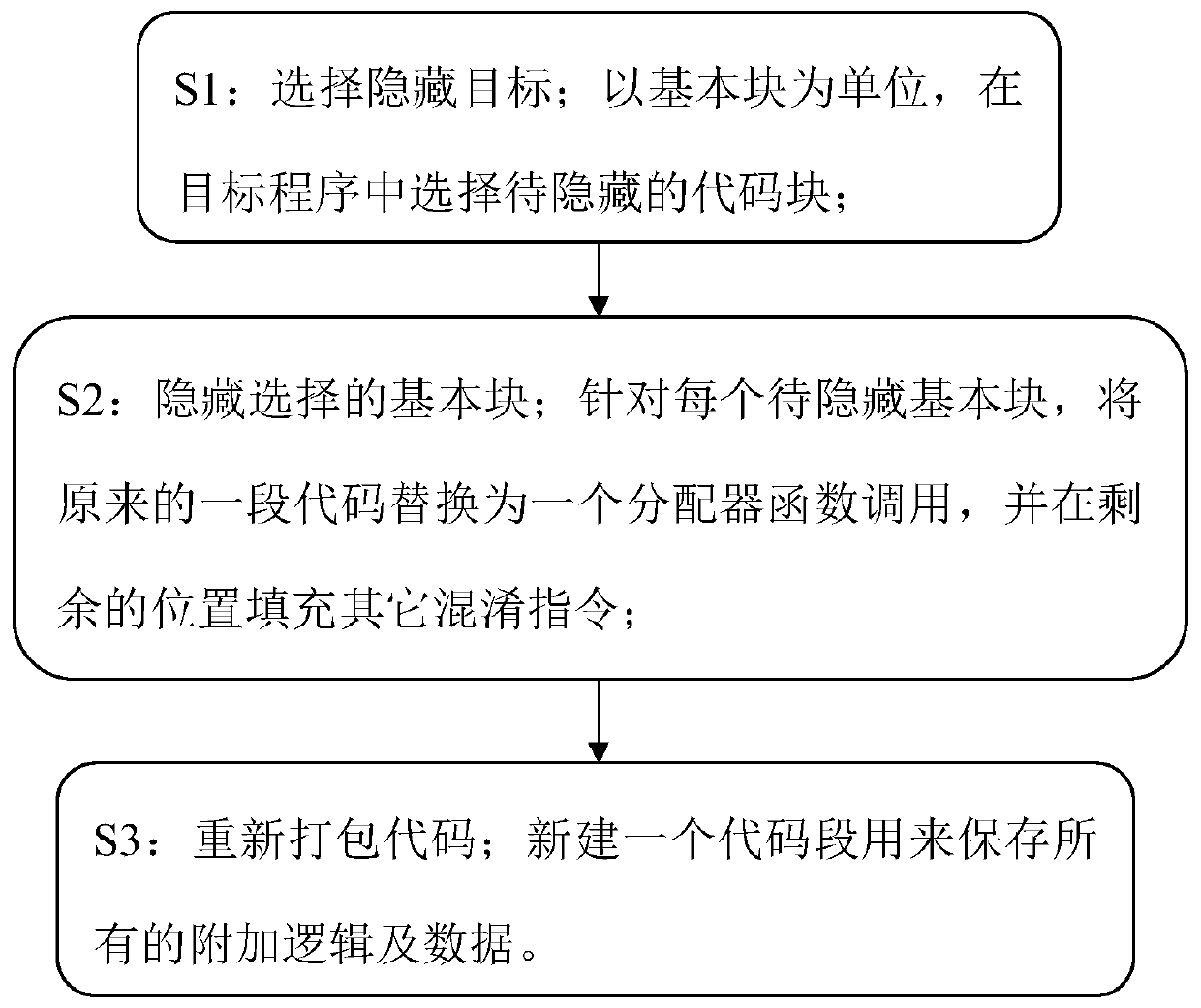
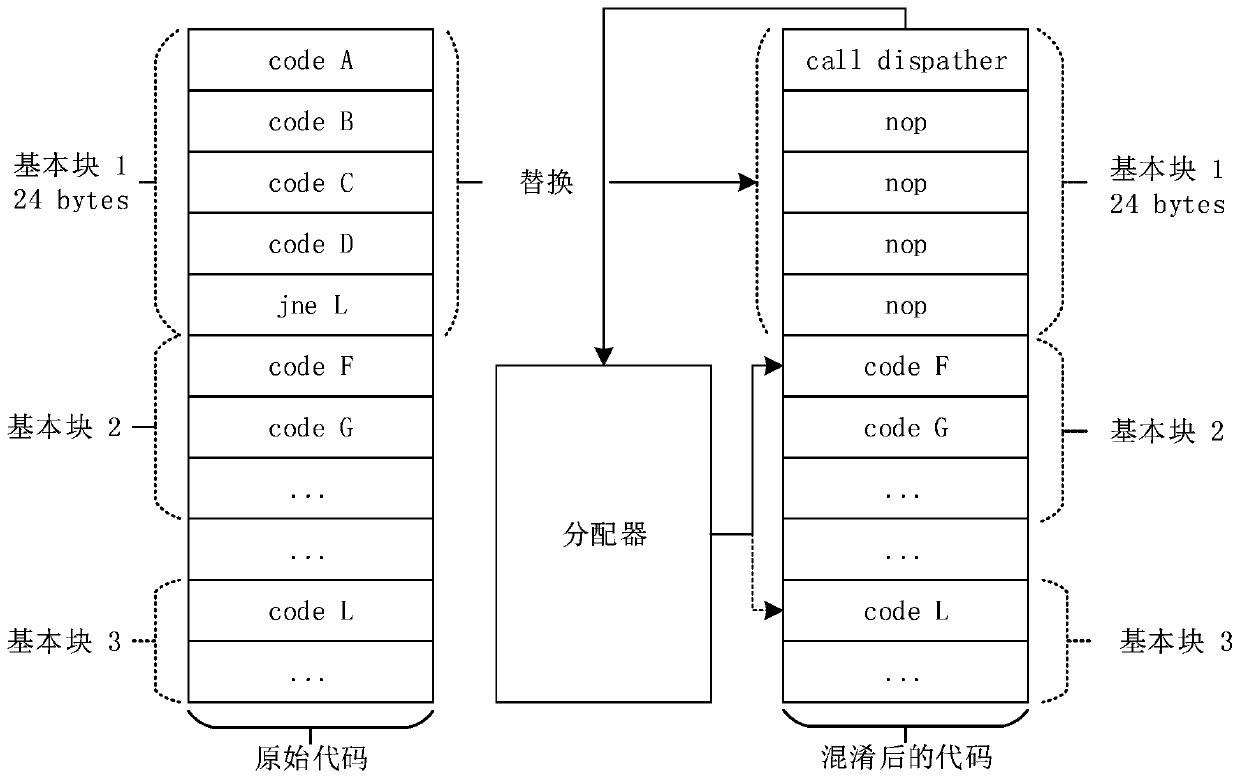
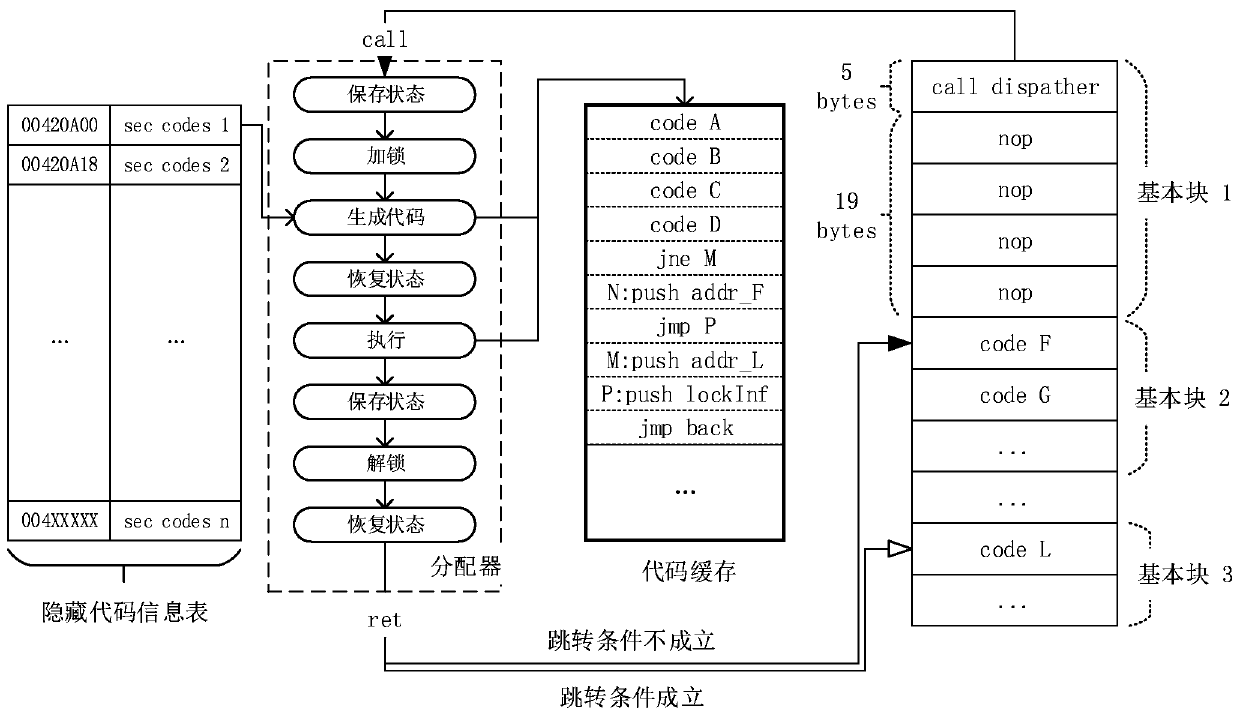
The invention discloses a binary software protection method adopting dynamic fine-grained code hiding and obfuscation technology, the steps of which are: S1: select a hidden target; select a code block to be hidden in a target program in units of basic blocks; S2: Hide the selected basic block; for each basic block to be hidden, replace the original piece of code with an allocator function call, and fill the remaining position with other confusing instructions; S3: repackage the code; create a new code section to save All additional logic and data. The invention has the advantages of wide application range, light weight, expandability, high security and the like.
Owner:NAT UNIV OF DEFENSE TECH
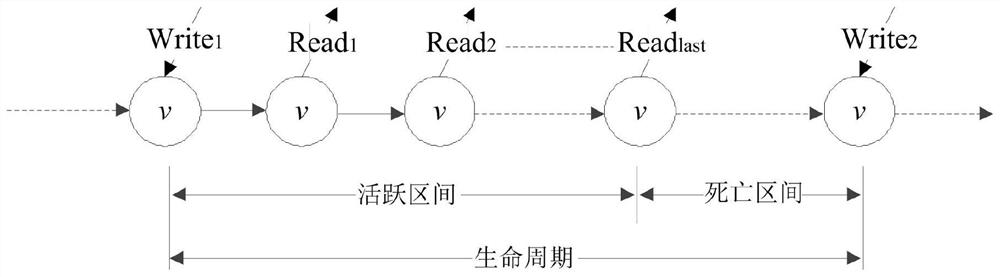
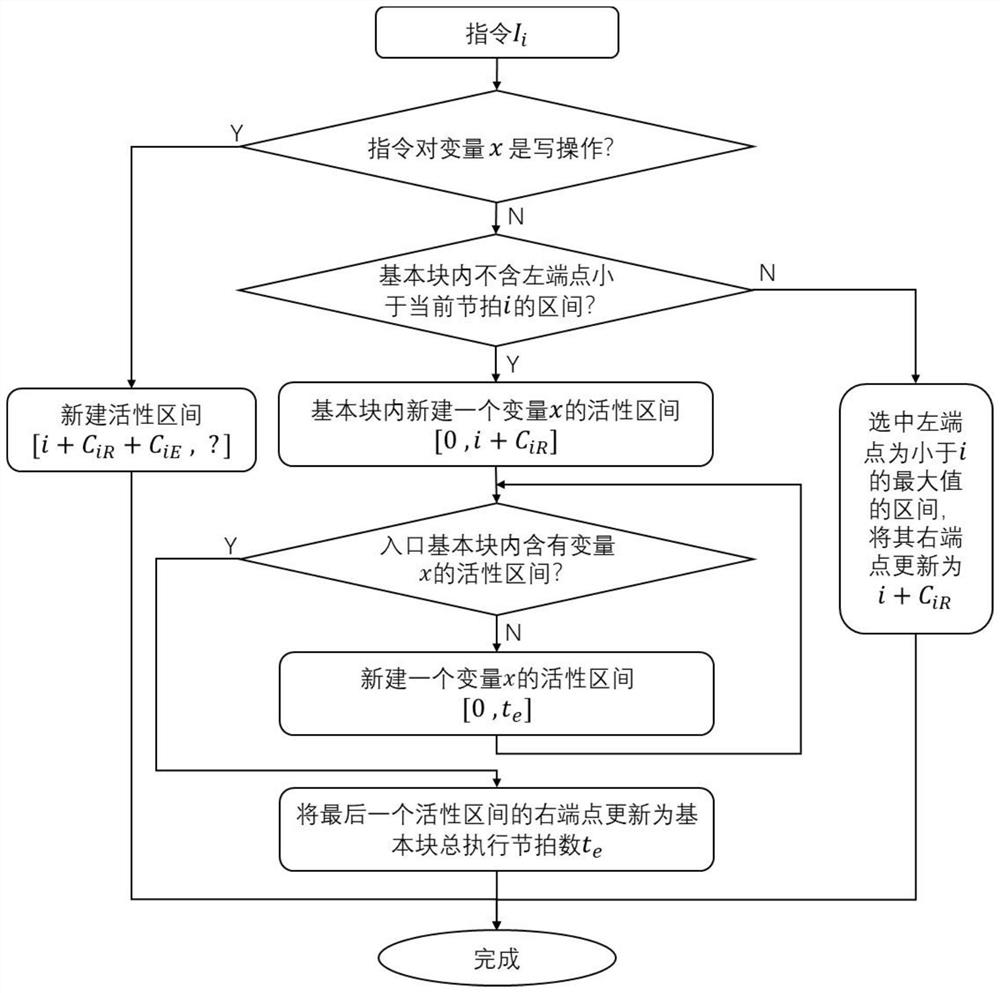
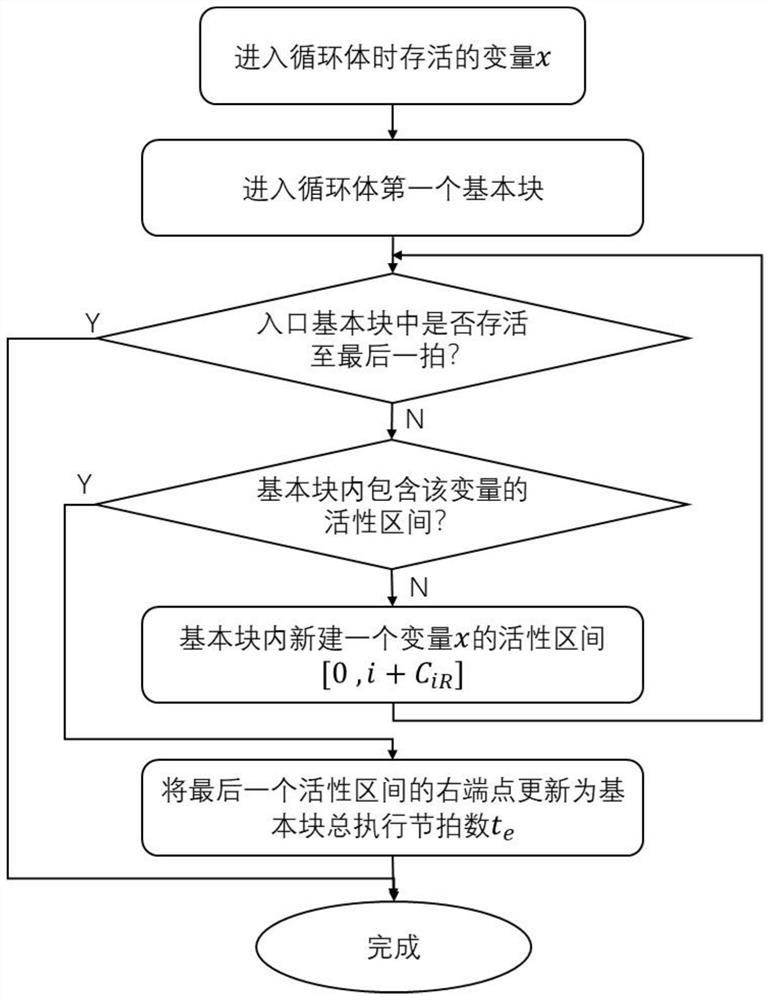
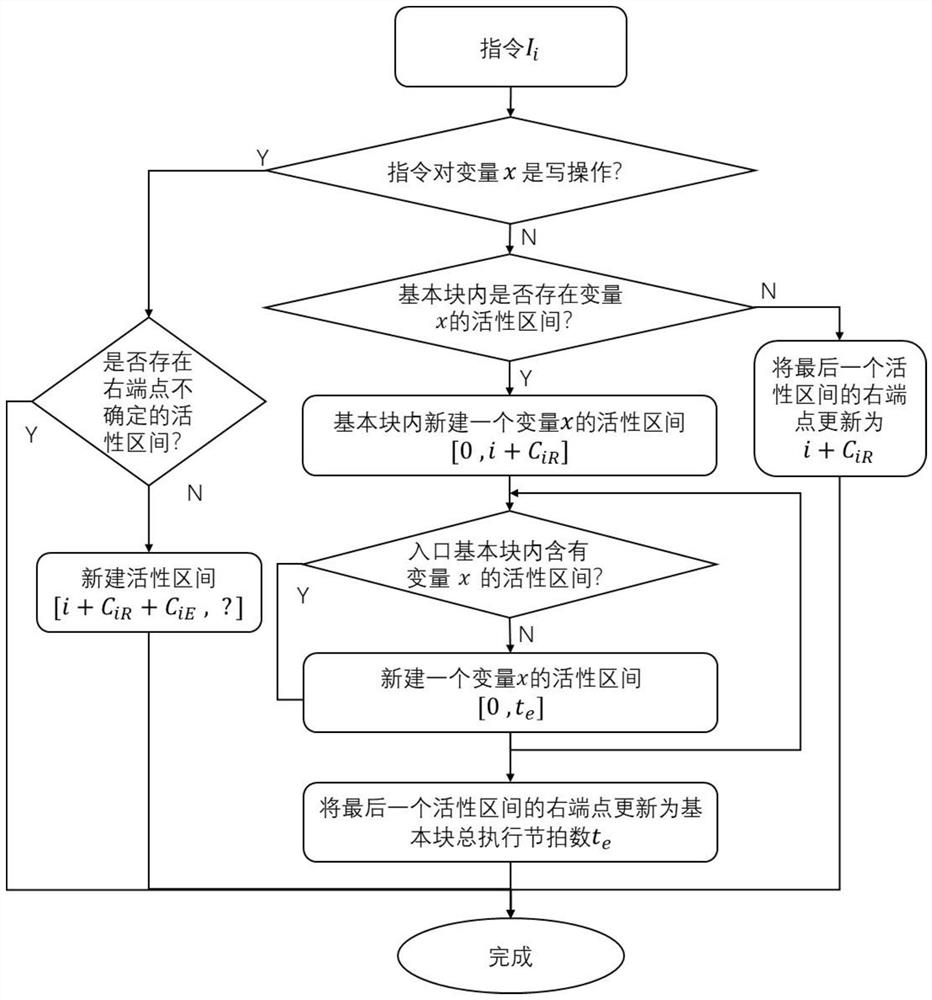
Activity analysis method and system for fine-grained variables in multi-beat instruction
The invention discloses an activity analysis method and system for fine-grained variables in a multi-beat instruction. The operation modes and effective time of a current instruction and a last operation instruction on variables are compared when each instruction is analyzed under the background of multiple beats of an instruction execution cycle, variable activity is not simply reserved according to 'read after write' and 'read after read', an active interval is newly created in each write operation, an active interval with the interval left end point being smaller than the maximum value of the current beat needs to be found in each read operation, and the interval right end point is updated to be the beat with the current instruction read operation effective. Activity analysis of the fine-grained variables in the multi-beat instruction can be achieved, on the premise that the execution beat and the instruction arrangement sequence of the instruction are determined, activity intervals of all the variables are obtained by traversing all the basic blocks and all the instructions, the period of the variables occupying the register can be obtained through activity analysis, and a judgment basis is provided for distribution and release of registers in the compiler.
Owner:NAT UNIV OF DEFENSE TECH
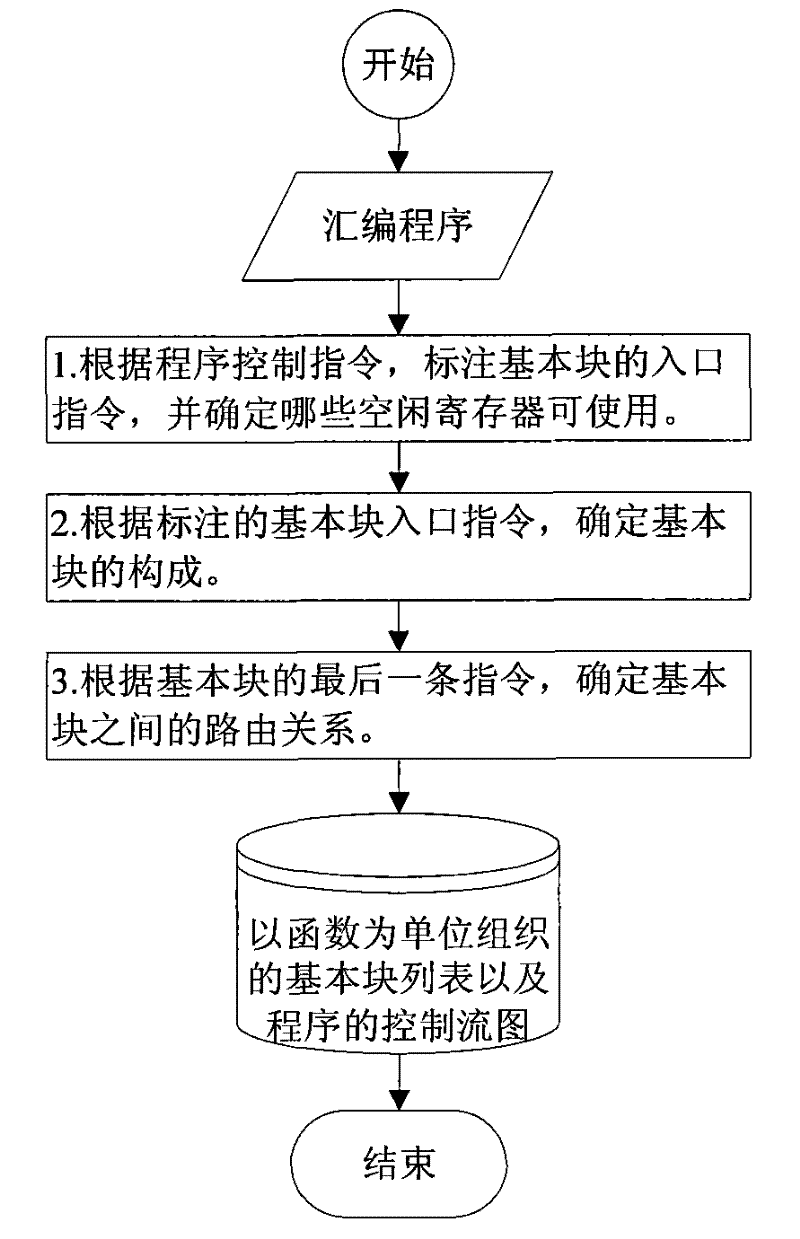
Method for detecting error of program control flow
InactiveCN101763291BDoes not require multithreading supportImprove detection rateError detection/correctionProgram controlControl flowSimulation
The invention discloses a method for detecting the error of a program control flow and intends to overcome the difficulties in increasing the detection rate of the errors of the control flow by the conventional method and solve the difficult problem with the detection of the control flow inside basic blocks and among processes. The method comprises the following steps according to the technical scheme of the invention: firstly, identifying basic blocks and confirming the routing relation among the basic blocks; then, confirming the maximum required number of detection commands of the internalcontrol flow of each basic block according to the requirements of the internal control flow and the constitutive characteristics of the basic blocks; designing the labels for the basic blocks on thatbasis, and distributing the unique static label to each basic block; then, inserting the detection commands into the head part, inner part and tail part of each basic block in the program respectively, re-assembling and re-linking the assembler of the inserted detection commands of the control flow, and generating an executable program for achieving the detection of the error of the control flow.
Owner:NAT UNIV OF DEFENSE TECH
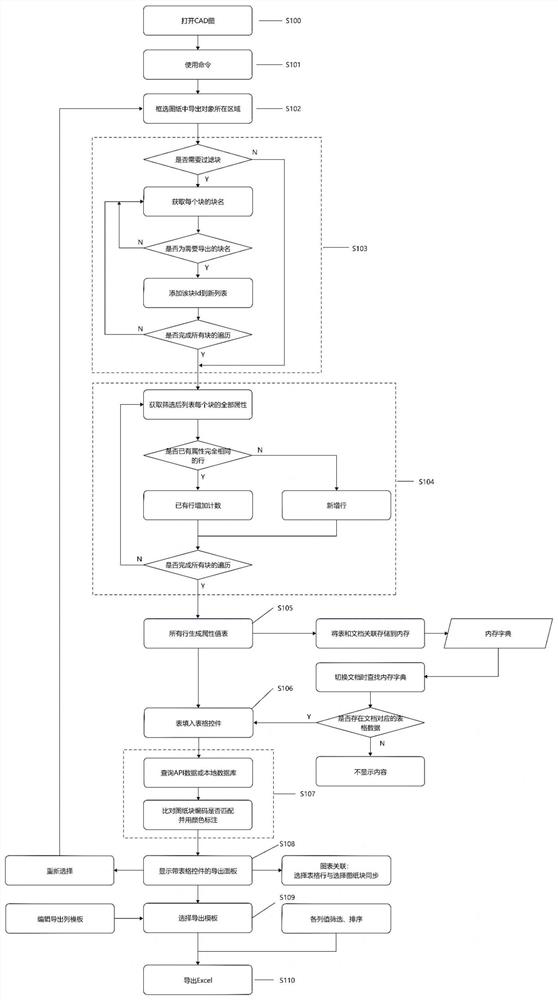
AutoCAD-based block attribute identification and export method
PendingCN114386129AImmediate detection of errors and omissionsFound mistakesGeometric CADConfiguration CADWorkloadData mining
The invention discloses a block attribute identification and export method based on AutoCAD. The method is characterized by specifically comprising the following steps: opening a drawing and selecting a preset area or totally selecting the preset area; judging whether a filtering block is needed and executing corresponding operation; traversing and acquiring attribute values of the blocks, judging whether rows with the same attributes exist or not, and executing corresponding operation; generating a specific attribute value table according to a template defined by a user or a default template, and placing the specific attribute value table into a table control; comparing the block name and the code with the standard code of the corresponding block and marking; and displaying an export panel with a preview table, and selecting, exporting and storing the export panel as an Excel file. According to the method, the block attributes in the process flow diagram are directly output to Excel, so that the workload of process designers is reduced, and the overall speed of design work related to flow diagram drawing is increased. Manual errors are reduced, and the problems caused by the manual errors can be avoided by means of the accuracy and the fatigue-free property of the working of the computer. According to the method, the process design accuracy is greatly improved.
Owner:福建凯壹信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com