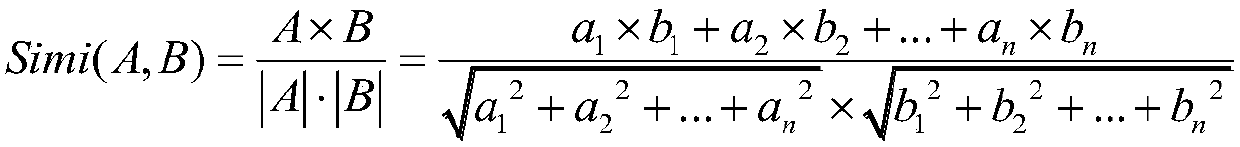Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
381results about How to "Reduce performance overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
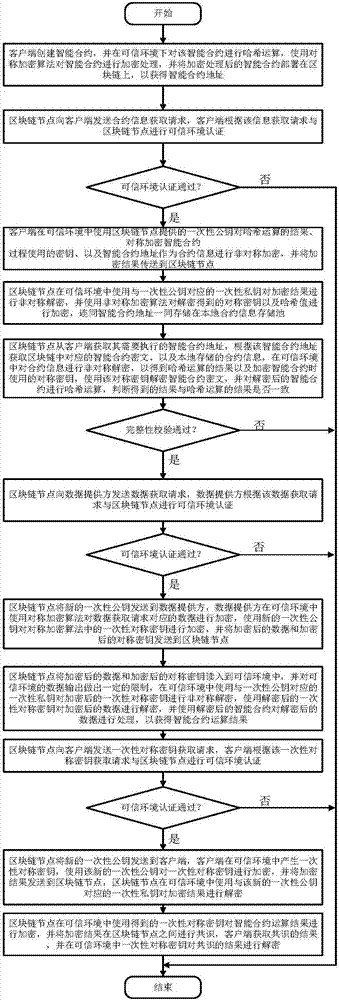
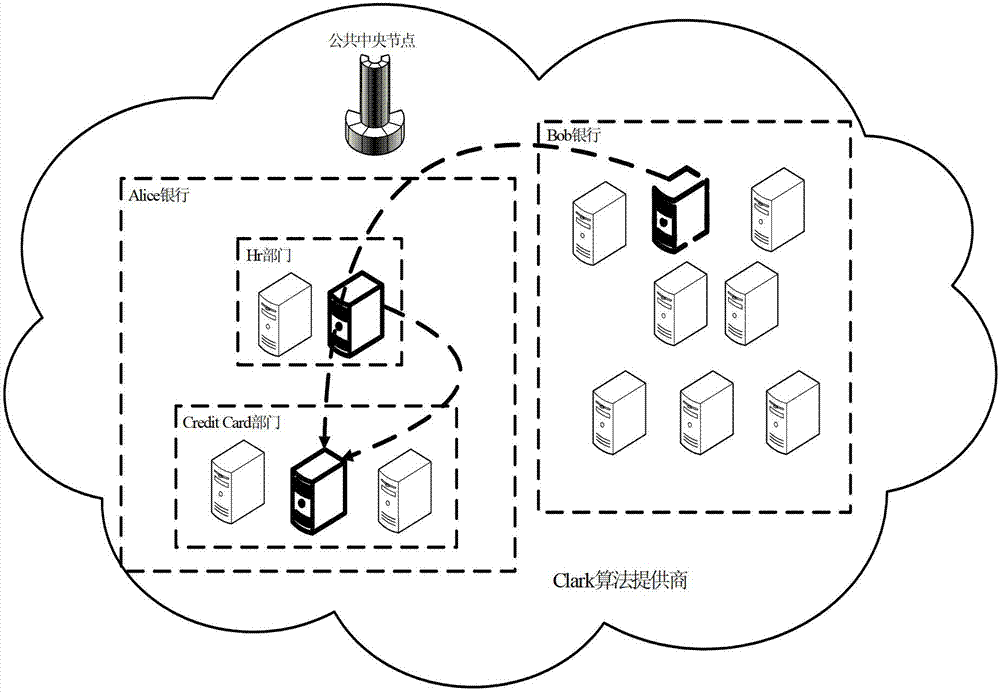
Smart contract protection method and system based on trusted environment
InactiveCN107342858ASolve the problem of smart contract versionSolve the problem of damage to rights and interestsKey distribution for secure communicationUser identity/authority verificationInformation processingInformation transmission
The invention discloses a smart contract protection system based on a trusted environment, including a client, block chain nodes, a data provider, a trusted environment, a non-trusted environment, a smart contract information processing module (A), a block chain node information transmission module (B) (such as a node interaction interface in the Ethereum), an input data transmission module (C), a smart contract execution module (D), a local contract information storage pool (E) and a block chain smart contract storage pool (F). The client is in communication connection with the block chain nodes. The data provider is in communication connection with the block chain nodes. The block chain nodes are in communication connection with one another. The technical problem that the copyright of smart contracts cannot be protected and the rights and interests of smart contract users are damaged due to the fact that the information of smart contracts may easily leak in the existing smart contract system and the technical problem that data may be stolen due to data leakage are solved.
Owner:武汉凤链科技有限公司
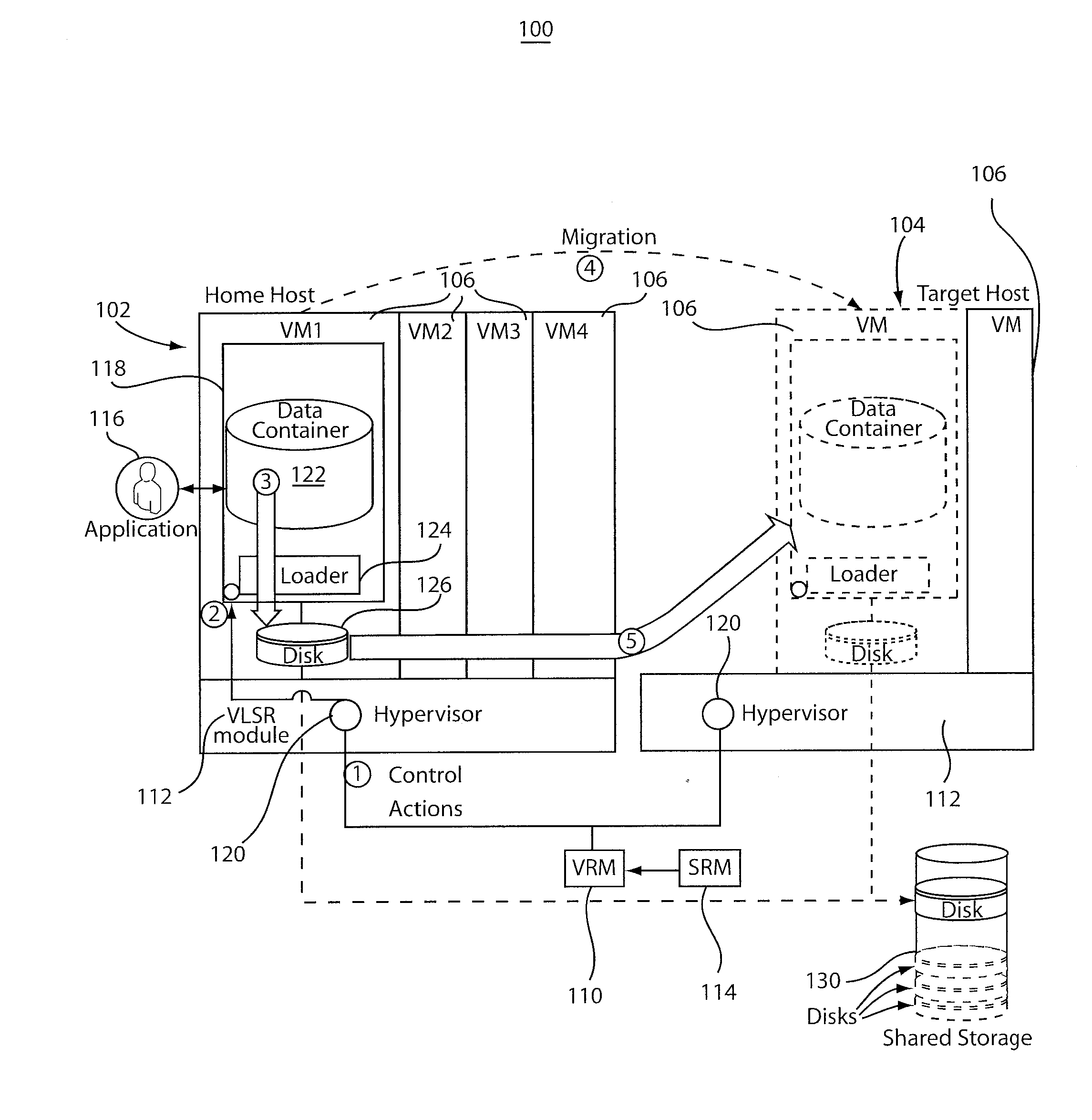
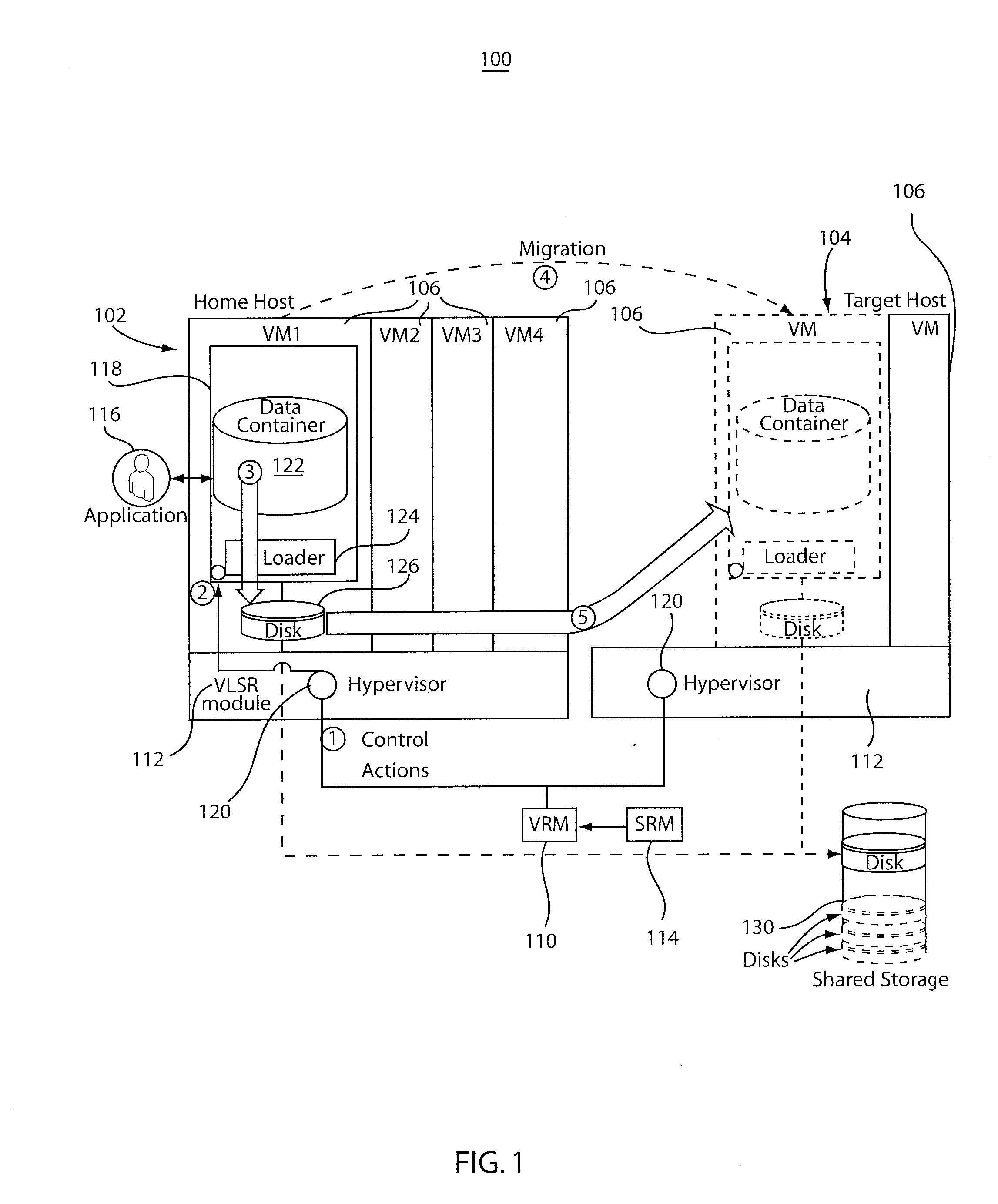
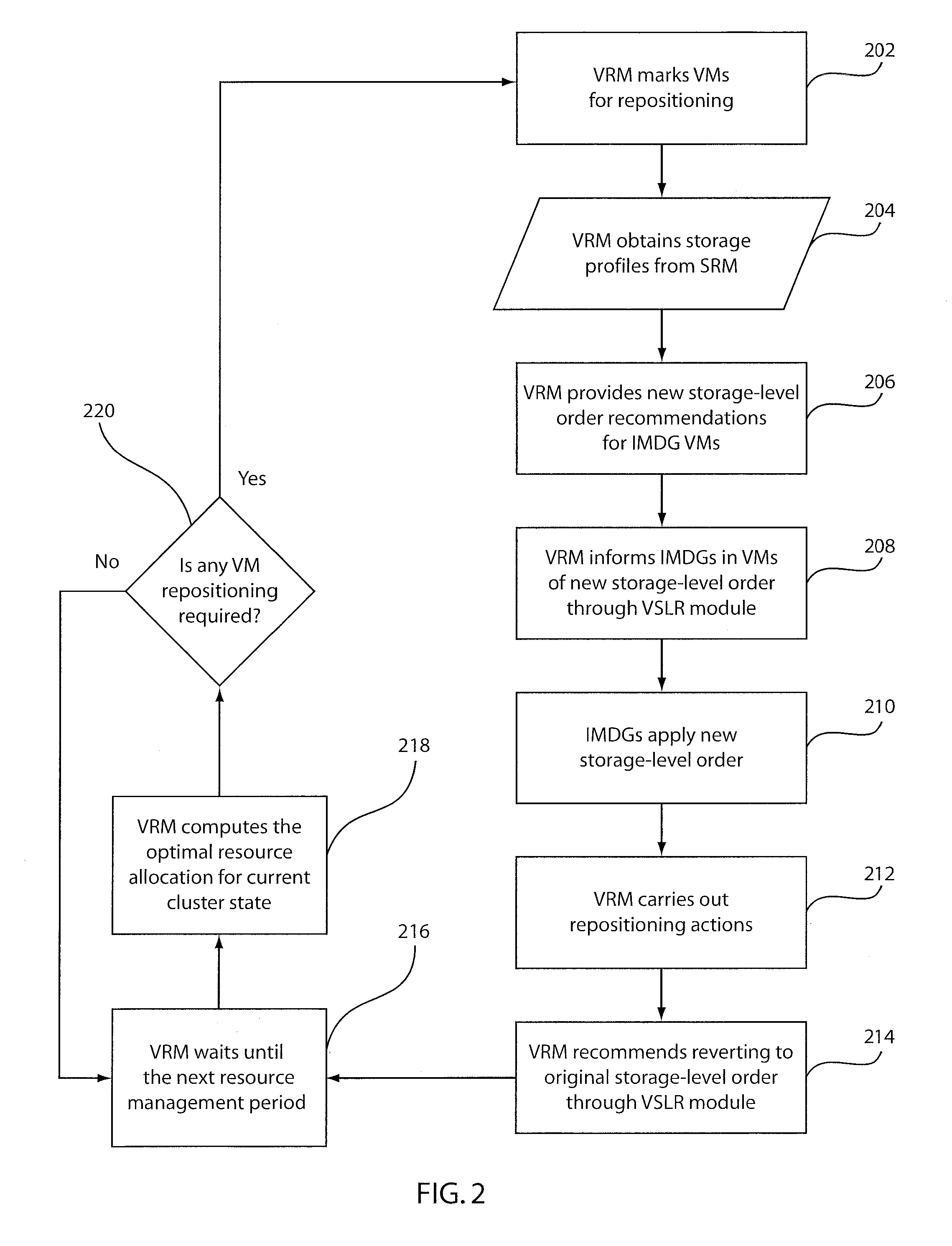
Virtualization and dynamic resource allocation aware storage level reordering
InactiveUS20110283277A1Reduce performance overheadReduce stepsMemory architecture accessing/allocationResource allocationVirtualizationLevel order
A system and method for reordering storage levels in a virtualized environment includes identifying a virtual machine (VM) to be transitioned and determining a new storage level order for the VM. The new storage level order reduces a VM live state during a transition, and accounts for hierarchical shared storage memory and criteria imposed by an application to reduce recovery operations after dynamic resource allocation actions. The new storage level order recommendation is propagated to VMs. The new storage level order applied in the VMs. A different storage-level order is recommended after the transition.
Owner:IBM CORP
Method and apparatus for big data cloud storage resource management
InactiveUS20160357443A1Improve efficiencyQuick and accurate predictionInput/output to record carriersError detection/correctionVirtualizationExponentially weighted moving average
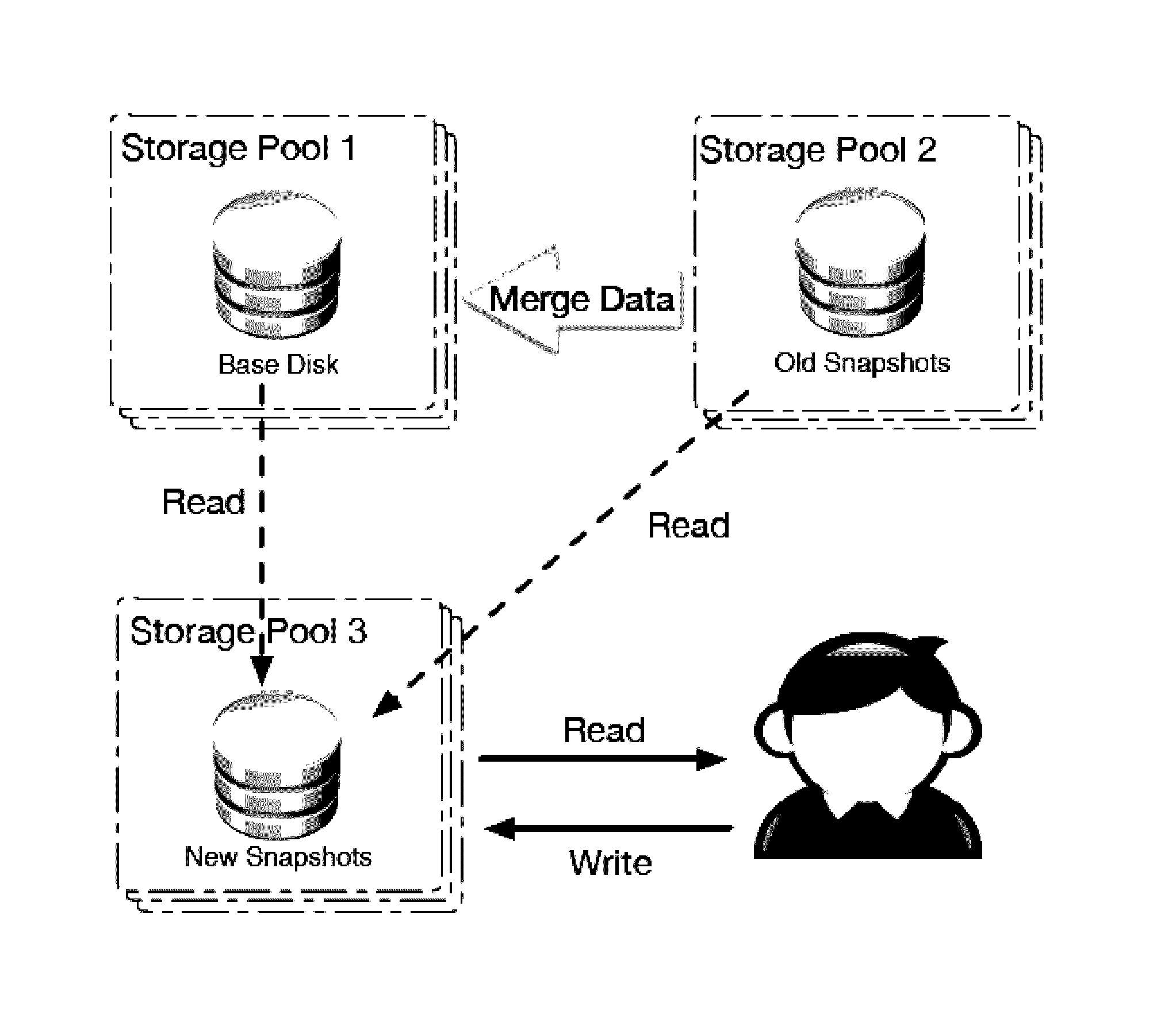
A system and method for storage resource management that improves the efficiency of big data cloud storage management using copy-on-write / read snapshots to redirect the I / O requests without moving the virtual disk is disclosed herein. The system includes storage pools, a virtualized server, and a centralized data center management server. The virtualized server includes a base disk and a virtualized disk having a copy-on-write and a copy-on-read snapshot process responsive to an I / O request that merges a previous snapshot stored on a first one of the plurality storage pools with the base disk stored on a second one of the plurality of storage pools, while it fetches a new snapshot to be stored on a third one of the plurality of storage pools from the previous snapshot or the base virtual disk. The system includes a performance model, employing an exponentially weighted moving average with an adjustable sliding window.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
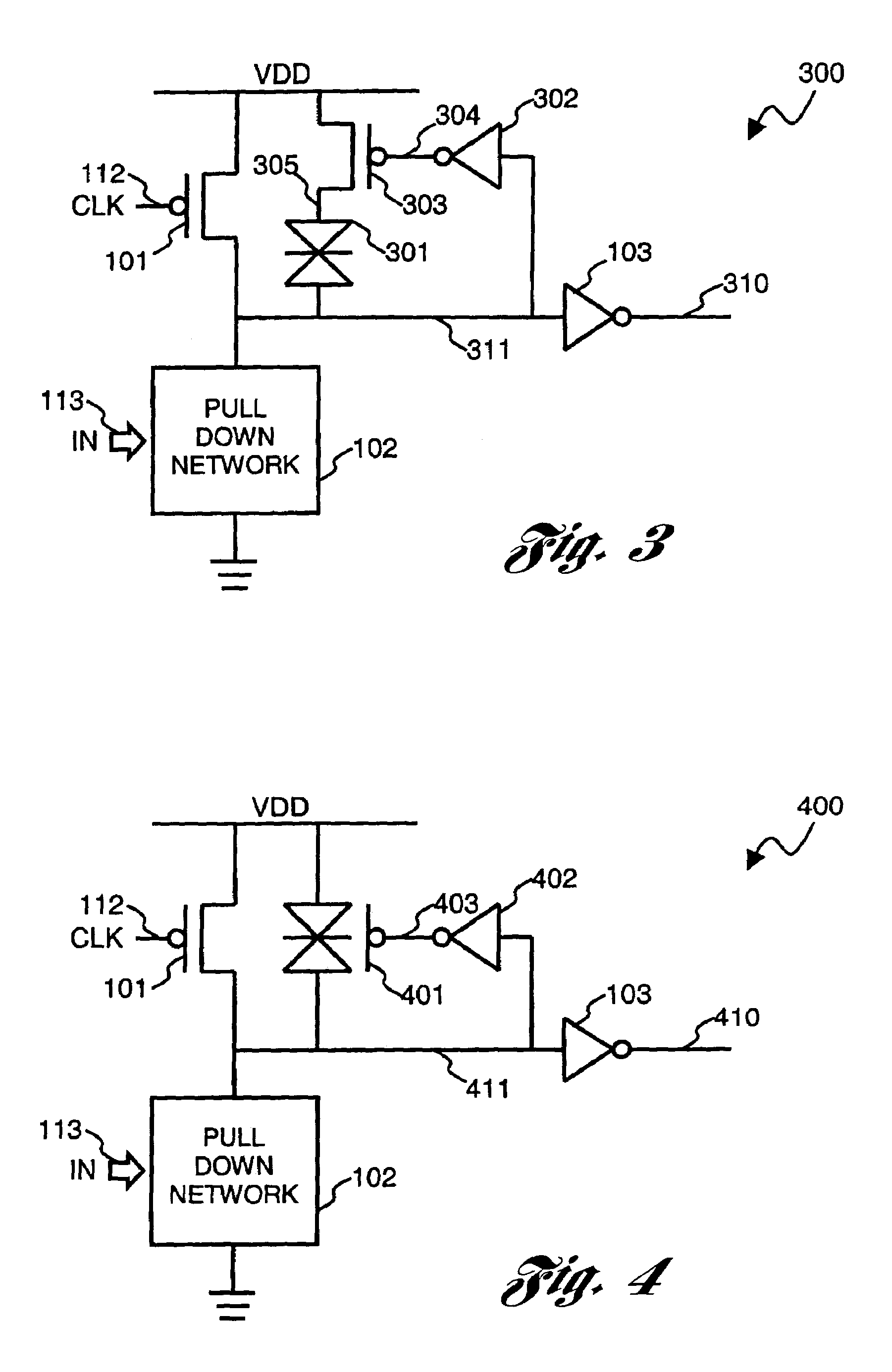
Dynamic circuits having improved noise tolerance and method for designing same
InactiveUS7088143B2Improved dynamic circuitsImprove methodLogic circuits characterised by logic functionElectrical resistance and conductanceEngineering
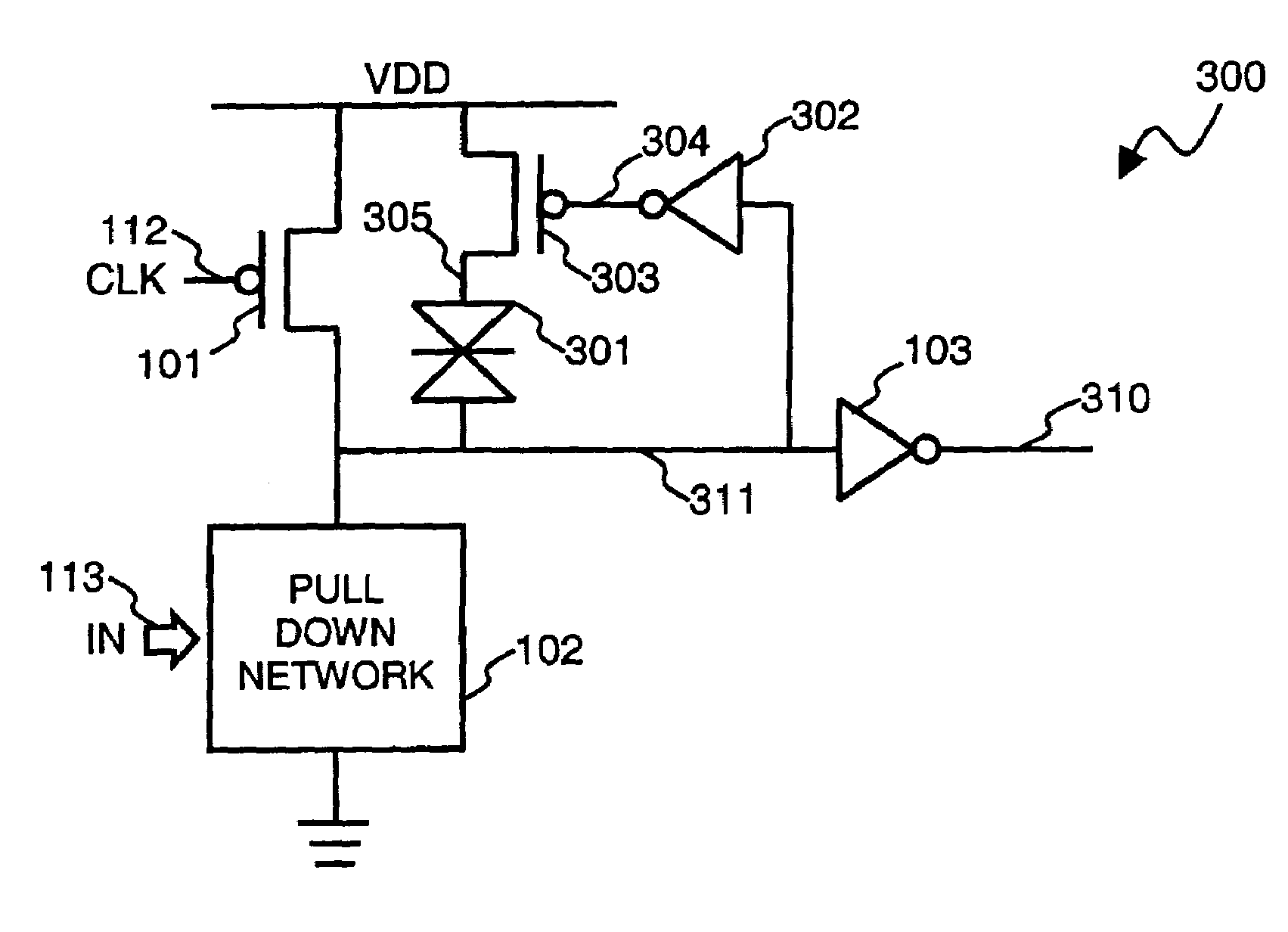
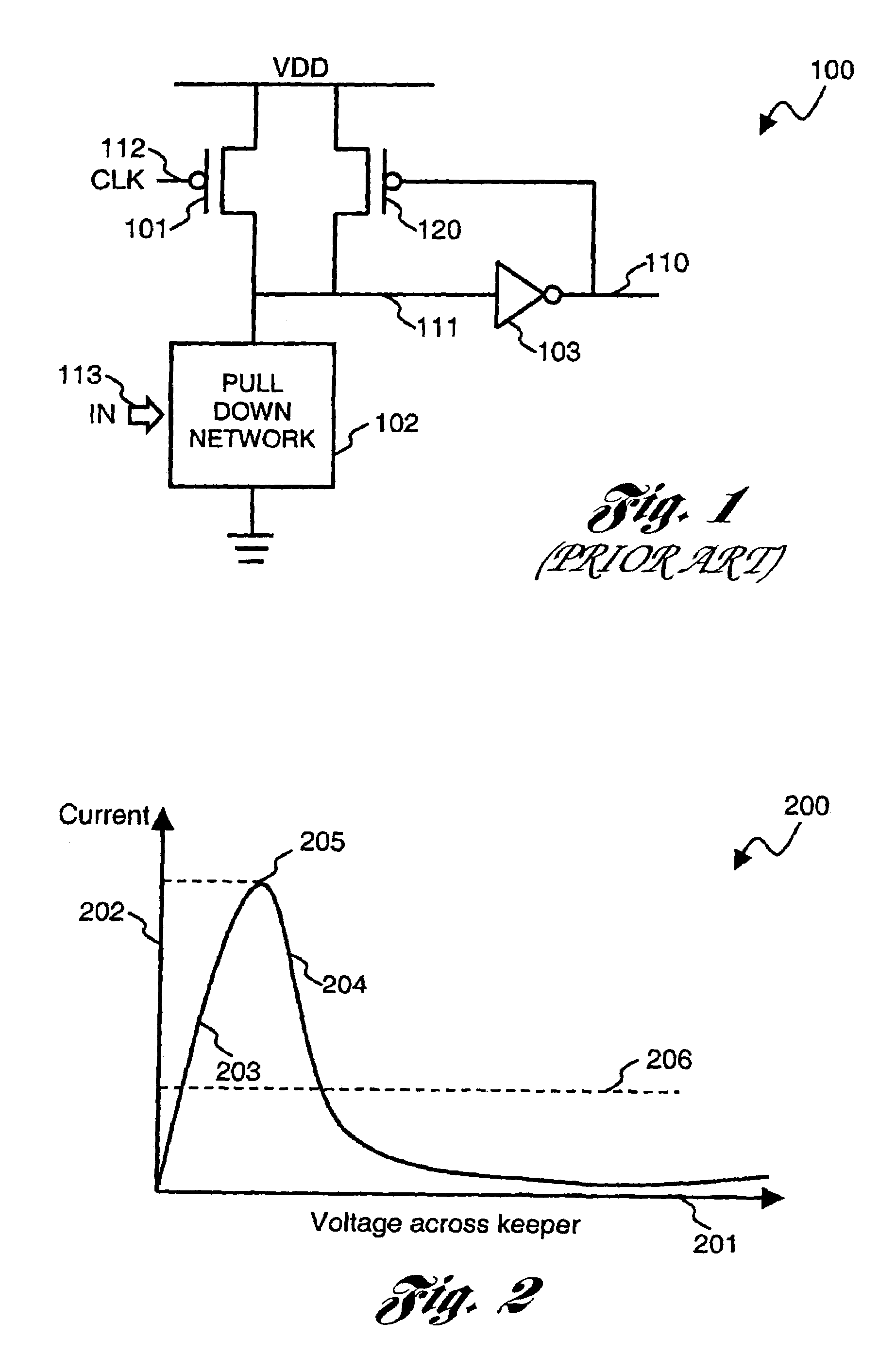
A number of different dynamic circuits having improved noise tolerance and a method for designing same are provided. The circuits include a power supply node and a precharge node. Keeper circuitry is connected to the nodes and has a current-voltage characteristic that exhibits a negative differential resistance property to improve noise tolerance of the circuits.
Owner:RGT UNIV OF MICHIGAN
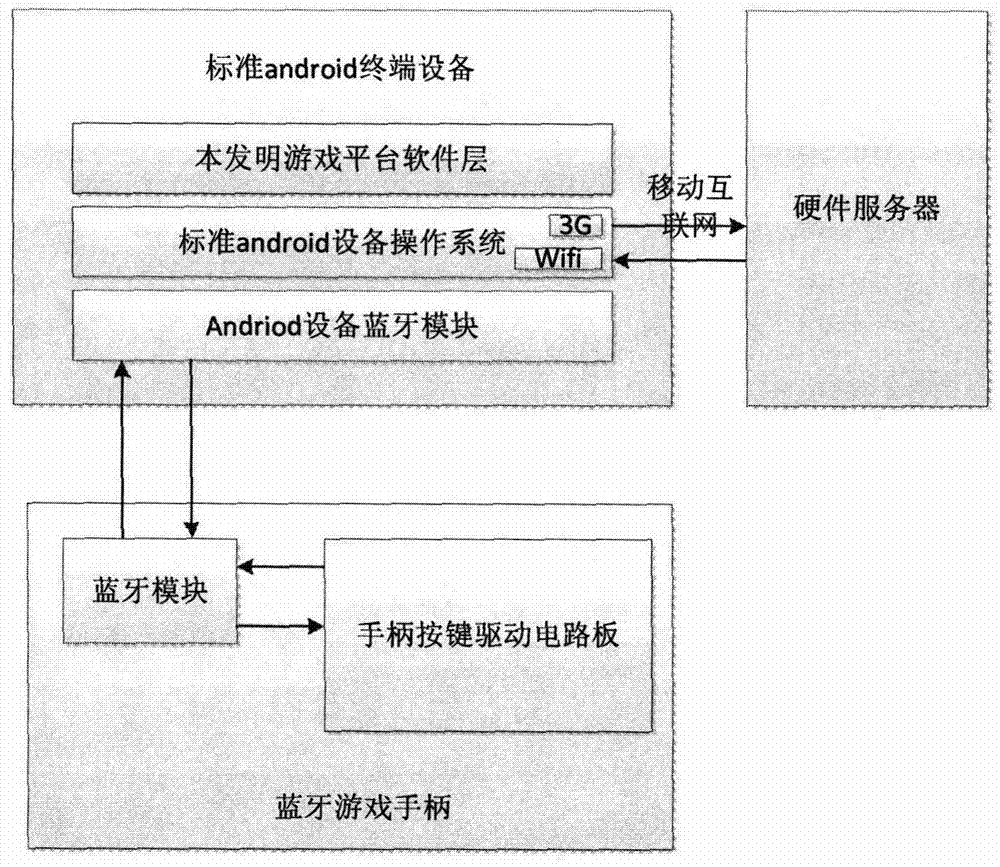
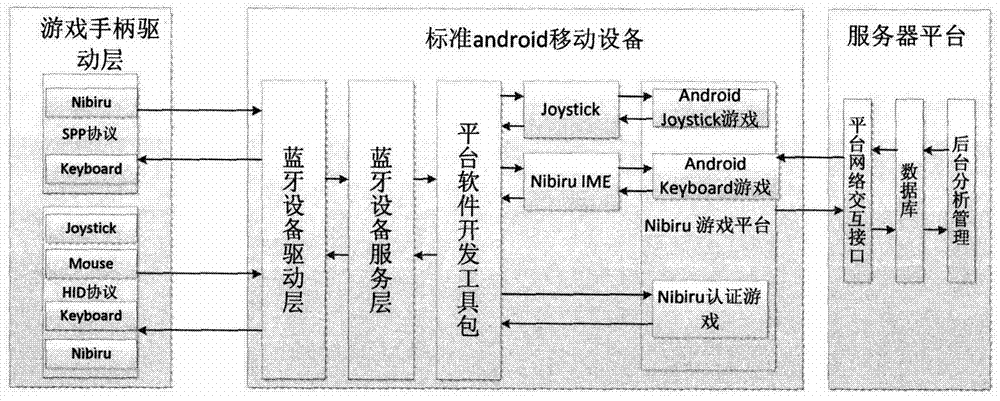
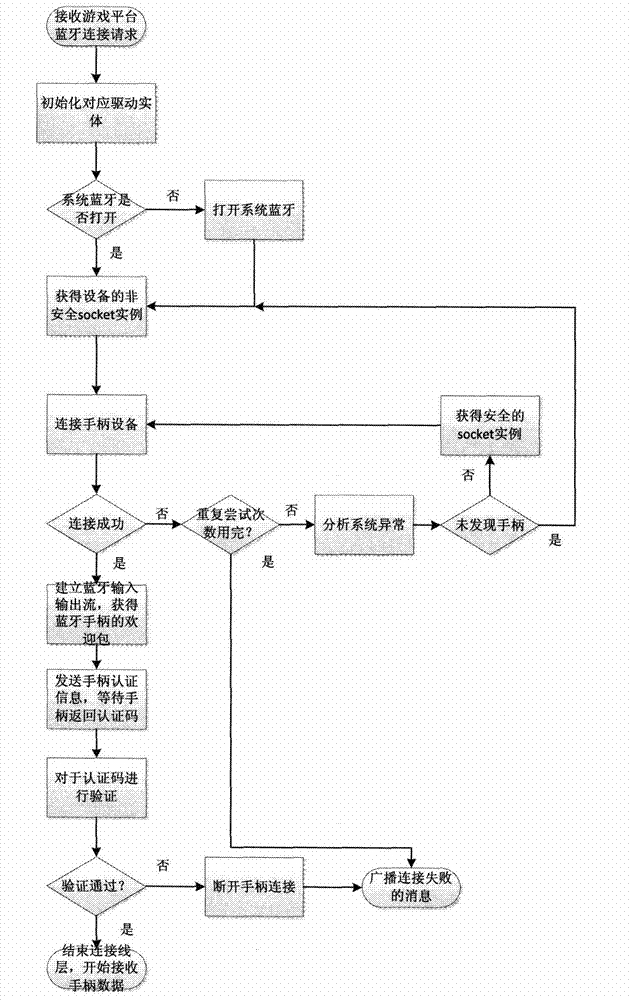
Android device gas platform system based on Bluetooth handle and implementation method of Android device gas platform system
ActiveCN103316472AReduce performance overheadReduce dependenceVideo gamesSpecific program execution arrangementsThe InternetSoftware engineering
The invention discloses an Android device gas platform system based on a Bluetooth handle and an implementation method of the Android device gas platform system. The interactive protocols of different Bluetooth handles on the market are unified, so that handles in different modes on the market can uniformly and conveniently have an access to a game platform and use the server technology, and the game platform is connected to a game content server through a network and can provide rich game resources so as to improve the user experience and the value of games. The game platform disclosed by the invention can be mounted on almost all Android devices so as to enable a common Android device mounted with the Android device gas platform system to become a game machine controlled by the handle in the Internet era.
Owner:NANJING RUIYUE INFORMATION TECH
Method for System Call Interception in User Space
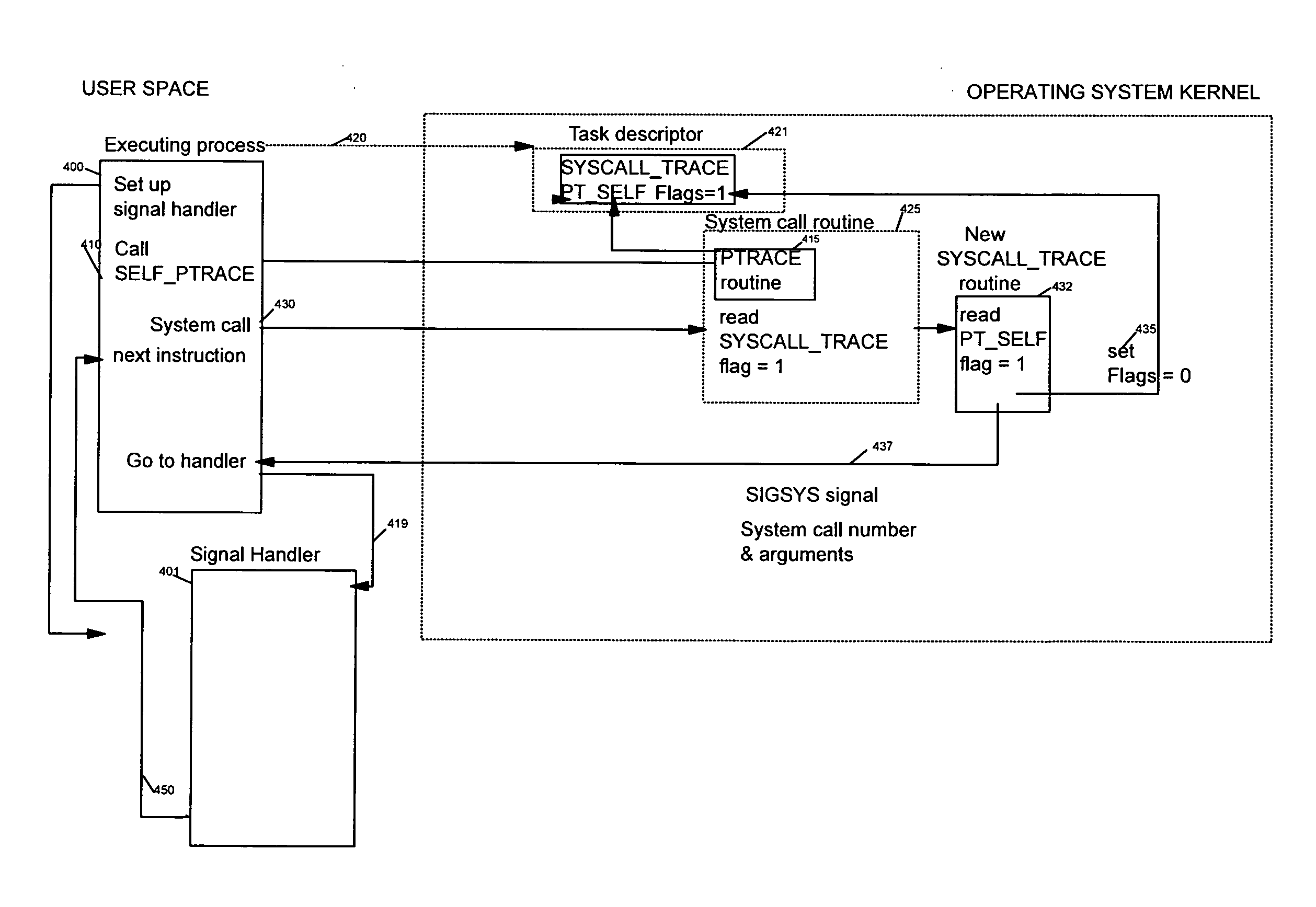
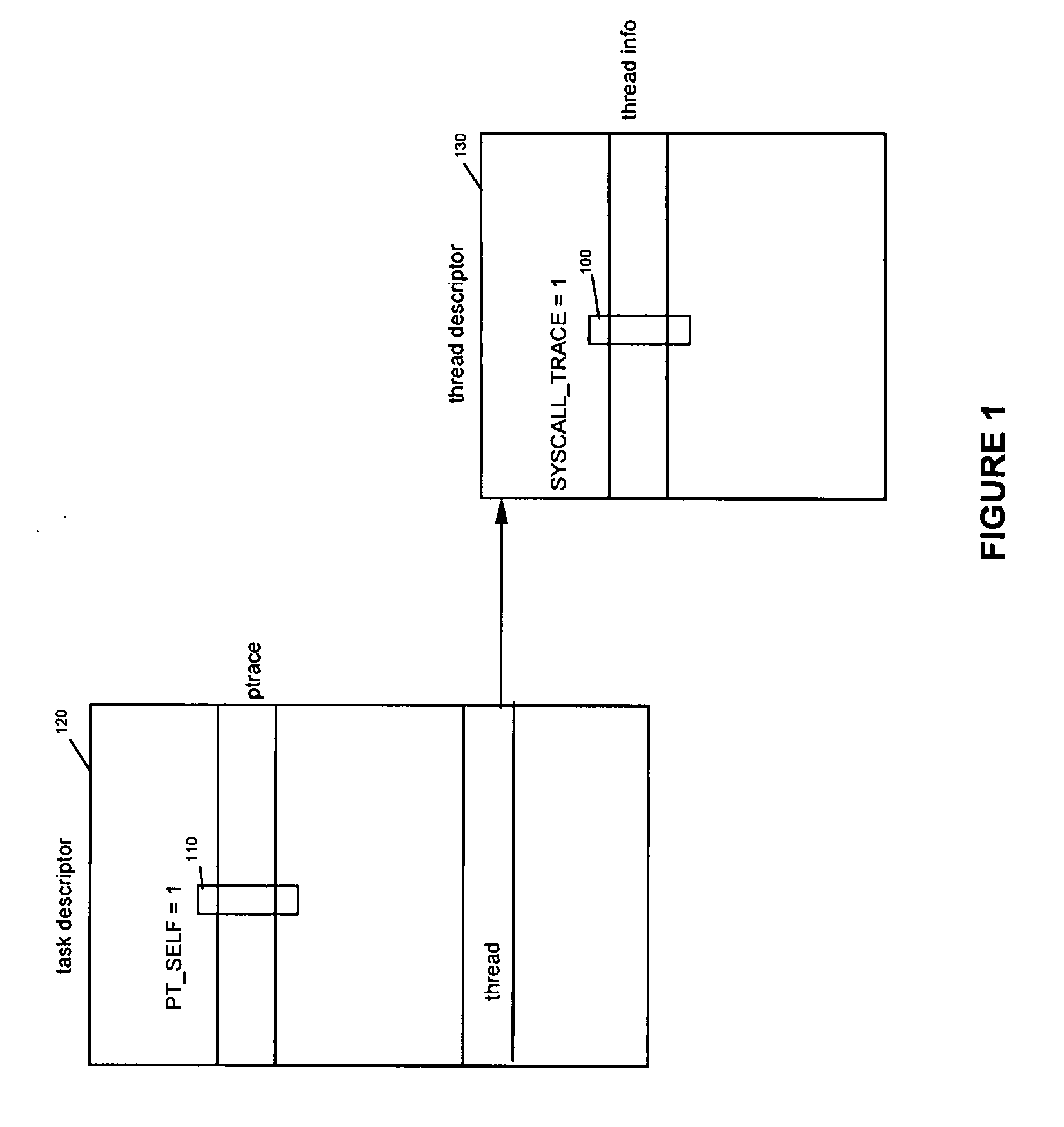
InactiveUS20080250400A1Raise the level of performanceReduce performanceSpecific program execution arrangementsMemory systemsSystem callSignal processing
A method, and system for intercepting a system call performed by a process and for executing processing in relation with the intercepted system call from user space. The method comprises a first step for setting up, in the executing process, a signal handler performing processing in relation with an interception of a system call in the executing process upon reception of a specific signal. The executing process performs a ptrace system call with a new request, the self ptrace, which sets, in the task descriptor of the executing process, the system trace flag corresponding to the existing system trace ptrace request and set a new flag, the pt_self flag. When a system call is performed in the executing process, a new system call trace is executed testing if the pt_self flag is set. If the pt_self flag is set a specific signal is sent to the executing process itself and the handler which has been set up is executed in user space.
Owner:IBM CORP
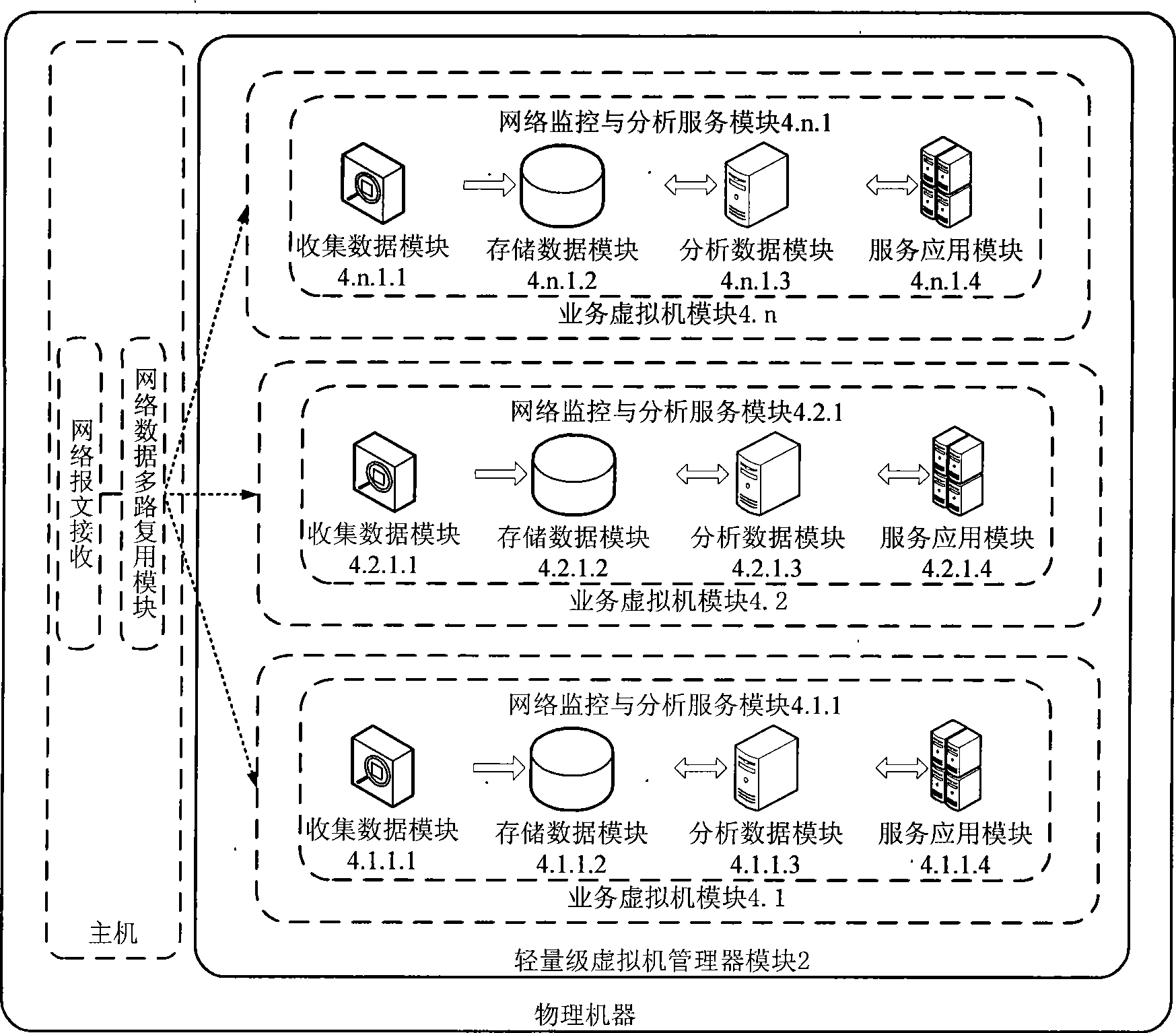
Network monitoring and analysis system under virtual machine circumstance
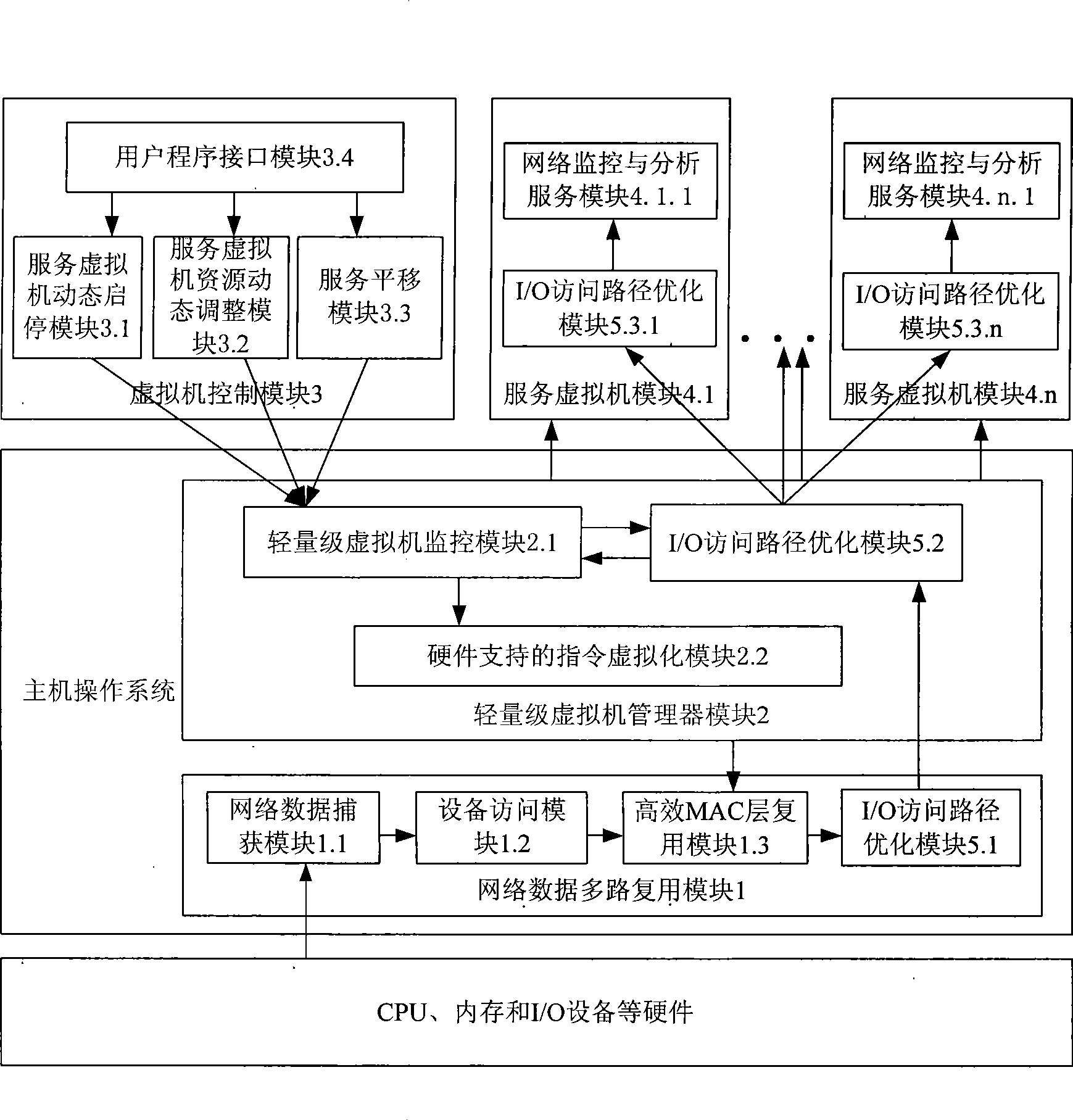
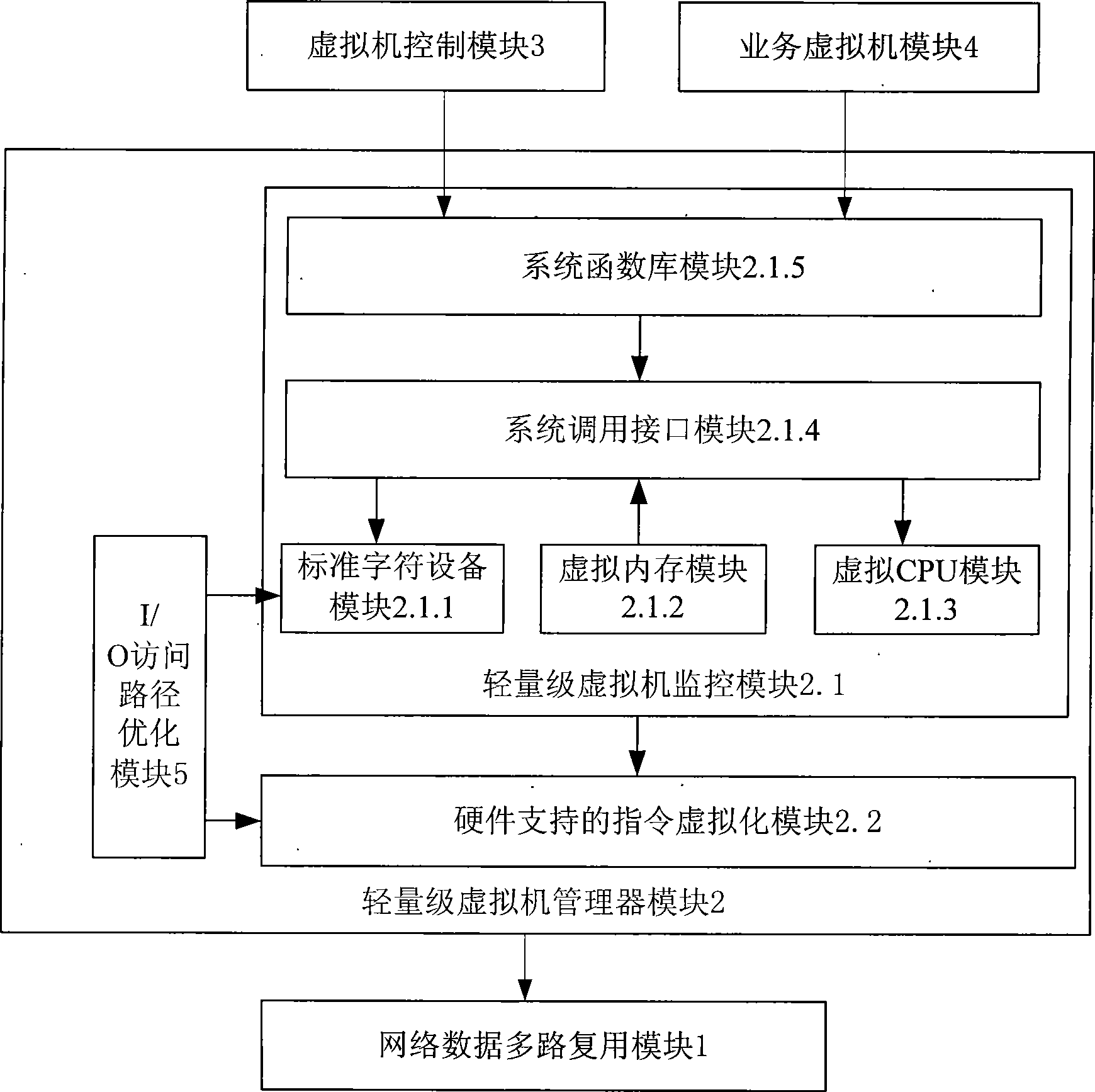
InactiveCN101436966AGood safety isolationTransparent sharingData switching networksSoftware simulation/interpretation/emulationMultiplexingOperational system
The invention discloses a network monitoring and analyzing system under an environment of a virtual machine. The system comprises a network data multiplexing module, a lightweight level virtual machine manager module, a virtual machine control module, a service virtual machine module and an I / O access path optimization module, wherein the network data multiplexing module and the lightweight level virtual machine manager module are positioned in an operating system of a host computer, the virtual machine control module and the service virtual machine module are positioned on the operating system of the host computer; and the I / O access path optimization module is positioned in the operating system of the host computer and the service virtual machine. The network monitoring and analyzing system is based on the virtual machine and realizes the network data multiplexing of a single physical machine to a plurality of network monitoring and analyzing service programs, thereby providing a plurality of monitoring and analyzing functions for the same network data in real time, realizing safe isolation between the service programs and dynamically adjusting and distributing resource to the service programs according to requirements. The network monitoring and analyzing system overcomes the problems that the prior network monitoring and analyzing system has resource competition, low safety, instability of the system, uneasy expansion and the like.
Owner:BEIHANG UNIV
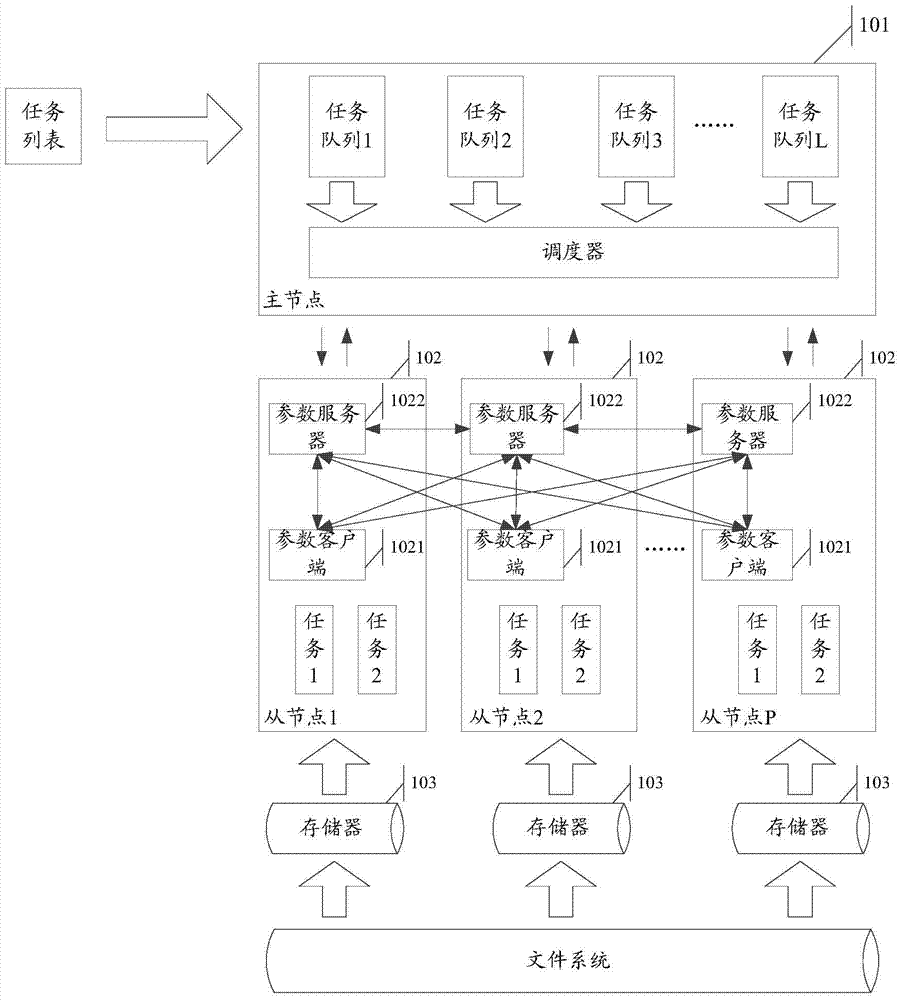
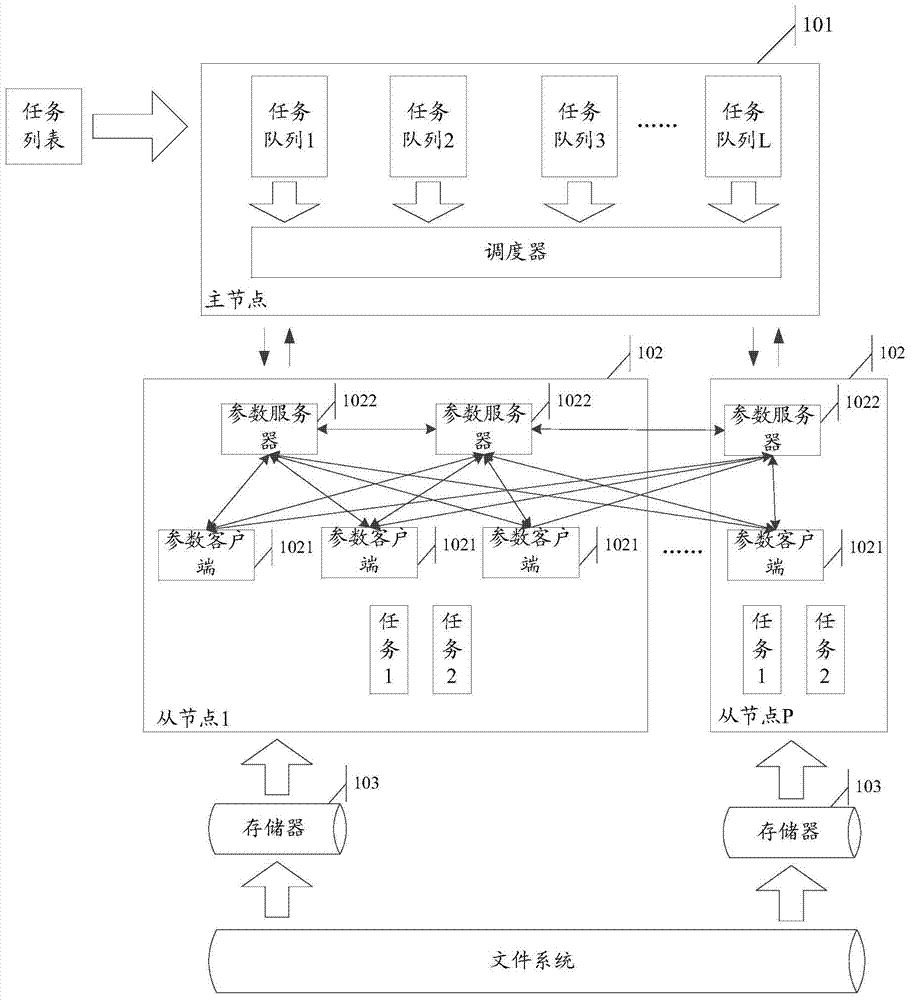
Method and equipment for model training in distributed system
ActiveCN107025205AReduce the burden onImprove training efficiencyDigital computer detailsProgram controlClient-sideDistributed computing
A method and equipment for model training in a distributed system are used to relieve burdens of main nodes in model training. The method comprises the steps that a parameter server in a first servo node receives training results which are sent by a parameter client side in at least one servo node in the distributed system, wherein the first servo node is a random servo node in the distributed system, and a parameter client side of each servo node executes a training task corresponding to a sub-model stored in the parameter server of the servo node so as to obtain the training results; and the parameter server in the first servo node updates the stored sub-model according to the received training results.
Owner:HUAWEI TECH CO LTD
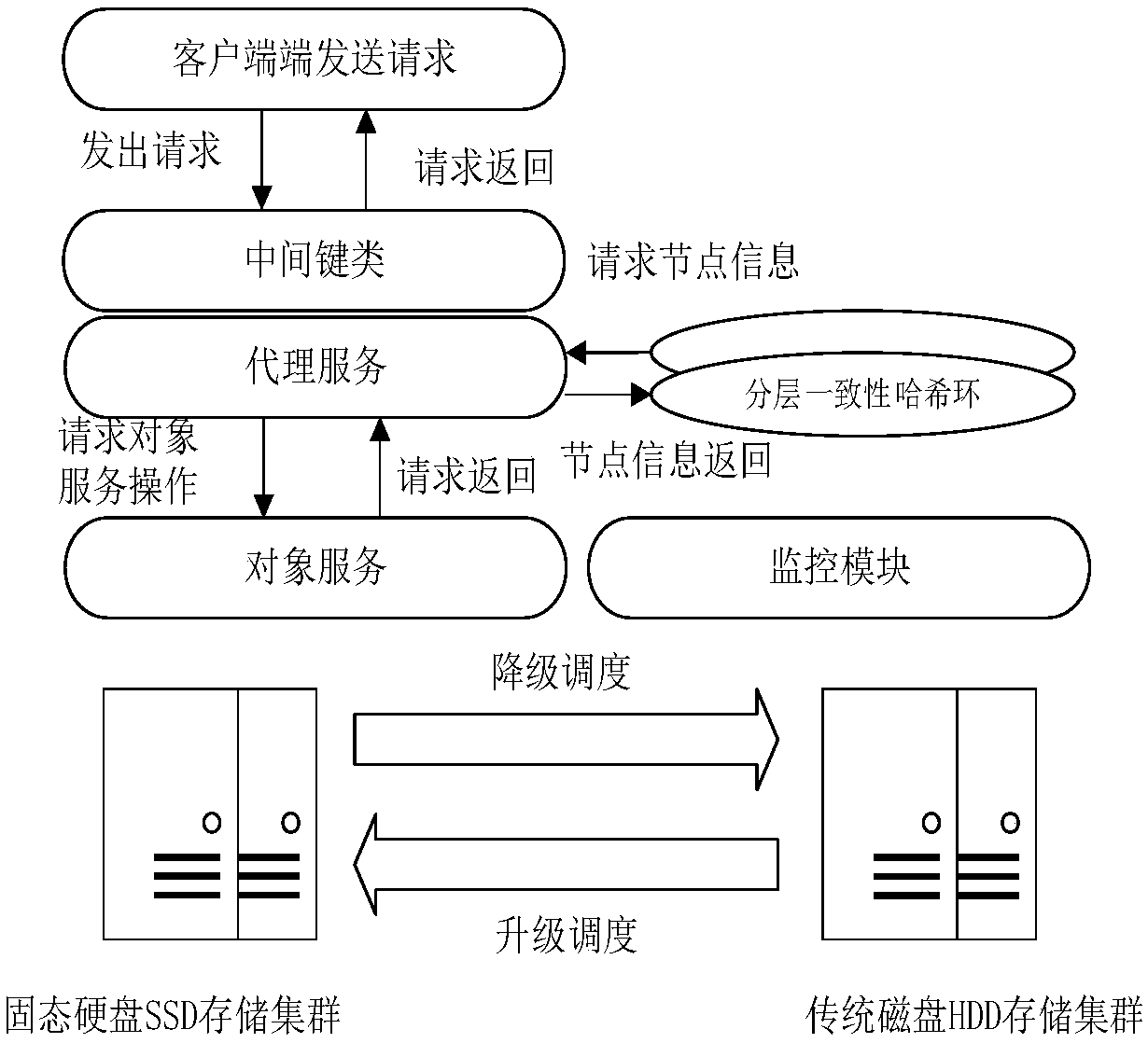
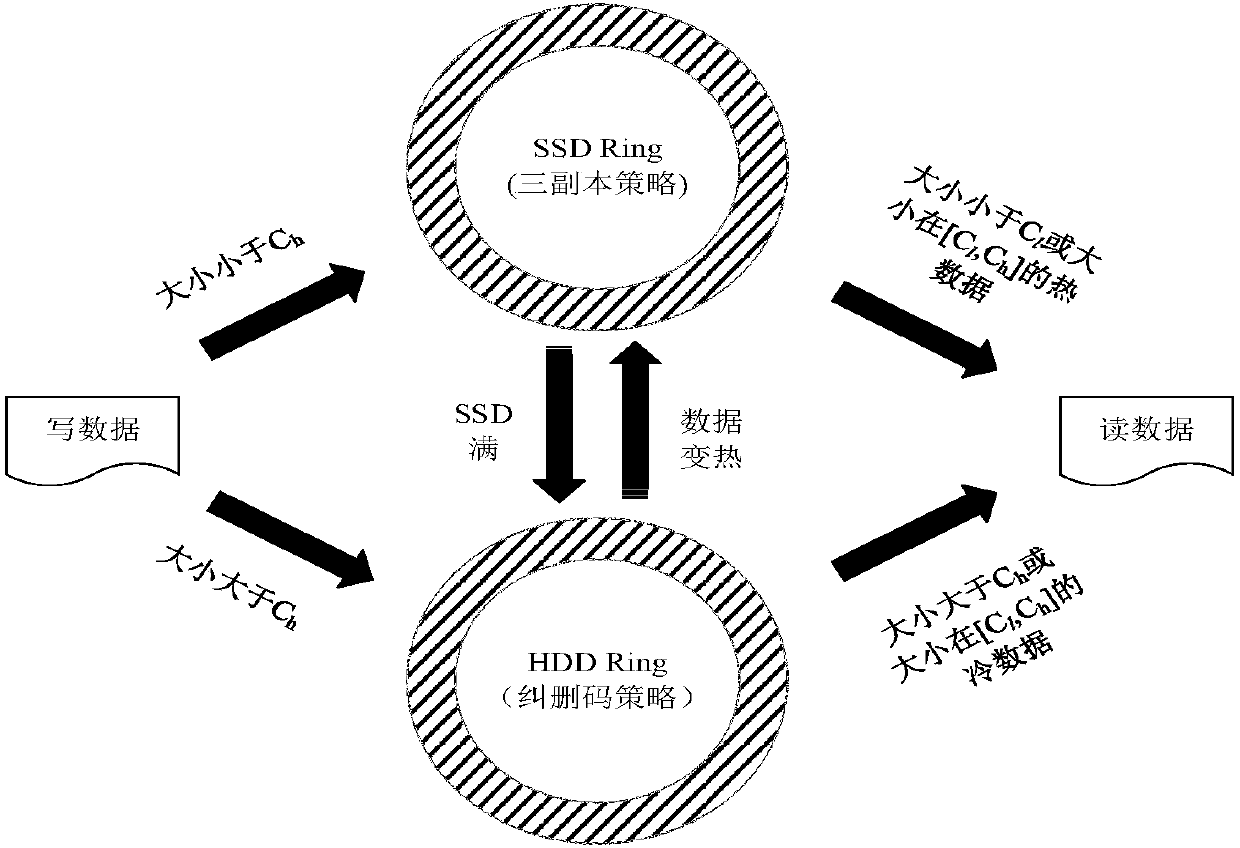
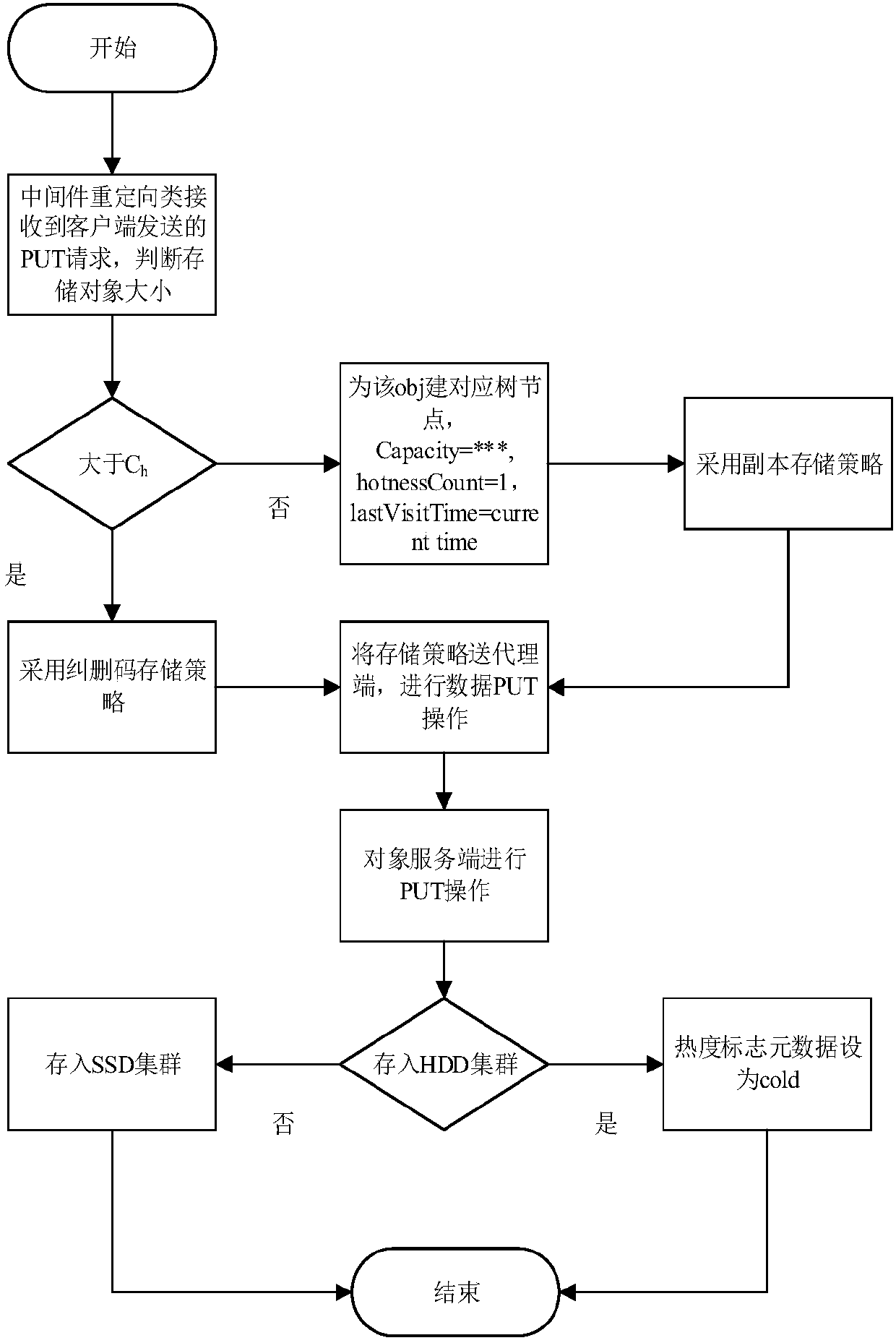
Consistent hash-based hierarchical mixed storage system and method
ActiveCN107844269ASmooth change of heat and coldInhibit migrationInput/output to record carriersComputer architectureData information
The invention discloses a consistent hash-based hierarchical mixed storage system and method, and belongs to the field of computer storage. The characteristics of various storage mediums can be utilized to the maximum extent; and storage policies are reasonably adopted, so that the system performance is improved. The method comprises the steps of designing a hierarchical consistent hash ring according to difference of the storage mediums and the storage policies; performing hierarchical storage in the hierarchical consistent hash ring through indexes such as access frequencies, capacity and the like by storage objects; introducing a monitoring module for determining data collection frequencies and data migration thresholds in different time periods; introducing a scheduling module for performing reasonable upgrading and downgrading data migration scheduling for cold and hot changes, with time, of data; and managing SSD cluster data information by adopting a forest data structure. The hierarchical storage is performed for load characteristics; different storage mediums and storage policies are provided according to the characteristics of the storage objects; the system flexibility is enhanced and the system read-write performance is improved; and the system stability is ensured.
Owner:HUAZHONG UNIV OF SCI & TECH
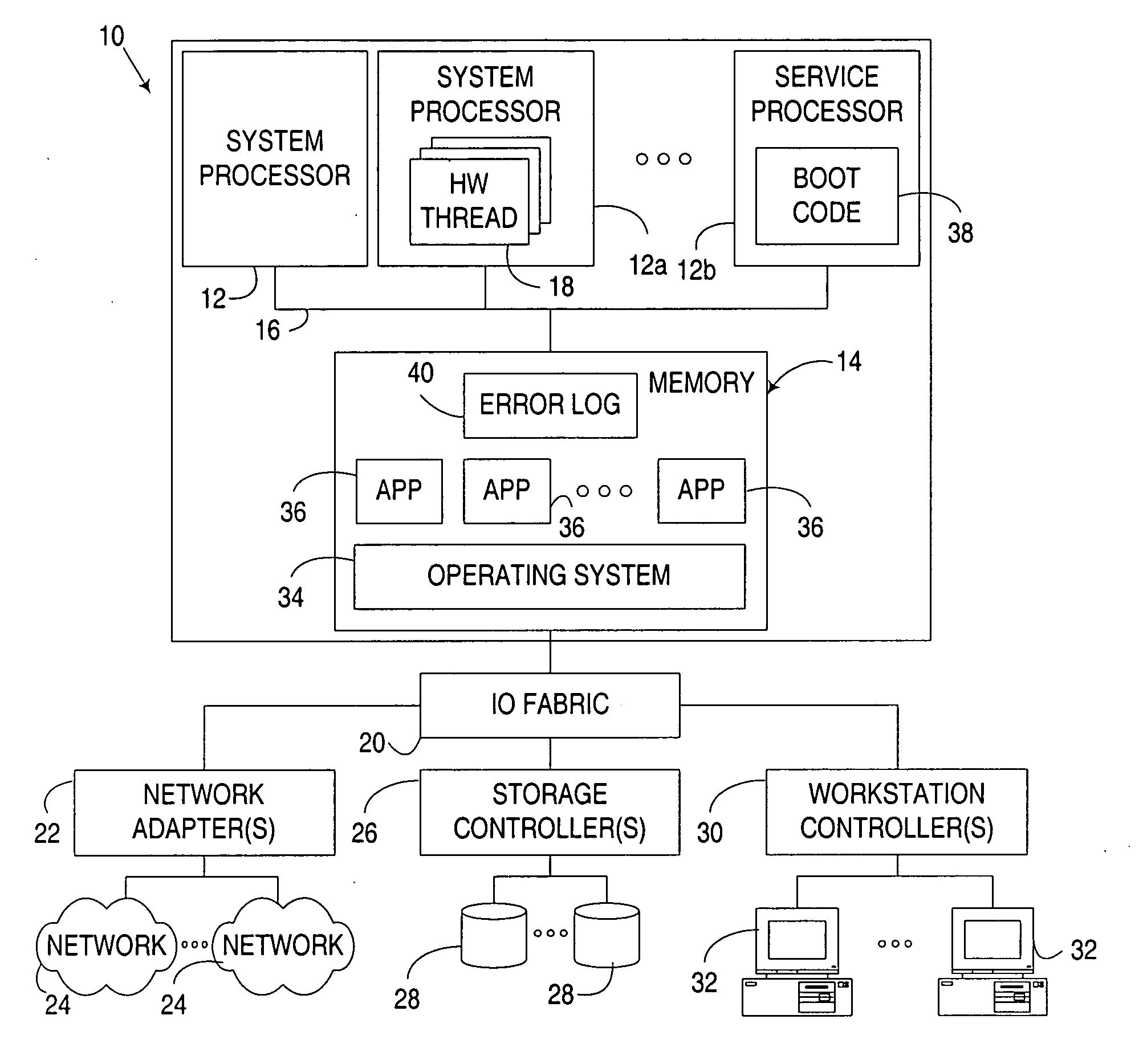
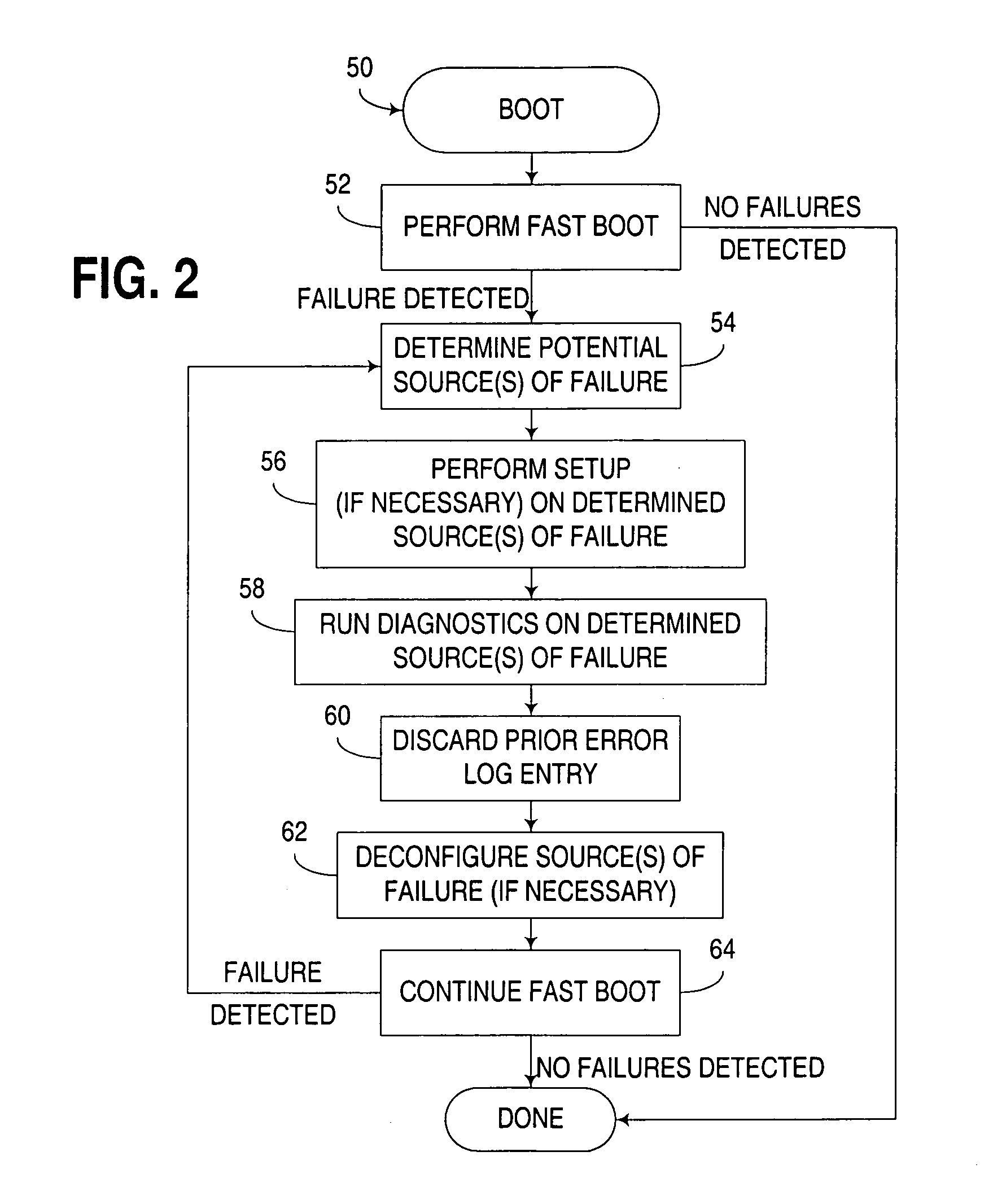
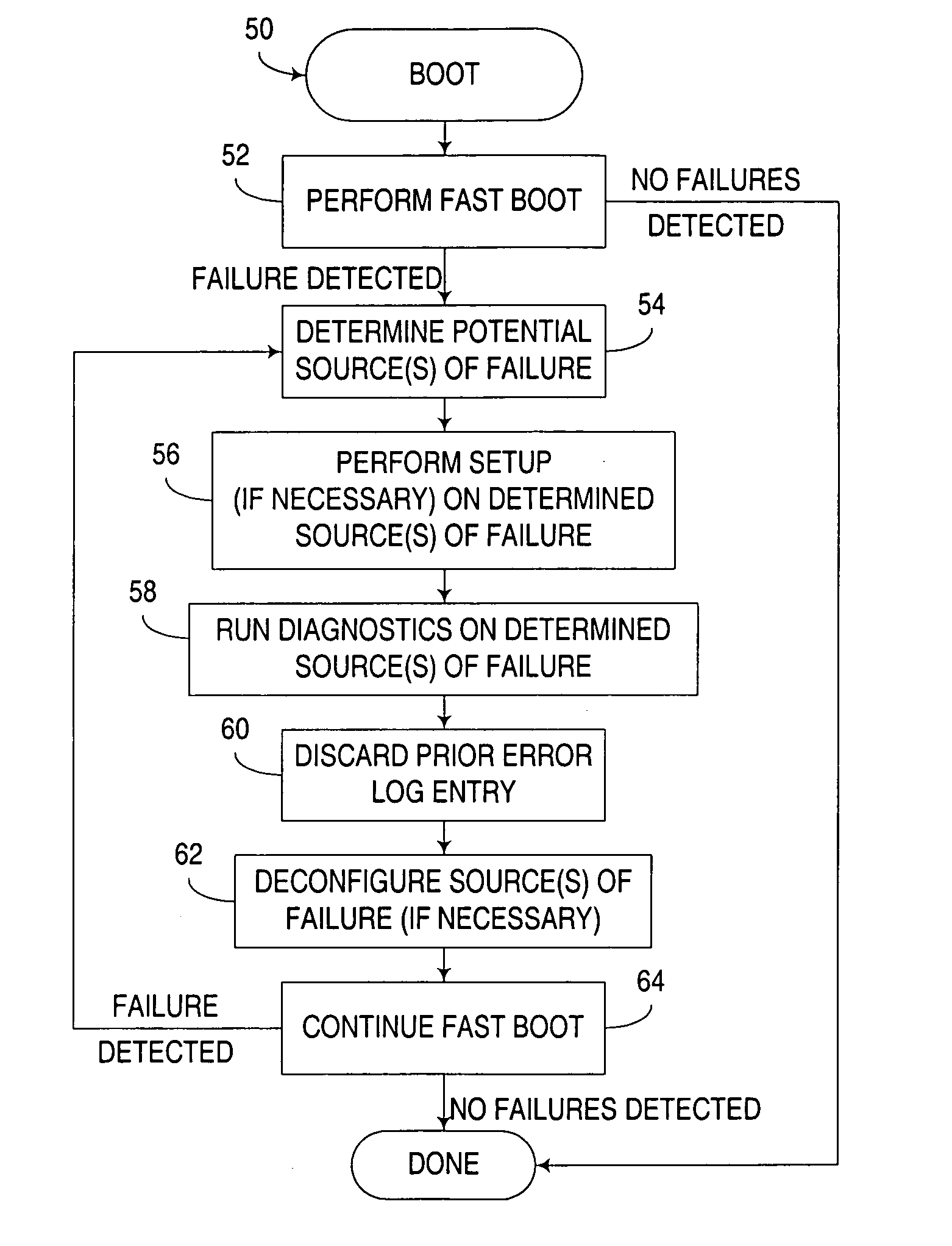
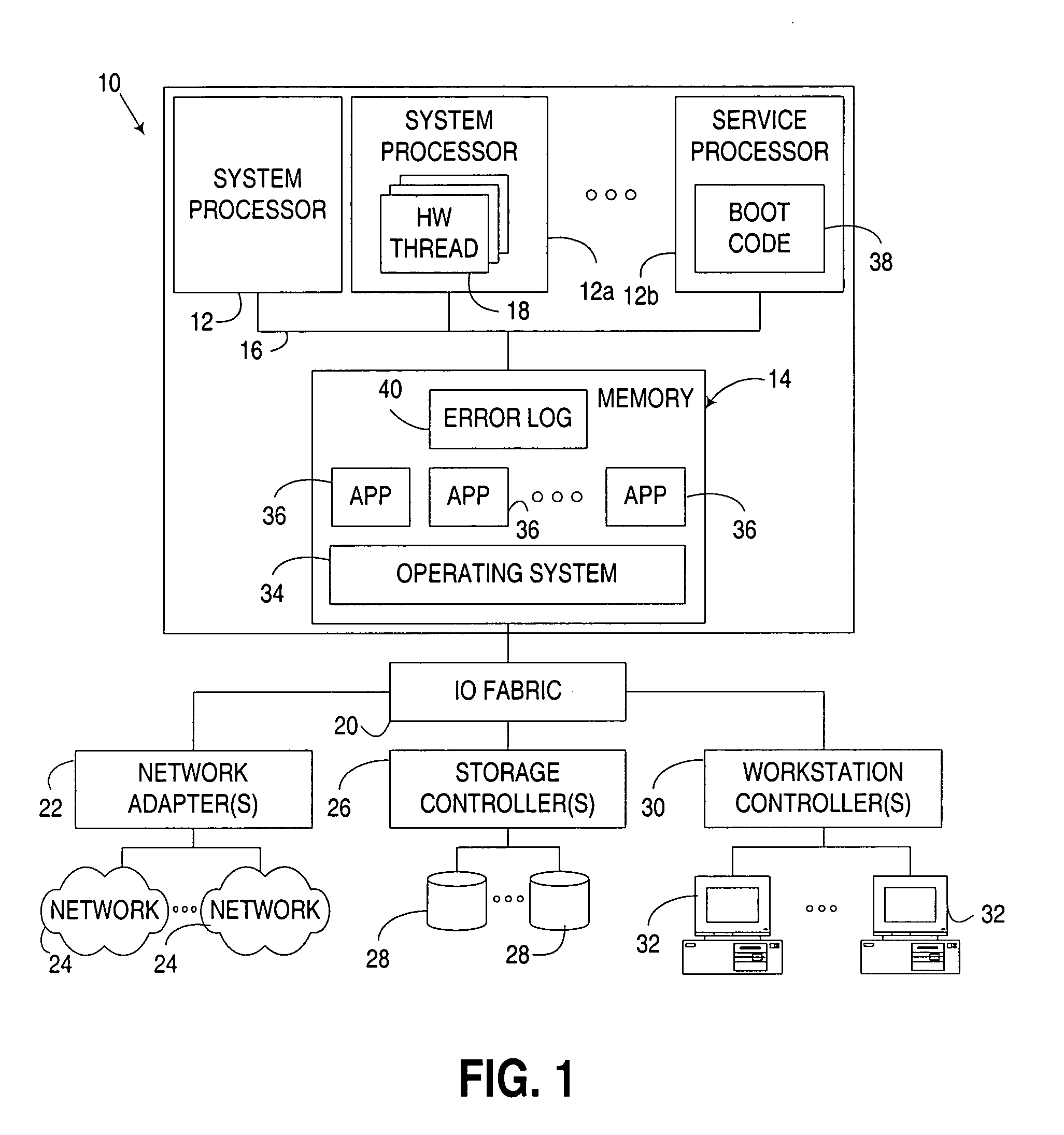
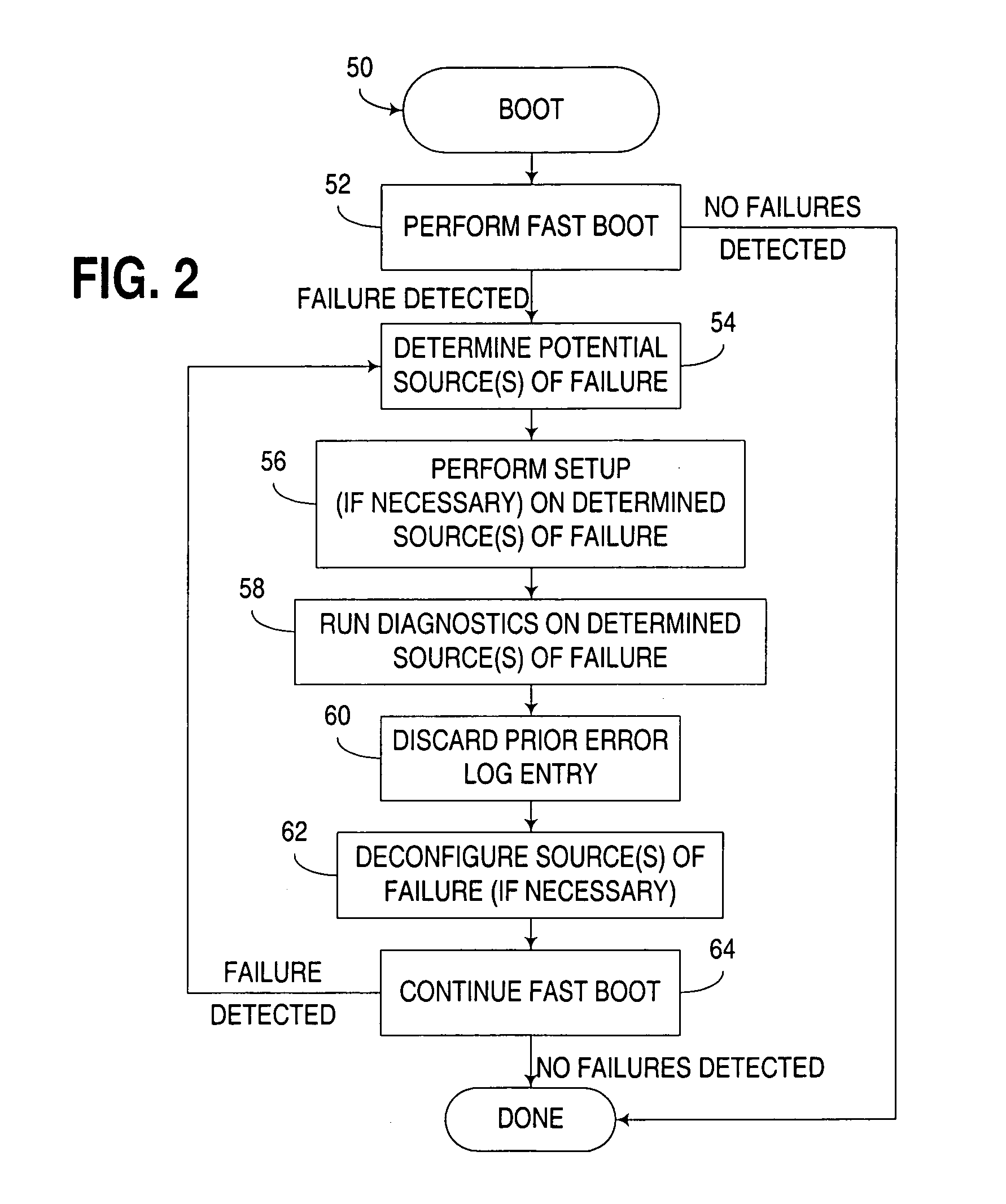
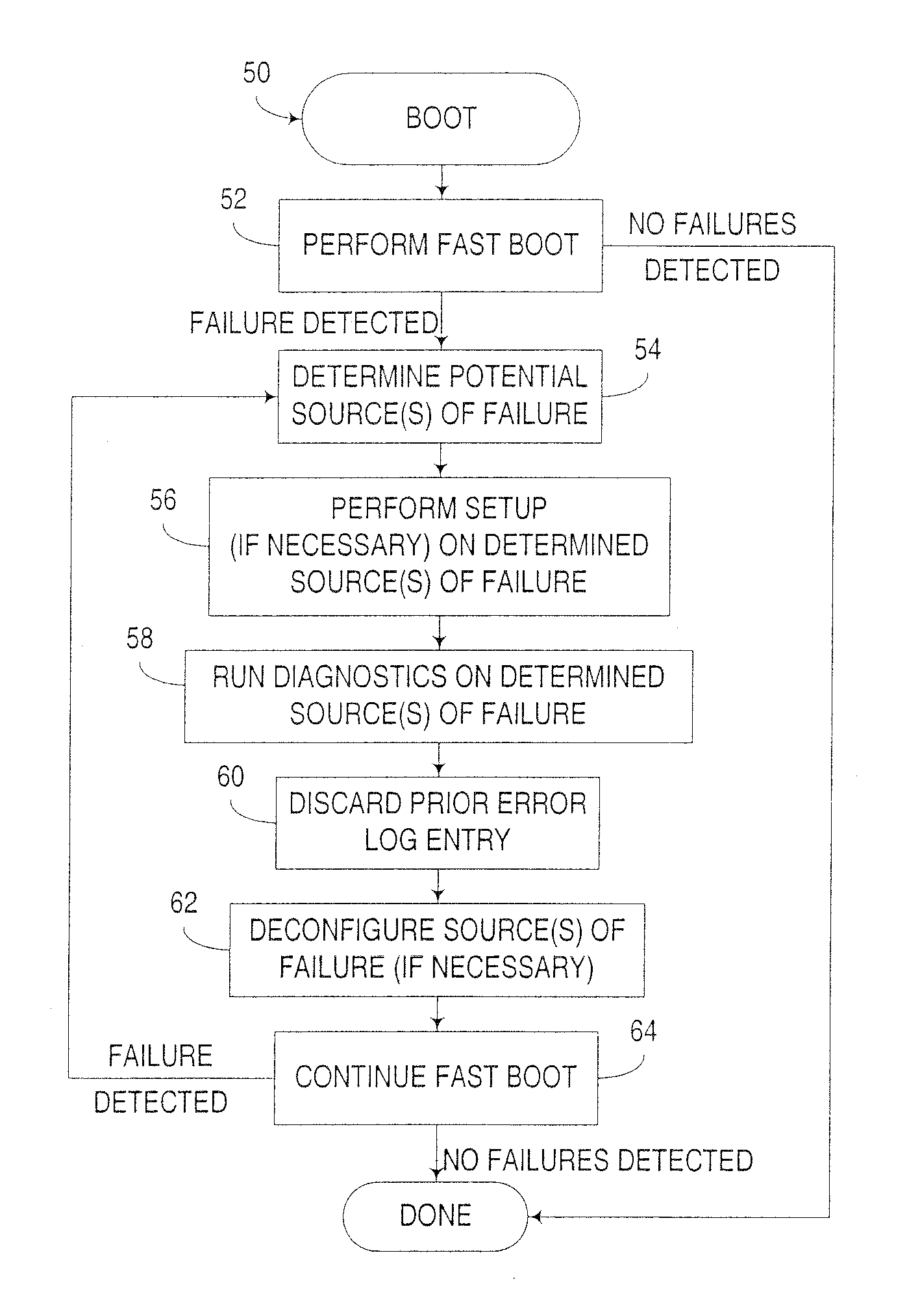
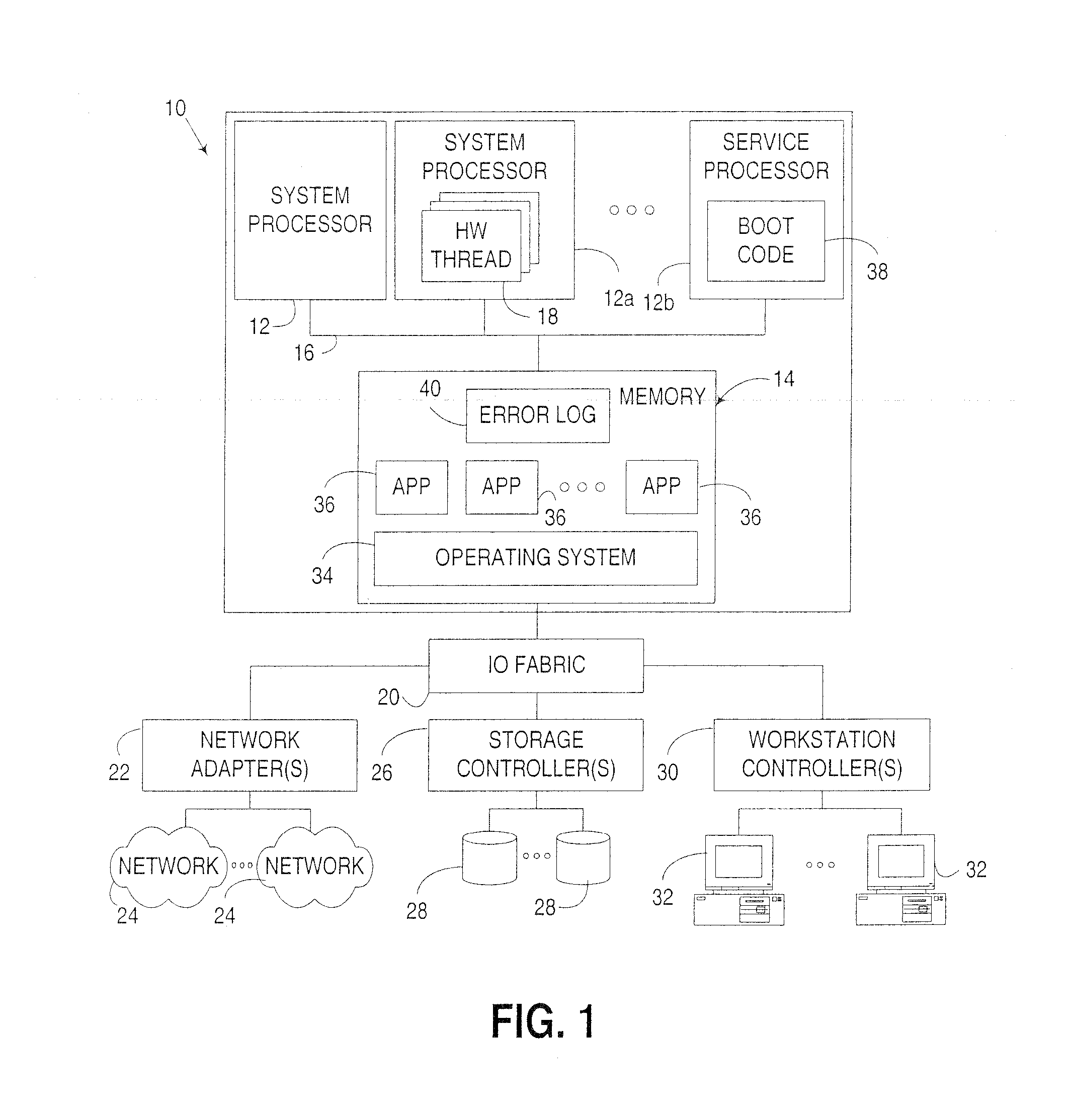
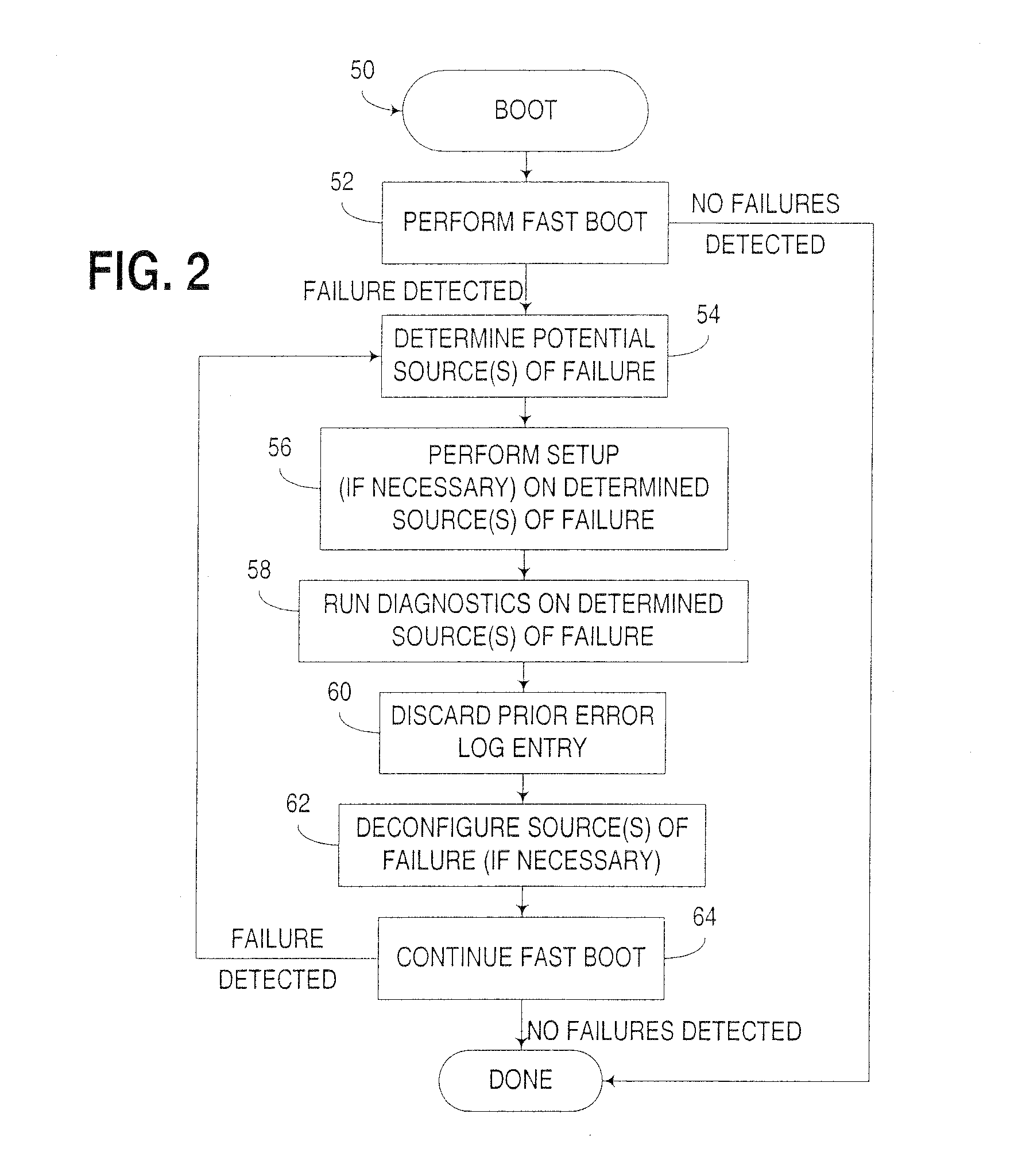
Computer boot operation utilizing targeted boot diagnostics
InactiveUS20050229042A1Reduce performance overheadEliminate needData processing applicationsDetecting faulty hardware by power-on testEngineering
An apparatus, program product and method utilize targeted boot diagnostics in connection with a boot operation to automate the handling of hardware failures detected during startup or initialization of a computer. In particular, in response to detection of a failure after initiation of and during performance of a boot operation, a targeted diagnostic operation is initiated on at least one hardware device in the computer in response to detecting the failure, such that after the targeted diagnostic operation is initiated, the boot operation may be completed.
Owner:IBM CORP
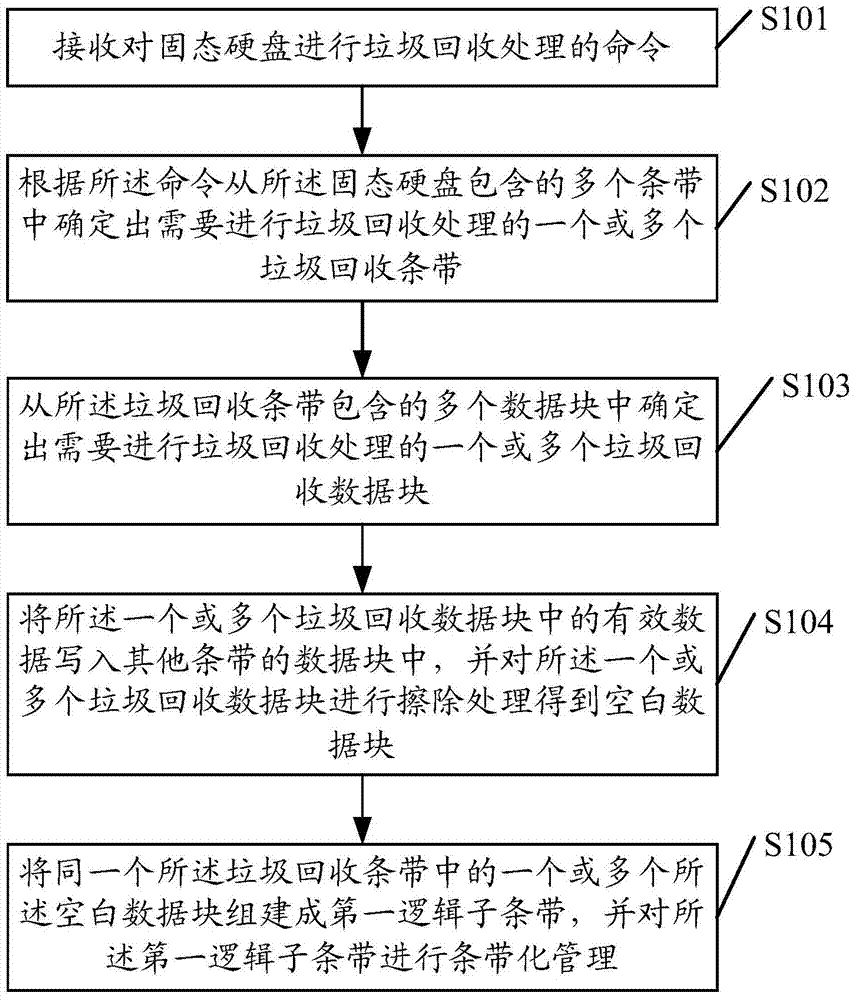
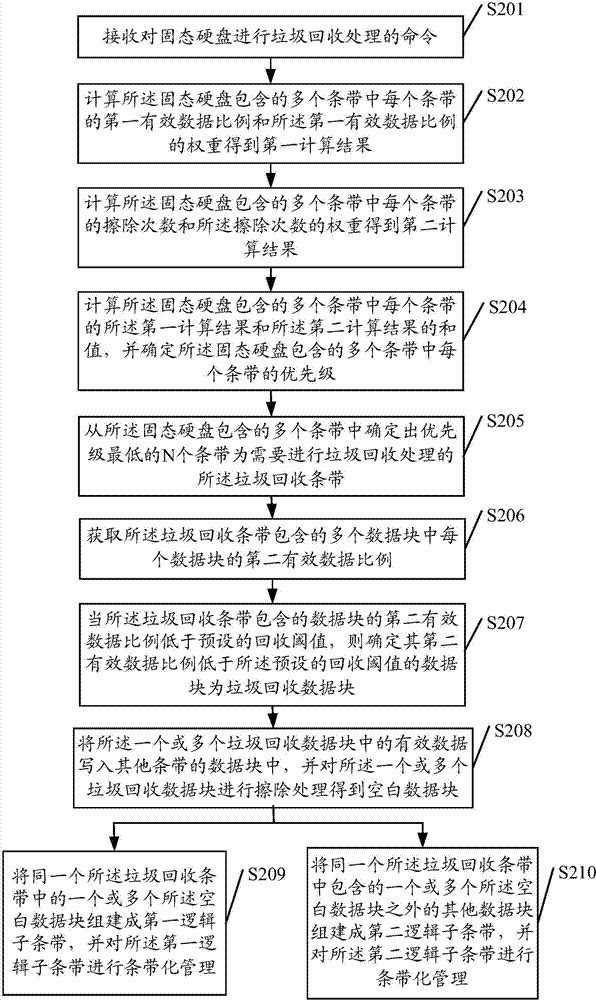
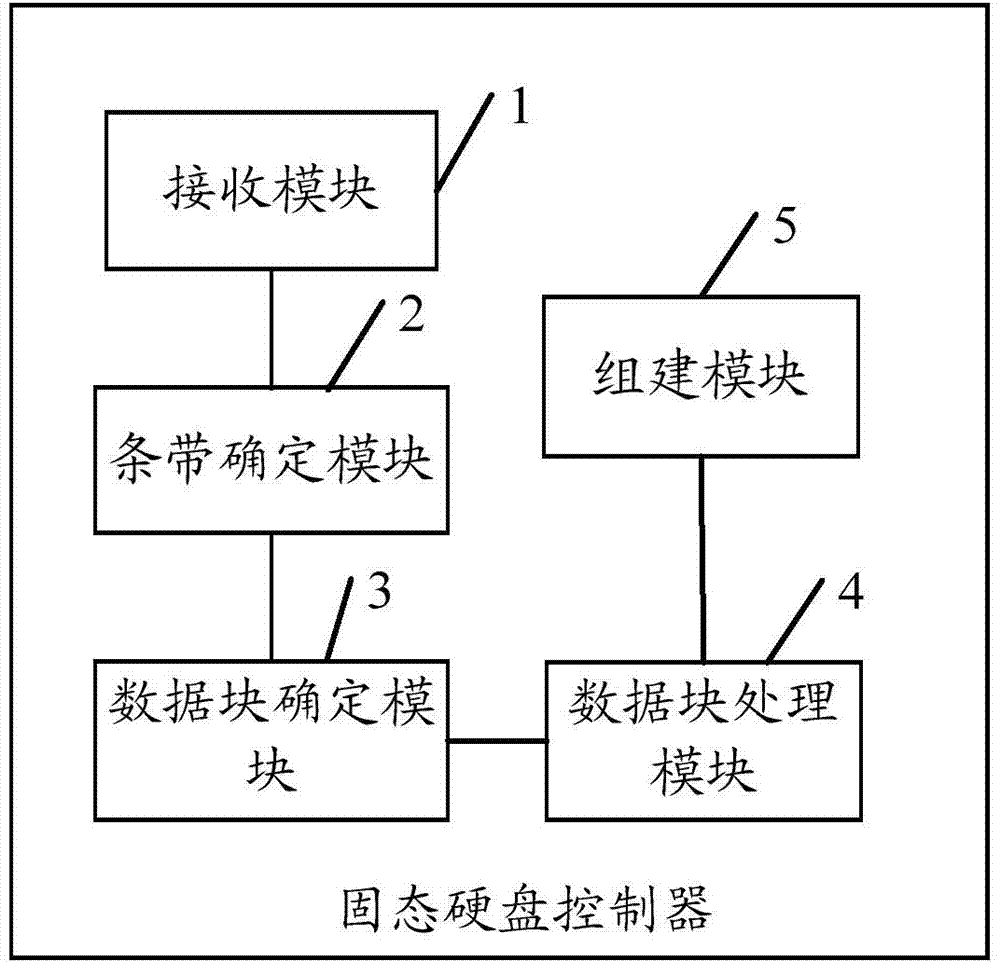
Method and system for recycling solid state disk junk and solid state disk controller
ActiveCN103902465AImprove garbage collection efficiencyReduce performance overheadMemory architecture accessing/allocationMemory adressing/allocation/relocationSolid-stateSolid-state drive
The invention relates to the technical field of storage and discloses a method and system for recycling solid state disk junk and a solid state disk controller. The method includes the following steps that an order for recycling junk on a solid state disk is received; junk recycling strips needing to perform junk recycling are determined from multiple strips included by the solid state disk according to the order; junk recycling data blocks needing to perform junk recycling are determined from multiple data blocks which are included in the junk recycling strips; effective data in the junk recycling data blocks are written into data blocks of other strips, and the junk recycling data blocks are erased to obtain blank data blocks. The blank data blocks in the junk recycling strips are built to form a first logic sub strip, and strip management is performed on the first logic sub strip. According to the scheme, the recycling efficiency of the solid state disk junk can be improved, and performance expenditure is reduced.
Owner:HUAWEI TECH CO LTD
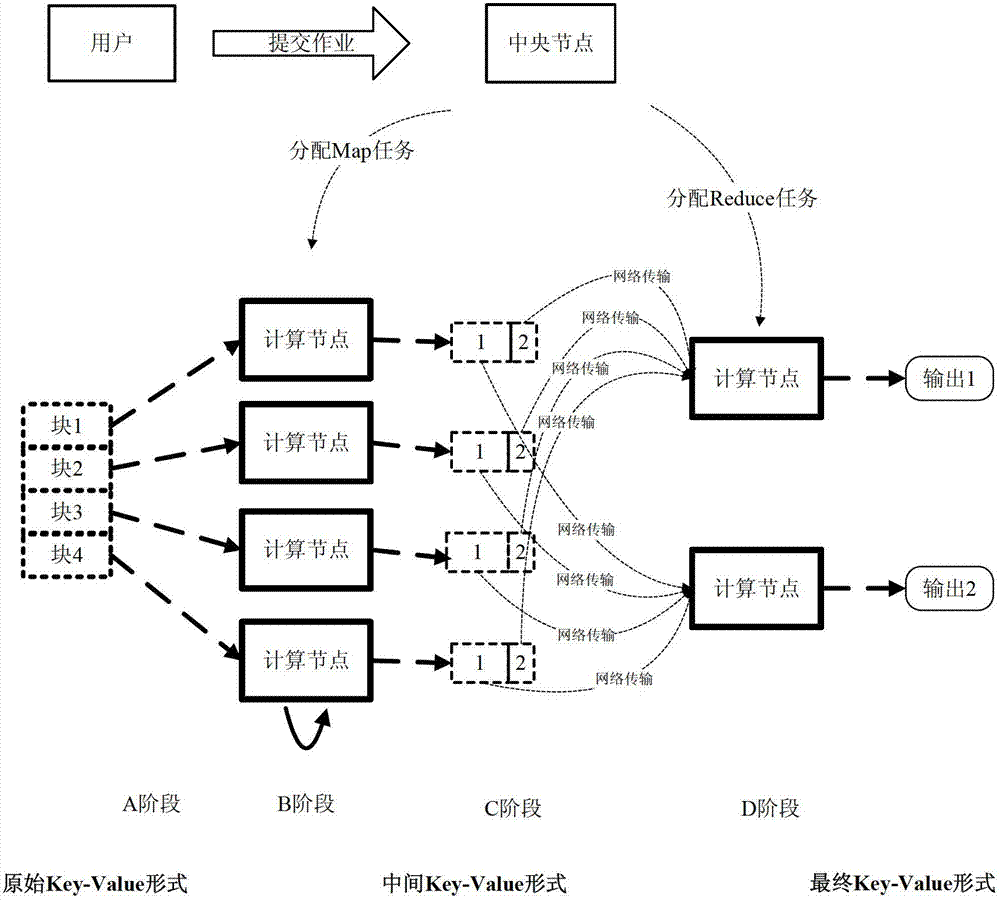
Task scheduling method and system based on MapReduce mechanism
InactiveCN102769615AIntegrity guaranteedReduce performance overheadTransmissionSecurity domainCollision domain
The invention provides a task scheduling method and a task scheduling system based on a MapReduce mechanism. The method comprises the following steps of: carrying out regional division on computing nodes in a MapReduce cloud computing environment, wherein a security domain, a scheduling domain and a collision domain are included; scheduling Map subtasks in a MapReduce task onto computing nodes of the security domain, and scheduling a copy of each Map subtask onto a computing node of the scheduling domain; and carrying out Hash verification on execution environments and partial intermediate results of the Map subtasks and the copies of the Map subtasks, wherein Reduce subtasks respectively utilize an execution environment verification value and an intermediate result verification value generated in a Map subtask stage to verify a self execution environment and input data. Due to the utilization of the method and the system, an operation environment of a task submitted by a common user can be effectively isolated from a malicious user, and the completeness of a task computing result can be ensured in a high-efficient way.
Owner:PEKING UNIV
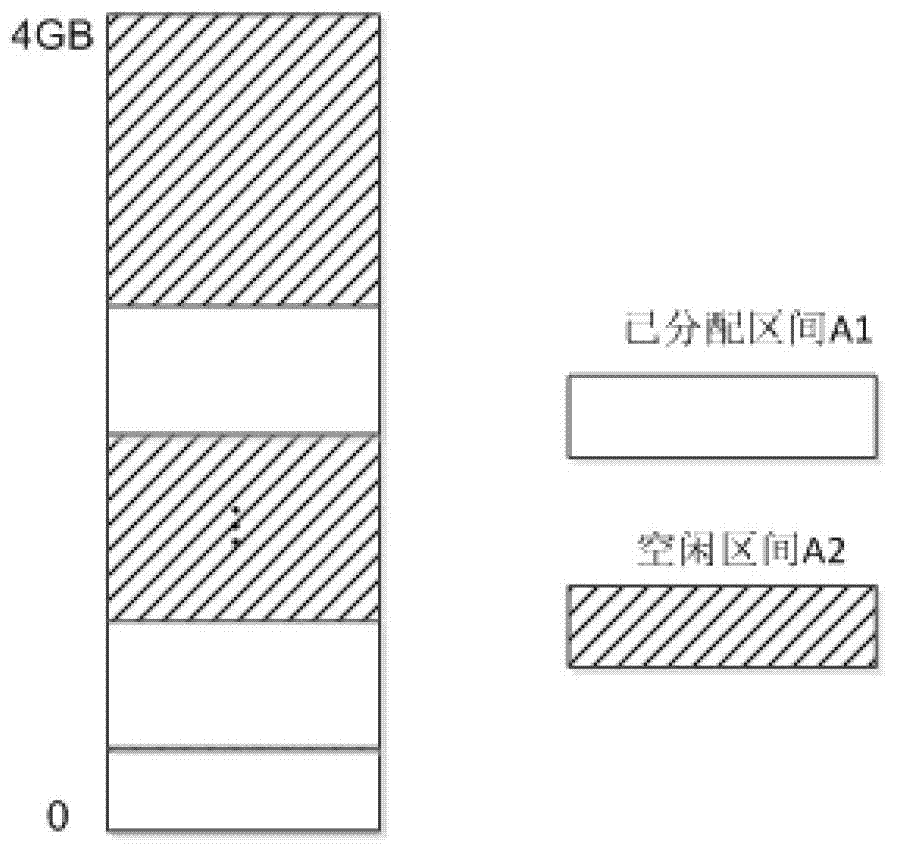
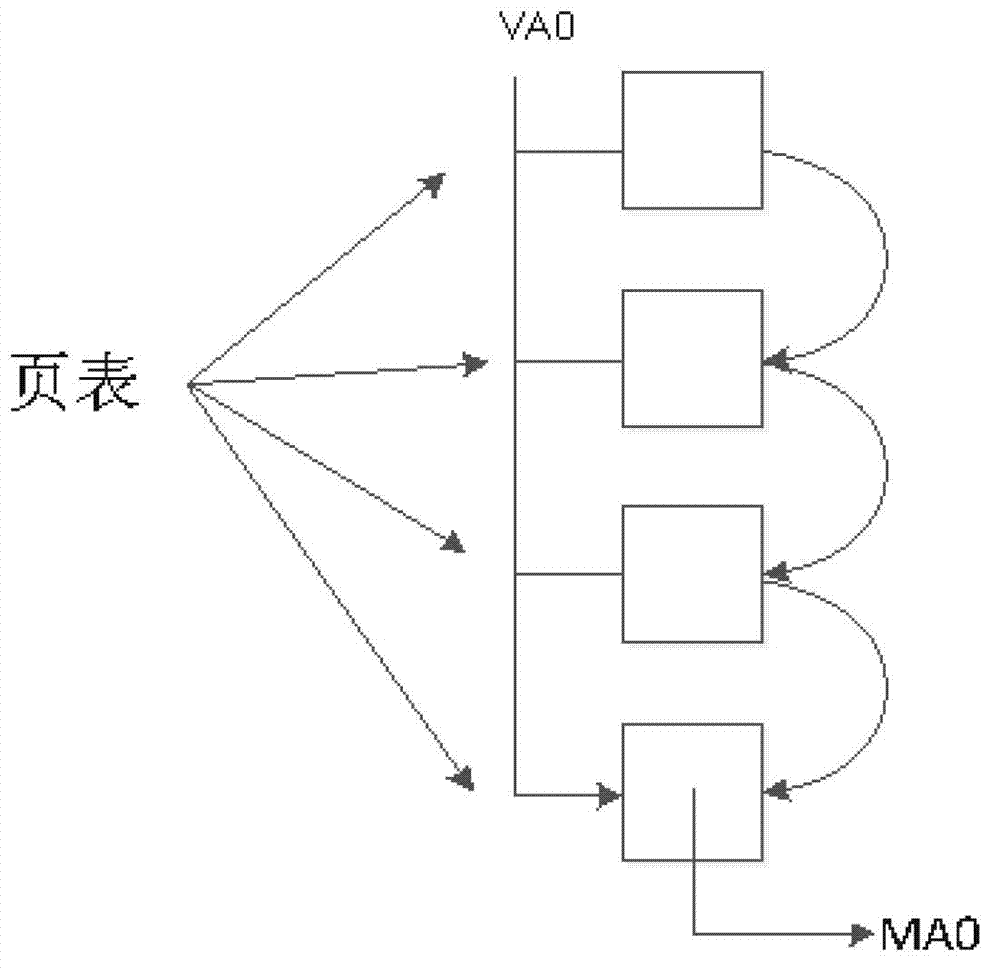
Internal storage static state partition and virtualization method
ActiveCN103116556AReduce performance overheadAvoid mappingMemory adressing/allocation/relocationVirtualizationProcessor register
The invention provides an internal storage static state partition and virtualization method which comprises that when a virtual address translation is conducted, a true launch bar (TLB) table is inquired, if the virtual address hits the target in the table, a machine address corresponding to the virtual address is directly confirmed according to a page frame number of a page table item in the TLB table; and if the virtual address does not hit the target in the table, a missing processing flow of the TLB is switched to. In the missing processing flow of the TLB, a physical address is acquired from the virtual address; then a machine address corresponding to the physical address is calculated through address offset of a virtual machine, wherein the address offset of the virtual machine is stored in a control register of a virtual machine; and then the machine address is filled in the TLB. The address offset of the virtual machine is the address offset of the virtual machine, wherein the address offset of the virtual machine is stored in the control register of the virtual machine.
Owner:JIANGNAN INST OF COMPUTING TECH
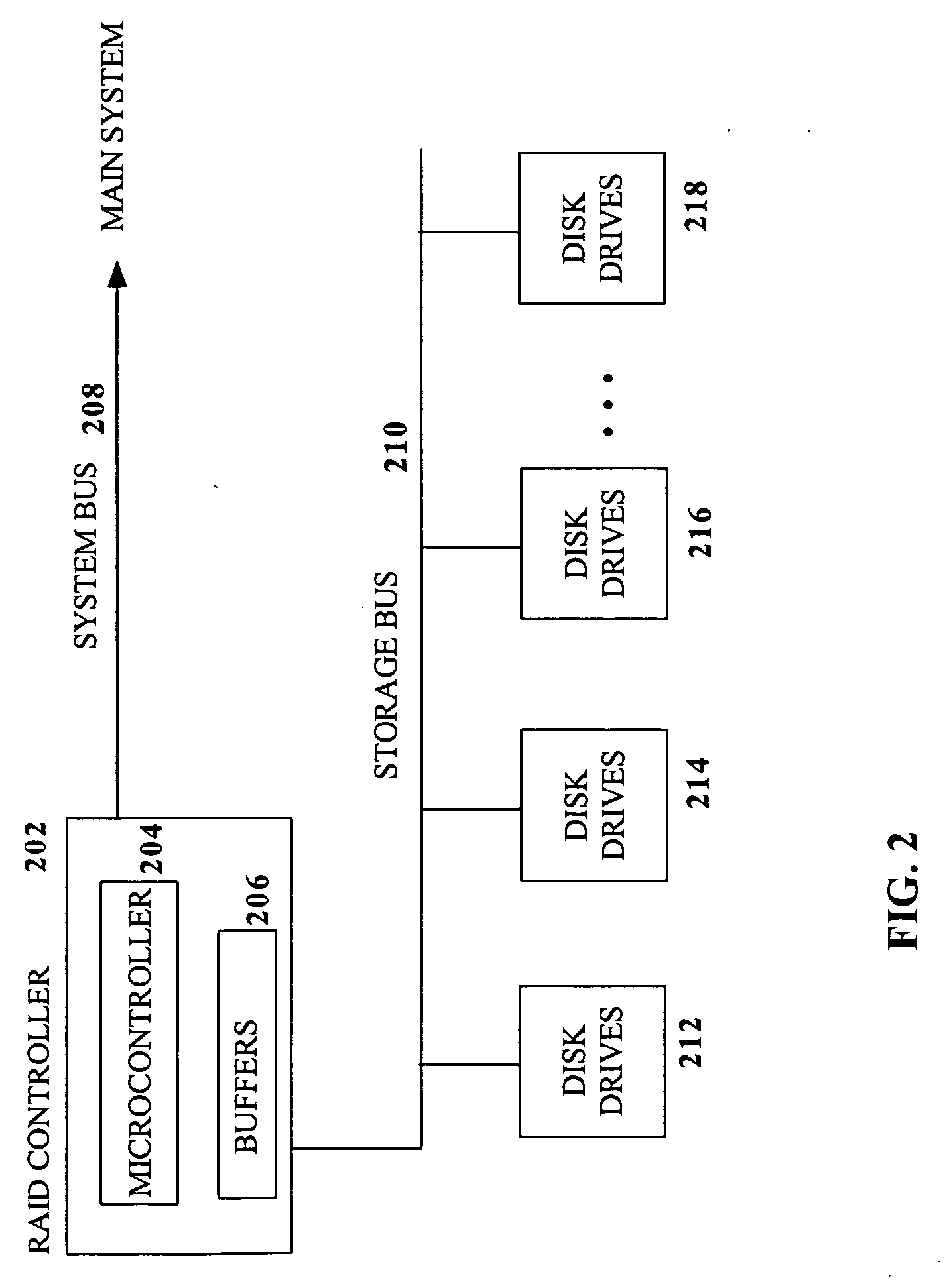
Method and system for increasing parallelism of disk accesses when restoring data in a disk array system
InactiveUS20060123312A1Solve excessive overheadImprove parallelismError detection/correctionCode conversionRAIDDisk array
In a disk array environment such as a RAID-6 environment, the overall performance overhead associated with exposed mode operations such as resynchronization, rebuild and exposed mode read operations is reduced through increased parallelism. By selecting only subsets of the possible disks required to solve a parity stripe equation for a particular parity stripe, accesses to one or more disks in a disk array may be omitted, thus freeing the omitted disks to perform other disk accesses. In addition, disk accesses associated with different parity stripes may be overlapped such that the retrieval of data necessary for restoring data for one parity stripe is performed concurrently with the storage of restored data for another parity stripe.
Owner:IBM CORP
Computer boot operation utilizing targeted boot diagnostics
InactiveUS7266727B2Eliminate needReduce performance overheadData processing applicationsDetecting faulty hardware by power-on testEngineering
An apparatus, program product and method utilize targeted boot diagnostics in connection with a boot operation to automate the handling of hardware failures detected during startup or initialization of a computer. In particular, in response to detection of a failure after initiation of and during performance of a boot operation, a targeted diagnostic operation is initiated on at least one hardware device in the computer in response to detecting the failure, such that after the targeted diagnostic operation is initiated, the boot operation may be completed.
Owner:INT BUSINESS MASCH CORP
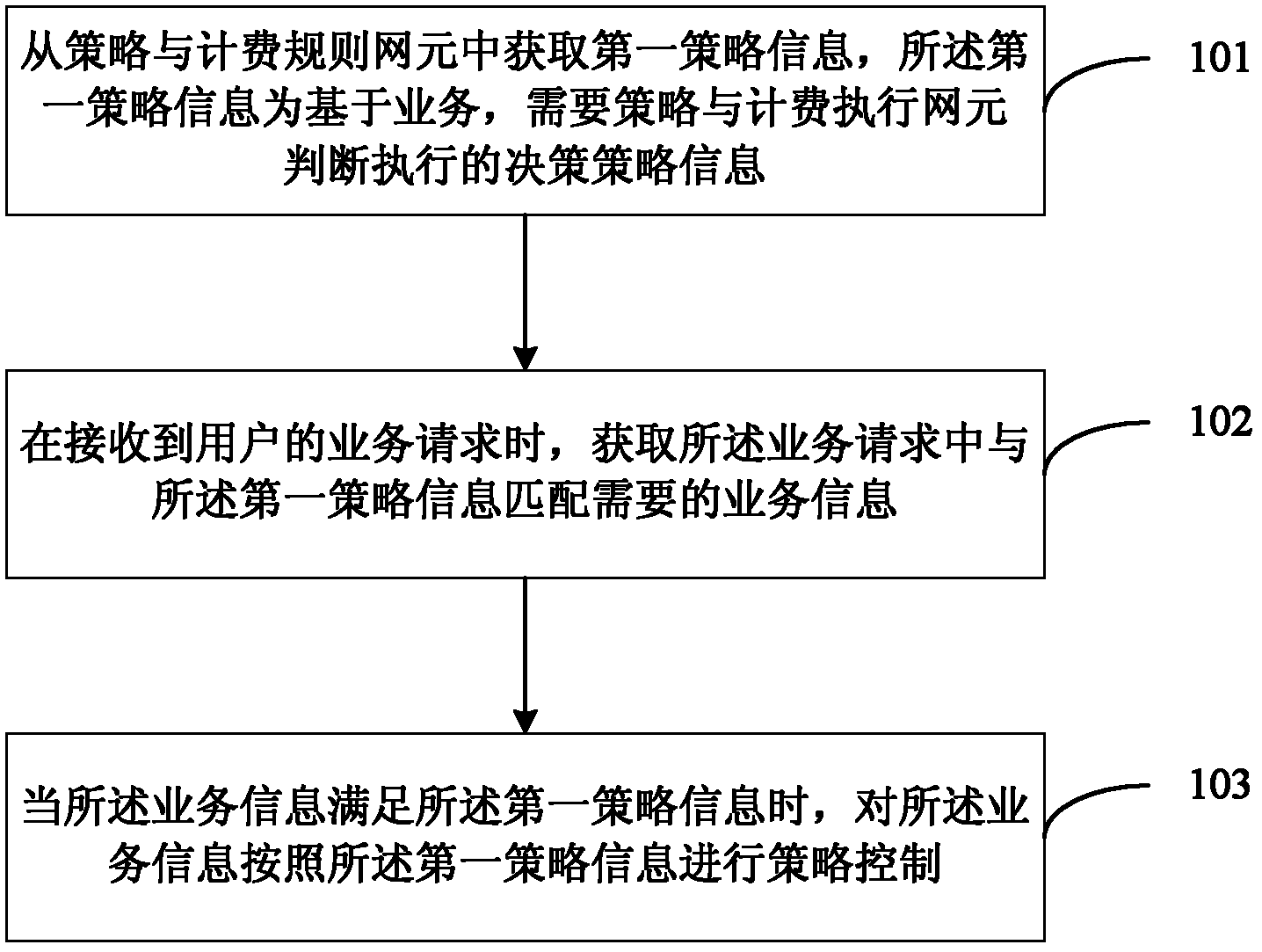
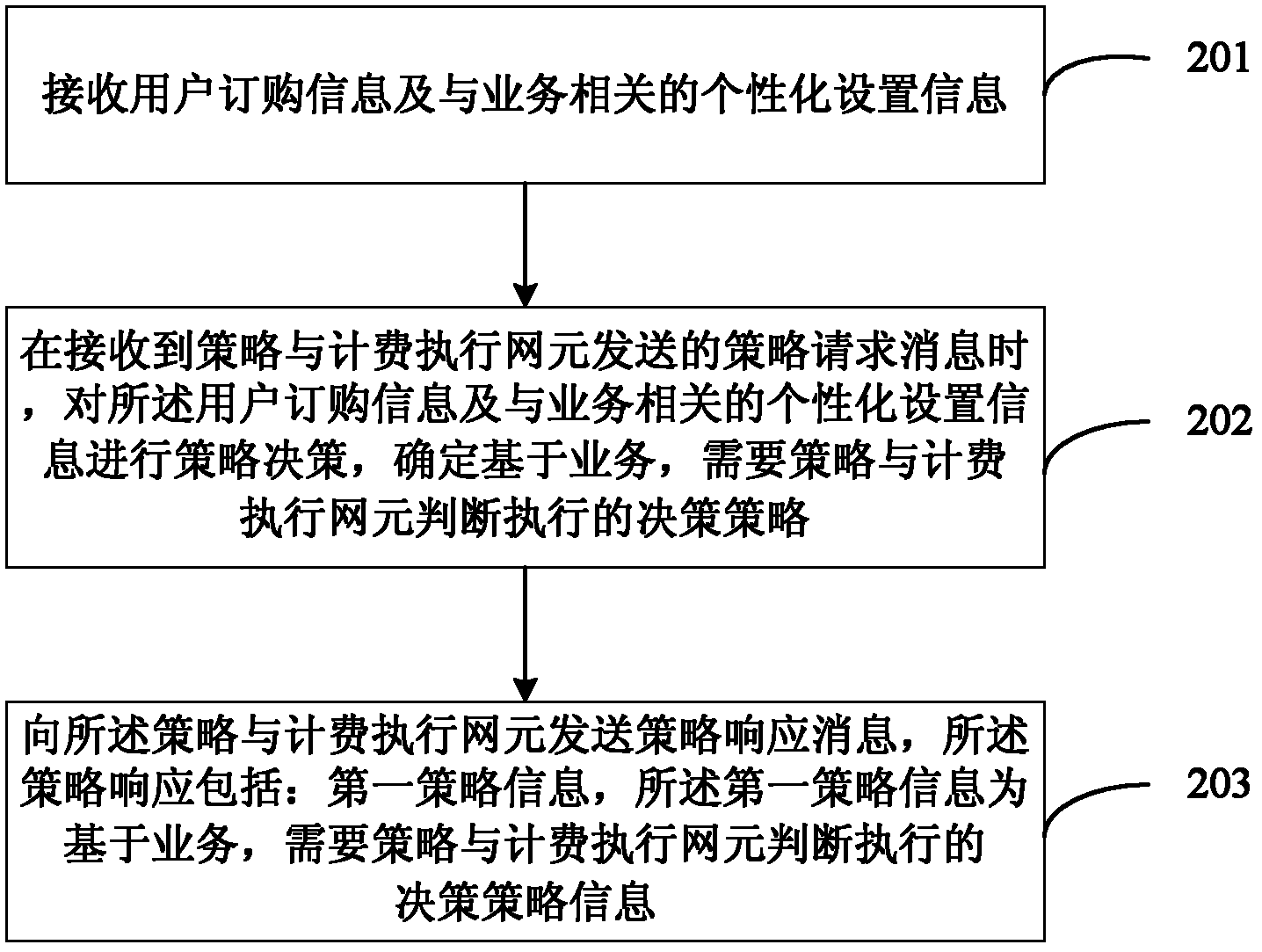
Policy control method, policy control device and policy control system for data services
ActiveCN102665191AReduce the number of interactionsReduce performance overheadTransmissionNetwork data managementControl systemDecision strategy
An embodiment of the invention provides a policy control method, a policy control device and a policy control system for data services. The method includes: acquiring first policy information from a policy and charging rule function network element, wherein the first policy information is decision policy information needing to be judged and enforced by a policy and charging enforcement function network element based on the services; when a service request is received from a user, acquiring service information needed in match with the first policy information from the service request; and when the service information satisfies the first policy information, performing policy control for the service information according to the first policy information. The method, the device and the system in the embodiment solve the technical problem of more interactive times between the PCRF (policy and charging rule function) network element and the PCEF (policy and charging enforcement function) network element in policy control of frequently modified service request information or result associated policy control in the prior art.
Owner:HUAWEI TECH CO LTD
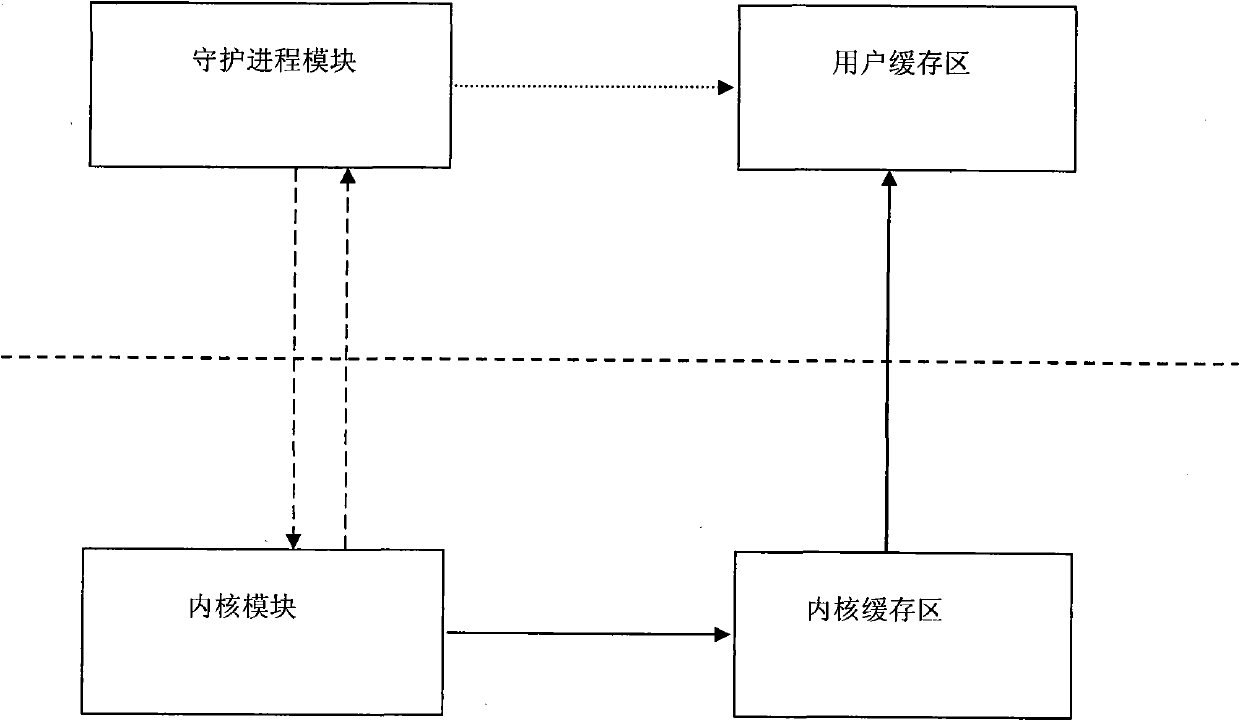
Continuous data caching system and data caching method thereof
InactiveCN101770412AReduce complexityReduce performance overheadMemory adressing/allocation/relocationRedundant operation error correctionComputer data storageNetwork performance
The invention discloses a continuous data caching system and a data caching method thereof, belonging to computer data storage system and backup method and solving the problem that continuous data capturing capability and protective capability are unmatched brought by burst I / O and network performance fluctuation. The inventive system is composed of a core cache zone, a user cache zone, a core module and a daemon process module. The inventive method comprises initializing, storing core cache zone data, storing user cache zone data, and transmitting user cache zone data. The inventive system adopts two-level cache mechanism comprising core cache and user cache, is structured on TCP / IP protocol, has little performance expenditure and reduces user node complexity. The inventive method adopts smaller core cache zone and larger user cache zone, thus lowering core processing complexity, allocating or recycling user cache zone node timely by proposing cache anticipation algorithm, optimizing use ratio of user cache zone and saving system internal storage resource.
Owner:HUAZHONG UNIV OF SCI & TECH
Asymmetric software triple-computer hot backup fault-tolerant method
InactiveCN101876926AReduce performance overheadImprove performanceSoftware simulation/interpretation/emulationRedundant operation error correctionOperating environmentVirtual machine
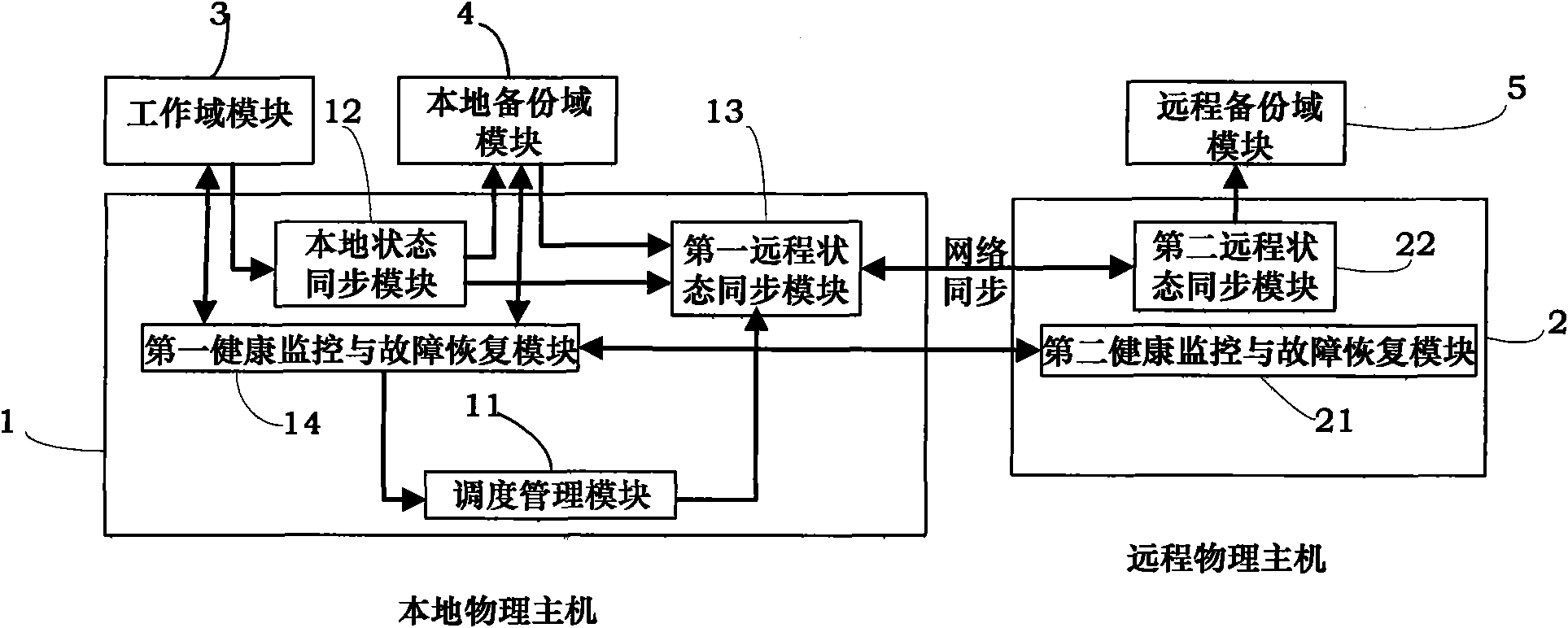
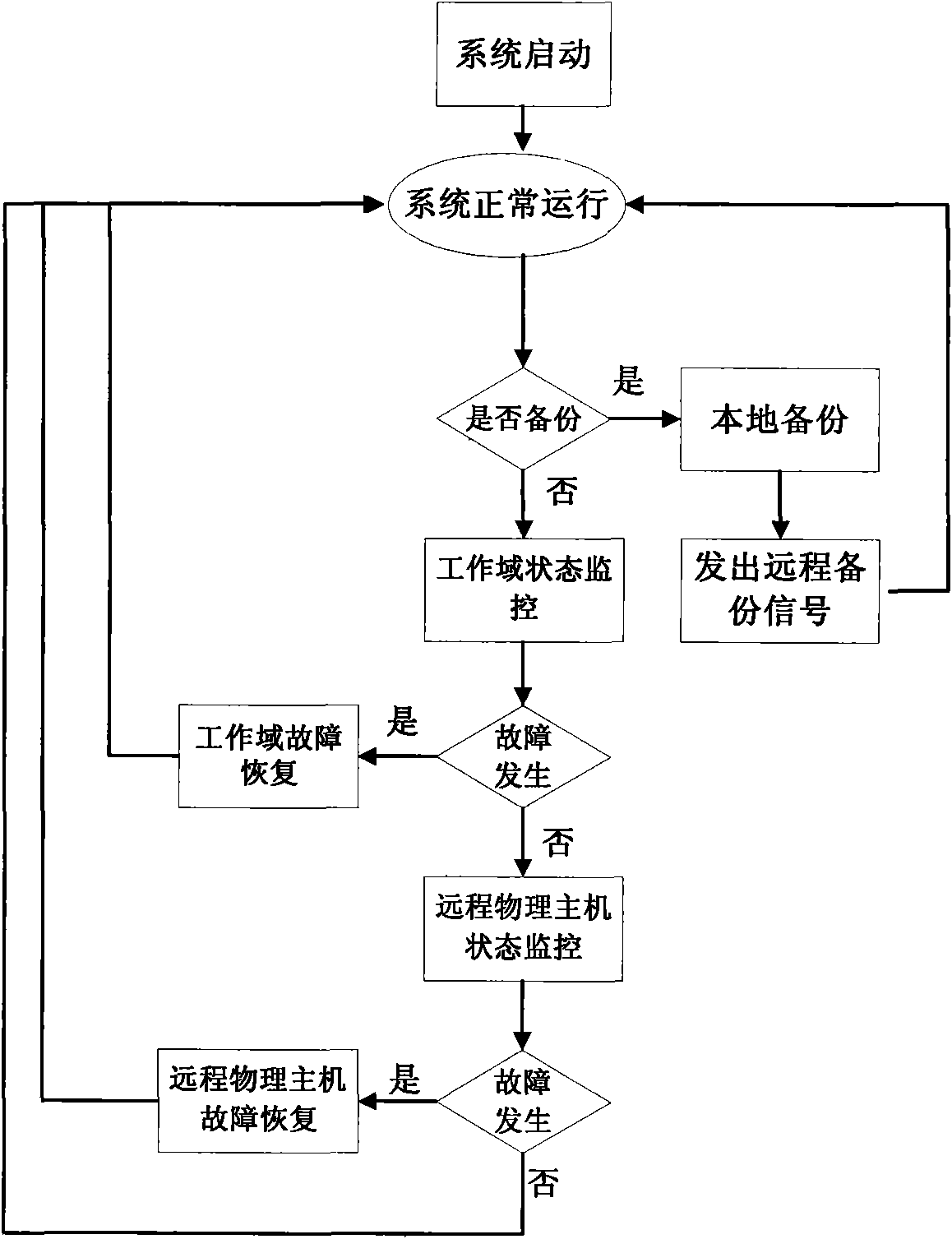
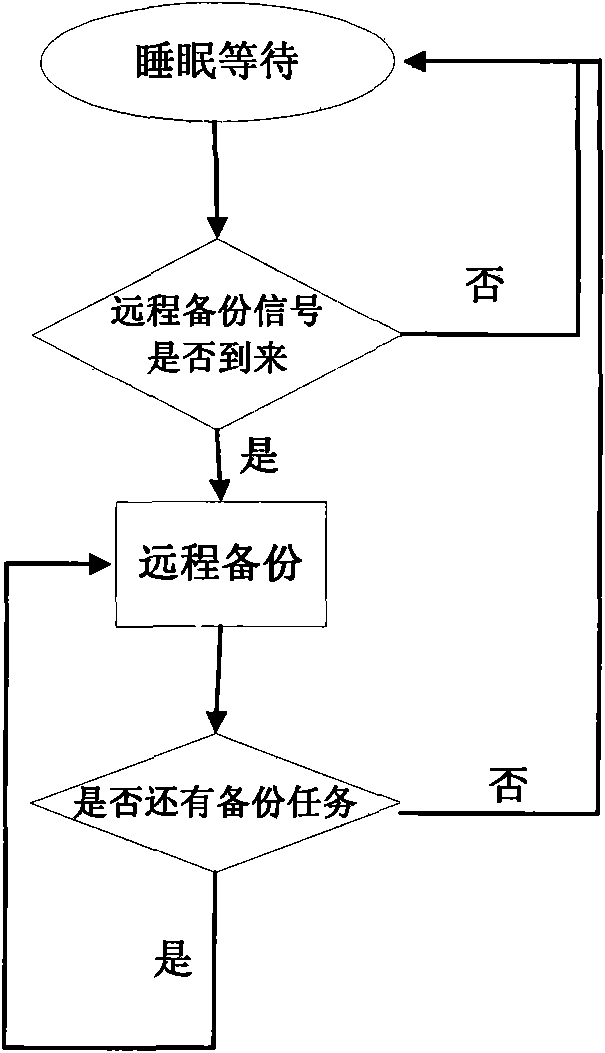
The invention provides an asymmetric software triple-computer hot backup fault-tolerant method. Both a local physical host and a remote physical host are loaded with virtual machine systems, simultaneously, a local backup domain and a remote backup domain are provided for user application and the operating environment, the user application and the operating environment are encapsulated into a work domain, the local backup domain and the work domain are run in the same physical host, the remote backup domain is run in another physical host, and the two physical hosts are connected with each other through the network. As the remote backup operation is completed by a specific processor, the executing process does not affect the running of the local work domain at all. The method greatly reduces the performance cost caused by synchronization of main and standby states at the same time of guaranteeing the reliability of the system, and simultaneously, the deployment of the fault-tolerant system is more flexible and has better expandability.
Owner:BEIHANG UNIV
Client page display method, apparatus and system
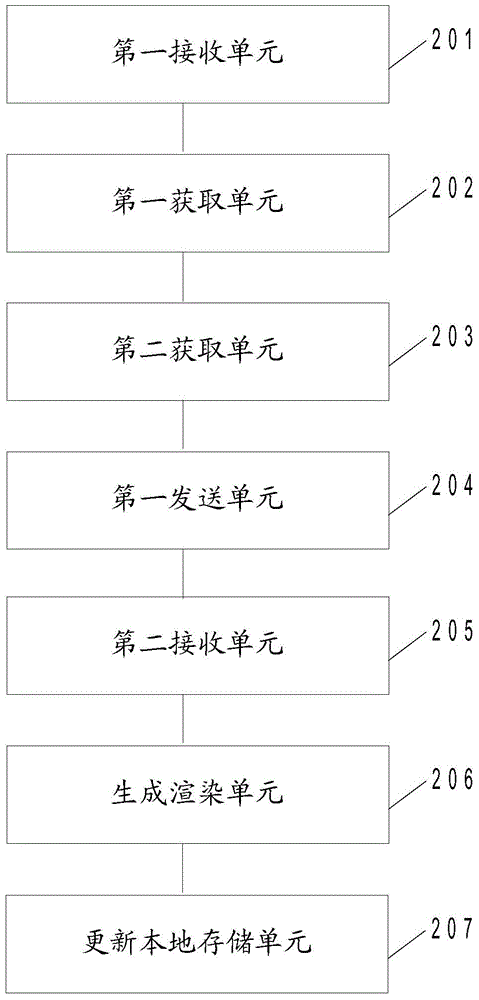
ActiveCN105404622AImprove experienceReduce performance overheadSpecial data processing applicationsClient-sideDynamic data
The application discloses a client page display method and apparatus, a client page updating method and apparatus, and a client page display system. The client page display method comprises: sending a page identifier of a page, a verification identifier of local dynamic data of a client and a verification identifier of a page structure to a server, and requesting for an updating part in two parts of the dynamic data of the page and the page structure from the server; receiving a response from the server; and from the response returned by the server and a page part pre-stored locally, selecting the dynamic data with a latest current version and the page structure, and generating and rendering the page. With the adoption of the method provided by the application, the dynamic data and the page structure can be updated, so that the effects of increasing the cache utilization rate of the page structure of the client, reducing performance overhead of the client, lowering network traffic and improving user experience are achieved.
Owner:ALIBABA GRP HLDG LTD
Sliding display method and sliding display device of list data of mobile terminal
InactiveCN105892831AReduce stepsReduce operation frequencyInput/output processes for data processingComputer engineering
The embodiment of the invention provides a siding display method and a siding display device of list data of a mobile terminal. The siding display method comprises the following steps of: displaying a data target in a list; when detecting list sliding operation on the data target, calculating the sliding speed of the data target; calculating the sliding distance of the data target according to the sliding speed; and if the sliding speed is greater than a first preset speed threshold, performing refresh display on the data target according to the sliding distance. By adopting the siding display method provided by the embodiment of the invention, the refresh frequency is dynamically adjusted under the situation that the sliding speed is relatively high, in primary refresh display, the time for moving the distance threshold is generally longer than conventional primary refresh time based on refresh frequency, that is, the refresh frequency after dynamic adjustment is smaller than the set refresh frequency, and the operation of re-drawing the interface of a whole list control can be reduced.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
Data flow monitoring-based code reuse attack defending method and system
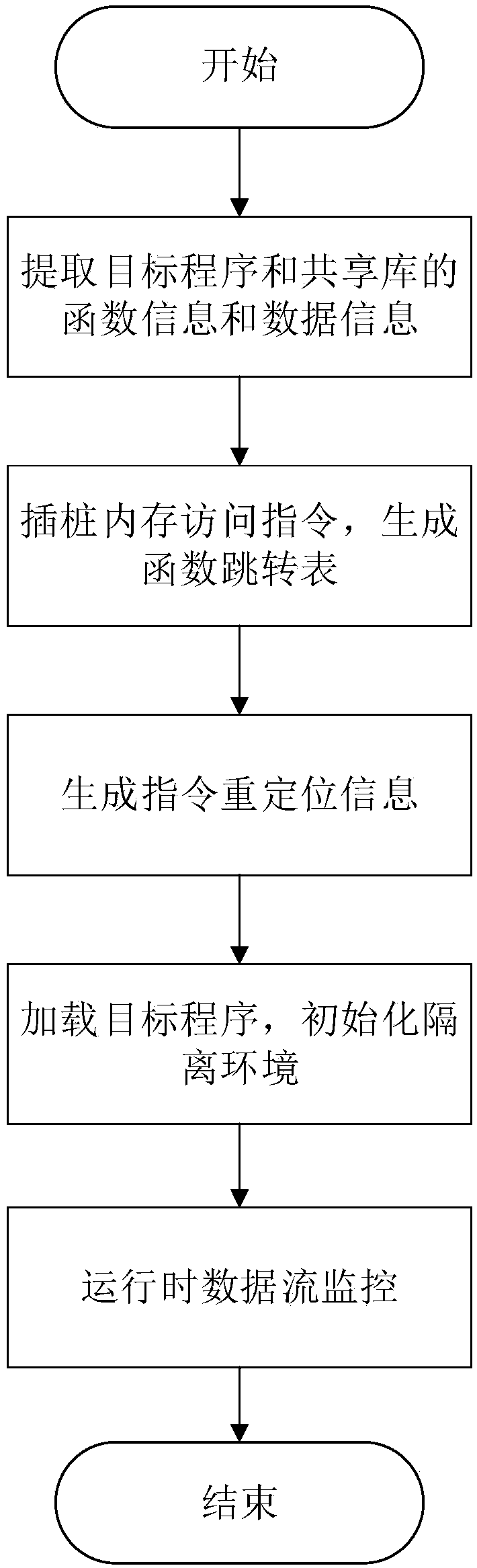
ActiveCN108090346AImprove defenseReduce performance overheadPlatform integrity maintainanceSystem safetyCode reuse
The invention discloses a data flow monitoring-based code reuse attack defending method and system, and belongs to the technical field of system security. The method comprises the steps of firstly extracting function and data information through source codes of a target program and a shared library; then analyzing intermediate language codes; identifying a memory access instruction in the target program and the shared library; and performing instrumentation on the instruction and generating a function jumping table and instruction relocating information. During target program loading, segments, stacks and heaps of the target program and the shared library are mapped to corresponding regions of a memory address space, and an isolation environment is set. During target program operation, ina mode of monitoring abnormal data flow, an attacker is prevented from performing a search in an isolation region, so that code reuse attack is prevented. The invention furthermore discloses a data flow monitoring-based code reuse attack defending system. The method and the system are suitable for code reuse attack defending in an X86_64 platform, so that huge loss caused by attack can be avoided.
Owner:HUAZHONG UNIV OF SCI & TECH
Regular expression memory region with integrated regular expression engine
ActiveUS20150032988A1Reduce performance overheadMemory architecture accessing/allocationMemory adressing/allocation/relocationMemory addressMain processing unit
A method and circuit arrangement selectively perform regular expression matching in connection with accessing data with a processing unit based upon one or more regular expression matching-related attributes stored in a memory address translation data structure such as an Effective To Real Translation (ERAT) or Translation Lookaside Buffer (TLB). A regular expression matching-related attribute in such a data structure may be used to control whether data being communicated between the processing unit and a communications bus is routed through an expression engine integrated with the processing unit such that regular expression matching may be performed in association with the data communication.
Owner:MEDIATEK INC
Method, Device and System for Recognizing Network Behavior of Program
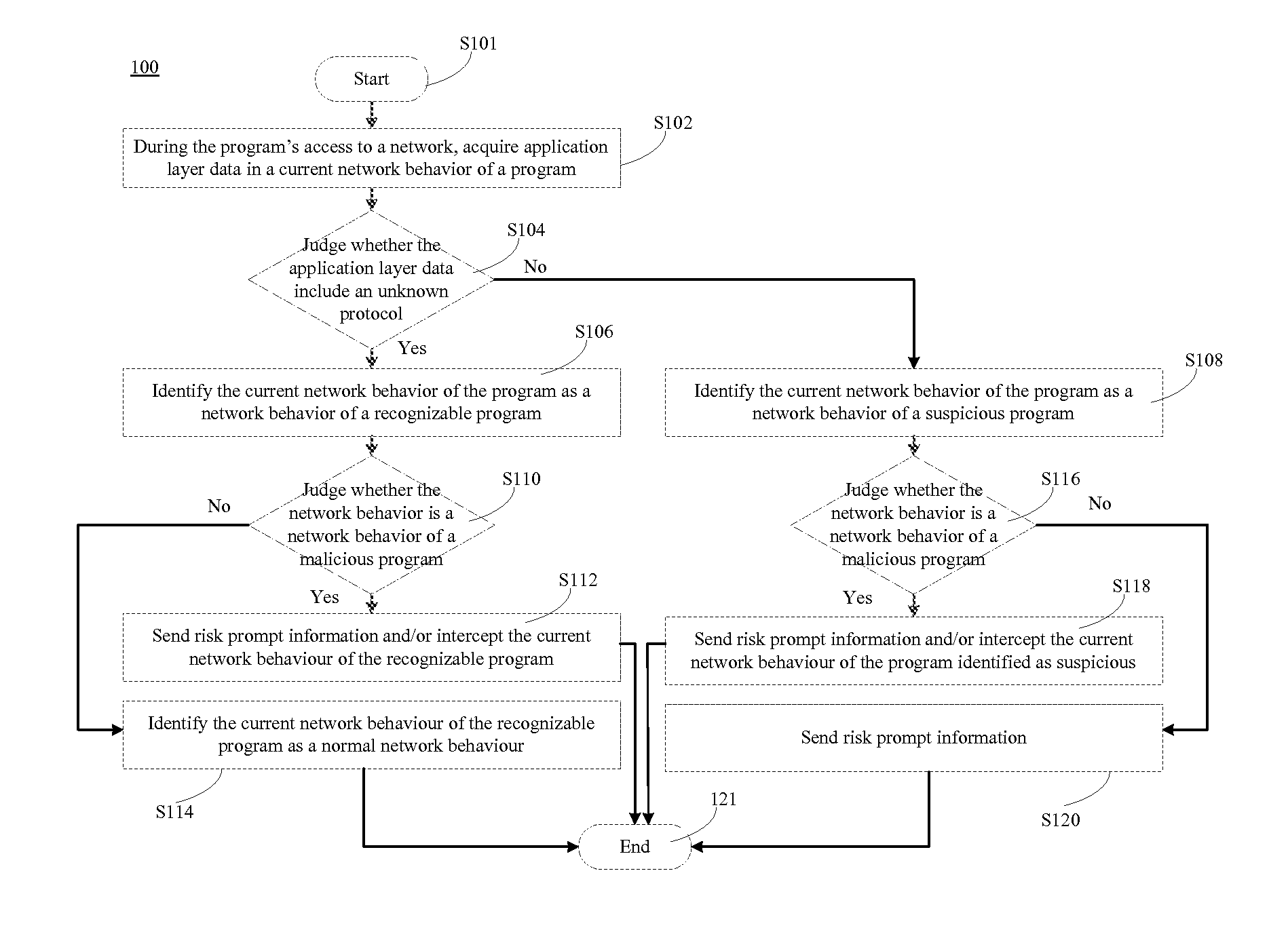
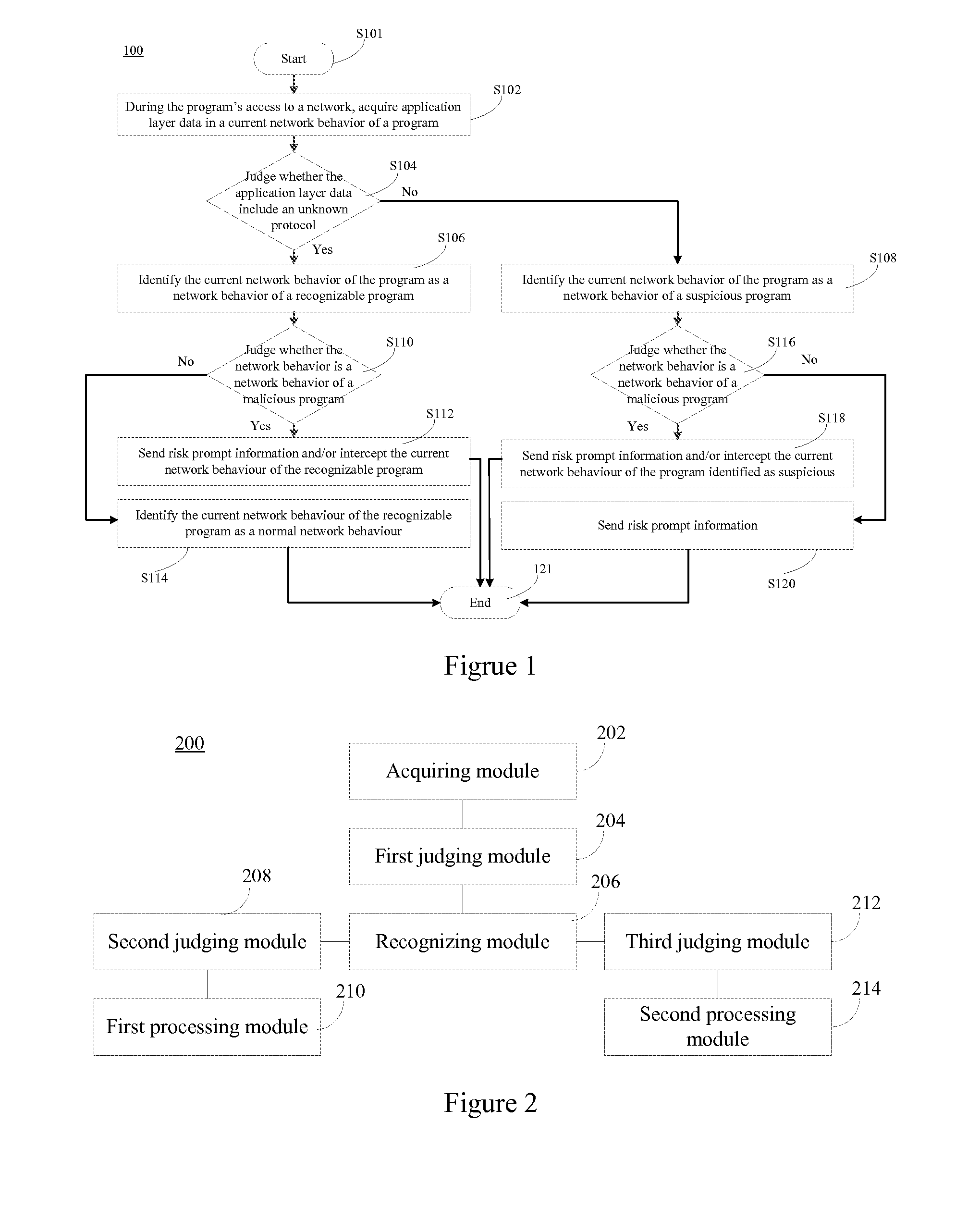
ActiveUS20150350232A1Accurate identificationImprove network securityMemory loss protectionError detection/correctionNetwork behaviorProtocol Application
The present disclosure discloses a method, device and system for recognizing network behavior of a program. The method comprises: during the program's access to a network, acquiring application layer data in a current network behavior of the program; judging whether the application layer data includes an unknown protocol; if protocols in the application layer data are all known protocols, identifying the current network behavior of the program as a network behavior of a recognizable program; and if the application layer data includes an unknown protocol, identifying the current network behavior of the program as a network behavior of a suspicious program. As such, a accurate recognition of a network behavior of a program is realized, the network behavior of the program including an unknown protocol is identified as a network behavior of a suspicious program, risk prompt information can be sent to a user, and a final selection is performed by the user, thereby solving the problem that conventional solutions for recognizing a network behavior of a program cannot accurately recognize a network behavior of a newly-emerging or new variant program.
Owner:BEIJING QIHOO TECH CO LTD
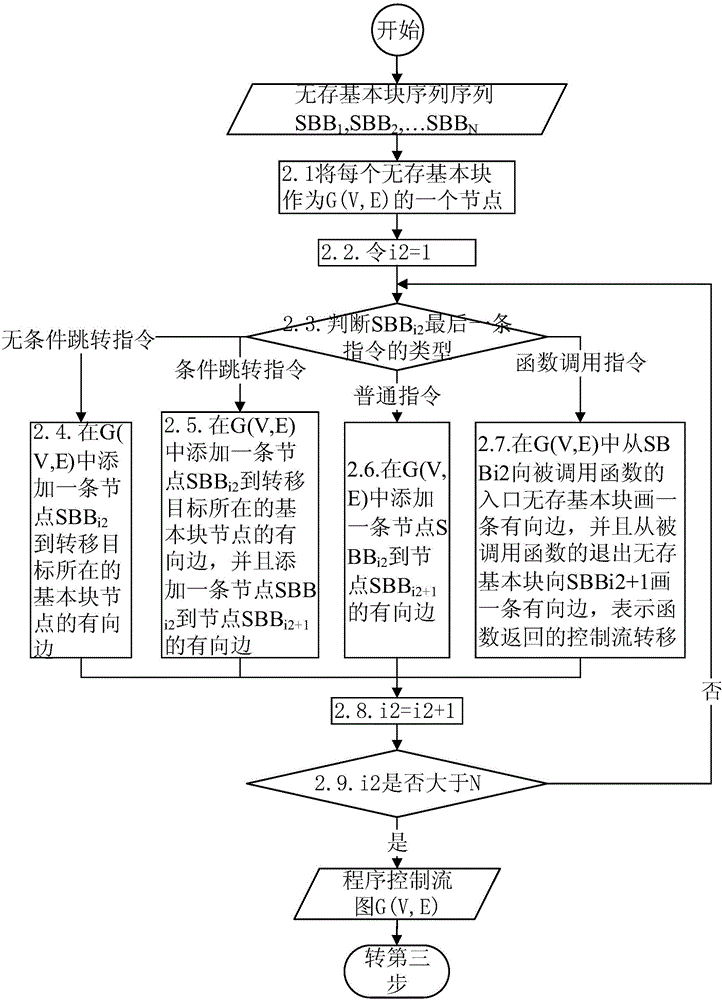
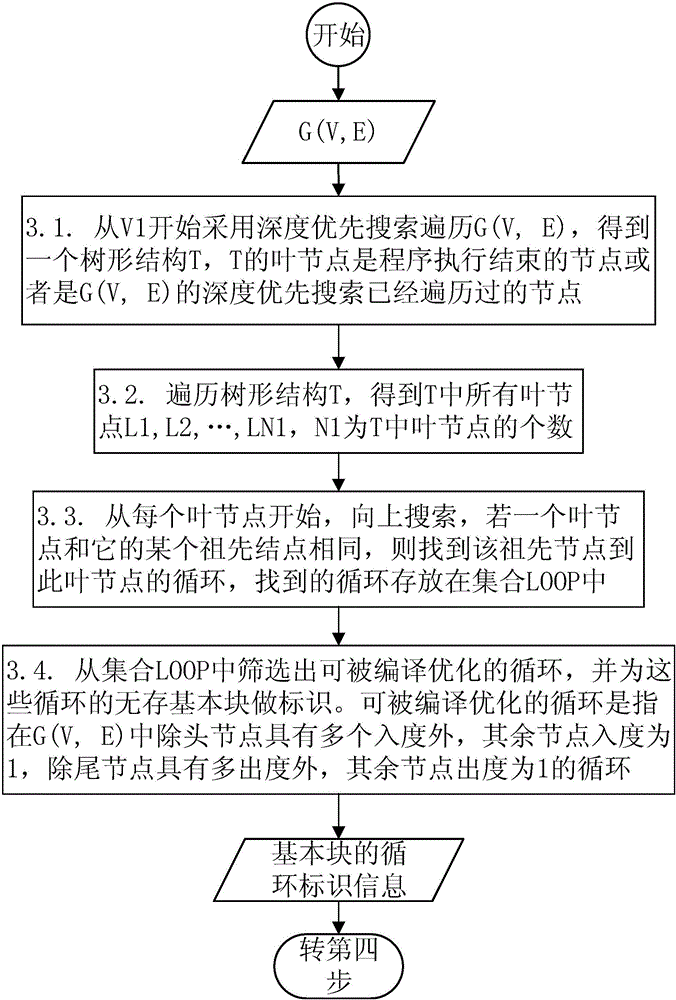
Linear assembly instruction diversity conversion based DSP soft error detection method
ActiveCN106021040ACapable of soft error detectionDoes not require multithreading supportFaulty hardware testing methodsSoft error detectionBasic block
The invention discloses a linear assembly instruction diversity conversion based DSP soft error detection method which can solve the problem that the conventional DSP soft error detection methods are large in performance cost. The DSP soft error detection method includes: dividing a program into storeless basic blocks, establishing a program control flow diagram, recognizing circulations, screening out circulations capable of arranging a software pipeline; reinforcing the program, adding error detection instructions to the program, performing equivalent conversion on a part of instructions through an instruction diversity conversion method, and performing double calculation on the rest instructions, inserting the detection instructions before instruction storage and instruction jumping, optimizing the detection instructions through DSP instruction condition execution characters and the equivalent conversion method, and reducing the performance cost due to reinforcement through the delay error processing method for the circulations capable of arranging the software pipeline; and executing the reinforcement program, and detecting soft errors during operation. The DSP soft error detection method is a DSP reinforcement method of pure software, is high in detection rate of date errors, and is low in performance cost of reinforcement.
Owner:NAT UNIV OF DEFENSE TECH
Computer boot operation utilizing targeted boot diagnostics
InactiveUS20070245170A1Eliminate needReduce performance overheadDetecting faulty hardware by power-on testData processing applicationsInitEngineering
An apparatus, program product and method utilize targeted boot diagnostics in connection with a boot operation to automate the handling of hardware failures detected during startup or initialization of a computer. In particular, in response to detection of a failure after initiation of and during performance of a boot operation, a targeted diagnostic operation is initiated on at least one hardware device in the computer in response to detecting the failure, such that after the targeted diagnostic operation is initiated, the boot operation may be completed.
Owner:INT BUSINESS MASCH CORP
Realization method of main memory database under host system
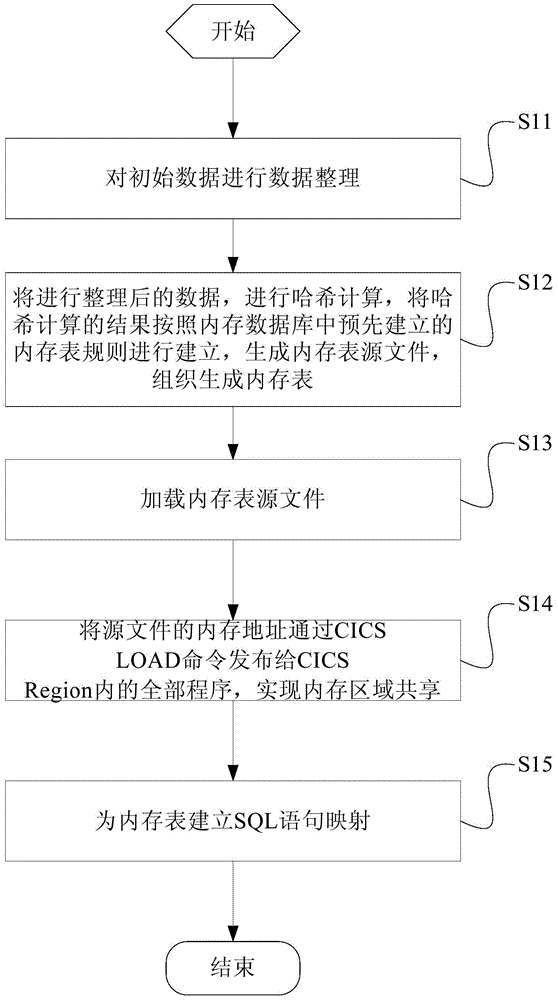
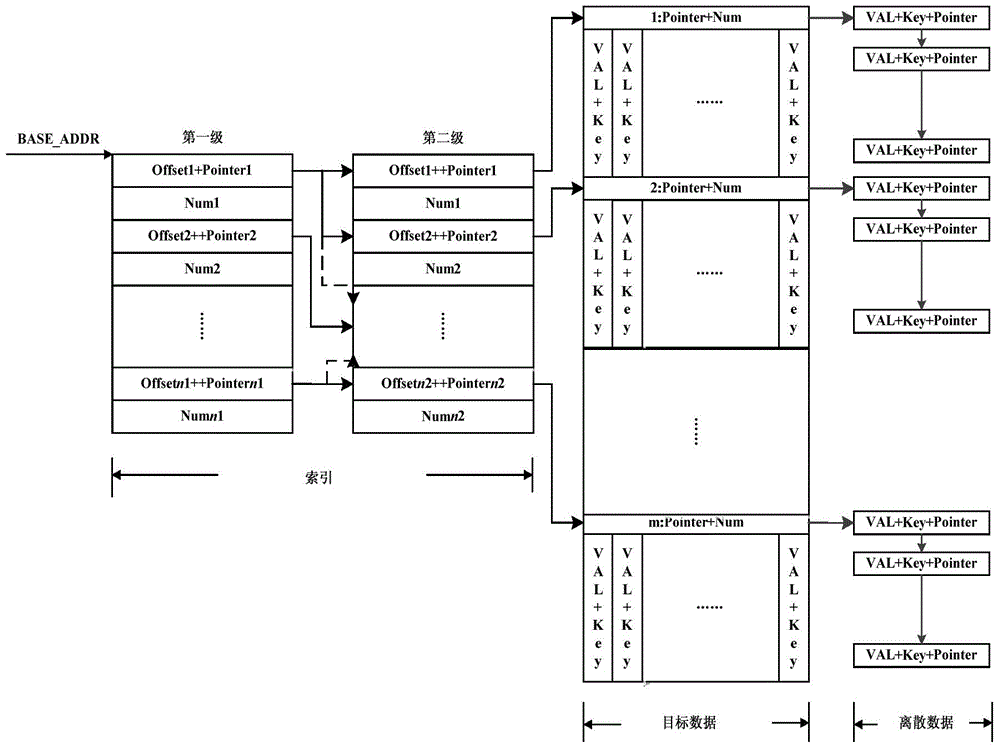
ActiveCN104615750AReduce performance overheadMeet performance requirementsSpecial data processing applicationsIn-memory databaseSentence mapping
The invention discloses a realization method of a main memory database under a host system. The realization method includes arranging initial data; performing Hash computing on the data after being arranged, subjecting a result of Hash computing to building according to memory table rules pre-established in the main memory database to generate a memory table source file, and organizing to generate a memory table; loading the memory table source file, setting a downloading instruction CICS LOAD, sending an entry address of the memory table source file to a program through CICS LOAD when a program in a CICS Region calls the main memory database, and establishing SQL sentence mapping. The above process shows that in the realization method, indexes and data in the memory table are constructed in a memory, and performance expenditure of data exchange between the memory and a magnetic disk is reduced in the process of access, so that access performance is higher than the main memory database, and performance requirements when application accesses a hotlist can be further met.
Owner:AGRICULTURAL BANK OF CHINA
Similarity detection method for unknown vulnerability discovery based on patch information
ActiveCN108268777AReduce distractionsFix false positivesPlatform integrity maintainanceFeature vectorAlgorithm
The invention relates to a similarity detection method for unknown vulnerability discovery based on patch information. The method comprises steps as follows: a known vulnerability function and a patchfunction after patching are sliced, and slices containing vulnerability related statements and slices containing patch statements are generated; variable names, variable types and function call namesof a to-be-detected function, the vulnerability slices and the patch slices are subjected to symbol normalization; the to-be-detected function, the vulnerability slices and the patch slices are mapped to vector space to generate to-be-detected function characteristic vectors, vulnerability characteristic vectors and patch characteristic vectors, one vector is formed by each of the to-be-detectedfunction characteristic vectors, the vulnerability characteristic vectors and the patch characteristic vectors, and a value of each dimension of the one vector represents a product of the number of appearing times of the characteristic statement in the function and TF-IDF weight; after generation of the characteristic vectors, similarity of the characteristic vectors is calculated and sequencing is performed, and whether unknown vulnerability with the characteristics similar to those of known vulnerability in a to-be-detected function set is judged. According to the method, disturbance of vulnerability unrelated statements can be effectively reduced, and detection accuracy is improved.
Owner:RENMIN UNIVERSITY OF CHINA
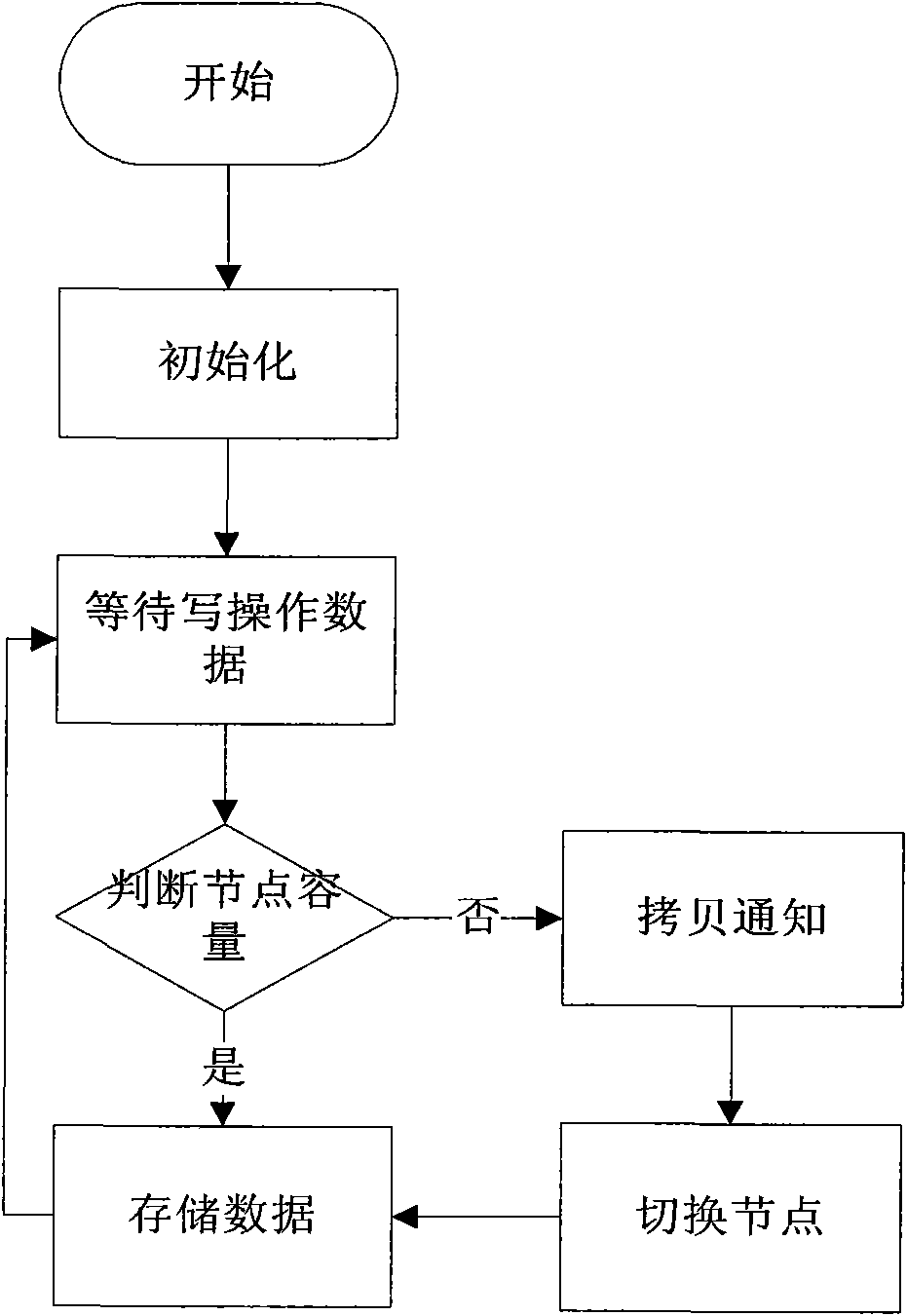
Automatic simplified-configured self-adaptation optimization method
InactiveCN104461914AIncrease profitReduce performance overheadMemory adressing/allocation/relocationAdaptive optimizationSelf adaptive
The invention discloses an automatic simplified-configured self-adaptation optimization method which comprises the following steps that S1. during initial running of a storing system, data blocks with fixed size are used for simplified distribution; S2. during running, the feature of a data IO request which is sent to the storing system is subjected to statistics; S3. according to the IO request statistics results, the size of the data blocks which are subjected to simplified distribution is adjusted automatically; S4. during system running, the space using situation of large data blocks is recorded, and meanwhile data migration and data block merging are carried out; and S5. when the storing system receives a space recycling request, recyclable data blocks are recycled, and data block merging is carried out. The distribution size of the data blocks can be adjusted automatically according to the storing system practical service requirement, on the basis that the requirement of management according to needs of a disk space is met, extra storing system performance expenditure caused by data block distribution is lowered, the disk space using rate is improved, and accordingly the storing system is suitable for various service application scenarios.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Data transmission method, device and equipment
InactiveCN110392047AReduce power consumptionReduce performance overheadTransmissionDigital output to display deviceData transmissionPower consumption
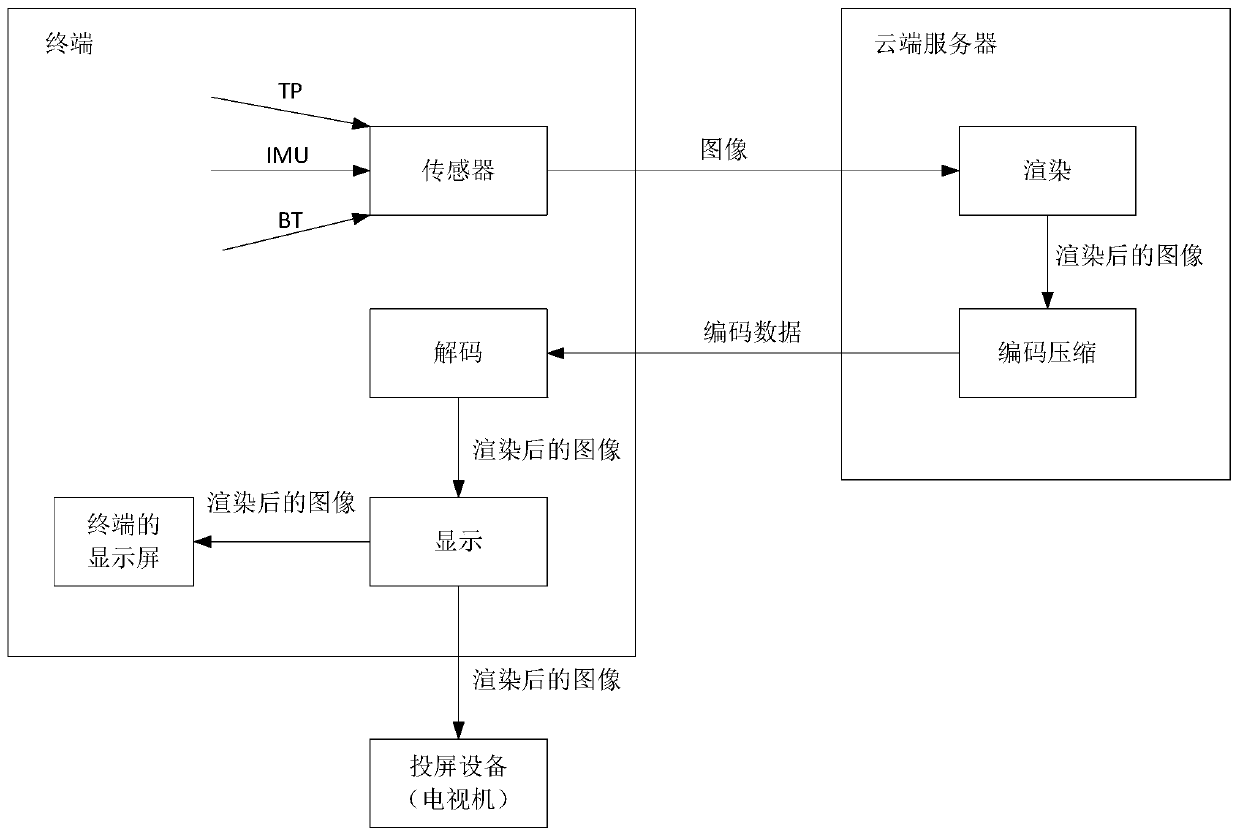
The embodiment of the invention provides a data transmission method, device and equipment, and the method comprises the steps that a terminal directly carries out the wireless screen projection protocol packaging of first data in an unvarnished transmission mode after receiving the first data from a server, obtains second data, and transmits the second data to wireless screen projection equipment.Since the terminal does not need to decode the first data and does not need to carry out secondary encoding on the first data when transmitting the first data to the screen projection equipment, thephenomenon of picture delay in the wireless screen projection process can be avoided, and the power consumption and the performance overhead of the terminal can be reduced.
Owner:HUAWEI TECH CO LTD
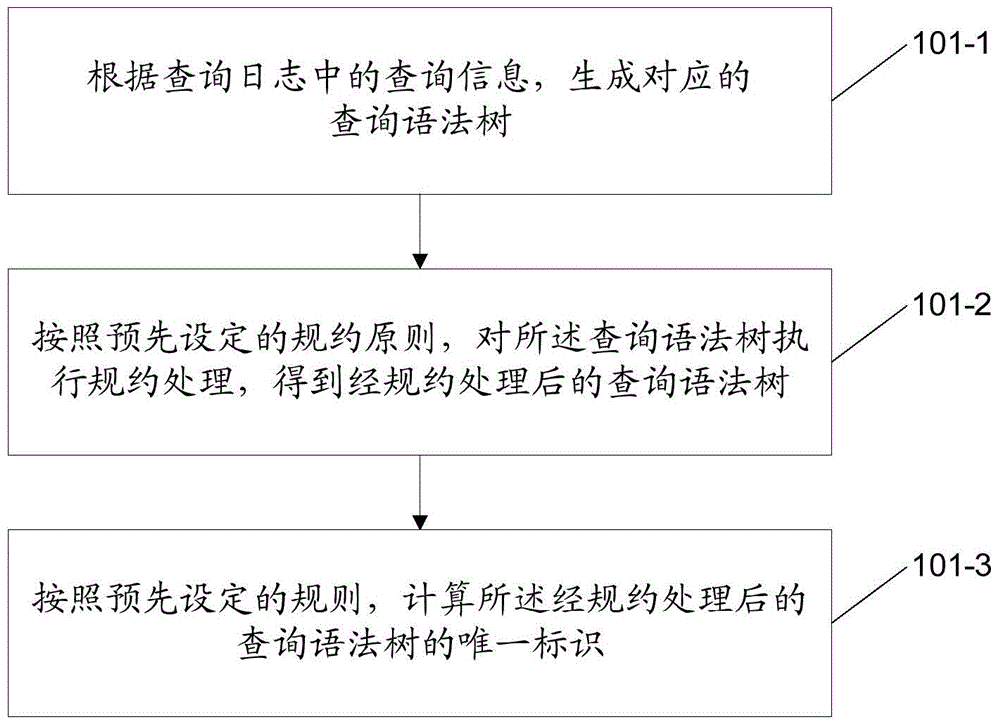
Search method, index data generation method and device on the basis of static Cache
ActiveCN105335402AReduce performance overheadImprove retrieval performanceSpecial data processing applicationsUnique identifierClient-side
The invention discloses a search method and device on the basis of static Cache, an index data generation method and device used for static Cache, and a method and a device used for obtaining a query syntax tree identifier. The search method on the basis of the static Cache comprises the following steps: receiving a search request of a client side; according to query information in the search request, generating a query syntax tree; looking up a pre-generated high-frequency syntax tree from the query syntax tree, and replacing parts of query information corresponding to the high-frequency syntax tree in the query information with a unique identifier, which is pre-calculated, of the high-frequency syntax tree according to a sequence from a root node to a leaf node, wherein the unique identifier of the high-frequency syntax tree is used for quickly recalling a search result corresponding to parts of query information from an index database in a retrieval stage; and according to the replaced query information, retrieving the index database, and returning the search result to the client side. The above method can reduce performance cost generated when a search engine carries out inverted recalling, and improves the retrieval performance of the search engine.
Owner:ALIBABA GRP HLDG LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com