A binary software protection method using dynamic fine-grained code hiding and obfuscation technology
A software protection, fine-grained technology, applied in program/content distribution protection, instrumentation, computing, etc., can solve problems such as difficult to hide program control flow, large plaintext window, etc., to reduce size and duration, high protection strength, Wide range of effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
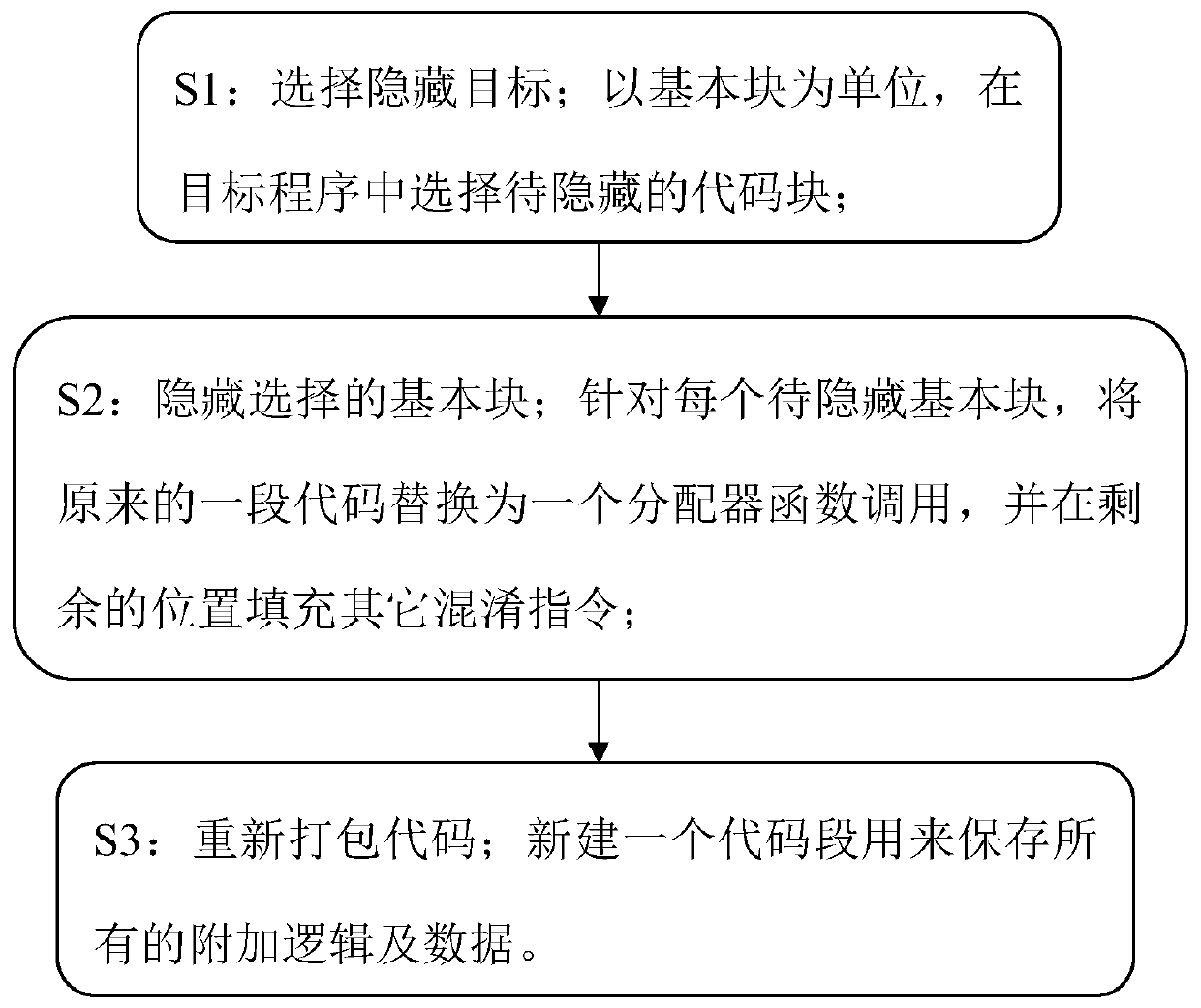
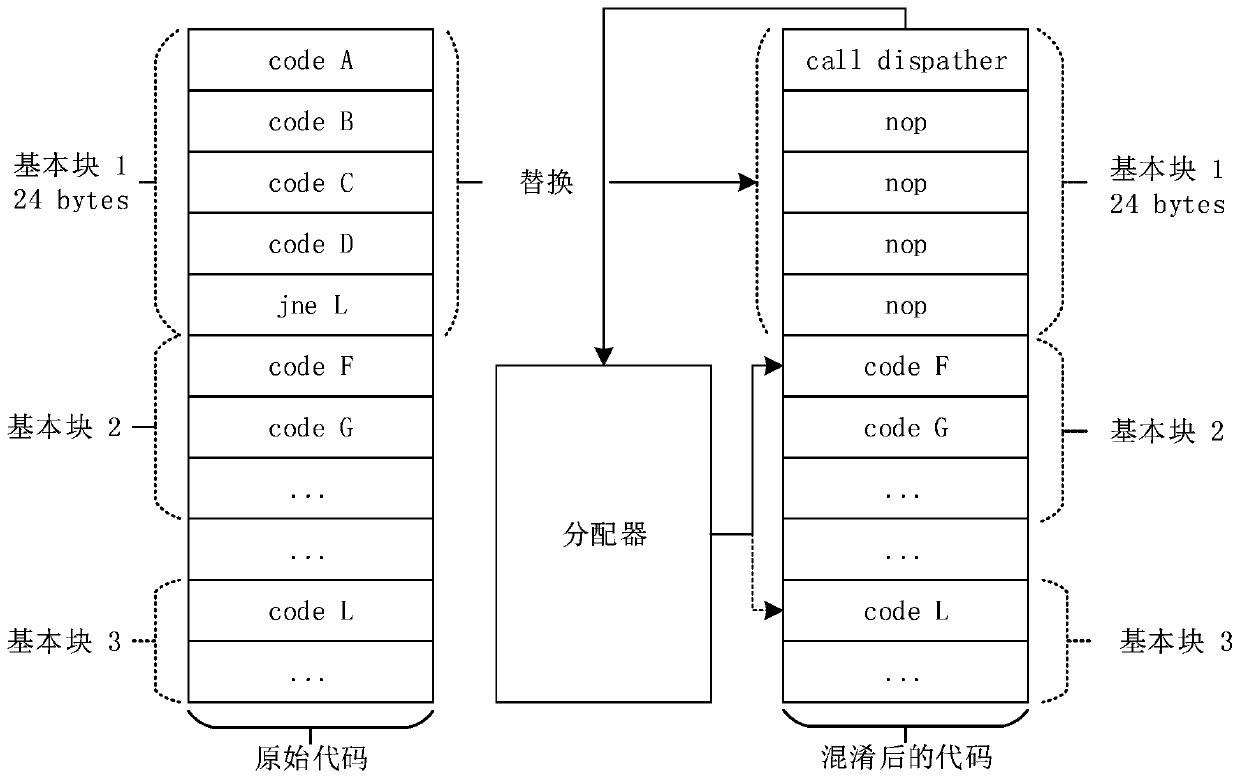
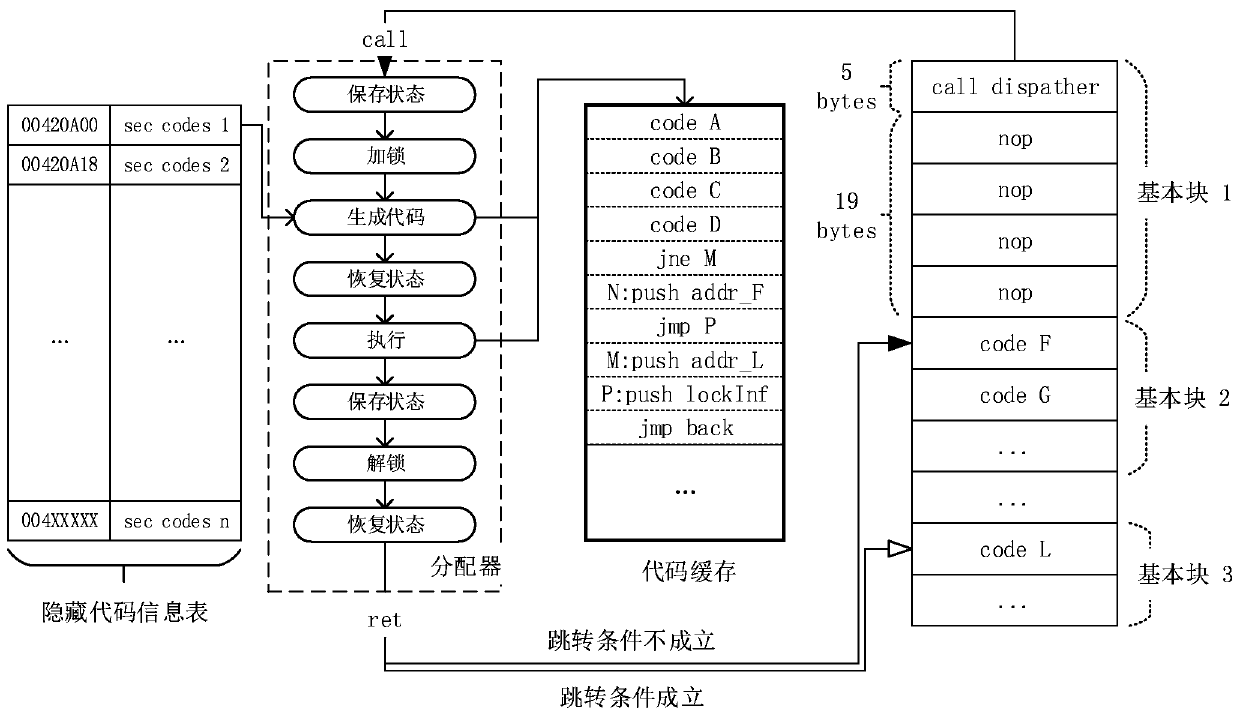
[0036] The invention is mainly used for binary software protection technology against software reverse analysis, that is, binary software anti-analysis technology. The binary software protection method (Dynamically Fine-grained Code Hiding and Obfuscation, referred to as dynFCHO) adopting dynamic fine-grained code hiding and obfuscation technology of the present invention achieves Purpose of concealment and protection. like figure 1 Shown, in specific application examples, the detailed steps of the present invention are:
[0037] S1: Select a hidden target;
[0038] In the unit of basic block, select the code block to be hidden in the target program.
[0039] The selection method is explained as follows:
[0040] Obfuscation of binary files is based on correct disassembly. DynFCHO uses basic blocks as the smallest unit for code h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com